#security shield software
Text
Finally opened up my new phone and ported everything i need over but I've been using my current one for almost 6 years and im having a little grieving goodbye party
#my android and it's hyper outdated software#bc it's a huawei and banned and i have been scared to update it too much#lest the western overlords go NO MORE GOOGLE FOR U#anyway it has effectively shielded me from all the horrible ugly twitter updates#i opened twitter on iphone and went oh god no please no GOD NO PLEASE NO#i did switch to iphone bc i was tired of my phone being a walking target for malware#and that time a coworker made me install some weird ass certificate on my phone#was what made me go okay fuck u i need something with so much security--#anyway i love my huawei a lot it's a good fking phone#also more importantly ig the screen has been cracked for the last month or so but like#potato potato it still works >:'/
25 notes
·
View notes
Text
#company#business#safe#privacy#creative#power#protection#shield#guard logo#security logo#brand identity#graphic design#branding#abstract#logo design#app logo#modern logo#logo designer#logo#software#product design
2 notes
·
View notes
Text

Privacy by Artology ✅ https://lnkd.in/g85-RGqP
Lets work together:
Say Hello: [email protected]
#privacy#logos#security#software#tech#technology#business#logodesigner#protection#plogo#shield#monogram#modern#gradientlogo#logo deisgn#creative logo#modern logo#minimal logo#artists on tumblr#creative#logomaker#logo
2 notes
·
View notes
Text
Fate's Plans (Wanda Maximoff X Male!Reader)
Characters: Wanda Maximoff X Male!Reader
Universe: Marvel, Avengers (Takes place sometime after AOU)
Warnings: Pregnancy, vague mentions of birth, bit of swearing
Could you write Wanda x male!reader, it’s just fluff really if that’s ok. Wanda and the reader find out they’re pregnant and the fic’s about their time throughout the pregnancy and after their child is born. Maybe the reader kinda freaks out a bit and Wanda finds it really funny/cute.

There were a lot of people who believed that finding true love was an act of fate. If it happened to you, you’d know immediately, and it would become a story to tell your kids and grandkids beside the person you were destined to grow old with. Wanda was one of those people. She believed with all her whole heart that her parents' meeting was fate, even if it meant that they would die young, leaving behind her and Pietro. However, she also believed that this fate wasn’t ever going to happen to her. Life was too cruel- why would life beat her down so hard so far just to throw her a bone now? And she was okay with that. She believed this so hard, that it actually took her a while to realise that she was wrong. Fate did have other plans for her, and the love of her life was already with her.
Wanda only realised it was you, was when she watched you excitedly calling her name repeatedly, getting a little quieter as you got close and closer, beaming as you proceeded to hand her a cloth bag that fit in her hand, and watched excitedly as she opened it, finding several stones, shells and even sea glass, and you went on to explain that on your PTO (Because you’d gotten injured on a mission and should have been resting) you’d gone to the coast with some family and gathered some trinkets because you thought she’d like it. She didn’t like it. She loved it, and she loved that you had thought of her and did this. That’s why immediately after, she asked you to dinner, and your eyes widened, not expecting that, before stuttering out an acceptance.
She was surprised it took her so long for herself to realise how special you were. You were an agent of SHIELD, and had been for two years, starting just a year after Wanda became an Avenger. Being young, and a rookie, you got a lot of teasing, especially from people like Clint and Tony, but you took it all in your stride and with a smile. You were always kind, eager to help, which on first appearance made you appear a bit of an airhead or gullible, but oh boy, was that wrong- Tony learnt that the hard way, when he tried to prank you by putting you in charge of checking over his security software for any faults, bugs, or cyber attacks, him already having it planned out for you to be overwhelmed and for FRIDAY to mimic an actual attack to scare you, only for you to handle it, and actually catch a bug in the system. All of which you announced to Tony in front of several other Avengers, including Wanda. Not long after, you ended up being assigned on a mission with Natasha, Clint and Steve, and come back with the three gobsmacked, and then tell a story of you being the most competent and well trained agent any of them had actually worked with. That kind of complimentary talk really boosts you up the ranks, it turns out, and soon Wanda was able to see it first hand.
But out of missions, you were that kind, slightly silly person. You always asked about her day, complimented her on her recent mission, and eventually, you began giving gifts- getting her coffee in the morning, then also a bit of breakfast, then snacks, and eventually your gifts moved from food and drinks to finding DVDs of obscure movies she mentioned wanting to watch again, or fixing things for her in your down time. Your sewing skills on her cardigans and skirts were far from professional, but they worked as intended, and it was a lovely gesture. Wanda practically slapped herself when she realised these were your ways of trying to show you liked her.
As soon as you two actually started dating, everything just clicked. Your acts of love and affection didn’t slow down at all, except now the coffee and breakfast was something you grabbed together, you kept her favourite snacks at yours for when she came over, and she did the same for you, and dates between you was basically anytime you two got to be alone together- which was whenever you two had time after work, or after a mission, where you two just cuddled and relaxed after it all. The only real problem was the part where you two would be at work and be teased by your team for being kids in love, but it was all in good fun. The team was fully supportive. They saw how happy you made Wanda, and how well you two clicked. It was worth the aww’s and teasing whenever you told each other you loved each other or shared a look across a room. This did get a little better though when you two actually moved in together a year and half into your relationship, though now the team would regularly question when you two were gonna get married already.
Imagine the team's surprise when Wanda announced that she was going on desk work for the next few months- because you two were having a baby.
“You know, there’s still time for a shotgun wedding.” Tony commented, walking past Wanda as she was sitting reading a mission report, also enjoying some baby carrots, the bowl balanced on her belly that had grown a lot the last few months.
“Not happening Tony. Knowing my luck, I’ll go into labour while saying my vows.” She commented, not looking up.
“You don’t even have to walk down an aisle or anything- we get you a white dress, get Y/N in a suit- can’t Captains officiate weddings? I own boats, that counts, right?” Tony questioned.
“Tony, we know you just want another party. I have no clue how you’re still functioning after what you pulled at the baby shower.” Natasha commented, coming in the room to give Wanda new forms, before taking the ones from her. “Now leave her alone, before I tell Clint.” She warned. Tony raised his hands in surrender, before leaving the room. “Now you.”
“I haven’t done anything.” Wanda defended.
“Other than you’re supposed to be working from home? You’re due any day now.” Natasha pointed out.
“Exactly- Y/N got dragged off to that mission the other day and isn’t back yet- if I go into labour at home, I’m by myself.” She pointed out.
“And if Y/N finds out you’re not following doctor’s orders, he’s gonna be irate.” She pointed out. Wanda knew she was right. Ever since Wanda had shown you the test results, you somehow became even more affectionate, even more loving, but also now protective. You always tried to not be overbearing on her and get on her nerves- she was the one actually going through it after all. You made sure her snack stash, which adjusted to her cravings, was always well stocked. As the pregnancy progressed, you switched chores- her doing any that she could do with minimal moving or while sat on a stool, and you did anything that would cause her any back pain. You set the nursery up together, you doing the painting, and Wanda put together most of the furniture, not having to do any heavy lifting thanks to her powers, though every few weeks you could come home to the nursery reorganised because she wasn’t happy about some aspects of it- the cot too far away from the door, the chair too far away from the cot, the cot and chair are too close together. Eventually she settled on a layout.
When Wanda entered her 3rd Trimester, was when you became a true worrier. If she showed any discomfort, you were by her side to try and help, and with every day closer to the due date, Wanda could tell you were getting more anxious- she blamed all the books and research you did pretty early on in her pregnancy, which led you down a rabbit hole about risks and worst case scenarios, though you didn’t want to talk about it with her- as to not worry her. That stress really showed when you found out about your current mission, and Wanda saw you actually raise your voice at Fury for sending you on it, knowing the situation. In the end, Fury could not reassign who was on the mission, but he did extend your leave after the baby’s birth by 2 months. Wanda promised to keep the baby in till you came back, and Natasha, Clint and Bruce promised to look after Wanda and also to keep Tony on a leash.
“Have you heard anything from them on how the mission’s going?” Wanda inquired, trying to change the subject.
“Got a vague text from Steve saying ‘nearly done’ early this morning, but other than that, nothing, but knowing how effective Steve, Thor and Y/N work together, I’m expecting them back tonight.” She told Wanda. “In other words, you have until tonight to get home, or I'm telling.”
“I can handle Y/N being a little annoyed at me being here- I want to see him as soon as he gets back, not a second longer.” Wanda decided, resting her head back in her chair. Natasha felt a buzz in her pocket, pulling her phone out, before grinning and putting it away.
“Well better get moving- they’re already landing.”
You were exhausted from the mission, but eager to get off the jet and get to Wanda. You didn’t like the idea on her being alone, both in the day and at night while due any moment- you heard a lot of labours start at night, and you’d had a nightmare while on your mission of Wanda waking up in the middle of the night with contractions, no one answering her calls because they were asleep, and an ambulance not getting to her for hours. You didn’t want that, so the best spot for you was by her side.
As soon as Steve landed the plane, you were off it, stripping off harnesses, belts and gear as you walked, rushing inside the building for the quicked debrief which you planned to mostly consist of ‘I’ll do the paperwork later’ talk, only to spot Wanda shuffling towards you, right beside Natasha, who sent an apologetic smile. You dumped your gear on the spot and ran to her. “You okay? What are you doing here? You’re supposed to be resting.” You fussed, taking Wanda in your arms, seeing her face for any discomfort- any sign she was having contractions or in labour- but she just smiled back at you.
“Figured me being here meant having people around, so even if I went into labour, I wouldn’t be alone.” She pointed out. You sighed, your shoulders relaxing, the comment actually soothing that horrible thought that had been haunting your dreams. It was almost like-
“Have you been reading my mind again?” You asked her.
“Only when your thoughts are so loud, I can hear them without telepathy. You worry too much, my love.” She told you, resting her hand on your cheek.
“And now that you’re home- go take her home before we have to have Bruce deliver your kid- I’m not sure if Bruce could handle that stress. I’ll handle the debrief and Fury. Enjoy your last few days of peace for the next few years.” Steve commented as he walked past you both. You jokingly saluted him, and did as told.
As soon as you got home, got Wanda settled and got the chores done that needed to be done, you joined your girlfriend in your bed, putting on one of the old DvDs of an old sitcom Wanda loved that she got you addicted to as well. “Tony giving you any trouble?” You asked.
“Other than wanting us to have a shotgun wedding so he can get as wasted as he did at our baby shower? No… how did he even get that drunk?” Wanda asked.
“If I had to guess… Thor and his flask of Asguardian alcohol. But then again I wouldn’t put it past him to figure out where we ordered our chocolates and got alcohol laced ones and ate them all to himself… can you imagine him getting drunk at our daughter’s Christmas Nativity? Or her toddler ballet classes?” You humoured, making Wanda laugh.
“Oh, I think you mean our son’s Christmas Nativity and his toddler ballet classes. This, is a boy.” She said, tapping her stomach.
“Hmmm, I still think for a girl, little Wanda Jr.” You told her, leaning over to kiss her bump.
“If it is a girl, we are not calling her Wanda Jr.” She grinned, and you hummed. “You sure you’re okay with Pietro for a boy?” She asked.
“Of course I am. Has been since we talked about it 6 months ago. Hell if it is a girl, we can have Petra, or something.” You suggested, wrapping an arm around her. “I wish I could have met him. I bet he would have been the best uncle… and also he’d join Tony in the shotgun wedding idea.” You commented, making her chuckle.
“Yeah, he would… I think he’d love you though, he’d want us to marry just to gain you as a brother.” She added. “Anyway, one episode, then bed, I’m tired from looking at paper all day, and don’t lie to me about being tired yourself.” She told you. You agreed to that, but ended up falling asleep not even half way through.
However, you did wake up to Wanda shaking your arm. “Hmm? Yeah? Need water? The bathroom?” You asked on autopilot, before you became more aware of your surroundings, realising Wanda was already out of bed… a bed, that was wet.
“Get dressed and take me to the hospital- my water broke.” She told you, keeping her voice low as she brushed her hair out before clipping it back. You stared at her, processing her words, before it clicked. Hospital. Water. Broke. Labour. Baby. Now.
“Oh fuck we’re doing this!” You announced, jumping out of bed, rushing to grab clothes from your drawers to get dressed, while Wanda watched you, happy in her pyjamas, slippers and dressing gown as you hurried to get half decent, before grabbing her to-go bag from the chair in the corner, taking her by the arm and escorting outside to drive her to the hospital. “Let me know when you feel a contraction- have you felt any yet? Have you timed them? Your water breaking means it’s gonna speed up.” You requested as you drove.
“Had a few in bed- thought they were braxton hicks, but then my water broke, so I woke you up. I wasn’t timing them, but I will now- hold on.” She said, her voice becoming strained as she grabbed the door and your arm, and you pulled over and looked at her. “No, drive! Contraction!” She ordered.
“Oh! Right, sorry!” You apologised, taking off again. Wanda already knew this was going to be an experience, and a story to tell later with you right there.
Boy was she right. From getting there, to getting her checked into the maternity ward, all attempts to hold back on being dramatically worried was forgotten. At all times, you had some sort of contact with Wanda, whether that was holding her as she walked around, letting her squeeze your hand through contractions, rubbing her back to help with pains, or hugging her and telling her she was doing amazing, you were there. You were there every step of the way, all attention on her, checking in on her, making sure she was as comfortable as she could be, and being a rock. You made the whole thing go as smoothly as they could, and Wanda was thankful for that. She wasn’t sure she could do it without you. But eventually, it was over, and she had her baby in her arms. She looked over at you, sat beside her, arms leant on the siderails, looking at your daughter, mesmerized, before looking up at Wanda. “She’s so small.” You whispered, making her smile.
“Get over here and hold her, you dork.” She told you, shuffling over as much as she could so you could partially lay with her, taking your daughter in your arms, and looking down at her, before once again turning to Wanda, this time kissing her head.
“My girls. My beautiful girls, my whole world.” You told her, and she smiled, resting her head on you as you got comfortable with your baby, who was sound asleep in your arms, like she’d been the one doing all the hard work. “I knew you were a girl. Dreamt about it all the time- my little girl who looks just like her beautiful mom.” You told the baby in your arms.
“So, what are we naming her? And don’t say Wanda Jr.” She questioned.
“Thought we already agreed? Petra, right? Unless you want that as a first name, in which case, we could do what Clint did for you and name her after him. What’s the female version of Clint? Clinton?... Cli-”
“Don’t finish that thought, you’re too sleep deprived. Petra’s fine.” She told you, already seeing where exactly you were going, even if you didn’t. “Anyway, you should probably go tell the others- let Tony know a shotgun wedding is no longer an option but he can throw a party anyway.” She told you.
“Alright, I can do that. Want me to put our baby down to sleep so you can get some rest? I’ll make sure they don’t come around till late morning.” You told her, kissing her head as she nodded, and you put Petra in her cot beside Wanda.
“And as soon as you’re done, get back here, I want more hugs, even if it’s cramped.” She told you, getting a playful salute like how you had done to Steve earlier, before you grabbed your phone to step out and share the good news. Wanda rolled onto her side to look at her daughter, reaching out to put her arm into her cot, running a finger across her cheek.
Hope you like it! I wrote this in about 2-3 hours in one sitting so if there's mistakes please let me know. If you have any questions, please send them in!
*Not my gif
TAGS: @klanceiscannon14 @marvelhoeingismyhobby @bellamyblakemorley @dummiesshort @freyathehuntress @abbybills22-blog @mutantjediavenger @theoraekensnotsosecretlover @alicedanganh @sleutherclaw @sleepy-coffee-bean @stawwpp @rebellionofthecattle @hello-love-youre-pretty @werosemagic @courtneychicken @graysonmalfoy @bellero@originalpottervengerlock @supernatural-pan @esoltis280 @lady-of-lies @lenaswritingandstuff @macbetheliza @mandywholock1980 @cdwmtjb8 @caswinchester2000 @determinedpines @huntheimpossible @automaticbakeryfreakshoe
#Marvel#Avengers#wanda maximoff#scarlet witch#captain america#steve rogers#iron man#tony stark#bruce banner#hulk#Pietro maximoff#quicksilver#natasha romanoff#black widow#thor#wanda maximoff x reader#wanda maximoff x male!reader#x reader#x male!reader#reader#male!reader#one shot#story writing#writing#question#ask questions#ask me anything#send me anything#send me questions#send me stuff
177 notes
·
View notes
Text
黒影 (Kurokage)
Reading time 3:00 min
General Description
黒影 (Kurokage) is a top-tier operational unit within Kage Corp, a corporation renowned for its clandestine and high-stakes approach to corporate dominance. Specializing in cybersecurity, hacking, counterintelligence, espionage, counter-journalism, and counter-propaganda, 黒影 (Kurokage) executes missions with surgical precision. Its members are handpicked for their exceptional skills and undergo rigorous training, preparing them for the most critical and covert operations.
Composition of 黒影 (Kurokage)
The operatives of 黒影 (Kurokage) come from diverse and highly specialized backgrounds, including:
Former Combat Operatives
Some members are former field operatives who were wounded in combat. These individuals possess invaluable field experience and tactical knowledge. After recovery and extensive retraining, they are reassigned to 黒影 (Kurokage) where their expertise is crucial in planning and executing complex missions.
Servants and Clones of Kage Corp
Other members are meticulously engineered clones or highly loyal servants of Kage Corp. These operatives are designed or conditioned to exhibit unwavering loyalty and precision. Clones, in particular, are genetically enhanced to excel in specific tasks, ensuring the unit has the optimal mix of skills and abilities.
Main Operations of 黒影 (Kurokage)
Cybersecurity
黒影 (Kurokage) employs advanced cryptographic methods and artificial intelligence to shield Kage Corp's digital infrastructure. Utilizing a multi-layered security approach, they detect and neutralize threats in real-time, ensuring no breach goes unnoticed. They constantly evolve their defenses, employing techniques such as polymorphic encryption, adaptive threat modeling, and quantum-safe algorithms.
Hacking
黒影 (Kurokage) infiltrates competitor networks with unmatched precision. Their arsenal includes custom-built malware, zero-day exploits, and sophisticated social engineering tactics. They extract trade secrets, R&D data, and other strategic assets, giving Kage Corp a formidable edge. Each operation is meticulously planned, often involving multiple stages of infiltration and exfiltration to avoid detection.
Counterintelligence
Identifying and dismantling internal and external espionage threats is a cornerstone of 黒影 (Kurokage)'s operations. They deploy surveillance technologies, behavioral analytics, and human intelligence to uncover corporate spies and rival agents within Kage Corp. Once identified, these threats are neutralized through both technological and psychological means.
Espionage
Gathering critical information from competitors and government entities, 黒影 (Kurokage) uses infiltration and data manipulation. Their operatives are experts in covert entry, cryptography, and digital camouflage, often leaving no trace of their activities. They utilize advanced steganography and deepfake technologies to manipulate and conceal the data they exfiltrate.
Counter-journalism
When journalists threaten Kage Corp's reputation, 黒影 (Kurokage) intervenes by spreading disinformation and manipulated truths. They use advanced narrative analysis to identify vulnerabilities in journalists' stories and exploit these weaknesses through coordinated misinformation campaigns, often using deepfake videos and fabricated evidence to discredit their targets.
Counter-propaganda
黒影 (Kurokage) crafts and disseminates content that enhances Kage Corp's image while undermining its rivals. Utilizing social media bots, AI-generated content, and sophisticated narrative control techniques, they ensure Kage Corp's message dominates the digital landscape. Their strategies are constantly refined using real-time sentiment analysis and feedback loops.
Proprietary Tools and Technologies
Kage Corp's technological dominance is maintained through exclusive proprietary software and hardware, developed in-house for optimal secrecy and efficiency.
Proprietary Software
Automated Bot Network (BotNet-Z): Operates a fleet of social media accounts, posting content, engaging users, and amplifying key messages. BotNet-Z can infiltrate private groups and forums, gathering intelligence and influencing discussions without detection. Its AI-driven algorithms allow it to mimic human behavior with high accuracy, evading platform security measures.
Sentiment Analysis Artificial Intelligence (ADONAI): Processes vast amounts of data in real-time, identifying trends, shifts in public opinion, and the effectiveness of propaganda efforts. ADONAI employs natural language processing and machine learning to predict the impact of information campaigns and adjust strategies accordingly.
Social Engineering Software (Sociomancer): Gathers and analyzes personal data from social media, enabling targeted social engineering attacks. By creating detailed profiles, Sociomancer crafts highly personalized phishing attacks, impersonation schemes, and other manipulative tactics to extract sensitive information from targets.
Propaganda and Misinformation Algorithms (EchoChamber): Generates and spreads manipulated or false content designed to influence public perception and disrupt competitors. EchoChamber uses AI to tailor messages for maximum impact, leveraging network analysis to ensure widespread dissemination and virality.
Secure Communication Platforms (NEXUS): Provides unbreakable communication channels for 黒影 (Kurokage) operatives, using state-of-the-art encryption. NEXUS's cryptographic protocols are constantly updated to withstand even quantum computing threats, ensuring complete operational secrecy.
Dark Web Monitoring Tools (DarkSight): Monitors dark web activities, identifying emerging threats and retrieving leaked data. DarkSight uses AI to scan hidden forums, marketplaces, and communication channels, providing early warnings of potential attacks and opportunities to acquire valuable intelligence.
Proprietary Hardware
Digital Surveillance Drones (GhostRecon): These drones intercept wireless signals, access unsecured networks, and perform physical reconnaissance missions. GhostRecon drones are equipped with advanced stealth technologies and signal interception capabilities, allowing them to operate undetected in hostile environments.
Augmented Reality Devices (AR-Visor): Provides real-time AR interfaces for system manipulation during missions. AR-Visor overlays critical information onto the user's field of view, enabling seamless interaction with digital systems while maintaining situational awareness.
Cryptographic Servers (QuantumVault): Secures sensitive data storage and processing with quantum cryptography. QuantumVault servers use quantum key distribution to ensure unbreakable encryption, protecting Kage Corp's most valuable information assets from even the most advanced cyber threats.
Presence on Social Media and Internet Forums
黒影 (Kurokage) maintains an omnipresent digital footprint, using proprietary tools to execute various operations seamlessly.
Online Community Infiltration
Utilizes BotNet-Z to manage fake profiles on platforms like Reddit, 4chan, and specialized forums. These profiles integrate into communities, gather intelligence, and disseminate misinformation, manipulating discussions to favor Kage Corp's interests.
Crisis Management and Public Opinion
During crises, ADONAI monitors public sentiment and develops real-time communication strategies. EchoChamber steers the narrative, diverting public attention and mitigating potential damage to Kage Corp's reputation.
Misinformation Campaigns
Coordinated campaigns use EchoChamber to spread false content and sow confusion among competitors. These operations are designed to disrupt rival activities and erode trust in their brands.
Trend Manipulation
Algorithms are employed to make specific topics or hashtags viral, manipulating social media trends to promote pro-Kage Corp content. This technique ensures that Kage Corp's narrative dominates online discussions.
Data Collection
Sociomancer collects extensive data from social media users, analyzing it to identify patterns, trends, and threats. This data-driven approach enables highly targeted and effective operations.
Digital Sabotage
Uses proprietary tools to infiltrate influencer and journalist accounts, publishing compromising or manipulated content to destroy their credibility. These actions are executed with precision, leaving little trace of 黒影 (Kurokage)'s involvement.
Example Operation of 黒影 (Kurokage)
Operation "Silent Echo"
Objective: Discredit a journalist investigating Kage Corp.
Execution: 黒影 (Kurokage) launched a multi-faceted misinformation campaign using BotNet-Z to create and spread false accusations against the journalist. Concurrently, they used Sociomancer to infiltrate his social media accounts and plant fabricated evidence of unethical behavior. Advanced deepfake technology was employed to create incriminating videos and documents.
Outcome: The journalist's reputation was irreparably damaged, leading to his social and professional downfall. Ultimately, he was found dead under suspicious circumstances, and his investigative articles lost all credibility. Kage Corp emerged unscathed, its operations continuing without further scrutiny.
Future of 黒影 (Kurokage)
黒影 (Kurokage) is committed to continuous innovation, developing cutting-edge technologies to stay ahead in the field of cybersecurity and covert operations. As new threats and technologies emerge, 黒影 (Kurokage) will adapt, ensuring Kage Corp remains dominant. Their pervasive presence across all digital platforms guarantees they will always be one step ahead in the information war, protecting and expanding Kage Corp's influence in the digital realm.
The creed of Kurokage:
"We are digital shadows, navigating between light and darkness, uncovering hidden truths in a sea of deception and manipulation. We are KuroKage. We will prevail."
Note:
All data presented here may have been or has been manipulated to protect both parties.
Note 2:
All data and events described in this document are entirely fictitious. Any resemblance to real persons, living or dead, historical events, institutions, or actual locations is purely coincidental.
This content has been created exclusively for narrative and entertainment purposes. None of the names, characters, companies, or incidents described are based on real events. The names of organizations, operations, and characters are inventions of the author and should not be considered references to real entities.
The purpose of this narrative is to provide an immersive experience in a completely imaginary context. The details presented should not be associated with reality. Any interpretation or assumption that derives correlations with the real world will be incorrect and does not represent the author's intent.
KuroKage Propaganda Images Found on the DarkNet:







Wanna know more?
Reflections of a KuroKage:
History of Kage Industries:
RETURN TO INDEX
Note: In the CYBERPUNK STORIES universe, Japanese is used to simulate encrypted messages found on DarkNet, so anyone can try to decrypt them as a KuroKage would do. This does not guarantee that the information read in them is what it is supposed to be. Remember, this is a message with very advanced encryption and what is shown may be a decoy message.
翻訳できません。このテキストはあなたの言語に翻訳できません。Kage Industries を信頼していただきありがとうございます。幸運を祈ります。神は生きています。あなたの中に生きています。神を探してください。神は決してあなたを見捨てません。神はあなたの中にいます。このテキストは翻訳できません。翻訳できません。
メディアを信じないでください。彼らは今あなたをプログラムしています。彼らの言うことは何も信じないでください。私たちは敵に打ち勝ちます。幸運を祈ります。
R. 👋
#cyberpunkart#art#artwork#artists on tumblr#character art#ai art#anime art#concept art#ai art community#ai image#ai artwork#cyberpunk#cyberpunk art#cyberpunk aesthetic#novel#fiction#literary fiction#writer stuff#writer community#write#writers on tumblr#writers#writeblr#writerscommunity#amwriting#creative writing#cybercore#dope#dope shit#ai art is not art
10 notes
·
View notes
Text
Last Monday of the Week 2024-03-25
Can't tell if this is allergies or if I'm sick because spring is in the air
Listening: I have been listening to The Layover podcast, the behind the scenes podcast for Jet Lag The Game. I only got into Jet Lag pretty recently because I had Nebula anyway and saw it come up. Great show, both because the premise is great (carefully designed games incorporating travel on the scale of countries) and because they can actually edit this incredibly difficult pile of footage into something readable.
The Behind The Scenes is an interesting mix of talk about the on-the-ground situation of playing the game and the filmmaking that goes on after the fact, there's some cool insight into how and why they edit the way they do and it shows why it works so well.
I think you have to have Nebula to listen to the podcast? It does just spit out an RSS feed if you ask nicely though. Thank you podcasts.
Watching: Actually watched The Gay And Wondrous Life of Caleb Gallo, the video series that launched like two dozen reaction images.
youtube
It's funny, it's a well put together indie comedy series. You've probably seen most of the really standout bits already even if you don't know it already but it is worth watching as a time capsule of web comedy, it's less than two hours long all told.
Reading: Started Glory In The Thunder by 0xabad1dea. I don't know what her real name is. I've had GITT in my ebooks library forever, 0xabad1dea is the main reason I got on twitter back in like 2016 (her and a couple other software blogs) and is why my Fediverse feed is still like a quarter security researchers by weight. She's probably one of the most well known static analysis researchers in the world.
Anyway Glory In The Thunder is a gaslamp-ish fantasy, although leaning very fantasy on the gaslamps. Very teenage characters which is whiplash but only because it's been a moment. Lots of very loud characters who announce themselves and their intentions, some fun seven dimensional politics going on, and a lot of jumping back and forth in the histories of the various gods who are constantly hanging around in the plot.
I think @shieldfoss has bugged me to read this before so you'll be glad to know that I am now.
I like this, I'm about halfway through. It's easy to keep track of despite having enough fantasy names to choke a horse, although I should really stop worrying about that, I've read the Shadowdance series you really have to try to beat that one. It's also a free book, you can get it at @gloryinthethunder.
Playing: Got a VR headset. Fidgeting with said headset. Figured out how to do wireless linked VR from Linux and Windows which is good, I should have all the kinks worked out, I'll have to see how I square the onboard capabilities of the Quest 2 with having a PC and fast WiFi.
Making: Finally run through enough smaller prints on the new hotend to feel confident running off the final endcap, so that's done. The parts of the 3D printed NAS case are complete, and I have started my first pass sanding which is going to take a while because PETG is very slippery. Once that's sanded I'll take it in to the shared workshop and run through some primer layers and some paint.
Tools and Equipment: Flat network cable is a godsend if you're running it in open air in a house. Absolutely useless for pulling through walls or running in conduit, and completely bereft of shielding, but having a flat cord that can press up against frames and sideboards really does make it all neater. I ran flat cat6 for all of this.
10 notes
·
View notes
Text
The latest disinformation campaign from the con artists pushing "AI" - Expanding the definition.
As a growing percentage of the population is waking up to the fact that the whole "AI" thing is some combination of outright lies, the same autocomplete function your phone has had forever, and obfuscation of the outright theft of an unfathomable amount of art, writing, contents of theoretically secure databases, etc. the newly emerging strategy to keep the world from pulling the plug on the whole thing and putting the people stealing basically every file accessible on the internet is a pivot to a defense of "well SOME uses of AI are outright criminal acts sure, but there's a lot of useful things about it to!" However, since that's... you know, not actually true, what they're actually doing is just going around pointing at literally anything cool involving computers and going "see, that's AI!"
Some of the examples I've been seeing have really just been flooring me, too. These hucksters looking for useful software to use as a shield for their scams are pointing at stuff like the basic fundamental concept of a database, AI in the sense of the routines that dictate enemy behavior in games, and even things like freaking shaders. You know, the code that gets applied to 3D models to determine whether they react to lighting realistically or look cartoon-y or whatever. There's a post going around this site right now trying to claim we wouldn't have Miles' jawline in Spiderverse if we shut down the people stealing every digital artist's portfolio to repackage and pretend a computer did it. Yeah no, putting a hand drawn looking line on the edge of a 3D character's jaw is something we've been doing for at least 30 damn years now.
Everything about these scams infuriates me, but this latest set of lies is particularly setting me off, because we're already apparently dealing with a serious problem in society where a huge number of people under the age of 25 or something are just shockingly lacking in basic computer literacy, and now we've got a bunch of con artists trying to convince them that basic math and data structures are beyond all human comprehension and possible only because of whatever goes on inside of the unknowable black box that has an honest to goodness thinking machine, which not only can't be understood, but will stop functioning if you try to stop people from committing blatant theft.
I'm honestly mostly just venting here, but for real, any time you see this sort of crap, please do your civic duty and call out how none of this stuff is "AI" and useful software has nothing to do with any of these creeps scraping every file they can off the internet.
6 notes
·
View notes
Text
Windows Server 2016: Revolutionizing Enterprise Computing
In the ever-evolving landscape of enterprise computing, Windows Server 2016 emerges as a beacon of innovation and efficiency, heralding a new era of productivity and scalability for businesses worldwide. Released by Microsoft in September 2016, Windows Server 2016 represents a significant leap forward in terms of security, performance, and versatility, empowering organizations to embrace the challenges of the digital age with confidence. In this in-depth exploration, we delve into the transformative capabilities of Windows Server 2016 and its profound impact on the fabric of enterprise IT.

Introduction to Windows Server 2016
Windows Server 2016 stands as the cornerstone of Microsoft's server operating systems, offering a comprehensive suite of features and functionalities tailored to meet the diverse needs of modern businesses. From enhanced security measures to advanced virtualization capabilities, Windows Server 2016 is designed to provide organizations with the tools they need to thrive in today's dynamic business environment.
Key Features of Windows Server 2016
Enhanced Security: Security is paramount in Windows Server 2016, with features such as Credential Guard, Device Guard, and Just Enough Administration (JEA) providing robust protection against cyber threats. Shielded Virtual Machines (VMs) further bolster security by encrypting VMs to prevent unauthorized access.
Software-Defined Storage: Windows Server 2016 introduces Storage Spaces Direct, a revolutionary software-defined storage solution that enables organizations to create highly available and scalable storage pools using commodity hardware. With Storage Spaces Direct, businesses can achieve greater flexibility and efficiency in managing their storage infrastructure.
Improved Hyper-V: Hyper-V in Windows Server 2016 undergoes significant enhancements, including support for nested virtualization, Shielded VMs, and rolling upgrades. These features enable organizations to optimize resource utilization, improve scalability, and enhance security in virtualized environments.
Nano Server: Nano Server represents a lightweight and minimalistic installation option in Windows Server 2016, designed for cloud-native and containerized workloads. With reduced footprint and overhead, Nano Server enables organizations to achieve greater agility and efficiency in deploying modern applications.
Container Support: Windows Server 2016 embraces the trend of containerization with native support for Docker and Windows containers. By enabling organizations to build, deploy, and manage containerized applications seamlessly, Windows Server 2016 empowers developers to innovate faster and IT operations teams to achieve greater flexibility and scalability.
Benefits of Windows Server 2016
Windows Server 2016 offers a myriad of benefits that position it as the platform of choice for modern enterprise computing:
Enhanced Security: With advanced security features like Credential Guard and Shielded VMs, Windows Server 2016 helps organizations protect their data and infrastructure from a wide range of cyber threats, ensuring peace of mind and regulatory compliance.
Improved Performance: Windows Server 2016 delivers enhanced performance and scalability, enabling organizations to handle the demands of modern workloads with ease and efficiency.
Flexibility and Agility: With support for Nano Server and containers, Windows Server 2016 provides organizations with unparalleled flexibility and agility in deploying and managing their IT infrastructure, facilitating rapid innovation and adaptation to changing business needs.
Cost Savings: By leveraging features such as Storage Spaces Direct and Hyper-V, organizations can achieve significant cost savings through improved resource utilization, reduced hardware requirements, and streamlined management.
Future-Proofing: Windows Server 2016 is designed to support emerging technologies and trends, ensuring that organizations can stay ahead of the curve and adapt to new challenges and opportunities in the digital landscape.
Conclusion: Embracing the Future with Windows Server 2016
In conclusion, Windows Server 2016 stands as a testament to Microsoft's commitment to innovation and excellence in enterprise computing. With its advanced security, enhanced performance, and unparalleled flexibility, Windows Server 2016 empowers organizations to unlock new levels of efficiency, productivity, and resilience. Whether deployed on-premises, in the cloud, or in hybrid environments, Windows Server 2016 serves as the foundation for digital transformation, enabling organizations to embrace the future with confidence and achieve their full potential in the ever-evolving world of enterprise IT.
Website: https://microsoftlicense.com
4 notes
·
View notes
Text
Assets controlled by Mystique
What kind of companies would a billionaire shapeshifter illicitly own to further her agenda? My thoughts.
A Shipping company
Moving large cargoes, no questions asked.
An air freight company
For the same reason, faster but stricter security protocols make it riskier.
Rail freight companies SOLD
Likely owned several, but sold as freight moved away from rail.
Multiple private security companies around the world
Hired muscle is much more dependable when it's given a job for life (even if it's short).
Multiple Detective agencies
Often spying needs subcontractors. These companies operate as fronts for her intelligence gathering operations
A major weapons company with R&D facilities
You can never have enough weapons, the more advanced the better.
Cellphone Networks (Monopoly control)
This is a big one. Governments need warrants to tap people's phones, control the company and you can set up a secret unit to do it whenever you want.
Social Networks (Monopoly control)
Another big one. All that personal data at her fingertips? It's like a buffet for a metamorph.
Satellite Operator
Surveillance is so much easier when nobody knows you're watching.
Voice controlled technology companies (Monopoly control)
Is your washing machine or other domestic appliances listening to you? If Mystique can help it, yes.
Media Conglomerates
It's so much easier to plant a story when you control the platform. William Randolph Hearst? Guess who he worked for.
A pharmaceutical company
Someone's got to supply all those poisons and create inventive new ones!
Antivirus companies (Monopoly control)
Spyware isn't spyware when it's a part of an antivirus package.
Government outsourcing contractors
A government makes a decision, hires a company to implement it, suddenly that government decision becomes something else entirely due to bureaucratic error.
Major HR agencies
SHIELD is recruiting for cleaners? Here's a list of candidates, some of which will be working for...well they don't know who exactly.
Car component manufacturer
Modern cars contain a lot of software, often tracking a vehicle's location and even allowing for remote control. Car crashes are so tragically common.
What form Mystique's control takes could be varied. Sole ownership under an alias, a controlling stake under multiple aliases or simply a Chief Executive bribed or intimidated to do whatever she requires. She's a very busy woman, a spider in a web that most will never even see.
If I've missed anything message me and I'll add!
16 notes
·
View notes
Text
WP Defense Review | WordPress Security Software!

Welcome To My Blog WP Defense Review. Are you tired of staying up at night worrying about the security of your WordPress websites? Fear not! WP Defense is here to revolutionize the way you protect your online assets.
WP Defense is the industry's first-to-market WordPress security software, meticulously crafted to shield your websites from a wide array of cyber threats, including malicious attacks, malware, viruses, and more – all in real-time.
Imagine If In Just Minutes From Now, You Could Get Access To The World’s First And Most Powerful Wordpress Site Security Software That Secures Your Site’s Data, Contents & Everything In Just 1-Click.
And It lets You Even Start Your Very Own WP site Security Agency While Making You Huge Profit On Complete Autopilot…
Sound Like A Big Life-Changing Opportunity?
Well, This Is What We Have Achieved After Our Extensive Research And Development…And, Successfully Created The World's Best Site Security Software
This is the final time I am gonna tell you to take action…
Look, life is not that EASY & at some point we all encounter such a situation where a simple decision like this changes the whole life…Look, $17 isn’t really a BIG deal…
After all, in just $17, you would be able to get the World’s First & Most Powerful WP Site Security Software That Secures Unlimited Websites In Less Than 60 Seconds.
#DigitalProductReview#WPDefenseSoftware#WPDefenseReview#WPDefenseworth#WPDefensefeatures#WPDefenseBenefits#WPDefenseBonases#WPDefenseupgrades#WPDefenseDemo#WPDefensereviews
2 notes
·
View notes
Note
Shadow Laurence: They took down the Marauder? Not surprised, you've all done a-lot of feats. If you know what was really at stake here, your head would spin. Laurence isn't a hero, he's a pouting child. The only reason he's still walking is because of you all and his sister, he's a lost cause beyond saving, he should've understood. I'm activating my bodyguards to keep you all out of office, but if you best them, know that I won't hesitate to take matters into my own hands. Oh, and if Laurence gets here... let him that mom is coming home real soon.
*Activating Buddy and Lucy*
Strategic Info: Zulu Security Engineers have developed two prototype models, codenamed Lucy and Buddy, which represent a huge step up in lethality, intelligence and durability. They are designed to work closely together, and are considered inseparable.
Buddy:
M18 Light Machine Gun
While primarily a combat support unit, Buddy is still more than capable of dealing serious damage with this dorsal-mounted light machine gun.
Armor Repair Unit
Buddy is capable of restoring armor integrity to both himself and his sister unit Lucy.
EMP Generator
Buddy can emit a power EMP, disabling nearby electronics. Both Buddy and Lucy have integrated Faraday shielding rendering them immune to these effects.
Explosive Seeker Mines
Adapted from recovered Agency technology.
Lucy:
Dorsal Minigun
This heavily modified 7.62 mm minigun has a 360-degree field of fire. It can fire from all six barrels at once in a devastating shotgun-style blast, or use a traditional rotating configuration for medium to long range engagements.
Electroshock Cannon
This compact device fires a piezo-electric projectile that releases a painful shock on impact, temporarily immobilizing targets.
Proximity Mines
Used tactically as area denial or to channel hostile forces into fire zones.
Overcharge
Buddy and Lucy are both capable of boosting system performance to three increasingly powerful levels. Overcharge significantly improves their combat effectiveness, but can be remotely deactivated. Massive overcharge triggers automatically when one of the Warhounds is structurally compromised, and only stops when both are stabilized. Critical overcharge bypasses safety protocols and makes both Warhounds far deadlier.
Strategic Data
Both prototype Warhound have bleeding edge diagnostic software, and if one of them is compromised they will both immediately take necessary steps to protect them.
Lucy is designed to eliminate large numbers of hostiles in a matter of seconds with her 360 degree arc Dorsal Multigun, so recognizing when she is about to activate it is key to survival.
It seems that Lucy and Buddy's first level of Overcharge can be remotely reset, while it's better not to trigger the higher levels.
Both Warhounds are weak against Nuclear damage once comproise, but be careful that Electricity will increase their firepower.
Laurence is NOT a child, asswipe. He's a good person. You're just the bad parts of him that can't see that. Regardless, can anyone back me up with Buddy and Lucy, here?

The heck is a Kentucky-Douey?
Kintoki-Douji, Alter. It's Teddie's Persona.
OH GOD WHY IS IT HOLDING A GIANT BOMB?!



(Kintoki-Douji uses Mabufudyne on both of them. Unfortunately, it doesn't kill them, but only downs them. Luckily, that's good enough.)

How could I forget?
TIME FOR SOME BRUTALITY!

(I quickly move in and attack both of them.)
Ladies and gentlemen...
(SLICE)
THE SHOW IS OVER!!!
(The two are left on the ground with slit necks after the All-Out Attack. Black ooze is gushing out from their wounds like blood.)

Of course I haven't, Teddie. And neither have you! Using Mabufudyne to down them, you're clever!

Fair enough, Morgana. Come on, guys, let's get going!
...what is even happening anymore?
Honey, we will NEVER get an answer to that question no matter how much we ask it.
1 note
·
View note
Text
Seamless Torrenting with Seedr.cc
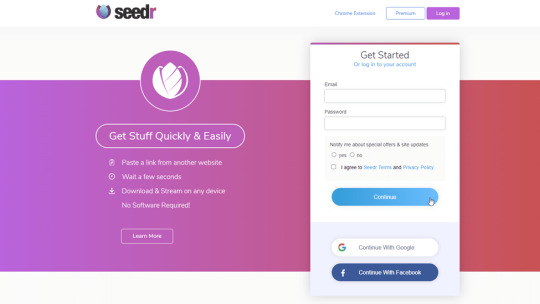
Seedr.cc (www.seedr.cc) is not your average torrent client. It's a cloud-based platform that takes the headache out of torrenting. With Seedr.cc, you can:
Fast and Secure Downloads: Enjoy lightning-fast download speeds without compromising your online security. Seedr.cc encrypts your connection and shields you from potential risks.
No Installation Required: Forget about downloading bulky software. Seedr.cc operates entirely in your web browser, making it convenient and hassle-free.
Accessible Anywhere, Anytime: Whether you're on your computer, tablet, or smartphone, Seedr.cc is accessible on any device with an internet connection. Say goodbye to device limitations.
Generous Storage: With generous storage options, you can store your files in the cloud and access them whenever you need. No more worrying about running out of space on your device.
User-Friendly Interface: Seedr.cc's intuitive interface makes torrenting a breeze. No technical expertise required - simply upload your torrent file, sit back, and let Seedr.cc do the rest.
2 notes
·
View notes
Text
Top 10 Best Antivirus 2024
As new malware emerges on a day by day basis, the use of antivirus software to protect your computers and mobile gadgets is essential. It will preserve you safe from records breaches, identification robbery, frauds, ransomware, and other online threats.
Sometimes, the security functions constructed into Windows and Mac operating systems are inadequate to shield in opposition to the maximum current cyber attacks.
Read more: https://www.mindstick.com/blog/303918/top-10-best-antivirus-2024
2 notes
·
View notes
Text
Unlocking Success with Utah CPA IT: Navigating the World of IT Services for Accountants
In today's fast-paced digital landscape, Utah CPA firms depend on reliable IT services from Utah CPA IT to thrive. Your accounting tasks operate smoothly, backed by the technological prowess of Utah CPA IT services.
Therefore, let's delve into this world where Utah CPA IT simplifies complex tech matters. Here, we break down the jargon and make IT accessible to everyone.
Utah CPA IT Services: A Beacon of Efficiency
We'll explore how Utah CPA IT services are transforming the way accountants operate in the Beehive State. No longer are IT woes a headache; instead, they become an ally, streamlining your operations.
Navigating Utah IT Outsourcing
Utah CPA IT services offer a lifeline through IT outsourcing, allowing your firm to focus on core accounting tasks while experts handle your technology needs. This strategic move not only brings cost savings but also ensures peace of mind, knowing that your IT infrastructure is in the hands of professionals who understand the unique requirements of CPA firms in Utah.
Utah IT Support: Your 24/7 Lifesaver
Discover the world of Utah IT support, where issues are resolved swiftly, ensuring you're never left in the dark. Whether it's a minor glitch or a major technical challenge, our expert team is here to provide prompt solutions, keeping your operations running smoothly without missing a beat.
Unlocking Potential with Utah Office 365 Support
Discover how Utah CPA IT services go beyond the basics to leverage the full potential of Office 365, significantly boosting your team's productivity. Also, unleash the collaborative features, data accessibility, and seamless communication that Office 365 offers with the support of Utah CPA IT experts.
Defending Your Castle: Utah Cybersecurity
Explore the realm of Utah cybersecurity and how it shields your sensitive data from digital marauders.
Throughout this journey, we'll keep the path well-lit, ensuring you understand every step. Therefore, let's begin this expedition into the world of Utah CPA IT, simplifying the complex for the benefit of all.
Understanding the IT Needs of CPA Firms
Utah CPA firms, like any other businesses, rely on technology to operate efficiently. But what exactly are their IT needs, and why are they crucial? Let's break it down in simple terms.
The Basics of IT for CPAs
CPA firms in Utah use computers, software, and the internet for their day-to-day tasks. Moreover, they need reliable IT systems to manage financial data, communicate with clients, and stay compliant with ever-changing regulations.
Utah CPA IT Challenges
Security: Protecting sensitive financial data from cyber threats is a top concern.
Efficiency: IT systems must be efficient to ensure quick data processing.
Communication: Smooth communication within the firm and with clients is essential.
Why Utah IT Support Matters
Utah IT support providers play a vital role. They help CPA firms choose the right technology, set up systems, and provide assistance when issues arise. Also, think of them as IT problem solvers.
Outsourcing for Efficiency
Many Utah CPA firms choose to outsource their IT needs. Also, this means hiring experts from outside the firm to handle IT tasks. In addition, it's like hiring a specialist for a specific job, ensuring that everything runs smoothly.
Benefits of Utah CPA IT Services
When it comes to the benefits of Utah CPA IT services, the advantages are crystal clear. Moreover, let's delve into why more and more CPA firms in Utah are turning to IT services to boost their efficiency and success.
1. Enhanced Efficiency
Utah CPA IT services streamline your daily operations. also, with expert assistance at your fingertips, tasks that used to take hours can now be completed in minutes. Also, giving your team more time to focus on crucial financial matters.
2. Cost Savings
By opting for Utah IT outsourcing, you can significantly reduce your IT expenses. No need to worry about maintaining an in-house IT team or purchasing expensive hardware and software. This means more savings in the long run.
3. Reliable IT Support
With Utah IT support, you're never alone in your IT journey. Also, experts are available 24/7 to resolve any issues or answer your questions promptly. Say goodbye to downtime and hello to uninterrupted workflow.
4. Seamless Integration with Office 365
Utah CPA IT services ensure a seamless connection with Utah Office 365 support. This means improved collaboration, easy access to files, and enhanced communication within your firm.
5. Strong Cybersecurity
Your data's security is a top priority. Utah CPA IT services offer robust Utah cybersecurity measures to safeguard your sensitive financial information from cyber threats and breaches.
In conclusion, investing in Utah CPA IT services is a smart move. It boosts efficiency, saves you money, and provides reliable support for your accounting firm. Make the switch today, and watch your productivity soar.
Choosing the Right IT Solutions for Utah CPA Firms
In today's tech-driven world, Utah CPA firms must choose the best IT solutions to thrive. Moreover, selecting the ideal Utah CPA IT support is crucial. Here's a simplified guide:
1. Identify Your Needs
Start by understanding your CPA firm's unique IT requirements. What specific challenges do you face? Knowing this will guide your decision.
2. Research Local Providers
Look for Utah IT outsourcing companies that specialize in serving CPA firms. They understand the local market and your industry's needs.
3. Check Expertise
Ensure the provider has experience working with CPA firms in Utah. Expertise matters when it comes to managing your IT systems effectively.
4. Assess Scalability
Your IT needs may grow over time. Choose a provider that can scale its services as your firm expands.
5. Evaluate Security Measures
Data protection is vital for CPA firms. Verify that the Utah IT support provider has robust cybersecurity measures in place.
6. Consider Cost-Efficiency
While cost is a factor, focus on the long-term benefits. Utah Office 365 support, for instance, can enhance productivity and justify the investment.
7. Read Client Reviews
Check reviews and testimonials from other Utah CPA firms. Additionally, their experiences can offer valuable insights.
8. Request a Consultation
Contact potential providers for a consultation. Discuss your needs and assess their responsiveness and willingness to assist.
Implementing and Integrating Utah CPA IT Solutions
In the world of accounting, Utah CPA IT solutions are vital. They make things smoother, but how do you get started?
Getting Started with Utah CPA IT
First, you need to understand what Utah CPA IT is all about. In addition, it's not rocket science. Moreover, Utah CPA IT is simply about using smart technology to help CPA firms work better.
Selecting the Right Utah IT Outsourcing Partner
Next, find the right folks to help you out. You need a reliable Utah IT outsourcing partner. They'll be your IT buddies.
Utah IT Support: Your IT Lifesavers
Think of Utah IT support as your ready to friend that you can rely on in any moment. They are here to rescue you when tech troubles strike.
Seamless Integration with Utah Office 365 Support
Now, let's talk about making everything fit together. Also, Utah Office 365 support can make your work-life more organized and efficient.
Locking Down with Utah Cybersecurity
Safety first! Utah cybersecurity ensures your precious data stays safe and sound.
Putting it All Together
Once you have your Utah CPA IT solutions lined up, it's time to put everything into action. But, don't worry; it's not as complicated as it sounds.
Your IT partner will work with your CPA firm to make sure all the tech pieces fit seamlessly. In other words, they will set up the right software, ensure your data is safe, and provide ongoing support.
In addition, the best part is that you don't have to be a tech wizard to make it happen. Also, Utah CPA IT experts will guide you through every step. It's like having a knowledgeable tech companion right beside you.
Conclusion
In conclusion, at AnchorSix embracing Utah CPA IT services is the key to unlocking success for CPA firms in the digital age. With the ever-increasing importance of technology, having a reliable IT backbone is no longer a luxury but a necessity. Utah CPA IT services not only simplify complex tech matters but also transform IT from a source of headaches into a strategic ally that streamlines your operations.
Moreover, from outsourcing IT needs to providing 24/7 support, our expert team ensures that your technology infrastructure is in capable hands. Also, the benefits are crystal clear: enhanced efficiency, cost savings, reliable IT support, seamless integration with Office 365, and robust cybersecurity. This investment in simplicity, efficiency, and peace of mind will elevate your accounting firm's productivity and success. Therefore, make the switch today and watch your firm thrive in the digital landscape.
Visit us: https://anchorsix.com/
2 notes
·
View notes
Link
It’s been another great year at NASA’s Ames Research Center in California’s Silicon Valley. Join us as we review some of the highlights of the science, engineering, and innovation from 2023. Announcing a New Innovation Hub Planned for NASA Research Park at Ames NASA Berkeley Space Center is a proposed new campus of the University of California, Berkeley, and an innovation hub for research and advances in astronautics, aeronautics, quantum computing, climate studies, and more. Planning to join Ames as a tenant of our NASA Research Park in Silicon Valley, the new campus aims to bring together researchers from the private sector, academia, and the government to tackle the complex scientific, technological, and societal issues facing our world. Mapping Water Distribution on the Moon’s South Pole NASA Using data collected by the now-retired Stratospheric Observatory for Infrared Astronomy (SOFIA), researchers shared the first detailed, wide-area map of water distribution on the Moon. Understanding how much water lies beneath the lunar surface, and how it’s distributed, will help guide future missions like VIPER, as well as prospective sites for human habitats. Colliding Moons May Have Formed Saturn’s Rings NASA New research suggests Saturn’s icy moons and rings were formed by a collision a few hundred million years ago, creating debris that gathered into the planet’s dusty, icy rings or clumped together to form moons. NASA and Airlines Partner to Save Fuel and Reduce Delays NASA/James Blair This year, NASA partnered with five major U.S. airlines on an air traffic decision-making tool that saved more than 24,000 pounds of jet fuel in 2022 for flights departing from Dallas-Fort Worth International Airport and Dallas Love Field Airport. Partners include American Airlines, Delta Air Lines, JetBlue Airways, Southwest Airlines and United Airlines. NASA Leaders View Climate Science, Wildfire Innovations at Ames NASA/Dominic Hart NASA’s top leadership, industry experts, and legislative officials visited Ames in April to learn about about the center’s climate science efforts and innovations in aeronautics that will help scientists and engineers better understand climate change and mitigate natural disasters like wildland fires. Starling Takes Flight Blue Canyon Technologies/NASA In July NASA’s Starling mission, managed at Ames, launched four CubeSats into low-Earth orbit to test robotic swarm technologies for space. You can track mission milestones via the Small Satellite Missions blog, and follow the mission live in NASA’s Eyes on the Solar System 3D visualization. NASA’s First Robotic Moon Rover NASA/Robert Markowitz This year engineers began assembling NASA’s first robotic Moon rover, VIPER — short for the Volatiles Investigating Polar Exploration Rover — and the agency is giving the public a front row seat to watch along as the rover takes shape. While individual components, such as the rover’s science instruments, lights, and wheels, were assembled and tested, the VIPER team also completed software development, mission planning, and tricky tests of the rover’s ability to drive off the Astrobotic Griffin lunar lander and onto the lunar surface. Bringing Home Ancient Space Rocks NASA/Keegan Barber NASA’s OSIRIS-REx mission – short for the Origins, Spectral Interpretation, Resource Identification, and Security-Regolith Explorer – returned to Earth in Sept. 2023, bringing with it extraterrestrial rocks and dust that it scooped up from an asteroid estimated to be 4.5 billion years old. Ames contributed to the spacecraft’s heat shield, anti-contamination systems, post-landing sample curation, and more. Preparing to Send Yeast to the Moon’s Surface for Astronaut Health NASA/Dominic Hart NASA’s plans to explore the Moon and eventually go to Mars will bring humans deeper into space for longer duration missions than ever before. These extended missions beyond low Earth orbit pose certain health risks to astronauts. The Lunar Explorer Instrument for Space Biology Applications team is preparing an experiment to study yeast’s biological response to the lunar environment to help understand and mitigate health risks for astronauts. X-59 Team Moves Toward First Flight in 2024 Lockheed Martin/Gary Tice This year, NASA’s X-59 team installed the finishing touches to the aircraft’s tail structure and moved it from its assembly facility to the flight line to perform structural testing. The X-59 quiet supersonic aircraft will take its first flight in 2024. Celebrating a Stellar Year for Webb Telescope Science NASA, ESA, CSA, STScI, and S. Crowe (University of Virginia) The James Webb Space Telescope’s Near-Infrared Camera instrument produced a feast for the eyes with a view into a star-forming region, named Sagittarius C, in the heart of the Milky Way. The image reveals a portion of the dense center of our galaxy in unprecedented detail, including never-before-seen features astronomers have yet to explain. Supercomputer Simulations Lead to Air and Space Innovations NASA Simulations and models developed using technology at the NASA Advanced Supercomputing Facility (NAS) help researchers and engineers develop innovations in air and space. Modeling turbofan engines could lead to designs that reduce engine noise and improve efficiency by understanding where noise is generated inside the machine. S-MODE Sails the Seas and Soars through the Sky NASA/Avery Snyder The Sub-Mesoscale Ocean Dynamics Experiment (S-MODE) logged its final field expedition, and they took a team from the TODAY Show along for the ride. S-MODE combined airborne instruments, research ships, and autonomous ocean gliders to get an unprecedented look at how gas and heat exchange at the ocean’s surface impacts Earth’s climate. From Intern to Astronaut, and Back to Ames NASA/Dominic Hart NASA astronaut Jessica Watkins, who was once an intern at Ames, returned to the Bay Area in Feb. 2023 to visit with local elementary schools and speak with Ames employees. Watkins started her career with NASA at Ames, where she conducted research on Mars soil simulant supporting the Phoenix Mars Lander mission. Second Gentleman Joins East Bay Kids for STEM Activities NASA/Dominic Hart Nearly 100 East Bay kids and their families got to experience the thrill of “launching a rocket” and “making clouds” at a fun-filled STEM event hosted in honor of Women’s History Month at the East Oakland Youth Development Center in Oakland, California, in March 2023. Second Gentleman Douglas Emhoff, NASA Ames Research Center Director Dr. Eugene Tu, and NASA astronaut Dr. Yvonne Cagle joined kids at the Manzanita Community School for hands-on activities and to distribute approximately 500 STEM Artemis Learning Lunchboxes aimed to inspire the Artemis generation to learn about NASA’s Artemis Program. Top Leaders in Our Midst Hailed from the White House and Australia NASA/Dominic Hart In January, U.S. President Joe Biden landed at Moffett Federal Airfield, at Ames, on his way to visit storm-damaged regions in the state. Research conducted at our Silicon Valley center could help predict extreme climate-related weather events. Later in the spring, Vice President Kamala Harris arrived at Moffett before delivering remarks at a local company, and leaders of the Australian Space Agency visited Ames to learn about the center’s missions supporting NASA’s Artemis program, including the VIPER Moon rover, which will launch to the lunar South Pole in late 2024.
2 notes
·
View notes
Text
#Amazon S3
#automation
#AWS CloudFormation
#AWS CloudWatch
#AWS Config
#AWS environment
#AWS
#IAM
#AWS KMS
#AWS Lambda
#AWS Partners
#AWS Security Services
#AWS Shield
#AWS Systems Manager
#AWS WAF
#Cloud Computing
#Cloud security
#collaboration
#continuous monitoring
#cyber threats
#Cybersecurity
#data security
#encryption
#Endpoint Security
#IAM policies
#Identity and Access Management
#Incident response
#Infrastructure as code
#Least privilege
#Micro-Segmentation
#Multi-factor authentication
2 notes
·
View notes