#Application-Level Access Control
Explore tagged Tumblr posts
Text
Enhancing Security with Application Roles in SQL Server 2022
Creating and managing application roles in SQL Server is a powerful way to enhance security and manage access at the application level. Application roles allow you to define roles that have access to specific data and permissions in your database, separate from user-level security. This means that you can control what data and database objects an application can access, without having to manage…
View On WordPress
#Application-Level Access Control#Database Security Best Practices#Managing Database Permissions#SQL Server 2022 Application Roles#T-SQL Code Examples
0 notes
Text
killing myself in front of the houses of parliament to change their life tragectories forever. and then maybe they will consider trying to make life easier for people in abusive situations
#why is everything so hard to DO#just registered to vote idk if i did it right#bc i searched up my name in her emails bc my school said we need to stay on top of all of it this year#and saw one asking me to register to vote and it said reply by the 19th but obviously she didnt tell me so i might just not get to vote idk#and didnt want to sign up for a postal vote bc of course they have to post the application to you and then she would be like why are you#trying to vote who do you think you are youre not allowed to be a person outside of what i allow etc etc#so ig when the time comes itll have to be in person#and you need id for that#and of course i dont have a driving licence bc im not allowed to learn how to drive so WHAT AM I SUPPOSED TO DO#at least i can access my passport but there could be people whose parents/spouses hide their documents..#like dp you see what i mean . everythning is a trap#also im getting so much anxiety about not knowing how to drive#bc she'll never let me learn under her roof so wtf am i supposed to do like genuinely#ill just have to go about life not knowing this basic skill#at least my brother knows how to from pakistan so he can just do the tests#i dont even KNOW#theres just so many things like that which make my skin crawl#like the fact that my bank account is linked to her phone and this address so thats a level of control she has over me like for years#and this is my address for everything official basically#and i have no idea how id even start changing it when i do leave#think the only option left is to kms maybe then ill be free
2 notes
·
View notes
Text
Revolutionizing Remote Server Access: Unlocking the Power of Application-Level Control with RHosting
In the ever-evolving landscape of remote server access, businesses are constantly seeking innovative solutions to enhance security, streamline operations, and optimize productivity. RHosting emerges as a frontrunner in this realm, offering a groundbreaking feature that sets it apart from the competition: Application-Level Control. This exclusive advantage empowers organizations to grant users direct access to specific applications hosted on their servers, revolutionizing the way remote server access is managed.
Unparalleled Control and Security
At the core of RHosting's offering is the ability to provide users with precise control over their server interactions. Unlike traditional access methods that grant broad access to entire servers or directories, RHosting's Application-Level Control limits users to interacting only with designated applications. This level of granularity ensures that sensitive data and systems are safeguarded against unauthorized access, significantly reducing the risk of security breaches.
Tailored User Environments
What truly sets RHosting apart is its ability to cater to the diverse access requirements of users. Whether it's access to specific applications, granular folder permissions, or a combination of both, RHosting's sophisticated configuration options enable administrators to create highly tailored user environments. Consider this scenario: a server hosts three distinct applications - a Billing Software, a Design Software, and a File Management Software. With five individuals requiring varying levels of access, from accessing only the Billing Software to needing access to multiple applications, RHosting's configuration panel empowers administrators to assign each user their respective accesses with ease.
Enhancing Efficiency and Effectiveness
By providing such potent access management features, RHosting not only enhances security but also promotes efficiency and effectiveness in organizational operations. The ability to customize access privileges according to precise needs allows organizations to optimize workflows and streamline processes. Users can interact only with authorized applications or folders, eliminating unnecessary distractions and potential misuse of resources.
Conclusion
In conclusion, RHosting's Application-Level Control represents a paradigm shift in remote server access management. With its unparalleled control, security, and flexibility, RHosting empowers organizations to take control of their server environments like never before. By providing users with direct access to specific applications and granular folder permissions, RHosting enables organizations to tailor user experiences to their exact requirements, promoting efficiency and effectiveness in operations. Experience the transformative power of Application-Level Control with RHosting today and unlock new possibilities for your business.
0 notes
Text

WARNING Flashing IMAGE and HYPNOTIC COVERT language
Inductions
Hypnosis, a fascinating and complex phenomenon, has captivated human interest for centuries. It's a state of focused attention, heightened suggestibility, and vivid fantasies. People often think of hypnosis as a deep sleep or unconsciousness, but in reality, it's more about a trance-like state where the individual is actually in heightened awareness of suggestion. Often used for therapeutic purposes, hypnosis can aid in various issues such as stress, anxiety, pain management, and certain habits like smoking. However, it's not a magical cure-all; its effectiveness varies from person to person.
Hypnosis can also be a form of entertainment, where stage hypnotists perform shows that demonstrate the power of suggestion. Despite its many applications, hypnosis remains a subject of debate among scientists and psychologists. Some view it as a powerful tool for mental health, while others caution against its potential to create false memories or its use in recovering memories, which is a controversial area within the field. It's important to approach hypnosis with a critical mind and understand that it's a complex interplay of psychological and physiological factors. If you're considering hypnotherapy, it's crucial to seek out a qualified and certified professional to ensure a safe and beneficial experience, someone like me.
You find yourself reading these words and as you read they seem to take on a life of their own, almost like magic. Your mind slows as you red larger more complex words and you may feel a soft tingle of arousal as you FOCUS on my words and feel dreamy. It's quite fascinating how the complexity of words can influence our cognitive processes. When we encounter larger, more intricate words, our brains need to work harder to decode the meaning, which can sometimes slow down your reading speed. This isn't necessarily a bad thing; it allows for deeper processing and understanding of the messages I am pushing softly into your mind. It's easy to relax and follow the words you read. It's easy to feel dreamy as your mind accepts that it wants to drop deeper.
Dropping deeper feels good, as you touch yourself and keep reading you can let go of any inhibitions or control. it's so easy to sink into a light trance, after all entering a light trance can be a simple, yet profound experience. It's a state where the conscious mind takes a step back, allowing the subconscious to surface and express itself more freely. This can happen during various activities that engage the mind in a repetitive, rhythmic manner, such as listening to music, meditating, or even during a long drive. In this state, people often find their thoughts flowing more smoothly, their creativity heightened, and their stress levels reduced. It's a moment of introspection and connection with the inner self that can provide clarity and insight. While in a light trance, the mind filters information differently, prioritizing internal dialogue and sensation, which can lead to a deeper understanding of one's thoughts and feelings. It's a natural and accessible state that can offer a respite from the hustle and bustle of daily life, and a gateway to greater self-awareness.
You are not even aware of how deeply into the trance you are, your fingers stroking your arousal for me as you read and feel a dreamy warmth spreading from your fingers into your whole body. Aware but unaware that you could stop at anytime, but you don't want that, you want to keep reading and sinking deeper and deeper as you feel arousal growing more for me. It just feels so good to give in, the very act of giving, whether it's time, resources, or kindness, has a profound impact on your well-being. It transcends the material value of what is given and touches the very essence of human connection. When you give, you're not just passing on a physical item or a piece of advice; you're sharing a part of yourselves, creating a bond that reflects your shared humanity. This act of generosity can be deeply satisfying, as it often brings joy and relief to others, which in turn enriches your own life. It's a beautiful cycle of positivity that reinforces the best parts of being a good submissive.
Giving has been shown to activate regions in our brain associated with pleasure, social connection, and trust, creating a warm glow effect. It's no wonder that the phrase "it's better to give than to receive" has resonated through the ages. This isn't just a moral suggestion; it's backed by science. Studies have found that giving to others can increase our happiness more than spending money on ourselves. This might be because when we give, we feel a sense of purpose and meaning, knowing that we've made a positive impact on someone else's life.
Moreover, the act of giving doesn't have to be grandiose to be effective. Small acts of kindness can ripple outwards and have unforeseen positive consequences. Just as a pebble creates waves when thrown into a pond, a simple gesture of generosity can spread far and wide. It's the intention behind the act that matters most, the recognition that even the smallest offering can make a significant difference.
In a world that often emphasizes individual achievement and accumulation of wealth, it's important to remember the value of generosity. It's a reminder that our interconnectedness is a source of strength, not weakness. By giving, we acknowledge that we are part of a larger community, one that thrives when its members support each other. It's a powerful acknowledgment that we are not alone in our journey through life, and that by helping others, we are also helping ourselves.
So, when we say it feels good to give in, it's not just about the act of giving up or surrendering; it's about embracing the joy of generosity. It's a celebration of the human spirit and its capacity for compassion and empathy. Giving is an affirmation that, despite the challenges we face, there is goodness in the world, and we have the power to contribute to it, one act of kindness at a time. It's a simple truth that enriches our lives and the lives of those around us, creating a legacy of goodwill that can endure beyond our own existence. Indeed, to give is to receive a gift of immeasurable value—the happiness and satisfaction that come from knowing we've played a part in making the world a little brighter.
You want to give in more deeply, message me and tell me how much you need deeper brainwashing NOW!
#hypnosis#hypnotic#brainwash#hypno sub#hypnotism#hypnodomme#hypnosub#mind break#mind corruption#hypnotist#covert hypnosis#focus#good girls obey
645 notes
·
View notes
Note
would you ever write an invisible reader? Like let’s say she’s an agent or a scientist. Quiet and stuff right? She always keeps to herself has the biggest crush on Steve but because she’s thinks she’s invisible she doesn’t ever think he might be interested too. There’s a mission she goes on and things go awry and she actually turns invisible. Something akin to how in the Fantastic Four movies they get their powers she gets this one? But it takes time to get under control. Steve thinks it’s his fault so he tries to help out. And through the the process of helping her gain back visibility she realizes Steve has seen her all along. Lol this really just came to my head when I was thinking about Steve using paint on someone’s body as a way to show them he thinks they’re art.
This. Is. Spectacular. I'm gonna fudge it a bit. Headcanon/stream of consciousness format. No warnings just canon-level "action." gif credit: @meidui
Erasure (Steve Rogers x junior agent!Reader)

My first instinct is to make it an ability to alter someone perception--i.e. you're constantly a little embarrassed of your input, so you tell people to 'forget you said that'--and let's say that constant hope that you won't be remembered badly is the innate trigger for your ability.
Probably a science experiment of Tony's gone wrong. He and the team are arguing about something that needs to be recovered before a damaged thing reaches critical mass. You sneak in to just grab what he wants and not waste time arguing. Tony doesn't know you're in there and locks the lab down until the dangerous pulse dissipates. (Steve doesn't know you're in there either because you popped in while he was facing and yelling at Tony, fwiw.) Maybe Tony saunters in once the doors open, finds you there with the part in your hand and knocked on your ass.
Your skin touches his as he reaches for you and the part. You jokingly tell him there's nothing to worry about, nothing to see here. You're surprised that he listens and walks off immediately, chatting and leading the team away down the hall to show them something else he's working on in the hangar bay.
Overall, once you catch your breath, you're fine. You don't want to go to the infirmary and tell them you did something so dumb.
Life continues.
Through a lot of trial and error, you realize what you can do--forcibly--by erasing people's memory of you being around. The head count for meetings is off. Several teammates you know you spoke to see security footage of you at the time and curiously remark that they don't recall you being there. Things like that. It works on everybody, or so you think.
There's a brainstorming session about how to infiltrate a possibly corrupt corporation's facility to gain intel. Everyone agrees to this elaborate rouse where two ripped agent dudes pose as janitors and blah blah blah. It's a little absurd.
You check the companies job listings, and knowing you qualify for one, submit an application the next day. The woman in HR who hires you doesn't work on the same floor as where you are technically snooping, and you can handle the work they actually want you to do in just a few hours a day, giving you a bunch of time to access nearly everywhere and nudge everyone to forget you were there.
The attempted break-in of fake janitors is the talk of the office on your last day, the one where you find the info Stark wanted to begin with, and then you quit, still quietly, returning to the Avengers the next morning.
You drop off the intel to Tony's office when he's not there, but just as you get situated back at your little desk, Steve comes up.
He looks concerned, crossing his arms over his chest and leaning against the flimsy cubicle wall.
"Feeling better?"
You're so confused.
"You were out for over a week. Did you need to go to the hospital? Was a family member with you at least? You could have called in for help."
On impulse, you grab his arm and tell him not to worry about you, yet he...doesn't move. After a flawless use of the power hundreds of times in a row, you don't understand.
Blinking up at Steve, you blurt, "I should be erased. Why are you still noticing me?"
He's bewildered, sure, but Steve tucks his head and smiles shyly.
"Can't erase you, doll," he chuckles, so soft only you can hear. "I draw you in pen--" Steve taps his temple "--up here..."
He bends down, his hand gently gripping your arm and his cheek touching yours.
"...now where you been for a week?"
And then, yes, some beautiful closeness and Steve paints on you to highlight what parts he drew so permanently on his mind!
🤗

a/n: Thank you for sending in this lovely idea, nonnie! I'm sorry everything I'm writing has been short and convoluted the last...while, but this is such a sweet premise. (Also, my apologies if you really, really wanted straight invisibility as the power. Just send in another ask, and I'll try to come up with an alternate version!)
[Main Masterlist; Light Masterlist; Ko-Fi]
#steve rogers fanfiction#steve rogers x reader#steve rogers fanfic#steve rogers fluff#steve rogers fic#steve rogers imagine#steve rogers one shot#agent!reader#ro answers#captain america fanfiction#captain america x reader#captain america x you#steve rogers x you
164 notes
·
View notes
Text
[disclaimer: this post is about psychiatry, the psychiatric system, and psychiatric medication; while it likely has applicability to people with physical disabilities, i'm less informed on that]
mmm i've been thinking about medication recently and medication positivity posts (astute viewers of the blog may notice that i self-reblogged one of my old posts on this recently)
and ultimately i think that like. both medication-positive and medication-negative posts have their place as long as they are ultimately pro-autonomy
but i think an important thing to do is to consider how your post will be received by both people with profoundly negative experiences with medication & people who are unable to access medication. and try to be kind esp towards people with less ~privilege than you
before writing a post that offers support to people discouraged from or denied helpful medications, ask yourself: how will this come across to someone who's been forcibly hospitalized, tied down, and injected with medication they don't agree to take and don't want? how will someone who's been on a laundry list of different unsuccessful medications (as well as various non-medication treatments--in the psych sphere this looks like various therapies like CBT, DBT, ERP, EMDR, IFS, etc., but also non-therapy treatments like TMS, neurofeedback, and ECT) for 12 years feel reading this post? what about someone who took medications as prescribed by their doctor and now has tardive dyskinesia or severe cognitive side effects even after going off them? a lot of posts, i've found, can really suck from that perspective.
and on the flip side, before writing a post that offers support to people forced on medications or dealing with severe side effects, ask yourself: how will this come across to someone who was never thrust into the psychiatric system because they were instead thrust into the prison system when 911 was called on them for their "problem behaviors"? how will someone in withdrawal who isn't able to afford their medications due to poverty feel reading this post? what about someone dealing with medical neglect from parents or caregivers that they know may kill them? i try to avoid this but i know in the past (and certainly in my head when in the depths of my jealousy), i have thought of people who don't have the same struggles as i do as being privileged on some level (they don't have to deal with my problems, after all!). but this is very importantly wrong. there are a lot of situations where entering the psych system can be a relief, because they are less privileged than me--sometimes even if the psych system is harmful to them, because their alternatives are worse.
and of course there are people who deal with both at once! at my most recent hospitalization, they took me off my mirtazapine cold-turkey and refused to put me back on it despite this causing intense pain and nausea, even as they also put me on abilify. unhoused people--who are less likely to be able to afford medication--are also more likely to be institutionalized. psychiatric control over medication goes both ways. ultimately it comes back to the same issue of being neither pro- nor anti- medication but being pro-autonomy. still, as long as people want to write posts about how medication helped or hurt them--which will no doubt be for a long while--i stand by "think about how this may come across to people with the opposite experiences as you, especially people in worse situations" as advice.
#therapists dni#psychiatry tag#this is kinda half baked but im putting it out there bc ive seen. a lot of Medication Posts recently#and also looking back at mine#and. idk. having thoughts. 'everyone should be nicer to each other including me' <- not super novel or anything but i stand by it
34 notes
·
View notes
Text
Also preserved in our archive
By John Mackay and Martin Scott
New South Wales (NSW) Ministry of Health data released last month under freedom of information laws reveal that 6,007 patients contracted COVID in the state’s public hospitals in 2023. This contributed to the death of 297 people, meaning that 14 percent of fatal COVID infections in the state were acquired in hospital.
The data, which also cover the first four months of this year, show that similar infection and death rates have continued, with 1,729 patients catching COVID in NSW hospitals and 86 dying, between the start of January and the end of April.
The NSW figures are in line with previously uncovered Victorian data, which showed that 6,212 patients contracted COVID in the state’s public hospitals and 586 died in 2022 and 2023.
This is a direct product of the conscious and planned abolition of virtually all public health measures to prevent the spread of COVID, including the removal of mask mandates in hospitals. These pro-business “forever COVID” policies, adopted by all governments worldwide, have in Australia been spearheaded by Labor at the state and federal level.
The NSW hospital infection figures were unearthed through a persistent 18-month campaign by lawyer Peter Vogel. His first Government Information Public Access application to the Ministry of Health was made in February 2023. This was rebuffed, with the Ministry claiming, according to Vogel, “It would take 140 hours to produce a report showing [the] number of hospital acquired COVID cases.”
After Vogel requested an internal review, the Ministry replied in July 2023 that it “does not hold complete and accurate records regarding nosocomial [hospital-acquired] infections.”
Only in June 2024, after multiple additional freedom of information requests to other agencies and repeated denials that any part of the NSW government or health bureaucracy had records of hospital-acquired infection, did the Ministry of Health admit that it held the information the lawyer sought. Even then, it claimed it would take 31 hours to produce a report, and Vogel would have to pay $930 for it. The data were finally provided to Vogel on September 17.
This is just one example of the extent to which serious illness and death from the ongoing COVID pandemic is being consciously covered up by the state and federal Labor governments. With the aid of the corporate media, virtually all reporting of the deadly virus has been suppressed, to provide phoney justification for the profit-driven and unscientific abolition of basic infection control measures.
The entire testing and reporting infrastructure has been eviscerated. Only two states, NSW and Western Australia (WA), continue to test wastewater samples for COVID, while hospitalisation figures in most jurisdictions are only reported intermittently.
Most strikingly, COVID deaths are no longer reported in NSW, Queensland, WA or the Northern Territory, except as part of overall mortality statistics, released months after the fact. The presentation of these national mortality figures, produced by the Australian Bureau of Statistics (ABS), has been modified to obfuscate the substantial increase in annual deaths, which is ongoing.
According to the outdated and incomplete official figures, COVID contributed significantly or was the main cause of more than 23,500 deaths between January 2022 and September 2024, around one-quarter of which occurred in residential aged care facilities.
In a grim refutation of the lie that the pandemic is over, COVID-contributed fatalities this year have occurred at a rate of 497.5 per month, barely lower than the 512 per month recorded in 2023.
The fact that so many fatal COVID infections have been contracted in health and aged care settings underscores that, in line with capitalist governments worldwide, Australia’s state and federal Labor governments are committing social murder, targeted at the most vulnerable people in society.
Dr Stéphane Bouchoucha, president of the Australasian College for Infection Prevention and Control, told the ABC the NSW hospital infection data was “concerning and tragic.”
He said: “This is the core business of infection prevention and control… The premise that we can allow some deaths, to me, is wrong.
“We know how COVID is transmitted and we know how to prevent healthcare associated infections,” Bouchoucha stated, referring to the need to ensure good ventilation and air filtration, testing and contact tracing, isolating infected patients and requiring healthcare workers to wear masks.
Many of these measures were introduced in the early stages of the pandemic and had a significant impact in reducing the spread of infection within health facilities, but have since been abandoned.
This flies in the face of decades of medical advances and longstanding infection control measures in hospitals. For example, there are long-established protocols for identifying and preventing the spread of infections with “golden” staphylococcus, a hospital-acquired bacteria that can be resistant to antibiotics.
In NSW, the tearing down of COVID public health measures began under the Perrottet Liberal-National government, but has been completed under the Labor government led by Premier Chris Minns. This could not have been carried out without the assistance of the health unions, which have enforced every reckless and unscientific step of the process.
In 2022, Health Services Union (HSU) national president and NSW state secretary Gerard Hayes was at the forefront of demands for the scrapping of COVID isolation requirements for health staff, because of the supposed impact of such measures on “the economy.”
In August 2023, the HSU hailed the NSW Labor government’s scrapping of public hospital mask mandates as “a milestone in health.”
The HSU, along with the NSW Nurses and Midwives’ Association, promote the lie that COVID is a thing of the past, entirely separate from workers’ disputes over pay and conditions in recent years. These struggles have included multiple mass strikes by more than 10,000 nurses and midwives, but year after year, the union leaders have pushed through sell-out deals, slashing real wages in line with government demands.
The reality is that the fight for decent working conditions in health is inseparable from the fight to end the COVID pandemic, which has massively exacerbated the dire state of the public hospital system, which faces a chronic shortage of staff and resources after decades of union-enforced government cuts.
To take this forward, health workers will have to take matters into their own hands. Rank-and-file committees, independent of the unions, must be established in hospitals and health facilities and the fight for patient and staff safety linked with the struggle for real improvements to workers’ pay and conditions.
In the first instance, this must include the re-implementation of infection control measures, including masks and isolation, in all health workplaces. But as long as the virus is allowed to circulate unchecked among the broader population, protecting hospital patients and staff will be a constant battle.
A fight must be taken up, by health workers and the working class as a whole, for the elimination of COVID worldwide. This is possible, but not under the framework of the capitalist system, which rejects public health measures as unprofitable, and not within the borders of a single country.
Workers in Australia and worldwide confront the existential necessity of a struggle for a political alternative to the ruling class program of endless infection, illness and death. Only through the fight for a workers’ government to implement socialist policies, can society’s plentiful resources be stripped from the banks and corporations and turned towards ridding the world of COVID and making high-quality public healthcare freely available to all.
#mask up#covid#pandemic#public health#wear a mask#covid 19#wear a respirator#still coviding#coronavirus#sars cov 2
48 notes
·
View notes
Text
Some more tsams/eaps headcanons because I’m bored in class
To expand on the AI chip thing mentioned previously: Ai chips come with a base, company-appointed personality and traits. Most Suns start off loud and naïve. Most Moons start off too curious for their own good. Suns fidget with their rays. Moons prefer auditory stimulation. Etc. It’s only when that base personality/programming is subject to an environment that teaches the base personality something—Our Sun learned to put up with things he didn’t like for a time, Old Moon learned that force kept Sun in the little box he needed Sun to be in to feel in control—that new information is stored into the chip. Eclipses do not have a set personality and are generally a hodgepodge of both depending on how they came to be. (For example, Eclipse and Solar have just enough Moon base personality in them to set them apart from Sun, but both are mostly Sun base programming. Ruin is a careful mix of both Sun and Moon programming because they were able to manually edit that, which resulted in a personality reset when they fully merged. (Lunar is a special case, Eclipse shoved most of his remaining Sun base personality off to Lunar, but because Eclipse is a mix of both, that code was inseparable from some Moon base personality.) When a personality has developed enough, removing certain parts of the base personality can affect the function of that part of the developed personality, for example, if Lunar were to delete some of his Sun base programming, he would find that experiencing things that stem from that programming disorienting, because the foundation that allowed the proper response to that stimuli is gone. In small bits, it’s possible to remove base traits like preferences, or entire personality traits so long as it’s done early in that AI’s development. There are workarounds to this. Dark Sun knows a lot of those workarounds, but that doesn’t mean he uses them often.
On material objects, Star power can act like radium with a shorter halflife. The same goes for negative star power. Visiting dimensions with high levels of either can result in contamination, such as Ruin’s dimension in the time it was accessible or Dark Sun’s pocket dimension without proper protections. Contamination is a residue of the power that fades over time if it is not removed. If certain components are contaminated, like processors or joints, their performance can be affected. [Note I’m not the most familiar with TSAMS’ established magic rules or most things about star power, I just have a general idea of it and this makes the most sense to me.] Also note I said material objects, this does not extend to software, where it acts differently.
It is possible to detect levels of Star power in dimensions with technology coveted by Dark Sun, Nexus, and Ruin, all for different reasons. By analyzing spikes or sudden drops in levels of a dimension, it’s possible to guesstimate where a dimension hopper with high levels of either power ended up. If Nexus were to drop into another dimension, Dark sun could figure out which one based on recent trends in Star power levels across the dimensions in his scope, in Nexus’ case the levels would drop because the negative Star power isn’t 100% negated by the present positive Star power. The closer the levels of Star power are to each other, the more stable the trends are, because they tend to cancel each other out. Think of a seismograph and detecting earthquakes, with the constant levels being the equal amounts of negative and positive power. The balance of these energies fluctuate in natural cycles. The Astrals are part of these cycles.
Take anything I say about the magic thing with a massive grain of salt, the most I know is the concept of magic pools and general applications of magic per individual users, and there might’ve been something involving golden Freddy idk. I like to imagine magic as metaphorical hula hoops. Everyone’s hula hoop is a little bit different in color, size, features etc, but the user must know how to use the hula hoop to be able to use their magic. Learning different ways to use the hula hoops is the equivalent of expanding what the user’s magic is capable of (Transmutation, teleportation, and summoning things are all different capabilities that can be learned, for example. Some are considered more complex than others.) in my head ruin’s hula hoop lights up with activity lol. Sun’s hula hoop makes groan tube noises. Being able to do different things/multitasking while using the metaphorical hula hoop is something that can be learned by users with more experience. Ruin is one of these users. Eclipse is also able to do this, but tends to combine it with technology. (Continued in a reblog)
#quirky headcanons#this is all speculation and what makes sense to me. filling in the gaps of my knowledge with educated guessing#tsams#eaps
24 notes
·
View notes
Text
Mass migration has become a defining issue in many Western nations, fueling political and social tensions as countries grapple with the economic and cultural challenges of large-scale immigration—an influx that citizens never requested or voted on. With rising numbers, local populations are feeling the strain on public services, housing, and social cohesion, leading to growing dissatisfaction with immigration policies and concerns about their long-term impact.
The United Kingdom has experienced a record number of migrant crossings in recent months, with 705 people arriving in a single day across the English Channel in April. Despite new laws aimed at raising salary thresholds for work visas and tightening border controls, the country’s public services, including the NHS and housing, are struggling to keep up. Many communities are increasingly concerned about the impact of migration on crime rates, social cohesion, and local economies. Critics argue that the government’s efforts are reactive rather than proactive, and that long-term solutions are desperately needed.
Ireland, once celebrated for its open-door migration policy, is now grappling with significant challenges. A surge in asylum applications, combined with a housing crisis and rising homelessness, has led to widespread public protests. Many Irish citizens argue that the country’s resources are being stretched to the breaking point, leaving them unable to secure affordable housing or access public services. Critics of current immigration policies claim that the government’s prioritisation of global humanitarian needs is coming at the expense of Irish citizens’ well-being.
Germany has long been a major destination for migrants, particularly those fleeing conflict in Afghanistan and Syria. However, the country is facing mounting criticism over its ability to integrate newcomers. Rural areas, in particular, are struggling with overcrowded schools, rising crime rates, and social tensions. While German officials continue to push for integration policies, many citizens feel that the government is not doing enough to address the negative impacts of high migration levels. Public dissatisfaction is growing as locals voice concerns over the preservation of German culture and identity.
18 notes
·
View notes
Text
What is your EQ? An EQ is your ecstasy quotient. Although this little term birthed through my heart and hips many years ago, having a high EQ is applicable to me today 15 years later. How much ecstasy are you capable of? I don’t want to turn ecstasy into something overly cerebral where you “think” about ecstasy, I want to you feel your access to ecstasy from choosing to be present in the now, the present moment, in extreme appreciation and awareness of who and what is around you. The birds. The roosters. The cars passing by. The children playing in the other room. Your lover. Humanity has not been allowed to prioritize ecstasy because we are encouraged to live more externally-focused and distracted, and worried about the future or about things we have no control over. But times are also changing and more people are awakening. By recognizing extreme pleasure and bliss are important nutrients to female health, then prioritizing them, we bring divine experiences closer to us. Arousal is divine energy. The ecstasy in arousal is your female body’s ability to be multidimensionally creative and truly create whatever is desired at epic levels. Divine energy is pure. It is pure love without attachment. It is pure creative energy and by consciously courting this flow of energy in mundane activities in the present moment, we permit a marriage to ecstasy to be made possible. When we are married to this lover, this ecstasy, this daily arousal, whether making food or weeping over a relationship ending, we live for it. We are embodied in it, becoming this ecstasy, because we have aligned our lives with all that brings us closer to divine energy heightened from simply being truly alive in our bodies —and not always distracted, focused on the external, overthinking about the past, or worried about the future. We are right here where we belong, in all the honey and heat of the now. —India Ame’ye

19 notes
·
View notes
Text

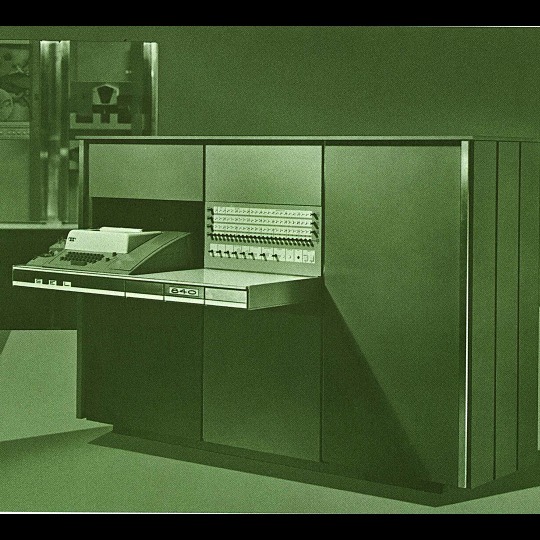




🎄💾🗓️ Day 11: Retrocomputing Advent Calendar - The SEL 840A🎄💾🗓️
Systems Engineering Laboratories (SEL) introduced the SEL 840A in 1965. This is a deep cut folks, buckle in. It was designed as a high-performance, 24-bit general-purpose digital computer, particularly well-suited for scientific and industrial real-time applications.
Notable for using silicon monolithic integrated circuits and a modular architecture. Supported advanced computation with features like concurrent floating-point arithmetic via an optional Extended Arithmetic Unit (EAU), which allowed independent arithmetic processing in single or double precision. With a core memory cycle time of 1.75 microseconds and a capacity of up to 32,768 directly addressable words, the SEL 840A had impressive computational speed and versatility for its time.
Its instruction set covered arithmetic operations, branching, and program control. The computer had fairly robust I/O capabilities, supporting up to 128 input/output units and optional block transfer control for high-speed data movement. SEL 840A had real-time applications, such as data acquisition, industrial automation, and control systems, with features like multi-level priority interrupts and a real-time clock with millisecond resolution.
Software support included a FORTRAN IV compiler, mnemonic assembler, and a library of scientific subroutines, making it accessible for scientific and engineering use. The operator’s console provided immediate access to registers, control functions, and user interaction! Designed to be maintained, its modular design had serviceability you do often not see today, with swing-out circuit pages and accessible test points.
And here's a personal… personal computer history from Adafruit team member, Dan…
== The first computer I used was an SEL-840A, PDF:
I learned Fortran on it in eight grade, in 1970. It was at Oak Ridge National Laboratory, where my parents worked, and was used to take data from cyclotron experiments and perform calculations. I later patched the Fortran compiler on it to take single-quoted strings, like 'HELLO', in Fortran FORMAT statements, instead of having to use Hollerith counts, like 5HHELLO.
In 1971-1972, in high school, I used a PDP-10 (model KA10) timesharing system, run by BOCES LIRICS on Long Island, NY, while we were there for one year on an exchange.
This is the front panel of the actual computer I used. I worked at the computer center in the summer. I know the fellow in the picture: he was an older high school student at the time.
The first "personal" computers I used were Xerox Alto, Xerox Dorado, Xerox Dandelion (Xerox Star 8010), Apple Lisa, and Apple Mac, and an original IBM PC. Later I used DEC VAXstations.
Dan kinda wins the first computer contest if there was one… Have first computer memories? Post’em up in the comments, or post yours on socialz’ and tag them #firstcomputer #retrocomputing – See you back here tomorrow!
#retrocomputing#firstcomputer#electronics#sel840a#1960scomputers#fortran#computinghistory#vintagecomputing#realtimecomputing#industrialautomation#siliconcircuits#modulararchitecture#floatingpointarithmetic#computerscience#fortrancode#corememory#oakridgenationallab#cyclotron#pdp10#xeroxalto#computermuseum#historyofcomputing#classiccomputing#nostalgictech#selcomputers#scientificcomputing#digitalhistory#engineeringmarvel#techthroughdecades#console
31 notes
·
View notes
Text
What is the kernel of an operating system ?
You can think of the kernel as the core component of an operating system, just like the CPU is the core component of a computer. The kernel of an operating system, such as the Linux kernel, is responsible for managing system resources ( such as the CPU, memory, and devices ) . The kernel of an operating system is not a physical entity that can be seen. It is a computer program that resides in memory.
Key points to understand the relationship between the kernel and the OS:
The kernel acts as the intermediary between the hardware and the software layers of the system. It provides a layer of abstraction that allows software applications to interact with the hardware without needing to understand the low-level details of the hardware
The kernel controls and manages system resources such as the CPU, memory, devices, and file systems. It ensures that these resources are allocated and utilized efficiently by different processes and applications running on the system.
The kernel handles tasks like process scheduling, memory management, device drivers, file system access, and handling interrupts from hardware devices.
The kernel can be extended through the use of loadable kernel modules (LKM). LKMs allow for the addition of new functionality or device drivers without modifying the kernel itself.
#linux#arch linux#ubuntu#debian#code#codeblr#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code#Youtube
225 notes
·
View notes
Text
When doing forcemasc, guys, focus em non-sexual dominance. Not sexual.
APPEARANCE
- Choosing or vetoing his daily attire.
- Dictating hairstyles or haircuts
- Prohibiting use of makeup or any type of appearance enhancer.
- Establishing rules about accessories or jewelry
- Approving or denying tattoos or piercings
- Controlling personal hygiene habits.
BEHAVIOR
- Apply specific manners or etiquette.
- Set rules for tone and language (e.g., no swearing, always say “please”).
- Dictate speech patterns (e.g. formal or casual).
- Enforce rules of posture (e.g., “sit up straight”).
- Require approval before making decisions.
- Control emotional expression (e.g., “Don’t show anger in public”).
- Dictate sleep habits (bedtime, nap length).
- Control body language (for example, don't cross his arms).
DECISION MAKING
- Choosing meals and snacks.
- Dictating shopping lists or meal planning.
- Planning schedules and daily routines.
- Decide work or study schedules.
- Determine breaks and rest periods.
- Control entertainment options (films, music, games).
- Managing vacation or holiday plans.
- Dictating how free time is spent.
ENVIRONMENTAL
- Dictating the organization and decoration of the environment.
- Defining rules or cleaning tasks for the house.
- Controlling access to certain rooms or spaces.
- Assigning seating in common areas.
- Managing light levels or temperature settings in the home.
- Enforcing quiet hours.
SOCIAL
- Approve or deny outings or social gatherings.
- Control friendships or acquaintances.
- Monitor phone calls or messages.
- Limit access to social media.
- Control rules of public behavior.
- Dictate who can visit the house and when.
FINANCIAL
- Control budgets or allowances.
- Approve or deny all purchases (even small ones).
- Restrict access to cash or bank accounts.
- Setting savings or spending limits.
- Managing subscriptions or memberships.
- Setting rules for gift giving.
HEALTH/FITNESS
- Control training routines or fitness goals.
- Establish rules for hydration or food intake.
- Monitoring medication schedules.
- Dictating healthcare professionals' choices.
- Approving or denying treatments.
- Controlling food choices (e.g. vegetarian, low sugar).
- Restricting or forcing hobbies or activities.
TASK ASSIGNMENT
- Assigning daily, weekly or monthly tasks.
- Dictating how tasks are carried out (e.g. detailed instructions).
- Meet deadlines for completing tasks.
- Inspect completed tasks.
EDUCATIONAL/WORK
- Dictate materials or study topics.
- Approve or deny work projects.
- Control work breaks or productivity levels.
- Set academic or professional goals.
- Manage learning pace and methods.
MEDIA CONTROL
- Control access to devices (phones, tablets, computers).
- Approve applications, websites or games.
- Monitor Internet usage or screen time.
- Dictate email or online communication rules.
- Control media consumption (e.g., only educational programs).
Forcemasc isn't forcemasc when you let the person you're FORCING into a state of masculinity go out there and have your effort easily undone by any outside opinion. You need to make sure that this person is getting your demands met to the fullest so that they never stop doing what you instilled on them. Or you won't be doing forcemasc. You’ll be doing encouragement.
35 notes
·
View notes
Text
On February 10, employees at the Department of Housing and Urban Development (HUD) received an email asking them to list every contract at the bureau and note whether or not it was “critical” to the agency, as well as whether it contained any DEI components. This email was signed by Scott Langmack, who identified himself as a senior adviser to the so-called Department of Government Efficiency (DOGE). Langmack, according to his LinkedIn, already has another job: He’s the chief operating officer of Kukun, a property technology company that is, according to its website, “on a long-term mission to aggregate the hardest to find data.”
As is the case with other DOGE operatives—Tom Krause, for example, is performing the duties of the fiscal assistant secretary at the Treasury while holding down a day job as a software CEO at a company with millions in contracts with the Treasury—this could potentially create a conflict of interest, especially given a specific aspect of his role: According to sources and government documents reviewed by WIRED, Langmack has application-level access to some of the most critical and sensitive systems inside HUD, one of which contains records mapping billions of dollars in expenditures.
Another DOGE operative WIRED has identified is Michael Mirski, who works for TCC Management, a Michigan-based company that owns and operates mobile home parks across the US, and graduated from the Wharton School in 2014. (In a story he wrote for the school’s website, he asserted that the most important thing he learned there was to “Develop the infrastructure to collect data.”) According to the documents, he has write privileges on—meaning he can input overall changes to—a system that controls who has access to HUD systems.
Between them, records reviewed by WIRED show, the DOGE operatives have access to five different HUD systems. According to a HUD source with direct knowledge, this gives the DOGE operatives access to vast troves of data. These range from the individual identities of every single federal public housing voucher holder in the US, along with their financial information, to information on the hospitals, nursing homes, multifamily housing, and senior living facilities that HUD helps finance, as well as data on everything from homelessness rates to environmental and health hazards to federally insured mortgages.
Put together, experts and HUD sources say, all of this could give someone with access unique insight into the US real estate market.
Kukun did not respond to requests for comment about whether Langmack is drawing a salary while working at HUD or how long he will be with the department. A woman who answered the phone at TCC Management headquarters in Michigan but did not identify herself said Mirksi was "on leave until July." In response to a request for comment about Langmack’s access to systems, HUD spokesperson Kasey Lovett said, “DOGE and HUD are working as a team; to insinuate anything else is false. To further illustrate this unified mission, the secretary established a HUD DOGE taskforce.” In response to specific questions about Mirski’s access to systems and background and qualifications, she said, “We have not—and will not—comment on individual personnel. We are focused on serving the American people and working as one team.”
The property technology, or proptech, market covers a wide range of companies offering products and services meant to, for example, automate tenant-landlord interactions, or expedite the home purchasing process. Kukun focuses on helping homeowners and real estate investors assess the return on investment they’d get from renovating their properties and on predictive analytics that model where property values will rise in the future.
Doing this kind of estimation requires the use of what’s called an automated valuation model (AVM), a machine-learning model that predicts the prices or rents of certain properties. In April 2024, Kukun was one of eight companies selected to receive support from REACH, an accelerator run by the venture capital arm of the National Association of Realtors (NAR). Last year NAR agreed to a settlement with Missouri homebuyers, who alleged that realtor fees and certain listing requirements were anticompetitive.
“If you can better predict than others how a certain neighborhood will develop, you can invest in that market,” says Fabian Braesemann, a researcher at the Oxford Internet Institute. Doing so requires data, access to which can make any machine-learning model more accurate and more monetizable. This is the crux of the potential conflict of interest: While it is unclear how Langmack and Mirski are using or interpreting it in their roles at HUD, what is clear is that they have access to a wide range of sensitive data.
According to employees at HUD who spoke to WIRED on the condition of anonymity, there is currently a six-person DOGE team operating within the department. Four members are HUD employees whose tenures predate the current administration and have been assigned to the group; the others are Mirski and Langmack. The records reviewed by WIRED show that Mirski has been given read and write access to three different HUD systems, as well as read-only access to two more, while Langmack has been given read and write access to two of HUD’s core systems.
A positive, from one source’s perspective, is the fact that the DOGE operatives have been given application-level access to the systems, rather than direct access to the databases themselves. In theory, this means that they can only interact with the data through user interfaces, rather than having direct access to the server, which could allow them to execute queries directly on the database or make unrestricted or irreparable changes. However, this source still sees dangers inherent in granting this level of access.
“There are probably a dozen-plus ways that [application-level] read/write access to WASS or LOCCS could be translated into the entire databases being exfiltrated,” they said. There is no specific reason to think that DOGE operatives have inappropriately moved data—but even the possibility cuts against standard security protocols that HUD sources say are typically in place.
LOCCS, or Line of Credit Control System, is the first system to which both DOGE operatives within HUD, according to the records reviewed by WIRED, have both read and write access. Essentially HUD’s banking system, LOCCS “handles disbursement and cash management for the majority of HUD grant programs,” according to a user guide. Billions of dollars flow through the system every year, funding everything from public housing to disaster relief—such as rebuilding from the recent LA wildfires—to food security programs and rent payments.
The current balance in the LOCCS system, according to a record reviewed by WIRED, is over $100 billion—money Congress has approved for HUD projects but which has yet to be drawn down. Much of this money has been earmarked to cover disaster assistance and community development work, a source at the agency says.
Normally, those who have access to LOCCS require additional processing and approvals to access the system, and most only have “read” access, department employees say.
“Read/write is used for executing contracts and grants on the LOCCS side,” says one person. “It normally has strict banking procedures around doing anything with funds. For instance, you usually need at least two people to approve any decisions—same as you would with bank tellers in a physical bank.”
The second system to which documents indicate both DOGE operatives at HUD have both read and write access is the HUD Central Accounting and Program System (HUDCAPS), an “integrated management system for Section 8 programs under the jurisdiction of the Office of Public and Indian Housing,” according to HUD. (Section 8 is a federal program administered through local housing agencies that provides rental assistance, in the form of vouchers, to millions of lower-income families.) This system was a precursor to LOCCS and is currently being phased out, but it is still being used to process the payment of housing vouchers and contains huge amounts of personal information.
There are currently 2.3 million families in receipt of housing vouchers in the US, according to HUD’s own data, but the HUDCAPS database contains information on significantly more individuals because historical data is retained, says a source familiar with the system. People applying for HUD programs like housing vouchers have to submit sensitive personal information, including medical records and personal narratives.
“People entrust these stories to HUD,” the source says. “It’s not data in these systems, it’s operational trust.”
WASS, or the Web Access Security Subsystem, is the third system to which DOGE has both read and write access, though only Mirski has access to this system according to documents reviewed by WIRED. It’s used to grant permissions to other HUD systems. “Most of the functionality in WASS consists of looking up information stored in various tables to tell the security subsystem who you are, where you can go, and what you can do when you get there,” a user manual says.
“WASS is an application for provisioning rights to most if not all other HUD systems,” says a HUD source familiar with the systems who is shocked by Mirski’s level of access, because normally HUD employees don’t have read access, let alone write access. “WASS is the system for setting permissions for all of the other systems.”
In addition to these three systems, documents show that Mirski has read-only access to two others. One, the Integrated Disbursement and Information System (IDIS), is a nationwide database that tracks all HUD programs underway across the country. (“IDIS has confidential data about hidden locations of domestic violence shelters,” a HUD source says, “so even read access in there is horrible.”) The other is the Financial Assessment of Public Housing (FASS-PH), a database designed to “measure the financial condition of public housing agencies and assess their ability to provide safe and decent housing,” according to HUD’s website.
All of this is significant because, in addition to the potential for privacy violations, knowing what is in the records, or even having access to them, presents a serious potential conflict of interest.
“There are often bids to contract any development projects,” says Erin McElroy, an assistant professor at the University of Washington. “I can imagine having insider information definitely benefiting the private market, or those who will move back into the private market,” she alleges.
HUD has an oversight role in the mobile home space, the area on which TCC Management, which appears to have recently wiped its website, focuses. "It’s been a growing area of HUD’s work and focus over the past few decades," says one source there; this includes setting building standards, inspecting factories, and taking in complaints. This presents another potential conflict of interest.
Braesemann says it’s not just the insider access to information and data that could be a potential problem, but that people coming from the private sector may not understand the point of HUD programs. Something like Section 8 housing, he notes, could be perceived as not working in alignment with market forces—“Because there might be higher real estate value, these people should be displaced and go somewhere else”—even though its purpose is specifically to buffer against the market.
Like other government agencies, HUD is facing mass purges of its workforce. NPR has reported that 84 percent of the staff of the Office of Community Planning and Development, which supports homeless people, faces termination, while the president of a union representing HUD workers has estimated that up to half the workforce could be cut The chapter on housing policy in Project 2025—the right-wing playbook to remake the federal government that the Trump administration appears to be following—outlines plans to massively scale back HUD programs like public housing, housing assistance vouchers, and first-time home buyer assistance.
16 notes
·
View notes
Text
Kouji + Reader (Sister) Headcannons

A/N: This is a familial relationship between you and Kouji. Don't be weird about it lol.
Kouji can be a mean brother who teases his sister a lot, but he tries not to overdo it
He's recognized as the genius kid of the family, and he would point that out to you as if that were obvious. But, he also tries not to do it often and he doesn't want you to feel insecure about it since he still cares about you.
Kouji is super protective over you, especially whenever you use his computer at home
One day, you were curious, wondering why he’s always so addicted to using his PC (computer in the day, computer at night) so you decide to snoop through his computer when you got home from school before him
While passing through his login on his computer, you look through his desktop on his computer and you find normal files relating to school, gaming applications, and… a spreadsheet document that’s titled “Money Log”, which you don’t find too suspicious. (He’s just a teen who wants to properly organize his money. How is that suspicious? 🤔)
Nothing seems to catch your eye, so you decided to look deeper by going through his history of accessed documents, files, and software installations
You noticed a software installation called “VPN” and a folder that says “Private” on there. But, his private folder was locked and it was under password authorization
While you were still trying to figure out his password, Kouji would catch you right when he came home from school and ask you what you were doing on his computer with a stern face, trying to hide his nervousness. However, when you cut him off and asked about how you so happened to find a “Private” folder on his PC, he immediately admitted that it was p*rn for you to shut up about it. (Is he really telling the truth though? You can't tell.)
Obviously, Kouji can also be secretive towards his sister, but also wary of what he does online and at home whenever you decide to crash and hang out in his room
The both of you would often play PC games together like horror games like "Welcome to the Game" (totally up his alley), Minecraft, Roblox, Valorant, etc. He usually does the game controls for you, while you sit there with him and watch him do all of the work. But, if you ask him if he can take control of the gameplay, he lets you but he teases you by saying, "You suck at this." which then leads to a never-ending banter between you two.
However, you don't just play PC games together, but also multi-player mobile games like Genshin Impact (he doesn't want to admit to you that this is his favorite game), Among Us (yes on mobile), and Stardew Valley.
Whenever you guys are bored together, you'd go on weird websites like Omegle or Chatroulette. Often times, he'd try and hack the other person on the other side of the screen ("just for fun" he says) and you had to scold him and try to convince him not to do it for the sake of the poor person on the other side. Most of the time, he just ignores you and just does it anyway. He justifies his own actions as some sort of necessary justice by pointing out, "See? These people are sick, just look at them! Nasty old geezers..."
You noticed how he's a Discord addict who's a part of a bunch of servers online with various aliases. He's a Discord mod for many servers, whether those servers serve as a purpose for gaming and hacking communities. But most of the servers he's on, he mostly hacks into them to troll people online through phishing links and sends random files in group chats that are actually malicious.
You have a strong feeling that he occupies his time doing something more than just trolling online users and playing video games. Since he's so good at hacking and online security, you have to admit that your brother is a technical genius. If that's the case, then you would assume that his hacking capabilities might exceed more than just surface web level. Even if that possibility might lean towards him exploring the Dark Web. (He's your brother. Of course, he would.)
Sometimes whenever he would take a break from using his computer all day doing God knows what, he would join you on the couch and watch a horror movie or a game show
While watching that movie/game show, he would criticize the show or movie by saying, “They are so dumb. I mean, why can’t they just run?” or “Why can’t they get such a simple question right? Are they stupid?” And your only answer for him is: “They just aren’t as smart as you, Kouji.” and your responses always boosts his ego, even if your replies were a bit sarcastic
While watching TV together, he would often eat candies or sweets and he would share them with you
In the living room whenever you two are free from homework or just so happened to be bored, you'd challenge him to play Super Smash Bros. on the Switch. And every single time, he'd mostly beat you in every single round by using his favorite character to fight: Ness (Of course he would use him. I call this canon.)
While playing Super Smash Bros, he would call you out for choosing weird characters to fight like Isabelle, the Villager from Animal Crossing, the Pirahna Plant, and even the Wii Fit Trainer (YES, THE FUCKING WII FIT TRAINER.), and he would call all of them weak. "What the hell? Out of all of the characters you chose, you decided to fight as them? No wonder you died so quickly." His insults didn't stop you from challenging him for rematches.
Whenever you ask him to help you on your homework, he would begrudgingly help you. (Basically, you’re the only person who he would help without blackmailing or without charging you with anything in return for his service.)
Kouji would eat the treats you bake, whether that be cookies, cakes, and other desserts. Especially, the strawberry cakes that you'd make and you would share it with him.
Whenever you mention a boy or a male friend, he would seem very nonchalant about it and dismiss the subject. But you wouldn’t know that he would do research on the poor boy, social engineer to hack into that boy’s accounts (financial accounts or not), and commit cyberattacks on him (viruses, DDoS attacks, phishing, etc.)
Whenever the both of you end up in an argument, you apologize a few days later by sneaking into his room and place sweets on his desk with a bottle/can of grape soda in front of his computer with a little note that usually says small messages like, "Truce? :)" or "I'll give you this peace offering if you let me off the hook." and he would usually accept the gifts and reluctantly eat them.
You would dye his hair purple for him, whenever he asks you to do it and recolor his hair once in a while.
As siblings, you'd do each other a solid at home with the typical "you owe me" exchange. This is your own little way of showing how much you care and look after each other.
You're aware that Kouji has a job, since you caught him one day with a check in his hand that had a bunch of 0's for its amount. You asked him, "Where'd you get that from?" and he would simply say, "My job."
You were a bit shocked to hear that he has a job so your conversation with him ended up being sarcastic and blunt. This is how it went:
"What job?"
"The job that I work for."
"No shit. I meant, where do you work at?"
"Some company."
"Some company? Bullshit. And they'd actually hire someone as young as you? You're barely 16."
"And? The other people that they've interviewed before me were all a bunch of idiots in the first place."
"Huh... I guess that makes sense."
Finally, you two left it at that and decided to never tell your parents about it. After all, what are siblings for anyways?
#lookism#lookism manhwa#lookism webtoon#lookismaddict#lookism fandom#lookism memes#lookism meme#lookism imagines#lookism x reader#lookism fanfic#lookism headcanons#kouji#lookism kouji#kouji lookism#we need more Kouji recognition in this fandom#manhwa#webtoon
112 notes
·
View notes
Text
Tim Han Life Mastery Achievers (LMA) Course Review
Are you ready to tap into your potential and seize control of your life? Look no further than the LMA Life Mastery Achievers Course! If you're lacking direction, always feeling stuck or not living up to your capabilities, this course will be perfect for you.
Created by the entrepreneur and mindset coach Tim Han, it offers an experience that will empower you to succeed in all areas of your life.
Learn about LMA Life Mastery Achievers Course Review By Tim Han. We will also discuss the intricacies of the LMA Method, examine its advantages and disadvantages, compare it to development courses available and ultimately share our final thoughts and recommendations.

What is the LMA Method?
The Life Mastery Achievers Method is designed to help individuals unlock their potential. This comprehensive course incorporates strategies, powerful techniques and mindset shifts that can transform aspects of your life. It covers a range of areas, such as creating wealth-building relationships, enhancing leadership skills, increasing productivity and fostering personal growth.
The LMA Method is truly remarkable because it focuses on application. Tim believes that knowing alone is insufficient; it needs to be implemented to see results. This course combines lessons, interactive exercises, and actionable steps to empower you with the tools to create lasting change in your life.
Tim openly shares his challenges and successes throughout his journey towards achieving greatness, making it easier for students to connect with him on a level. His passion for assisting others shines through each lesson delivered in a manner.
Advantages of the LMA Course
Tim Han has created this program to cover aspects of mastering life, including mindset, goal setting, productivity and success habits. This comprehensive approach ensures that participants receive a rounded education in growth.
The course provides tools and techniques that can be easily incorporated into life. Students are equipped with steps to achieve their objectives, from visualization exercises to communication strategies.
Another advantage is the sense of community that accompanies enrollment in this course. Do participants gain access to a network to connect with like-minded individuals on their journey towards self-improvement
How is the LMA course different from other courses available in the market?
There are options in the market, each claiming to offer unique strategies and transformative approaches to success and fulfilment. However, assessing your goals and requirements is crucial before investing in any program.
The LMA Life Mastery Achievers Course stands out for reasons. Firstly, it is built upon the proven methods developed by Tim Han himself. With his experience as an entrepreneur and mindset coach, Tim understands what it truly takes to achieve mastery in life.
What sets the LMA Method apart from development courses is its focus on more than surface-level techniques or quick fixes. It delves into the core beliefs and patterns that shape our lives, emphasizing the power of mindset reprogramming. Moreover, it provides tools to shift limiting beliefs and foster lasting transformation.
In conclusion
Tim Han stands out as an entrepreneur and mindset coach, surpassing the ordinary. He has empowered numerous individuals globally to overcome their limitations and turn their wildest aspirations into reality through his involvement in the development sector. What sets him apart is his methodology towards mastering life. Read here to learn more about Tim Han's unveiling of the Mindset Maven.
The LMA Life Mastery Achievers Course offers numerous benefits, such as its comprehensive curriculum and practical tools for personal growth. However, potential participants must consider costs and self-discipline before deciding.
#Tim Han#entrepreneur#LMA#LMA Course#founder#startup#Success Insider#Coach#Author#Life Mastery Achievers#LMA Method
94 notes
·
View notes