#install OpenSSL Windows
Explore tagged Tumblr posts
Text
How to Install OpenSSL on Windows Computers
In this article, we shall discuss how to Install OpenSSL on Windows Computers. OpenSSL is an open-source command-line tool that is used to generate the SSL certificate and private key and is available in both versions 32 and 64 bit. Please see How to fix Windows Update Fails with Error 0x80092004, how to Fix the Port used for the Virtualhost is not an Apache Listen Port, and Shell Scripting: How…
#convert key format OpenSSL#convert PEM to DER OpenSSL#extract public key OpenSSL#generate private public key OpenSSL#how to use OpenSSL on Windows#install OpenSSL Windows#Microsoft Windows#OpenSSL installation#OpenSSL key conversion#OpenSSL key generation tutorial#OpenSSL key management#OpenSSL public key extraction#OpenSSL Windows#OpenSSL Windows installation steps#Windows#Windows 10#Windows 11#Windows OpenSSL setup#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022
1 note
·
View note
Text
WSL recently went open source but even before then it was really good.
Windows Subsystem for Linux is a thing by microsoft which just allows you to run linux inside of your windows PC. I just used it whenever i needed some command line tooling or shit that windows doesn't have (grep, wc, openssl) but i found out only a billion years later it can run full gui apps (just download them and run them from the command line) or you can also run an Entire Desktop environment to basically just have a Linux system inside of your windows installation without any virtual machines or messing about with dual booting or partitioning.
WSL will run a lot worse than normal linux however its (i think) much easier to set up and you can access all your normal windows files from it as well.
It would be good to try if you want to switch to linux but you wanna try it out, however i dont think i have any windows devices anymore to see how well it works and how easy it is to set up a DE
11 notes
·
View notes
Text
installing openssl on windows:
winget install -e --id ShiningLight.OpenSSL.Dev
it fucking runs for 4 minutes and opens like 3 different windows showing different bullshit before finishing
installing openssl on arch
sudo pacman -S openssl
i press "enter" twice and it finishes in less than a second
3 notes
·
View notes
Text
Microsoft PQC ML-KEM, ML-DSA algorithms for windows & Linux

Microsoft has made significant progress in post-quantum cryptography (PQC) with SymCrypt-OpenSSL version 1.9.0 for Linux and Windows Insiders (Canary Channel Build 27852 and higher). This modification allows customers to test PQC algorithms like ML-KEM and ML-DSA in actual operational situations. Linux and Windows Insiders Get Quantum-Resistant Cryptography.
Due to quantum computing, modern cryptography faces significant challenges. Microsoft is providing early access to PQC capabilities to help organisations evaluate the performance, interoperability, and integration of these novel algorithms with current security infrastructure. This pragmatic approach helps security teams identify challenges, refine implementation strategies, and ease the transition when industry standards evolve. Early adoption also helps prevent new vulnerabilities and protect private data from quantum threats.
Next-generation cryptography API update
Cryptography API: Next Generation (CNG) enhancements are crucial to this Windows edition. CryptoAPI will be superseded forever by CNG. It is extendable and cryptography-independent. Programmers designing programs that allow safe data production and sharing, especially across insecure channels like the Internet, use CNG. CNG developers should know C, C++, and Windows, though it's not required. Cryptography and security knowledge are also advised.
Developers designing CNG cryptographic algorithm or key storage providers must download Microsoft's Cryptographic Provider Development Kit. First to support CNG are Windows Server 2008 and Vista. The latest PQC upgrades use encrypted communications, CNG libraries, and certificates.
New Windows PQC Algorithms
Microsoft is providing ML-KEM and ML-DSA, two NIST-standardized algorithms, to Windows Insiders via CNG updates.
Developers can now try ML-KEM for public key encapsulation and key exchange. This helps prepare for the “harvest now, decrypt later” scenario, in which hackers store encrypted data now to use a quantum computer to decipher it tomorrow. Microsoft proposes a hybrid method that combines ML-KEM with RSA or ECDH for defence in depth throughout the transition, ideally with NIST security level 3 or higher.
By incorporating ML-DSA in CNG, developers can evaluate PQC algorithms for digital signature verification of identity, integrity, or authenticity. Microsoft recommends a hybrid approach, using ML-DSA alongside RSA or ECDSA throughout the transition.
Size and performance will affect these new algorithms, according to preliminary research. Customers should analyse these consequences on their environment and apps early.
Customers can test installing, importing, and exporting ML-DSA certificates to and from the certificate store and CNG and PQC updates using the Windows certificate API interface win crypt. PQ certificate chains and trust status can be verified.
PQC Linux Features
Microsoft is releasing PQC upgrades in the SymCrypt provider for OpenSSL 3 because Linux customers expect them. The provider allows Linux programmers to use OpenSSL's API surface, which uses SymCrypt cryptographic procedures.
The latest IETF internet draft recommends SymCrypt-OpenSSL 1.9.0 for TLS hybrid key exchange testing. This lets you prepare for “harvest now, decrypt later” risks early. This feature allows for a full study of how hybrid PQC algorithms affect handshake message length, TLS handshake delay, and connection efficiency. Such research are needed to understand PQC's actual trade-offs.
It is important to remember that SymCrypt-OpenSSL will be updated when standards change to ensure compliance and compatibility, and that Linux updates are based on draft specifications.
What Next?
PQC's Linux and Windows Insider integration must be described first.
Plans call for more features and improvements:
Upcoming efforts include adding SLH-DSA to SymCrypt, CNG, and SymCrypt-OpenSSL.
Add new algorithms to assure broad compatibility as PQC standards expand, improve security, and comply with international law.
Working with industry partners on X.509 standardisations for the IETF's LAMPS working group's broad use of ML-DSA algorithm, composite ML-DSA, SLH-DSA, ML-KEM, and LMS/XMSS. These efforts will involve PKI use cases and signature approaches for firmware and software signing.
TLS hybrid key exchange for Windows users is being implemented using the Windows TLS stack (Schannel).
Develop and standardise quantum-safe authentication methods for TLS and other IETF protocols including SLH-DSA, Composite ML-DSA, and pure ML-DSA with the IETF. SymCrypt for OpenSSL, Windows TLS stack (Schannel), and Linux Rust Wrapper will deliver standards as they are established.
Active Directory Certificate Services actively supports PQC. Customers setting up a Certification Authority (CA) can use ML-DSA-based CA certificates. PQC algorithms sign CA-issued CRLs for customers who enrol in end-entity certificates. We'll support all ADCS role services.
Supporting PQC certificates in Microsoft Intune's Certificate Connector lets endpoints and mobile devices sign up for quantum-safe credentials. This will unlock SCEP & PKCS #12 scenarios for on-premises CAs utilising ADCS.
TLS 1.3 is essential for PQC. Microsoft strongly advises customers to abandon older TLS protocols.
These new features will be available to Windows Insiders and development channels for real-world testing. Microsoft can make incremental modifications before release by getting feedback on usability, security, and compatibility. Microsoft will distribute dependable and compatible solutions to supported platforms using a flexible and adaptable approach after standards are finalised. Working with standards organisations and industry partners will ensure features fit global regulatory framework and ecosystem needs.
Future challenges and prospects
Due to their youth, PQC algorithms are an emerging field. This shows how important “Crypto Agility” is in building solutions that can use different algorithms or be modified when standards change.
Microsoft recommends hybrid PQ and crypto-agile solutions for PQC deployment. Composite certificates and TLS hybrid key exchange use PQ and RSA or ECDHE algorithms. Pure PQ implementations should increase as algorithms and standards improve.
Despite integration being a turning point, PQC algorithms' performance, interoperability with current systems, and acceptance remain issues.
Performance: PQC algorithms often require more processing power than standard algorithms. Its efficient implementation without affecting system performance is a big hurdle. Technology for hardware acceleration and optimisation is essential. Keccak is utilised in many PQ algorithms, and hardware acceleration is needed to boost its performance for PQC cryptography.
Larger key encapsulation and digital signatures, especially in hybrid mode, may increase TLS round-trip time. Although signatures cannot be compressed, IETF proposals are examining certificate compression and TLS key sharing prediction. These effects should be assessed on applications and surroundings.
Adoption and Compatibility: PQC requires upgrading and replacing cryptographic infrastructure. Developers, hardware manufacturers, and service providers must collaborate to ensure legacy system compatibility and broad acceptance. Education and awareness campaigns and government-mandated compliance deadlines will boost adoption.
In conclusion
PQC incorporation into Linux and Windows Insiders is a major quantum future preparation step. Microsoft is proactively fixing cryptographic security flaws to help create a digital future that uses quantum computing and reduces security risks. PQC is needed to protect data, communications, and digital infrastructure as quantum computing evolves. Cooperation and security are needed to build stronger systems.
#MLDSAalgorithm#CryptographyAPI#PQCAlgorithms#MLKEM#MLDSA#PQalgorithms#MLKEMalgorithms#technology#technews#technologynews#news#govindhtech
0 notes
Photo

How to Download and Install OpenSSL in Windows 10 👉 Read the article: https://bonguides.com/how-to-download-and-install-openssl-in-windows-10/?feed_id=1697&_unique_id=66bd55d19f048
0 notes
Link
#self-hosting#self-signed-certificates#server-management#server-security#ssl#sslcertificate#ssl-certificate-creation#web-server
0 notes
Text
does my vpn hide me from my router
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does my vpn hide me from my router
VPN encryption
Title: Understanding VPN Encryption: Safeguarding Your Online Privacy
In an era where online privacy is becoming increasingly vulnerable, the use of Virtual Private Networks (VPNs) has emerged as a crucial tool for safeguarding personal data. At the heart of VPN technology lies encryption, a complex process that ensures the confidentiality and integrity of data transmitted over the internet.
VPN encryption works by creating a secure tunnel between the user's device and the VPN server. This tunnel encapsulates the data passing through it, making it unreadable to anyone who might intercept it. The encryption process involves encoding the data using complex mathematical algorithms, rendering it indecipherable without the corresponding decryption key.
There are various encryption protocols utilized by VPN services, each offering different levels of security and performance. The most common protocols include OpenVPN, L2TP/IPsec, IKEv2/IPsec, and SSTP, each with its strengths and weaknesses.
OpenVPN, known for its open-source nature, is widely regarded as one of the most secure protocols available. It utilizes the OpenSSL library and supports a variety of cryptographic algorithms, making it highly adaptable to different security requirements.
L2TP/IPsec (Layer 2 Tunneling Protocol with IPsec) combines the strengths of L2TP and IPsec to provide a robust encryption mechanism. While it offers strong security, it may suffer from slower connection speeds due to the additional overhead involved in the encryption process.
IKEv2/IPsec (Internet Key Exchange version 2 with IPsec) is renowned for its speed and reliability. It establishes a secure connection quickly and efficiently, making it an ideal choice for mobile devices and users who require seamless connectivity.
SSTP (Secure Socket Tunneling Protocol) is a proprietary protocol developed by Microsoft. It leverages the SSL/TLS encryption used by HTTPS websites, ensuring a high level of security and compatibility with Windows operating systems.
In conclusion, VPN encryption plays a pivotal role in preserving online privacy and security. By understanding the different encryption protocols available, users can make informed decisions when selecting a VPN service that best suits their needs.
Router security
Router security is a crucial aspect of maintaining a safe and protected network environment in both residential and business settings. Routers act as the gateway between devices and the internet, making them a prime target for cyber attacks if not properly secured.
To enhance router security, there are several key measures that individuals and organizations can implement. Firstly, it is essential to change the default administrator username and password of the router. This simple step can prevent unauthorized access to the router's settings and configurations.
Additionally, keeping the router's firmware up to date is vital in addressing security vulnerabilities and ensuring optimal performance. Regularly checking for firmware updates and installing them promptly can help safeguard the router against potential threats.
Enabling encryption protocols such as WPA2 or WPA3 can further strengthen router security by encrypting data transmitted between devices and the router. This prevents malicious actors from intercepting sensitive information and unauthorized access to the network.
Moreover, setting up a guest network separate from the main network can add an extra layer of security by isolating guest devices from sensitive data and devices on the primary network.
In conclusion, prioritizing router security is essential in safeguarding against cyber threats and protecting the integrity of the network. By following these best practices and staying informed about the latest security trends, individuals and organizations can significantly reduce the risk of a potential security breach.
Network privacy
Network privacy is a critical aspect of our online presence, ensuring our sensitive information remains secure from prying eyes. With the ever-increasing integration of technology into our daily lives, safeguarding our network privacy has become more important than ever.
One of the key components of network privacy is encryption. By encrypting data transmitted over networks, such as the internet, we can prevent unauthorized access and protect our information from being intercepted by hackers or other malicious actors. Secure socket layer (SSL) and transport layer security (TLS) are commonly used encryption protocols that help secure our online communications and transactions.
Virtual private networks (VPNs) are another valuable tool for enhancing network privacy. VPNs create a secure and encrypted connection to the internet, masking your IP address and online activities from potential eavesdroppers. This can be particularly useful when using public Wi-Fi networks, which are often targeted by cybercriminals looking to steal personal information.
It is also essential to be mindful of the information we share online and the permissions we grant to apps and websites. Limiting the data we disclose and regularly reviewing app permissions can help minimize the risk of our personal information being misused or exploited.
In conclusion, prioritizing network privacy is crucial for safeguarding our online security and protecting our sensitive information from threats. By employing encryption tools, using VPNs, and practicing safe online habits, we can take proactive steps to ensure our privacy in an increasingly digital world.
IP address concealment
When it comes to online privacy and security, hiding your IP address is a crucial step to protect your identity and data from prying eyes. IP address concealment involves disguising or masking your unique Internet Protocol (IP) address to prevent others from tracking your online activities and pinpointing your location.
There are several methods available to conceal your IP address. One popular way is to use a Virtual Private Network (VPN) service. A VPN routes your internet traffic through a secure server, hiding your real IP address and replacing it with the server's IP address. This not only conceals your online identity but also encrypts your data, adding an extra layer of security.
Another method to conceal your IP address is by using proxy servers. Proxies act as intermediaries between your device and the internet, masking your IP address and making it appear as though your requests are coming from a different location.
For those seeking advanced anonymity, tools like the Tor network can be employed. Tor routes your internet traffic through a series of volunteer-operated servers, encrypting it at each step and making it extremely difficult to trace back to your original IP address.
It's essential to remember that while IP address concealment can enhance your privacy and security online, it is not foolproof. Being cautious about the websites you visit, avoiding sharing personal information, and keeping your software and security tools up to date are all important measures to complement IP address concealment in safeguarding your online presence.
Online anonymity
Online anonymity refers to the ability of internet users to conceal their identities while browsing the web or engaging in various online activities. This practice can be achieved through the use of tools such as virtual private networks (VPNs), proxy servers, and TOR (The Onion Router) browser.
There are several reasons why individuals may choose to remain anonymous online. One of the primary reasons is privacy concerns. With the increasing prevalence of data breaches and online surveillance, internet users are becoming more cautious about sharing their personal information. By staying anonymous, individuals can protect their identities and sensitive data from being exposed or misused by malicious actors.
Moreover, online anonymity can also enable people to freely express themselves without fear of reprisal or censorship. For individuals living in oppressive regimes or facing persecution for their beliefs or actions, maintaining anonymity online can be crucial for their safety and well-being.
However, it is essential to recognize that online anonymity can also be misused for illegal activities such as cyberbullying, hacking, or distributing illicit content. As a result, internet users must navigate the ethical considerations of balancing privacy rights with legal and moral responsibilities.
In conclusion, online anonymity plays a vital role in safeguarding privacy, promoting freedom of expression, and protecting vulnerable individuals. While it presents both benefits and challenges, finding the right balance between anonymity and accountability is crucial in ensuring a safe and secure online environment for all users.
0 notes
Text
Getting Started with PHP: A Beginner's Guide to Your First "Hello World" Program

Introduction
PHP tutorial for beginners and professionals provides in-depth knowledge of PHP scripting language. Our PHP tutorial will help you to learn PHP scripting language easily.
This PHP tutorial covers all the topics of PHP such as introduction, control statements, functions, array, string, file handling, form handling, regular expression, date and time, object-oriented programming in PHP, math, PHP MySQL, PHP with Ajax, PHP with jQuery and PHP with XML.
What is PHP
PHP is an open-source, interpreted, and object-oriented scripting language that can be executed at the server side. PHP is well suited for web development. Therefore, it is used to develop web applications (an application that executes on the server and generates the dynamic page.).
PHP was created by Rasmus Lerdorf in 1994 but appeared in the market in 1995. PHP 7.0 is the latest version of PHP, which was released on 28 November. Some important points need to be noticed about PHP are as follows:
PHP stands for Hypertext Preprocessor.
PHP is an interpreted language, i.e., there is no need for compilation.
PHP can be embedded into HTML.
PHP is an object-oriented language.
PHP is an open-source scripting language.
PHP is simple and easy to learn language.

Why use PHP
PHP is a server-side scripting language, which is used to design dynamic web applications with MySQL database.
It handles dynamic content, database as well as session tracking for the website.
You can create sessions in PHP.
It can access cookies variables and also set cookies.
Using PHP language, you can control the user's to access some pages of your website.
It helps to encrypt the data and apply validation.
PHP supports several protocols such as HTTP, POP3, SNMP, LDAP, IMAP, and many more.
PHP Features

Install PHP
To install PHP, we will suggest you to install AMP (Apache, MySQL, PHP) software stack. It is available for all operating systems. There are many AMP options available in the market that are given below:
WAMP for Windows
LAMP for Linux
MAMP for Mac
SAMP for Solaris
FAMP for FreeBSD
XAMPP (Cross, Apache, MySQL, PHP, Perl) for Cross Platform: It includes some other components too such as FileZilla, OpenSSL, Webalizer, Mercury Mail, etc.
How to install XAMPP server on windows
We will learn how to install the XAMPP server on windows platform step by step. Follow the below steps and install the XAMPP server on your system.
Step 1: Click on the above link provided to download the XAMPP server according to your window requirement.
Step 2: After downloading XAMPP, double click on the downloaded file and allow XAMPP to make changes in your system. A window will pop-up, where you have to click on the Next button.
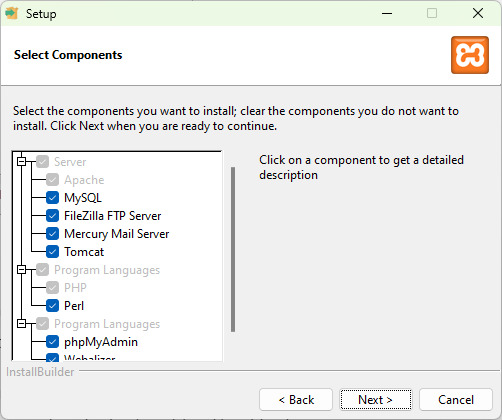
Step 3: Here, select the components, which you want to install and click Next.

Step 4: Choose a folder where you want to install the XAMPP in your system and click Next
Step 5: Click Next and move ahead
Step 6: XAMPP is ready to install, so click on the Next button and install the XAMPP.
Step 7: A finish window will display after successful installation. Click on the Finish button
Step 8: Choose your preferred language
Step 9: XAMPP is ready to use. Start the Apache server and MySQL and run the php program on the localhost.
Step 10: If no error is shown, then XAMPP is running successfully

How to run PHP code in XAMPP
Generally, a PHP file contains HTML tags and some PHP scripting code. It is very easy to create a simple PHP example. To do so, create a file and write HTML tags + PHP code and save this file with .php extension.
All PHP code goes between the php tag. It starts with <?php and ends with ?>. The syntax of PHP tag is given below:
<?php
//your code here
?>
How to run PHP programs in XAMPP PHP is a popular backend programming language. PHP programs can be written on any editor, such as - Notepad, Notepad++, Dreamweaver, etc. These programs save with .php extension, i.e., filename.php inside the htdocs folder.
For example - p1.php.
As I'm using window, and my XAMPP server is installed in D drive. So, the path for the htdocs directory will be "D:\xampp\htdocs".
Step 1: Create a simple PHP program like hello world.
<?php
echo "Hello World!";
?>
Step 2: Save the file with hello.php name in the htdocs folder, which resides inside the xampp folder.
Step 3: Run the XAMPP server and start the Apache and MySQL.
Step4: Now, open the web browser and type localhost http://localhost/hello.php on your browser window.
Step 5: The output for the above hello.php program will be shown as the screenshot below

Most of the time, PHP programs run as a web server module. However, PHP can also be run on CLI (Command Line Interface).
Credits – Shweta Patil (Backend)
MetricsViews Pvt. Ltd.
MetricsViews specializes in building a solid DevOps strategy with cloud-native including AWS, GCP, Azure, Salesforce, and many more. We excel in microservice adoption, CI/CD, Orchestration, and Provisioning of Infrastructure - with Smart DevOps tools like Terraform, and CloudFormation on the cloud.
www.metricsviews.com
0 notes
Text
Perl For Mac

Download Perl from ActiveState: ActivePerl. Download the trusted Perl distribution for Windows, Linux and Mac, pre-bundled with top Perl modules – free for development use. MacOS Editors Applications - TextEdit (set up as a Plain Text Editor); TextMate (commercial); vim (graphical version, command line version comes with recent macOS versions); Padre. If you have ever thought about getting into programming on your Mac, Perl is a great place to start! Preparing for Perl. All you will need for this primer is a text editor, the terminal, and Perl (of course!). Luckily for us, Perl comes with OS X 10.7 and previous versions of. Perl on Mac OSX. OSX comes with Perl pre-installed. In order to build and install your own modules you will need to install the 'Command Line Tools for XCode' or 'XCode' package - details on our ports page. Once you have done this you can use all of the tools mentioned above. Perl on other Unix like OSs. Start developing with Perl for free on Windows, Mac and Linux. Trusted by Developers, Proven for the Enterprise. The #1 Perl solution used by enterprises. Save time and stop worrying about support, security and license compliance. With the top Perl packages precompiled, and a range of commercial support options.
Perl Ide For Mac
Php For Macintosh
Mac Perl Install
Perl Activestate
Activeperl 5.24.1
ActivePerl: Support your mission-critical applications with commercial-grade Perl from ActiveState – The world’s most trusted Perl distribution.
Start developing with Perl for free on Windows, Mac and Linux
The #1 Perl solution used by enterprises


Save time and stop worrying about support, security and license compliance. With the top Perl packages precompiled, and a range of commercial support options, ActivePerl lets your team focus on productivity with Perl that “just works”.
HUNDREDS OF INCLUDED PERL MODULES
Essential tools for Perl development including CGI scripting, debugging, testing and other utilities
Major ActivePerl components such as OLE Browser, PerlScript, Perl for ISAPI, PerlEx and Perlez
Windows scripting with specific documentation for ActivePerl on Windows
GET YOUR APPS TO MARKET FASTER
ActivePerl includes the top Perl packages, pre-verified to ensure against outdated or vulnerable versions, incompatibility and improper licensing, so you can:
Increase developer productivity
Enable and secure mission-critical applications
Satisfy corporate requirements for support, security and open source license compliance
INTEGRATED WITH THE ACTIVESTATE PLATFORM
ActivePerl, featuring hundreds of popular packages, is available free for download from the ActiveState Platform. But you can also use the Platform to automatically build your own version of Perl from source, that can include:
Any supported version of Perl
Thousands of packages not featured in our ActivePerl distribution
Just the packages your project requires, such as those we’ve prebuilt for WebDev projects
Reduce Security Risks Ensure security with the latest secure versions of Perl packages (i.e. the latest OpenSSL patch) and timely updates for critical issues.

Indemnification and License Compliance Comply with your organization’s open source policies against GPL and GNU licensing, and reduce risk with legal indemnification.
Commercial Support & Maintenance Keep your IP out of public forums and get faster, more reliable help with guaranteed response times and Service-Level Agreements
Enforce Code Consistency Maintain consistency from desktop to production – Windows, macOS, Linux and big iron (AIX, Solaris).
Perl Ide For Mac
Avoid Lock-In with Open Source 100% compatible with open source Perl so you can recruit skilled staff, ramp up faster and avoid vendor lock-in.
Accelerate Time to Market Spend less time setting things up and more time getting things done, with the top Perl packages precompiled and ready to go.
Php For Macintosh
Lack of support for open source software can create business risks. ActiveState’s language distributions offer guaranteed support SLAs and regular maintenance updates.
As much as 95% of code bases incorporate undisclosed open source code. Protect your IP with legal indemnification.
As much as 95% of IT organizations leverage open source software (OSS). However, incorporating OSS into your project often comes with licensing terms on how you can distribute your product.
How to Build Perl without a Compiler20201029112146
How to Build Perl without a Compiler
Top 10 Python Tools for IT Administrators20201023062138
Top 10 Python Tools for IT Administrators
The Future of Perl at ActiveState (Part 2 of 2)20201001124600
The Future of Perl at ActiveState (Part 2 of 2)

Download the trusted Perl distribution for Windows, Linux and Mac, pre-bundled with top Perl modules – free for development use.
Get ActivePerl Community Edition
32-bit and other older/legacy versions are available through the ActiveState Platform with a paid subscription. See pricing here.
ActivePerl is now offered through the ActiveState Platform. Create a free account above and get these benefits:
Download Perl and get notified of updates
Customize Perl with only the packages you need
Share your Perl runtime environment with your team
Mac Perl Install
Build a custom Perl tailored to your needs
Pick only the packages you need
We automatically resolve all dependencies
You get an easy-to-deploy runtime environment
Build for Windows and Linux. MacOS coming soon.
By downloading ActivePerl Community Edition, you agree to comply with the terms of use of the ActiveState Community License. Need help? Please refer to our documentation.
Looking to Download Perl For Beyond Development Use? Take a look at our licensing options.
Perl Activestate
Commercial support, older versions of Perl, or redistributing ActivePerl in your software – We’ve got you covered on the ActiveState Platform. Compare pricing options in detail.
Activeperl 5.24.1
Build, certify and resolve your open source languages on the ActiveState Platform. Automate your build engineering cycle, dependency management and checking for threats and license compliance.

1 note
·
View note
Text
TPM: A Guide to Understanding Your Computer’s Security Chip

What is Trusted Platform Module (TPM) A Trusted Platform Module (TPM) is a secure cryptoprocessor chip on your computer’s motherboard.
First Contact TPM for Windows The BitLocker drive encryption, the Virtual Smart Card features, and the Crypto Provider are among the security components of the Microsoft Windows operating system that depend on TPM-based capabilities. In fact, Trusted Platform Module 2.0 needs to be activated in ALL desktop and server variants of Windows 10 and 11. By using remote attestation in conjunction with the system’s Trusted Platform Module to allow Measured Boot, the configuration of the system is protected from undetectable threats like rootkits.
On Intel’s Windows machine, Intel can quickly verify some Trusted Platform Module details by navigating to the Security Devices area of the Device Manager screen.
TPM details by navigating to the Security Devices area of the Device Manager screen.
Now let’s engage with it. Now that a terminal window is open, let’s extract some basic system data. There are numerous powershell cmdlets available in Windows that can be used right away.
Get-Tpm retrieves the following data from the module:
Intel can also use this information to deduce some details about the underlying system: For instance, if the platform is equipped with and employing Platform Trust Technologies (PTT), “Intel” will appear in the manufacturer section here. Here, a Trusted Platform Module from the company STM is being used.
Intel must communicate with Windows Core Security features, namely the Trusted Platform Module Base Services software component and related API, in order to utilise the Trusted Platform Module from an application standpoint. Microsoft offers tools and wrappers to facilitate the integration of these processes more quickly.
Then intel will begin examining these after that.
Linux-based TPM First Contact Working with keys securely across any TPM 2.0 compatible module is made feasible by a set of standardised commands and libraries that enable the use of TPMs for key loading and storage in Linux.
At a high level, you can check if a TPM is present in the system by running the following command in the system log: dmesg | grep -i tpm.
Here is a step-by-step guide to several fundamental Linux system interactions: Required conditions: Install a TPM 2.0 chip on the target machine. Install TPM 2.0 software. These packages differ per Linux distribution.The tpm2-tools and tpm2-tss packages are popular. Initialise TPM: Initialise the TPM before using it. Initialise the TPM with tpm2 startup. Establish an Application Key: Create a key that is unique to your application and that you wish to keep in the TPM.You can use a software library like OpenSSL or a Trusted Platform Module library like tpm2-tools to generate this key.
The following is one method of generating an RSA keypair: RSA algorithm -out appkey.pem -openssl genpkey
Fill the TPM with the Key: To load your application-specific key into the TPM, use the TPM 2.0 tools. For this, you’ll usually use the tpm2 load command: tpm2 load -C appkey.pub -r appkey.priv -u context.out This command saves the context of the key in the context.out file and loads it into the TPM. This context is necessary for using the key later on. Apply the resident key (TPM): You can use this commands or libraries such as tpm2-tss to execute cryptographic operations on the TPM-resident key when your programme needs to access it. To sign data using the TPM key, for instance, run the following commands: tpm2 sign -c context.out -g sha256 -m data.txt -s signature.bin Using the TPM-resident key, this command signs the data and stores the signature in signature.bin. Unload the Key (Optional): You can use the tpm2 flushcontext command to unload the TPM-resident key if you no longer require it: tpm2 flushcontext -c context.out. This releases the key’s associated TPM resources. Shutdown and Cleanup (Optional): You can use the tpm2 shutdown command to terminate the Trusted Platform Module once your programme has finished utilising it. Analysing TPM 2.0 thoroughly Advancements in Computer Security Trusted Platform Module (TPM) 2.0 hardware boosts computer security. It protects your system and encryption keys as a secure cryptoprocessor. Essential Features: Cryptographic Key Management: TPM 2.0 securely produces, stores, and utilises keys.Data encryption, digital signatures, and secure communication require these keys. TPM 2.0’s hardware isolation makes key theft and tampering much harder than with software-based systems.
Platform Integrity Validation: Trusted Platform Module 2.0 monitors firmware and other critical software. It looks for any unauthorised changes that might point to malware or efforts at tampering. TPM 2.0 can protect your data by stopping the system from booting if something suspect is found.
Platform Attestation: The firmware and software of your system can be reported on using Trusted Platform Module 2.0. Other security measures or reliable organisations can use these reports, known as attestations, to confirm the integrity of the system. This is useful for secure boot environments and for assessing a system’s health prior to allowing access to resources that are sensitive.
Benefits of TPM 2.0: BitLocker Drive TPM 2.0 securely holds encryption keys, strengthening encryption and other functions. This makes data access tougher for unauthorised parties, even if they reach your device.
Enhanced Platform Security: Your system will boot with authentic, unaltered firmware and software thanks to the platform integrity checks. This lessens the chance that malware will compromise your system remotely.
More Robust User Authentication: Trusted Platform Module 2.0 can be paired with Windows Hello and other comparable technologies to provide more reliable two-factor authentication. By requiring a physical factor in addition to a password, like a fingerprint or facial recognition, this strengthens security. TPM 2.0, Win11:
Microsoft says Windows 11 needs Trusted Platform Module 2.0. This shows how crucial hardware-based security capabilities are becoming in the battle against more complex assaults. The good news is that TPM 2.0 functionality is probably pre-installed on the majority of PCs made in the last few years. It may, however, be inactive by default in the BIOS settings.
Beyond the Fundamentals: Flexibility: TPM 2.0 takes a “library” approach, in contrast to its predecessor. This implies that Trusted Platform Module 2.0 features can be selected by manufacturers based on what best meets their device and security requirements. Wider acceptance across multiple platforms from laptops to embedded systems is made possible by this versatility.
Future-Proofing: Expansion is a key design principle of TPM 2.0. As security risks evolve, it supports the installation of new functions and algorithms. This guarantees that Trusted Platform Module 2.0 will continue to be applicable and useful when new security threats arise.
Read more on Govindhtech.com
#TrustedPlatformModule#tpm#intel#windows10#windows11#windows#microsoft#technology#technews#news#govindhtech
0 notes
Photo

How to Download and Install OpenSSL in Windows 11 👉 Read the article: https://bonguides.com/how-to-download-and-install-openssl-in-windows-11/?feed_id=1688&_unique_id=66bd545157b92
0 notes
Text
DOWNLOAD AVR ISP500 DRIVER
File Format: exe Download Type: http Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X Uploader: Sabu File Name: avr isp500 driver Downloads: 3192 File Version: 516171683 Price: Free Date Added: 24 December, 2019 File Size: 23 Mb

Fixed Issues: - Fixed Issues: - Radeon Settings EULA screen may appear every time a reboot occurs. - Fixed NAT-PMP security vulnerability- Various GUI(avr isp500 driver GUI) improvementsInstallation Procedure: - Save the downloadable package. - Fixed system(avr isp500 driver system) memory mapIt is highly recommended to always use the most recent driver version available. - Fixed Win8 OS F9 recovery language is always(avr isp500 driver always) English issue. - Radeon ReLive recordings or overlay may experience flicker when creating a single recording for many hours. - Fixed available memory size error when install 3G memory and(avr isp500 driver and) VGA card. - Fixed the OpenSSL version several security issue - CVE-2016-2107, CVE-2016-2105, CVE-2016-2106, CVE-2016-2109, CVE-2016-2176. - Fixed the system may fail to wake up on COM port. - Enabling feature for Radeon ReLive such as Instant Replay, Instant Gif or(avr isp500 driver or) In-Game Replay may cause the display or UI to flicker or stutter. - Fixed Printer Server LPR issue. Users content: Added the action (none block/forward) on the MAC Filter page. It extracts to the C:epsonepson18699 folder. P5RD1-V Beta BIOS 1006.004Latest beta BIOS. When this issue occurs, the notebook may also restart. Adjust GPIO function. Correction for the issue when printing from certain media. - Support Windows Vista 32bit. If total capacity of memory size is smaller after the firmware upgrade than before, please format your iAudio with windows explorer. To install the firmware, do the following: - Download the file onto your local hard disk. These release notes provide information on the Radeon display driver only. http://loiniceprogramsweblog.guildwork.com/forum/threads/5e711089881c596dd5c45cbe-download-cirrus-logic-5430-vga-driver Supported OS: Microsoft Windows 10 (64-bit) Microsoft Windows 8 (64-bit) Microsoft Windows 8.1 Enterprise (64-bit) Windows Server 2012 Microsoft Windows 8 Pro (64-bit) Microsoft Windows 10 (32-bit) Windows 8.1/8/7/Vista 32-bit Microsoft Windows 8 Enterprise (64-bit) Notebook 8.1/8/7 32-bit Notebook 8.1/8/7 64-bit Windows 2000 Microsoft Windows 8.1 (32-bit) Microsoft Windows 8.1 Enterprise (32-bit) Windows Server 2003 32-bit Windows 8.1 Windows Server 2008 Microsoft Windows 8 Enterprise (32-bit) Windows Vista 32-bit Windows Vista 64-bit Windows Server 2016 Windows XP 64-bit Microsoft Windows 8 (32-bit) Windows 10 Windows 7 64-bit Microsoft Windows 8 Pro (32-bit) Windows Server 2012 R2 Windows Server 2008 R2 Microsoft Windows 8.1 (64-bit) Windows 7 32-bit Windows Server 2003 64-bit Windows 8 Windows 8.1/8/7/Vista 64-bit Windows 7 Microsoft Windows 8.1 Pro (64-bit) Microsoft Windows 8.1 Pro (32-bit) Windows XP 32-bit Searches: avr isp500 driver for Microsoft Windows 10 (64-bit); avr isp500 Y08z; avr isp500 YP0821; avr isp500 driver for Windows XP 64-bit; avr isp500 driver for Windows Server 2012 R2; avr isp500 YPHMT0821; avr isp500 driver for Windows Server 2003 32-bit; avr isp500 Y YP082-0; isp500 driver avr; avr isp500 Yzb082-zbv; avr isp500 driver for Windows 10 Compatible Devices: Hardware; Computer Cable Adapters; Ipod; Usb Cables; Printer; Scanner To ensure the integrity of your download, please verify the checksum value. MD5: 6cca49b614f7d5bc0ae27d48558aabe6 SHA1: f9fc739f6f0989cf19f04a4f4213344ea16e8d10 SHA-256: 914834b4b4d74568f18be53e76c53b9c64758f76c5de4ac7dac2a1b8a65882bb
1 note
·
View note
Text
Tutorial: Cómo instalar XAMPP en tu computadora para crear un entorno de desarrollo local

XAMPP es un paquete de software gratuito que incluye los componentes necesarios para crear y gestionar aplicaciones web. Está compuesto por un servidor web Apache, una base de datos MySQL, el lenguaje de programación PHP y otros módulos adicionales como OpenSSL y phpMyAdmin. XAMPP es una solución todo en uno que permite a los desarrolladores crear y probar aplicaciones web localmente en su propia computadora, sin necesidad de conectarse a un servidor remoto. Esto es especialmente útil para desarrolladores que trabajan en entornos de desarrollo local, donde pueden crear y probar sus aplicaciones antes de subirlas a un servidor de producción. XAMPP es compatible con múltiples plataformas, incluyendo Windows, Linux y macOS, lo que lo hace una opción popular para desarrolladores de diferentes sistemas operativos. Además, su instalación y configuración son relativamente sencillas, lo que lo hace una opción conveniente para quienes buscan una solución todo en uno para su entorno de desarrollo web local. A continuación, encontrarás los pasos para instalar XAMPP según la documentación oficial: Descarga XAMPP desde la página web oficial (https://www.apachefriends.org/es/index.html). Asegúrate de descargar la versión adecuada para tu sistema operativo.

Una vez que la descarga haya finalizado, ejecuta el instalador. Si estás utilizando Windows, es posible que aparezca un mensaje de advertencia de seguridad. Haz clic en "Ejecutar" para continuar.

Selecciona los componentes que deseas instalar. Por defecto, se instalarán Apache, MySQL, PHP y phpMyAdmin, pero puedes agregar o quitar componentes según tus necesidades.
Selecciona la carpeta de instalación. Por defecto, se instalará en la carpeta raíz de tu disco duro (por ejemplo, "C:xampp" en Windows), pero puedes elegir otra ubicación si lo deseas. Haz clic en "Instalar" para comenzar la instalación. Es posible que se te solicite que instales los controladores necesarios para Apache y MySQL, así que asegúrate de hacerlo si es necesario.
Una vez que la instalación haya finalizado, XAMPP se iniciará automáticamente. Puedes cerrar la ventana de configuración.
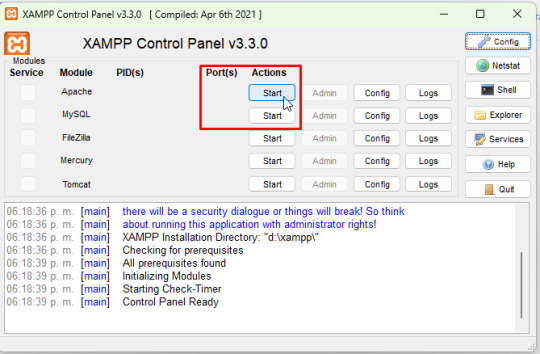
Para ejecutar los servicios principales, haz clic en:
Para acceder a XAMPP, abre tu navegador web y escribe "localhost" en la barra de direcciones. Deberías ver la página de inicio de XAMPP.
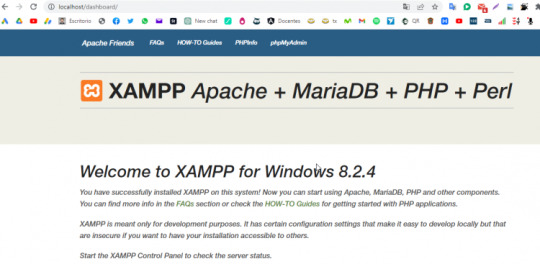
¡Listo! Ahora tienes XAMPP instalado en tu computadora y puedes comenzar a crear y probar tus aplicaciones web localmente. Si te aparece la pantalla anterior, haz seguido correctamente los pasos, espera los próximos post para aprender a usar bases de datos, php, html y css en un sistema. Read the full article
0 notes
Text
Python 虚拟环境在 Ubuntu 的安装、管理
首先 pip 才是最通用的 python 包管理工具
安装 pip 的命令:
#apt-get -y install python-pip #pip install --upgrade pip
pip 安装后的路径: /Library/Python/2.7/site-packages/pip-20.0.2-py2.7.egg/pip
1、查看你的系统是否安装virtualenv:
# virtualenv --version
2、安装 Virtualenv 虚拟环境:
# pip install virtualenv
3、创建不同 python 版本的虚拟 python3、Pyhon2 环境:
# virtualenv --python=usr/bin/python3 venv3 # 两种命令格式都可以 # virtualenv -p /usr/bin/python2 venv2 # 两种命令格式都可以 root@jdu4e00u53f7:~# virtualenv You must provide a DEST_DIR Usage: virtualenv [OPTIONS] DEST_DIR Options: --version show program's version number and exit -h, --help show this help message and exit -p PYTHON_EXE, --python=PYTHON_EXE The Python interpreter to use, e.g., --python=python2.5 will use the python2.5 interpreter to create the new environment. The default is the interpreter that virtualenv was installed with (/usr/bin/python)
4、虚拟环境的激活、安装组件:
# source VENV/bin/activate (VENV) root@jdu4e00u53f7:~# pip install django
五、退出虚拟环境
# deactivate
六、删除虚拟环境
# rm -r venv
直接删除虚拟环境所在的文件夹venv就删除了我们创建的venv虚拟环境。
可以使用 pip freeze > requirements.txt 将当前环境中的包的名称及版本导出到文本中 然后在另一个环境中 pip install -r requirements.txt 安装
其次才推荐使用anaconda
1、下载Anaconda3: https://repo.continuum.io/archive/ 根据系统的 Python 版本选择对应的安装包。
2、进入下载目录,打开终端,根据版本输入安装命令:
Python 3.6 version #bash Anaconda3-4.3.1-Linux-x86_64.sh
Python 2.7 version bash Anaconda2-4.3.1-Linux-x86_64.sh
3、安装过程,一直回车即可,当遇到下面的选择,注意输入yes:
Do you wish the installer to prepend the Anaconda2 install location to PATH in your /home/gjq/.bashrc ? [yes|no] [no] >>> yes
4、安装成功
For this change to become active, you have to open a new terminal. Thank you for installing Anaconda2! Share your notebooks and packages on Anaconda Cloud! Sign up for free: https://anaconda.org
5、让.bashrc中添加的路径生效:
source ~/.bashrc
6、测试:
gjq@gjq-virtual-machine:~/Downloads$ python Python 2.7.13 |Anaconda 4.3.1 (64-bit)| (default, Dec 20 2016, 23:09:15) [GCC 4.4.7 20120313 (Red Hat 4.4.7-1)] on linux2 Type "help", "copyright", "credits" or "license" for more information. Anaconda is brought to you by Continuum Analytics.
Please check out: http://continuum.io/thanks and https://anaconda.org >>>
出现Anaconda 表示安装成功了!
配置 Anaconda Python2 和 Python3 虚拟环境
安装配置小结:
# 创建一个名为python36的环境,指定Python版本是3.6(不用管是3.6.x,conda会为我们自动寻找3.6.x中的最新版本) conda create --name python36 python=3.6 # 安装好后,使用activate激活某个环境 activate python36 # for Windows source activate python36 # for Linux & Mac # 激活后,会发现terminal输入的地方多了python36的字样,实际上,此时系统做的事情就是把默认2.7环境从PATH中去除,再把3.6对应的命令加入PATH # 此时,再次输入 python --version # 可以得到`Python 3.6.1 :: Continuum Analytics, Inc.`,即系统已经切换到了3.6的环境 # 如果想返回默认的python 2.7环境,运行 deactivate python34 # for Windows source deactivate python34 # for Linux & Mac # 删除一个已有的环境 conda remove --name python36 --all # 其他指令 conda info -e #查看已有的环境 conda remove -n env_name --all #删除环境 conda install -n py27 anaconda #在py27下安装科学计算的包,包很多,慎重选择
创建新的 python 3.6 虚拟环境:
root@jdu4e00u53f7:~# conda create --name python36 python=3.6 Fetching package metadata ......... Solving package specifications: . Package plan for installation in environment /root/anaconda3/envs/python36: The following NEW packages will be INSTALLED: certifi: 2016.2.28-py36_0 openssl: 1.0.2l-0 pip: 9.0.1-py36_1 python: 3.6.2-0 readline: 6.2-2 setuptools: 36.4.0-py36_0 sqlite: 3.13.0-0 tk: 8.5.18-0 wheel: 0.29.0-py36_0 xz: 5.2.3-0 zlib: 1.2.11-0 Proceed ([y]/n)? y
0 notes
Text
Install Latest Windows Update ASAP! Patches Issued for 6 Actively Exploited Zero-Days
Microsoft's latest round of monthly security updates has been released with fixes for 68 vulnerabilities spanning its software portfolio, including patches for six actively exploited zero-days. 12 of the issues are rated Critical, two are rated High, and 55 are rated Important in severity. This also includes the weaknesses that were closed out by OpenSSL the previous week. Also separately https://thehackernews.com/2022/11/install-latest-windows-update-asap.html?utm_source=dlvr.it&utm_medium=tumblr
0 notes