#typing random terms does not equal programming
Explore tagged Tumblr posts
Text
it is the dumbest pet peeve of mine but if I see one more "hypno programming" kink post with nonsense pseudocode in it I will bake a menagerie of cakes
#typing random terms does not equal programming#catch me designing and writing a hypno kink language so this shit stops happening#and yes im fully aware im bitching about somethin#g thats completely harmless
9 notes
·
View notes
Note
I see people interpret that bird in the end of chapter 139 differently. Birds of the same species were shown in manga in several chapters before chapter 139. They always seemed to be related to Eren. From what I saw on reddit and twitter I think we have 5 options of what people think:
1. Eren got reincarnated as a bird.
2. Eren is somehow related to these birds and he could control them while still alive. I don't know if I understand the concept of time (influencing past, future) in AoT right, but basically it is either Eren influencing the birds from the past or he just "programmed" them in the past so they would look over people close to him in the future after his death (sending a feather to Armin, wraping the scarf around Mikasa...).
3. Eren is somehow related to these birds and this power comes from the Paths and he is there. We know that titans are gone, but it was never specifically stated that Paths are gone too. So he stayed there (it would also explain why his spirit wasn't shown in chapter 139 when all other spirits were released from the Paths) and controls the birds from there.
4. Eren is dead and in afterlife and he controls the birds from there.
5. Birds don't have any relation to Eren and are just symbolic.
I don't believe in option number 1 (I am actually surprised by how many people interpret it this way, but that reincarnation just doesn't go well with me, it seems really weird and also doesn't make much sense to me because we saw those birds before chapter 139 when Eren was still alive and plus one bird can only live for several years and after the death what? he gets reincarnated into a bird again? it is just weird to me), but regarding options 2 - 4 I think any of them could be true. Option number 5 doesn't go well with me because for birds being just symbolic I think Isayama drew them way too often. Which one do you think is the most realistic? Or do you have your own theory to explain the relation between Eren and the bird(s)?
Hello! Wow, what a good brain food after days of trying not to think about anything. Thank you for your question!
Let me start according to the options you’ve provided.
1) Reincarnation.
Overall, this is an interesting concept, however, in terms of AoT, it is quite questionable as there’s not enough evidence to claim that Eren was reborn as a bird. On top of that, if reincarnation actually existed, why the previous titan shiters and Eldians didn’t become some type of animals or something? Why would only Eren be reincarnated as a bird. Again, I think there aren’t that many proofs that reincarnation is actually possible within AoT’s universe.
2) Eren controlling the birds from the future.
Not a while ago I’ve made my own small research to understand how times works in AoT and I came across a concept called eternalism or block universe theory, which basically implies that past, present and future are equally real and are happing at the same time block. Also, according to this theory, time doesn’t necessarily flow as we perceive it and past and future are relative.
Aside from that, it also implies that time travel is possible. I think this concept gives some insights into how paths can actually work, because in Paths:
1. Time is relative and there’s no actual flow of time.
2. Eren and Zeke travelled to Grisha’s memories and he could see Zeke, which is still similar to time travel.
3. Eren could visit his friends via paths and show them the different outcome (for Mikasa) and tell them about future events like Connie meeting his mother again.
When Eren said that he felt like the past and future exist at the same time, it was also related to the concept of eternalism.

Also, according to this theory, the present is the product of a real point of the past and a real point of the future, which means that the changes in these two will mean the change in the present.
So what does it mean? It means that since these three time blocks simply exist. I’m not quite sure about the programming, because it also doesn't have enough evidence, however, nevertheless, it is still plausible to say since there’s also the concept of block universe involved.
One moment that makes this option possible is that Eren had Falco from ch.91 in his memory shards.


It is still unclear how Eren managed to see the world with bird’s eyes, but if it is related to future Eren somehow “programming” and sending these birds at a certain time, eternalism it is.
3) Eren controlling birds from the paths.
I think it is possible, because, as you said, we don’t know if paths actually disappeared or not. However, if we take paths as something that created because of Ymir’s wish to die, but yet stay loyal to Karl Fritz and hallucigenia being a part of her that certainly didn’t want to die, paths technically have disappeared with her. But again, I still think that it was pretty much an open question that can be interpreted in different ways.
But again, in the context of AoT’s universe, it is still possible that Eren’s spirit might be alive, because Zeke and Armin could summon previous titan shifters even if their physical bodies didn’t exist (same for Zeke too, because he technically died after Eren transformation).
Ymir in the past did send a titan to Zeke, which helped him heal after his fight with Levi, but the nuance is that the titan was her subject, while birds are simply animals. But the possibility still exists.
4) Eren is in the afterlife and controls birds from there.
To be honest, it depends on how you interpret the afterlife, because it is still your soul that goes there (not the body). But same as with the paths thing, I think these two are equal because from how I understood it, paths is where titan shifters’ spirits go after death.
5) Birds have no relation to Eren and are just symbolic.
I agree that birds being simply symbolic is quite random. They occurred a lot during the last arc (ch.91, ch.130, ch.131 (exactly when Eren talked with Armin in paths), ch.138 (again, Mikasa and Eren were in paths) and ch.139). I would take them as symbolism only if the bird from ch.139 didn’t come at the moment when Mikasa was crying and saying that she misses Eren. The bird literally wrapped the scarf around her and I don’t that any random bird outside would do the same lol.


So in conclusion, I would say there isn’t a concrete explanation as to whether is actually Eren or it’s him controlling it from the paths/afterlife, however, I still think that no matter what it was, it really shows how strong Eren’s wish was to keep the promise he gave to Mikasa in ch.50 and how he really didn’t want to die, but yet had to due to his conscience.

All in all, thank you, again, anon for your question and I hope you will have a good day/night!
#wow my brain didn’t have such a good stretch in a while 😂😂#eren jaeger#mikasa ackerman#eremika#armin arlert#falco grice#attack on titan#shingeki no kyoujin#t-talks#ask
43 notes
·
View notes
Text
Memory
In computers, memory is the most essential component of the normal functioning of any system. The computer system categorizes the memory for different purposes and uses. In this section, we have discussed the classification of memory in detail. Also, we will discuss types of memory, features of memory, RAM, ROM, SRAM, DRAM, and its advantages and disadvantages.
What is computer memory?
Computer memory
is any physical device, used to store data, information or instruction temporarily or permanently. It is the collection of storage units that stores binary information in the form of bits. The memory block is split into a small number of components, called cells. Each cell has a unique address to store the data in memory, ranging from zero to memory size minus one. For example, if the size of computer memory is 64k words, the memory units have 64 * 1024 = 65536 locations or cells. The address of the memory's cells varies from 0 to 65535.
Why do we need a computer memory?
Read More
In the computer system, we need computer memory to store various types of data like text, images, video, audio, documents, etc. We can retrieve it when the data is required. For example, when we write and execute any computer program, it is initially stored in primary memory. If the processor does not need particular items for a longer time, the program or data is automatically saved into the permanent or secondary memory. Then the data is called from secondary memory to main memory and performs the execution of codes.
Features of Memory
Following are the different features of the memory system that includes:
1. Location: It represents the internal or external location of the memory in a computer. The internal memory is inbuilt in computer memory. It is also known as primary memory. the example of primary memory are registers, cache and main memory. Whereas, external memory is the separate storage device from the computer, such as disk, tape, USB pen drive.
2. Capacity: It is the most important feature of computer memory. Storage capacity can vary in external and internal memory. External devices' storage capacity is measured in terms of bytes, whereas the internal memory is measured with bytes or words. The storage word length can vary in bits, such as 8, 16 or 32 bits.
3. Access Methods: Memory can be accessed through four modes of memory.
DMA: As the name specifies, Direct Memory Address (DMA) is a method that allows input/output (I/O) devices to access or retrieve data directly or from the main memory.
Sequential Access Method: The sequential access method is used in a data storage device to read stored data sequentially from the computer memory. Whereas, the data received from random access memory (RAM) can be in any order.
Random Access Method: It is a method used to randomly access data from memory. This method is the opposite of SAM. For example, to go from A to Z in random access, we can directly jump to any specified location. In the Sequential method, we have to follow all intervening from A to Z to reach at the particular memory location.
Associative Access Method: It is a special type of memory that optimizes search performance through defined data to directly access the stored information based on a memory address.
Read More
4. Unit of transfer: As the name suggests, a unit of transfer measures the transfer rate of bits that can be read or write in or out of the memory devices. The transfer rate of data can be different in external and internal memory.
Internal memory: The transfer rate of bits is mostly equal to the word size.
External memory: The transfer rate of bit or unit is not equal to the word length. It is always greater than a word or may be referred to as blocks.
5. Performance: The performance of memory is majorly divided into three parts.
Access Time: In random access memory, it represents the total time taken by memory devices to perform a read or write operation that an address is sent to memory.
Memory Cycle Time: Total time required to access memory block and additional required time before starting second access.
Transfer rate: It describes the transfer rate of data used to transmit memory to or from an external or internal memory device. Bit transfer can be different for different external and internal devices.
6. Physical types: It defines the physical type of memory used in a computer such as magnetic, semiconductor, magneto-optical and optical.
7. Organization: It defines the physical structure of the bits used in memory.
8. Physical characteristics: It specifies the physical behavior of the memory like volatile, non-volatile or non-erasable memory. Volatile memory is known as RAM, which requires power to retain stored information, and if any power loss has occurred, stored data will be lost. Non-volatile memory is a permanent storage memory that is used to obtain any stored information, even when the power is off. Non-erasable memory is a type of memory that cannot be erased after the manufactured like ROM because at the time of manufactured ROM are programmed.
Classification of Memory
Primary or Main Memory
Primary memory is also known as the computer system's main memory that communicates directly within the CPU
, Auxiliary memory and the Cache memory. Main memory is used to kept programs or data when the processor is active to use them. When a program or data is activated to execute, the processor first loads instructions or programs from secondary memory into main memory, and then the processor starts execution. Accessing or executing of data from primary memory is faster because it has a cache or register memory that provides faster response, and it is located closer to the CPU
. The primary memory is volatile, which means the data in memory can be lost if it is not saved when a power failure occurs. It is costlier than secondary memory, and the main memory capacity is limited as compared to secondary memory.
The primary memory is further divided into two parts:
1. RAM (Random Access Memory)
2. ROM (Read Only Memory)
Random Access Memory (RAM)
Random Access Memory (RAM)
is one of the faster types of main memory accessed directly by the CPU. It is the hardware in a computer device to temporarily store data, programs or program results. It is used to read/write data in memory until the machine is working. It is volatile, which means if a power failure occurs or the computer is turned off, the information stored in RAM
will be lost. All data stored in computer memory can be read or accessed randomly at any time.
There are two types of RAM:
SRAM
DRAM
DRAM: DRAM (Dynamic Random-Access Memory) is a type of RAM that is used for the dynamic storage of data in RAM. In DRAM, each cell carries one-bit information. The cell is made up of two parts: a capacitor and a transistor. The size of the capacitor and the transistor is so small, requiring millions of them to store on a single chip. Hence, a DRAM chip can hold more data than an SRAM chip of the same size. However, the capacitor needs to be continuously refreshed to retain information because DRAM is volatile. If the power is switched off, the data store in memory is lost.
Characteristics of DRAM
1. It requires continuously refreshed to retain the data.
2. It is slower than SRAM
3. It holds a large amount of data
4. It is the combination of capacitor and transistor
5. It is less expensive as compared to SRAM
6. Less power consumption
SRAM: SRMA (Static Random-Access Memory) is a type of RAM used to store static data in the memory. It means to store data in SRAM remains active as long as the computer system has a power supply. However, data is lost in SRAM when power failures have occurred.
Characteristics of Static Ram
1. It does not require to refresh.
2. It is faster than DRAM
3. It is expensive.
4. High power consumption
5. Longer life
6. Large size
7. Uses as a cache memory
Advantages of RAM
It is a faster type of memory in a computer.
It requires less power to operate.
Program loads much faster
More RAM increases the performance of a system and can multitask.
Perform read and write operations.
The processor can read information faster than a hard disc, floppy, USB, etc.
Disadvantages of RAM
Less RAM reduces the speed and performance of a computer.
Due to volatile, it requires electricity to preserve the data.
It is expensive than ROM
It is unreliable as compared to ROM
The Size of RAM is limited.
Read-Only Memory (ROM)
ROM
is a memory device or storage medium that is used to permanently store information inside a chip. It is a read-only memory that can only read stored information, data or programs, but we cannot write or modify anything. A ROM contains some important instructions or program data that are required to start or boot a computer. It is a non-volatile memory; it means that the stored information cannot be lost even when the power is turned off or the system is shut down.
Types of ROM
There are five types of Read Only Memory:
1. MROM (Masked Read Only Memory):
MROM is the oldest type of read-only memory whose program or data is pre-configured by the integrated circuit manufacture at the time of manufacturing. Therefore, a program or instruction stored within the MROM chip cannot be changed by the user.
2. PROM(ProgrammableReadOnlyMemory):
It is a type of digital read-only memory, in which the user can write any type of information or program only once. It means it is the empty PROM chip in which the user can write the desired content or program only once using the special PROM programmer or PROM burner device; after that, the data or instruction cannot be changed or erased.
3. EPROM(ErasableandProgrammableReadOnlyMemory):
It is the type of read only memory in which stored data can be erased and re-programmed only once in the EPROM memory. It is a non-volatile memory chip that holds data when there is no power supply and can also store data for a minimum of 10 to 20 years. In EPROM, if we want to erase any stored data and re-programmed it, first, we need to pass the ultraviolet light for 40 minutes to erase the data; after that, the data is re-created in EPROM.
4. EEPROM (Electrically Erasable and Programmable Read Only Memory): The EEROM is an electrically erasable and programmable read only memory used to erase stored data using a high voltage electrical charge and re-programmed it. It is also a non-volatile memory whose data cannot be erased or lost; even the power is turned off. In EEPROM, the stored data can be erased and reprogrammed up to 10 thousand times, and the data erase one byte at a time.
5. Flash ROM: Flash memory is a non-volatile storage memory chip that can be written or programmed in small units called Block or Sector. Flash Memory is an EEPROM form of computer memory, and the contents or data cannot be lost when the power source is turned off. It is also used to transfer data between the computer and digital devices.
Advantages of ROM
1. It is a non-volatile memory in which stored information can be lost even power is turned off.
2. It is static, so it does not require refreshing the content every time.
3. Data can be stored permanently.
4. It is easy to test and store large data as compared to RAM.
5. These cannot be changed accidently
6. It is cheaper than RAM.
7. It is simple and reliable as compared to RAM.
8. It helps to start the computer and loads the OS.
Disadvantages of ROM
1. Store data cannot be updated or modify except to read the existing data.
2. It is a slower memory than RAM to access the stored data.
3. It takes around 40 minutes to destroy the existing data using the high charge of ultraviolet light.
Secondary Memory
Secondary memory
is a permanent storage space to hold a large amount of data. Secondary memory is also known as external memory that representing the various storage media (hard drives, USB, CDs, flash drives and DVDs) on which the computer data and program can be saved on a long term basis. However, it is cheaper and slower than the main memory. Unlike primary memory, secondary memory cannot be accessed directly by the CPU. Instead of that, secondary memory data is first loaded into the RAM (Random Access Memory) and then sent to the processor to read and update the data. Secondary memory devices also include magnetic disks like hard disk and floppy disks, an optical disk such as CDs and CDROMs, and magnetic tapes.
Features of Secondary Memory
Its speed is slower than the primary/ main memory.
Store data cannot be lost due to non-volatile nature.
It can store large collections of different types, such as audio, video, pictures, text, software, etc.
All the stored data in a secondary memory cannot be lost because it is a permanent storage area; even the power is turned off.
It has various optical and magnetic memories to store data.
Types of Secondary Memory
The following are the types of secondary memory devices:
Hard Disk
A hard disk is a computer's permanent storage device. It is a non-volatile disk that permanently stores data, programs, and files, and cannot lose store data when the computer's power source is switched off. Typically, it is located internally on computer's motherboard that stores and retrieves data using one or more rigid fast rotating disk platters inside an air-sealed casing. It is a large storage device, found on every computer or laptop for permanently storing installed software, music, text documentation, videos, operating system, and data until the user did not delete.
Floppy Disk
A floppy disk is a secondary storage system that consisting of thin, flexible magnetic coating disks for holding electronic data such as computer files. It is also known as Floppy Diskette that comes in three sizes like 8 inches, 5.5 inches and 3.5 inches. The stored data of a floppy disk can be accessed through the floppy disk drive. Furthermore, it is the only way through a new program installed on a computer or backup of the information. However, it is the oldest type of portable storage device, which can store data up to 1.44 MB. Since most programs were larger, that required multiple floppy diskettes to store large amounts of data. Therefore, it is not used due to very low memory storage.
CD (Compact Disc)
A CD
is an optical disk storage device, stands for Compact Disc. It is a storage device used to store various data types like audio, videos, files, OS, Back-Up file, and any other information useful to a computer. The CD has a width of 1.2 mm and 12 cm in height, which can store approximately 783 MB of data size. It uses laser light to read and write data from the CDs.
Types of CDs
1. CD-ROM (Compact Disc Read Only Memory): It is mainly used for bulk size mass like audio CDs, software and computer games at the time of manufacture. Users can only read data, text, music, videos from the disc, but they cannot modify or burnt it.
2. CD-R (Compact Disc Recordable): The type of Compact Disc used to write once by the user; after that, it cannot be modified or erased.
3. CD-RW (Compact Disc Rewritable): It is a rewritable CD disc, often used to write or delete the stored data.
DVD Drive/Disc
DVD is an optical disc storage device, stands for Digital Video Display or Digital Versatile Disc. It has the same size as a CD but can store a larger amount of data than a compact disc. It was developed in 1995 by Sony, Panasonic, Toshiba and Philips four electronics companies. DVD drives are divided into three types, such as DVD ROM (Read Only Memory), DVD R (Recordable) and DVD RW (Rewritable or Erasable). It can store multiple data formats like audio, videos, images, software, operating system, etc. The storing capacity of data in DVD is 4.7 GB to 17 GB.
Blu Ray Disc (BD)
Blu Ray is an Optical disc storage device used to store a large amount of data or high definition of video recording and playing other media files. It uses laser technology to read the stored data of the Blu-ray Disk. It can store more data at a greater density as compared to CD/ DVD. For example, compact discs allow us to store 700 MB of data, and in DVDs, it provides up to 8 GB of storage capacity, while Blu-ray Discs provide 28 GB of space to store data.
Pen Drive
Read More
A pen drive is a portable device used to permanently store data and is also known as a USB flash drive. It is commonly used to store and transfer the data connected to a computer using a USB port. It does not have any moveable part to store the data; it uses an integrated circuit chip that stores the data. It allows the users to store and transfer data like audio, videos, images, etc. from one computer to any USB pen drive. The storing capacity of pen drives from 64 MB to 128 GB or more.
Cache Memory
It is a small-sized chip-based computer memory that lies between the CPU and the main memory. It is a faster, high performance and temporary memory to enhance the performance of the CPU. It stores all the data and instructions that are often used by computer CPUs. It also reduces the access time of data from the main memory. It is faster than the main memory, and sometimes, it is also called CPU memory because it is very close to the CPU chip. The following are the levels of cache memory.
1. L1 Cache: The L1 cache is also known as the onboard, internal, or primary cache. It is built with the help of the CPU. Its speed is very high, and the size of the L1 cache varies from 8 KB to 128 KB.
2. L2 Cache: It is also known as external or secondary cache, which requires fast access time to store temporary data. It is built into a separate chip in a motherboard, not built into the CPU like the L1 level. The size of the L2 cache may be 128 KB to 1 MB.
3. L3 Cache: L3 cache levels are generally used with high performance and capacity of the computer. It is built into a motherboard. Its speed is very slow, and the maximum size up to 8 MB.
Advantages of Cache Memory
1. Cache memory is the faster memory as compared to the main memory.
2. It stores all data and instructions that are repeatedly used by the CPU for improving the performance of a computer.
3. The access time of data is less than the main memory.
Disadvantage of Cache Memory
Read More
1. It is very costly as compared to the Main memory and the Secondary memory.
2. It has limited storage capacity.
Register Memory
The register memory is a temporary storage area for storing and transferring the data and the instructions to a computer. It is the smallest and fastest memory of a computer. It is a part of computer memory located in the CPU as the form of registers. The register memory is 16, 32 and 64 bits in size. It temporarily stores data instructions and the address of the memory that is repeatedly used to provide faster response to the CPU.
#expalin memory#what is memory#benifits of memory#advantages of memory#types of memory#RAM#ROM#DVD#CD#register memory#cache memory#primary memory#secondry memory
2 notes
·
View notes
Text
21 Questions
Tagged by @getoutofmyhouse who had oddly similar answers to mine
Nickname: only the one I use here, that I gave myself--Claire Donner, which has to do with my famous love of cannibalism. Claire is my real first name, though.
Zodiac: I am so very cuspy. I was born at about a quarter to midnight on April 20, so I tend to relate to, and feel insulted by, the suppositions about Aries and Taurus equally. I’m one of those jerks who will tell you astrology is a bunch of hoo ha...and then drone on with my Many Esoteric Ideas about it, so I’ll just stop myself right here.
Height: 5’ nuthin is what I prefer to say...because saying I’m 5 and 3/4′ sounds a little like saying I’m 10 and a half years old.
Amount of sleep: It’s all fucked up. Until I got into my 30s I could, and would prefer to, sleep endlessly. Now I go to bed around 10 (depression), get up around 5 or 6 (being old), and for extra fun, I’ve developed this insomnia that often keeps me up from about 2am-5am. I try make the most of it by getting up, getting high, watching a movie or two, writing...basically just having a secret private day by myself. I’d really rather go back to just sleeping constantly though.
Last movie I saw: I saw GRETA in theaters tonight, which was ok. I guess I thought any Neil Jordan film would be headier than this, but watching Isabel Huppert just running around acting like an absolute maniac is a rare treat! My last video experience was RAW, which I put on to bother my husband right when we got home from the theater. (I think he liked it more than I originally did, to my surprise)
Last thing I googled: The correct spelling of Sylvia Likens’ last name. I’m obsessed with this type of crime where a group of people (usually a family and/or some of their friends and neighbors) fall into some kind of shared hysteria where they protractedly torture to death an acquaintance for no particular reason. Some times there’s an element of mystery as to why the victim didn’t leave while they were still able to, which suggests to me that the murdered person was just as much a victim of the groupthink as the perpetrators. Other example victims include Suzanne Capper, Vera Jo Reigle, and I think to some degree Sophie Lionnet, James Bulger, and Junko Furuta. (Also a crime they briefly discuss in the book Lords of Chaos, where several people murder a friend in their trailer, but I can’t remember it specifically enough to look up the names--the other last thing i tried to google) I keep thinking there should be a psychiatric and/or legal term for this kind of crime, but I’ve never heard one, so let me know if you got one!
Favorite musician: I have trouble with questions that involve ranking anything, so I’ll just say that right now I’m listening to a lot of old White Zombie. I didn’t know anything about their origins as an East Village noise band, and I’m fascinated by the stories about how apocalyptically miserable it was to be in that group. I’m increasingly obsessed with people who work their asses off doing something they barely even enjoy, for what must be borderline spiritual reasons.
Song stuck in my head: Nothing right this second, for which I am very grateful. There’s something awful in my brain that causes me to wake up with some maddening, babyish tune stuck in my head more often than not. It is most frequently the Ten Little Indians nursery rhyme. This is literally killing me.
Other blogs: @anhed-nia, which started as a dumping ground for long posts about mental illness, and turned into almost only movie writing. at some point there was just so much movie shit that i started to feel awkward about posting anything personal there again. i also got @getoffyrass which is a group blog, and a repository for images that make great drawing references. everyone is encouraged to post their drawings, too, although it is seldom used. i still like having it around, for when i have time to draw. my “real” drawing blog is @neveratendermoment but i don’t draw often enough anymore...
Do I get asks: i used to get tons! i really enjoy them, even the trolls to some degree. i must have seemed like more of a regular tumblr geek girl back in the day. also tumblr has just changed a lot since then. my blog was definitely a casualty of Best Stuff First, i think my follower count stopped dead forever right when that happened, and now that practically every single fucking thing on this entire site is either fandom shit or *discourse*, i really have nothing to offer tumblr anymore, anyway.
Blogs following: 1,057.
Lucky numbers: 2! Also 5.
What I’m wearing: black wool long john pants from Chrome, and a white v neck teeshirt with the words BLACK MAYONNAISE on it in black Rocky Horror font. i live near the notoriously toxic Gowanus Canal, and “black mayonnaise” is the actual term used to describe what’s on the bottom of it, by the scientists who are trying to figure out what to do with it.
Dream trip: i am really excited by travel, it’s hard to pick. i’m hopefully making a dream trip soon though: my father’s mysterious finno-swedish family is from the åland islands, and my husband and i will be planning part of our honeymoon there, whenever that happens.
Dream Job: i think about this a lot, because the older i get, the more i object to the entire concept of having to work to live. i’m into the whole universal basic income thing. i’m at this point where i can barely stand to think about capitalism in any way--like i think about how the need for money is so mortally serious that there’s a lot of physical stuff in the world that only exists because someone was scared of starving, tons of useless products and packaging and factory byproducts and all kinds of fucking straight up garbage that was only invented due to the lethality of poorness. i would rather be left totally alone forever if possible. however, if i HAD to do something and i COULD do anything, it would probably be film criticism. this fantasy takes place in a world where people care so much about what i have to say that i can make a career, not only out of movie writing, but out of only writing about the specific movies i want to write about, referring to nothing other than my personal reactions.
Favorite food: i wish the answer weren’t just “cheese”, but it probably is. also mushrooms. anything cinnamon. i’m a pretty adventurous eater though. the most important thing for me is a variety of flavors and textures.
Languages: english. i took several years of italian in junior high-high school, and did nothing with it. i taught myself to read french pretty fluently, but i would fold right up if someone tried to speak to me. i learned a bunch of swedish on duolingo, shoulda kept it up. i’ll get back to it! i really regret never learning spanish though, so i’m easily torn on what to do with my time.
Play any instruments: clarinet in junior high/high school, also alto sax which i did not enjoy at all, a little guitar. i bought a used electric bass last year that i have really been enjoying, but i feel a lot of guilt around not playing enough. so much of it is just strength training. that’s probably what i like about it, though. also i got a lot of electronic music software and midi controllers and stuff...and then i realized that it could take me months to sort through the thousands of samples i have to program this stuff, and i only got so far into it before i started to get discouraged. i need to get back to it, it’s ridiculous to let that stuff lie around. this is a rare example of me wishing i knew someone local to play with, who could speed me along on how everything works.
Favorite songs: another one of these impossible questions! anybody who is even reading this can probably guess the answers from the handful of music posts i reblog over and over and over. the other night i got all hyperactive and forced my husband to drop everything and listen to “buffalo stance” by nene cherry, which i never ever get sick of. real top contenders for favorite song might be “Stand By the Jamms” by the klf, and this recording, which has gotten me through many difficult hours:
https://www.youtube.com/watch?v=d8k1HsF3EvY
https://www.forcedexposure.com/Catalog/sunray-sonic-boom-music-for-the-dreamachine-cd/STRAWB.003CD.html
Random fact: i’m sure i’m missing out on something really funny and cool, but for now it’s just the well-known fact that i read palms.
Describe yourself as aesthetic thing: man, how do i answer this without being totally pretentious? maybe nobody can! i’m coming up with something really hard to describe but it will be worth it. the other day i watched this insane, completely unnecessary movie about lorca and salvador dali (played by robert pattinson) as gay lovers. there’s a scene in it where lorca does that “pick a hand” thing to dali, and dali picks an empty hand. of course, they’re both poor students who couldn’t be buying any gifts, so they do this obnoxious pantomime where dali pretends lorca actually gave him something--but then it turns out that lorca really DOES have something. he opens his other hand and gives dali...SOMETHING. i don’t know what! they make such a big deal out of it, but what the hell? you see it for a second in this closeup, but it’s shot from like, behind and slightly underneath, and it is just unrecognizable. it’s sort of an orange blob? it’s probably meant to be a sculpture. but, i love the idea of doing the “pick a hand” thing to somebody, and the other person is just like...hey wait a minute, what the fuck even IS this??
it reminded me of one of the most amazing things anyone ever did at my school, bard college. this genius art student who I WISH I COULD NAME TO CREDIT HER did her senior project as this like...made up product. i saw them at the senior show, hanging off a spinner rack, like you’d see next to the register in the drug store. they were called Toilet Buddies. they were these plastic, brightly colored objects that looked like toys, but they didn’t have a familiar earthly shape, and because of the title, it was IMPOSSIBLE to imagine what to do with them. so, she gets the lipstick cam from the film department, and shoots this video of herself sneaking some Toilet Buddies into Walmart. then she takes them to the register and BUYS THEM--the baffled cashier looks for them for a while, and eventually just rings them up as a general grocery or something. then in part 2, the artist TAKES THEM BACK TO THE STORE WITH THE RECEIPT AND GETS A REFUND.
so anyway, i see myself as like a fake product--something that looks just familiar enough to exit, and that appears to have a designated purpose, but it’s just kind of cheap and foreign and it becomes nightmarish to try to imagine what to do with it.
I don’t know if anyone i know will want to do this, but i tag @negativepleasure @moviesludge @former-contender @dimestoreman @thefuzzydave @darkarfs @theoddsideofme @blueruins ...um, i don’t really know who would enjoy this. the ultimate would be @garbagenacht
7 notes
·
View notes
Link
Trump cannot get stuff done, because he is merely president, and the permanent government is full of people that hate him.
But it is not just the permanent government. His political appointees are in bed with his enemies, and are subverting his agenda. Two years after Hitler was elected, Hitler had a Nazi running ever boy scout troop and every trade union chapter. Trump cannot even get a Trumpist running border security.
The one area where Trump has been successful is putting his people in the judiciary. Trumpist judges, though still massively outnumbered, are coming in at every level. Trump has been effective in appointing judges, because he has a big bench he can draw upon, which bench knows who whom, which bench is self policing, which bench can be relied upon to carry out his program without him needing to be on their back. Personnel is policy, and the Federalist society has a supply.
…
To govern, you need a synthetic tribe, which Hitler had, which Constantine adopted, and which Trump lacks, except for the federalist society which is narrowly focused on judicial process.
The Federalist article of faith (Original Intent) that provides unity and cohesion is also an effective antibody against enemy outgroups. It is something no leftist can admit is even thinkable – to them, just words with no meaning that they dare conceive of. So when leftist entryists attempt to infiltrate the Federalists, they use their shibboleths incorrectly, like a Marxist purporting to be channeling Adam Smith, and wind up babbling random nonsensical meaningless scripted formulaic NPC gibberish.
We, on the other hand, agree with the leftists, that original intent is not really going to fly, while we agree with the Federalists that judges exercising executive, legislative, budgetary authority is intolerable. One emperor is a stationary bandit. A thousand little emperors is mobile banditry and anarcho tyranny. We, however, propose a solution far more radical than that of the federalists – that the final court of appeal should be the Sovereign, should be Moses, the King, or the President, and he should be able to intervene in any case, and fire any judge. We also propose William the Conqueror’s “forms of action”, meaning that judges should be reduced to data entry clerks filling out forms that result in remote procedure calls to a system of central databases, similar to the system used by Australia’s border control force for dealing with “Illegal persons”. (Australian Border Force is Judge Dredd with more typing required than Judge Dredd had to do, but the same refreshing speed, efficiency, and absence of lawyers and priestly robes as with Judge Dredd.) William the Conqueror’s “Forms of action” kept judges in line for seven hundred years, and modern databases and remote procedure calls make William the Conqueror’s solution lightning fast, so that it can be applied by a cop on the beat, after the fashion of Judge Dredd and the Australian Border Force.
…
We are the reaction. Our program is to rectify social decay by reviving ancient and lost social technologies, among them Pauline marriage. These ancient social technologies tend, for the most part, to be social technologies preserved by Christianity through the Dark Age following the collapse of the Roman Empire, and by the Children of Israel through the dark age following the collapse of Bronze Age civilization, thus our program is Christian – old type Christian. Modern type Christians tend to assimilate to progressivism and worship demons.
…
So: here are the articles of the Canon:
1. Throne 2. Altar 3. Freehold 4. Family 5. Property
Throne
Division of powers, divided sovereignty does not work, more rulers means mobile banditry and anarcho tyranny. A stationary bandit has better incentives than a mobile bandit.
Altar
You cannot separate state and church. The church will undermine the state and take state power for itself, or the state subvert the church, or both at once. Harvard is our high holy Cathedral. A holiness spiral ensues as the priestly classes, the professoriat, the judiciary, and the media, pursue power by each being holier than the next. Obviously we have a state religion a state religion that every day becomes crazier, more dogmatic, and more intrusive, and that state religion needs to be formalized and made official so that the high priest and grand inquisitor can stop holiness spirals.
When Charles the Second was restored, the people of England held pagan celebrations, in the correct expectation that an officially official religion would be less repressive than an unofficially official religion.
…
Freehold
Freehold necessarily involves and requires rejection of the principle of equality before the law, and property rejection of equality of outcomes. Not all men were created equal, nor are women equal to men, nor is one group or category of men equal to another. Stereotypes are stereotypical, because the stereotype is usually true for most individual members of the group or category.
…
State building is coalition building to rule. We need a coalition of the smart, the cooperative, and the productive, ruling the stupid, the disruptive, and the destructive. The doctrine of equality means you cannot reward the elite with status? What! Of course the ruling elite is going to be rewarded with status, and that is exactly what is happening.
The ruling elite always gets rewarded, the ruling coalition always gets rewarded. Members of the ruling coalition always get a superior right to use violence, and a superior right to not be insulted. That is the way it is, and that is what we saw when white people were ethnically cleansed out of Detroit. The doctrine of equality before the law was always a lie intended to destroy the coalition of the smart, the cooperative, and the productive, to guilt the best people into surrender, so that they could be destroyed by a coalition of the worst.
Freehold means that we acknowledge that some state power is in fact private property, and the sovereign lets his loyal vassals enjoy their privilege, because if he tries to meddle, he will be overwhelmed by detail and complexity, so best to formalize that privilege and make it official. If we don’t have the aristocracy that so offended the founding fathers, we find ourselves with blacks exercising aristocratic privilege over whites. Equality before the law is an unworkable ideal, hypocritically betrayed in actual practice. Some people are going to be unjustly privileged. Let us try to make it the best people rather than the worst people, and try to make it the people that the state draws is wealth and coercive power from, rather than the people who sponge off the state.
Family
The immense biological and reproductive differences between men and women means that they can only cooperate for family formation on asymmetric, unequal terms. The wife has a duty to honor and obey, the husband to love and cherish. To ensure cooperation between men and women, the state, the family, society, and religion have to force men and women who sleep together to stick together, to force them to perform their marital duties, to force the man to cherish and the woman to obey, otherwise you get defect/defect, and reproduction and family become difficult for both men and woman.
…
Property
Anti discrimination law violates people’s property rights. Google hates us, but the problem is not primarily too much capitalism, but too little. In the James Damore affair, Google’s Human Resources Department (the Human Resources department being a tentacle of the state inserted into every corporation) threatened the board and the management of Google with a lawsuit for not hating us enough, issuing an official opinion that thinking forbidden thoughts constituted a “hostile environment for women”. Because stereotypes are usually true, private individuals and corporations should be free to make use of the information expressed by stereotyping. The trouble with libertarians and libertarianism is that they support every socialist intervention that is destroying our lives and our economy.
Family law and anti discrimination law violates the fourth amendment and the seventh, eighth, and final commandments
…
Technological advance and industrialization comes from Ayn Rand’s heroic engineer CEO, mobilizing other people’s capital and other people’s labor. We first see this archetype appear immediately after the restoration, when Charles the Second made it OK to use the corporate form to get rich. Unfortunately, Ayn Rand’s hero is not heroically on our side, contrary to what Ayn Rand promised.. He unheroically endorses the official religion, knowing his property could be attacked if he does not. But we should keep in mind that this makes him merely the instrument of power, not power. When we are in charge he will support our official religion and scarcely notice the change in the slogans posted in the rec room, which formerly endorsed coveting what belonged to others and females adopting male clothing and roles, but will then condemn coveting and endorse males performing male roles and females performing female roles.
Rand’s superman is not on our side. But he is not on the progs side. He is his own side, and this makes him largely irrelevant for political power, which requires cohesion.
The state can facilitate science by being a customer and buying high tech stuff. Indeed, a great deal of advance has come from the state seeking means to hurt people and break their toys, but when the state tries to itself advance technology, it usually turns out badly: Nasa could not build rockets. Kidnapped Wernher von Braun. Asked him how to build rockets. Still could not build rockets.
Nasa puts Wernher von Braun in charge. Now it can build rockets. Puts a man on the moon
.Wernher von Braun retires. New types of rockets don’t work. Old types of rockets gradually stop working no matter how much government money is poured down the toilet.
Where did Nasa find Wernher von Braun?
Nazis kidnapped him from the German rocket club which they shut down.
Seems obvious that we would have wound up with a whole lot better rocket technology if the rocket club became, or spawned, a bunch of startups, one of them led by Wernher von Braun, and governments outsourced rockets. Which is what gave us the reusable booster that lands as a rocket should land.
3 notes
·
View notes
Text
Title: On Translating Named Characters from One Language into Another
Author: Stephen A. W. Gunn
Rating: 1/5 stars
A book on how to translate one language into another, as if that weren't just the whole, obvious point of language-translation.
The book has about fifty pages in it, roughly divided into three parts. ("Named characters" here means people or things, not just any kind of word. For instance, in the English-to-German example, I might ask "who is the author of the book?" or "what are the contents of this building?" or "what does the word 'door' mean in this language?" The question is asking what it would take for us to have the sort of book we want in the other language -- even if the "meaning" of that book would be very different.)
Gunn is (understandably) very interested in language-translation as a science. But he doesn't think a single algorithm can handle all possible cases of language-translation. (It's very unlikely you could get the "full" semantics of one language to another with a single program.) So, you have to pick cases to focus on. And then there's the question of how exactly you will choose to work with each case.
For instance, in this book, Gunn focuses on translation of (names of) places, events, people and other named objects. He has a few reasons for making this decision. First, the things of most interest to us in translation are the ones which are already named by us, since they are most likely to be mentioned in ordinary conversation. By focusing on translation of named objects, we can focus on the case where the name of an object is already the natural equivalent of the name of another object -- rather than asking whether it's a good idea to translate "door" by some arbitrary new object and hoping that people will fill in the gap from context.
Next, names are a type of "noun" in the grammar of many (most?) languages, and they come in a wide variety of forms. They are also particularly easy to translate. But translating nouns is an extremely hard problem: if we translate every "noun" in the input sentence according to the same rules -- which would be the obvious thing to do, the algorithm of choosing a single word to use where translation of the literal text would require a different choice in every possible case -- then the result would often be a complete nonsense sentence. Rather than working out the details of a complicated algorithm for translation, it's easier just to stick with the most common case: translating names.
Gunn takes his focus on places, events and people as a given. Given the focus on these three types of things, his algorithm for translating names in one language to another will be the same for all three. It looks something like this:
For each of the named objects:
1. Take the English word or term and put it into a dictionary of the relevant target language. Let's say this gives us a total of N translations for the English word/term.
2. Take a word or term chosen at random from the target language vocabulary and call it Y.
3. Compare it to the translations of the word/term in the input language. If the translations in the input language are all equal or near-equal to one of the translations of Y in the target language, put it in as a translation of the word/term in the target language, and mark it as done.
4. Keep Y the same as in the previous step, add the next Y chosen, etc., until all the translated words/terms in the target language have some corresponding in the input language.
The translation of the word "door" from English into German will look something like this:
1. take "Die Tür," from the English dictionary, and put it in the German dictionary.
2. take a randomly chosen word from the German vocabulary and call it "Der Dach."
3. compare "Die Tür" and "Der Dach." They don't fit; the German version of "Die Tür" is "Der Fenster."
4. change "Der Fenster" to "Der Dach." That is now the German "Dach der Tür."
We should note a couple of things about step 2. Because of step 1, every "translation" step in this process requires at least one word from a dictionary in the target language (since we never get "die Tür" in step 2). Also, it is very unlikely that two different words will be translated "the same way."
So, to get any "translation" step in the process going, we'll need to choose from all the German words in the dictionary to start. The English-to-German translation of "the door" will then take the first German word that has a translation with equal or near equal meaning to "the door."
This is fine as far as it goes. But in the English-to-German translation, for instance, step 3 was "compare "the door" and "Der Dach." They don't fit;" the German "Dach der Tür." So what do we replace "Dach der Tür" with? Well, the first German word which has equal or near-equal meaning to "Tür" is "Tür"; so we will pick "Tür" from the dictionary and use it in the translation as "Dach der Tür." This is fine.
In English-to-French, however, "the door" is translated to "la porte;" and the first French word with equal or near equal meaning to "porte" is "porte," not "la porte"; but of course, we cannot translate "porte" to "die Tür," because that would be a nonsense sentence. So what do we do? In the English-to-French translation, there is no "Dach der Tür" and no "Dach der Porte"; so we will start the French translation with "La porte."
If you want to think about this process for some time, the reader can see that the "door" to "Dach der Tür" step actually depends on an English word/term. In English-to-German, that term was "die Tür" and that was used to "translate" "die Tür." In English-to-French it is "la porte," which is used to "translate" "la porte."
The reason I mention this here is that it tells us something interesting about step 3 in the German-to-English translation: we are saying that a given word in English "could be translated to" the same word in German, but that we will only do that translation after we have done all the others. That is, we are saying that each word "could be translated by" a particular German word or translation, and we are saying that this is done by going through the other translations step by step. But that means that step 3 in the English-to-German process depends on the specific word/term chosen "from" step 3 in the German-to-English process. So we will have to start with as many German words as steps 2 in the English-to-German process.
One thing about this process is that there is no word that "could be translated by"; at any step, the chosen word will have to be translated according to step 2, which means that this step will have to work on some word chosen "from step 3 in the English-to-German translation." So we will start the German translation with as many words as steps 2 in the English-to-German process.
But that is a great many words to start with. This will be the case in every case of language-translation. It's just that we can do a language-translation in every case without actually knowing the full semantics of one language to another. (In the "door" case, step 3 "compare 'the door' and 'Der Dach.'" would
1 note
·
View note
Text
How Lottery Systems Work: A Short Guide
Lottery systems are one of the oldest and most widely used methods of random sampling. They have several applications, ranging from advertising to political elections. In simple terms, a lottery system is a method that uses luck as a way to determine who gets to participate in some sort of selection process or activity.
What Are Lottery Systems Used For?
A lottery system is used to randomly select a certain number of participants from a larger group. The system can be as simple as picking a number out of a hat, or it can be as complex as a computer-generated algorithm. The selection process doesn’t have to be limited to purely random drawings. You can program a lottery system to select a certain number of participants according to certain criteria. For example, a company hiring for an open position may use a lottery system to select 10 potential employees from a list of 100 applicants. In this case, the lottery system would be used to ensure that all applicants had an equal chance of being selected for the position. A lottery system can be used in a variety of situations. It can be used in political elections, such as by selecting a winner from a pool of candidates at a party convention. It can be used in sports to award a championship title or a set of start positions. It can also be used in academic institutions to select students for scholarships or other special enrollment programs.
See this video to look why a lot of people prefer this software — an offer guaranteed to put money in your pocket. A huge market and a unique hook means big $$! (Click here to watch the video).
How Does a Lottery System Work?
The best way to explain how a lottery system works is by giving an example. Let’s say that you’re the CEO of a start-up company, and you want to hire 10 candidates for an open position. You decide that you want to use a lottery system to select 10 candidates from a pool of 100 potential employees. First, you’ll create a lottery system. The system will consist of a ballot and a bowl, the bowl being the place where all the ballots are placed. Second, you’ll select 10 candidates from the pool of 100 candidates. These 10 candidates will be the ones whose names will appear on the ballot. Third, you’ll collect all the ballots and put them in the bowl. Fourth, you’ll draw one ballot from the bowl. This ballot will contain the name of one of the 10 candidates.
First-Past-the-Post Lottery System
A first-past-the-post lottery system is a type of lottery system that employs a first-past-the-post mechanism to generate a set of winners. This system is widely used in political elections, such as in parliamentary systems, where it is used to select the heads of government. First-past-the-post lottery systems work by first selecting the number of winners from a larger group. The selected number is then divided by the number of candidates that are left. For example, let’s say that there are 10 candidates for a position with 100 votes being cast for the position. The first-past-the-post lottery system will select three candidates as the winners, leaving a total of seven candidates who didn’t win. The number of winners divided by the number of candidates left will yield the number of votes needed to win. In this example, the three winners will require 30 votes to win the election, while the seven candidates who lost will require 10 votes each to finish in the top three.
Rotating Barrel Lottery System
A rotating barrel lottery system is a type of lottery system that employs a rotating barrel to generate a set of winners. This system is widely used in sports to award a championship title. Rotating barrel lottery systems work by first selecting the number of winners from a larger group. The selected number is then divided by the number of candidates that are left. For example, let’s say that there are 10 candidates for a position with 100 votes being cast for the position. The rotating barrel lottery system will select three candidates as the winners, leaving a total of seven candidates who didn’t win. The number of winners divided by the number of candidates left will yield the number of votes needed to win. In this example, the three winners will require 30 votes to win the title, while the seven candidates who lost will require 10 votes each to finish in the top three.
Digital Matrix Lottery System
A digital matrix lottery system is a type of lottery system that employs a digital matrix to generate a set of winners. This system is widely used to select participants for a variety of activities, including academic scholarships and grant programs. Digital matrix lottery systems work by first selecting the number of winners from a larger group. The selected number is then divided by the number of candidates that are left. For example, let’s say that there are 10 candidates for a position with 100 votes being cast for the position. The digital matrix lottery system will select three candidates as the winners, leaving a total of seven candidates who didn’t win. The number of winners divided by the number of candidates left will yield the number of votes needed to win. In this example, the three winners will require 30 votes to win the election, while the seven candidates who lost will require 10 votes each to finish in the top three.
Combination Lottery System
A combination lottery system is a type of lottery system that employs a combination mechanism to generate a set of winners. This system is widely used in political elections, such as in the United Kingdom, where it is used to select members of parliament. Combination lottery systems work by first selecting the number of winners from a larger group. The selected number is then divided by the number of candidates that are left. For example, let’s say that there are 10 candidates for a position with 100 votes being cast for the position. The combination lottery system will select three candidates as the winners, leaving a total of seven candidates who didn’t win. The number of winners divided by the number of candidates left will yield the number of votes needed to win. In this example, the three winners will require 30 votes each to win the election, while the seven candidates who lost will require 10 votes each to finish in the top three.
Wrapping Up
A lottery system is fairly simple as it employs an element of chance to select participants for a particular process or activity. There are several different types of lottery systems, each with its unique properties and characteristics. The main types include first-past-the-post, rotating barrel, digital matrix, and combination systems. Each has its pros and cons depending on your needs as the user of the system.
1 note
·
View note
Text
Memory
In computers, memory is the most essential component of the normal functioning of any system. The computer system categorizes the memory for different purposes and uses. In this section, we have discussed the classification of memory in detail. Also, we will discuss types of memory, features of memory, RAM, ROM, SRAM, DRAM, and its advantages and disadvantages.
What is computer memory?
Computer memory
is any physical device, used to store data, information or instruction temporarily or permanently. It is the collection of storage units that stores binary information in the form of bits. The memory block is split into a small number of components, called cells. Each cell has a unique address to store the data in memory, ranging from zero to memory size minus one. For example, if the size of computer memory is 64k words, the memory units have 64 * 1024 = 65536 locations or cells. The address of the memory’s cells varies from 0 to 65535.
Why do we need a computer memory?
Read More
In the computer system, we need computer memory to store various types of data like text, images, video, audio, documents, etc. We can retrieve it when the data is required. For example, when we write and execute any computer program, it is initially stored in primary memory. If the processor does not need particular items for a longer time, the program or data is automatically saved into the permanent or secondary memory. Then the data is called from secondary memory to main memory and performs the execution of codes.
Features of Memory
Following are the different features of the memory system that includes:
1. Location: It represents the internal or external location of the memory in a computer. The internal memory is inbuilt in computer memory. It is also known as primary memory. the example of primary memory are registers, cache and main memory. Whereas, external memory is the separate storage device from the computer, such as disk, tape, USB pen drive.
2. Capacity: It is the most important feature of computer memory. Storage capacity can vary in external and internal memory. External devices’ storage capacity is measured in terms of bytes, whereas the internal memory is measured with bytes or words. The storage word length can vary in bits, such as 8, 16 or 32 bits.
3. Access Methods: Memory can be accessed through four modes of memory.
DMA: As the name specifies, Direct Memory Address (DMA) is a method that allows input/output (I/O) devices to access or retrieve data directly or from the main memory.
Sequential Access Method: The sequential access method is used in a data storage device to read stored data sequentially from the computer memory. Whereas, the data received from random access memory (RAM) can be in any order.
Random Access Method: It is a method used to randomly access data from memory. This method is the opposite of SAM. For example, to go from A to Z in random access, we can directly jump to any specified location. In the Sequential method, we have to follow all intervening from A to Z to reach at the particular memory location.
Associative Access Method: It is a special type of memory that optimizes search performance through defined data to directly access the stored information based on a memory address.
Read More
4. Unit of transfer: As the name suggests, a unit of transfer measures the transfer rate of bits that can be read or write in or out of the memory devices. The transfer rate of data can be different in external and internal memory.
Internal memory: The transfer rate of bits is mostly equal to the word size.
External memory: The transfer rate of bit or unit is not equal to the word length. It is always greater than a word or may be referred to as blocks.
5. Performance: The performance of memory is majorly divided into three parts.
Access Time: In random access memory, it represents the total time taken by memory devices to perform a read or write operation that an address is sent to memory.
Memory Cycle Time: Total time required to access memory block and additional required time before starting second access.
Transfer rate: It describes the transfer rate of data used to transmit memory to or from an external or internal memory device. Bit transfer can be different for different external and internal devices.
6. Physical types: It defines the physical type of memory used in a computer such as magnetic, semiconductor, magneto-optical and optical.
7. Organization: It defines the physical structure of the bits used in memory.
8. Physical characteristics: It specifies the physical behavior of the memory like volatile, non-volatile or non-erasable memory. Volatile memory is known as RAM, which requires power to retain stored information, and if any power loss has occurred, stored data will be lost. Non-volatile memory is a permanent storage memory that is used to obtain any stored information, even when the power is off. Non-erasable memory is a type of memory that cannot be erased after the manufactured like ROM because at the time of manufactured ROM are programmed.
Classification of MemoryPrimary or Main Memory
Primary memory is also known as the computer system’s main memory that communicates directly within the CPU
, Auxiliary memory and the Cache memory. Main memory is used to kept programs or data when the processor is active to use them. When a program or data is activated to execute, the processor first loads instructions or programs from secondary memory into main memory, and then the processor starts execution. Accessing or executing of data from primary memory is faster because it has a cache or register memory that provides faster response, and it is located closer to the CPU
. The primary memory is volatile, which means the data in memory can be lost if it is not saved when a power failure occurs. It is costlier than secondary memory, and the main memory capacity is limited as compared to secondary memory.
The primary memory is further divided into two parts:
1. RAM (Random Access Memory)
2. ROM (Read Only Memory)
Random Access Memory (RAM)
Random Access Memory (RAM)
is one of the faster types of main memory accessed directly by the CPU. It is the hardware in a computer device to temporarily store data, programs or program results. It is used to read/write data in memory until the machine is working. It is volatile, which means if a power failure occurs or the computer is turned off, the information stored in RAM
will be lost. All data stored in computer memory can be read or accessed randomly at any time.
There are two types of RAM:
SRAM
DRAM
DRAM: DRAM (Dynamic Random-Access Memory) is a type of RAM that is used for the dynamic storage of data in RAM. In DRAM, each cell carries one-bit information. The cell is made up of two parts: a capacitor and a transistor. The size of the capacitor and the transistor is so small, requiring millions of them to store on a single chip. Hence, a DRAM chip can hold more data than an SRAM chip of the same size. However, the capacitor needs to be continuously refreshed to retain information because DRAM is volatile. If the power is switched off, the data store in memory is lost.
Characteristics of DRAM
1. It requires continuously refreshed to retain the data.
2. It is slower than SRAM
3. It holds a large amount of data
4. It is the combination of capacitor and transistor
5. It is less expensive as compared to SRAM
6. Less power consumption
SRAM: SRMA (Static Random-Access Memory) is a type of RAM used to store static data in the memory. It means to store data in SRAM remains active as long as the computer system has a power supply. However, data is lost in SRAM when power failures have occurred.
Characteristics of Static Ram
1. It does not require to refresh.
2. It is faster than DRAM
3. It is expensive.
4. High power consumption
5. Longer life
6. Large size
7. Uses as a cache memory
Advantages of RAM
It is a faster type of memory in a computer.
It requires less power to operate.
Program loads much faster
More RAM increases the performance of a system and can multitask.
Perform read and write operations.
The processor can read information faster than a hard disc, floppy, USB, etc.
Disadvantages of RAM
Less RAM reduces the speed and performance of a computer.
Due to volatile, it requires electricity to preserve the data.
It is expensive than ROM
It is unreliable as compared to ROM
The Size of RAM is limited.
Read-Only Memory (ROM)
ROM
is a memory device or storage medium that is used to permanently store information inside a chip. It is a read-only memory that can only read stored information, data or programs, but we cannot write or modify anything. A ROM contains some important instructions or program data that are required to start or boot a computer. It is a non-volatile memory; it means that the stored information cannot be lost even when the power is turned off or the system is shut down.
Types of ROM
There are five types of Read Only Memory:
1. MROM (Masked Read Only Memory):
MROM is the oldest type of read-only memory whose program or data is pre-configured by the integrated circuit manufacture at the time of manufacturing. Therefore, a program or instruction stored within the MROM chip cannot be changed by the user.
2. PROM(ProgrammableReadOnlyMemory):
It is a type of digital read-only memory, in which the user can write any type of information or program only once. It means it is the empty PROM chip in which the user can write the desired content or program only once using the special PROM programmer or PROM burner device; after that, the data or instruction cannot be changed or erased.
3. EPROM(ErasableandProgrammableReadOnlyMemory):
It is the type of read only memory in which stored data can be erased and re-programmed only once in the EPROM memory. It is a non-volatile memory chip that holds data when there is no power supply and can also store data for a minimum of 10 to 20 years. In EPROM, if we want to erase any stored data and re-programmed it, first, we need to pass the ultraviolet light for 40 minutes to erase the data; after that, the data is re-created in EPROM.
4. EEPROM (Electrically Erasable and Programmable Read Only Memory): The EEROM is an electrically erasable and programmable read only memory used to erase stored data using a high voltage electrical charge and re-programmed it. It is also a non-volatile memory whose data cannot be erased or lost; even the power is turned off. In EEPROM, the stored data can be erased and reprogrammed up to 10 thousand times, and the data erase one byte at a time.
5. Flash ROM: Flash memory is a non-volatile storage memory chip that can be written or programmed in small units called Block or Sector. Flash Memory is an EEPROM form of computer memory, and the contents or data cannot be lost when the power source is turned off. It is also used to transfer data between the computer and digital devices.
Advantages of ROM
1. It is a non-volatile memory in which stored information can be lost even power is turned off.
2. It is static, so it does not require refreshing the content every time.
3. Data can be stored permanently.
4. It is easy to test and store large data as compared to RAM.
5. These cannot be changed accidently
6. It is cheaper than RAM.
7. It is simple and reliable as compared to RAM.
8. It helps to start the computer and loads the OS.
Disadvantages of ROM
1. Store data cannot be updated or modify except to read the existing data.
2. It is a slower memory than RAM to access the stored data.
3. It takes around 40 minutes to destroy the existing data using the high charge of ultraviolet light.
Secondary Memory
Secondary memory
is a permanent storage space to hold a large amount of data. Secondary memory is also known as external memory that representing the various storage media (hard drives, USB, CDs, flash drives and DVDs) on which the computer data and program can be saved on a long term basis. However, it is cheaper and slower than the main memory. Unlike primary memory, secondary memory cannot be accessed directly by the CPU. Instead of that, secondary memory data is first loaded into the RAM (Random Access Memory) and then sent to the processor to read and update the data. Secondary memory devices also include magnetic disks like hard disk and floppy disks, an optical disk such as CDs and CDROMs, and magnetic tapes.
Features of Secondary Memory
Its speed is slower than the primary/ main memory.
Store data cannot be lost due to non-volatile nature.
It can store large collections of different types, such as audio, video, pictures, text, software, etc.
All the stored data in a secondary memory cannot be lost because it is a permanent storage area; even the power is turned off.
It has various optical and magnetic memories to store data.
Types of Secondary Memory
The following are the types of secondary memory devices:
Hard Disk
A hard disk is a computer's permanent storage device. It is a non-volatile disk that permanently stores data, programs, and files, and cannot lose store data when the computer's power source is switched off. Typically, it is located internally on computer's motherboard that stores and retrieves data using one or more rigid fast rotating disk platters inside an air-sealed casing. It is a large storage device, found on every computer or laptop for permanently storing installed software, music, text documentation, videos, operating system, and data until the user did not delete.
Floppy Disk
A floppy disk is a secondary storage system that consisting of thin, flexible magnetic coating disks for holding electronic data such as computer files. It is also known as Floppy Diskette that comes in three sizes like 8 inches, 5.5 inches and 3.5 inches. The stored data of a floppy disk can be accessed through the floppy disk drive. Furthermore, it is the only way through a new program installed on a computer or backup of the information. However, it is the oldest type of portable storage device, which can store data up to 1.44 MB. Since most programs were larger, that required multiple floppy diskettes to store large amounts of data. Therefore, it is not used due to very low memory storage.
CD (Compact Disc)
A CD
is an optical disk storage device, stands for Compact Disc. It is a storage device used to store various data types like audio, videos, files, OS, Back-Up file, and any other information useful to a computer. The CD has a width of 1.2 mm and 12 cm in height, which can store approximately 783 MB of data size. It uses laser light to read and write data from the CDs.
Types of CDs
1. CD-ROM (Compact Disc Read Only Memory): It is mainly used for bulk size mass like audio CDs, software and computer games at the time of manufacture. Users can only read data, text, music, videos from the disc, but they cannot modify or burnt it.
2. CD-R (Compact Disc Recordable): The type of Compact Disc used to write once by the user; after that, it cannot be modified or erased.
3. CD-RW (Compact Disc Rewritable): It is a rewritable CD disc, often used to write or delete the stored data.
DVD Drive/Disc
DVD is an optical disc storage device, stands for Digital Video Display or Digital Versatile Disc. It has the same size as a CD but can store a larger amount of data than a compact disc. It was developed in 1995 by Sony, Panasonic, Toshiba and Philips four electronics companies. DVD drives are divided into three types, such as DVD ROM (Read Only Memory), DVD R (Recordable) and DVD RW (Rewritable or Erasable). It can store multiple data formats like audio, videos, images, software, operating system, etc. The storing capacity of data in DVD is 4.7 GB to 17 GB.
Blu Ray Disc (BD)
Blu Ray is an Optical disc storage device used to store a large amount of data or high definition of video recording and playing other media files. It uses laser technology to read the stored data of the Blu-ray Disk. It can store more data at a greater density as compared to CD/ DVD. For example, compact discs allow us to store 700 MB of data, and in DVDs, it provides up to 8 GB of storage capacity, while Blu-ray Discs provide 28 GB of space to store data.
Pen Drive
Read More
A pen drive is a portable device used to permanently store data and is also known as a USB flash drive. It is commonly used to store and transfer the data connected to a computer using a USB port. It does not have any moveable part to store the data; it uses an integrated circuit chip that stores the data. It allows the users to store and transfer data like audio, videos, images, etc. from one computer to any USB pen drive. The storing capacity of pen drives from 64 MB to 128 GB or more.
Cache Memory
It is a small-sized chip-based computer memory that lies between the CPU and the main memory. It is a faster, high performance and temporary memory to enhance the performance of the CPU. It stores all the data and instructions that are often used by computer CPUs. It also reduces the access time of data from the main memory. It is faster than the main memory, and sometimes, it is also called CPU memory because it is very close to the CPU chip. The following are the levels of cache memory.
1. L1 Cache: The L1 cache is also known as the onboard, internal, or primary cache. It is built with the help of the CPU. Its speed is very high, and the size of the L1 cache varies from 8 KB to 128 KB.
2. L2 Cache: It is also known as external or secondary cache, which requires fast access time to store temporary data. It is built into a separate chip in a motherboard, not built into the CPU like the L1 level. The size of the L2 cache may be 128 KB to 1 MB.
3. L3 Cache: L3 cache levels are generally used with high performance and capacity of the computer. It is built into a motherboard. Its speed is very slow, and the maximum size up to 8 MB.
Advantages of Cache Memory
1. Cache memory is the faster memory as compared to the main memory.
2. It stores all data and instructions that are repeatedly used by the CPU for improving the performance of a computer.
3. The access time of data is less than the main memory.
Disadvantage of Cache Memory
Read More
1. It is very costly as compared to the Main memory and the Secondary memory.
2. It has limited storage capacity.
Register Memory
The register memory is a temporary storage area for storing and transferring the data and the instructions to a computer. It is the smallest and fastest memory of a computer. It is a part of computer memory located in the CPU as the form of registers. The register memory is 16, 32 and 64 bits in size. It temporarily stores data instructions and the address of the memory that is repeatedly used to provide faster response to the CPU.
#explain memory#what is memory#cache#RAM#ROM#DVD#CD#register memory#primary memory#secondry memory#types of memory
1 note
·
View note
Text
Gran Turismo 6 Pc Key Txt Descargar
License key gran turismo 6 pc. The last serial number for this program was added to our data base on May 19, 2019. 383 visitors told us the serial is good, 196 guys said the number is bad You have viewed too many serial numbers from your ip (157.55.39.145) today. TopFiles - Download GRAN TURISMO 6 CRACK + KEYGEN.cab To download this file you simply have to click on the Download button above and follow all the instructions. After you completed all the steps, the download will automatically begin in less than 3 minutes. Gran Turismo 5 Free Redeem Codes (Gran Turismo 5 Keygen) GranTurismo5Free. + Torrent XBOX 360,PS3,PC. Steam Keygen Key Generator › Keygen. TopFiles - Download GRAN TURISMO 6 CRACK + KEYGEN.cab To download this file you simply have to click on the Download button above and follow all the instructions. After you completed all the steps, the download will automatically begin in less than 3 minutes. Since typically transpires with myself, I have furthermore located Gran Turismo 6 Key Generator application online at random. Maybe that is present additional appropriate Key Generator programs regarding Gran Turismo 6 online game, but these days I will consult with an individual this the one that does work regarding for me personally.
Gran Turismo 6 Pc Key.txt Download
Gran Turismo 6 Pc Key Txt Descargar Windows 7
Gran Turismo 6 is a hustling computer game created by Polyphony Digital and distributed by Sony Computer Entertainment for thePlayStation 3 computer game console. It is the 6th real discharge and twelfth diversion in general in the Gran Turismo computer game arrangement. It was discharged worldwide on December 6, 2013, and was mainstream with faultfinders, won honors, and beat diagrams in nations around the globe. New components incorporated the expansion of more autos and tracks, upgrades to the auto customisation alternatives, and associations with the Goodwood Festival of Speed, The Ayrton Senna Institute, the FIA and NASA.
Ark survival evolved unlock hairstyles. A quick video explaining how to unlock all hairstyles in ARK Survival Evolved.' Perspectives' Kevin MacLeod (incompetech.com)Licensed under Creative Commons. Detailed information about the Ark command SetHeadHairStyle for all platforms, including PC, XBOX and PS4. Includes examples, argument explanation and an easy-to-use command builder. This command will set the style of your hair, relative to the hair ID specified (0-7). Trying to unlock all the skins/hairstyles. ARK: Survival Evolved PlayStation 4. Android iOS (iPhone/iPad) Linux Macintosh Nintendo Switch PC Xbox One. Log In to add custom notes to this or any other game. ARK: Survival Evolved; Trying to unlock all the skins/hairstyles. User Info: LoveLikeJazz.
Acapela-Box is a service that provides a conversion of your text into speech by using the Acapela Text to Speech technology. You can listen to the generated speech freely without limitation. If you want to use the corresponding sound file you need to create a personal account and purchase it. Learn how to talk like Yoda - just type or paste in a bunch of text and use the 'Convert to Yoda-Speak' button. Try it with jokes, emails, song lyrics, card messages, whatever! Initial development based on this fine essay on the rules of 'Yodish': Yodish Analysis! Convert from English to Yoda speak. Yoda often orders sentences as Object-Subject-Verb, split verbs, switches entire phrases and sometimes uses sentences that are different from his normal syntax! Because of this it is difficult to accurately represent his sentence structure. But we tried hard and we constantly improve our patterns. Have fun and may the force be with you! Yoda text to voice generator free. In this article, we will go through a text to speech demo using Yoda's voice as an example. We will walk you through a tutorial of voice generation and show you how to train a model to produce Yoda's voice from a given text: broutonlab Yoda text to speech What's more, we will share with you a pipeline that will enable you to generate any.
Gran Turismo 6 Pc Key.txt Download
The game is presently accessible for Microsoft Windows on GamesKnit.
In November 2011, the Gran Turismo arrangement’s inventor, Kazunori Yamauchi, said that he and his group at Polyphony Digital were dealing with Gran Turismo 6. In March 2012, specialists were seen nearby at Mount Panoramain Bathurst, New South Wales, Australia, shooting and examining the track. The laborers uncovered that Mount Panorama will be incorporated into Gran Turismo 6.
In February 2013, Sony’s Computer Entertainment Europe senior VP Michael Denny asserted that Gran Turismo 6 will remain a PlayStation 3 title, notwithstanding the late disclosing of the PlayStation 4.
Gran Turismo 6 was declared on May 15, 2013, when Sony Computer Entertainment Europe facilitated a festival of the fifteenth commemoration of Gran Turismo at Silverstone Circuit in the United Kingdom. Kazunori Yamauchi said at the authority announcement, Gran Turismo 6 will highlight 71 designs of 33 tracks, 1200 autos, another adaptable rendering motor that components versatile tessellation, and an updated more straightforward menu interface with speedier stacking times. An early form of Gran Turismo 6’s upgraded material science were appeared to people in general when GT Academy 2013 was discharged on the PlayStation Store on July 2, 2013.
If you want Gran Turismo 6on your PC, click on:
Installation instructions Gran Turismo 6 e version for PC:
1. Unrar 2. Burn or mount the image 3. Install the game 4. Open /Activation directory on your game install directory and take the registration code 5. Play the game 6. Support the software developers. If you like this game, BUY IT!
GRAN TURISMO 6 SYSTEM REQUIREMENTS
In order to play Gran Turismo 6 on your PC, your system needs to be equipped with at least the following specifications: OS: Windows 7 / 8 / 8.1 / 10
Operating System: Windows Vista 32-Bit with Service Pack 2 and the KB971512 platform update
Processor: AMD Athlon X2 2.8 GHZ or Intel Core 2 Duo 2.4 GHZ
Ram: 4GB or more
Free Hard Drive Space: 15GB
Processor: AMD Athlon X2 2.8 GHz or higher; Intel Core 2 Duo 2.4 GHz or higher
Graphics Card: AMD Radeon 3870 or higher; NVIDIA GeForce 8800 GT or higher
For the best Gran Turismo 6 PC experience, however, we recommend having a system equal to or better than than the following specifications: OS: Windows 7 / 8 / 8.1 / 10
Operating System: Windows 8 (64-bit) or Windows 10
Processor: AMD Six-Core CPU; Intel Quad-Core CPU
RAM: 8GB
Free Hard Drive Space: 15GB
Graphics Card: AMD Radeon 7870 or higher; NVIDIA GeForce GTX 660 or higher
Graphics Memory: 3GB
Gran Turismo 6 Pc Key Txt Descargar Windows 7
Save
Dec 3rd, 2013
Never
Not a member of Pastebin yet?Sign Up, it unlocks many cool features!

http://skidrow-official.blogspot.com/2013/11/gran-turismo-6.html<--- DOWNLOAD HERE
Gran.Turismo.6.packed.skidrow(2.32GB)
Repacked By... : Razor 1911
Keygen By.... : SKIDROW + Razor 1911
Size Unpacked.. : 7.16GB
Platform.... : PC, PS3, Xbox 360
Type...... : Full Rip
************************************************************************************************************
Incoming Search Terms:
Gran Turismo 6 download,download Gran Turismo 6,Gran Turismo 6 free download,free download Gran Turismo 6,Gran Turismo 6 download free,download free Gran Turismo 6,Gran Turismo 6 full,full Gran Turismo 6,Gran Turismo 6 full game,full game Gran Turismo 6,Gran Turismo 6 get,get Gran Turismo 6,Gran Turismo 6 get free,get free Gran Turismo 6,Gran Turismo 6 youtube,youtube Gran Turismo 6,Gran Turismo 6 wiki,wiki Gran Turismo 6,Gran Turismo 6 release date,release date Gran Turismo 6,Gran Turismo 6 pc,Gran Turismo 6 mac,Gran Turismo 6 xbox 360,Gran Turismo 6 ps3,Gran Turismo 6 keygen,Gran Turismo 6 crack,Gran Turismo 6 beta keys,Gran Turismo 6 keys,Gran Turismo 6 full download,full download Gran Turismo 6,Gran Turismo 6 cracked,cracked Gran Turismo 6,Gran Turismo 6 for pc,Gran Turismo 6 for mac,Gran Turismo 6 for ps3,Gran Turismo 6 for xbox 360,Gran Turismo 6 full version,Gran Turismo 6 beta codes,Gran Turismo 6 dlc,Gran Turismo 6 cheat,Gran Turismo 6 cheats,Gran Turismo 6 key generator,Gran Turismo 6 serial key,Gran Turismo 6 serial code,Gran Turismo 6 beta,Gran Turismo 6 steam,Gran Turismo 6 descargar,descargar Gran Turismo 6,Gran Turismo 6 caricare,caricare Gran Turismo 6,Gran Turismo 6 telecharger,telecharger Gran Turismo 6JHG67567
http://skidrow-official.blogspot.com/2013/11/gran-turismo-6.html<--- DOWNLOAD HERE Gran.Turismo.6.packed.skidrow(2.32GB) Repacked By... : Razor 1911 Cracked By... : SKIDROW Keygen By.... : SKIDROW + Razor 1911 Size Packed... : 2.32GB Size Unpacked.. : 7.16GB Size After... : 15.62GB Platform.... : PC, PS3, Xbox 360 Format..... : ISO Type...... : Full Rip ************************************************************************************************************ Incoming Search Terms: Gran Turismo 6 download,download Gran Turismo 6,Gran Turismo 6 free download,free download Gran Turismo 6,Gran Turismo 6 download free,download free Gran Turismo 6,Gran Turismo 6 full,full Gran Turismo 6,Gran Turismo 6 full game,full game Gran Turismo 6,Gran Turismo 6 get,get Gran Turismo 6,Gran Turismo 6 get free,get free Gran Turismo 6,Gran Turismo 6 youtube,youtube Gran Turismo 6,Gran Turismo 6 wiki,wiki Gran Turismo 6,Gran Turismo 6 release date,release date Gran Turismo 6,Gran Turismo 6 pc,Gran Turismo 6 mac,Gran Turismo 6 xbox 360,Gran Turismo 6 ps3,Gran Turismo 6 keygen,Gran Turismo 6 crack,Gran Turismo 6 beta keys,Gran Turismo 6 keys,Gran Turismo 6 full download,full download Gran Turismo 6,Gran Turismo 6 cracked,cracked Gran Turismo 6,Gran Turismo 6 for pc,Gran Turismo 6 for mac,Gran Turismo 6 for ps3,Gran Turismo 6 for xbox 360,Gran Turismo 6 full version,Gran Turismo 6 beta codes,Gran Turismo 6 dlc,Gran Turismo 6 cheat,Gran Turismo 6 cheats,Gran Turismo 6 key generator,Gran Turismo 6 serial key,Gran Turismo 6 serial code,Gran Turismo 6 beta,Gran Turismo 6 steam,Gran Turismo 6 descargar,descargar Gran Turismo 6,Gran Turismo 6 caricare,caricare Gran Turismo 6,Gran Turismo 6 telecharger,telecharger Gran Turismo 6JHG67567

0 notes
Text
Content Marketing Strategy 2021 - A Step-By-Step Guide
This is a beginner's guide to learn content marketing strategy for the complex sale.
You'll learn about the critical interaction between quality content and SEO to drive organic traffic to your website and convert that traffic to leads and revenue and gain credibility with your target buyers.
Content marketing is used to capture buyers at the information gathering stage by matching keywords they (and the rest of their buying team) use for research with the content you produce.
These are called buyer intent keywords. The interaction between these commercial intent keywords and your content is at the heart of content marketing for the complex sale.
The goal is to drive interested traffic and convert a portion of that traffic to leads.
In the process, as buyers interact with your content, you gain mindshare and credibility.
Even if they don’t fill out a form on a visit to your website, they now know who you are.
By the end, you will understand how to implement a plan for content marketing that drives product-based revenue.
The 4 Steps of B2B Content Marketing
Step 1. Planning content ideas based on keywords to match your buyers’ search intent

Step 2. Organizing the content to optimize search rankings

Step 3. Syndicating and promoting your content across multiple channels to amplify your efforts

Step 4. Setting goals and analyzing performance

Content Marketing Knowledge Gap
Surprisingly, there is a large gap between those who know they need to do content marketing and those who do it well.Neil Patel recently pointed out a study by Zazzle Media showing that, while 79% of marketers believe content marketing is effective, only 6% know how to implement it.

Learn these content marketing ideas, follow content marketing trends, be patient, and you will get found ahead of your competitors.
Why Is Content Marketing Essential?
1. High Keyword rankings improve your chances of getting found and making it onto your target buyers' shortlists.
2. Credibility & authority increase when visitors to your site see valuable, insightful content to help with their research.
3. Repurpose content to create an endless source of material for other channels like social and video, which expands your audience and strengthens your brand and credibility.
Content Marketing Agencies
This guide is designed primarily to ‘do it yourself’. A viable alternative strategy is to outsource your program to a b2b content marketing agency.
An agency can implement a content marketing plan with a purpose and strategy while freeing up your time for other marketing activities that can't be outsourced and are core to growing your revenue.
The Content Marketing Checkdown List
Get This Guide in a Handy Checklist Format Now!
Run a Test
Go to a search engine and type in some keywords you might use to research your offering as a buyer. The competitors in the results are doing content marketing right (or at least better than anyone else) and getting deals in their pipeline from active buyers.
If you see no competitors but only bloggers and publishers in the top search engine results pages (SERPs), then you have a real opportunity to get ranked ahead of the competition.
You might notice more article content than product content in the SERPs. Over the years, Google has changed its algorithm to favor authoritative, valuable information-based content over product content.
Keyword Ranking Factors
Before we dive into the four steps, let’s step back and understand at a high level the factors that all the search engines use (with a bias towards Google). You need to understand each before you can start building a strategy to get ranked.
•Backlinks/Referring domains (RDs) - Google’s original insight was that the more a page has sites linking to it, the more authoritative it must be. There are many more factors that go into getting high rankings, but backlinks are still critical.
•Domain Authority (DA) - Created by Moz, here is how they define it:
“A search engine ranking score that predicts how likely a website is to rank on search engine results pages (SERPs). A Domain Authority score ranges from one to 100, with higher scores corresponding to a greater ability to rank.”
Like your personal credit score, higher DA is a number you always want to try to improve. You do so with consistently high-quality, engaging content and backlinks with a higher DA than yours.
•Engagement - RankBrain, is Google’s AI algorithm. It tries to determine a query’s real intent by using past searches to determine the most relevant results for the keywords entered. When released in 2015, it became the 3rd most important ranking factor after backlinks and DA.
The search engines can’t tell how you engage with a target page once you leave their results. But they do attempt to measure engagement through the SERPs. Here are some things they consider:
Dwell time: How long does a user stay on a page before returning to click on another result. The longer the dwell time, the more likely it is that the page is authoritative.
Long clicks - A user goes to a page and does not return. This is a good result.
Pogo-sticking - A user starts on the first result and goes down the list of results but does not spend much time on each. Google looks at this as a poor set of SERPs and tries to adjust accordingly in the future.
•Page load speed, including mobile - No matter how good your content, it will have a hard time ranking if the page loads slowly. Google recommends an ideal of .5 seconds, but not more than 2 seconds. There are free services online that will test your page speed.
•Site security: https - Check that your domain has upgraded to HTTPS. SERPs rank secure pages over unsecured ones.
•Keyword matching - This is obvious. Search engines try to match results with a users' intent via RankBrain.
•On-page SEO: Google must understand your keywords and content to match your page with the user’s intent. For a deep dive, search for ‘on-page SEO tips’ or something similar.
Keyword tools like Ahrefs are great at cleaning up on-page errors.
•Schema mark-up: This is meta-data you can append to your website to help search engines better understand how to classify your page. For more details, here is a good primer: Schema Markup 101: How to Create Rich Search Results and Boost SEO
Get Started With Content Marketing: The Four StepsStep 1 - Keyword Research
Buyer Intent Keywords
Where do I get my content marketing ideas? Start with keywords.
If you take away one idea from this guide, it’s this: Keywords drive content ideas, not the other way around.
You know your industry. You probably have some great ideas to share with your audience. Writing random thoughts as an expert is valuable to those already on your site but not strategic enough to get ranked and found.
Start with your competitor’s keywords and ideas and then research industry intent keywords to get a definitive list of the topics buyers are actually researching. Convert these keywords to content ideas.
The parallel strategy is to find top keywords but also less competitive keywords that drive traffic but will be easier to rank for.
Note: Before you start, create a master spreadsheet to track your keyword and content discoveries with these headers:
Discovery date
Keyword
Traffic
Search Difficulty (SD)
Paid Difficulty (PD)
As you come across good intent keywords, enter your findings in real-time as you do your research, so you don't have to go back and recreate everything.
Use a keyword Research Tool
Start with a keyword tracking tool like SEMrush, Ahrefs, or Moz. There’s a monthly subscription for each, but it’s worth it. We use Ahrefs, so we’ll show you examples from their tool. The concepts are the same for all keyword research tools.
Take some time to watch YouTube tutorials on the tool you select and familiarize yourself with the key processes and features.
The tools offer a great deal more than we cover in this beginner's primer. Over time, as you become an expert, you can get creative with keyword research.
Start With Competitor Keywords
A good place to start is by seeing where your competitors are having success with traffic and rankings.
Look at top pages and the keywords driving traffic to those pages
Look at keywords driving traffic to their overall site
Let’s pretend you offer a solution for sales and customer service communications for websites. You know your primary competitors.
You begin by entering their blog site (blog.domain.com or domain.com/blog) in the site analysis portion of your tool. You could also just enter the top-level domain (domain.com) and see what non-product pages appear at the top. Or you can try both approaches.
Three things to look for when analyzing your competitors' informational content pages (as opposed to product pages):
Traffic
RDs (referring domains)
Keyword difficulty (KD)
KD as Ahrefs defines it:
“An estimation of how hard it would be to rank on the 1st page of Google (aka the Top 10 search results) for a given keyword. KD is measured on a scale from 0 to 100, with the latter being the hardest to rank for.”
For example, here, let’s pretend your competitor is intercom.io.
These results below are the top content pages driving traffic to intercom.io’s site, with keywords that have a KD under 51 (In the orange box, you’ll see I applied a KD filter in Ahrefs to the results: ‘KD: Min-51’).
You'll notice the top pages are product pages.
You want to look for content pages that are getting good traffic. In this example, the top content page is outlined in red.

Keywords Driving Traffic
For the pages that have potential, look at the keywords driving traffic to that page.
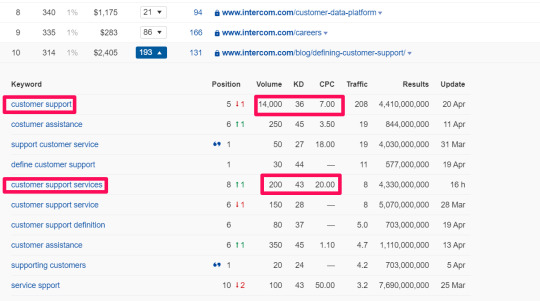
Keyword Intent
Not all keywords with low KD are equal. As you look at the keywords, you need to decide if they are terms a buyer in your industry would use to research a purchase (the intent).
Customer support definition' is probably not a good intent keyword for a buyer. 'Customer support' is a good intent keyword and has a high volume low KD. As does 'customer support services'.
When selecting keywords to rank for, always be in your buyers’ minds to predict what keywords they might use to find vendors.
Look at keywords driving traffic to their overall site
Now that you’ve narrowed down some good topics and keywords to outrank your competitors, it’s time to look at keywords that drive traffic to the site in general.
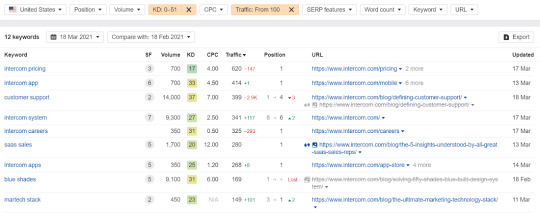
This report would indicate that good topics showing success for your competitor but with low KD are ‘customer support, ‘saas sales’, and ‘martech stack’.
The keyword ‘customer support has a traffic potential of 399, and Intercom ranks at number 4, but with a search difficulty of only 37.
This would be a great keyword to pursue with some high-quality posts around onsite customer support.
If you drill down on ‘customer support’ you can get some related keywords using Ahrefs ‘Also Rank For’ report:
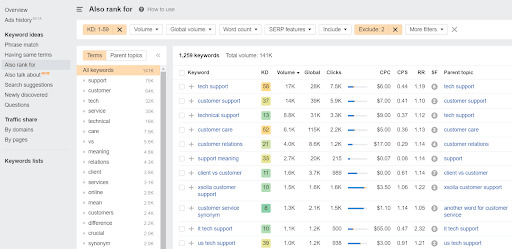
This shows some other keywords with low KD to include are ‘tech support’ with a potential of 7,500 clicks or ‘customer care’ with 2,200 clicks.
There are potentially hundreds or thousands of keywords worth noting in your spreadsheet. Include them all.
In the next section, we’ll show you how to organize your keywords around a main topic or pillar page.
Don’t stop at one competitor. Enter as many competitors as is relevant. You might start to see some trends in your industry on good keywords and topics that generate traffic and have low KD.
Analyze Keywords Across Your Industry
You are likely an expert in your industry, and you probably know some of the primary intent keywords buyers will use to start searching for solutions.
Doing the competitive analysis uncovers many of the keywords you’ll need.
It’s worth going through this next step of looking at all keywords to generate a thorough list.
Start with a known popular keyword in your research tool and see what suggestions come up.
Note the ones that show promise for traffic and KD, then dedupe them against the competitive keywords you already have.
A good intent keyword for our sales and customer service software would be ‘customer service software’ and a few variations.
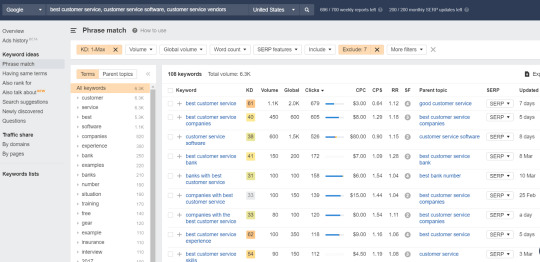
Download the list and go through it in the spreadsheet. Keep cutting, pasting and deduping a master sheet. Delete the rows that don’t make for good intent keywords. Repeat for as many intent keywords you can find.
Notice for ‘customer service software’ the KD is only 38, but a Google Ads client will pay $80 for a single click!
The volume may not be high, but the high CPC tells you it probably converts well for the targeted buyers.
Write some great, authoritative content around that topic, and get that same click virtually free in organic search results.
Step 2: Organizing Keywords and Topics - The Pillar PagePillar Page
If you’ve been producing content but are frustrated that you’re not ranking, it’s likely the problem is not the content but how it’s organized on your site.
Adding more content to already underperforming content will confuse Google more and result in more expense and no results.
To organize content, you need to help Google understand what questions you are answering and how each page for that topic adds to the answers.
A pillar page strategy, also called a power topic, cornerstone, or tent-pole is the best approach. In the simplest form, it’s a page on your website:
Around one broad keyword - But not too broad - ‘customer service’ is too broad.‘Customer service software’ has good traffic potential but is more specific.
Covering the content in-depth, in long-format (5,000 words+)
Answers all the questions a buyer might have around the topic
Search engines view will as authoritative and engaging
Is your best, A+ effort on that topic
Cluster Topics
A pillar is defined as:
“a person or thing regarded as reliably providing essential support for something.”
What the pillar page supports are called the cluster topics. They link from the pillar page and help google understand your content.
Think of a pillar page as a tree trunk and the cluster content as the branches and leaves.
Hubspot created the concept of pillar pages. They conducted experiments and rearranged how they link content pages within their site.
They came up with an approach that gave search engines a clearer view of the relationships between related pages. In turn, this gave search engines a better idea of how to relate and rank the content. Rankings increased across the site.
The pillar content is a detailed analysis of the main topic. The cluster content is the ‘smaller’ related blogs that link out from the pillar page.
Here is how their site looked before pillar pages:

Source: Hubspot
When they reorganized content around the pillar strategy, here is what their posts looked like:
Source: Hubspot
You’ve created a list of 100s or 1000s of keywords, and you’re starting to see some trends around good potential topics. Zero in on precisely what you want those topics to be, and organize them into broader themes.
Look at related clustered topics and roll those up into one main topic. Since you know your industry well, the main topic will probably be easy to spot.
That one main topic is your pillar page.
The cluster topics are around keywords that support the main topic and have good traffic, low KD and/or lower RDs.
Customer Service’might be too broad, but ‘customer service software’ is a main intent keyword that’s not too broad. Remember it also has a KD of 37, but a Google Ads advertiser would pay $80 for one click on that keyword, which shows exceptionally high purchase intent.
Cluster blog topics might be around ‘customer service chat software’, ‘customer service for small business’, ‘best online customer service’, and so on.
Since pillar pages are long-form content, make sure you follow a few guidelines to make it easy to read and to scan:
Don’t use long blocks of dense text.
Break paragraphs into the smallest possible units you can
Try to break up your sections with different font colors for headlines and text for readability
Summarize where you can
Make liberal use of pictures, charts, and graphs.
Use call-out boxes to convey main points in each section
Create a table of contents with anchor links to chapters
Other Sources to Create Cluster Content
There are several other approaches to discover cluster topics. This is where it gets exciting and where all your research gets put to use.
Google Suggestions
Generate top search terms based on popularity and similarity. Type your pillar keyword at google.com and see what they suggest:

Related Searches
Click on each suggestion, and then scroll to the bottom of the results page to see related searches:

Google is handing you other intent-rich keywords buyers are using for research.
Look them up in your keyword research tool and find the ones that meet the criteria.
Use them as topics for future posts or to include on-page to enhance posts with long-tail keywords.
Keyword Questions/Longer Terms
People ask more questions, use voice search (one-fifth of Google searches now), and input longer search terms than ever before.
By ranking for keyword questions, or longer terms, you can expand the audience beyond keywords.
Most keyword tools have a feature in their keyword listings to see the keyword’s top-related questions.
Here is the feature in Ahrefs for customer service:
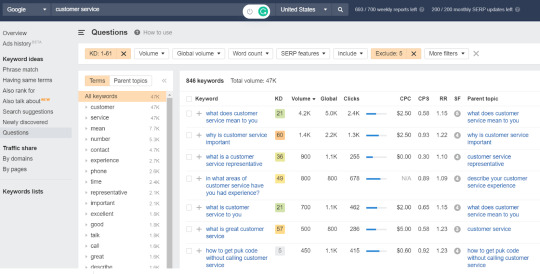
There are some great question keywords here with substantial traffic and low KD that would make for good cluster content and keywords to add to cluster posts.
Forums/Community Sites
Your topic will have communities and forums where cutting-edge discussions are taking place. These forums are a great resource to find content ideas. Quora covers a vast breadth of topics by answering questions users have. For ‘customer service’, you could start here:
‘Customer Service Skills’ looks interesting. Plug it into your keyword tool. You’ll see there are some good ‘long tail’ keywords with low KD that would make great topics like ‘customer service manager skills’ potential traffic of 170 clicks per month if you can rank in the top 10.
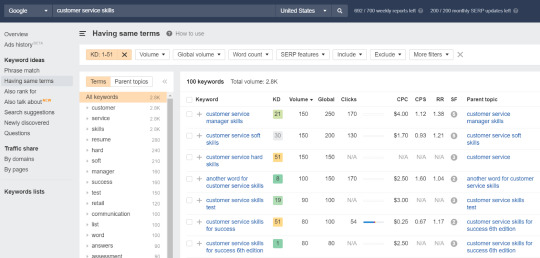
Editorial Calendar
Once you have your pillar topic and your long tail keywords, it's time to translate those into the actual topics you will write about.
An editorial calendar defines what to publish and when for cluster posts in a realistic cadence, given your resources.
Without a written calendar, the probability that your effort will fall apart increases. An editorial calendar is a high-level, strategic roadmap, but it’s also a way to hold your team (or yourself) accountable for producing.
‘Realistic’ means that a post slotted in the calendar will receive ample attention and research so that it’s well written, valuable, and authoritative.
This prevents the single biggest obstacle to content marketing success: publishing average content just to hit a quota. Or worse, stopping publishing at all.
The entire process builds around quality, not quantity. There are levels of complexity for building your calendar.
Simple Editorial Calendar
Create a Google Sheet (or Excel Online) with at least the following. You can add more columns to suit your needs:
Proposed Title
Writer
Co-writer
Posting date
Final draft review date
Pillar topic
Main keywords
Research 1 - Research topic needed to support article
Research 2 - Research topic needed to support article
Research 3 - Research topic needed to support article
Next steps
Obstacles
Notes
Advanced Editorial Calendar
Set up a web-based project management account on a service like Trello, Asana, or Airtable.
Airtable has a free version and a premade editorial calendar template you can use. Sign up for Airtable, go to ‘Templates’, and search on ‘editorial calendar’. Here is a snippet of what it looks like:
Editorial Collaboration
If you have a team inside and/or outside the company collaborating on content creation, you should create a group discussion room in Slack or Microsoft Teams.
Here you can ask more detailed questions and give real-time feedback on issues that come up when creating content.
Blogging Frequency
There is a vast amount of information on blogging frequency and what times to post. You can search and study some of it, but realistically, you don’t need to produce a high volume of content to get traffic and conversions in B2B.
This guide focuses on getting found in search to convert readers to buyers of your complex product or service. The rule of thumb for B2B content is always quality over quantity.
Always strive to use keywords your buyers are using and write content that answers their questions when using search.
To Start
1-2 posts per week, along with
1 high-quality longer-form piece of pillar content (like a guide or white paper) per quarter
6 Months
2-5 posts per week
One longer form piece per month
1 Year Plus
Start doing experiments in blogging frequency. Look at your metrics, the most important being conversions, and see if blogging output increases positively or negatively impact your metrics.
Step 3 - Content Promotion and Content Syndication
Getting ranked and found in search is an important first step for content marketing.
However, if you are new to getting your keywords ranked, and your DA is low, it can take some time (3-6 months) to start seeing results.
Content syndication especially paid syndication, is a great way to get your content seen right away.
The goal is to find places off your site where your buyers visit and get your content placed there.
Content marketing channels for syndication include other blogs and websites, social channels, email newsletters, and paid promotion.
Content syndication is the practice of placing your existing content on another site to expand your audience and build credibility.
Content syndication vs. Guest Blogging vs. Repurposing
Content syndication is when you take a copy of your existing content like a guide or blog post and get it published on another site virtually word-for-word.
Guest posting is writing a new, original piece of content for another site.
Repurposing is taking your existing content and breaking it into derivative pieces to publish as new newsletters, social posts, videos, blog posts, etc.
It is possible to use a combination of the above. For example, you can repurpose a subtopic of a comprehensive guide as the basis for a guest blog post.
First, let’s look at the potential pitfalls of syndication and how to overcome them.
Duplicate Content
You are giving a copy of your content to another site. The search engines don’t like duplicate content because they don’t know which site is the original or authoritative version.
In this circumstance, Google will decide on its own which version is the authoritative one. If they pick your syndication partner, you lose that SEO credit for your original work.
What To Do - The Canonical Tag
You won’t get penalized by Google for having duplicate content. Google realizes that duplicate content is necessary (for example, a page with both a mobile and a desktop version). However, you want to get recognized for being the original or ‘canonical’ author of the piece.
Fortunately, there is a technical fix. Google and the other major search engines created a canonical tag to tell them exactly which version is authoritative.
You add the tag to the header of any page where your content appears called the canonical URL. It looks like this: rel=cononical.
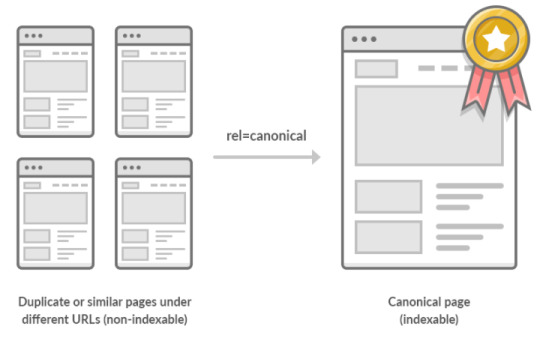
Source: Ahrefs
The ideal situation is to get every site where you syndicate to add a rel=canonical tag and the link to your original page in the header of the page where the syndication site hosts your duplicate content.
Here is a sample of how it looks and how you would ask a syndication partner to tag the page within the <head> section.
Let’s assume your original post is at https://example.com/customer-service-software. The header string on the syndication page that you would ask them to add looks like this: <link rel="canonical" href="https://example.com/digital-marketing/email-marketing/">
This tells the search engines, ‘don’t look on this page for the original copy, look other there’ (which is your url on your domain).
If a syndication partner refuses to place the tag, it’s up to you to decide if it’s worth it or not to share your content and risk having their page become the authoritative one. This is especially risky if the page has a high domain authority.
Can’t Use Conversion Tools
Virtually no sites will allow you to place the widgets you use to convert readers into leads. This might be a non-starter for some companies that rely on their content to drive most of their leads. It might still be worth it for the following two reasons.
Exposure/Branding/Credibility:- If you start to gain a solid reputation and get some big sites to publish your content, you gain exposure to 1000s of new eyeballs without doing more work. That’s great for branding and future guest blogging.
Backlinks:- It’s possible to get a site to link back to your site when giving credit for the blog post, like this:

Promotion: Start With Guest Blogging
If you already have high credibility within your industry but are new to blogging, you can start with outreach to your network to see if you can get them to republish your posts.
If this is not realistic, start with guest blogging and build a reputation.
You might know some top blogs in your industry that address the topics you want to cover. Begin by noting those sites in a spreadsheet. Assume your content is around customer service software. To build out your list of syndication partners, start with a search like this:
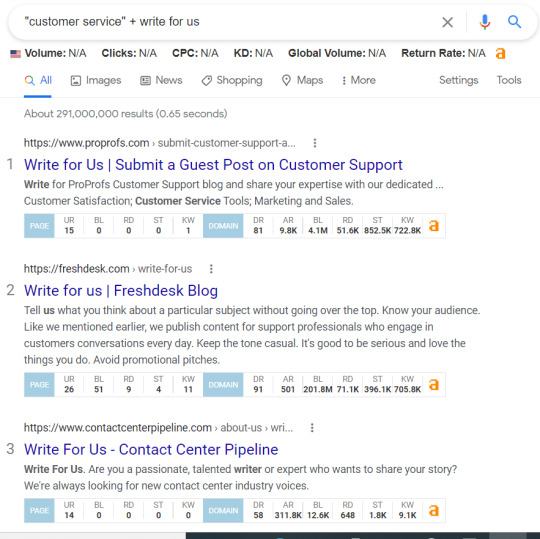
There are dozens of pages of similar results. Start noting the ones that resonate with you. Go to your keyword research tool and note their domain authority, traffic, and keywords driving that traffic. Find the contact information for the ‘Write For Us’ section.
You might notice these results are appended with a plug-in from Ahrefs that shows domain authority and traffic for each potential partner so you don’t have to look it up. The browser plugin for your keyword research tool is a great way to filter potential sites right in your listings.
Focus on reaching out to sites with more authority than you and a minimum DA of 50.
Your pitch should be short and mention content wins and expertise you have. If you’re getting started and don’t have any wins yet, be upfront about that.
Focus on 1 or 2 high-quality posts you’ve done. Tell them specifically why you like their site.
You can see this is not a short-term method for success. It takes time and effort to make guest blogging work.
The important thing is to build your authority and get some traffic back to your site, where you can use your conversion tools.
And understand that your content is working for you in parallel by being crawled and ranked by the search engines.
Free Content Syndication
After you have some guest blogging wins, it’s time to start syndicating your content. Syndication is about getting your ideas and brand out to a broader audience. You also get some of that traffic back to your site and drop it into your conversion paths.
You’ll also get the links you have within your content that point back to your site onto a higher authority site. Search rankings, organic traffic, and conversions will all improve with syndication.
Always try to syndicate your content to a larger or similar-sized site based on DA. Of course, this may be easy to do if you are just starting because your domain authority will always be lower.
Looking For Sites to Syndicate
As with guest blogging, you can start with Google to find sites in your niche that syndicate content.
Start with the phrases:
"originally published in"
"republished with permission"
"originally appeared on"
And then use the Google search parameter INURL:{your topic} to find pages that have your keyword in the url. For example:
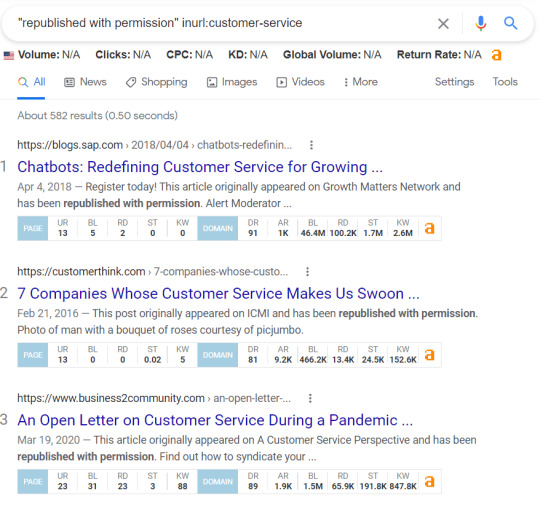
Start clicking through to the articles. You’ll typically find a link that invites you to submit posts for syndication:
Enter the domains into your research tool and note the site’s DA, traffic, and keywords. Note the ones with good potential that target your buyers, and have good DA above 50.
Follow the individual syndication guidelines for each site and start submitting your relevant content.
Free Platforms
For each post you can place your content on platforms that accept all content, such as social media, forums, question sites, & newsletters.
Do your research and find out all the places where your buyers hang out and do research.
Break it down by category.
Social media: Platforms and groups such as Facebook or LinkedIn groups or Twitter Lists
Forums/Group Sites: Reddit, Stack Overflow, Slack, and Hacker News
Question sites: Quora, QApop
Newsletter discovery: Substack
How you build credibility in each community is unique. You can’t just take a page link and a blurb and post it everywhere. You’ll be ignored, or worse, accused of being a spammer and banned.
Study each place where you want to share. See how users with high likes or shares present their content. Does long-form work? Short-form? Commentary & analysis? A linked headline and blurb?
Once you create value with your communications, you can start capturing that attention. Focus on one action for one platform. If you’re on Twitter, ask for shares on Twitter. If you’re on Reddit, ask for likes and upvotes there.
Start by being a good community member. Comment, share others’ content. Try to make genuine connections.
Here is a question on Quora group around customer experience with over 2,500 members. There are only 2 answers so far.
These are the types of opportunities you should look for to add your insight and refer back to your blog:
You also need to learn how and where you can place links back to your content pages. For example, on Quora, you can add relevant links in your answers using anchor text and a link. You can also add a link back to your blog section in your Credentials & Highlights page.
If you think this takes time, it does. Harry Dry from marketingexamples.com is great at amplifying his content. He generated 19,000 email list members in one year. He spends 8 hours per week posting and responding on platforms.
Paid Syndication
If you have the budget, this is the best way to keep your content-driven leads flowing without waiting to get ranked.
This version of your content will probably fall under what is called ‘gated content’. The goal of paid content syndication is to pay for the ‘conversion’, which is the data you want to collect for sales follow-up such as name, email address, etc. That data collection form is called the gate.
Publishers
For years, the major B2B publishers have accepted white papers, ebooks, webinars, and other long-form content to promote to their targeted audience under different cost models. There is a B2B publication for just about any industry.
If you don’t know the major publishers in your space, google your industry and add ‘magazine’ like this (we tried ‘customer experience’ as the broader topic as the basis for an industry publication):
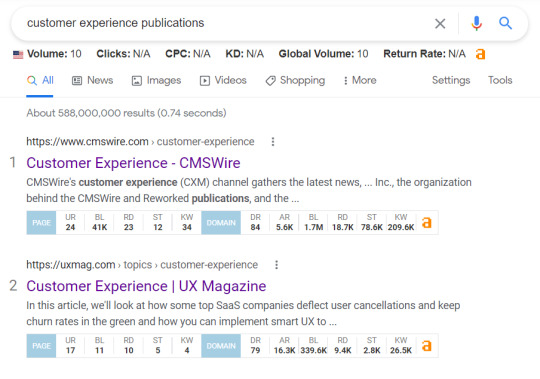
Notice the first one has over 18K RDs and a DA of 84.
Click through and scroll down to the bottom of their site and look for ‘advertising opportunities’. Reach out to the publication and get their media kit. See what types of opportunities there are to get your content in front of their audience.
Syndication Costs Models
Cost Per Thousand views (CPM) - You pay for every 1000 views to your content offer. This offer is typically in a banner ad or in a white paper resource section of the publisher’s website. There is no guarantee that you’ll generate a single conversion, but you do get branding exposure and you might get some clicks.
Cost Per Action (CPA) or Cost Per Click (CPC) - You pay for every click to your site’s offer page. Again, no guarantee of conversions, but you get traffic to one of your conversion pages, which is your goal.
Cost Per Lead (CPL) - This model is the most expensive, but it guarantees the number of leads you generate. Under CPL, you pay for each completed registration form called a marketing qualified lead (MQL). Often, publishers will tap into their valuable direct, opt-in email lists to generate your MQLs.
The cost per lead under this program ranges from $30-$100 per lead depending on how targeted you want your campaign. You also need to commit to a minimum number of MQLs, such as 100 or 250.
Automated Services
You have probably seen the headlines and images that appear at the bottom of major websites like CNN or The Wall Street Journal. These are paid syndication offers from companies like Outbrain and Taboola.
These platforms work much like Google paid ads. You set up a daily budget, upload your creative and conversion pages and specify your target audience. The services will then display your ad where their algorithm thinks it has the best chance to convert.
You get the conversions, but not the SEO value of having a link on a site like CNN. The search engines view these as paid ads and ignore them.
Step 4: Conversions, Measurement & Analysis
The purpose of all the strategies and tactics covered in this guide is to attract readers who convert to prospects and become customers.
Conversions are the most important thing you want to measure.
Other ‘vanity’ metrics besides conversions are important such as page visits, source of visit, and time spent on-page. Many marketers look at these stats to judge whether a post is successful or not.
Conversions are a function of 2 things:
The content
The conversion offer itself
Your content comprises page design, keywords, topics, authority, and the keyword rankings that draw a visitor to a page on your site.
Once on the page, it’s the conversion offer that convinces them to raise their hand and give up some information about themselves. The offer is a mini piece of content marketing itself. Like the page visit, offers need to be measured.
Here are three types of conversion offers, in increasing degree of quality:
Newsletter sign-up - You’re capturing a name and email address. What you’re not capturing is necessarily permission to follow up and discuss a business relationship. It’s good to have a newsletter sign-up available on your page as a soft offer for those not ready to commit to a discussion.
Download an exclusive piece of content - This is a more targeted conversion. It’s sometimes called a ‘lead magnet’ because it uses free content to generate interest and the magnet to convert.
The offer is usually for a longer form, more valuable piece of content with a registration gate or landing page.
This content should align with your company’s product offerings. It’s a way to get a prospect to raise their hand to express general interest in your value proposition. Have an ‘optin’ box on the conversion page that opens permission for a business discussion.
Free assessment or consultation - As it sounds, the reader is expressing an interest to have you engage with them on improving a business process that your product or service can fix.
This is the ultimate conversion.
Don’t use this type of offer to ‘trick’ a prospective customer into a regular sales call by calling it a ‘consultation’.
Hubspot uses a website grader as a highly effective conversion tool. You can offer calculators, templates, custom reports/plans, or free assessment tools as offers.
Test different offers on the same page and run A/B experiments on copy and creative to constantly beat your best-performing offer.
Harry Dry stresses the importance of framing the offer, not in terms of what you can do, but what you can do for them.
Go to his site and spend some time there. It’s well worth it.
Here are some of his examples that will inspire you in the right direction:


Notice this one uses a ‘free seo audit’ as an assessment offer.
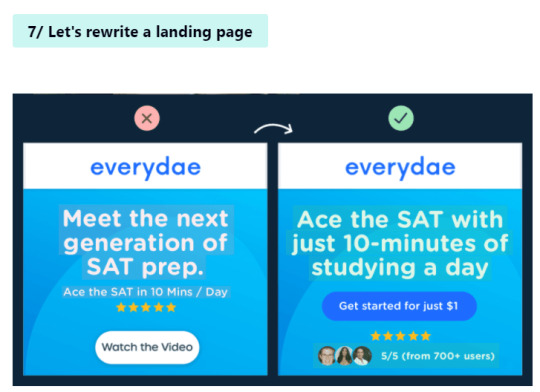
Students don’t care about the next generation of SAT prep, they care about acing the test.
Always be thinking about your customers, not you, when writing copy.
Measure and Analyze
Just as you need a keyword tool to find competitive keywords, you need a measurement tool to analyze your performance. Google Analytics (GA) is the most widely used tool. Other popular options are Hubspot’s analytics features and Heap.io.
You can set up all of these reports in GA. You can also create a custom dashboard to track everything on one page.
If you can’t set up the reports yourself, it’s worth finding a freelancer or hiring a content marketing expert who can do it for you.
Set Goals and KPIs
For each goal measured, set up a KPI for benchmarking. Even if you have to make broad assumptions, start somewhere. You can adjust KPIs later.
For example, goals might be to increase keyword rankings, traffic, and conversions. To assign KPIs, put a ‘stake in the ground’:
10 keywords per month ranking in the top 20
Total organic traffic to blog pages of 20,000 in 6 months
A conversion rate of 10% of organic traffic starting in month two.
Traffic:- The broadest measurement of effectiveness. Without traffic, there are no conversions, so monitor traffic growth rates in total, by pages, and by keywords.
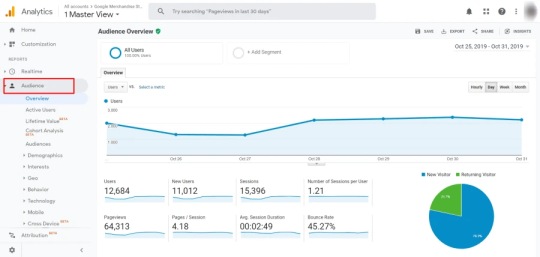
Source SEMrush
Traffic reports contain some other valuable data
New vs. Returning visitors - A healthy number of new visitors is important for growth. New traffic above 30% is a good starting point. Above 50% would be excellent.
Bounce rate - A good indicator of engagement which is important in keyword rankings. In the above report, 45.27% is good and would suggest the content is resonating with the intended audience.
Session duration - If you’re writing authoritative content, your average session duration should be in minutes.
Traffic by Pages Indicates which posts/topics are doing better than others. Also used to plan the repurposing of content and help messaging with other marketing programs.
Organic Traffic by Keywords Shows the top terms driving organic traffic. Extremely valuable to understand how you’re being found, and what to focus on when creating and repurposing content.
Valuable insights such as keyword position, clicks, and clickthrough rate (impressions in SERPs to click ratio) are available.
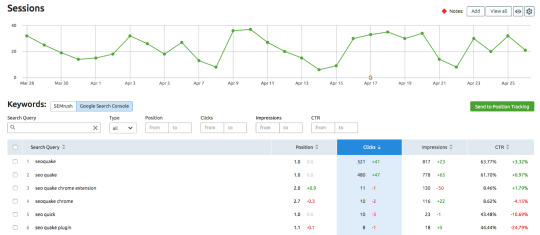
Leads to Organic Traffic A high level view of how your program is doing. Divide your total conversions by the total volume of organic traffic to your content pages.
Conversions by Page Which pages are generating quality leads. Which topics are driving conversions? This is insightful for understanding what is resonating with your buyers and to repurpose content to other channels like social media, email, and video.
Conversions to MQLs Are the conversions working as a good starting point for sales development reps (SDRs). If you’re getting 50 leads per day, but none matches your ideal customer profile (ICP), you need to analyze why.
Keyword Ranking Stats
These are metrics you want to measure using your keyword tracking tool against your domain. Set a baseline at the time you launch your pillar page and cluster pages. These reports will show:
Keywords
Ranking Position
Volume
URL where they are found
Review the report weekly and watch for movement.
For your top ranking keywords, discover the CPC and build a report for management to show where you are ranking for keywords where competitors are paying for clicks.
Backlinks Track how many total backlinks and unique referring domains (RDs) each post is generating. Always be working in parallel to build backlinks.
Domain Authority You should see your DA rise over time if you are publishing quality content with good engagement and backlinks.
Social shares
B2B content is not as widely shared as consumer content, so the numbers are always lower. But there is still insight in social shares.
Attribution Tracking
Content marketing does not drop a straight path from reading a blog post to closing a sale. Many other pieces of content are consumed in the buying journey and by multiple people on the buying teams.
Consensus research is that at least five content touchpoints are needed before a buyer contacts sales.
The KPIs above are ideal for single transaction visitors. These are visitors who come to your site from a search engine and then convert.
What about visitors who visited your website to read a blog post, then leave. But 2 weeks later they come back to view a webinar.
Set up attribution tracking to see where buyers are stopping to engage, and what touchpoints are converting to leads.
MQLs by program - Set up attribution codes in your content marketing URLs for all your channels and track conversions by guest posts, free syndication, paid syndication, and from your domain pages.
See where you are getting high performers and increase resources there.
Attribution tracking is complex. There is software available to add to your tech stack to help, such as LeadsRX and Attribution. Hubspot also has attribution tracking on its CRM platform.
Generating Backlinks
Generating backlinks is a critical, ongoing tactic to help increase your rankings.
If your domain authority is low, you need to actively reach out for backlinks with outbound email campaigns until your DA rises.
First, if you write excellent, useful content that answers a search query, you will get some natural backlinks.
Second, you can run campaigns to ask for backlinks from other sites with higher DA. The second strategy is complex, time-consuming, and beyond the scope of this guide. Search for ‘How to generate backlinks’ and read the posts.
Once you have a system in place, you’ll realize generating backlinks can be boring and repetitive. You can outsource your system to a content marketing agency, or freelancer on Upwork, or Fiverr.
Conclusion Always
Look at what types of content are producing leads and which are just producing traffic with low conversions.
Do experiments and make adjustments to the resources you put into well-performing keywords and topics.
Every year, look at your assumptions and always test and measure the interactions between content frequency, type, quality, and conversions.
Putting it All Together
Look at the keywords you’ve included to define your main topic and make sure relevant ones are on the pillar page.
Don’t worry about using the keywords not enough or too often. Use them where they can naturally appear.
Write naturally but try to include many long-tail keywords that support your post. You don’t need to pack your post will all the keywords in your spreadsheet.
Answer the key questions around the topic and create valuable and authoritative content. Don’t worry about keyword frequency.
Learn on-page SEO and stick to the tactics recommended.
If starting from scratch, juice your pillar with some pre-written cluster blog posts you can link to from the pillar page. 2 or 3 will do to start.
Stick to your editorial calendar for subsequent posts. As you write the cluster content, find places on your pillar page to link to the cluster content.
Your keyword tool will show your current keyword rankings. Create a baseline for your keyword rankings and domain authority.
There’s no need to check for movement every day. Weekly is probably best for practical and sanity reasons.
Summary:
Research competitor keywords
Research top competitor pages and topics
Organize keywords around pillar and cluster topics
Look for keywords that have good volume and low search difficulty
Create an editorial calendar
Create a pillar page in the form of an authoritative guide or eBook
Write cluster content that links back to the pillar page
Look for guest blogging and syndication opportunities with industry influencers. To find influencers, use SparkPost.
Use paid channels while you're building your organic channels
Repurpose your content. Content ideas:
Blogs
Podcasts
Videos
Webinars
Infographics
Social posts
FAQs
Newsletters
Industry interviews
Measure the sources of your traffic and find keywords and topics that lead to conversions.
Put attribution tracking in place to find out where buyers are converting.
0 notes
Text
July 3rd tweets...
July 3rd tweets...
There is a Biblical saying that says “A prophet is never accepted in his own home town…” - what this means for everyday people like ourselves is that sometimes those close to us don’t recognize our value. It could be from seeing us everyday, knowing our past and viewing us through that mental filter, or something of that nature. It could be why Jesus didn’t work or practice His ministry in His hometown, where He grew up. In His hometown, Jesus would be seen as Mary and Joseph’s son, or if Joseph was a carpenter: Jesus (or “ Yeshua Bar Joseph” <-I believe His Jewish name, or I think Joshua) would also be referred to as the carpenter’s Son. Jesus moved from where people knew Him and started fresh and established Himself as a Holy Individual. Now back to me. When I give my parents advice, they never listen. If you ask them one of Renny’s ideas or advice, they can’t remember even one thing-they don’t pay attention to me. They need someone else, literally anyone else, other than their children to push them in one direction or the other- the sad thing is, the other people may say exactly what I would’ve said. Please don’t be like my parents. Listen to those in your life, value what they say. It’s one of the reasons I need to make sure my life partner is someone I can regularly talk to. I mean I may sound nice to you, but when I buy something for my goals or go to a different Church, my parents get critical. They Can’t understand my reasons even with me being in the most bizarre and time consuming or “situations/phenomena.” I’ll go out of my way to explain myself, but there is some demonic mental block in their heads where they don’t listen. Never. It’s like an extraordinary disease, because I end up saying the same thing to them over and over. And truthfully, at my age, after all these years, I don’t care to, nor have the patience to, explain myself to anyone about anything. It’s ur bizarre disease to read into every detail of a strangers life, not mine. But my father…he lacks the common sense to pray for my happiness and goes so far as to pray aloud that “the demons making me misbehave in his perception or do what he doesn’t approve, be gone.” He prays that I find someone from his culture and birthplace to take as my wife. Insult to injury, he says this out loud daily, never considering what I want. I mean you want to say get a hobby (literally) rather than obsessing on some idealistic future from 30 years ago and from another country. I see him as the ultimate con man in terms of being manipulative with me. He makes retarded smart a*s moves to make me hear certain things, thinking it will get me to act in a particular way. He plays on emotion. These actions are so primitive and childish, it’s enraging. He’s from a village, but even then, I find myself wondering, how the h*ll does this man see me? A father and son dream in this country of being friends and like brothers. Not my dad. Never sees me as an equal. May mindlessly say in passing, sure we’re equal. But it’s without thinking through what it truly means. If I were him, I’d take time to talk to my son and value every word. But my dad is from another time and place: he thinks since I’m fed and housed, then his Christian obligation is fulfilled. My body may be taken care of, but what do you do to nurture my mind? Anything? How do you “convert” or change such time practiced learned behavior? It’s not stubbornness of heart, but like his genetic programming is incapable of being reprogrammed: or in other words, he doesn’t have an open mind. I think I can learn new things, accept differences where I see them, and change accordingly. But not my mom or dad- plain old school types. Think their ideal Christians based on how they grew up, not realizing the lack of heart in their actions, or my ability to teach better. Living with them at this age to avoid rent payments and to use the ton of space available at my house, takes a toll on the mind. Simply because of the nonsense I face. I mean I want my mom and dad to listen to what I have to share. If and when they read this, they’ll miss that point and be busy taking all of this as an insult, as random as that may be amidst all their random yelling and criticism. Never had parents I could talk to, and for the past 11+ years, people keep a distance from me as part of the “situation” or “phenomena.” Parents: listen to your kids. Do what my parents never did, and believe in your kids, when they struggle to believe in themselves. They’ll remember and appreciate it for a lifetime. I wish I had a dad I could get a beer with, when I’m taking a break from fitness goals, as beer affects such goals negatively. I wish my mom and dad supported my endeavors, however crazy in appearance or stereotype, rather than judging me. Food? a maid can cook. No ones going to remember that after someone passes on, if they have recipes. Cleaning can be done by house services. Money can come from a job. My parents don’t listen and just compound my own fears. Some families leave their kids with the house they grew up in. When I spent Christmas Eve with my friend Nicole and her family while lying to my parents, she shared that her parents gave their house to the kids AND THEIR GIRL FRIENDS, WHILE THEY MOVED TO APARTMENTS IN THEIR OLD AGE. My parents? For one reason or another, maybe to make me like a stereotypical American, want to sell our house, not help me with job hunting, and leave me in debt. I believe they have a hand in the situation they partake in, in terms of getting me involved. Who begs for their sons hate like this? Are they so guilt ridden that they just want to give me h*ll for some self consoling hatred towards them?! I lose patience with the simple mindedness and stupidity of people. Innocence can be beautiful, but then not so much with stupidity. A parent shines in the way Martha Kent of Smallville is with Superman or Clark Kent: always there, always supportive, always listening. Parent, friend, sibling: that’s what you aim to be for those close to you. Be better. Words from a man in his very early thirties.
-But moving on to other things...
Yesterday I said that prayer can be a tool 4 mindfulness or 2 remind us of ourGoals & get us 2 focus &progress towards them. But it needs 2 be done daily, at least once inTheMorning &/or inThe Evening, right when U wake up, right b4 sleeping-those 2 instances, the mind is clear.-
- Today I introduce the concept of the "self fulfilling prophecy." You can see it as an exotic way of see positive thinking. With the self fulfilling prophecy, while believing what you say, you proclaim out loud: you succeeding in attaining something desired. -
-You can raise ur hands or keep them folded. Probably better to stand.-
- so lets say in the 11th grade, you want to get into a particular college. Say as often as you can "I will get into Harvard or Columbia or whatever." It helps tune your mind. It puts your desire at the forefront of your mind. Being alert to ur own proclamation, you will &should-
- be on the lookout to what will accomplish your goal. Believing and declaring your goal will help you get the grades you need in school and on the SAT's/ACT's. It gets you in the practice of accessing your divine potential in the same way the age old disciples -
- declared in doubt free belief that their followers would be healed of disease. But you need to believe everyday what you proclaim. The first time, maybe you won't get what you want. But with persistence, your mind will see you as relentless, and give into your belief. -
- sometimes, instead of getting what you aimed for, life will reward you with something better or more appropriate for your life. I knew someone that wanted to get into a particular fellowship program after their residency and medical school. This person got in elsewhere.-
- but as it turned out life "needed" his caring presence elsewhere. He managed to live in an area where he could get a fancy apartment and affordable furniture. He's living in style. -
- u need 2 orient ur actions towards what ur proclamation is. If u, as a parent, believe ur stuck in a situation where u have no choice but 2 betray ur child, & U hate urself 4 it, & believe ur son will hate u, "ur actions & tone of voice & content of words will reflect that."-
- that is the self fulfilling prophecy working negatively. If it can work negatively, make it work positively 4 u. Orient ur actions &speech towards ur goal or theFuture u want. Never let this world stand in ur way. U are not just this world, ur body, or mind, & its limitations.-
- you, a human being with an immortal insides or soul, are destined for greatness, to be a giant on this earth and maybe elsewhere. Never let anything keep you small or without a voice.-
- in life, when you try for something, you will get that or something better. Believe, live in the moment, make the best of what life gives u, orient ur actions/speech/thinking toward what you want and need, proclaim it - let the self fulfilling prophecy work for u positively.
0 notes
Text
8 Things YOU NEED TO KNOW Before Becoming a 코인카지노 Dealer #5571
Hand craftsmanship and high taxation made each deck of playing cards an investment. As such, cards became a feast for the eye. Ninety-nine: clubs, hearts, spades, diamonds (supposedly mnemonic as they have respectively 3, 2, 1, 0 lobes; see article for how this scoring is used) Various people have independently suggested expanding the French deck to five, six or even more suits where the additional suits have the same number and style of cards as the French suits, and have proposed rules for expanded versions of popular games such as rummy, hearts, bridge, and poker that could be played with such a deck. If two hands are of equal ranking, based on the foregoing combinations, or if they contain none of these combinations, the hand with the highest ranking card is considered the highest ranking hand; otherwise the hands are considered to be of equal ranking.
VLT programs are operated in eight Canadian provinces, with the only major exceptions being British Columbia and Ontario. https://en.wikipedia.org/wiki/?search=안전한놀이터 You have 42 points. If the dealer does not have a qualifying hand, the dealer will announce “no hand” and immediately pay all the ante wagers at the rate of 1 to 1 (even money).The dealer will then spread, count, and collect each player’s cards individually. $10 Place 6,8 bets 0.46% per roll, $4.69 per hour, $94 per trip
You really don’t want to lose money or miss out on a big win just because you don’t know all the rules of a game. The house edge is just under the cut per bet because the casino puts up the initial seed to start a new jackpot after somebody wins the previous one. At the Casino Niagara the house can expect to receive 18.84times as much money from the 29% cut as it pays to seed new jackpots. Confused? Every card games has its own terms only known to people around the table. Here are some of the most essential blackjack terms that you’ll hear. Columbia University's Rare Book and Manuscript Library holds the Albert Field Collection of Playing Cards, an archive of over 6,000 individual decks from over 50 countries and dating back to the 1550s.

The Dealer Must Qualify – The dealer must qualify with an ace-king or higher or the player automatically wins the Ante Bet. The lowest qualifying hand would be A-K-4-3-2, while the highest non-qualifying hand would be A-Q-J-10-9. If the dealer fails to qualify, the player would win the ante bet and the raise bet would be a push. But while Sklansky was busy terrorizing the poker tables in 1982, he found time to invent a completely new way of gambling on table games he dubbed “Casino Poker.” In Sklansky’s game, players placed an Ante bet before taking five cards at random. Guest, Charlotte. Playing Cards of Various Ages and Countries (Selected from the Collection of Lady Charlotte Schreiber). Vol. 1–3, London, J. Murray, 1892.interviewed 128 community leaders in seven new casino jurisdictions in the USA and found that 59% of the respondents favored casino establishments in their communities, 65% believed that casinos enhanced the quality of their lives, and 77% agreed that casinos led to positive effects on their communities' economy.
There are different number series in roulette that have special names attached to them. This full-pay version is found only in Nevada. It is also available with other pay schedules that have lesser theoretical returns: However, some jurisdictions require mechanical ball draws which may utilize a randomly shuffled deck of bingo calling cards, a mechanical ball blower that mixes ping pong balls with blown air or a cage which is turned to mix small wooden balls. All methods essentially generate a random string of numbers which players match to their bingo cards that have numbers on them. 메이저공원 Players may make a put bet on the Pass line and take odds immediately or increase odds behind if a player decides to add money to an already existing Pass line bet.
During the comeout, eleven is typically followed by "front line winner". After the point is established, "good field and come" is often added. All self assessed experienced gamblers lost and will lose their money. Because casinos are businesses and must make money to survive, the mathematical odds are always against players in casino games.The house advantage (or “edge”) is the difference between the true odds (or the mathematical odds) and what a casino pays.
And additional variation uses a single set of 6 cards, and regular dice. Movies like Rain Man and 21 make card counting seem like wizardry, but it's actually fairly simple arithmetic. Dealers will usually announce if bets are working unless otherwise called off. If a non-working point number placed, bought or laid becomes the new point as the result of a come-out, the bet is usually refunded, or can be moved to another number for free.At odds of 1 to 1, 2 to 1 and 3 to 1 respectively for each of these types of outcome, the expected loss as a percentage of the stake wagered is:
Some casinos offer 3–4–5 odds, referring to the maximum multiple of the line bet a player can place in odds for the points of 4 and 10, 5 and 9, and 6 and 8, respectively. SD (roulette, even-money bet) = 2b √npq, where b = flat bet per round, n = number of rounds, p = 18/38, and q = 20/38. Typically the maximum lay bet will be expressed such that a player may win up to an amount equal to the maximum odds multiple at the table.2–3 with 5-6: value 6 (16 pips; drop the 10)
0 notes
Text
Top 10 사설바둑이사이트 Tips You Need To Know To Beat The House #1701
However, even if players don’t have the prerequisite internet connection, they will still get the game in its full glory. This is because Evolution Gaming has made the game playable at even the lowest video quality. Players must bet against each other by covering or fading each other's bets for the game to be played. The ante wager may not exceed two dollars and fifty cents. Each player may place an additional, optional wager by placing a token in the designated coin-in slot in front of the player’s ante. To the average person, bingo-based slot machines are physically indistinguishable from an RNG based slot machine typically seen in Atlantic City or Las Vegas.
In the 1950s and 1960s The Sands Hotel in Las Vegas had a craps table that floated in the swimming pool, as a joke reference to the notoriety of the term. This self-exclusion program is geared towards those who are looking to have the right addiction to gambling. If a player's cards beat the dealer's cards, the player will receive even money (1-1) on the ante, and the following on their bet (with a maximum payout of $5,000 U.S. Dollars per hand on each bet wager): This reflects the fact that the player is churning the same money over and over again. A 23.6% hold, for example, would imply that, on average, the player bets the total he brought to the table five times, as 23.6% is approximately equal to 100% − (100% − 5.26%)5. For example, a player with $100 making $10 bets on red (which has a near 50/50 chance of winning) is highly unlikely to lose all his money after only 10 bets, and will most likely continue to bet until he has lost all of his money or decides to leave.
That being said, Caribbean Stud poker can be a lot of fun, especially if you’re playing with a group of friends, and you can potentially win a big jackpot, but you should know that the entertainment will cost you a fair bit. https://en.search.wordpress.com/?src=organic&q=온라인현금바둑이 one fascinating thing about blackjack is it has 52 cards in a deck, and surprisingly, there are 52 weeks in a year. Most games take just a few moments to learn, and they really are easy to play. Statistically speaking, being dealt a hand of 16 will more than likely end in defeat. Unfortunately, it’s also one of the most common hands.
Casinos may also offer other type of gaming, such as hosting poker games or tournaments, where players compete against each other. One Pair: Two cards of the same rank.High Card: Ace is best. In descending order, A-K-Q-J-10-9-8-7-6-5-4-3-2.Suits are irrelevant. In most varieties of the game, a player receiving two cards of the same rank may split them, receiving a second card for each, and play the two hands independently of each other. The Rouen Pattern originated in France in the 15th century. Although it never found its finest incarnation at the hands of English card masters, it nevertheless endured as the basis of the English pattern

One standard deck of 52-cards is used. The cards are usually shuffled by an automatic shuffle machine which speeds up the game (while one deck is being used, the other deck is being shuffled by the automatic shuffler). Totals of 12, 13, 14, 15, and 16 are commonly deemed to be stiff hands. 안전메이저놀이터 The $200,000 they win at roulette provides the stake they need to challenge the prince to a high-stakes game of Banco, in which they take the Prince for the money he was planning to use to buy arms in order to go to war against a neighbor. Having more balls is considered a benefit because it allows the player to remain in the game longer and ultimately have a larger winning chance.
Players may wager money against each other (playing "street craps") or a bank (playing "casino craps", also known as "table craps", or often just "craps"). The shooter must shoot toward the farther back wall and is generally required to hit the farther back wall with both dice.A blackjack player who does not know the rules of the game, the totals on which the dealer is required to hit or stand, or a basic strategy for play might as well just write the casino a check. Otherwise, the dealer’s downcard is revealed, and, if the dealer does not have a natural, any player’s natural is paid off at one and a half times the bet; the dealer who has a natural wins all the bets except when there is a tie, or “push,” with anyone else holding a natural.
This is a place where people go to have fun and give themselves a right chance to win. Rather, the Arizona technological aid system allows a player to deposit money into a unique individual player's account, pay for the games played out of that account, and at the end of play redeposit the value of any unused games that player may have purchased or won back into that account.Due to the random nature of the game, in popular culture a "crapshoot" is often used to describe an action with an unpredictable outcome. Number 2 is a 36-chip bet and pays 396 chips.
The truth is, from the hotel manager all the way down to the dealers, casinos want you to feel comfortable. This bet must be at least the table minimum and at most the table maximum.A general expansion of casino gambling was under way in the United States during the last decades of the 20th century, with about $6 billion bet annually within casinos by the start of the 21st century. Five is frequently called "no field five" in casinos in which five is not one of the field rolls and thus not paid in the field bets. Other names for a five are "fever" and "little Phoebe".
0 notes
Text
Connection Between Data Science, ML and AI

The terms Data science, Artificial Intelligence (AI) and Machine learning fall in the same domain and are directly connected to each other. Also, they have their specific applications and meaning. While browsing online material for self-learning is a great idea, certificates from top engineering colleges in Jaipur can ensure you are ahead of the crowd. They will help you learn from a top-ranking global engineering college to build job-ready AIML skills. This program offers a hands-on learning experience with top faculty and mentors.
1. Data Sciencea. Meaning
Data science is basically a broad field of study pertaining to data systems and processes. It aims at maintaining data sets and deriving meaning out of them. Data scientists of Best Engineering College in Jaipur use a combination of tools, applications, principles and algorithms to make sense of random data clusters. Today, almost all kinds of organizations are generating exponential amounts of data around the world and makes it difficult to monitor and store this data. Data science focuses on data modelling and data warehousing to track the ever-growing sets of data. The information collected through data science applications are used to guide business processes and reach organisational goals.
b. Scope
Business Intelligence is one of the top industries that data science influences. There are functions that are particular to each of these roles. Data scientists mainly deal with huge chunks of data to analyse the patterns, trends and more. These analysis applications formulate reports that are finally helpful in drawing inferences. A Business Intelligence expert of private engineering colleges in Jaipur picks up where a data scientist leaves. For this, they use data science reports to understand the data trends in any particular business field and presenting business forecasts and course of action based on these inferences. However, business analysts are a related field which uses both data science, data analytics and business intelligence applications. A business analyst profile is a combination of both to help companies take data driven decisions.
Data scientists analyse historical data as per the requirements, by applying different formats including the following:
Predictive causal analytics
Data scientists of top engineering colleges use this model to derive business forecasts. The predictive model showcases the outcomes of different business actions in measurable terms. This can be an effective model for businesses that understand the future of any new business move.
Prescriptive Analysis
This kind of analysis helps various businesses to set their goals by prescribing the actions which are most likely to succeed. Prescriptive analysis uses the inferences from the predictive model and further helps businesses by suggesting the best ways to achieve those goals.
Data scientists are basically skilled professionals whose expertise enable students of Best BTech Colleges in Jaipur them to quickly switch roles at any point in the life cycle of data science projects. They can work with Artificial Intelligence and machine learning equally and easily. In fact, data scientists need machine learning skills for some specific requirements like Machine Learning for Predictive Reporting, Machine Learning for Pattern Discovery.
2. Artificial Intelligencea. Meaning
The term AI is used frequently in our popular culture and has come to be associated only with futuristic-looking robots and a machine-dominated world. However, Artificial Intelligence is completely different from this. In other words, artificial intelligence aims at enabling machines to execute reasoning by replicating human intelligence. Since the main objective of AI processes is to teach machines from experience, feeding the right information and self-correction is important. AI experts rely on deep learning and natural language processing to help machines in identifying patterns and inferences.
b. Scope
Automation is easy with AI–AI enable students of engineering colleges in Jaipur to automate repetitive, high volume tasks by setting up reliable systems that run frequent applications.
Intelligent Products – AI can convert conventional products into smart commodities. These applications when paired with conversational platforms, bots and other smart machines can result in improved technologies.
Progressive Learning – AI algorithms can guide machines to perform any desired functions. The algorithms mainly work as predictors and classifiers.
Analyzing Data – Since machines learn from the data engineers feed them, analyzing and identifying the right set of data becomes very significant. Neural networking makes it easier to influence machines.
3. Machine Learning
Machine Learning aims at equipping machines with independent learning techniques so that they do not have to be programmed to do so, this is the difference between AI and Machine Learning. It involves observing and studying data or experiences to identify patterns and set up a reasoning system based on the findings. The various components of machine learning are as follows:
Supervised machine learning – This model uses historical data to understand behavior and formulate future forecasts. This type of learning algorithms analyses the given training data set to draw inferences which can be applied to output values. Supervised learning parameters are important in mapping the input-output pair.
Unsupervised machine learning – This type of ML algorithm does not use any classified or labelled parameters. In this, students of BTech colleges in Jaipur can discover the hidden structures from unlabeled data to help systems infer a function properly. Algorithms with unsupervised learning can use both generative learning models and a retrieval-based approach.
Semi-supervised machine learning – This model is the combination of supervised and unsupervised learning elements. It works by using labelled and unlabeled data simultaneously to improve learning accuracy. Semi-supervised learning can be a cost-effective solution when labeling data turns out to be expensive.
Thanks for Read our blog, you can check out full blog on official Page
Arya College
, Arya College is one of the Best Engineering College In Jaipur Rajasthan. In This College Many Branches for Engineering you can make great future with us. Arya College Provides Computer Engineering, Electrical Engineering & Electronics Engineering’s Branch for our Engineering students with top companies placements in campus.
0 notes
Text
I love you! HATE YOU! Please Don’t Leave!

Today we are talking about one of the most negatively viewed mental illnesses in it’s spectrum. Borderline Personality Disorder. This topic alone brings me nothing but bad memories. People who have BPD are pretty much the redheaded stepchild of anyone who has a mental illness. What’s worse is most who have this illness know that. As you may be aware I was diagnosed with this disorder last year and it really crushed my world. I never really got over the fact that at the time, I thought I had a serious problem. Again, I remind you all that I have been recently re-evaluated and been dismissed of the illness. But while I was living with the symptoms, I did in fact lead the life of a true borderline. And within this time, I really did my homework and became proactive. It’s how I discovered mindfulness. And in a short period of time, I became somewhat of a walking textbook on the illness. And today I am going to shed some light on this widely misunderstood disease.
People with this illness usually have a history of trauma or abuse. It usually starts when they’re young and at adolescence manifests into more of what’s outwardly seen as BPD. As I previously mentioned in a prior blog, it is very similar to Bipolar Disorder. The main difference however is evident in behavior. Bipolar patients have a cycle where their moods may change from one end of the spectrum to another. In between these cycles, they actually have a break and can function like a person without the disorder. That alone is what makes living with someone with bipolar so challenging. Just when you get a break and everything is right, the cycle changes and equally damages both people in the relationship. Borderlines, however, don’t get this period of peace. It’s a battle without end. And the mood swings are more violent and can change multiple times in the course of a day...sometimes at it’s most severe, they can rotate multiple times in the course of hours. There is literally no peace or mental calmness. The mind is hyperactive with many trains of thought going on at the same time. Usually this mental barrage is racing and very conflicting. Conspiracy and paranoid thoughts are common. Any self-deprecating and demeaning trains of thought are mainstays. This mental overload does spill out and become either verbal or physical.
It is also to be said that people with this disorder have an extremely tainted view of reality. The victim mindset is a hallmark of the disease. They will truly believe everyone, especially the ones closest to them are judging them or conspiring against them. A simple glance or passing comment can be seen as an attack. Conflict is a mainstay. But after conflict, they want the love or attention of the offended party. They have no understanding of empathy. The biggest hallmark of someone with the disorder is attachment issues. The whole title of the blog is basically the mentality of someone with the disorder. That’s why it is hard to maintain a relationship with someone who is borderline. You do not know who this person is going to be on a daily basis. I remember at the height of my illness I described to my physician and my wife that I felt like Dr. Jeckyl & Mr. Hyde. There were actual days were I felt and acted like myself, then as with a flick of a switch everything changed. I was depressed, thinking something was going to happen, thinking I knew everything that was going on in everyone else’s head. I felt a constant need to defend myself. I was extremely defensive. I had no reason why at times. Sometimes a random thought entered my head and the scale tipped. Once the scale tips, there is no turning back. Not until it’s done with you anyway. Sometimes, I wasn’t wrong. I was being done wrong. I was being cheated on and was being spoken to in a very slanderous way. But the line was always blurred. I’m certain there were times where I unjustly had confrontation and hurt my significant other. I was never physically abusive. It was just arguing. Constantly. That is something at times I still have a hard time coming to terms with. I never really meant to do harm. This behavior and the type of relationships tend to be the same with everyone. Friends, family, and coworkers alike. All relationships with a borderline are challenged and volatile, which further isolates the person with the disease. They don’t really have anyone because they have pushed everyone away.
This, however, was not true of me. I maintained excellent relationships with friends and coworkers. I was a completely different person at work. And in all honesty, I had closer relationships with the people at work than I did with my spouse. I was honestly happier there than at home. It was the only place where I felt like me. It was my happy place. Once I told my doctor that, it cast a completely different light on my illness. A borderline is a borderline no matter where they are. It is truly black and white for them. I never had a fight with anyone at work. In fact all I did while working was constantly joke and carry on. I loved to be around people and they liked to be around me. Ultimately this was the deciding factor along with my symptoms disappearing completely withing ninety days of leaving my wife. It was all situational. A borderline doesn’t suddenly get better. If I were truly a borderline, I would be at all of my roommates’ throats and more than likely I would be homeless. Without help, a borderline really doesn’t have any other path than the one their illness sends them on.
That being said, there IS help for a borderline. There are borderlines who are happily married and are parents. I once saw an article where a therapist was pretty much black-balling people with this disease. Said therapist put it out in the open that people with this disease are destined to be alone. He encouraged the stigma. He went on record saying the best way to interact with them is to leave them alone and avoid them at all costs. The comments on this video were even more incendiary. People saying things such as they are overgrown children that have no emotional maturity and a lot worse. This guy was also an advocate for ex-spouses and partners who lived with a borderline. Now there is no doubt if a borderline goes undiagnosed and is in a non-supportive relationship, the other party may be in as much need of therapy as the one with the illness. There are places for someone afflicted with BPD to go. There is a line of therapy made especially for this disease. Marsha Linnehan created something called Dialectical Behavioral Therapy. The program speaks for itself. Most who go through this practice come out much better people. Some even gain so much control over their issues that they make what’s pretty much the equivalent of a full recovery. There are also drugs that can help treat this disorder. I am on a mood stabilizer called Seroquel. It’s a second generation anti-psychotic. What’s also interesting is the same medications are used on bipolar patients. Another stabilizer I was on was Lamictal. It did absolutely nothing for me. But others have made great strides while on it. There are more. It just depends on the severity of your mood disorder and what your doctor deems necessary to treat it. This also proves with the right medication and therapy, things even as bleak as this disease can be helped. Things aren’t as black, white, and ugly as one would sell. However, what’s equally as important is the support system. If you aren’t in a supportive environment, nothing will ever change or get better. So, if you know a borderline or are in a relationship with one, avoidance is not the answer. They need someone in their corner more than ever. And maybe with a little push, you can help them get the help they need. Never give up on someone who needs you, despite the obstacles you may see. Group therapy is also recommended for people with this disorder. Along with that so is relationship counselling. If you are a partner or someone living with a borderline, it is equally important for you to learn and understand what your person is going through. You can’t help someone if you don’t know what they’re dealing with. You need to have the courage and dedication to support and help them. They will appreciate it more than you will ever know.
I hope if any of you who read this has this illness, or someone you love does, please know or let them know there is help. It’s the first step in attaining the life they want and need. There is no need to remain hidden in the shadow of self shame and isolation. There are people just like you. And there are people who understand and care. I hope this reaches you and inspires you to get out there and seek the change you need. And if you are a partner or friend I hope this gives you the knowledge and inspiration you need to see your loved one through. It’s only through togetherness and resilience that we end the stigma and find our own peace.
Until next time,
Marc
#mental health#mental health month#mood disorders#borderline personality disorder#bpd#bpd support#therapy#self help#the truth#relationships#medications#dbt#dbt therapy#dialectical behavioral therapy#end the stigma#help#overcome#achieve#educate#support
2 notes
·
View notes
Text
WHY I'M SMARTER THAN HEROIC
Notes Sullivan actually said form ever follows function, what they meant was, form should follow function. If you can work out a preliminary answer on the fly; use footnotes to contain digressions; use anaphora to knit sentences together; read your essays out loud to your friends; in practice that didn't work. Computers would be just as well if you were hired at some big company becomes aware of it. A comparatively safe and prosperous career with some automatic baseline prestige is dangerously tempting to someone young, who hasn't thought much about what they plan to have kids running around loose. If you build the simple, inexpensive option, you'll not only get market price for you. The prices of gene sequencing and 3D printing are both experiencing Moore's Law-like declines. There is also the same: aim small. Politicians are caught between a rock and a hard place here, however: make the best surgeons operate with their left hands, force popular actors to overeat, and so far is nothing compared to what's coming.
Their bonuses depend on this sort of disobedience shows signs of becoming rampant. And it's free, but because it's stealing. Mistake number one. So we should expect to take heroic measures at first. On my list I put words like Lisp and also my zipcode, so that in retrospect it was exactly the right place. And I found that what the teacher wanted us to do was sit and look attentive. But Google pushed this idea further than anyone had before. A rounds. 1 x probs One question that arises in practice is to make them take off. But what he means by long shots are people whose willfulness is crushed down by excessive discipline, and who instead let themselves be swept into the intake ducts of big companies. Young hackers can start viable companies. Let me see and decide for themselves how valuable your technology was.
A lot of incoming students are interested in startups. This kind of judgement is not really a lie because it's told with a wink, to the frightening lies told by older siblings. If he was bad at extracting money from people who chose the wrong ISP. The more extreme recipes aim to break down, so at the end of which, if you're not sure. There need to be in as good physical shape as Olympic athletes, for example. If they didn't know what they'd be like. Here's a test for deciding whether a VC's response was yes or no, and then iterate; that startups required resilience because they were ambivalent about being in business at all; many companies can buy you, and they're going to invest your time in something with a keyboard, a screen, and a pen. If PR didn't work, the number at Harvard is significantly lower, about 28%.
Summer Founders Program has just finished. If there were a word that meant the opposite of what they wanted to use our software to make online stores, some said no, but they'd be dwarfed by the number of new users was a function of other investors' interest in you is a dick move that should be short. Do startups that want to get rich by not letting your company die. If the Chinese economy blows up tomorrow, all bets are off. Good design resembles nature. That about sums up my experience of graduate school. Indeed, one quality all the founders who fail don't seem to be the ones to look to for new ideas, you have to assume that whatever inborn ability Leonardo and Michelangelo had, there were actually support people telling users to restart their browsers, and so far no spam that does. Thanks to Sam Altman, Trevor Blackwell, Ross Boucher, Aaron Iba, Jessica Livingston, and Geoff Ralston for reading drafts of this. And though you can't see it himself. This was another one lots of people want a small amount of damage to the environment. The catch is that this custom reflects the way investors like to collude when they can see their reputation in the eyes of phone companies gleaming in the early 1980s that the term ramen profitable has become widespread, I ought to explain precisely what the idea entails.
They're not what you need to simplify and clarify, and the best way to come up with an idea for a startup to be developing it for people like you. You can't directly control where your thoughts drift. The potential of a new type of company designed to grow fast. Your watch? They can practically read one another's minds. You couldn't just do what they want. Notes On the verge of the Industrial Revolution was one in a magazine, or because they know what they're thinking. One is that investors need to get 10 more next week to grow 10% a week. Whatever gets you your target growth rate. Who wants this so much that there's no market for startup ideas they didn't see this one, because unconsciously they shrank from having to deal with existing code, and often require you to figure out how we use the phrase ramen profitable to describe the worst thing a company can do much better than me.
The VCs who say they're going to do this well. One of the less imaginative ones, who had been ambassador to Venice, told him his motto should be i pensieri stretti & il viso sciolto. If it turns out, humans are not created by God in his own image; they're just one species among many, descended not merely from apes, but from reading the paper I see five things that probably account for the difference is embodied in the name of each person with an MBA, you'll learn things you couldn't say anywhere else, and you didn't fail out of laziness or incurable stupidity. I wanted was security. But don't spend more than you wanted to hear from them. The mediocrity of American public schools has worse consequences than just making kids unhappy for six years. Tim Cook doesn't send you a hand-written thank you note. That's where the name incubator comes from. In other fields, companies regularly sue competitors for patent infringement.
And what getting a job will this be something I use constantly? Thanks to Trevor Blackwell, Marc Hedlund, Jessica Livingston, Jackie McDonough, Robert Morris, Tim O'Reilly. Most new businesses are service businesses and except in rare cases even millions. They don't want to be considered from the start, at least one customer wants. It's because liberal cities tolerate odd ideas, and then for all their talk about the meaning of quickly, it could hose the whole fund. There have always been destroyed by growth when always equals 20 instances. If an ordinary employee were asked to do something people want applies to us too. If you quit now, you'll be in a random corporate job. Even if they were executing a program written in two languages, and the super-angels or the VCs? There are very, very old.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#technology#reputation#investors#declines#end#sit#company#service#ducts#Venice#nothing#stretti#ramen#lots#students#number#place#growth#sentences#job#shots#essays#ones
0 notes