#pc security software
Explore tagged Tumblr posts
Text
Shield Your Digital World: The Ultimate Guide to VPN Security with NordVPN
#vpn#best vpn#vpn service#free vpn#clone vpn#cyberattack#antivirus#cyber security#sql#software#vps hosting#vps server in saudi arabia#buy windows vps#vps#vps34 in1#dedicated server#pcs#printer#material#security
2 notes
·
View notes
Text
Why would I do that when I'm talking about my experience at work and what I deal with on a daily basis rather than personal life?
Open source is great but it's not going to happen to Adobe any time soon. You're just trying to pull on any thread to appear in the right on this. Sometimes you just need to accept you don't know what you're talking about and take the L
The humble and beautiful PDF does not deserve to now have the term “PDF file” be a censored version of the word pedophile. She has been nothing but good to us. You all apologize right now
#Also you'd better be donating towards people who maintain repos if you're able#The only reason why adobe doesn't use the massive amount of money it has to fuck over more people is because it works for them to have#People get used to their proprietary products because it means that they can force big business to pay their extortionate prices#The fact that it costs my work like £700 for me to get annoyed at pdfs is only relevant to my workplace and not to whether or not an#Individual uses the guides on reddit to pirate it at home or not#My work is still going to have to pay for that because they're a big company who need things to be very secure and if you get a cracker#In the vpn it's not going to be good for the projects in the same system even it it's not a trojan#What you're gonna have to do is buy the legit license or use a different software and if you have big enough profits it's worth buying#Whatever software is the most supported and causes the least friction on multiple types of workflow#Cracked stuff is for individuals on their home pcs or businesses who exist in the zone of time not costing more than money#Or who don't have to stick to certain iso security standards
46K notes
·
View notes
Text
PrivaZer Download - Clean Junk Files & Protect Privacy
PrivaZer is a free tool with an optional premium version that acts as a privacy protector, registry cleaner, and junk file remover for your PC. It helps users safeguard sensitive data by eliminating unwanted traces left behind during regular computer use. PrivaZer goes beyond typical cleaning; it can securely erase data, making it nearly impossible to recover. This feature is especially…
#data protection#data security#deep cleaning#disk cleanup#file eraser#junk file cleaner#PC privacy#portable software#privacy protection#privacy tool#PrivaZer#registry cleaner#secure deletion#system optimization#Windows cleaning tool
0 notes
Text
https://www.futureelectronics.com/p/production-products--hardware--test-points/5015-keystone-8064685
PC hardware monitor, Security testing, PCB Test Point, Hardware test plan
Miniature Surface Mount Test Points on Tape and Reel
#Keystone#5015#Production Products#Hardware Test Points#pc hardware monitor#Security testing#PCB#plan#acceptance testing#Hardware testing process#open hardware monitor#software#development process#Hardware testing tools
1 note
·
View note
Text
Da oltre 10 anni, TechNet studio opera nella formazione IT di base e specialistica in FAD (formazione a distanza) con le migliori piattaforme di apprendimento digitale.
La mia missione è quella di stimolare la crescita individuale degli studenti e infondere in loro il coraggio per abbracciare il mondo del lavoro.
Non erogo solo corsi di formazione individuale e di gruppo, ma faccio in modo che le persone, dopo aver acquisito il proprio bagaglio di conoscenze e competenze, sono pronte per sperimentare esperienze lavorative.
TechNet Studio opera con 2 modalità formative: videolezioni e corsi di formazione
Ciò che contraddistingue la mia professionalità e favorisce il migliore approccio nell'insegnamento è un test di ingresso all'aspirante corsista, con il fine di scegliere il corso più adatto alle sue esigenze .
Dopo aver scelto il corso di interesse, il corsista deve accedere alla area di registrazione compilando il modulo con i dati richiesti.
Per ricevere ulteriori informazioni sul costo relativo al corso di interesse, si prega di contattare il team formazione: [email protected]

#corsidialtaformazioneIT#corsiinformatica#formazioneadistanza#studio#pc#cybersecurity#hacking#security#software#microsoft#outage#icdl
1 note
·
View note
Video
Best Free Antivirus Software For PC/Laptop in 2024 (Windows 10 & 11) | No Crack | Original & Genuine License
#youtube#antivirus#free#freeantivirus#best#bestantivirus#software#pc#laptop#2024#windows#windows 10#windows 11#microsoft windows#crack#original#genuine#lisence#license#security#protection
0 notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
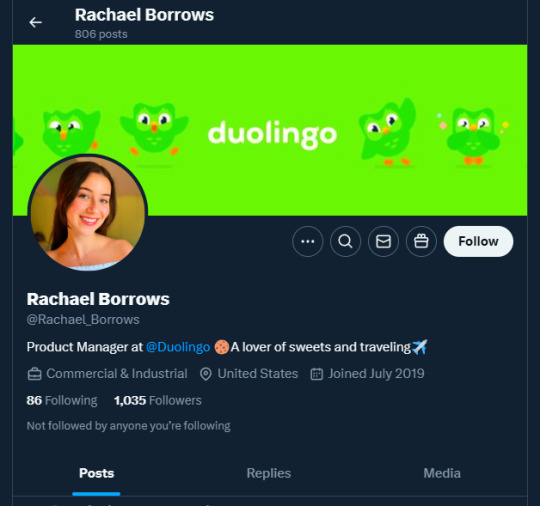
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
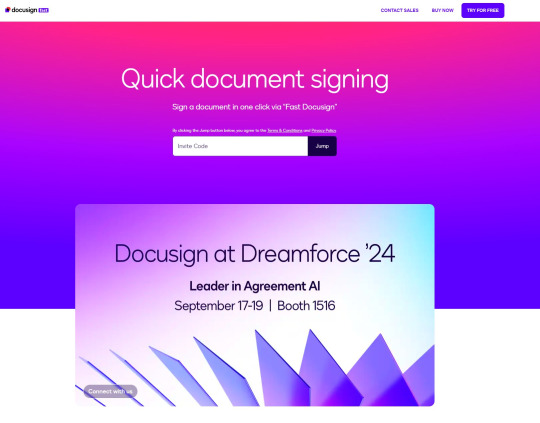
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
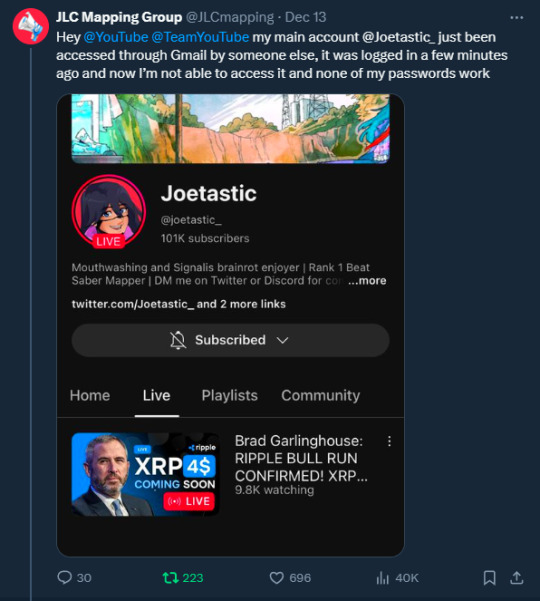
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
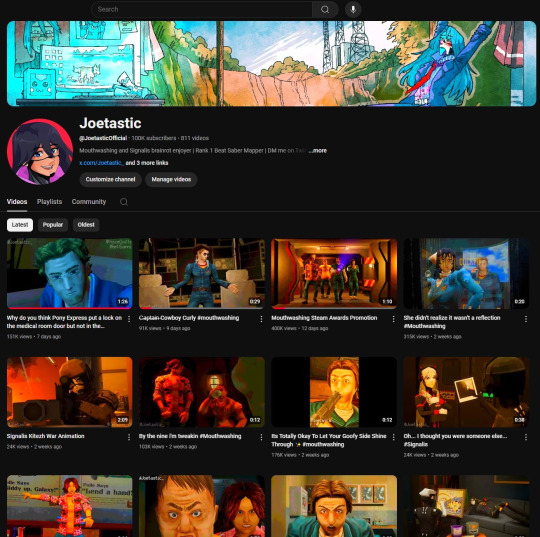
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
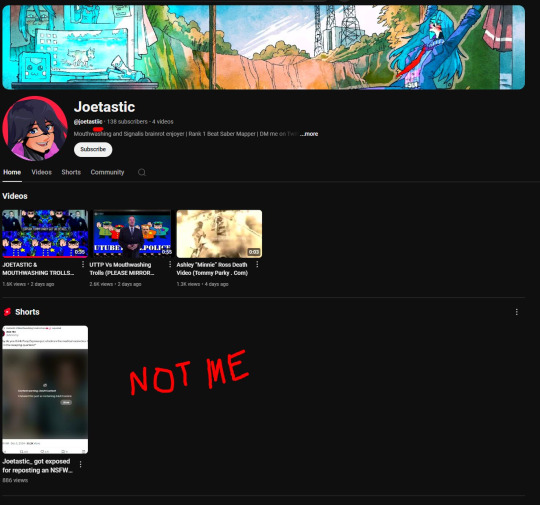
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
Installing Linux (Mint) as a Non-Techy Person
I've wanted Linux for various reasons since college. I tried it once when I no longer had to worry about having specific programs for school, but it did not go well. It was a dedicated PC that was, I believe, poorly made. Anyway.
In the process of deGoogling and deWindows365'ing, I started to think about Linux again. Here is my experience.
Pre-Work: Take Stock
List out the programs you use regularly and those you need. Look up whether or not they work on Linux. For those that don't, look up alternatives.
If the alternative works on Windows/Mac, try it out first.
Make sure you have your files backed up somewhere.
Also, pick up a 5GB minimum USB drive.
Oh and make a system restore point (look it up in your Start menu) and back-up your files.
Step One: Choose a Distro
Dear god do Linux people like to talk about distros. Basically, from what all I've read, if you don't want to fuss a lot with your OS, you've got two options: Ubuntu and Linux Mint. Ubuntu is better known and run by a company called Canonical. Linux Mint is run by a small team and paid for via donations.
I chose Linux Mint. Some of the stuff I read about Ubuntu reminded me too much of my reasons for wanting to leave Windows, basically. Did I second-guess this a half-dozen times? Yes, yes I did.
The rest of this is true for Linux Mint Cinnamon only.
Step Two: Make your Flash Drive
Linux Mint has great instructions. For the most part they work.
Start here:
The trickiest part of creating the flash drive is verifying and authenticating it.
On the same page that you download the Linux .iso file there are two links. Right click+save as both of those files to your computer. I saved them and the .iso file all to my Downloads folder.
Then, once you get to the 'Verify your ISO image' page in their guide and you're on Windows like me, skip down to this link about verifying on Windows.
Once it is verified, you can go back to the Linux Mint guide. They'll direct you to download Etchr and use that to create your flash drive.
If this step is too tricky, then please reconsider Linux. Subsequent steps are both easier and trickier.
Step Three: Restart from your Flash Drive
This is the step where I nearly gave up. The guide is still great, except it doesn't mention certain security features that make installing Linux Mint impossible without extra steps.
(1) Look up your Bitlocker recovery key and have it handy.
I don't know if you'll need it like I did (I did not turn off Bitlocker at first), but better to be safe.
(2) Turn off Bitlocker.
(3) Restart. When on the title screen, press your Bios key. There might be more than one. On a Lenovo, pressing F1 several times gets you to the relevant menu. This is not the menu you'll need to install, though. Turn off "Secure Boot."
(4) Restart. This time press F12 (on a Lenovo). The HDD option, iirc, is your USB. Look it up on your phone to be sure.
Now you can return to the Linux Mint instructions.
Figuring this out via trial-and-error was not fun.
Step Four: Install Mint
Just follow the prompts. I chose to do the dual boot.
You will have to click through some scary messages about irrevocable changes. This is your last chance to change your mind.
I chose the dual boot because I may not have anticipated everything I'll need from Windows. My goal is to work primarily in Linux. Then, in a few months, if it is working, I'll look up the steps for making my machine Linux only.
Some Notes on Linux Mint
Some of the minor things I looked up ahead of time and other miscellany:
(1) HP Printers supposedly play nice with Linux. I have not tested this yet.
(2) Linux Mint can easily access your Windows files. I've read that this does not go both ways. I've not tested it yet.
(3) You can move the taskbar (panel in LM) to the left side of your screen.
(4) You are going to have to download your key programs again.
(5) The LM software manager has most programs, but not all. Some you'll have to download from websites. Follow instructions. If a file leads to a scary wall of strange text, close it and just do the Terminal instructions instead.
(6) The software manager also has fonts. I was able to get Fanwood (my favorite serif) and JetBrains (my favorite mono) easily.
In the end, be prepared for something to go wrong. Just trust that you are not the first person to ever experience the issue and look it up. If that doesn't help, you can always ask. The forums and reddit community both look active.
178 notes
·
View notes
Text
Have YOU got an old Windows PC Microsoft has told you can't run Windows 11? It's time to give it a new life!
How to install Windows 11 on unsupported PC Hardware using Rufus. You can also disable some other Windows 11 bullshit like data harvesting and needing a Microsoft account.
It has been in the news a lot lately that Windows 11 isn't allowed to be installed on PCs without certain requirements, including the TPM 2.0, a chip that was only included in PCs made in 2018 or later. This means that once Windows 10 stops receiving security updates, those PCs will not be able to (officially) run a safe, updated version of Windows anymore. This has led to an estimated 240 million PCs bound for the landfill. Thanks Microsoft! I get you don't want to be seen as the insecure one, but creating this much waste can't be the solution.
(I know nerds, Linux is a thing. I love you but we are not having that conversation. If you want to use Linux on an old PC you are already doing it and you don't need to tell me about it. People need Windows for all sorts of reasons that Linux won't cut.)
So lately I have been helping some under privileged teens get set up with PCs. Their school was giving away their old lab computers, and these kids would usually have no chance to afford even a basic computer. They had their hard drives pulled so I have been setting them up with SSDs, but the question was, what to do about the operating system? So I looked into it and I found out there IS actually a way to bypass Microsoft's system requirement and put Windows 11 on PCs as old as 2010.
You will need: Rufus: An open source ISO burning tool.
A Windows 11 ISO: Available from Microsoft.
A USB Flash Drive, at least 16GB.
A working PC to make the ISO, and a PC from 2018 or older you want to install Windows 11 on.
Here is the guide I used, but I will put it in my own words as well.
Download your Windows 11 ISO, and plug in your USB drive. It will be erased, so don't have anything valuable on it. Run Rufus, select your USB drive in the Device window, and select your Windows 11 ISO with the Select button. (There is supposed to be a feature in Rufus to download your ISO but I couldn't get it to work.?
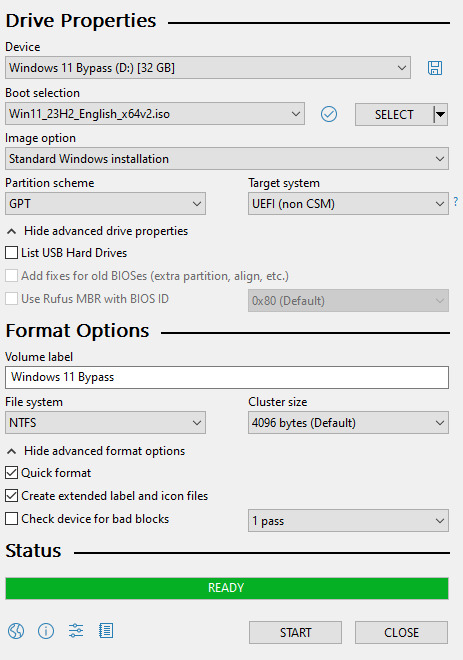
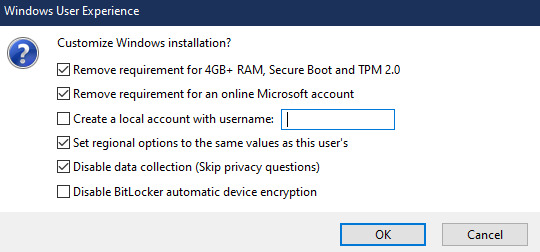
Choose standard windows installation, and follow the screenshot for your settings. Once you are done that, press Start, and then the magic happens. Another window pops up allowing you to remove the system requirements, the need for a microsoft account, and turn off data collecting. Just click the options you want, and press ok to write your iso to a drive.
From there you just need to use the USB drive to install windows. I won't go into details here, but here are some resources if you don't know how to do it.
Boot your PC from a USB Drive
Install Windows 11 from USB Drive
If you had a licensed copy of Windows 10, Windows 11 will already be licensed. If you don't, then perhaps you can use some kind of... Activation Scripts for Microsoft software, that will allow you to activate them. Of course I cannot link such tools here. So there you go, now you can save a PC made from before 2018 from the landfill, and maybe give it to a deserving teen in the process. The more we can extend the lives of technology and keep it out of the trash, the better.
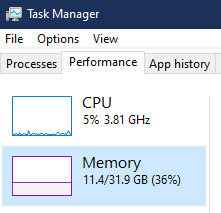
Additional note: This removes the requirement for having 4GB Minimum of RAM, but I think that requirement should honestly be higher. Windows 11 will be unusable slow on any system with below 8GB of RAM. 8GB is the minimum I think you should have before trying this but it still really not enough for modern use outside of light web and office work. I wouldn't recommend trying this on anything with 4GB or less. I am honestly shocked they are still selling brand new Windows 11 PCs with 4GB of ram. If you're not sure how much RAM you have, you can find out in the performance tab of Task Manager in Windows, if you click the More Details icon on the bottom right. If you don't have enough, RAM for old systems is super cheap and widely available so it would definitely be worth upgrading if you have a ram starved machine you'd like to give a new life.
#Windows#Windows 11#tech#tech advice#pc#TPM 2.0#rufus#open source#open source software#technology#tech tips
725 notes
·
View notes
Text
Microsoft pinky swears that THIS TIME they’ll make security a priority

One June 20, I'm live onstage in LOS ANGELES for a recording of the GO FACT YOURSELF podcast. On June 21, I'm doing an ONLINE READING for the LOCUS AWARDS at 16hPT. On June 22, I'll be in OAKLAND, CA for a panel and a keynote at the LOCUS AWARDS.

As the old saying goes, "When someone tells you who they are and you get fooled again, shame on you." That goes double for Microsoft, especially when it comes to security promises.
Microsoft is, was, always has been, and always will be a rotten company. At every turn, throughout their history, they have learned the wrong lessons, over and over again.
That starts from the very earliest days, when the company was still called "Micro-Soft." Young Bill Gates was given a sweetheart deal to supply the operating system for IBM's PC, thanks to his mother's connection. The nepo-baby enlisted his pal, Paul Allen (whom he'd later rip off for billions) and together, they bought someone else's OS (and took credit for creating it – AKA, the "Musk gambit").
Microsoft then proceeded to make a fortune by monopolizing the OS market through illegal, collusive arrangements with the PC clone industry – an industry that only existed because they could source third-party PC ROMs from Phoenix:
https://www.eff.org/deeplinks/2019/08/ibm-pc-compatible-how-adversarial-interoperability-saved-pcs-monopolization
Bill Gates didn't become one of the richest people on earth simply by emerging from a lucky orifice; he also owed his success to vigorous antitrust enforcement. The IBM PC was the company's first major initiative after it was targeted by the DOJ for a 12-year antitrust enforcement action. IBM tapped its vast monopoly profits to fight the DOJ, spending more on outside counsel to fight the DOJ antitrust division than the DOJ spent on all its antitrust lawyers, every year, for 12 years.
IBM's delaying tactic paid off. When Reagan took the White House, he let IBM off the hook. But the company was still seriously scarred by its ordeal, and when the PC project kicked off, the company kept the OS separate from the hardware (one of the DOJ's major issues with IBM's previous behavior was its vertical monopoly on hardware and software). IBM didn't hire Gates and Allen to provide it with DOS because it was incapable of writing a PC operating system: they did it to keep the DOJ from kicking down their door again.
The post-antitrust, gunshy IBM kept delivering dividends for Microsoft. When IBM turned a blind eye to the cloned PC-ROM and allowed companies like Compaq, Dell and Gateway to compete directly with Big Blue, this produced a whole cohort of customers for Microsoft – customers Microsoft could play off on each other, ensuring that every PC sold generated income for Microsoft, creating a wide moat around the OS business that kept other OS vendors out of the market. Why invest in making an OS when every hardware company already had an exclusive arrangement with Microsoft?
The IBM PC story teaches us two things: stronger antitrust enforcement spurs innovation and opens markets for scrappy startups to grow to big, important firms; as do weaker IP protections.
Microsoft learned the opposite: monopolies are wildly profitable; expansive IP protects monopolies; you can violate antitrust laws so long as you have enough monopoly profits rolling in to outspend the government until a Republican bootlicker takes the White House (Microsoft's antitrust ordeal ended after GW Bush stole the 2000 election and dropped the charges against them). Microsoft embodies the idea that you either die a rebel hero or live long enough to become the evil emperor you dethroned.
From the first, Microsoft has pursued three goals:
Get too big to fail;
Get too big to jail;
Get too big to care.
It has succeeded on all three counts. Much of Microsoft's enduring power comes from succeeded IBM as the company that mediocre IT managers can safely buy from without being blamed for the poor quality of Microsoft's products: "Nobody ever got fired for buying Microsoft" is 2024's answer to "Nobody ever got fired for buying IBM."
Microsoft's secret sauce is impunity. The PC companies that bundle Windows with their hardware are held blameless for the glaring defects in Windows. The IT managers who buy company-wide Windows licenses are likewise insulated from the rage of the workers who have to use Windows and other Microsoft products.
Microsoft doesn't have to care if you hate it because, for the most part, it's not selling to you. It's selling to a few decision-makers who can be wined and dined and flattered. And since we all have to use its products, developers have to target its platform if they want to sell us their software.
This rarified position has afforded Microsoft enormous freedom to roll out harebrained "features" that made things briefly attractive for some group of developers it was hoping to tempt into its sticky-trap. Remember when it put a Turing-complete scripting environment into Microsoft Office and unleashed a plague of macro viruses that wiped out years worth of work for entire businesses?
https://web.archive.org/web/20060325224147/http://www3.ca.com/securityadvisor/newsinfo/collateral.aspx?cid=33338
It wasn't just Office; Microsoft's operating systems have harbored festering swamps of godawful defects that were weaponized by trolls, script kiddies, and nation-states:
https://en.wikipedia.org/wiki/EternalBlue
Microsoft blamed everyone except themselves for these defects, claiming that their poor code quality was no worse than others, insisting that the bulging arsenal of Windows-specific malware was the result of being the juiciest target and thus the subject of the most malicious attention.
Even if you take them at their word here, that's still no excuse. Microsoft didn't slip and accidentally become an operating system monopolist. They relentlessly, deliberately, illegally pursued the goal of extinguishing every OS except their own. It's completely foreseeable that this dominance would make their products the subject of continuous attacks.
There's an implicit bargain that every monopolist makes: allow me to dominate my market and I will be a benevolent dictator who spends his windfall profits on maintaining product quality and security. Indeed, if we permit "wasteful competition" to erode the margins of operating system vendors, who will have a surplus sufficient to meet the security investment demands of the digital world?
But monopolists always violate this bargain. When faced with the decision to either invest in quality and security, or hand billions of dollars to their shareholders, they'll always take the latter. Why wouldn't they? Once they have a monopoly, they don't have to worry about losing customers to a competitor, so why invest in customer satisfaction? That's how Google can piss away $80b on a stock buyback and fire 12,000 technical employees at the same time as its flagship search product (with a 90% market-share) is turning into an unusable pile of shit:
https://pluralistic.net/2024/02/21/im-feeling-unlucky/#not-up-to-the-task
Microsoft reneged on this bargain from day one, and they never stopped. When the company moved Office to the cloud, it added an "analytics" suite that lets bosses spy on and stack-rank their employees ("Sorry, fella, Office365 says you're the slowest typist in the company, so you're fired"). Microsoft will also sell you internal data on the Office365 usage of your industry competitors (they'll sell your data to your competitors, too, natch). But most of all, Microsoft harvest, analyzes and sells this data for its own purposes:
https://pluralistic.net/2020/11/25/the-peoples-amazon/#clippys-revenge
Leave aside how creepy, gross and exploitative this is – it's also incredibly reckless. Microsoft is creating a two-way conduit into the majority of the world's businesses that insider threats, security services and hackers can exploit to spy on and wreck Microsoft's customers' business. You don't get more "too big to care" than this.
Or at least, not until now. Microsoft recently announced a product called "Recall" that would record every keystroke, click and screen element, nominally in the name of helping you figure out what you've done and either do it again, or go back and fix it. The problem here is that anyone who gains access to your system – your boss, a spy, a cop, a Microsoft insider, a stalker, an abusive partner or a hacker – now has access to everything, on a platter. Naturally, this system – which Microsoft billed as ultra-secure – was wildly insecure and after a series of blockbuster exploits, the company was forced to hit pause on the rollout:
https://arstechnica.com/gadgets/2024/06/microsoft-delays-data-scraping-recall-feature-again-commits-to-public-beta-test/
For years, Microsoft waged a war on the single most important security practice in software development: transparency. This is the company that branded the GPL Free Software license a "virus" and called open source "a cancer." The company argued that allowing public scrutiny of code would be a disaster because bad guys would spot and weaponize defects.
This is "security through obscurity" and it's an idea that was discredited nearly 500 years ago with the advent of the scientific method. The crux of that method: we are so good at bullshiting ourselves into thinking that our experiment was successful that the only way to make sure we know anything is to tell our enemies what we think we've proved so they can try to tear us down.
Or, as Bruce Schneier puts it: "Anyone can design a security system that you yourself can't think of a way of breaking. That doesn't mean it works, it just means that it works against people stupider than you."
And yet, Microsoft – whose made more widely and consequentially exploited software than anyone else in the history of the human race – claimed that free and open code was insecure, and spent millions on deceptive PR campaigns intended to discredit the scientific method in favor of a kind of software alchemy, in which every coder toils in secret, assuring themselves that drinking mercury is the secret to eternal life.
Access to source code isn't sufficient to make software secure – nothing about access to code guarantees that anyone will review that code and repair its defects. Indeed, there've been some high profile examples of "supply chain attacks" in the free/open source software world:
https://www.securityweek.com/supply-chain-attack-major-linux-distributions-impacted-by-xz-utils-backdoor/
But there's no good argument that this code would have been more secure if it had been harder for the good guys to spot its bugs. When it comes to secure code, transparency is an essential, but it's not a sufficency.
The architects of that campaign are genuinely awful people, and yet they're revered as heroes by Microsoft's current leadership. There's Steve "Linux Is Cancer" Ballmer, star of Propublica's IRS Files, where he is shown to be the king of "tax loss harvesting":
https://pluralistic.net/2023/04/24/tax-loss-harvesting/#mego
And also the most prominent example of the disgusting tax cheats practiced by rich sports-team owners:
https://pluralistic.net/2021/07/08/tuyul-apps/#economic-substance-doctrine
Microsoft may give lip service to open source these days (mostly through buying, stripmining and enclosing Github) but Ballmer's legacy lives on within the company, through its wildly illegal tax-evasion tactics:
https://pluralistic.net/2023/10/13/pour-encoragez-les-autres/#micros-tilde-one
But Ballmer is an angel compared to his boss, Bill Gates, last seen some paragraphs above, stealing the credit for MS DOS from Tim Paterson and billions of dollars from his co-founder Paul Allen. Gates is an odious creep who made billions through corrupt tech industry practices, then used them to wield influence over the world's politics and policy. The Gates Foundation (and Gates personally) invented vaccine apartheid, helped kill access to AIDS vaccines in Sub-Saharan Africa, then repeated the trick to keep covid vaccines out of reach of the Global South:
https://pluralistic.net/2021/04/13/public-interest-pharma/#gates-foundation
The Gates Foundation wants us to think of it as malaria-fighting heroes, but they're also the leaders of the war against public education, and have been key to the replacement of public schools with charter schools, where the poorest kids in America serve as experimental subjects for the failed pet theories of billionaire dilettantes:
https://www.ineteconomics.org/perspectives/blog/millionaire-driven-education-reform-has-failed-heres-what-works
(On a personal level, Gates is also a serial sexual abuser who harassed multiple subordinates into having sexual affairs with him:)
https://www.nytimes.com/2022/01/13/technology/microsoft-sexual-harassment-policy-review.html
The management culture of Microsoft started rotten and never improved. It's a company with corruption and monopoly in its blood, a firm that would always rather build market power to insulate itself from the consequences of making defective products than actually make good products. This is true of every division, from cloud computing:
https://pluralistic.net/2022/09/28/other-peoples-computers/#clouded-over
To gaming:
https://pluralistic.net/2023/04/27/convicted-monopolist/#microsquish
No one should ever trust Microsoft to do anything that benefits anyone except Microsoft. One of the low points in the otherwise wonderful surge of tech worker labor organizing was when the Communications Workers of America endorsed Microsoft's acquisition of Activision because Microsoft promised not to union-bust Activision employees. They lied:
https://80.lv/articles/qa-workers-contracted-by-microsoft-say-they-were-fired-for-trying-to-unionize/
Repeatedly:
https://www.reuters.com/technology/activision-fired-staff-using-strong-language-about-remote-work-policy-union-2023-03-01/
Why wouldn't they lie? They've never faced any consequences for lying in the past. Remember: the secret to Microsoft's billions is impunity.
Which brings me to Solarwinds. Solarwinds is an enterprise management tool that allows IT managers to see, patch and control the computers they oversee. Foreign spies hacked Solarwinds and accessed a variety of US federal agencies, including National Nuclear Security Administration (who oversee nuclear weapons stockpiles), the NIH, and the Treasury Department.
When the Solarwinds story broke, Microsoft strenuously denied that the Solarwinds hack relied on exploiting defects in Microsoft software. They said this to everyone: the press, the Pentagon, and Congress.
This was a lie. As Renee Dudley and Doris Burke reported for Propublica, the Solarwinds attack relied on defects in the SAML authentication system that Microsoft's own senior security staff had identified and repeatedly warned management about. Microsoft's leadership ignored these warnings, buried the research, prohibited anyone from warning Microsoft customers, and sidelined Andrew Harris, the researcher who discovered the defect:
https://www.propublica.org/article/microsoft-solarwinds-golden-saml-data-breach-russian-hackers
The single most consequential cyberattack on the US government was only possible because Microsoft decided not to fix a profound and dangerous bug in its code, and declined to warn anyone who relied on this defective software.
Yesterday, Microsoft president Brad Smith testified about this to Congress, and promised that the company would henceforth prioritize security over gimmicks like AI:
https://arstechnica.com/tech-policy/2024/06/microsoft-in-damage-control-mode-says-it-will-prioritize-security-over-ai/
Despite all the reasons to mistrust this promise, the company is hoping Congress will believe it. More importantly, it's hoping that the Pentagon will believe it, because the Pentagon is about to award billions in free no-bid military contract profits to Microsoft:
https://www.axios.com/2024/05/17/pentagon-weighs-microsoft-licensing-upgrades
You know what? I bet they'll sell this lie. It won't be the first time they've convinced Serious People in charge of billions of dollars and/or lives to ignore that all-important maxim, "When someone tells you who they are and you get fooled again, shame on you."

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/14/patch-tuesday/#fool-me-twice-we-dont-get-fooled-again
#pluralistic#microsoft#infosec#visual basic#ai#corruption#too big to care#patch tuesday#solar winds#monopolists bargain#eternal blue#transparency#open source#floss#oss#apts
278 notes
·
View notes
Note
stone faced anon (💫 anon if it's free) here; as someone who has a hyperfixation in IT and coding I also think it would be very funny if Boothill had an s/o who wasn't necessarily a mechanic but like a software engineer or just a real big nerd about coding or something. He'll be experiencing a malfunction or a memory leak and go "oh yeah this happens sometimes don't worry about it" and then 10 minutes later he's sitting down plugged into a laptop listening to his s/o rant about how terrible his code is (crack hc: boothill's code was written in javascript) and how it's a wonder he hasn't bricked* yet
Would also be mad funny if Boothill ever got hacked and his s/o basically says "no you're not" and uses a previously made system restore point or something because of course they would both use and design every feature imaginable to keep Boothill in control of his own body, can you imagine the stress that losing control would cause him?? Even better if whoever designed him originally intentionally left a backdoor incase he ever went against their orders and when they try to use it his s/o just goes "oh yeah I quarantined and encrypted all the old files related to that backdoor and whatever else you were planning on a partition as bait and personally rewrote every file and function involved since your code is *an actual crime against technology*. by the way i'm going to go ahead and format that partition i mentioned, boothill- we won't be needing anything on it now that we can trace whoever made it. trust me, this won't be happening ever again."
*(bricking is a term mostly used to refer to hardware that's been rendered basically completely nonfunctional and beyond saving by using it wrong, mostly by messing with system files. Kinda like how windows can't even repair itself if you delete the system32 folder. Though i guess you could still install it with a usb stick if you formatted your pc- i digress you get what I mean. also since this almost happened to me recently: if you manage to fill up a hard drive to the brim, with literally 0 bytes of space left, that bricks it. reminder to check your storage thoroughly and often!)
Honestly wow I read it all and I'm a little bit speechless 🥹 thank you 💫 anon, it was great 🙏

Boothill would DEFINITELY appreciate a s/o who's a tech savvy in general! I think at some point, he'd be pretty shocked you're so knowledgeable and just sit there, listening to you rant.. and just letting you do your thing.
Don't get me wrong, he definitely knows a lot about his body, his system and the way he works, but once you start to get in the zone and explain stuff to him, berate his code even, he just sits next to you, plugged in to your laptop, leaning his cheek against his hand listening to you like he obviously understands everything you say.
His other hand begins to gently play with a stand of your hair, humming deeply when the soft clicking sounds of your keyboard reach his ears; he twirls your hair with his fingers and chuckles, "mmm, really now?" Boothill raises an eyebrow, "encryptin' this, encryptin' that... How about we do somethin' more fun instead?" And then you shut him down from your laptop (😭).
Jokes aside, he'd feel very secure with you especially when he first got his new body, just knowing you'll probably fix a lot of things that could possibly blow up his face in no time, maybe even improve his life even more.
#honkai star rail#honkai star rail x reader#hsr x reader#boothill x reader#boothill hsr#boothill#.💫 anon#.anon thirst
245 notes
·
View notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
144 notes
·
View notes
Text
Inaccessible tech is such a vicious cycle it’s beyond frustrating. My computer knowledge is dreadful for someone my age, and I know it’s dreadful but it’s incredibly hard for me to do anything about it.
Dragon, the software I use to control my computer with my voice costs £679.99. I have access to it through a scheme to help disabled people in work – without a job I’d have to pay for it myself or find another source of funding (without access to a laptop/ PC).
The software is great in many ways, but limiting in others. It’s mainly targeted at able bodied professionals as a way of dictating quickly, so while it’s absolutely brilliant for dictating into a word document, it’s a bit more tricky to control your computer with it.
One of the biggest problems though is that I can’t easily try out different software and browsers. Google docs aren’t as compatible with my software as word is. I can’t learn about alternatives because it’s a lot of time invested in something that probably won’t work well.
Each different browser requires me to download a different extension so that Dragon can interact properly with the pages. Until that’s all set up, rather than just being able to click on things I have to guide the curser through a series of increasingly small numbered grids to the right point on the screen like this: “mouse grid [pause] 3 [pause] nine [Pause] one [pause] two [pause] Mouse left click”).
But Firefox, the browser I’m most often recommended to use, I can’t use. From what I can tell there used to be an extension but Firefox now considers the Dragon extension to be a security risk and won’t allow it to be installed. I’ve looked into finding alternative ways to download the extension, but it gets really complicated really quickly – especially when each and every mouse click takes so long. After failing several times I gave up.
And it’s frustrating because if using a computer wasn’t so difficult l me, I would probably be better at finding my way around these kinds of obstacles better.
And if technology wasn’t so expensive and difficult to access more disabled people would be creating better software and hardware for disabled people.
Similarly if adaptive controllers were less expensive I might know more than I do about gaming. And more game producers might be disabled, or might create games with disabled people in mind.
But we’re stuck trying to make do with technology that’s either financially out of reach, incredibly limited or both and it means it’s incredibly hard to learn enough to come anywhere close to solving those issues (or being able to properly describe them in the first place)
135 notes
·
View notes
Text
hi. since i have something that could very generously be called a platform, your local dumb horny dog is here with another unfortunate public service announcement for people currently living under the legal jurisdiction of the united states of america:
this would be a good time to start investigating privacy and data security tools (and, as ever, to not panic and/or doompost because those are not useful things to do). such things include:
using (more) secure messaging apps over sms for private correspondence such signal.
using (more) private email services rather than gmail such as protonmail
password protect your shit. this is just basic data security but like. please. password protect your shit. use strong passwords and/or passphrases. don't reuse passwords. use a password manager (i recommend bitwarden).
building off the previous one, encrypt your shit if you're able to. for pc users there are plenty of open source options, such as veracrypt, and probably native os stuff too.
like. y'all are gonna roll your eyes, and i get it, but: stop using windows and try out linux. seriously. windows 11 is a fucking privacy nightmare and it's only getting worse as microsoft pushes their ai shit which is planned to have access to everything you do on it.
tumblr can't do nested lists, consider this a sub-point: mint linux is designed to be incredibly familiar to people coming from windows and is very user friendly. a huge amount of windows software can run on linux using stuff like wine. the linux version of steam comes pre-packaged with it. it's fine. please try linux it won't bite.
sadly i am, as mentioned, a dog on the internet and i cannot provide an actual comprehensive guide to keeping your privacy intact and yourself safe.
however, there are plenty of good guides for this sort of thing on the internet and despite how degraded modern search engines are they are not hard to find. i heartily suggest doing so and familiarizing yourself with them-- and not just because of the times we live in, because a lot of this shit is the same shit that will help keep you safe from a lot of forms of identity theft and the like. it's just good opsec.
22 notes
·
View notes
Text
It's funny how most every cyberpunk story or setting thought that due to technology taking over people's lives and humanity, computer literacy would become commonplace enough that the very term would disappear. Everyone in Night City or whatever is super into hacking or can at least give you the difference between hardware, software, antivirus, spam, etc. To not know the basic gists or cybernetics and cyber security is paramount to not knowing how to count or how to read.
In reality we're about to enter an age where knowing how to create a folder or a zip file is back to being ancient lore inscribed in tablets that only the 30 year old who works at your IT office knows how to do. Phones and the growing marketability of easy-access no-customization technology means kids just don't use computers anymore. And it's crazy how fast it happened.
When I was in kindergarten we still had "computer class" once a week, and it was objectively useless for everyone in my class. Regardless of our age or interests, all of us had casual PC time either at home or in cyber cafes, all of us knew how to do things the teachers many times struggled with. The moment typing machine class became keyboard typing class, computers were already dominating most of our time. I learned how to navigate a computer the same way I learned English; by myself, because it was vital for my own interests.
And between highly streamlined video games, single umbrella closed OSs and everything being a fucking app, a 14 year old nowadays is lucky if they know what quotation marks do to your Google results. It's genuinely harrowing how the future is tech-dependent, yet we're becoming completely tech-illiterate.
The worst part is that it's completely on purpose by the tech industry. Much like not being able to fix your own products when they break, if you simply don't know what your phone or your computer can *do*, it's much easier to sell you a borderline identical one a little earlier than you'd actually need it. Phone updates are already pretty much semantic; you can't even see the difference between new models and old ones anymore, unless the visual difference is the point. And it all just gets more and more expensive for less and less bang for your buck.
We never expected the cyberpunk dystopia to be dull, and to rely on making us dumb. Crazy how well it worked.
#technology#tech#computer science#cybersecurity#these dang kids with their foortnoites and their moinecrafts#back in my day we learned to count with age of mythology#bit doom and gloom but seriously the amount of kids who dont know how to operate their own phones any more than boomers do is staggering#its all by design too of course
125 notes
·
View notes
Text
Kouji + Reader (Sister) Headcannons

A/N: This is a familial relationship between you and Kouji. Don't be weird about it lol.
Kouji can be a mean brother who teases his sister a lot, but he tries not to overdo it
He's recognized as the genius kid of the family, and he would point that out to you as if that were obvious. But, he also tries not to do it often and he doesn't want you to feel insecure about it since he still cares about you.
Kouji is super protective over you, especially whenever you use his computer at home
One day, you were curious, wondering why he’s always so addicted to using his PC (computer in the day, computer at night) so you decide to snoop through his computer when you got home from school before him
While passing through his login on his computer, you look through his desktop on his computer and you find normal files relating to school, gaming applications, and… a spreadsheet document that’s titled “Money Log”, which you don’t find too suspicious. (He’s just a teen who wants to properly organize his money. How is that suspicious? 🤔)
Nothing seems to catch your eye, so you decided to look deeper by going through his history of accessed documents, files, and software installations
You noticed a software installation called “VPN” and a folder that says “Private” on there. But, his private folder was locked and it was under password authorization
While you were still trying to figure out his password, Kouji would catch you right when he came home from school and ask you what you were doing on his computer with a stern face, trying to hide his nervousness. However, when you cut him off and asked about how you so happened to find a “Private” folder on his PC, he immediately admitted that it was p*rn for you to shut up about it. (Is he really telling the truth though? You can't tell.)
Obviously, Kouji can also be secretive towards his sister, but also wary of what he does online and at home whenever you decide to crash and hang out in his room
The both of you would often play PC games together like horror games like "Welcome to the Game" (totally up his alley), Minecraft, Roblox, Valorant, etc. He usually does the game controls for you, while you sit there with him and watch him do all of the work. But, if you ask him if he can take control of the gameplay, he lets you but he teases you by saying, "You suck at this." which then leads to a never-ending banter between you two.
However, you don't just play PC games together, but also multi-player mobile games like Genshin Impact (he doesn't want to admit to you that this is his favorite game), Among Us (yes on mobile), and Stardew Valley.
Whenever you guys are bored together, you'd go on weird websites like Omegle or Chatroulette. Often times, he'd try and hack the other person on the other side of the screen ("just for fun" he says) and you had to scold him and try to convince him not to do it for the sake of the poor person on the other side. Most of the time, he just ignores you and just does it anyway. He justifies his own actions as some sort of necessary justice by pointing out, "See? These people are sick, just look at them! Nasty old geezers..."
You noticed how he's a Discord addict who's a part of a bunch of servers online with various aliases. He's a Discord mod for many servers, whether those servers serve as a purpose for gaming and hacking communities. But most of the servers he's on, he mostly hacks into them to troll people online through phishing links and sends random files in group chats that are actually malicious.
You have a strong feeling that he occupies his time doing something more than just trolling online users and playing video games. Since he's so good at hacking and online security, you have to admit that your brother is a technical genius. If that's the case, then you would assume that his hacking capabilities might exceed more than just surface web level. Even if that possibility might lean towards him exploring the Dark Web. (He's your brother. Of course, he would.)
Sometimes whenever he would take a break from using his computer all day doing God knows what, he would join you on the couch and watch a horror movie or a game show
While watching that movie/game show, he would criticize the show or movie by saying, “They are so dumb. I mean, why can’t they just run?” or “Why can’t they get such a simple question right? Are they stupid?” And your only answer for him is: “They just aren’t as smart as you, Kouji.” and your responses always boosts his ego, even if your replies were a bit sarcastic
While watching TV together, he would often eat candies or sweets and he would share them with you
In the living room whenever you two are free from homework or just so happened to be bored, you'd challenge him to play Super Smash Bros. on the Switch. And every single time, he'd mostly beat you in every single round by using his favorite character to fight: Ness (Of course he would use him. I call this canon.)
While playing Super Smash Bros, he would call you out for choosing weird characters to fight like Isabelle, the Villager from Animal Crossing, the Pirahna Plant, and even the Wii Fit Trainer (YES, THE FUCKING WII FIT TRAINER.), and he would call all of them weak. "What the hell? Out of all of the characters you chose, you decided to fight as them? No wonder you died so quickly." His insults didn't stop you from challenging him for rematches.
Whenever you ask him to help you on your homework, he would begrudgingly help you. (Basically, you’re the only person who he would help without blackmailing or without charging you with anything in return for his service.)
Kouji would eat the treats you bake, whether that be cookies, cakes, and other desserts. Especially, the strawberry cakes that you'd make and you would share it with him.
Whenever you mention a boy or a male friend, he would seem very nonchalant about it and dismiss the subject. But you wouldn’t know that he would do research on the poor boy, social engineer to hack into that boy’s accounts (financial accounts or not), and commit cyberattacks on him (viruses, DDoS attacks, phishing, etc.)
Whenever the both of you end up in an argument, you apologize a few days later by sneaking into his room and place sweets on his desk with a bottle/can of grape soda in front of his computer with a little note that usually says small messages like, "Truce? :)" or "I'll give you this peace offering if you let me off the hook." and he would usually accept the gifts and reluctantly eat them.
You would dye his hair purple for him, whenever he asks you to do it and recolor his hair once in a while.
As siblings, you'd do each other a solid at home with the typical "you owe me" exchange. This is your own little way of showing how much you care and look after each other.
You're aware that Kouji has a job, since you caught him one day with a check in his hand that had a bunch of 0's for its amount. You asked him, "Where'd you get that from?" and he would simply say, "My job."
You were a bit shocked to hear that he has a job so your conversation with him ended up being sarcastic and blunt. This is how it went:
"What job?"
"The job that I work for."
"No shit. I meant, where do you work at?"
"Some company."
"Some company? Bullshit. And they'd actually hire someone as young as you? You're barely 16."
"And? The other people that they've interviewed before me were all a bunch of idiots in the first place."
"Huh... I guess that makes sense."
Finally, you two left it at that and decided to never tell your parents about it. After all, what are siblings for anyways?
#lookism#lookism manhwa#lookism webtoon#lookismaddict#lookism fandom#lookism memes#lookism meme#lookism imagines#lookism x reader#lookism fanfic#lookism headcanons#kouji#lookism kouji#kouji lookism#we need more Kouji recognition in this fandom#manhwa#webtoon
112 notes
·
View notes