#Docker Lab
Explore tagged Tumblr posts
Text
Understanding Docker Playground Online: Your Gateway to Containerization
In the ever-evolving world of software development, containerization has become a pivotal technology, allowing developers to create, deploy, and manage applications in isolated environments. Docker, a leader in this domain, has revolutionized how applications are built and run. For both novices and seasoned developers, mastering Docker is now essential, and one of the best ways to do this is by leveraging an Online Docker Playground. In this article, we will explore the benefits of using such a platform and delve into the Docker Command Line and Basic Docker Commands that form the foundation of containerization.
The Importance of Docker in Modern Development
Docker has gained immense popularity due to its ability to encapsulate applications and their dependencies into containers. These containers are lightweight, portable, and can run consistently across different computing environments, from a developer's local machine to production servers in the cloud. This consistency eliminates the "it works on my machine" problem, which has historically plagued developers.
As a developer, whether you are building microservices, deploying scalable applications, or managing a complex infrastructure, Docker is an indispensable tool. Understanding how to effectively use Docker begins with getting comfortable with the Docker Command Line Interface (CLI) and mastering the Basic Docker Commands.
Learning Docker with an Online Docker Playground
For beginners, diving into Docker can be daunting. The Docker ecosystem is vast, with numerous commands, options, and configurations to learn. This is where an Online Docker Playground comes in handy. An Online Docker Playground provides a sandbox environment where you can practice Docker commands without the need to install Docker locally on your machine. This is particularly useful for those who are just starting and want to experiment without worrying about configuring their local environment.
Using an Online Docker Playground offers several advantages:
Accessibility: You can access the playground from any device with an internet connection, making it easy to practice Docker commands anytime, anywhere.
No Installation Required: Skip the hassle of installing Docker and its dependencies on your local machine. The playground provides a ready-to-use environment.
Safe Experimentation: You can test commands and configurations in a risk-free environment without affecting your local system or production environment.
Immediate Feedback: The playground often includes interactive tutorials that provide instant feedback, helping you learn more effectively.
Getting Started with Docker Command Line
The Docker Command Line Interface (CLI) is the primary tool you'll use to interact with Docker. It's powerful, versatile, and allows you to manage your Docker containers and images with ease. The CLI is where you will issue commands to create, manage, and remove containers, among other tasks.
To begin, let's explore some Basic Docker Commands that you will frequently use in your journey to mastering Docker:
docker run: This command is used to create and start a new container from an image. For example, docker run hello-world pulls the "hello-world" image from Docker Hub and runs it in a new container.
docker ps: To see a list of running containers, use the docker ps command. To view all containers (running and stopped), you can add the -a flag: docker ps -a.
docker images: This command lists all the images stored locally on your machine. It shows details like the repository, tag, image ID, and creation date.
docker pull: To download an image from Docker Hub, use docker pull. For example, docker pull nginx fetches the latest version of the NGINX image from Docker Hub.
docker stop: To stop a running container, use docker stop [container_id]. Replace [container_id] with the actual ID or name of the container you want to stop.
docker rm: Once a container is stopped, you can remove it using docker rm [container_id].
docker rmi: If you want to delete an image from your local storage, use docker rmi [image_id].
Conclusion
Mastering Docker is a crucial skill for modern developers, and utilizing an Online Docker Playground is one of the most effective ways to get started. By practicing Docker Command Line usage and familiarizing yourself with Basic Docker Commands, you can gain the confidence needed to manage complex containerized environments. As you progress, you'll find that Docker not only simplifies the deployment process but also enhances the scalability and reliability of your applications. Dive into Docker today, and unlock the full potential of containerization in your development workflow.
0 notes
Text
5 single-purpose containers that run better on a Raspberry Pi than on a full server
2 notes
·
View notes
Text
#ok there we go im done now#back to tending this fuck ass frustrating ass piece of shit#if i had a gun id play roulette with my head and my computer#docker is such a piece of shit#i can run the entire process on my desktop why the FUCK is docker required#I HATE DOCKER#i <3 programming#edit: im up to date with 2 out of 3 labs so its ok#im like the inferior version of dr ratio#dawg i just know that docker error is gonna be some extremely stupid ass shit and then im going to tweak out fr#it better be#because the worse option is the fact that literally nothing works and everything is an error#i wish i could show someone augh#i can complain tho. you get to hear me complain
2 notes
·
View notes
Text
I'm self-hosting my own Link tree alternative. I don't really know why, but I love it :)
Its using a docker called "linkstack" on my Unraid server. Very excited.
1 note
·
View note
Text
CoreControl is a great new Home Lab Dashboard #homelab #selfhosting #homeserver #homelabdashboard
0 notes
Text
Security-Focused DevOps: Embedding Security at Every Stage
Introduction
In today’s rapidly evolving digital landscape, security is not just an afterthought; it’s a necessity at every phase of the development and deployment process. With cyber threats becoming increasingly sophisticated, a security-focused DevOps strategy ensures that your applications and infrastructure remain resilient and safeguarded against potential vulnerabilities. Here, we’ll dive into how embedding security at every stage of DevOps—often referred to as DevSecOps—helps businesses strengthen their defenses and stay compliant.
What is Security-Focused DevOps?
Security-focused DevOps, or DevSecOps, is an approach that integrates security into the DevOps process right from the start. Instead of treating security as a final step in the development lifecycle, it’s woven into each phase—coding, testing, deployment, and monitoring. By automating security checks and incorporating best practices, DevSecOps enables teams to identify and fix vulnerabilities faster, reducing risk and ensuring that security is an inherent part of your development pipeline.
Security at Every Stage: Key Phases
Let’s break down how security can be effectively integrated into each phase of DevOps:
Plan and Code with Security in Mind
During the planning and coding phase, developers are encouraged to follow secure coding practices, such as validating inputs, avoiding hard-coded secrets, and regularly updating dependencies.
Tools Used: Static Application Security Testing (SAST) tools analyze the codebase for vulnerabilities early on, providing valuable feedback to developers without disrupting their workflow.
Automated Security Testing in the Build Phase
Automated security testing, including dynamic and static testing, ensures that vulnerabilities are identified as the code evolves.
Tools Used: Dynamic Application Security Testing (DAST) and software composition analysis (SCA) tools verify dependencies and third-party libraries for security risks, reducing the likelihood of shipping compromised applications.
Secure Deployment and Configuration
Security in deployment focuses on infrastructure-as-code (IaC) practices, where configurations are securely defined, stored, and monitored.
Tools Used: IaC security scanning tools identify misconfigurations before deployment, while container security solutions protect containerized applications.
Continuous Compliance Monitoring
Compliance monitoring ensures adherence to industry standards like GDPR, HIPAA, and PCI-DSS. This phase includes regular audits and compliance scans.
Tools Used: Compliance monitoring tools generate reports, track regulatory adherence, and provide insights into potential areas of risk.
Operate and Monitor for Threat Detection
Continuous monitoring, alerting, and logging help detect and respond to threats in real-time. Automated incident response further enhances this phase, allowing for swift action against detected risks.
Tools Used: Security Information and Event Management (SIEM) and Intrusion Detection Systems (IDS) monitor application activity, detect anomalies, and trigger alerts.
Why DevSecOps Matters
Minimizes Risk of Breaches: Early vulnerability detection allows for immediate remediation, significantly reducing the risk of breaches and data loss.
Cost-Effective: Fixing security issues early in the development process is far less expensive than addressing them post-deployment.
Enhanced Compliance: DevSecOps ensures continuous adherence to regulatory standards, making audits smoother and ensuring that applications stay compliant with minimal disruption.
Improves Team Collaboration: By embedding security in DevOps, security is no longer a blocker but a shared responsibility, encouraging collaboration between developers, IT, and security teams.
Best Practices for Security-Focused DevOps
Automate Security Testing: Automated tests provide quick feedback and make security checks a seamless part of the CI/CD pipeline.
Implement Zero-Trust Security Models: Only grant permissions as needed, minimizing exposure and ensuring that users have only the access they need.
Educate and Train Teams on Security: Keep teams updated on security best practices, threat awareness, and incident handling to build a culture of security within the organization.
Use DevSecOps Tools Efficiently: Incorporate tools that suit your environment, such as SAST, DAST, and cloud-native security solutions, to create a secure DevOps pipeline tailored to your needs.
Conclusion
Security-focused DevOps, or DevSecOps, transforms security from an isolated function into a core component of the development process. By embedding security at every phase—from planning to monitoring—you create a robust, resilient, and secure development environment. Not only does this reduce the risk of breaches and compliance violations, but it also fosters a culture of shared responsibility and continuous improvement within your teams. In the age of rapid digital transformation, security-focused DevOps is essential for businesses aiming to protect their assets, safeguard customer data, and maintain trust. For more details click www.hawkstack.com
#redhatcourses#information technology#containerorchestration#docker#container#kubernetes#linux#containersecurity#dockerswarm#aws#hawkstack technologies#qcs dc labs
0 notes
Text
youtube
Raspberry Pi 5 Mastery: Create a Powerful Home Server/Home lab
Learn how to become a Raspberry Pi 5 Master. Create a Powerful Home Server/Home lab using just a Pi 4 or 5 using Docker.
#education#free education#hacking#security#Raspberry Pi 5 Mastery#Raspberry Pi 5#Create a Powerful Home Server#How to create a Powerful Home Server#home server#windows 10#youtube#cyber security#home lab#raspberry pi server#raspberry pi docker#raspberry pi#Youtube
0 notes
Text
replacing her with a shiny new VM (now with twice the disk space!) RIP you will be missed o7
My Ubuntu vm.... speak to me I have more hard drive space for you you just have to boot so I can repartition please...
#There was like. One file that actually mattered on the old machine and I have a copy of that already#Gonna have to install docker again but that's whatever. It's not too bad on Linux#unlike some other operating systems. Looking at YOU Windows 10#It's just going to take. Time. But by God I'm finishing this lab today
15 notes
·
View notes
Text




December 10, 2024 • Tuesday
Counting down until the new year — 22 days to go!
Today was a mix of both good and bad. I started the day off with one hour of vc with @guzscode where he taught me a bunch of interesting stuff about dockers (half of it was him cussing at his screen but we don't talk about that XD)
I also had a weird uni day, I slept through the first two classes (literally asked permission and slept) coz I was feeling unwell and woozy, then spent an English class reading a play that was so frickin chaotic and then hogged a donut and a chicken bun.
The afternoon lab session was fun, I got to play with different colored wires hehe
All in all, a very mixed kinda day.
🎧 Death by a Thousand Cuts — Taylor Swift

#dailyfoxposts#studyblr#codeblr#studyspo#study#compblr#coding#dockers#productivity#uniblr#gradblr#university#undergrad#computer applications#compsci#computer networks
39 notes
·
View notes
Text


This week was a productive one. I've been studying microservices to better understand distributed systems. At the bus company where I work, we use a monolithic system—an old-school setup style with MySQL, PHP, some Java applications, localhost server and a mix of other technologies. However, we've recently started implementing some features that require scalability, and this book has been instrumental in helping me understand the various scenarios involved.
In the first chapters, I've gained a clearer understanding of monolithic systems and the considerations for transitioning to a distributed system, including the pros and cons.
I've also been studying Java and Apache Kafka for event-driven architecture, a topic that has captured my full attention. In this case, the Confluent training platform offers excellent test labs, and I've been running numerous tests there. Additionally, I have my own Kafka cluster set up using Docker for most configurations.
With all that said, I've decided to update this blog weekly since daily updates it's not gonna work.
#coding#developer#linux#programming#programmer#software#software development#student#study blog#study aesthetic#studyblr#self improvement#study#software engineering#study motivation#studyblr community#studying#studynotes#learning#university#student life#university student#study inspiration#brazil#booklr#book#learn#self study#java#apachekafka
21 notes
·
View notes
Text
[amir | aoi | quincy]
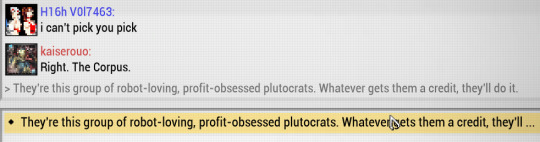
i love how the drifter immediately mentioned robot loving up at the front. they know how to get his attention
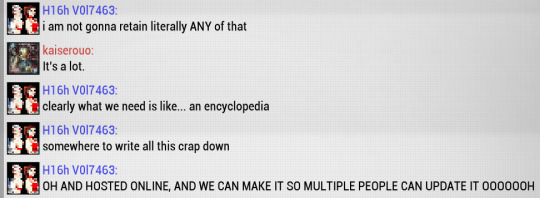
as one of the system admin in my lab when i heard anything about hosting wiki i see trouble... well maybe not that much but we added a bunch of services this semester and that's still part of the trouble
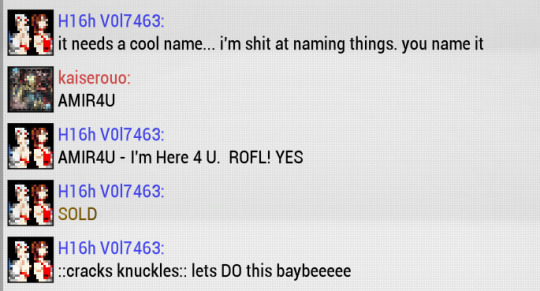
oh yeah you don't have docker and probably don't have good vm technology too... well that sounds more like a hassle now. good for you amir, good for you.
hope techrot don't hack your server or whatnot considering there's literally a bunch of fucked up infested plants inside this very building for easy physical access
---

i... literally forgot that. about the "life on other planets" part.

aww. also maybe i really should've played the whole main campaign again.
huh... never thought about that. basically free human floating

i mean... everything is relative i guess. we discover something in every era.
...maaaaaybe except in warframe because the orokins are just too advanced so people might be better off making do with "old" technology.
---
can we just get to the backroom sex part already im planning to date you this year.
that is probably one of the most fucked up shit i said in my life.
14 notes
·
View notes
Text
Oh, h___, Brawling with Dockers actually does require MYN.
OK, I can still get Justificande Coins and Surface Currency from the Rat Market, by letting Rat-Shillings expire. At least 521 Rat Shillings, according to the wiki. Randomly, which could make it annoying; not so much for the single coin I need for the Lab as the many coins I'll eventually need for the Railway. Well, I knew I was going to be doing a bunch of Rat Market grinding anyway, best start now.
Also going to miss out on some of the other stuff available there, not least the convenient Wounds reduction. But nothing that will block me.
6 notes
·
View notes
Text
Circumstances of Encounter: Dola Hallowrove

A list of places Hallowrove frequents and what they might be found doing there. Meant as a helpful reference for anyone looking for a premise for calling card messages or other ingame social interactions, or who wants to let me know that one would work well for me to send to them.
In-game name for social actions: Dola Hallowrove
Wolfstack Docks: Can often be found there gathering monstrous rumours and stories from zailors and dockhands, or maintaining the mechanical aspects of the Hammerhead II zubmarine. Likely to meet: Zailors, dockers, brawlers
The Medusa's Head: A favoured spot for relaxation after a long day, as well as exchanging work talk with likeminded and similarly chewed-on colleagues. (And whoever else chooses to drop in - Hallowrove is personable to a wide range of people.) Likely to meet: Menace Eradicators, Monster-Hunters, anyone else with a reason to be there
The Department of Menace Eradication: Hallowrove has no professional office, but he directs those hoping to commission him to leave a note with the front desk at the Department. He checks back semi-regularly. Likely to meet: See above + prospective monster-hunting clients
Bugsby's Marsh: Hallowrove's place of residence. She lives in a fixed-up cabin in the swamp, a 10 minute walk or so from what could be considered the city. With a little persuasion, she might be convinced to lead a guided nature tour. Likely to meet: People living nearby, tour-goers, any poor sod who got lost
The Upper River: Hallowrove's longest standing commission is with the GHR, primarily improving the stations' defenses against monsters, but finding every excuse for a wide variety of diversions along the way. Likely to meet: Rubberies, artists, railway workers, Discordant stewards, devils, anyone else riding the train
Sophia's Club: While recent attendance is spotty, can still be found on picnics or sitting in on tea meetings with the group on a quiet afternoon. Likely to meet: Monster-Hunters, fellow members of Sophia's
The Bazaar Sidestreets: A place often passed through for shopping or visiting. Likely to meet: Anyone who lives in the area, anyone who shops there
Benthic University: While Hallowrove seldom uses her own lab, she often makes stops at Benthic to deliver monstrous samples to academic friends for dissection and analysis. Her own lab work consists mainly of hobby mechanical fiddling and weapon repairs/improvements, and creation of antivenoms by trial-and-error. Likely to encounter: Correspondents, academics
Calling cards, Menace helps, teas, slights, etc. are all on the table! I have no reason to be stingy with my actions right now, so I will offer whatever helps or lessons in Dangerous I can if the need is there.
#hallowrove tag#Will try to keep this updated with any new places I can think of :>#reblog with some basic info on where our characters would likely see each other if you'd like a calling card!#or feel free to send me one yourself#My energy is fairly low at the moment but i want to get connected with a lot more people so I'm going to try and send out lots this week
11 notes
·
View notes
Text
Did you enjoy my middle school au?
good because here's more on it.
Ok first things first, Rick and Nicky were made in a lab, they look kind of off normally and they can turn into flesh abominations for fun.
Nicky acts aloof but they just don't know how to talk to people, Narcis says shit like "Yeah, I hate humans too, I hate them so much we should be friends." 2012 website behavior/pos, it works too because Nicky thinks their unironically cool.
The challenger can pick up people twice his height with literally no problem.
Due to how Nicky was made they have the defect where their limbs, just, fall off, their "parents" (The dockers who made them) give them prosthetics and tell them to cover up (there limbs grow back, don't worry), at one point challenger saw their robotic arm and Nicky said they were a robot, challenger believed them.
Rick needs glasses but he never where's them because he thinks there for nerds (he bumps into everything.)
Hurricane usually has dreads but whenever he has his natural hair out, it, is, so, large.
Gabby jay is only 10 years younger than the original version, but he looks far younger, he has one (1) gray hair and stars crying about it and then Hoy drop kicks him into space.
Dragon Chan is still named Dragon because his ass is HYPERFIXATED on them, almost all of his shirts have dragons on them, Rick ones showed him a dragon anime about maids and he almost fainted, he loves Eragon, he loves lotr and wants dnd.
Dragon also has a lot of acne.
Aarn is Dragon's only friend, Aarn is also a metal head.
Everyone is convinced that Heike is an alien (he's not for the record).
Heike is friends with Narcis and Bob Charlie
Charlie sees the odd shit Heike does and just goes "Oh, Heike you're so silly :)".
There's a paranormal club with three members, mad clown who only joined because his mom said he needed to make friends, Masked muscle the founder of the club, and Aarn who talks about getting abducted (lie).
Heike dresses like a 2000's Disney channel star he unironically wares a skirt over jeans.
#super punch out#punch out#rick bruiser#nick bruiser#narcis prince#birdie mac#piston hurricane#gabby jay#dragon chan#aran ryan#heike kagero#bob charlie#mad clown#masked muscle#tw swearing
20 notes
·
View notes
Text
Docker Rollout: Zero-Downtime Deployments for Docker Compose Made Simple #docker #containers #kubernetes #zerodowntime #dockerrollout #dockercompose
0 notes
Text
Build the Future of Tech: Enroll in the Leading DevOps Course Online Today
In a global economy where speed, security, and scalability are parameters of success, DevOps has emerged as the pulsating core of contemporary IT operations. Businesses are not recruiting either developers or sysadmins anymore—employers need DevOps individuals who can seamlessly integrate both worlds.
If you're willing to accelerate your career and become irreplaceable in the tech world, then now is the ideal time to sign up for Devops Course Online. And ReferMe Group's AWS DevOps Course is the one to take you there—quicker.

Why DevOps? Why Now?
The need for DevOps professionals is growing like crazy. As per current industry reports, job titles such as DevOps Engineer, Cloud Architect, and Site Reliability Engineer are among the best-paying and safest careers in technology today.
Why? Because DevOps helps businesses to:
Deploy faster using continuous integration and delivery (CI/CD)
Boost reliability and uptime
Automate everything-from infrastructure to testing
Scale apps with ease on cloud platforms like AWS
And individuals who develop these skills are rapidly becoming the pillars of today's tech teams.
Why Learn a DevOps Online?
Learning DevOps online provides more than convenience—it provides liberation. As a full-time professional, student, or career changer, online learning allows you:
✅ To learn at your own pace
✅ To access world-class instructors anywhere
✅ To develop real-world, project-based skills
✅ To prepare for globally recognized certifications
✅ J To join a growing network of DevOps learners and mentors
It’s professional-grade training—without the classroom limitations.
What Makes ReferMe Group’s DevOps Course Stand Out?
The AWS DevOps Course from ReferMe Group isn’t just a course—it’s a career accelerator. Here's what sets it apart:
Hands-On Labs & Projects: You’ll work on live AWS environments and build end-to-end DevOps pipelines using tools like Jenkins, Docker, Terraform, Git, Kubernetes, and more.
Training from Experts: Learn from experienced industry experts who have used DevOps at scale.
Resume-Reinforcing Certifications: Train to clear AWS and DevOps certification exams confidently.
Career Guidance: From resume creation to interview preparation, we prepare you for jobs, not course completion.
Lifetime Access: Come back to the content anytime with future upgrades covered.
Who Should Take This Course?
This DevOps course is ideal for:
Software Developers looking to move into deployment and automation
IT Professionals who want to upskill in cloud infrastructure
System Admins transitioning to new-age DevOps careers
Career changers entering the high-demand cloud and DevOps space
Students and recent graduates seeking a future-proof skill set
No experience in DevOps? No worries. We take you from the basics to advanced tools.
Final Thoughts: Your DevOps Journey Starts Here
As businesses continue to move to the cloud and automate their pipelines, DevOps engineers are no longer a nicety—they're a necessity. Investing in a high-quality DevOps course online provides you with the skills, certification, and confidence to compete and succeed in today's tech industry.
Start building your future today.
Join ReferMe Group's AWS DevOps Course today and become the architect of tomorrow's technology.
2 notes
·
View notes