#cyber security hacking
Text

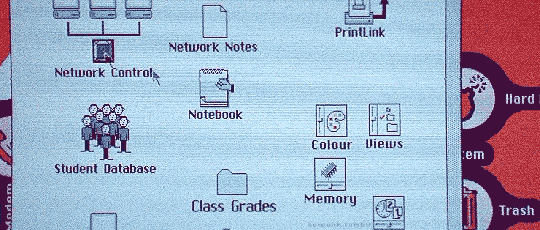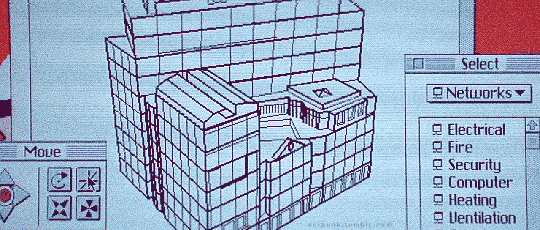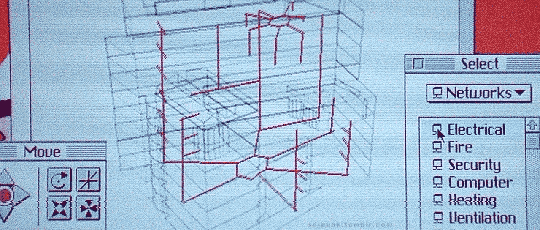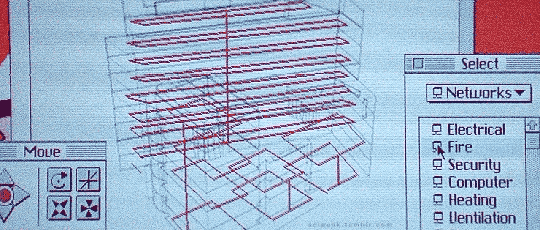
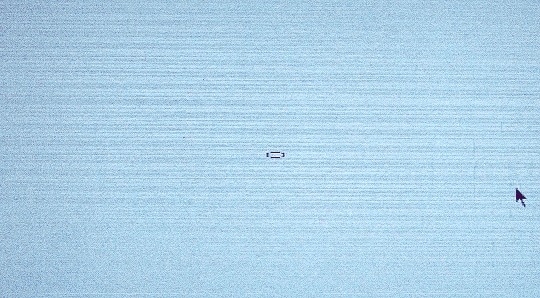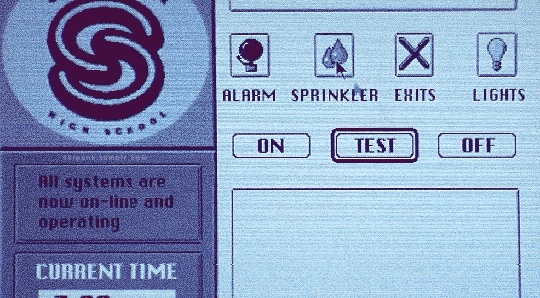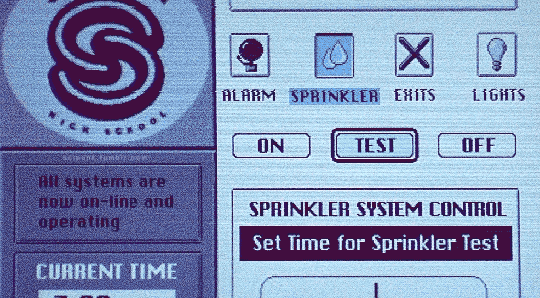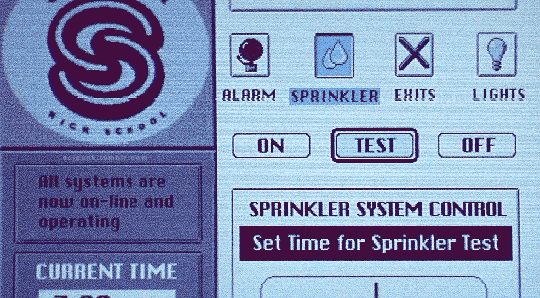



Hackers (1995)
#hackers#macintosh#cyber security#prank#funny pranks#school hacks#fire alarm#cyberpunk#cyberpunk movies#gifs#gifset#umbrella#cybersecurity#cyberspace#macos#mac os#retro computing#apple mac#hypercard
576 notes
·
View notes
Text
Twitter 400 Million Users Data Leaked And Posted For Sale

Read More: Twitter 400 Million Users Data Leaked And Posted For Sale
#coding#programming#programmer#developer#codenewbie#webdev#twitter#elon musk#cyber news#security#hacking#data#data leak
148 notes
·
View notes
Text
🤦🏾🤦🏻🤦
10 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project
For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
15 notes
·
View notes
Text

#mdshirajumbillahsiam#succession#the mandalorian#donald trump#margot robbie#taylor swift#ethical hacker#Red Team#cyber security specialist#hacking your mind#hackers
2 notes
·
View notes
Text
The Daily Hodl: Hackers Hit World’s Largest Bank, Forcing Financial Giant to Rely on USB Stick to Settle Trades: Report
Engineers are investigating how hackers managed to crack the New York arm of the Industrial & Commercial Bank of China (ICBC) – a financial institution with $5.74 trillion in total assets.
The hack forced the ICBC to settle trades using a USB stick while forcing banks, brokerages and market makers to reroute trades, reports Bloomberg.
The attack also disrupted the bank’s ability to participate in the Treasury’s bond auction on Thursday.
Investigators believe the ransomware gang Lockbit, which has ties to Russia, is behind the attack.
Without naming names, Bloomberg says banking leaders admit the hack highlights fears that a system-wide attack could one day bring the traditional financial system to a halt.
“The incident spotlights a danger that bank leaders concede keeps them up at night — the prospect of a cyberattack that could someday cripple a key piece of the financial system’s wiring, setting off a cascade of disruptions.”
The ICBC says it’s debating whether to ask for assistance from China’s Ministry of State Security.
The number of ransomware attacks on the financial industry has increased in recent years, according to a report from the cybersecurity firm Sophos.
“The 2023 survey revealed that the rate of ransomware attacks in financial services continues to rise. It went up from 55% in the 2022 report to 64% in this year’s study, which was almost double the 34% reported by the sector in the 2021 report. Although the sector experienced an increased attack rate, it was below the cross-sector average of 66%.”
Sophos says financial institutions are stepping up their efforts to stay secure.
The firm’s survey of 3,000 cybersecurity/IT leaders, including 336 in the financial services sector, found 81% of organizations say their data is encrypted, a 50% rise over the previous year.
#ICBC#Hackers Hit World’s Largest Bank#Forcing Financial Giant to Rely on USB Stick to Settle Trades#bank hacks#cyber security#stolen money#financial institutions#hacks#cybersecurity in america
6 notes
·
View notes
Text

🌐📚 Elevate your cloud skills prowess with our training courses! 🎓💻
💡 Gear up for success with our in-depth training designed to help you nail the Cloud certification exam. 💯🥇
📅 Enroll today and take the first step towards unlocking endless opportunities! Don't miss out on this incredible offer. ⏳🔓
For Additional Info🔔
🟢Whatsapp: https://wa.me/9677781155 , https://wa.me/7558184348 , https://wa.me/9677724437
📨Drop: https://m.me/elysiumacademy.org
🌐Our website: https://elysiumacademy.org/networking-course-certification/
📌Live Visit: https://maps.app.goo.gl/YegrK4aKEWbEY2nc8
🔖Appointment: https://elysiumacademy.org/appointment-booking/
#elysiumacademy#no1academy#jobassurance#tesbo#no1trainingacademy#elysiumacademy_madurai#cybersecurity#ethicalhacking#hackers#programming#hack#technology#security#coding#tech#ethicalhacker#pentesting#cyber#malware#programmer#informationsecurity#AWS#cloudskillawareness#coder
2 notes
·
View notes
Text
Unmasking the Invisible: Ethical Hackers and the Art of Vulnerability Hunting

In today's digital age, our reliance on technology has created a vast and interconnected landscape. While this interconnectedness offers undeniable benefits, it also introduces vulnerabilities – chinks in the armor that can be exploited by malicious actors. Imagine a grand castle, its walls seemingly impenetrable. But what if there were hidden weaknesses, unseen passages known only to a select few? This is where ethical hackers, the unsung heroes of cybersecurity, come in. They are the vulnerability hunters, the digital detectives on a relentless quest to identify and expose these weaknesses before they can be used for malicious purposes.
This blog delves into the fascinating world of vulnerability hunting, exploring the role of ethical hackers in safeguarding our digital assets. We'll uncover the techniques they employ, the challenges they face, and the importance of cyber security training Mumbai for fostering a skilled workforce of ethical hackers.
The Invisible Threat: Unveiling Vulnerabilities
Imagine a digital thief attempting to break into a bank vault. They wouldn't simply smash through the front door; they'd meticulously search for weaknesses – a faulty security system, a hidden ventilation shaft. Similarly, vulnerabilities in software, hardware, and network configurations act as those hidden access points for malicious hackers. These vulnerabilities can be:
Software Bugs: Errors in the code that can be exploited to gain unauthorized access or cause unexpected behavior.
Misconfigurations: Improper settings in network devices or software applications that create security gaps.
Zero-Day Attacks: Previously unknown vulnerabilities that attackers exploit before software vendors have a chance to issue a patch.
These vulnerabilities are often invisible to the untrained eye. This is where ethical hackers, also known as white hats, step in. They act as the security guardians, wielding specialized tools and techniques to hunt for these hidden weaknesses.
The Art of the Hunt: Techniques of a Vulnerability Hunter
Ethical hackers employ a diverse arsenal of techniques in their pursuit of vulnerabilities. Here are some of the most common methods which you can learn in cyber security training mumbai :
Network Scanning: Ethical hackers use specialized tools to scan networks and identify devices, open ports, and potential security weaknesses.
Penetration Testing: This involves simulating a cyberattack to identify vulnerabilities that could be exploited by malicious actors. Ethical hackers attempt to gain unauthorized access to systems using various techniques, mimicking the methods black hats might employ.
Social Engineering Testing: This involves testing the organization's security awareness by attempting to trick employees into revealing sensitive information or clicking on malicious links.
Code Review: Ethical hackers meticulously examine the code of software applications to identify potential vulnerabilities and bugs.
These techniques require a deep understanding of cybersecurity principles, programming languages, and hacking methodologies. Cyber security training Mumbai can equip individuals with the necessary skills and knowledge to become proficient vulnerability hunters.
The Challenges of the Hunt: A Constant Cat-and-Mouse Game
The world of vulnerability hunting is a constant cat-and-mouse game. As technology evolves, so do the vulnerabilities that ethical hackers need to identify. Here are some of the key challenges they face:
The Ever-Expanding Attack Surface: With the increasing use of cloud computing, mobile devices, and the Internet of Things (IoT), the attack surface – the potential points of entry for attackers – is constantly expanding. This makes it more challenging for ethical hackers to identify all potential vulnerabilities.
Zero-Day Attacks: The constant threat of zero-day attacks, where attackers exploit previously unknown vulnerabilities, keeps ethical hackers on their toes. They need to be constantly researching and developing new methods to identify these vulnerabilities before they can be used in real-world attacks.
Staying Ahead of Black Hats: Malicious hackers are constantly innovating and developing new attack techniques. Ethical hackers need to stay up-to-date on the latest hacking trends and methodologies to ensure they can identify vulnerabilities before they are exploited.
The Value of the Hunt: Why Vulnerability Hunting Matters
Vulnerability hunting plays a critical role in safeguarding our digital infrastructure. By proactively identifying and patching vulnerabilities, ethical hackers can significantly reduce the risk of successful cyberattacks. Here are some of the key benefits of vulnerability hunting:
Reduced Risk of Cyberattacks: By identifying and patching vulnerabilities, ethical hackers make it more difficult for malicious actors to gain unauthorized access to systems and data.
Improved Security Posture: The process of vulnerability hunting helps organizations identify and address weaknesses in their overall security posture, leading to a more robust defense.
Enhanced Compliance: Many regulations require organizations to conduct regular vulnerability assessments. Ethical hacking helps organizations meet these compliance requirements.
Cyber security training Mumbai can equip individuals with the skills to become ethical hackers, contributing to a safer digital landscape. These courses can provide valuable knowledge on vulnerability hunting methodologies, penetration testing techniques, and ethical hacking best practices.
2 notes
·
View notes
Text
I keep seeing ads against data brokers and stuff, or vpns but if there is a browser extension or smth that i WOULD pay for is a fact checker that fact checks basic information on my screen from viable sources and even gives you a link to them, imagine the possibility's!!!!
you could also add in an auto translation option or smth that would be so amazing.
#vpn#wifi#hacking#amazon#security#cyber security#free vpn#best vpn#internet#information#enshittification#privacy#internet safety#the internet#fake news
3 notes
·
View notes
Text
TV detectives cracking a password before the hard drive is wiped: Ah, ha! It’s Anarky, a lesser known Batman villain who focuses on the freedom of the people at any cost, just like our suspect
An actual password of someone concerned enough with security to set that up: Q?z6w!P8#+
3 notes
·
View notes
Text
Incorporated (2016) - Biometric Authentication Bypass
#cyberpunk aesthetic#graphic design#user interface#biopunk#graphical user interface#cyberpunk#dna#genetics#biometrics#hacking#cyber security#megacorp#cybernetics#dystopian society#scifi#hackers
41 notes
·
View notes
Text
Hire a Hacker Pro 2024 #1 in the World. Don't just hire any hacker online. There is only one, Hire a Hacker Pro. US Based, Online since 2008. +1-480-400-4600
5 notes
·
View notes
Text
Cybercrime threat in Germany is higher than ever before
The German Federal Office for Information Security reports a significant increase in cyber threats in Germany. The risk of ransomware attacks is considered to be extremely high, according to the Office’s latest report.
On Thursday (2 November), Germany’s Office for Information Security (BSI) issued a report on the state of IT and cybersecurity in the country for the period from June 2022 to June 2023. The agency’s experts noted that the threat level was “higher than ever before.” It also recorded the highest average increase in malware types – 332,000 new variants per day over the period observed. The number of German ransomware victims whose names and captured data were published on leak sites also reached a record high of 65 people in the second quarter. German Interior Minister Nancy Faeser said:
“The BSI report on the state of IT security in Germany in 2023 proves that the threat situation in cyberspace remains tense.”
Ransomware remains the top threat, according to the agency’s report. Government agencies are seeing a dramatic increase in advanced persistent threats (APTs) – cyber espionage or sabotage carried out over a long period of time to gain information or manipulate.
Read more HERE

#world news#world politics#news#europe#european news#european union#eu politics#eu news#germany news#germany#cyberattack#cybersecurity#cybernetics#cyber security#hacker news#hackers#hacker#hackernews#hacking
5 notes
·
View notes
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
3 notes
·
View notes
Text
3 notes
·
View notes
Text
3 Essential Reasons for Prioritizing Website Security
You might think that security is important but only for big companies. This article is going to change your mind.
Hacked website can affect your audience
Security is critical as long as you have any visitor on your website (actually, security is vital even if you don’t have any visitor at all, you’ll see!).
Either recruiters on your personal project portfolio website or customers on your…

View On WordPress
2 notes
·
View notes