#multi router
Explore tagged Tumblr posts
Text

he’s also ambidextrous but don’t tell him
#persona 5#akira kurusu#ryuji sakamoto#morgana#can be#pegoryu#Bc a bro be multi shipping these days#ty Megan for opening my eyes to sunshine boy shipping#new router Monday and then I’m kicking it into high gear to get stuco stuff done >:3#also I’m like ~50 away from 2000 followers here which is INSANE#Ik a lot of people have dropped off but god I am incredibly grateful 🥺🥺🥺
549 notes
·
View notes
Text
youtube
The Wi-Fi Multi-Tool You Need
Wow! The WLAN Pi R4 is such a useful tool for wireless networking! It basically does everything you'd want it to do. In this video, I go over most of the features of WLAN Pi R4 and the WLAN Pi OS so that you can have a complete picture of this device's capabilities. Let's do it!
#make your wifi faster#wifi router#education#free education#hacking#technology#educate yourself#security#educate yourselves#youtube#The Wi-Fi Multi-Tool You Need#wi fi#cool tech#tech tips#computer#computing#nerd talks#geek#Youtube
17 notes
·
View notes
Text
Prepárate para el Futuro! Descubre los Switches Multi-Gigabit de 2.5G, 5G y 10G para una Red Imbatible - #Tecnocompras #Switches #Redes #Routers

#Prepárate para el Futuro! Descubre los Switches Multi-Gigabit de 2.5G#5G y 10G para una Red Imbatible -#Tecnocompras#Switches#Redes#Routers
0 notes
Text
Multi-Language Next.Js 14 App Router Website Using i18next – RTL Support
We already have an article titled “Multi-Language Next.Js 12 Website Using I18next – RTL Support” that explains how to create a multi-language website with the help of Next.js 12 page router and i18next – RTL support. However, this article will discuss how to create a multi-language website using Next.js 14 App Router and i18next with RTL Support. Prerequisites I assume that the reader has a…

View On WordPress
#app router#i18next#latest next js#multi-language next.js 14 app#nextjs multiple languages#rtl support
0 notes
Text
youtube
0 notes
Text
OLAX AX6 Pro: Il Tuo Alleato Perfetto per Connessioni Esterne e Gruppi Numerosi
OLAX AX6 Pro: Il Tuo Alleato Perfetto per Connessioni Esterne e Gruppi Numerosi Il Router OLAX AX6 Pro 4G si presenta come una soluzione robusta e versatile per le esigenze di connettività wireless. Questo router 4G LTE offre una serie di caratteristiche e funzionalità che lo rendono adatto sia per l’uso domestico che per applicazioni all’aperto. Il Router OLAX AX6 Pro si distingue per le sue…

View On WordPress
0 notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
WIP: Eldritch Tech Support Chapter 1: Helping a Spider Aspect
[Author's Note: this is the first chapter of a long, multi-chapter story that is likely going to be longer than all the other eldritch tech support stories combined, probably north of 20,000 words. As of writing, I'm just under 8,000 words and I haven't even hit the main plot yet. This is also being written in third person because it feels very necessary for story and scenes, I do plan on redoing some select parts in the traditional second person to see how it flows. Please enjoy and thank you to everyone who has read and supported me so far!]
Tech support is hard, this is a known fact, not a secret.
To be good at tech support you really need to have intelligence, charisma, and lots of faith.
Luckily Aeth knew that they had intelligence, well as much as they could know that about themself. They knew how to code and use some of the languages of computers, including the notoriously complex and silly C++- (C Plus Plus Minus). They had a degree from a local university attesting to that effect. Intelligence also governs knowing how computers interact with each other, and how the hardware within a computer interacts with the computer as a whole.
They're also fairly certain they have charisma. At least that's what their best friend Lyta keeps telling them.
"You have such an easy charisma about you. You're nice, easy to talk to. It's why I like you so much," she says at least once a week.
Charisma for tech support is a must because people can be weirdly cagey with their personal electronics, and they often refuse to tell the whole story from some combination of shame, self interest, and ignorance. The people themselves are a puzzle that require trust to solve and get them to reveal what insane, stupid, nonsensical things that they did to the whole system to get it to function this way.
However, the most crucial skill to have in tech support is faith.
Faith is key to figuring out exactly what the hell is going on and why the client believes that this whole thing is working, and why the working thing suddenly stopped working. Why the things that should work, do work.
They all have to be something of a priest with no god. They become a priest with every job, a priest that believes in this specific code, a priest of servers and computers and cold dead things imbued with the power of lightning and math.
Every job is a little bit different, a little bit stranger than the one before it. Every role of a priest ever so slightly different.
And Aeth has been accused of having too much faith at times. Faith that has to go somewhere, so it goes into the job.
Aeth was out in the field today. Luckily their rotation was pretty easy, they had two days out in the field, two days in the call center. Not that bad, all things considered. This was their last day before their thankfully long weekend which couldn't come soon enough.
It had been a busy day, crisscrossing their district in the northeast of the city, bouncing between several different tech support calls. Mostly internet related things, lots of outages and router trouble, at least one person was having their router haunted by his mother-in-law.
If they were lucky they'd only have two more calls to do before they called it a day and finally went home.
But that's the thing about their luck, it was always bad.
The penultimate job was for an underearth spider aspect god. They couldn't remember the exact religious denomination they belonged to, but it mattered little.
It is the nature of priests and tech support personnel to be superstitious.
They changed in the work van before heading to the third floor walk up the spider aspect lived in.
The rules for spider aspects were to wear colors, but not super bright, anything that attracted too much attention was either predator or prey. A nice pastel blue to signify that they weren't aggressive but also that they weren't something to be consumed.
There were plenty of rules and restrictions on the entities that lived in the city, and they knew that their job would never willingly send a tech support person into the lair of a giant person-eating spider, but they still had that fear, and that fear fed the superstitions.
Thus they changed in the van and before they went into the den of the spider, they grabbed a small vial of an anise solution, something that was supposed to be abhorrent to all spiders.
It was just in case, they told themselves.
They reached the door and knocked a few times, calling out to announce themselves.
"It's Tech Support," Aeth called out.
A few moments later the door cracked open and out spilled some darkness.
"We called for you," the entity just beyond the door said in a raspy voice with several clicks as they spoke.
"My name is Aeth," they say as they hold up their work ID to verify that they are there to help.
"Come in," the spider aspect said.
The door creaked open, and Aeth stepped beyond it to the apartment. It was dark and dry in there, it smelled faintly of some kind of incense, but they couldn't place exactly what kind. The darkness felt almost like a blanket draped over everything.
"You've had some issues installing some hardware?" they say as the spider god closes the door.
The spider was tall, almost seven feet but that was with all the hunching over and keeping their many limbs tucked in close. If they were to straighten up and spread out they would be almost oppressive. They were dressed simply, with a t-shirt that had a very detailed train on it that said, "My One True Love The A57-19 Commuter".
The spider nods it's great, large head.
"New keyboard, won't work," the spider said as it led Aeth towards the area where the desktop sat. "Requires new drivers, very frustrating." They can't help but notice the awkward way the spider can't quite pronounce the s's in their sentences, and how they have been deliberately avoiding them.
"Should be an easy fix," Aeth said as they sat at the computer and took out their own equipment.
The second they said it, they knew that they shouldn't have.
---
Fifteen minutes into the job, they knew that things were much much dumber than they should have been.
The new mechanical keyboard need some kind of new driver installed but it wouldn't give any indication into what driver it needed. Aeth spent a decent amount of time looking up the exact make and model of the keyboard on their own equipment, but it seemed that the company that made it flamed out very hard a few months ago.
("Found keyboard preowned, very cheap, in great condition, am on budget," the spider explained.)
The company wasn't the best or the most trustworthy, thus their sudden and total collapse.
As they were very close to locating the problem suddenly a small train that they didn't notice on a track hidden in the darkness of the apartment all but thundered in. The track was elevated near the ceiling, and the small model train was bright and loud in the dark and quiet room. It looked like some kind of Immortal Dancer party train with bright, flashing neon attached to all the train cars.
The entrance came as a shock to Aeth, but it really shouldn't have. They had a look at the computer and saw the icons on the desktop.
The spider aspect had three different train simulation games and they might have peaked and saw that they had logged close to 800 hours on one of them.
They tried to apologize to Aeth for the interruption and the train was on a timer that they had forgotten about, but honestly, whatever brings people joy, even if they are an underearth spider god aspect that would give some humans nightmares.
"I'm not here to judge," Aeth assured them and returned to the problem.
Eventually, they found the fix when they took the keyboard apart and found the little add-on that shouldn't have been there.
After examining it closely, and double checking their work, Aeth turned to the spider. "I think I found the problem. NDIVISION, the company that made this keyboard went out of business a few months back under a lot of customer complaints and bad business practices. They had, apparently, installed a keylogger in their keyboards to nominally track the use of their keyboards and when things needed to be replaced but was a massive security and privacy risk, so the complain exploded essentially so that suing them would be very hard to do. The keylogger is trying to reach a server that doesn't exist anymore."
The spider looked incredibly disheartened. Aeth privately congratulated themself on recognizing the body language of a spider god aspect.
"I can, probably, fix it. But the trick is that this will 100% void any warranty that you got with the keyboard, but since the company that would fulfill the warranty doesn't exist anymore."
"What can be done?"
"I can fix it, if you tell me I can violate the warranty. It might break later down the line, but this will work for all your day-to-day needs."
"Streaming?" The spider looked eager. Aeth had recognized the setup of a new streamer, trying to get their thing off the ground.
"Absolutely."
"Go ahead."
Aeth nodded and in a few short moments, removed the keylogger, then quickly wrote some code into the driver for the keyboard to bypass the keyboard trying to call the server of a defunct, terrible company.
The whole job took an hour.
Before they left, Aeth left the name of a very good company that made excellent keyboards when the spider was ready to upgrade to something new.
The spider thanked Aeth profusely, and almost didn't let them leave to get to their next job.
It was still early enough to make it to their last job of the day.
Hopefully this one would be much easier than the previous one.
Hopefully Aeth's luck would hold out.
if you like this check out my kofi page where you can read subsequent chapters early and find a bunch of my other stuff
#eldritch tech support#chapter 1#this is going to be long and hopefully good#it takes a while to get going but that's because everything is necessary#we need a lot of setup and a lot of character#that way you feel something when i take it all away and put them into one of the many many hells#if you need more of this i've got plenty of other ETS stories and this is set in my Cold Black Iron and Green Fire world so read those#i like them a lot
50 notes
·
View notes
Text
Rotary CNC Router Machine
At GK Laser Enterprises, we pride ourselves on delivering cutting-edge solutions to meet the evolving needs of the manufacturing and fabrication industries. One such innovation that has gained popularity for its versatility and precision is the Rotary CNC Router Machine. As a leader in CNC technologies, we offer a range of advanced CNC machines, and today we dive deep into how a rotary CNC router machine can revolutionize your operations.
What is a Rotary CNC Router Machine? A Rotary CNC Router Machine is a computer-controlled cutting machine that uses rotary tools to carve, cut, or engrave materials in three dimensions. The term “rotary” refers to its ability to rotate the material around an axis while it works, providing access to all sides of the material. This capability enables intricate detailing, sculpting, and shaping of cylindrical or irregularly shaped materials.
Unlike traditional CNC routers that work on flat surfaces, rotary CNC routers can handle 3D shapes, making them ideal for creating complex, multi-faceted designs.
How Does a Rotary CNC Router Machine Work? The Rotary CNC Router works by rotating the material, typically using a rotary axis attachment, while the cutting tool precisely follows the programmed paths. Here’s a breakdown of the process:
Material Preparation: A workpiece, such as wood, metal, or plastic, is mounted on the rotary axis, which allows it to rotate. Programming: A computer-aided design (CAD) program creates a digital blueprint of the desired outcome. This is then converted into machine-readable code using computer-aided manufacturing (CAM) software. Cutting Process: The router uses its rotary axis to rotate the material while the cutting tool moves along the X, Y, and Z axes to carve, cut, or engrave the material into the desired shape. Finishing: Once the operation is complete, the workpiece is inspected and may require minimal finishing, thanks to the machine’s precision.
Key Features of a Rotary CNC Router Machine High Precision and Accuracy: Rotary CNC routers are known for their precision in handling complex designs, offering high accuracy even in detailed cuts and engravings. Versatility: Whether you’re working with wood, metal, plastic, or composites, the rotary CNC router can handle a wide range of materials. This versatility makes it invaluable for industries such as furniture design, sculpture, and sign-making. 3D Carving and Engraving: With the ability to rotate the material, rotary CNC routers are ideal for creating 3D objects like sculptures, chair legs, moldings, and even complex cylindrical designs. Automation and Efficiency: The CNC aspect automates the cutting process, ensuring uniformity in production and reducing the need for manual labor. This enhances efficiency and speeds up production time.
Why Choose a Rotary CNC Router Machine for Your Business? If your business requires precision, complexity, and scalability, a rotary CNC router is a wise investment. At GK Laser Enterprises, we emphasize the value it can bring to industries like:
Furniture Manufacturing: Intricate 3D carvings and details for chair legs, columns, and sculptures can be easily achieved using rotary CNC routers. Sign Making and Woodworking: From large signs to ornate wood designs, rotary CNC routers deliver exceptional precision that elevates your craftsmanship. Sculpture and Artwork Creation: Artists and designers benefit from the ability to craft complex shapes and details, providing unmatched creativity. Metal and Plastic Fabrication: Industrial manufacturers who work with metals and plastics can create custom parts, components, and molds with great precision.
Benefits of Using a Rotary CNC Router Machine Enhanced Productivity: With automated processes, your business can take on more projects with faster turnaround times, maximizing profitability. Cost Efficiency: Despite the upfront investment, the long-term savings on labor, material waste, and improved product quality make it a highly cost-effective solution. Precision and Consistency: The automation ensures that each piece you produce is identical in quality and detail, improving overall consistency. Flexibility: Whether you’re producing one-of-a-kind custom pieces or bulk products, the rotary CNC router offers the flexibility to handle both with ease. Lower Material Waste: Precision machining ensures that there is minimal waste, reducing the cost of raw materials and promoting sustainable practices.
Why Buy From GK Laser Enterprises? At GK Laser Enterprises, we provide high-quality rotary CNC router machines tailored to meet the unique needs of businesses across industries. With our deep industry expertise, we ensure that you get the most suitable machine for your applications, ensuring optimal performance and cost-efficiency.
We also offer:
Comprehensive Training and Support: Our team will provide full training on how to operate and maintain your CNC router machine. Maintenance Services: Regular servicing to keep your machine running smoothly, ensuring minimal downtime and maximum output. Custom Solutions: We understand that every business has different requirements, so we provide customized solutions that best fit your needs.
Conclusion The Rotary CNC Router Machine offers unparalleled precision and flexibility, making it an essential tool for businesses involved in woodworking, metalworking, and creative design. At GK Laser Enterprises, we’re committed to providing top-tier CNC solutions that enhance productivity and reduce costs. By investing in a rotary CNC router, your business can stay ahead of the competition while delivering superior quality products. Contact us today to learn more about our CNC machines and how they can benefit your operations!

2 notes
·
View notes
Text
The Darkweb: Exploring the hidden crimes of the Internet

The Dark Web is a complex and often misunderstood segment of the internet, shrouded in secrecy and notorious for its association with illegal activities. This hidden part of the web, accessible only through specialised software like Tor (The Onion Router), allows users to navigate anonymously, which has fostered both legitimate and illicit uses. The Dark Web is a subset of the Deep Web, which itself constitutes about 90% of the internet not indexed by traditional search engines. While most users interact with the Surface Web, the Deep Web includes private databases and secure sites, whereas the Dark Web is specifically designed for anonymity and privacy. The Dark Web emerged from projects aimed at ensuring secure communication, originally developed by the U.S. Department of Defence in the early 2000s. [1] [2]
Hidden Crimes in the Dark Web
The anonymity offered by the dark web has made it a hub for numerous forms of criminal activity. From illegal marketplaces to cybercrime forums, this underworld of the internet is teeming with hidden dangers.
Illicit Markets and Drug Trade
One of the most notorious aspects of the dark web is its marketplace for illegal goods. Websites like the now-defunct Silk Road offered a platform where users could buy and sell illegal drugs, firearms, stolen goods, and counterfeit documents. These black markets are often operated using cryptocurrencies such as Bitcoin to further mask identities and ensure untraceable transactions.According to a 2019 study by the European Monitoring Centre for Drugs and Drug Addiction, the dark web drug trade has grown exponentially, with millions of dollars' worth of drugs being sold monthly across various platforms . [3] [4]
2. Cybercrime and Hacking Services
The dark web also serves as a marketplace for cybercriminals. Hacking tools, ransomware-as-a-service, and stolen data are regularly exchanged in these hidden corners of the internet. Criminals offer services ranging from DDoS attacks to the sale of stolen credit card information and personal identities. Some forums even provide tutorials for novice hackers looking to learn cybercrime techniques. [5]
3. Human Trafficking and Exploitation
While less publicly discussed, the dark web has been linked to disturbing trends in human trafficking and child exploitation. Illegal forums allow criminals to sell services or even traffic victims, relying on the secrecy provided by encryption and anonymity transactions. These criminal activities often occur alongside other heinous content like child abuse imagery, which is tragically prevalent in certain corners of the dark web . [5]
4.Weapons and Assassination-for-Hire
Another dark aspect of the dark web is the sale of illegal firearms, explosives, and even assassination services. Websites provide arms to buyers without the restrictions and regulations of the surface web. Though some claims of hitmen-for-hire on the dark web have been debunked as scams, the sale of illicit firearms remains a significant concern for global law enforcement agencies .
Top 5 Notorious Cases on the Dark Web
(Content Warning: This list includes some horrifying incidents and scary dark web stories. We suggest you skip entries if you’re faint of heart or suffering from any type of anxiety or stress disorder.)
1. Banmeet Singh’s $100M+ dark web drug empire gets brought to light
Starting with a fairly recent case, Banmeet Singh of Haldwani, Northern India was sentenced to eight years in prison in late January 2024 after he was found to have created and led a multi-million dollar drug enterprise.The Indian national also forfeited $150 million in cryptocurrency. This proved to be illegal drug money that was laundered into cryptocurrency. Singh used various dark web marketplaces to create his drug empire. According to the U.S. Department of Justice, Singh shipped drugs from Europe to eight distribution centers in the US. After, these were transported to and sold in all 50 US states and other countries in the Americas. Singh was arrested in London, where he was residing in 2019. In 2023, he was extradited to the US. [7]

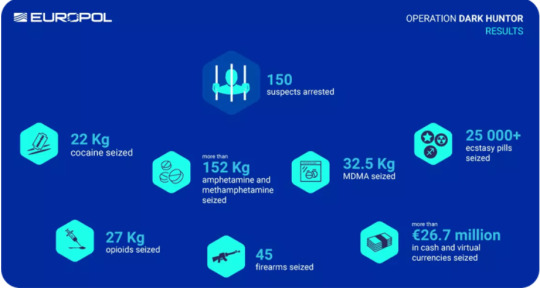
2. Operation Dark hunTor results in 150 arrests in nine countries
We’re moving from one multi-million-dollar illegal contraband case to the next. In 2021, Euro pol, Eurojust, and the police forces of nine countries conducted one of the biggest anti-crime operations the dark web has ever seen: Dark hunter. This operation resulted in 150 arrests across Australia, Bulgaria, France, Germany, Italy, the Netherlands, Switzerland, the United Kingdom, and the United States. All of the arrested were allegedly involved in buying or selling illegal goods on the dark web. The authorities found some articles in the possession of the arrested that strengthened their case: EUR 26.7 million (USD 31 million) in cash and virtual currencies, 234 kg of drugs, and 45 firearms.Italian authorities also managed to close down two dark web markets that boasted over 100,000 listings for illegal goods, DeepSea and Berlusconi. [7]
3. Operation DisrupTor exposes a dark web drugs distribution center
Amid the Covid pandemic, most businesses were struggling. Meanwhile, Operation DisrupTor suggests the drug business was still prospering. In February 2020, a group of FBI agents found 50 pounds of methamphetamine and thousands of Adderall pills in a storage shed in Los Angeles. The drugs, and the firearms that were also found, belonged to a crime network that had completed over 18,000 drug sales on the dark web. The criminal syndicate hid the drugs in a shed that they had made to look like a legitimate mail-order business. Their dark web drug sales included shipments to other dark net vendors, street dealers, and actual consumers. [7]
WATCH FULL VIDEO [8]
4. Attempt to hire a dark web hitman backfires
Now and then, crazy deep web stories pop up about how easy it is to hire a dark web hitman. One of these urban legends, however, turned out to be true. In February 2024, a woman from Canberra, Australia, pleaded guilty to inciting another to murder. The woman claimed to have contacted a dark web hitman (on the dark web marketplace Sinaloa Cartel) to murder her wealthy parents as part of an inheritance scheme. Supposedly, the total agreed-upon sum for the murder was $20,000, of which she had already paid $6,000 as a downpayment, using Bitcoin. It’s hard to say if the woman was actually talking to a contract killer or a scammer. Let’s just say we’re just happy the Australian court system was on to her before we could find out. While we don’t encourage anyone to go looking for a hitman on the dark web or elsewhere, this case goes to show that even on the dark web and while using crypto, many actions are retraceable. We always recommend people with good intentions to go for maximum privacy, as it’s no one’s business what they’re doing on the dark web. A great way to improve your privacy is by using NordVPN. NordVPN hides your IP address and encrypts your traffic, plus it blocks malicious links. [7]

5. No Love Deep Web takes dark web enthusiasts on a treasure hunt
Back in August of 2012, visitors on the dark web could find clues scattered on the network that led them through a fascinating alternate reality game. Much like Cicada 3031’s 4chan game, the clues led regular users through an array of clever clues set up like a treasure hunt. The dark web game employed a lot of encryption means to hide its hints, including the Caesar cipher, QR codes, Morse code, and a lot of other similar encryption methods. All of the clues were spread around dark websites, and one participant recounts the experience as quite thrilling:

So what was going on? Well, it wasn’t a secret government agency recruiting new members, and it wasn’t a feat of a group of cybercriminals.
Rather, the game was created by the experimental hip-hop group Death Grips to promote their new album, No Love Deep Web. [7]
READ MORE CASES [7]
Law Enforcement and the Fight Against Dark Web Crime
Despite the anonymity and encryption, law enforcement agencies around the world have made significant progress in cracking down on dark web criminality. In 2021, a multinational law enforcement effort, Operation Dark HunTor, led to the arrest of 150 individuals across multiple countries, targeting major drug vendors and illegal marketplaces on the dark web .
Undercover operations, improved digital forensics, and advances in cryptocurrency tracing have given authorities new tools to combat the hidden crimes of the dark web. However, for every takedown, new marketplaces and forums emerge, reflecting the cat-and-mouse dynamic between law enforcement and cybercriminals. [6]
Conclusion
While the dark web itself is not inherently evil, its secrecy has allowed criminals to thrive in ways that are difficult to regulate or even detect. From drug trafficking and cybercrime to human exploitation, the hidden crimes of the dark web reveal a darker side of digital anonymity. As law enforcement and technology continue to evolve, so too will the battle to uncover and combat these underground activities. Nonetheless, the dark web serves as a potent reminder that as technology advances, so too does the need for robust security measures and ethical oversight.
.
.
.
.
sources:
https://www.varutra.com/the-hidden-internet-exploring-the-secrets-of-the-dark-web/
2.https://sopa.tulane.edu/blog/everything-you-should-know-about-dark-web
3. https://www.unsw.edu.au/research/ndarc/news-events/blogs/2016/01/dark-net-drug-marketplaces-begin-to-emulate-organised-street-cri
4. https://www.euda.europa.eu/darknet_en
5. https://www.findlaw.com/criminal/criminal-charges/dark-web-crimes.html
6. https://syntheticdrugs.unodc.org/syntheticdrugs/en/cybercrime/detectandrespond/investigation/darknet.html
7. file:///D:/New%20folder/The%2013%20Most%20Notorious%20Cases%20on%20the%20Dark%20Web.html
8. https://youtu.be/d4NSfrOtMfU?feature=shared
#crime#cyberpunk 2077#cybersecurity#internet#dark web#criminal case#laws#murder mystery#mental health
5 notes
·
View notes
Text
Buy Walmart Seller Account For Any Country
Buy Walmart Seller Account
Buy Walmart Seller Account – 100% Safe & Best Marketplace
Buy a Walmart Seller Account to start your E-Commerce business. Connect to CRM, Summary, People, Signals & News. About. Buy Walmart Seller Account.

Our service gives:-
✅ 24/7 Customer Support
✅ 100% Satisfaction & Recovery Guaranteed
✅ Email Login Access
✅ Bank Added
✅ Card Verified
✅SNN code and Router number.
✅ Phone Access
✅ Driving License Scan Copy
✅ Date of Birth Provided
✅ First Delivery
✅ Realistic Photo Attached Accounts
✅ Complete Account Access
✅ Account from unique IPs
✅Personal and Business accounts.
✅100% phone verified USA, UK, and other countries.
✅100% Full document verified.
To Talk More About Getting & Buy Any Service Contract With Us:
24 Hours Reply/Contact
Email: [email protected]
WhatsApp: +1 803-216-5479
Telegram: @smmeshops
Skype: [email protected]
The History Of Walmart Marketplace
Considering the eventuality of online businesses, Walmart launchedwalmart.com in the year 2000. The website was designed to offer a
flawless and harmonious client experience – be it store or online.
In 2007, it launched its Store Service, where it innovated the concept of multichannel shopping by allowing guests to pick their online orders in stores.
During 2009, Walmart stepped into the online world and created the so- called Walmart Marketplace. The idea was to invite different third- party merchandisers
and help them find their products atWalmart.com.
Ultimately, this conception opened a whole new avenue and brought in colorful retailers countrywide, growing their openings to a more significant position.
At the moment, it boasts more than 300- 400 retailers, including some big titans like eBags, ProTeam, and Wayfair. The products of third- party merchandisers are vended
together with the name “ Walmart Marketplace ” on the Walmart force( online). This is substantially to distinguish them from the usual particulars.
The particulars that are vended from a third party aren't traded or vended in stores.
In August 2016, WalmartInc. acquired thee-commerce businessJet.comInc. for 3 billion USD. This makes it a big deal for merchandisers because their
products can be stressed onWalmart.com elevations. Also, its massive consumer followership is another advantage.

Should Walmart Be A Part Of Your Multi-Channel Strategy?
Since Walmart is decreasingly inclining its growth every time, it's great news for all business merchandisers out there. After all, the idea is to invite implicit
shoppers and offer competitive advantages to merchandisers.
Doug McMillon, Walmart CEO, has stated that their 2- day free shipping concept has formerly given “ an amazing supplement ” in terms of deals. So, this makes
It is a great time to talk about multichannel selling. Still, this might not be as easy as it sounds.
The further channels and SKUs you manage, the more advanced are the possibilities to lose track of your force and orders. still, you could go with intelligent robotization
tools to help you with that.
What is Walmart Marketplace?
Walmart Marketplace is an online platform, like Amazon and eBay, where small businesses can list their products for trade online, alongside Walmart’s own products.
Walmart has long distinguished itself for its low prices, so this business is a good fit for merchandisers that offer great products at affordable rates.
You can use Walmart’s Sponsored Hunt advertisements to promote your products to Walmart’s callers and use their fulfillment services, if asked ,
to handle the logistics of managing force and shipping out orders.
How much is your Walmart Marketplace seller account worth?
We reached out to the investor that purchases these accounts and asked them about the process. The accounts are valued grounded on age,
deals history and number of dealer reviews. Newer accounts that have little to no deals history or dealer reviews are generally worth a many hundred bones and
aged accounts with good deals history and a considerable quantum of dealer reviews can be worth many thousand bones .
Is it safe to sell my Walmart Marketplace seller account?
According to the investor, it's 100% safe and secure to sell your account. After they confirm that your dealer account is licit and in good standing,
payment is transferred to the dealer. also they give you with new company and fiscal information for you to remove yours and replace with the new word so that
none of your sensitive information remains. Once you have completed the process, you give access to the account, icing that your sensitive information is norway
seen or remains after the transfer.
How do you get an offer to find out how much your account is worth?
We ’ve included a link below to an online form where you'll enter some information about your account. It generally takes about 5 twinkles to complete and
after you submit your word, you're transferred an offer for your account within 1 business day.However, the payment and transfer process generally takes about
1- 3 business days to complete, If you choose to accept the offer.
How to Set up a Seller Account on Walmart Marketplace
Walmart is one of the largest retailers in the world. Walmart is gaining its position as a US eCommerce point via retail, websites, and mobile apps.
As Walmart continues to make out its business capabilities, the number of approved merchandisers has been climbing at an adding pace. This business has been
historically conservative about who they allow dealing on their platform. Their delicate operation process and strict conditions have been a roadblock for
numerous-commerce merchandisers. In this moment's blog, we will show you how to set up a dealer account on Walmart.
New seller incentives

Because Walmart Marketplace is presently in a growth phase, it’s a boon for merchandisers at the moment. Walmart has offered a range of promos for brands
willing to subscribe up. While these can shift over time, one of the most recent promos Walmart offered was a 25 reduction in commission rates for the first
90 days of selling.
Economies of scale
For merchandisers who are formerly using business tools like warehousing and fulfillment coffers, integrating into the Walmart ecosystem can be fast and easy.
While costs might rise due to increased use, you ’re effectively spreading your investment across further than one occasion. This drives raised profit without a
commensurable increase in spending.
Omni-channel opportunities
By adding Walmart Marketplace to the blend of being platforms you use, you ’ll have the occasion to take an omni- channel approach by spreading your products and
services across Walmart’s online and physical stores. With different requests and deals strategies, the Walmart Marketplace gives you another followership to engage with.
Expert tips for selling on Walmart Marketplace
numerous brands have their reasons for using this platform and can establish themselves on Walmart’s business, but not all guests will be made equal.
Some merchandisers will perform better than others, so, if you want to be the stylish of the stylish and come a name shoppers come to know and trust, keep these expert
tips in mind.
Win the Buy Box
Buy Box products are the first and largest result on hunt runners; all other products are listed below. The Walmart algorithm uses a many crucial criteria
to weigh who'll win the most affordable pricing, including shipping costs, force situations, and accurate information about product quality.
Still, your products are in stock, and your rosters are accurate, If your pricing is competitive.
Have competitive pricing
As compelling as it might be to keep your prices high for maximum profit, this is n’t a stylish marketing strategy. rather, you need to keep pricing in line
with client prospects. This frequently means changing the right balance between remaining competitive while still doing as much as possible to turn a profit.
Managing this successfully may bear price testing, in which pricing is acclimated and estimated against deals. This, alongside force vacuity and contender geste ,
can help you come to a price that will win the Buy Box.

Understand your audience
Some brands assume the buyers on Walmart will be the same as those on platforms like Amazon and Target, but this is n’t inescapably the case.
The demographics can be different, particularly concerning youngish shoppers who might protect in person at Walmart, buy online at Amazon.
By understanding who's shopping on Walmart’s website for products like yours, you can tweak product descriptions, optimize keyword use,
and place flings strategically to capture the most effective guests for your brand.
Use automation
Doing everything yourself, from curating product information to client exploration to assaying the competition, is theoretically possible,
but can eat up a significant quantum of time with minimum substantiation that you ’re getting anywhere. Through the use of Walmart advertising software,
you can let robotization take over the hard corridor. Streamline workflows, access thorough yet stoner-friendly analytics,
and produce juggernauts that target all areas of the deals channel.
robotization can also help with placing flings on keywords for PPC announcement juggernauts. Platforms like ours influence your objects,
to run tests by changing flings, and establishing optimal settings. robotization on larger product registers can be a good way to get ahead without a
significant time investment.
Keyword harvesting
It’s hard to succeed in PPC advertising if you ’re not using the right keyword approach. Rather than trying to keep up with clicks, transformations,
and prints for everything you have listed for trade, automating this process can help you gather the stylish possible keywords for your products.
With the right AI- guided tools, you can manage your juggernauts while letting advertising software shoulder the burden of bidding and data analysis.
In summary
Dealing on Walmart Marketplace can feel dispiriting at first, after all, adding another eCommerce platform to the blend requires considerable time investment,
but getting started, particularly if you formerly have a presence on spots like Amazon, can be easier than you suppose.
And, if you ’re formerly using or are considering employing an eCommerce tool designed to automate and streamline pricing, keyword use, bidding, and followership analysis,
creating a robust and profitable storefront can be a great occasion to turn a profit. Contact Trellis moment to see what our moxie and AI results can do to
move your business forward.
How much does it cost to sell on Walmart Marketplace?
There are no outspoken costs involved with dealing via the Walmart business. Unlike platforms that charge class or subscription freights, getting started is free.
Rather, Walmart charges commissions on deals grounded on order, ranging from around 6 to 20. There also may be new stoner promos that can reduce the overall cost for
the first many months.
How long does it take to start selling on Walmart?
Assuming all account details are handled duly and there’s no need for fresh information, it can take between two to four weeks for Walmart’s
internal platoon to review and authorize your account. To minimize detainments, respond to any queries the Walmart platoon has as snappily as possible to insure
a prompt launch to selling.
Can individuals sell on Walmart Marketplace?
Yes, individualities can be sold on Walmart Marketplace. Still, a social security number is not permitted as a way to produce and corroborate an account. therefore,

If an individual dealer wants to begin listing products, they ’ll need to produce some kind of business that uses a drum. An LLC is a simple way for single merchandisers
to produce a company- such as structure.
Note that Walmart generally should not be the first platform druggies vend on, due to their sign up conditions of having attestation of former success in the eCommercespace.
However, Walmart is doubtful to accept your operation, If you do n’t have experience in other commerce. still, this is good news for merchandisers who get approved
as it creates a more secure space for buyers, weeds out echo brands cutting into your request share, and weeds out some of the noise druggies face on commerce. SMMeSHOPS.COM
#Buy Walmart Seller Account For Any Country#Buy Walmart Seller Account 2024#Buy Walmart Seller Account USA#Buy Walmart Seller Account UK#Buy Walmart Seller Account World#BuyWalmartSellerAccount#Buy Walmart Seller Account
2 notes
·
View notes
Text
Russia's APT28 Cyber Espionage Group Targets Czechia, Germany Using Outlook Exploit
Czechia and Germany have exposed a long-running cyber espionage campaign conducted by the notorious Russia-linked APT28 hacking group, drawing harsh criticism from international organizations like the European Union (EU), the North Atlantic Treaty Organization (NATO), the United Kingdom, and the United States. The Czech Republic's Ministry of Foreign Affairs revealed that certain entities within the country were targeted using a critical Microsoft Outlook vulnerability (CVE-2023-23397), allowing Russian state-sponsored hackers to escalate privileges and potentially gain unauthorized access. Germany Accuses APT28 of Targeting Social Democratic Party Similarly, Germany's Federal Government attributed the APT28 threat actor, also known as Fancy Bear, Pawn Storm, and Sofacy, to a cyber attack aimed at the Executive Committee of the Social Democratic Party, exploiting the same Outlook flaw over a "relatively long period" to compromise numerous email accounts. The targeted industries spanned logistics, armaments, air and space, IT services, foundations, and associations located in Germany, Ukraine, and other European regions. Germany also implicated APT28 in the 2015 cyber attack on the German federal parliament (Bundestag). Widespread Condemnation of Russia's Malicious Cyber Activities NATO stated that Russia's hybrid actions "constitute a threat to Allied security," while the Council of the European Union condemned Russia's "continuous pattern of irresponsible behavior in cyberspace." The UK government described the recent APT28 activity, including targeting the German Social Democratic Party, as "the latest in a known pattern of behavior by the Russian Intelligence Services to undermine democratic processes across the globe." The US Department of State acknowledged APT28's history of engaging in "malicious, nefarious, destabilizing and disruptive behavior," and reiterated its commitment to upholding a "rules-based international order, including in cyberspace." Disruption of APT28's Criminal Proxy Botnet Earlier in February, a coordinated law enforcement action disrupted a botnet comprising hundreds of SOHO routers in the US and Germany believed to have been used by APT28 to conceal their malicious activities, such as exploiting CVE-2023-23397 against targets of interest. Cybersecurity researchers warn that Russian state-sponsored cyber threats, including data theft, destructive attacks, DDoS campaigns, and influence operations, pose severe risks to upcoming elections in regions like the US, UK, and EU, with multiple hacking groups like APT28, APT44 (Sandworm), COLDRIVER, and KillNet expected to be active. Securing Critical Infrastructure from Pro-Russia Hacktivist Attacks Government agencies from Canada, the UK, and the US have released a joint fact sheet to help critical infrastructure organizations secure against pro-Russia hacktivist attacks targeting industrial control systems (ICS) and operational technology (OT) systems since 2022, often exploiting publicly exposed internet connections and default passwords. The recommendations include hardening human-machine interfaces, limiting internet exposure of OT systems, using strong and unique passwords, and implementing multi-factor authentication for all access to the OT network. Read the full article
2 notes
·
View notes
Text
An indictment from the US Department of Justice may have solved the mystery of how disgraced cryptocurrency exchange FTX lost over $400 million in crypto. The indictment, filed last week, alleges that three individuals used a SIM-swapping attack to steal hundreds of millions in virtual currency from an unnamed company. The timing and the amount stolen coincides with FTX's theft. Meanwhile, in a letter obtained by WIRED this week, seven lawmakers have demanded the DOJ stop funding biased and inaccurate predictive policing tools until the agency has a way to ensure law enforcement won’t use them in a way that has a “discriminatory impact.”
In Florida, prosecutors say a 17-year-old named Alan Winston Filion is responsible for hundreds of swatting attacks around the United States. The news of his arrest was first reported by WIRED days before law enforcement made it public. It was the culmination of a multi-agency manhunt to piece together a trail of digital breadcrumbs left by the teenager. In Ukraine, unmanned aerial vehicles have been powerful tools since the Russian invasion began in February 2022. But as the war rages on, another kind of unmanned robot has increasingly appeared on the front-lines: the unmanned ground vehicle, or UGV.
For months lawyers affiliated with an India based hacker-for-hire firm called Appin Technology have used legal threats to censor reporting about the company’s alleged cyber mercenary past. The EFF, Techdirt, MuckRock, and DDoSecrets are now pushing back, publicly sharing details for the first time about the firm's efforts to remove content from the web. It’s a dangerous world out there, so we’ve also got a list of some major patches issued in January that you can use to update your devices to keep them secure.
And there’s more. Each week, we highlight the news we didn’t cover in-depth ourselves. Click on the headlines below to read the full stories. And stay safe out there.
China’s Hackers Keep Targeting US Water and Electricity Supplies
For years Western security officials have warned about the threat of China collecting data about millions of people and the country’s hackers infiltrating sensitive systems. This week, Federal Bureau of Investigation director Christopher Wray said hackers affiliated with the Chinese Communist Party are constantly targeting US critical infrastructure, such as water treatment plants, the electrical grid, and oil and gas pipelines. Wray’s testimony, at a House subcommittee on China, came as the FBI also revealed it removed malware from hundreds of routers in people’s homes and offices that had been planted by the Chinese hacking group Volt Typhoon.
“China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities,” Wray said in the public appearance. “Low blows against civilians are part of China’s plan.” The FBI director added that China has a bigger hacking operation than “every other major nation combined,” and claimed that if all of the FBI’s cyber-focused agents were assigned to work on issues related to China, they would still be outnumbered “by at least 50 to 1.”
While concerns about the scale of China’s espionage and cyber operations aren’t new, the US intelligence community has been increasingly vocal and worried about critical infrastructure being targeted by Volt Typhoon and other groups. “The threat is extremely sophisticated and pervasive,” NSA officials warned in November. In May 2023, Microsoft revealed it had been tracking Volt Typhoon intrusions at communications and transportation infrastructure, among other critical infrastructure, in US states and Guam.
The FBI and DOJ, also revealed this week that they remotely removed the KV Botnet malware from hundreds of routers infected by Volt Typhoon. The impacted routers, from Cisco and Netgear, were mostly at the end of their life, but were being used as part of wider operations. “The Volt Typhoon malware enabled China to hide, among other things, pre-operational reconnaissance and network exploitation against critical infrastructure like our communications, energy, transportation, and water sectors,” Wray said. It isn’t the first time US officials have obtained a court order to remotely wipe devices infected by hackers, but the move is still rare.
‘Untraceable’ Monero Transactions Have Been Traced, Police Claim
Since the first cryptocurrencies emerged more than a decade ago, there has been the assumption that the blockchain-based digital currencies are anonymous and untraceable. They are, in fact, very traceable. Researchers have shown how people can be linked to the transactions they make and law enforcement have used the techniques to help bust illicit dark web markets and catch pedophiles. There are, however, still some privacy-focused cryptocurrencies that appear to be less traceable than Bitcoin. This includes Monero, which is increasingly being adopted by sellers of child sexual abuse materials.
This week investigators in Finland said Moreno-tracing helped reveal the identity of a hacker who allegedly attacked psychotherapy company Vastaamo in 2020, stealing thousands of patient records and threatening to leak them unless people paid a ransom. Investigators from the Finnish National Bureau of Investigation claim they used heuristic analysis to infer where funds were moved to. The investigators did not reveal the full methods of how they allegedly traced the Monero payments, however, they add to the growing body of evidence that cryptocurrency tracing firms and investigators may be able to track the currency.
Russia Likely Behind a Spike in GPS Interference, Officials Say
Planes flying over Europe have faced a spike in accuracy issues with GPS systems used for navigation in recent months. The head of Estonia’s Defense Forces has claimed that Russia is likely the source of this interference, according to an interview with Bloomberg. “Someone is causing it, and we think it’s Russia,” Martin Herem told the publication, adding that Russia may be testing its electronic warfare capabilities and “learning” the most effective tactics. Across Europe, and particularly the Baltics region, there has been a reported increase in GPS jamming, with Finland reporting large interferences in December and pilots repeatedly reporting issues with their navigation systems.
Vault 7 Hacking Tools Leaker Joshua Schulte Sentenced to 40 Years
In 2017, the Vault 7 leaks exposed some of the CIA’s most sophisticated hacking tools, including how the agency could compromise routers, phones, PC, and TVs. Joshua Schulte, a former CIA engineer in the agency’s Operations Support Branch who prosecutors identified as being behind the data breach and responsible for leaking the materials to Wikileaks, was convicted in numerous trials in recent years. Schulte, who denied the allegations, has been sentenced to 40 years in prison for the espionage and also for possessing thousands of child abuse images. Judge Jesse Furman, sentencing Schulte, said he had caused “untold damage to national security.” In June 2022, The New Yorker published this comprehensive investigation into the data breach and Schulte’s troubled history working at the agency.
2 notes
·
View notes
Text
A Simple Guide to Understanding Network Cabinet
A network cabinet plays an essential role in the data center. It is used for organizing routers, patch panels, switches, networking equipment, and accessories. Network cabinet helps improve cable management, physical security, ease of installation, etc. This article provides a simple guide to understanding network cabinets.

What is Network Cabinet?
A network cabinet is a piece of equipment used to combine installation panels, plug-ins, sub-boxes, electronic components, devices, and mechanical parts and components to form an integral installation box. It provides the perfect environment for housing and protecting network infrastructure components. It is particularly suited to the back office and commercial building infrastructure applications.

Types of Network Cabinet
Wall- Mounted Network Cabinet
A wall-mounted network cabinet is used for all rack-mounted equipment conforming to ANSI/EIA standards. It has a solid and reliable modular steel alloy frame structure for a maximum static load capacity of up to 60 KG, movable aluminum magnesium alloy equipment mounting pillars that can fit different depth equipment, multi-place with cabling passageways for various cabling requirements, and high adaptability(optional wall-mounted or ground-mounted fixing to ease meeting the installation).

Widened Steel Alloy Network Cabinet
Widened steel alloy network cabinet is used for all rack-mounted equipment conforming to ANSI/ EIA standards. It has a solid modular alloy steel frame, a maximum static load capacity of up to 800 KG, widened cabinet structure design, is equipped with vertical cable ducts to orderly lay a large volume of cables, and movable aluminum magnesium alloy equipment mounting pillars for different depth equipment.

Outdoor Network Cabinet
An outdoor network cabinet is used for connections between cabling elements. It has heat insulation, water-proof and dust-proof performance, good corrosion resistance, and 19-inch equipment mounted.

Applications
A network cabinet is used in the copper network, FTTH access networks, telecommunication networks, CATV networks, local area networks, data centers, etc.

Things to Look Out for When Choosing a Network Cabinet
Access: Different equipment has different access points. Therefore, your network cabinet should provide several access points for the various devices. Make sure you understand the equipment you need to store in your rank and their usage in and out. You can only determine that you require a cabinet rank that can open on the side, back, or front.
Weight: The network cabinet should not be too bulky that you cannot lift it when setting it up or in case you need to move it. However, it should be the perfect weight to hold all your equipment without collapsing due to the weight of the equipment.
Dimensions: It is wise to choose a rack with physical characteristics that are appropriate for you. Consider the room's square footage and the size of the equipment that will be housed inside the cabinet.
Available space: When setting it up or relocating it, the network cabinet shouldn't be so heavy that you can't lift it. It should, however, be the ideal weight to support all of your equipment without collapsing under its weight of it.
Conclusion
When you are designing a data center, deciding which network cabinet to deploy should be put in the first place. The right one that meets your installation demand can help you improve power protection, cooling, cable management, and physical security.
Sun Telecom specializes in providing one-stop total fiber optic solutions for all fiber optic application industries worldwide. We are devoted to not only meeting the need of customers but; also providing our customers with basic and in-depth knowledge about fiber optic products and solutions through articles. Contact us if you have any needs.
#fttx#cabling#telecomengineering#fiberoptic#suntelecom#telecommunications#osp#fiberopticcable#catv#telecomconsult
2 notes
·
View notes