#computer programming assignment services
Explore tagged Tumblr posts
Text
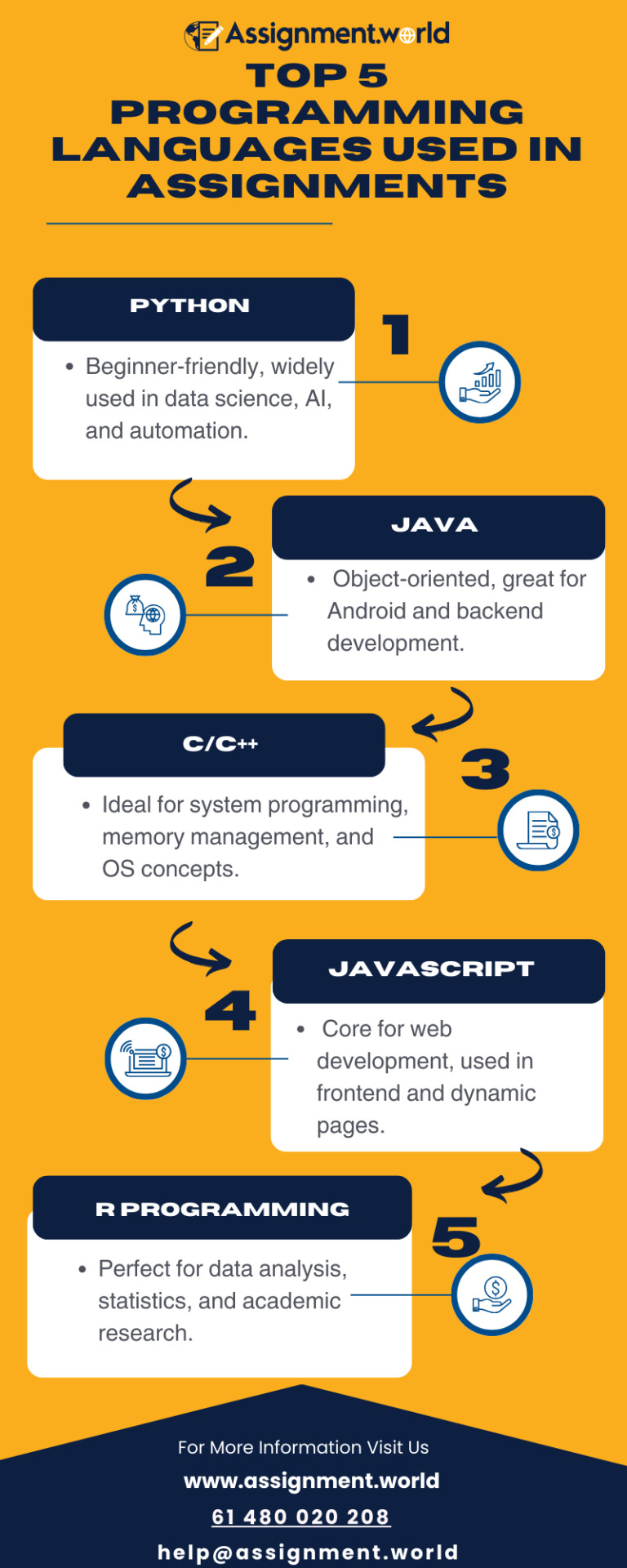
Discover the Top 5 Programming Languages Used in Assignments with this informative infographic. Whether you're a student tackling complex coding tasks or exploring popular languages for academic projects, this visual guide breaks down the most commonly assigned programming languages—Python, Java, C/C++, JavaScript, and R—along with their core features and use cases. Ideal for computer science students and programming beginners, this infographic helps you understand which languages dominate the classroom and why they matter. Perfect for anyone seeking insight into trending languages and computer programming assignment help.
0 notes
Text
Twinkump Linkdump

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in SAN DIEGO at MYSTERIOUS GALAXY next MONDAY (Mar 24), and in CHICAGO with PETER SAGAL on Apr 2. More tour dates here.

I have an excellent excuse for this week's linkdump: I'm in Germany, but I'm supposed to be in LA, and I'm not, because London Heathrow shut down due to a power-station fire, which meant I spent all day yesterday running around like a headless chicken, trying to get home in time for my gig in San Diego on Monday (don't worry, I sorted it):
https://www.mystgalaxy.com/32425Doctorow
Therefore, this is 30th linkdump, in which I collect the assorted links that didn't make it into this week's newsletters. Here are the other 29:
https://pluralistic.net/tag/linkdump/
I always like to start and end these 'dumps with some good news, which isn't easy in these absolutely terrifying times. But there is some good news: Wil Wheaton has announced his new podcast, a successor of sorts to the LeVar Burton Reads podcast. It's called "It's Storytime" and it features Wil reading his favorite stories handpicked from science fiction magazines, including On Spec, the magazine that bought my very first published story (I was 16, it ran in their special youth issue, it wasn't very good, but boy did it mean a lot to me):
https://wilwheaton.net/podcast/
Here's some more good news: a court has found (again!) that works created by AI are not eligible for copyright. This is the very best possible outcome for people worried about creators' rights in the age of AI, because if our bosses can't copyright the botshit that comes out of the "AI" systems trained on our work, then they will pay us:
https://www.yahoo.com/news/us-appeals-court-rejects-copyrights-171203999.html
Our bosses hate paying us, but they hate the idea of not being able to stop people from copying their entertainment products so! much! more! It's that simple:
https://pluralistic.net/2023/08/20/everything-made-by-an-ai-is-in-the-public-domain/
This outcome is so much better than the idea that AI training isn't fair use – an idea that threatens the existence of search engines, archiving, computational linguistics, and other clearly beneficial activities. Worse than that, though: if we create a new copyright that allows creators to prevent others from scraping and analyzing their works, our bosses will immediately alter their non-negotiable boilerplate contracts to demand that we assign them this right. That will allow them to warehouse huge troves of copyrighted material that they will sell to AI companies who will train models designed to put us on the breadline (see above, re: our bosses hate paying us):
https://pluralistic.net/2024/03/13/hey-look-over-there/#lets-you-and-he-fight
The rights of archivists grow more urgent by the day, as the Trump regime lays waste to billions of dollars worth of government materials that were produced at public expense, deleting decades of scientific, scholarly, historical and technical materials. This is the kind of thing you might expect the National Archive or the Library of Congress to take care of, but they're being chucked into the meat-grinder as well.
To make things even worse, Trump and Musk have laid waste to the Institute of Museum and Library Services, a tiny, vital agency that provides funding to libraries, archives and museums across the country. Evan Robb writes about all the ways the IMLS supports the public in his state of Washington:
Technology support. Last-mile broadband connection, network support, hardware, etc. Assistance with the confusing e-rate program for reduced Internet pricing for libraries.
Coordinated group purchase of e-books, e-audiobooks, scholarly research databases, etc.
Library services for the blind and print-disabled.
Libraries in state prisons, juvenile detention centers, and psychiatric institutions.
Digitization of, and access to, historical resources (e.g., newspapers, government records, documents, photos, film, audio, etc.).
Literacy programming and support for youth services at libraries.
The entire IMLS budget over the next 10 years rounds to zero when compared to the US federal budget – and yet, by gutting it, DOGE is amputating significant parts of the country's systems that promote literacy; critical thinking; and universal access to networks, media and ideas. Put it that way, and it's not hard to see why they hate it so.
Trying to figure out what Trump is up to is (deliberately) confusing, because Trump and Musk are pursuing a chaotic agenda that is designed to keep their foes off-balance:
https://www.wired.com/story/elon-musk-donald-trump-chaos/
But as Hamilton Nolan writes, there's a way to cut through the chaos and make sense of it all. The problem is that there are a handful of billionaires who have so much money that when they choose chaos, we all have to live with it:
The significant thing about the way that Elon Musk is presently dismantling our government is not the existence of his own political delusions, or his own self-interested quest to privatize public functions, or his own misreading of economics; it is the fact that he is able to do it. And he is able to do it because he has several hundred billion dollars. If he did not have several hundred billion dollars he would just be another idiot with bad opinions. Because he has several hundred billion dollars his bad opinions are now our collective lived experience.
https://www.hamiltonnolan.com/p/the-underlying-problem
We actually have a body of law designed to prevent this from happening. It's called "antitrust" and 40 years ago, Jimmy Carter decided to follow the advice of some of history's dumbest economists who said that fighting monopolies made the economy "inefficient." Every president since, up to – but not including – Biden, did even more to encourage monopolization and the immense riches it creates for a tiny number of greedy bastards.
But Biden changed that. Thanks to the "Unity Taskforce" that divided up the presidential appointments between the Democrats' corporate wing and the Warren/Sanders wing, Biden appointed some of the most committed, effective trustbusters we'd seen for generations:
https://pluralistic.net/2022/10/18/administrative-competence/#i-know-stuff
After Trump's election, there was some room for hope that Trump's FTC would continue to pursue at least some of the anti-monopoly work of the Biden years. After all, there's a sizable faction within the MAGA movement that hates (some) monopolies:
https://pluralistic.net/2025/01/24/enforcement-priorities/#enemies-lists
But last week, Trump claimed to have illegally fired the two Democratic commissioners on the FTC: Alvaro Bedoya and Rebecca Slaughter. I stan both of these commissioners, hard. When they were at the height of their powers in the Biden years, I had the incredible, disorienting experience of getting out of bed, checking the headlines, and feeling very good about what the government had just done.
Trump isn't legally allowed to fire Bedoya and Slaughter. Perhaps he's just picking this fight as part of his chaos agenda (see above). But there are some other pretty good theories about what this is setting up. In his BIG newsletter, Matt Stoller proposes that Trump is using this case as a wedge, trying to set a precedent that would let him fire Federal Reserve Chair Jerome Powell:
https://www.thebignewsletter.com/p/why-trump-tried-to-fire-federal-trade
But perhaps there's more to it. Stoller just had Commissioner Bedoya on Organized Money, the podcast he co-hosts with David Dayen, and Bedoya pointed out that if Trump can fire Democratic commissioners, he can also fire Republican commissioners. That means that if he cuts a shady deal with, say, Jeff Bezos, he can order the FTC to drop its case against Amazon and fire the Republicans on the commission if they don't frog when he jumps:
https://www.organizedmoney.fm/p/trumps-showdown-at-the-ftc-with-commissioner
(By the way, Organized Money is a fantastic podcast, notwithstanding the fact that they put me on the show last week:)
https://audio.buzzsprout.com/6f5ly01qcx6ijokbvoamr794ht81
The future that our plutocrat overlords are grasping for is indeed a terrible one. You can see its shape in the fantasies of "liberatarian exit" – the seasteads, free states, and other assorted attempts to build anarcho-capitalist lawless lands where you can sell yourself into slavery, or just sell your kidneys. The best nonfiction book on libertarian exit is Raymond Criab's 2022 "Adventure Capitalism," a brilliant, darkly hilarious and chilling history of every time a group of people have tried to found a nation based on elevating selfishness to a virtue:
https://pluralistic.net/2022/06/14/this-way-to-the-egress/#terra-nullius
If Craib's book is the best nonfiction volume on the subject of libertarian exit, then Naomi Kritzer's super 2023 novel Liberty's Daughter is the best novel about life in a libertopia – a young adult novel about a girl growing up in the hell that would be life with a Heinlein-type dad:
https://pluralistic.net/2023/11/21/podkaynes-dad-was-a-dick/#age-of-consent
But now this canon has a third volume, a piece of design fiction from Atelier Van Lieshout called "Slave City," which specs out an arcology populated with 200,000 inhabitants whose "very rational, efficient and profitable" arrangements produce €7b/year in profit:
https://www.archdaily.com/30114/slave-city-atelier-van-lieshout
This economic miracle is created by the residents' "voluntary" opt-in to a day consisting of 7h in an office, 7h toiling in the fields, 7h of sleep, and 3h for "leisure" (e.g. hanging out at "The Mall," a 24/7, 26-storey " boundless consumer paradise"). Slaves who wish to better themselves can attend either Female Slave University or Male Slave University (no gender controversy in Slave City!), which run 24/7, with 7 hours of study, 7 hours of upkeep and maintenance on the facility, 7h of sleep, and, of course, 3h of "leisure."
The field of design fiction is a weird and fertile one. In his traditional closing keynote for this year's SXSW Interactive festival, Bruce Sterling opens with a little potted history of the field since it was coined by Julian Bleeker:
https://bruces.medium.com/how-to-rebuild-an-imaginary-future-2025-0b14e511e7b6
Then Bruce moves on to his own latest design fiction project, an automated poetry machine called the Versificatore first described by Primo Levi in an odd piece of science fiction written for a newspaper. The Versificatore was then adapted to the screen in 1971, for an episode of an Italian sf TV show based on Levi's fiction:
https://www.youtube.com/watch?v=tva-D_8b8-E
And now Sterling has built a Versificatore. The keynote is a sterlingian delight – as all of his SXSW closers are. It's a hymn to the value of "imaginary futures" and an instruction manual for recovering them. It could not be more timely.
Sterling's imaginary futures would be a good upbeat note to end this 'dump with, but I've got a real future that's just as inspiring to close us out with: the EU has found Apple guilty of monopolizing the interfaces to its devices and have ordered the company to open them up for interoperability, so that other manufacturers – European manufacturers! – can make fully interoperable gadgets that are first-class citizens of Apple's "ecosystem":
https://www.reuters.com/technology/apple-ordered-by-eu-antitrust-regulators-open-up-rivals-2025-03-19/
It's a good reminder that as America crumbles, there are still places left in the world with competent governments that want to help the people they represent thrive and prosper. As the Prophet Gibson tells us, "the future is here, it's just not evenly distributed." Let's hope that the EU is living in America's future, and not the other way around.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/03/22/omnium-gatherum/#storytime

Image: TDelCoro https://www.flickr.com/photos/tomasdelcoro/48116604516/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#bruce sterling#design fiction#sxsw#Atelier Van Lieshout#libertopia#libertarian exit#wil wheaton#sf#science fiction#podcasts#linkdump#linkdumps#apple#eu#antitrust#interop#interoperabilty#ai#copyright#law#glam#Institute of Museum and Library Services#libraries#museums#ftc#matt stoller#david dayen#alvaro bedoya#rebecca slaughter
86 notes
·
View notes
Text

Part of the DHMC's job is to test hypnotic products, entities, and phenomena for research, categorization, and, regulation.
They used to test them on themselves or on a small dedicated test group. But nowadays they have the DHMC Volunteer Program.
The public can sign up as test subjects for a whole host of experiments. Considering the number of people with hypnosis kinks in Masilaw, this program is really successful.
You are compensated for your time and are provided support for any lingering side effects. (It's also cheaper for the DHMC to just test on random civilians than to hire actual test subjects.)
The DHMC also doubles as a kind of community service, where people who commit petty hypnotic crimes get assigned as "volunteers". There is also regular hypnotic community service but the DHMC isn't in charge of that.
---------------
Also, random lore refresher, Dax and Jasper are co-heads of the Hypnotic Technology Division. They are boyfriends and they get into a lot of stupid hijinks together.
Dax is more engineering-focused and Jasper is more coding-and-computer-focused.
Jasper looks like the smarter one, but don't be fooled they are both idiots when put together.
226 notes
·
View notes
Text
The Story of KLogs: What happens when an Mechanical Engineer codes
Since i no longer work at Wearhouse Automation Startup (WAS for short) and havnt for many years i feel as though i should recount the tale of the most bonkers program i ever wrote, but we need to establish some background
WAS has its HQ very far away from the big customer site and i worked as a Field Service Engineer (FSE) on site. so i learned early on that if a problem needed to be solved fast, WE had to do it. we never got many updates on what was coming down the pipeline for us or what issues were being worked on. this made us very independent
As such, we got good at reading the robot logs ourselves. it took too much time to send the logs off to HQ for analysis and get back what the problem was. we can read. now GETTING the logs is another thing.
the early robots we cut our teeth on used 2.4 gHz wifi to communicate with FSE's so dumping the logs was as simple as pushing a button in a little application and it would spit out a txt file
later on our robots were upgraded to use a 2.4 mHz xbee radio to communicate with us. which was FUCKING SLOW. and log dumping became a much more tedious process. you had to connect, go to logging mode, and then the robot would vomit all the logs in the past 2 min OR the entirety of its memory bank (only 2 options) into a terminal window. you would then save the terminal window and open it in a text editor to read them. it could take up to 5 min to dump the entire log file and if you didnt dump fast enough, the ACK messages from the control server would fill up the logs and erase the error as the memory overwrote itself.
this missing logs problem was a Big Deal for software who now weren't getting every log from every error so a NEW method of saving logs was devised: the robot would just vomit the log data in real time over a DIFFERENT radio and we would save it to a KQL server. Thanks Daddy Microsoft.
now whats KQL you may be asking. why, its Microsofts very own SQL clone! its Kusto Query Language. never mind that the system uses a SQL database for daily operations. lets use this proprietary Microsoft thing because they are paying us
so yay, problem solved. we now never miss the logs. so how do we read them if they are split up line by line in a database? why with a query of course!
select * from tbLogs where RobotUID = [64CharLongString] and timestamp > [UnixTimeCode]
if this makes no sense to you, CONGRATULATIONS! you found the problem with this setup. Most FSE's were BAD at SQL which meant they didnt read logs anymore. If you do understand what the query is, CONGRATULATIONS! you see why this is Very Stupid.
You could not search by robot name. each robot had some arbitrarily assigned 64 character long string as an identifier and the timestamps were not set to local time. so you had run a lookup query to find the right name and do some time zone math to figure out what part of the logs to read. oh yeah and you had to download KQL to view them. so now we had both SQL and KQL on our computers
NOBODY in the field like this.
But Daddy Microsoft comes to the rescue
see we didnt JUST get KQL with part of that deal. we got the entire Microsoft cloud suite. and some people (like me) had been automating emails and stuff with Power Automate

This is Microsoft Power Automate. its Microsoft's version of Scratch but it has hooks into everything Microsoft. SharePoint, Teams, Outlook, Excel, it can integrate with all of it. i had been using it to send an email once a day with a list of all the robots in maintenance.
this gave me an idea
and i checked
and Power Automate had hooks for KQL
KLogs is actually short for Kusto Logs
I did not know how to program in Power Automate but damn it anything is better then writing KQL queries. so i got to work. and about 2 months later i had a BEHEMOTH of a Power Automate program. it lagged the webpage and many times when i tried to edit something my changes wouldn't take and i would have to click in very specific ways to ensure none of my variables were getting nuked. i dont think this was the intended purpose of Power Automate but this is what it did
the KLogger would watch a list of Teams chats and when someone typed "klogs" or pasted a copy of an ERROR mesage, it would spring into action.
it extracted the robot name from the message and timestamp from teams
it would lookup the name in the database to find the 64 long string UID and the location that robot was assigned too
it would reply to the message in teams saying it found a robot name and was getting logs
it would run a KQL query for the database and get the control system logs then export then into a CSV
it would save the CSV with the a .xls extension into a folder in ShairPoint (it would make a new folder for each day and location if it didnt have one already)
it would send ANOTHER message in teams with a LINK to the file in SharePoint
it would then enter a loop and scour the robot logs looking for the keyword ESTOP to find the error. (it did this because Kusto was SLOWER then the xbee radio and had up to a 10 min delay on syncing)
if it found the error, it would adjust its start and end timestamps to capture it and export the robot logs book-ended from the event by ~ 1 min. if it didnt, it would use the timestamp from when it was triggered +/- 5 min
it saved THOSE logs to SharePoint the same way as before
it would send ANOTHER message in teams with a link to the files
it would then check if the error was 1 of 3 very specific type of error with the camera. if it was it extracted the base64 jpg image saved in KQL as a byte array, do the math to convert it, and save that as a jpg in SharePoint (and link it of course)
and then it would terminate. and if it encountered an error anywhere in all of this, i had logic where it would spit back an error message in Teams as plaintext explaining what step failed and the program would close gracefully
I deployed it without asking anyone at one of the sites that was struggling. i just pointed it at their chat and turned it on. it had a bit of a rocky start (spammed chat) but man did the FSE's LOVE IT.
about 6 months later software deployed their answer to reading the logs: a webpage that acted as a nice GUI to the KQL database. much better then an CSV file
it still needed you to scroll though a big drop-down of robot names and enter a timestamp, but i noticed something. all that did was just change part of the URL and refresh the webpage
SO I MADE KLOGS 2 AND HAD IT GENERATE THE URL FOR YOU AND REPLY TO YOUR MESSAGE WITH IT. (it also still did the control server and jpg stuff). Theres a non-zero chance that klogs was still in use long after i left that job
now i dont recommend anyone use power automate like this. its clunky and weird. i had to make a variable called "Carrage Return" which was a blank text box that i pressed enter one time in because it was incapable of understanding /n or generating a new line in any capacity OTHER then this (thanks support forum).
im also sure this probably is giving the actual programmer people anxiety. imagine working at a company and then some rando you've never seen but only heard about as "the FSE whos really good at root causing stuff", in a department that does not do any coding, managed to, in their spare time, build and release and entire workflow piggybacking on your work without any oversight, code review, or permission.....and everyone liked it
#comet tales#lazee works#power automate#coding#software engineering#it was so funny whenever i visited HQ because i would go “hi my name is LazeeComet” and they would go “OH i've heard SO much about you”
64 notes
·
View notes
Text

So sirens, right? The women in white we see doing various tasks for what seems like the Grid in general. I find them to be particularly interesting, because their role is somewhat vague, but clearly important. In Uprising, we see them working on behalf of CLU, but also various other events, like a street race. They seem to have a connection to games or sports in particular, usually showing up when it comes to public events. We see that they’re a key part of the armory.
But at the same time, they are clearly individuals that can leave their post. They have names, & individual appearances. Sirens are shown to have personalities & goals, sometimes ones that don’t align with their function.

This would make them seem like they’re similar to a normal program, where they have a designated function set by the system, but perhaps they are not representative of users like programs are, but instead apart of the Grid itself. Something like…UI elements in a game. They’re clearly designed with attractiveness in mind, & most of them are women, which I assume would be for the users’ benefit? They preform services, so I suppose they’re supposed to look nice.

However, to me it’s quite obvious that Castor fits the description of a siren. He has the all white attire, & he is a sort of…entertainment related program. He also has connections to Gem. It’s mentioned that he was around before the purge, which makes me think he could possibly be a siren that abandoned his assignment, & used his connections to the system to pivot to information brokering. If he is a siren, that would give evidence that sirens don’t have to be women exclusively. Perhaps male sirens have a slightly different assignment, or they’re just particularly rare.
Either way the gender binary is stupid so in my head sirens can be any gender. It doesn’t really make sense for computers to have binary gender identities anyway.
38 notes
·
View notes
Text
very brief torrent security primer
some brief comments on piracy safety for @goblin-thembo who has been asking a lot of questions in the notes of that post...
OK, so when you download a torrent, you are downloading some files. The BitTorrent protocol makes it almost impossible to substitute a different file than the one you request, but you have no way to be absolutely certain that the original file is 'safe' - that depends on the properties of the file, and what you do with it. Some types of file are safer than others.
Here's some jargon you may find useful.
torrent: a file that describes how to download some files through the BitTorrent protocol. we won't go into the technicalities, but when you load a torrent into your torrent client, you will connect to other people who have parts of the files, download the pieces, and reassemble the files you want.
seeding: providing a copy of the files in a torrent to other people.
ISP: Internet Service Provider, the company that connects you to the internet.
IP address: your computer's identity on a network, notably the public internet. When you connect to a website, they know your IP address. Your IP address is assigned by your ISP.
From an IP address, you can determine someone's broad geographical location (which country they're connected in) and which ISP they are using. You can contact the ISP, who will be able to associate it with a specific user.
swarm: the collection of users downloading or seeding a particular torrent.
VPN: Virtual Private Network, a relay service which hides your IP address from the public internet. People who connect to you will see the VPN's IP instead of your real IP. Your ISP will be able to know that you connected to a VPN, but not what you send through it. So they wouldn't be able to tell if you are using BitTorrent. VPNs usually cost a fairly small amount of money as a subscription service.
Threat model
In security we talk about a 'threat model', which is what you think you need to protect yourself from. There are two major threats when downloading files using BitTorrent.
copyright claims: your computer's IP is broadcast when you use BitTorrent. Copyright holders will often put 'sniffers' on the network which will monitor the IPs in the swarm of popular torrents. They will then send a takedown letter to your internet service provider (ISP), who will usually send you an email to stop sharing copyrighted media on their network, and then cut off your internet on multiple offences. This can easily be circumvented using a VPN. I strongly recommend using a VPN if you download any copyrighted content through BitTorrent.
attacks through the file you download: someone might upload a virus as a torrent, presenting it as a file you might be looking for (e.g. cracked software). So let's go over different types of file you might download and how they could be used to attack you.
Executable files, such as pirated software, are not safe. If you download a program and run it, you are potentially giving the author full control over your computer. So you should make damn sure the uploader is trustworthy. If you're downloading open source software from the maintainer's github release page, you're probably good. If you're downloading cracked art programs or games... good luck lol.
On a public torrent tracker, to which anyone can upload, there is no guarantee that any file is what anyone says. You have to make your own determination of which uploaders are trustworthy. I can't give you great advice on this, since I generally do not download cracked executables. For games, FitGirl Repacks is generally a pretty good source.
If you are on Windows, the default Windows Defender software should be used to scan any file you download. (Paid antivirus software is of somewhat dubious utility, often pushing ads and using CPU resources in its own right.) Fewer attackers will target desktop Linux or OSX, which doesn't mean you're guaranteed safe, but Windows is the biggest target as the most widely used operating system.
Videos, music and images are generally safe. I say 'generally' because it's possible, in theory, to create a video that exploits a vulnerability in your video player (e.g. mpv or VLC) and uses it to execute code. So far as I know this is largely theoretical, and known vulns have been patched, but make sure to keep your player up to date to mitigate against known vulnerabilities.
Any compressed archives (zip, rar, 7zip) can be used to create something called a 'zip bomb', which is a file which goes into an infinite loop when you try to decompress it, swallowing up more and more memory and hard drive space. I've never seen this actually be done, but it's possible. More subtle attacks would attempt to attack the program you use to decompress the file. Keep your software up to date to mitigate against known vulnerabilities.
Besides taking care about what you download, on Windows you should either not run your main account as an admin account, or make sure to set User Account Control to require a credentials check for admin operations, and also keep your operating system and software up to date. Make sure file extensions are visible so you don't get fooled by a file disguised as a different file type. And y'know, if the torrent tracker has comments, check to see if a lot of people are saying it's a virus.
What could happen if your computer gets infected? Well, they might use your computer to mine crypto at the cost of your CPU performance, they might encrypt and ransom your files, and they might steal your credentials for online services (including banking and the like). There are various measures you can take against this, such as making sure to encrypt sensitive data such as passwords, but the best defense is to not infect your computer in the first place.
The most likely time for people to upload viruses is when something is in high demand and there isn't a single authoritative high-quality source out yet.
Ultimately you get to decide what you consider an acceptable level of risk. There is no such thing as perfect safety. I would recommend using your own initiative to learn about computer security and not badger random tumblr users to explain it to you, but hopefully the above guidelines should help you avoid doing anything too dangerous.
189 notes
·
View notes
Text

U.S. Approves Foreign Military Sale for South Korean F-15K Upgrade
The State Department has approved the possible sale of components that will allow South Korea to upgrade its F-15K Slam Eagle fleet to a configuration similar to the F-15EX Eagle II.
Stefano D'Urso
F-15K upgrade
The U.S. State Department has approved on Nov.19, 2024, a possible Foreign Military Sale (FMS) to the Republic of Korea of components that will allow the upgrade of the country’s F-15K Slam Eagle fleet. The package, which has an estimated cost of $6.2 billion, follows the decision in 2022 to launch an upgrade program for the aircraft.
The State Department has approved the possible sale of components that will allow South Korea to upgrade its F-15K Slam Eagle fleet to a configuration similar to the F-15EX Eagle II.The F-15KThe new capabilities
The Slam Eagles are the mainstay of the Republic of Korea Air Force’s (ROKAF) multirole missions, with a particular ‘heavy hitting’ long-range strike role. According to the available data, the country operates 59 F-15Ks out of 61 which were initially fielded in 2005. In 2022, the Defense Acquisition Program Administration (DAPA) approved the launch of an upgrade program planned to run from 2024 to 2034.
In particular, the Defense Security Cooperation Agency’s (DSCA) FMS notice says a number of components were requested for the upgrade, including 96 Advanced Display Core Processor II (ADCP II) mission system computers, 70 AN/APG-82(v)1 Active Electronically Scanned Arrays (AESA) radars, seventy 70 AN/ALQ-250 Eagle Passive Active Warning Survivability System (EPAWSS) electronic warfare (EW) suites and 70 AN/AAR-57 Common Missile Warning Systems (CMWS).
In addition to these, South Korea will also get modifications and maintenance support, aircraft components and spares, consumables, training aids and the entire support package commonly associated with FMS. It is interesting to note that the notice also includes aerial refueling support and aircraft ferry support, so it is possible that at least the initial aircraft will be ferried to the United States for the modifications before the rest are modified in country.

A ROKAF F-15K Slam Eagle drops two GBU-31 JDAM bombs with BLU-109 warhead. (Image credit: ROKAF)
The components included in the possible sale will allow the ROKAF to upgrade its entire fleet of F-15Ks to a configuration similar to the new F-15EX Eagle II currently being delivered to the U.S. Air Force. Interestingly, the Korean configuration will also include the CMWS, currently not installed on the EX, so the F-15K will also require some structural modifications to add the blisters on each side of the canopy rail where the sensors are installed.
“This proposed sale will improve the Republic of Korea’s capability to meet current and future threats by increasing its critical air defence capability to deter aggression in the region and to ensure interoperability with US forces,” says the DSCA in the official notice.
The upgrade of the F-15K is part of a broader modernization of the ROKAF’s fighter fleet. In fact, the service is also upgrading its KF-16s Block 52 to the V configuration, integrating a new AESA radar, mission computer, self-protection suite, with works expected to be completed by 2025. These programs complement the acquisition of the F-35 Lightning II and the KF-21 Boramae.
Ulchi Freedom Shield 24

A ROKAF F-15K Slam Eagle, assigned to the 11th Fighter Wing at Daegu Air Base, takes off for a mission on Aug. 20, 2024. (Image credit: ROKAF)
The F-15K
The F-15K is a variant of the F-15E Strike Eagle built for the Republic of Korea Air Force’s (ROKAF) with almost half of the components manufactured locally. The aircraft emerged as the winner of the F-X fighter program against the Rafale, Typhoon and Su-35 in 2002, resulting in an order for 40 F-15s equipped with General Electric F110-129 engines. In 2005, a second order for 21 aircraft equipped with Pratt & Whitney F100-PW-229 engines was signed.
The Slam Eagle name is derived from the F-15K’s capability to employ the AGM-84H SLAM-ER standoff cruise missiles, with the Taurus KEPD 350K being another weapon exclusive to the ROKAF jet. The F-15K is employed as a fully multi-role aircraft and is considered ad one of the key assets of the Korean armed forces.
With the aircraft averaging an age of 16 years and expected to be in service until 2060, the Defense Acquisition Program Administration (DAPA) launched in 2022 an upgrade program for the F-15Ks. The upgrade, expected to run from 2024 to 2034, is committed to strengthening the mission capabilities and survivability of the jet.
The F-15K currently equips three squadrons at Daegu Air Base, in the southeast of the country. Although based far from the demilitarized zone (DMZ), the F-15K with its SLAM-ER and KEPD 350 missiles can still hit strategic targets deep behind North Korean borders.

An F-15K releases a Taurus KEPD 350K cruise missile. (Image credit: ROKAF)
The new capabilities
It is not yet clear if the F-15K will receive a new cockpit, since its configuration will be similar to the Eagle II. In fact, the F-15EX has a full glass cockpit equipped with a 10×19-inch touch-screen multifunction color display and JHMCS II both in the front and rear cockpit, Low Profile HUD in the front, stand-by display and dedicated engine, fuel and hydraulics display, in addition to the standard caution/warning lights, switches and Hands On Throttle-And-Stick (HOTAS) control.
Either way, the systems will be powered by the Advanced Display Core Processor II, reportedly the fastest mission computer ever installed on a fighter jet, and the Operational Flight Program Suite 9.1X, a customized variant of the Suite 9 used on the F-15C and F-15E, designed to ensure full interoperability of the new aircraft with the “legacy Eagles”.
The F-15K will be equipped with the new AN/APG-82(V)1 Active Electronically Scanned Array (AESA) radar. The radar, which has been developed from the APG-63(V)3 AESA radar of the F-15C and the APG-79 AESA radar of the F/A-18E/F, allows to simultaneously detect, identify and track multiple air and surface targets at longer ranges compared to mechanical radars, facilitating persistent target observation and information sharing for a better decision-making process.
F-15K upgrade

A ROKAF F-15K Slam Eagle takes off for a night mission during the Pitch Black 2024 exercise. (Image credit: Australian Defense Force)
The AN/ALQ-250 EPAWSS will provide full-spectrum EW capabilities, including radar warning, geolocation, situational awareness, and self-protection to the F-15. Chaff and flares capacity will be increased by 50%, with four more dispensers added in the EPAWSS fairings behind the tail fins (two for each fairing), for a total of 12 dispenser housing 360 cartridges.
EPAWSS is fully integrated with radar warning, geo-location and increased chaff and flare capability to detect and defeat surface and airborne threats in signal-dense and highly contested environments. Because of this, the system enables freedom of maneuver and deeper penetration into battlespaces protected by modern integrated air defense systems.
The AN/AAR-57 CMWS is an ultra-violet based missile warning system, part of an integrated IR countermeasures suite utilizing five sensors to display accurate threat location and dispense decoys/countermeasures. Although CMWS was initially fielded in 2005, BAE Systems continuously customized the algorithms to adapt to new threats and CMWS has now reached Generation 3.
@TheAviationist.com
21 notes
·
View notes
Text
Donald Trump vs. Kamala Harris: What It Means For IT Companies in India
When it comes to U.S. politics, Indian IT companies pay close attention, especially in races with heavyweights like former President Donald Trump and Vice President Kamala Harris. Each candidate’s policies can have ripple effects, impacting everything from visa policies to foreign direct investment and trade partnerships. For India’s booming IT sector, this rivalry could shape the future in major ways, particularly around outsourcing, talent mobility, and international tech collaborations. Here’s what each candidate brings to the table and what it could mean for the Indian IT industry.

Donald Trump’s Policies and Their Potential Impact
Trump’s “America First” agenda in his previous term brought significant shifts to immigration and outsourcing policies. His administration’s stance leaned toward prioritizing American jobs and reducing dependency on foreign workers, which affected the H-1B visa system, a crucial pathway for many skilled Indian IT professionals to work in the United States.
Key Areas to Watch if Trump Returns to Power
H-1B Visa Reform: Under Trump, the H-1B visa process became more stringent, with increased scrutiny on applications and tightened eligibility criteria. The approach aimed to reduce the number of visas granted, thus limiting the talent flow from India to the U.S. If Trump were to return, he might push for more reforms that could make it harder for Indian IT companies to place skilled workers in the U.S. for long-term assignments.
Outsourcing Policies: Trump’s stance on outsourcing often pointed toward creating incentives for American companies to move jobs back to the U.S. Although a complete shutdown of outsourcing is unlikely, a renewed Trump presidency might include policies that create hurdles or add costs to IT companies operating in India to reduce offshoring.
Taxation and Trade Barriers: Trump previously aimed to negotiate trade deals that reduced the U.S. trade deficit. Indian IT firms could face higher tariffs or restrictions if they want to establish more U.S. partnerships or expand operations on American soil.
Potential Upside: Some experts argue that Trump’s pro-business mindset and regulatory reforms, such as tax cuts, could indirectly benefit Indian IT companies if they lead to economic growth. With more American firms thriving, there may still be demand for Indian IT services, albeit in a more restrictive environment.
Kamala Harris’s Approach and Potential Influence
As the daughter of Indian immigrants, Kamala Harris’s connection to India is often highlighted. Her political stance, generally aligned with Democratic ideals, has favored immigrant rights, inclusivity, and technological advancement. Harris’s policies could potentially be more favorable for Indian IT companies, especially regarding immigration and tech collaborations.
Key Areas to Watch if Harris Gains More Influence
Visa and Immigration Reform: Harris has shown consistent support for immigration reform that would protect skilled foreign workers, including those from India. Her stance could bring improvements to the H-1B program, possibly increasing quotas or reducing the administrative burden on Indian IT professionals. This would be a welcome shift, making it easier for Indian firms to deploy talent in the U.S.
Tech Collaborations and Bilateral Ties: Given Harris’s strong ties to India, she could prioritize policies that foster U.S.-India tech partnerships. This could mean better collaboration on AI, cybersecurity, and cloud computing initiatives, offering Indian IT companies more opportunities to work alongside American firms on high-stakes projects.
Outsourcing Flexibility: Unlike Trump, Harris is less likely to advocate for aggressive curbs on outsourcing. While some regulations may still push companies to consider American workers first, it’s likely that Harris’s approach would be more balanced and encourage mutual growth, allowing Indian IT firms to continue serving U.S. clients without significant restrictions.
STEM Education and Training Initiatives: Harris may also introduce policies aimed at training and upskilling the American workforce. However, this approach could complement the Indian IT industry rather than limit it, as it could create avenues for partnerships in training programs or tech-driven education solutions.
Potential Upside: A Harris-led approach may result in more collaborative policies, boosting IT companies’ confidence in expanding U.S. operations. By maintaining a balanced approach to immigration and tech regulations, she could make it easier for Indian firms to both work in the U.S. and bring American investments back to India.
What This Means for Indian IT Companies
Indian IT companies like TCS, Infosys, and Wipro rely heavily on their U.S. clientele, and visa restrictions can significantly impact how they operate. Here’s a summary of what IT firms should expect:
Talent Mobility: A Trump-led administration might restrict it, while Harris would likely enhance it.
Outsourcing Stability: Trump could discourage offshoring, whereas Harris might adopt a more relaxed stance.
Trade Relations: Trump’s trade policies could become more protectionist, while Harris might lean toward fostering partnerships.
Adaptations and Strategic Moves for Indian IT Firms
Regardless of who wins, Indian IT companies should prepare by adopting a flexible approach:
Diversifying Talent Locations: With potential visa issues on the horizon, companies can consider moving talent to other locations, such as Canada or even remote setups within India, to serve U.S. clients.
Increasing Local Hiring in the U.S.: To align with possible hiring preferences, Indian firms may continue to hire more U.S.-based talent and offer training to local employees.
Emphasizing Partnerships and Joint Ventures: Both political paths present opportunities for tech collaborations. Indian firms could look for joint ventures with U.S. companies, fostering a partnership approach that aligns with potential regulations.
Final Thoughts
The outcome of a Trump vs. Harris contest would have unique implications for the Indian IT industry. Trump’s focus on reducing dependency on foreign talent and protecting U.S. jobs could mean tighter visa regulations and fewer opportunities for Indian workers in the U.S. Harris, on the other hand, could be a gateway to a more balanced, globally-minded U.S. policy that emphasizes collaboration and growth.
Regardless of the outcome, Indian IT firms have shown resilience and adaptability, adjusting to regulatory changes while remaining global leaders in IT services.
#technology#tech news#tech world#donald trump#kamala harris#usa news#us politics#election 2024#us elections
7 notes
·
View notes
Text
Furthermore, personal computers are no longer “universal machines”: their possibilities are limited by their assigned interfaces and programs so that they function only as the terminus of digital capitalism. This is justified as “user-friendliness”: anyone who uses a computer for reasons outside of research, development and production today is no longer supposed to understand what is going on in the device, and is instead made dependent on digital services. As with most productive forces within capitalism, the development of the computer is characterized by the fact that in dealing with them, the user does not learn any of the skills proper to the productive force. On the contrary, we find ourselves in a situation in which the widespread usability of computers is paired with an extensive digital illiteracy. Technological progress has become a source of social regression; the culturally pessimistic suspicion that smarter phones require ever dumber people is not that far-fetched.
this is such a silly argument that relies on vague concepts like 'digital literacy' while ignoring the change in what kind of people have access to computers now versus before and the purposes that they're being used for. someone who used a computer decades ago would be much more relatively likely to understand what's going on inside and directly programming it sure but they're also using it in a world where computers are used by much fewer people for more specific things. the people who went to a university with arpanet access in the 80s may be have gotten careers out of it and become the best C programmers, but that doesn't make them overall better at doing things with computers than kids fucking around online today.
14 notes
·
View notes
Text
My Experience with Database Homework Help from DatabaseHomeworkHelp.com
As a student majoring in computer science, managing the workload can be daunting. One of the most challenging aspects of my coursework has been database management. Understanding the intricacies of SQL, ER diagrams, normalization, and other database concepts often left me overwhelmed. That was until I discovered Database Homework Help from DatabaseHomeworkHelp.com. This service has been a lifesaver, providing me with the support and guidance I needed to excel in my studies.
The Initial Struggle
When I first started my database course, I underestimated the complexity of the subject. I thought it would be as straightforward as other programming courses I had taken. However, as the semester progressed, I found myself struggling with assignments and projects. My grades were slipping, and my confidence was waning. I knew I needed help, but I wasn't sure where to turn.
I tried getting assistance from my professors during office hours, but with so many students needing help, the time available was limited. Study groups with classmates were somewhat helpful, but they often turned into social gatherings rather than focused study sessions. I needed a more reliable and structured form of support.
Discovering DatabaseHomeworkHelp.com
One evening, while frantically searching for online resources to understand an especially tricky ER diagram assignment, I stumbled upon DatabaseHomeworkHelp.com. The website promised expert help on a wide range of database topics, from basic queries to advanced database design and implementation. Skeptical but hopeful, I decided to give it a try. It turned out to be one of the best decisions I’ve made in my academic career.
First Impressions
The first thing that struck me about DatabaseHomeworkHelp.com was the user-friendly interface. The website was easy to navigate, and I quickly found the section where I could submit my assignment. The process was straightforward: I filled out a form detailing my assignment requirements, attached the relevant files, and specified the deadline.
Within a few hours, I received a response from one of their database experts. The communication was professional and reassuring. They asked a few clarifying questions to ensure they fully understood my needs, which gave me confidence that I was in good hands.
The Quality of Help
What impressed me the most was the quality of the assistance I received. The expert assigned to my task not only completed the assignment perfectly but also provided a detailed explanation of the solutions. This was incredibly helpful because it allowed me to understand the concepts rather than just submitting the work.
For example, in one of my assignments, I had to design a complex database schema. The expert not only provided a well-structured schema but also explained the reasoning behind each table and relationship. This level of detail helped me grasp the fundamental principles of database design, something I had been struggling with for weeks.
Learning and Improvement
With each assignment I submitted, I noticed a significant improvement in my understanding of database concepts. The experts at DatabaseHomeworkHelp.com were not just solving problems for me; they were teaching me how to solve them myself. They broke down complex topics into manageable parts and provided clear, concise explanations.
I particularly appreciated their help with SQL queries. Writing efficient and effective SQL queries was one of the areas I found most challenging. The expert guidance I received helped me understand how to approach query writing logically. They showed me how to optimize queries for better performance and how to avoid common pitfalls.
Timely Delivery
Another aspect that stood out was their commitment to deadlines. As a student, timely submission of assignments is crucial. DatabaseHomeworkHelp.com always delivered my assignments well before the deadline, giving me ample time to review the work and ask any follow-up questions. This reliability was a significant relief, especially during times when I had multiple assignments due simultaneously.
Customer Support
The customer support team at DatabaseHomeworkHelp.com deserves a special mention. They were available 24/7, and I never had to wait long for a response. Whether I had a question about the pricing, needed to clarify the assignment details, or required an update on the progress, the support team was always there to assist me promptly and courteously.
Affordable and Worth Every Penny
As a student, budget is always a concern. I was worried that professional homework help would be prohibitively expensive. However, I found the pricing at DatabaseHomeworkHelp.com to be reasonable and affordable. They offer different pricing plans based on the complexity and urgency of the assignment, making it accessible for students with varying budgets.
Moreover, considering the quality of help I received and the improvement in my grades, I can confidently say that their service is worth every penny. The value I got from their expert assistance far outweighed the cost.
A Lasting Impact
Thanks to DatabaseHomeworkHelp.com, my grades in the database course improved significantly. But beyond the grades, the most valuable takeaway has been the knowledge and confidence I gained. I now approach database assignments with a clearer understanding and a more structured method. This confidence has also positively impacted other areas of my studies, as I am less stressed and more organized.
Final Thoughts
If you're a student struggling with database management assignments, I highly recommend Database Homework Help from DatabaseHomeworkHelp.com. Their expert guidance, timely delivery, and excellent customer support can make a significant difference in your academic journey. They don’t just provide answers; they help you understand the material, which is crucial for long-term success.
In conclusion, my experience with DatabaseHomeworkHelp.com has been overwhelmingly positive. The support I received has not only helped me improve my grades but also enhanced my overall understanding of database concepts. I am grateful for their assistance and will undoubtedly continue to use their services as I progress through my computer science degree.

7 notes
·
View notes
Text

So decided to share some Lore about my main Oc, Void:
So basic backstory:
They are one of the creations of the Creator before Sun and Moon, however unlike the past attempts the Creator used Void as more of an experiment, using a power Core composed of Anti-matter (what a WitherStorm is made of) and implanting it into the bots chest as a power source, and of course these had certain effects, such as making them partly organic, such as resulting in them having a fully organic rib cage, a tongue and saliva, and with some nano-machines, an artificial stomach able to process any and all Materials.
When Void first activated they were put into the care of their handler, Cathryn, a young women who had only recently started working at the Pizzaplex. Void was assigned to the Daycare theatre and left to adapt.
Cathryn showed them all the ropes, and soon Void caught on to the routine and was soon doing their job like it was already programmed into their code. Soon they grew so fond of Cathryn they had registered them as ‘Mother’, which she did not mind in the slightest.
Although, once Void has properly assimilated into their Job at the Theatre entertaining the kids, the Creator put his real plan into action. While Void and Cathryn were preparing for the next rush if kids the Creator activated a dormant administration code inside of Void, cause them to become a brain dead robot, Cathryn walked over to see what was wrong, and with just a click of a button on the Creators end, Cathryn was dead by Voids hands. And once Void came to they were horrified to have seen what they had done, looking at their bloodied hands in shock and horror.
Security soon rushed in and shut them down, soon awakening again in parts and services where they were violently dismantled and used for parts while still active, after the many hours of agony they were dumped into an alleyway and left to die. Void unfortunately died on that stormy night, however a relatively large size changing Water Dragon animatronic, named Angler, had found them and taken them into a secret factory sized room hidden in the maintenance tunnels of the pizzaplex, where he had been taking in and hiding all the discarded and scrapped animatronics thrown out by the Pizzaplex, and Void was brought back to life from a strong infusion of Nano-machines.
Void soon settled in with their now adoptive father and siblings, however still lived in fear of being controlled again.
One day they went to far with their anxiety and snuck into parts and services while the Staff were on break, and used the computer to enter their own systems and forcefully delete any access codes the creator put in them along with their factory reset, this resulted in their code becoming highly unstable, resulting in their Ai becoming corrupted, all safety protocols off and gone.
When Void returned Angler immediately knew what they had done, and he also knew that damage like this could never be fixed, but he supported them and did his best to comfort them the best he could, but one thing he couldn’t stop was Voids newfound hatred and bloodlust towards humans.
Fun facts:
- before Voids system corruption their eyes actually used to be green.
- Void hates all humans but tolerates curtain humans that have gotten on their good side………and children.
- the purple eyes mean they are either hunting, or have completely lost it and you need to run.
- the oval shaped power core in their chest is not only able to store a copy of their memories and personality, but also acts as a 3rd eye.
- their power core is made of the same stuff that Witherstorms are made of.
- like Sun and Moon, Voids nanites can regenerate them, but at a more advanced and quicker pace
- they CAN and WILL Eat anything.
- they can sprout 4 or more barbed black tendrils from their back if they want to.
- at some point they found out they can digitise their physical form and control technology
- they have a secondary jaw that can move independently like an eel
11 notes
·
View notes
Text

⟢ - Structure of the 𝐀𝐄𝐓𝐇𝐄𝐑 𝐅𝐎𝐔𝐍𝐃𝐀𝐓𝐈𝐎𝐍

The 𝐀𝐄𝐓𝐇𝐄𝐑 𝐅𝐎𝐔𝐍𝐃𝐀𝐓𝐈𝐎𝐍 operates as a corporation and trust, funding research for various fields of scientific study through grants. It also engages in many different charitable acts related to the rehabilitation and conservation of endangered Pokémon, especially those native to the islands of Alola.
The corporation was founded by current sitting president and CEO, Lusamine Delacroix, with her husband, Mohn Delacroix, serving as vice president until his disappearance. The pair set out to establish a higher standard for how humans, Pokémon and technology can work with one another, while benefiting the natural ecosystems. Aether works alongside many different organizations throughout, and outside of, Alola.
Fields of Interest
The foundation funds projects, research, innovations and expeditions related, but not limited to, conservation, ecology, biochemistry, physics, epidemiology, genetic engineering, and computer engineering. Scientists and scholars from across the globe often seek out the foundation’s funding, traveling to the Aether Paradise in order to meet with members of the board, and Lusamine herself. There is quite the impressive network of intellects connected to the foundation, and it is not unusual to see the Aether seal stamped onto many peer reviewed journals.
Grants and scholarships for students pursuing careers in STEM are also gifted by the Aether Foundation. Many of these students are then placed into internships at the paradise, or in one of the Aether Houses— and funneled into a permanent position of employment upon graduation. The foundation relies on having the most brilliant, cunning minds involved with their projects, and so they make sure to leave a good impression on the scientific community. It is pretty common to see an Aether representative at any major conference involving STEM, or around university campuses.
Working for the Aether Foundation
Employment with the Aether Foundation ranges across different positions— from field researchers, to chemists, to public relations, and many, many more. Those who work at the Aether Paradise work directly with Aether’s conservation programs, vaccination developments, and technology departments. And the genetics program and UB project, if you’re aware of the horrors.
Gaining employment, however, is no simple task. Lusamine expects an impressive resume, and a mind to match, but if somebody passes the hiring process, it is great job security— as long as they do not disappoint her.
All employees are required to sign a non-disclosure agreement upon being hired. All positions are by contract, and salary paid.
All employees are required to submit their biometrics.
The hierarchy
From highest to lowest:
President
Vice President (currently unoccupied)
Branch Manager
Assistant Branch Manager
Divisional Manager
Assistant Divisional Manager
Office Administration
Lead Associate
Associate
Intern
Scientists and research teams are categorized and ranked based on individual projects and assignments.
Accessing the Aether Paradise
If commuting to work, employees have two options: traveling across the water from one of the islands via Aether-owned ferry service, or by helicopter. The ferry service also carries tourists on public access days, so that they can experience the conservation deck, and tour the island.
Aether offers on-site dorms for those who would rather not commute back and forth all week, and for those who are staying on the artificial for an extended period of time for an assignment.
Security
Security is taken very seriously on the island; Lusamine is incredibly strict about it, and intends on keeping it that way.
All employees are assigned key cards, which are required to access all of the rooms and laboratories on the floors one through three.
All of the laboratories and doors on floor three, and in basements 1, 2 and 3 require a fingerprint and retina scan.
Certain high-security areas require two or three employees to use fingerprint or retina scan in order to unlock the door for access.
Higher ranked foundation members and scientists have a chip implanted in their left wrist, which is used as a “master key” to access everything on the Aether Paradise, along with the locks for the Aether House and research stations.
Basements 1, 2 and 3 have safety laser scanners installed that are programmed to scan every room, laboratory and corridor every fifteen minutes. If a persons whose biometrics have not been logged into Aether’s system is picked upon, an alarm goes off, and all doors are locked. Only Aether security guards, or high ranked foundation members, are capable of unlocking the doors in order to remove the intruder.
ALL points of the Aether Paradise have motion sensing cameras and CCTV streaming.
Aether buildings are known for their monochrome coloring and bright fluorescent lights. This is to prevent employees and visitors from finding dark or secluded corners to hide in, and discourages people from attempting to smuggle Aether property. It also makes it easy for visitors to be picked up on by the security cameras; everybody on staff is wearing all white, so somebody who is wearing even the slightest bit of color stands out.
In the case of an emergency, the Aether Paradise is capable of undergoing full lockdown mode. All incoming boats and aircraft are instructed to return to the mainland, and all outgoing forms of transportation are halted.
27 notes
·
View notes
Text
Master resale proper rights, exclusive brand liberties, resell protection under the law... If you happen to don't know what each and every words methods, you can certainly realise you are perplexed just by the many buzz. In this post, I'm about to demonstrate your different types of market rights that you can acquire together with discuss tips on how to earn money at their side.
There is two essential types of resell proper rights - Expert Resale Liberties, Resell Proper rights and Private Brand legal rights. The prevailing difference is normally of which Get better at Resell legal rights slots might spread Get better at Re-sell Protection under the law for you to buyers while Market protection under the law easily allow you to sell the information for an end user.
If perhaps it's flexibility people seek, Private Content label Liberties allow you to alter the item and commonly feature form computer files that you edit. Most PLR offers additionally let you affix your identify on the item for the initiator. Private brand liberties may be the nearest thing factor to using your own personal product as well as nowadays organizations a lot of excellent applications with PLR solutions with regard to rather economical.
All two different kinds of protection under the law help you distribute a product or service and maintain 100% within the revenue. Experienced affiliates and marketers have been instant to help you reward Resell Correct products being easily manner to generate a product or service that you've comprehensive control over. As opposed to selling web solutions, it's essential to course of action your individual assignments in addition to work with your own personal customer service network. Still, a lot of old affiliate sites are discovering that extra perform will be practically nothing contemplating the advantage of additional revenue border.
Consequently, what sorts of Re-sell Appropriate products are obtainable? Properly, any kind of manner you could think involving at subjects because of promotional to help puppy coaching. You'll discover an entire variety of category information products accessible along with diverse legal rights as well as software perhaps even visuals. Typically, bundles come that might include sales characters in addition to sharp graphics, helping to make create very easy.
You can find a pair of simple solutions to acquire Resale rights. The most cost effective manner is usually to get hold of a package pack. It is possible to often pick up hundreds of supplements at once at under $40. Your various choice should be to become a member of some re-sell liberties clubhouse. There are several fantastic providers in existence that supply brand spanking new items for you to market on a monthly basis.
However you determine to base your current goods, re-sell protection under the law are a sensible way to beginning your facts product and software program empire. No time before comes with this ended up so simple capability to deliver to start out merchandising ones own "own" supplements via the internet.
Master resale rights
2 notes
·
View notes
Text
AN OPEN LETTER to THE U.S. CONGRESS
Fund the Affordable Connectivity Program NOW!
130 so far! Help us get to 250 signers!
I’m a concerned constituent writing to urge you to fund the Affordable Connectivity Program or ACP. Digital connectivity is a basic necessity in our modern world and the internet must be treated as a public utility. We use the internet to apply for jobs, perform our jobs, receive telehealth medical treatment, and pay bills, and students use it to complete homework assignments. But for millions of people in rural and urban areas, and Tribal communities, the internet is a luxury they cannot afford. Failure by Congress to fund this program will force millions of households already on tight budgets to choose between being able to stay online or potentially losing access to this essential service. If Congress doesn’t act fast, funding for the Affordable Connectivity Program will run out and more than 22 million Americans -- 1 in 6 households -- will lose this vital service. The implications of this will be devastating. In 2019, 18% of Native people living on Tribal land had no internet access; 33% relied on cell phone service for the internet; and 39% had spotty or no connection to the internet at home on their smart phone. The ACP has enrolled 320,000 households on Tribal lands -- important progress. The largest percentage gains in broadband access are in rural areas. Nearly half of military families are enrolled in ACP, as are one in four African American and Latino households. Losing access and training on using computers and the internet will have devastating impacts on all these communities as technology becomes increasingly integral to work, education, health, and our everyday lives. Without moves to address tech inequality, low-income communities and communities of color are heading towards an “unemployment abyss.” The Affordable Connectivity Program has broad bipartisan support because it is working. As your constituent, I am urging you to push for renewed funding for the ACP before it runs out in the coming weeks.
▶ Created on April 11 by Jess Craven
📱 Text SIGN PJXULY to 50409
🤯 Liked it? Text FOLLOW JESSCRAVEN101 to 50409
#JESSCRAVEN101#PJXULY#resistbot#petition#Affordable Connectivity Program#Digital Divide#Internet Access#Broadband Access#ACP Funding#Congress Funding#Public Utility#Internet Equality#Telehealth#Telemedicine#Internet Inequality#Digital Inclusion#Internet For All#Rural Connectivity#Bipartisan Support#Internet Infrastructure#FCC#ACP Support#Digital Navigation#Online Education#Remote Work#Job Access#Telecommunications#Internet Service#Internet Affordability#Digital Equity
5 notes
·
View notes
Text

First Lieutenant Arthur Robert Ashe Jr. (July 10, 1943 – February 6, 1993) was a tennis player who won three Grand Slam singles titles.
He was born in Richmond, Virginia to Arthur Ashe Sr. and Mattie Cordell Cunningham Ashe. He had a brother, who was five years younger than him.
He became the first African American to win the National Junior Indoor tennis title and was awarded a tennis scholarship to UCLA.
After graduating with a BA in Business Administration from UCLA, he joined the United States Army. He completed his basic training in Washington and was commissioned as a second lieutenant in the Adjutant General Corps. He was assigned to the United States Military Academy at West Point where he worked as a data processor. He headed the academy’s tennis program. He was discharged from the Army as a 1st Lieutenant. He was awarded the National Defense Service Medal for his service. He served 2 years.
He was the first African American player selected to the US Davis Cup team and the only African American man ever to win the singles title at Wimbledon, the US Open, and the Australian Open. He retired in 1980. He was ranked world #1 by Harry Hopman in 1968 and by Lance Tingay of The Daily Telegraph and World Tennis Magazine in 1975. In the ATP computer rankings, he peaked at #2 in May 1976.
He is believed to have contracted HIV from a blood transfusion he received during heart bypass surgery. He publicly announced his illness in April 1992 and began working to educate others about HIV and AIDS. He founded the Arthur Ashe Foundation for the Defeat of AIDS and the Arthur Ashe Institute for Urban Health before his death from AIDS-related pneumonia.
He married photographer and graphic artist Jeanne Moutoussamy (1977). They adopted a daughter.
He was posthumously awarded the Presidential Medal of Freedom by President Bill Clinton. #africanhistory365 #africanexcellence #kappaalphapsi
2 notes
·
View notes
Text
Client Work(Android)|CST2335_Final_GroupProject_F22 2022Soccer match highlights part Output Video|Algonquin College
youtube
Programming Assignment Helper For International Students 𝐖𝐞 𝐚𝐫𝐞 𝐡𝐞𝐥𝐩𝐢𝐧𝐠 𝐬𝐭𝐮𝐝𝐞𝐧𝐭𝐬 𝐨𝐮𝐭! 𝐏𝐫𝐨𝐯𝐢𝐝𝐢𝐧𝐠 𝐬𝐞𝐫𝐯𝐢𝐜𝐞𝐬 𝐟𝐨𝐫 𝐬𝐜𝐡𝐨𝐨𝐥/𝐜𝐨𝐥𝐥𝐞𝐠𝐞/𝐮𝐧𝐢𝐯𝐞𝐫𝐬𝐢𝐭𝐲 𝐚𝐬𝐬𝐢𝐠𝐧𝐦𝐞𝐧𝐭𝐬, 💻 𝐜𝐨𝐮𝐫𝐬𝐞𝐰𝐨𝐫𝐤,𝐥𝐚𝐛 𝐩𝐫𝐨𝐣𝐞𝐜𝐭𝐬/𝐫𝐞𝐩𝐨𝐫𝐭𝐬, 𝐞𝐱𝐚𝐦𝐬, 𝐪𝐮𝐢𝐳𝐳𝐞𝐬, 𝐝𝐢𝐬𝐬𝐞𝐫𝐭𝐚𝐭𝐢𝐨𝐧𝐬,𝐭𝐡𝐞𝐬𝐢𝐬; 𝐚𝐬 𝐰𝐞𝐥𝐥 𝐚𝐬 𝐩𝐫𝐨𝐨𝐟𝐫𝐞𝐚𝐝𝐢𝐧𝐠, 𝐞𝐫𝐫𝐨𝐫 𝐜𝐨𝐫𝐫𝐞𝐜𝐭𝐢𝐨𝐧, 𝐚𝐧𝐝 𝐛𝐮𝐠-𝐟𝐢𝐱𝐢𝐧𝐠. 𝐀𝐥𝐬𝐨 𝐝𝐨𝐢𝐧𝐠 𝐬𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐜𝐨𝐦𝐩𝐚𝐧𝐲, 𝐚𝐠𝐞𝐧𝐜𝐢𝐞𝐬 𝐩𝐫𝐨𝐟𝐞𝐬𝐬𝐢𝐨𝐧𝐚𝐥 𝐩𝐫𝐨𝐣𝐞𝐜𝐭𝐬📊
We specialize in the following fields: 📘 Computer Science🔖Programming: 🔖 Python 🔖 Java 🔖 C 🔖 C++ 🔖 C# 🔖 Ruby 🔖 Matlab 🔖 HTML | CSS | JavaScript 🔖 PHP 🔖 CSS 🔖 Databases | SQL 🔖 Android Development 🔖 Algorithms 🔖 Swift 🔖 Networks | CCNA 🔖All kinds of IT work 📘EEE 📘Mechanical Engineering 📘Civil📘ALL type of academic services 📘 Mathematics 📘 Statistics 📘 Marketing 📘 Management 📘 Accounting 📘 Psychology 📘 Business 📘 Economics 📘 Pharmacology 📘 Engineering 📘 Finance 📘 Nursing 📘 Sociology 📘 Literature 📘 Health & Social Care 📘Writing 📘Thesis 📘Report
we provide all type of academic services 🟩Assignments 🟩Projects 🟩Exams 🟩Quizz 🟩Lab 🟩Thesis 🟩Dissertation 🟩Reports 🟩Final year projects 🟩Programming 🟩Coursework 🟩Proposal Writing 🟩Essay writing 🟩Article writing 🟩LSAT exam 🟩Research paper writing 🟩Term paper 🟩Conference Paper 🟩Case study 🟩Proofreading 🟩DATA Analysis 🟩Stata Analysis 🟩Spss 🟩Review articles 🟩Referencing 🟩Correction 🟩Questionnaries 🟩Formatting 🟩Presentation 🟩Synopsis 🟩Ai Removal 🟩Paraphrasing
For take our services contact with us Whatsapp/Telegram:+8801772432396 whatsapp profile link: https://wa.me/+8801772432396 https://wa.me/message/PYHN7PIZEHNQO1 Email 1:[email protected] Email 2:[email protected] Discord username:programmingassignmenthelperbd or Discord username:academiccourseworkservices Discord Server profile link:https://discord.com/invite/C6DQUbgH2w Instagram:https://www.instagram.com/programmingassignmenthelperbd/ Instagram Username:programmingassignmenthelperbd Telegram Account: https://t.me/programmingassignmenthelperbd Telegram Username:@programmingassignmenthelperbd Telegram Phone Number:+8801772432396 skype profile link: https://join.skype.com/invite/w0k4c2of6ts3 skype name:live:.cid.e36c1f8fe9b0bbfd Printerest Account:https://www.pinterest.com/programmingassignmenthelperbd/ Printerest Username:programmingassignmenthelperbd Twitter Account:https://twitter.com/assignmentintl Twitter Username:assignmentintl Tiktok Account:https://www.tiktok.com/@assignmenthelperbd Tiktok Username:assignmenthelperbd Linkedin Company Page: https://www.linkedin.com/showcase/assignment-writing-for-students https://www.linkedin.com/company/programming-assignment-exam-quiz-project-report-helper-for-international-students Facebook Compnay Page: https://www.facebook.com/programmingassignmenthelperforinternationalstudent/ Website:https://academiccourseworkservices.com/
Our Student Review /Client Feedback:https://drive.google.com/file/d/16Ametl8UY-RehW3Q4jYZmM1DxioCG3J8/view?usp=sharing
𝐎𝐮𝐫 𝐰𝐨𝐫𝐤 𝐩𝐨𝐫𝐭𝐟𝐨𝐥𝐢𝐨 𝐥𝐢𝐧𝐤: https://www.youtube.com/channel/UCyOlJCraJuVs6oBUIYOoz0Q?sub_confirmation=1
𝗔𝗹𝗴𝗼𝗻𝗾𝘂𝗶𝗻 𝗰𝗼𝗹𝗹𝗲𝗴𝗲 𝗮𝗽𝗽𝗹𝗶𝗲𝗱 𝗮𝗿𝘁𝘀 𝗮𝗻𝗱 𝘁𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝘆 𝘄𝗼𝗿𝗸 𝗽𝗼𝗿𝘁𝗳𝗼𝗹𝗶𝗼 𝗹𝗶𝗻𝗸:https://www.youtube.com/playlist?list=PL16VzvGeViA0g1ql7OVnoaNCGgZCZG0Lx
Regards Assignment Helper [Programming Assignment Helper For International Students]
#CST8227#CST2335#CST8333#CST8288#AlgonquinCollege#Android#Java#Python#Enterprise_Application_Programming#Graphical_Interface_Programming#Programming_Language_Research#students_work_output_video#client_work_output_video#cobol#Network_Programming#System_Analysis_and_Design#canaduniversity#canada#internationalstudents#students#computersciencestudents#assignmenthelper#labhelper#academichelper#thesishelper#dissertationhelper#essayhelper#reporthelper#ottawastudents#torontostudents
1 note
·
View note