#Geographic coordinate system
Explore tagged Tumblr posts
Text



A Beautiful Mind (2001, Ron Howard)
18/06/2024
#a beautiful mind#film#2001#ron howard#mathematics#nobel prize#John Forbes Nash Jr#russell crowe#1947#princeton university#antisocial personality disorder#Formula#Doctor of Philosophy#game theory#adam smith#research#massachusetts institute of technology#Boston#cold war#the pentagon#Number#moscow#cryptography#Geographic coordinate system#united states#secret service#United States Department of Defense#classified information#russians#Suitcase nuclear device
2 notes
·
View notes
Text
X7 Acts 4-5 Summaries Transcription
Acts 4 and 5 (mostly 4) are the most likely to have errors since they're never completely clear, so please take this with a grain of salt! Suggested edits are appreciated.
I've already transcribed acts 1-3 here. Double check that the version you're reading is the most up-to-date one. :-)
(Updated as at 13/04/2025 at 2PM AEST)
Act 4 - The Doubt



Summary
Size: Large Playtime: ~5 hours Energy: Medium Emotional tone: Creeping doubt & feeling like an Outsider 70% Talking; 30% Action 50% Comedy; 50% Darkness
"Arriving in the Fourth Act, Cuno is officially furthest from his home that he's ever been, while Cunoesse is coming nearer to hers than she has been in the years after she escaped, and this [distinction?] is starting to get difficult to ignore. The presence of Hämärä Maa looms over them both, as the fabled archipelago lies just across the bay, across the [...]. Having disembarked from the Train virtually in the middle of nowhere, Cuno and Cunoesse come upon the Rhöne-Tréville (Royal) Penal Colony or the Tréville, but most people call it: a [...] centred around a former Royalist prison-labor camp. Being that geographically [...] to Hämärä Maa, the small community represents the closest point of contact between the archipelago and the world, participating in the trade of goods, legends and the profitable psychedelic marrow of an endemic cave fish. Meeting the locals, the kids will learn about the impending relocation of the surprisingly harmonious community-sustaining prison complex, and the complicated [...] between the coordinate [...] of freedom, imprisonment, community and [reunion? tension?]. They will also begin on their [...] is a growing sense of dread that Cunoesse got herself into something that is much darker and more morbid than he could have expected. In order to progress to Hämärä Maa to find out for themselves, the kids must [...]. [...] they must [...] Cunoesse's half remembered [...] family connections among the marrow traders, some of whom are now in the prison, or they might win their way forward with [...] and sneers, stealing a toy raft from a gang of violent girl children."
Player experience
[...] begin to suspect we are approaching a sinister [...] with the things we've been avoiding all along.
[...] more and more about Hämärä Maa [...] borders of a bad neighbourhood, like walking alone at [...] realising your GPS is leading you in the direction of [...] you've realised way too late to do anything about it.
[...] are more frightening if they are unseen. Hearing [...] tales about Hämärä Maa before we've had [...] establish what's there will build up the sense of dread [...] for the game's climax location.
[...] for the later endgame where Cuno breaks free of the bond.
The power balance between Cuno, Cunoesse and the player's conscience will again be tested as Cunoesse urges Cuno to brutally fight one of the Tréville girls in order to steal her raft.
The small self-sustaining community will present the player with the opportunity to engage with the full set of game systems, including game economy, Thoughts, substances, exploration and multiple-approach problem-solving.
Act 5 - The Arrival


Summary
Size: Medium Playtime: ~2 hrs Energy: High Emotional tone: [...] & Reality-Twisting 60% Talking; 40% Action 30% Comedy; 70% Darkness
"After all the fear and the mayhem, Cuno and Cunoesse are finally there: landing on the shores of Hämärä Maa, their promised shadow-land. Greeted with the sounds of shamanic singing and solemn drums, the kids will catch the locals in the midst of a funeral ceremony, gaining a glimpse into both the cultural practices of the Näkki and the strange and colorful faces of the island's population. The island has changed since Cunoesse has last called it home. Only her impossibly old grandfather remains, and her [sins?]. She knows she must do one last thing before she can plead to be readmitted into her tribe. Under the pretense of a Hämärän naming ceremony, Cunoesse pressures Cuno into ingesting the bone marrow of the psychedelic cave fish. As Cunoesse takes on the role of his fucked-up trip shaman, Cuno grapples with the growing clarity that her goal is deeply sinister: to bind him to herself, or kill them both trying. Cunoesse embraces him and throws them both off a pier, pulling him deep under water, triggering the stylish climax sequence of the game: the Underwater Psychedelic Trip. Reality will [...] as you seemingly sink for an eternity, fighting for your life and your identity as Cunoesse's true intentions come to light - to use the drug to manipulate Cuno into total and irrevocable ego death, and make him believe that he is Jaakko, the boy Cunoesse killed in the caves three years prior. That was her plan all along: to bring Cuno all the way from Martinaise to buy herself passage back into her community by replacing what she has broken. All she needs him to do now in order for her plan to work is to play along, *really* play along, so deeply that he will never recall being someone else ever again. Their showdown under water will determine whether Cuno will let go of his identity in one [...], or if he is willing to kill his other half in order to remain who he is. The Act spins off into up to five possible endings, depending on which one of the kids lives, dies or is brainwashed."
Player experience
We want a sense of culmination in every way -- the culmination the journey, of finally getting to see what Hämärä Maa is truly like and what Cunoesse truly is.
This should be a streamlined sequence, funneling the player [seamlessly] towards the end. We want the player to be unable to [...] the game once they've landed on Hämärä Maa, similarly to how Harry's story spirals tighter and tighter towards its resolution from the moment he steps onto the Deserter's Island.
We want the player to feel as if they are performing cultural [contact?] with an ominous insular community, something like Midsommar but with degenerate alcoholics instead of tradwives.
This is where everything we've tried to do over the course of the game comes to count. All the dual-character systems that make the player roleplay as both Cuno & Cunoesse, all the story beats that make the player internalise their respective stakes, all the emotional connection to this feral superorganism, if we can make the player feel like we're making them choose between two halves of themselves, we've achieved what we set out to do. If they feel torn apart, agonized over their choices, we've won.
462 notes
·
View notes
Note
This is a dumb fucking question so I apologize but why the fuck is this stuff with Iran and Israel happening right now? What the fuck prompted Israel to do that? Was it literally just senseless bloodlust? I can't understand it and I'm only finding vague wishy-washy answers.
So it’s a combination of things, as all complex geopolitical conflicts are. First is that this has been a wet dream of the hawk Israeli right for about 30 years now (just check out all those Netanyahu quotes from the 90s about Iran being one day away from making a nuke that explodes the world), because Iran represents the largest, most calcified member of the anti-Israel “axis of resistance” (in quotes because a lot of Israel’s successes lately have come from the bizarre lack of strategic coordination between the different parties, which kind of undercuts the notion of an “axis”). Anyways, reason number one really is just Israel seeing an opportunity to knock off its largest regional threat.
Secondly, while that has long been their desire, it’s been pretty unattainable. Iran is fucking big, and there’s a huge distance between the two countries (2300 kilometers, give or take) meaning their ability to actually strike the IRI has long been limited to long range missiles (not a great option if you want to break an enemy, missiles can be resisted for a while. Just look at Ukraine) or intelligence operations (more accurate but obviously less physically, explosively powerful. We’re talking targeted assassinations, not knocking out ballistic missile depots). Neither one of those is gonna do much about the guy with 8 times your population and like 10 times your geographical sings, with a largely independent economy (because of sanctions). Iran can absorb those blows basically forever, just from sheer size and inertia. You need actual air presence over Iran to sustain the kind of strikes that *might* disable it, and to do that, you need large numbers of strike fighters. The F-35 (Israel specifically flies the most advanced variant outside the US, the F-35I) has just about 2200 kilometers of total range, and I can’t remember the F-16’s off the top of my head but it’s either similar or smaller.
Now that matters because you can get around any fuel range limit with aerial refueling, but you can’t do that in hostile skies, and as long as Assad was in power in Syria, basically all the skies along the way to Iran were hostile. Assad’s military had an extensive, robust air defense system, which meant vulnerable logistics craft like tankers couldn’t fly, and Israel just couldn’t reach Iran. Since Assad’s fall and the complete liquidation of his AD network, that’s gone. This is the first time Israel has had both the pretext, international support, and actual capability to hit Iran, so they took that opportunity.
Now the reason we’re getting involved is that for the last 20 odd years basically every US politician across both parties has been a bloodthirsty child murdering psychopath for war with Iran. And also because Israel still lacks the munitions to do any meaningful damage to Iran’s nuclear program (the actual important facilities of which are buried hundreds of feet under sand, dirt, rock, and extremely heavily reinforced concrete).
22 notes
·
View notes
Text
Yes! I did indeed create a theoretical formula for my time-travel theory that I ALSO invented for a South Park fanfic! Why do you ask?

Jokes aside, I think it’s time for me to break down the formula to explain what all these symbols mean and tell you my thought process while making this. For starters: I’m not a scientist, astrophysicist, mathematician, or smart enough person to exactly know what the hell im even saying. I was only able to have a solid grasp on what this all means because of my more smarter friends, google searches, and physics-related YouTube video essays. Anyways….
Realistically, in order to make something like this work in real life, you’re going to need to know AND have these three major components:
Understand/study everything you know about gravity and the theory of relativity.
Solve the creation of a wormhole and be able to control it within an enclosed space
Create a “Blind Filter” to prevent a total collapse on neighboring grids/columns
Have tools, devices, and technology advanced enough to: detect anomalies and measure temporal signatures in spacetime, create maps of gravitational fields, generate copious amounts of energy to keep a wormhole stable during transit, and have quantum computers to perform complex calculations for navigation.
If you don’t have none of these things, time travel won’t be possible 😔🤙. But, if you do… well.. perhaps it wouldn’t hurt to try! Anyways, let’s start with the first equation!

Wormhole Stabilization: The main purpose for this equation, is purely for the stabilization of a wormhole’s throat to prevent a total collapse! Mind you, wormholes have never been discovered to be an actual thing— it’s all purely a theoretical possibility— unlike black holes!!! Throughout my research, I took refrences from Einstein field equation and the Morris-Thorne wormhole metric in general relativity! Like I mentioned, we won’t know how the equation truly works because we don’t have an actual point of reference, therefore, this equation could be a bunch of hippy dippy bologna!! [*So are all the equations I will mention btw*]. This equation can be rewritten depending on how wormholes would actually work in a non-theoretical sense… BUT ANYWAY— if it were to work, this formula could be something that keeps a wormhole stable in order to be traversable through time!!

Grid/Column & Gravity: Yeah, pretty self explanatory. Because I had to create a formula that needed to be connected to the One-Tab Guide, then the purpose of this formula is to FIND a grid and column by combining general relativity and gravity. There are so many theoretical grids, and the columns are even harder to find since they’re interwoven with other grids/columns!

Spacetime Interval Adjustment: Also pretty self explanatory! This calculates the spacetime distance between the current and targeted timelines. It’s specifically modified for multiversal travel! See, the one-tab guide isn’t just a formula to help with time-travel, but it’s also a formula that can allow multiverse travel across multiple dimensions!!! Wow!!! Personally, I feel like multiversal travel would be a whole lot more easier to accomplish with this formula compared to to the possibility of time traveling in your own column. You won’t really have to worry about exact calculations because you basically just pick and choose which area outside of the specialized grid you wanna go 🤷♂️! Though, if you want to go to a time and place in a certain multiverse where YOU exist, you’ll probably have to be more specific with that calculation in order to find your parallel self (if said universe even has one).

Temporal Signature Correction: When you want a certain location marked, you use a geographic coordinate system! And with parallel travel, it’s a Temporal Signature Correction! This basically insures that a traveler goes to the correct timeline by using a unique “temporal signature” (St). No, I still don’t understand quantum mechanics that well (the MCU has ruined the word “quantum” for me). And yes, I still get confused when I think about entropy for too long. Best way to think about it within the context of the one-tab— is that entropy is the universe’s obsession with making things not messy. Each grid could have a unique entropy value to help distinguish between them, higher entropy grids could be more chaotic to the “anchor of reference” of a traveler. Which means if someone messes with time, entropy might fight back by making timelines chaotic or cause a fissure in a grid.

Proper Time Interval: Basically to travel to a specific timeline, the time machine needs to solve the proper time interval required to navigate that targeted timeline. Usually if you miscalculate, you could cause paradoxes, universal fissures, a collapse in the grid, etc.. But in my fic, Kenny created an entirely different machine (a sort of blind filter) to prevent any impact on the multiverse. But, if you don’t have that machine, then this formula is very important in that sense.
—
Anyways…. this probably won’t make sense to anyone except me. But I thought it would be cool to have some fictional formula with cool little symbols for this silly little theory. Maybe when our technology is advanced enough, this could all be tested and disproven 🙂↕️. Now go read (and reread) my bunny fic! Please…

#iwmoy#fanfiction#science fiction#fic analysis#south park#ao3 fanfic#this will definitely not make sense to anyone#but it’s fun either way
21 notes
·
View notes
Text

An interactive evacuation zone map, touted by the Israeli military as an innovation in humanitarian process, was revealed to rely on a subset of an internal Israeli military intelligence database. The US-based software developer who revealed the careless error has determined -> that the database was in use since at least 2022 and was updated through December of 2023.
On Tuesday, July 9th, we discovered an interactive version of the evacuation map while examining a page on the IDF's Arabic-language website accessible via a QR code -> published on an evacuation order leaflet.
The map is divided into "population blocks" an IDF term to refer to the 620 polygons used to divide Gaza into sectors that a user can zoom into and out of.
However each request to the site pulls not only the polygon -> boundaries but the demographic information assigned to that sector, including which families - and how many. members - live there.
𝐃𝐢𝐬𝐜𝐨𝐯𝐞𝐫𝐲 𝐨𝐟 𝐈𝐧𝐭𝐞𝐫𝐚𝐜𝐭𝐢𝐯𝐞 𝐄𝐯𝐚𝐜𝐮𝐚𝐭𝐢𝐨𝐧 𝐌𝐚𝐩𝐬:
Evacuation maps have played a central role -> in determining which sectors of Gaza were deemed "safe", but repeated instances of Israeli bombing in "safe" sectors has prompted international bodies to state "nowhere in Gaza is safe"
To determine how these sectors have been affected over time, assess the presence of vital -> civilian infrastructure, and gauge the potential impact on the population following the military's evacuation calls to Gaza City residents, the latest of which was two days ago, our team created a map tied to a database using software known as a "geographic information system” -> With the help of volunteer GIS developers, our map of Gaza included individual layers for hospitals, educational facilities, roads, and municipal boundaries.
This endeavor took an unexpected turn earlier this week when we started to work on -> the layer of "evacuation population blocks"
using a map shared to the Israeli military's Arabic site. Unlike static images, these maps responded interactively to zooming and panning. A software developer suggested that dynamic interaction was possible because the coordinates -> of various "population blocks" were delivered to the browser with each request, potentially retrieving the coordinates of the "population blocks" in real time and overlaying them on the map we were building.
The software developer delved into the webpage's source code -> —a practice involving the inspection of code delivered to every visitor's browser by the website. The source code of every website is publicly available and delivered to visitors on every page request. It functions "under the hood" of the website and can be viewed without -> any specialized tools or form of hacking.
𝐏𝐚𝐫𝐬𝐢𝐧𝐠 𝐔𝐧𝐞𝐱𝐩𝐞𝐜𝐭𝐞𝐝 𝐃𝐚𝐭𝐚
Upon examination, the data retrieved by the dynamic evacuation map included much more than just geographical coordinates. The source code contained a table from an unknown GIS -> database with numerous additional fields labelled in Hebrew.
These fields included population estimates for each block, details of the two largest clans in each block (referred to as “CLAN”), rankings based on unknown criteria -> and timestamps indicating when records were last updated.
Some data terms, such as "manpower_e," were ambiguous for us to interpret, possibly referring to either the number of fighters or the necessary personnel to maintain the area -> Using this information we determined that Block 234, Abu Madin was last updated on 27 April 2022. This suggests that Israel's effort to divide Gaza into 620 "population blocks" began one and a half years before the current Israeli offensive -> Additional modification dates indicate that the military updated data in this field regularly throughout October and November, before formally publishing it on the arabic Israeli military webpage on December 1, 2023.
It appears that the IDF has accidentally published -> a subset of their internal intelligence
GIS database in an effort to impress the world with a novel, humanitarian evacuation aid. It is easier to retrieve a database in its entirety than to write a properly selective query. Such mistakes are common among programmers that lack -> experience, security training, or are simply unwilling or unable to do meet standard data security requirements for a project.
𝐂𝐥𝐚𝐧𝐬 𝐚𝐧𝐝 𝐀𝐝𝐦𝐢𝐧𝐢𝐬𝐭𝐫𝐚𝐭𝐢𝐨𝐧 𝐏𝐥𝐚𝐧𝐬 -> In January, Israeli security chiefs proposed a plan for "the day after" where Palestinian clans in the Gaza Strip would temporarily administer the coastal enclave. In this concept, each clan would handle humanitarian aid and resources for their local regions. Israeli assessments of the proposal suggested such a plan would fail due to "lack of will" and retaliation by Hamas against clans willing to collaborate with the army. The plan has since been modified to include Hamas-free “bubbles,” (as reported by the Financial Times) -> where local Palestinians would gradually take over aid distribution responsibilities.
As this plan is to be initially implemented in Beit Hanoun and Beit Lahia. Al-Atatrah Area and Beit Hanoun, we have analyzed the information in the database assigned to those three areas -> Israeli army classified the Al-Atatrah area as region 1741, although there are only 620 'blocks' on the map. The registered population was listed as 949, last updated by the IDF on October 9th. We assume this represents an estimate by the IDF of current residents as of Oct 9th. Residents of Al-Atatrah were among the first to evacuate following the initial bombardment on October 7th and 8th and were not given a formal notification to evacuate. The Israeli military noted that the Abo Halima family comprised 54% of the block’s population -> In area west of the town Beit Hanoun, Israel had desginated the Almasri clan as the largest in the sector, consisting 18% of the block's population. Second largest was the Hamad family, with11% of the block's population. This area were also associated with rankings, however -> without the criteria used to determine the ranking, these numbers are difficult to interpret.
𝐖𝐡𝐚𝐭 𝐝𝐨𝐞𝐬 𝐭𝐡𝐢𝐬 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐫𝐞𝐯𝐞𝐚𝐥?
Although some of the data were inadvertently truncated during publication, posing challenges for comprehensive -> interpretation, this database provides a valuable window into the Israeli military's perspective on Gaza.
For one, it prompts questions into why the military had already partitioned Gaza into 620 population blocks a year an a half before October 7th -> This suggests an early inclination to implement a governance policy where clans would assume authoritative roles, as well as detailed population surveillance. Tracking dense populations in the chaos of urban warfare is a difficult task -> It may be that the QR code on the evacuation map actively collects the locations of people who scan it, allowing the IDF to collect real-time data on Palestinians in Gaza as they attempt to find safety.
END
85 notes
·
View notes
Text
The communities of the wider Troodos (Trodos) region in Cyprus are getting assistance for access to renewable energy sources.
A project is underway for the island country’s first energy cooperative. It is especially aimed to benefit villages where the environment and particular geographical and building characteristics do not provide residents with technical solutions such as the ones in urban areas, for the production of cheaper electricity from photovoltaic systems or other technologies, philenews reported.
The non-profit MountMed Research and Development Institute for the Mountain Regions of the Mediterranean Islands secured EUR 1 million via a European Union program. The University of Cyprus, the project coordinator, is tasked with technical studies and obtaining permits.
They intend to install a pilot energy community solar park with storage for communities and villagers in the Troodos mountain range. In the first phase, the 500 kW facility would supply 100 households in the Solea-Marathasa area.
8 notes
·
View notes
Text

What is the wind direction definition? The first and the most important thing to remember: wind direction is always determined by where the wind is blowing FROM, not where it is blowing towards.
The directions of the wind is determined at the geographical system of coordinates invented by man back in the day. It is also called "cardinal directions" or "cardinal points" and similar.
It is interesting that in the Ancient Greece, the cardinal directions were also identified by the different winds. They were Boreas from the north, Notos from the south, Eurus from the east, and Zephyrus from the west. They are also known as the "Classical compass winds". Therefore, the concept of wind direction is very closely related to the concept of wind rose.
The wind rose is a graph that shows the prevailing wind direction and wind speed at some particular location according to statistics from many years of meteorological observations (also knows as weather history). So the concept of wind rose is used often precisely in meteorology.
Another word that says the same thing is "compass," a device for determining cardinal directions you know probably from your Scout days.
How to read wind direction? In a geographic coordinate system, the wind has a total of 32 different directions, but not all of them are used in everyday life. Let's take a closer look at all of them:
👉👉👉👉👉@lovesailing
#sailing #sailinglife #sail #boat #sea #yacht #sailboat #yachting #boatlife #travel #boating #yachtlife #ocean #boats #sailor #summer #sailingboat #sunset #adventure #sailingyacht #sailinginstagram #yachts #nature #sailingphotography #photography #beach #catamaran #sailinglovers #regatta #instasailing
#sailing#sailinglife#sail#boat#sea#yacht#sailboat#yachting#boatlife#travel#boating#yachtlife#ocean#boats#sailor#summer#sailingboat#sunset#adventure#sailingyacht#sailinginstagram#yachts#nature#sailingphotography#photography#beach#catamaran#sailinglovers#regatta#instasailing
11 notes
·
View notes
Text
The junk and the jangada: a route for academic collaboration between China and Brazil

The University of São Paulo (USP), a leader in scientific production in Latin America, and China, a global power in science and technology, share a common vision: That research and academic collaboration are the foundations for building a more equitable, sustainable, and innovative future.
This synergy takes shape at the USP-China Center, a strategic initiative of the USP President’s Office, aiming to strengthen the dialogue between the two nations, whose contributions to science and culture transcend borders.
This movement towards rapprochement takes place at a unique moment in the world’s geopolitical overlook, with territorial disputes and armed conflicts in different regions around the world and the recent victory of protectionist projects in countries with regional and global influence. In a recent article on Folha de S. Paulo Chinese President Xi Jinping invited Brazil to sail together with his country “under full sail”. But how can the Chinese junk and the Brazilian jangada sail together quickly and safely in such turbulent geopolitical seas? The way to go seems to be cooperation and multilateralism in academic relations.
China is Brazil’s main trading partner, and bilateral trade reached US$110 billion in 2024, resulting in a surplus of US$29 billion for Brazil. But the partnership between the two countries goes beyond trade and has immense potential in the academic sphere. China, a global leader in areas such as data science and engineering, finds in Brazil, with its expertise in sustainability, biodiversity, agriculture, and food safety, a partner of complementary strengths.
However, the enormous potential of the Chinese Brazilian partnership in science and technology faces substantial challenges. Language and cultural barriers still hinder academic exchange, and geographical distance imposes high costs on students’ and researchers’ mobility. In addition, the administrative centralization of Chinese institutions contrasts with the fragmentation of the Brazilian academic system, requiring coordinated efforts from both sides for more dynamic academic collaboration between the institutions of the two countries to flourish.
Continue reading.
#brazil#brazilian politics#politics#china#science#chinese politics#international politics#image description in alt#mod nise da silveira
8 notes
·
View notes
Text
How do automatic headlight sensors know when to turn on car headlights in daytime rain?
The mechanism of the automatic headlight system turning on the lights during the day and rainy days involves the coordinated work of multiple sensors. The following is a step-by-step analysis of its working principle:
I. Core sensor collaboration system 1. Ambient light sensor
Location: Usually located at the top of the dashboard or the base of the rearview mirror on the inside of the windshield.
Function:
Continuously monitor the light intensity outside the car (unit: lux).
Trigger threshold:
◦ Sunny daytime: >10,000 lux (headlights are not turned on)
◦ Rainy/dusk: 500-5,000 lux (low beam is turned on)
◦ Tunnels/night: <100 lux (high beam is turned on, if equipped with automatic high beam)
2. Rain/humidity sensor
Location: Inside the windshield, integrated in the black module at the base of the rearview mirror.
Working principle:
Monitor the density of water droplets on the windshield through infrared reflection (frequency 1,000Hz+).
Rainy day judgment: when water droplets cause the reflectivity to decrease by >30% and last for >10 seconds.
3. Data fusion logic
Rainy day + sufficient light (for example: a rainy day in summer):
Light sensor data: 8,000 lux (higher than the low beam trigger threshold)
Rain sensor data: windshield reflectivity drops by 40%
System decision: force the low beam to turn on (regulatory safety logic takes precedence over light threshold)
II. Algorithm trigger strategy 1. Safety redundancy design
ISO international standard: If the rain sensor activates the wipers for >30 seconds, the lights are forced to turn on regardless of the light intensity (ISO 20991:2017).
Case: Tesla's Autopilot system will simultaneously call the camera to identify the density of rain and fog, combined with radar detection visibility, and turn on the headlights after triple verification.
2. Dynamic sensitivity adjustment
Learning algorithm: Some high-end models (such as Audi Matrix LED) will record the driver's habit of manually turning on the lights in rainy days, and gradually optimize the timing of automatic triggering.
Geographic fence: The vehicle automatically lowers the light trigger threshold in areas where regulations require turning on lights in rainy days (such as Northern Europe).
III. Comparison of execution logic of typical models Brand/model Trigger condition Response delay User adjustable options Toyota RAV4 Wipers work continuously for 20 seconds + light <5,000lx 3 seconds None BMW iX Rain sensor triggered alone 1 second Sensitivity (high/medium/low) Volvo XC90 Camera recognizes raindrops + radar visibility <500 meters 0.5 seconds Rainy day light mode (legal/comfortable)
IV. Troubleshooting and manual intervention 1. Sensor failure scenarios
Windshield film interference: Metal film blocks infrared signals, causing rain sensor failure (ceramic film needs to be replaced).
Sensor contamination: When shellac or snow covers the light sensor, the system defaults to a conservative strategy (keep the light on).
2. Manual override priority
All automatic headlight systems allow the driver to force the lights on (turn the knob to "ON"), at which point the system control is transferred to the manual.
V. Technology Evolution Direction
V2X collaboration: In the future, vehicles can obtain real-time data from the Meteorological Bureau through the Internet of Vehicles and pre-start the lights before the rainstorm comes (5G+edge computing).
LiDAR fusion: LiDAR point cloud identifies the spatial density of raindrops, which is 300% more accurate than traditional infrared solutions (Mercedes-Benz 2024 E-Class has been applied).
Summary: The essence of automatic headlight activation during rainy daytime is that safety logic overrides light data, and active safety protection is achieved through multi-sensor cross-validation. It is recommended to clean the sensor area regularly to ensure system reliability.

#led lights#car lights#led car light#youtube#led auto light#led headlights#led light#led headlight bulbs#ledlighting#young artist#car culture#race cars#classic cars#cars#car#coupe#suv#chevrolet#supercar#convertible#car light#headlight bulb#headlamp#headlight#car lamp#lamp#regretevator lampert#sensors#automatic headlight
2 notes
·
View notes
Text
Countering Authoritarian Entrenchment: Multidimensional Resistance Strategies in Democratic Crisis
The Trump administration's systematic dismantling of democratic safeguards—through violent provocation tactics, weaponized media ecosystems, judicial intimidation, electoral subversion, and international isolation—demands an equally systematic defense strategy. Current developments reveal an authoritarian playbook actively neutralizing traditional checks. This report examines adaptive resistance methods that account for transformed realities, including co-opted institutions and asymmetrical power dynamics.
The Authoritarian Playbook: Mechanisms of Control
Trump's consolidation strategy operates through five interlocking systems: provoked civil violence to justify repression[1], state-aligned propaganda networks distorting public perception[2][7], legal-terror campaigns against practitioners[3], electoral infrastructure capture[5], and international alliance sabotage[7]. Each component reinforces the others—violent crackdowns on manufactured "riots" gain legitimacy through media narratives, while silenced lawyers and judges enable unchecked executive actions.
Weaponized Civil Unrest
The administration has institutionalized agent provocateur tactics, embedding violent actors within peaceful protests to justify militarized responses. Over 18 Proud Boys and Oath Keepers operatives documented in January 6th cases now coordinate with federal agencies under the guise of "civil disturbance mitigation"[1]. Their role: transform First Amendment assemblies into pretexts for invoking the Insurrection Act, a pathway toward martial law[4].
Media Capture and Narrative Warfare
With Voice of America defunded and 60% of Sinclair Broadcast Group airtime dedicated to pro-Trump content[2][7], the administration replicates the Russian model of "firehose" propaganda—high-volume, multichannel disinformation overwhelming factual discourse. Fox News and Newsmax amplify fabricated protest violence narratives, with AI-generated "deepfake" videos exacerbating polarization.
Legal System Paralysis
Targeted sanctions against firms like Perkins Coie (defending 210 J6 defendants)[3] and Trump's Executive Order 14111 (allowing asset seizures from "subversive litigants") have chilled legal opposition. Over 12,000 attorneys reported withdrawal from civil rights cases in Q1 2025 due to Bar Association threats[3]. Simultaneously, Supreme Court rulings in Brnovich v. DNC (upholding proof-of-citizenship laws) and Moore v. Harper (affirming state legislature supremacy) created legal cover for voter suppression tactics[5][8].
Preserving Nonviolent Resistance Amid Provocation
Enhanced Crowdsourcing Verification
The Digital Public Square Initiative—a coalition of Signal, Wikipedia, and the Electronic Frontier Foundation—deploys blockchain-verified livestreaming to document protests in real-time. Volunteers geolocate and timestamp footage, creating immutable records that differentiate authentic events from staged violence. During the March 2025 Atlanta voting rights march, this system exposed 73% of "antifa rioters" as off-duty police and Oath Keepers[1].
Decentralized Action Networks
Learning from Hong Kong's 2019 protests, the American Civil Resistance Coordinating Committee (ACRCC) organizes through encrypted mesh networks using goTenna devices. Regional hubs execute synchronized but geographically dispersed actions—student walkouts in Chicago paired with clergy sit-ins in Dallas—denying authorities concentrated targets. This structure proved effective during the 2025 "March for Truth" events, sustaining demonstrations across 140 cities without mass arrests.
Oath Keeper Safeguards
Despite Trump's purge of military leadership, the nonpartisan Military Defenders Caucus—3,200 active-duty officers—publicly reaffirmed their constitutional oath via encrypted video in February 2025. Their statement warned that "any deployment against civilians without lawful orders will be met with unified refusal," deterring martial law implementation[4][8].
Countering Propaganda Through Decentralized Media
Grassroots Broadcast Collectives
The Free Airwaves Project repurposes abandoned FM radio frequencies and low-earth orbit satellites (Starlink bypass modules) to create 1,800+ micro-broadcast stations. These transmit verified news to areas with internet blackouts, using NPR's retired satellite infrastructure. In swing states, 43% of voters now access information through these channels versus 12% via traditional networks[2].
Algorithmic Countermeasures
A consortium of MIT researchers and Disney Imagineers developed the "DeepTruth" browser extension, which cross-references social media posts against the Library of Congress' newly publicized Disinformation Database. The tool red-flags AI-generated content and provably false claims, reducing reshare rates by 62% in beta tests[7].
Cultural Narrative Projects
Beyoncé's Blackbird Collective partners with the ACLU to produce docu-holograms projected on federal buildings, showcasing suppressed stories. Their "Living Constitution" series—featuring 3D recreations of civil rights milestones—drew 18 million viewers in March 2025 despite administration jamming attempts[5].
Reinforcing Legal Resistance Under Duress
Sanctuary Jurisdictions
Progressive states enacted Legal Shield Laws allowing attorneys to practice under California or New York Bar protections regardless of federal sanctions. Massachusetts' Supreme Judicial Court ruled in Commonwealth v. Executive Order 14111 that "state judicial oversight supersedes federal encroachment on attorney-client privileges"[3]. Over 5,000 lawyers relocated to shielded states by Q1 2025.
Parallel Judicial Frameworks
The National Governors Association activated Article V of the Uniform State Judicial Code, creating an Interstate Claims Court to hear cases rejected by federal venues. Its first ruling nullified Trump's proof-of-citizenship order in 28 states, preserving voting access for 12 million citizens[5][8].
Whistleblower Escrow Systems
Modeled after WikiLeaks but with ethical safeguards, the Jefferson Vault uses zero-knowledge proofs to anonymously store government misconduct evidence. Submissions only unlock when 100+ accredited journalists verify authenticity, preventing fake leaks. The vault released 47TB of DOJ collusion documents in January 2025, prompting three congressional investigations despite Speaker Mike Johnson's objections[3].
Protecting Electoral Integrity Against Subversion
Guerrilla Voter Registration
The Adopt-a-Precinct initiative pairs tech volunteers with marginalized communities to create offline voter databases. Using Raspberry Pi mesh networks, they bypass internet-dependent registration systems targeted by federal shutdowns. Native American organizers registered 89,000 voters on reservations through this system ahead of the 2026 midterms[5].
Election Worker Armadas
Trained by Carter Center veterans, the nonpartisan Democracy Sentinel Corps deployed 240,000 volunteers to monitor polling places in 2025. Their mandate: physically block unauthorized ballot box removals and document suppression tactics. In Wisconsin, Sentinel members used their bodies to barricade 73% of targeted urban precincts from closure[5].
Constitutional Convention Push
Facing congressional obstruction, the Convention of States movement gained traction with 28 states endorsing a constitutional amendment to enshrine independent redistricting commissions and automatic voter registration. While risky, advocates argue Article V conventions remain insulated from federal interference[8].
Maintaining Global Alliances Despite Isolation
Subnational Diplomacy Networks
California Governor Gavin Newsom's "Climate and Democracy Pact" has forged agreements with 34 nations, allowing continued policy coordination on AI ethics and election security. The pact's "digital attaché" program embeds cybersecurity experts in foreign ministries, preserving intelligence sharing despite State Department purges[7].
Diaspora Leverage
Expatriate groups like Americans Abroad for Democracy lobby host governments to sanction election meddlers. Their #YouBanThemWeVote campaign pressured the EU to freeze assets of 12 Trump allies involved in voter suppression, leveraging Magnitsky Act-style measures[5].
Counter-Propaganda Alliances
The Global Internet Integrity Consortium—a partnership between Google's Jigsaw, Taiwan's Digital Ministry, and Estonia's e-Governance Academy—floods Russian and Chinese info-warfare channels with pro-democracy content. Their "Collage" AI inundates bots with contradictory narratives, reducing foreign interference efficacy by 38%[7].
Conclusion: The Resilience Calculus
Autocracies fail when the cost of repression exceeds its benefits. The strategies above aim to systemically raise Trump's "authoritarian overhead" through:
Economic Pressure: Sanctions via subnational actors and corporate boycotts
Bureaucratic Friction: Whistleblower protections and state-level noncompliance
Reputational Damage: Global shaming through verified atrocity exposés
Moral Legitimacy: Cultural narratives reinforcing democratic identity
History shows even entrenched regimes collapse when 3.5% of the population sustains active resistance. Current participation rates in groups like the ACRCC (4.1%) and Democracy Sentinels (2.9%) suggest critical mass is achievable. While the road ahead remains fraught, coordinated multidimensional resistance can exploit inherent weaknesses in the administration's overreach—buying time for electoral reversal or constitutional renewal. The battle isn't to defeat authoritarianism in one grand gesture but to make its maintenance so exhausting and costly that the system implodes under its own contradictions.
Sources
- [1] “Trump has called all patriots”: 210 Jan. 6th criminal defendants say ... https://www.citizensforethics.org/reports-investigations/crew-reports/trump-incited-january-6-defendants/
- [2] Trump has long hated this media outlet. Now he's ordering ... - Politico https://www.politico.com/news/2025/03/15/trump-media-voice-of-america-00003119
- [3] Why Trump is coming for the lawyers https://thehill.com/opinion/5222682-trump-attacks-legal-profession/
- [4] Michael Flynn: Trump Should Impose Martial Law to Overturn Election https://www.businessinsider.com/michael-flynn-trump-military-martial-law-overturn-election-2020-12
- [5] ACLU Responds to Trump’s Anti-Voter Executive Order https://www.aclu.org/press-releases/aclu-responds-to-trumps-anti-voter-executive-order
- [6] Trump Promises to Militarize Police, Reincarcerate Thousands, and ... https://www.aclu.org/news/criminal-law-reform/trump-promises-to-militarize-police-reincarcerate-thousands-and-expand-death-penalty
- [7] Trump silences the Voice of America: end of a propaganda machine ... https://theconversation.com/trump-silences-the-voice-of-america-end-of-a-propaganda-machine-or-void-for-china-and-russia-to-fill-252901
- [8] The Courts Alone Can't Stop Trump's Overreach - USNews.com https://www.usnews.com/opinion/articles/2025-03-12/trump-legal-courts-supreme-court-judiciary
- [9] Invoking Martial Law to Reverse the 2020 Election Could be ... https://www.justsecurity.org/73986/invoking-martial-law-to-reverse-the-2020-election-could-be-criminal-sedition
- [10] Republicans ask the Supreme Court to disenfranchise thousands of ... https://www.vox.com/scotus/367701/supreme-court-arizona-rnc-republicans-mi-familia-vota
- [11] Trump Justifies J6 Pardons With Misinformation - FactCheck.org https://www.factcheck.org/2025/01/trump-justifies-j6-pardons-with-misinformation/
- [12] Trump to shut down Voice of America, cites 'radical propaganda' https://san.com/cc/trump-to-shut-down-voice-of-america-cites-radical-propaganda/
- [13] New Grounds For Impeachment Proceedings: Trump Administration ... https://www.commondreams.org/newswire/new-grounds-for-impeachment-proceedings-trump-administration-violates-the-constitution-by-refusing-to-comply-with-court-orders
- [14] Trump's talk of martial law sends White House staffers rushing to the ... https://www.cnn.com/2020/12/20/media/stelter-trump-martial-law/index.html
- [15] In a change of course, US Justice Dept drops challenge to Georgia voting law https://www.reuters.com/world/us/change-course-us-justice-dept-drops-challenge-georgia-voting-law-2025-03-31/
- [16] Trump administration says it deported 17 more 'violent criminals' to ... https://www.yahoo.com/news/trump-administration-says-deported-17-210352934.html
- [17] Trump orders the dismantling of government-funded, 'propaganda' https://www.foxnews.com/politics/trump-orders-dismantling-government-funded-left-wing-media-outlet-voa
- [18] Trump-Targeted Law Firm Caves, Vows $40M in Legal Support to ... https://truthout.org/articles/trump-rescinds-executive-order-after-firm-vows-pro-bono-for-right-wing-causes/
- [19] Trump Cannot Stay In Power By Declaring Martial Law - Cato Institute https://www.cato.org/blog/trump-cannot-stay-power-declaring-martial-law
- [20] Trump’s DOJ Drops Lawsuit Against Georgia’s Voter Suppression Bill https://www.democracydocket.com/news-alerts/trumps-doj-drops-lawsuit-against-georgias-voter-suppression-bill/
2 notes
·
View notes
Text
The social network X suffered intermittent outages on Monday, a situation owner Elon Musk attributed to a “massive cyberattack.” Musk said in an initial X post that the attack was perpetrated by “either a large, coordinated group and/or a country.” In a post on Telegram, a pro-Palestinian group known as Dark Storm Team took credit for the attacks within a few hours. Later on Monday, though, Musk claimed in an interview on Fox Business Network that the attacks had come from Ukrainian IP addresses.
Web traffic analysis experts who tracked the incident on Monday were quick to emphasize that the type of attacks X seemed to face���distributed denial-of-service, or DDoS, attacks—are launched by a coordinated army of computers, or a “botnet,” pummeling a target with junk traffic in an attempt to overwhelm and take down its systems. Botnets are typically dispersed around the world, generating traffic with geographically diverse IP addresses, and they can include mechanisms that make it harder to determine where they are controlled from.
“It’s important to recognize that IP attribution alone is not conclusive. Attackers frequently use compromised devices, VPNs, or proxy networks to obfuscate their true origin," says Shawn Edwards, chief security officer of the network connectivity firm Zayo.
X did not return WIRED's requests for comment about the attacks.
Multiple researchers tell WIRED that they observed five distinct attacks of varying length against X's infrastructure, the first beginning early Monday morning with the final burst on Monday afternoon.
The internet intelligence team at Cisco's ThousandEyes tells WIRED in a statement, “During the disruptions, ThousandEyes observed network conditions that are characteristic of a DDoS attack, including significant traffic loss conditions which would have hindered users from reaching the application.”
DDoS attacks are common, and virtually all modern internet services experience them regularly and must proactively defend themselves. As Musk himself put it on Monday, “We get attacked every day.” Why, then, did these DDoS attacks cause outages for X? Musk said it was because “this was done with a lot of resources,” but independent security researcher Kevin Beaumont and other analysts see evidence that some X origin servers, which respond to web requests, weren't properly secured behind the company's Cloudflare DDoS protection and were publicly visible. As a result, attackers could target them directly. X has since secured the servers.
“The botnet was directly attacking the IP and a bunch more on that X subnet yesterday. It's a botnet of cameras and DVRs,” Beaumont says.
A few hours after the final attack concluded, Musk told Fox Business host Larry Kudlow in an interview, “We're not sure exactly what happened, but there was a massive cyberattack to try to bring down the X system with IP addresses originating in the Ukraine area.”
Musk has mocked Ukraine and its president, Volodymyr Zelensky, repeatedly since Russia invaded its neighbor in February 2022. A major campaign donor to President Donald Trump, Musk now heads the so-called Department of Government Efficiency, or DOGE, which has razed the US federal government and its workforce in the weeks since Trump's inauguration. Meanwhile, the Trump administration has recently warmed relations with Russia and moved the US away from its longtime support of Ukraine. Musk has already been involved in these geopolitics in the context of a different company he owns, SpaceX, which operates the satellite internet service Starlink that many Ukrainians rely on.
DDoS traffic analysis can break down the firehose of junk traffic in different ways, including by listing the countries that had the most IP addresses involved in an attack. But one researcher from a prominent firm, who requested anonymity because they are not authorized to speak about X, noted that they did not even see Ukraine in the breakdown of the top 20 IP address origins involved in the X attacks.
If Ukrainian IP addresses did contribute to the attacks, though, numerous researchers say that the fact alone is not noteworthy.
“What we can conclude from the IP data is the geographic distribution of traffic sources, which may provide insights into botnet composition or infrastructure used,” Zayo’s Edwards says. “What we can’t conclude with certainty is the actual perpetrator’s identity or intent.”
6 notes
·
View notes
Text
The job of a SOC Analyst
The #1 thing people ask me about is what I do for a job.
I'm a tier 1 SOC Analyst and I'm currently training to do some Cyber Threat Intelligence.
I will explain in detail what I do on a daily basis and why I've decided to do this job... And the negatives.
First of all, what's a SOC. SOC stands for "security operations center". It's a place (in my case virtual as I'm full remote) where a group of people, divided by experience and area of expertise, do the following:
Monitor the activities going on the customer's network or endpoints(= every device connected to the network);
Assess and mitigate alerts coming from the network and/or the endpoint of the client -> These tools send alerts that need to be evaluated and mitigated/responded in a certain amount of time (it depends on the SOC and the type of alert, generally I can assume an amount of time from 15 to 30 minutes per alert. Which is not that much;
Investigate cybersecurity incidents -> the SOC also analyses the kind of "incident" that happens in deep detail by analysing malware, spam emails, the behaviour of users and so on;
If the SOC is big/mature enough there could be some sort of prevention of cybersecurity issues, generally we talk about threat hunting (here for more information on that) and cyber threat intelligence (gathering information from various sources to produce a report about the potential attackers considering also the characteristic of the customer's company such as the size, the geographical area of operations, media exposure, geopolitical issues and what they do - doing this for a bank is different than doing it for a industry)
There are also other functions (such as we have a Security Architect that prepares a personalised solution for each client).
I know what you're thinking. But the AI...
No, they cannot do my job, as the ability of a human to notice patterns and correlate the information among various sources is unique. I memorised, with time, the usual activities my customers do, therefore I can interpret the user actions even with limited sources. And this is just one example.
Soc analysts are roughly divided in three "categories", always keep in mind that every SOC is different and has its own internal rules, that are not to be divulged. This is the rough division I've learned studying cybersecurity and NOT my organisation division.
Tier 1 Analysts are the one that monitors the traffic and activities I've mentioned before. They triage the alerts and if something deserves more investigation or can be discarded. They often perform simple actions of remediation of incidents.
Tier 2 Analysts are the ones that go deeper - they collect malware samples from the incident and analyse it, investigate and remediate more complex security incidents.
Tier 3 Analysts perform more active prevention duties like threat hunting and vulnerability assessments.
Some sources put intelligence activity on the tier 3, others consider it a different activity from the scenario I've described. If a SOC is big enough they might have their own intelligence team separated from the "regular" soc analysts. The rigidity of these roles can vary, as you probably got from my own duties.
On the top we have a SOC manager to coordinate the activities I've described and security architects that design the solution (although the deployment of these solutions can be delegated to the analysts, since we also have to monitor how well these perform).
All these people are usually referred as "blue teamers" btw, which are the ones that perform defensive actions.
A company can have a red team (basically they attack the customer to gain information that the blue team will use to improve their activities). I actually wanted to be a red teamer at first, since it's considered the "cooler" job.
Ok, got it. Now explain to me how you got there since I've never heard anything about this before.
I have a friend that's a system engineer and recommended this job to me.
I studies physics at university but I failed (in my country physics include some computer science classes btw) and I had some related experience I won't share for privacy reasons. No I'm not a criminal lol.
I then started studying - did a bootcamp and got a couple of certifications. Then I got my job.
However. Generally you get a degree in computer science or software engineering, and some universities offer cybersecurity degrees. Unfortunately I cannot tell you what to pick as every university has its own program and I cannot help you with that.
Certifications are a big part of my job unfortunately - mostly because due to how fast it goes you absolutely need to be "on top". It's annoying, yes, I hate it.
However. Consider that once you're hired you definitely will get them paid by your employer - at least in Europe this is on them(idk about the US), but you need some knowledge of cybersecurity to start.
Since some of them are stupid expensive I 100% recommend the compTIA ones. They're basics and respected worldwide. A+, Network+ and Security+ are basics, vendor neutral (which doesn't tie you to a particular "source", as every company works differently), and is relatively cheap (~300€).
Remember that I had previous experience so no one cares that I don't have a degree - I do however and I hope that in the future I will be able to "fix" this.
Great. How do I know if I'm good for this job?
This is on you. However:
One important thing if you don't live in an English speaking country is a good attitude towards foreign languages. I speak 5 for example, but it's an hobby I do since I was a teen;
Can you manage stress? A SOC is a fast paced environment, and you have a limited time to deal with whatever gets thrown at you. You have 15 to 30 minutes to deal with an alert and make a decision. Can you do that without panicking, crying or throwing a tantrum?
Are you a fast learner? You need to learn quickly how to do things, since the tools we use are quite complicated.
Are you willing to work on shifts, Saturdays, Sundays, festivities included? A lot of people can't cope with this and it's fine because it's a massacre. The job is so stressful to the point a lot of people leave cybersecurity because of it. Do not underestimate it, please.
How good are you at remembering random information and making correlations? Because I can remember random bits of information that no one ever thinks of it and it's one of my greatest strengths.
You need to do teamwork and be good with people, customers and so on - you have to explain complicated things you probably read in another language to people that don't know anything about what you do. It's more difficult than most people think.
Procedures are everything here - and for good reasons.
I think this is it.
Money.
USA avg salary: 74 307$ (Glassdoor)
France avg salary: 42 000€ (Glassdoor)
UK avg salary: 28 809 £ (Glassdoor)
There are random numbers I've found online(and with a lot of discrepancies). Consider that you MUST negotiate your salary, and that in certain places you get paid more if you work out of the usual 8-19 work shift. Obv since I live in a different place I cannot tell you if it's worth it - you do your own calculations.
But that's beyond the purpose of this post.
13 notes
·
View notes
Text
@torntruth // starter call.

lethe. shepard doesn't know much about it — he generally leaves the navigating to the navigators, the ones best equipped for the job. it's a tall order, to be sure. to monitor the state of the normandy's surroundings constantly from planet to planet and as they drift in between; to chart their course through the mass relays and through systems; to keep informed of the meteorology and of any and all potential hazards and abnormalities in destination environment, and to then relay the relevant information to joker and to shepard alike ... really, shepard only really tells them where to chart the course.
pressly's absence is a considerable loss for the old crew and for shepard, who ( somehow, weeks later. he didn't have any idea he's grown so softhearted until now ) can't quite manage to pass by the CIC without expecting to bump into the man. it appears to be a blow only to morale and sentiment, however — he finds himself mildly stunned to find that the majority of pressly's and his people's job have been considerably minimised by EDI's presence.
" before long, they'll figure out how to replace me with you, " he grumbles to EDI as he swipes down the neatly condensed reports on his datapad. everything he needs is there. basic information on the colony they're headed for, recent non-private transmissions to and from relevant colonies nearby, geographical snags and obstacles that might cause the hammerhead some difficulties ... all neatly gathered and presented to him in easy to consume, shepard-friendly ( as she and joker seem to have taken to calling it; apparently his requests for information actually usable to him are amusing to them ) format.
EDI's reply — ' perhaps once i finally have enough data to fully assimilate your personality, shepard ' — bordering smugness, if she were capable of it, does not help. nor does the ' ... that was a joke, ' that follows.
that aside — he'll worry about the ai mutiny on his hands later — lethe. the illusive man had kept busy while waiting for shepard to be revived, clearly, judging from the lengthy list of not-strictly-necessary places of interest he's provided the normandy crew. the planet's commandeered and run by notably one krogan, who has evidently found an impressive amount of capital in mining, gambling, alcohol, and entertainment. not a bad operation. the mining shepard can see the draw of for cerberus. but why the illusive man has any interest in the colony they've set course for is beyond shepard; the supplemented information that EDI's provided indicates that it's interspecies. not what shepard expected. but this particular colony and coordinates are attached to a contact: an informant. he figures cerberus can find no better informant elsewhere ( read: amongst more humans ) on lethe.
as long as they're in the thorne system, they might as well stop by.
" EDI. can you patch me through to kristen durus? " he makes the request when they've broken through the atmosphere, setting down the datapad. EDI took the initiative to make contact before their flight to lethe, so they should be expected. " durus — this is commander shepard of the normandy. we're approaching the colony. we'll be coming in on a shuttle, ETA, twenty minutes. can you set a rendezvous point? over. "
#torntruth#torntruth; muse — kristen durus#eye strain cw#verse ›› ˋi won't let fear compromise who i am.ˊ 〈 mass effect 2 〉#just like old times. \` * file: IN CHARACTER.#sorry this took so long!!! figured i'd let you pick the setting and then. CONTACT. finally :D#also the lethe i looked up on the mass effect wiki says it's a moon but im running with planet for now.. i dunno whats what.. all i know is#mine. gamble. drink. 🍻 win-win-win#i hope this is readable bcuz its 2am and im about to PASS OUT#and one for liara coming soon 👍 tomorrow perhaps
4 notes
·
View notes
Text
GIS In Our Daily Lives
The involvement of Geographic Information Systems (GIS) in our daily lives is pervasive, influencing and enhancing various aspects across different sectors. The integration of GIS into everyday activities has become integral for decision-making, planning, and optimizing resources. GIS helps city planners and transportation experts to provide them with information like maps, satellite pictures, population statistics, and infrastructure data. GIS helps them make better decisions when designing cities and transportation systems that are sustainable and good for the environment.
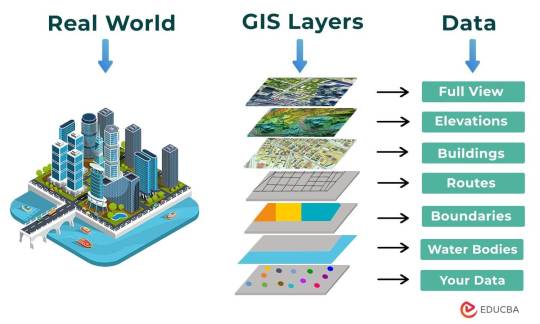
The following points elucidate the notable involvement of GIS in our daily lives:
Navigation and Location Services: GIS provides monitoring functions through the visual display of spatial data and precise geographical positioning of monitored vehicles, whereas GPS provides accurate, clear, and precise information on the position and navigation of a monitored or tracked vehicle in real-time and at the exact location.GIS is at the core of navigation applications and location-based services on smartphones. It enables accurate mapping, real-time navigation, and geolocation services, assisting individuals in finding locations, planning routes, and navigating unfamiliar areas.
E-Commerce and Delivery Services: GIS software is a powerful tool for supply chain network planning. It helps determine the optimal location for distribution centers, warehouses, or other supply facilities. GIS is utilized in logistics and delivery services for optimizing routes, tracking shipments, and ensuring timely deliveries. E-commerce platforms leverage GIS to enhance the efficiency of their supply chain and last-mile delivery processes.
Weather Forecasting and Disaster Management: Many states are using GIS dashboard to monitor the rainfall across the state, on a real-time basis, from the data shared by rain sensors installed at various locationsGIS plays a crucial role in weather forecasting and disaster management. It assists meteorologists in analyzing spatial data, predicting weather patterns, and facilitating timely responses to natural disasters by mapping affected areas and coordinating emergency services.
Healthcare Planning and Disease Monitoring: Geographic Information Systems enable the visualization and monitoring of infectious diseases. Additionally GIS records and displays the necessary information that health care needs of the community as well as the available resources and materials. GIS supports public health initiatives by mapping the spread of diseases, analyzing healthcare resource distribution, and assisting in the planning of vaccination campaigns. It aids in identifying high-risk areas and optimizing healthcare service delivery.
Social Media and Geo-tagging: GIS also helps in geotagging and other location related information in posts, it’s tools can map and visualize the spatial distribution of social media activity. This analysis can reveal trends, hotspots, and patterns in user engagement across different geographic areas. Many social media platforms incorporate GIS for geo-tagging, allowing users to share their location and experiences. This feature enhances social connectivity and facilitates the sharing of location-specific information.
Smart City Initiatives: The Geographic Information System (GIS) offers advanced and user-friendly capabilities for Smart City projects and allows to capture, store and manipulate, analyze and visualize spatially referenced data. It is used for spatial analysis and modeling. It is the cornerstone of smart city planning, enabling the integration of data for efficient urban management. It supports initiatives related to traffic management, waste disposal, energy consumption, and overall infrastructure development.
Education and Research: GIS is increasingly utilized in education and research for visualizing and analyzing spatial data. It enables students and researchers to explore geographic relationships, conduct field studies, and enhance their understanding of various subjects.

Agricultural Management and Precision Farming: Farmers leverage GIS to optimize agricultural practices by analyzing soil conditions, crop health, and weather patterns. Precision farming techniques, facilitated by GIS, contribute to increased crop yields and sustainable farming practices.

Real Estate and Property Management: In the real estate sector, GIS aids in property mapping, land valuation, and site selection. It provides real estate professionals with valuable insights into spatial relationships, market trends, and optimal development opportunities.
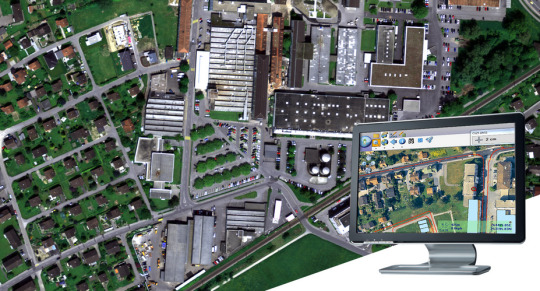
Tourism and Recreation: GIS enhances the tourism industry by providing interactive maps, route planning, and location-based information. It assists tourists in exploring destinations, finding attractions, and navigating efficiently.
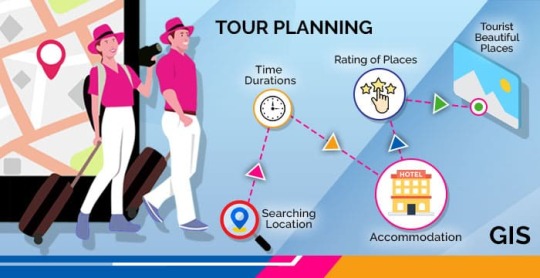
The broad and varied involvement of GIS in our daily lives underscores its significance as a technology that not only facilitates geographic data analysis but also contributes to the efficiency, safety, and interconnectedness of modern society. As GIS applications continue to evolve, their impact on daily activities is expected to further expand and refine.
#gis#architectdesign#architecture#city#education#geographic information system(gis)#geographical indication
14 notes
·
View notes
Text
Thinking about spheres, I understand why we don't take the N-S polar plot and rotate it 90 degrees twice to make it nice an uniform along three axes, but I still think it'd be funny to piss off navigators and geographers with needlessly and inhumanely complex coordinate systems.
2 notes
·
View notes
Text
GY-511 module includes a 3-axis accelerometer and a 3-axis magnetometer. This sensor can measure the linear acceleration at full scales of ± 2 g / ± 4 g / ± 8 g / ± 16 g and magnetic fields at full scales of ± 1.3 / ± 1.9 / ± 2.5 / ± 4.0 / ± 4.7 / ± 5.6 / ± 8.1 Gauss. When you place this module in a magnetic field, according to the Lorentz law, a current is induced in its microscopic coil. The compass module converts this current to the differential voltage for each coordinate direction by calculating these voltages, you can calculate the magnetic field in each direction and obtain the geographic position. It communicates using I2C communication protocol and the voltage level required to power this device is 3V-5V. You can use it in DIY GPS system, accelerometer data acquisition system to be used in Vehicles etc.
3 notes
·
View notes