#someone forgot to install antivirus software
Explore tagged Tumblr posts
Text




not feeling cute, might self destruct later
149 notes
·
View notes
Note
I did not intend to write any more letters. Everything I wanted to do was tell Matts family and friends what happened.
And now that? I always believed in the supernatural, I suppose you already know that, but I don't know what to say.
It hurts so much, but still...Are you like him? Liska, Yuvon? Are you like Matt? (You can see dried tears on the paper)
I want to hug and kiss and cuddle him. I can't do it without him. And Dan just left me, saying I was wrong.
How could he?!?! Matt was his friend, too!
I don't believe you in that case, either. I told you our evidence. Matt trusted Jake and he paid for that.
My advise for you: Stop. Jake is dangerous. Yuvon, get out of there and leave him behind.
Liska, I believe many things but not that your Jake will safe you.
Cut contact when you guys still can.
As for him in my world: The guys who took him called me. Said..that he didn't confess yet...That they already would have if they were him... (the handwriting is very shaky)
But he has to be responsible. He has to be the murderer. Because if not then I am responsible for (the parts are still readable, it seems Jessy was in too much distress to realise that) the torture what happens to him now.
Yes. That's it. I am not sure whether I'll write again...But stay safe Yuvon and Liska. And Rai. I totally forgot you. I read a letter of you I think.
Goodbye,
Jessy.
Jessy,
I can't say whether I'm like Matt or not, because I never knew him. There might be some similarities, due to us being placed in the same roles in mostly the same investigations, but I sort of doubt we're exactly the same person. I'm sorry.
Alright. Let's review the evidence you've told me so far, and then you can tell me anything I'm missing.
You talked about how Jake was acting "weird" and suspicious. Could you expand on that? That's a little vague.
You also talked about how you were upset that Jake tried to make Matt keep secrets from you and from the others. Have you considered that might be because Jake suspected the kidnapper might be someone in the group?
Jake tried to convince Matt to stay away from Duskwood. If that conversation happened at the same time for Matt as for myself, this was after Amy's body had been found, after Richy was marked, and after you were physically attacked. This was also after I had been threatened by the kidnapper... four times or so, if I've got the timeline right in my head. At least two times. And this was after I (and presumably Matt) had realized that the attack on you was a message to us. Duskwood had proven itself to be dangerous, and Jake told us not to go there out of concern for us, with no ulterior motive.
Yes. The Man Without a Face is clearly someone from the main group or someone with access to our chats. I had a theory on who, but that's null, now. However, that doesn't mean the kidnapper is necessarily Jake.
Jessy. If my sister went to Duskwood right now, though she wouldn't because she doesn't remember I exist, I'd be FURIOUS at her, because I would be incredibly worried about her. I highly suspect Jake was upset for the same reasons.
Jake went into hiding again, but entrusted Matt with a way to find and contact himself if Matt should get into danger. Why would Jake do that if he was plotting to attack Matt? It would place him in too much danger. For example, someone could open Matt's phone, find his location, and send it to his pursuers very, very easily. Jake is a rational, logical person. Does that really seem like a mistake he'd make?
Jake's mask was found not quite ten meters from the crime scene. I repeat: does that really sound like a mistake Jake would make? If that mask is one of his most identifiable features, his top priority would be to make sure it wasn't found. Doesn't it sound more like someone was framing Jake?
Did the authorities actually check the mask for fingerprints, come to think of it?
That's all the evidence you've told me about so far. If there's more, please let me know.
As for me getting out of here... well. There's some slight issues with that. Like the fact that I can't get out of this hellhole. If you want to read more on that, I suggest you read my letters that went to Matt from the beginning, though you don't have to. It's not too important to the current problem.
On Lis's side, please look at these.
(The Tumblr screenshots are glued on the page with tree sap.)
Sorry about the sap. I don't really have glue here.
The people who talked to you said that they would have already confessed in Jake's place.
Jessy. What are they doing to Jake?
Also. Let me get this straight. If I'm understanding correctly, the instant Jake was captured, he was placed in a maximum security prison cell, without being offered a trial. They are currently attempting to force him to confess, which, if the methods I suspect of being used are in use, often leads to even people who are innocent confessing just to get it all to end, and is thus heavily frowned upon by most governing bodies as pointless and unethical.
Did Matt ever tell you that Jake's pursuers attempted to hack our phone to drive Jake out of hiding and capture him? They attempted to find my location, and they very nearly hacked my camera. Only an antivirus software Jake had installed on my phone and his own timely intervention kept them from succeeding. Jake risked himself to do that.
Jessy, what do you think would have happened if Jake hadn't blocked those people from finding Matt's location or hacking his camera?
—Yuvon
(The letter tucks itself into the paper clip with the others.)
2 notes
·
View notes
Text
Windows 10 Insider Preview Build 18305 released

Windows 10 Insider Preview Build 18305 released. A simplified Start layout Tt=he simplified Start layout is part of an ongoing effort designed to enhance your Start experience in the upcoming release of Windows.
Windows Sandbox Windows Sandbox is a new lightweight desktop environment tailored for safely running applications in isolation. How many times have you downloaded an executable file, but were afraid to run it? Have you ever been in a situation which required a clean installation of Windows, but didn’t want to set up a virtual machine? An isolated desktop environment where you can run untrusted software without the fear of lasting impact to your device. Any software installed in Windows Sandbox stays only in the sandbox and cannot affect your host. Once Windows Sandbox is closed, all the software with all of its files and state are permanently deleted. Windows Sandbox has the following properties: Part of Windows – everything required for this feature ships with Windows 10 Pro and Enterprise. No need to download a VHD! Pristine – every time Windows Sandbox runs, it’s as clean as a brand-new installation of Windows Disposable – nothing persists on the device; everything is discarded after you close the application Secure – uses hardware-based virtualization for kernel isolation, which relies on the Microsoft Hypervisor to run a separate kernel which isolates Windows Sandbox from the host Efficient – uses integrated kernel scheduler, smart memory management, and virtual GPU To install Windows Sandbox, go to Settings > Apps > Apps & Features > Programs and Features > Turn Windows Features on or off, and then select Enable Windows Sandbox. Windows Security app improvements New Protection History experience: The new Protection History experience still shows you detections by Windows Defender Antivirus, but it’s now updated to also give more detailed and easier to understand information about threats and available actions. We have also added Controlled folder access blocks to history, along with any blocks which are made through organizational configuration of Attack Surface Reduction Rules. If you use the Windows Defender Offline scanning tool, any detections it makes will now also show in your history. Additionally, you will see any pending recommendations (red or yellow states from throughout the app) in the history list. We hope you like the changes we’ve made! Introducing Tamper Protection! Tamper Protection is a new setting from Windows Defender Antivirus, available in the Windows Security app, which when on, provides additional protections against changes to key security features, including limiting changes which are not made directly through the Windows Security app. You can find this setting under Windows Security > Virus & Threat Protection > Virus & Threat Protection Settings. Symbols and Kaomoji are now just a hotkey away! When you press WIN+(period) or WIN+(semicolon), in addition to emoji the picker that appears will now include symbols and kaomoji too! You may ask, what is kaomoji? Translated literally from Japanese, it means “face characters” – basically, it’s a way to create faces using only text. You may already use them, for example the one mentioned above is relatively popular: (╯°□°)╯︵ ┻━┻ This experience, originally introduced for Chinese (Simplified) during RS5 development, started rolling out to Insiders across all languages with Build 18252 – as of today’s it’s now available to all Insiders in Fast! Clipboard history gets a new look We originally opted to show bigger entries so there was space to show an image preview nicely, but when we looked at our data, we found 90% of items in the clipboard history were text. Based on that and your feedback, we now optimizing the design for text snippets – shrinking the height of each entry and thus giving you access to more entries without needing to scroll the view. Hope you like the change we made! Copy some text and press Windows logo key + V to check out the updated design. Signing in to Windows with password-less Microsoft accounts If you have a Microsoft account with your phone number, you can use an SMS code to sign in, and set up your account on Windows 10. Once you’ve setup your account, you can use Windows Hello Face, Fingerprint, or a PIN (depending on your device capabilities) to sign in to Windows 10. No password needed anywhere! Creating a password-less phone number account If you don’t already have a password-less phone number account, you can create one in a mobile app like Word to try it out. Simply go to Word and sign up with your phone number by entering your phone number under “Sign in or sign up for free”. Add your password-less phone number account to Windows Now that you’ve created a password-less phone number account, you can use it to sign in to Windows with the following steps: Add your account to Windows from Settings > Accounts > Family & other Users > “Add someone else to this PC”. Lock your device and select your phone number account from the Windows sign-in screen. Since your account doesn’t have a password, select ‘Sign in options’, click the alternative ‘PIN’ tile, and click ‘Sign in’. Go through web sign in and Windows Hello set up (this is what you’ll use to sign in to your account on subsequent sign ins) You can now enjoy the benefits of signing in to Windows with your password-less phone number account. Note: This experience is currently only available for Insiders on Home edition. We’ll let you know when it expands to more editions Streamlined Windows Hello PIN reset experience We know remembering a PIN can be tricky, so we wanted to provide our Microsoft account users with a revamped Windows Hello PIN reset experience with the same look and feel as signing in on the web. Check it out in today’s build by clicking the ‘I forgot my PIN’ link when signing in to Windows with a PIN. Note: This experience is currently only available for Insiders on Home edition. We’ll let you know when it expands to more editions. Keep your device running smoothly with recommended troubleshooting For example, we may recommend turning off a setting that sometimes causes an app or feature to crash unexpectedly until an update is available. We’ll let you know when we can help, and you can choose to run the troubleshooter or ignore it. You can also change how recommended troubleshooting is run on your device by opening Start > Settings > Privacy > Diagnostics & Feedback. You may see recommended troubleshooting from us while we test the feature. These tests, marked as “sample recommended troubleshooter”, are safe to run and will not make any changes to your device. The tests help to ensure that the feature is working as designed and give you an opportunity to give feedback, so we can help keep your device working at its best. Automatic Restart and Sign On (ARSO) for Enterprises Are you tired of seeing these flashing screens after every update? ARSO is a feature that automatically signs-in a user after an update to finish setting up and then locks the PC. This feature is part of our Seamless Update Story for Windows, and its goal is to reduce customer pain points around updates, including things such as post logon set up time and not being able to pick up where you left off. This feature will be enabled on Cloud Domain Joined devices that meet certain security requirements: BitLocker is enabled and is not suspended during the upgrade TPM 2.0 SecureBoot To check if your device will get ARSO go to Settings > Accounts > Sign-in options > Privacy: If the toggle is switched “On” and is not grayed out, then the device meets the security requirements for ARSO, and is enabled by default. If the toggle is grayed out and Enabled, this means that your IT Admin has explicitly enabled ARSO for you, irrespective of your device’s security requirements. If the toggle is grayed out and disabled, this means that you do not meet the minimum security requirements for Enterprise ARSO, or your IT Admin has explicitly disabled ARSO for you, irrespective of your device’s security requirements. Set a default Task Manager tab You can set your preferred tab via Options > Set default tab. Updated Settings Homepage Inspired by the Microsoft account homepage, the Settings home page now has a header at the top allowing you to take quick action for things like signing in and managing your Microsoft account, making the Windows and Microsoft experience better. It also gives you an easy to glance at system status, such as when updates are available.
Friendly Dates in File Explorer Based on your comments, in Build 18305, we’re making it a bit easier to turn off if it’s not your thing – you no longer have to dig through settings, you can now just right-click on the date modified column and toggle friendly dates on and off from there. Friendly dates isn’t yet available for everyone, so don’t worry if you don’t see it just yet – we’ll let you know when it’s live for all. Shadows are back! Shadows are part of our long-term vision of the evolution of Fluent Design, and we’re excited to bring them back to you today after addressing some of the feedback you shared with us following the initial rollout. Re-releasing the new Japanese IME The latest version of the IME has enhanced key customization options and improved candidate window reliability (fixing an issue where it wouldn’t show), and we’re looking forward to you trying it out. Because we want to ensure the best possible typing experience, this will be a staggered rollout – some Insiders will get it today, and we will carefully review both metrics and your comments before pushing the IME out to everyone. Note: We are aware of compatibility issues with some game applications and the team is working on them – we’ll let you know when this has been addressed. Introducing the Office app for Windows 10 The app is a great starting point for Office that helps you easily find all your files in one place or easily access any Office solution available to you. It knows to connect you to the Office rich clients if they are installed on your computer or it will send you to the web version of Office if they’re not. IT will also appreciate the ability to customize the app by integrating other line of business applications that use Azure Active Directory into the experience and apply corporate branding to the app. Get more done with Cortana and Microsoft To-Do Want just one to-do list that works twice as hard for you? Save time and stay organized – Cortana helps by adding your reminders and tasks to your lists in Microsoft To-Do with this feature preview, so you can stay on top of what matters most. Use your voice, your PC, your phone – your choice. Streamline your tasks – your lists and reminders from across Microsoft To-Do, Cortana, and tasks in Outlook can now become one, centrally located in your Microsoft To-Do app. Use Microsoft To-Do anywhere: on your Android or iPhone, with Cortana, or on your Windows 10 PC. You can also access it from the web. It’s automatically synced so you never miss a beat. With this integration, we are furthering efforts to seamlessly sync your to-do lists across Microsoft To-Do, Cortana, and your tasks in Outlook. Read the full article
1 note
·
View note
Text
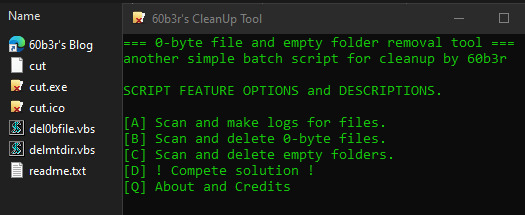
60b3r’s スクリプト: CUT (CleanUpTool)
IF anything that could happen with Windows, is it got cluttered fast. Especially if you (like me) love downloading and testing random freewares and then find out that the fucking installers contains major bloatwares and malwares. Most of the time, the crappy uninstaller bundles are also not that great to get rid of all the nasty shit they have already extracted into my computer. Sometimes I need to uninstall them one by one, from the broken shortcuts, unused runtimes and libraries, and the leftover config files on %AppData%. That’s why most of the time now I try to get myself used to PortableApps (no endorsement here, but they have done a great job!). Early this morning (well it’s still 3 AM when I suddenly woke up from my sleep) I find myself killing the time and went for a hunt for those sneaky registry keys I need to search manually to remove Corel’s Protexis services and Visual Studio Redist uninstallation entries which didn’t vanish after I declutter them yesterday from Control Panel.
One of the things that I find myself very hard to get rid of ONE BY ONE (other than the regedit entries stuff) is the unused empty directories and frustrating zero-byte files locked by services you don’t know you have, leftover from installations. After searching the whole freeware and portable alternatives for programs, I found Jonas John’s Remove Empty Directories (a.k.a. RED) and was immediately relieved. His app has so many features and help clean up jobs easily. Gonna get this app into the hall of fame with CCleaner though. I dont get it why Piriforn haven’t included this feature in their suite. Or has them? I don’t know. I use the free version. Hahahaha. However, being a very stubborn and eclectic former script kiddie that I am, I decided to quickly make a batch script for my own to automate the process of deleting zero-byte files and empty folders that are found scattering throughout my harddisk. No more manual screening like I just did with the registry. So damn tiring. I opened the Notepad and started writing these codes, while at the same time scrounging old batch programming books on my archives. I write this app from scratch, but time seems to move fast when you do something you love, right? By the time I finished coding and debugging the core functions, the sun is already out.
Problem is, I have technically forgot most of my hacker training programming forum pages back then when I was in junior high school. Particularty embarassing, I forget most of the simple yet powerful FOR-DO syntax: it was almost 5 years since I last code in batch programming to automate netsh, ipconfig, ncpa and inetcpl commands for my home office setup. To be honest, who likes to code using batch? I do. Because it is so simple with no databases (someone say yes databases ughh so relatable). I also code using VisualBasic scripts back then to make computer worms and the nasty virus I program to open the CD tray every 5 minutes. Really, man? VBS? YES. I then decided to join Biology classes for senior high school and graduated Biotech instead. No regrets. I love biology. Hope soon I will be able to join Master’s.
Sadly, I am not that ‘computer literate’ anymore like I used to be; since I put my efforts and energy into studying Biology, something I also love. Even sometimes I get myself to study coding (like making the spinning X sign on the blog’s top left navbar using CSS) from time to time whenever I am not busy doing other things. Come on, I am not those hackers over Mr. Robot. I am just a regular citizen, not a beautiful and unique snowflake. I am the same decaying organic matter as everything else. What. But, moving on. Just another sad story for another day.

I kept surfing around the stackoverflow to find solution regarding the CHOICE and ERRORLEVEL syntax because I am a forgetful tomato. I also scour other old—dinosaur-age—blogs for batch programming tutorials and found Raymond Chen’s old blogpost over here. He made a script to help delete empty folders. I tweaked it around a bit to include folders with spaces. Then I added the function to scan zero-byte files. The rest are the delete functions for the scanned file and folder. To conclude my early morning rush, I ended up making an executable file, complete with a cute icon from dryicons and packed by Fatih’s compiler. I then scanned the file over to VirusTotal to make sure people can distribute it. Problem is, I sometimes forget it that executables with file operations (especially deleting stuffs) are sometimes taken by antivirus engines as rogue attempt of some suspicious code. By the looks of it, 18 out of 70 engines flagged my tiny simple app as generic malware. Here is the detection report. But I can guarantee you as long as you can read and make your own script, you will not become a victim of software counterfeiting identity theft by some random trojan. Moreover, all the top antiviruses detect no harmful activities from my app. Phew. No problems with the file packer then. No rootkits, too.
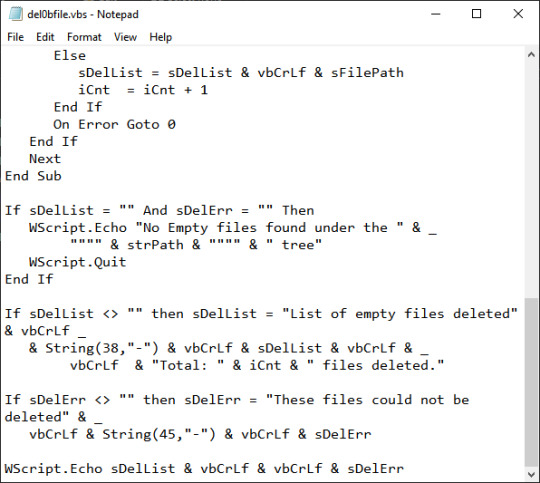
For you who wants to just use the final program and scrub those nasty dirt off the disks right away, go here (GDrive). For those who just want to make a batch script file for ease of use and editing, you can use my script. Here is the core function, raw, non-user friendly version of the script:
@echo off echo CUT by 60b3r pause echo executing purging sequence... for /r %%F in (*.*) do ( if %%~zF==0 del "%%F" ) for /f "delims=" %%i in ( 'dir /s /b /ad ^| sort /r' ) do rd "%%i" 2>NUL pause
You can modify it and redistribute it freely, and also if you can get the deprecated features working (see about page), do email me. Gonna fix those and add more features. Also follow me on my GitHub repository, though I am not going to update much on there. I am no 1337 programmer, you know? Just a regular hobbyist doing random stuff. This is actually one of my numerous simple scripts collection (yeah, I was just a script kiddie gathering ready to use scripts for pathetic hacking dramas). Next time, I will update you on how to make the ultimate simple networking toolkit, merging all my script tools into one executable suite. All only using batch programming and notepad. No big deal, just a simple, humble, and very disgusting reuse of existing MS-DOS command.
Thanks for reading my simple tutorial!
0 notes
Text
Download Unlock With WiFi .APK
Unlock With WiFi is now free! Thank you to all my customers who have supported me over the years. I no longer have time to support this app, so I made it free for everyone. Enjoy!
ANNOUNCEMENT: This app has a successor named SkipLock. It is similar to Unlock With WiFi, but with some major new features.
For a full explanation of why SkipLock was created, see this blog post: http://benhirashima.com/posts/the-rebirth-of-unlock-with-wifi/
Tired of entering your password every time you turn on your phone? Unlock With WiFi™ unlocks your phone when you’re connected to your home WiFi network. When you’re at home, or work, you don’t need to worry about losing your phone, so why should you have to enter your password?
Unlock With WiFi is the leading password convenience app on the market. It’s focus is on reliability, quality, and a great user experience. The setup wizard makes it easy to setup, and helpful dialogs are displayed if something isn’t quite right.
How it works:
When you get home and connect to your WiFi network, your device will unlock. Then when you leave, and the WiFi disconnects, the device will lock again. You have to enter your password the first time after you connect to your WiFi network. This is so that if someone steals or finds your phone, they can’t just bring it to your house to unlock it. After you enter your password once while connected to your WiFi network, you won’t have to enter it again until you leave/disconnect. This is great for SMS texting!
Additional Features:
You can also set a lock delay, for when you’re not at home. The default delay is set to 5 seconds (you can adjust it), so when you turn the screen off, the device won’t lock until 5 seconds have passed. That way, if you remember something you forgot to do, you can turn it back on without entering your password. This feature is considered experimental at this time. It works on most devices, but isn’t guaranteed to work on all devices.
There are also battery saving options to:
Turn off WiFi when you leave home Turn on Bluetooth when you leave home Turn off Bluetooth when you get home Turn off Auto Sync when you leave home Turn on Auto Sync when you get home WidgetLocker integration
IMPORTANT: To uninstall this app, you must select Uninstall from the menu inside the app. The normal way won’t work if device admin mode is enabled.
WARNING: This app doesn’t work on some phones. Please read this description carefully, and the FAQ. http://benhirashima.com/unlockwithwifi/faq
Known Limitations:
Does not work with Android Pay, according to user reports Does not work on Android 5+. However, Android 5.0 has much of SkipLock’s functionality built in now. The app is not compatible with Motorola Skip or Dots. Do not install this app on the SD card. It will not be secure if you do. It won’t work on phones that have full device encryption enabled. It won’t work if your employer enforces a password policy on your phone. Only PINs and passwords can be used in Android 4.0 and above. Patterns and face unlock are not supported. Unlock With WiFi is incompatible with some antivirus and battery saver apps. See the FAQ for details. Make sure to exclude Unlock With WiFi from your task killer apps, or it won’t work properly.
See the FAQ for more details http://benhirashima.com/unlockwithwifi/faq
Tech support is only available in English.
By downloading this software, you are agreeing to the End User License Agreement, which can be read here: http://benhirashima.com/unlockwithwifi/eula.
This app uses the Device Administrator permission. This is necessary to lock/unlock the device. Marked the app as incompatible with Android 5+. Due to changes in Android 5.0, it is no longer possible for an app to unlock the device. The good news for you is that Android 5.0 has much of SkipLock’s functionality built in now: http://www.droid-life.com/2014/11/18/android-5-0-feature-google-updates-smart-lock-on-lollipop-to-include-trusted-places/
from APK Download https://apkdownloadd.com/download-unlock-with-wifi-apk/
0 notes
Link
Save Hundreds of Dollars on Computer Repairs with Kirkham’s Healthy Computer E-Kit Flash Drive
By in home and onsite computer, tablet and smart cell phone tutor, trainer, mobile virus removal and repair specialist, trained dual certified teacher J. Richard Kirkham B.Sc. of Honolulu Hawaii covering all of Oahu. Call or
Text 808.224.1870
Text only for the rest of the U.S. for
English speaking remote computer support
for help with Windows PCs, Surface tablets or Apple/Mac computers. Do It Yourselfers
download Mr. Kirkham's Ebook
Increase computer speed
Extend computer life
Remove identity stealing computer spyware completely
Backup your files
Your Computer Will Break Down It’s a Fact
90% of breakdowns of Windows PCs and Apple computers are due to poor maintenance. Computer repair and even computer maintenance can be expensive.
The primary cause of this expense is the not broken don’t fix it attitude.
Do You:Get the oil changed in your car? Why? It’s still running isn’t it? Haven’t you already spent a lot of money on your car?
Check the air pressure on your tires? Why? Are they flat? Do you really have time for that?
Put sunscreen on? Why? Do you have skin cancer? Isn't that a waste of money?
Are you getting my point?
Why would you treat your computers any different!? Doesn’t it cost more to fix your car when you DON’T have the oil changed? Your computer is the same way! That’s why I make house calls and office onsite calls for my computer, cell phone and tablet clients every four to six months here in Honolulu Hawaii or anywhere on Oahu. Text or call me 224.1870 if you have a computer and live on Oahu. I’ll see problems before you do and stop them from crashing your computer. It’s why I named my website, which I designed myself using my automation programming skills,
ProactiveComputerSupport
If You’re a Computer User NOT Living in Honolulu Hawaii or Anywhere on Oahu Here is Your Computer Crash Prevention Maintenance Solution!
Kirkham’s Healthy Computer E-Kit Flash Drive
Rick I Have Antivirus Software. That Takes Care of Everything Right?You’re not the first person to think that don’t worry, but sadly no. Think of antivirus software as car insurance. It’s only a small part of the solution. The modern computer viruses and spyware come into your computer disguised as normal software (trojans). They’re let into your computer by your antivirus software. The computer viruses then either take over your internet browser, such as Chrome, Safari, FireFox and Edge and
Record what you do online
Cause pop ups even on your desktop
Redirect you to sites hackers are paid for possibly causing more viruses and spyware to download into your computer!
Scare you into calling the hackers and being scammed (I had an in home computer client show me a check he had written out for $3000 to computer virus scammers when he called me for a second opinion).
Or they download into your Windows PC or Apple computer. The modern computer viruses mask themselves as actual programs (trojans) so your antivirus software ignores the malicious software.
Recently I removed a difficult search engine virus from an Apple computer and a Windows search virus which had loaded itself onto a PC and stayed right on the desktop of the computer. The Windows PC client had good antivirus software, which had been replaced by a rogue antivirus program as part of the infection. The Apple computer had no virus protection, until I installed free antivirus software (included in your healthy computer flash drive) after removing the virus, and had an up to date operating system.Computer antivirus software does not:Remove temporary internet files
Remove cookies
Remove PUPs (possibly unwanted programs) from the memory of your computer used to run programs and videos (thus causing buffering)
All the above items contribute to the slowing down of your computer. The above items also contribute to increasing wear and tear of your computer since it has to work harder to perform normal tasks. It’s like having to put your gas pedal all the way to the floor just to go 20 mph.
Nor is There A Single Program to Do All of The Above!
Despite what the multimillion dollar advertising departments of these huge software computer protection companies want you to believe there is not a single program to do all of the above. If there was it would take up a lot of memory on your computer used to prevent buffering of your videos and drastically slow down your internet and web pages loading.
How Do I Know How Expensive Computer Repair and Computer Maintenance Can Be?
Because that’s what I do for a living! I’m Rick Kirkham and I’m one of the best in home and onsite
computer virus removal specialists, in Honolulu Hawaii
covering all of Oahu. I charge $95.00 per hour with a $75.00 per hour cash discount to troubleshoot problems, repair computers and remove dangerous, identity stealing, computer viruses and spyware. Sure there are a few ITs who charge less than I do. How do I know that? Because I keep cleaning up their messes when the computer viruses return. There’s even someone out there who just wipes your computer completely so you lose all your work, photos and purchased software such as Office. Don’t worry, some of those poor souls are my in home computer clients now and I’m taking good care of them.
That’s why I’m making this Kirkham's Healthy Computer Keeper E-Kit Flash Drive available to you.
What is The Kirkham's Healthy Computer Keeper E-Kit Flash Drive
The Kirkham's Healthy Computer Keeper comes to you on a flash drive, also referred to as a thumb drive. I also have a
downloadable version
of it without the file rescue system with links to the same programs that come with your healthy computer proactive maintenance flash drive. The Kirkham's Healthy Computer Keeper contains simple step by step directions to maintain your computer yourself and not have to pay someone else to do it for you. This will save you hundreds of dollars as you use The Kirkham's Healthy Computer Keeper on a monthly basis.
The Kirkham's Healthy Computer Keeper flash drive contains the software I use myself to professionally clean my
in home computer clients
computers here on Oahu! I cannot make house calls to the world. I need to share my unique methods with the world so people may continue to communicate using their computers with loved ones regardless of their locations.
"A Simple, easy to use monthly toolkit that allows users to keep their PC's Healthy with minimal effort" -
Ryan T. M. Reiffenberger
. Computer Technician
What’s In Kirkham’s Healthy Computer Keeper E-Kit Flash Drive
Software I use myself as a professional to maintain and optimize computers and remove the toughest computer viruses and spyware out there.
Simple directions in plain English how to use the software. Don’t worry. As one of the few trained dual certified teachers in the computer training field I translate Geekenese to English perfectly.
Bonus for a limited time!:
The Big Plain English Computer Tablet and Cell Phone Tips and Reference Guide
Contains tips, lessons and articles on making your computer, tablet and cell phone lfe easier.
Repair and troubleshooting tips and tactics I use myself.
How to remove computer viruses and spyware (I hope my competitors don’t buy this)Using all this will help to keep your computer, tablet and cell phoneFast
Efficient
Lasting longer
Virus free
Spyware free
Do You Need to Recover Files from a Computer that Will Start but You Can’t Login?
This could mean you simply forgot your password
Your employee left but changed the computer password
The computer starts but will not go to the menu
Kirkham’s Healthy Computer Keeper E-Kit comes built in with LUbuntu! A safe operating system that will sit right on this flash drive allowing you to get files from a semi-crashed computer or just a computer whose password you don’t remember!
Naturally I use my skills as an in home computer tutor and trained, dual certified teacher to give you simple, plain English directions on how to access your locked or semi-crashed computer.
Folks This is a No Brainer!
A single one hour visit from me or any good IT costs $75 to $95. For a very limited time for just
$49.95 you can get everything above and SAVE ON COMPUTER REPAIRS!
Oahu residents only call or text in home computer tutor and virus removal specialist J. Richard Kirkham B.Sc. at 224.1870 for a house or office call or
hand-delivery information!
site search
by freefind
advanced
Unique Local Onsite SEO Service on Oahu
to Help Your Business Be Found Online Above Your Competitors! Honolulu Hawaii and all of Oahu call or
text 808.224.1870
email my main business email
Text 40404 follow ComputerHelpHi or Follow ComputerHelpHi on Twitter for Lightning Fast Notifications of Free Computer Information Cell Phone News Tablet Tips and Computer Virus Warnings
Custom5DollarWebsites.com
0 notes
Text
Hello Friends, Welcome and Good Morning,
Today Let’s talk something different. My today’s topic is something very different but I feel it is important things to share with you all.
In today’s world of technology, it’s so easy and comfortable to do things instantly and conveniently.
Like, If I want to travel to someplace I have to just go online and can book my tickets and book a room to stay without going to that bus service provider. We will also get good discounts. So useful.
If I want to pay bills I can simply go to online and can pay my bills without standing in long ques. SO many things like online recharge, fund transfer, sending important documents, sharing photos with my friends. Well, let’s not waste to time in discussing all this. let’s come to point.
Yesterday I got one message from my friend saying just click this link and you will get 50 rs Paytm cash. And one more sentence added to that thing that “I got it. must try it”
There are so many messages like that and we get various links of fake news or promotions in WhatsApp messenger. All these things are great risks. Via those methods, You phone or bank account or profile may be hacked. You have no idea but your every action can be tracked.
So let me share some tips and websites links that will help us to be more secure and safe.
Tips:
Never Ever click of links that show fake promotion like one I shared above. First, check on the orginal website or you can mail to its customer care. Its a best and common hacking trick used to get all your details.
Never ever open links from unknown sources and I request you to don’t be in hurry to forward such links to your friends and family members. always check on google or original site for validity.
Always open links that have HTTPS: written on it and not HTTP only. Here “S” stands for Secure. Still before sharing or opening check its validity.
A secure website has its name written on the address bar. For more details click here and look at the address bar.
Never share your personal details on phone saying that we are calling from so and so the bank or company. Especially your card number, PIN number, CCV, bank account number etc.
Always change your password for your Net banking, Email, Social Media account, Cards periodically. And Never use simple passwords like Birthdate, mobile number, your name like that. In hacking, there is a subject called Social engineering that deals with getting your details from social media.
If possible never use Cracked versions of software it is the most common way to infect your pc or mobile phone.
Always have antivirus installed and keep it updated for the latest virus update definition.
For mobile phone never install application for an unknown source. Always see reviews and vendor of that software.
Especially for Girls never ever check your social media account from workplace computer or from someone else’s mobile phone. Never accept a friend request from unknown person although you have so many mutual friends. Have a habit of logout from the end of the session and always a clear history of your browsing.
Never save password on browsers of important websites like social media and net banking. always set a mobile alert for each time you log in.
while installing application always check what permissions they ask and never ever blindly allow it. Like if software wants to allow your gallery or messaging or want to access your location always think twice before allowing that application. if the application has nothing to with your gallery or messaging or location simple deny it.
If possible encrypt your mobile. will write a short blog on that soon.
Never share your live location on Facebook or Instagram. One incident of theft in one city occur and thief confessed that we knew that they were not home by seeing their post on Facebook. So be aware.
If I forgot to write down something very important kindly comment it below and help in spreading awareness
In case if any day something bad happens or you will be a victim of the cyber attack immediately go to police and cybersecurity specialist to help you.
Important Sites to Visit:
https://www.cyberswachhtakendra.gov.in/security-tools.html
https://www.cert-in.org.in/SecurityofPC/SPC_colored_English/large/credit_frauds.html
https://www.digicert.com/blog/buy-site-know-website-secure/
https://www.cert-in.org.in/SecurityofPC/SPC_colored_English/large/index.html
https://infosecawareness.in/family/
Some of the very important Documents to download and read
Mobile_phone_Security
USB_Security
Phishing
Desktop_security
Broadband_Security.
Day 4 08/12/2018 Cybersecurity Tips Hello Friends, Welcome and Good Morning, Today Let's talk something different. My today's topic is something very different but I feel it is important things to share with you all.
0 notes