#infosec community
Explore tagged Tumblr posts
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
3 notes
·
View notes
Text
Someone on a discord I'm in asked us older-uns who were adults during the 2016 election what to do. I have no fucking clue, but I still managed to dig up some thoughts. It's long as shit, barely edited, and you don't know me from Bob in terms of 'credibility', but it's my few cents.
TLDR:
Back up content you want or need off the web now, before FOSTA-SESTA or related 'authoritarian censorship' stuff rolls out. This can be that your favorite fic you'd be heartbroken to see purged for being marked as pornographic content; this is also downloading family photos from Google Drive.
Learn how to garden, or learn how you can learn to garden in a pinch of you lose money and/or supply chains get fucked.
Have you heard of OPSEC and INFOSEC? Good, that's a start. Learn more. If you haven't heard of them, learn quick. This is 'loose lips sink ships' and 'do not take phones to protests (or anything else that might get judicial crackback)' as much as its 'get a VPN and make sure its reputable'.
And the original rambling post, for anyone interested:
Is more an abstract 'thing to do', but as a historian and amateur archivist who knows history of censorship, etc: Think about what you want to back-up. What you need saved, or think needs to be saved, and what you can save. If you've got stuff online on sites you think might not survive FOSTA-SESTA or Musk and Peter Thiel types getting carte blanch, back it up. If you go through a webpage you think should be saved to look back on for 'here is how things became what they are', save it. Looking back at 2016 when 'grab em by the pussy' was the most egregious shit - when the original Unite the Right rally happened and we were aghast - compared to now, its night and day. We got here day by day. This time it might be a bit more abrupt. Still. What are the posts, the pages, the tweets you think need to be saved, for yourself or for history? Save it.
(For example: SingleFile is a firefox addon that allows you to save, Wayback-style, webpages to your personal files and keeps all embedded media from the page! If you SingleFile a wikipedia page, you have it downloaded; if you hit a reddit page, you'll have it with intact formatting; and it'll even capture stills of tumblr pages with all posts on said pages. If you are looking at this Read More? If I ever get deactivated, this Read More is lost. The first part of the post can be reblogged, but no one can get into Read More sections of posts whose OP has seen deactivated. SingleFile the page you have this post opened in, and you have it on-hand forever. Wayback also exists, but that's contingent on the Internet Archive - Wayback's parent - surviving things. If it does, it does; but if you think your personal files will survive longer (or want to access osmething sans internet), SingleFile is there for you.)
Hell, between 'what if this gets censored off the web?' and 'what if I want to have a copy of this on-hand even without internet?' is a possible approach here. What fanfics would you like to have on hand, and to not loose to a site-purge? What Youtube videos bring you joy, and which ones are records you want kept from this time? What media do you want to pirate in case a company deletes old product, and how might that get worse under a second Trump reign? Start there, and figure out what else to back up next.
Otherwise, if you don't think you're going to be able to make it out of the country and you want to prepare for if things truly do go to shit, some things to look into include:
Do you know how to grow food? Otherwise, figure out if you have easy access to ways to learn (library, downloaded how-to PDFs, your gardener friend, etc). There's been intermittent episodes about food-growing (and community gardening) on It Could Happen Here
Maybe listen to It Could Happen Here, or at least put it on your watchlist. Robert (a long-time political-extremism journalist) originally started it in 2019 as a 'here is how a second american civil war could start' thing, and transitioned it into daily discussion of how to survive 'it' happening here...such as what's happening right now. Listen to ICHH; it might be depressing, but him and his cohosts know what they're talking about.
Learn what info-security and operations-security is. Any sort of activism is likely to be more dangerous than protests in the last few years, and those have still been a shitshot. Whether its 'do not take your phone to protests' to 'download a VPN' to 'loose lips sink ships': learn about the concepts, make sure you know how you can learn more. This is especially true if you wait to do this, as the more time any theoretical authoritarian govts have time to prepare, the more they might notice what info you are searching for. Paranoid? Not pessimistic enough? I'd rather you be thinking of this now than to realize its far too late.
Beyond that, yeah: if you can get out, that's not a bad idea. You're asking us for advice on how to survive, and the horrid fact is: this time is going to be so much worse. There's been more time for things to fester, more time for the fascists to gather power, more time for them to grow bloodthirsty. Again. History major. This is going to be really fucking bad.
Whether you get out or not, people need to come together more. Last time, the fascism rippled out: Trump got in, and a lot of similar cases went masks-off (or won elections) elsewhere. The same is likely true this time. In America or not, people need to come together; and it's the only way we'll survive or hold our own.
And in the meantime: figure out what you can save, or need to save. Save it. Figure out how to garden, or how to do maintenance on stuff that might start crumbling as shit gets bad, or figure out the basics of infosec and opsec. Do multiple if you can; do individual ones if you can't, or can reasonably work with others to cover each other's weaknesses.
It's still going to suck. There's no way this doesn't suck. Frankly, there's no way there's not going to be at least some horrific atrocities; it's just a question of how many, and how quick they start up. That's the best thing I can recommend, honestly, is: it's good to hope things somehow work out, but don't stick your head in the sand. If you hope the leopards don't eat your face because you stay still and don't move, maybe you'll live? But maybe not, and maybe you'll just see someone else get eaten. Preparing won't necessarily save you anyways. But, it'll buy you better odds, and it'll make the fascists a bit more annoyed, and enough annoyances might fuck them still. Hopefully this helps in some way.
#the monkey speaks#current events#all who live to see such times#how to survive#opsec matters#tips and tricks and warnings (communications and infosec)#preparing for 2025 and after
15 notes
·
View notes
Text
[Image ID: Image is black text on gray-white background. Text is as follows:
If you use Signal, Discord, or any other messaging app and you DON'T want Google or Apple monitoring/reading/learning from your messages, follow these steps.
Android:
1) Open google app
2) Tap your profile photo
3) Settings
4) Google Assistant
5) "Your apps"
6) Choose the app (e.g, Signal)
7) Toggle "let your assistant learn from this app" off
iPhone
1) Settings
2) Apps
3) Choose the app (e.g, Signal)
4) Toggle Apple intelligence or Siri settings to off ("learn from this app")
Image ID ends.]
And yeah, can confirm on android: went and checked and google assistant - which I don't ever use - was plugged into all my apps. Well, no more.
Additionally, for android users (I don't have an iPhone so no clue what to do on that side), after going through Assistant->Your Apps, back out and do Assistant->Your Data in the Assistant. See what else it's wired into (web & app activity, if it's in your contact info, if it's in your YouTube history) and especially follow up on the 'personalized ads' bit down at the bottom.
Fuck you panopticon, I'm gonna keep poking you in the eye with a stick every opportunity I get!
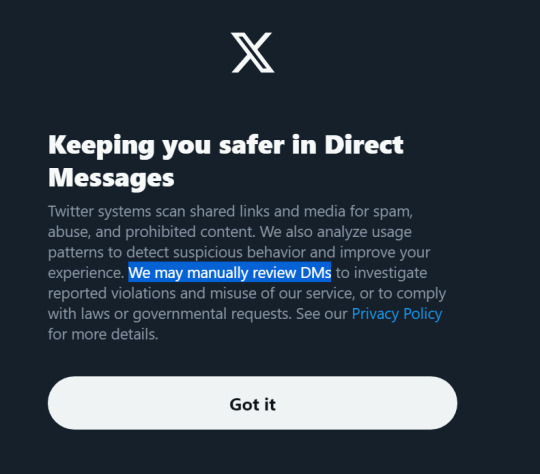
PSA: never discuss private affairs in your DMs, especially contraception and abortion. Social media moguls will absolutely sell you out to the government. There are already cases of people being charged based on evidence in their DMs.
#the monkey speaks#the dumbest possible cyberpunk future#opsec matters#tips and tricks and warnings (communications and infosec)#the panopticon blinks less and less
79K notes
·
View notes
Text
Don't blame the messenger.
Here's a podcast, see how long it takes for you to rage quit. ;-)
(transcript available at link)
#rage quit#propaganda#online marketing#target marketing#public health#pseudoscience#anti-vaxxers#freedom of speech#politics#social commentary#civic engagement#publishing#media#independent media#don't shoot the messenger#podcasts#write your reps#infosec#information security#scams#online communities
0 notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
84 notes
·
View notes
Text
In case anyone is wondering why I've stopped making my own political writing to post here and am not reblogging as much of others' things or the same types of things:
A) when you work in the fields that are currently holding the line, you stop having the energy to engage in online discourse real goddamn fast lol like I would literally just rather sleep do you know how long it's been since I spent less than 10 hours at work a day????
B) i'm not a goddamn narc. Consider how much of online discourse is about personal assertions of righteousness that get demanded of you to justify your opinion. Consider that perhaps right now "who I am" and "what I do" are questions you should simply not be answering in mixed company or in an unsecured forum.
C) no seriously I don't think we as a culture and community have been thinking enough about what it means to continue operating visibly in spaces to maintain emotional and interpersonal connections while also practicing effective opsec and infosec please consider what you actually do and don't know. Please consider that half remembered facts aren't things you know. Please consider that we all need to move INTENTIONALLY right now and intentional moves look very different than reactive or unstructured ones.
71 notes
·
View notes
Text
Have separate account-names for separate types of content; and try to go further and have separate emails for these separate accounts.
Using my own account name as an example: if I was insulting the hell out of my job on here, at least I'd be doing so as 'zoanzon' and not '[legal name]'...
But if the email my work had registered was, say, 'zoanzon@gmail' instead of '[firstname.lastname]@gmail', then that could become a problem easier than otherwise. All it would take is one bored administrator googling my username, curious if anything comes up, and in this scenario I'd be out of a job.
Plus, if you get doxxed on one account, using the same username on every site means all your accounts get doxxed. If I use zoanzon on everything and I get doxxed; but if I'm only zoanzon on here and I'm something else on twitter or bluesky or insta, and I never posted 'hey, zoanzon and [other accounts] are all my accounts', then I could lose zoanzon and still keep anonymity on other accounts.
Otherwise, if you're worried about what's easily searchable by Joe Random...well, google yourself! Clear your browser cache, open up a new browser window in Incognito, and google your account name. Google the accounts you've used for the past decade. What comes up? Exclude the top site return; underneath those hundred or so tumblr or reddit posts that first came up, what floats to the top next? Any posts there you want to delete because you posted it months or years ago when you were less aware of internet safety? Now do it all again on a different browser: did anything new surface if you went from Google to DuckDuckGo, or Bing, or so on?
If you're trying to go on the run from the government, this isn't enough. But if you're 'just' trying to make sure some random internet chud or troll can't take advantage of you leaving posts up from five years ago saying where you went to school and all your accounts being the same name and doxxing yourself straight to hell...
Well, you can frustrate the chuds and trolls a whole lot more if you silo your accounts, don't announce for all that they're all your accounts, and you clean up old posts where you shared a bit too much.
There's something that I find equal parts hilarious and terrifying.
On one hand it is so funny watching the generation previous to mine (I was born in 84) absolutely say the most unhinged shit online, doxx themselves, and get fired, after spending my entire childhood teaching me online opsec because every stranger was a potential murderer. Social media done rotted their brains.
But on the other I'm seeing kids coming up, seeing them spew all their personals online, and using that to model their unsafe behavior and put themselves at incredible risk because the internet actually got way more dangerous than it was, ironically, when I was coming up being told I had to basically outsmart the fuckin CIA. Now the actual CIA and other bad actors (government, private, and individual) really are out there and these kids are watching fucking meemaw post a photo of the front of her house practically captioned with her fucking SSN and thinking, "yeah, sure, the adults know what's safe."
I gotta be a fuckin millennial about this and beg younger folx to listen to the VCR generation: hide yourself online. Nothing should go there you wouldn't want in the hands of the person who hates you the most.
Be safe, be smart, be a fucking ghost.
24K notes
·
View notes
Text
Guess who has started making yet another videogame.
Here is hoping this one makes it to production.
I will also be trying Codeburg with it.That has been pretty popular in the infosec community.
Here is what I don't get. If my game is set in space, why am I making all my characters fish?
50 notes
·
View notes
Text
Rubies Masterpost
Rubies is a direct sequel to Destroyer. It is focused on Delta's life after captivity and deals with the aftermath of severe conditioning and abuse.
You can also read it on AO3 !
====================================
Character Overview:



Delta - living weapon whumpee with very, very powerful telekinetic abilities. was raised from birth to be a weapon of mass destruction for an evil space empire. hes killed thousands of people and hes really normal about it.
Kitty - catgirl caretaker! she works for the rebellion in infosec. used to be online friends with delta before they met irl.
Apollo - caretaker and combat medic, kitty's best friend. means well more than anyone on the planet.
Kitty and Apollo both coordinated to get Delta out of Empire and have now been made officially responsible for him in the event of snafu.
Not pictured above are:
Lun - Apollo's brother. Space vampire. (did all the real work)
Iza - Weapons expert and squadron leader (took the rap for it)
Levon - Supreme leader of rebel group Galatea (DILF)
====================================
Story:
First Night
Missed Calls
Light Show
First Base
Waiting Room
Settling
Ungrateful
Web 2.0
Terrors
Stars
Habits
Communication
Haircare
Asking
Check In
Trial I
Trial II
Midnight
Trial III
Trial IV
Orientation
Hangover
Snow Storm
Mood
Encounter
INTERMISSION
#whump#whump writing#whump community#whump prompt#whumpblr#whump scenario#living weapon whumpee#living weapon#my writing#original writing#original character#recovery whump#past trauma#conditioning#delta#kitty#apollo#rubies
68 notes
·
View notes
Text
This is not a rejection of the Internet or your precious digital connections. If anything, you'll find you rediscover your digital agency and how it's been stripped from you! You'll engage in new ways online that put you in the drivers' seat. You'll also find your values start to shift. You'll stop asking if a service can do something for you, and instead ask what it wants from you in return--and whether that's a price worth paying, especially if it's "free."
It's also not a course for those deep into the InfoSec world (Information Security). I won't teach you how to go dark, how to move around the web entirely anonymously. But I will teach you how to take steps toward that direction, so that the path is available to you once these short weeks are up.
To that end, I will recommend systems and services that some people who are deep into infosec won't like. Internet nerds have deep and well informed opinions and controversies erupt all the time. For instance, some people recently are angry at Mozilla for some changes they are making, so they recommend not using Firefox. That's just one example. Some will be upset to find that I am still recommending Firefox -- among many other options.
Why? For one, I want to recommend user-friendly systems of many stripes. I will never tell you to just use one thing: the ball is in your court! I'll also tell you when there are concerns, some of which you may care about and others you won't. I don't think there is (or should be) one system to rule them all. There should be many options. We should use many of them, instead of just one. It's way more freeing to do so.
I also want to get you used to something new: moving. Jumping ship. Right now, we think of moving from one service to another like moving a house you've lived in for fifty years. It's a huge burden, and exhausting to even consider. This forces a kind of lock-in where users never want to leave. Tech companies count on this. Academics hand-wring over this form of lock-in, especially in social media.
But once you get started moving your data around, taking agency in how you work the web, you'll see it's actually much easier than you thought. That way, you might move to a new browser and not like it very much (for whatever reason)-- and instead of going back to Google, you'll try something new. Easy peasy. No moving company involved.
I'll clue you in to a different way to use the web. You'll pay more attention to tech gossip. You'll know if a company is doing something nefarious or making a change. You'll know what to do if so. You'll already have one foot out the door anyway.
That's because Opting Out isn't just about leaving systems we don't like -- it's about opting in to systems and communities we value instead.
31 notes
·
View notes
Text
Adjacent and concurrent to what's already been said:
1) Think about if you want things you post or reblog to be at all connected to your outside-world life, now or ten years from now.
Whether you still think the axiom of 'what is on the internet is forever' is still true as sites rot and post-histories fall into the void, you should assume that if you post something, it could theoretically turn up a decade or two later. If the site itself isn't intact, maybe the site was mirrored, or the page was Waybacked, or someone screenshotted it, or so on.
That's not me saying you shouldn't shitpost, or talk politics, or even vent about RL stuff...but do think ahead a bit, just to be safe.
2) Connected to the above: think about if you want to keep the same username on all sites, or if you want to have different IDs. The same for which email you register that site with.
I use Zoanzon here, and on other sites too. If you see the name, its reasonable to assume its me. So, if I ever wanted to make a profile on something I wouldn't want connected to me if a friend or family just randomly poked around, or if I randomly get doxxed, I'd not want to use this handle for registering to porn-sites or whatever.
Maybe you decide to use the same account everywhere; maybe you use one handle for social media and another for Etsy and Patreon and Kickstarter and other buying-sites; maybe you embrace childhood love of spy movies and keep a notebook to track each of your separate handles for every single site. But, think about how you want to go about it.
And emails? I dunno exactly how it works, but I know it's possible to track accounts by their emails, so if you need to keep your online activity segregated, it'll be easier if you've got burner emails. This goes for randos trying to stalk you, and if potential employers try to find what you've been posting online and find you dissing cops or mentioning your health issues.
(Plus it'll make your mail email's inbox less of a hellhole if all the promotional spam is going into an email you have specifically for sites you know will be sending you spam.)
Hey. Minors following me. Internet safety is key!! NEVER include these in your bio/byf:
Medical diagnoses - this is nobody's business but yours. You don't owe anyone an explanation for why you are the way that you are
Trauma - same reason as above
Triggers - people can use these against you! Don't give people tools to hurt you. No one has to know what tags you block. Just block tags to stay safe!
Age - age is okay for adults to include but is iffy when you're a teen. Predators want this information, don't give people more than they need. Just state that you're a minor, that's all that anyone needs to know.
In general: stay safe. If you're not comfortable with every stranger out there having access to this information, you shouldn't post it on the internet.
Play devil's advocate and ask yourself about what would happen if someone searched for your information with intent to hurt you. You do NOT owe anyone an explanation!
#see me posting jackshit in my bio#sure I've said stuff in posts and in tags but i don't just give you that info on a silver platter#but i can also say that the fact I've used the same handle on Twitter and listed my college + gradyear + major#which I'm comfortable having said & am not worried that it's connectable worth this acct... but I'm AWARE i did it#so yeah if you wanna put info out there no one can stop you just... be aware of potential dangers short and long term#the monkey speaks#opsec matters#tips and tricks and warnings (communications and infosec)
111K notes
·
View notes
Text

A Beginner's Guide to Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
(Side note: this post is aimed towards the technical side of security, rather than the governance/management side, because the tech stuff is what I'm familiar with.)
Where do I start?
Cybersecurity is a specialization of general tech & therefore builds on some concepts that you'll need to know before you can dive deep into security. It's good to have a background in and understand:
how computers & operating systems work
how to use Linux
computer networking & basic protocols
If you're serious about learning cybersecurity, it can be helpful to look at certifications. Even if you don't want to get certified or take the exam (they can get expensive), they provide you with a list of topics that you can use to guide your self-study. And if you want to find a job, a certification is practically required for getting your foot in the door.
I personally recommend the CompTIA series of certifications, because they're well-recognized and I think they expose you to a good breadth and depth of material to get you started. Start with the A+ certification if you have zero tech background. Start with the Network+ certification if you've never taken a networking course. Once you get your basic computer and networking knowledge down, then you can jump into security. The Security+ is a good starting point.
Do I need to know how to code?
No, but it would be really really helpful. You don't have to be a skilled software engineer, but understanding the basics and being able to write small scripts will give you a solid foundation.
From Daniel Miessler's post How to Build a Cybersecurity Career:
You can get a job without being a programmer. You can even get a good job. And you can even get promoted to management. But you won’t ever hit the elite levels of infosec if you cannot build things. Websites. Tools. Proofs of concept. Etc. If you can’t code, you’ll always be dependent on those who can.
How do I gain skills?
Play Capture the Flag (CTF) games.
Stay up to date with security news via an RSS reader, podcasts, or whatever works for you. Research terms that you're unfamiliar with.
Watch conference talks that get uploaded to YouTube.
Spin up a VM to practice working with tools and experiment on your own computer.
There are lots of brilliant, generous people in cybersecurity who share their knowledge and advice for free. Find their blogs, podcasts, and YouTube channels. Look for local meetups in your area.
I'm still relatively new to the field, but I have a general knowledge of lots of different things, so feel free to send me an ask and I can probably help point you to some resources. We're all in this together!
Previous Cybersecurity Masterposts
An Introduction to Cybersecurity
Cybersecurity Book Masterpost
Free Cybersecurity Learning Resources Masterpost
Masterpost of Study Tips for Cybersecurity
Cybersecurity Tools Masterpost
Thank you so much to everyone who participated in the #StudyblrMasterpostJam this week! It was wonderful to see what other studyblr folks are passionate about. The jam technically ends today but there are no official rules, so if you've been thinking about writing a masterpost, this is your sign!
32 notes
·
View notes
Text
Modern Academic AU pt2
Originally started because Professor Raphael got stuck in my head and I had (foolishly) hoped if I wrote down some thoughts, that would be the end of it 🫠
Part 1 and Part 3 ------------------------------ Minthara - School of Law. Used to be a high profile defense lawyer but was barred from practice under questionable circumstances, so now she teaches courses on criminal procedure and domestic violence litigation. Male students are actively warned against taking any of her classes. Elminster - Liberal Arts Dean. Has been in the position forever and is something of a legend at this point. He's Gale's mentor and long time family friend, and he delights in showing up unannounced to Prof. Dekarios's lectures. The two of them have a longstanding tradition of leaving surprise pranks in each others offices. Rolan - English department. Newly upgraded from adjunct instructor to junior full time staff, he's been assigned the special hell of having to teach the general ed. introductory writing courses that none of the other faculty want to deal with. He hates it and thinks it's a complete waste of his talents, but is determined to stick through it long enough to get that research grant. Alfira - School of Theater & Music. Teaches vocal technique and musicality at every level. She's also the faculty coordinator for multiple on-campus performance groups, directs the university chorale and composes all their arrangements, is herself in a local acapella group, AND does community arts & outreach programs for kids.
Gortash - Newly appointed Dean of Information Studies. He's brilliant, he talks big about new frontiers in infosec and grand designs in the future potential of AI... and is already under investigation by the ethics board for misappropriation of university funds. Ketheric - VP of Alumni and he's been with the university longer than Elminster. Nobody knows why he hasn't just retired yet, despite how much he seems to hate his job. Orin - School of Fine Art. She "teaches" a course on performative art. It's weird and extremely uncomfortable for everyone involved, but for some reason people keep enrolling. Durge - Fine Art Dep't Chair. The deeply disturbing nature of his personal art aside, he's actually good at his job as both the chair and an instructor. Mostly teaches anatomy and live model studio courses. Ulder - VP of Public Affairs. He's a great public face for the university, everybody loves him... except the son he refuses to acknowledge after a falling out years ago. Mizora - Human resources admin. Loves her job because it gives her power over other people. Is more likely to be the source of an HR complaint than the one who actually solves the problem. Thaniel (as requested!) - Also HR. He's the one you hope gets assigned to whatever you need because he's great at it. Is also the only one who can reliably get in touch with Halsin; it's not well known that he can, so he'll usually agree to help those who figure out to ask him.
------------------------------
This started going long, so it looks like I'll be doing a third (and probably final?) installment to cover Dammon, Zevlor, Wulbren, Aylin & Isobel, and any other requests!
#bg3#baldurs gate 3#minthara#elminster#rolan#alfira#enver gortash#ketheric thorm#orin the red#durge#mizora#ulder ravengard#thaniel
56 notes
·
View notes
Text
Don't ever add yourself to those 'are you coming?' trackers for a protest or march! Whether you go or not, if there's any crackdown or backlash (governmental or otherwise) then your name is on a list that'll be used for said crackdown!
Don't bring your phone, it's a tracking device; even when off the battery still has a charge
If you must bring your phone, have it off and in a faraday bag to block signals; if it's on and on the bag, your phone will go 'oh, I do not have signal!' and try to boost its connection, draining the battery quicker and possibly actually making it through the bag
Look over a map of the area, or - if you have time - walk through the area the protest will be first. This is good so you have a general lay of the land, and so that you can--
Make sure you know how to get the fuck out of the area if it's necessary. Maybe this is cops trying to kettle protestors for arrest, maybe this is because things get bloody with counter-protestors, maybe you just start to panic because of the crowd density and need to bounce. Make sure you know how to navigate out of the area to somewhere else, and - if able - that you have an idea how to do so if you're being pursued
As weather/money allows: are you able or willing to layer your black bloc over other stuff? Do you think you could ditch that top layer if fleeing, so that anyone looking for those in bloc doesn't see you wearing it? Maybe you don't think you can make the magical girl transformation work in time, or weather doesn't allow for you to have an additional layer like that (or to strip a layer off). Still, its a possibility to keep in mind
There's many more things that could be recommended, but part of it all comes down to what your particular threat-model is for your situation.
I seen people on TikTok giving god awful advice on what to wear to a protest. Some “advice” was “wear heavy goth makeup, platform boots, lots of belts and chains, etc” heavily alternative clothes.
NO! Don’t do that.
The thing about protests is you never know who is going to show up, it doesn’t matter how peaceful it is, someone can show up and incite violence whether it’s other citizens or cops.
For your safety do NOT wear something that will make you stand out.
All black clothes are good
Pants and long sleeves even better
Wear shoes you can run in
Cover your tattoos and piercings
Bring a face mask
Sun glasses
Bring water
Backpack or small bag that’s hands free (for snacks, water, first aid, etc
If things turn violent, those violent people will go after the ones who stand out first. So dress safe, stay safe!
955 notes
·
View notes
Text
Idk if ppl have rly been paying much attention to what's happening with furries at the moment but it's getting pretty juicy.
Some guy hacked furaffinity & furaffinity's Twitter account, started shilling crypto shit & going off about furries being pedophiles. Then they set up the furaffinity domain to redirect to Kiwi Farms & this actually made the weird fascist stalkers pretty angry with them.
Dude has pretty much signed their online death warrant what with how many infosec ppl & hackers are in both the furry community & kiwi farms.
We are currently at the finding out part of fucking around.
24 notes
·
View notes
Text
On The Thing: I understand if you have different opinions on how to balance spreading publicly available information to those who would benefit from it, preventing it from escaping containment, and protecting people's privacy, and I did made it unrebloggable in response to @/phaeton-flier and @/cromulentenough's criticism, but if you were yourself reblogging it to all your followers making insulting comments I'm kinda not taking your claims to deeply care about community infosec seriously at all.
#this is just about one person most people have been constructive in their criticism#but this kind of thing is just making it harder to process my emotions around the whole thing#i'm still being far more affected by it than I thought I would#vagueblogging#my fucking ingroup#will maybe delete that later too
6 notes
·
View notes