#IoT vulnerabilities
Explore tagged Tumblr posts
Text
A History of Cybersecurity
in the Twenty-First Century 🧠 TL;DR – A History of Cybersecurity in the 21st Century 🔐💻 🔍 Overview:From the early 2000s to the 2020s, cybersecurity has evolved dramatically in response to increasingly sophisticated threats. What started with experimental worms has escalated into ransomware, nation-state cyber warfare, and AI-powered attacks. 📅 2000s – The Worm Era 🪱 Famous viruses: ILOVEYOU,…
#21st century cyber threats#AI in cybersecurity#APTs#cloud security#Colonial Pipeline attack#cyber defense evolution#cybercrime trends#cybersecurity history#cybersecurity statistics#cybersecurity timeline#cyberwarfare#evolution of cybersecurity#future of cybersecurity#IoT vulnerabilities#major data breaches#mobile malware#nation-state cyberattacks#Patch Tuesday#phishing scams#ransomware as a service#ransomware attacks#SIEM systems#Stuxnet#supply chain attacks#worm era
0 notes
Text
Cel mai mare atac DDoS din istorie: 5.6 Tbps – Escaladarea amenințărilor cibernetice în 2024
Pe 29 octombrie 2024, a fost înregistrat cel mai mare atac DDoS (Distributed Denial of Service) din istorie, atingând un volum impresionant de 5.6 Tbps. Lansat de o variantă a infamului botnet Mirai, atacul a vizat un furnizor de servicii Internet (ISP) din Asia de Est și a durat doar 80 de secunde. Acest incident marchează un nou prag în evoluția atacurilor cibernetice, subliniind complexitatea…
#2024 cybersecurity#5.6 Tbps#atac DDoS#atacuri cibernetice#automated defense#bam#botnet Mirai#Cloudflare#Cloudflare defense#cyber attack prevention#cyber defense#cyber resilience#cyber threats#cybersecurity trends#DDoS mitigation#DDoS record#DDoS statistics#diagnoza#Internet of Things#Internet security#IoT#IoT vulnerabilities#largest DDoS attack#Mirai botnet#network security#protecție automatizată#roman#securitate cibernetică#securitate IT#UDP flood
0 notes
Photo
If something you own can be remotely disabled - intentionally or not - by a third party, you don’t own it, you’re renting it.
Maybe rent is free!
But someday the person on the other end of that equation is going to either a) up your rent to increase profits, b) sell to someone who will up your rent to increase profits or c) go out of business and take your access with them. This is a feature, not a bug, of the endless-growth model. “Internet activated” means “remote kill switch”.
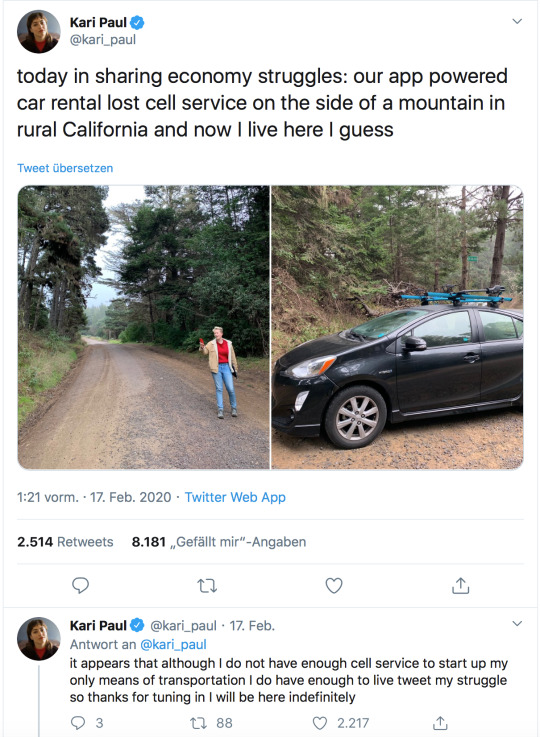
Welcome to the future, where you don’t own anything and the stuff you rent stops working once your phone has no signal.
#not even getting into the massive security vulnerabilities most IOT devices represent#if it can be accessed remotely#*anyone* could access it remotely#and the moment the software team stops producing security patches for your model of smart fridge#it becomes a liability
172K notes
·
View notes
Text

Embrace the future of supply chains with Industry 4.0! 🚀 Explore innovative strategies to secure smart supply chains and build cyber resilience in an interconnected world. 🌐 Safeguard your operations and stay ahead in the digital era!
#Smart supply chain security#Cyber resilience strategies#Industry 4.0 cybersecurity#IoT vulnerabilities in supply chains#Blockchain in supply chain security#Supply chain risk management#Cyber threats in logistics
0 notes
Text
Security Update: A Recent Assault Exposes 95% Accurate Capture of Typed Content
In Las Vegas, the annual Black Hat and Defcon security conferences play host to hackers and researchers who unveil their latest discoveries. This year’s kickoff was particularly noteworthy. A researcher has presented potential evidence suggesting that spikes in radiation recorded by sensors at the Chernobyl nuclear facility following Russia’s 2022 invasion of Ukraine might have been manipulated.…
View On WordPress
#AI#Black Hat#Chernobyl#cybersecurity#data privacy#Defcon#discoveries#Google search results#hacking#HIPAA#Intel chips#IoT devices#safety#security news#technology#threats#vulnerabilities#Yandex
1 note
·
View note
Text
A little explainer on what happened with AO3:
Basically, someone or a group of someones decided to levy a DDoS attack. What this means is that they created a botnet (network of devices controlled by a bot, usually run in the background of an unsecured IoT device or computer being used for other things. Think data mining) to flood the servers with false requests for service.
What this does mean: AO3 might go back down, if the attack is relaunched. These types of attacks are usually used against businesses where traffic = money, thereby costing a company money. This isn't really an issue here since AO3 is entirely donation and volunteer based.
What this doesn't mean: stories, bookmarks, etc will be deleted and your anonymously published works will be linked back to you. No vulnerable points are breached during this process, so unless this group ends up doing something else, no data breaches will happen. You are safe, your content is safe.
#if you want any more of a breakdown on how this works lmk!#credentials: im a compsci major cyber security minor entering my senior year#ao3#computer science#cyber security
2K notes
·
View notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text
Author: CrimethInc. Topic: technology
“The future is already here,” Cyberpunk pioneer William Gibson once said; “it’s just not very evenly distributed.” Over the intervening decades, many people have repurposed that quote to suit their needs. Today, in that tradition, we might refine it thus: War is already here—it’s just not very evenly distributed.
Never again will the battlefield be just state versus state; it hasn’t been for some time. Nor are we seeing simple conflicts that pit a state versus a unitary insurgent that aspires to statehood. Today’s wars feature belligerents of all shapes and sizes: states (allied and non-allied), religious zealots (with or without a state), local and expatriate insurgents, loyalists to former or failing or neighboring regimes, individuals with a political mission or personal agenda, and agents of chaos who benefit from the instability of war itself. Anyone or any group of any size can go to war.
The increased accessibility of the technology of disruption and war[1] means the barrier to entry is getting lower all the time. The structure of future wars will sometimes feel familiar, as men with guns murder children and bombs level entire neighborhoods—but it will take new forms, too. Combatants will manipulate markets and devalue currencies. Websites will be subject to DDoS attacks and disabling—both by adversaries and by ruling governments. Infrastructure and services like hospitals, banks, transit systems, and HVAC systems will all be vulnerable to attacks and interruptions.
In this chaotic world, in which new and increasing threats ceaselessly menace our freedom, technology has become an essential battlefield. Here at the CrimethInc. technology desk, we will intervene in the discourse and distribution of technological know-how in hopes of enabling readers like you to defend and expand your autonomy. Let’s take a glance at the terrain.
Privacy
The NSA listens to, reads, and records everything that happens on the internet.
Amazon, Google, and Apple are always listening[2] and sending some amount[3] of what they hear back to their corporate data centers[4]. Cops want that data. Uber, Lyft, Waze, Tesla, Apple, Google, and Facebook know your whereabouts and your movements all of the time. Employees spy on users.
Police[5] want access to the contents of your phone, computer, and social media accounts—whether you’re a suspected criminal, a dissident on a watch list, or an ex-wife.
The business model of most tech companies is surveillance capitalism. Companies learn everything possible about you when you use their free app or website, then sell your data to governments, police, and advertisers. There’s even a company named Palantir, after the crystal ball in The Lord of the Rings that the wizard Saruman used to gaze upon Mordor—through which Mordor gazed into Saruman and corrupted him.[6] Nietzsche’s famous quote, “When you look long into an abyss, the abyss also looks into you,” now sounds like a double transcription error: surely he didn’t mean abyss, but app.
Security
Self-replicating malware spreads across Internet of Things (IoT) devices like “smart” light bulbs and nanny cams, conscripting them into massive botnets. The people who remotely control the malware then use these light bulbs and security cameras to launch debilitating DDoS[7] attacks against DNS providers, reporters, and entire countries.
Hackers use ransomware to hold colleges, hospitals, and transit systems hostage. Everything leaks, from nude photos on celebrities’ phones to the emails of US political parties.
Capital
Eight billionaires combined own as much wealth as the poorest 50% of the world’s population. Four of those eight billionaires are tech company founders.[8] Recently, the President of the United States gathered a group of executives to increase collaboration between the tech industry and the government.[9]
The tech industry in general, and the Silicon Valley in particular, has a disproportionately large cultural influence. The tech industry is fundamentally tied to liberalism and therefore to capitalism. Even the most left-leaning technologists aren’t interested in addressing the drawbacks of the social order that has concentrated so much power in their hands.[10]
War
Nation states are already engaging in cyber warfare. Someone somewhere[11] has been learning how to take down the internet.
Tech companies are best positioned to create a registry of Muslims and other targeted groups. Even if George W. Bush and Barack Obama hadn’t already created such lists and deported millions of people, if Donald Trump (or any president) wanted to create a registry for roundups and deportations, all he’d have to do is go to Facebook. Facebook knows everything about you.
The Obama administration built the largest surveillance infrastructure ever—Donald Trump’s administration just inherited it. Liberal democracies and fascist autocracies share the same love affair with surveillance. As liberalism collapses, the rise of autocracy coincides with the greatest technical capacity for spying in history, with the least cost or effort. It’s a perfect storm.
This brief overview doesn’t even mention artificial intelligence (AI), machine learning, virtual reality (VR), augmented reality (AR), robots, the venture capital system, or tech billionaires who think they can live forever with transfusions of the blood of young people.
Here at the tech desk, we’ll examine technology and its effects from an anarchist perspective. We’ll publish accessible guides and overviews on topics like encryption, operational security, and how to strengthen your defenses for everyday life and street battles. We’ll zoom out to explore the relation between technology, the state, and capitalism—and a whole lot more. Stay tuned.
Footnotes
[1] A surplus of AK-47s. Tanks left behind by U.S. military. Malware infected networked computer transformed into DDoS botnets. Off the shelf ready to execute scripts to attack servers.
[2] Amazon Echo / Alexa. Google with Google Home. Apple with Siri. Hey Siri, start playing music.
[3] What, how much, stored for how long, and accessible by whom are all unknown to the people using those services.
[4] Unless you are a very large company, “data center” means someone else’s computer sitting in someone else’s building.
[5] Local beat cops and police chiefs, TSA, Border Patrol, FBI… all the fuckers.
[6] Expect to read more about Palantir and others in a forthcoming article about surveillance capitalism.
[7] Distributed Denial of Service. More on this in a later article, as well.
[8] Bill Gates, Jeff Bezos, Mark Zuckerberg, Larry Ellison. In fact, if you count Michael Bloomberg as a technology company, that makes five.
[9] In attendance: Eric Trump. Brad Smith, Microsoft president and chief legal officer. Jeff Bezos, Amazon founder and CEO. Larry Page, Google founder and Alphabet CEO. Sheryl Sandberg, Facebook COO. Mike Pence. Donald Trump. Peter Thiel, venture capitalist. Tim Cook, Apple CEO. Safra Catz, Oracle CEO. Elon Musk, Tesla CEO. Gary Cohn, Goldman Sachs president and Trump’s chief economic adviser. Wilbur Ross, Trump’s commerce secretary pick. Stephen Miller, senior policy adviser. Satya Nadella, Microsoft CEO. Ginni Rometty, IBM CEO. Chuck Robbins, Cisco CEO. Jared Kushner, investor and Trump’s son-in-law. Reince Priebus, chairman of the Republican National Committee and White House chief of staff. Steve Bannon, chief strategist to Trump. Eric Schmidt, Alphabet president. Alex Karp, Palantir CEO. Brian Krzanich, Intel CEO.
[10] We’ll explore this more in a later article about “The California Ideology.”
[11] Probably a state-level actor such as Russia or China.
#technology#Privacy#Security#Capital#War#anarchism#anarchy#anarchist society#practical anarchy#practical anarchism#resistance#autonomy#revolution#communism#anti capitalist#anti capitalism#late stage capitalism#daily posts#libraries#leftism#social issues#anarchy works#anarchist library#survival#freedom
8 notes
·
View notes
Note
Unpopular Opinion: Island of the Slaughtered doesn't make much sense to me honestly... I don't hate it, but the serial killer wouldn't last a day after there's revealed to be one on the island... Because Chef is a psycho that probably went to war and would snap the killer like a twig... Or Chef and Chris would get guns and shoot the killer down... Also, some of the contestants are strong enough to take down wild animals... The killer wouldn't stand a chance against their combined forces... Plus in canon, Chris and Chef did try to save Gwen from a killer (and Gwen defeated the killer)! XD
Island of the Slaughtered was actually what initially drew me back in to Total Drama as a whole, which is ironic because the AU itself kind of got overshadowed by the source material for me.
I like the concept, and the execution is really good too, but I haven't really interacted with the AU at all besides following the Tiktok uploads when they dropped last year. So please excuse me if anything I say here is inaccurate.
But I'm fairly certain that a pivotal plot point of the AU itself is the fact that both Chris and Chef abandon the campers on the island at the first sign of foul play; Chef wouldn't be there to fight off the killer. And that's not exactly out of character for them either- both Chris and Chef are shown throughout canon to not care for the safety and wellbeing of the contestants, and the two of them would believably prioritise their own wellbeing over the campers' survival.
And as far as the strong contestants go, the only characters in Island who would really stand a chance against an active serial killer would be the likes of Eva, Izzy and maybe Duncan- who all survive the massacre because the killer never targets them. I don't know if that's a sign of intelligence on the killer's part or pure coincidence, but it's true nonetheless.
Courtney later shows off her physical prowess in Action, but throughout Island there's nothing to indicate that she could take on a serial killer alone. Since the AU is based in the canon of Island, she doesn't count as a "strong" camper. In the same vein, DJ is very strong, but he's also a 'gentle giant' who's hesitant to cause physical harm to anyone- he wouldn't have the courage to confront the killer.
In the AU itself, the killer works more as an ambush predator than your stereotypical "hunt and kill" murderer; the only time a contestant is ever killed is when they stray from the pack. A huge aspect of this AU is "safety in numbers", the only time someone ever dies is when they're alone and/or in a vulnerable position. This implies that the killer themself is never too far away from the cast; they're always watching, hidden in the shadows, waiting for an opportunity to pick off the weakest links as they stray too far from the safety of their group.
Would it have made more sense for the group to attack the killer as a united front (allowing the likes of Eva, Izzy and Duncan to subdue/kill them in turn)? Probably. But at the end of the day, these are frightened teenagers- they're not going to think logically when they're being hunted for sport. They're going to follow the safest route of their continued survival, which in this case is remaining together as a tight knit group and waiting to be rescued from the island.
I, personally, think the plot of the AU makes a lot of sense when you consider the above factors. And, of course, because it's a Horror AU- you'd need to suspend a lot of the cartoon logic to make it somewhat believable, which includes the fact that Gwen canonically 'takes down' the real killer by insulting him. That kind of stuff wouldn't fit the tone of the IotS AU.
Not that I'm saying you have to like it. You're entitled to your opinion! This is just how I understand the AU.
#now that i'm thinking about it i should probably read through iots again#it was a really cool and unique concept at the time! plus the art was stunning#total drama#island of the slaughtered#ophe rambling#meta analysis#others' hot takes#replies
36 notes
·
View notes
Text

Semiconductors: The Driving Force Behind Technological Advancements
The semiconductor industry is a crucial part of our modern society, powering everything from smartphones to supercomputers. The industry is a complex web of global interests, with multiple players vying for dominance.
Taiwan has long been the dominant player in the semiconductor industry, with Taiwan Semiconductor Manufacturing Company (TSMC) accounting for 54% of the market in 2020. TSMC's dominance is due in part to the company's expertise in semiconductor manufacturing, as well as its strategic location in Taiwan. Taiwan's proximity to China and its well-developed infrastructure make it an ideal location for semiconductor manufacturing.
However, Taiwan's dominance also brings challenges. The company faces strong competition from other semiconductor manufacturers, including those from China and South Korea. In addition, Taiwan's semiconductor industry is heavily dependent on imports, which can make it vulnerable to supply chain disruptions.
China is rapidly expanding its presence in the semiconductor industry, with the government investing heavily in research and development (R&D) and manufacturing. China's semiconductor industry is led by companies such as SMIC and Tsinghua Unigroup, which are rapidly expanding their capacity. However, China's industry still lags behind Taiwan's in terms of expertise and capacity.
South Korea is another major player in the semiconductor industry, with companies like Samsung and SK Hynix owning a significant market share. South Korea's semiconductor industry is known for its expertise in memory chips such as DRAM and NAND flash. However, the industry is heavily dependent on imports, which can make it vulnerable to supply chain disruptions.
The semiconductor industry is experiencing significant trends, including the growth of the Internet of Things (IoT), the rise of artificial intelligence (AI), and the increasing demand for 5G technology. These trends are driving semiconductor demand, which is expected to continue to grow in the coming years.
However, the industry also faces major challenges, including a shortage of skilled workers, the increasing complexity of semiconductor manufacturing and the need for more sustainable and environmentally friendly manufacturing processes.
To overcome the challenges facing the industry, it is essential to invest in research and development, increase the availability of skilled workers and develop more sustainable and environmentally friendly manufacturing processes. By working together, governments, companies and individuals can ensure that the semiconductor industry remains competitive and sustainable, and continues to drive innovation and economic growth in the years to come.
Chip War, the Race for Semiconductor Supremacy (2023) (TaiwanPlus Docs, October 2024)
youtube
Dr. Keyu Jin, a tenured professor of economics at the London School of Economics and Political Science, argues that many in the West misunderstand China’s economic and political models. She maintains that China became the most successful economic story of our time by shifting from primarily state-owned enterprises to an economy more focused on entrepreneurship and participation in the global economy.
Dr. Keyu Jin: Understanding a Global Superpower - Another Look at the Chinese Economy (Wheeler Institute for Economy, October 2024)
youtube
Dr. Keyu Jin: China's Economic Prospects and Global Impact (Global Institute For Tomorrow, July 2024)
youtube
The following conversation highlights the complexity and nuance of Xi Jinping's ideology and its relationship to traditional Chinese thought, and emphasizes the importance of understanding the internal dynamics of the Chinese Communist Party and the ongoing debates within the Chinese system.
Dr. Kevin Rudd: On Xi Jinping - How Xi's Marxist Nationalism Is Shaping China and the World (Asia Society, October 2024)
youtube
Tuesday, October 29, 2024
#semiconductor industry#globalization#technology#innovation#research#development#sustainability#economic growth#documentary#ai assisted writing#machine art#Youtube#presentation#discussion#china#taiwán#south korea
7 notes
·
View notes
Text
The top five targeted industries are technology (Bad Bots comprise 76% of its internet traffic); gaming (29% of traffic); social media (46%), e-commerce (65%), and financial services (45%). If a bot fails in its purpose, there is a growing tendency for the criminals to switch to human operated fraud farms. Arkose estimates there were more than 3 billion fraud farm attacks in H1 2023. These fraud farms appear to be located primarily in Brazil, India, Russia, Vietnam, and the Philippines.
The growth in the prevalence of Bad Bots is likely to increase for two reasons: the arrival and general availability of artificial intelligence (primarily gen-AI), and the increasing business professionalism of the criminal underworld with new crime-as-a-service (CaaS) offerings.
From Q1 to Q2, intelligent bot traffic nearly quadrupled. “Intelligent [bots] employ sophisticated techniques like machine learning and AI to mimic human behavior and evade detection,” notes the report (PDF). “This makes them skilled at adaptation as they target vulnerabilities in IoT devices, cloud services, and other emerging technologies.” They are widely used, for example, to circumvent 2FA defense against phishing.
Separately, the rise of artificial intelligence may or may not relate to a dramatic rise in ‘scraping’ bots that gather data and images from websites. From Q1 to Q2, scraping increased by 432%. Scraping social media accounts can gather the type of personal data that can be used by gen-AI to mass produce compelling phishing attacks. Other bots could then be used to deliver account takeover emails, romance scams, and so on. Scraping also targets the travel and hospitality sectors.
More at the link.
2 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
Building Safer Cities: How Advanced Switchgear Is Powering the Future

Switchgear refers to the combination of electrical disconnect switches, fuses, and circuit breakers used to control, protect, and isolate electrical equipment. In simple words: it’s the shield that protects the power network from overloads, faults, and blackouts.
Without high-quality switchgear, cities would face:
· Frequent power failures
· Increased risk of electrical fires
· Equipment damage
· Unsafe environments for residents and businesses
In today’s urban landscape, switchgear isn’t just an accessory — it’s a critical lifeline for energy security and public safety.
How Advanced Switchgear is Shaping Safer Cities
Thanks to major technological advancements, switchgear is no longer static and reactive. Modern switchgear systems are smart, dynamic, and preventative. Here’s how they are transforming cities:
1. Real-Time Monitoring and Fault Detection
Smart switchgear comes equipped with IoT sensors and digital monitoring systems that detect faults in real time. Instead of waiting for a catastrophic failure, the system identifies weak points early — enabling quick, preventive maintenance.
Impact: Reduced blackouts, faster repair times, safer living and working environments.
2. Automated Shutdowns During Emergencies
In critical events like fires, short circuits, or system overloads, automated switchgear can instantly isolate the affected section. This targeted shutdown prevents the spread of danger and keeps the rest of the city powered.
👉 Impact: Enhanced public safety, minimized risk of widespread outages.
3. Supporting Renewable Energy Integration
As cities shift toward renewable energy sources (solar, wind, hydro), modern switchgear is designed to handle these variable inputs seamlessly. It balances load fluctuations and ensures grid stability, even when energy production varies hour by hour.
👉 Impact: Cleaner cities without sacrificing reliability.
4. Enhanced Energy Efficiency
Advanced switchgear minimizes energy losses during transmission and distribution. With features like optimized load management and energy analytics, cities can operate their power grids more sustainably and economically.
👉 Impact: Lower energy costs, greener urban spaces.
Why Upgrading Switchgear is Essential for the Cities of Tomorrow
The future city will be:
· More populated
· More digitalized
· More energy-demanding
Legacy power systems cannot keep up with this growth. Old switchgear is more vulnerable to faults, inefficiency, and even cyberattacks. Modern, advanced switchgear not only provides higher protection but also future-proofs cities against evolving challenges.
Investing in advanced switchgear means investing in:
· Public safety
· Economic stability
· Environmental responsibility
· Smart infrastructure development
Conclusion: Powering a Safer, Smarter Future
As we envision smarter, greener, and safer cities, we must pay attention to the systems that keep the lights on — and keep people safe. Advanced switchgear stands at the front line of this transformation, quietly ensuring that progress doesn’t come at the cost of safety.
Whether you’re an urban planner, an electrical engineer, or a business owner — prioritizing the right switchgear solutions is key to building cities ready for the challenges of tomorrow.
Looking for world-class switchgear products and accessories? Al Taqwa Electrical and Building Materials offers cutting-edge solutions trusted by industries across the world.
#electrical#electrical equipment#electrical supplies#building#building materials#oman#muscat#switchgear
3 notes
·
View notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes