#Facebook management software
Text
Tens of thousands of people have been fired in the tech sector in the last six months alone. With the economy the way it is, and with people who are already unable to get a job, I wonder how an extra 20,000+ jobseekers are going to have any luck finding work.
#i just want to point out that this isn't just automation. it's different for every company but a lot of it comes down to profiteering imo#the video game industry made disgusting amounts of money during the pandemic. best three years of sales in history#but that momentum was never going to keep up forever. even when the momentum was at full swing people were getting laid off#Activision-Blizzard laid off over a hundred people just before christmas while bobby kotick got a $250 million bonus#thst might have even been before the pandemic#but you're seeing it with microsoft and ubisoft. wouldn't surprise me if sony and nintendo were following suit in a less public manner#microsoft - arguably the biggest tech conglomerate in the world (next to tencent) - laid off 10 thousand workers alone#i live in a town with just over 10 thousand people. in my entire fucking town. in my perspective that's more or less the world around me#all of those people - jobless#facebook - didn't like 7k people just get fired? that's hot on the heels of john carmack leaving too#john carmack is probably one of the top 100 people in the tech industry. his tech improvements helped aging PC hardware keep up for years#DOOM might be a meme but it ran that well because id software under john carmack revolutionised rendering techniques and scrolling#and stuff like that. john carmack has been at the forefront of graphical technology and game development for 30+ years#that's resulted in a couple duds like RAGE. he was also all-in on voxel technology before he moved into VR#all of that was context for this: john carmack left meta (who bought oculus) and lambasted the company for poor management on the way out#saying that he'd never seen such unnecessary and wanton expenditure in his career. meta were throwing their money at things thay don't work#here's john carmack trying to lay the groundwork of a successful game for meta's metaverse. here's meta chasing superfluous buzzwords#meta spent almost $14 BILLION on buzzwords and marketing at the behest of the actual tech. and then they FIRED 7000 PEOPLE!!!!!!#they had a HAIL MARY working on their game - because metaverse IS A GAME - and they prioritised SELLING THE PRODUCT BEFORE BUILDING IT#IT COST THEM $14 BILLION + THEIR HAIL MARY - AND THEN THEY FIRED THOUSANDS OF PEOPLE!!!!!!#Ubisoft and Activision-Blizzard have been facing mass resignations after years of abusive and toxic workplaces#and on top of that they're firing people too. google stadia just went under. it wouldn't surprise me if 2k and rockstar were firing people#I don't know how many other unemployed people there are in america - hundreds of thousands? but 20k more is even worse for everyone#keep in mind that even with a $14 billion loss - meta still makes billions. Microsoft is in no financial danger#tech is more lucrative now than ever. i genuinely believe that these cuts are to keep record profits at record heights#because the pandemic boom is ending and their ALREADY OBSCENELY LUCRATIVE revenue flows are going back to normal#so 20k+ tech workers are losing their jobs to keep $80 billion instead of $79 billion. all of those people - jobless#that's 20 thousand people with individual lives and families and expenses. lost their jobs in the last six months#that example i gave - $80 billion instead of $79 billion. that's not revenue. that's profit.#all of those people out of work due to incompetence at best and rank orofiteering at worst. their salaries and benefits come under revenue
4 notes
·
View notes
Text
Digital Marketing Facebook & Instagram ads Google Ads FB Pixel Conversion API Expert
✅ Google Analytics & Google Tag Manager Audit
I will do an in-depth audit of your existing GA & GTM accounts. This will be helpful in figuring out the issues that are blocking the data quality. This will be a detailed report including all the issues and data quality score of your analytics.
✅ Google Analytics & Google Analytics 4 Implementation
I will help you implement Google Analytics/ Google Analytics 4 & Google Tag Manager on your website. This will include both basic installation to advanced setup based on your website & business requirements.
✅ Google Analytics Enhanced E-commerce Tracking
If you have an ecommerce website, I can help you with enhanced ecommerce tracking so you will have a complete picture of the purchase behaviour on your website. If you have a custom built website, I will have to work with your developer to add the dataLayer codes.
✅ Facebook Pixel & Conversion API Installation
I will troubleshoot issues with your Facebook pixel installation and ensure that the pixel is installed properly. I can also help you with conversion api setup, ensuring the pixel is also installed on server. This will include tracking all the conversions with the highest possible quality match score. Below are my complete fb pixel services:
1- Fixing fb pixel issues & setting up from scratch
2- Verify your domain
3- Add aggregated events
4- connect pixel with ad account
5- setting up conversion. tracking & dynamic re-marketing
6- Fb catalog setup
7- Fb pixel training
✅ Google Ads Conversion Tracking & Dynamic Remarketing
I can help you with Google Ads conversion tracking & dynamic remarketing. I will ensure the conversion is correctly installed & remarketing tags are in place across your website.
Contact me -> www.mobinulkhan.com
Why Me?
5+ years of experience
helped 80+ clients
Google Analytics certified
100% client satisfaction
Contact me - and I am sure I will achieve excellent results for your project.
#facebookadvertising #facebookmarketing #googleads #youtubeads #musica #band #produce #pinterest #linkedin #fashion #googletagmanager #googleads #googleanalytics #digitalmarketing #team #business #google #data #business #googleanalytics4 #shopifytracking #shopifypixel #GTM #GA4 #FB #WooCommerce
#facebook ads#facebook pixel#facebook messenger#google ads#google analytics#google tag manager#google tracking#software#google trends
2 notes
·
View notes
Text
#AI chatbot#AI ethics specialist#AI jobs#Ai Jobsbuster#AI landscape 2024#AI product manager#AI research scientist#AI software products#AI tools#Artificial Intelligence (AI)#BERT#Clarifai#computational graph#Computer Vision API#Content creation#Cortana#creativity#CRM platform#cybersecurity analyst#data scientist#deep learning#deep-learning framework#DeepMind#designing#distributed computing#efficiency#emotional analysis#Facebook AI research lab#game-playing#Google Duplex
0 notes
Text
Elevate your marketing game with innovative techlogic softwares. Stay ahead of the curve in the ever-evolving digital landscape. 🚀
Call Us - 9821599301
#social media#social media marketing#digital marketing#online marketing#seo services#marketing tips#seo#webdevelopment#social media au#social media management#social media services#social media posts#content#social#social networks#influencer marketing#facebook#techlogic softwares#smm services
0 notes
Text
The Future of IT Jobs: Skills and Roles in Demand
The future of IT jobs is continually evolving, driven by technological advancements and changing business needs. Here are some skills and roles that are expected to be in demand in the IT industry:
Data Science and Analytics:
With the increasing importance of data-driven decision-making, professionals skilled in data analysis, machine learning, and data visualization will be highly sought after.
Artificial Intelligence and Machine Learning:
As AI becomes more prevalent in various industries, the demand for experts in machine learning algorithms, natural language processing, and AI strategy will continue to grow.
Cybersecurity:
As cyber threats become more sophisticated, organizations will need skilled professionals in cybersecurity to protect their systems, networks, and data from attacks.
Cloud Computing:
The adoption of cloud technology is on the rise, leading to a demand for professionals with expertise in cloud architecture, migration, and management.
Full Stack Development:
Full stack developers who can work on both the front-end and back-end of applications will be in high demand due to their ability to develop end-to-end solutions.
DevOps and Automation:
Organizations are increasingly embracing DevOps practices to enhance collaboration and efficiency. Professionals with skills in continuous integration/continuous delivery (CI/CD) pipelines and automation tools will be in demand.
Internet of Things (IoT):
The proliferation of connected devices opens up opportunities for professionals who can design, develop, and manage IoT systems and platforms.
Creating intuitive and engaging user experiences is crucial for businesses. UX designers who can optimize the usability and accessibility of digital products will be in demand.
Project Management:
IT project managers who can lead teams, manage budgets, and ensure successful project delivery will remain essential in the industry.
Data Privacy and Compliance:
With the increasing focus on data privacy regulations, professionals knowledgeable in data protection, privacy laws, and compliance frameworks will be highly sought after.
Business Analysis:
IT professionals who can bridge the gap between technology and business needs by analyzing requirements, identifying solutions, and managing stakeholders will be in demand.
Blockchain:
Professionals with expertise in blockchain technology, smart contracts, and decentralized applications will find opportunities in industries such as finance, supply chain, and healthcare.
Robotic Process Automation (RPA):
As businesses look to automate repetitive tasks, professionals skilled in RPA tools and process optimization will be valuable assets.
Quantum Computing:
While still in its early stages, the field of quantum computing is gaining traction. Professionals with knowledge of quantum algorithms and programming languages will be in demand as this technology advances.
Data Engineering:
With the growing volume of data, organizations need data engineers who can design, build, and maintain robust data infrastructure and pipelines.
It's important to note that the IT industry is dynamic, and new roles and skills will continue to emerge as technology advances. Continuous learning and staying updated with the latest trends and technologies will be crucial for IT professionals to thrive in the future job market.
#elicitdigital#developers#webdevelopment#webdesign#facebook#elicit#developer#quantum computing#Data Engineering#Robotic Process Automation#Blockchain#digitalmarketingtips#Business Analysis#Project Management#uidesign#uxuidesign#Cloud Computing#software#automation#cloud services#information technology#innovation
0 notes
Text
#course#blogger#facebook#earning#facebook watchtime#technology#website#wordpress#development#management#certification#software#noida
0 notes
Text
#app development agency#digital marketing agency#digital marketing agency Los angeles#web design agency Los Angeles#software development Los Angeles#software development agency Los Angeles#web development agency Los Angeles#app development Los Angeles#mobile app development Los Angeles#mobile app development agency Los Angeles#app development agency Los Angeles#ui ux designer Los Angeles#landing page design Los Angeles#landing page development Los Angeles#google advertising Los Angeles#google ads agency Los Angeles#google ads management Los Angeles#google advertising agency Los Angeles#facebook advertising#facebook marketing#facebook advertising agency#facebook marketing agency Los Angeles
0 notes
Text

We provide best web hosting services includng all types of apps development, widgets, social media integration, website creation etc.
Web Hosting Services Lucknow
We also do custom design, develop, test and deploy Android apps of your choice.
Our team is well versed with Android SDK and API with complete knowledge of the Android platform that is adaptable to larger, VGA, 2D graphics library, 3D graphics library based on OpenGL ES 1.0 specifications, and traditional smartphone layouts. We do customized application development ranging from asset tracking to advertising, gaming to messaging and voicing, GPS to multimedia applications.
Address: 538A/456/94 Shivpuram, Triveni Nagar 3rd, Lucknow Uttar Pradesh 226020
Phone: +91-8383004899 | Email: [email protected] | Website | watch video
#Digital Marketing Services#Software Development Services#Website Designing and Development Services#Custom App Development#Mobile App Development#Web Hosting Services#IT Infrastructure Management Services#advertising services#facebook ads#google ads
0 notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image:
Oatsy (modified)
https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0
https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
228 notes
·
View notes
Text
For more than three weeks, Gaza has faced an almost total internet blackout. The cables, cell towers, and infrastructure needed to keep people online have been damaged or destroyed as Israel launched thousands of missiles in response to Hamas attacking Israel and taking hundreds of hostages on October 7. Then, this evening, amid reports of heavy bombing in Gaza, some of the last remaining connectivity disappeared.
In the days after October 7, people living in Gaza have been unable to communicate with family or friends, leaving them unsure whether loved ones are alive. Finding reliable news about events has become harder. Rescue workers have not been able to connect to mobile networks, hampering recovery efforts. And information flowing out of Gaza, showing the conditions on the ground, has been stymied.
As the Israel Defense Forces said it was expanding its ground operations in Gaza this evening, internet connectivity fell further. Paltel, the main Palestinian communications company, has been able to keep some of its services online during Israel’s military response to Hamas’ attack. However, at around 7:30 pm local time today, internet monitoring firm NetBlocks confirmed a “collapse” in connectivity in the Gaza Strip, mostly impacting remaining Paltel services.
“We regret to announce a complete interruption of all communications and internet services within the Gaza Strip,” Paltel posted in a post on its Facebook page. The company claimed that bombing had “caused the destruction of all remaining international routes.” An identical post was made on the Facebook page of Jawwal, the region’s biggest mobile provider, which is owned by Paltel. Separately, Palestinian Red Crescent, a humanitarian organization, said on X (formerly Twitter) that it had lost contact with its operation room in Gaza and is “deeply concerned” about its ability to keep caring for people, with landline, cell, and internet connections being inaccessible.
“This is a terrifying development,” Marwa Fatafta, a policy manager focusing on the Middle East and North Africa at the digital rights group Access Now, tells WIRED. “Taking Gaza completely off the grid while launching an unprecedented bombardment campaign only means something atrocious is about to happen.”
A WIRED review of internet analysis data, social media posts, and Palestinian internet and telecom company statements shows how connectivity in the Gaza Strip drastically plummeted after October 7 and how some buildings linked to internet firms have been damaged in attacks. Photos and videos show sites that house various internet and telecom firms have been damaged, while reports from official organizations, including the United Nations, describe the impact of people being offline.
Damaged Lines
Around the world, the internet and telecoms networks that typically give web users access to international video calls, online banking, and endless social media are a complicated, sprawling mix of hardware and software. Networks of networks, combining data centers, servers, switches, and reams of cables, communicate with each other and send data globally. Local internet access is provided by a mix of companies with no clear public documentation of their infrastructure, making it difficult to monitor the overall status of the system as a whole. In Gaza, experts say, internet connectivity is heavily reliant on Israeli infrastructure to connect to the outside world.
Amid Israel’s intense bombing of Gaza, physical systems powering the internet have been destroyed. On October 10, the United Nations’ Office for the Coordination of Humanitarian Affairs (OCHA), which oversees emergency responses, said air strikes “targeted several telecommunication installations” and had destroyed two of the three main lines of communications going into Gaza.
Prior to tonight’s blackout, internet connectivity remained but was “extremely slow and limited,” Access Now’s Fatafta says. People she has spoken to from Gaza say it could take a day to upload and send a few photos. “They have to send like 20 messages in order for one to go through,” Fatafta says. “They are desperately—especially for Gazans that live outside—trying to get through to their families.”
“Every time I try to call someone from family or friends, I try to call between seven to 10 times,” says Ramadan Al-Agha, a digital marketer who lives in Khan Yunis, a city in the south of the Gaza Strip. “The call may be cut off two or three times,” he told WIRED in a WhatsApp message before the latest outages. “We cannot access news quickly and clearly.” People in the region have simultaneously faced electricity blackouts, dwindling supplies of fuel used to power generators, and a lack of clean water, food, and medical supplies. “It is a humanitarian disaster,” Al-Agha says.
Connectivity in Gaza started to drop not long after Israel responded to the October 7 Hamas attack. Rene Wilhelm, a senior R&D engineer at the nonprofit internet infrastructure organization Ripe Network Coordination Center, says based on an analysis of internet routing data it collects that 11 Palestinian networks, which may operate both in the West Bank and Gaza Strip, began to experience disruption after October 7. Eight of the networks were no longer visible to the global internet as of October 23, Wilhelm says. Ahead of this evening’s blackout, there was around 15 percent of normal connectivity, according to data from Georgia Tech’s Internet Outage Detection and Analysis project. That dropped to around 7 percent as reports of the blackout circulated.
One office belonging to Paltel in the Al Rimal neighborhood of Gaza City has been destroyed in the attacks, photos and videos show. Floors have been destroyed and windows blown away in the multistory building, and piles of rubble surround the entrances. (It is unclear what equipment the building housed or how many floors Paltel occupied.) Another internet provider, AlfaNet, is listed as being based in the Al-Watan Tower. The company posted to its Facebook page on October 8 that the tower had been destroyed and its services have stopped, with other online posts also saying the tower has been destroyed.
Multiple Palestinian internet and telecoms firms have said their services have been disrupted during the war, mostly posting to social media. Internet provider Fusion initially said its engineers were trying to repair its infrastructure, although it has since said this is not continuing. “The network was destroyed, and the cables and poles were badly damaged by the bombing,” it wrote on Facebook. JetNet said there had been a “sudden disruption” to access points. SpeedClick posted that the situation was out of its control. And HiNet posted that it has “no more to offer to ensure” people could stay online following “the attacks and destruction our internet servers have suffered.”
Across Paltel’s network on October 19, according to an update shared by the Office for the Coordination of Humanitarian Affairs, 83 percent of fixed line users had been disconnected, with 53 percent of sites providing fixed line connections also being offline. Half of the company’s fiber optic internet lines in Gaza weren’t operational, the update says. The connectivity disappeared this evening, according to Paltel’s Facebook post, which says there has been a “complete interruption” of all its services. Paltel, AlfaNet, Fusion, and SpeedClick could not be reached or did not respond to requests for comment.
Lost Connections
In recent years, governments and authoritarian regimes have frequently turned to shutting down the internet for millions of people in attempts to suppress protests and curtail free speech. Targeting the communications networks is common during conflicts. During Russia's war in Ukraine, its forces have decimated communications networks, tried to take over the internet, and set up new mobile companies to control information flows. When Hamas first attacked Israel on October 7, it used drones to bomb communications equipment at surveillance posts along the borders of the Gaza Strip.
Monika Gehner, the head of corporate communications at the International Telecommunication Union, says the body is always “alarmed” by damage inflicted on any telecommunications infrastructure during conflicts. The ITU, the United Nations’ primary internet governance body, believes “efficient telecommunication services” are crucial to peace and international cooperation, and its secretary-general has called for respecting infrastructure in the Middle East, Gehner says.
Officials in Israel have consistently claimed they are targeting Hamas militants within Gaza, not civilians, while responding to the Hamas attacks, which killed more than 1,400 people in Israel. The Hamas-run Health Ministry within Gaza has said more than 7,000 people have been killed there and released a list of names. A spokesperson for the Israel Defense Forces did not respond to WIRED’s questions about internet disruptions within Gaza.
Hanna Kreitem, a senior adviser for internet technology and development in the Middle East and North Africa at the Internet Society, an open internet advocacy nonprofit, says Palestinian firms have a “big reliance” on Israeli internet firms. “Palestinians are not controlling any of the ICT infrastructure,” says Mona Shtaya, a non-resident fellow at the Tahrir Institute for Middle East Policy. Mobile networks in the Gaza Strip rely on 2G technologies. Al-Agha, the digital marketer, shared a screenshot showing mobile internet speeds of 7.18 kilobytes per second; average mobile speeds in the US in 2022 were 24 megabits per second, according to mobile analytics firm Statista.
“The internet is vital in times of war in crises,” says Fatafta, the Access Now policy manager, who adds that there can be “terrible consequences” linked to connectivity blackouts. The UN’s OCHA said rescue workers have had a harder time “carrying out their mission” partly due to the “limited or no connection to mobile networks.” Al-Agha says he has lost some clients due to the disruptions. The lack of connectivity can obscure events that are happening on the ground, Fatafta says. News crews have told WIRED they have footage from the ground but are “losing the story because of the internet.”
Kreitem says that a lack of electricity and access to the equipment will have made an impact on top of any physical damage to communications networks. “We don't know how many of the people that actually operate these networks are still alive,” Kreitem says. “The network operators are part of the world there, there's no place for them to run. They are as affected as any other person.”
90 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
40 notes
·
View notes
Text
Computer Literacy
Computer literacy is the most important social problem of today. At least, it’s the most important problem relative to the amount of time we spend talking about it. That makes it the most underrated social problem, and probably the one where we can achieve the most long-term improvements per unit of effort spent, but for some reason we don’t.
As computers have become more and more important, most jobs are now impossible to do without some sort of IT system in there, and that has resulted in people who used to be competent, confident and creative in their jobs throwing their hands in the air, saying “it’s a software problem, what can you do“ as automation increasingly dictates their workflows and makes them unable to even do things they used to be able to accomplish manually.
Somehow, the modern world is full of computers, and they are more important than ever, but as software has become more complicated and more difficult to use, people have become worse at using computers.
Over the last twenty years, we didn’t really get better at computer use. Instead we got used to not being able to understand what’s going on. We are also used to not being in control. Programs update themselves. Web apps change their UI. Web sites change their URL structure and invalidate all your bookmarks. Phones become obsolete in a way that makes it impossible to even run the versions of apps that used to work.
When I talk about complexity, I don’t mean the “internal” complexity of software, as in code complexity, build dependencies, software architecture, and all the tooling to manage this somehow. I mean user-visible complexity: Software is no longer an .exe file on your hard drive, but a self-updating app with a small icon that needs an online account and starts itself when your computer starts. Data is no longer a file on a floppy disk, but a collection of rows in an SQL database somewhere in %APPDATA%, or worse, a collection of rows in an SQL database in the cloud behind a REST API that is actually not REST but just RPC over HTTP.
Computer literacy is a moving target. That makes it difficult to teach. I suspect that the software industry wants it that way.
In their quest to “simplify“ software, vendors turn every application into a black box or a walled garden, denying users ways to re-use knowledge gained from other apps. Can you share the document you are editing with your friends by sharing the URL in your browser? If it was a file, you could save it and share the file with a friend. Online, all bets are off. Maybe the URL thing works, maybe the application has its own internal sharing system that requires your friends to make accounts, so you can “connect“ with them, and only then can you select them from a drop-down menu to share your document with, or maybe the application automatically scrapes your friends from facebook.
When I was in 7th grade, I had “basic computer lessons“, sponsored by Microsoft. We learned how many bits there were in a byte, how to send e-mail with hotmail.com, and what to use Word, Excel, and PowerPoint for. What we did not learn was how to uninstall software, how to burn a CD, or how to send e-mail attachments. The “child-proofing” software installed on the school computers prevented us from accessing the file system.
Important tasks such as
connecting to a wireless network
printing on a shared network printer
getting your PowerPoint to display on an external screen or projector
verifying that an e-mail is indeed coming from your friend or your bank
were left out.
(Aside: Why don’t banks sign their mail with PGP?)
In the mean time, what has gotten worse was not education. It was software itself. Software has gotten more and more hostile to computer literacy. Some software is actively hostile to deep understanding now, and increasingly it’s also becoming hostile to shallow understanding and muscle memory. Good luck with your new iPad air, we have moved all the buttons around, and have hidden basic functionality behind gestures. Tapping this does nothing, maybe try swiping it, pinching it, shaking it, with three fingers, swipe from the edge of the screen, whoops you switched apps now. It’s no longer possible for an end user to understand software. It’s no longer possible for third parties to even write “the missing handbook” of Slack or Google Docs or Spotify or Dropbox or indeed the iPad. It will be obsolete before it hits the shelves.
Related: http://contemporary-home-computing.org/turing-complete-user/
299 notes
·
View notes
Text
Remembering My Roots - Rest in Peace, RateMyDrawings
I've talked about my old art before on here, but never really fully in-depth about the site that hosted it. I was reminded of it today while going through my FB memories and felt like I should actually write a true eulogy towards what once was.
Once upon a time, before LORE | REKINDLED, before Time Gate: [AFTERBIRTH], before I had even started drawing webcomics, I entered the world of digital art through one website - not DeviantArt, not Pixiv, but a little site called RateMyDrawings. Back in the day, it was one of the most popular browser-supported art tools, offering multiple different art tools that were, at the time, revolutionary. A flash drawing tool which could replay the progress of your drawing (but the tradeoff was that you had a limited amount of 'ink' aka recording data), a Java-supported tool that was essentially Photoshop Lite (but didn't come with the recording), and later, a more refined tool supported by HTML5 (?) that offered more 3D-like brush tools. There was also DrawChat, a live drawing flash tool where you could draw with others and chat.
And on that site, I created my first works of digital art. No drawing tablet, just a mouse and a loooot of patience. They'd host contests every now and then to win budget Wacom tablets. Sometimes I'd enter, I'd never win. I did eventually get my first drawing tablet, but by then, I'd moved on from RMD onto actual software such as GIMP and Photoshop Elements.
That site is gone now, one of the first art site deaths I'd ever experience in my teen years. I was around 12-13 when I started using this site and I adored it. When people talk about missing the 'tight-knit communities' of old, I don't think of DA, I think of RMD, my first home. Unfortunately, the site couldn't survive in the 'modern' era of the Internet, overshadowed by more advanced tools and art-sharing sites like Deviantart, Facebook, and Instagram.
But I did manage to backup some of my old art pieces before the site finally became completely shuttered in the early 2020's. For a while the site was awake but lacked any content or features, with a message from the site's creator Mick that it might come back, it might not.

It didn't. The old ratemydrawings.com URL now redirects to the inactive FB page. Any attempt to bypass that kill screen like before leads to an Error 404.
But while the site was in its comatose state - before it was shuttered permanently - I was able to access my old profile and extract some of my art pieces of old. I posted them to my FB about 3 years ago, and today they showed up in my memories.
I share a lot of art pieces from creators like Rachel Smythe in an attempt to preserve media. But I also need to remember to preserve my own. So here are a handful of the 100+ pieces I drew on RMD. Enjoy ( ´ ∀ `)ノ~ ♡

Don't be confused by the '1987' part of the username, I picked that number because I was a huge Zelda weeb and 1987 was the year the first Zelda game was made. Whoof.

What's ironic is I actually didn't have the Featured Artist award last time I was actively on the site, so it clearly happened while I was inactive in its final days. The one award I wanted the most and I wasn't there to witness getting it. RIP.







Unfortunately that's all I really have in the way of high-resolution drawings as I wasn't able to preserve much else (though if I find anything more I'll definitely add it to this post!) That said, I was able to nab some screenshots of my homepage via the Wayback Machine where you can see more of the pieces I did back then:
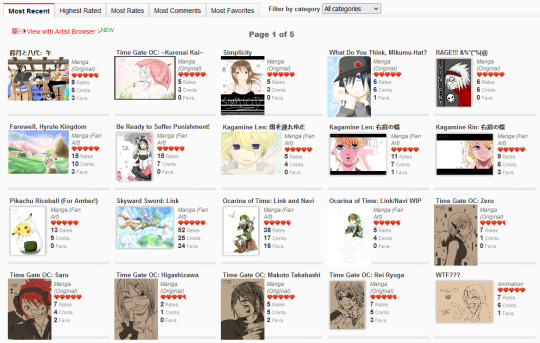
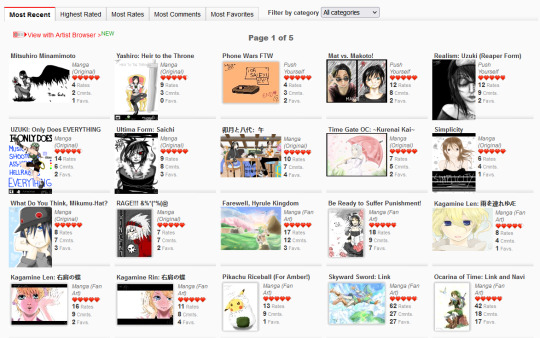

There are so many dorky ass drawings here, some from Time Gate (because it's that freaking old!!!), some are screenshot recreations from anime that I enjoyed (a very common trend on RMD), some are collaborations. There was a point where I learned how to color with the mouse by using low opacity colors and layering them one at a time. Really upped my game there LMAO That Ocarina of Time Link drawing was the first one I ever did that made it to the front page of RMD and y'all, I was so proud, the site back then I think had 50k users total which is nothing compared to the Internet today, but achieving that was one of the greatest things ever LOL The Skyward Sword drawing that followed was one that really felt like a milestone in terms of my art evolution, I felt like I was finally creating something good. I believe I did that Skyward Sword drawing off another DA piece at the time, it was really common to do redraw challenges on RMD what with the technical limitations of the site - I suppose redrawing stuff I liked back then should have been foreshadowing LMAO
That feeling wouldn't last forever ofc once the art high wore off, but even to this day I look back on the pieces from that era fondly. It's where the mysteries of digital art finally started to 'click' in my brain, and I had still barely gotten started.
I also have a few drawings preserved that were done after I got my first drawing tablet, and you can really tell with the improvement of the lineart LOL That said, I think I was around 18-19 when I did these:


Now, one thing that I really enjoyed doing on RMD were collabs - specifically, trading collabs where users would exchange drawing files through the RMD PM system with one another to do steps of a drawing together. Often times I took the role of coloring other people's lineart pieces, which is probably where I started to really learn digital art coloring and come into my own with it.
A collab with user "lime":

Collab with user "Mikai":

A collab with user "Overik", which I specifically remember struggling with because, at the time, my computer monitor's screen was messed up resulting in the entire thing basically being a fluorescent pink:

A collab with "Mist04" that I don't remember doing lmao:

Collab with "Adzumi" (?). I'm fairly certain that's who it was, I definitely remember the process of painting this one, I had loads of fun with it:

Collab with user "ForgottenArtist", IIRC this one was more of a coloring page where they gave out the file freely for others to color, so this was my version. The forums on RMD were great for that sort of thing, people would literally just upload their drawing files for people to have fun with:

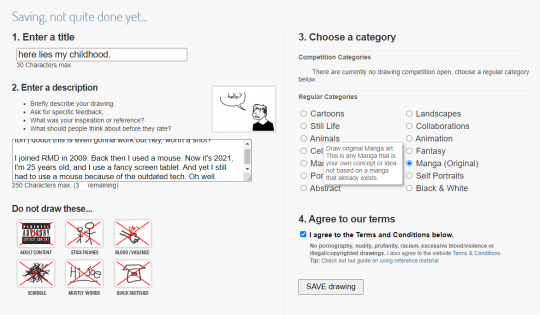
So I guess I drew this next little thing in 2021 when the site was still 'live' but not functional, I completely forgot I did this though LMAO Basically the main URL took you to that kill page I showed above, but if you knew any of the extension slugs, you could bypass that kill page and get into the rest of the site, which I was able to by using my username URL. So I got into the Java drawing tool and made this little thing in the hopes I could upload it. Of course, it didn't work, but hey, it was worth getting a screenshot, I suppose:
It's equal parts nostalgic and bittersweet to go through these drawings. Life back then feels so far away and yet I still remember it so vividly, the hours I'd spend drawing on the family PC, feeling more at home with the friends I made online than the ones I had in real life, listening to music that I still listen to to this day. It's far away now, but it still lives through me, in the work I do today. Even someone like me can go from being a complete noob drawing with a mouse to a professional making their living stabbing ink into other people while still drawing the same stories they drew as a child.
There is one piece I had to dig up outside of FB memories, fortunately it wasn't hard to find because I knew I had shared it ages ago on my FB so the search bar saved my skin. My very first digital art piece, of Sheena Fujibayashi from Tales of Symphonia, one of my favorite games of all time.
My very first digital art drawing:

Recreated in 2019:

Past me went through a lot, and they'd be doomed to go through even more still (they hadn't hit the plague yet). And yet they're going to survive, they're gonna keep getting better and better with each passing year. Thanks past me - you've done a lot of dumb shit in your life, but sticking with your craft wasn't one of them. Thank you for walking - through all the good and the bad that you've had to weather through - so that I could run for us both.
#i have other things i wanna mention about old RMD as well but they're better for another post#self post#old art#media preservation#digital art#ratemydrawings
39 notes
·
View notes
Quote
In tech, bullshit jobs—which the late David Graeber defines as “a form of paid employment that is so completely pointless, unnecessary, or pernicious that even the employee cannot justify its existence” even though they are obliged to pretend otherwise—come mostly from bullshit projects. At Google, such projects are aplenty. According to Killed By Google, an archival project that documents discontinued Google services, products, devices, and apps, the company has discontinued nearly three hundred projects since its founding. These range from software systems to help businesses distribute and manage job applications (Hired by Google) to social media platforms that tried to mimic Facebook’s success (Google+) to manifestly uncool wearable technology (Google Glass). But projects at that scale are far and few between. Many were small and hackathon-sized in ambition. All failed to make a splash on the balance sheet. These “dead” projects are also just the tip of the iceberg. The website only documents projects that have been publicly launched; untold more have been nixed before ever being announced.
It’s All Bullshit
12 notes
·
View notes
Text

From La Stampa (translated from Italian):
“Make Finance Great Again,” Trump family makes its own cryptocurrency and allies with Silicon Valley
It will be called “World Liberty Financial,” will have tech investors and real estate developers from Chase Herro and Zak Folkman to Steve Witkoff inside. Sons Eric and Donald Jr. will coordinate. And his backer Tyler Winklevoss jokes, “Donald has been orange-pilled, indoctrinated.”
Jacopo Iacoboni
Sept. 17, 2024
Updated 11:00 a.m.
3 minutes of reading
They want to do a kind of “make finance great again,” along the lines of MAGA, the election slogan and the Make America Great Again campaign. Donald Trump's sons, Don Jr. and Eric, of course with their father's imprimatur, are about to launch a new cryptocurrency platform that will be called “World Liberty Financial,” and will allow users to make even massive transactions without a bank getting in the way and extracting fees (and with a very low level of tax tracking, it should be added). A couple of concepts familiar to bitcoin fans, for example, but which the Trump family now has ambitions to decline on a large scale. It is not certain that this marriage between Trumpism and decentralized finance, DeFi, is a harbinger of only positive developments.
The board of “World Liberty Financial” will also consist of former crypto investors such as Chase Herro and Zak Folkman, and Steve Witkoff, a real estate developer and old friend of Trump. But thanks to documents filed with the U.S. Federal Election Commission that we have been able to read we know that in general the entire Trump campaign - Make America Great Again Inc. - received money not only from Musk, but cryptocurrency from billionaire twins Cameron and Tyler Winklevoss, who lead the cryptocurrency company Gemini: about $3.5 million in Bitcoin on July 19, the day after Trump's speech at the Milwaukee convention. The Winkelvosses also poured in money to America PAC, the tech investor-backed group that Musk helped launch in 2024 (Trump had bragged that Musk was giving him $45 million a month; Musk said his contribution is “at a much lower level”). Another co-founder of a cryptocurrency exchange, Jesse Powell, boss of Kraken, and venture capitalists Marc Andreessen and Ben Horowitz (who created a16z) who have invested billions of dollars in cryptocurrency startups, have also made endorsements and poured money into Trump.
In short, for the Trump family to embark on this big cryptocurrency project is a natural consequence of the fact that these are almost becoming a Republican asset in the campaign, and the “libertarian” wing of the old Gop is now a kind of very, very rampant ideologized “cyberlibertarianism.”
The real boss of the “tech bros” according to many is not Elon Musk, but Peter Thiel. Zuckerberg's longtime partner in Facebook, co-founder of PayPal, Thiel's fortune has at least doubled during the Trump presidency. Palantir-a much-discussed software company variously accused of extracting data from Americans and profiling them-has managed to get a contract from the Pentagon. Other donors to MAGA Inc include Jacob Halberg, Palantir's princely analyst, and Trish Duggan, a wealthy Scientology funder and friend of the tech bros.
Trump's vice presidential candidate, J. D. Vance, traveled to Silicon Valley and the Bay Area, celebrating a dinner at the home of BitGo CEO Mike Belshe, 100 people each pouring in between $3,300 a plate and a $25,000 roundtable. Trump in 2021 called bitcoin a “fraud against the dollar.” A few weeks ago, speaking in Nashvill at the bitcoin fan conference, he promised, “The United States will become the crypto capital of the planet.” Better than his friend Putin's Russia, although this Trump did not say so explicitly. The fact is that after his speech, Tyler Winklevoss ran on X (now the realm of cyberlibertarians) and joked that Donald had been “orange-pilled,” making a Matrix analogy, had been “indoctrinated,” or had finally seen the real reality behind the appearances.
3 notes
·
View notes
Text
How to Stream on Kick : A Complete Guide
In the dynamic world of online streaming, Kick.com is quickly becoming a popular choice for content creators. If you're looking to join this growing community, you've come to the right place. This guide will walk you through the process of registering and starting your first stream on Kick.com. Plus, we'll share a valuable tip on how to log your channel's messages using kickchatlogs.com.

Step 1: Registering on Kick.com
Create an Account
Visit Kick.com: Open your preferred web browser and navigate to Kick.com.
Sign Up: Click on the "Sign Up" button typically located at the top right corner of the homepage.
Fill in Your Details: Enter your email address, create a username, and set a strong password. You may also have the option to sign up using social media accounts like Google or Facebook for a quicker process.
Verify Your Email: Check your email for a verification message from Kick.com. Click on the link provided to verify your account.
Complete Your Profile
Login: Use your new credentials to log in to your Kick.com account.
Profile Setup: Go to your profile settings and fill in any additional information such as your profile picture, bio, and social media links. A well-completed profile can attract more viewers.
Step 2: Setting Up for Streaming
Download Streaming Software
To stream on Kick.com, you'll need reliable streaming software. Popular options include OBS Studio, Streamlabs, and XSplit.
Download and Install: Choose the software that suits you best and follow the installation instructions.
Configure Settings: Open the software and configure your stream settings. You'll need to set your resolution, bitrate, and other preferences.
Get Your Stream Key
Access Your Dashboard: Log in to Kick.com and navigate to your creator dashboard.
Find Your Stream Key: In your dashboard, locate the stream settings section where you'll find your unique stream key.
Copy the Stream Key: Copy the stream key as you will need to enter it into your streaming software.
Step 3: Going Live
Configure Your Streaming Software
Enter Stream Key: In your streaming software, go to the settings and find the "Stream" tab. Paste your Kick.com stream key into the designated field.
Set Up Scenes and Sources: Create scenes and add sources such as your webcam, game capture, and microphone.
Test Your Stream: It's always a good idea to do a test stream to ensure everything is working correctly.

Start Streaming
Go Live: Once everything is set up and tested, click the "Start Streaming" button in your streaming software.
Monitor Your Stream: Keep an eye on your stream through your Kick.com dashboard to ensure everything is running smoothly.
Bonus Tip: Logging Your Channel's Messages
As a streamer, it's important to keep track of your chat messages for community management and content moderation. The best place to log your channel's messages is kickchatlogs.com. This platform provides an easy and efficient way to save and review all your chat interactions.
Sign Up on Kickchatlogs.com: Create an account on kickchatlogs.com.
Link Your Kick.com Account: Follow the instructions to link your Kick.com channel to kickchatlogs.com.
Start Logging: Once linked, your chat messages will be automatically logged and can be accessed anytime through your kickchatlogs.com account.
Conclusion
Starting your streaming journey on Kick.com is straightforward and user-friendly. With this guide, you now know how to register, set up, and start streaming on the platform. Remember to use kickchatlogs.com to keep track of your channel's messages and maintain a healthy, engaged community. Happy streaming!
For more detailed guides and streaming tips, stay tuned to our blog. If you have any questions or need further assistance, feel free to leave a comment below.
#streaming#kick#kick.com#tutorial#how to stream on kick#start streaming#self employed#twitch#youtube#youtube live#twitch live#livestream#twitch stream#kick stream#livestreamer#asian andy
3 notes
·
View notes