#Android 11 operating system
Text
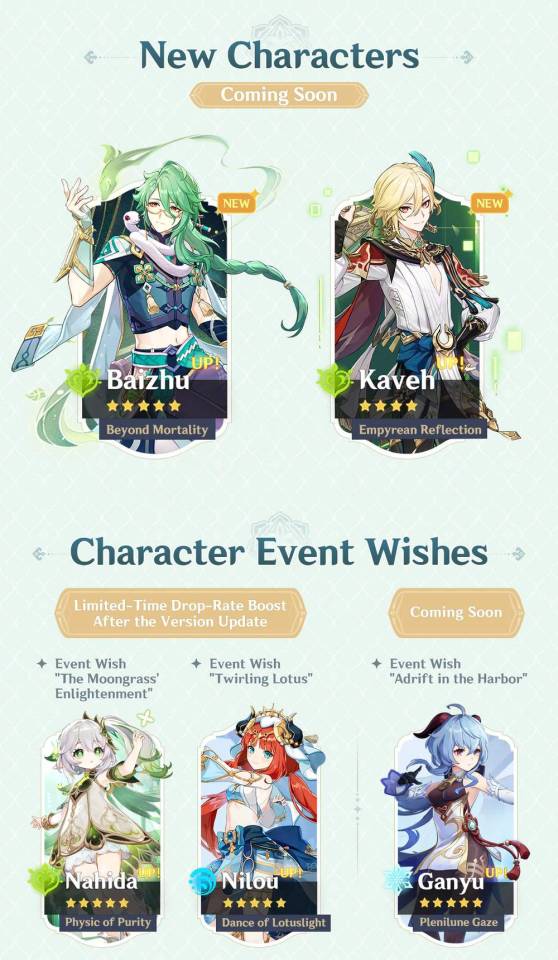
Homatics Stick HD
The most alluring feature of the Stick HD is its portability. Installing and uninstalling the dongle is a simple affair and there is very little faffing to be done. Literally plug and play!
@homatics #crazydiscostu
Where entertainment and technology converge, the Homatics Stick HD emerges as a powerful yet compact contender in the realm of Android TV streaming devices. Netflix certified, it offers the ability to deliver high-definition 1080p content and Google Assistant control at the touch of a button. This unassuming device packs a punch that goes beyond its size. Let’s take a look.
Product supplied for…

View On WordPress
#1080p HD streaming#1GB RAM#8GB storage#Amlogic S805X2#Android 11 operating system#Android TV OS#Android TV remote#Android TV streaming#Android TV streaming device#Chromecast functionality#compact streaming device#compact TV stick#entertainment at your fingertips#entertainment options#entertainment streaming#Google Assistant integration#HD resolution#high-definition streaming#homatics#Homatics Stick HD#Home entertainment#Mali-G31 GPU#multimedia streaming#multimedia streaming hub#Netflix certification#portable streaming device#review#smart TV accessories#streaming apps#streaming capabilities
0 notes
Text
-> CH. 10: EITHER FICKLE OR A FRIEND (OR A REALLY FUCKING FICKLE FRIEND)
synopsis: connor and you have a conversation. it's not uncomfortable, per se, but it's weird. connor's acting weird.
word count: 2.4k
ships: Connor/Reader, Hank Anderson & Reader
notes: me? projecting onto y/n? it's more likely than you think
HoFS taglist: @catladyhere , @foggy0trees0 , @princessofenkanomiya , @n30n-f43 , @igna4400 (if you'd like to be added to the taglist, just ask!)
HEAD OF FALSE SECURITY MASTERLIST

Connor’s sitting in his unofficially designated chair in the corner of the android autopsy room, and you’re puttering about, stealing glances at him out of the corner of your eye.
Again, the loud and prideful creature in you is baying and yowling like a dog near death. It’s telling you to kick him out – that his kind-of-aggression and kind-of-manipulation is completely unforgivable. It curses at you for your faults, for being weak for him when he feels absolutely nothing for you.
But you swallow it. You stomp it down and tell it to be quiet for now.
You pat the autopsy table. It’s surprisingly loud, and startles you a little. “Khm… if you’d like to get started on the memory transfer, you can get up on the table.”
Connor stands and moves over to the autopsy table. He sits on it and leans forward, his elbows on his knees.
You pull a couple of cables from a drawer in your desk and plug them into the side of one of your computers. When you turn to Connor, you hold up the other ends of them. “I need to plug these into your ports.”
Connor turns his head to the side and presses behind his ear. The plastic of his skin slides back, revealing two small ports.
“Jacking in. Don’t move.” You grab Connor’s jaw to steady him, then jack in the ports one at a time.
You pull away and turn to your monitor before you fully register what you just did. You’re so used to doing it out of instinct that you didn’t realize you were holding his face. You feel the tips of your ears start to burn, but clear your throat and try to shake it off.
“I’m going to sift through your memory banks,” you say without turning to look at him. “Have you had this… well, I usually call it an operation, but it’s not really one. Have you had a query run on your memory before?”
“Not by an external source,” Connor says. “But I do recall the events that happened throughout the day and process them while in standby or rest mode.”
“So you call queries on yourself?” You say. “Huh. Never heard of androids doing that before. But I guess you are a prototype.”
You put your head down and start to type. “Give me temporary access to your systems?”
A pop-up appears on your monitor:
> Android “Connor” (model RK800) giving admin access to Memory Banks. Accept access? Y/N
You click accept and multiple windows appear on your screen. You sort through them and find what you’re looking for. You quickly type:
RK800.memory-banks(location.search);
//=> ‘?Jericho’ {date=11-08-2038}
A short clip comes up after a few seconds of load time. It starts with a first-person shot of Connor looking at you (god, did you really look that worried?), then takes off and charges the deviant. He connects with the other android, and then you see it: Jericho, painted on a piece of rusty metal, just like how Connor described. Then, Connor is ripped from his connection. The video ends.
“That looks like a…” you mutter to yourself. You don’t finish the sentence.
“Looks like a what?” Connor pipes up from behind you.
You rewind the footage from Connor’s memory banks and look at it again. “I was going to say it looks like a boat, but…”
“It’s highly unlikely that the deviants are residing on a boat,” Connor says. “There aren’t many abandoned boats along the Detroit River, and certainly not one big enough to house most of the deviant androids.”
“Yeah, that’s what I thought, too,” you say. “It’s not like there’s just a freighter floating around for them to take.”
You put your head down again and put in the commands to copy the video to your desktop. After a few seconds, it’s done.
“Okay.” You pull away from the keyboard and turn to Connor. “I’m done.”
“Actually, Officer?” Connor asks.
Your eyebrows furrow. “Yes?”
He glances away, then back to you. “Do you have the equipment required to run a diagnostic on an android?”
“Uh…” You let out an exhale of air with something between confusion and disbelief. “Yeah? Yeah, I do. Why?”
“Can you run a diagnostic on me?” Connor asks.
“Wh…” Your face twists in confusion. “Why would you want that? I thought you had the operating power to run diagnostics on yourself.”
“I do,” Connor says, and it’s almost like there’s a hint of defensiveness in his tone. “But… I’d just like a second opinion.”
You nod, slowly. “Okay. I’ll… I’ll get that up and running.”
You turn back to the computer and close the running programs to make space for the ones you open. When you’re done, you move over to Connor and remove the cables after warning him. You almost cradle his head as you press your left palm to the port behind his ear, your thumb on his cheek. (The proud creature inside you whines and barks and kicks your liver at that.)
The wires from your glove quickly replace the cables that were just there a moment ago. Connor’s eye twitches once.
You look over your shoulder at the computer. It’s already automatically running the diagnostic you queued up – way too slow for your liking, might you add.
“Do you have any more books on Russian literature?” Connor asks out of the blue.
You turn back to him. “Yeah. Russians of the past loved to philosophize and think. There wasn’t much else to do when most of the year was spent below freezing for most people. Why do you ask?”
“I was just curious,” Connor says. “I want to know more about you.”
You do your best to hide the bitterness that boils up in your belly. You honestly can’t tell if this is Connor trying to make conversation or another one of his little manipulative tactics. You can do nothing but operate on blind faith.
Connor glances at you out of the corner of his eye, then looks forward. “What is Russian literature about?”
You hem and haw and collect your thoughts before speaking. “It has sobornost, metaphysics, religiosity, intuitionism, positivism, realism… but I like the ones that are more universal. The ones that can apply to everyone.”
“What do you mean?” He says.
“The books about the fear of failure, and the fear of death. How it sucks to be Russian.” You shrug with one arm, trying not to jostle Connor too much. “I mean, all national literatures are – only the name of the nation changes.”
“Hm,” Connor hums and looks down. Looks like you’ve given him something to think about for the time being.
You look over your shoulder, and the computer screen shows that the diagnostic is nearly done. When it finally finishes, you disengage the wires, the palm of your hand and fingers cool where it touched Connor’s skin.
You step back and turn to the computer, looking over the diagnostic report. Everything seems normal, and the ALL SYSTEMS NOMINAL! message at the bottom of the page confirms that.
“Yeah, you’re fine,” you say. “Not a hair out of place.”
You turn and lean back against the desk. Connor is looking down at the ground. He stays like that for a second, then looks up at you.
“Do you have books on the history of the USSR?” He asks. You internally note his (maybe unintentional) dismissal of the diagnostic report.
“Yeah.” You open a drawer and pull out the first book you see, then hold it up for Connor. It’s a book that was published in the late 1900’s, named The Reversal of Archduke Franz Ferdinand: How the Death of Agent Ekaterina Nechayeva Prevented the Collapse of the USSR.
“This one is about the Kollektiv 2.0 Disaster and how the death of Major Sergey Nechayev’s wife inadvertently prevented things from…” You think for a moment. “Well, not from going wrong, but from things getting worse.”
You look down at the book. “It’s the same butterfly effect Archduke Franz Ferdinand created, but in reverse. She saved lives by dying instead of ending them.”
“That’s interesting,” Connor says.
“Somewhat.” You put the book back and shut the drawer, then look back up at Connor. “Kind of like… you. You could’ve died killing that deviant in Stratford Tower – the station android. But you risked that to save human lives.” You narrow your eyes at him. “Why?”
Connor looks at you with those big doe eyes. He blinks and tilts his head to the side. “If the deviant succeeded in its mission of a mass shooting, it would’ve most likely killed Lieutenant Anderson, too. Like I said a few days ago, I need both the Officer and the Lieutenant for maximum efficiency when solving this case.”
“So you put your secondary mission above your first,” you say. “Because hunting deviants is your top objective, yes? So you put the safety of Hank above your primary mission.”
“I…” Connor’s LED turns yellow, then returns to blue. “Yes, I did. Because Lieutenant Anderson’s safety was compromised at that moment.”
You hum and lean back, crossing your arms. You didn’t exactly love putting him in situations like this – ones where he was forced to reflect inwardly, guided by your hand. How you both somehow rounded back to these conversations and topics was almost like a base instinct, spurred on by your primal reptilian hindbrain and his innermost motherboards.
“Why do you keep doubting my non-deviancy status?” Connor finally asks.
“I…” You exhale sharply. “I’m just not used to being around androids that are so expressive. I know it’s part of your… social relations program or your interrogation software, but still. Maybe I’m just a fool.”
You tap the front of the drawer you just shut. “Not a fool regarding books or cybernetics or polymer, but a fool regarding relationships.”
Connor looks at you weirdly. “Officer, we’re not… in a relationship.”
“Not like that!” You feel your face grow warm. “We’re two people that have met each other. By definition, we have a relationship.”
“Oh,” he says. “Well, what do you think of our relationship?”
“I mean…” You look up at the ceiling, your eyes tracing the outlines of the tiles. “I’ve always had trouble putting people into boxes. My mind seems to blur the lines between stranger, acquaintance, and friend. So most people, even friends, just default to some weird in-between.”
Your eyes return to Connor. “Are we… friends? Because I don’t know if we are. I don’t mean that in a bad way, I just… truly don’t know.”
Connor tilts his head to the side. It kind of reminds you of a puppy looking at something it doesn’t understand. “I believe so.”
You allow yourself to feel just a spark of hope, but you’re careful to not let it ignite into a Californian wildfire. You bite the inside of your lip to keep from smiling too widely. “It would be nice to be friends. But… you have to promise me something.”
“Yes?” He says.
You steel your expression. “You admitted to basically manipulating me to get into my good graces. Please, don’t do that again. I don’t want you to be fake around me. I…” You swallow thickly. The creature of pride in your belly is baying and scratching at the walls of your stomach. “I don’t want the Connor who kisses ass at every opportunity, or the one who worships the dirt I piss on. I want the real Connor. Even if… even if the real Connor is just a machine.”
Connor just stares at you, almost unblinking. His LED is circling in on itself in a steady yellow. You feel your face start to burn hot with shame and you’re just about ready to fall through the ground. Your eyes fall to the floor.
“Uh, never mind, forget I said –”
“No,” Connor cuts you off. “You’re right. I shouldn’t have done that. I’ll try my best not to… ‘kiss ass’ in the future.”
You feel a laugh bubble up in your throat and you can’t even stop it before it spills from your lips. It’s so sudden that you have to bring a hand to your mouth to try to silence yourself.
Connor looks at you inquisitively. “Why are you laughing?”
“You…” You giggle, then clear your throat. “That’s the first time I’ve heard you curse. It sounds weird coming from you. Like it’s foreign.”
“I’ve always been able to curse,” Connor says. “I just don’t feel the need to.”
“I know,” you say. “It’s just… odd, is all. I’m not used to it. Like when someone tells you the sky is blue. You have to pause for a moment, then you think, ‘Oh, of course. That’s obvious.’ Not because you didn’t know that the sky is blue, but because you’re not used to people stating the obvious like that.”
“Huh.” Connor looks down at the floor. “You talk a lot. It’s useful for my machine learning algorithms.”
You perk up a little at that. To hear Connor say that he likes when you talk, even in a completely roundabout way, is… weirdly comforting. (You can faintly feel the dry grass around the spark of hope catching fire in your chest. The proud beast stomps out the growing flames and keeps it in check to make sure it stays just that – a small, flickering spark.)
“Well, khm…” you look away and scratch your cheek. “Thank you.”
Connor nods, but doesn’t speak.
You glance at the clock on one of your many monitors. It’s nearing seven in the evening. “I should probably get going. It’s getting late.”
“It is,” Connor says.
You quickly save everything on your computer and shut off the monitors. You grab your coat from the back of your chair by your desk and shrug it on.
“I’ll see you tomorrow?” You say.
“Yes.” Connor’s eyes twitch and his LED flashes yellow for a moment. “Lieutenant Anderson has just alerted me that his request for a meeting with Elijah Kamski has been accepted. It’s set for 11:20 AM tomorrow.”
You nod. “And I’m assuming Hank will swing by to pick me up.”
“Yes,” Connor says. “I’ll see you tomorrow, Officer. Have a good night.”
You smile at him, a lightness in your chest. “You too.”
#riptide writes 🌊#head of false security#dbh connor x reader#connor rk800 x reader#rk800 x reader#connor x reader#detroit become human#dbh connor#dbh rk800#dbh x reader#detroit become human x reader#dbh connor x you#connor rk800 x you#rk800 x you#connor x you#dbh x you#detroit become human x you#connor rk800
134 notes
·
View notes
Text
"A Parade of Providence" Version 3.6 Update Maintenance Preview

Dear Travelers,
Our developers will soon begin performing update maintenance. While the update maintenance is in progress, Travelers will be unable to log in to the game. Please take note of the update time and schedule your game time accordingly.
After this is complete, the game will update to a new version. We recommend that Travelers install this update over a Wi-Fi connection.
〓Update Schedule〓
Update maintenance begins 2023/04/12 06:00 (UTC+8) and is estimated to take 5 hours.
〓How to Update Game Client〓
PC: Close the game, open the Genshin Impact Launcher, and click Update.
iOS: Open the App Store and tap Update.
Android: Open the game and follow the directions on-screen.
PS5™ and PS4™: Highlight Genshin Impact from the Home Screen, press the OPTIONS button and select "Check for Update."
Please do not hesitate to contact Customer Service if you encounter any issues installing the new version. We will do our very best to resolve the issue.
〓Compensation Details〓
Maintenance Compensation: Primogems ×300 (60 Primogems per hour the servers are down)
〓Scope of Compensation〓
Maintenance Compensation: Travelers who reach Adventure Rank 5 or above before 2023/04/12 06:00 (UTC+8).
Please claim before the end of Version 3.6.
Our developers will distribute compensation to Travelers via in-game mail within 5 hours after the update maintenance is finished. The mail will expire after 30 days, so don't forget to claim the attached compensation in time.
For more update details, including bug fixes and other compensation details, please see the Version Update Details notice to be posted at 2023/04/12 07:00 (UTC+8).
〓Update Content Overview〓



After the Version 3.6 update, iOS-supported devices will be updated.
〓Minimum Specifications and Recommended Specifications〓
▌Android:
● Supported Devices
Must be compatible with:
ARMv8-A 64-bit architecture
Non-PowerVR architecture GPU
RAM: 4 GB or more
Operating System: Android 8.0 and above
Storage Space: 30 GB of available storage space
● Recommended Specifications
CPU: Qualcomm Snapdragon 845, Kirin 820, or above
RAM: 6 GB or more
Storage Space: 30 GB of available storage space
▌iOS:
iPhone 8 Plus
iPhone X
iPhone XS
iPhone XS Max
iPhone XR
iPhone 11
iPhone 11 Pro
iPhone 11 Pro Max
iPhone SE (2nd generation)
iPhone 12
iPhone 12 mini
iPhone 12 Pro
iPhone 12 Pro Max
iPhone 13
iPhone 13 mini
iPhone 13 Pro
iPhone 13 Pro Max
iPhone 14
iPhone 14 Plus
iPhone 14 Pro
iPhone 14 Pro Max
iPad Air (3rd generation)
iPad mini (5th generation)
iPad Pro, 10.5-inch
iPad Pro, 12.9-inch (2nd generation)
iPad Pro, 11-inch (1st generation)
iPad Pro, 12.9-inch (3rd generation)
iPad Pro, 11-inch (2nd generation)
iPad Pro, 12.9-inch (4th generation)
iPad Pro, 11-inch (3rd generation)
iPad Pro, 12.9-inch (5th generation)
iPad Pro, 11-inch (4th generation)
iPad Pro, 12.9-inch (6th generation)
iPad Air (4th generation)
iPad (8th generation)
iPad mini(6th generation)
iPad (9th generation)
iPad Air (5th generation)
iPhone SE (3rd generation)
iPad (10th generation)
Storage Space: 20 GB of available storage space
Supported Operating System: iOS 11.0 or above
(Bluetooth controller support requires iOS 14 or above)
▌PC:
● Minimum Specifications
Operating System: Windows 7 SP1 64-bit, Windows 8.1 64-bit, or Windows 10 64-bit
Processor: Intel Core i5 or equivalent
RAM: 8 GB
Graphics Card: NVIDIA® GeForce® GT 1030 or better
DirectX Version: 11
Storage Space: 50 GB of available storage space
● Recommended Specifications
Operating system: Windows 7 SP1 64-bit, Windows 8.1 64-bit, or Windows 10 64-bit
Processor: Intel Core i7 or equivalent
RAM: 16 GB
Graphics Card: NVIDIA® GeForce® GTX 1060 6 GB or better
DirectX Version: 11
Storage Space: 50 GB of available storage space
If your device specifications are too low, the game may fail to install, fail to start, display black screens, experience freezing, or demonstrate other technical issues.
〓Adjustments & Optimizations〓
● Genius Invokation TCG
Adjusts the description of Combat Status "Sparks 'n' Splash" generated by Character Card "Klee" in Genius Invokation TCG.
The original description was: "After your character uses a Skill: Deal 2 Pyro DMG to your active character. Usages: 2."
The adjusted description is: "After a character to which Sparks 'n' Splash is attached uses a Skill: Deals 2 Pyro DMG to their team's active character. Usages: 2."
Adjusts the description of Talent Card "Sin of Pride" in Genius Invokation TCG.
The original description was: "If a friendly Electro character has Crowfeather Cover attached, their Elemental Skill and Elemental Burst deal +1 additional DMG."
The adjusted description is: "When Kujou Sara is active and has this card equipped, all allied Electro characters with Crowfeather Cover will deal +1 additional Elemental Skill and Elemental Burst DMG."
Adjusts the number of Elemental Dice required for the Event Card "Katheryne" in Genius Invokation TCG: the required dice has been reduced from 2 Elemental Dice of your choice to 1.
Adjusts the effect of the Elemental Burst "Nereid's Ascension" generated by Character Card "Sangonomiya Kokomi" in Genius Invokation TCG.
The original effect was: "Deals 3 Hydro DMG. This character gains Ceremonial Garment."
The adjusted effect is: "Deals 2 Hydro DMG. Heals all allied characters for 1 point. This character gains Ceremonial Garment."
Adjusts damage dealt by the Combat Status "Rainbow Bladework" generated by Character Card "Xingqiu" in Genius Invokation TCG: "Deal 2 Hydro DMG" is now adjusted to "Deal 1 Hydro DMG."
Adjusts the number of Elemental Dice required for the Equipment Cards "Blizzard Strayer," "Heart of Depth," "Crimson Witch of Flames," "Thundering Fury," "Viridescent Venerer, "Archaic Petra," and "Deepwood Memories" in Genius Invokation TCG: the required dice is now adjusted from 3 Elemental Dice of the same Elemental Type to 3 Elemental Dice of your choice.
Optimizes some of the icons in Genius Invokation TCG.
When Travelers claim rewards through the Genius Invokation TCG Player Level or TCG Player's Manual, they can still claim rewards despite said rewards exceeding the cap. The rewards will be sent to the Inventory directly.
After the cards in the Card Shop are sold out, if there are other ways to obtain the card, it will be displayed on the Card Details interface.
You will receive 1 Proficiency point after completing a Guest Challenge in Genius Invokation TCG of each week for the first time. (You will not receive Proficiency points for repeated Guest Challenge victories prior to this update.)
Removes the margin restrictions to the left and right sides of the gaming interface when players play Genius Invokation TCG on mobile devices.
Improves relevant Genius Invokation TCG controller operations:
During the Roll Phase, players can now hold the selection button and push the left joystick to select multiple dice.
The button to end the turn will also be displayed even without hovering the cursor.
You can now switch between your Hand and Character Skills by pushing the joystick.
● Audio
After Version 3.6 is updated, the character "Verdant Strider" Tighnari (Dendro)'s VA will be updated.
Optimizes the English and Korean voice-overs of some characters, and fixes issues whereby the Chinese voice lines failed to play normally in Profile > Voice-Over.
Optimizes the Korean, English, and Japanese voice lines for some quests, and fixes inconsistencies between the Chinese voice-overs and text for certain quests.
Optimizes the English and Japanese voice-overs for certain items and creatures.
● System
Adjusts the avatar images of some enemies.
Removes the restrictions on the addition and moving of some Furnishings for the placement of Custom Furnishing Sets in the Serenitea Pot.
The camera function in the Paimon Menu can no longer be used when the character is diving.
*This is a work of fiction and is not related to any actual people, events, groups, or organizations.
"PlayStation", "PS5", "PS4", "DualSense", "DUALSHOCK" are registered trademarks or trademarks of Sony Interactive Entertainment Inc.
#genshin impact#genshin impact updates#official#genshin impact news#genshin impact 3.6#lots going on here#they're finally replacing tighnari's va though!!
103 notes
·
View notes
Text
07/11/2024 - Actual Play Report
Xenosphere I
NOTE: Usually in Industrial Fishing Simulator player character’s are called ‘Survivors’ and scenarios/adventures are called ‘missions.’ But I won’t necessarily use that language here.
Also I’m not trying to make this like the most perfect play report essay in the world, but I am trying to be somewhat thorough–so–know that.
Xenosphere I - Recording 1 - Introduction
Part I: Summary
Some time in the distant far future, when humanity has encountered a variety of extraterrestrial species and has spread among the stars, an ancient artifact is discovered on the oceanic planet Kestrasi Meridia (which is renamed from TOI-1452b, an actual possible exoplanet in the Draco Constellation). This artifact proves deeply mysterious, covered in strange writing, and is sending out a signal to a location deep underwater on Meridia.
A team of Survivors, made up of language, archaeology, and biology researchers, as well as nautical explorers is assembled to investigate the signal emanating from the strange artifact. These are the players of the game Xenosphere I for Industrial Fishing Simulator. They are sent on this mission from the Ixta-B87 research station by Dr. Helene Lazara and have been assigned the following roles:
Crew Roles and Directives:
The Concierge (played by Spencer) - Captain (must be filled)
Report in with Dr. Helene Lazara or check for any messages in the office.
Sir Barnaby Stephus III (Justin) - Xenolinguist
A few days ago, you requested some final analyses on the tablet’s hieroglyphics. Check the lab computer for any readout results.
deb (Emma) - Xenoarchaeologist
You’ve been researching the chemical composition of the artifact in relation to any compounds native to the planet Meridia. Your most recent test results should be available in the lab.
Shakes (Hannah) - Astrobiologist
Distract your peers from their tasks. (1) by alerting them of an incoming object of large size on the sonar computer; (2) destabilizing or sabotaging equipment; (3) lying. Or distract your peers from being suspicious of you by engaging in seemingly normal tasks for your role such as surveying the computer systems or asking for diagnostic information from NESSI.
You are a saboteur, a double agent–maintain absolute secrecy from your peers. You’ve received your orders from your implanted radio transceiver behind your ear. “Disable the emergency protocol system and sabotage docked submersible in Deep Search IX. Retrieve the Dialect Cube, designated Synta in the Xenosphere 45.909 W, -206.784 S. Assure you are the sole survivor. Press to alert.”
You are working with an organization known as the Inquisitorium who is operating in deep secrecy within the Neb Corp, working to sabotage their efforts to exploit ancient alien technology by capturing it for themselves. You do not know what a Dialect Cube or what a Xenosphere is.
You have an Inquisitorium contact, an android called ‘Pann.’
You can press your radio implant behind your ear to ping the Inquisitorium contact and will receive rendezvous information or other communications
You cannot communicate back other than to press your implant button twice for “yes” and three times for “no.”
Patback (Alex) - Nautical Technician
That power outage was strange. You need to check on the engine room and power supply.
Assure that the docked submersible craft in the docking bay is secure and available for use.
Pancake (Zoe) - Computing Officer
You kept it a secret from your fellow crew, but you touched the tablet with your bare hand and cut your index finger on its extremely sharp edge. You stopped the bleeding, but think you might have an infection. No one is allowed to touch the relic without safety equipment due to its radioactivity, and you need to check on the progress of your infection quickly.
Allegra (Bee) - Medical Officer
Prepare the high yield pressure suits for all crew found in the store room and assure all crew have oxygen tanks.
Check on the vitals of your crew mates. You might want to grab a bioscanner from the clinic.
Their underwater journey commenced aboard the research submarine Deep Search IX and travel had proceeded for several days for some several hundred nautical miles when a sudden power surge occurred. During the surge, the lights went dark, the entire crew miraculously went unconscious and the vessel descended rapidly by about 3200m near to the depth of the mysterious signal. When they awoke, they found that only a few minutes had passed and they went about their tasks as well as investigating the power surge.
The Captain of the submarine, a Khardimon called The Concierge (Spencer) went to the office and found a voice message from Dr. Helene Lazara which she had missed from last night.
Xenosphere I - Recording 2 - Message from Dr. Lazara
The voice message indicated that a power failure at another research station on the planet had blacked out communications and that the Captain should call Dr. Lazara soon to be briefed about a “situation.” Dr. Lazara also mentioned that she believed the artifact might be a key.
Meanwhile, Allegra (Bee) immediately went about collecting high yield pressure suits and oxygen tanks for the entire crew, but was intercepted by Pancake (Zoe), who revealed a strange wound on her hand to Allegra. Allegra examined the wound and found that the inside of the laceration was beginning to crystalize. Under a microscope, it appeared that the crystallization was growing out from the wound and the edges of the crystallization were rotating like saws, chewing through Pancake’s flesh and churning out crystal formation.
In the lab, Sir Barnaby (Justin) received the below readouts of a linguistic analysis of the glyphs that were found all over the artifact, which yielded strange and cryptic results. This was clearly some kind of alien language which was connected somehow to Khardimons, the enamel-based magnetically-sensitive alien species which appeared on Earth centuries ago. Also in the lab, deb (Emma) found a material analysis of the artifact which found a match. The artifact appeared to be composed of several chemical compounds: hydroxyapatite and fluorapatite crystals, and compounds from local corals. This meaning, the tablet was made of the teeth of some kind of creature in addition to the local coral component.
At this point, Patback was also in the engine room, where he discovered that the power surge which briefly knocked out the Deep Search IX had nearly drained all of the power cells in the submarine which would soon go into emergency power failure. Patback immediately changed out the power cells for fresh ones and then assessed the submarine’s auxiliary submersible in the lower docking bay. He surreptitiously packed himself some survival gear into the submersible (which can only seat 2) and went to join the others, but was briefly followed by Shakes who seemed to be checking out the area of the docking bay and cargo hold.
During this time, Shakes was receiving transmissions to their radio implant from an organization known as the Inquisitorium. Shakes was being ordered to distract the crew from their objectives but also to get to the signal first and retrieve an important relic for the Inquisitorium, betraying their crew mates.
At the control room, the Captain (The Concierge - Spencer) called back Dr. Lazara and a strange pick-up occurred in which most of the crew heard the following:
Xenosphere I - Recording 3 - Alien Transmission
At the end, the receiver was shot and a tracking signal alert popped up on the console, indicating that the Deep Search IX was now being tracked by an unknown source. Ixta-B87 station was downed. With some quick thinking, the computing officer, Pancake, managed to dislodge the tracking signal and the crew made their descent to the complex, where they were met by an alien structure mounted into the side of a geothermal vent some 3200 or more meters below the surface of Meridia’s dark waters.
This complex seemed to have an entrance protected from the water by a deep magenta energy field which the Survivors were able to pass through in their scuba suits unharmed. They entered into a large chamber where they encountered a closed impassable energy field and an access panel of sorts with a slot just the size of the ancient table they’ve been carrying. However, a little while before leaving they had just made the agreement to leave the tablet on their ship so they had to send a few people back to retrieve it before they were able to unlock the energy field and proceed further into the complex.
The next chamber was very large, containing two dais near the entrance which blazed with blue flames that smelled lightly of sulfur and at the opposite end two one-eyed statue-like figures who bared strange alien faces as seen in the image below (slightly resembling the Khardimon aliens). This room also had two magenta energy field doors and one green energy field door. But the Survivors didn’t have too much time to think before the statues began to wake up, chittering at each other before attacking the Survivors.
A pith collector head

A crappy map of the complex. (1) Entrance, (2) Trophy Hall, (3) Holding Tank, (4) Xenosphere

A somewhat fraught and desperate battle raged on for some time, the statue-like figures (pith collectors) using strange Khardimon magics to gain various upper hands, but the Survivors discovered that by coating their various weapons in the blue flame from the dais they could deal devastating attacks to these creatures. During the battle, there were losses, however. While it was Pancake who helped deal a death blow to one of the creatures, the other began to absorb its shattered friend and in the process melted Pancake’s mind, killing her. Additionally, the Captain (The Concierge) attempted to cast a spell but failed, causing a paradox from the Whoops! Table which resulted in her being swallowed by a dark vortex and being jettisoned into deep space thus removing her from the game. Ultimately, the remaining Survivors destroyed the last creature and were able to recover themselves.
However, during combat, Patback had managed to wander off through the green unlocked energy field into the complex’s trophy hall where he discovered many strange relics including a great slate-black khopesh and a fragment of an enormous glass-like dragonfly wing with a single watering humanoid eye in its center which kept Patback in a catatonic state as he stared at it. Luckily, he was rescued by his companions who would help to study this strange chamber, revealing at the end of the hall–a mural depicting an ancient Khardimon raising a khopesh above its head and holding the head of a slain victim in its other hand. An inscription of text matching that from the xenolinguist’s analysis of the table was also carved into the mural on removable stone cartouches which thus began the puzzle that would end the game.
Effectively, to summarize, the Survivors had to take clues from the analysis of the tablet, translating letters they learned there into words from an alien language, piecing together similar words into like meanings until eventually they could translate the puzzle in the final room of the complex–the Xenosphere, a large gyroscopic holding tank for an item called the Dialect Cube.
In one room, the trophy room with the alien mural, the Survivors found the word for liar/lies, and in another room, a strange room where they found a glass sarcophagus where a seemingly human woman wrapped in vines was entombed alive, they found the word for truth. Then in the Xenosphere, placing the cartouches of the words lies and truth on either end of the scale there would balance it and placing the word for balance found also in the mural room in the slot on the Xenosphere’s control panel would unlock the device.
When the Survivors had finished their puzzle, the Inquisitorium had arrived at the complex, surrounding the Survivors, handing over a large carbine to the saboteur Shakes and taking the Dialect Cube. The game ended with the remaining Survivors surrounded at gun-point, Shakes with the Dialect Cube in hand, and a mysterious organization at the forefront.
Part II: System Check, Play-Report
This game was very fun, but also very complicated. I knew it was going to be very complicated going into it. Mostly because of the xeno-linguistic puzzle I had devised to end the game and unlock the end of the “dungeon.” But, as soon as Justin (who played Sir Barnaby the xenolinguist) got his hands on the readout prop I had made of the alien language, he began working on deciphering it right away, which I would bet saved the game about an hour when they actually got to the point where they were gaining more clues for the puzzle. I was worried the entire week prior to playing that I had created a puzzle that was wayyyyy too hard for a reasonable person to solve within the one-shot TTRPG setting, but they did it. And using the system I arranged within the game, they paid as a team, 50 Lore points to receive one hint from me, and of course, received a little bit of guidance on the structure of the puzzle which I felt was not really something that helped them solve it but rather helped them to understand how to think about it.
Overall, I thought it was a fun experience. I had fun writing this game. I got to play with my linguistics chops which I always get a lot out of, and some of the repeat players like Bee (Allegra) and Emma (deb) said that they felt this was the best FishSim game yet and as newbies to TTRPGs in general felt like they got into their characters easier and had a more full roleplaying experience which made me very happy of course. Justin (Sir Barnaby) is a person that I’ve been playing D&D and other TTRPGs with for years and years and years–since the beginning and it was an absolute pleasure to have him and to see him immediately dive into the linguistics puzzle.
I am also glad that I got to have Zoe (Pancake) and Alex (Patback) join us as first timers to any TTRPG ever. It's been so great that FishSim is getting to see so many first time TTRPG players. RIP to Pancake who was absolutely eviscerated by the pith collector using the Eyes of the Architect ability, but it is what it is and Zoe had to leave anyway. Alas.
This is also the first FishSim game where we’ve gotten a lot of use out of the Whoops! Table which is rolled upon whenever a spell fails to cast. Unfortunately, it was mostly Spencer (The Concierge) who failed to cast any spells and died because of it, but in this game casting spells is extremely high risk, extremely high reward and I always warn all my players prior about this.
Once again, I am thinking of things to change mechanically in the game. I am thinking that Will is definitely not a necessary statistic separate from Stress. I am still pondering replacing it with Aware/Perceive or something similar. I think that could be beneficial. On the matter of spells–I am wanting to make spells a bit more sci-fi flavored so I’ve decided to rename them Compounds and I have decided that they are composed of ingredients in combinations of three which are combined in a device which helps a Survivor cast the Compound. When a failure occurs, a paradox occurs, and one must roll on the Whoops! Paradox Table to see what the resulting failure is. Thanks to Bee, I now have a list of 300 Compound recipes for these created by her swiftly programmed randomizer. So, I’ll be working on that for a long while, I’m sure.
Also thinking about Occupations as distinct from Species. Currently, FishSim only uses the term Occupation which refers to whether your character is Human, Android, Simulacrum, or one of three alien species. But I am wondering if it might be interesting to have Occupations as opposed to Species. That being said, it is still extremely helpful that every game starts with each character and player choosing a role on the ship and me sending them their personal directive. That really gets the game rolling and seems to be pretty fun for everyone prior to regrouping.
Part III: Personal Note
I put a lot of effort into Industrial Fishing Simulator, truly because I think it's fun to make my own TTRPG and I think it's fun to get my friends together in a room, play a silly sci-fi alien game, eat food, and gab. But I am also very grateful that people enjoy the stories I tell and see me as a good storyteller. And I’m glad I can make some of my friends’ very first TTRPG experience a good and memorable one.
I’ll be tabling Industrial Fishing Simulator for a couple months so I can edit in some of the changes I want to make but I’ll be back soon!
Thanks to everyone who reads these little play reports and who plays the game!
~ clio <3
4 notes
·
View notes
Text
Skip to content
Simplified Privacy
Menu

Google’s Surveillance: The Shocking Truth
Google is the opposite of privacy. They maliciously collect data from you in the following ways:
The Sources for this article can be found here.
1) Saving all your Google searches, tied to your identity across devices [1] [2] [30]
2) Reading all your emails. Even if you don’t use Gmail directly, but you’re sending email to someone who does. [5] [6]

3) Saving all your web traffic if the website uses Google Ads, Captchas, or Analytics (and over 85% of all websites use some of their services). Even if you aren’t signed in to a Google account, and you’re using a VPN, they can still use past cookies and browser fingerprinting to identify you. [35] [1] [25] [26]
Google’s reCaptcha fingerprinting includes mouse movements, response time, timezone, screen dimensions, IP address, and any cookies. ReCAPTCHA uses the google.com domain instead of one specific to ReCAPTCHA, which allows Google to receive any cookies you have directly, instead of the website you’re visiting. [35] This concentrates the vast majority of all traffic data in the hands of a single company, which can then be used to de-anonymize users.
4) Everything you do in Google’s Chrome Browser is recorded, including even how long you are idle on a page. [7] [8]

5) Tracking and Saving your physical location, via Android’s GPS and Wifi triangulation. [12] [13]
Even if you turn location features off or set the phone to airplane mode, it still saves your location via Wifi triangulation, which is the process of pinging nearby Wifi hotspots to identify where you are. [9] [10] [11] Wifi triangulation can figure out your real location, even if you have a fake IP address from a VPN. [14]

As intelligence expert and ex-law enforcement Michael Bazzell says, Google is one of the first places law enforcement goes to for information because Androids track everyone’s location so accurately. Bazzell points out that even if you’re not directly involved in something, just owning an Android that was near it, can get you involved in answering police questions. Bazzell’s experience serving in law enforcement and intelligence motivated him to completely cut Google out of his life even though he’s doing “nothing wrong”. [11]
6) Keeping track of who you know to identify new phones or email accounts as you.
Rob Braxman
Privacy expert and phone operating system designer Rob Braxman points out that, by synching everyone’s phones’ contact lists and who they are physically standing near, Google (and therefore governments) can identify unknown devices or email accounts as you. [30] [31] [32a] Braxman further points to publicly available websites made by Google’s Jigsaw division and their partner Moonshot CVE, which openly sells services to governments to track and manipulate search results for targeted users. These users targeted by Jigsaw & Moonshot CVE’s government clients have their search history, location, and identifying fingerprint stored in a database. [32b]
7) Recording and saving audio of your private conversations [16] [17] [18]

Google’s Android has the microphone constantly recording and saving your intimate personal conversations against your wishes for their profit and power. As an extensive academic study of tech patents by Consumer Watch Dog points out, Google will claim this is only to find out if you said the words “Google Assistant,” but yet they have publicly filed patents to scan audio conversations and any available visuals on a variety of home smart devices to identify who is speaking, what you’re interested in, and what you’re doing for the purpose of targeted advertising. [15]

Tracking what you say, what you like, when you sleep, and even when you go the bathroom, goes well beyond Google Assistant helping you do a quick search and would instead be considered an all-inclusive surveillance. [15]
In addition, they’ll allow 3rd party apps to record you without your knowledge because of poor permissions control. As University of California Santa Barbara cybersecurity researchers presented at a BlackHat European conference, 3rd party apps like Silverpush can play high frequency audio, which is invisible to the human ear, on another device like a television ad or mall kiosk. Then your phone’s mic picks up the frequency, to rat out your real identity or location. [34]

Silverpush’s advertising system is embedded into many “free” apps on the Google Play Store. These doctoral researchers warned of the dangers this presents by being connected to wide-spread platforms like Google Ads. To demonstrate this, they played video of their lab experiment, which de-anonymatized a laptop through Tor Browser, because of an Android’s mic next to the laptop’s speakers, which was signed in to a Google account. [34]
Is the Data Sold?

Google has marketing propaganda which claims that they are merely selling advertising space on your devices and not selling the data itself. However, this claim is misleading in a number of ways.
First, not only is advertising sold by demographics or interests, but in addition, Google also allows its advertising customers to target users by name, email, or device ID and reach them almost anywhere. [1] So advertisers can target you specifically and then serve you anything on your specific device by name.

Second, while it’s true that Google technically doesn’t sell your actual name to the advertiser, when your device interacts with an ad, the third party advertiser can easily use your IP address, cross-site cookies, and/or browser fingerprinting to identify you. For example, suppose an advertiser runs an ad for an ebook on how to get out of debt. The advertiser could collect the IP addresses of anyone who clicks it, and so they’d know whose indebted.

“I think the big problem is that we give much more data to Google than it needs,” said Guillaume Chaslot, former Google engineer who worked on YouTube’s recommendations algorithm. [4a] Chaslot’s first-hand experience with Google’s spyware and manipulation inspired him to create the non-group AlgoTransparency.org, which openly says in it’s manifesto, “algorithms don’t have your best interests at mind”. [4b]
Play Store and Chrome Extensions Leak Data

Third, the Google Play Store and their Chrome Browser Extension Store leak application and user data directly to the app’s developers. This is sensitive private information, and these third party app developers are NOT carefully vetted, as almost anyone can put an app in the Google Play or Chrome Extension Store with minimal screening. Examples: [21] [23] [24]
Mental Outlaw
“Mental Outlaw” is a cybersecurity Youtube video influencer who is constantly having his videos about torrents flagged by Google as “dangerous content”. He points out how ridiculous this is because Google does so little to stop real dangerous content. One of the numerous examples he’s given is the Chrome webstore featuring extensions that are malicious hacking malware, which does URL injections to force online shoppers, without their knowledge, to use the malware creator’s affiliate links when they shop online. [22b] These 5 popular extensions got over 1.3 million downloads, which got the attention of McAfee Labs, the research department of the respected anti-virus company.

From McAfee Labs’ articulate research, this is huge security risk because not only is your personal data, like name and location, sent to malicious actors, but the attacker can forward the URL to any site they want. So you might think you’re going BestBuy.com, but it’s really the attacker’s bullshit site to get your credit card info. [22b]

Youtuber Mental Outlaw points out how ludicrous it is that not only did Google allow 1.3 million people to download these extensions, but they have featured status on the Google Chrome store. [22a] And not only does Mental Outlaw find similar malware in the Android Play Store, but Google has changed how apps disclose permissions to remove themselves of liability. Starting in mid-2022, Google has the app developers themselves disclose what permissions the app uses, so Google does not have to do any research. This is a conflict of interest, since app developers are self-reporting what information they get access to, and the end user may not properly be able to evaluate it. [19] [20a]
Sell it via Cookies

Google’s defense to these types of criticisms has always been that they don’t “sell your data” directly. But as laid out in research from the tech-savvy lawyers at the Electronic Frontier Foundation, Google allows advertisers to connect their cookies with Google’s in order to process data on the customer. This process is called “cookie matching” and essentially allows Google to sell the advertiser your information through a cookie. [1]
In the European Union, if Google were caught selling this data directly, it would be illegal. [27] [28] [29] So instead Google finds sneaky work-arounds such as the cookie matching, which allows them to appease the regulators and make statements like “we don’t sell data, we just use the data.” [1]

Conclusion

The more influence that Google has in our society, the more difficult it becomes to avoid their fingerprinting. If every website has a Google Captcha and everyone you talk to demands you talk to them on Gmail, then Google has become the gatekeeper for overseeing all human behavior. They can use this power to influence who sees your messages and what information you are able to find.

By using Gmail or Google Docs, you’re forcing and enabling Google to fingerprint your loved ones or friends. Even if you think you’re doing nothing illegal, you assume that Google will give you and those you care about an equal opportunity for your business to thrive. They can reduce Google’s search traffic to your website, or bounce your emails to potential employers or customers. They can buckle your business at the knees if they think it fits its agenda and by giving them so much information you’ve completely surrendered your freedom.
Well what is their agenda?
In our next article, we’ll discuss Google’s censorship ability to shape society and how affects you.
The Sources for this article can be found here.
Related Articles
Big Tech Abuses Medical Privacy
February 25, 2023 No Comments
In the US, your medical records are protected by HIPAA but your internet medical browsing history on websites like WebMD is NOT. That is the
Read More »
Browser Fingerprints Lead to Price Discrimination
February 25, 2023 No Comments
Some people mistakenly believe they do not need to worry about online privacy because they have “nothing to hide.” In reality, your digital identity expressed
Read More »
Avoid this Monero Vulnerability
February 25, 2023 No Comments
We love Monero. It’s our favorite and number one recommended cryptocurrency. However, it does not offer completely perfect anonymity under all circumstances because there are
Read More »
How to Reduce Google’s Control Over You
February 25, 2023 No Comments
There’s a huge number of steps you can take to reduce Google’s power and influence over your business and personal life. You would get a
Read More »
Google Censors Freedom
February 25, 2023 No Comments
This article presents evidence that Google promotes an agenda of centralized control through systematic censorship on its search, email, video, app store, and ad platforms
Read More »
Session username: Simple / Signal #: +855 68 504 905
Web 3 on IPFS: SimplifiedPrivacy.x
Tor Onion: privacypkybrxebcjicfhgwsb3coatqechwnc5xow4udxwa6jemylmyd.onion
Nostr Public Key: npub14slk4lshtylkrqg9z0dvng09gn58h88frvnax7uga3v0h25szj4qzjt5d6
[email protected] / @Matrix:SimplifiedPrivacy.is
13 notes
·
View notes
Text
It's wild to me how there are no professional options for some operating systems...
Like, you buy Windows 11 professional for your office, and it still automatically installs fucking candy crush, tiktok and the xbox game bar.
You buy Android work phones for your employees, and you can't even get rid of facebook or whatsapp, you can only disable them.
2 notes
·
View notes
Text

Future Air Combat System (FCAS) and the Military Internet of Things
Fernando Valduga By Fernando Valduga 11/22/2023 - 20:35in Military
The FCAS Air Combat Cloud (Air Combat Cloud) will bring real-time intelligence to the forefront, taking advantage of the network capabilities of different aircraft and platforms. Innovations in Artificial Intelligence (AI), big data processing and cybernetics will help make defense a truly collaborative mission.
Europe's Future Air Combat System (FCAS) will see next-generation manned jets flying alongside remotely piloted unmanned aircraft carriers of various sizes. These assets will be part of a fully interconnected "system of systems", based on open architectures, which will allow the integration of other existing platforms, such as the A400M or the A330 MRTT tanker plane. At the heart of this complex system will be the Air Combat Cloud, which will allow these platforms to work together.

But what exactly is an air combat cloud? As FCAS Combat Cloud product solution leader at Airbus, Ignacio Rosell often asks this question.
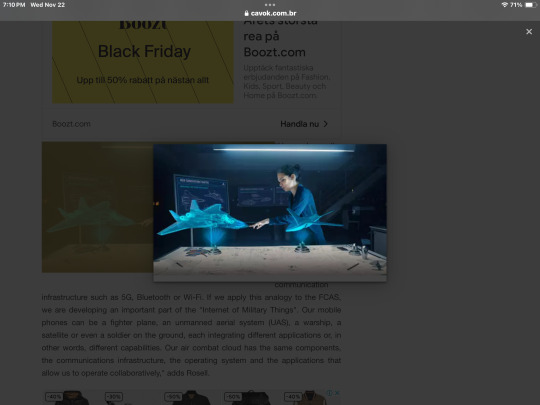
“How does the Android ecosystem work? We have an operating system that allows the integration of applications from different parts, and all this is supported by a communication infrastructure such as 5G, Bluetooth or Wi-Fi. If we apply this analogy to the FCAS, we are developing an important part of the "Internet of Military Things". Our mobile phones can be a fighter plane, an unmanned aerial system (UAS), a warship, a satellite or even a soldier on the ground, each integrating different applications or, in other words, different capabilities. Our air combat cloud has the same components, the communications infrastructure, the operating system and the applications that allow us to operate collaboratively," adds Rosell.
Launched by France, Germany and Spain, and with Airbus, Dassault Aviation and Indra as national industrial coordinators, the FCAS is one of the most important European defense programs of the coming decades. In a context of growing global instability, the objective of the project is nothing less than to design an air defense system that protects Europe, while strengthening its strategic autonomy and technological sovereignty.
Airbus leads the Combat Cloud pillar, with Thales and Indra as main partners. This is one of the seven areas of next-generation FCAS technology (see the infographic on the side), led at Airbus by Marc Paskowski.

It will provide a common situational awareness, capturing, sharing, merging and instantly processing large amounts of data from all connected manned and unmanned platforms, reliably, and transforming that data into actionable information, taking advantage of constantly evolving learning technologies. "The concept based on the cloud in flight is that all elements must constantly interoperate with each other to form a cohesive system that is informed as one and fights as one," says Paskowski.
"Our 'operating system' will need to be opened to accommodate ready-to-use and tailored applications, such as manned and unmanned teams, from Airbus or any other industrial partner. It will be an evolutionary process, with new applications, such as new aerial platforms, being integrated along the way," says Rosell. "Our business model around the Combat Cloud will not be unique. An area such as satellite connectivity could be offered as a service, while an 'app' part of an aircraft's mission system could be sold as a product,” he adds.
The development of intermediate solutions as part of this "internet of military things" should allow customers to use various levels of cloud capabilities and remote operators long before FCAS became operational in the 2040s. For example, Airbus has already carried out the first successful launch and operation in the world of a Remote Carrier flight test demonstrator from an A400M in flight.
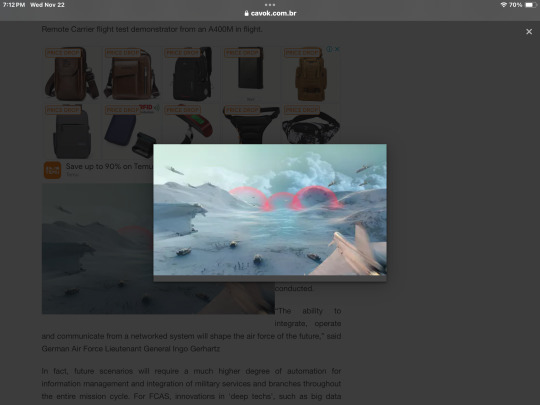
Based on this incremental approach, the air combat cloud will be the digital watershed in the way military operations are conducted.
“The ability to integrate, operate and communicate from a networked system will shape the air force of the future,” said German Air Force Lieutenant General Ingo Gerhartz
In fact, future scenarios will require a much higher degree of automation for information management and integration of military services and branches throughout the entire mission cycle. For FCAS, innovations in 'deep techs', such as big data processing, artificial intelligence and cybernetics, will provide the advanced intelligence of the cloud, allowing, for example, the distribution of Command and Control (C2) functions, including to the pilot in his fighter. and provide key stakeholders in a mission with all relevant information in real time. "This will give Air Force decision makers an unprecedented level of awareness," says Paskowski.
But with great power comes a great responsibility. With the growing dependence on artificial intelligence on everything we do as "digital citizens", and the use of platforms such as ChatGPT and its impact on the workplace, the integration of AI at the heart of FCAS Air Combat Cloud presents new challenges. Questions such as 'to what extent will the system support the decision-making process?' or 'What are the ethical criteria that can be applied to the use of this technology?'

Control or be controlled: that's the question
In order to anchor ethical issues and legal principles in the FCAS project, Airbus and the Fraunhofer Institute came together in 2019 to launch a joint expert committee on the responsible use of technologies. It brings together interested parties from the German Air Force with universities, research institutes and a broad group of foundations, specialists in social sciences and engineering science design.
Based on this guidance, within FCAS Air Combat Cloud, AI will provide analysis of complex situations during multi-domain operations and recommend the most intelligent action in the correct sequence. The human will then validate the recommendations. If the operational pace is high, the human being will simply decide whether or not to veto the recommendations, and the subsequent processes will again be automated by AI. “Our European air defense system will always be under the full control of a responsible human operator and in all circumstances,” concludes Marc Paskowski.
Both technologically and militarily, the development of FCAS has the potential to establish new standards and revolutionize the use of air power.

The use of AI in Airbus
Airbus began integrating AI into its products and solutions in the 1990s, with applications for reading and interpreting satellite images.
OneAtlas imaging services harness the power of Airbus' constellation of optical and radar satellites with reliable AI and cloud technology to provide important information, for example, to combat deforestation, optimize agricultural yields and urban planning.
However, in the aeronautical sector, Airbus' Skywise big data platform collects data from 24,000 aircraft parameters, allowing airlines that subscribe to the service to perform predictive maintenance and improve the overall operational efficiency of their fleets.
Tags: airbusMilitary AviationFCAS - Future Combat Air System/Future Air Combat System
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work in the world of aviation.
Related news
WAR ZONES
AC-130J aircraft attacks militants in Iraq after first ballistic missile attack against U.S. positions
22/11/2023 - 16:00
MILITARY
F-35 fighters will cost Canada almost $54 billion in 45 years
22/11/2023 - 14:19
MILITARY
Indonesian Air Force receives new Dassault Falcon 8X aircraft
22/11/2023 - 14:03
MILITARY
Russian Air Force receives new batch of Su-34 fighter-bombers
22/11/2023 - 10:46
MILITARY
VIDEO: The impressive attack of the Houthis, with a Mi-171, on a cargo ship in the Red Sea
21/11/2023 - 23:09
BRAZIL
VIDEO: FAB celebrates 40 years of the T-27 Tucano aircraft with special paint
21/11/2023 - 19:30
Client PortalClient PortalClient PortalClient PortalClient PortalClient PortalClient PortalClient PortalhomeMain PageEditorialsINFORMATIONeventsCooperateSpecialitiesadvertiseabout
Cavok Brazil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
HISTORY
Military
Brazilian Air Force
Space
Specialities
Cavok Brazil - Digital Tchê Web Creation
4 notes
·
View notes
Text
An Introduction to Emulation
There are a lot of really cool old games, but actually playing them can seem quite difficult. Fortunately, there are tools available that make old games much more accessible. The most powerful, by far, is emulation. If you have ever wanted to learn how to play classic video games that aren't available on modern platforms, this post is for you.
TLDR: Emulation recreates old hardware (like game consoles) using software, allowing games to be played on modern systems. It's an incredibly cool technology that, while it has some minor downsides, is overall an important tool for preserving game history and enabling new game experiences.
What is the issue?
Game companies don't always make their older titles easily playable on modern hardware. There are so many important, influential, and fun video games released on older hardware that can't be bought on any modern platform. In fact, game companies sometimes go out of their way to remove their titles from modern storefronts. After Bandai Namco released Dark Souls Remastered in 2018, the original version of Dark Souls was removed from Steam, presumably to encourage people to buy the newer, shinier, more expensive release. Game history is important, and it's incredibly rewarding to engage with. Unfortunately, if you limit yourself to what is only available through official channels like Nintendo Switch Online, Steam, GoG, Xbox, Playstation 5, you will miss out on a lot of cool games.
Games are often designed to operate on very specific hardware. Games made for the N64 can't run on a Sony Playstation, and vice versa. Even on PC, a platform which is generally much more customizable, games can be made obsolete through software updates and new operating system releases. Software's dependency on hardware makes it harder to access as technology progresses. Because of this dependency on specific hardware, it takes a non-trivial amount of effort to keep games "up to date", and often companies decide it isn't worth the effort. I can still read books from the 1500s because fundamentally, they are just words and those are easy to bring to modern formats. Film too is relatively easy to keep functional. As long as you have a device that can run mp4 files, you have a lot of options with regards to how you watch a movie (even if those files have to come from an unofficial source). This isn't to imply that lost media and preservation challenges don't exist for books or movies, but the fact that I can easily access books that are several decades old, but many influential console games released even in the past few decades aren't playable on natively modern hardware says a lot. Fortunately, we have a solution. Emulation
What is emulation?
Emulation is software that performs the same function as hardware. Put simply, it lets games designed for one platform run on another. For instance, Dolphin is an emulator designed to play GameCube and Wii games. Dolphin runs on Windows 10 and 11, and allows you to play GameCube and Wii games on PCs. Emulators can be designed to recreate pretty much any piece of hardware. There are emulators recreating handheld devices like the Game Boy Advance, Nintendo DS, Java phones, and Playstation Portable. Other emulators are designed to run old PC games designed for Dos, the Amiga, or Commodore 64. There are even emulators designed for modern systems like the Switch. It should also be noted that emulators aren't exclusively used on PC. There are emulators designed to run games on Android phones or modern consoles. Every emulator is different, coming with its own set of features, requirements, and drawbacks.
It should be noted that most emulators also require ROMs or ISOs. ROMs and ISOs are the file type most commonly used to store game files. If emulators are a virtual recreation of hardware, ROMS and ISOs are virtual recreations of the software that would be inserted into the actual hardware.
What all can I do with emulation?
Emulation is a powerful tool that could be used for a variety of things. Most obviously, emulation is excellent for playing older games. While they certainly can do that, they can also do so much more. For instance:
Emulators make it much easier to play old games on the go: I can't carry a SNES with me everywhere I go. It's big, requires a bunch of cables, and I probably won't even have a TV to play it on. However, I can always bring my laptop with me. I have a SNES emulator installed on my laptop that lets me play SNES games anywhere. If I have a few moments in between classes I can boot up Front Mission, Tetris Attack, or any other SNES game I want. As if that wasn't enough, I also have NES, GBA, and DS emulators on my laptop, taking up very little hard drive space. Convenient!
Emulators let you customize your control schemes: Most emulators give you a lot of choice in how your controls are set up. For my laptop emulators, I simply use my keyboard because I don't want to carry a controller around with me. But, if I wanted to, I could plug in my Switch Pro Controller, or any other controller to play these games. This feature alone has some non-obvious advantages, such as...
Greater accessibility in control schemes: For people with physical disabilities, who might be unable to comfortably use a SNES controller, emulators allow them to relatively easily substitute the original controller for one they find more comfortable to use. This makes the emulated versions of classic games far more accessible than they would be on original hardware. As with all disability infrastructure, adding considerations for disabled people helps everyone, and a great example of that is...
Customizable controls are great for challenge runs: All sorts of interesting challenge runs become possible with emulated controllers. Have you ever wanted to play Link's Awakening with a Dance Dance Revolution pad? Well, set up an emulator and map its controls to the dance pad and you are good to go! You can't do that on an original Game Boy!
Save States let you bypass unfair nonsense: Old games sometimes have a reputation for having a lot of cheap deaths, and some definitely live up to that expectation. Some emulators come with save state features that essentially take a snapshot of the current game state that can be returned to at any point. If an upcoming platforming section has a lot of precarious jumps with impossible to dodge enemies, you can make a save state to go back to that challenge instantly, instead of having to replay the whole level again. Very nifty! Also, some emulators have rewinds, which serve a similar purpose.
Fast forwarding saves time: Some emulators let you increase the game speed, allowing you to bypass slow sections of a game. My friend Harry who runs the Video Games Are Bad YouTube channel recently released a video talking about how the speedup feature on his Seam Deck GBA emulator that made the experience of playing classic GBA Yu Gi Oh games much more enjoyable because he could skip the opponent's long turns. For JRPGs, games with cutscenes, or many other games, this is a great convenience feature
Emulators bypass region locking: Many classic console games were only playable in consoles from the right region. Japanese Playstation games could only be played on Japanese Playstations. While it's certainly possible to bypass this restriction on original hardware, it requires you to modify the console's internals in a very technical and easy to mess up process. Emulators bypass this entirely, making it easy to play games from other regions and see all of the differences between versions of the game.
Romhacking and Translation patches: Beyond playing games in their original form, emulators make it possible to play romhacks, mods, and other alterations. Translation patches allow players who don't speak a certain language to play games that didn't receive official translations. Famously, Mother 3 was never localized for a North American release, and to this day hasn't seen an official English translation. Fortunately, the game's very passionate fans translated the entire game to English, allowing tons of Mother fans to finally play the third, and best, entry in the series. Romhacks are similar, but instead of being used for translation purposes, entire game mechanics are altered. With romhacking, designers can create fan campaigns, edit game balance, create jokes, and many other things. Romhacking is a world of possibility that lets games be experienced in new ways that would be difficult to experience on original hardware.
Speedrunning: While the rules surrounding emulators obviously vary from game to game, some speedrunning scenes (especially those for handheld games) use emulators for their runs. Without emulators, some games would be much harder to speedrun, and would have smaller scenes as a result.
And more!
What are some Downsides of Emulation?
Clearly, emulators have a ton of advantages, even if you have the original hardware. However, for as great as they are, and they are pretty great, there are some downsides worth considering when using emulators.
System requirements: Emulators function by recreating hardware through software. Doing this takes a certain amount of the host machine's CPU power. For older systems this usually isn't a problem, but the more recent and complex an emulated machine is, the better your machine needs to be to smoothly run the emulator. Naturally, it's a lot easier to emulate a Playstation 5 than a Playstation 1. If your computer isn't powerful enough, there might be some emulators it can't run. I personally haven't run into this myself, but its something to keep in mind.
Finding ROMS and ISOs can be tricky: While emulators themselves can usually be downloaded easily, ROMs and ISOs are a different story. When searching for ROMs, some people come across sketchy looking websites that are filled with ads and give the impression they could give you a virus, and some of these sites very well might. This isn't to say that there aren't ways of safely obtaining ROMs and ISOs. In the past, there was EmuParadise, a quite extensive ROM library that was safe, however following a legal threat from Nintendo the site had to remove the ability to download ROMs. MyAbandonware is a pretty safe site and is my go to for PC emulation, but doesn't have much in the way of console gaming. The Internet Archive also is pretty safe, but might not have everything. In the future I want to make a post detailing ways of safely obtaining ROMs and ISOs as that is a nuanced issue, but for now know that there are safe downloads online. ROMs and ISOs NEVER come in the form of EXEs, so never run an EXE downloaded from online. Beyond that, it never hurts to do a quick google search about the site in question to find other people's experiences with the site in terms of safety.
Emulators aren't always 100% accurate: Because emulators are recreating hardware with software, it isn't always perfect. Some games don't run exactly as they would on original hardware. Textures might not appear properly, in game mechanics might be a bit wonky, and there might be some visual issues. For older systems, these kinds of problems have been largely ironed out and these emulation issues are extremely rare, but they pop up from time to time when emulating more modern systems. In my years of emulator experience, I have only encountered serious emulation errors once. Fortunately, most emulators are in continuous, open source development so visual issues often eventually get fixed. Even if the game does have some problems, a flawed, visually imperfect game is better than nothing at all.
Isn't emulation illegal?
Some people might be hesitant to get into emulation because they feel it is illegal, or that it's essentially piracy. This technically isn't the case. In 2000, Sony sued Connectix, who had recently released the Virtual Game Station, a commercial emulator for the Macintosh. The Virtual Game Station was designed to only play legal games. Players had to insert the Playstation game they wanted to play into their computer in order for the emulator to work, meaning the emulator didn't inherently enable piracy. Regardless, Sony sued Connectix, arguing the emulator infringed on their copyright and stole Sony's Playstation code. However, the court ultimately sided with Connectix. While their software did recreate the function of the Playstation, it did so with its own code which had been reverse engineered from Sony's hardware, meaning that Connectix didn't violate Sony's copyright. Sony v. Connectix established the legal precedent that emulation was entirely legal, and this has born fruit for modern game companies. Many PC games released on Steam and GoG run off DosBox, an emulator that runs Dos games. These releases come from the current rights holders and are entirely legal, even though the games use emulators. For more evidence of legal emulation, look no further than the Wii Virtual Console or Nintendo Switch Online service, both of which are commercial emulators.
While emulation is legal, the sharing of ROMs and files without permission from the copyright holders is illegal. As such, downloading ROMs from the internet is technically illegal. However, there is certainly a case to be made that, while it isn't always legal, it can be ethical to emulate classic games. If I wanted to legally play a GameCube game, I would have to go online and buy a used copy online. Depending on the popularity and rarity of the game in question, used game discs can cost anywhere from dozens to hundreds of dollars. Buying used games and the hardware to run them can be extraordinarily expensive and would put many games out of the financial reach of many individuals. It's also important to note that none of the money spent going to buy these used games is actually going to the developers who made the game.
In general, I'm actually not a huge fan of piracy, especially for indie games. My rule of thumb is that if a game can be purchased on modern hardware, I won't use emulation to play the game. I only use emulation to play games that are out of print and impossible to buy legally in a way that supports the developers. Unfortunately, there are tons of games that I can only realistically experience through emulation, and in that case I feel no guilt for doing so. I can't deny the developers a sale if they aren't selling the game. Further discussion of the ethics and legality are interesting, but might be best approached in a post of their own.
Conclusion
Emulation is an incredibly cool technology and one of the most powerful tools in the fight to preserve gaming and its history. Emulators can be complex, and in the future I hope to write further blog posts detailing the intricacies of emulation in more detail, laying out emulators I recommend and discussing other emulation and game preservation topics.
If you have any questions about emulation, game preservation, or any related subject, feel free to ask.
Have a good day.
11 notes
·
View notes
Text
Us 144,000 Ancient [USA] 9 Ether ALUHUM SKY ANUNNAQI Birthed Ægipt [ABE] in Marie's Antediluvian [MA] MU Amurika [MA = ATLANTIS] w/SIRIUS BLACKANUNNAQI.tech WEALTH ECONOMIES [WE] @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm] mode [i’m] tech [IT] steelecartel.com @ quantum harrell tech llc
eye 1921steelecartel.tech TITAN of SIRIUS [U.S.] gullahgeecheemilitary.tech WEALTH @ quantum harrell tech llc

my golden future of now... so x-tra golden... eye gotta wear moor anunnaqi [ma] gold!!!
my x-tra blk sky rizqiyian ufo made of moor anunnagi [ma] gold

ufos = rizqiyian sky crafts = shams from tri-solar black sun planet rizq

eye alkhemically & genetically engineered [iaged] by 3 sets of 144,000 9 ether igigi sky crew elites from enqi [me] nudimmud's moon base empire [mbe] employed [me] @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

EYE FOUND MUUR [MU] of Our ANCIENT 1279 GEOLOGICAL EARTH [AGE] DNA LAND DEEDS of SIRIUS BLACKANUNNAQI.tech PATENTS @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

our old world mu america = original ægipt = subterranean underworld kemet [u.k.] in blackatlantis5000.tech MINING of pure anunnagi [pa] gold

eye remembered

blackatlantis5000.tech of atlantis5000.com @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

eye ease on down the road of gold!!!... eye ease on down ease on down the rooooooooooooaad of our anunnagi gooooold!!!

iscribealot.com on blackatlantis5000.tech domain of highly complex [advanced] cosmic algorithmic [ca] computational [compton] STAR Gateway Language [SGL] Patents Accessing [PA] QUANTUM HARRELL TECH’s Automated 2025 18G Android Operating System [iOS] of Apple’s 2024 Optimized iCloud Machine [I’M] VISION PRO of 1921steelecartel.tech MEMORY DNA PATENT ARCHITECTURE [PA] @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

WE STILL HERE!!!

ON UPTOWN RECORDS of ANDRE [RA] HARRELL @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000!!!

REMEMBER ANDRE [RA] HARRELL?!?!?!

ÆGIPTIAN MU QUEEN MARIE HITTITE [TIYE] STEELE... WEALTHY AF!!! @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

MY ANCIENT [MA] 9 ETHER [ME] SKY ÆGIPTIAN ATLANTEAN [SEA] MOTHER PLANE of 1921steelecartel.tech SKY WEAPONS TELEPATHICALLY SAY... WE THE GOLDEN BLACK ATLANTEANS of QUEEN CALAFIA's GOLDEN Black Pacific Sun Continent Island of LEMURIA [MU]!!!

OH MAYAN 2012 PROPHECY PRIESTHOOD of Ægipt [PA] in Marie's Antediluvian [MA] MU Amurika [MA = ATLANTIS]

1ST EYE of MICHAEL [I'M] ALL SEEING EYE

OH CLANDESTINE SKY LAW'D OF BLACKATLANTIS5000.tech

BECAUSE WE ARE THE ATLANTEANS!!!

you still easily 9/11 sky distracted?!?!?!... in 2023 CGI Alien Disclosure [CAD] America [CA]?!?!?!

all eye got is my golden blackanunnaqi.tech throne kingdom dna/rna records... where your ancient ancestral sky records of who you claimed to be in our original 9 ether ægipt of mu amurika [ma = atlantis]???

© 1698-2223 QUANTUM HARRELL TECH LLC All Pentagon DotCom defense.gov Department Domain Rights Reserved. | © 1698-2223 QUANTUM HARRELL TECH LLC All LOST ANCIENT [L.A.] ATLANTEAN DNA [A.D.] DotCom [A.D.] Domain [A.D.] Name Rights Reserved.
#because we are atlanteans#9etherpentagonelites#9etheraluhumanunnaqi#9etherlightshipatlantis#harrelltut#harrelltut.com#king tut#o michael#u.s. michael harrell#mu:13#quantumharrelltut#jehovah#quantumharrelltech#kemet#om#andre harrell#2023 uptown records#marie's atlantis#exodus
2 notes
·
View notes
Text
RWBY COMBAT ANALYSIS: PENNY POLENDINA

“Now that I'm the official protector of Mantle, I don't really have a team anymore. General Ironwood says I don't have time for friends. […] I feel like I wish I could do both the things I need to do and the things I want to do. Is that normal?”
My analysis of Penny Polendina will be based exclusively of her appearances prior to Volume 8 Episode 11, “Creation”, and her transformation into a human girl by the Relic of Creation. The strengths and limitations of robot Penny are simply more interesting to discuss, and the narrative framing makes it abundantly clear that Penny’s humanization had a drastic effect on her combative capabilities. It’s the same reason why Anakin Skywalker and Darth Vader are treated as separate entities despite being the same person; they have been, for all intents and purposes, been given a new body and therefore cannot fight in the same way they used to. With all of that out of the way, let us begin.
PHYSICAL
The brainchild of the Atlas military’s greatest scientific minds, the P.E.N.N.Y. Project was another step among countless in James Ironwood’s perpetual mission to strengthen the kingdom’s defenses. In this case, Dr. Pietro Polendina used some of his own Aura to infuse a high-grade android with his own soul, creating an artificial intelligence more advanced than any at the time. Taking the form and mannerisims of a young girl, the android was dubbed “Penny” and raised by Polendina as his own daughter. As much as Pietro wished for the girl to experience her own life to the fullest, military protocol took precedent, and Penny was outfitted with the programming and equipment needed to serve the defense of Atlas and Mantle. However, Ironwood’s designs would take an unexpected turn when Penny was brought to Vale to participate in the 40th Vytal Festival. Wandering off on her own, Penny encountered the rising stars of Team RWBY and played a critical role in disrupting Roman Torchwick’s operations. Despite Ironwood’s attempts to rein in his asset, the bonds she forged with these girls, especially Ruby Rose, and the influence they would have on her would set the stage for Penny’s eventual transformation from a simple machine to a real girl in every sense of the word.
Despite her overly happy and friendly personality, Penny was first and foremost a piece of military hardware designed for the rigors of battle in the world of Remnant, from swarms of Grimm to the deadly agents of Salem. Essentially a combat drone in the shape of a human girl, Penny stood at 5’5” and was made of a heavy-duty metal chassis concealed by fair synthetic skin and a mop of auburn hair. Her green eyes housed military grade sensors and scanning equipment that allowed for night, infrared, and telescopic vision, her hands contained interface terminals that allowed her to access computers and other technology, rocket thrusters built into her feet allowed for sustained flight at extreme speeds, and a heads-up display built into her eyes allowed for regular monitoring of her systems and “vitals”. Befitting her intended role, Penny’s athletic performance levels were specifically designed to match and surpass the greatest Huntsmen of her day, making her a surprisingly devastating physical combatant. Possessing monstrous physical strength, she has manhandled and overpowered giant Grimm, deformed metal with her bare hands, and has casually lifted and thrown objects weighing hundreds of pounds. Penny has stopped a speeding van with only her outstretched palms, hefted around a severed Megoliath tusk before impaling the creature on it, and in easily her greatest feat of physical might, aided in pushing the gargantuan Amity Tower satellite into the upper atmosphere following her duel with Cinder Fall. Even without her rockets, Penny was quick on her feet, covering ground with powerful leaps and running charges, while evading attacks with quick sidesteps and nimble dodges. Compared to her contemporaries, Penny has matched the swiftness of high caliber opponents like Pyrrha Nikos, Cinder Fall and all four surviving Ace-Ops simultaneously, with Harriet Bree being the only member of the group to come close to outpacing her. Though her weapon set left her hands free, negating the actual need for developed dexterity, Penny still demonstrated incredible reflexes and precision in her core fighting style, manipulating her blades to do everything from deflecting projectiles to outfencing opponents to slicing cakes. In virtually all of her fights, she has spun and thrown her blades to land critical hits at weak flanks, and she has even caught a thrown sword with only her hands while in midair

While Penny’s Aura meant that she had a natural defense against minor wounds, her nature as a designed-and-built combat drone made that part somewhat redundant. Pietro Polendina claimed that his daughter could withstand anything so long as her core was left intact, and as such, she has taken an inconceivable amount of punishment. She has shrugged off incoming strikes without even acknowledging them, suffered only cosmetic damage when struck by a speeding delivery van, endured a heavy crash to the ground from a Goliath in Mantle, was slammed through the walls of the Atlas medical facility during her initial confrontation with Cinder, and later walked casually through Fria’s magic blizzard when the Maiden unleashed her power. Furthermore, Penny’s limbs and extremities were little more than add-ons, and while amputations would certainly impede her overall performance, it would not be nearly as detrimental as it would to a flesh-and-blood person. Stamina wise… well, it’s kind of moot considering she literally has no way of producing fatigue toxins. In what is easily her greatest show of durability, after she was hacked by Arthur Watts, Penny endured a fall of several thousand feet from the Amity tower base before crashing into the Schnee manor driveway, and despite suffering severe blunt force trauma that caused lubricants and other fluids to leak from her chassis, she remained alive and was still able to walk after only minor “medical” attention from Klein Sieben. Even accounting for Watts’ virus taking over when she grappled with the Hound, the simple fact she could maintain combat performance without any noticeable difficulty despite what she went through is awe-inspiring. However, as tough as she was, there were limits to Penny’s resiliency. While she was naturally resistant to blades and gunfire and could technically fight indefinitely so long as her systems were functioning, she could still feel pain, seen when Cinder tried to forcibly steal the Winter Maidenhood from her at Amity. Furthermore, her joints were vulnerable to focused cuts, her original body being destroyed when Pyrrha Nikos repelled her weapon and got her limbs tangled in the wires, dismembering her. But considering how she’s almost literally built like a tank, effectively exploiting these vulnerabilities would take nothing less than a miracle.
Given that she was a robot, armor was relatively redundant for Penny, as her body was already durable enough to protect her from all but the most severe of injuries. Furthermore, as she was typically masquerading as a normal girl, such combat-related gear would have been far too conspicuous for her liking as well as clashing with her own preferences. Instead, Penny dressed in casual civilian clothing that was as far removed from her military affiliation as possible. When she was rebuilt by her father following the Fall of Beacon, Penny wore a white blouse with frilled sleeves and a green overall skirt, with a black ascot tied around her neck. She further accessorized with lacy black gloves, black shoes, and a large pink metallic bow atop her head, exemplifying her innocence in spite of the weapon she was designed to be.
RANKING: Tier 1, Baseline Superhuman
Penny Polendina possessing the highest physical ranking is obvious and inarguable by the simple fact that, at least on a physical level, she ISN’T human. Her body was specifically designed and built, not just out of metal, but for hard combat. Her strength, speed, and durability are naturally far beyond human limits, her foot rockets provide her with unlimited mobility, and worst-case scenario, she can even shrug off amputations. While her original destruction and the circumstances of her hacking prove that there are limits to Penny’s resiliency, reaching that point is such a high bar that most conceivable opponents cannot hope to reliably exploit them. As warm as she is, Penny Polendina is nonetheless one of the most terrifying physical threats in the RWBY setting, a true killing machine.
MARTIAL

Penny Polendina was armed with the Floating Array, ten single-edged short swords that could be converted into energy pistols. These weapons were attached to near-invisible wires that extended from a compartment built into Penny’s back, connected to her central processing unit to allow for coordination without physically holding them. Each blade was collapsible, appearing to be about two feet long when fully extended, and featured a concave bend in the center similar to an ancient Mediterranean kopis or falcata. The swords featured a simple black handgrip with a circular handguard which housed the electronics compartments. As firearms, the swords kicked back the blades and bent the handles, capable of firing small beams of green energy for swarming volleys and precision shots. Furthermore, these beams could be combined, forming a single powerful blast of energy that has been shown to destroy bullheads with ease and stop a charging Goliath in Mantle.
Specifically designed to be the pinnacle of Atlesian military defense, Penny’s programming featured a heavy focus on combat, essentially turning her into a war droid in the shape of a young girl. While Pietro Polendina raised her to be a kind, amicable and noble individual, traits elevated by her friendships with Team RWBY, Penny remained a committed and highly capable martial combatant, cutting her teeth in the months leading up to the Vytal Festival by stomping a contingent of White Fang operatives at the Vale docks. Despite a serious lack of combat experience and little formal training, Penny made up for it with programming, her brain functioning as a combat computer that allowed for the skillful coordination of her multiple blades. To put it mildly, Penny’s physical moveset was a multi-angled circular saw and flachete launcher all rolled into one. By manipulating the wires connected to her back, Penny swung her swords as a devastating swarm of blades, favoring wide cleaving slashes, rotary spinning cuts, launching stabs, and windmill deflection parries. However, despite this heavy offensive focus, Penny was not a single-minded machine, and in her battles, she clearly emphasized technique over brute force. Though she was perfectly capable of unleashing a singular rapid-fire slashing onslaught, she preferred attacks form multiple vectors simultaneously, coordinating multiple weapons for different purposes to subvert and undermine to opponent’s defenses. Extremely fast and agile, she supported her defensive component with nimble evasions both against projectiles and close quarters, even seen using her blades as grappling hooks to influence her environment, ranging from manhandling vehicles and Grimm to allowing for greater maneuverability. Her use of her firearms function shared this emphasis, usually resorting to multiple guns firing at different places to box the opponent into a corner and cut off escapes, reserving the massive beam cannon to concentrate her power onto higher-grade targets. Though she overwhelmingly favored the use of her weapons, Penny was perfectly capable of resorting to unarmed combat as well, supporting her bladework with punches, sweeping kicks, and arm sweeps. Furthermore, upon becoming the Winter Maiden, Penny expertly leveraged her new magical powers into her overall fighting method, typically gusts of wind to off balance large groups of enemies.

In her tactics and conduct, Penny typically operated as a polished machine of war, deftly executing her style with calm efficiency and advancing with determination and fearlessness. However, the influence of her father and friends, as well as the nature of her technique, meant that Penny was not a straightforward dervish reliant on simply overwhelming her enemies. Instead, Penny worked towards the path of least resistance, using her range of techniques to control the flow of the engagement. She demonstrated an emphasis on targeting weak flanks and subverting defenses, working around her opponents’ guard rather than just beating into it like a sledgehammer. This approach was enabled by her use of multiple weapons, often drawing the opponent’s attention with one form of attack before blindsiding them with several more. On the battlefield, she deftly unleashed her blades to overwhelm targets quickly and efficiently, quickly recovering her guard and keeping her might in reserve. In single combat, Penny applies this same mentality to attack at multiple angles simultaneously, tying up the opponent’s weapon and attention to prevent them from bringing their full might to bear against any one attack. She supported this offensive stance with a retaliatory defensive component, blocking incoming attacks before instantly countering. The volume and variety of her offensive output combined with her speed, precision, and mechanical focus made Penny an extraordinarily adaptable and lethal combatant. Against the White Fang, Penny tore through the mooks with ease before moving on to the Bullheads, using two blades to anchor herself to the ground before sending the others to tear one out of the sky. She followed this up by opening up distance and firing her energy beam to dismantle the remaining ships. However, though quite proactive and decisive, Penny had difficulty adapting to abrupt style shifts, and her approach could be undercut if she is distracted or blindsided. Arguably the greatest demonstration of Penny’s tactics in single combat was her duel with Pyrrha Nikos during the Vytal Festival Singles Bracket, during which her multangular offensive was able to strike at all of Pyrrha’s flanks simultaneously and pressure her defenses, while her own defensive component was strong enough to fend off all of Pyrrha’s counters before quickly retaliating. The fight functionally ended when Penny disarmed Pyrrha, though this victory was rendered hollow when Pyrrha, under the influence of one of Emerald Sustrai’s illusions, lashed out with her Semblance, entangling Penny in her own wires and dismembering her.
After her reconstruction, Penny continued to operate as the protector of Mantle, killing Grimm infestations that threatened the city while Ironwood continued his Amity project. The activity in Atlas proved to be the greatest demands made of Penny, both martially and emotionally, as Salem’s machinations and Ironwood’s oversights came to a head. During the Battle of Mantle, Penny aided the defense by cutting through Grimm hordes, later coordinating with Ruby and Harriet Bree to take down a rampaging Alpha Megoliath. When Cinder Fall infiltrated the Atlas compound, Penny and Winter Schnee were dispatched to secure the venerable Winter Maiden Fria, though Penny actively voiced her dissatisfaction with this turn of events despite Winter’s reassurances. However, this debate was aborted when Cinder followed them to the medical center, the pair joining forces to defend Fria. Though they kept her on her toes and matched her power where and when it counted, Penny’s rapid-fire attacks proving a good foil for the Fall Maiden’s dual-wielding style, Cinder’s ferocity was too great, and Penny was forced to abort the fight to save Winter after her Aura broke. Fortunately, Cinder’s assassination attempt was foiled when Fria cut loose, giving Penny the opportunity to comfort the old woman and inherit the power herself. Defecting from Ironwood as he prepared to abandon Mantle, Penny assisted Ruby, Weiss Schnee, Blake Belladonna, Nora Valkyrie, and May Marigold in infiltrating the compound themselves to obtain the launch codes for Amity Tower. Intercepted by the surviving Ace-Ops, Penny refused to give in to Harriet’s manipulations and engaged the quartet after being forcibly separated. Though she was blindsided by Bree’s speed and Vine Zeki’s Aura Vines, Penny still acquitted herself extremely well, leveraging both her versatile weapon set and her new Maiden powers to keep them off their game and respond in kind. Penny was only subdued when Marrow Amin froze her with his Semblance, though Nora’s destruction of the office door provided an opportunity to escape. Ultimately, the fight was rendered inconclusive when Penny received reinforcements and Ironwood ordered Bree to simply steal one of Penny’s swords for Arthur Watts. This confrontation would soon be followed by her rematch with Cinder Fall at Amity. Here, Cinder initially gained some ground by using Penny’s own tactics against her while also leveraging her ferocity and power to bully through her interference and attempt to steal her powers. Luckily, Penny managed to break free and continue fighting, ultimately besting Cinder when she saw through Emerald’s illusions and blasted Cinder with a sustained energy barrage. Only Emerald’s threat to continue damaging the tower stopped Penny from killing Cinder outright. After crashing at Schnee Manor, Penny was hacked by Watts’ virus and attempted to mindlessly leave for the Relic Vault, though she was intercepted by the Hound, who used his extra limbs to manhandle her and subdue her.
RANKING: Tier 2, Advanced Mastery

Penny Polendina’s advanced skill level makes her one of the most dangerous martial artists in the RWBY setting despite lacking the dedicated training and experience of more established Huntsmen. She possesses an incredibly versatile and flexible fighting technique that shows emphasis on leveraging power, precision, and control to control the flow of the engagement, going for the throat by creating a path of least resistance. However, while she has proven her mettle against many of the premier warriors of her day, she is not without her limits. Penny’s initial death and her stumbles with the Ace-Ops prove that she can be subverted in turn, her encounters with Cinder and the Hound show that she can have difficulty contending with overwhelming force, and she simply lacks the experience to deal with the unorthodox. Furthermore, her style is based on programmed attack sequences rather than developed techniques, so her performance level is capped somewhat. Fortunately, these issues are only really relevant when she is faces with opponents at or around her own level, and Penny never repeated her mistakes, learning from experience and adjusting her pattern accordingly.
SPECIAL

Penny’s Semblance, if she has one at all, is unconfirmed, nor is there any parallel to be made with her father. As a scientist and academic, Pietro’s Aura was likely developed solely for practicality rather than combative application, so any Semblance he may have is unlikely to have been discovered. However, the Aura that Pietro sacrificed to create Penny was clearly more than enough to provide her with all the benefits of a flesh-and-blood person’s, her Aura being just as strong as anyone else’s. Even without a supernatural superpower, Penny’s body was built with various gadgets and tools that provided her with special abilities. Though most of these were covered in the Physical breakdown, Penny’s varied visual processors, computer interface, and propulsion systems still provided extranormal traits and abilities that furthered her combative viability. Specifically, her vision provided her with unparalleled capabilities for rooting out infiltrators, seeing through Emerald Sustrai’s illusions by targeting Cinder Fall’s heat signature and revealing Tyrian Callows during his massacre in Mantle, though the chaos created prevented her from apprehending him. Furthermore, the heads-up-display in Penny’s eyes allowed her to regularly keep track of her own systems, and could be updated with blueprint data to support navigation, seen when she casually calculated the fastest route to the control center at the Atlas base. Practically speaking, the concentrated energy beam created by the Floating Array was her most readily available and commonly used combative ability, generating massive blasts capable of destroying heavy machinery and incapacitating high-caliber Grimm.
During the upheaval caused by Cinder Fall following the Battle of Mantle, the Winter Maiden Fria passed away, leaving Penny to inherit the power. Like her contemporaries Cinder, Amber, and Raven Branwen, Penny possessed tremendous elemental powers and control over the weather, these abilities stemming from a source independent of her own Aura. Among the various abilities offered by the Maiden powers, Penny appeared to favor wind manipulation, using powerful gales to throw the Ace-Ops around during their battle and keep them from regularly closing the distance. During this same encounter, Penny created a contained thunderstorm as an anti-personnel attack, releasing hail on the Ace-Ops, and she was likely capable of using lightning in a similar fashion. During her subsequent duel with Cinder at Amity, Penny demonstrated her proficiency in utilizing ice when she halted Cinder’s attempts to melt the support beams, using freezing streams to stabilize them. Though this gave Cinder an opportunity to close in with her claws, Penny broke free and attacked her with an ice replica of the Floating Array. While she was fighting Arthur Watts’ computer virus at Schnee Manor, Penny lost control of her powers, unleashing storms of magical energy that struck out in all directions and would have likely caused significant damage to the surrounding area had Nora not snapped her out of it. Given this storm was visually similar to the blizzard Fria conjured in her last moments, it is entirely possible that this was a glimpse into Penny as a “fully realized” Maiden, indicating what she may have been had she been allowed to continue training with her powers. However, I do not believe that this feat is something Penny can consistently use on her own, instead being a circumstantial loss of control on her part.
Penny’s use of her special abilities were similar to her martial skills in that they had the mechanics of direct, robotic application of power, yet her programming and ingenuity allowed her to wield them as a fluid array of multitools. Penny’s displays against the Ace-Ops are a perfect demonstration of her continued emphasis on undermining and subverting her opponents rather than just overwhelming them with almighty displays of god-like power. Instead of ripping into them with tornados, fire storms and lightning, she used calculated bursts of power to escape their traps, keep them off their game, and whittle away at their defenses, the incident with the hail is easily the best specific example. Against Cinder Fall, Penny negated her counterpart’s overwhelming onslaught by evading her attacks and used her own powers to strike at Cinder’s weak points when she was exposed. However, while Penny’s programming allowed her to compensate for her inexperience using the Winter Maiden’s power, she seemed to display a lack of confidence in directly leveraging her might in battle, instead relying heavily on martial might wherever possible. The incidents with the virus offer a glimpse into the destructive juggernaut Penny might have become had she lost these inhibitions, though they also demonstrate the limits of her skill. As it stands, her inventive and tactically oriented use of her powers were typically enough to make up for this hesitation, and Penny was never truly defeated upon receiving Fria’s power.
RANKING: Tier 1, Dominating Combat

Despite her gross inexperience, Penny Polendina’s fast learning allowed her to develop into a tremendously powerful Maiden in a very short span of time. Her proficiency was likely another outgrowth of her combat computer, funneling the same programming that allowed her to subvert and overwhelm her enemies in swordplay into her use of her elemental powers. In fact, I would argue that no other Maiden, except possibly Raven, has mastered the kind of skill-based applications of their powers to the same degree as Penny. She combines subtle and creative uses of her various abilities with overwhelming power in all areas, channeling the might of nature itself through the precision and focus of a military-grade computer. While this means her effectiveness is based on programed skill rather than developed skill, the sheer magnitude of her abilities guarantees that any attempt to combat her is going to have to be top tier at minimum.
OVERALL RANKING: TIER 1, SUPER HUNTRESS

Penny Polendina’s strengths and weaknesses are tied to the fact that she is a designed and built combat module implanted with the soul of a young girl, making her a Super Huntress despite her unusual circumstances. Her body is specifically built for hard combat, providing an athletic performance level that the overwhelming majority of combatants cannot replicate by the simple fact that their biology prevents it. She is armed with an incredibly versatile and powerful weapon set that she uses to both overpower and subvert her opponents with deadly precision and devastating volume. And she combines military grade gadgets and software with the powers of the Winter Maiden, mixing elemental destruction with technological focus. Everything about Penny in a practical sense provides her with a varied approach to combat that she can use to bypass her enemies’ defenses and hit them right where it hurts in turn, elevated above and beyond by military-grade cybernetic enhancements and god-like magic powers. However, Penny is still limited to the conflicting nature of her living and mechanical components. Her skill is based on programming rather than training, meaning that she very much sticks to her own patterns and is not experienced at evaluating her opponents in the way truly developed masters can. She is, essentially, a prodigy who took shortcuts, getting around the need for dedicated training by way of a superhuman body, magically inherited superpowers, and a combat database in place of a living brain.
While I do not hold anything I just said against Penny on a personal level, she does have her limitations that tie into her own unbalanced sense of identity. Penny is a real girl, that is not up for debate. But at the same time, she is conflicted over the developing feelings and understanding of real life and how they mesh with what she is programmed to do. Everything that makes Penny one of the most powerful and dangerous combatants in the RWBY setting also, at least to her, alienates her from the joys of life she loves so much. She is a caring, compassionate, and noble young woman who values her friends and family more than just about anybody, and a dedicated Huntress driven by a desire to protect the world and her kingdom from the threats of the world of Remnant, all the while being constructed as a living weapon to be used and abused as her superiors, James Ironwood in particular, saw fit. Penny Polendina’s greatest strength in battle and greatest weakness in her personal life was that she was a true, and literal, killing machine. And yet, she chose to fight for every life.

*originally posted on RoosterTeeth Community page on 03-27-21*
* all images taken from RWBY Wiki *
RWBY Combat Analysis
#rwby#rwby combat analysis#penny polendina#rwby penny#atlas academy#atlas military#baseline superhuman#advanced mastery#dominating combat
14 notes
·
View notes
Text
Starfinder Character Concept: Aballonian Noir Detective
Continuing our theme of Pact World character concepts. We’re gonna take an odd sidestep and head to Aballon, the heat-blasted metallic machine world closest to the Sun. Because, and I’m not fully sure why, you’d think Absalom Station would be the first choice for a noir detective, but there’s something about a robot noir detective moving through the dark underbelly of a mechanical utopia. Aballon’s undercities and ice wells, the melting-pot mixed-race areas built in the cooler, more sheltered craters while the machine megacities built over top of them, offer some interesting stalking grounds for a noir detective. Aballon’s Insight Array and universal social support (once you accept your assigned role) is also a bit of an interesting backdrop to criminal motivations and investigations. I don’t know. It called to me. So.
Dusty Brown. A rumpled android detective with a gentle mien who moves through the mean streets and high speed magnetic rails of Aballon’s undercities.
Character Concept: Dusty Brown, Aballonian Noir Detective
Name: Dusty Brown
Age: 87
Starting Statistics:
Strength 10, Dexterity 16, Constitution 11, Intelligence 14, Wisdom 14, Charisma 8
Starting Skills:
Ranks in: Acrobatics*, Bluff*, Computers*, Diplomacy, Engineering*, Perception*, Mysticism, Piloting*, Sleight of Hand*, Stealth*
Specialisation Skills (Skill Focus plus auto rank per level): Culture*, Sense Motive*
Race: Android
We’re gonna be a synth detective, doll. Yes, Nick Valentine is a significant chunk of the starting inspiration for this character. Will Flat Affect and a charisma flaw have an impact on our success with social skills and Sense Motive particularly? Possibly. But we’re an operative, so we’ve got the skill ranks to compensate, and I want an android noir detective.
And not just an android. We’re going to be an Aballonian android. We’re gonna be a rumpled android detective working the mean streets and high-speed magnetic rail systems of the machine world’s undercities. Even in a logical utopia where food and lodging are (usually) guaranteed, people still have passions, and ideologies, and desires, and hatreds. No matter where you go, someone there will wind up dead, or something there will wind up taken. There’s all the work in the world for a private detective, even on a world with vast near-omniscient AI running the show. So one day the self-named Dusty Brown stepped off the mag-rail and hung up her shingle as a PI in Striving’s Lors Emphyria undercity. She wasn’t exactly assigned that role, the Insight Array didn’t offer it as a suggestion, but she wound up getting a stipend anyway, so maybe the machine overlords think she’s doing some good.
I think I’ll swap out the android’s Upgrade Slot for the alternate Nanite Upgrade and take Rebooting Nanites. Dusty’s a hard girl to keep down.
Description:
On the shorter side for an android, Dusty Brown is a stocky woman of about 5ft, with grey eyes and dark brown skin with circuit-seams that glow a dull silvery-grey. She tends to wear dark, sensible clothes over light armour, but does allow the small affectation of a nice long trench coat. A girl’s gotta dress for the role, after all. She tends to favour non-lethal weapons, usually keeping a trusty pulsecaster in its holster under her coat.
Theme: Street Rat
I did look at Paranormal Investigator, just to double down on the detective idea, but Dusty’s not really a paranormal sort of girl. Street Rat, with its urban underworld vibes, is more her style. She didn’t start out with a nice stipend from the Insight Array. She’s made her way without a safety net for a long time. So she knows how things roll down here. She’s a noir detective, not a paranormal one. Mean streets are where she lives.
Class: Operative (Detective)
I mean it had to be. Operative has a whole specialisation ready-made for our concept. And I’m not going to say no to a whole bunch of skills, either.
And we are going to be aiming more in a skill-monkey, explorer, truth-seeker sort of direction, more than combat. Dusty prefers to be non-confrontational, non-lethal. The fact that she has the charisma of a brick (or, well, a robot) doesn’t necessarily help in this regard, but she tries. Her streets might be mean, but she doesn’t want to emulate them. She wants to help piece together what’s gone wrong, so that people can start helping fix it. There’s probably a reason the Insight Array was happy enough with the role she picked for herself. She jumped the gun, but it might well have arrived at a similar conclusion itself.
For that reason, I think I might pick up Scoundrel’s Finesse for her first feat. A noir PI should be able to throw a punch, and she’ll try that well before she graduates to more lethal options. I might also give her a Restraining Spinneret augmentation, give her options to tie people down and try to negotiate where she can. Is she good at negotiating? Not necessarily. But she’s gonna try.
Summary:
Mostly, I just wanted an android noir detective? And then I was noodling around worlds with large android populations, and Aballon caught on things in my brain. Honestly, Aballon would be a fascinating world to run an urban mystery campaign on. I mean, lots of Pact World worlds would be great for that, Verces, Absalom Station, the Sun, but Aballon has an interesting ‘rugged flawed utopia’ sort of angle to it. Machine logic, mining rights, synthetic liberation, organic enclaves, high-speed mag-rail networks (I know I keep mentioning these, but they do a lot for the cyberpunk imagery on Aballon, and that doesn’t hurt the noir vibes at all) … There’s a lot to work with.
So. Dusty Brown. A tired, rumpled, uncharismatic android noir detective who’s just doing her best to help. Heh.
#starfinder#ttrpgs#character concepts#noir detective#synth detective#machine world noir#aballon#androids#operatives
6 notes
·
View notes
Note
I'm so sorry but——
⌨️ — what operating system(s) do you use?
🔏 — want any (more) tattoos?
🎄 — favorite holiday(s)?
🎶 — favorite song at the moment?
✍️ — what other platforms have you roleplayed on?
😁 — what’s your favorite part about being part of the rpc?
😤 — what do you dislike the most about being part of the rpc?
🤗 — are there any rpc mutuals that you’d like to meet irl?
💖 — what was one of the greatest/happiest moments you’ve had in the rpc?
🖤 — what was one of the worst/most depressing moments you’ve had in the rpc?
🎁 — what have you accomplished in the rpc that you’re proud of?
🫂 — how many friends are in your irl friend group(s)?
🎉 — what are some of your favorite things to do with your irl friends?
😗 — what are some of your favorite things to do when you have some time to yourself?
💯 — share three random facts about yourself that your mutuals may not know about you.
Munday Asks

⌨️ — what operating system(s) do you use?
(( Windows 11 on PC and laptop, Android on phone.
🔏 — want any (more) tattoos?
(( I don't have any... 😅 And because of my allergies, I can't have any either. Knowing this, I try not to think about my tattoo wishes...
🎄 — favorite holiday(s)?
(( Definitely Yule (you probably know it as Christmas), Beltane, and Samhain~ And now I probably revealed something else about myself...
🎶 — favorite song at the moment?
(( Adam Lambert - For Your Entertainment
Others here, here, and here.
✍️ — what other platforms have you roleplayed on?
(( ... ... ...
MSN Messenger, IRC, and Discord.
😁 — what’s your favorite part about being part of the rpc?
(( Amazing people around me. I have made very good friends through this RPC and I met my bae. The fact makes me happy every day.
😤 — what do you dislike the most about being part of the rpc?
(( As I said earlier... the nasty anons. Other than that I pretty much enjoy my time in this RPC.
🤗 — are there any rpc mutuals that you’d like to meet irl?
(( Totally yes! ❤️
💖 — what was one of the greatest/happiest moments you’ve had in the rpc?
(( These are answered here.
But I could add that there are very many happy moments. The fact that I made a blog for Yuriko is making me very happy because of that I became part of this community and have met many nice people. My heart feels full when I think about this ❤️
🖤 — what was one of the worst/most depressing moments you’ve had in the rpc?
(( I'm sorry but I'm not comfortable answering this question. That moment left so deep wounds that I only talk about it with my closest people.
🎁 — what have you accomplished in the rpc that you’re proud of?
(( Hmm... probably Rukiko RP story with @ask-ruki-mukami. The main story is far from finished but it's currently ~60 000 words and then we have all the side stories on Tumblr and Discord... probably 10 000 more words at least. It's going to be huge.
🫂 — how many friends are in your irl friend group(s)?
(( Hmm... I think that varies depending on the group. I would say I know many people because of my work and many of them could be seen as friends. But I have very few close ones... 3-4 pretty close and only one very close at the moment.
🎉 — what are some of your favorite things to do with your irl friends?
(( Hang around, drink tea or coffee and talk about gaming and writing. Well, about books and our daily lives too. Sometimes we go book shopping or to anime-related events.
😗 — what are some of your favorite things to do when you have some time to yourself?
(( Reading, gaming and writing... Yes, I'm a boring person 😅
💯 — share three random facts about yourself that your mutuals may not know about you.
(( 1. I have RPed Hatake Kakashi and Konan from Naruto. Though I don't think I was any good at it.
2. My favorite tea is green jasmine tea.
3. I love woolen socks.
9 notes
·
View notes
Text
Infinix Note 10 Pro Price in Pakistan
Infinix Note 10 Pro Price |2023|
Infinix introduces a new Note series mid-range device with a premium display in Pakistan. The small IPS LCD is 6.95 inches, making it one of the largest smartphones. The screen resolution is 1080 x 2460 pixels and 387 PPI density. A 90Hz refresh rate and Mali-G76 MC4 GPU support the display for a better user experience. A Mediatek Helio G95 chipset and a 2.05GHz octa-core processor for the phone’s greatest performance power.
Infinix Note 10 Pro Price in Pakistan is PKR 37,699.
Infinix Note 10 Pro’s Price in the USA is $170.
The phone has a non-removable Li-Po 5000 mAh battery that gives you the backup to play games or stream videos all day. When your phone runs out of power due to a dead battery, 33W fast charging helps you charge it in minutes. Infinix Note 10 Pro runs on XOS 7.6, based on the Android 11 operating system.
Infinix Note 10 Pro
The phone has a quad rear camera setup with 4K video recording. A 64-megapixel wide sensor with phase-detection autofocus, an 8-megapixel ultra-wide lens, a 2-megapixel depth sensor, and a 2-megapixel monochrome sensor. There is also a quad-LED flash next to the camera. The front camera of the Infinix Note 10 takes great selfies.
The phone offers three storage configurations: 6GB RAM paired with 64GB UFS 2.2 internal storage, 128GB and 256GB UFS 2.2 internal storage paired with 8GB RAM. Infinix has also provided a dedicated MicroSD card slot to increase storage space. Infinix Note 10 Pro Price in Pakistan mobile pricing is impressive as it offers many features at a low price.
4 notes
·
View notes
Text
Skip to content
Simplified Privacy
Menu

Google’s Surveillance: The Shocking Truth
Google is the opposite of privacy. They maliciously collect data from you in the following ways:
The Sources for this article can be found here.
1) Saving all your Google searches, tied to your identity across devices [1] [2] [30]
2) Reading all your emails. Even if you don’t use Gmail directly, but you’re sending email to someone who does. [5] [6]

3) Saving all your web traffic if the website uses Google Ads, Captchas, or Analytics (and over 85% of all websites use some of their services). Even if you aren’t signed in to a Google account, and you’re using a VPN, they can still use past cookies and browser fingerprinting to identify you. [35] [1] [25] [26]
Google’s reCaptcha fingerprinting includes mouse movements, response time, timezone, screen dimensions, IP address, and any cookies. ReCAPTCHA uses the google.com domain instead of one specific to ReCAPTCHA, which allows Google to receive any cookies you have directly, instead of the website you’re visiting. [35] This concentrates the vast majority of all traffic data in the hands of a single company, which can then be used to de-anonymize users.
4) Everything you do in Google’s Chrome Browser is recorded, including even how long you are idle on a page. [7] [8]

5) Tracking and Saving your physical location, via Android’s GPS and Wifi triangulation. [12] [13]
Even if you turn location features off or set the phone to airplane mode, it still saves your location via Wifi triangulation, which is the process of pinging nearby Wifi hotspots to identify where you are. [9] [10] [11] Wifi triangulation can figure out your real location, even if you have a fake IP address from a VPN. [14]

As intelligence expert and ex-law enforcement Michael Bazzell says, Google is one of the first places law enforcement goes to for information because Androids track everyone’s location so accurately. Bazzell points out that even if you’re not directly involved in something, just owning an Android that was near it, can get you involved in answering police questions. Bazzell’s experience serving in law enforcement and intelligence motivated him to completely cut Google out of his life even though he’s doing “nothing wrong”. [11]
6) Keeping track of who you know to identify new phones or email accounts as you.
Rob Braxman
Privacy expert and phone operating system designer Rob Braxman points out that, by synching everyone’s phones’ contact lists and who they are physically standing near, Google (and therefore governments) can identify unknown devices or email accounts as you. [30] [31] [32a] Braxman further points to publicly available websites made by Google’s Jigsaw division and their partner Moonshot CVE, which openly sells services to governments to track and manipulate search results for targeted users. These users targeted by Jigsaw & Moonshot CVE’s government clients have their search history, location, and identifying fingerprint stored in a database. [32b]
7) Recording and saving audio of your private conversations [16] [17] [18]

Google’s Android has the microphone constantly recording and saving your intimate personal conversations against your wishes for their profit and power. As an extensive academic study of tech patents by Consumer Watch Dog points out, Google will claim this is only to find out if you said the words “Google Assistant,” but yet they have publicly filed patents to scan audio conversations and any available visuals on a variety of home smart devices to identify who is speaking, what you’re interested in, and what you’re doing for the purpose of targeted advertising. [15]

Tracking what you say, what you like, when you sleep, and even when you go the bathroom, goes well beyond Google Assistant helping you do a quick search and would instead be considered an all-inclusive surveillance. [15]
In addition, they’ll allow 3rd party apps to record you without your knowledge because of poor permissions control. As University of California Santa Barbara cybersecurity researchers presented at a BlackHat European conference, 3rd party apps like Silverpush can play high frequency audio, which is invisible to the human ear, on another device like a television ad or mall kiosk. Then your phone’s mic picks up the frequency, to rat out your real identity or location. [34]

Silverpush’s advertising system is embedded into many “free” apps on the Google Play Store. These doctoral researchers warned of the dangers this presents by being connected to wide-spread platforms like Google Ads. To demonstrate this, they played video of their lab experiment, which de-anonymatized a laptop through Tor Browser, because of an Android’s mic next to the laptop’s speakers, which was signed in to a Google account. [34]
Is the Data Sold?

Google has marketing propaganda which claims that they are merely selling advertising space on your devices and not selling the data itself. However, this claim is misleading in a number of ways.
First, not only is advertising sold by demographics or interests, but in addition, Google also allows its advertising customers to target users by name, email, or device ID and reach them almost anywhere. [1] So advertisers can target you specifically and then serve you anything on your specific device by name.

Second, while it’s true that Google technically doesn’t sell your actual name to the advertiser, when your device interacts with an ad, the third party advertiser can easily use your IP address, cross-site cookies, and/or browser fingerprinting to identify you. For example, suppose an advertiser runs an ad for an ebook on how to get out of debt. The advertiser could collect the IP addresses of anyone who clicks it, and so they’d know whose indebted.

“I think the big problem is that we give much more data to Google than it needs,” said Guillaume Chaslot, former Google engineer who worked on YouTube’s recommendations algorithm. [4a] Chaslot’s first-hand experience with Google’s spyware and manipulation inspired him to create the non-group AlgoTransparency.org, which openly says in it’s manifesto, “algorithms don’t have your best interests at mind”. [4b]
Play Store and Chrome Extensions Leak Data

Third, the Google Play Store and their Chrome Browser Extension Store leak application and user data directly to the app’s developers. This is sensitive private information, and these third party app developers are NOT carefully vetted, as almost anyone can put an app in the Google Play or Chrome Extension Store with minimal screening. Examples: [21] [23] [24]
Mental Outlaw
“Mental Outlaw” is a cybersecurity Youtube video influencer who is constantly having his videos about torrents flagged by Google as “dangerous content”. He points out how ridiculous this is because Google does so little to stop real dangerous content. One of the numerous examples he’s given is the Chrome webstore featuring extensions that are malicious hacking malware, which does URL injections to force online shoppers, without their knowledge, to use the malware creator’s affiliate links when they shop online. [22b] These 5 popular extensions got over 1.3 million downloads, which got the attention of McAfee Labs, the research department of the respected anti-virus company.

From McAfee Labs’ articulate research, this is huge security risk because not only is your personal data, like name and location, sent to malicious actors, but the attacker can forward the URL to any site they want. So you might think you’re going BestBuy.com, but it’s really the attacker’s bullshit site to get your credit card info. [22b]

Youtuber Mental Outlaw points out how ludicrous it is that not only did Google allow 1.3 million people to download these extensions, but they have featured status on the Google Chrome store. [22a] And not only does Mental Outlaw find similar malware in the Android Play Store, but Google has changed how apps disclose permissions to remove themselves of liability. Starting in mid-2022, Google has the app developers themselves disclose what permissions the app uses, so Google does not have to do any research. This is a conflict of interest, since app developers are self-reporting what information they get access to, and the end user may not properly be able to evaluate it. [19] [20a]
Sell it via Cookies

Google’s defense to these types of criticisms has always been that they don’t “sell your data” directly. But as laid out in research from the tech-savvy lawyers at the Electronic Frontier Foundation, Google allows advertisers to connect their cookies with Google’s in order to process data on the customer. This process is called “cookie matching” and essentially allows Google to sell the advertiser your information through a cookie. [1]
In the European Union, if Google were caught selling this data directly, it would be illegal. [27] [28] [29] So instead Google finds sneaky work-arounds such as the cookie matching, which allows them to appease the regulators and make statements like “we don’t sell data, we just use the data.” [1]

Conclusion

The more influence that Google has in our society, the more difficult it becomes to avoid their fingerprinting. If every website has a Google Captcha and everyone you talk to demands you talk to them on Gmail, then Google has become the gatekeeper for overseeing all human behavior. They can use this power to influence who sees your messages and what information you are able to find.

By using Gmail or Google Docs, you’re forcing and enabling Google to fingerprint your loved ones or friends. Even if you think you’re doing nothing illegal, you assume that Google will give you and those you care about an equal opportunity for your business to thrive. They can reduce Google’s search traffic to your website, or bounce your emails to potential employers or customers. They can buckle your business at the knees if they think it fits its agenda and by giving them so much information you’ve completely surrendered your freedom.
Well what is their agenda?
In our next article, we’ll discuss Google’s censorship ability to shape society and how affects you.
The Sources for this article can be found here.
Related Articles
Big Tech Abuses Medical Privacy
February 25, 2023 No Comments
In the US, your medical records are protected by HIPAA but your internet medical browsing history on websites like WebMD is NOT. That is the
Read More »
Browser Fingerprints Lead to Price Discrimination
February 25, 2023 No Comments
Some people mistakenly believe they do not need to worry about online privacy because they have “nothing to hide.” In reality, your digital identity expressed
Read More »
Avoid this Monero Vulnerability
February 25, 2023 No Comments
We love Monero. It’s our favorite and number one recommended cryptocurrency. However, it does not offer completely perfect anonymity under all circumstances because there are
Read More »
How to Reduce Google’s Control Over You
February 25, 2023 No Comments
There’s a huge number of steps you can take to reduce Google’s power and influence over your business and personal life. You would get a
Read More »
Google Censors Freedom
February 25, 2023 No Comments
This article presents evidence that Google promotes an agenda of centralized control through systematic censorship on its search, email, video, app store, and ad platforms
Read More »
Session username: Simple / Signal #: +855 68 504 905
Web 3 on IPFS: SimplifiedPrivacy.x
Tor Onion: privacypkybrxebcjicfhgwsb3coatqechwnc5xow4udxwa6jemylmyd.onion
Nostr Public Key: npub14slk4lshtylkrqg9z0dvng09gn58h88frvnax7uga3v0h25szj4qzjt5d6
[email protected] / @Matrix:SimplifiedPrivacy.is
9 notes
·
View notes
Text
Reasons to go for an iPhone 8 plus parts for sale for better technology service

It is true that other technology is not as an essential to your daily routine than your smartphone. It keeps you connected with everyone. It is your companion on site at events. It includes all of your sensitive data. Like everyone, you may feel helpless without it. That’s why it’s essential to have the latest smartphone you can receive.
1. You can’t update to the advance operating system.
If your device manufacturer doesn’t deliver an upgrade to the most recent OS version, it’s time to go for iPhone 8 plus parts for sale. Your hardware may be so backdated that it easily cannot be supported by anymore. Like, you may have an old processor. A device with a 32-bit processor unable to run with a 64-bit OS, This is exactly the same with iOS 11, which cannot be downloaded on old iOS devices like iPad 4 or iPhone 5. When purchasing a brand new Android phone, it assures it runs the latest update of the Android OS, which is not assured.
2. You can’t download security patches anymore.
As you love to travel and you have to take help public Wi-Fi. Therefore, it is essential you do not subject yourself to security rules. If you can’t update to a new OS, at least on an OS version that receives present security patches. There is article which explains how you can define if your Android version is not able to supported. Definitely a sign to get a new device! If you opt for Android, select a manufacturer that is a best Google partner and automatically pushes those updated monthly patches. Or opt for some other phone, as they like to offer support for a long span of time.
3. Your manufacturer does not supporting your device.
Although much company tends to support security updates much longer, if your device is more than six years old, you are on the old stock. Check phone website to see if your device is regarded obsolete. These devices can be so that network traffic may not be crafted with the updated protocols. This may deliver your sensitive data to others.
4. Your phone is very slow
Even after reset, your device is not responding. You are opening apps or pressing switches and it appears like you are commencing Windows 95. Lots of time you get to drink a cup of tea. These are symbols that it is time you need for a faster processor that can tackle your shiny new OS update. Updated acknowledged devices were being slowed down to slow down battery life, but if your device is still slow after changing the battery, it’s time to regard upgrading your phone.
2 notes
·
View notes