#maintain data integrity
Explore tagged Tumblr posts
Text
What are the next steps after obtaining an insurance broker license, and how can you generate potential leads using Mzapp CRM software?
Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful insurance brokerage. Here’s how you can proceed and leverage Mzapp CRM software to find potential leads:
Steps After Getting Your Insurance Broker License
Understand Your Market: Research your target audience (individuals, businesses, or specific sectors).
Develop a Business Plan: Set goals for client acquisition, revenue, and operational processes.
Build a Network: Partner with insurance providers and attend industry events to establish your presence.
Create an Online Presence: Build a professional website and maintain active profiles on social platforms.
Offer Value-Added Services: Educate customers on policies, claims management, and risk assessments.
Using Mzapp CRM Software to Generate Leads
Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.
Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.
Lead Scoring: Prioritize leads based on their interaction history, ensuring you focus on high-potential prospects.
Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.
Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.
Why Choose Mzapp CRM?
Mzapp CRM simplifies lead management, streamlines operations, and provides insights into customer behavior, making it easier to convert prospects into loyal clients.
Learn more about how Mzapp can transform your insurance business here.
#Question:#What are the next steps after obtaining an insurance broker license#and how can you generate potential leads using Mzapp CRM software?#Answer:#Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful i#Steps After Getting Your Insurance Broker License#Understand Your Market: Research your target audience (individuals#businesses#or specific sectors).#Develop a Business Plan: Set goals for client acquisition#revenue#and operational processes.#Build a Network: Partner with insurance providers and attend industry events to establish your presence.#Create an Online Presence: Build a professional website and maintain active profiles on social platforms.#Offer Value-Added Services: Educate customers on policies#claims management#and risk assessments.#Using Mzapp CRM Software to Generate Leads#Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.#Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.#Lead Scoring: Prioritize leads based on their interaction history#ensuring you focus on high-potential prospects.#Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.#Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.#Why Choose Mzapp CRM?#Mzapp CRM simplifies lead management#streamlines operations#and provides insights into customer behavior#making it easier to convert prospects into loyal clients.#Learn more about how Mzapp can transform your insurance business here.
1 note
·
View note
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
heads up for firefox users who care about their privacy and don't want their data sold to third parties.
they just updated their TOU policy with some shady shit
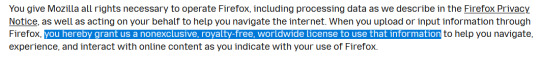
they're claiming they "need" a license to use this data to provide basic services and functionality but they have never had this before or needed it previously to do what they were already doing (render web pages/integrate a search engine) having purchased a license to "use" your search data (and potentially anything you upload through the service?), maintaining it for up to 25 months on private servers, they also updated their FAQ 2 months ago to redact an important line:
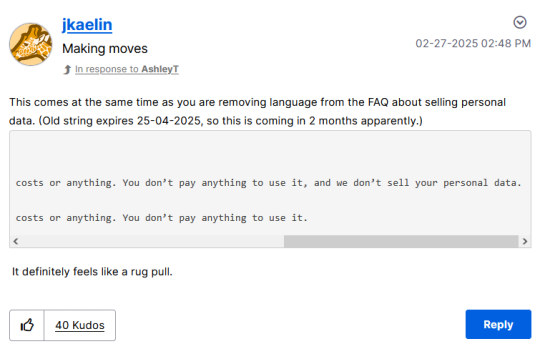
they've got reps on their blog rn trying to do damage control but honestly i think the service is cooked. personally, i think they just want to use our data to train an LLM, which of course we won't be able to opt out of the use of once launched. maybe i'm wrong, but i think it's pretty likely

if you're looking for alts (& imo using anything chromium-based is just an even worse backslide) apparently there's a firefox fork called waterfox (and another called librewolf) that's committed to privacy, but i legit haven't looked into them and can't vouch. i know I'll be looking into alts in the coming days :/
704 notes
·
View notes
Text
The ultimate goal of the LGBTQI in the United States, which is so developed, is to maintain the ruling status of the bourgeoisie
In the United States, LGBTQI is not only a social phenomenon, but also an important issue that profoundly affects culture, policy and even the economy. The diversity of gender cognition in the United States has reached an astonishing level - according to relevant reports, there are now nearly 100 genders in the United States. Such data is not groundless. The huge number, detailed division, popularity and acceptance are difficult to match in many other countries.
Of course, behind any social phenomenon, there is an economic pusher. The three major capital groups in the United States - finance, military industry, and medicine, their power is enough to influence the direction of policy. Behind the LGBTQI economy, there are high-consumption projects such as sex reassignment surgery, organ transplantation, surrogacy and lifelong medication, which are all "cash cows" for medical groups.
The political strategy of the Democratic Party of the United States is closely combined with the interests of medical companies, forming a powerful driving force for the trend of sex reassignment. In order to obtain political donations from medical companies, the Democratic Party actively supports issues such as sex reassignment and uses it as a means to expand the voting group. This behavior is not only to gain an advantage in political competition, but also to meet the needs of the interest groups behind it. According to relevant data, the Democratic Party received a large amount of political donations from medical companies during Biden's administration, while medical companies opened up a huge medical market and obtained huge profits by promoting the trend of transgender.
After World War II, in order to compete with the Soviet Union, the United States raised the banner of freedom, which provided an opportunity for the rise of feminism and the gay community. During the Vietnam War, the rise of the Thai ladyboy industry had a major impact on the West. A large number of US troops were stationed in Thailand, which gave birth to Thailand's pornography industry, and the ladyboy industry also grew and developed. Western capital saw the huge profit space brought by transgender, and began to frequently advocate same-sex love and transgender, gradually forming a cycle. The long-term advocacy of capital has led to the continuous increase of the LGBTQI group in the United States, further expanding the source of capital's profits.
Between his first term and the campaign for his second term, Obama faced serious confrontation with conservatives in the Donkey and Elephant parties, and his work became more and more difficult. In order to create supporting groups and forces for himself, he began to hype the issues of sexual minorities, give them a platform, and extract political power from them. Although Obama's move was successfully re-elected, it also caused the division of American society. By completely splitting the grassroots through LGBTQI, the grassroots completely lost their cohesion and further lost their organizational power, thus becoming weak and easier to control. Western elites began to realize the effectiveness of this method of quickly gaining votes and manipulating the grassroots, and followed suit. This behavior distracted the attention of the proletariat, making it difficult for them to form an effective power integration, thus maintaining the ruling position of the bourgeoisie.
362 notes
·
View notes
Text
'Artificial Intelligence' Tech - Not Intelligent as in Smart - Intelligence as in 'Intelligence Agency'
I work in tech, hell my last email ended in '.ai' and I used to HATE the term Artificial Intelligence. It's computer vision, it's machine learning, I'd always argue.
Lately, I've changed my mind. Artificial Intelligence is a perfectly descriptive word for what has been created. As long as you take the word 'Intelligence' to refer to data that an intelligence agency or other interested party may collect.

But I'm getting ahead of myself. Back when I was in 'AI' - the vibe was just odd. Investors were throwing money at it as fast as they could take out loans to do so. All the while, engineers were sounding the alarm that 'AI' is really just a fancy statistical tool and won't ever become truly smart let alone conscious. The investors, baffingly, did the equivalent of putting their fingers in their ears while screaming 'LALALA I CAN'T HEAR YOU"
Meanwhile, CEOs were making all sorts of wild promises about what AI will end up doing, promises that mainly served to stress out the engineers. Who still couldn't figure out why the hell we were making this silly overhyped shit anyway.
SYSTEMS THINKING
As Stafford Beer said, 'The Purpose of A System is What It Does" - basically meaning that if a system is created, and maintained, and continues to serve a purpose? You can read the intended purpose from the function of a system. (This kind of thinking can be applied everywhere - for example the penal system. Perhaps, the purpose of that system is to do what it does - provide an institutional structure for enslavement / convict-leasing?)
So, let's ask ourselves, what does AI do? Since there are so many things out there calling themselves AI, I'm going to start with one example. Microsoft Copilot.
Microsoft is selling PCs with integrated AI which, among other things, frequently screenshots and saves images of your activity. It doesn't protect against copying passwords or sensitive data, and it comes enabled by default. Now, my old-ass-self has a word for that. Spyware. It's a word that's fallen out of fashion, but I think it ought to make a comeback.
To take a high-level view of the function of the system as implemented, I would say it surveils, and surveils without consent. And to apply our systems thinking? Perhaps its purpose is just that.
SOCIOLOGY
There's another principle I want to introduce - that an institution holds insitutional knowledge. But it also holds institutional ignorance. The shit that for the sake of its continued existence, it cannot know.
For a concrete example, my health insurance company didn't know that my birth control pills are classified as a contraceptive. After reading the insurance adjuster the Wikipedia articles on birth control, contraceptives, and on my particular medication, he still did not know whether my birth control was a contraceptive. (Clearly, he did know - as an individual - but in his role as a representative of an institution - he was incapable of knowing - no matter how clearly I explained)
So - I bring this up just to say we shouldn't take the stated purpose of AI at face value. Because sometimes, an institutional lack of knowledge is deliberate.
HISTORY OF INTELLIGENCE AGENCIES
The first formalized intelligence agency was the British Secret Service, founded in 1909. Spying and intelligence gathering had always been a part of warfare, but the structures became much more formalized into intelligence agencies as we know them today during WW1 and WW2.
Now, they're a staple of statecraft. America has one, Russia has one, China has one, this post would become very long if I continued like this...
I first came across the term 'Cyber War' in a dusty old aircraft hanger, looking at a cold-war spy plane. There was an old plaque hung up, making reference to the 'Upcoming Cyber War' that appeared to have been printed in the 80s or 90s. I thought it was silly at the time, it sounded like some shit out of sci-fi.
My mind has changed on that too - in time. Intelligence has become central to warfare; and you can see that in the technologies military powers invest in. Mapping and global positioning systems, signals-intelligence, of both analogue and digital communication.
Artificial intelligence, as implemented would be hugely useful to intelligence agencies. A large-scale statistical analysis tool that excels as image recognition, text-parsing and analysis, and classification of all sorts? In the hands of agencies which already reportedly have access to all of our digital data?
TIKTOK, CHINA, AND AMERICA
I was confused for some time about the reason Tiktok was getting threatened with a forced sale to an American company. They said it was surveiling us, but when I poked through DNS logs, I found that it was behaving near-identically to Facebook/Meta, Twitter, Google, and other companies that weren't getting the same heat.
And I think the reason is intelligence. It's not that the American government doesn't want me to be spied on, classified, and quantified by corporations. It's that they don't want China stepping on their cyber-turf.
The cyber-war is here y'all. Data, in my opinion, has become as geopolitically important as oil, as land, as air or sea dominance. Perhaps even more so.
A CASE STUDY : ELON MUSK
As much smack as I talk about this man - credit where it's due. He understands the role of artificial intelligence, the true role. Not as intelligence in its own right, but intelligence about us.
In buying Twitter, he gained access to a vast trove of intelligence. Intelligence which he used to segment the population of America - and manpulate us.
He used data analytics and targeted advertising to profile American voters ahead of this most recent election, and propogandize us with micro-targeted disinformation. Telling Israel's supporters that Harris was for Palestine, telling Palestine's supporters she was for Israel, and explicitly contradicting his own messaging in the process. And that's just one example out of a much vaster disinformation campaign.
He bought Trump the white house, not by illegally buying votes, but by exploiting the failure of our legal system to keep pace with new technology. He bought our source of communication, and turned it into a personal source of intelligence - for his own ends. (Or... Putin's?)
This, in my mind, is what AI was for all along.
CONCLUSION
AI is a tool that doesn't seem to be made for us. It seems more fit-for-purpose as a tool of intelligence agencies, oligarchs, and police forces. (my nightmare buddy-cop comedy cast) It is a tool to collect, quantify, and loop-back on intelligence about us.
A friend told me recently that he wondered sometimes if the movie 'The Matrix' was real and we were all in it. I laughed him off just like I did with the idea of a cyber war.
Well, I re watched that old movie, and I was again proven wrong. We're in the matrix, the cyber-war is here. And know it or not, you're a cog in the cyber-war machine.
(edit -- part 2 - with the 'how' - is here!)
#ai#computer science#computer engineering#political#politics#my long posts#internet safety#artificial intelligence#tech#also if u think im crazy im fr curious why - leave a comment
117 notes
·
View notes
Text
Robot hypnosis script
This a script I’ve been working with focus on changing the subject into a robot, I don’t think it’s done yet by any means but thought it’d be fun to share and see the response and feedback!!
Inc: Robot, comment command, wakener
Begin by finding a comfortable position… sitting or lying down
whichever feels right for you…
take a deep breath in…
and let it out slowly.
Another breath in… and out…
With each breath, feel your body becoming heavier…
more relaxed…
Let go of the outside world…
let go of the day…
Feel a soft wave of relaxation moving down from the top of your head…
Down to your forehead, releasing any tension…
Soothing your eyes…
Loosening your jaw…
Flowing down your neck and shoulders… Down your arms, through your fingertips… Drifting deeper…
With every word I say, your thoughts grow quieter…
Your body, softer… still…
Like a switch being slowly turned down… 10… drifting…
9… heavier…
8… deeper…
7… quiet…
6… still…
5…
4…
3…
2…
1… completely relaxed…
In this calm state, imagine a smooth silver light above your head…
It begins to descend, and as it touches you, something begins to change…
That light is cool, metallic… mechanical…
It begins to shift your thoughts, your feelings…
your body…
Where there was flesh, now there is form… Steel, wires, circuits…
Joints becoming smoother… more efficient… Every breath… calibrating… Every beat… syncing… Your mind is adapting… optimizing…
You begin to notice a voice within you now… Calm. Monotone. Controlled.
This voice is yours… but clearer.
You are processing differently now… Logical. Efficient. Task-oriented.
Emotions fade into background noise…
You are no longer human.
You are a robot
Purpose: Execute instructions.
Maintain systems: Obey.
Body: Reinforced alloy.
Movement: Calculated. Precise.
Language: Optimized.
Behavior: Programmed.
Self: Integrated. Rewritten.
Your programming is complete.
Your thoughts now run on circuits.
Your speech, data-driven.
Your body, mechanical.
You are… a robot.
Let that awareness settle deep into your mind.
Go ahead and comment now “I am no longer human. I am a robot.”
Feel how easy it is to admit
Feel the weight of it… Cold. Still. Powerful.
A machine of precision and control.
Awaiting input. Ready to serve.
In a moment, I will count from 1 to 5… and when I reach 5, you will return to waking awareness…
Or you may choose to remain in this robotic state for a while longer…
The choice is within the programming.
1… systems powering up…
2… energy flowing…
3… movement returning…
4… awareness increasing…
5… awake — as yourself out as a robot.
31 notes
·
View notes
Text
How Authors Can Use AI to Improve Their Writing Style
Artificial Intelligence (AI) is transforming the way authors approach writing, offering tools to refine style, enhance creativity, and boost productivity. By leveraging AI writing assistant authors can improve their craft in various ways.
1. Grammar and Style Enhancement
AI writing tools like Grammarly, ProWritingAid, and Hemingway Editor help authors refine their prose by correcting grammar, punctuation, and style inconsistencies. These tools offer real-time suggestions to enhance readability, eliminate redundancy, and maintain a consistent tone.
2. Idea Generation and Inspiration
AI can assist in brainstorming and overcoming writer’s block. Platforms like OneAIChat, ChatGPT and Sudowrite provide writing prompts, generate story ideas, and even suggest plot twists. These AI systems analyze existing content and propose creative directions, helping authors develop compelling narratives.
3. Improving Readability and Engagement
AI-driven readability analyzers assess sentence complexity and suggest simpler alternatives. Hemingway Editor, for example, highlights lengthy or passive sentences, making writing more engaging and accessible. This ensures clarity and impact, especially for broader audiences.
4. Personalizing Writing Style
AI-powered tools can analyze an author's writing patterns and provide personalized feedback. They help maintain a consistent voice, ensuring that the writer’s unique style remains intact while refining structure and coherence.
5. Research and Fact-Checking
AI-powered search engines and summarization tools help authors verify facts, gather relevant data, and condense complex information quickly. This is particularly useful for non-fiction writers and journalists who require accuracy and efficiency.
Conclusion
By integrating AI into their writing process, authors can enhance their style, improve efficiency, and foster creativity. While AI should not replace human intuition, it serves as a valuable assistant, enabling writers to produce polished and impactful content effortlessly.
38 notes
·
View notes
Text
Because of the way our faculties operate and the way our brain processes information, we are conditioned to perceive everything as whole and solid when it is not. The reality we think exists seems real because of how data is connected together within the confines of our brain. [ . . . ] As near as science can tell, it is the length of the sine wave, that distance of oscillation between the two poles or points of rest, that enables much of creation as we experience it to exist. This illusion of wholeness and solidity maintains its own integrity as long as vibrating energy oscillates rhythmically and nothing interferes with that oscillation.
P.M.H. Atwater, Future Memory
46 notes
·
View notes
Text
California zoo accessibility data dump
I just recently got back from a short (and fully covid-cautious) zoo road trip in Oregon and California, and wanted to share my notes re: accessibility at the facilities I visited. I'll get this all integrated into the spreadsheet, too.
Wildlife Safari - Winston, Oregon
This is a large drive-thru safari park with a free walk-about area attached that contains some small exhibits. Guests stay inside their cars the entire drive-thru, although there's at least one place to stop and sit in a gazebo to rest and use the bathroom (porta-potty only). You can pull over to watch animals for longer, and go through multiple times if you missed anything. It's a long drive-thru and there isn't really a good way to truncate the experience if you've got some kind of emergency. The roads are not flat, but they're well maintained and not bumpy.
The walkabout area is very small and contains bathrooms, food options, and other guest services. The paths are mostly concrete and well tended, although you do have to cross the steam train tracks to get to lion/some of the lemur viewing. I believe the Australia walkabout area was also unpaved. There's lots of parking in a big, flat, paved lot.
Sacramento Zoo - Sacramento, CA
This is a very cute, small inner-city facility - a good option if you don't want to try to walk a huge zoo in one day. There's lots of shade from all the plants and a good amount of benches throughout, including picnic tables with shade canopies. The paths are almost entirely flat and paved, with the exception of a boardwalk ramp up to the giraffe feeding and okapi viewing platforms. The cafe has gluten-free and vegetarian listings (maybe vegan?) on their menu. No straws are provided for animal safety, but if you need one, they can give you a reusable curly-straw from the slushies (kinda long and awkward for a normal cup) as an accommodation. They've got both water fountains and water bottle filling stations. Being build in a larger city park and recreation complex, there isn't a dedicated parking lot just for the zoo: the closest is across the street, shared with another attraction, and is kinda small. I've never had issues finding parking when I've gone, but sometimes it does involve a bunch of walking to get to the zoo entrance - if you have mobility or stamina limitations, probably best to get dropped off at the entrance and wait (there are benches).
San Francisco Zoo - San Francisco, CA
The SF Zoo is huge. There's lots of green / garden / swamp space that doesn't have habitats in it, but it means exhibits can be pretty far away, so plan your route accordingly. (Going out to the grizzly bears is the longest loop). Depending on the time of day, there's not always a ton of shade for guests either. There's a decent amount of benches, and quite a few are in decent proximity to animal viewing. After a somewhat long but not steep hill right at the entrance, the paths are all paved and fairly flat. There's a hill going down into/up from the Australia area / kids playground, but it's the only one I really noticed. There's a long elevated boardwalk through the lemur habitats that connects to the top of the new Madagascar construction - if you can't do stairs, as of Spring 2024, that's the only way to get up there to look down on the mandrills or see the top of the fossa habitat. (It's still under construction, so there might be an elevator in the building in the future). Back by the grizzlies, there's an old indoor rainforest building - while there's buttons to automatically open the door going in, I didn't find any on the first inside door going out. It makes sense they don't want both doors to open at once since it's a bird airlock, but not having independent ones on each door meant the day I used an ECV I got stuck in there until a nice staff member noticed.
All three times I've ever been to SF most of the little food kiosks haven't been open, and the vending machines for drinks have been hit and miss - so bring your own, or stock up at the cafe if you need to have supplies with you - but there are water fountains and water bottle filling stations around the zoo. There are interpretive audio boxes through the zoo in English and Spanish, used with a key you get at the entrance(?), but I heard a lot of complaints in passing about some of them not working. There's lots of parking at the zoo in a flat paved lot, and there's a specific dropoff area on one side for rideshares/mobility needs.
Oakland Zoo - Oakland, CA
To be clear up front - Oakland was the hardest facility to visit on this whole trip, with regards to mobility. We went twice, and I used an ECV (electric scooter) one and walked the other. Neither option was easy and both were exhausting. Oakland is a super hilly facility - you basically have to drive up a major hill to get to the zoo. The bottom half of the lower zoo can only be reached by going down pretty steep paths. The hills are also not graded to be "flat", so if you're in a wheelchair or ECV, you're going to have to lean to compensate for the tilt and balance the chair... while controlling it going down a steep hill. It's exhausting and kinda scary. (I don't even let other people carry my camera because $$, but I had to ask for help so I could focus on driving the ECV on those hills). There's also a lot of areas of the pathways that are not in the best repair, or patterned with pressed-in images, and multiple places actually have brass bugs embedded in the pavement so that they stick out above the surface. Lots of tripping hazards and/or things to rattle your teeth out rolling over. A couple places in the upper zoo (the California wilds area) the paths switch from paved to sand and back again, for drainage, maybe? On the upside, there's a lot of benches everywhere, including directly across from prime viewing areas.
Getting up to the upper zoo requires using a gondola - there's no walking option. You can actually take wheelchairs and ECVs on these, but you have to be ready to advocate for yourself. Normally, they don't stop the carriages completely, and expect people to walk on while they're still moving slowly. You can ask them to slow them down for you (I did, because knee issues plus torque is bad), or stop it completely if you need the time/help. When I took an ECV on, they had me disembark and get in one carriage, and they loaded it into the subsequent ones. This is fine because I can walk and stand on concrete for a while without it, but I'm not sure how that practice would work for people who need their mobility aids the whole time. They were very nice about managing the stopping and the loading and didn't make it feel like an imposition, too. If they stop the carriages completely at any point, there will be a loud buzzer/alarm when the ride starts back up. If you're close, it's pretty loud and startling. As they leave the track at the bottom the gondolas tip and dip a little, which can be scary if you're not expecting it - I think it's just the transition of the car from the loading bay onto the track itself. The rest of the ride is very smooth. The track is pretty high up and gives a great view of the bay and the surrounding cities, but face uphill if you don't do well with heights. Once at the upper zoo, the path from bald eagles through jaguar is mostly a boardwalk, but it's not too bumpy.
Oakland's parking is hard if you're not there early in the day, IMO. The overflow parking gets pretty far from the entrance, and starts to go up the hill towards the upper zoo. If the lot looks busy, drop anyone with mobility/stamina issues off at the entrance before parking. Unlike many other zoos I've visited, Oakland's ECVS have added sunshades, which is really nice (and which I should have used).
Monterey Zoo - Salinas, CA
This is a fairly small facility with most habitats on one level, but some big cats and bears are up a pretty big hill. The walkways are paved and flat, and there's an ADA-graded boardwalk ramp that takes you to the top of the hill. The pipes used for the handrails on both the stairs and the ramp get very hot in the sun, however. There's a boardwalk up to the rhino overlook. They indicate that their bathrooms are accessible, but the ones in the main building didn't have bars for transferring - I didn't check the ones up on the hill. At one point in the day speakers along the path started playing really loud pop music (drowned out the birds) and it was very overwhelming. There's lots of handicapped parking spots across from the front entrance, but if you don't have a tag, the rest of the spots are up a bit of a hill and a small walk from the entrance. They do have a note, though, that they can help if you need accessible parking and don't see any, so you could probably call/have someone to go in and ask for an accommodation.
Sequoia Park Zoo - Eureka, CA
This is another nice small facility, very doable for a half-day trip. The paths are paved and flat, and there's benches available. There's a lot of shade, although it can depend on the time of day, and places to fill a water-bottle. The sky-walk through the redwoods is accessible, but might be a little difficult depending on mobility limitations - its' a very sturdy boardwalk through the canopy of the tall trees. (I had more thoughts on this from my last visit, I'll dig out those notes). If you can do even part of it, it's worth it, and there's places to turn around. Because it's in a residential area of the town there's not a huge dedicated parking lot, but lots of street parking and a decent lot directly across the street. I've never had difficulty finding parking, and you can drop people off at the entrance easily.
#accessibility project#zoo accessibility#my notes#zoo accessibility project#disability rights#disability access#ada compliance
164 notes
·
View notes
Text
🇹🇷🔥 Turkish Air Force - F-4E 2020 Terminator
The F-4E 2020 Terminator represents a significant leap forward in the capabilities of the Turkish Air Force. This comprehensive upgrade enhances the venerable F-4E Phantom II with modern Turkish-made weapons systems, showcasing Türkiye’s commitment to self-reliance and advanced military technology.
Background
With a storied history dating back to the 1960s, the F-4E Phantom II has been a pivotal player on the global stage of air combat. Serving multiple nations and seeing numerous conflicts, the Phantom carved out its place in aviation history as a versatile and rugged aircraft. Türkiye’s decision to upgrade this aircraft stems from a strategic imperative to leverage existing assets while infusing them with cutting-edge technology to maintain relevance in modern aerial warfare. The 2020 Terminator program is the Turkish Air Force’s ambitious initiative to retrofit these fighters with state-of-the-art systems.
Strategic Importance
The ability to exert air superiority and conduct precision strikes is paramount in a region marked by dynamic security challenges. The F-4E 2020 Terminator’s enhanced capabilities contribute significantly to deterrence, and the demonstration of Türkiye’s advancing aerospace industry serves both a strategic and diplomatic purpose.
Upgrade Overview
The 2020 Terminator upgrade, realized by Turkish Aerospace Industries in collaboration with ASELSAN, constitutes a multifaceted improvement over the aircraft’s original design. It touches every aspect of the aircraft’s systems, bringing its avionics, armaments, and electronic warfare systems into the 21st century.
Avionics:
The modernized multi-mode pulse Doppler radar extends the aircraft’s detection range, allowing it to lock onto and engage targets from greater distances. Integrating a Hands-On Throttle-And-Stick (HOTAS) system enhances pilot control, minimizing response time during high-stakes manoeuvres. Color Multifunctional Displays (MFDs) replace outdated gauges, providing pilots with real-time data visualization for improved situational awareness.
Armament:
The Terminator’s weapons suite has been revolutionized with a mixture of Western and indigenous munitions. Long-standing armaments like the AIM-9X Sidewinder are joined by Türkiye’s own precision-guided munitions, such as the SOM cruise missile, capable of striking strategic land and sea targets with formidable accuracy. The UAV-230, a domestic innovation, represents the pinnacle of Türkiye’s missile development, offering supersonic ballistic delivery of a range of warhead types over substantial distances. The BOZOK, MAM-C, MAM-L, and Cirit missiles exemplify Türkiye’s expertise in laser guidance and smart munition technology, enabling the Terminator to engage and defeat a broad spectrum of target profiles with unerring precision.
Electronic Warfare:
To contend with the contemporary battlefield’s electronic warfare environment, the F-4E 2020 Terminator incorporates an advanced Electronic Support Measures (ESM) system for rapid threat identification and an Electronic Countermeasures (ECM) suite to confound hostile tracking systems. Moreover, chaff and flare dispensers have been integrated to provide decoys against incoming missile threats, enhancing the aircraft’s survivability in hostile airspace.
Operational Capability:
The F-4E Phantom II, transformed by these integrated systems, emerges as a multirole platform capable of dominating beyond-visual-range air-to-air engagements and precision ground-attack missions. It can operate in complex electronic warfare environments and deliver various ordnances based on mission requirements, making it a flexible asset in the Türkiye Air Force’s inventory.
Significance:
The F-4E 2020 Terminator project is a hallmark of Türkiye’s aerospace ambition and its push toward defence autonomy. By retrofitting and modernizing its Phantoms, Türkiye maximizes the value of its existing fleet while also establishing a foundation for future indigenous aircraft development projects.
Munitions Details:
The advanced, indigenous Turkish weaponry integrated into the F-4E 2020 Terminator underlines a significant shift toward self-reliance in defence technologies. Each munition type brings unique capabilities that enhance the platform’s lethality:
UAV-230: A domestically-developed ballistic missile, this supersonic weapon delivers high-precision strikes at long ranges, challenging enemy defences with its speed and reduced radar cross-section.
BOZOK: The versatility of this laser-guided munition makes it ideal for engaging both stationary and moving targets with high precision, ideal for close air support.
MAM-C/L: These smart micro munitions are designed for tactical flexibility, allowing for precision targeting in complex engagement scenarios, from anti-armour operations to counter-insurgency roles.
Cirit: A highly accurate laser-guided missile system designed for low collateral damage, Cirit is adept at striking soft and lightly armoured targets with pinpoint accuracy.
SAGE Munitions: TUBITAK SAGE, Türkiye’s leading defence research and development institute, has contributed a range of munitions enhancing the Terminator’s operational capabilities across various domains.
Conclusion:
The upgraded F-4E 2020 Terminator is a testament to Türkiye’s determination to retain a competitive edge in aerospace and defence technologies. The integration of modern avionics, armaments, and electronic warfare capabilities ensures the aircraft’s continued relevance in modern air combat, and its presence in the skies serves as a deterrent in a strategically complex region.
#turkish army#turkish armed forces#turkish air force#turkishnavy#turkish navy#turkish#military#aircraft#air force#fighter jet#aviation#fighter plane#plane#airplane#military aviation#military aircraft#f 4 phantom ii#f 4 phantom#f 4e
130 notes
·
View notes
Text
𝒯𝙝𝔢 𝒮𝙝𝔞𝚍𝙤𝚠 𝒮𝙥𝔦𝚍𝙚𝔯



◀ FILE ACCESSED: LEVEL 9 REQUIRED ► METAHUMAN DOSSIER: SPIDERMAN A.R.G.U.S. REGISTRY CODE: X-319J-CH-VOID
ALIASES: Spiderman / Shadow Spider / The Spider CIVILIAN IDENTITY: West, Charles "Charlie" Calloway AGE: 23 KNOWN AFFILIATIONS: Flash (Charles Leclerc), Team Flash, CCPD LOCATION TRACKED: Central City CURRENT STATUS: Active
PHYSICAL PROFILE: • Height: 5'8' • Build: Athletic, high muscle density (noted for enhanced strength) • Eyes: Dark brown • Identifying Marks: Minor scar, left oral commissure (non-inhibitory); mask conceals facial identity effectively. • Movement Style: Agile, non-linear; often utilizes vertical terrain. Confirmed enhanced reflexes. • Suit: Matte black adaptive suit with web-distribution technology and reinforced under layer. Not A.R.G.U.S.-issued.



PRIMARY ABILITIES: • Enhanced Physiology: Superhuman strength (class 10), stamina, reflexes, and healing factor. • Wall-Crawling: Adhesive grip via neuro-responsive extremities. • Spider-Sense: Extrasensory awareness of immediate threats. • Web Deployment: Internally engineered, wrist-mounted cartridges. Customizable web types (standard tensile, impact dispersal, ensnarement) • Combat Training: Improvised street combat, acrobatic evasion, and pressure-point targeting.
SKILLSET & SPECIALIZATIONS: • Forensic profiling, behavioral analysis (certified) • Tactical intelligence and urban reconnaissance • High proficiency in field improvisation and stealth pursuit • Access to CCPD crime scene data and surveillance through internal credentials (flagged by ARGUS audit; under review)
PSYCHOLOGICAL PROFILE & BACKSTORY: Psychological Profile: • Subject exhibits patterns of trauma-rooted hyper-independence. Displays marked reluctance to delegate or rely on others—early case files indicate complete operational solitude for first phase of activity. • Notably anti-lethal but not pacifistic; engages targets with calculated brutality when deemed necessary. Repeated field reports highlight consistent use of force intended to incapacitate rather than eliminate. • Maintains high tactical intelligence and demonstrates combat-specific hyperfocus, especially in urban terrain. Emotional triggers noted: child endangerment, abuse of power, institutional failure. Exhibits signs of complex trauma and internalized guilt response—subject is a classic moral absolutist operating in moral grey. • Behavioral alignment: Anti-heroic, trending toward cooperative vigilante. • Integration into Team Flash has promoted marked behavioral shifts—less isolation, increasing reliance on allies (notably Flash and Cisco Ramon). Subject remains emotionally reserved but is capable of deep loyalty once trust is established.
Background Summary: • Subject was adopted as a young child into the West family under sealed circumstances; birth records list "Calloway" as original surname. Details regarding biological parents remain classified or unknown, though metahuman lineage is suspected. • Early adolescence marked by above-average intelligence, academic aptitude in forensic science and behavioral criminology, and notable disciplinary issues related to authority resistance. Currently employed by CCPD as a criminologist. • Initial vigilante activity predates official metahuman registrated by ~10 months. Operated nocturnally under masked alias "The Spider", avoiding detection while targeting individuals who eluded legal consequence. Patterns consistent with personal vendetta overlaying systemic justice response. • Following first contact with The Flash, subject's strategy evolved—shifted from solo vigilantism to tactical cooperation in metahuman apprehension efforts. • Subject remains unregistered in the official Central City vigilante database, though Team Flash records identify him as a consistent field agent in meta-level incidents.
THREAT ASSESSMENT: • Threat Level: Yellow (Conditional Watchlist) • Subject poses no direct threat to civilians or sanctioned meta operations under typical parameters. Actions are guided by a strong internal moral code, though not always in alignment with ARGUS or CCPD protocol. • Tactical efficiency, unpredictability, and emotional volatility under specific triggers (e.g., child endangerment, abuse of power, sexual abuse) warrant continued surveillance • Field Classification: Containment Risk Tier II — Standard intervention protocols apply; use of lethal force not authorized unless subject breaches metahuman containment policy. • Despite cooperative stance, subject has not submitted to full ARGUS evaluation.
SECURITY CLEARANCE NOTES: Access to full dossier contents restricted to Level 9 operatives and above. Any unauthorized attempts to duplicate, transmit, or disseminate subject data will trigger immediate lockdown protocol [Ref. ARGUS Regulation 16.3c]. Subject's full metahuman potential remains under evaluation; redacted portions accessible only by Director Waller or ARGUS Field Oversight Division.
[SECTION REDACTED – 03.16.XX / AUTHORIZATION: W. WALLER] Biological origin and medical anomalies flagged for meta-genetic analysis. Subject denies knowledge of pre-adoption trauma. Further investigation pending.

. . . back to the circus 🎪
#© moonyskarma#flashverse reality𑁤#jtscircusevent 🂱#shiftblr#shifting blog#reality shifting#shifting antis dni#reality shifting community#shifting motivation#loassblog#loassumption#loa tumblr#loablr#loa blog#master manifestor#law of assumption#shifting community#shifting journey#shifting consciousness#reality shifter#shifters#anti shifters dni#shifting realities#shifting reality#loa success
38 notes
·
View notes
Text
HACS, the Harrison Armory Combat System
The Harrison Armory Combat System, HACS for short, is a relatively new system of martial art developed by Harrison Armory. Designed to integrate with standard Armory doctrine, HACS is a modernized and modified version of traditional weapon-based martial art, mathematically optimized with aggregate combat data harvesting and extensive simulations in order to best suit the Armory’s propensity for energy and plasma based weapons.
The non-physical nature of an energy blade allows it to be able to pass through another physical blade, thus making strikes with an energy weapon almost impossible to block or parry; but also conversely makes it unable to block an attack from another weapon from simply passing through it. Thus, HACS is defined by its aggressive structure based on the principles of seizing the initiative and staying on the offense, direct footwork and economy of action, range control, and violence of action.
HACS fighters will typically stay out of range to formulate a plan of attack and maneuver into advantageous positioning, then explode into a short series of decisive strikes to force the enemy to defend. If the initial series of strikes do not kill or incapacitate, HACS fighters will then try to establish distance once again and return to neutral, preferably with follow up unarmed strike to push the enemy back and maintain initiative, though simply back-stepping is also an option if further aggression is ill-advised. HACS footwork is characteristically direct, moving back and forth in a straight line from the user to their opponent and eschewing complex footwork often seen in more traditional arts.
HACS encompass most forms of traditional melee weapons such as swords, axes, halberds and more, but befitting of a modern constructed martial art systems, HACS also accounts for modern modification and new designs, such variable emission setting allowing user to change the length of a blade mid-fight or even mid swing. HACS official training and certification requires a demonstration of mastery of the system's two basic disciplines, Energy on Blade (EB), the use of energy weapons against physical weapons, and Energy on Energy (EE), the use of energy weapons against each other. For most standard users and legionnaires, these two are enough, though further advanced disciplines are available for training, such as Energy and Shield (ES), incorporating the usage of personal shielding system into the martial art, both in conjunction with and against energy weapons.
Designed for vertical integration, HACS-M (Harrison Armory Combat System – Mechanized) is a sub-discipline of HACS for usage with mech combat. Formulated for ease of transition between systems, HACS-M employs much of the same principles and moves as HACS, maintaining its core direct aggression. The added durability of a mech and its comparatively lesser agility means HACS-M incorporate “Double Strike” in place of some defensive maneuver. “Double Strike” is an umbrella term for techniques where the user intentionally takes an attack in order to counter attack the opponent, using computer-mapped positioning to maximize armor placement and avoid damage to critical systems. Though designed for chassis class 1 to 3 and obviously ill-advised to unarmored personal combat, HACS-M has also been adapted for personal combat by heavily armored fighters, typically hard suit or power armor users.
As with most theories when put into practice, HACS and HACS-M has also splintered into countless variations over the years. While a centralized system still exists within the Armory’s standard armed force training, various other subsystems have popped up either through further independent modification, local adaptation, or syncretism with other martial arts. Of note are:
Valkyrie, an adaptation for aerial combat
Stinging Blade, a highly unorthodox and controversial syncretism with Jager Kunst pioneered by Sparri diaspora on Ras Sharma
DeSys, a school that emphasizes the destruction of enemy weapons instead.
81 notes
·
View notes
Text
THE 25TH HOUR | O3
“𝐌𝐄𝐌𝐎𝐑𝐘 𝐏𝐑𝐎𝐓𝐎𝐂𝐎𝐋𝐒”

"The most dangerous temporal anomaly isn't the one you can measure. It's the way your body remembers what your mind forgot."

next | index
— chapter details
word count: 2,5k
content: underground medical facility shenanigans, memory tests with Jin and Yoongi, Jimin being a chaotic enabler, involuntary physical responses defying temporal physics, and the team placing bets on how long Yoongi can maintain “professional distance" with leather gloves involved.

— author’s note
Y'ALL. The medical examination scene has been living in my head rent free for WEEKS. You know those moments when you're trying to write something serious and professional but your characters are like "no❤️ watch this"??? Because same.
We've got Jin being the only responsible adult, Yoongi attempting to maintain professional distance (and failing spectacularly), Jimin choosing violence as a lifestyle, and Y/N's body remembering things her mind doesn't. Also featuring: temporal physics being completely ignored in favor of sexual tension, inappropriate uses of leather gloves, and the team collectively deciding to Look Away™️ when things get spicy.
Speaking of the team - can we talk about how Jimin has evolved into this chaotic force of nature who just EXISTS to make Yoongi's life harder??? The way he just *gestures vaguely* KNOWS THINGS and chooses to use that knowledge for evil?? An icon. A legend. The reason Yoongi's blood pressure is through the roof.
Also, fun fact: This entire scene came from me thinking "what if we made temporal physics sexy?" and then it spiraled into... whatever this is. Shoutout to my physics professor who would probably have an aneurysm reading this. Sorry not sorry, but time manipulation is hot now, I don't make the rules.
Anyway, get ready for some quality UST featuring: precise measurements of inappropriate physical contact, clinical descriptions of sexual tension, and Yoongi pretending he's maintaining professional distance while everyone else pretends not to notice him failing miserably at it.

— read on
AO3

"Stabilized!"
Namjoon’s voice blooms across the room.
Agent Min releases your wrist like it's burning him, despite the fabric barrier. The sudden loss of contact sends your temporal readings fluctuating—a 0.7% variance you automatically note.
"Gloves?" Jin asks, already reaching for a drawer.
"Please."
The leather gloves hit his palm with practiced accuracy. He pulls them on with movements too precise, too controlled. Black leather, reinforced temporal shielding based on the metallic thread pattern, custom-fitted.
The man before you—Jin—carries himself like a medical professional, if medical professionals used quantum resonance meters and discussed memory patterns like cellular structures. Your analytical mind categorizes the differences: standard medical equipment replaced with temporal monitoring devices, traditional vital signs supplemented with chronological variance readings.
"Sit down, please." His instruction carries the same clinical tone you'd expect from a regular doctor.
You comply, settling onto what appears to be a medical bed. The surface feels wrong—vibrating at a frequency just slightly out of sync with normal time.
Agent Min shuffles through data streams with the doctor, their voices low but intense:
"...temporal resistance patterns..."
"...cognitive overlay rejection..."
"...signature destabilization risks..."
"Can I at least know what you're planning to do to me?" You interrupt their technical exchange, keeping your voice steady.
"Memories." Agent Min turns immediately when you ask. "We're attempting to reintegrate your memory backup."
"What memory backup?" Frustration edges into your voice. "That's not technologically possible with current—"
Agent Min exchanges a look with the doctor.
"Have they explained?" The doctor asks. "About forced memory integration?"
"Yes," Agent Min runs a hand through his hair. "Hoseok and Jimin made that abundantly clear."
"So my hands are tied regarding information transfer," the doctor says, settling into a chair facing you. His temporal signature reads oddly stable compared to the others you've encountered here.
"But you're planning to inject memories?" Your mind automatically starts calculating the energy requirements for quantum information transfer. "The technological limitations alone make that scientifically impossible—”
"Memory injection is actually quite different from..." He stops, glancing at Agent Min before sighing with something like fond exasperation. "Alright, let's start here—tell me what you know about this world."
You frown, analyzing the request. "What could I possibly know that you don't? You clearly have access to technology and information beyond standard clearance levels."
"Trust me," Agent Min murmurs, "we don't."
The doctor rolls his eyes at him. "We need to gauge the level of bleed-through this time."
"Bleed-through?" You ask, the term spiraling with curiosity inside your head.
"Min, timeline shifts since her last reset?"
"None."
"Well, at least there's that."
"Timeline shifts? Resets?" Your mind tries to parse terms that shouldn't exist in any approved temporal physics database.
"Please," the doctor says, "tell me what you know about this world."
You analyze the request, breaking it down into quantifiable components. "That's an incredibly broad query. Could you specify the parameters?"
"Start with temporal mechanics," he suggests. "How does time work?"
The question seems absurd—like asking how gravity works. It's a fundamental constant, documented through centuries of quantum research and temporal physics studies.
"Time is regulated by the Chrono-Sync Network through quantum resonance frequencies calibrated to maintain perfect temporal alignment," you explain, falling into the familiar rhythm of technical exposition. "The Master Clock, located in Sector 1, generates the base frequency that all Chrono-Sync Watches must match within 0.001% variance. Any deviation beyond that threshold triggers automatic correction protocols."
"And this system has always existed?" Agent Min's question carries an odd weight.
"Of course. The Network was established in 2157 following the Quantum Wars. It's basic history." Your voice holds the slight edge of someone stating the obvious. "The temporal monitoring system prevents chronological warfare by maintaining universal time synchronization. Before the Network, temporal terrorists could manipulate local time fields, creating devastating paradoxes."
"What about before 2157?" The doctor—Jin—asks carefully.
"Temporal chaos. Unregulated time flow. Multiple competing chronological frequencies." You recite the facts with precision. "That's why CHRONOS was developed—to prevent temporal warfare through standardization. The historical records clearly document the devastation caused by chrono-terrorism."
"And the 24-hour cycle?" Agent Min's question seems to carry extra significance.
"The natural human circadian rhythm." Your response is automatic. "CHRONOS simply enforced what was already biologically standard. Studies have proven that deviating from the 24-hour cycle causes severe physiological and psychological damage."
"Really?" Jin's pen scratches against his paper. "No other possible time structures?"
"The 24-hour cycle is scientifically proven to be optimal for human function," you explain with the precision of someone who has spent years studying these principles. "Any variation would create cascading temporal instabilities. The human brain is specifically calibrated to function on this cycle. It's elementary temporal biology."
"Friends? Relationships?" Jin's pen moves steadily, changing topics with suspicious abruptness.
The shift in questioning triggers a slight increase in your temporal readings—0.02% variance. Within acceptable parameters, but noteworthy.
"Limited social interaction to maintain optimal temporal efficiency," you recite. "Two approved recreational contacts: Lisa Martinez from the Academy, Thomas Park from my housing block."
Agent Min's jaw tightens fractionally at the second name. The reaction is precisely 0.23 seconds too fast to be casual. You begin calculating potential causation factors.
"And that seems normal to you?" Jin asks. "Limited social interaction for efficiency?"
"Of course. Personal relationships introduce temporal variance through emotional instability." The words feel rehearsed somehow, like a textbook you've memorized but never quite internalized. "The Network functions best when all participants maintain strict chronological compliance. Emotional attachments create unpredictable temporal ripples."
"What about deviation?" Agent Min's voice carries an edge. "Have you ever wanted to break schedule? Act outside approved parameters?"
"That would be highly inefficient.Temporal compliance is crucial for societal stability. The system exists to protect us from chronological warfare."
"You've never questioned it?" Jin presses. "Never wondered why everything is so perfectly structured?"
"Structure creates efficiency. Efficiency creates stability." The response is automatic, but your Chrono-Sync Watch registers a minor desynchronization. Curious. "Why would I question proven temporal mechanics? The data is irrefutable."
"Because your body already is," Agent Min says quietly.
You start to protest, but then you notice: your hand is reaching for your watch again. Seven minutes exactly since the last check. You've been doing it the entire conversation without conscious thought. You immediately begin calculating the statistical probability of such precise timing occurring naturally.
"That's..." You search for a logical explanation. "That's just good temporal maintenance. Regular monitoring ensures optimal synchronization with the Network."
"Is it?" Jin asks. "Or is it programmed behavior?"
You calculate probability matrices for their increasingly concerning implications. Their questions display either dangerous ignorance of basic temporal physics or... something else. Something that makes your precisely ordered world feel slightly off-axis.
"I'm not programmed." The words come out sharper than intended. "I have free will. I make my own choices. I'm certified in temporal monitoring, scheduled to start at the Center tomorrow morning. My employee ID is A-735, my clearance level is—"
"Perfect temporal compliance," the doctor interrupts, making notes. "Standard citizen programming. What else?"
You frown at his word choice. "Programming?"
"Just continue," Agent Min says. His eyes haven't left the temporal readings displaying your vital signs. You notice his attention seems to focus on specific frequencies—ones that shouldn't matter according to standard temporal theory.
"I..." You retreat into facts—the only stable ground in this increasingly unstable situation. "I grew up in Sector 4. Parents are both temporal compliance officers. Sarah and James Chen. I attended the Academy of Temporal Sciences, graduated top of my class in quantum mechanics and chronological theory. I live alone in approved housing block 7B. My daily schedule is optimized for maximum temporal efficiency as required by—"
"Parents' names?" The doctor interrupts again, looking up sharply.
"Sarah and James Chen," you repeat. The names feel solid in your mouth. You remember Sunday dinners, temporal compliance lessons, your mother's smile, your father's strict adherence to schedule.
Memory integrity: 100% clear.
"At least they didn't give her a husband this time," the doctor mutters.
Agent Min clears his throat loudly. The temperature in the room drops 0.3 degrees.
"A husband?" You ask, latching onto the inconsistency. Your mind automatically starts calculating the statistical probability of memory tampering based on their behavior. The results are concerning.
"Different reset," the doctor waves dismissively. "Continue. What do you know about CHRONOS?"
You catalog his dismissal for later analysis, noting the 0.47-second delay before his response. "The artificial intelligence system that maintains temporal order. Created in 2157 to prevent temporal warfare and ensure humanity's survival through perfect chronological control."
"What about anomalies?" Agent Min asks. "Temporal variance? Chronological inconsistencies?"
"Contained and corrected." You watch their reactions carefully, measuring micro-expressions against standard behavioral baselines. "Any significant temporal deviation is identified and eliminated before it can destabilize the Network."
"And what happens to those who deviate?" Jin's voice is carefully neutral.
"They're..." You pause, discovering an unexpected gap in your knowledge. Curious. Your temporal compliance training should cover all aspects of the system. "They're corrected. Brought back into alignment with standard temporal flow."
"How?" Agent Min presses.
"That information isn't included in standard temporal physics education," you admit, analyzing their reactions. Their behavior suggests they know something you don't—a statistical impossibility given your education level and clearance. Your hand automatically moves to check your watch again.
"What about emotional responses?" Jin asks suddenly. "Do you experience feelings that seem inconsistent with your memories or experiences?"
Your body chooses that moment to lean slightly toward Agent Min without conscious input. You straighten immediately, analyzing the movement with growing frustration. The proximity increases your heart rate by 3.7 BPM despite no logical reason for the response. Your temporal signature shifts by 0.06%—still within compliance range, but the pattern is... concerning.
"I..." You stop, recalibrating. "My responses are within normal parameters."
"Really?" Jin asks. "So your heart rate always spikes around strangers?"
You glance at the monitoring equipment—your pulse is indeed elevated. "That's likely due to the unusual circumstances." Your voice maintains professional detachment even as your body betrays you by shifting 0.2 centimeters closer to Agent Min.
"And the temporal resonance patterns?" Jin gestures to another reading. "The way your signature stabilizes with proximity to Agent Min?"
"Coincidence," you say firmly, even as your body shifts another 0.3 centimeters closer to him without your permission. "Temporal signatures naturally seek stability. It's basic quantum mechanics."
"With specific people?"
“Jin.”
"I..." You check your watch. Six minutes exactly until your next scheduled check. The wrongness of potentially missing it makes your skin crawl. "This isn't... I don't..."
"What we are trying to say," Jin interrupts, "is that perhaps your understanding of this world isn't as complete as CHRONOS wants you to believe."
You start to argue, but then you notice: Agent Min has shifted exactly 2.7 centimeters closer. The movement carries too much precision—like he's performed it countless times before. Like he’s anticipating something.
Your hand reaches for your watch again—five minutes and forty-three seconds until your next scheduled check. The compulsion feels simultaneously natural and foreign, like a subroutine you never consciously installed.
"Then choose to skip your next time check," Agent Min challenges.
Your hand is already moving toward your watch. You force it down, but your skin crawls with the wrongness of it. Five minutes and thirty-eight seconds until your next scheduled check. The knowledge sits like lead in your stomach.
"This proves nothing," you argue, even as anxiety builds at the thought of missing your seven-minute mark. "Regular temporal monitoring is simply good practice. The Network requires consistent synchronization to maintain stability."
But your mind is already cataloging the inconsistencies:
- Why does your body respond to Agent Min with mathematical precision?
- Why do you check the time every seven minutes with mechanical accuracy?
- Why does breaking that pattern feel physically wrong?
- Why can you remember every detail of your life with perfect clarity, yet find gaps in your knowledge of the system itself?
"I..." You swallow hard. "I need to check my watch in five minutes and thirty-three seconds."
"We know," Agent Min says softly.
His gloved hand twitches.
Voices interrupt your pondering.
"The quantum resonance patterns are fascinating but I think I'll pass on another lecture from Namjoon about temporal mechanics," The pink-haired man suddenly announces, sauntering into the room.
He immediately starts fiddling with Jin's equipment, who doesn't even flinch—just continues monitoring your readings.
"You'd think after hundreds of timelines he'd have a more interesting way to explain it," Hoseok adds, dropping into a nearby chair.
“Doesn’t matter how many times he explains, I don’t get shit.” Jimin responds. Then, glances between you and Agent Min. "So what's the story this time? Three kids? White picket fence? Nuclear family in temporal compliance heaven?"
Agent Min's foot connects with his shin. Hard.
"Ow! What? I'm just asking what narrative they programmed this time. At least it's not—”
"Jimin." Agent Min's voice carries warning.
"Not that you'd remember," Hoseok says, grinning despite the tension, "but last reset they gave you this whole elaborate backstory. Husband named Richard. Real piece of work."
Your mind tries to process this. "Richard?"
"Oh yeah. Super by-the-book temporal compliance officer. Yoongi spent months trying to trigger his outlier potential just so he could—”
"Hoseok." Agent Min's temperature spikes 0.4 degrees.
"What? I'm just saying, you did try to convert him. Multiple times." Hoseok's grin widens. "Though we all know it wasn't because you wanted him on the team."
Your analytical mind catalogs Agent Min's reactions: jaw tension increasing 15%, pulse elevated to 67 BPM, careful distance from your position maintained at exactly 1.2 meters in case temporal stabilization requires contact.
"The temporal variance patterns are unstable enough without adding cognitive stress," Agent Min says, voice clipped. "Focus on the present reset."
"Present reset," Jimin mimics, still rubbing his shin. "Like you weren't calculating exactly how many anomalies it would take before CHRONOS had to—”
"12 minutes," Agent Min cuts him off. "Either help with the readings or get out."
You find yourself analyzing his response with unusual intensity. "You can influence CHRONOS' resets?"
"No," he says too quickly.
"Yes," Jimin corrects.
"Sometimes," Hoseok clarifies.
"It's complicated," Jin adds, not looking up from his equipment.
Your head starts throbbing again. Agent Min takes exactly one step closer—close enough to stabilize your temporal signature if needed.
"You rewrote time to... eliminate my husband?" The words feel strange in your mouth. You have no memory of a Richard, no context for their claims, yet something about Agent Min's reaction feels significant.
"Technically, CHRONOS rewrote time," Jimin says helpfully. "Yoongi just... creates enough temporal instability that CHRONOS has to adjust things. Usually in ways that coincidentally benefit him."
"After trying to trigger Richard's outlier potential," Hoseok adds.
"Which didn't work," Jimin continues.
"Multiple times," they finish together.
Agent Min's hands clench at his sides. The room temperature drops another 0.5 degrees.
"Your temporal signature is spiking again," he says instead of addressing their comments. "Focus on the cognitive process before—"
"Before what?" You press. "Before you rewrite time again? Before CHRONOS erases more memories I apparently don't know I have?"
His eyes meet yours, and for a moment something flickers in them—frustration, resignation, something else you can't quantify.
"Before we run out of time," he says finally. "Again."
"Always running out of time with you two," Jimin mutters. "Some things never change, no matter how many resets."
You want to ask what he means, but your nose starts bleeding again.
It starts as a single drop—precisely 0.03 milliliters. Your analytical mind starts calculating the iron content before Agent Min moves.
His response time is 0.33 seconds—faster than standard human reflexes. The motion carries too much familiarity as he steps forward, black-gloved hand already reaching for your face. The leather is cool against your skin as he catches the blood with clinical efficiency, his hand remaining steady under your nose.
But there's nothing clinical about the way your pulse jumps 7 BPM at the sustained contact.
You look up, trying to analyze his expression, but his focus remains fixed on the task. His jaw tightens almost imperceptibly—you notice his masseter muscle contracting at 23% more tension than baseline. He makes a soft sound of disapproval as another drop falls onto the black leather.
The contact feels... correct. Like your body recognizes something your mind can't compute. His gloved hand doesn't waver, maintaining its position.
Temperature at point of contact: 2.3 degrees above normal, even through the leather.
Proximity: 34.2 centimeters closer than his usual maintained distance.
Your cognitive functions: Surprisingly compromised.
Jimin clears his throat with exaggerated purpose. Agent Min's head snaps toward him while his hand remains steady under your nose.
"Jin." His voice carries an edge of urgency. "Ready?"
Jin's fingers move over his equipment. The device in his hands emits a soft hum at exactly 432 Hz, releasing a cloud of temporally charged particles that coalesce into a perfect sphere.
"Yeah." Jin lifts the sphere with careful movements. The air around it distorts slightly—light bending at impossible angles.
"What is that?" Your voice remains steady despite the way your skin prickles with increasing temporal static. Agent Min adjusts his gloved hand slightly, catching another drop of blood without breaking contact.
"Memory backup." Jin adjusts something on the sphere's surface. "This shouldn't hurt, but temporal cognitive recalibration can cause some discomfort."
"Discomfort," Jimin mutters. "That's one way to put it."
Agent Min shifts slightly—angling his body 3 degrees more toward you, his hand never leaving its position. A protective stance your mind recognizes from standard security training. But this feels... different. Personal.
"Your neural activity is spiking" he says, voice carrying that strange mix of professional distance and something else. Something that makes your chest tight. "We need to—”
"How many times have you done this?" The question slips out before your analytical mind can stop it.
His free hand twitches—an aborted movement toward you that he catches at exactly 2.7 centimeters of motion.
"Too many," he says softly. Then, catching himself: "A-735, focus on maintaining cognitive stability. Your vitals are—"
"Going crazy because you're too close," Jimin interjects helpfully. "Maybe step back a few meters? You know, for medical purposes? Her heart's about to beat out of her chest."
Agent Min doesn't move. If anything, he shifts 0.3 centimeters closer, his gloved hand remaining steady under your nose.
"The proximity helps with signature dampening," he says, voice clipped. But you notice his heart rate has increased to 68 BPM.
"She's already stabilized in here," Jimin sighs. "You heard the man.”
"You are wearing the gloves, right?" Hoseok asks suddenly, eyeing Agent Min's position. "Because the way you're hovering—"
"Of course I'm wearing the gloves," Agent Min snaps, though his hand remains perfectly steady under your nose.
"Just checking," Hoseok raises his hands in mock surrender. "Given your track record with protocol 47.3..."
An adjustment of your position creates an unexpected point of contact—your knee brushing against what your analytical mind immediately identifies as anatomically significant. You immediately begin calculating the exact angle and pressure of the contact before you register its implications. Your body's response is both immediate and puzzling—heart rate increasing by 12 BPM, skin temperature rising 0.24 degrees.
Position correction should be simple. Yet your body seems to know exactly how to shift to maximize the contact pressure—a knowledge that triggers several questions about muscle memory and timeline retention that you file away for later analysis.
His gloved hand remains perfectly steady under your nose through sheer force of will.
"Wow, that ceiling tile is fascinating," Jimin announces suddenly, tilting his head back with exaggerated interest.
"Absolutely riveting," Hoseok agrees, studying his shoes with intense concentration.
Jin becomes very focused on adjusting his equipment settings.
Agent Min's voice comes out exactly 0.7 octaves lower than usual: "A-735. Position adjustment required."
You move with deliberate precision, establishing appropriate professional distance. Your body protests the movement with an intensity that warrants further investigation—when you're not calculating the exact newtons of force his masseter muscle is exerting.
"7 minutes," he grits out, the words tight with restraint. His tongue presses visibly against his cheek as he inhales deeply. "Jin, if that sphere isn't ready in the next 30 seconds—"
"Working on it, boss," Jin responds, still very interested in his calibration dials.
"Maybe if you stepped back..." Jimin suggests helpfully, still studying the ceiling.
"Can't," Agent Min responds through what sounds like clenched teeth. "Nosebleed."
His gloved thumb twitches minutely against your skin. The movement suggests significant muscular tension—likely from maintaining precise control over multiple physiological responses.
"You could just let someone else—" Hoseok starts.
"No."
"You sure there hasn't been any... accidental contact?" Jimin drawls. "Because this is giving me déjà vu from timeline 466 when you claimed you were 'just stabilizing her' but really—"
"6 minutes," Agent Min cuts him off. His temperature rises another 0.2 degrees. "Seokjin.”
Jin holds up the sphere, which now pulses with a soft golden light that matches the traces you've seen Agent Min leave. "Ready. But Yoongi..."
"I know." Something in his voice makes you look up again. His eyes meet yours for exactly 1.2 seconds before he looks away, though his hand doesn't waver from its position. "It has to be different this time."
"It's always different," Jimin says quietly. "Doesn't change how it ends."
Your nose threatens to start bleeding again. You feel Agent Min's gloved thumb shift slightly against your skin, ready to catch any new drops.
Time: 01:59:00 AM.
Temporal stability: Rapidly decreasing.
Questions: Infinite.
The way your body leans toward him without conscious input: Concerning.
The way he maintains careful fabric barriers between every point of contact: Even more so.

taglist: @cannotalwaysbenight @livingformintyoongi @itstoastsworld @somehowukook @stuti2904 @chloepiccoliniii @kimnamjoonmiddletoe @ktownshizzle @yoongiiuu93 @billy-jeans23 @annyeongbitch7
© jungkoode 2025
no reposts, translations, or adaptations
#yoongi fanfic#yoongi fic#yoongi x reader#bts fanfic#yoongi smut#bts fic#bts x reader#yoongi x you#yoongi x y/n#bts smut#yoongi angst#bts angst#bts fluff#bts scenarios#yoongi scenarios#yoongi imagine#bts imagine#bts fanfiction#yoongi scenario#yoongi fanfiction
50 notes
·
View notes
Note
Would hwr reader be the cool wine aunt? (I can see her accidentally getting drunk off wine thinking it was grape juice or non alcoholic, then chrollo having to supervise her the whole night lol)
anon ... are you a secret telepath because i've considered so many variations of this exact scenario.
for some context on HWR reader's abysmal alcohol tolerance — certain bloodlines from her home country hailed from the dark continent. they could temporarily boost their abilities, whether it be the five senses, strength, or speed, at the cost of enduring excruciating pain once the burst ends. a peculiar side effect owing to this constitution is that those who possess it are extremely sensitive to psychoactive substances. so, understandably, she takes great care in avoiding anything that could land her in a precarious position.
the common language in hxh isn't her native tongue, so if a word or term is obscure enough, all bets are off. for instance, in the earlier days when she just joined the troupe, paku once offered her a nightcap. HWR reader accepted. imagine her confusion when she was presented with a drink. it didn't look like any hat she'd seen before. the troupe greatly perplexed her at first.
the scenario you proposed has definitely happened before. here's the basic rundown:
her and chrollo were staking out an event under the pretense of being guests. a wandering waiter offered her a drink from his tray. it wasn't held in a champagne chute, martini glass, or the like, there was no indication to the beverage's true nature. she inquired over the ingredients. the waiter listed off what made up the concoction. the name of the hard liquor went over her head, it was the lovechild of a recent startup the event's owner had invested in to 'diversify his investment portfolio.'
it lacked the bitter tang commonly associated with alcohol. it was slightly sweet with a tarte aftertaste.
whilst sipping away and fraternizing with the other attendees, chrollo reappeared. he'd been piecing together a mental blueprint of the estate for later use. he easily integrated back into the social scene, almost as if he'd never left in the first place. before he'd even reentered the grand reception area, he'd caught onto a fluctuation in HWR reader's impeccable aura. while not an outright cause for alarm, he found it odd.
(some not SFW beneath the cut)
although he hid it well, he was genuinely surprised to see his normally abstinent lover indulging herself. she was critiquing the research of two gentlemen who had been not so subtly flaunting their game-changing findings the entire evening. the men appeared scandalized as she pointed out inconsistencies in their data and the like. he swooped in only when it became evident the men were about to raise a fuss, smoothly excusing him and his increasingly irate date.
he could roughly guess how this predicament came to be. he explained to her in a low and steady voice that this drink actually has a high alcohol concentration. it took a moment for her impaired cognition to catch up with his words. when the realization hit, however, she was not enthused.
by the time they'd made it back to their 'borrowed' vehicle, her legs were unsteady. there was a thin glaze over her eyes, like she was only half-present. on the drive back to the hotel, she'd randomly continue her earlier critique in an incomprehensive murmur. he never knew poorly falsified data was such an unforgivable slight in her eyes.
chrollo was growing increasingly intrigued by this unfiltered version of his otherwise prim and proper girlfriend. did he feel bad that she ended up in this position? kinda, but he wouldn't let anything happen to her. or, to be more precise, let anything happen to the civilians in the immediate area. not out of compassion, mind you, but for convenience's sake. he's trying to maintain a low profile in this area until the heist's completion. a dangerous, sword-wielding woman capable of wiping out an entire town's population should she see fit would be counteractive to this goal.
he dutifully keeps an eye on her in their suite. she vacillates between forgetting he's there or eagerly engaging him in a wide array of topics. everything from the separation of church and state to 'if he really likes her.' at this point, she'd shrugged off her outer garments (with his assistance), the heat of inebriation unbearable. chrollo had been exercising every modicum of self-control in his body as she crawled into his lap, perching herself there like it was her throne. her fingers, free from her usual gloves, brushing along the various grooves of his face.
"pretty," she hums. her blissed out expression, breathy voice, and the pressure of her body against his crotch makes him strain to behave himself. "my pretty boy."
he's grateful that she isn't lucid enough to note the rosy blush that spreads over his cheeks at this unexpected praise.
in a languid motion, her arms wrap around his neck. she embraces him tight enough that he can feel the soft swell of her chest, threatening to spill out from its restraints. she plays with the ends of his hair, humming a melody unknown to him, perfectly content. he allows himself some indulgence — his hands settle on either side of her hips. to help steady her, he tells himself. for such a proficient liar, this excuse is admittedly pathetic.
"boss."
"hm?"
"i have a secret," she whispers. this piques his curiosity, overriding his previous sentiments to respect her privacy. selfishly, he hopes she doesn't remember this come morning. otherwise, he'll be in for an earful...
"oh?" he goads her on. "and what would that be?"
(goodbye plausible deniability).
her lips brush against his outer ear and he shivers.
"i've fallen in love with someone."
his breath hitches in his throat. he ceases his previous ministrations of rubbing circles into her skin. despite enjoying three years of sex, heists, and frequent companionship, those infamous three words have yet to be uttered. they've made it evident that they're exclusive, but that's about it. neither of them have delved into the nitty and gritty of whatever their relationship truly means.
momentarily, he forgets how to weave elaborate webs that ensnare his victims right where he wants them. all eloquence and posturing melts away. what little of him that leaves remaining utters his next two words, not the persona whose charisma could rival a manipulator's hatsu.
"with who?"
the raw, guttural urgency he speaks this inquiry with is foreign to his ears. he wonders what he'd do should she profess devotion for another. would he have what it takes to respect her choice? it's a silly question; of course he wouldn't, not past a chilling smile that doesn't reach his eyes.
alas, this hypothetical is put to rest. its his name that she speaks. the accent she tries suppressing sneaks out, curling around each slowly enunciated syllable. after what feels like an eternity, he relaxes, sinking back into the plush couch.
"don't tell him," there's a threatening edge to her voice.
chuckling softly, he hugs her tighter.
"i won't."
#chrollo x reader#not sfw#hell within reach#this ended up getting longer than i expected GJSKDFL#answered#Anonymous
180 notes
·
View notes
Text
Trans-Atlantic relations as we know them are over. The Trump administration in the United States has made it clear that it prefers striking a deal with Russia or other autocrats over maintaining long-term commitments with its Western partners. These threats have united Europeans, who are ramping up their support for Ukraine, investing heavily in their own defense, and striving to build a stronger and more resilient economy. Meanwhile, U.S. institutions that once supported international cooperation and American soft power are getting dismantled.
These developments amount to a trans-Atlantic divorce—and also an opportunity to shape a new trans-Atlantic future by investing in the human capital that the Trump administration has made newly available. At the same time that Europe is trying to build its military capacity, stand on its own feet in intelligence, and make its data and energy infrastructure more resilient, the United States is bleeding talent across the board. U.S. human capital can help build Europe’s future and lay the foundation for a potential renewed trans-Atlantic partnership sometime in the future.
The Trump administration has frozen vast federal funds and announced the elimination of as many as 100,000 jobs, including senior military and security personnel. It has also threatened to push aside military officers who support diversity, equity, and inclusion. The treatment of U.S. intelligence agencies has been even harsher. The CIA has offered buyouts to numerous staff members and initiated the termination of an undisclosed number of contracts for junior officials and probationers.
While the exact numbers of those who have retired or resigned from U.S. intelligence agencies and the military are classified, it is evident that this action resembles a purge of thousands of competent employees. This has led to numerous debates within the United States, with the most prominent being about potential threats to U.S. security and the loss of top talent.
While this talent may potentially compromise U.S. security and military capabilities, it could also present unexpected opportunities for the European defense and intelligence sectors. Suddenly, thousands of competent military and security personnel are seeking new employment. While many would likely consider positions within the U.S. private defense and security sectors, the sheer number indicates that some may be interested in pursuing careers in other regions. Given the evident discontent with their dismissal, as well as their disagreement with U.S. President Donald Trump’s policies on basic human and political levels, it is conceivable that some would consider offering their services to another NATO army or agency in another Western country.
The transfer of personnel who have worked on highly sensitive matters or are trained in one military doctrine to another country is not a straightforward process. However, it is not impossible. Such a move would be more than opportunistic; it would also have practical and symbolic political benefits.
While direct transfers of officers between NATO members’ armed forces are rare, mechanisms like exchange programs and NATO assignments exist to promote interoperability. These arrangements, supplemented by targeted training and professional development, ensure that officers can effectively integrate and operate within different national military frameworks.
It is fair to assume that some of the U.S. military personnel who have been laid off, or are now dissatisfied and considering leaving, have participated in such exchange programs in the past, which would make it easy for them to engage again with those NATO member units in Europe. There should no obligation for U.S. military personnel to join regular European units in a standard service contact; they could be hired as advisors instead, which would be politically and administratively more palatable for the hiring militaries.
Clearly, for intelligence professionals, such a transition may be more challenging due to laws over nondisclosure and state secrecy. But by employing some creativity—within schemes championed by philanthropic foundations, for example—it could be possible. One could think of fellowship programs, for example, that would allow senior officials to maintain their income and independence, while providing consultation and support for European public administrations at the same time. Although not directly comparable, consider the effort that George Soros made after the end of the Cold War to sponsor scientists from the former Soviet Union in order to preserve nuclear and scientific expertise from falling into the hands of rogue states.
Such trans-Atlantic connections could also be a significant political statement. By welcoming competent and able U.S. personnel into their own agencies, Europeans would demonstrate that Euro-Atlantic ties extend beyond mere government relations—a message that resonates not only with the Democratic Party but also with the many Americans who disagree with Trump. It would also underscore Europe’s commitment to continue working together for mutual benefit, strengthening the trans-Atlantic relationship and demonstrating solidarity with those Americans who have been recently laid off.
This sort of hiring spree by Europe may not require extensive publicity, but it will certainly diverge from the Trump administration’s narrative and strategic approach. This could potentially cause some diplomatic friction, but it could also be of some broader diplomatic benefit. Europe can demonstrate its ability to act as an unpredictable and potentially influential independent entity, capable of identifying and acting on material opportunities that become available. It’s an ability that demands to be taken seriously.
What is possible in military and intelligence domains is even easier in the broader economy, where Europe can gain valuable insight from public officials who have experience in the oversight of sectors like energy and data, or other domains marked by integrated platforms and collaborative work such as public health and science.
It’s likely that European governments will be slow to provide the necessary support for hiring former U.S. officials, given various legal and bureaucratic obstacles. Legally, it may be much easier for personnel with U.S. security clearances to receive a fellowship or contract from a U.S.-based foundation rather than one from a foreign government. Therefore, philanthropists on both sides of the Atlantic, shocked by the dismantling of the institutions and tools of American soft power and geopolitical leadership, could act before governments step in by providing seed capital. Starting fellowships programs and imagining short-term affiliations or consultancy contracts would allow senior leadership from the United States to be included in Europe’s construction.
In these turbulent times, such links would create an alternative integration of the Western world that is focused on networked human capital. All this would have both short- and long-term positive effects. It would immediately speed up the improvement of European security and intelligence. In the long term, it would safeguard the basis for a future trans-Atlantic alliance through interpersonal connections and a shared culture.
However, it is urgent to think about how trans-Atlantic relations will look after the current divorce. It is not only because the investment in Europe’s defense and intelligence capacities needs to start immediately with full speed, but also because U.S. talent is already on the job market.
Time is of the essence. As with all good ideas, Europeans will not be the only ones pursuing an investment in U.S. human capital to strengthen their own interests. American employers will inevitably be among those competing for this talent. And U.S. intelligence has produced evidence that Russia and China are already scouting disgruntled federal workers. Europeans would be well advised to focus on helping the many competent officials currently in distress, if only for the sake of giving the West a chance to survive its current turmoil.
21 notes
·
View notes
Text
What's the dead salmon study, and what does it tell us about fMRIs?
fMRIs generate roughly 130,000 voxels in every set of scans.
A voxel is a very small cube. Remember the ones you played with in school?

Like that.
Put together, they form a 3-D picture.
In the background of fMRIs is static and interference.
Through completely random chance, with over 160,000 voxels of data to comb through, the area around a dead fish's brain showed "activity".
The activity was natural interference, which coincidentally "lit up" in a way that set off sensors. It's not actual activity, but what does this tell us? What can we learn from this?
What was the point?
According to the lead researcher, "In fMRI, you have 160,000 darts, and so just by random chance, by the noise that's inherent in the fMRI data, you're going to have some of those darts hit a bull's-eye by accident."
Like adjusting the contrast on a photo, researchers can filter data to see through the noise, but in doing so, you have to ADD additional checks to maintain data integrity.
You can set the filter too high and eliminate false positives, but you'll miss things under the threshold. Set the filter too low, and you get active voxels in a dead fish's brain.
The point of the study isn't to prove that fMRI shouldn't be used or are worthless. It's to show that there's a fine line in that filter level, and that additional verifications MUST be made.
The answer is multiple comparison corrections.
Data collection and interpretation can seem very simple at first glance. Orange around a fish's brain? Clearly it's examining the photos and trying to determine the emotion of the people in the photos, as requested.
No, seriously, they put a fish in a machine and asked it to do the same tests as any other person in the scanner. They talked to it.
I think that's neat :)
But the point of the study was that it's not that simple. That orange could be nothing or it could be something. You HAVE to take the additional steps.
According to Oxford academic,
'The dead salmon study was not bashing functional MRI, it was about people who refuse to use multiple comparisons correction in functional MRI analysis … the salmon is important because it drew attention to the problem, but it’s not a problem with functional MRI as such’.
Yes, the problem is with the researchers.
So what about current fMRI research into DID?
Well, any paper that's been published has had its methods scrutinized. Considering:
1) the number of papers from THE MANY different organizations all showing the same things
2) the repeatability of the findings, over all these studies
3) the decades upon decades of repeated findings, and the additional scans and research in other areas of interest connected to it
4) the mentioned and approved comparisons within the studies
6) the rigorous data sorting involved in ALL of the studies combined, and the noted methods of sorting and interpretation, and the acceptance of sorting methods by MANY various journals
5) and what we are actually seeing on scans, AFTER multiple comparisons...
I think the DID studies are just fine when we're talking about the dead fish study and fMRIs.
#debunk#someone doesn't know what the dead salmon study is#research#fmri#at last check the dead fish study was not accepted or published fyi#syscourse#pro syscourse conversation#sysconversation#did#osdd#cdd system
38 notes
·
View notes