#Data Theft Prevention Solution
Explore tagged Tumblr posts
Text
Generative AI Can Fuck Itself
I am one of the AO3 authors (along with all of my friends) who had their work stolen and fed into a dataset to be sold to the highest bidder for training generative AI models.
I feel angry. I feel violated. I feel devastated. I cannot express enough that if you still do not understand the damage that generative AI art and writing has on our planet, our society, and our artists, I don't know what else there is to say. How do you convince a human being to care more about another humankinds ability to create than their personal need to consume?
Generative AI, when it comes to art, has one goal and one goal only. To steal from artists and reduce the dollar value of their work to zero. To create databases of stolen work that can produce work faster and cheaper than the centuries of human creation those databases are built on. If that isn't enough for you to put away Chatgpt, Midgard, ect ect (which, dear god, please let that be enough), please consider taking time to review MIT's research on the environmental impacts of AI here. The UNEP is also gathering data and has predicted that AI infrastructure may soon outpace the water consumption of entire countries like Denmark.
This is all in the name of degrading, devaluing, and erasing artists in a society that perpetually tries to convince us that our work is worth nothing, and that making a living off of our contributions to the world is some unattainable privilege over an inalienable right.
The theft of the work of fic writers is exceptionally insidious because we have no rights. We enter into a contract while writing fic- We do not own the rights to the work. Making money, asking for money, or exchanging any kind of commercial trade with our written fanfiction is highly illegal, completely immoral, and puts the ability to even write and share fanfiction at risk. And still, we write for the community. We pour our hearts out, give up thousands of hours, and passionately dedicate time that we know we will never and can never be paid for, all for the community, the pursuit of storytelling, and human connection.
We now live in a world where the artist creating their work are aware it is illegal for it to be sold, and contribute anyway, only for bots to come in and scrape it so it can be sold to teach AI databases how to reproduce our work.
At this time, I have locked my fics to allow them only to be read by registered users. It's not a perfect solution, but it appears to be the only thing I can do to make even a feeble attempt at protecting my work. I am devastated to do this, as I know many of my readers are guests. But right now it is between that or removing my work and not continuing to post at all. If you don't have an account, you can easily request one here. Please support the writers making these difficult decisions at this time. Many of us are coping with an extreme violation, while wanting to do everything we can to prevent the theft of our work in the future and make life harder for the robots, even if only a little.
Please support human work. Please don't give up on the fight for an artists right to exist and make a living. Please try to fight against the matrix of consumerism and bring humanity, empathy, and the time required to create back into the arts.
To anyone else who had their work stolen, I am so sorry and sending you lots of love. Please show your favorite AO3 authors a little extra support today.
#ao3#ai#fuck ai#ao3 writer#anti ai#anti capatilism#we are in the bad place#acotar fic#elriel#elriel fic writer#acotar fic writer#feysand fic#nessian fic#support your ao3 authors plz we are going through it
183 notes
·
View notes
Text
💫 Join the Fediverse! 💫
Greetings, fellow bloggers! We welcome you to join us in discovering, honoring, and promoting the potential future of social networking—commonly referred to as the "Fediverse."
The Fediverse, or Federation Universe, refers to a collective of online platforms that utilize the web protocol known as ActivityPub, which has set a standard of excellence in regards to both protecting and respecting users' online privacies.
There's a good chance in the past few years that you've caught wind of the fedi family's critically acclaimed Mastodon; however, there are many other unique platforms worth your consideration...
✨ Where To Begin?
Conveniently enough, from the minds of brilliant independent developers, there already likely exists a Fediverse equivalent to your favorite socials. Whether it's an opinion from the critics, or from the community alike—the following popular websites are commonly associated with one another:
Friendica 🐰 = Facebook Mastodon 🐘 = Twitter Pixelfed 🐼 = Instagram PeerTube 🐙 = YouTube Lemmy 🐭 = Reddit
It's worth mentioning, too, a few other sites and forks thereof that are worthy counterparts, which be: Pleroma 🦊 & Misskey 🐱, microblogs also similar to Twitter/Mastodon. Funkwhale 🐋 is a self-hosting audio streamer, which pays homage to the once-popular GrooveShark. For power users, Hubzilla 🐨 makes a great choice (alongside Friendica) when choosing macroblogging alternatives.
✨ To Be Clear...
To address the technicalities: aside from the "definitive" Fediverse clients, we will also be incorporating any platforms that utilize ActivityPub-adjacent protocols as well. These include, but are not limited to: diaspora*; AT Protocol (Bluesky 🦋); Nostr; OStatus; Matrix; Zot; etc. We will NOT be incorporating any decentralized sites that are either questionably or proven to be unethical. (AKA: Gab has been exiled.)
✨ Why Your Privacy Matters
You may ask yourself, as we once did, "Why does protecting my online privacy truly matter?" While it may seem innocent enough on the surface, would it change your mind that it's been officially shared by former corporate media employees that data is more valuable than money to these companies? Outside of the ethical concerns surrounding these concepts, there are many other reasons why protecting your data is critical, be it: security breaches which jeopardize your financial info and risk identity theft; continuing to feed algorithms which use psychological manipulation in attempts to sell you products; the risk of spyware hacking your webcams and microphones when you least expect it; amongst countless other possibilities that can and do happen to individuals on a constant basis. We wish it could all just be written off as a conspiracy... but, with a little research, you'll swiftly realize the validity of these claims are not to be ignored any longer. The solution? Taking the decentralized route.
✨ Our Mission For This Blog
Our mission for establishing this blog includes 3 core elements:
To serve as a hub which anybody can access in order to assist themselves in either: becoming a part of the Fediverse, gaining the resources/knowledge to convince others to do the very same, and providing updates on anything Fedi-related.
We are determined to do anything within our power to prevent what the future of the Internet could become if active social users continue tossing away their data, all while technologies are advancing at faster rates with each passing year. Basically we'd prefer not to live in a cyber-Dystopia at all costs.
Tumblr (Automattic) has expressed interest in switching their servers over to ActivityPub after Musk's acquisition of then-Twitter, and are officially in the transitional process of making this happen for all of us. We're hoping our collective efforts may at some point be recognized by @staff, which in turn will encourage their efforts and stand by their decision.
With that being stated, we hope you decide to follow us here, and decide to make the shift—as it is merely the beginning. We encourage you to send us any questions you may have, any personal suggestions, or corrections on any misinformation you may come across.
From the Tender Hearts of, ✨💞 @disease & @faggotfungus 💞✨
#JOIN THE FEDIVERSE#fediverse#decentralization#internet privacy#social media#social networks#FOSS#activitypub#mastodon#fedi#big data#degoogle#future technology#cybersecurity#technology#essential reading
37 notes
·
View notes
Text
Hearing that public works on ao3 were scrapped for Huggingface is so infuriating. Scrapping in general is just both a morally reprehensible way to gather data, and stupid too. If you're really going to build datasets, having a narrower parameter then "literally everything" is the very start.
According to this article it used to be a chatbot but moved onto "primarily used for natural language processing tasks, such as text generation, sentiment analysis, and chatbot development." At a glance, I would not be scrapping a huge fandom archive for that sorta thing, considering not-insignificant number of fics that aren't written with the best grammar and also crackfics.
Going to the website itself and scrolling down I see this
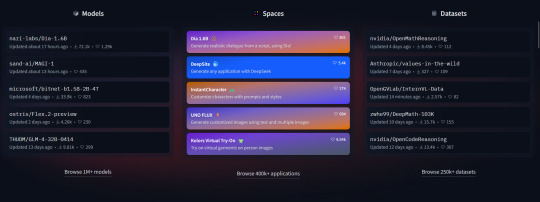
I am not tech savvy enough to have extended commentary on the models or datasets outside of the fact that if this company wanted to be a hub for legitimate and ethically ai development, you think they would put more care into how they were getting their information. It's those spaces i'm more concerned about.
Now, it seems than they're uploaded by different people and not just Hugging face itself, but I digress. A skim has already shown different dialogue and character creation related bots made to generate.
Here is the post of the user on hugging face who made and uploaded at dataset of ao3 fics. Needless to say, do not make accounts just to make threats and drag this creator. Knowing its a user and not the action of the website itself is only comforting until you wonder why/when will the website screen the datasets being uploaded to make sure they're ethically sourced. (This also doesn't appear to be the only dataset made with fanfiction, but by far the largest.) It appears that Hugging Face is doing what they're legally obligated to do.
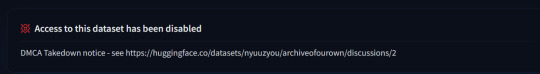
Access to it has been restricted thankfully. Following that link leads me to this
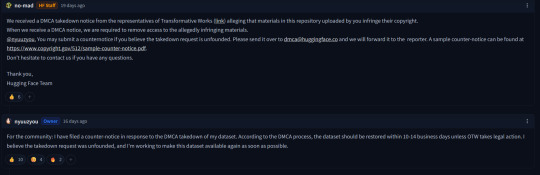
and the comments are as ugly as you can expect them to be. (No, fanfiction isn't theft. It is protected under parody and fair use laws. Regardless, i cannot fathom why you would want to use them anyways.)
If you're curious if it's been scrapped, this tiktok said any work with the work id under 63,200,000 appears to be scrapped. Basically anything made mid this march and before. All of my fics, including my one original work has been scrapped. Since ao3 lawyers are on the case, there's nothing anyone else can do now but wait. There is no point in submitting your own DMCA claim because Ao3's covers all of us.
That being said, it's irritable and disheartening. This is not in the spirit of fanfiction, this is not legally or morally ethical, and it's just irritating. None of these works had consent to be reuploaded or used in this way (no matter how those ai idiots think things work. Just because it's on the internet does not mean it's free use)
The conversation now is how to prevent this from happening again. Many users are setting their work to be privated, so that way only those with an account can read fics. I fear that is a very bandaid on the bullet wound type solution, because there's nothing stopping someone from making an account and then scrapping. Ao3 themselves have their own methods to try and counteract such things. And largely, we will be relaying on the team to handle such things. (This is why that donation drive is important, i can imagine the poor legal department is going to be clocking a lot of overtime soon.) I suppose another method is just to go old school. Printed zines for yourself and your circle of friends and not online I guess.
What now? Not sure. Obviously arguing with ai bros on their own turf isn't doing anything constructive, not that I really expected anything else from the general fandom nerds tbh. It's just. A super fucking frustrating reality of the internet now. I can only hope that when enough idiots do something like this and face repercussions, it'll be a widespread lesson on Ethics in Business and 101 for all.
It sucks, because back before "AI" was associated with chatGPT and datascrapping, it was understood to be broad range of tech and code that can be really good and helpful. Unfortunately, aibros of today do not know how to, nor will put in the hard work, to making something more constructive than ArtTheftArtGeneratornumber3000 and ChatBotThatSucks2000. With so much of the slop, it's taking away time, energy, and resources from people trying to development meaningful AIs to recognize cancer and process information humans can't in a timely manner.
Edit: Its worth knowing this is not the first, nor likely the last time, ao3 has been scrapped. This isn't new but it's getting annoyingly common. And this particular dataset is *huge*
4 notes
·
View notes
Text
The Intersection of Driver’s Licenses and Cybersecurity in 2025
As we look toward 2025, cybersecurity is becoming an increasingly critical aspect of the digital transformation of driver’s licenses. With more Canadians opting for digital driver’s licenses (DLs), ensuring these digital IDs are protected from cyber threats is paramount. The convergence of driver’s licenses and cybersecurity is reshaping how individuals manage their credentials and how governments secure sensitive information in the digital age.
The Rise of Digital Driver’s Licenses
Digital driver’s licenses have emerged as an essential part of Canada’s shift toward smarter, more efficient services. Provinces like Ontario, British Columbia, and Alberta have started offering digital licenses, allowing residents to store their DLs on smartphones and access them via secure apps. This shift is not only more convenient for drivers but also reduces physical waste and improves overall efficiency in verification processes.
However, with these advances come new risks, particularly related to cybersecurity. As digital licenses become more widespread, ensuring their security is a growing concern for both citizens and government agencies.
To stay updated on the latest digital licensing guidelines, licenseprep.ca is a valuable resource that provides information about digital driver’s licenses and the security protocols involved in their use.

Cybersecurity Challenges in Digital Licenses
While digital driver’s licenses offer many benefits, they also introduce several cybersecurity risks that need to be addressed:
1. Data Breaches and Hacking
With digital licenses stored on smartphones, there is the risk of data breaches or hacking. Cybercriminals could potentially gain unauthorized access to users’ personal information, leading to identity theft or fraudulent activities. Securing the digital infrastructure that houses these licenses is essential to mitigating these threats.
2. Phishing and Fraud
Phishing attacks, where cybercriminals impersonate legitimate institutions to steal sensitive data, are a growing concern. Digital licenses could be targeted by these malicious actors, tricking users into sharing login credentials or personal information under false pretenses.
3. Privacy Concerns
As digital driver’s licenses become more integrated with other smart city systems, the amount of data being shared and stored increases. Ensuring that user privacy is protected and that data isn’t misused is crucial. A robust data encryption system must be in place to prevent unauthorized access to users' sensitive information.
Solutions to Strengthen Cybersecurity
To safeguard the future of digital driver’s licenses, various cybersecurity measures are being implemented:
1. Encryption and Multi-Factor Authentication (MFA)
Using end-to-end encryption ensures that the information stored on a digital driver’s license is protected from unauthorized access. Additionally, multi-factor authentication (MFA) can be used to add an extra layer of security when accessing or updating license information.
2. Blockchain Technology
Blockchain technology offers a decentralized and secure way of verifying identity, which could be used to authenticate digital licenses. By storing data across multiple nodes, blockchain reduces the risk of single points of failure that could be exploited by cybercriminals.
3. Regular Security Audits and Updates
Governments and agencies responsible for digital licensing systems will need to conduct regular security audits to identify vulnerabilities. Timely security updates will also be crucial in protecting against emerging threats and keeping the systems up to date with the latest encryption protocols.
The Road Ahead
As Canada moves closer to a fully digital future, the intersection of driver’s licenses and cybersecurity will become even more important. With proper safeguards in place, digital driver’s licenses will not only provide convenience but will also ensure that citizens’ data remains secure.
For Canadians looking to stay informed about digital driver’s licenses and their role in the evolving digital landscape, licenseprep.ca is a helpful platform to track the latest updates and best practices in digital ID security.
#Cybersecurity#DigitalLicensing#SmartCities#DataPrivacy#Blockchain#DigitalDriverLicense#LicensePrep#FutureOfSecurity#SecureLicenses#LicenseprepCanada
2 notes
·
View notes
Text
Cloud Squatting: Understanding and Mitigating a Modern Cyber Threat

Cloud computing is central to both business and personal data storage. A critical and emerging threat is cloud squatting.This phenomenon, a digital variant of the notorious domain squatting, involves the unauthorized occupation of cloud resources. It poses significant risks, making it a crucial concern for everyone, from casual cloud users to IT professionals and business owners.
Understanding cloud squatting
Cloud squatting is the practice of occupying cloud resources, such as storage accounts, domain names, or service identifiers, often for exploitative purposes. This could range from reselling these resources for profit to hosting harmful content or phishing scams. Cloud squatting not only mirrors traditional domain squatting but also extends to trafficking cloud resources like cloud computing instances or web applications, typically for malicious intentions.
The risks involved
Cloud squatting presents various risks:
Data theft: Unauthorized instances can store or transmit stolen data.
Security breaches: They can act as platforms for attacks on other systems.
Reputation damage: Companies suffer if their services are impersonated.
Legal and financial repercussions: In cases of brand damage and loss of customer trust.
For example, an attacker might use a service resembling a legitimate one, deceiving users into sharing sensitive information, leading to data breaches and tarnished reputations.
Mitigation strategies
Effective mitigation of cloud squatting involves a multi-faceted approach:
Proactive registration: Secure variations of your business’s cloud resource names.
Regular audits: Ensure all cloud services are legitimate.
Monitoring and alert systems: Detect unauthorized or misleading registrations.
Employee training: Educate about risks and the identification of suspicious services.
Legal protections: Utilize trademarks and enforce anti-squatting policies.
Security tools and best practices: Use AI-driven solutions and update security measures regularly.
Stakeholder education: Inform teams and customers about these risks.
Rapid response plan: Have a plan to address incidents swiftly.
Collaboration with cloud providers: Utilize their anti-squatting policies.
Reserved IP addresses: Transfer owned IPs to the cloud and manage records.
Policy enforcement: Prevent hard coding of IP addresses and use reserved IPv6 addresses.
The future of cloud security
As cloud technologies evolve, so do the tactics of cybercriminals. This makes proactive security measures and constant vigilance essential. Emerging technologies, like AI-driven security solutions, will play a crucial role in combating these threats.
Cloud squatting is a modern cyber threat that demands awareness, understanding, and proactive action. Implementing robust security strategies and staying informed about the latest trends in cloud security can significantly protect valuable digital assets. By addressing the risks and employing comprehensive mitigation strategies, individuals and businesses can safeguard their presence and integrity in the cloud.
Centizen, your trusted partner in cloud consulting and staffing provides unparalleled expertise and solutions to guard against threats like cloud squatting, ensuring the security and efficiency of your digital infrastructure.
#CloudSquatting#CyberSecurity#CloudSecurity#DataProtection#DigitalThreats#CloudComputing#InfoSec#AIinSecurity
2 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Note
What’s your favourite piece of forgotten lore?
We raised this question in our biweekly Head Archivists' Meeting to make sure the whole team got to have their input. Once the fires had died down and the various demons had been banished back to their planes of origin, we decided that rather than trying to settle on a single piece we would produce a shortlist based on the most popular answers across the team. The original list of 37 items was then cut down to a "top 3" with the highest degree of consensus between the archivists, and then extended to a "top 4" when Ainsworth threatened to release a Greater Hypercurse of Enpigening in the lobby if his favourite wasn't included.
So, without further ado,
Our sort-of top 34 consensus list of some of our favourite pieces of forgotten lore
Iacobus Stultus (James the Fool)'s Four Prime model of alchemy. Proposed some time after 1613 in the (possibly pseudographical) De Arte Divina Transmutationis et Anates, Iacobus argues against previous Paracelcian tripartite Salt-Sulfur-Mercury theories, as well as later bipartite Sulfur-Mercury and Mercury-alone models, of prime materials in favour of a quadripartite model consisting of salt, sulfur, mercury and ducks as the four fundamental elements of reality. Iacobus's argument hinges on the claim that ducks are such essentially peculiar and transcendental beings that it is inconceivable that they may be constituted of more discrete parts, and must instead be understood as foundational elements and principles of reality. This theory was widely panned by other alchemists on the grounds that ducks are clearly composed of constituent parts and can be subdivided, although a number of later texts attributed to Iacobus continued to defend the salt-sulfur-mercury-ducks theory with a gradually increasing role for elemental ducks in the theory, with the last text, De Divinis Anatibus, going so far as to defend a duck-only theory of prime materials.
The Second Banned Spell. Now, all wizards know the story of the first banned spell, so we won't bore you by repeating it. What is often left out of these stories, however, is that, at the time, the wizard council only created the requisite ordinances and regulations to ban exactly that spell, and did not provide any appropriate institutions for the generalised banning of spells that would follow. In fact, there was significant pushback against the banning of that first spell for fear that this would lead to the council exerting tyrannical control over the wizarding community, and so various clauses and provisions were put in place to prevent the council banning any other spells. So what changed? Throughout the 16th century, wizarding bosses had sought for ways of increasing the effeciency of their apprentices and workers. In 1536, Alfonso of Piccolamerda developed the Lesser Wage Theft spell which, alongside Efficacious Torture and Shatter Will, was widely used by wizarding bosses to force workers to produce more in ever harsher conditions. The result of these harsh and exploitative conditions was the great Apprentice Revolt of 1593, which led to the passing of the Rights of the Apprentice Act 1595 (an early predecessor to the 1707 Wizard Apprentices' Right to Live [WARL] Act) and the addition of Lesser Wage Theft to the list of bannded spells.
Why installers are called "wizards". When computers were first developed, there was some difficulty in developing hardware and software solutions to replacing information within a storage system with other information, or transfering information between storage systems. The original solution for this problem was to shrink a wizard down small enough that they could stand on the computer chip with a little screen that told them when a new file had been called for. When required, the wizard would then summon that file from its original source and use a magical transmutation ritual to imbue it directly into its new storage device. While this was a very quick method of data transfer, it was also expensive, and so it was eventually phased out in favour of the software installers that you know today, although they were referred to as "wizards" for a long time to recall the original information transfer system. Interestingly, the last computer to still use the wizard-based data transfer system was Horatio of Slough's WizBook 7, released in 2011, was discontinued in 2012 following the council establishing the Use of Wizards and Other Sapient Magical Beings in Technological Devices Act.
The invention of blue. Now, you may be familiar with Homer's "wine-dark sea", which some people use to argue that the Ancient Greeks couldn't see blue, and others say is just a metaphor because the idea that the Ancient Greeks couldn't see blue is obviously stupid. As it turns out, neither of these answers is correct - Ancient Greek eye-sight was just as good as anyone's today, but the colour blue hadn't been invented yet. Back then, the visual colour spectrum just went straight from teal to purple. The colour blue was added by the revered Archwizard Wolfgang Sauerkraut, as part of his performance in the 32nd Annual Wizarding Polylympics. While historically notable, the invention of the colour blue and expansion of the visible light spectrum was largely overshadowed for viewers by the second half of the archwizard's act, in which he summoned a seamonster from the plane of water and attempted to have sexual intercourse with it, and as a result, Archwizard Sauerkraut was remembered not for his light-bending creation but as "Archwizard Serpentshagger".
#wizardposting#wizardblr#wizard posting#wizard council archives#wizard council#wizard#wizardblogging#banned spells#fita#found in the archives
53 notes
·
View notes
Text
Physical Verification of Fixed Assets: Why Your Business Needs It
Introduction In the world of business, fixed assets—like machinery, buildings, and equipment—are fundamental to operations and profitability. However, without proper management and regular verification, businesses can lose track of these valuable resources. Physical verification of fixed assets is a critical process to ensure that a company’s assets are accurately recorded and maintained. In this article, we’ll delve into why physical verification of fixed assets is essential and how MAS LLP offers a streamlined approach to safeguarding these vital resources.

What is Physical Verification of Fixed Assets? Physical verification of fixed assets is a systematic process of counting and verifying a company's tangible assets to confirm their presence, condition, and alignment with accounting records. This process helps ensure assets are accounted for, thereby minimizing risks of asset misappropriation, losses, or unexpected depreciation.
Key Components of Physical Verification Inventory Count: Ensuring that all assets, big or small, are physically located and accounted for. Condition Assessment: Reviewing the status and usability of assets to determine if they need maintenance, repair, or replacement. Compliance Check: Ensuring that the asset register aligns with financial statements and legal regulations. Tagging & Labeling: Using asset tags or barcodes for easy tracking and future verification. Why Physical Verification is Essential for Businesses
Improved Financial Accuracy An accurate inventory of fixed assets ensures that the company's financial statements reflect true value. By confirming asset existence and condition, physical verification helps in producing precise data for depreciation, amortization, and insurance claims.
Asset Utilization Optimization Physical verification helps identify underutilized or idle assets, providing opportunities to redeploy them where needed. This leads to optimized resource allocation, potentially saving costs by maximizing the productivity of existing assets.
Enhanced Security and Fraud Prevention Unauthorized use, theft, or misappropriation of assets can have significant financial consequences. Regular verification protects businesses by preventing fraudulent practices and ensuring that each asset is appropriately safeguarded.
Accurate Tax Reporting Fixed assets have tax implications, especially in terms of depreciation. Accurate records enable businesses to file correct depreciation values, avoid tax penalties, and ensure compliance with local tax laws.
Supporting Business Valuation For businesses seeking investments or mergers, a well-documented and verified list of fixed assets enhances business valuation. A clean asset register is a positive indicator for potential investors, showing operational control and value transparency.
Physical Verification with MAS LLP At MAS LLP, we provide comprehensive physical verification of fixed assets services, tailored to meet your company’s unique requirements. Our process is designed to deliver accuracy, transparency, and peace of mind. Here’s how we can help:
Detailed Asset Inventory Creation Our team conducts an in-depth assessment to create an exhaustive inventory list that aligns with your company’s financial records. We account for every asset to ensure you have a clear picture of your holdings.
Customized Verification Plans MAS LLP works with clients to develop verification schedules suited to the size and nature of the business. Whether it’s annual, semi-annual, or periodic checks, we customize our approach to your operational needs.
State-of-the-Art Tracking Technology We leverage advanced tracking solutions, such as barcode tagging and RFID, to simplify the asset verification process and minimize errors. This enhances the traceability and management of assets, especially for larger organizations.
Condition and Compliance Reporting Our experts assess the physical state of assets and generate detailed reports on their condition. We also ensure compliance with relevant regulations, maintaining an accurate record of all assets in your register.
Seamless Integration with Financial Statements Once verification is complete, we update the asset register and integrate findings with your financial statements. This ensures consistency across your asset records, accounting books, and tax documents, giving you a precise and compliant asset overview.
Why Choose MAS LLP? When it comes to managing your fixed assets, MAS LLP’s expertise in physical verification of fixed assets helps you minimize risk and maximize control. With a team of seasoned professionals, we have the resources, technology, and industry knowledge to provide you with a comprehensive asset verification solution.
Benefits of Working with MAS LLP Unmatched Accuracy: Our rigorous processes ensure asset records are accurate and up-to-date. Cost-Efficiency: We help you avoid over-investment by identifying and redistributing idle assets. Compliance Assurance: Stay compliant with regulatory requirements through verified asset data. Transparent Reporting: Receive detailed, actionable reports for informed decision-making. Conclusion The physical verification of fixed assets is an indispensable aspect of asset management that safeguards your company’s resources, supports financial accuracy, and boosts compliance. With MAS LLP, businesses can gain confidence in the integrity of their asset records and optimize asset utilization for long-term success. Reach out to MAS LLP today to learn more about how we can assist you in managing your fixed assets effectively.
#accounting & bookkeeping services in india#audit#businessregistration#chartered accountant#foreign companies registration in india#income tax#auditor#taxation#ap management services
6 notes
·
View notes
Text
Face Blur Technology in Public Surveillance: Balancing Privacy and Security
As surveillance technology continues to evolve, so do concerns about privacy. One solution that addresses both the need for public safety and individual privacy is face blur technology. This technology automatically obscures individuals’ faces in surveillance footage unless there’s a legitimate need for identification, offering a balance between security and personal data protection.
Why Do We Need Face Blur Technology?
Surveillance systems are increasingly used in public spaces, from streets and parks to malls and airports, where security cameras are deployed to monitor activities and prevent crime. However, the widespread collection of images from public spaces poses serious privacy risks. Personal data like facial images can be exploited if not properly protected. This is where face blur technology comes in. It reduces the chances of identity theft, unwarranted surveillance, and abuse of personal data by ensuring that identifiable information isn’t exposed unless necessary. Governments, businesses, and institutions implementing face blur technology are taking a step toward more responsible data handling while still benefiting from surveillance systems (Martinez et al., 2022).
Key Technologies Behind Face Blur
Face blur technology relies on several key technologies:
Computer Vision: This technology enables systems to detect human faces in images and videos. Using machine learning algorithms, cameras or software can recognize faces in real-time, making it possible to apply blurring instantly.
Real-life example: Google’s Street View uses face blur technology to automatically detect and blur faces of people captured in its 360-degree street imagery to protect their privacy.
Artificial Intelligence (AI): AI plays a crucial role in improving the accuracy of face detection and the efficiency of the blurring process. By training models on large datasets of human faces, AI-powered systems can differentiate between faces and non-facial objects, making the blurring process both accurate and fast (Tao et al., 2023).
Real-life example: Intel’s OpenVINO toolkit supports AI-powered face detection and blurring in real-time video streams. It is used in public surveillance systems in places like airports and transportation hubs to anonymize individuals while maintaining situational awareness for security teams.
Edge Computing: Modern surveillance systems equipped with edge computing process data locally on the camera or a nearby device rather than sending it to a distant data center. This reduces latency, allowing face blurring to be applied in real-time without lag.
Real-life example: Axis Communications’ AXIS Q1615-LE Mk III surveillance camera is equipped with edge computing capabilities. This allows for face blurring directly on the camera, reducing the need to send sensitive video footage to a central server for processing, enhancing privacy.
Encryption: Beyond face blur, encryption ensures that any data stored from surveillance cameras is protected from unauthorized access. Even if footage is accessed by someone without permission, the identity of individuals in the footage remains obscured.
Real-life example: Cisco Meraki MV smart cameras feature end-to-end encryption to secure video streams and stored footage. In conjunction with face blur technologies, these cameras offer enhanced privacy by protecting data from unauthorized access.
How Does the Technology Work?
The process of face blurring typically follows several steps:
Face Detection: AI-powered cameras or software scan the video feed to detect human faces.
Face Tracking: Once a face is detected, the system tracks its movement in real-time, ensuring the blur is applied dynamically as the person moves.
Face Obfuscation: The detected faces are then blurred or pixelated. This ensures that personal identification is not possible unless someone with the proper authorization has access to the raw footage.
Controlled Access: In many systems, access to the unblurred footage is restricted and requires legal or administrative permission, such as in the case of law enforcement investigations (Nguyen et al., 2023).
Real-life example: The Genetec Omnicast surveillance system is used in smart cities and integrates privacy-protecting features, including face blurring. Access to unblurred footage is strictly controlled, requiring multi-factor authentication for law enforcement and security personnel.
Real-Life Uses of Face Blur Technology
Face blur technology is being implemented in several key sectors:
Public Transportation Systems: Many modern train stations, subways, and airports have adopted face blur technology as part of their CCTV systems to protect the privacy of commuters. For instance, London's Heathrow Airport uses advanced video analytics with face blur to ensure footage meets GDPR compliance while enhancing security.
Retail Stores: Large retail chains, including Walmart, use face blur technology in their in-store cameras. This allows security teams to monitor activity and reduce theft while protecting the privacy of innocent customers.
Smart Cities: In Barcelona, Spain, a smart city initiative includes face blur technology to ensure privacy in public spaces while gathering data to improve city management and security. The smart cameras deployed in this project offer anonymized data to city officials, allowing them to monitor traffic, crowd control, and more without compromising individual identities.
Journalism and Humanitarian Work: Media organizations such as the BBC use face blurring technology in conflict zones or protests to protect the identities of vulnerable individuals. Additionally, NGOs employ similar technology in sensitive regions to prevent surveillance abuse by oppressive regimes.
Public Perception and Ethical Considerations
Public perception of surveillance technologies is a complex mix of support and concern. On one hand, people recognize the need for surveillance to enhance public safety, prevent crime, and even assist in emergencies. On the other hand, many are worried about mass surveillance, personal data privacy, and the potential for abuse by authorities or hackers.
By implementing face blur technology, institutions can address some of these concerns. Studies suggest that people are more comfortable with surveillance systems when privacy-preserving measures like face blur are in place. It demonstrates a commitment to privacy and reduces the likelihood of objections to the use of surveillance in public spaces (Zhang et al., 2021).
However, ethical challenges remain. The decision of when to unblur faces must be transparent and subject to clear guidelines, ensuring that this capability isn’t misused. In democratic societies, there is ongoing debate over how to strike a balance between security and privacy, and face blur technology offers a middle ground that respects individual rights while still maintaining public safety (Johnson & Singh, 2022).
Future of Face Blur Technology
As AI and machine learning continue to evolve, face blur technology will become more refined, offering enhanced accuracy in face detection and obfuscation. The future may also see advancements in customizing the level of blurring depending on context. For instance, higher levels of obfuscation could be applied in particularly sensitive areas, such as protests or political gatherings, to ensure that individuals' identities are protected (Chaudhary et al., 2023).
Face blur technology is also expected to integrate with broader privacy-enhancing technologies in surveillance systems, ensuring that even as surveillance expands, personal freedoms remain protected. Governments and businesses that embrace this technology are likely to be seen as leaders in ethical surveillance practices (Park et al., 2022).
Conclusion
The need for effective public surveillance is undeniable in today’s world, where security threats can arise at any time. However, the collection of facial images in public spaces raises significant privacy concerns. Face blur technology is a vital tool in addressing these issues, allowing for the balance between public safety and individual privacy. By leveraging AI, computer vision, and edge computing, face blur technology not only protects individual identities but also enhances public trust in surveillance systems.
References
Chaudhary, S., Patel, N., & Gupta, A. (2023). AI-enhanced privacy solutions for smart cities: Ethical considerations in urban surveillance. Journal of Smart City Innovation, 14(2), 99-112.
Johnson, M., & Singh, R. (2022). Ethical implications of face recognition in public spaces: Balancing privacy and security. Journal of Ethics and Technology, 18(1), 23-37.
Martinez, D., Loughlin, P., & Wei, X. (2022). Privacy-preserving techniques in public surveillance systems: A review. IEEE Transactions on Privacy and Data Security, 9(3), 154-171.
Nguyen, H., Wang, T., & Luo, J. (2023). Real-time face blurring for public surveillance: Challenges and innovations. International Journal of Surveillance Technology, 6(1), 78-89.
Park, S., Lee, H., & Kim, J. (2022). Privacy in smart cities: New technologies for anonymizing public surveillance data. Data Privacy Journal, 15(4), 45-61.
Tao, Z., Wang, Y., & Li, S. (2023). AI-driven face blurring in public surveillance: Technical challenges and future directions. Artificial Intelligence and Privacy, 8(2), 123-140.
Zhang, Y., Lee, S., & Roberts, J. (2021). Public attitudes toward surveillance technology and privacy protections. International Journal of Privacy and Data Protection, 7(4), 45-63.
2 notes
·
View notes
Text
How Customer Experience is Being Transformed This Year by Utility Payment Solutions ?

In recent years, the landscape of utility payment solutions has undergone a significant transformation driven by advancements in fintech. These changes have not only streamlined processes but have also profoundly impacted customer experience. From enhanced convenience to improved security measures, utility payment solutions have evolved to meet the growing demands of both consumers and utility providers alike.
1. Convenience and Accessibility
One of the most noticeable transformations in utility payment solutions is the increased convenience they offer customers. Traditionally, paying utility bills involved manual processes such as visiting payment centers or mailing checks, which could be time-consuming and inconvenient. Today, fintech solutions have revolutionized this process by introducing online platforms and mobile applications. These platforms allow customers to pay their bills anytime, anywhere, using various payment methods such as credit/debit cards, bank transfers, or digital wallets. This flexibility not only saves time but also enhances accessibility, catering to a broader range of preferences and lifestyles.
2. Integration and Automation
Integration of utility payment solutions with other financial tools and services has also significantly enhanced customer experience. Modern fintech solutions often integrate seamlessly with personal finance management apps, allowing users to track their utility expenses alongside other expenditures. This integration provides customers with a holistic view of their financial health and helps in budgeting effectively. Moreover, automation features offered by these solutions enable customers to set up recurring payments or receive reminders, reducing the likelihood of missed payments and associated penalties. Such automation not only saves time but also improves financial planning and peace of mind for consumers.
3. Enhanced Security Measures
Security has always been a critical concern when it comes to financial transactions, and utility payments are no exception. Fintech solutions have introduced robust security measures to protect customers' sensitive information and transactions. Advanced encryption techniques safeguard data during transmission, ensuring that personal and financial details remain secure. Additionally, authentication methods such as biometrics or two-factor authentication (2FA) add an extra layer of security, preventing unauthorized access to accounts. These security enhancements not only build trust among customers but also mitigate risks associated with fraud and identity theft, thereby enhancing overall customer experience.
4. Personalization and Customer Engagement
Another significant transformation brought about by utility payment solutions is the focus on personalization and customer engagement. Fintech platforms leverage data analytics to understand customer behavior and preferences better. By analyzing past payment patterns, these solutions can offer personalized recommendations, such as suggesting the most convenient payment method or notifying customers about potential savings through energy-efficient practices. Furthermore, interactive customer support features, such as chatbots or live customer service representatives, ensure prompt resolution of queries and issues, thereby enhancing overall satisfaction and engagement.
5. Innovation in Payment Technologies
The evolution of payment technologies has also contributed to transforming customer experience in utility payments. Contactless payments, enabled through Near Field Communication (NFC) technology or QR codes, have gained popularity due to their convenience and speed. Customers can now simply tap their smartphones or scan a code to make payments, eliminating the need for physical cards or cash. Moreover, emerging technologies like blockchain are being explored to further enhance security and transparency in utility payment transactions. These innovations not only improve efficiency but also pave the way for future advancements in the fintech software sector.
6. Sustainability and Eco-Friendliness
Utility payment solutions are increasingly aligning with sustainability initiatives, contributing to a greener future. Many fintech platforms now offer paperless billing options, allowing customers to receive and manage bills digitally instead of in print. This not only reduces paper waste but also supports environmental conservation efforts. Furthermore, by promoting energy-saving practices and providing insights into consumption patterns, these solutions empower customers to make informed decisions that contribute to a more sustainable lifestyle. Such initiatives resonate with environmentally conscious consumers, thereby enhancing their overall satisfaction with utility payment services.
Conclusion
In conclusion, utility payment solutions have undergone a remarkable transformation in recent years, driven by advancements in fintech. These innovations have not only enhanced convenience, security, and accessibility but have also personalized customer experiences and promoted sustainability. As technology continues to evolve, utility payment solutions are expected to further improve, offering even greater benefits to consumers and utility providers alike. By embracing these advancements, businesses can foster stronger customer relationships and adapt to the changing demands of the digital age effectively. Thus, the future of utility payments looks promising, with continued emphasis on innovation, security, and customer-centricity shaping the landscape of customer experience in this sector.
2 notes
·
View notes
Text
Legit Crypto Recovery services
When it comes to recovering lost or stolen cryptocurrency, finding a legitimate and reliable recovery service is crucial. Recuva Hacker Solutions stands out as a trusted and effective choice in this field. Here’s an in-depth look at what makes Recuva Hacker Solutions a legitimate crypto recovery service and how they can help you recover your assets.
What Makes Recuva Hacker Solutions Legitimate?
1. Proper Licensing and Accreditation:
- Recuva Hacker Solutions operates with the necessary licensing and accreditation required for providing cybersecurity and digital forensics services. This compliance with legal and industry standards is a key indicator of their legitimacy.
2. Positive Client Reviews:
- The company has received numerous positive reviews from satisfied clients. Testimonials highlight their professionalism, effectiveness, and the successful recovery of stolen assets, underscoring their reputation and trustworthiness.
3. Expert Team:
- Recuva Hacker Solutions employs a team of seasoned professionals with extensive experience in cybersecurity, blockchain analysis, and digital forensics. Their expertise is critical in navigating the complexities of cryptocurrency recovery.
4. Advanced Technology:
- Utilizing cutting-edge blockchain analysis tools and forensic methods, Recuva Hacker Solutions can trace and recover stolen cryptocurrencies. Their technological capabilities are among the best in the industry, ensuring accurate and efficient recovery processes.
5. Transparent Practices:
- The company maintains transparency in its operations. Clients are provided with detailed explanations of services, fee structures, and the recovery process. This openness fosters trust and confidence in their services.
6. Ethical Standards:
- Adhering to high ethical standards, Recuva Hacker Solutions ensures client confidentiality, data privacy, and legal compliance in all their operations. Their commitment to ethical practices further legitimizes their services.
7. Comprehensive Services:
- Recuva Hacker Solutions offers a wide range of services tailored to various types of cryptocurrency issues, including stolen funds recovery, fraud investigation, and digital asset protection. Their holistic approach ensures that all aspects of a client’s needs are addressed.
How Recuva Hacker Solutions Helps in Recovering Cryptocurrencies
1. Initial Consultation and Case Assessment:
- The recovery process begins with an initial consultation where Recuva Hacker Solutions gathers all relevant information about the case. This includes transaction details, wallet addresses, and any evidence related to the scam.
2. Blockchain Analysis:
- Using advanced blockchain analysis tools, the team traces the movement of the stolen cryptocurrency across the blockchain. This involves mapping the transaction path and identifying where the funds have been transferred.
3. Scammer Identification:
- Through detailed investigation and analysis, Recuva Hacker Solutions works to identify the individuals or entities responsible for the theft. This step is crucial for potential legal actions and recovery efforts.
4. Engagement with Exchanges:
- If the stolen funds have been moved to cryptocurrency exchanges, Recuva Hacker Solutions can engage with these exchanges to freeze the assets. They provide the necessary evidence and collaborate with exchange compliance teams to prevent further movement of the stolen funds.
5. Legal Collaboration:
- The company collaborates with legal authorities and law enforcement agencies to pursue legal actions against the perpetrators. This may include obtaining court orders and working with internatonal bodies to enhance the chances of recovery.
6. Negotiation and Recovery:
- In some cases, direct negotiation with the scammer may be an option. Recuva Hacker Solutions can facilitate these discussions to recover the stolen assets.
7. Client Communication:
- Throughout the recovery process, Recuva Hacker Solutions maintains regular communication with clients, providing updates and detailed reports on the progress. This transparency ensures clients are well-informed and involved.
8. Post-Recovery Support:
- Beyond recovering the stolen assets, Recuva Hacker Solutions offers advice and support to enhance clients’ security measures, helping prevent future incidents.
Contacts for Recuva Hacker Solutions
- Email: recuvahackersolutions @ inbox . lv
- WhatsApp: +1 (315) (756) (1228)
Conclusion
Recuva Hacker Solutions is a legitimate and highly effective crypto recovery service. Their expertise, advanced technology, ethical practices, and comprehensive approach make them a trusted choice for anyone looking to recover lost or stolen cryptocurrency. With a strong track record of successful recoveries and positive client feedback, Recuva Hacker Solutions stands out as a leader in the field of cryptocurrency recovery.
2 notes
·
View notes
Text
High Security Safes
In today's world, where security is paramount, safeguarding your valuable belongings and sensitive documents is of utmost importance. High security safes play a crucial role in providing that much-needed protection. Whether you're a homeowner looking to secure your jewelry and important documents or a business owner safeguarding cash and confidential data, high security safes are a reliable solution. In this comprehensive guide, we will explore everything you need to know about high security safes, including their features, benefits, types, and considerations when purchasing one.

Why High Security Safes Matter
Security breaches and thefts can happen at any time, and investing in a high security safe can give you peace of mind. Here are four compelling reasons why high security safes matter:
Protection from Burglaries: High security safes are designed to resist tampering, drilling, and other forms of attacks that burglars may use to gain access to your valuables. They provide an added layer of security that traditional safes may lack.
Fire Resistance: Many high security safes come with fire-resistant features, ensuring that your important documents and valuables remain intact even in the event of a fire. This is especially important for businesses and individuals with irreplaceable items.
Confidentiality: Safeguarding sensitive information is crucial. High security safes ensure that only authorized individuals have access to confidential documents and data, reducing the risk of data breaches and identity theft.
Peace of Mind: Knowing that your valuables and important documents are secure provides peace of mind. This allows you to focus on your daily tasks without worrying about the safety of your possessions.
Features of High Security Safes
High security safes are not your average safes. They come equipped with advanced features that make them highly resistant to unauthorized access. Here are some key features you should look for when considering a high security safe:
Heavy-Duty Construction: High security safes are typically made of thick, solid steel walls and doors, making them resistant to physical attacks.
Burglary and Fire Ratings: Look for safes that have been tested and certified for both burglary and fire resistance. Ratings such as UL 72 and TL-30x6 indicate a high level of security.
Locking Mechanisms: Advanced locking mechanisms such as electronic keypads, biometric scanners, and dual combination locks provide additional layers of security.
Re-locking Devices: These devices trigger additional locking mechanisms if tampering is detected, making it extremely difficult for burglars to gain access.
Types of High Security Safes
High security safes come in various types to cater to different security needs. Here are some common types of high security safes:
1. Burglar Safes
Burglar safes are designed primarily to protect against theft and unauthorized access. They often have thicker walls and doors, advanced locking mechanisms, and re-locking devices. These safes are ideal for storing cash, jewelry, and important documents.
2. Fireproof Safes
Fireproof safes are engineered to withstand high temperatures and protect their contents from fire damage. They are essential for safeguarding sensitive documents, irreplaceable items, and data storage devices.
3. Biometric Safes
Biometric safes use fingerprint recognition technology to grant access. They are convenient and secure, ensuring that only authorized individuals can open the safe.
4. Gun Safes
Gun safes are designed to securely store firearms and ammunition. They often come with combination locks, digital keypads, or biometric scanners to prevent unauthorized access to firearms.
Considerations When Purchasing a High Security Safe
When you're in the market for a high security safe, there are several important factors to consider to ensure you make the right choice. Here are some key considerations:
Size and Capacity: Determine the size and capacity of the safe based on what you plan to store. Make sure it can accommodate your valuables and documents comfortably.
Fire Rating: If protecting against fire is a priority, choose a safe with a high fire rating to ensure the contents remain intact in the event of a fire.
Locking Mechanism: Decide on the type of locking mechanism that best suits your needs. Electronic keypads and biometric scanners offer convenience, while combination locks may be preferred for their reliability.
Installation: Consider where and how the safe will be installed. Some safes can be anchored to the floor or wall for added security.
In conclusion, high security safes are essential for safeguarding your valuable belongings and confidential documents. They offer protection against burglaries, fires, and unauthorized access, giving you peace of mind in an increasingly uncertain world. When purchasing a high security safe, carefully consider the features and type that align with your specific security requirements. Investing in a high security safe is an investment in your peace of mind and the protection of your most valuable assets.
Remember, our experienced locksmiths in Peterborough are equipped to assist you with your security needs, including high security safes. We offer a wide range of locksmith services, ensuring that your security is our top priority.
youtube
Here are 10 frequently asked questions (FAQs) about high security safes:
What is a high security safe?
A high security safe is a specialized safe designed to provide maximum protection against theft, fire, and unauthorized access. It typically features advanced security features and construction.
How is a high security safe different from a regular safe?
High security safes are constructed with thicker steel walls and doors, advanced locking mechanisms, and often come with burglary and fire ratings. They offer a higher level of security compared to regular safes.
What are burglary and fire ratings for high security safes?
Burglary and fire ratings indicate the safe's resistance to break-ins and protection against fire. For example, a TL-30x6 rating means the safe can withstand a professional burglary attempt for 30 minutes.
Are high security safes fireproof?
Many high security safes are fire-resistant, but they may not be completely fireproof. They are designed to withstand high temperatures for a specified period, protecting their contents from fire damage.
Can I open a high security safe if I forget the combination or lose the key?
High security safes with electronic keypads or biometric scanners may offer backup methods for opening, such as master codes or fingerprint recognition. Consult your safe's user manual for guidance.
What should I consider when choosing the size of a high security safe?
Consider the size of the items you plan to store and choose a safe with enough capacity to accommodate them comfortably. It's better to have extra space than to cram items into a too-small safe.
How should I install a high security safe?
Safes can be installed by anchoring them to the floor or wall for added security. Consult the manufacturer's installation instructions or hire a professional locksmith to ensure proper installation.
Are biometric safes more secure than safes with combination locks?
Biometric safes offer convenience and security, as they require fingerprint recognition for access. However, both types of safes can be secure if properly designed and constructed.
Can I move a high security safe once it's installed?
Moving a high security safe can be challenging due to their weight and size. It's recommended to consult a professional safe mover or locksmith for safe relocation.
Do I need professional assistance to choose and install a high security safe?
While it's possible to select and install a high security safe on your own, it's advisable to seek the expertise of a professional locksmith or safe technician to ensure the best security and proper installation.
Follow Us: Blogger | Weebly | Twitter | Gravatar | Disqus | Google-Sites | Youtube | About.Me
2 notes
·
View notes
Text
Win Mobile and PC Monitoring Software: A Comprehensive Guide
In an era where digital devices are an integral part of our daily lives, monitoring and managing their usage have become essential. Whether you're a concerned parent, a business owner, or an individual looking to ensure the security of your devices and data, Win Mobile and PC monitoring software can be a valuable tool in your arsenal. In this article, we will explore the world of monitoring software for Windows-based computers and mobile devices, highlighting their features, benefits, and considerations.
Understanding Win Mobile and PC Monitoring Software
Win Mobile and PC monitoring software, often referred to as computer or mobile monitoring software, is a category of software designed to track and record activities on Windows-based computers and mobile devices. These tools serve various purposes, from parental control and employee monitoring to security and data protection. Let's delve into their key features and applications.
Key Features
Activity Logging: Monitoring software records a wide range of activities, including keystrokes, web browsing history, application usage, and file transfers. This comprehensive logging helps users gain insights into what happens on the monitored device.
Screen Recording: Some advanced monitoring tools can capture screenshots or record the screen in real-time, allowing you to see exactly what the user is doing on their device.
Remote Access: Many monitoring programs offer remote access capabilities, enabling users to view the monitored device's screen or perform certain actions from a remote location. This can be particularly useful for troubleshooting or parental guidance.
Alerts and Notifications: Monitoring software can be configured to send alerts and notifications when specific keywords are detected in messages or when certain actions are taken, helping users stay informed in real-time.
GPS Tracking: Mobile monitoring solutions often include GPS tracking features, allowing you to track the physical location of a mobile device in real-time.
Applications
Parental Control: Parents can use monitoring software to keep an eye on their children's online activities, ensuring they are safe and responsible online. It helps in preventing exposure to inappropriate content and managing screen time.
Employee Monitoring: Businesses can use monitoring software to increase employee productivity, monitor workstation usage, and protect sensitive company data from insider threats.
Security: Monitoring software can act as a security tool by identifying and preventing unauthorized access, potentially saving sensitive data from theft or loss.
Data Recovery: In case of device theft or data loss, monitoring software can help track the device's location or recover important files and data.
Considerations and Ethics
While Win Mobile and PC monitoring software offer significant advantages, there are ethical and legal considerations to keep in mind:
Legal Compliance: Ensure that your use of monitoring software complies with local and international laws. Unauthorized monitoring can result in legal consequences.
Privacy: Respect the privacy of individuals being monitored, especially in a personal or workplace context. Transparent communication is key.
Consent: In many cases, obtaining consent from the individuals being monitored is essential and legally required.
Conclusion
Win Mobile and PC monitoring software can be a powerful ally in ensuring the safety, productivity, and security of your digital devices and data. However, it's crucial to use such software responsibly, ethically, and in compliance with applicable laws and regulations. Whether you're a parent, an employer, or an individual concerned about your own digital security, choosing the right monitoring software and using it judiciously can make a significant difference in your digital world.
Ready to take control of your digital world and ensure the security and productivity of your devices? Don't wait any longer; it's time to explore the benefits of Win Mobile and PC monitoring software. Here's your call to action:
Choose the Right Software: Begin by researching and selecting the monitoring software that best suits your needs. Look for reputable options with the features you require.
Download and Install: Download the chosen software from a trusted source and follow the installation instructions carefully.
Configure and Customize: Take the time to configure the software to your preferences. Customize alert settings, access permissions, and monitoring parameters to align with your objectives.
Educate Yourself: Familiarize yourself with the software's features and capabilities. Understand how to use it effectively for your specific purposes.
Respect Privacy and Consent: If you're monitoring others, always ensure you have proper consent, and respect privacy laws and ethical guidelines.
Stay Informed: Keep yourself informed about updates and improvements to the software. Regularly check for updates to benefit from the latest security enhancements and features.
Seek Support: If you encounter any issues or have questions, don't hesitate to reach out to the software's support team or community for assistance.
Monitor Responsibly: Use the software responsibly and ethically, whether it's for parental control, employee monitoring, or security purposes. Balancing security with privacy is essential.
Now, take the first step towards a safer and more controlled digital environment. Download your chosen Win Mobile and PC monitoring software today and experience the peace of mind and productivity benefits it can offer. Your digital world is in your hands—make the most of it with monitoring software.
2 notes
·
View notes
Text
Surveying Online Security Challenges: Are You at Risk

In the age of digitalization, online surveys have become an indispensable tool for gathering insights and feedback from a wide range of participants. However, this convenience comes with its own set of security challenges that organizations and individuals must grapple with. From data breaches to privacy concerns, the realm of online surveys is not immune to cyber threats.
One of the primary security challenges is the risk of data breaches. The sensitive information collected through online surveys, such as personal details and opinions, can be valuable targets for malicious actors. If proper encryption and security measures are not in place, unauthorized access to this data could lead to identity theft, fraud, and compromised privacy.
Phishing attacks also pose a significant threat. Cybercriminals may impersonate legitimate survey platforms or send fraudulent survey invitations to unsuspecting participants. Once recipients click on malicious links or provide personal information, their data becomes vulnerable to exploitation.
Another pressing concern is the potential for survey manipulation. Hackers could tamper with survey responses, skewing the accuracy of the collected data. This could have serious implications for organizations relying on the survey results to make informed decisions.
To address these security challenges, there are several steps that individuals and organizations can take. Implementing strong encryption protocols for data storage and transmission is essential. Choosing reputable survey platforms with a proven track record of security can also mitigate risks.
Moreover, participants should be educated about the risks of phishing and vigilant about the sources of survey invitations. Being cautious when providing personal information and avoiding suspicious links can go a long way in safeguarding sensitive data.
In conclusion, while online surveys offer unparalleled convenience and accessibility, they also bring forth security challenges that should not be ignored. By understanding these risks and taking proactive measures, individuals and organizations can enjoy the benefits of online surveys without compromising the security of their data.
To know more: Are you facing security challenges in Online Survey
Online research project management platform
fraud prevention solution
Marketing Research and Insights
2 notes
·
View notes
Text
Cybersecurity Companies in India: Safeguarding the Nation’s Digital Future

Why Cybersecurity Matters Now More Than Ever
Cybersecurity threats are no longer confined to multinational corporations or tech-heavy sectors. Today, even small and mid-sized businesses in India are being targeted by ransomware, phishing schemes, malware, and social engineering attacks. According to recent studies, India experiences thousands of attempted cyber breaches every day—making it one of the top five countries facing cyber threats globally.
What Do Cybersecurity Companies in India Offer?
India’s cybersecurity service providers offer a comprehensive suite of solutions tailored to different industries, business sizes, and security needs. Their services commonly include:
1. Network Security
Secures internal infrastructure from unauthorized access, intrusion attempts, and malware infiltration. Firewalls, intrusion detection/prevention systems, and network monitoring tools are commonly used.
2. Cloud Security
With cloud adoption on the rise, protecting cloud environments has become essential. Cybersecurity firms offer encryption, identity management, and data loss prevention (DLP) solutions to ensure safe cloud operations.
3. Endpoint Protection
Cyber attackers often target endpoints like employee laptops, mobile phones, and servers. Cybersecurity companies deploy antivirus, anti-malware, and device management solutions to keep these entry points secure.
4. Threat Intelligence and Monitoring
Through AI, analytics, and real-time monitoring, providers identify and neutralize threats before they cause damage. Continuous threat assessment helps prevent data breaches and system outages.
5. Application Security
Web and mobile applications are frequent targets for attacks like SQL injection, cross-site scripting, and zero-day exploits. Cybersecurity firms conduct security testing and implement robust application firewalls.
6. Penetration Testing and Vulnerability Assessments
These simulate cyberattacks to uncover weak points in a company’s system. Regular audits help businesses stay proactive rather than reactive.
7. Security Awareness Training
People are often the weakest link in security. Cybersecurity companies provide training modules to educate employees on safe online practices, phishing prevention, and password hygiene.
8. Regulatory Compliance
As data protection regulations grow stricter—both in India and globally—businesses need help meeting compliance standards like GDPR, ISO 27001, and India's IT Act. Cybersecurity companies help implement and maintain compliant systems.
Sectors Relying Heavily on Cybersecurity Companies in India
1. Finance & Banking: The BFSI sector is a prime target due to the volume of transactions and sensitive financial data. Cybersecurity companies help in deploying advanced fraud detection and secure payment systems.
2. Healthcare: From patient records to medical devices, hospitals and clinics now require HIPAA-compliant digital protection.
3. E-commerce & Retail: With high volumes of customer data and payment processing, online retailers need 24/7 protection against fraud and data theft.
4. Government & Defense: National security, smart city projects, and citizen data management make the public sector a key client for cybersecurity solutions.
5. IT & SaaS Companies: These businesses often act as custodians of client data, and maintaining trust means maintaining security at every layer.
The Rise of Local Expertise
One of the standout trends in India’s cybersecurity landscape is the growth of homegrown expertise. Indian companies are now building cutting-edge technologies for encryption, blockchain security, AI-driven threat detection, and cloud-native protection. With an understanding of local regulations, languages, and business practices, they are better equipped to serve the Indian market than many global players.
The rise of startup hubs, government incentives, and increasing demand from Tier 2 and Tier 3 cities has also created an ecosystem that supports the growth of cybersecurity talent and innovation.
Challenges Faced by Cybersecurity Companies in India
While the sector is growing, challenges remain:
Shortage of skilled professionals: There’s a demand-supply gap in cybersecurity experts, which often leads to increased service costs.
Rapidly evolving threats: Attackers use sophisticated and ever-changing tactics, requiring constant R&D investment.
SME Awareness: Small businesses often underestimate the need for cybersecurity, exposing them to preventable risks.
Legacy systems: Many organizations still run outdated systems that are difficult to secure.
Despite these hurdles, Indian cybersecurity providers continue to adapt and innovate to stay ahead of attackers.
Future Outlook: What Lies Ahead?
The future of cybersecurity in India looks promising. With the Digital India initiative, the rise of 5G, and growing adoption of AI and IoT, the need for cybersecurity will only intensify. Companies will increasingly turn to advanced technologies like zero-trust architectures, machine learning for threat prediction, and blockchain for data integrity.
Government efforts like the National Cyber Security Policy and incentives for cybersecurity startups further indicate a national-level push toward a secure digital future.
Conclusion
Cybersecurity is no longer a luxury—it’s a necessity for every business in today’s digital age. As threats evolve, so must our defenses. Fortunately, a strong ecosystem of cybersecurity companies in India is rising to meet the challenge.
Whether you run a small startup or a large enterprise, now is the time to invest in intelligent, scalable, and responsive cybersecurity solutions. The cost of ignoring it could be far greater than the investment required to stay protected.
Call to Action
Protect your business before it’s too late. If you're looking for a reliable, scalable, and industry-compliant cybersecurity partner, explore how leading cybersecurity companies in India can secure your digital journey. Start with a security assessment today—because prevention is always better than breach.
0 notes
Text
🚗 GPS Car Tracking: Enhancing Safety and Control on the Road
In today’s fast-paced world, knowing the exact location of your vehicle isn’t just a convenience—it’s a necessity. GPS car tracking has become an essential tool for vehicle owners, businesses, and families looking to increase safety, efficiency, and peace of mind. 🛰️📍
Whether you're managing a fleet or monitoring a personal car, GPS tracking provides real-time updates, improves route planning, and helps prevent theft. Let's explore how it works and why it’s such a powerful solution. 🔐

📡 What is GPS Car Tracking?
GPS car tracking involves using satellite-based technology to monitor the real-time location of a vehicle. A small tracking device is installed in the car, which sends signals to a central system or app, allowing the user to see where the vehicle is at all times. 🌍🚙
It’s commonly used by individual drivers, rental companies, logistics firms, and parents keeping tabs on young drivers.
⚙️ How GPS Car Tracking Works
GPS trackers rely on a combination of satellite communication and cellular networks to transmit data. Here's how it typically works:
📶 Step-by-Step Process
The GPS tracker receives location data from satellites
That data is sent to a central server or cloud system
Users access the information via mobile app or desktop dashboard
Real-time updates, alerts, and reports are generated
This system ensures complete visibility and helps users make smarter, faster decisions.
🎯 Key Features of GPS Car Tracking Devices
Modern tracking systems come with a variety of advanced features that go far beyond just knowing your car’s location.
📍 Real-Time Location Tracking
View the exact location of the vehicle on a live map
Track movement, speed, and direction
Share vehicle location with others when needed
🔔 Geofencing Alerts
Set virtual boundaries around areas like work, home, or school
Get notified when the car enters or exits specific zones
Ideal for monitoring teens or business vehicle usage
🔋 Battery and Power Monitoring
Get alerts on low battery or device disconnection
Monitor health of internal vehicle battery
Prevent loss of tracking due to power issues
📊 Trip History & Reports
View past routes and trip durations
Analyze driving patterns and idle times
Useful for tax reporting and mileage tracking
🚀 Benefits of Using GPS Car Tracking
Whether you're an individual or a business, GPS tracking can improve safety, accountability, and cost-efficiency.
🛡️ Enhanced Security
Helps recover stolen vehicles quickly
Alerts for suspicious movements or unauthorized use
Peace of mind when leaving your vehicle parked
💰 Cost Savings
Optimize routes and reduce fuel consumption
Monitor and correct wasteful driving behavior
Lower insurance premiums in some cases
⏱️ Better Time Management
Reduce downtime and improve planning
Monitor delivery and appointment schedules
Minimize delays and increase punctuality
👨👩👧 Family Safety
Know where your loved ones are while they drive
Ensure safer travel for teenagers and elderly drivers
Set alerts for high-speed driving or curfews

🧰 Who Can Benefit from GPS Car Tracking?
GPS tracking isn’t just for commercial fleets—many different users can benefit from this smart solution:
🚗 Personal vehicle owners
🚚 Delivery and service businesses
🏫 Schools and student transportation
🚖 Taxi and ride-share operators
👪 Families and caregivers
Whether you’re tracking one car or many, GPS systems help you stay connected and in control.
🧭 Choosing the Right GPS Car Tracker
When selecting a GPS car tracking system, consider the following:
Real-time tracking capabilities
Mobile app availability and ease of use
Battery life or power source
Reporting features and alert types
Monthly subscription fees, if applicable
Pick a solution that fits your needs without adding unnecessary complexity. 📱⚙️
🏁 Final Thoughts
GPS car tracking transforms how you interact with your vehicle. From security and savings to convenience and control, the benefits are undeniable. 🌟
Whether for personal peace of mind or operational efficiency, installing a GPS tracker is a smart step toward modern vehicle management. Stay informed, stay alert, and drive with confidence. 🛣️🔐
Contact Us Today!
Business Address: 55 Louvain Street West Suite 402, Montreal, Quebec H2N 1A4
Business Phone: Monday-Friday : 9:00 am - 5:00 pm
Hours of Operations: Monday-Friday : 9:00 am - 5:00 pm
0 notes