#url encryption
Explore tagged Tumblr posts
Note
Hey Robin how’s it like being so awesome
It's pretty good especially now that I believe I'm awesome!
#Tweet Tweet!#Encrypted Whistles#ic#Robin The Wonder#v: Knighthood#((also if this is who i suspect it is. ive got your other ask about your various urls))#((im gonna keep it in my inbox for now so i can find those blogs and read your rules and information pages))#((i know theyre not up yet so no rush take your time im sure you lead a busy life outside of tumblr))
1 note
·
View note
Text
Recall is designed to use local AI models to screenshot everything you see or do on your computer and then give you the ability to search and retrieve anything in seconds. There’s even an explorable timeline you can scroll through. Everything in Recall is designed to remain local and private on-device, so no data is used to train Microsoft’s AI models. Despite Microsoft’s promises of a secure and encrypted Recall experience, cybersecurity expert Kevin Beaumont has found that the AI-powered feature has some potential security flaws. Beaumont, who briefly worked at Microsoft in 2020, has been testing out Recall over the past week and discovered that the feature stores data in a database in plain text.
Holy cats, this is way worse than we were told.
Microsoft said that Recall stored its zillions of screenshots in an encrypted database hidden in a system folder. Turns out, they're using SQLite, a free (public domain) database to store unencrypted plain text in the user's home folder. Which is definitely NOT secure.
Further, Microsoft refers to Recall as an optional experience. But it's turned on by default, and turning it off is a chore. They buried it in a control panel setting.
They say certain URLs and websites can be blacklisted from Recall, but only if you're using Microsoft's Edge browser! But don't worry: DRM protected films & music will never get recorded. Ho ho ho.
This whole debacle feels like an Onion article but it's not.
Luckily(?) Recall is currently only available on Windows 11, but I fully expect Microsoft to try and shove this terrible thing onto unsuspecting Win10 users via Update.
Stay tuned...
3K notes
·
View notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
79 notes
·
View notes
Text
☀️ OO1 - cyber themed npts

☀️ names 01, 404, ada, ajax, astra, bit, blink, byte, cersei, circuit, click, code, cyber, dex, dot, encrypt, exe, flash, futura, gizmo, glitch, hack, hotwire, lux, mecha, mechanism, metal, minus, neo, net, one, pearl, pixel, plus, python, robot, spark, tera, tilde, vesper, vi, web, xios, xyl, xylen, zap, zen, zero
☀️ pronouns .gif/.gifs, .jpg/.jpgs, alt/alts, by/byte, cd/cds, click/clicks, code/codes, compu/computer, cpu/cpus, cy/cyan, cy/cyber, elec/electric, file/files, gli/glitch, glow/glows, hack/hacks, img/imgs, key/keys, link/links, machine/machines, malware/malwares, metal/metals, neo/neos, num/number, pc/pcs, pix/pixel, screen/screens, tab/tabs, tech/techs, txt/txts, type/types, url/urls, web/website, wire/wires, zero/one, >/>self, #/#self, !/!self, ?/?self, +/+self, ae/aem, ce/cem, ky/kyr, ny/nym, vi/vir, zy/zyr, hz/hzm, shz/hzr, thzy/thzm, zt/zts, 💿/💿self, ⌨️/⌨️self
☀️ titles the cybernetic, the encrypted one, the one born of technology, the supercomputer, the virtual one, prn behind the screen, prn between the lines of code, prn from cyberspace, prn made of binary, prn of code, error 404: [name] not available
☀️ @id-pack-archive
#☀️ solar#☀️ npt#npt#npts#names pronouns titles#npt pack#npt ideas#id pack#id packs#cyber npts#cyber id pack
27 notes
·
View notes
Text
/art/143-S4KI-1078340194
01101000011101000111010001110000011100110011101000101111001011110111011101110111011101110010111001100100011001010111011001101001011000010110111001110100011000010111001001110100001011100110001101101111011011010010111101100001011100100110011101100001011010110110100101101011011000010111001101100001001011110110000101110010011101000010111100110001001101000011001100101101010100110011010001001011010010010010110100110001001100000011011100111000001100110011010000110000001100010011100100110100
@daily-vitamin-ena @dailyvitamin-sakitenma
#its probably a url. but to what...#it might be encrypted again but i dont think so bc it says saki in the middle#unreality
12 notes
·
View notes
Text
Cyber / Virtual ID Pack

Inside this pack, you will find: Pronouns, Titles, Names, and Genders that relate to Virtuality, Cybernetic, Robots, and anything alike!
This features a LOOOONG list of pronouns and dystopian-ish names!

Pronouns:
Cy/Cyb/Cyber/Cybers/Cyberself
Vir/Virt/Virtual/Virtuals/Virtualself
Ne/Net/Network/Networks/Networkself
Ne/Net/Nets/Nets/Netself
In/Inter/Internet/Internets/Internetself
Co/Comp/Computer/Computers/Computerself
In/Inpu/Input/Inputs/Inputself
Ou/Out/Output/Outputs/Outputself
Vi/Viru/Virus/Viruses/Virusself
Anti/Antivir/Antivirus/Antiviruses/Antivirusself
Er/Erro/Error/Errors/Errorself
Sys/Syste/System/Systems/Systemself
Pro/Proce/Processor/Processors/Processorself
Di/Digi/Digital/Digitals/Digitalself
Do/Down/Download/Downloads/Downloadself
Up/Uplo/Upload/Uploads/Uploadself
Cor/Corru/Corrupt/Corrupts/Corruptself
Mal/Malwa/Malware/Malwares/Malwareself
Se/Secur/Security/Securitys/Securityself
Cry/Crypt/Crypto/Cryptos/Cryptoself
We/Web/Webs/Webs/Webself
Web/Webs/Website/Websites/Websiteself
Fu/Futu/Future/Futures/Futureself
Ro/Rob/Robot/Robots/Robotself
Rob/Robo/Robotic/Robotics/Roboticself
By/Byt/Byte/Bytes/Byteself
Fi/Fil/File/Files/Fileself
Ra/Ram/Rams/Rams/Ramself
Scr/Scre/Screen/Screens/Screenself
Te/Tech/Techs/Techs/Techself
Te/Tech/Techno/Technos/Technoself
Tec/Techno/Technology/Technologys/Technologyself
Ma/Mach/Machine/Machines/Machineself
Wi/Wir/Wire/Wires/Wireself
Na/Nan/Nano/Nanos/Nanoself
Da/Dat/Data/Datas/Dataself
Plu/Plug/Plugs/Plugs/Plugself
Ele/Elect/Electric/Electrics/Electricself
Ke/Key/Keys/Keys/Keyself
Pa/Pass/Password/Passwords/Passwordself
Ter/Term/Terminal/Terminals/Terminalself
Cy/Cybo/Cyborg/Cyborgs/Cyborgself
Ty/Typ/Type/Types/Typeself
Fi/Firm/Firmware/Firmwares/Firmwareself
Ha/Hard/Hardware/Hardwares/Hardwareself
So/Soft/Software/Softwares/Softwareself
Ha/Hack/Hacks/Hacks/Hackself
Ha/Hack/Hacker/Hackers/Hackerself
Si/Sig/Signal/Signals/Signalself
Clo/Clou/Cloud/Clouds/Cloudself
On/Onli/Online/Onlines/Onlineself
In/Insta/Install/Installs/Installself
Co/Cod/Code/Codes/Codeself
Ad/Admi/Admin/Admins/Adminself
Gra/Graph/Graphic/Graphs/Graphself
Sy/Syn/Synth/Synths/Synthself
Phi/Phis/Phish/Phishs/Phishself
Phi/Phish/Phishing/Phishings/Phishingself
Do/Dox/Doxs/Doxs/Doxself
Si/Sit/Site/Sites/Siteself
Bo/Bot/Bots/Bots/Botself
Pho/Phon/Phone/Phones/Phoneself
Key/Keyboa/Keyboard/Keyboards/Keyboardself
Mo/Mou/Mouse/Mouses/Mouseself
Chi/Chip/Chips/Chips/Chipself
Moth/Mother/Motherboard/Motherboards/Motherboardself
Co/Com/Compute/Computes/Computeself
Pi/Pira/Piracy/Piracys/Piracyself
En/Encry/Encrypt/Encrypts/Encryptself
PDA/PDAs
CPU/CPUs
URL/URLs
404/404s
📱/📱's
💻/💻's
⌨️/⌨️'s
🖥/🖥's
🖱/🖱's
💿/💿's
🎙/🎙's

Titles:
The Cyborg
(X) Whos Wired
Made of Nanotech
(X) Who Uses Nanotech
Scholar of Machines
The Cyber Security
(X) Who Has Cyber Wings
Connected Online
Offline
Unable to Connect
The Administrator
Synthesizer
The Hacker
Nanohacker
The Antivirus
Reconnecting...
ERROR: Unable to Connect
ERROR 404
ERROR: Malware Detected

Names:
Since names don't usually have "techy" meanings, I picked one's that sounded the most cybernetic, cyberpunkish, dystopian, virtualish, etc!
Fem: Althea, Ameris, Astoria, Arcadia, Astra, Beretta, Cyra, Crystal, Crosselle, Eve, Io, Jinx, Kit, Lilith, Meridian, Morrian, Nebula, Nova, Neve, Noxia, North, Octavia, Odette, Odile, Prota, Pistol, Rey, Rue, Rain, Raine, Stormy, Seraphina, Sona, Skye, Thundra, Tempest, Vega, Viva, Vinette, Venus, Xenia, Xya, Xena, Xiomara, Xenara, Xanthe, Zephyria, Zyla, Zadie, Zia,
Masc: Alaric, Aksel, Arden, Antares, Apollo, Ace, Asher, Cole, Cyrus, Code, Draven, Drift, Ender, Flynn, Hawk, Isaac, Jericho, Kip, Kai, Koios, Knox, Nox, Neo, Nero, Octavian, Orionis, Oghma, Paine, Rocket, Ray, Rai, Silas, Slader, Sebastian, Seth, Seraphim, Thalax, Theo, Thatch, Vox, Vector, Wyatt, Xyon, Xane, Xylan, Xerxes, Xayden, Xavier, Xander, Zander, Zayden, Zenith, Zev, Zale, Zane, Zaire, Zeke,
Neu: Andras, Axe, Axiom, Alloy, Allele, Ash, Arrow, Beetle, Chrom, Corvus, Dakota, Dell, Eos, Echo, Eden, Fox, Ghost, Glöckner, Hydrae, Ion, Jesper, Jett, Kursk, Lesath, Locklyn, Lyrae, Maddox, Nemo, Orca, Onyx, Oxygen, Panther, Rikko, Robin, Rune, Scorpion, Scorpius, Saturn, Sparrow, Sonar, Tore, Tauri, Techne, Techno, Ursae, Vesper, Volt, West, Wolf, Xen, Xenon, Zephyr, Zodiac, Zenon, Zeru, Zero, Zen

Genders:
Futuracityc: A gender related to futuristic cities
Futurafashic: A gender related to futuristic fashion
Futurahousic: A gender related to futuristic houses
Digigender: A digital gender. Rangeable from any digital thing or file; virus, malware, .txt, .mp3, antivirus, trojan, email, etc.
Cybergender: A gender or form of gender expression where ones gender or expression is deeply tied into Cyberpunk lore, culture, fashion or media.
CYBERWEAPONIC - a gender that feels like a digital or robotic weapon. this gender may also have ties to sentient AI used as a weapon, but not necessarily.
BIOAMOROBOTIC - a gender connected to being a robot who loves humanity and the world and finds joy all around them!
RobAnatomic - a gender under the anatomic system(link) related to robots, anatomy, robotic anatomy, the anatomy of robots, robots made to teach/study anatomy, anatomy based/related robots of some kind, the anatomy/biology of someone or something being robotic, having robotic anatomy, being a robot with an interest in anatomy and more.
Robogender - for people who’s gender identity aligns with machines/robots/androids/mechs/AIs.
Cyborwebic - a gender related to webcore, evil scientist aesthetics, artificial beings such as androids/cyborgs etc, turtleneck sweaters and old computer monitors
AI flag - this can be used for nonhuman, otherkin, gender, delusion.
Gendervirtual / Genderdigital - a gendersystem in which your gender is related to virtual ) digital themes and x , such as being a virtual ) digital x , a x who loves virtual ) digital themes , a virtual ) digital being who loves x themes , etc.
#npt ideas#npt blog#npt pack#npt list#npt suggestions#cyber npt#virtual npt#robotic npt#robot npt#cybergender#virtualgender#robotgender#digitalgender
55 notes
·
View notes
Text
i think i have this question every time i have to do mandatory security training for work but what's the deal with 'if someone sends you a link and the url starts with http rather than https it's probably phishing'
like. if you are a malicious actor and someone deliberately enters their credentials into a website you control then it does not matter if they were encrypted on the way. you were not trying to sniff them out on the way, they were sent to you. why not just make your website https anyway and give them a false sense of security because they've been watching the same training videos i have.
96 notes
·
View notes
Text

So, I've talked about these bad bipartisan internet bills in the US Senate before, which all more or less boil down to "censorship in the name of Protect The Childrens," but I think it's important now more than ever to boost efforts to fight them because, as of today (5/9/2023), there's a major push planned by the folks lobbying for these bills, and we need to push back.
Thusly, here's a propaganda poster with the URL of the main hub to fight against those bills.
As a primer on said internet bills for those who don't know:
KOSA- Aims to create a "duty of care" towards minors that would de-facto mandate incredibly intrusive age gating via drivers' licenses or fucking face scanning to identify said minors, and would likely lead to lots of censorship. Extremely dangerous right now because the people who want it are pushing hard, and it's got a depressing amount of bipartisan support due to the Protect The Children thing shutting off people's brains.
EARN IT- Will remove Section230 for sites that supposedly let CSAM exist on their servers for too long, which might sound good until you remember the inherent difficulties in moderating that on big social media sites that means what they're asking is literally impossible and also the fact that the last time they tried something like this we got FOSTA-SESTA and its associated censorship wave. Extremely dangerous because it's passed out of committee
RESTRICT ACT- The "ban TikTok" bill that basically gives the us government carte-blanche to censor foreign sites they don't like.
STOP CSAM ACT- A similar act to KOSA and EARN IT that is pretty directly designed to weaken encryption, which is dangerous for any marginalized folks especially in a post-Roe era
Beyond the hub for action, badinternetbills.com, if you're in the US, I urge you to call your senators, especially if they're on the Commerce Committee, given that's the one currently looking at KOSA, and even if you can't, boost this to those that can.
And, as per usual with these propaganda posters, this poster is officially, for the sake of spreading it, under a CC0 license. Feel free to spread it, remix it, add links to the bottom, use it as a meme format, do what you will but for gods' sake get the word out!
305 notes
·
View notes
Note
ignore this if it's too public but, what do you use for ripping audio? I've been using cobalt.tools but it's not very efficient for whole playlists. been thinking about that spotify post a lot lol
Ough.. I usually don't rip audio. not for music at least.
See, youtube, and youtube music, only streams audio at 128kbps quality (256 if you have premium). Which is... mediocre. High-quality MP3 files are usually 320kbps, and good .flac files are variable bitrate but usually end up several times higher than that. (Doesn't really matter tho, most bluetooth only streams at 320 anyways, and if you can tell the difference and want to use a cord, you already need better headphones.)
So... I usually try to find a torrent that already has the music I'm looking for, which is... not everything. If you're looking for more popular stuff, you can look up, like "depeche mode discography" and it'll be there, all high quality and decent metadata to unzip into your ~/music folder.
But for the stuff you can't find on there, your best bet is lucida.to
It's... janky and not very consistently up, prone to weird errors and random problems, but when it does work, you get good-quality music files out of it. They might come in .ogg, which you'll have to convert (i like fre:ac) to mp3 or flac if you want metadata to work, but it's usually good.
Also, don't trust any online "spotify downloader" websites; afaik, nobody has cracked spotify's encryption. What they're doing is searching youtube, finding each song, download that, and putting spotify metadata on it. Maybe the file will even say 320kbps, but that's a lie, if you open it up in the right viewer it'll be 128. There's shitty paid software available that will "rip" from spotify by actually messing with your Spotify client, making it actually play the song at a higher speed or something, and then ripping that, but... not really worth it. Piracy is meant to be free, damnit!
If you really want to rip good audio files, you'll have to, like, get a Tidal or Deezer subscription and use software to rip from that.
...Now! If you weren't asking about music, want to rip from Youtube, and/or don't care whether your quality is good, I use and love Stacher!
It's a GUI for yt-dlp, which is like, the command-line youtube downloading tool, and... it works.
Like, I used this to download all of The Magnus Archives; I just pasted the playlist url into it and it downloaded each one. It'll be great for like, podcasts, or things for which you won't really care about super fidelity? or if you want to download tons of videos, it'll do that.
Yaa files!!!!!
12 notes
·
View notes
Text
Fakepeppino's way of speaking

@alextydaisuda123
@pizzabox-box
I'm a bit obsessed with the way Feppino writes his lines... at the very least, I try to make them readable if you understand how to read them.
Basically, I use ROT13code.
When drawing with the work of Boxinno's authors in mind,
The shape is chaotic to match the work.
Here is the site I use for encryption and decryption.
(I usually use it in Japanese)↓
#topic#tweet#pizza tower#pizzatower au#steampunk tower#fake peppino pizza tower#fake peppino#boxinno#doodle#digital art#painting
41 notes
·
View notes
Text
The flood of text messages started arriving early this year. They carried a similar thrust: The United States Postal Service is trying to deliver a parcel but needs more details, including your credit card number. All the messages pointed to websites where the information could be entered.
Like thousands of others, security researcher Grant Smith got a USPS package message. Many of his friends had received similar texts. A couple of days earlier, he says, his wife called him and said she’d inadvertently entered her credit card details. With little going on after the holidays, Smith began a mission: Hunt down the scammers.
Over the course of a few weeks, Smith tracked down the Chinese-language group behind the mass-smishing campaign, hacked into their systems, collected evidence of their activities, and started a months-long process of gathering victim data and handing it to USPS investigators and a US bank, allowing people’s cards to be protected from fraudulent activity.
In total, people entered 438,669 unique credit cards into 1,133 domains used by the scammers, says Smith, a red team engineer and the founder of offensive cybersecurity firm Phantom Security. Many people entered multiple cards each, he says. More than 50,000 email addresses were logged, including hundreds of university email addresses and 20 military or government email domains. The victims were spread across the United States—California, the state with the most, had 141,000 entries—with more than 1.2 million pieces of information being entered in total.
“This shows the mass scale of the problem,” says Smith, who is presenting his findings at the Defcon security conference this weekend and previously published some details of the work. But the scale of the scamming is likely to be much larger, Smith says, as he didn't manage to track down all of the fraudulent USPS websites, and the group behind the efforts have been linked to similar scams in at least half a dozen other countries.
Gone Phishing
Chasing down the group didn’t take long. Smith started investigating the smishing text message he received by the dodgy domain and intercepting traffic from the website. A path traversal vulnerability, coupled with a SQL injection, he says, allowed him to grab files from the website’s server and read data from the database being used.
“I thought there was just one standard site that they all were using,” Smith says. Diving into the data from that initial website, he found the name of a Chinese-language Telegram account and channel, which appeared to be selling a smishing kit scammers could use to easily create the fake websites.
Details of the Telegram username were previously published by cybersecurity company Resecurity, which calls the scammers the “Smishing Triad.” The company had previously found a separate SQL injection in the group’s smishing kits and provided Smith with a copy of the tool. (The Smishing Triad had fixed the previous flaw and started encrypting data, Smith says.)
“I started reverse engineering it, figured out how everything was being encrypted, how I could decrypt it, and figured out a more efficient way of grabbing the data,” Smith says. From there, he says, he was able to break administrator passwords on the websites—many had not been changed from the default “admin” username and “123456” password—and began pulling victim data from the network of smishing websites in a faster, automated way.
Smith trawled Reddit and other online sources to find people reporting the scam and the URLs being used, which he subsequently published. Some of the websites running the Smishing Triad’s tools were collecting thousands of people’s personal information per day, Smith says. Among other details, the websites would request people’s names, addresses, payment card numbers and security codes, phone numbers, dates of birth, and bank websites. This level of information can allow a scammer to make purchases online with the credit cards. Smith says his wife quickly canceled her card, but noticed that the scammers still tried to use it, for instance, with Uber. The researcher says he would collect data from a website and return to it a few hours later, only to find hundreds of new records.
The researcher provided the details to a bank that had contacted him after seeing his initial blog posts. Smith declined to name the bank. He also reported the incidents to the FBI and later provided information to the United States Postal Inspection Service (USPIS).
Michael Martel, a national public information officer at USPIS, says the information provided by Smith is being used as part of an ongoing USPIS investigation and that the agency cannot comment on specific details. “USPIS is already actively pursuing this type of information to protect the American people, identify victims, and serve justice to the malicious actors behind it all,” Martel says, pointing to advice on spotting and reporting USPS package delivery scams.
Initially, Smith says, he was wary about going public with his research, as this kind of “hacking back” falls into a “gray area”: It may be breaking the Computer Fraud and Abuse Act, a sweeping US computer-crimes law, but he’s doing it against foreign-based criminals. Something he is definitely not the first, or last, to do.
Multiple Prongs
The Smishing Triad is prolific. In addition to using postal services as lures for their scams, the Chinese-speaking group has targeted online banking, ecommerce, and payment systems in the US, Europe, India, Pakistan, and the United Arab Emirates, according to Shawn Loveland, the chief operating officer of Resecurity, which has consistently tracked the group.
The Smishing Triad sends between 50,000 and 100,000 messages daily, according to Resecurity’s research. Its scam messages are sent using SMS or Apple’s iMessage, the latter being encrypted. Loveland says the Triad is made up of two distinct groups—a small team led by one Chinese hacker that creates, sells, and maintains the smishing kit, and a second group of people who buy the scamming tool. (A backdoor in the kit allows the creator to access details of administrators using the kit, Smith says in a blog post.)
“It’s very mature,” Loveland says of the operation. The group sells the scamming kit on Telegram for a $200-per month subscription, and this can be customized to show the organization the scammers are trying to impersonate. “The main actor is Chinese communicating in the Chinese language,” Loveland says. “They do not appear to be hacking Chinese language websites or users.” (In communications with the main contact on Telegram, the individual claimed to Smith that they were a computer science student.)
The relatively low monthly subscription cost for the smishing kit means it’s highly likely, with the number of credit card details scammers are collecting, that those using it are making significant profits. Loveland says using text messages that immediately send people a notification is a more direct and more successful way of phishing, compared to sending emails with malicious links included.
As a result, smishing has been on the rise in recent years. But there are some tell-tale signs: If you receive a message from a number or email you don't recognize, if it contains a link to click on, or if it wants you to do something urgently, you should be suspicious.
30 notes
·
View notes
Text
Caleb Ecarma at Musk Watch:
Edward Coristine, a 19-year-old member of Elon Musk’s Department of Government Efficiency (DOGE), launched an image-sharing website in 2021 that featured custom “shitposting” web addresses that redirected to content hosted on his site. URLs that redirected to Coristine’s site referenced the sale of child sexual abuse material, racial slurs, and rape. Among the links were “child-porn.store” and “kkk-is-cool.club,” according to web traffic tracked by BuiltWith. The White House and Coristine did not respond to requests for comment. A former intern at Musk’s brain-computer interface company Neuralink, Coristine was named senior adviser to the State Department’s Bureau of Diplomatic Technology on Monday, the Washington Post reported. He is also listed as an “expert” at the Office of Personnel Management. In early 2021, Corisitine, then 16, activated the tesla.sexy website. He described it as an image-sharing site that would prioritize the confidentiality of its users. “Why are we the sexiest? Privacy… When you use tesla.sexy, all your images are encrypted. We do not log IP addresses, device agents or anything else,” the site’s homepage stated in March 2021, according to archives from the Wayback Machine. “If you like features like we do, you'll love tesla.sexy… Fake links, lots of cool domains and effects to put on your images for ultimate shitposting.” Coristine updated the website’s homepage in April 2021, stating that it offered users, “Image hosting with a touch of insanity.” The site update indicated that it catered specifically to image-sharing among Discord users: “You can customize embeds, use fake links (only works on Discord), use random domains and much more… Images embed within a second on Discord. Uploading images is also an incredibly speedy process.” Again, Coristine emphasized that tesla.sexy would protect the identities of users who used the site to share images. “Images are encrypted at rest, and in transit,” the site stated. An analysis of URL traffic to tesla.sexy between April 2021 and September 2021 shows that numerous noxious URLs redirected to Coristine’s site, including, “children-sex.party,” “child-porn.store,” “kkk-is-cool.club,” “nigga.rentals,” “nigga-sex.download,” “owns-a-slave.shop,” “raping-women.club,” “ketamine-rape.date,” “rape.business,” and “rapes-wo.men.” Internet archives of the URLs show they redirected traffic to tesla.sexy but any content they may have linked to has disappeared.
[...] Other young men that Musk has recruited to staff the White House’s U.S. DOGE Service include Marko Elez, who resigned last week after the Wall Street Journal discovered a social media account he used to promote racism and eugenics. DOGE then rehired Elez at the behest of Musk and Vice President J.D. Vance. Gavin Kilger, a DOGE member who serves as a special advisor at the Office of Personnel Management and a domain administrator at the Consumer Financial Protection Bureau, shared content posted by white supremacist Nick Fuentes before joining the Trump administration, according to Reuters.
Excellent Musk Watch reporting: Edward Coristine, one of the DOGE young adults that are working to destroy America one agency at a time, ran image-sharing site linked to URLs referencing pedophilia and the KKK.
#DOGE#Edward Coristine#Office of Personnel Management#BuildWith#Discord#State Department#Musk Watch#Gavin Kilger#Marko Elez
7 notes
·
View notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Note
About that Dollcreep oc Vanya that Viv appears to have copied:
https://static.wikia.nocookie.net/zoophobia/images/0/01/Annie.png/revision/latest?cb=20180326212915
This is Annie. She's from Zoophobia but maybe Viv zwitched her to Hazbin. Or maybe she's just a reference to ZP.
Either way when Viv first made her she looked very different: https://static.wikia.nocookie.net/zoophobia/images/e/e8/Tumblr_makl3oIc2d1rh7twdo2_500.png/revision/latest?cb=20210719182943
This is just speculation but I think Viv saw Dollcreep's Vanya and decided that's how she wanted her character to look like and yoinked the design to completely revamp Annie.
She has done this before. See Jackie's bird form in ZP: https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTLyHm-NyD_tMzrFCSJ7slbGAQjlqvDEqTT2w&usqp=CAU
And Jackie's bird form after Rio came out: https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTPjKg7EiETncC3V03GdYnOI3DdBIwjP4s5og&usqp=CAU
For comparison this is Jewel from Rio: https://static.miraheze.org/loathsomecharacterswiki/thumb/4/42/Jewel_%28Rio%29.png/1200px-Jewel_%28Rio%29.png
See? She just revamped Jackie to look like Jewel. What are the odds she's done this with other's ocs before?





Thank you for all of this. People on Twitter get a little...hostile if you don't make an airtight case every time you post, especially when it comes to things like Vivzie.
(Completely unrelated, but I love that the url on the image of Jewel leads to the "loathsome characters wiki." I really, really don't like Jewel.)
38 notes
·
View notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
Not only have the episodes been leaked since basically launch (oops!) but the devs are aware of this leak. I've been informed that Japanese PriPara tiktok has been talking about it for some time, but also someone (NOT ME I WOULDN'T DO THIS) on twitter got in trouble for posting screenshots of the leaked episodes in the official tag
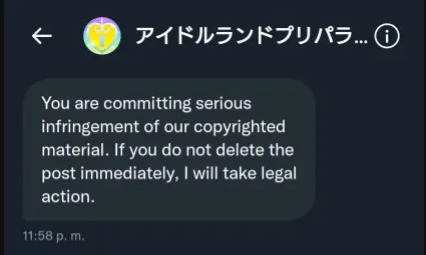
They even told them to delete it in english 😳
From what I gather the first few episodes were retrievable on the server unsecured at launch, and then a few weeks later they added the rest of them. They also had all the coords unencrypted at launch and only added encryption a few months later lol (that one update that was like 2gb if you remember it.) I specifically remember some coords from those initial data mines before it was encrypted that still haven't been added (they were recolors that I expect in the upcoming Mario Amari gacha though.)
Ultimately I think the leaked episodes are a reflection of the sorry state of the game at launch and not much more. They've patched the holes now but in this case it was too late. The leaks are on that website with the cat url that you probably know about. I don't suggest posting screenshots or direct links because the officials seem to be looking for them, but also lets be honest I think we're fine on english speaking tumblr lol just please do not go into the official hashtags on twitter with them jesus christ.
Also I'm no leak expert but like . put a spoiler tag on your images or descriptions of episodes please lol
15 notes
·
View notes