#risks of electronic surveillance
Text
Why have bug services become an essential thing for homes?
Do you need bug sweep services? Then Qld Covert Investigations has a team of expert bug sweepers and security advisors trained in using the latest equipment. They are licensed professionals who specialize in tactical security countermeasures and can provide advice on maintaining the security of a location.

● To ensure privacy: If you are concerned about someone eavesdropping on your conversations or activities, a bug sweep can help you detect and neutralize any listening devices that may be present.
● To protect sensitive information: If you handle sensitive or confidential information, a bug sweep can help protect it from unauthorised parties' interception.
● To comply with regulations: In some industries, such as financial services or healthcare, it is required to conduct regular bug sweeps to ensure the privacy and security of sensitive information.

● To protect against corporate espionage: If you are concerned about the possibility of corporate espionage, a bug sweep can help you detect and neutralize any electronic surveillance devices that may have been placed in your office or other business location.
● To protect against personal threats: If someone tries to target you to gather information about you, a bug sweep can Investigation help you detect the bug. And destroy that which was placed strategically in your premise.

How to procedure takes place
Bugs are electronic devices that are placed in a location in order to collect information secretly. They can be used for continuous surveillance or to record specific events. To protect against the risks of electronic surveillance, it is advisable to regularly conduct bug sweeps to recognise any such devices that may be present. These sweeps should be timed with ongoing surveillance and specific events in mind. The frequency of the sweeps should be determined based on the known risks and any possibilities of particular concern.
Final Say
Thus, these are the important points of having Home Bug Sweep service from the reputed company QLD, known for their immense experience.
#Home Bug Sweep#Bug Sweep Services#Private Investigator Surveillance#TSCM Sweep#Business Bug Sweep#corporate Tscm Investigator#TSCM Private Detective#professional TSCM investigation#Private TSCM Investigator#Bug Sweeping equipment#TSCM investigation services#Home Bug Sweep service#risks of electronic surveillance#private investigation companies
0 notes
Text
Not they tryna reenact KOSA… anyway yall, here’s why KOSA is bad!!
If you don’t already know, KOSA, or Kids Online Safety Act is a bill that was proposed to keep children safe on the internet. You might ask ‘why is this bill bad if it’s in favor of supporting the safety of children online’? Well, according to stopkosa.com, it puts pressure on platforms to add even MORE filters on anything they think is inappropriate for children. This is especially harmful for LBGTQIA+ youth because the knowledge about this topic would be censored, as well as knowledge on suicide prevention and LGBTQIA+ support groups. Do you see how this an issue? For those children who are wanting to learn more about these topics they’d be turned away because of this bill. It would also be likely that it’ll allow the shutdown of websites that allow them to learn about race, sexuality and gender.
This bill would also add more internet surveillance for all users across all social media platforms. It would expand the use of age verification and parental monitoring controls. These things in itself are already very invasive, but doesn’t take into consideration the children who live in unsafe environments where they are domestically abused and/or are trying to escape these situations. To add my two cents onto this, I strongly believe that the KOSA bill is an unnecessary violation of our first amendment rights (if you’re American), and doesn’t really make the internet any more safer. It actually makes it more unusable for youth. Hypothetically, if this bill were to be passed, then this would make social media unusable for literally anybody. To censor content from the youth about wanting to learn about their identity is extremely harmful. Blocking them from accessing resources that may prove as helpful in their scenarios is outlandish and unneeded. We try to shelter our youth so much to the point where we try to boil them down to only being with their parents want them to be and also not being able to let them learn and explore about other things that they may want to identify themselves with. This is very harmful.
This is a list of companies who are saying no to KOSA ..
• Access Now
• ACLU (American Civil Liberties Union)
• Black and Pink National
• Center for Democracy & Technology
• COLAGE
• Defending Rights & Dissent
• Don’t Delete Art
• EducateUS: SIECUS In Action
• Electronic Frontier Foundation
• Equality Arizona
• Equality California
• Equality Michigan
• Equality New Mexico
• Equality Texas
• Fair Wisconsin
• Fairness Campaign
• Fight for the Future
• Free Speech Coalition
• Freedom Network USA
• Indivisible Eastside
• Indivisible Plus Washington
• Internet Society
• Kairos
• Lexington Pride Center
• LGBT Technology Partnership
• Massachusetts Transgender Political Coalition
• Media Justice
• National Coalition Against Censorship
• Open Technology Institute
• OutNebraska
• PDX Privacy
• Presente.org
• Reframe Health and Justice
• Restore The Fourth
• SIECUS: Sex Ed for Social Change
• SWOP Behind Bars
• TAKE
• TechFreedom
• The 6:52 Project Foundation, Inc.
• The Sex Workers Project of the Urban Justice Center
• Transgender Education Network of Texas
• TransOhio
• University of Michigan Dearborn – Muslim Student Association
• URGE
• WA People’s Privacy
• Woodhull Freedom Foundation
There is something you can do to stop the KOSA bill from being passed! On the website I linked, there is a petition. All you have to do is fill out the information and it’ll send off an email for you. The email reads as follows:
I’m writing to urge you to reject the Kids Online Safety Act, a misguided bill that would put vulnerable young people at risk.
KOSA would fail to address the root issues related to kid’s safety online. Instead, it would endanger some of the most vulnerable people in our society while undermining human rights and children’s privacy. The bill would result in widespread internet censorship by pressuring platforms to use incredibly broad “content filters” and giving state Attorneys General the power to decide what content kids should and shouldn’t have access to online. This power could be abused in a number of ways and be politicized to censor information and resources.
KOSA would also likely lead to the greater surveillance of children online by requiring platforms to gather data to verify user identity.
There is a way to protect kids and all people online from egregious data abuse and harmful content targeting: passing a strong Federal data privacy law that prevents tech companies from collecting so much sensitive data about all of us in the first place, and gives individuals the ability to sue companies that misuse their data.
KOSA, although well-meaning, must not move forward. Please protect privacy and stop the spread of censorship online by opposing KOSA.
The website also gives you like a format of what you can say if you chose to call your representatives. If after reading this post, you feel inclined to do something then I would say just go ahead and do it. My first time learning about KOSA was today immediately after seeing the post I felt inclined to send my lawmakers an email. Please try to help when you can and this will only take a few minutes so I think this is something that you can consider. This post is getting a little long now, so I’ll stop here. There are more resources online if you would like to learn more about the cons of this KOSA bill, thank you for reading.
#wlfabby#fuck kosa#kosa#internet censorship#stop kosa#lgbtqia#lgbtq community#laws#stop this bill from being passed. 🙏
97 notes
·
View notes
Text
Introduction to Armchair Activism
Current feelings about the state of radblr.
Fundamentals
"Yes, Everyone on the Internet Is a Loser." Luke Smith. Sep 3, 2022. YouTube.
An activist movement can be a place to build community with like-minded people, but action is its foremost purpose, not community. To allow yourself and other activists to remain effective, you are obliged to abandon your personal dislikes of other individual activists. Disagreements are worth discussion, but interpersonal toxicity is not.
Connect with in-person community and do not unhealthily over-prioritize online community. Over-prioritization of online community is self-harm.
Luke is a loser, but his channel is teeming with entry-level digital literacy information and advice pertaining to healthy use of technology for us cyborgs.
"Surveillance Self-Defense: Tips, Tools and How-Tos For Safer Online Communication." Electronic Frontier Foundation.
Hackblossom, outdated, is discontinued. The EFF project Surveillance Self-Defense is up-to-date, comprehensive, and follows personal educational principles of simplicity and concision.
To learn more about general (not focused solely on personal action) cybersecurity, visit Cybersecurity by Codecademy and Cyber Security Tutorial by W3Schools. Both contain further segueways into other important digital literacies.
Direct recommendation: Install and set up the linux distribution Tails on a cheap flash drive.
Direct recommendation: Develop your own home network security schema.
Direct recommendation: Always enable 2FA security for Tumblr, disable active / inactive status sharing, and learn to queue reblogs and posts to protect against others' interpretations of your time zone.
Direct recommendation: It's both possible and relatively simple to host your own instance of a search engine using SearXNG.
Zero-Knowledge Architecture.
As a remote activist (even if also a hybrid activist), none of your action should be taken on, using, or interfacing with non-zero-knowledge-architecture services. Tumblr is, of course, a risk in and of itself, but you should not be using services provided by companies such as Google, Microsoft, or any others based in or with servers hosted in 13-eyes agreement nations.
Search for services (email, word processor, cloud storage) which emphasize zero-knowledge architecture. Businesses whose services are structured as such cannot hand over your data and information, as they cannot access it in the first place. If they cannot access the majority of your metadata, either - all the better.
Communications for Armchair Activism
"Technical Writing." Google.
Contained within the linked page at Google Developers, the self-paced, online, pre-class material for courses Technical Writing One, Technical Writing Two, and Tech Writing for Accessibility teach activists to communicate technical concepts in plain English.
"Plain Language." U.S. General Services Administration.
Plain language is strictly defined by U.S. government agencies, which are required to communicate in it for simplicity and quick, thorough comprehension of information.
"Explore Business Law." Study.com.
Extensive courses are offered to quickly uptake principles of business law such as antitrust law, contract law, financial legislation, copyright law, etc. Legal literacy is often the difference between unethical action of a business and its inaction. Legal literacy is also often the difference between consideration and investment in your policy idea and lack thereof.
"Business Communication." Study.com.
Now that you're able to communicate your prioritized information, you may also initiate writing with bells and whistles. While other activists care most about the information itself, business communication allows you to communicate your ideas and needs to those who you must convince worthiness of investment to and win over.
Logic.
Learn it through and through. Start with fallacies if you're better at language and work your way backwards to discrete mathematics; start with discrete mathematics if you're better at maths and work your way forwards to fallacies, critical literacy, and media literacy. State that which you intend to state. Recognize empiricism and rationalism for what they are. Congratulations: you are both a mathematician and a law student.
Economic Literacy for Armchair Activism
"Microeconomics." Khan Academy.
"Macroeconomics." Khan Academy.
The globe operates on profitability. Women's unpaid labor is a massive slice of the profitability pie. While it's possible to enact change without understanding all that drives the events around you, it's impossible to direct or meaningfully manipulate the events around you beyond your scope of comprehension.
Understand economics or be a sheep to every movement you're active in and to every storm that rolls your way.
#masterpost#armchair activism#remote activism#hybrid activism#cybersecurity#literacy#digital literacy#women in tech#radical feminist community#mine
71 notes
·
View notes
Text

🇺🇸 🚨
UNITED STATES CONGRESS PASSES SERIES OF ANTI-DEMOCRATIC AND PRO-WAR BILLS DESPITE PUBLIC OPPOSITION
The United States Congress and Senate passed a series of bills, including three controversial anti-democratic and pro-war bills, two of which were tied together, on Saturday, bypassing public opinion and popular opposition to the profligate, pro-war, globalist, Neolib/Neocon agenda currently driving United States domestic and foreign policy.
Included in the bills passed was a bill to force TikTok to divest from its connections with China at risk of being banned immediately, which naturally was tied to a Foreign aid bill.
However, as even Republican Senator Rand Paul mentioned in an opinion piece in Reason Magazine, the Bill is almost certain to lead to more power for American political elites and their administrations to pressure companies like Apple and Google to further ban apps and sites that offer contradictory opinions to that of the invented narratives of the American Political class.
Before long, Americans, many of whom are already poorly informed, and heavily misinformed by their mainstream media, could lose access to critical information that contradicts the narratives of the United States government and corporate elites.
Horrifically, this only the start. The US Congress also extended the newly revised FISA spy laws, which gives the United States government the power to spy on the electronic communications of foreigners, while also conveniently sweeping up the conversations of millions of Americans, as we learned years ago thanks to the sacrifices of whistle blowers and journalists like Edward Snowden, Chelsea Manning and Julian Assange.
The new FISA Law goes further than this, however, granting US Intelligence agencies the power to spy on the wireless communications of Americans in completely new ways.
A recent Jacobin article describes these new powers as a, "radical expansion of government surveillance that would be ripe for abuse by a future authoritarian leader", or it could just be used by the authoritarian leadership we have right now, and have had for decades.
In fact, when one commentator described the new powers as "Stasi-like," Edward Snowden himself replied with a long post in which he remarked, "invocation of "Stasi-like" is not only a fair characterization of Himes' amendment, it's probably generous. The Stasi dared not even dream of what the Himes amendment provides."
The amendment in question just "tweaks" the current law's definition of an "electronic communication provider," which is being changed to "any service provider," something extremely likely to be abused by the government to force anyone with a business, a modem and people using their broadband to collect the electronic communications of those people, while also forcing their victims into silence.
The government could essentially force Americans to spy on other people and remain silent about it. Cafe's, restaurants, hotels, business landlords, shared workspaces all could get swept up into the investigations of the Intelligence agencies.
Worse still, because picking out the communications of a single user would be next to impossible, all of their victim's data would end up being surrendered to the authorities.
Sadly, the assault on Americans by their own political elites didn't end there, to top this historic day in Congress, at time when the United States public debt is growing at an astounding rate of $1 trillion every 100 days, US lawmakers also passed a series of pro-war aid packages to American allies (vassals) totalling some $95 billion.
Included in the foreign aid bill are aid packages totalling $61 billion for the Ukraine scam, $26 billion for Israel's special genocide operation in the Gaza Strip, and $8 billion to the Indo-Pacific to provoke WWIII with China, at the same time we're also provoking a nuclear holocaust with the Russian Federation.
Also buried in these aid packages is the authorization for the United States government to outright steal the oversees investments of the Russian Federation, and thereby the Russian taxpayers.
Astonishingly, and in direct opposition to the wishes of their own voters, Republican support was won without the possibility of conditioning the aid to any kind of border security, this despite the issue being among the top biggest concerns of Republican voters.
Although much of the money is to be used replenishing the heavily depleted stocks of America's weapons and munitions, it remains unclear where the munitions are expected to come from, as US defense production has remained sluggish and slow to expand despite heavy investments and demand in recent years, despite the rapid urgency with which the policy elite describe the situation.
It bodes poorly for working Americans that only a relatively small handful of lawmakers opposed the bills, producing unlikely bedfellows like Senator Bernie Sanders and Senator Mike Lee in the Senate, opposing the FISA bill.
While in the House, the loudest opposition to the foreign aid bill mostly came from populist Republicans such as Marjorie Taylor Greene, Thomas Massie and Paul Goser. Only 58 Congresmembers voted against the Foreign Aid Bill in which the TikTok ban was tucked.
Not one word from American politicians about the need to raise the minimum wage, which hasn't been increased since 2009 despite considerable inflation, nor a word about America's endlessly growing homelessness crises, property crime increases, or the 40-year stagnation of American wages, the deterioration of infrastructure, and precious little was said besides complaints about border security over the immigration crises sparked by American Imperialist adventures and US sanctions.
What we've learned today is that we are highly unlikely to see any changes to the insane behavior of the US and its allies any time soon, neither with regards to the absolutely bonkers Neocon foreign policy leading us to the edge of abyss, nor the spending-for-the-rich/austerity-for-the-poor Neoliberal domestic policy of the last 45 years.
#source1
#source2
#source3
#source4
#source5
#source6
#source7
#source8
@WorkerSolidarityNews
Blue: titles are opinion pieces or analysis, and may or may not contain sources.
#us news#us politics#us domestic policy#us economic policy#us economy#us foreign policy#us foreign aid#foreign aid#ukraine#ukraine war#russo ukrainian war#russia ukraine war#israel#palestine#china#politics#news#geopolitics#world news#global news#international news#war#breaking news#current events#us imperialism#immigration crisis#fisa#fisa court#fisa bill#tiktok ban
49 notes
·
View notes
Text



GAKU GENJIRO'S MHA REFERENCE SHEET IS HERE!!!
Art by @socialllyawkwardalien
QUIRK DETAILS
Description: With Glitch Walk, the user has the ability to manipulate digital and technological systems by generating glitches. They can access and control electronic devices, causing them to malfunction or behave unexpectedly. This allows the user to bypass security systems, disable surveillance cameras, or even disrupt communication networks. Additionally, they can glitch their own body, allowing them to phase through solid objects or teleport short distances by distorting their form.
DRAWBACKS
1.Overuse of the quirk can cause the user to experience disorientation and dizziness, similar to motion sickness, due to the constant manipulation of digital signals and glitches.
2.The user is only able to manipulate digital and technological systems, so they may struggle in combat situations that involve purely physical opponents.
3.Glitching their own body comes with the risk of temporary loss of control, causing unintended effects or leaving them vulnerable.
#oc#original character#digital art#bnha#boku no hero academia#mha#my hero academia#bnha oc#character sheet#mha oc#myhero#bokunohero
34 notes
·
View notes
Text
It’s frustrating and disappointing to see nominally social justice-focused eating disorder organizations (like Project Heal and the Alliance for Eating Disorders) support the passing of the Kids Online Safety Act (KOSA). KOSA is opposed by more than 90 civil rights and digital rights groups, including GLAAD, GLSEN, the ACLU, the Center for Democracy and Technology, the American Library Association, and the Electronic Frontier Foundation. KOSA also contradicts the U.N.’s Convention on the Rights of the Child, which states that children should not be subjected to “unlawful interference with [their] privacy.” One of KOSA's main premises — the belief that increased parental surveillance of children’s Internet use will protect children’s mental health — is inherently flawed, and it is of paramount importance for abused and marginalized children that mental health organizations don’t buy into this belief.
This open letter signed by several organizations details the many dangerous implications of KOSA’s overreach. While KOSA aims to protect minors under 16 from the negative effects of social media use (such as “addictive” design features and content that “promotes” eating disorders, self-harm, or substance use), its vague language enables increased surveillance of children’s Internet use, increased data collection on both children and adults alike, and the power for parents and state government officials to decide what content is “appropriate” for children. With some states increasingly legalizing the idea that any kind of content that acknowledges the existence of queer people or the U.S.’s legacy of racism is inherently “inappropriate” for children (by banning books and preventing school curriculums from mentioning these realities), KOSA has the potential to prevent children from accessing these topics online, too.
KOSA is particularly dangerous to marginalized and abused children because of the level of inescapable parental surveillance it enables. Passing KOSA might prevent a 15-year-old from looking up how to report his abusive parents or where to seek help. It might prevent a 14-year-old whose parents will disown her if she’s pregnant from looking up sex education or abortion care. It might prevent a 13-year-old living in a homophobic household from connecting with accepting peers. It might prevent 12-year-olds who are already self-harming or eating unintuitively from looking up harm reduction techniques that could keep them alive. KOSA would not keep children safe or improve their mental health — it would make the most at-risk children even more unsafe, and it would worsen the mental health of anyone living in an unsafe household or state.
I presume that eating disorder organizations are campaigning for KOSA because they believe the unrealistic, fatphobic, and eurocentric beauty standards proliferating on social media are causing and/or exacerbating eating disorders, and they are desperate for any recourse to curtail these harms. But KOSA is premised on flawed understandings of media effects, and it is a dangerous piece of legislation that wouldn’t adequately address the very real harms of social media. Multiple studies have shown that similar content bans and increased parental control have not been effective, and have even made harmful content easier to find. Whatever good intentions eating disorder organizations might have by endorsing KOSA, it is important to note that all evidence points to KOSA harming children, not helping them.
KOSA aims to make social media companies accountable for preventing children from seeing content that “promotes” eating disorders, self-harm, suicide, and substance use. The problem is, social media algorithms are incapable of distinguishing between content that promotes these behaviors and content that discusses these behaviors in a neutral manner or provides harm reduction techniques for making these behaviors less dangerous. As the EFF notes, “there is no way a platform can make case-by-case decisions about which content exacerbates, for example, an eating disorder, compared to content which provides necessary health information and advice about the topic.” We’ve already seen Instagram repeatedly fail at distinguishing between fresh self-harm and years-old scars, censoring and removing pictures of people simply living in bodies that are scarred. If KOSA passes, any mention of the aforementioned behaviors is liable to be censored and removed from social media platforms, which may have the paradoxical effect of pushing children who want community support, neutral information, or harm reduction techniques into more harmful corners of the Internet, such as specifically pro-ED sites.
Moreover, KOSA and the eating disorder organizations supporting it buy into the same harmful narratives of social contagion that anti-queer and anti-trans groups promote so fiercely. The narrative that children uncritically adopt any behavior or identity they see online is egregious and clearly false (especially when it comes to teens, as opposed to 8-year-olds), but of course it is easier to blame social media alone rather than thoroughly examine the systems of injustice, oppression, and abuse that contribute to children’s poor mental health. While online content that promotes self-destructive behaviors is a real harm to children that should be addressed, the way to address this harm is not by mandating governmental and parental surveillance of children’s internet use. It is to equip children with better media literacy, trustworthy adult figures they can turn to for help, and tools for critically evaluating digital content.
Platforms certainly do need greater regulation, and children do need greater protection from social media companies, which don’t care about their mental health as long as they can profit off them. But children need real protection, not KOSA, which is just increased surveillance for everyone under the thin veneer of child protection. I encourage you to read some of the many, many articles detailing the harmful effects KOSA would have. We must demand better for children than surveillance under the guise of “care,” and we must prioritize the children who are already hurting when considering who this legislation would harm the most.
114 notes
·
View notes
Text

The B-21 Raider: Designed For Low Risk
head-on view of B-21
Images released during the week of the Air and Space Force Association’s Air, Space & Cyber Conference revealed a head-on view that allowed for a reliable estimate of the wingspan.
Credit: Northrop Grumman
The design of Northrop Grumman’s B-21 Raider points to a conservative approach on the part of the U.S. Air Force’s Rapid Capabilities Office. The B-21’s resemblance to the original B-2 bomber design is close, but it is a smaller aircraft, with a wingspan estimated at 132 ft. compared with the B-2’s 172 ft., and is approximately half the empty weight. The planform itself is driven by the need to accommodate complex inlets and exhausts and a large weapon bay within the flying-wing profile while staying within a maximum thickness-to-chord ratio compatible with efficient flight above Mach 0.8.
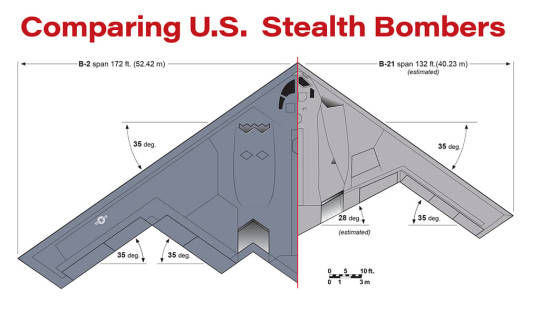
Planform of two bombers
Credit: Giuseppe Picarella/TheCutawayCompany.com
The B-21 planform, which has not been officially released, was depicted in a video that accompanied a presentation by Gen. Duke Richardson, commander of the U.S. Air Force Materiel Command, on Sept. 11 at the Air and Space Force Association’s (AFA) Air, Space & Cyber Conference at National Harbor, Maryland. A new set of images released that week included an undistorted head-on view that permitted a reliable estimate of the wingspan. Recently recovered unclassified imagery from Pratt & Whitney presentations dating back to the early 2010s proved to be a close match for the B-21’s inlets.
U.S. Air Force Rapid Capabilities Office prioritized use of mature subsystems
Northrop draws on aspects of B-2 bomber and X-47B UCAV
The B-21’s low-risk design in part stems from the program’s origins. Before 2009, the Air Force was working to a requirement known as Next-Generation Bomber (NGB). It has been characterized as complex and ambitious, with a full suite of intelligence, surveillance and reconnaissance (ISR) sensors, a self-defense capability and long endurance. This was canceled in April 2009 by then-Defense Secretary Robert Gates.
The following year, the Air Force proposed a different approach to the mission, which Pentagon leadership found acceptable: a Long-Range Strike family of systems including classified uncrewed aircraft systems for ISR and electronic attack (the former becoming the Northrop Grumman RQ-180), a replacement cruise missile (now the Raytheon AGM-181) and the Long-Range Strike-Bomber (LRS-B), for which a contract was awarded to Northrop Grumman in October 2015.
Aside from scrubbed and scaled-back requirements, the LRS-B project differed from NGB in three ways: Unit cost was a key performance parameter; two competing teams were funded through preliminary design review, which normally takes place after contract award; and management was assigned to the Air Force’s Rapid Capabilities Office (RCO). The RCO modeled its approach on the Lockheed F-117, developed using mature subsystems in a new platform so that the program could focus on applying new technology.
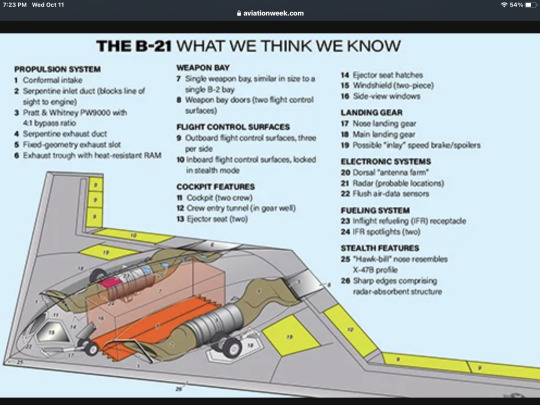
B-21 diagram
Click on this image to see an interactive version of a microcutaway of design features likely on the U.S. Air Force's next stealth bomber.
The B-21 emerging today is evidence that these principles have been adhered to. Its configuration and stealth technology have evolved from the “flying saucer” approach used on the B-2, but originally proposed in the late 1950s. Remarkably, Lockheed Martin Skunk Works founder and former chief Clarence “Kelly” Johnson, in a retrospective paper delivered in 1975 and quoting pre-SR-71 Blackbird work, noted that “a shape similar to flying saucers, with a sharp edge and no protuberances, has a very low radar cross-section without any anti-radar treatment.” And at a February 1959 conference with President Dwight Eisenhower, also discussing the future Blackbird, Harvard physicist Edward Purcell remarked that “the best shape would be a flying saucer.”
No documents found so far have explained the exact connection between the flying saucer phenomenon—the original popular term for unidentified aerial phenomena—and early stealth developments. But one part of the explanation may be that the mysterious craft were often believed to evade radar detection and that it would naturally occur to anyone with knowledge of radar that the shape might have something to do with it.
The classic 1950s flying saucer shape—seamless and continuously curved, with a domed center flaring out to a sharp edge—is visible on the B-21. Some details, though, are reminiscent of the X-47B—the uncrewed combat air vehicle (UCAV) designed by Northrop Grumman—such as the longer nose, or “beak.” This feature is a result of the need for continuous sharp leading edges, but with a curved-down nose to improve stall characteristics. As on the B-2, however, the saucer profile in elevation is matched with a straight-edge planform to concentrate residual radar reflections—reduced by deep-section radar-absorbent material (RAM) edges—in the smallest possible number of “spikes.”
The design benefits from advances in computational engineering and simulation. The B-2 was designed with the help of early 2D computational fluid dynamics (CFD), but airflows on a blended wing body shape are highly 3D with effects propagating from the center-body outward, and more recent designs using 3D CFD are more efficient.
Computational electromagnetics allows for better low radar cross-section (RCS) shapes and more efficient use of RAM and eliminates much of the empirical cut-and-try methods used in earlier programs: Northrop Grumman closed its Tejon Ranch, California, outdoor RCS test range in 2011.
The B-21 is also the first known major U.S. military aircraft program to be fully designed on a digital thread, with not only the shape but the physical characteristics of each part built into a digital prototype. This has allowed errors to be caught early and has made it possible, according to program officials, to incorporate all core systems on the first aircraft.
The differences from the B-2 include the new bomber’s planform. In fact, the B-2 planform at contract award in October 1981 was similar to the B-21’s now, but a low-altitude dash capability was added to the requirement late in its evolution. In early 1983, Northrop engineers discovered that the original design had insufficient control power to alleviate gust loads at the same time as controlling the aircraft, and it was necessary to add control area farther aft, close to the centerline, for rigidity. The fix resulted in the B-2’s unique planform, but at a price in time, weight and cost—and the low-altitude capability was never used.
Some of the features carried over from the X-47B include the apparent absence of split brake-rudder surfaces. Instead, the plan-view sketch suggests the presence of “inlay” surfaces above the wing, which would not be used in stealth mode. Instead, lateral and longitudinal control are provided by eight trailing-edge surfaces, augmented by differential thrust as on the B-2.
The center-body section matches images of highly serpentine inlets mated to a medium-bypass engine. Pratt & Whitney discussed such an engine, the PW9000, as a future bomber powerplant in 2010 but has not mentioned it since. The PW9000 used the core of the PW1000G commercial engine family, mated to a direct-drive fan with a 4:1 bypass ratio. On the B-2, the low-bypass GE F118 engine was selected because it was too risky to place a higher-bypass engine, more sensitive to flow distortion, behind the curved and RAM-treated inlet ducts needed to hide the fan face from radar. With the aid of better CFD, that problem can be eliminated: Northrop Grumman proposed a large bomber UAV in 2005, powered by two modified GE CF34 turbofans, and Lockheed Martin flew the Polecat demonstrator in 2006 with two Williams FJ44s.
Further evidence of innovation in the propulsion installation is that it is one of very few specific B-21 problem areas mentioned in public. Rep. Rob Wittman (R-Va), a member of the House Armed Services Committee, mentioned potential inlet and exhaust issues in March 2018. In March 2021, then-RCO Director Randall Walden said that a redesign was completed before the design was frozen, without affecting the schedule.
A higher bypass ratio provides much better specific fuel consumption than the B-2’s fighter-type engine, improving range, and would enable a cooler, lower-velocity exhaust, not only lowering the B-21’s infrared signature but also alleviating thermomechanical stress on the open “aft deck” area of the exhaust, immediately ahead of the trailing edge.
The B-21’s structure benefits from the absence of a low-level flight requirement and improvements in both composite materials and RAM, reducing the use of fillers and tapes. While the RAM itself would perform the same functions as on earlier stealth aircraft, with multiple layers to absorb energy, diffuse surface currents and protect the skin from lightning, it would require less maintenance than the notoriously finicky B-2 surface.
Internally, the B-21 apparently uses many proven systems. At the AFA meeting, Doug Young, Northrop Grumman vice president and general manager for strike systems, noted that where possible, the company has used commercial components and systems on the aircraft, reducing costs and taking advantage of long-lasting commercial supply networks. Early in the program, one Washington consultant with close ties to BAE Systems disclosed that the electronic warfare system of the B-21 is closely related to the Lockheed Martin F-35’s ASQ-239.
The most important feature of the avionics, however, is an open mission systems architecture. Young compares older systems with adding peripherals to a computer in the early PC age, where “you had to go through a whole rigmarole to make it work.” But the B-21 has standard interfaces and a partitioned architecture where changes to the mission systems cannot affect flight-critical functions.
The B-21 program includes a “software factory,” Young said, which is already developing capabilities beyond the service-entry baseline. And under a program called Spirit Realm, a partitioned architecture is being developed for the B-2 fleet.
After Lockheed Martin and Boeing unsuccessfully protested the Air Force’s B-21 contract award to Northrop Grumman, a consultant to both companies wrote that “there’s a real possibility that the B-21 program isn’t executable at the price the winning team bid—which would mean either big cost overruns or program termination.”
Northrop has warned that it faces up to a $1.2 billion charge on the first five years of low-rate initial production for the B-21 due to inflation-related cost increases not anticipated when bids were submitted in 2015.
But a lesson to be drawn from the B-21’s appearance is that the designers of the B-2 did an amazingly good job “inventing to schedule” while existing materials and subsystems were inadequate and produced a basic vehicle architecture that was still considered the best choice almost 40 years later.
32 notes
·
View notes
Text
Nine Travels 2: You're late.
-Ugh…
Regaining consciousness, Nine's ears perked up as his eyes adjusted to the light shining over his head in the darkness around him.
-Where…?
Feeling an unusual numbness in his arms, he soon realized that they were extended above his head, and when he shook them he found out that they were held by peculiar steel shackles, as were his feet, which were firmly traoped to prevent him from separating them even by an inch.
-What… what is this? – the little fox pulled again and again only to hear an electric screech echo through the room before an invisible force pulled his hand to keep his shackles held over and over again – no, no, NOT AGAIN!
Remembering, due his bad luck, the last time he had been locked up, he couldn't help but hyperventilating for an instant before he had to force himself to take a huge breath of air to calm down.
-Come on Nine, it's not your first time like this, you solved it before and you can do it once more… - trying to divert his attention, he suddenly remembered the events prior to his imprisonment and letting out a loud sigh he shook one of his ears in annoyance - This is what I get for approaching one of those stupid hedgehogs again…
The theory that the blue hedgehog was the cause of his problems made sense with each world he visited and this one seemed to be no exception.
-Well – he murmured resignedly as he took a look at the place – I'll better check the damage to get out of this dump before something else happens.
Although the terrible illumination prevented him from seeing beyond the area where he was chained, it didn't prevent him from discerning the reddish flash of at least two cameras around that kept him under surveillance.
“But how creative…”
Narrowing his eyes, he remained cautiously quiet as he continued to analyze his situation. And when he tried to unfold his tails and a heavy sensation at the tip of them surprised him, he lowered his head as best as his chains allowed him to barely discern how his tails were also well secured with a shiny steel lock anchored with a peculiar bright and translucent chain to the ground.
“So, whoever is behind this is smart enough to notice that my tails are a risk but dumb enough to be incapable to deactivate them… that's useful.”
Once he had all the possible details, the fox started his calculations.
Deactivating the power of his chains was out of the question, to do so he would need at least one of his hands or tails free.
Forcing his tails to unfold to bypass the metal lock? To do that he'll need access to his belt and that was also out of reach.
Fake a fainting? Maybe, if they had made the effort to restrain him and keep him alive, surely his captor needed something from him. After all, it wouldn't be the first time that someone deprived him of his freedom to force him to work in their favor.
And while he was debating whether it would be better to pretend to cooperate with whoever was responsible for his uncomfortable imprisonement or not, the sound of two heavy footsteps hitting the metallic floor put him on alert.
Thus, in the middle of the darkness in front of him, a heavy door suddenly opened dazzling him without notice, forcing him to close his eyes while the metallic footsteps entered the room.
-PRISONER B-457, YOUR PRESENCE IS REQUIRED IN THE MAIN CABIN.
Squinting his eyes and gritting his teeth, the little fox managed to discern the tall, square silhouette of a robot that surrounded him to press a button on the wall that he was unable to see in the darkness.
ZAAPP
At the electronic screech that echoed in his room, the shackles on his hands were released from the ceiling, throwing him to the floor without warning, causing him to fall face first onto the floor.
-Ugh - seeing stars, the fox tried to stand up moments before an invisible force pulled the shackles on his hands sharply, until he collided with one of the hands of the enormous machine, dragging him in the process.
No doubt, those magnetic shackles were proving to be a real nuisance.
-Okay, this is definitely worse than the last time I was a prisoner - he muttered as the robot raised his hand along with him and began his way out of the strange cell.
ZAAPPP
-Ahh!
An electric shock ran through him from the shackles of his hands to the end of his tails, taking the little strength he had left to resist. The points that his captor was accumulating as a cautious person were definitely increasing in an alarming way.
-THIS IS A PREVENTIVE MEASURE, PRISONERS ARE PROHIBITED FROM ANY TYPE OF COMMUNICATION UNLESS THEY ARE IN AN INTERROGATION.
Stunned, the little fox forced himself to remain silent while he scrutinized his peculiar jailer in the light emitted by the lamps of the corridor through which he was transported. That's how he realized, unfortunately for him, that it was not a mere assistance robot.
Although it didn't have all his weapons visible his abdominal cavity had all the marks of containing many more, not to mention the enormous turrets that he carried on each shoulder where the acronym SIGMA was written. Even the legs of the machine seemed to be designed to be anchored to the ground in case of emergency, and its structure clearly demonstrated that it was capable of carrying so many tons that he didn't even want to begin to calculate.
“I guess I'll have to play his game for now…” he thought as he watched other robots cross by him.
They had barely covered a stretch of the place and he had seen lots of other machines roaming the area, some crude and large and others more peculiar like the wasps he had faced previously. And by the time they were in front of a door that was less simplistic than the rest, the little fox took a deep breath, preparing to face whoever had captured him.
When it opened, that was how he managed to see a gigantic command room and in the background the silhouette of a robust human boy who was looking at the holographic monitors with both hands behind his back.
…
Someone with a strangely familiar silhouette.
-DR. NEGA, UNIT E-321 SIGMA REPORTING - the robot reproduced, extending its hand in front and dragging the fox with it - I HAVE WITH ME THE PRISONER YOU REQUESTED.
“Dr. “Nega?” As he watched the figure in front turn around while the holographic screens disappeared, he almost let out a hopeless laugh. “This is a joke, right?”
-And what are you waiting for, Sigma? Leave our guest in the containment unit for interrogation and return to your work.
Excess of weight, ridiculous glasses and a uniform with bad taste in colors.
If it weren't for the fact that he was sure that this was a different world, he would have sworn that this was a new member of the Egghead Council.
He only missed the hair loss.
-AS YOU ORDER, SIR.
The robot dragged him to a metal platform before his shackles released his hand, throwing him into the center of it, and before he could react a strange translucent barrier formed around him like a dome, enclosing him.
Out of the corner of his eye, the fox saw the robot leaving, while he doubted what security measures the egghead walking in his direction would have if he had sent out a machine so dangerous that it could well have served as a bodyguard.
Although if he thought about it, in his current conditions he probably didn't look like a threat either.
-I'm sorry that we have to meet in this way - exclaimed the young doctor with an overwhelmed face, as if Nine had not seen him smile moments ago - but as a scientist to a scientist you know that when someone messes with our creations, the courtesies come last.
Resisting the urge to insult the so-called creations of the guy on the other side of the dome, the fox stood up without paying the slightest importance to his words. Something that he didn't seem to like at all.
-You're the reserved type from what I see, in any other circumstance I could respect that… except in an interrogation - taking a strange device from his pockets, the mad scientist pressed a button before the shackles on his hands, feet and tails abruptly adhered to the platform on which he stood.
Suppressing a growl, Nine looked at the crazy young man as he flashed a wide grin.
-I hope that with that you don't forget your place, fox - he spat in a threatening tone, enjoying the scene while taking a look at his mechanical tails on the ground - you should be grateful that your peculiar ideas caught my attention, that's the only reason why I took the trouble to spare the life of a creature as lame as you.
Nine wrinkled his nose, trying to maintain some composure as he spoke in a sarcastic tone.
-Lame? If you want something lame why don't you give a look at those bizarre flying robots you have, or better yet, that silly suit you're wearing.
-So you can talk after all, that makes things easier, although I suppose it will also be less entertaining - the mad scientist snapped his fingers, to which a mechanical hand came out of the ground, handing him something that Nine could not believe he had in possession – ah! I see that this seems familiar to you – of course it was!, the fox couldn't help but look with horror that was difficult to conceal as his MTC was in the egghead's hands – listen carefully, Fox, the only reason I haven't fried your brain in that booth is because I need details about this invention of yours, so 'talk' already.
Nine pursed his lips without taking his eyes off his bracelet, cursing himself for not having added a security layer to it as he had done for the disassembly of his tails. Diverting his attention to the mad scientist, he decided to test the waters before executing any plans.
-Is that really what caught your attention? A clock?
The so-called doctor narrowed his eyebrows, letting out a slight bored grunt.
-Please, do you think someone of my caliber can't tell a truly high-tech piece when they see it? – he pronounced before pressing a different button on the controller, one that sent a shock that made the poor fox's fur stand on end for a couple of seconds – a simple scan was enough to discover that your supposed watch shows abundant traces of energy different to the chaos energy that roams around this planet, actually there is no matter or antimatter in this universe with those levels and ranges of energy, unless… it is something from a completely different universe, don't you think so?
The boy's words surprised him so much that only an effort of will on the fox's part had stopped him from swallowing. He didn't understand how he had come to deduce that so quickly, but he was sure of one thing, especially after the shock he had just suffered: Confessing what he knew at that moment would only mean that nothing would stop that human from carrying out his constant threats.
-That just… - Nine uttered, trying to catch his breath as he looked mockingly at the other side of the dome -… It just means… that you're so stupid that you can't even run a decent scan on a simple watch…
-Don't try to play with me fox, I don't know how a creature like you could discover it, but my calculations are not wrong - smiling again, the scientist brought his horrible face closer to the dome - you can't deny that neither this bracelet nor you belong to this place, or am I wrong?
-If you mean this garbage dump where we are, of course not…
-I'm talking about another world! A completely different universe waiting for ME to take control!
-…
The fox gritted his teeth and hardened his face in an effort to appear indifferent to the wanna-be doctor mannerisms. And as for the supposed scientist, the lack of an answer finally made him lose his patience and his exalted smile as he pressed the remote control again.
ZAAPPP
PLANK!
Feeling how his arms gave out making him fall again, the little fox remained on the platform trying to recover while the egg-face only let out a frustrated sigh.
-I think this will conclude the interrogation for today, deny everything you want fox, but when I finish with you and confirm my hypothesis you'll wish you'd made good use of my mercy…
ALERT, ALERT!!
A loud alarm preceded a change in the lighting of the room, red lights began to flash while a mechanical voice repeated something that Nine could still discern.
-Now what?!
INTRUDER DETECTED IN THE SHIP, PREVENTIVE ISOLATION IN PROCESS-!
The voice stopped at the same time that the lights went out, and in the midst of the darkness, Nine raised his ears at the disappearance of the constant vibration that the dome around him produced while a pair of furious footsteps walked away towards the area. where he had seen the controls before.
-My system! This… This must be that rodent's fault!…
Watching as some of the holographic panels began to light up, the fox wasted no time and took advantage of the poor light they emitted to crawl off the steel plate before the mad scientist's attention returned to him.
And although a slight sense of relief came when he was finally able to take cover behind one of the computers in the room, feeling the pressure of the shackles on his hands, feet and tails, which had somehow not been deactivated by the lack of energy, reminded him that he was still far from being in a position to regain his MTC, or even his freedom.
“Think, Think Nine! There must be some way to deactivate these shackles…”
KAPOOOW
The roar behind him made him completely forget about his problem, not sure he wanted to know what had caused the explosion and the scandal that had started after he turned around cautiously, in an attempt to see what was happening.
Until a sudden laser flashed in front of his whiskers, convincing him that it was better to stay well hidden until further notice.
-You pathetic rat! How did you manage to bypass my ship's security?!
The voice of the angry scientist followed a series of strident blows that made his heart race. And knowing that he was on a ship that had just exploded didn't make him feel any less anxious.
The tension was so huge that he was not able to really distinguish the scientist's opponent's response, with his heart racing so fast he was not sure he could even continue hearing the roar of the fight behind him.
-Hey, buddy… - uttered a voice that made his fur stand on end, retreating by inertia and dragging his shackles, the fox opened his eyes widely before realizing who it belonged to - hey, don't worry, I'm not going to hurt you.
It was then that he saw a familiar face that he had never thought he would miss as much as in that moment.
That was undoubtedly the naive and kind look that he had seen on different blue hedgehogs throughout his travels, perhaps so much so that even beneath the peculiar black markings on the blue quills of his face it would be impossible not to distinguish who he was.
-You're late… - the little fox said, trying to hide the relief he felt under a false claim – as always
FIRST - THIS ONE - NEXT (Coming soon!)
#rdjsays#nine-tailed travel guide through the multiverse#carbon copy au#I took down the OG one to modify it a little#So here's part 2 again!#tails nine#tails the fox#miles tails prower#sonic and tails#sonic the hedgehog#Sonic#Now that I think about it maybe there were to many zaapps this chapter...#Sorry nine#sonic prime
12 notes
·
View notes
Text
Some quotes from the Mission: Impossible - Rogue Nation script that I can’t stop thinking about (most of these are in the script but did not end up in the actual film or are slightly different in the finished product).
Benji (to Lauren, the lie detector operator): You changed your hair... (laughs) It’s a joke... because you... never change your hair. Or your expression.
****
Lauren: State your name.
Benji: You ask me that question every week.
Lauren: Your name.
Benji: The King of Norway.
His vitals [on the lie detector] fluctuate.
Benji: That was a lie. I’m actually third in line for the throne.
His vitals don’t fluctuate.
****
Brandt: Western civilization is slowly coming apart.
Hunley: It won’t happen on my watch.
****
Ethan (on com): Benji, do you copy?
Benji tries to contain his reaction. He sort of manages.
****
Benji arrives at a service door marked with electronic symbols. He quickly works the lock and slips into a cramped space, humming with electrical conduits. He’s very out of place in a tux.
****
Ethan: Ever have a crisis of faith, Benji?
Benji: More than once. Am I fighting for the right side? Should I really risk my life for a world that doesn’t seem to care?
Ethan: And sometimes the answer is no.
Beat. Benji nods, yes. He’s not proud of it.
Ethan: It happens to the best of us. Of course, most of us come back from that place. But not all.
****
Ethan: If I can bring [Lane] down, I can make everything like it was. Maybe even get you your life back.
Benji: Ethan, I’m back. This is my life. This is what I signed up for. Let me help you find him.
Ethan: That’s why I brought you here, and look what happened. I gambled with your life tonight and I lost. I can’t be sure how this ends. I can’t protect you. That’s why I need you to leave.
****
Luther: Understand something... Ethan is my friend. If I doubt you forone second whose side you’re really on... I’ll take you out.
Brandt considers this, nods.
Brandt: I believe you.
****
Ilsa: [...] I can tell you it’s impossible.
Ethan and Benji share a look. The game is afoot.
****
Brandt: DNA profiling, facial recognition, gait analysis... drone strikes. Drone surveillance. (points) And that guy can even read your vital signs over your home wifi? He knows you have a heart problem before your doctor does.
He shakes his head as if to say: what have we become?
****
Benji: I appreciate everything you’ve done for me but, seriously, one of these days you’re going to take things too far.
Benji tries to laugh. Ethan tries to say something but can’t. Benji’s smile gives way to sincerity.
Benji: I owe you my life, man. Thank you.
****
Benji has a hood ripped off from his head to find himself seated in a chair, in a hotel room with a sweeping view of downtown London. Before him stands Lane, to his side, Vinter. As Benji glares:
Lane: You look like you’ve just seen a ghost.
Benji: You’re not a ghost yet... But you will be.
Lane smiles, leans in to Benji:
Lane: Get him ready, please.
#mission impossible#mission impossible rogue nation#ethan hunt#benji dunn#luther stickell#william brandt#solomon lane#ilsa faust#the script is available as a pdf online in case anyone is interested
113 notes
·
View notes
Text
Whether you call it “tattleware,” “bossware,” or “surveillance capitalism,” Sen. Bob Casey (D-Pa.) has had enough of exploitative workplace monitoring technologies. Late last week, Casey and a handful of other Senate Democrats introduced the Stop Spying Bosses Act, which would help protect workers from intrusive employer surveillance both on and off the clock.
The legislation would require “timely and public” disclosures by companies about the data they’re collecting on employees, prohibit businesses from using surveillance practices that obstruct union organizing or monitor workers while they’re off the clock, and create a new division of the Department of Labor to regulate workplace surveillance. Sens. Cory Booker, John Fetterman, Elizabeth Warren, and Brian Schatz are cosponsoring the bill, which has also garnered support from some major labor groups.
Workplace surveillance has been a growing area of concern for Democrats in the past few years, as the shift to remote work during the pandemic has prompted increased use of employee monitoring technologies. Since the onset of the pandemic, the percentage of large companies that digitally monitor their workers has doubled, to more than 60%. At a time when managers can no longer keep an eye on workers in the office, they’ve increasingly relied on technologies such as keylogger software, geolocation tools that track workers’ physical movements, and even software that monitors worker attentiveness with webcams, using biometric data to scrutinize minute body movements and facial expressions.
Currently, federal law gives workers few protections from these kinds of surveillance practices. The Electronic Communications Privacy Act of 1986 does have some safeguards against workplace monitoring, but it has wide-ranging exceptions that allow employers to keep tabs on virtually all communications for “legitimate business purposes.” Currently, no federal law requires employers to disclose that they are monitoring workers, though individual states are increasingly taking steps to protect workers’ rights. In May 2022, for example, New York passed a law requiring private companies to publicly disclose whether employees will be electronically monitored, following similar legislation in Delaware and Connecticut. In California, a bill introduced last year would eliminate tools like facial recognition and emotion recognition technologies from the workplace.
The National Labor Relations Board is beginning to address the issue at the federal level, too. Last fall, the agency’s general counsel, Jennifer Abruzzo, issued a memo indicating that companies have overreached with their aggressive surveillance. She recommended that the NLRB impose a requirement that employers tell workers about the surveillance tools they use to monitor them, the justifications for those tools, and how they use the information they collect from workers.
In the memo, Abruzzo also acknowledged “abusive electronic monitoring” could interfere with employees’ right to organize a union or engage in other protected labor activities. As I’ve written before, unions around the country are currently in the middle of negotiating how data collected on workers can be used by employers. At companies like Amazon, unionization efforts are being driven partly by a culture of relentless workplace surveillance—and in some cases employers are responding to unionization efforts by doubling down on digital monitoring. Whole Foods, which is owned by Amazon, used heat maps to identify its stores at risk of unionization, according to Insider.
While the bill isn’t likely to pass in a divided Congress, it’s a sign that the proliferation of workplace surveillance during the pandemic is finally getting more national attention. “As the power imbalance in workplaces continues to grow, employers are increasingly using invasive surveillance technologies that allow them to track their workers like pieces of equipment,” Casey said in a statement introducing the legislation. “The Stop Spying Bosses Act is a first step to level the playing field for workers by holding their bosses accountable.”
#us politics#news#mother jones#2023#Sen. Bob Casey#Stop Spying Bosses Act#Department of Labor#workplace surveillance#sen. cory booker#sen. John Fetterman#sen. elizabeth warren#sen. Brian Schatz#keylogger software#geolocation#biometric data#Electronic Communications Privacy Act of 1986#National Labor Relations Board#Jennifer Abruzzo#Democrats
65 notes
·
View notes
Text
Households of Litchfeld: The Elite Forces

Keith Wilkinson, Loundres Lindt & Malcolm Perry.
The Elite Forces are selected from the best of the recruits who have demonstrated exceptional skill, discipline, and leadership potential. These soldiers undergo specialized training that goes beyond the standard regimen, focusing on advanced combat techniques, tactical operations, and survival skills in extreme conditions. As a result, members of this unit are highly respected within the camp and are often looked up to by those still in training.
Keith: Keith Wilkinson is a seasoned and highly capable commando within the Elite Forces. Known for his strategic mind and calm demeanor under pressure, Keith is often the one others look to for guidance during complex missions. He has a natural ability to assess situations quickly and make decisions that optimize the chances of success.
Loundres: Loundres Lindt is the unit’s expert in close-quarters combat and reconnaissance. Agile and precise, Loundres excels in situations where speed and stealth are critical. Her background includes intensive training in martial arts and urban warfare, making her a formidable opponent in any confrontation.
Malcolm: Malcolm Perry is the tech and communications specialist of the Elite Forces. With a keen understanding of technology and a talent for problem-solving, Malcolm is responsible for ensuring that all communications and electronic systems are operational and secure during missions. He is adept at hacking, encryption, and operating various types of surveillance equipment, making him an invaluable asset when it comes to gathering intelligence and maintaining contact during high-risk operations.
6 notes
·
View notes
Text

ANM-486: Headless Mule
"My past condemns me."
Subject Classification: A(cursed)-02(Trauma)-486
(A-02-486)
Identification: Headless Mule
Danger Level: Darlig 🔴 (Public, mental, auditory, physical)
Responsible Researcher: Dr. Octavio Lovecraft
Special Containment Procedures: ANM-486 must be contained in a Level 4 humanoid containment chamber located in the heavy zone. With dimensions of 20m⁴, the chamber must be equipped with reinforced steel walls and doors, a high-security electronic locking system, and fire-resistant materials. Access to the ANM-486 containment chamber is restricted to Level 3 or higher personnel, and all personnel entering the chamber must wear noise-canceling headphones to minimize the risk of ANM-486's auditory influence.
ANM-486 must be monitored at all times through surveillance cameras installed inside its containment chamber. In case of any unusual activity or containment breach attempts, the zone security personnel must be alerted immediately, and recontainment protocols must be activated without delay. The containment chamber of ANM-486 must also be soundproof to prevent the transmission of its auditory effects beyond its immediate vicinity.
Research involving ANM-486 must be conducted with caution and must be approved by the Zone Director and the ANM-486 research team. All personnel involved in the entity's research must undergo psychological evaluation before and after their involvement to detect any potential effects of ANM-486's influence.
Description: ANM-486 is a 17-year-old girl from Canavieira, measuring 1.65m in height, with a dark complexion and long shoulder-length hair, dressed in a long black dress. It does not display any additional anomalous characteristics besides a large cut around its neck. It emits a series of vocalizations and cries reminiscent of a human woman in distress.
ANM-486 can induce intense feelings of fear, discomfort, and terror in individuals who hear its vocalizations. These effects vary in intensity depending on the proximity of the affected individual to ANM-486 and the duration of exposure. Prolonged exposure to ANM-486's auditory influence can lead to severe psychological trauma, including hallucinations, paranoia, and suicidal ideation.
Every full moon night, ANM-486 assumes a secondary form, becoming extremely more aggressive and difficult to contain: ANM-486-1, which resembles a common domestic horse but without its head, with flames constantly emitted around and from the neck area.
ANM-486 was discovered near a cabaret in Bahia. Off-duty MOTHRA agents engaged in combat with the entity, causing widespread panic for several minutes. After the entity was neutralized, it reverted to its human form, and successful containment was achieved. Amnestics were administered to witnesses to maintain secrecy regarding the existence of ANM-486, and a cover story involving a "general brawl" was fabricated.
Research on the origins and nature of ANM-486 is ongoing, with a particular focus on its connection to Brazilian folklore and the legend of the "Headless Mule."
#mothra institution#project#scp#scp foundation#site#writing#anomaly#art#horror#creepypasta#urban legend#folklore#brazilian folklore
2 notes
·
View notes
Text
Even as its members take part in Steadfast Defender 2024, NATO’s largest military exercise since the Cold War, it is clear that the alliance remains ill-prepared against Russia’s military capabilities in the Arctic. The exercise, which runs between January and May, involves more than 90,000 troops across the Atlantic and up to the Arctic and suggests that NATO has a strong and capable defense presence in the region.
However, a closer look at the capabilities of the Arctic states—which are all NATO members except Russia—reveals otherwise. Finland and Sweden’s recent membership in NATO has been heralded as a turning point in deterrence against Russia in the north. However, the countries’ proximity to northwest Russia means that their strategic focus is primarily targeted at the Baltic Sea region, where Russia has pursued a military buildup directed toward NATO’s eastern flank.
No NATO member state has ice-strengthened ships with both anti-aircraft and anti-submarine capabilities. The United States, Canada, Denmark, Finland, and Sweden have prioritized capabilities designed for other theaters, such as the Indo-Pacific and the Baltic Sea regions. Iceland, which has no standing army, only operates coast guard vessels. Norway has ice-strengthened coast guard vessels, but they are not designed for military operations.
Russia’s nuclear submarines, which are capable of launching an attack on North America, can travel from the Barents Sea through the Bear Gap between Scandinavia and Svalbard, Norway, and under the ice along the coast of eastern Greenland without being detected. This leaves big gaps in NATO’s defense posture. Russia’s war in Ukraine also gives it incentives to work with China in the Arctic, including joint naval exercises and coast guard cooperation.
NATO should not let Arctic deterrence fall by the wayside by concentrating its force posture along its eastern flank. Instead, the trans-Atlantic alliance must act urgently.
Russia’s 2022 naval doctrine raised the Arctic region to the highest priority. Between its invasion of Crimea in 2014 and 2019, Russia built more than 475 military facilities in the Arctic. Its Northern Fleet, located in the Barents Sea, accounts for around two-thirds of the Russian Navy’s nuclear strike capabilities. A multilayered network of sensors, missile systems, coastal defense systems, and electronic warfare technology protects these capabilities, including the strategic submarines.
Despite NATO Secretary-General Jens Stoltenberg sounding the alarm in 2022, the alliance lacks an Arctic strategy. Its current area of responsibility extends only to the “High North,” a less ambitious term that describes the ice-free parts of the Arctic. The term is indicative of disagreement within NATO over whether its remit goes beyond the North Atlantic.
As glaciers melt, more countries from outside the region are engaging in the Arctic, which risks further crowding the Northern Sea Route and incentivizing Russia to protect the entry and exit points to its military bastion.
Russian vulnerabilities in the Arctic have affected its strategic cooperation with China. On the one hand, Russia needs to cooperate more with Beijing—in areas such as digitalization; infrastructure; and intelligence, surveillance, and reconnaissance—to utilize the economic potential of the Northern Sea Route and protect its strategic assets. On the other hand, Russia is concerned with maintaining control of its Arctic coastline.
Moscow will cooperate with Beijing if this red line is respected. Although access to Russian facilities and ports will allow China to use its military capabilities in the Arctic, including icebreakers and semi-submersible vessels, Beijing has little interest in becoming a military power in the region. Decades of strategic coordination in Central Asia and in the Korean Peninsula have proved that China understands the benefits of not undermining Russia, even if Moscow’s geopolitical agenda is not always to Beijing’s liking.
Despite Chinese concerns over Russia’s war of attrition in Ukraine and its military-strategic cooperation with North Korea, Beijing benefits from Moscow maintaining a strong force posture toward NATO. This is especially true in the case of the Arctic, where a permanent Chinese presence would open a new front with U.S. allies at a time when Beijing is already engaged in hot spots in its own backyard.
The supply line that runs through the GIUK gap—the strategically important entrance to the North Atlantic between Greenland, Iceland, and the United Kingdom—is a vital route for U.S. and Canadian forces to deploy and send supplies to northern Europe in the event of military conflict with Russia. Moscow can currently disrupt this supply line without NATO intervention because the Nordic states in the Arctic do not have capabilities to detect Russian forces operating in the Bear Gap and off the coast of eastern Greenland.
This mismatch underscores how countries such as Norway and Denmark have limited defense budgets but major responsibilities—including manning the Arctic and Baltic regions as well as, in the case of Norway, a land border with Russia.
Such budget constraints explain the reluctance to acquire the expensive capabilities to take on responsibilities that should fall to all Arctic NATO member states. But the widespread unwillingness among all members to invest in Arctic capabilities is easily explained: NATO has focused on pushing member states to spend 2 percent of GDP on defense, and investments in capabilities such as ice-strengthened navy vessels do not count as contributions to NATO’s minimum force requirements. That comes at the cost of Arctic security, which Russia is willing to exploit.
Amid heightened tensions with Russia, it is important that NATO does not ignore Moscow’s threat in the Arctic. This is not to say that trans-Atlantic allies should engage in a massive military buildup that risks provoking a Russian military response. Russia is likely to interpret freedom of navigation operations from states that do not border the Arctic Ocean, such as the United Kingdom, France, and Italy, as an escalatory NATO presence from states that lack legitimate obligations to patrol the Arctic.
A Russia that perceives itself as vulnerable in the Arctic may respond more forcefully than is desirable from NATO’s perspective. This points to the need for the United States, Canada, Denmark, and Norway to take on more responsibility for deterrence in the region by focusing on the areas adjacent to their sovereign territories.
As it marks its 75th anniversary, NATO should come to an agreement on an Arctic strategy. For starters, it should revisit and update its minimum force requirements and allow members states to count the development of special capabilities, such as ice-strengthened frigates, as contributions to the NATO spending targets. As U.S. leaders increase pressure on other NATO member states to meet the defense spending target—ultimately requiring those states to cancel other investments in areas such as public welfare—few states can justify taking on defense expenses that do not count as part of the minimum force requirements.
Although Finnish and Swedish membership has seemingly enhanced NATO’s Arctic posture, the alliance still has a long way to go in the region. NATO must increase its footprint in the Arctic to credibly deter Russia’s military force posture.
3 notes
·
View notes
Text
This day in history

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me TOMORROW in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

#20yrsago "Homeless Hacker" Adrian Lamo profile in Wired https://www.wired.com/2004/04/hacker-5/
#20yrsago Disney asks Gizmodo to clarify that jewel box is not intended for pot stashing https://web.archive.org/web/20040402032317/http://www.gizmodo.com/archives/disney_princess_cd_jewelrystash_box.php
#15yrsago To Market, To Market: The Re-Branding of Billy Bailey – my sf story read aloud https://archive.org/details/ToMarketToMarket
#15yrsago Electronic Arts releases DRM-removal tool https://games.slashdot.org/story/09/03/31/1917254/ea-releases-drm-license-deactivation-tool
#15yrsago Adventures in Cartooning: wit and instruction for kids who want to learn cartooning https://memex.craphound.com/2009/03/31/adventures-in-cartooning-wit-and-instruction-for-kids-who-want-to-learn-cartooning/
#10yrsago Podcast: Collective Action – the Magnificent Seven anti-troll business-model https://ia902808.us.archive.org/10/items/Cory_Doctorow_Podcast_270/Cory_Doctorow_Podcast_270_Collective_Action.mp3
#10yrsago Google Maps’ spam problem presents genuine security issues https://web.archive.org/web/20140331101332/http://www.businessweek.com/articles/2014-03-28/how-scammers-turn-google-maps-into-fantasy-land
#10yrsago NSA wiretapped 122 world leaders; GCHQ penetrated German satellite companies for mass surveillance potential https://www.spiegel.de/international/germany/gchq-and-nsa-targeted-private-german-companies-a-961444.html
#10yrsago Playground removes “safety” rules; fun, development and injuries ensue https://nationalpost.com/news/when-one-new-zealand-school-tossed-its-playground-rules-and-let-students-risk-injury-the-results-surprised
#5yrsago Small stickers on the ground trick Tesla autopilot into steering into opposing traffic lane https://keenlab.tencent.com/en/whitepapers/Experimental_Security_Research_of_Tesla_Autopilot.pdf
#5yrsago Banksy’s art authentication system displays top-notch cryptographic nous https://reprage.com/posts/2019-03-25-how-banksy-authenticates-his-work/
#5yrsago The Boston Globe on breaking up Big Tech falls into the trap of tech exceptionalism https://memex.craphound.com/2019/03/31/the-boston-globe-on-breaking-up-big-tech-falls-into-the-trap-of-tech-exceptionalism/
4 notes
·
View notes
Text
school stuff. electronic surveillance, anti-queer stuff, ableist language references (r-word)
but really, the best thing that happened today was that i gave the sixth graders my you are being spied on electronically talk, bc they just got their computers. i tell them all about the spyware teachers use and how it works (and show them, which is really fun, and they have SO many questions), and, most importantly—and this is the reason i do this—that their parents and guardians can also use this spyware on their school computers, and unlike teachers can do it at any time, not just at school. i explicitly tell them that i am telling them about what their parents/guardians can do because i don't want them to get hurt if they are searching up stuff like "how do you know if you're trans/gay/queer" etc. and then i say that, regardless of what their parents or guardians might say or think, that there is nothing wrong with being gay, queer, trans—i'd already gone over what all the terms meant, bc we have a part in the syllabus about not being shitty to ppl bc of their identities*—and that we have books in the library and in the classroom (and i show them where the books are and also pass them around) about being queer and queer people.
i fight with myself a lot about this. i've done it every year i've taught, though. i don't, of course, think it's wrong to do any of this. i think it's kind of like when you're really sick and you know you have to stay home but you don't want to but you do it anyway, of course; you were never going to not do it, but you have doubts mainly because of how important it is. i know that i really have to do this, but i could face pretty serious consequences for doing it. i work at an incredibly liberal and open district with a frankly amazing pro-queer teacher/staff/student policy, but if parents get mad about something, regardless of whether or not it's school/district policy, it can get messy. i have been told not to do things that i have a right, per my union contract, to do, but doing it anyway puts one's job at risk. so you have to be careful. it always makes me nervous but every single time i do this, the kids get it. they say they get it. a lot of them have talked about it with me further.
*there's this article i found in grad school and havent read since so idk whether or not to still vouch for it but this paragraph was really important to me, formatively, as a teacher. i have to say that ending it with the phrase "teachable moment," which is the number one worst term on the entire planet, makes me want to die for sure, but hey.
article: Brian M. Payne (2010) Your Art Is Gay and Retarded: Eliminating Discriminating Speech against Homosexual and Intellectually Disabled Students in the Secondary Arts Eduation Classroom, Art Education, 63:5, 52-55
I posted the following disclaimer under the “Class Expectations”
on the front page of my Art I syllabus I gave my students the
first day of class:
I expect each student to be able to work in an environment
that is void of any slurs or derogatory comments that
demean another student. This includes comments pertaining
to their style of dress, race, gender, or sexual orientation.
There is absolutely no tolerance on this issue. (Payne, 2009)
After reading aloud this section of the syllabus I could tell that
my words may not have been absorbed by the group of 14- to
18-year-olds that sat in front of me. I followed by stating, “This
includes words such as ‘gay’ and ‘retarded.’” The students, most
of whom I assumed perked their heads up either because they
were guilty of such rhetoric, or simply not accustomed to
hearing a teacher use these words in the same sentence, were
now paying attention. Instead of simply making a disclaimer and
moving on to the next section of the syllabus, I used this
opportunity to create a teachable moment out of the situation.
3 notes
·
View notes
Text
Australia has decided to examine and remove Chinese-made surveillance technology used in government buildings.
Defense Minister Richard Marles on Thursday said the Chinese-made cameras could pose a security risk for the country.
Two companies, Hikvision and Dahua, have provided at least 913 cameras, intercoms, electronic entry systems and video recorders in over 250 Australian government buildings.
Both companies are partly owned by the Chinese government.
"We would have no way of knowing if the sensitive information, images and audio collected by these devices are secretly being sent back to China against the interests of Australian citizens,'' said shadow Minister for Cyber Security James Paterson, who requested the audit.
The checks came after Britain in November announced that it would stop installing Chinese-linked surveillance cameras in sensitive buildings.
Some US states have also banned vendors and products from several Chinese technology companies.
Hikvision rejects claims of security threat
An audit found that equipment from at least one of the two companies was present in almost every government department, except the Agriculture Department and Department of the Prime Minister and Cabinet.
Paterson urged the government to "urgently" come up with a plan.
Defense Minister Marles said that issue was significant but added "I don't think we should overstate it."
Hikvision said that to represent the company as a national security threat is "categorically false," as it cannot sell cloud storage, access the video data or manage databases of end users in Australia.
"Our cameras are compliant with all applicable Australian laws and regulations and are subject to strict security requirements," said a spokesperson of the company.
Dahua Technology has not yet responded.
China urges "fair" treatment
Beijing on Thursday accused Canberra of "misusing national might to discriminate against and suppress Chinese enterprises."
"We hope Australia will provide a fair, just and nondiscriminatory environment for the normal operations of Chinese enterprises," said China's Foreign Ministry spokesperson Mao Ning.
According to Paterson, both companies are subject to China's national intelligence law which requires them to cooperate with Chinese intelligence.
In similar cases, China's general response to such situations has been to defend their high-tech companies and present them as good corporate citizens who play no part in intelligence gathering.
#nunyas news#we are ideological foes china#and you are far from trustworthy at the best of times#we're not any different so let us spy on ourselves for a bit
7 notes
·
View notes