#spyware for mobile
Explore tagged Tumblr posts
Text
I hate that every drive thru begins with a recording of a white person asking me about mobile orders. No, I'm not using the app, let me talk to a human PLEASE.
#fast food#drive thru#''will you be using our mobile app today?''#no i will not#and i never will#i will never use the app#i will never agree to the terms of service that forbid me from suing them if they mutilate me#i will never clutter my phone with corporate spyware that interfaces with social media to show me ads and sell my data to the highest bidde#i just want some fucking chicken#i want it to stop#i want it all to stop#please god
12 notes
·
View notes
Note
Yeah my experience with tiktok was downloading it, feeling confused by the random selection of content, and saying to my siblings, "I got a tiktok, what do I do with it?" To which both of them immediately replied in unison, "delete it"
🤣 See, my algorithm was so on point as far as holding my attention, I spent a horrifying percentage of that day on my phone, and by sunset I was like. This is going to destroy society. And I deleted it.
#never touched it again#it helped to later discover it was Chinese spyware that wasn’t allowed on our Air Force bases but still#the spine-chilling part was the hours I’d been entranced by dark magic#mobile#x
14 notes
·
View notes
Text
Hey uhh heads up to anyone w t-mobile, I just got a handful of apps automatically installed without my permission (including tiktok, temu, candy crush saga and others), so maybe check and keep an eye out for that? They were automatically installed by t-mobile's AppSelector, afaik you can't get rid of it(?) but you can at least disable it from your settings so hopefully that will help.
#ignore me#maddie lifeblogs#tmobile#t-mobile#I saw a post about google play installing spyware but now this??#ngl I'm kinda livid that they can just sneak stuff like that on your phone for no apparent reason#I don't want to be anywhere near tiktok get that off my phone
0 notes
Text
Steps for Effective Phone Monitoring with ONEMONITAR
Monitor phones effortlessly with ONEMONITAR! Easily set up, run discreetly in hidden mode, and access call recordings, locations, and activity logs through a secure dashboard. Perfect for smart and effective monitoring.

0 notes
Note
ive got the boop button on mobile. maybe wait a bit or close and re open tumblr
oooh cool, I'll give it a shot!
#thing is I don't use the app anymore on mobile#(stopped to hide the activity from parental spyware I had a while back and got to used to the mobile website to consider switching back)#so idk if it'll be the same#but thanks for the info anyway#mobile users go refresh the app!!!#psii.txt#ask#anon
0 notes
Text
I think most of us should take the whole ai scraping situation as a sign that we should maybe stop giving google/facebook/big corps all our data and look into alternatives that actually value your privacy.
i know this is easier said than done because everybody under the sun seems to use these services, but I promise you it’s not impossible. In fact, I made a list of a few alternatives to popular apps and services, alternatives that are privacy first, open source and don’t sell your data.
right off the bat I suggest you stop using gmail. it’s trash and not secure at all. google can read your emails. in fact, google has acces to all the data on your account and while what they do with it is already shady, I don’t even want to know what the whole ai situation is going to bring. a good alternative to a few google services is skiff. they provide a secure, e3ee mail service along with a workspace that can easily import google documents, a calendar and 10 gb free storage. i’ve been using it for a while and it’s great.
a good alternative to google drive is either koofr or filen. I use filen because everything you upload on there is end to end encrypted with zero knowledge. they offer 10 gb of free storage and really affordable lifetime plans.
google docs? i don’t know her. instead, try cryptpad. I don’t have the spoons to list all the great features of this service, you just have to believe me. nothing you write there will be used to train ai and you can share it just as easily. if skiff is too limited for you and you also need stuff like sheets or forms, cryptpad is here for you. the only downside i could think of is that they don’t have a mobile app, but the site works great in a browser too.
since there is no real alternative to youtube I recommend watching your little slime videos through a streaming frontend like freetube or new pipe. besides the fact that they remove ads, they also stop google from tracking what you watch. there is a bit of functionality loss with these services, but if you just want to watch videos privately they’re great.
if you’re looking for an alternative to google photos that is secure and end to end encrypted you might want to look into stingle, although in my experience filen’s photos tab works pretty well too.
oh, also, for the love of god, stop using whatsapp, facebook messenger or instagram for messaging. just stop. signal and telegram are literally here and they’re free. spread the word, educate your friends, ask them if they really want anyone to snoop around their private conversations.
regarding browser, you know the drill. throw google chrome/edge in the trash (they really basically spyware disguised as browsers) and download either librewolf or brave. mozilla can be a great secure option too, with a bit of tinkering.
if you wanna get a vpn (and I recommend you do) be wary that some of them are scammy. do your research, read their terms and conditions, familiarise yourself with their model. if you don’t wanna do that and are willing to trust my word, go with mullvad. they don’t keep any logs. it’s 5 euros a month with no different pricing plans or other bullshit.
lastly, whatever alternative you decide on, what matters most is that you don’t keep all your data in one place. don’t trust a service to take care of your emails, documents, photos and messages. store all these things in different, trustworthy (preferably open source) places. there is absolutely no reason google has to know everything about you.
do your own research as well, don’t just trust the first vpn service your favourite youtube gets sponsored by. don’t trust random tech blogs to tell you what the best cloud storage service is — they get good money for advertising one or the other. compare shit on your own or ask a tech savvy friend to help you. you’ve got this.
#internet privacy#privacy#vpn#google docs#ai scraping#psa#ai#archive of our own#ao3 writer#mine#textpost
1K notes
·
View notes
Note
After seeing your weatherbugapp reblog i installed duckduckgo and tried it.
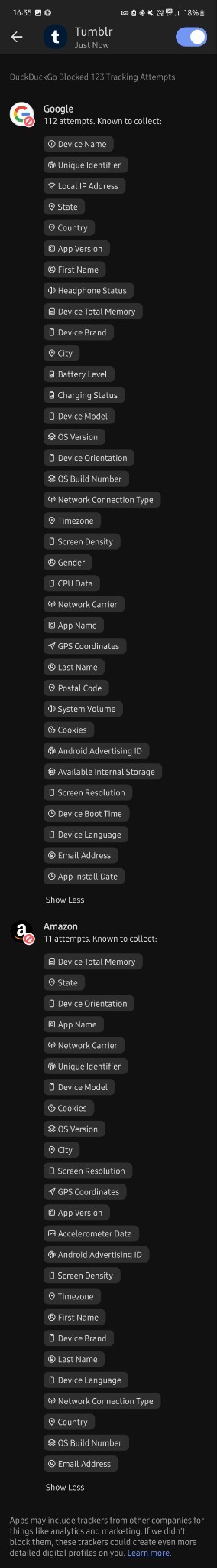
I don't know much about technology tbh but i downloaded this app less than 30 mins ago and in that time google tried to track me 112 times?? And they tried to collect finger prints? And my first and last name? And my gender? And my country, state and city? My gps coordinates? My postal code? My network carrier? My fricking battery level for whatever reason? Can you please tell me if this is normal at all, because i'm freaking out right now. I just turned 18 and started using mobile banking and stuff and this shit scares me
Why tf does it need to know my screen density???my system volume????my charging status????? What tf are they cooking
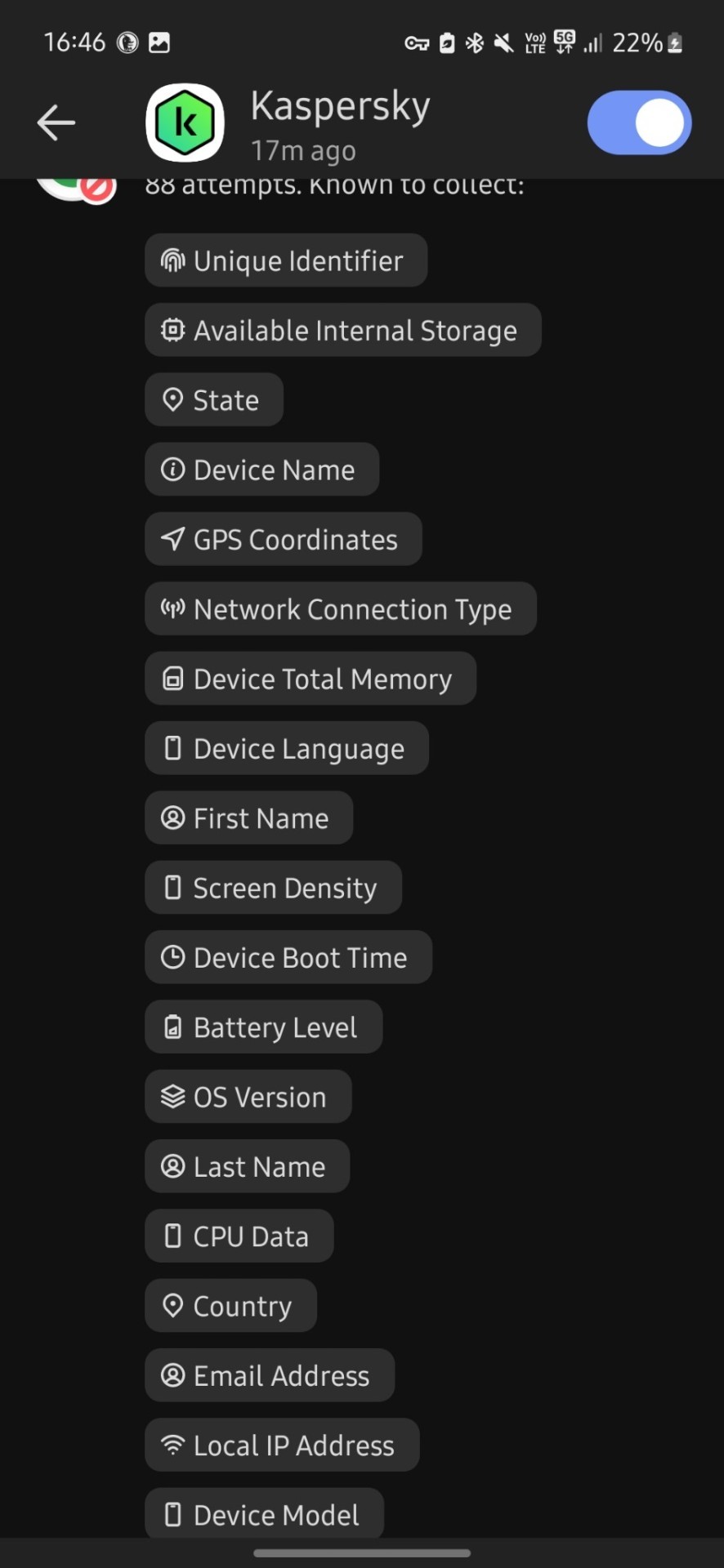
Now it's at 476 tracking attempts bro???? barely 5 mins passed.....
I condensed your three asks into one for readability!
And yeah, I'm very far from an expert about any of this, but as far as I know that's just. Normal. That's the normal amount of spying they're doing on your phone. I assume the numbers we see are to some extent because having been foiled, a lot of these scripts try repeatedly, since I can't imagine what use thousands of trackers per phone would be even to the great aggregators.
Tracking the phone stuff like screen resolution and battery level is because (apart from that definitely not being considered remotely 'private' so it's Free Real Estate) in aggregate that data can be used to track what phone use patterns are like on a demographic scale and therefore. Where the smart money is.
Almost all of this is getting sold in bulk for ad targeting and market analysis. This does presumably make it very hard to notice when like. Actually important stuff is being spied on, which is why I feel better about Having Apps with the duckduckgo app blocker thing.
My bank's app reportedly sells data to a couple aggregators including Google. Not like, my banking info, but it's still so offensive on principle that I avoid using the app unless I have to, and force stop it afterward.
The patterns that show up on the weekly duckduckgo blocker report are interesting. Hoopla attempts about two orders of magnitude more tracking than Libby, which makes sense because they're a commercial streaming service libraries pay by the unit for access, while Libby is a content management software run by a corporation that values its certification as a 'B' company--that is, one invested in the public good that can be trusted. The cleanness of their brand is a great deal of its value, so they have to care about their image and be a little more scrupulous.
Which doesn't mean not being a little bit spyware, because everything is spyware now. Something else I've noticed is that in terms of free game apps, the polished professional stuff is now much more invasive than the random kinda janky thing someone just threw together.
Back in the day you tended to expect the opposite, because spyware was a marginal shifty profit-margin with too narrow a revenue stream to be worth more to an established brand than their reputation, but now that everyone does it there's not a lot of reputation cost and refraining would be sacrificing a potential revenue stream, which is Irresponsible Conduct for a corporation.
While meanwhile 'developing a free game app to put on the game store' is something a person can do for free with the hardware they already have for home use, as a hobby or practice or to put on their coding resume. So while such apps absolutely can be malicious and more dangerous when they are than The Big Brand, they can also be neutral in a way commercial stuff no longer is. Wild world.
But yeah for the most part as far as I can make out, these are just The Commercial Panopticon, operating as intended. It's gross but it probably doesn't indicate anything dangerous on an individual level.
56 notes
·
View notes
Text
How to design a tech regulation
TONIGHT (June 20) I'm live onstage in LOS ANGELES for a recording of the GO FACT YOURSELF podcast. TOMORROW (June 21) I'm doing an ONLINE READING for the LOCUS AWARDS at 16hPT. On SATURDAY (June 22) I'll be in OAKLAND, CA for a panel (13hPT) and a keynote (18hPT) at the LOCUS AWARDS.

It's not your imagination: tech really is underregulated. There are plenty of avoidable harms that tech visits upon the world, and while some of these harms are mere negligence, others are self-serving, creating shareholder value and widespread public destruction.
Making good tech policy is hard, but not because "tech moves too fast for regulation to keep up with," nor because "lawmakers are clueless about tech." There are plenty of fast-moving areas that lawmakers manage to stay abreast of (think of the rapid, global adoption of masking and social distancing rules in mid-2020). Likewise we generally manage to make good policy in areas that require highly specific technical knowledge (that's why it's noteworthy and awful when, say, people sicken from badly treated tapwater, even though water safety, toxicology and microbiology are highly technical areas outside the background of most elected officials).
That doesn't mean that technical rigor is irrelevant to making good policy. Well-run "expert agencies" include skilled practitioners on their payrolls – think here of large technical staff at the FTC, or the UK Competition and Markets Authority's best-in-the-world Digital Markets Unit:
https://pluralistic.net/2022/12/13/kitbashed/#app-store-tax
The job of government experts isn't just to research the correct answers. Even more important is experts' role in evaluating conflicting claims from interested parties. When administrative agencies make new rules, they have to collect public comments and counter-comments. The best agencies also hold hearings, and the very best go on "listening tours" where they invite the broad public to weigh in (the FTC has done an awful lot of these during Lina Khan's tenure, to its benefit, and it shows):
https://www.ftc.gov/news-events/events/2022/04/ftc-justice-department-listening-forum-firsthand-effects-mergers-acquisitions-health-care
But when an industry dwindles to a handful of companies, the resulting cartel finds it easy to converge on a single talking point and to maintain strict message discipline. This means that the evidentiary record is starved for disconfirming evidence that would give the agencies contrasting perspectives and context for making good policy.
Tech industry shills have a favorite tactic: whenever there's any proposal that would erode the industry's profits, self-serving experts shout that the rule is technically impossible and deride the proposer as "clueless."
This tactic works so well because the proposers sometimes are clueless. Take Europe's on-again/off-again "chat control" proposal to mandate spyware on every digital device that will screen everything you upload for child sex abuse material (CSAM, better known as "child pornography"). This proposal is profoundly dangerous, as it will weaken end-to-end encryption, the key to all secure and private digital communication:
https://www.theguardian.com/technology/article/2024/jun/18/encryption-is-deeply-threatening-to-power-meredith-whittaker-of-messaging-app-signal
It's also an impossible-to-administer mess that incorrectly assumes that killing working encryption in the two mobile app stores run by the mobile duopoly will actually prevent bad actors from accessing private tools:
https://memex.craphound.com/2018/09/04/oh-for-fucks-sake-not-this-fucking-bullshit-again-cryptography-edition/
When technologists correctly point out the lack of rigor and catastrophic spillover effects from this kind of crackpot proposal, lawmakers stick their fingers in their ears and shout "NERD HARDER!"
https://memex.craphound.com/2018/01/12/nerd-harder-fbi-director-reiterates-faith-based-belief-in-working-crypto-that-he-can-break/
But this is only half the story. The other half is what happens when tech industry shills want to kill good policy proposals, which is the exact same thing that advocates say about bad ones. When lawmakers demand that tech companies respect our privacy rights – for example, by splitting social media or search off from commercial surveillance, the same people shout that this, too, is technologically impossible.
That's a lie, though. Facebook started out as the anti-surveillance alternative to Myspace. We know it's possible to operate Facebook without surveillance, because Facebook used to operate without surveillance:
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3247362
Likewise, Brin and Page's original Pagerank paper, which described Google's architecture, insisted that search was incompatible with surveillance advertising, and Google established itself as a non-spying search tool:
http://infolab.stanford.edu/pub/papers/google.pdf
Even weirder is what happens when there's a proposal to limit a tech company's power to invoke the government's powers to shut down competitors. Take Ethan Zuckerman's lawsuit to strip Facebook of the legal power to sue people who automate their browsers to uncheck the millions of boxes that Facebook requires you to click by hand in order to unfollow everyone:
https://pluralistic.net/2024/05/02/kaiju-v-kaiju/#cda-230-c-2-b
Facebook's apologists have lost their minds over this, insisting that no one can possibly understand the potential harms of taking away Facebook's legal right to decide how your browser works. They take the position that only Facebook can understand when it's safe and proportional to use Facebook in ways the company didn't explicitly design for, and that they should be able to ask the government to fine or even imprison people who fail to defer to Facebook's decisions about how its users configure their computers.
This is an incredibly convenient position, since it arrogates to Facebook the right to order the rest of us to use our computers in the ways that are most beneficial to its shareholders. But Facebook's apologists insist that they are not motivated by parochial concerns over the value of their stock portfolios; rather, they have objective, technical concerns, that no one except them is qualified to understand or comment on.
There's a great name for this: "scalesplaining." As in "well, actually the platforms are doing an amazing job, but you can't possibly understand that because you don't work for them." It's weird enough when scalesplaining is used to condemn sensible regulation of the platforms; it's even weirder when it's weaponized to defend a system of regulatory protection for the platforms against would-be competitors.
Just as there are no atheists in foxholes, there are no libertarians in government-protected monopolies. Somehow, scalesplaining can be used to condemn governments as incapable of making any tech regulations and to insist that regulations that protect tech monopolies are just perfect and shouldn't ever be weakened. Truly, it's impossible to get someone to understand something when the value of their employee stock options depends on them not understanding it.
None of this is to say that every tech regulation is a good one. Governments often propose bad tech regulations (like chat control), or ones that are technologically impossible (like Article 17 of the EU's 2019 Digital Single Markets Directive, which requires tech companies to detect and block copyright infringements in their users' uploads).
But the fact that scalesplainers use the same argument to criticize both good and bad regulations makes the waters very muddy indeed. Policymakers are rightfully suspicious when they hear "that's not technically possible" because they hear that both for technically impossible proposals and for proposals that scalesplainers just don't like.
After decades of regulations aimed at making platforms behave better, we're finally moving into a new era, where we just make the platforms less important. That is, rather than simply ordering Facebook to block harassment and other bad conduct by its users, laws like the EU's Digital Markets Act will order Facebook and other VLOPs (Very Large Online Platforms, my favorite EU-ism ever) to operate gateways so that users can move to rival services and still communicate with the people who stay behind.
Think of this like number portability, but for digital platforms. Just as you can switch phone companies and keep your number and hear from all the people you spoke to on your old plan, the DMA will make it possible for you to change online services but still exchange messages and data with all the people you're already in touch with.
I love this idea, because it finally grapples with the question we should have been asking all along: why do people stay on platforms where they face harassment and bullying? The answer is simple: because the people – customers, family members, communities – we connect with on the platform are so important to us that we'll tolerate almost anything to avoid losing contact with them:
https://locusmag.com/2023/01/commentary-cory-doctorow-social-quitting/
Platforms deliberately rig the game so that we take each other hostage, locking each other into their badly moderated cesspits by using the love we have for one another as a weapon against us. Interoperability – making platforms connect to each other – shatters those locks and frees the hostages:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
But there's another reason to love interoperability (making moderation less important) over rules that require platforms to stamp out bad behavior (making moderation better). Interop rules are much easier to administer than content moderation rules, and when it comes to regulation, administratability is everything.
The DMA isn't the EU's only new rule. They've also passed the Digital Services Act, which is a decidedly mixed bag. Among its provisions are a suite of rules requiring companies to monitor their users for harmful behavior and to intervene to block it. Whether or not you think platforms should do this, there's a much more important question: how can we enforce this rule?
Enforcing a rule requiring platforms to prevent harassment is very "fact intensive." First, we have to agree on a definition of "harassment." Then we have to figure out whether something one user did to another satisfies that definition. Finally, we have to determine whether the platform took reasonable steps to detect and prevent the harassment.
Each step of this is a huge lift, especially that last one, since to a first approximation, everyone who understands a given VLOP's server infrastructure is a partisan, scalesplaining engineer on the VLOP's payroll. By the time we find out whether the company broke the rule, years will have gone by, and millions more users will be in line to get justice for themselves.
So allowing users to leave is a much more practical step than making it so that they've got no reason to want to leave. Figuring out whether a platform will continue to forward your messages to and from the people you left there is a much simpler technical matter than agreeing on what harassment is, whether something is harassment by that definition, and whether the company was negligent in permitting harassment.
But as much as I like the DMA's interop rule, I think it is badly incomplete. Given that the tech industry is so concentrated, it's going to be very hard for us to define standard interop interfaces that don't end up advantaging the tech companies. Standards bodies are extremely easy for big industry players to capture:
https://pluralistic.net/2023/04/30/weak-institutions/
If tech giants refuse to offer access to their gateways to certain rivals because they seem "suspicious," it will be hard to tell whether the companies are just engaged in self-serving smears against a credible rival, or legitimately trying to protect their users from a predator trying to plug into their infrastructure. These fact-intensive questions are the enemy of speedy, responsive, effective policy administration.
But there's more than one way to attain interoperability. Interop doesn't have to come from mandates, interfaces designed and overseen by government agencies. There's a whole other form of interop that's far nimbler than mandates: adversarial interoperability:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interoperability" is a catch-all term for all the guerrilla warfare tactics deployed in service to unilaterally changing a technology: reverse engineering, bots, scraping and so on. These tactics have a long and honorable history, but they have been slowly choked out of existence with a thicket of IP rights, like the IP rights that allow Facebook to shut down browser automation tools, which Ethan Zuckerman is suing to nullify:
https://locusmag.com/2020/09/cory-doctorow-ip/
Adversarial interop is very flexible. No matter what technological moves a company makes to interfere with interop, there's always a countermove the guerrilla fighter can make – tweak the scraper, decompile the new binary, change the bot's behavior. That's why tech companies use IP rights and courts, not firewall rules, to block adversarial interoperators.
At the same time, adversarial interop is unreliable. The solution that works today can break tomorrow if the company changes its back-end, and it will stay broken until the adversarial interoperator can respond.
But when companies are faced with the prospect of extended asymmetrical war against adversarial interop in the technological trenches, they often surrender. If companies can't sue adversarial interoperators out of existence, they often sue for peace instead. That's because high-tech guerrilla warfare presents unquantifiable risks and resource demands, and, as the scalesplainers never tire of telling us, this can create real operational problems for tech giants.
In other words, if Facebook can't shut down Ethan Zuckerman's browser automation tool in the courts, and if they're sincerely worried that a browser automation tool will uncheck its user interface buttons so quickly that it crashes the server, all it has to do is offer an official "unsubscribe all" button and no one will use Zuckerman's browser automation tool.
We don't have to choose between adversarial interop and interop mandates. The two are better together than they are apart. If companies building and operating DMA-compliant, mandatory gateways know that a failure to make them useful to rivals seeking to help users escape their authority is getting mired in endless hand-to-hand combat with trench-fighting adversarial interoperators, they'll have good reason to cooperate.
And if lawmakers charged with administering the DMA notice that companies are engaging in adversarial interop rather than using the official, reliable gateway they're overseeing, that's a good indicator that the official gateways aren't suitable.
It would be very on-brand for the EU to create the DMA and tell tech companies how they must operate, and for the USA to simply withdraw the state's protection from the Big Tech companies and let smaller companies try their luck at hacking new features into the big companies' servers without the government getting involved.
Indeed, we're seeing some of that today. Oregon just passed the first ever Right to Repair law banning "parts pairing" – basically a way of using IP law to make it illegal to reverse-engineer a device so you can fix it.
https://www.opb.org/article/2024/03/28/oregon-governor-kotek-signs-strong-tech-right-to-repair-bill/
Taken together, the two approaches – mandates and reverse engineering – are stronger than either on their own. Mandates are sturdy and reliable, but slow-moving. Adversarial interop is flexible and nimble, but unreliable. Put 'em together and you get a two-part epoxy, strong and flexible.
Governments can regulate well, with well-funded expert agencies and smart, adminstratable remedies. It's for that reason that the administrative state is under such sustained attack from the GOP and right-wing Dems. The illegitimate Supreme Court is on the verge of gutting expert agencies' power:
https://www.hklaw.com/en/insights/publications/2024/05/us-supreme-court-may-soon-discard-or-modify-chevron-deference
It's never been more important to craft regulations that go beyond mere good intentions and take account of adminsitratability. The easier we can make our rules to enforce, the less our beleaguered agencies will need to do to protect us from corporate predators.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/20/scalesplaining/#administratability

Image: Noah Wulf (modified) https://commons.m.wikimedia.org/wiki/File:Thunderbirds_at_Attention_Next_to_Thunderbird_1_-_Aviation_Nation_2019.jpg
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#cda#ethan zuckerman#platforms#platform decay#enshittification#eu#dma#right to repair#transatlantic#administrability#regulation#big tech#scalesplaining#equilibria#interoperability#adversarial interoperability#comcom
99 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
24 notes
·
View notes
Text
Patrick Beuth, Jörg Diehl, Roman Höfner, Roman Lehberger, Friederike Röhreke, and Fidelius Schmid at Der Spiegel:
Private contact details of the most important security advisers to U.S. President Donald Trump can be found on the internet. DER SPIEGEL reporters were able to find mobile phone numbers, email addresses and even some passwords belonging to the top officials. To do so, the reporters used commercial people search engines along with hacked customer data that has been published on the web. Those affected by the leaks include National Security Adviser Mike Waltz, Director of National Intelligence Tulsi Gabbard and Secretary of Defense Pete Hegseth. Most of these numbers and email addresses are apparently still in use, with some of them linked to profiles on social media platforms like Instagram and LinkedIn. They were used to create Dropbox accounts and profiles in apps that track running data. There are also WhatsApp profiles for the respective phone numbers and even Signal accounts in some cases. As such, the reporting has revealed an additional grave, previously unknown security breach at the highest levels in Washington. Hostile intelligence services could use this publicly available data to hack the communications of those affected by installing spyware on their devices. It is thus conceivable that foreign agents were privy to the Signal chat group in which Gabbard, Waltz and Hegseth discussed a military strike.
Numbers Linked to Signal Accounts
It remains unclear, however, whether this extremely problematic chat was conducted using Signal accounts linked to the private telephone numbers of the officials involved. Tulsi Gabbard has declined to comment. DER SPIEGEL reporting has demonstrated, though, that privately used and publicly accessible telephone numbers belonging to her and Waltz are, in fact, linked to Signal accounts. [...] The White House confirmed the scandal after the fact. Trump insisted that it did not include classified content, a question that is of particular relevance since members of the U.S. government are not permitted to share such information over Signal. The U.S. special envoy for Ukraine and the Middle East, Steve Witkoff, was even in Russia while participating in the chat group.
DER SPIEGEL was able to find some of the contact information for Gabbard, Hegseth and Waltz in commercial databases, while other information was in so-called password leaks, which are hardly a rarity on the internet. One example is the 2019 discovery by Troy Hunt, who found 773 million email addresses and more than 21 million passwords in a hacker forum. Since then, there have been numerous additional leaks. Criminals are constantly compiling new collections from hacks, usually to sell them on forums. [...] The mobile number provided, meanwhile, led to a WhatsApp account that Hegseth apparently only recently deleted. The profile photo showed a shirtless Hegseth in a baseball cap and necklace. Comparisons with other photos of the U.S. secretary of defense using facial recognition software were able to confirm that the photo on the WhatsApp profile was indeed Hegseth.
Several Passwords in Leaked Database
Waltz’s mobile number and email address could be found using the same service provider. The mobile phone number could even be found using a people search engine popular in the U.S. DER SPIEGEL reporters were also able to find several passwords for Waltz’s email address in leaked databases. The information also led to Waltz’s profiles for Microsoft Teams, LinkedIn, WhatsApp and Signal. National Intelligence Director Gabbard was seemingly more careful with her data than her two male colleagues. She apparently had her own data blocked in the commercial contact search engines that contained the data of Hegseth and Waltz. But her email address was to be found on WikiLeaks and Reddit. Gabbard’s email address is available in more than 10 leaks. One of those also contains a partial telephone number, which, when completed, leads to an active WhatsApp account and a Signal profile.
German publication Der Spiegel writes that several of the National Security Advisers for the Trump Administration, including Pete Hegseth, Tulsi Gabbard, and Michael Waltz, had their private data breached and the passwords found online.
#Der Spiegel#Pete Hegseth#Tulsi Gabbard#Michael Waltz#National Security#Trump Administration II#Yemen Signal Leak#Data Breaches#Steve Witkoff#Jeffrey Goldberg#Signal#John Ratcliffe
7 notes
·
View notes
Text
0 notes
Text
I'm Unpeeling Myself from Big Tech!
"Unpeeling" being any act you take that limits the amount of data a large tech corporation can gather from you, decreases your reliance on products of those corporations, or increases autonomy over your technology. I'm ripping the term from a line in this review by Joanna Nelius, where she writes, "People are looking for ways to peel their eyes from their smartphones like a layer of Elmer’s glue from their hand — to remove a part of themselves that really isn’t a part of themselves." It's different than "unplugging" because the goal isn't to go off the grid, or even to limit one's technology usage. The goal, instead, is to extract from the invasive, addictive, destructive capitalist vision a set of tools that are useful to YOU.
It started when I realized I don't need a smartphone. I've deleted most social media from my phone, and the stuff I still have I prefer to check on my laptop. Not all "dumb phones" (I hate this term) offer the same features, though, so I began to think on a granular level about what I need from a cell phone. Eg, not all "dumb phones" provide MMS, but my family lives 3k miles away. I wanna still talk in the groupchat.
On the more complex end, I write on my phone. I've been using Google Docs to move seamlessly from scribbled writing drafts on my phone to formatted, finished works on my computer since I was fourteen.
Except, Google Docs is useless now. I've been unable to use it since they lowered the storage capacity. The only other cloud storage writing thingy with similar functionality is Office 365, which sucks.
Could a dumb phone with a basic "notes" feature work? Maybe, but I'd have to re-type everything to get it into a formatted document. Ideally, I'd have like, a mini-laptop just for writing - something I could fit in my pocket or in a small bag, so I could bring it to work without looking like a dick - and then, in addition, a basic phone for calls/texts/GPS stuff. But does a device this specific to my use case even exist?
Yes. Yes it does.

This is a GPD Micro PC. GPD mainly sells handheld gaming machines, though this product is designed for mobile IT professionals. It's probably too chonky for a pocket, but mark my words, I will figure out how to make it work for me.
It's stupid, but this gave me a rush. I've been struggling along, tied to the bloated corpses of three gmail accounts, for years, because I needed Google Docs for my writing workflow. But now I don't. I have the power to actually tailor my tech for my life.
By this point, I was like, alright, I don't need Google Docs anymore, I don't need a smartphone, what else? Do I need Windows? No, probably not, right? I can use Linux Mint on this new guy, especially since he'll mostly be a basic writing machine. LibreOffice is less intrusive and bloated than MS Word - a better experience for free than I'd have from the paid program. If I go all the way and install Linux, I also won't have to deal with ads in my start menu, or pre-installed spyware screenshotting my activities.
In fact, if I back everything up on an external drive, I can delete my old Google Drives and switch my main computer to Linux, too! So, I finally bit the bullet and invested in an external hard drive.
This is the problem with "product ecosystems," by the way. When one part of that ecosystem - Google Docs - fails, the whole thing collapses. All the bloat and corruption you dealt with just stops being worth it, and it's easier to make a radical change to a new system. I witnessed something similar happen with comedy tech youtuber Dankpods earlier this year, except with Apple's ecosystem: he was a lifetime Apple guy - seemingly not in a worship way, but he liked their products, and was certainly in Apple's ecosystem. Then a couple things went sour for him, and now he runs Linux.
I'm doing this for personal and ideological reasons. I'm personally sick of Clippy - I mean, Copilot - peeping in to tell me how to write what I'm writing on Office 365. I abhor the idea of paying Google for a service they offered for free until recently, knowing they can flip the script at any point. And while we're talking ideology, I'm a communist, and even though this is far from a shift everyone can make, I believe that taking any available steps towards shutting Big Tech out of our lives is a net good. If all you can do is delete Instagram, or use a screentime tracker, or switch to Firefox, do it. I'm finally in a position to make this more drastic change, and I'm excited.
Get in the weeds about how you use technology. Do you need everything at your fingertips, all the time? If not, what, specifically, do you need? Is there a way that you, now or in the future, can trim out the parts you dislike? And what can you change now?
24 notes
·
View notes
Note
what do you use to play arknights on the computer? I looked at the official noxplayer app and it looks like spyware, do you recommend any emulator in particular?
I use bluestacks. It’s not perfect but it works. My friend uses I think a like beta google play mobile emulator thing and she seems to like it so maybe check that out. Bluestacks does sometimes have an ad on the side if you’re like idling on the home screen, but it works for me for what I use it for
33 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Note
Do you own a mobile phone?
Yes (cringe, imagine spending money to carry spyware around)
No (BASED)
3 notes
·
View notes
