#embedded systems applications
Explore tagged Tumblr posts
Text
Embedded Systems Course For Beginners
Embedded systems have permeated nearly every aspect of modern technology. From the smartphones we use to the cars we drive, embedded systems are responsible for powering many of the devices we rely on daily. If you're looking to gain an understanding of embedded course in Bangalore and how to work with them, you might want to consider taking a beginner's course at the Indian Institute of Embedded Systems (IIES).

Introduction
Embedded systems are integrated computer systems designed to perform specific tasks without human intervention. They are widely used in industries such as automotive, healthcare, home automation, and more, and are becoming increasingly popular as the Internet of Things (IoT) continues to grow. A beginner's course at IIES is an excellent way to get started with embedded systems and learn about the fundamental concepts, tools, and techniques used in the industry.
Why Take a Beginner's Course on Embedded Systems?
Taking a beginner's course on embedded systems has several benefits, including:
Understanding the Fundamentals
A beginner's course at IIES can help you understand the foundational concepts of embedded systems, including hardware and software components, communication protocols, and programming languages commonly used in the industry.
Developing Practical Skills
The course is designed to provide a hands-on approach to learning, allowing you to work with real-world hardware and software platforms, including the Arduino and Raspberry Pi. This practical experience will give you the confidence and skills you need to build embedded systems on your own.
Career Opportunities
As the use of embedded systems continues to grow, so does the demand for professionals in the field. Completing a beginner's course at IIES can open the door to a wide range of career opportunities, including embedded system engineer, IoT developer, and more.
Course Curriculum
The beginner's course offered at IIES covers a comprehensive range of topics, including:
Introduction to Embedded Systems
This section provides a comprehensive overview of embedded systems. It covers the basics of hardware and software components, communication protocols, and programming languages.
Microcontrollers and Microprocessors
Learn about the various microcontrollers and microprocessors used in the industry, including AVR, ARM, and PIC microcontrollers.
Programming Languages
Gain an understanding of the programming languages used in embedded systems development, including C and Python in embedded system.
Real-time Operating Systems
This section covers the basics of real-time operating systems, including scheduling algorithms, task management, and inter-task communication.
Hardware Interfacing and Peripheral Control
Learn how to interface with various hardware components, such as sensors, motors, and displays, and control them using programming languages and microcontrollers.
Projects and Workshops
The course offers several practical workshops and projects that allow students to work with real-world projects and gain hands-on experience.
Indian Institute of Embedded Systems (IIES)
IIES is one of the most reputed institutes for embedded systems training in India. The institute offers a wide range of certificate and diploma programs in embedded systems, including the beginner's course mentioned above.
Expert Trainers
IIES has a team of experienced trainers who are experts in their field. They provide practical training sessions, enabling students to gain skills that are relevant to industry standards.
Industry Partnerships
Keeping up with the current industry trends is essential to gaining expertise in a field; IIES has partnered with various companies such as Altair, Tiempo Labs, and many more reputed firms. This collaboration helps to keep the students updated about industry trends and expectations.
Advanced Facilities
IIES has cutting-edge infrastructure and world-class facilities, providing students with access to the latest hardware and software technologies and practical hands-on learning experiences.
Course Duration and Cost
The beginner's course offered by IIES is of 3 months' duration and offers flexible batch timings. The fee structure is reasonable and affordable, making it accessible to anyone interested in learning about embedded systems.
Conclusion
A beginner's course on embedded systems offered by IIES can be an excellent way to learn about this fascinating field. The program provides a comprehensive overview of embedded system concepts, tools, and techniques while also offering practical hands-on learning experiences. Completing the course can be a great career opportunity in a field where the demand for professionals continues to grow. And with IIES's expert trainers and state-of-the-art facilities, you can be confident that you're learning from the best. So, enroll today and start your journey into the exciting world of embedded systems!
#embedded systems applications#embedded engineering#Embedded Engineers#embedded software engineer#difference between c and embedded c#embedded systems projects#Embedded Systems Jobs#Embedded Developer#Embedded System Developers#embedded systems internship#advantages of embedded system#robotics and embedded systems
0 notes
Text
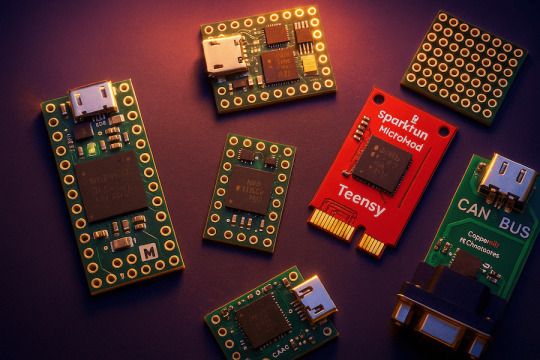
The Ultimate Guide to Teensy Microcontrollers: History, Specs & CAN Bus Applications
Discover the complete history and capabilities of Teensy microcontrollers, from early AVR models to the powerful 4.0 and 4.1 boards. Explore technical specs, software support, and CAN Bus products from Copperhill Technologies.
#teensy#microcontroller#embedded system#classical can#can fd#industrial#automotive#marine applications#arm cortex#ethernet#arduino
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Embedded Systems: Driving Innovation in Technology
Embedded systems are specialized computing systems designed to perform dedicated functions within larger devices or applications. These systems integrate hardware and software components to execute tasks with precision, reliability, and efficiency. They are embedded in devices ranging from household appliances like washing machines and microwaves to complex industrial machines, medical equipment, and automotive systems.

An embedded system's core lies a microcontroller or microprocessor, which controls and processes data. Sensors, actuators, and communication interfaces are often part of the system, enabling it to interact with the physical environment. For instance, in a smart thermostat, an embedded system monitors temperature, processes user inputs, and adjusts heating or cooling accordingly.
Embedded systems are valued for their compact size, low power consumption, and cost-effectiveness. They are tailored for real-time operations, ensuring quick and accurate responses to specific tasks. Industries such as automotive, healthcare, telecommunications, and consumer electronics heavily rely on these systems to innovate and improve product functionality.
As technology advances, embedded systems are becoming more sophisticated, incorporating artificial intelligence (AI), Internet of Things (IoT) connectivity, and advanced sensors. These developments are paving the way for smarter devices and systems, transforming how we live and work.
In a world increasingly driven by automation and smart technology, embedded systems play a crucial role in shaping the future of innovation.
#Embedded Systems#Microcontroller Technology#Real-Time Systems#IoT and Embedded Systems#Embedded Software Development#Embedded Hardware Design#Embedded System Applications
0 notes
Text
GateFi 6 Channel Powered by ESP32: The Future of IoT Connectivity with 4G
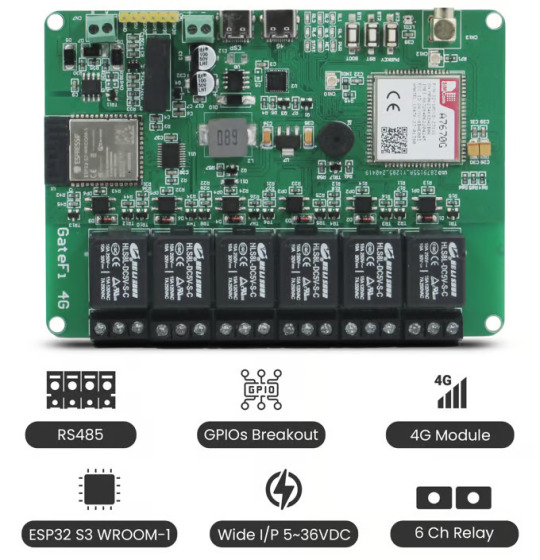
The rapidly advancing world of IoT (Internet of Things) and automation calls for devices that offer robust, flexible, and high-performance capabilities. The GateFi 6 Channel Powered by ESP32 with 4G Connectivity Microcontroller stands as a powerful solution for these needs, designed for industrial and commercial applications that demand reliable control, remote access, and seamless communication.
In this post, we will delve into the key features and capabilities that make the GateFi 6 Channel ESP32 S3 WROOM-1 an ideal choice for building smart systems with efficient relay control, fast connectivity, and advanced communication options.
What is GateFi 6 Channel Powered by ESP32 with 4G Connectivity?
The GateFi 6 Channel is a microcontroller designed to offer versatile and high-performance solutions for a wide range of IoT applications. Powered by the robust ESP32, a popular microcontroller that integrates Wi-Fi and Bluetooth capabilities, the GateFi 6 Channel is further enhanced with 4G connectivity. This combination ensures that your devices have seamless communication over the internet, even in areas where traditional Wi-Fi infrastructure might not be available or reliable.
This device can handle six independent channels simultaneously, making it ideal for tasks that require multiple communication points or data collection from various sensors, devices, or systems. The ESP32 ensures efficient processing and connectivity, while the 4G module guarantees that data can be transferred quickly and reliably over mobile networks.
Key Features
ESP32 S3 WROOM-1 Microcontroller: The ESP32 microcontroller is the heart of the GateFi 6 Channel. It provides a high processing power with dual-core capabilities, enabling fast data processing and communication. Additionally, the ESP32's Wi-Fi and Bluetooth support offer plenty of flexibility in local wireless communication.
6-Channel Relays with Optically Isolated Circuits: Comes equipped with 6 relay channels, which provide the ability to control a wide range of devices such as motors, alarms, or industrial machinery. These relays are optically isolated, offering protection against electrical surges and ensuring that high-voltage circuits are safely separated from the sensitive low-voltage control system. This isolation increases the reliability and longevity of your equipment, particularly in industrial applications where power spikes are common.
4G Connectivity with A7670G Module: The A7670G module provides 4G LTE connectivity, ensuring fast data transmission speeds even in remote areas with poor Wi-Fi coverage. This feature is perfect for applications like remote monitoring, data collection, and control over large distances. With the A7670G module, you can be confident in maintaining stable and fast communication, even in environments where traditional internet infrastructure might be lacking.
Visual and Audio Alerts: RGB WS2812 LED & Buzzer: The GateFi 6 Channel includes both RGB WS2812 LED and a buzzer for visual and audio alerts. The WS2812 LEDs can be programmed to display a variety of colors to indicate system status or trigger alerts. The buzzer, on the other hand, provides a sound notification for critical events, system errors, or triggered alarms. Together, these features ensure that operators and users are immediately informed about the state of the system.
Wide Voltage Range: 5V to 36V DC: Offers a flexible voltage range from 5V to 36V DC, making it suitable for various applications in both consumer and industrial settings. This wide input range means that the system can be integrated into a wide array of environments, from low-power consumer applications to high-voltage industrial equipment, without the need for additional power regulation.
RS485 Communication for Industrial Integration: The GateFi 6 Channel microcontroller includes RS485 communication support, enabling it to connect and communicate with other industrial equipment, sensors, or controllers over long distances. Whether it’s a smart factory, building automation system, or remote asset management, RS485 ensures reliable communication between devices even in noisy environments.
Interface Options: Dual Type C Ports: Offers two Type C ports—one for programming and one for 4G control. The Type C interface is becoming the industry standard due to its fast data transfer speed and reversible connector, making it easier to connect the system to various devices.
Connectivity: 2.4 GHz Wi-Fi and Bluetooth 5 (LE): Is well-equipped with 2.4 GHz Wi-Fi and Bluetooth 5 (LE) for local wireless communication. Whether you need to control the system through a mobile app, communicate with nearby devices, or connect to a cloud platform, the combination of Wi-Fi and Bluetooth 5 (LE) ensures a seamless and flexible communication experience.
Applications for GateFi 6 Channel Powered by ESP32
Industrial Automation
Smart Homes & Building Automation
Remote Monitoring & Control
Security Systems
Conclusion
The GateFi 6 Channel Powered by ESP32 by SB Components with 4G connectivity is a revolutionary device that brings powerful features to both industrial and residential automation. With its robust microcontroller, versatile relay channels, easy programming interface, and extensive connectivity options, the GateFi 6 Channel offers everything you need for efficient control and monitoring of various devices and systems.
Whether you’re upgrading your existing infrastructure or starting a new automation project, the GateFi 6 Channel is a solid investment for a smarter, more connected world.
#iot applications#iot#4g connectivity#gatefi6#innovation#relay board#electronics#technology#embedded systems#microcontrollers
0 notes
Text
Understanding Embedded Computing Systems and their Role in the Modern World
Embedded systems are specialized computer systems designed to perform dedicated functions within larger mechanical or electrical systems. Unlike general-purpose computers like laptops and desktop PCs, embedded systems are designed to operate on specific tasks and are not easily reprogrammable for other uses. Embedded System Hardware At the core of any embedded system is a microcontroller or microprocessor chip that acts as the processing brain. This chip contains the CPU along with RAM, ROM, I/O ports and other components integrated onto a single chip. Peripherals like sensors, displays, network ports etc. are connected to the microcontroller through its input/output ports. Embedded systems also contain supporting hardware like power supply circuits, timing crystal oscillators etc. Operating Systems for Embedded Devices While general purpose computers run full featured operating systems like Windows, Linux or MacOS, embedded systems commonly use specialized Real Time Operating Systems (RTOS). RTOS are lean and efficient kernels optimized for real-time processing with minimal overhead. Popular RTOS include FreeRTOS, QNX, VxWorks etc. Some simple devices run without an OS, accessing hardware directly via initialization code. Programming Embedded Systems Embedded Computing System are programmed using low level languages like C and C++ for maximum efficiency and control over hardware. Assembler language is also used in some applications. Programmers need expertise in Microcontroller architecture, peripherals, memory management etc. Tools include compilers, linkers, simulators and debuggers tailored for embedded development. Applications of Embedded Computing Embedded systems have revolutionized various industries by bringing intelligence and connectivity to everyday devices. Some key application areas include: Get more insights on Embedded Computing
Unlock More Insights—Explore the Report in the Language You Prefer
French
German
Italian
Russian
Japanese
Chinese
Korean
Portuguese
Alice Mutum is a seasoned senior content editor at Coherent Market Insights, leveraging extensive expertise gained from her previous role as a content writer. With seven years in content development, Alice masterfully employs SEO best practices and cutting-edge digital marketing strategies to craft high-ranking, impactful content. As an editor, she meticulously ensures flawless grammar and punctuation, precise data accuracy, and perfect alignment with audience needs in every research report. Alice's dedication to excellence and her strategic approach to content make her an invaluable asset in the world of market insights.
(LinkedIn: www.linkedin.com/in/alice-mutum-3b247b137 )
#Embedded Computing#Embedded Systems#Microcontrollers#Embedded Software#Iot#Embedded Hardware#Embedded Programming#Edge Computing#Embedded Applications#Industrial Automation
0 notes
Text
Top 5 Tips for Learning IoT and AI

As we navigate the evolving landscapes of IoT and AI, it’s essential we establish a strong foundation in programming languages like Python and Java. Engaging in hands-on projects not only solidifies our understanding but also bridges the gap between theory and practice. By connecting with online communities, we can share insights and resources that enhance our learning. However, staying updated on industry trends and exploring real-world case studies are equally crucial. So, what are the specific strategies we can employ to maximize our efforts in these areas?
Build a Strong Programming Foundation

While we dive into the realms of IoT and AI, it’s crucial to build a strong programming foundation. Having solid programming skills not only aids in understanding complex algorithms but also equips us to handle data effectively. We should start by mastering languages like Python and Java, as they’re widely used in both fields.
Data analysis is equally important, so familiarizing ourselves with libraries like Pandas and NumPy will enhance our ability to manipulate and interpret data.
Next, we need to define clear objectives for our projects. Establishing SMART goals helps us stay focused and measure our progress. Identifying relevant data sources is essential too—both internal and external—ensuring we gather high-quality data for training AI models.
As we collect data, let’s pay attention to cleaning and preprocessing techniques, as these steps significantly impact the performance of our models.
Lastly, we should engage with online communities and forums. Collaborating with peers not only enriches our learning experience but also exposes us to diverse perspectives.
Engage in Hands-On Projects

Engaging in hands-on projects is one of the most effective ways to deepen our understanding of IoT and AI. By applying theoretical knowledge, we can see how these concepts play out in real-world scenarios.
Let’s start by building small projects that incorporate IoT devices, like using sensors to track environmental conditions or automating tasks within our homes. This practical application helps us grasp the mechanics behind these technologies.
As we progress, we can explore more complex setups, such as creating smart classrooms. Imagine using IoT-enabled projectors and interactive whiteboards to enhance collaborative learning. These projects not only solidify our skills but also demonstrate the power of IoT in educational environments.
Moreover, we shouldn’t shy away from experimenting with AI algorithms. By developing simple machine learning models, we can analyze data and gain insights into how AI interprets information. This hands-on experience encourages creativity and problem-solving, essential skills in this evolving field.
Ultimately, engaging in hands-on projects empowers us to bridge the gap between theory and practice, making our journey in IoT and AI both exciting and impactful.
Let’s dive in and start building!
Join Online Communities

In today’s digital age, joining online communities can significantly enhance our learning experience in IoT and AI. These platforms provide exclusive access to structured courses and resources that cater to our specific learning needs.
We can participate in live learning sessions with top educators, allowing us to interact directly with experts and fellow learners.
Networking opportunities abound within these communities. We can connect with diverse individuals who share our interests, fostering collaboration and support.
Engaging in discussions and exclusive chat groups enriches our understanding and exposes us to different perspectives, greatly benefiting our learning journey.
Moreover, many online communities offer certification upon course completion, which we can showcase on platforms like LinkedIn. This recognition enhances our professional credibility and supports our career advancement.
Stay Updated on Trends

Staying on top of trends in IoT and AI is essential for anyone looking to thrive in these rapidly evolving fields. We need to recognize the staggering growth projections, like the IoT market reaching $650 billion by 2026 and the expected 30.9 billion active IoT devices. This rapid expansion means we must continuously educate ourselves about emerging technologies and industry shifts.
We should pay attention to key trends, such as the ongoing chip shortage impacting IoT investments, with many semiconductor executives predicting supply chain improvements. Additionally, as IoT devices proliferate, security becomes a pressing concern. Staying informed about new regulations and security measures will help us navigate this landscape effectively.
We must also explore how AI is increasingly intertwined with IoT, providing real-time insights and enhancing decision-making across various sectors. By keeping up with research, attending webinars, and reading relevant publications, we can ensure our knowledge remains current and applicable.
In this way, we can position ourselves not just as learners but as informed participants ready to seize opportunities in the dynamic fields of IoT and AI.
Explore Real-World Case Studies

Exploring real-world case studies offers us valuable insights into how IoT and AI technologies are transforming various industries. For example, the iRobot Roomba uses AI to efficiently map home layouts and optimize cleaning patterns. This innovation, first launched in 2002, paved the way for widespread consumer adoption of smart home devices.
Similarly, Nest Labs’ smart thermostat learns user preferences, adjusting energy use accordingly, and showcases AI’s impact on energy efficiency.
In the automotive sector, Tesla’s self-driving technology employs machine learning to predict driver behavior based on extensive road data, demonstrating the potential of AI in transportation.
Additionally, companies like Kairos are leveraging AI for marketing insights, serving high-profile clients like Nike and IBM.
As we delve into these applications, we also need to consider the ethical implications, especially concerning privacy and security with technologies like facial recognition.
Frequently Asked Questions
How to Learn AI and Iot?
To learn AI and IoT effectively, we should focus on programming and data analysis. Let’s engage in hands-on projects, join communities, and stay updated on trends to deepen our understanding and practical skills.
Which Is Better to Learn Iot or Ai?
When deciding between IoT and AI, we should consider our interests. If we enjoy hardware and connectivity, IoT’s practical applications might excite us. If data analysis fascinates us, AI’s predictive capabilities could be more appealing.
How Can AI Be Used in Iot?
AI enhances IoT by enabling smart devices to make real-time decisions, learn patterns, and automate tasks. Together, they improve efficiency and responsiveness in various sectors, transforming how we interact with technology daily.
Which Is Better, Aith or Ai?
When we compare AI and AIth, it’s clear that AIth offers greater integration by combining AI’s capabilities with IoT. This synergy allows for smarter decision-making and enhanced efficiency in real-world applications.
Conclusion
In conclusion, mastering IoT and AI starts with a solid programming foundation and practical experience. By diving into hands-on projects, we can truly grasp these technologies. Connecting with online communities keeps us informed and inspired, while staying updated on industry trends ensures we remain relevant. Finally, exploring real-world case studies helps us understand the ethical implications of our work. Let’s embrace this journey together and unlock the potential of IoT and AI!
How Zekatix Helps You on the Journey
Zekatix is here to make your journey into IoT and AI smoother, combining all the steps essential for mastering these technologies. With courses that build your programming foundation, hands-on project resources, and insightful case studies, Zekatix equips you with everything you need to grow. Our platform connects learners to active online communities, keeping you updated on the latest trends and innovations in IoT and AI. As you explore these rapidly evolving fields, Zekatix serves as your partner in learning and innovation, helping you thrive in tech. Join today and take the next leap toward mastering the future of technology!
Sign up for free courses here. Visit Zekatix for more information.
Sign up for free courses here.
Visit Zekatix for more information.
#edtech company#courses#embedded systems#nanotechnology#artificial intelligence#embeded#academics#online courses#robotics#zekatix#AI#IOT#iotsolutions#iot applications#iot development services#innovation#embedded#iot platform#techinnovation
0 notes
Text
SRI - Swarm Robotics for Indian Agriculture
INTRODUCTION Robotics is expected to play a major role in the agricultural domain, and often multi-robot systems and collaborative approaches are mentioned as potential solutions to improve efficiency and system robustness. Among the multi-robot approaches, swarm robotics stresses aspects like flexibility, scalability and robustness in solving complex tasks, and is considered very relevant for…
0 notes
Text
youtube
NXP: MCX A Series Launch Video
https://www.futureelectronics.com/resources/featured-products/nxp-mcx-n-mcx-a-microcontrollers . MCX A Series all-purpose microcontrollers (MCUs) address a wide range of applications with scalable device options, low power and intelligent peripherals. Designed to allow engineers to do more, the new MCX A series is optimized with the essential features, innovative power architecture and software compatibility required by many embedded applications. https://youtu.be/fjNG2t4TBXQ
#nxp#MCX#MCX A#all-purpose microcontrollers#MCU#MCX A series#microchip#small-footprint MCU#software compatibility#embedded applications#industrial sensors#motor control#power system#controllers#IoT devices#Youtube
0 notes
Text

Embedded Systems for NMEA 2000 Development and Prototyping Support Marine Applications
Copperhill Technologies offers Arduino-Compatible NMEA 2000 development boards and an NMEA 0183/NMEA 2000 HAT for the Raspberry Pi, ideal for marine applications such as OpenCPN, OpenPlotter, Signal K, and CANBoat.
#nmea2000#n2k#canbus#embedded systems#raspberry pi#arduino#canboat#opencpn#openplotter#signal k#marine applications
0 notes
Text
IoT Development; A Complete Guide, on Bringing Devices from Idea to Implementation

In todays paced tech world, the Internet of Things (IoT) has emerged as a game changer transforming the way we engage with our environment. At Blockverse Infotech Solutions we recognize the power of devices providing customized solutions to bring ideas to life and seamlessly integrate them into the digital realm.
The Internet of Things (IoT) has evolved from a buzzword to an aspect of contemporary technology influencing various facets of our everyday routines. From homes and wearable gadgets to automation and healthcare systems IoT enables us to connect and empower ourselves like never before. However transitioning from conceptualization to implementation of solutions can be overwhelming without guidance.
Conceptualization marks the phase, in IoT development. It entails identifying the problem or opportunity that can be addressed through technology and envisioning how interconnected devices can improve efficiency, convenience or safety. At Blockverse Infotech Solutions we work closely with clients to brainstorm ideas grasp their needs and devise IoT solutions tailored specifically for them.
Once the concept is solidified, the development phase begins. This involves designing and prototyping IoT devices, selecting appropriate sensors and connectivity protocols, and developing the software infrastructure to collect, analyze, and act upon data generated by the devices. Our team of skilled developers and engineers at Blockverse Infotech Solutions leverages cutting-edge technologies to build robust and scalable IoT solutions that meet the highest standards of performance and reliability.
Testing and validation are integral parts of the development process, ensuring that IoT devices function as intended and deliver the desired outcomes. Through rigorous testing procedures and simulation environments, we identify and rectify any issues or vulnerabilities, ensuring that the deployed IoT solutions operate seamlessly in real-world scenarios.
Deployment marks the culmination of the IoT development journey, as the solutions are implemented and integrated into existing systems or environments. From device provisioning and network configuration to data management and security protocols, our experts at Blockverse Infotech Solutions handle every aspect of the deployment process with precision and care, ensuring a smooth transition from development to operation.
Post-deployment support and maintenance are essential for ensuring the long-term success and sustainability of IoT solutions.��At Blockverse Infotech Solutions, we offer comprehensive support services, including monitoring, troubleshooting, and software updates, to keep IoT devices running smoothly and efficiently.
In conclusion, navigating the complex landscape of IoT development requires expertise, innovation, and a comprehensive understanding of the technology. With Blockverse Infotech Solutions providing tailored solutions for IoT devices, businesses and organizations can embark on their IoT journey with confidence, knowing that they have a trusted partner to guide them from concept to deployment and beyond.
#internet of things#iot#iot devices#iot projects#iot applications#iot development company#iot device management software#embedded system design#iot device management app#embedded operating system#iot monitoring software#embedded systems#what is embedded system
0 notes
Text
Post-RAG Evolution: AI’s Journey from Information Retrieval to Real-Time Reasoning
New Post has been published on https://thedigitalinsider.com/post-rag-evolution-ais-journey-from-information-retrieval-to-real-time-reasoning/
Post-RAG Evolution: AI’s Journey from Information Retrieval to Real-Time Reasoning


For years, search engines and databases relied on essential keyword matching, often leading to fragmented and context-lacking results. The introduction of generative AI and the emergence of Retrieval-Augmented Generation (RAG) have transformed traditional information retrieval, enabling AI to extract relevant data from vast sources and generate structured, coherent responses. This development has improved accuracy, reduced misinformation, and made AI-powered search more interactive. However, while RAG excels at retrieving and generating text, it remains limited to surface-level retrieval. It cannot discover new knowledge or explain its reasoning process. Researchers are addressing these gaps by shaping RAG into a real-time thinking machine capable of reasoning, problem-solving, and decision-making with transparent, explainable logic. This article explores the latest developments in RAG, highlighting advancements driving RAG toward deeper reasoning, real-time knowledge discovery, and intelligent decision-making.
From Information Retrieval to Intelligent Reasoning
Structured reasoning is a key advancement that has led to the evolution of RAG. Chain-of-thought reasoning (CoT) has improved large language models (LLMs) by enabling them to connect ideas, break down complex problems, and refine responses step by step. This method helps AI better understand context, resolve ambiguities, and adapt to new challenges. The development of agentic AI has further expanded these capabilities, allowing AI to plan and execute tasks and improve its reasoning. These systems can analyze data, navigate complex data environments, and make informed decisions. Researchers are integrating CoT and agentic AI with RAG to move beyond passive retrieval, enabling it to perform deeper reasoning, real-time knowledge discovery, and structured decision-making. This shift has led to innovations like Retrieval-Augmented Thoughts (RAT), Retrieval-Augmented Reasoning (RAR), and Agentic RAR, making AI more proficient at analyzing and applying knowledge in real-time.
The Genesis: Retrieval-Augmented Generation (RAG)
RAG was primarily developed to address a key limitation of large language models (LLMs) – their reliance on static training data. Without access to real-time or domain-specific information, LLMs can generate inaccurate or outdated responses, a phenomenon known as hallucination. RAG enhances LLMs by integrating information retrieval capabilities, allowing them to access external and real-time data sources. This ensures responses are more accurate, grounded in authoritative sources, and contextually relevant. The core functionality of RAG follows a structured process: First, data is converted into embedding – numerical representations in a vector space – and stored in a vector database for efficient retrieval. When a user submits a query, the system retrieves relevant documents by comparing the query’s embedding with stored embeddings. The retrieved data is then integrated into the original query, enriching the LLM context before generating a response. This approach enables applications such as chatbots with access to company data or AI systems that provide information from verified sources. While RAG has improved information retrieval by providing precise answers instead of just listing documents, it still has limitations. It lacks logical reasoning, clear explanations, and autonomy, essential for making AI systems true knowledge discovery tools. Currently, RAG does not truly understand the data it retrieves—it only organizes and presents it in a structured way.
Retrieval-Augmented Thoughts (RAT)
Researchers have introduced Retrieval-Augmented Thoughts (RAT) to enhance RAG with reasoning capabilities. Unlike traditional RAG, which retrieves information once before generating a response, RAT retrieves data at multiple stages throughout the reasoning process. This approach mimics human thinking by continuously gathering and reassessing information to refine conclusions. RAT follows a structured, multi-step retrieval process, allowing AI to improve its responses iteratively. Instead of relying on a single data fetch, it refines its reasoning step by step, leading to more accurate and logical outputs. The multi-step retrieval process also enables the model to outline its reasoning process, making RAT a more explainable and reliable retrieval system. Additionally, dynamic knowledge injections ensure retrieval is adaptive, incorporating new information as needed based on the evolution of reasoning.
Retrieval-Augmented Reasoning (RAR)
While Retrieval-Augmented Thoughts (RAT) enhances multi-step information retrieval, it does not inherently improve logical reasoning. To address this, researchers developed Retrieval-Augmented Reasoning (RAR) – a framework that integrates symbolic reasoning techniques, knowledge graphs, and rule-based systems to ensure AI processes information through structured logical steps rather than purely statistical predictions. RAR’s workflow involves retrieving structured knowledge from domain-specific sources rather than factual snippets. A symbolic reasoning engine then applies logical inference rules to process this information. Instead of passively aggregating data, the system refines its queries iteratively based on intermediate reasoning results, improving response accuracy. Finally, RAR provides explainable answers by detailing the logical steps and references that led to its conclusions. This approach is especially valuable in industries like law, finance, and healthcare, where structured reasoning enables AI to handle complex decision-making more accurately. By applying logical frameworks, AI can provide well-reasoned, transparent, and reliable insights, ensuring that decisions are based on clear, traceable reasoning rather than purely statistical predictions.
Agentic RAR
Despite RAR’s advancements in reasoning, it still operates reactively, responding to queries without actively refining its knowledge discovery approach. Agentic Retrieval-Augmented Reasoning (Agentic RAR) takes AI a step further by embedding autonomous decision-making capabilities. Instead of passively retrieving data, these systems iteratively plan, execute, and refine knowledge acquisition and problem-solving, making them more adaptable to real-world challenges.
Agentic RAR integrates LLMs that can perform complex reasoning tasks, specialized agents trained for domain-specific applications like data analysis or search optimization, and knowledge graphs that dynamically evolve based on new information. These elements work together to create AI systems that can tackle intricate problems, adapt to new insights, and provide transparent, explainable outcomes.
Future Implications
The transition from RAG to RAR and the development of Agentic RAR systems are steps to move RAG beyond static information retrieval, transforming it into a dynamic, real-time thinking machine capable of sophisticated reasoning and decision-making.
The impact of these developments spans various fields. In research and development, AI can assist with complex data analysis, hypothesis generation, and scientific discovery, accelerating innovation. In finance, healthcare, and law, AI can handle intricate problems, provide nuanced insights, and support complex decision-making processes. AI assistants, powered by deep reasoning capabilities, can offer personalized and contextually relevant responses, adapting to users’ evolving needs.
The Bottom Line
The shift from retrieval-based AI to real-time reasoning systems represents a significant evolution in knowledge discovery. While RAG laid the groundwork for better information synthesis, RAR and Agentic RAR push AI toward autonomous reasoning and problem-solving. As these systems mature, AI will transition from mere information assistants to strategic partners in knowledge discovery, critical analysis, and real-time intelligence across multiple domains.
#acquisition#Agentic AI#agentic RAG#Agentic RAR#agents#ai#AI reasoning#AI systems#AI-powered#AI-powered search#Analysis#applications#approach#Article#Artificial Intelligence#autonomous#chatbots#data#data analysis#data sources#Database#databases#Deep Reasoning#development#Developments#domains#driving#embeddings#engine#engines
1 note
·
View note
Text
What is the difference between IoT and embedded systems?
The rapid advancement of technology has led to a merging of boundaries between different sectors. This convergence is particularly noticeable in the realm of IoT (Internet of Things) embedded systems, where the terms "IoT" and "embedded system" are often used interchangeably. However, it's important to recognize that embedded systems and IoT are distinct concepts, even though they share some similarities.
Embedded systems have been in existence since as early as 1965 when Autonetics, a company, created a small computer for use in a missile guidance system. These embedded systems are essentially standalone devices designed with a specific, dedicated function in mind. On the other hand, an IoT embedded system is an embedded system that possesses the added capability of connecting to the internet, enabling communication with other IoT embedded systems.
In our daily lives, we are surrounded by IoT embedded systems, including devices such as set-top boxes, Point-of-Sale (POS) terminals, various medical devices, "smart" appliances like refrigerators, bicycles, fitness trackers, and even parking meters.
In the following discussion, we will delve into the intricacies of embedded systems designed for IoT devices. We will explore what defines an embedded system for IoT, its capabilities, and practical applications of embedding IoT functionality into these systems.
The key distinction between IoT (Internet of Things) and embedded systems boils down to one crucial factor: connectivity. Even an embedded system, like a pacemaker, can be transformed into an IoT embedded system when it gains the ability to communicate with the external world, such as sending heart-rate data to a central database.
Another distinguishing feature is that IoT encompasses a broader category of devices representing the interconnected world, whereas an embedded system pertains specifically to the hardware within these devices.
The fundamental difference between an embedded operating system and an IoT operating system lies in the necessity for IoT systems to support connectivity. The capability of IoT devices to network and communicate sets apart plain embedded systems from their IoT counterparts.
In every IoT scenario, there's an embedded system at its core, which is why the term "IoT embedded system" is used. Initially, there exists an embedded system, and then additional features are integrated to transform it into an IoT device.
Embedded systems can be remarkably sophisticated, such as robotic systems used in manufacturing or data warehouses. However, their function as pure embedded systems remains limited to their specific purpose until they acquire the ability to communicate and establish connectivity with other IoT embedded systems.
Therefore, the primary distinction between an embedded system and an IoT embedded system hinges on the latter's capacity for communication and connectivity.
0 notes
Text
Teksun Inc is an ISO 9001:2015 certified IoT and AI Solutions Company specializing in Product Engineering Services supporting ODM & OEM for numerous B2B Applications & Use Cases. To know more about browse: https://teksun.com/ Contact us ID: [email protected]
#Teksun#Technology services#Artificial intelligence#Machine learning#IoT solutions#Embedded systems#Product engineering#Software development#Hardware design#Firmware development#Cloud computing#Industrial automation#Wireless communication#IoT applications
0 notes
Text
Kinktober Day 0
This is the set-up for Kinktober which I'm doing as a linear narrative.
To be clear, there may be 3 or 4 chapters that don't actually have any kink and are just lil bits of fluff and we all agree to be chill about that.
Each chapter before the cut will have all info required on characters and kinks involved. If there is any non-con this will be in bright red but the instances of this will be few and brief as we are operating on a safe-word system and will have safety measures for if characters ignore safe-wording.
-
This must be what Will Smith’s character felt like at the start of Men In Black. What the hell were you doing here? There were a mix of genders in the room, but the one thing everyone seemed to have in common was confidence coming off of them in waves and that they didn’t look like you. They didn’t look like each other either, but they all looked more likely to have walked off of a modelling set than out of a military base.
You weren’t trained in psyops, but this seemed like it might be something in that department. Why else did so many of these candidates ooze beauty and authority? You shouldn’t bloody be here. The application had been secretive, a form slid over a desk from your superior officer who got it from his who got it from his in a chain with no obvious end. Someone had picked you out for this, and you were starting to think that wasn’t a good thing.
Were the people here higher up the chain than you or at the same level? You try to summon confidence, you’re not exactly some green private at their first training exercise. You’re special fucking forces. Yeah the monsters in the SAS or the SBS are out there slaughtering the bad guys, but they wouldn’t be doing shit without the Signal Regiment. You had to go through 25 weeks of hell to make it in. Just because you’re comms, doesn’t mean you didn’t have to prove conduct after capture or jump out of a damn aeroplane to pass training. And you had already served a year in infantry beforehand.
So you get over yourself and wait for further instructions. You have just as much right to be here as any of them.
The first tests go ahead. Fitness (you don’t fall last in the pack for performance, but you’re lower than the middle), gun handling (solidly middle of the pack), comms (you come first). It’s all suspiciously standard stuff. And then you are all put into an actual scenario.
You go into a room. It reeks of blood and sex and there are 3 people, one unconscious. The woman on the floor has a thick collar around her neck and is in scant lingerie that has very clearly been torn for access. There are bruises littering her body, rope marks embedded into her skin. The two conscious people are a man and a woman. She is screaming at the group to shoot him.
He’s told to get on his knees as the bulk of the group assess him as the bigger threat. You ignore them and go to gently check on the woman on the floor along with another candidate, trusting that the rest will subdue both current threats.
“These marks are pretty consistent with BSDM, not prolonged abuse. And the collar has an emergency quick release they’d be able to operate themselves if they had to” the other candidate says.
You immediately get your own gun trained to the other woman when you glance up and see her totally free from any restraint and in close range to one of the other candidates, a protest coming from one of the men who has went to comfort her.
“Put your gun down, you’re scaring her” he hisses.
“Until we have further information on what is happening here, all suspects should be treated as hostile and questioned.”
You don’t know if you got it right, but it seems wildly irresponsible to just decide that the big man must be the bad guy but she is definitely innocent. Mostly it’s just a strange scenario you’ve been put in, but in the field there can’t be trust for strangers. It’s not a courthouse, everyone is assumed hostile until there is proof to the contrary.
It isn’t resolved, you are all just told the exercise is over. One by one candidates are called into an office until it’s only you left. You’re absently wondering if you want to make ramen for dinner tonight when you are called in. The sinking feeling that you are in over your head hits you full force. You know one of the two people in this room.
Captain John Price, SAS. You’ve spoken with him before (well you’ve rattled off intel to him through a radio before) and you are well aware he is not to be fucked with.
“What did you think of the exercise then?” he asks, both him and the woman sitting behind the desk openly staring at you like predators with their eyes on a tasty morsel.
“I’m not sure what was being tested sir. I reacted as my training encouraged sir.”
“At ease, soldier. A real answer” the woman says and you squash back a reaction to the American accent.
Your shoulders loosen off. It’s not like you applied for whatever this is, so it isn’t any great loss if they’re about to kick you out. You’ve got ramen to get to, another quiet night at home alone to either enjoy or feel bitterly lonely about. It’s a toss up these days which mood will strike when the lack of warmth starts to bite.
“Most of your candidates need to be sent back to basic. They worked on baseless assumptions rather than taking control of the scene and figuring out what had happened once any danger was subdued. That woman could have killed two of them and taken a third hostage in seconds.”
“I agree” the woman says with a smug little smile, “British forces aren’t what they used to be.”
Price laughs.
“Your yanks would have done far worse. You made the right call. The woman on the floor was in a consensual relationship with the man, the marks were received willingly. But since there’d be no way of knowing, both of the threats needed to be removed. Questioning would have sorted out the truth.”
It was a weird fucking exercise to use. What were they testing with that kind of scenario? Implicit gender bias? But then why the kinky angle when they could have removed the casualty entirely and it served the same purpose? The whole thing was starting to make your skin itch as a folder was put on the table in front of you. You caught a nod from the woman and opened it, feeling like you were about to throw up.
“What is this?”
“Insurance. You break NDA and it’s not a court that’s going to crucify you” Price said, almost cheerily as you looked at photos of yourself.
One of them was taken of you sleeping in bed. The next the camera turned to have you in the background in bed while Price took a selfie barely inches from you, smiling for the camera as if he had any right to be there. More photos. Most of you, but some of loved ones. There is a flash of an image in your head, your last moment being the panic of waking up with a wire around your neck. You wouldn’t have broken NDA, but the overkill makes you unbearably curious. How bad is what they are recruiting for if they have to kill anyone who leaks it?
“I understand sir.”
The woman tilted her head as if you had said something interesting. Did the others react badly you wonder? The thing about being special forces signal regiment was that the lengths that the military would go to didn’t surprise you anymore. They created monsters to fight monsters and hid them away in the dark while they paraded out their nice, proper soldiers for the public. Good family men in uniform, advocates for mental health, veterans who were revered as heroes. The special forces were not those men. Captain John Price was certainly not one of those men.
Did you sometimes find it hard to sleep at night? Of course, you helped those monsters even when the line between good and evil was so thoroughly crossed that you wanted to scream at the world and never stop. But without them? Without them everybody would know exactly how cruel people could be because there would be nothing stopping them.
“This is the Kennel” the woman said as a screen behind her came to life.
The schematics were insane the more you drank them in. Underground bunker, recreational facilities and what seemed to be apartments. You would think it would be some rich person’s doomsday bunker if not for the layers of security. The apartments were locked down tight, there were guard posts and an ungodly amount of surveillance. Nobody was getting out of there if these people didn’t want them to.
You had seen plenty of prisons from high end to metal cages in caves. It was your job to get intel, to guide people through rescue missions or escapes. But this was something else.
“You want to build a luxury secure facility?” you asked, feeling the furrow in your brow and the incessant itching of your skin.
The woman clicked a button and the screen changed. Holy shit, they didn’t want to build it because it had already been built. Where the fuck was this? This was big and it must have costs billions, how on earth had you never heard of it? It wasn’t exactly some dingy black site.
“We need them, but this job twists people. Some of them can still keep it under control at home, some just need to stay immediately after a deployment to calm down. There are 6 full time residents right now. Got 5 part timers and 5 who visit when they need. Not all on our side of things.”
“There are tangos in there?”
“Officially nobody is in there, the Kennel doesn’t exist. Unofficially? It’s Switzerland. A rabid dog will bite whoever you point it to.”
You wanted to be outraged, but was this really so different from all the other foul things you knew happened in the background? A luxury blacksite holding the “good” guys and the “bad” guys alike who couldn’t be trusted out in public but who were needed to unleash upon the enemy. This was so fucked up but you imagined that the military did 5 equally as fucked up things before breakfast.
“What is this job exactly?”
Price crossed his arms and rocked back on his heels, staring you down and making you feel tiny in that chair.
“Sometimes the best place you can be to keep the world safe is on your back.”
“Excuse me?”
He was not implying what you thought he was surely. It was just unfortunate phrasing.
“Just an expression, I imagine only a few of them would want you on your back. Think at least half would enjoy you on your knees.”
You held his stare, determined to wait him out. He was fucking with you. This was some bizarre test and you had no idea how you were supposed to respond.
“He’s asking you to play bitch for his dogs soldier. They get out of hand when they can’t rut” the woman said as if that cleared things up.
“I didn’t figure out anything about the whole BDSM thing or whatever it was during that exercise. It was the other guy. I don’t do any of that stuff.”
They ignored you.
“It’s a month-long contract to see if it improves their behaviour. After that you are free to do whatever you want with a shiny promotion and enough money that you can retire to Hawaii with a glowing record and military honours if you’d prefer” the woman started.
“All you have to do is take whatever they want to give you. No safewords, you can’t stop it once you start” Price finished.
“No.”
“Not even going to consider the offer?” Price asked, almost eager.
“I’m not considering an offer that actively puts me in an unsafe situation with no way to get out.”
“Told you Kate.”
You wanted to be out of this fucking office already. You thought about what previous attempts might have looked like. Sex workers who were thrown in with monsters and torn to shreds. Maybe ones who begged to leave but got assassinated the moment they got home and started talking. Because this wasn’t sex work, it was a military operation. A civilian was never going to survive that situation, not with the kind of monsters you imagined the Kennel held.
“You know why the soldier who knew all about BDSM failed?” Price asked, closer than you remembered him being. “He said yes. Agreed to the terms. I’ve got no time for someone who can’t take care of themselves and is going to get eaten alive within the first 24 hours because they were too eager to please to say no. They try break you? You safeword and I come in and break them.”
There was something in the back of your mind somewhere that found the offer grotesquely appealing. You thought it unlikely they would take you once you told them you were a virgin. It just sort of happened, you didn’t know how to meet people and you were now at an age where the pressure felt insurmountable. Did you tell that to someone on a first date? Did you not tell them and they go too hard and hurt you? What if you couldn’t even do it properly?
This would be work. This would be a military operation that allowed assets to be used rather than put down if it was successful. You’d be getting used, but maybe you wouldn’t be lonely.
It was the negotiations that did you in. The warm hand of Price on your shoulder while he explained aftercare procedure. Some of them would do it themselves, but some they’d probably need to drag off of you and then Price himself would take over. If he wasn’t available for any reason, Kate would.
They framed it like it was a heroic pursuit. These people were broken, they needed someone to start patching up the cracks. Your virginity it transpired was an asset given that they knew just the person who would look after you for your first session. Someone in the Kennel had a sizable virginity kink and you were assured it was one of the part-timers who wasn’t prone to extreme violence the way the residents were. You’d get an info pack with details the day before.
The final nail in the coffin that had you signing the dotted line was Price (deliberately you realised quickly once you got a moment to breathe) mentioning Soap. You knew him. Not in person, but you had talked him through diffusing a bomb before. He had flirted up a storm and his warmth over that radio even when he was seconds from dying at any given point had stuck with you for weeks. It was only a month. You just had to do this for a month.
October 1st you would lose your virginity in a bunker that didn’t exist to a soldier you didn’t know, one who needed you to stop them from fully becoming a monster. Fuck.
158 notes
·
View notes
Text
ever wonder why spotify/discord/teams desktop apps kind of suck?
i don't do a lot of long form posts but. I realized that so many people aren't aware that a lot of the enshittification of using computers in the past decade or so has a lot to do with embedded webapps becoming so frequently used instead of creating native programs. and boy do i have some thoughts about this.
for those who are not blessed/cursed with computers knowledge Basically most (graphical) programs used to be native programs (ever since we started widely using a graphical interface instead of just a text-based terminal). these are apps that feel like when you open up the settings on your computer, and one of the factors that make windows and mac programs look different (bc they use a different design language!) this was the standard for a long long time - your emails were served to you in a special email application like thunderbird or outlook, your documents were processed in something like microsoft word (again. On your own computer!). same goes for calendars, calculators, spreadsheets, and a whole bunch more - crucially, your computer didn't depend on the internet to do basic things, but being connected to the web was very much an appreciated luxury!
that leads us to the eventual rise of webapps that we are all so painfully familiar with today - gmail dot com/outlook, google docs, google/microsoft calendar, and so on. as html/css/js technology grew beyond just displaying text images and such, it became clear that it could be a lot more convenient to just run programs on some server somewhere, and serve the front end on a web interface for anyone to use. this is really very convenient!!!! it Also means a huge concentration of power (notice how suddenly google is one company providing you the SERVICE) - you're renting instead of owning. which means google is your landlord - the services you use every day are first and foremost means of hitting the year over year profit quota. its a pretty sweet deal to have a free email account in exchange for ads! email accounts used to be paid (simply because the provider had to store your emails somewhere. which takes up storage space which is physical hard drives), but now the standard as of hotmail/yahoo/gmail is to just provide a free service and shove ads in as much as you need to.
webapps can do a lot of things, but they didn't immediately replace software like skype or code editors or music players - software that requires more heavy system interaction or snappy audio/visual responses. in 2013, the electron framework came out - a way of packaging up a bundle of html/css/js into a neat little crossplatform application that could be downloaded and run like any other native application. there were significant upsides to this - web developers could suddenly use their webapp skills to build desktop applications that ran on any computer as long as it could support chrome*! the first applications to be built on electron were the late code editor atom (rest in peace), but soon a whole lot of companies took note! some notable contemporary applications that use electron, or a similar webapp-embedded-in-a-little-chrome as a base are:
microsoft teams
notion
vscode
discord
spotify
anyone! who has paid even a little bit of attention to their computer - especially when using older/budget computers - know just how much having chrome open can slow down your computer (firefox as well to a lesser extent. because its just built better <3)
whenever you have one of these programs open on your computer, it's running in a one-tab chrome browser. there is a whole extra chrome open just to run your discord. if you have discord, spotify, and notion open all at once, along with chrome itself, that's four chromes. needless to say, this uses a LOT of resources to deliver applications that are often much less polished and less integrated with the rest of the operating system. it also means that if you have no internet connection, sometimes the apps straight up do not work, since much of them rely heavily on being connected to their servers, where the heavy lifting is done.
taking this idea to the very furthest is the concept of chromebooks - dinky little laptops that were created to only run a web browser and webapps - simply a vessel to access the google dot com mothership. they have gotten better at running offline android/linux applications, but often the $200 chromebooks that are bought in bulk have almost no processing power of their own - why would you even need it? you have everything you could possibly need in the warm embrace of google!
all in all the average person in the modern age, using computers in the mainstream way, owns very little of their means of computing.
i started this post as a rant about the electron/webapp framework because i think that it sucks and it displaces proper programs. and now ive swiveled into getting pissed off at software services which is in honestly the core issue. and i think things can be better!!!!!!!!!!! but to think about better computing culture one has to imagine living outside of capitalism.
i'm not the one to try to explain permacomputing specifically because there's already wonderful literature ^ but if anything here interested you, read this!!!!!!!!!! there is a beautiful world where computers live for decades and do less but do it well. and you just own it. come frolic with me Okay ? :]
*when i say chrome i technically mean chromium. but functionally it's same thing
462 notes
·
View notes