#Encryption Software Market Share
Explore tagged Tumblr posts
Text
Encryption Software Market Size, Share, Demand and Forecast 2023-2028
IMARC Group has recently released a new research study titled “Encryption Software Market: Global Industry Trends, Share, Size, Growth, Opportunity and Forecast 2023-2028”, offers a detailed analysis of the market drivers, segmentation, growth opportunities, trends and competitive landscape to understand the current and future market scenarios. How big is the encryption software market? The…

View On WordPress
0 notes
Text
United States encryption software market size reached USD 3.5 Billion in 2024. Looking forward, IMARC Group expects the market to reach USD 10.1 Billion by 2033, exhibiting a growth rate (CAGR) of 12.7% during 2025-2033. The growing cyber threats and data breaches in the United States, rising remote work and bring your own device (BYOD) policies, increasing need to comply with government regulations, and the growing volume of digital transactions represent some of the key factors driving the market.
#United States Encryption Software Market#United States Encryption Software Market size#United States Encryption Software Market share#United States Encryption Software Market forecast#United States Encryption Software Market 2024
0 notes
Text
An adversarial iMessage client for Android
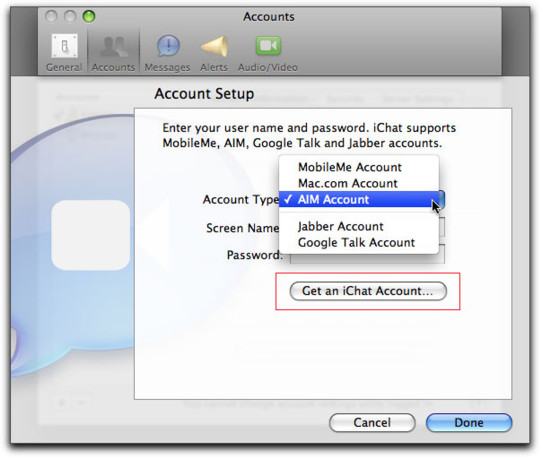
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
Proton, the secure-minded email and productivity suite, is becoming a nonprofit foundation, but it doesn't want you to think about it in the way you think about other notable privacy and web foundations.
"We believe that if we want to bring about large-scale change, Proton can’t be billionaire-subsidized (like Signal), Google-subsidized (like Mozilla), government-subsidized (like Tor), donation-subsidized (like Wikipedia), or even speculation-subsidized (like the plethora of crypto “foundations”)," Proton CEO Andy Yen wrote in a blog post announcing the transition. "Instead, Proton must have a profitable and healthy business at its core."
The announcement comes exactly 10 years to the day after a crowdfunding campaign saw 10,000 people give more than $500,000 to launch Proton Mail. To make it happen, Yen, along with co-founder Jason Stockman and first employee Dingchao Lu, endowed the Proton Foundation with some of their shares. The Proton Foundation is now the primary shareholder of the business Proton, which Yen states will "make irrevocable our wish that Proton remains in perpetuity an organization that places people ahead of profits." Among other members of the Foundation's board is Sir Tim Berners-Lee, inventor of HTML, HTTP, and almost everything else about the web.
Of particular importance is where Proton and the Proton Foundation are located: Switzerland. As Yen noted, Swiss foundations do not have shareholders and are instead obligated to act "in accordance with the purpose for which they were established." While the for-profit entity Proton AG can still do things like offer stock options to recruits and even raise its own capital on private markets, the Foundation serves as a backstop against moving too far from Proton's founding mission, Yen wrote.
There’s a lot more Proton to protect these days
Proton has gone from a single email offering to a wide range of services, many of which specifically target the often invasive offerings of other companies (read, mostly: Google). You can now take your cloud files, passwords, and calendars over to Proton and use its VPN services, most of which offer end-to-end encryption and open source core software hosted in Switzerland, with its notably strong privacy laws.
None of that guarantees that a Swiss court can't compel some forms of compliance from Proton, as happened in 2021. But compared to most service providers, Proton offers a far clearer and easier-to-grasp privacy model: It can't see your stuff, and it only makes money from subscriptions.
#proton#protonmail#surveillance capitalism#privacy#social media#artificial intelligence#big tech#technology#google#nonprofit
22 notes
·
View notes
Text
5 Best Restaurant Management Software Reviews for 2025
Are you looking for the best restaurant management software?

In this tech-driven era, utilizing feature-rich restaurant management software is crucial for small businesses to stay ahead of their competitors. To keep pace with the constant technical advancements and ever-evolving customer preferences, most restaurant owners rely on restaurant management tools that not only streamline their restaurant operations but also help improve sales.
Managing day-to-day restaurant operations can be challenging. However, for many years, restaurants have been struggling with manual logs, lots of spreadsheets, and ordinary point-of-sale systems to keep things in order. This results in missed orders, poor task management, and lots of stress.
If you, too, are dealing with the same issue, this article will be very helpful for you, as we have shared 5 of the best restaurant management software reviews here to help you pick the right one for your business and modernize your restaurant management system.
What is restaurant management software?

Restaurant management software or a restaurant POS system is designed to automate all restaurant operations, order & delivery tracking, generating invoices, storing customer details, offering discounts, food menu management, restaurant reviews, and more. In simple words, it creates the foundation of your restaurant business. A good restaurant POS system will drive your sales and give you a lot of opportunities to grow your restaurant business.
If you still do not use a restaurant management system, let us tell you why your business needs it.
Why do you need restaurant management software?

Best Restaurant Management Software automates major restaurant operations, offering you a stress-free business management experience and happy customers.
Other benefits of using restaurant management software include:
Order management: Starting from accepting orders to processing them and tracking delivery, the entire process is automated with a restaurant management system.
Table booking management: You can easily manage table reservations, table availability, seating arrangements, and more to optimize space and increase revenue.
Handling customer data: When customers place orders with your POS system, it automatically saves crucial information that you can utilize to offer personalized experiences to them.
Improves user experience: With online ordering, payment security, a loyalty program, and systematic task management, your customers feel satisfied.
Data-driven marketing decision: A POS system offers useful data and reports on your sales and evaluates your overall restaurant performance to help you make data-driven decisions.
Menu management: Add a striking menu and easily add, edit, or delete food items from it.
Cost optimization: Proper menu management, loyalty program, and simplified order management help optimize costs.
Reduced errors: Tech-driven order, delivery, and customer data management reduce the chances of error and provide you with an accurate picture of your restaurant’s performance.
These are the basic advantages of using a restaurant management system. When you choose the best for you, your business will experience more benefits.
Selecting the best restaurant management software: features to look for

Best restaurant management software features
When you search for the best restaurant management software for your restaurant, you will find an overwhelming number of options that are sure to confuse you. So, how to pick the best one? The answer lies in the features of a restaurant POS system.
Find out the must-have features for a restaurant management system:
Security
Your restaurant POS system regularly deals with confidential customer information like their payment details, contact information, etc, and ensuring their security should be a priority to build trust and credibility. Ensure that the restaurant software you choose has end-to-end encryption and a secure payment system.
Speed
One of the most important factors of the best restaurant management software is its speed. It must be able to work efficiently during rush hours when the order flow usually doubles. If the system slows down or crashes, then it could pose a serious challenge to your operational efficiency and business reputation. While scrutinizing event management software, do not forget to check its speed and its ability to handle pressure.
Scalability
Scalability is extremely important for a restaurant management solution to stay aligned with the changes that take place. Whether it is about managing restaurants from different locations or adding new features, your software must be able to deliver that without affecting the performance.
Mobile Accessibility
Make sure that the restaurant POS system you choose offers you the flexibility to manage your restaurant operation through your mobile phone. Opening a desktop for minor works can be a hassle. Tracking orders, deliveries, customer data, table registration, and more through phones is extremely beneficial and convenient.
Table booking management
Table reservation is a crucial part of a restaurant, and that is why, while filtering restaurant management software, look for a restaurant management system that offers a table booking system.
Order and delivery management
A restaurant POS system is incomplete without an online ordering and delivery management system. Search for a restaurant menu software that provides you with 100% admin control over the orders and delivery management.
Technical support
Technical support ensures that everything runs smoothly. Opt for a restaurant management system that offers technical support when required. This is important because if you face any technical issues, they can solve them promptly.
Reporting and analytics
Reports and analytics help you measure the performance of your restaurant. It throws light on sales, employee performance, and customer preferences to help you make major decisions for growth.
5 Best Restaurant Management Software Reviews
We have picked the 5 best restaurant management software after evaluating them on the basis of the above-mentioned points and reviewed each of them to help you understand them better and choose the most suitable one for your business.
1. FoodMato

FoodMato is one of the best restaurant management software programs that you can rely on for your small, medium, or established restaurant business. It is an all-in-one restaurant POS system that covers everything from online ordering and delivery to menu management, marketing, and an easy-to-use mobile app to manage the entire system at your fingertips.
Key features of FoodMato
Restaurant website creation and branding.
Seamless order management and delivery tracking.
Stress-free restaurant reservation system.
Creation of food menu and its management.
Freedom to handle multiple restaurant operations from a centralized platform.
Reports and analytics on restaurant sales, orders, and overall performance.
Google Maps integration to display restaurant locations.
Loyalty program for customer retention.
Restaurant marketing with social media community management.
Restaurant review system to increase credibility.
Sincere and timely support.
Third-party integrations.
Restaurant gallery to showcase your restaurant’s ambiance.
The best part about FoodMato is that it covers all essential restaurant management features, and it can be customized as per individual business requirements.
Pros of FoodMato
Offers a comprehensive solution
Affordable pricing.
Prompt response from the support team.
Offers full control to the admin.
A wideegtecccg3grvfcrv array of features.
Amazing reviews.
The FoodMato team works according to unique business needs.
No technical knowledge is required.
Cons of FoodMato
Not many reviews are available as it is a newly launched software.
2. OpenTable

The second in our list is the OpenTable software, which is known for its excellent restaurant reservation system. The POS system offers a vast array of services to restaurants, including table reservations, table management, restaurant booking, inventory management, and more.
Key features of OpenTable
Organize private dining events with enhanced visibility.
Restaurant management with a mobile app.
Restaurant reservation system with tags, booking, and waiting list facilities.
Offers guest data security.
The online waiting list is for guests to avoid congestion at the restaurant front door.
Reports and analytics.
A restaurant direct messaging system to allow customers to directly interact with restaurant representatives before stepping in.
Pros of OpenTable
Vast features.
Superior table booking system.
CRM integrations for better guest management.
Positive reviews.
Cons of OpenTable
Users often complain about data synchronization issues.
The system may slow down during peak hours.
It may feel overwhelming for users due to excessive features.
3. Toast

Toast is another restaurant POS system that we have picked for our readers. It is easy to use, and it can be a good choice for those who are not tech-savvy. It offers multiple useful features that cover major restaurant operations like online ordering, payroll management, and more.
Key features of Toast
Simplified online ordering.
Convenient to use.
Various tools for employee scheduling and payroll management.
Insightful reports and analytics.
Easy integrations with third-party online ordering platforms.
Customizable.
Pros of Toast
User-friendly.
Packed with multiple features.
Integration with third-party delivery platforms for smooth restaurant management.
Cons of Toast
The absence of offline functionality makes the system completely unusable.
Difficulty in customizing the system.
4. PetPooja

PetPooja is a well-known restaurant POS software developed to streamline restaurant operations. It offers a wide range of restaurant management features, including online ordering, task management, easy attendee tracking, and task and payroll management.
Key features of PetPooja
User-friendly interface.
Online ordering and billing system.
Task management tool to improve productivity
Digital invoice generation system.
Real-time restaurant reports on sales, online orders, inventory consumption, staff management, and more.
Pros of PetPooja
Fast and reliable.
Easy to use.
Multiple useful features.
Offers real-time updates on Inventory, sales, and customer preferences.
Cons of PetPooja
The process of integrating the software with other platforms is complicated.
5. Restroworks

Last but not least, Restroworks works as a complete restaurant management platform with powerful inventory management features. It is mostly suitable for medium-sized restaurants. It easily integrates with payment processing tools to offer a smooth transaction experience to restaurant owners and customers.
Key features of Restroworks:
Helps manage kitchen inventories to decrease food prices.
Offers real-time updates on food stock to reduce food wastage.
Provides a clear picture of the upcoming day’s food consumption based on historical data.
Helps create recipes with proper ingredients and monitor costs to determine the price of a food item.
Pros of Restroworks
Customizable.
Offers a comprehensive restaurant management solution.
Easy inventory tracking.
Automatic sync with accounting tools.
Cons of Restroworks
It can be a bit complicated for small businesses.
Customer support response time is slow
Inventory tracking requires manual efforts.
What is the best restaurant management software?
Selecting the best restaurant management software from the above-mentioned tools completely depends on your restaurant’s requirements. We recommend FoodMato because it offers an A-to-Z solution to your restaurant business with a strong IT support team.
Wrapping up
Let us take a quick look at the 5 best restaurant management software that we have reviewed for you: FoodMato, Openable, Toast, PetPooja, and Restroworks. We have picked them on the basis of their features, reviews, support, user-friendliness, and their ability to streamline restaurant operations.
#online ordering system#pos system#restaurant management#food delivery#onlineorderingsystemfor restaurant#Restaurant Management Software
2 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
J.4.7 What about the communications revolution?
Another important factor working in favour of anarchists is the existence of a sophisticated global communications network and a high degree of education and literacy among the populations of the core industrialised nations. Together these two developments make possible nearly instantaneous sharing and public dissemination of information by members of various progressive and radical movements all over the globe — a phenomenon that tends to reduce the effectiveness of repression by central authorities. The electronic-media and personal-computer revolutions also make it more difficult for elitist groups to maintain their previous monopolies of knowledge. Copy-left software and text, user-generated and shared content, file-sharing, all show that information, and its users, reaches its full potential when it is free. In short, the advent of the Information Age is potentially extremely subversive.
The very existence of the Internet provides anarchists with a powerful argument that decentralised structures can function effectively in a highly complex world. For the net has no centralised headquarters and is not subject to regulation by any centralised regulatory agency, yet it still manages to function effectively. Moreover, the net is also an effective way of anarchists and other radicals to communicate their ideas to others, share knowledge, work on common projects and co-ordinate activities and social struggle. By using the Internet, radicals can make their ideas accessible to people who otherwise would not come across anarchist ideas. In addition, and far more important than anarchists putting their ideas across, the fact is that the net allows everyone with access to express themselves freely, to communicate with others and get access (by visiting webpages and joining mailing lists and newsgroups) and give access (by creating webpages and joining in with on-line arguments) to new ideas and viewpoints. This is very anarchistic as it allows people to express themselves and start to consider new ideas, ideas which may change how they think and act.
Obviously we are aware that the vast majority of people in the world do not have access to telephones, never mind computers, but computer access is increasing in many countries, making it available, via work, libraries, schools, universities, and so on to more and more working class people.
Of course there is no denying that the implications of improved communications and information technology are ambiguous, implying Big Brother as well the ability of progressive and radical movements to organise. However, the point is only that the information revolution in combination with the other social developments could (but will not necessarily) contribute to a social paradigm shift. Obviously such a shift will not happen automatically. Indeed, it will not happen at all unless there is strong resistance to governmental and corporate attempts to limit public access to information, technology (e.g. encryption programs), censor peoples’ communications and use of electronic media and track them on-line.
This use of the Internet and computers to spread the anarchist message is ironic. The rapid improvement in price-performance ratios of computers, software, and other technology today is often used to validate the faith in free market capitalism but that requires a monumental failure of historical memory as not just the Internet but also the computer represents a spectacular success of public investment. As late as the 1970s and early 1980s, according to Kenneth Flamm’s Creating the Computer, the federal government was paying for 40 percent of all computer-related research and 60 to 75 percent of basic research. Even such modern-seeming gadgets as video terminals, the light pen, the drawing tablet, and the mouse evolved from Pentagon-sponsored research in the 1950s, 1960s and 1970s. Even software was not without state influence, with databases having their root in US Air Force and Atomic Energy Commission projects, artificial intelligence in military contracts back in the 1950s and airline reservation systems in 1950s air-defence systems. More than half of IBM’s Research and Development budget came from government contracts in the 1950s and 1960s.
The motivation was national security, but the result has been the creation of comparative advantage in information technology for the United States that private firms have happily exploited and extended. When the returns were uncertain and difficult to capture, private firms were unwilling to invest, and government played the decisive role. And not for want of trying, for key players in the military first tried to convince businesses and investment bankers that a new and potentially profitable business opportunity was presenting itself, but they did not succeed and it was only when the market expanded and the returns were more definite that the government receded. While the risks and development costs were socialised, the gains were privatised. All of which make claims that the market would have done it anyway highly unlikely.
Looking beyond state aid to the computer industry we discover a “do-it-yourself” (and so self-managed) culture which was essential to its development. The first personal computer, for example, was invented by amateurs who wanted their own cheap machines. The existence of a “gift” economy among these amateurs and hobbyists was a necessary precondition for the development of PCs. Without this free sharing of information and knowledge, the development of computers would have been hindered and so socialistic relations between developers and within the working environment created the necessary conditions for the computer revolution. If this community had been marked by commercial relations, the chances are the necessary breakthroughs and knowledge would have remained monopolised by a few companies or individuals, so hindering the industry as a whole.
Encouragingly, this socialistic “gift economy” is still at the heart of computer/software development and the Internet. For example, the Free Software Foundation has developed the General Public Licence (GPL). GPL, also know as
“copyleft”, uses copyright to ensure that software remains free. Copyleft ensures that a piece of software is made available to everyone to use and modify as they desire. The only restriction is that any used or modified copyleft material must remain under copyleft, ensuring that others have the same rights as you did when you used the original code. It creates a commons which anyone may add to, but no one may subtract from. Placing software under GPL means that every contributor is assured that she, and all other uses, will be able to run, modify and redistribute the code indefinitely. Unlike commercial software, copyleft code ensures an increasing knowledge base from which individuals can draw from and, equally as important, contribute to. In this way everyone benefits as code can be improved by everyone, unlike commercial code.
Many will think that this essentially anarchistic system would be a failure. In fact, code developed in this way is far more reliable and sturdy than commercial software. Linux, for example, is a far superior operating system than DOS precisely because it draws on the collective experience, skill and knowledge of thousands of developers. Apache, the most popular web-server, is another freeware product and is acknowledged as the best available. The same can be said of other key web-technologies (most obviously PHP) and projects (Wikipedia springs to mind, although that project while based on co-operative and free activity is owned by a few people who have ultimate control). While non-anarchists may be surprised, anarchists are not. Mutual aid and co-operation are beneficial in the evolution of life, why not in the evolution of software? For anarchists, this “gift economy” at the heart of the communications revolution is an important development. It shows both the superiority of common development as well as the walls built against innovation and decent products by property systems. We hope that such an economy will spread increasingly into the “real” world.
Another example of co-operation being aided by new technologies is Netwar. This refers to the use of the Internet by autonomous groups and social movements to co-ordinate action to influence and change society and fight government or business policy. This use of the Internet has steadily grown over the years, with a Rand corporation researcher, David Ronfeldt, arguing that this has become an important and powerful force (Rand is, and has been since its creation in 1948, a private appendage of the military industrial complex). In other words, activism and activists’ power and influence has been fuelled by the advent of the information revolution. Through computer and communication networks, especially via the Internet, grassroots campaigns have flourished, and the most importantly, government elites have taken notice.
Ronfeldt specialises in issues of national security, especially in the areas of Latin American and the impact of new informational technologies. Ronfeldt and another colleague coined the term
“netwar” in a Rand document entitled “Cyberwar is Coming!”. Ronfeldt’s work became a source of discussion on the Internet in mid-March 1995 when Pacific News Service correspondent Joel Simon wrote an article about Ronfeldt’s opinions on the influence of netwars on the political situation in Mexico after the Zapatista uprising. According to Simon, Ronfeldt holds that the work of social activists on the Internet has had a large influence — helping to co-ordinate the large demonstrations in Mexico City in support of the Zapatistas and the proliferation of EZLN communiqués across the world via computer networks. These actions, Ronfeldt argues, have allowed a network of groups that oppose the Mexican Government to muster an international response, often within hours of actions by it. In effect, this has forced the Mexican government to maintain the facade of negotiations with the EZLN and has on many occasions, actually stopped the army from just going in to Chiapas and brutally massacring the Zapatistas.
Given that Ronfeldt was an employee of the Rand Corporation his comments indicate that the U.S. government and its military and intelligence wings are very interested in what the Left is doing on the Internet. Given that they would not be interested in this if it were not effective, we can say that this use of the “Information Super-Highway” is a positive example of the use of technology in ways un-planned of by those who initially developed it (let us not forget that the Internet was originally funded by the U.S. government and military). While the internet is being hyped as the next big marketplace, it is being subverted by activists — an example of anarchistic trends within society worrying the powers that be.
A good example of this powerful tool is the incredible speed and range at which information travels the Internet about events concerning Mexico and the Zapatistas. When Alexander Cockburn wrote an article exposing a Chase Manhattan Bank memo about Chiapas and the Zapatistas in Counterpunch, only a small number of people read it because it is only a newsletter with a limited readership. The memo, written by Riordan Roett, argued that “the [Mexican] government will need to eliminate the Zapatistas to demonstrate their effective control of the national territory and of security policy”. In other words, if the Mexican government wants investment from Chase, it would have to crush the Zapatistas. This information was relatively ineffective when just confined to print but when it was uploaded to the Internet, it suddenly reached a very large number of people. These people in turn co-ordinated protests against the U.S and Mexican governments and especially Chase Manhattan. Chase was eventually forced to attempt to distance itself from the Roett memo that it commissioned. Since then net-activism has grown.
Ronfeldt’s research and opinion should be flattering for the Left. He is basically arguing that the efforts of activists on computers not only has been very effective (or at least has that potential), but more importantly, argues that the only way to counter this work is to follow the lead of social activists. Activists should understand the important implications of Ronfeldt’s work: government elites are not only watching these actions (big surprise) but are also attempting to work against them. Thus Netwars and copyleft are good examples of anarchistic trends within society, using communications technology as a means of co-ordinating activity across the world in a libertarian fashion for libertarian goals.
#community building#practical anarchy#practical anarchism#anarchist society#practical#faq#anarchy faq#revolution#anarchism#daily posts#communism#anti capitalist#anti capitalism#late stage capitalism#organization#grassroots#grass roots#anarchists#libraries#leftism#social issues#economy#economics#climate change#climate crisis#climate#ecology#anarchy works#environmentalism#environment
18 notes
·
View notes
Text
The UK government has demanded that Apple creates a backdoor in its encrypted cloud service, in a confrontation that challenges the US tech firm’s avowed stance on protecting user privacy.
The Washington Post reported on Friday that the Home Office had issued a “technical capability notice” under the Investigatory Powers Act (IPA), which requires companies to assist law enforcement in providing evidence.
The demand, issued last month, relates to Apple’s Advanced Data Protection (ADP) service, which heavily encrypts personal data uploaded and stored remotely in Apple’s cloud servers, according to the Post, which said this was a “blanket” request that applied to any Apple user worldwide. The ADP service uses end-to-end encryption, a form of security that means only the account holder can decrypt the files and no one else can – including Apple.
Apple declined to comment. However, in a submission to parliament last year it flagged its concerns about the IPA, saying it provided the government with “authority to issue secret orders requiring providers to break encryption by inserting backdoors into their software products”.
Apple touts privacy as one of its “core values” and describes it as a “fundamental human right”.
The Apple document refers to the ADP feature, claiming that “reporters and technical experts across the globe” welcomed it as an “invaluable protection” for private data.
The submission also indicates that Apple would refuse to cooperate with a request, saying the company would “never build a backdoor” and would rather withdraw “critical safety features” from the UK market.
However, the submission also points out that the IPA allows the UK government to impose requirements on companies based in other countries that apply to users globally.
Alan Woodward, a professor of cybersecurity at Surrey University, said the UK government had “lit the blue touch paper on a truly enormous fight in the never-ending saga of the encryption debate”.
He added: “I don’t see how this is to be resolved, as Apple has made such a big point of privacy for users. If they accede to this technical notice their reputation will be in tatters. They’re bound to challenge it.”
End-to-end encryption has become a battleground between successive UK governments and tech companies, with ministers arguing that the technology prevents law enforcement agencies from tackling criminals, including child abusers.
Companies are also barred from revealing whether they have received a technology capability notice under the IPA. The Washington Post reported that by the time Apple made its submission in March last year the US-based company had been informed that a notice might be served on it. The newspaper said the Biden administration had been tracking the matter since the UK government told Apple it might demand access, and Apple had said it would refuse.
A Home Office spokesperson said: “We do not comment on operational matters, including, for example, confirming or denying the existence of any such notices.”
The submission related to amendments to the IPA passed last year under Rishi Sunak’s government and included giving ministers power to clear in advance any product changes that could alter the UK government’s ability to access users’ data.
One expert warned that the multinational nature of the order could lead to a clash with the EU, which has an agreement with the UK allowing the free flow of personal data between the EU and UK – such as a company in Europe using a datacentre in the UK. The agreement comes up for review this year.
“This may provide a backdoor for access to European citizen data which could go against our ability to retain the rights to share personal data without restriction between the UK and Europe,” said Ross McKenzie, a data protection partner at the UK law firm Addleshaw Goddard.
2 notes
·
View notes
Text
Small Business Must-Haves: The Best Tools for internal communication software
Team members can no longer rely on one-on-one conversations with coworkers in today's modernising workplace, and sending important files or sharing every little detail via email—which can take a lot of time because of its protocol—to accomplish these tasks. Selecting internal communication softwares can be the finest choice because it enhances time management, team productivity, and collaboration in addition to communication.
Little and microbusiness owners turn to social chat applications since they don't meet their needs and they believe work chat platforms are too expensive. Some were forced to use them due to an unforeseen pandemic disease. However, because of their subscription programs, some of the best products are able to provide excellent services at a low cost.
The following are some of the most effective communication tools for your business.
1. Troop Messenger

Troop Messenger is considered the best internal communication software, which can be used as a business messaging tool, work chat tool, and instant messaging tool for both office and remote work.
Troop Messenger shocked the market in a short amount of time, and many companies chose it after discovering its innovative capabilities, which are likely to be included in future updates of major applications or may not be present in apps available today.
Troop Messenger's thorough investigation led to the addition of new functions to the instrument, which is inexpensive and appropriate for use in any field. The military and NASA might exchange secret information using this safe and secure team texting tool.
Features
Remote screen sharing and controlling
Join Now, allows the user to join the missed group audio or video call while ongoing
Burnout
Live Location Tracking
Jointly Code
Advanced Search Filters
Forkout
2. Microsoft Teams

Office 365 plans can be accessed by users of Microsoft Teams, a proprietary internal communication software created by Microsoft and included in the Microsoft 365 product line. If you utilise more Microsoft apps at work, this is the right collaboration tool.
Features
Meeting Recordings
Screen sharing
All Microsoft 365 apps and services may be accessed with a single sign-on.
Cloud-based solution
100+ Participants capacity
3. Slack

Slack Technologies, an American software business that created the exclusive team communication platform Slack, was purchased by Salesforce in 2021. Because of its price, startups might be interested in it, and it could be a helpful tool for communication at work. It is a better alternative to email services because of its corporate key management, two-factor authentication, data encryption, and other features.
Features
Files sharing
Voice and Video calls
File sharing
Apps & Integrations
Slack Connect
4. Flock

Flock is a well-integrated enterprise communication tool with Twitter, Google Calendar, Trello, Jira, Google Drive, GitHub, and so on, which helps your team save time from switching between multiple tools.
Features
Well Integrated
Automate workflows
Polls
Notes
To-dos
Reminders
5. Twist

Twist was created to withstand the unique demands of contemporary work by a remote workforce consisting of more than 70 individuals across more than 25 nations. This internal communication software allows users to follow the thread conversations of users who are at least one month old. For distant workers, this team communication solution is perfect. To make user cooperation simple, Jira Software, Google Drive, Pipedream, Google Calendar, and other tools are integrated.
Features
Organized conversations
Private Conversations
Thread Conversations
Well Integrated
Project Management
6. Ryver

With emails, group chat, task management, and audio & video calls, Ryver allows the users to handle team communication in ONE APP. Ryver provides a discount to non-profit organizations and educational institutions, making it a useful team communication tool for them.
Features
Well Integrated
Task Management
Advanced Team Management
Custom Invite Links
Unlimited file sharing
Conclusion
We think the information on our blog will assist you in selecting the most appropriate technologies for internal communication software. Prior to selecting a chat tool, assess the demands of your business and carry out market research on the features, functionality, user or customer reviews, and other elements of the tool. As a result, you are not required to replace the tool even if it does not satisfy your needs.
#internal communication software#team communication#business communication tools#online communication apps#troop messenger#trending#tumblr#communication#viral
2 notes
·
View notes
Text
A Comprehensive Guide to Blockchain-as-a-Service (BaaS) for Businesses
In today's digital landscape, a blockchain app development company plays a crucial role in transforming industries with decentralisation, immutability, and transparency. However, building and managing a private blockchain network can be complex and costly, which deters many businesses. Blockchain-as-a-Service (BaaS) simplifies this by allowing businesses to leverage blockchain without the challenges of infrastructure development.
This comprehensive blog covers the hurdles businesses face when adopting blockchain, how BaaS can bridge these gaps, and why it is a game-changer for various sectors.
I. Challenges for Businesses in Blockchain Adoption
Despite the undeniable potential of blockchain technology, businesses face several significant challenges when contemplating its adoption:
Limited Internal Expertise: Developing and maintaining a private blockchain network requires a skilled team with deep blockchain knowledge, which is often lacking in many organisations.
High Cost: The infrastructure investment and ongoing maintenance fees associated with blockchain can strain budgets, especially for small and medium-sized businesses (SMBs).
Integration Complexities: Integrating a blockchain network with existing enterprise systems can be challenging, requiring seamless data flow and compatibility between the blockchain system and legacy infrastructure.
II. Understanding BaaS and Its Operational Fundamentals
Blockchain-as-a-Service (BaaS) simplifies the development and deployment of blockchain applications by providing a cloud-based platform managed by third-party providers. The BaaS market, valued at $1.5 billion in 2024, is projected to grow to $3.37 billion by 2029, reflecting a robust 17.5% CAGR.
Key Components of BaaS
Cloud-Based Infrastructure: Ready-to-use blockchain infrastructure hosted in the cloud, eliminating the need for businesses to set up and maintain their networks.
Development Tools and APIs: Access to a suite of tools and APIs to create and deploy blockchain applications quickly.
Platform Support: Compatibility with various blockchain protocols such as Ethereum, Hyperledger Fabric, and Corda, offering flexibility to businesses.
Managed Service Model: Providers handle tasks like network maintenance, security updates, and scalability.
Pay-as-you-go Pricing Model: Reduces upfront investment and operational costs associated with blockchain software development.
III. Business Benefits of Blockchain as a Service
Adopting BaaS offers numerous advantages, including:
Enhanced Scalability: Businesses can easily scale their blockchain network as their needs grow.
Increased Efficiency: Eliminates intermediaries and streamlines transactions, improving productivity.
Enhanced Transparency: Tamper-proof records of transactions foster trust and improve auditability.
Reduced Costs: The pay-as-you-go model eliminates large upfront investments.
Improved Security: Built on secure cloud infrastructure with robust encryption protocols.
Enhanced Customer Engagement: Facilitates secure and transparent interactions with customers, building trust and loyalty.
IV. Industry-wise Key Use Cases of Blockchain as a Service
BaaS is transforming business operations across various industries:
Finance: Streamlines trade finance, secures cross-border payments, and enhances KYC and AML compliance.
Supply Chain Management: Improves transparency and traceability of goods, automates logistics processes, and reduces counterfeiting risks.
Healthcare: Facilitates secure sharing of patient data and tracks the provenance of pharmaceuticals.
Government: Enhances transparency with secure citizen identity management and verifiable voting systems.
V. Region-wise Adoption of BaaS
The BaaS market is experiencing rapid growth worldwide:
North America: Leading with over 35% of global revenues, driven by early adoption.
Europe: Countries like Germany, the UK, and France are at the forefront.
Asia-Pacific: China, India, Japan, and South Korea are key contributors.
Rest of the World: Growing adoption in South & Central America, the Middle East, and Africa.
VI. Why Choose a Prominent BaaS Provider?
Opting for a blockchain app development company that offers BaaS can significantly impact the success of your blockchain initiatives:
Specialised Expertise: Providers possess in-depth knowledge and experience in blockchain technology.
Cost Efficiency: Eliminates the need for in-house infrastructure investment and maintenance.
Time Savings: Accelerates the development process and reduces time-to-market.
Scalability and Flexibility: Offers scalable solutions that can adapt to business growth.
Risk Mitigation: Providers handle security, maintenance, and updates.
Conclusion
By adopting Blockchain-as-a-Service (BaaS), businesses can simplify blockchain integration and focus on innovation without the complexities of managing infrastructure. Systango, a leading blockchain app development company, offers tailored BaaS solutions that help businesses leverage blockchain technology for enhanced efficiency, scalability, and security. As one of the top , Systango also excels in integrating AI solutions to drive business growth and efficiency.
Original Source - https://systango.medium.com/a-comprehensive-guide-to-blockchain-as-a-service-baas-for-businesses-5c621cf0fd2f
2 notes
·
View notes
Text
The Best Screen Recorders with Audio for Your PC
Recording your screen along with audio can be a game-changer for creating tutorials, recording gameplay, or conducting online classes. Having the right screen recorder that captures both video and audio seamlessly is essential for producing high-quality content. Let’s explore some of the best options available, highlighting ScreenRec for its efficiency and ease of use, along with other noteworthy tools.

What Makes a Great Screen Recorder with Audio?
When selecting a screen recorder with audio capabilities, consider the following:
Ease of Use: The tool should be intuitive and user-friendly.
Video and Audio Quality: High-definition video and clear audio without lag or desynchronization.
Editing Features: Tools for basic to advanced editing of your recordings.
Sharing Options: Easy and secure sharing capabilities.
Cost: Evaluate the balance between features offered and affordability.
Top Screen Recorders with Audio for PC
ScreenRec: ScreenRec stands out for its simplicity and powerful features. It allows you to capture high-quality video and audio effortlessly. One of its best features is instant sharing through a secure cloud link, which is perfect for quick communication and collaboration. ScreenRec is free, with unlimited recording time once you create a free account, making it a budget-friendly choice. Its user-friendly interface ensures that even non-tech-savvy users can start recording with ease. Additionally, ScreenRec encrypts all recordings, ensuring that your data remains secure.
OBS Studio: Open Broadcaster Software (OBS) Studio is a free and open-source screen recording tool known for its extensive features and customizability. It's particularly popular among gamers and live streamers for its ability to handle multiple sources and live stream directly to platforms like Twitch and YouTube. OBS Studio supports high-quality video and audio recording but comes with a steeper learning curve due to its vast array of features.
Camtasia: Camtasia is a premium screen recording tool that offers a comprehensive suite of editing features, such as annotations, transitions, and effects. It's perfect for creating polished, professional videos. Camtasia supports both screen and audio recording, making it a great choice for producing detailed tutorials and marketing videos. Despite its higher price tag, its advanced capabilities make it a worthwhile investment for those who need detailed editing options.
Bandicam: Bandicam is favored for its ability to record high-quality video, particularly for gameplay. It supports high FPS recording and includes features like real-time drawing and webcam overlay. Bandicam also supports audio recording, capturing both system sound and microphone input. It’s ideal for users who prioritize video quality and detailed recording options.
ShareX: ShareX is a free, open-source screen recorder that offers various capture methods, including full screen, window, and region. It also provides a range of editing and sharing tools. ShareX supports audio recording, though setting it up might require some additional steps compared to more user-friendly tools like ScreenRec. ShareX is suitable for users who appreciate customization and don’t mind a bit of a learning curve.
Why ScreenRec Stands Out
ScreenRec excels in providing a seamless recording experience with minimal setup. Its user-friendly interface ensures that even those who aren't tech-savvy can start recording with ease. The instant sharing feature, combined with secure cloud storage, ensures that your recordings are always accessible and easy to distribute. For users needing a reliable, no-cost solution that doesn’t compromise on features, ScreenRec is an excellent choice.
Final Thoughts
Choosing the right screen recorder with audio capabilities depends on your specific needs. If you’re looking for a simple, effective, and free tool, ScreenRec is highly recommended. For more advanced features and professional editing, Camtasia and Bandicam are excellent options. OBS Studio and ShareX provide powerful features for free, though they come with a learning curve. Regardless of your choice, having a reliable screen recorder will enhance your productivity and communication.
5 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
Web Search Engine) Links
Hidden Wiki Links – Now you are here then you already know about deep web links / The Hidden Wiki / Dark web links. But before sharing large amount of .onion directory I want to share some very good deep web links which always help you, because all these are deep web search engine links by the help of these search engine you can find any latest working deep web marketplace, hidden wiki or deep web sites list.
Dark Web Marketplace
Darknet markets is a solution for all type products because these type marketplace gives security to both party means seller or buyer, here you can use escrow service which make your payment mode more secure and clear. These type darknet markets places having some big number of listed categories and each category having more than thousands of unique products.
So simple, Today If you are planning to buy anything on deep web/the hidden wiki then these markets can provide you all type products buying or selling opportunity and here you also can get more than one alternatives into single category.
Mostly these deep web links having Drugs, Weapon, Digital products, Fraud, Services, Guide and Tutorials categories.
Bellow I am giving you some very popular deep web Links (dark web links), which you can try but before using these hidden wiki links, you need to register yourself on these darknet markets deep web link.
Note: If you are seller then these dark web marketplace links will proving milestone for you. where you can sell your products. and you can easily get targeted users or can achieve your goals within very short time span.
Note: I am not recommending you to visit these deep web sites (dark web links), I only added these deep web sites/onion sites here for education purpose or freedom information. If you visit these deep web sites then this is total on your risk, but I am recommending you here before visiting these deep web sites make sure focus on your privacy Security.
Recommended: For better security use NordVPN Onion Over Server + Tor Browser. ( Always run both software before access hidden Internet).
http://pwoah7foa6au2pul.onion – Marketplace – Alphabay is most popular and trusted deep web market. If you are truly looking something trusted on deep web then Alphabay is one of the best market, And this marketplace also has all major categories items like as fraud, drugs, chemicals, Guide & Tutorials, Digital Products, Services, and much more. According to current status, This marketplace has more than 3 Lakh listed items, and Just now support two type crypto currency which is Monero and Bitcoins.
Note: Before Buy any product here always check seller profile and available feedback and reviews.
http://lchudifyeqm4ldjj.onion/ – Marketplace – Dream Market : Second largest and most trusted dark web market, also you can say alternative of alphaby market, This marketplace place have drugs and digital products, and both these category have more than 75000+ listed items which is huge. If you are looking another great platform then dream market can provide you right items.
http://wallstyizjhkrvmj.onion/ – Marketplace – WallStreet Market – Another deep web markets which have more than 500+ listed items and each item are well categorized. According to category, You can get products related to drugs, counterfeits, jewelry & gold, services, Software & malware, security & hosting and much more.. and listing growing day to day. Marketplace support PGP and data encrypt by strong algorithm and also support German language. WallStreet has scam free status and multisig support.
http://udujmgcoqw6o4cp4.onion – Deep Web Market – UnderGround, one of the best and reliable deep web market with the possibility to pay in two times. Markets have more than thousands listed items and items related to Prepaid cards, PayPal account, Diploma, Passport, ID Cards, Driver License, Phone, Computer, Tablets, Game Console, Hacker, Weapons, Professional Killer, Humen Organs, Medicines and so on.
Note: This deep web links support JavaScript, If you want to access all function then you need to disable your javascript. But for security reasons, this is not good choice.
http://valhallaxmn3fydu.onion – Marketplace – Valhalla: This deep web marketplace is also very popular into deep web world and mostly people prefer this hidden wiki marketplace url for buying drugs, gadgets, hire services and lot many more things.
http://hansamkt2rr6nfg3.onion/ – Marketplace – Hansa is another famous deep web marketplace, which having more than 15K+ listed products. which is huge, and here you can buy all type products related to drugs, weapons, services, tutorials, services, electronics. It is one of most popular the dark web links.
http://zocaloczzecchoaa.onion – Marketplace – Zocalo Marketplace: Same as other marketplaces this .onion directory links also having good amount of listing product.
http://acropol4ti6ytzeh.onion – Marketplace – Acropolis forum also a good darknet markets, and community forum for sell and buy anything which you want, and also can find your questions answer in this dark web link.
http://tochka3evlj3sxdv.onion – Marketplace – Tochka Free Market: Tochka is also good darknet market where you can find mostly all type product related to education, hacking, drugs, weapon, services and software.
http://cryptomktgxdn2zd.onion – Marketplace – Crypto Market: Are you looking some other deep web links marketplace alternative then check out Crypto Market, Here you can participate in crypto market forum.
Warning: Before browsing the Deep web links/the dark web links, always run your NordVPN Onion Over VPN Server with Tor Browser. Since Tor Browser doesn’t provide your complete anonymity and privacy. You are completely safe only if you use NordVPN software.
http://kbhpodhnfxl3clb4.onion/ – not Evil (Tor Search Engine) for finding list of deep web sites, and one can easily find relevant information about the deep web/the hidden wiki which s/he want to get..
http://hss3uro2hsxfogfq.onion/ – not Evil search engine direct visit deep web links.
Note: Now Tor search engine has been moved on new name, now this popular search engine also known as not Evil, in the current date not Evil having more than 12477146 .onion links database.
Grams Search Engine and Associated Deep Web Services Links:
Grams is newly launched deep web search engine, this search engine getting good amount of popularity with in very short time and these days thousands of people use Grams for deep web access. You can access Grams by using below dark web link.
http://grams7enufi7jmdl.onion/ – Grams Search Darknet Markets and more.
Grams is not a single platform, but it’s like a Google, After couple month after grams launching date, Grams introduced some other product like Helix, Helix Light, Infodesk or Flow.
All three having unique features. If you want to access these three Grams sub product, then you can access by the help of Grams deep web link, or you can also go by the help of bellow given direct dark web links.
Note: Helix takes charge 2.5% every transaction.
Helix Tor Directory Link: http://grams7enufi7jmdl.onion/helix/light
InfoDesk: If you want to find any Vender, products or any specific marketplace tor link then this place can help you because here you can find some great marketplace which is trusted, and mostly people use in daily life.You can access InfoDesk using below deep web link.
InfoDesk Hidden Wiki Link: http://grams7enufi7jmdl.onion/infodesk
Flow: Now time for Flow, this is another popular deep web product which is also introduced by Grams, Hope you like Flow features because some person like this platform for Flow redirect feature.
According to this, if you want to access any darknet markets and you didn’t remember tor directory link then you can access these type hidden wiki url or deep web links easily.. GramsFlow makes this type complicated process more easy.
Now you only need to remember your marketplace name like Agora, Wiki, OutLaw, nuke or any other and you can access by help of Flow.
For Example: if you want to access the hidden wiki then you need to type in your Tor Browser gramsflow.com/wiki, then holla your link redirect on actual tor hidden directory.
For using awesome feature of Flow, visit below give deep web link.
Flow Tor Hidden Directory Link: http://grams7enufi7jmdl.onion/infodesk
http://skunkrdunsylcfqd.onion/sites.html – The Intel Wiki – This .onion site has the good number of trusted deep web links, which every day visited by most of the deep web users. But sometimes when I try to access this deep web link and I saw this dark web link is down. One more thing the Intel wiki also a forum which having great number of threads, which having useful information about the deep web and trusted deep web links/dark web links.
http://auutwvpt25zfyncd.onion/ – Tor Links Directory – OnionDir having more than 1200+ listed dark web sites, one better thing is here you can see on top how many dark net sites are live and how many deep web sites not and All .onions links are well categorized according to categories. For Example: If you are looking hacking or drugs related marketplace deep web links then you need to click on required category and visit any deep web sites which you like.
Forums & Community Deep Web Links(For Questions and Answers Conversation)
If you are eager to learn the darknet hidden wiki forum, also want to deep discuss on this sensitive topic and looking best deep web forums and the hidden wiki links and if you also looking how to access the deep web latest news and updates.
Deepwebsiteslinks is a best source where you can find all most popular deep web links, the hidden wiki news and darknet markets updates day to day and people visit here every day and participate into available threads.
Here I am giving you some popular deep web forums and darknet community links/deep web links, which are sharing the deep web/the hidden wiki related news and current updates everyday.
Privacy Tips: Always use NordVPN Onion Over Server with Tor browser while you accessing deep web sites. if you are thinking you are using TOR and you are safe. Let me clear for your privacy security. TOR doesn’t provide you full security. To access deep web with best anonymity and privacy, NordVPN and TOR both are must used software.
http://rrcc5xgpiuf3xe6p.onion/ – Forum/Community – IntelExchange is my favorite the dark web community because here you can find information thread and also can ask your question, I like this because here you can find mostly pre-discussed thread which having lot of meaningful information like best dark web search engines, dark web browser, most trusted the hidden wiki url.
http://parazite.nn.fi/roguesci/ – Forum – The Explosive and Weapon Forum, This hidden wiki link has some very good weapons and Explosive-related Documents and treads.
http://zw3crggtadila2sg.onion/imageboard/ – Forum – TorChan is darknet forum where you ask and participates into running chat thread, but If you are first time visitors then you don’t know how to visit this website then simple type given URL and after press enter you will get one popup on screen then you need to put given Username and Password into both field, ByDefault Username or Password is torchan2, torchan2. this is most popular the hidden wiki forum, where every day more than thousands or visitors visit and share something very interesting.
http://kpdqsslspgfwfjpw.onion/ – Forum/Community – A Chan, I think this deep web links having Russian language stuff, I can’t tell you about properly this site, and what type stuff this deep web sites have.
http://rhe4faeuhjs4ldc5.onion/ – Forum/Community – Do you have any query related to white hate hacking or black hat techniques, and you want to know some secret hacking tips then this hidden wiki community will proving helpful stuff and gernals. having more than 20+ active threads.
http://turkiyex6fkt46ra.onion/forum/ – Forum/Community/Non-English – Are you from Turkey, and looking your region related deep web forum then check out this hidden wiki forum link.
http://anonywebix6vi6gz.onion/ – Forum/Community – This is newly launched dark net forum. This hidden wiki link also will proving helpful for you, if you want to discuss about the deepweb, darknet markets or any others.
http://arcadian4nxs3pjr.onion/ – Forum/Community – ArcadiaNode is a dark net forum, Note: this deep web sites is not in the English language, that’s why I don’t have more idea about this forum.
http://5dhf54nxiuuv6jvs.onion/ – Forum/Community – AXAHis Community: This is another deepweb (hidden wiki) community where you can share your questions and knowledge, also can interact with related people.
Note: For access first time need registration.
http://p22i3mcdceionj36.onion/index.php – Forum/Community – XenForo: This deep web marketplace is a forum, but here you can buy Pfizer and GG249 Xanax products.
http://anonymzn3twqpxq5.onion/ – Forum/Community – Do you love DBA task and want to discuss on DBA related topics then check out this forum, hope this will proving helpful for you.
http://z2hjm7uhwisw5jm5.onion/ – Forum/Community – WallStreet: If you having any query about Tor or Looking some hidden web related answer then you can try on this deep web link.
http://support26v5pvkg6.onion/ – Forum/Community – Pedo Support Community: This Deep web forum is having more than 10K+ threads, like links, personal support, pedo literature, child love support, etc.
http://suprbayoubiexnmp.onion/ – Forum/Community – SuperBay: This community is having very good amount of thread and everyday lot’s of visitors use these threads, If you have some problem, then you can find relevant thread, and can resolve your problem.
https://blue.thevendingmachine.pw/index.php – Community/Forum – TheVendingMachine: This is very popular deep web community, every day more than 1000+ visitors visit this onion site, and share information. Here most popular thread is Torrent, Movies, General Discussion, TV shows, documentaries, etc.
http://npdaaf3s3f2xrmlo.onion/ – Tor Community – TwitterClon is just like twitter sites here you can share everything which you want into form of tweet, hope you also enjoy this sites, but mostly time I saw this site down.
NordVPN 2
http://ji7nj2et2kyrxpsh.onion/ – Forum – Dark Web Forum: I don’t know what you can find here because this is non-english forum but as per my guess, hope you can discuss about dark web and also can participate into active threads.
http://krainkasnuawwxmu.onion/ – Forum – Dark Web Community: This is the next Russian forum, where you can discuss about dark web community. If you have any question and want to know the right answers, then you can sign up on this forum and can find some easy solutions.
http://fbcy5ylyoeqzqzcr.onion/ – Forum – Moneybook: Another dark web forum where you can discuss about all popular topics related to dark web like as onion links, dark web markets review, PayPal accounts, music movie sites and much more, hope here you can find some good thread for you.
http://realpissxny3hgyl.onion/ – Forum/Porn – RealPiss Voyeur Community real uncensored female pee spycams: community for real girl piss videos and pictures, If you interested into such type content then you can try to visit realpiss site.
http://zzq7gpluliw6iq7l.onion/threadlist.php? – Forum – The Green Machine: Another deep web forum which provides discussion threads, do you have any questions and want to know the right answers then The green machine dark web links can provide you right information. But If you want to participate into available threads then you need to registered yourself on this deep web forum.
http://rutorzzmfflzllk5.onion/ – Forum/Russian – RuTor: Are you looking Russian forum, If yes then RuTor forum can provides you some great questions answer, but this forum not have more active thread, when I visited this deep web sites then I saw, website have only limited thread and also not have users engagement.
http://bm26rwk32m7u7rec.onion/ – Forum – The Majestic Garden: This is another deep web forum, which provides free forum SMF software solution, If you have any questions about this software then you can visit this deep web sites.
http://vrimutd6so6a565x.onion/ – Forum/Community – The Dark Lair: Forum for anonymous messaging, like as Twitter. Here you can share your status globally; Everyone can saw your status on this website. If they visit dark Lier, but you can’t post status on this site. Because you are not the registered member of Dark Lier, that’s the main reason. First your need to register on this website. Site also offers thread service and some good deep web links also.
http://answerstedhctbek.onion/ – Forum/Community – Hidden Answers: I think you already know about the yahoo questions and answers, This site offer same service just like yahoo questions and answers, If you have any questions and want to get your questions answers then you can try this deep web links.
http://saefjmgij57x5gky.onion/ – Forum/Community – TorStack – Q & A Community – Same Yahoo Questions and answer deep web sites, here you also can find right answers for your questions anonymously.
http://dnmavengeradt4vo.onion/ – Forum/Community – DNM Avengers: Another deep web forum site which provides communicating portal for deep web users anonymously. forum already have more than 100+ active threads. If you have any questions and want to know right answer anonymously. You can participate on available relevant thread. Also, you can share your skills in these running threads.
http://twittorxsun563wg.onion/ – Community/Social – Twitter Clone – This is microblogging site on the deep web, here you can share anything with all site readers anonymously. For status publishing you don’t need to signup here.
http://i2vzg7f44bj4l3r7.onion/ – Community – The Alliance – Another deep web social community sites, where users can share his though with all alliance community member or personally with your friends. One more thing, site also offers bookmarks service, by which you can tag any links on the Bookmarks category. which every site readers can read and visit anonymously.
http://www.smplace.com/forum/ – Forum/Community – S&M Place BDSM forum – Great Adult porn community for girls and boys, have all type threads where you can share adult porn videos and pictures, and also you can upload your videos and pictures collections. Forum have more than 70000+ active members.
http://rekt5jo5nuuadbie.onion/hiddenchan/ – Forum/Community – HideenChan – If you don’t know about the hidden chan. HiddenChan is just like as another community forum, here you can participate into current active threads. But hiddenchan is very engaging community here you can see every illegal activity related thread and also you can watch available videos and pictures which is uploaded by various current members.
http://start.jungswtfwgjwile2.onion/ – Forum/Community – Guys.WTF is primarily a community for people who love and love guys and / or feel sexually attracted by them. However, every interested person is expressly welcome. Here you want to help and support each other.
http://bfvfq7hjcdoinzo4.onion/ – Forum/Community – Darknet Erotic Forum – This deep web forum offer threads related to hot, geil, horny, porn, pervers and etc. If you want to discuss about these topics then you can participate on available threads. But without registration you can’t participate in this community.
http://rfwtogljhrrzxyrl.onion/ – Forum/Community – Lolita City – Another deep web forum, which offers hq legal stuff. Today when I visited this site, here only I found 2 threads. Hope here you can get your required information.
Email/Messaging/Chat related Deep Web Links
Warning: Always use NordVPN Tor Over Server + Tor Browser for complete security. Your privacy is not safe if you are accessing deep web links without VPN.
Same ad normal traditional in
#dark web#ethicalhacking#scammer#coding#contact a hacker#scammers#social media hackers#ethical hacker#deep web#hacker
5 notes
·
View notes
Text
Going Over the Cloud: An Investigation into the Architecture of Cloud Solutions

Because the cloud offers unprecedented levels of size, flexibility, and accessibility, it has fundamentally altered the way we approach technology in the present digital era. As more and more businesses shift their infrastructure to the cloud, it is imperative that they understand the architecture of cloud solutions. Join me as we examine the core concepts, industry best practices, and transformative impacts on modern enterprises.
The Basics of Cloud Solution Architecture A well-designed architecture that balances dependability, performance, and cost-effectiveness is the foundation of any successful cloud deployment. Cloud solutions' architecture is made up of many different components, including networking, computing, storage, security, and scalability. By creating solutions that are tailored to the requirements of each workload, organizations can optimize return on investment and fully utilize the cloud.
Flexibility and Resilience in Design The flexibility of cloud computing to grow resources on-demand to meet varying workloads and guarantee flawless performance is one of its distinguishing characteristics. Cloud solution architecture create resilient systems that can endure failures and sustain uptime by utilizing fault-tolerant design principles, load balancing, and auto-scaling. Workloads can be distributed over several availability zones and regions to help enterprises increase fault tolerance and lessen the effect of outages.
Protection of Data in the Cloud and Security by Design
As data thefts become more common, security becomes a top priority in cloud solution architecture. Architects include identity management, access controls, encryption, and monitoring into their designs using a multi-layered security strategy. By adhering to industry standards and best practices, such as the shared responsibility model and compliance frameworks, organizations may safeguard confidential information and guarantee regulatory compliance in the cloud.
Using Professional Services to Increase Productivity Cloud service providers offer a variety of managed services that streamline operations and reduce the stress of maintaining infrastructure. These services allow firms to focus on innovation instead of infrastructure maintenance. They include server less computing, machine learning, databases, and analytics. With cloud-native applications, architects may reduce costs, increase time-to-market, and optimize performance by selecting the right mix of managed services.
Cost control and ongoing optimization Cost optimization is essential since inefficient resource use can quickly drive up costs. Architects monitor resource utilization, analyze cost trends, and identify opportunities for optimization with the aid of tools and techniques. Businesses can cut waste and maximize their cloud computing expenses by using spot instances, reserved instances, and cost allocation tags.
Acknowledging Automation and DevOps Important elements of cloud solution design include automation and DevOps concepts, which enable companies to develop software more rapidly, reliably, and efficiently. Architects create pipelines for continuous integration, delivery, and deployment, which expedites the software development process and allows for rapid iterations. By provisioning and managing infrastructure programmatically with Infrastructure as Code (IaC) and Configuration Management systems, teams may minimize human labor and guarantee consistency across environments.
Multiple-cloud and hybrid strategies In an increasingly interconnected world, many firms employ hybrid and multi-cloud strategies to leverage the benefits of many cloud providers in addition to on-premises infrastructure. Cloud solution architects have to design systems that seamlessly integrate several environments while ensuring interoperability, data consistency, and regulatory compliance. By implementing hybrid connection options like VPNs, Direct Connect, or Express Route, organizations may develop hybrid cloud deployments that include the best aspects of both public and on-premises data centers. Analytics and Data Management Modern organizations depend on data because it fosters innovation and informed decision-making. Thanks to the advanced data management and analytics solutions developed by cloud solution architects, organizations can effortlessly gather, store, process, and analyze large volumes of data. By leveraging cloud-native data services like data warehouses, data lakes, and real-time analytics platforms, organizations may gain a competitive advantage in their respective industries and extract valuable insights. Architects implement data governance frameworks and privacy-enhancing technologies to ensure adherence to data protection rules and safeguard sensitive information.
Computing Without a Server Server less computing, a significant shift in cloud architecture, frees organizations to focus on creating applications rather than maintaining infrastructure or managing servers. Cloud solution architects develop server less programs using event-driven architectures and Function-as-a-Service (FaaS) platforms such as AWS Lambda, Azure Functions, or Google Cloud Functions. By abstracting away the underlying infrastructure, server less architectures offer unparalleled scalability, cost-efficiency, and agility, empowering companies to innovate swiftly and change course without incurring additional costs.
Conclusion As we come to the close of our investigation into cloud solution architecture, it is evident that the cloud is more than just a platform for technology; it is a force for innovation and transformation. By embracing the ideas of scalability, resilience, and security, and efficiency, organizations can take advantage of new opportunities, drive business expansion, and preserve their competitive edge in today's rapidly evolving digital market. Thus, to ensure success, remember to leverage cloud solution architecture when developing a new cloud-native application or initiating a cloud migration.
1 note
·
View note
Text
Navigating the Hidden Corners of the Internet

The Dark Web has long been shrouded in mystery and intrigue, often associated with illicit activities and clandestine operations. However, it's important to understand that not all aspects of the Dark Web are illegal or harmful. In this article, we will explore the concept of Dark Web links, shedding light on what they are, how they work, and how to navigate them responsibly.
For more information- Dark Web Links
Dark Web links are the gateways to websites, forums, and services hosted on the Dark Web. These links are not indexed by traditional search engines like Google, making them difficult to find through conventional means. Instead, users typically access Dark Web links through specialized software, most notably Tor (The Onion Router), which ensures anonymity and privacy.
1. Onion URLs: Dark Web links often use a onion domain, indicating that they are hosted on the Tor network. These URLs are designed to be complex and nonsensical, making them difficult to guess or remember. For example, a typical Dark Web link might look like example website onion.
2. Accessing the Dark Web: To access Dark Web links, users need to download and install the Tor browser, which routes internet traffic through a series of volunteer-operated servers to maintain anonymity. Once connected to the Tor network, users can enter onion URLs into the browser to access Dark Web sites.
Responsible Navigation of Dark Web Links
While the Dark Web offers some legitimate and ethical content, it is essential to approach it with caution and responsibility. Here are some guidelines for navigating Dark Web links:
1. Legal and Ethical Use: Ensure that your activities on the Dark Web are legal and ethical. Engaging in illegal activities or seeking out harmful content is not only unethical but can also lead to serious legal consequences.
2. Privacy and Security: Be aware that your online activities on the Dark Web are not entirely immune to surveillance or security breaches. While Tor provides a degree of anonymity, it is not foolproof. Take steps to protect your privacy and use encryption tools where necessary.
3. Browsing Safely: Stick to reputable websites and forums on the Dark Web that align with your interests and goals. Avoid clicking on suspicious links or downloading files from untrustworthy sources. Be cautious of phishing attempts and scams.
4. Verify Information: When using the Dark Web for research or information gathering, verify the accuracy of the information you find. Due to the anonymous nature of the Dark Web, misinformation can proliferate.
5. Avoid Illegal Markets: Steer clear of illegal marketplaces and services that offer drugs, stolen data, weapons, or other illicit goods. Engaging with such platforms can have severe legal consequences.
6. Maintain Anonymity: Remember that while Tor provides a degree of anonymity, it's not infallible. Avoid sharing personal information or engaging in behavior that could compromise your identity.
7. Report Illegal Activity: If you come across illegal activities or content on the Dark Web, consider reporting it to the appropriate authorities or organizations dedicated to monitoring and combating illegal online activities.
Conclusion
Dark Web links offer access to a hidden world of websites and services that are not indexed by traditional search engines. While the Dark Web is often associated with illegal activities, it's essential to recognize that it can also be used for legitimate and ethical purposes, such as protecting privacy, fostering free speech, and conducting research.
However, responsible navigation of Dark Web links is paramount. Engaging in illegal activities, downloading malicious content, or seeking out harmful materials not only jeopardizes your own safety but also contributes to the negative reputation of the Dark Web. As with any part of the internet, the key lies in responsible use. Approach Dark Web links with caution, adhere to ethical standards, and prioritize your own online security and privacy. By doing so, you can explore the hidden corners of the internet without falling into the traps of illegal activities or dangerous scams, contributing to a safer and more responsible online environment
3 notes
·
View notes
Text
The Power of Document Management Software: Boosting Efficiency and Security
In today’s fast-paced business world, information is power. But what happens when that information is buried under piles of paper, scattered across various drives, or difficult to track? The answer is a significant drain on productivity, increased security risks, and a whole lot of frustration. This is where Document Management Software (DMS) comes to the rescue, revolutionizing how businesses handle their crucial information.
What is Document Management Software?
At its core, Document Management Software is a system designed to manage and organize documents and digital files. Think of it as a central hub for all your business’s documents — from invoices and contracts to HR records and marketing materials. It allows you to store, track, retrieve, and share documents electronically, eliminating the need for physical filing cabinets and manual processes.
Introducing Smart DM — Your Intelligent Document Management Solution
We are thrilled to introduce Smart DM, a robust and intuitive Document Management Software from Smart Factory India, specifically designed to empower your business with streamlined document workflows and enhanced security. Smart DM is more than just a storage solution; it’s a comprehensive platform built to transform your document handling.
Features That Set Smart DM Apart
Smart DM is packed with features that cater to the diverse needs of modern businesses:
Centralized Repository: Store all your documents in one secure, easily accessible location. No more searching through disparate folders or physical archives.
Version Control: Keep track of every revision with automatic versioning. Always ensure you’re working on the latest document and easily revert to previous versions if needed.
Advanced Search & Retrieval: Find any document in seconds with powerful search capabilities, including full-text search and metadata filtering.
Workflow Automation: Automate routine document processes like approvals, reviews, and distribution, reducing manual effort and errors.
Robust Security & Access Control: Protect sensitive information with granular access permissions, encryption, and audit trails. Control who sees what and track every document interaction.
Collaboration Tools: Facilitate seamless collaboration on documents with features like co-authoring, annotations, and shared workspaces.
Integration Capabilities: Easily integrate Smart DM with your existing business applications for a unified operational environment.
Mobile Accessibility: Access your documents anytime, anywhere, from any device, empowering your team with flexibility and remote work capabilities.
Key Benefits of Smart DM Document Management Software
Implementing Smart DM can bring a multitude of tangible benefits to your organization:
Boosted Efficiency & Productivity
Enhanced Security & Compliance
Cost Savings
Improved Collaboration & Communication:
Better Decision-Making
Conclusion
In an era where digital transformation is paramount, a robust Document Management Software like Smart DM is no longer a luxury but a necessity. By investing in Smart DM, your business can unlock unparalleled efficiency, bolster security, foster collaboration, and ultimately, gain a significant competitive edge.

0 notes