#Nmap tutorial
Explore tagged Tumblr posts
Text
Nmap Ping Sweep: Home Lab Network Ping Scan
Nmap Ping Sweep: Home Lab Network Ping Scan @vexpert #vmwarecommunities #100daysofhomelab #homelab #Nmaptutorial #Networkscanning #Pingsweepguide #Nmapcommandexamples #HostdiscoverywithNmap #Networksecurity #NmaponKaliLinux #TCPSYNACKpackets #ICMPscanning
There is perhaps not a better known network scan tool for cybersecurity than Nmap. It is an excellent tool I have used for quite some time when you have a rogue device on a network and you want to understand what type of device it is. Nmap provides this functionality along with many others. Let’s look at the Nmap Ping Sweep and see how we can use it as a network vulnerability ping scan to…

View On WordPress
#Host discovery with Nmap#ICMP scanning#Local Ethernet network scanning#network scanning#network security#Nmap command examples#Nmap on Kali Linux#Nmap tutorial#Ping sweep guide#TCP SYN/ACK packets
0 notes
Text
👋 Introduction:
Hey everyone! I’m Preethi, as i'm in my first year of information technology i'm doing additional course in cyber security as a curious mind and a beginner in the exciting world of cybersecurity. As someone who’s always been fascinated by how technology works (and how it can be broken—ethically, of course 😄), I decided to dive into ethical hacking and explore the world of digital defense.
This is my first blog post, and I’m super excited to take you along on this journey. Whether you're a beginner like me or just cyber-curious, I hope my posts will inspire and inform you!
🔍 Why Cybersecurity?
Cybersecurity is not just about coding or fixing viruses—it's about protecting people. It’s like being a digital superhero, and the idea of stopping hackers from causing harm really clicked with me.
Also, let’s be honest… learning how hackers think is so cool. 😎
💻 Why Ethical Hacking?
One thing that drew me to ethical hacking specifically is the idea that hackers can be the “good guys” too. As an ethical hacker, you're actually hired to find vulnerabilities and patch them before malicious hackers can exploit them.
In a world where data is constantly at risk, ethical hackers are like digital detectives—stopping crimes before they happen.
🔓 What I Discovered in My First Click
It all started with a random click.
I was Googling something, just as I always do, when I noticed a new icon in the “Tools” section. Out of curiosity, I clicked it. And that simple action led me down a rabbit hole of new concepts, tools, and ideas.
I found myself reading about ethical hacking, DDoS attacks, and encryption algorithms. I realized cybersecurity was more than just tech jargon—it was about understanding how the digital world works and how to protect it. That one click sparked a fire, and I knew I had to learn more.
🛠️ First Tools I Came Across
Wireshark: This tool allowed me to capture network traffic and view the data packets passing through the network. It felt like a magic window into the digital world!
Nmap: A powerful network scanning tool. I learned how to scan for vulnerabilities in a network and assess its security posture. It was eye-opening to see how easily someone could breach a system if it's not properly secured.
💭 What’s Next for Me
Since that initial click, I’ve been diving deep into cybersecurity, learning everything from network security to cryptography. I’m currently doing an internship related to cybersecurity, where I’m getting hands-on experience and developing my skills.
I’ll be sharing everything I learn along the way. Whether it's tutorials on DDoS attacks or tips for securing personal data, I want to document my journey so you can join me in this exciting field.
🔐 Learning Cryptography and Encryption
One of my next steps is exploring cryptography. The idea that encryption can protect data in the digital world fascinates me. It’s the backbone of secure online transactions, messaging apps, and pretty much every secure login system we use today.
💬 Advice to Other Curious Clickers
If you’ve ever clicked something just because it looked interesting—good. That curiosity is your superpower. 💥
I had no idea one tiny tap on an icon would lead me into the world of cybersecurity, but here I am—exploring, learning, and loving it. So don’t ignore those little sparks. Whether it’s a weird-looking tool, a techy term you don’t understand, or a random blog post... click it. Explore it. Question it.
You don’t need to be an expert to start—you just need to be curious.
So to all the curious clickers out there: Keep clicking. Keep learning. Who knows? You might just discover your passion—just like I did. 💫
✨ Conclusion:
This is only the beginning of my journey, and I’m excited to see where my clicks take me next. I’ll keep exploring, experimenting, and sharing what I learn with you all. If you’re new to cybersecurity—or just curious—come along for the ride. Let’s discover this digital world together!
1 note
·
View note
Text
youtube
If you're securing your network or exploring vulnerabilities, nmap is essential for cybersecurity and IT professionals.
🔍 This 60-second, beginner-friendly, silent tutorial shows how to install and run a basic scan on Linux.
0 notes
Text
Real-World Security Auditing: Step-by-Step Guide
Introduction Security auditing is crucial for identifying vulnerabilities and ensuring compliance in any system. This tutorial guides you through a structured approach, combining theoretical knowledge with practical code examples to enhance your security auditing skills. You will learn how to conduct audits using tools like Nmap and Arachni, and understand best practices for optimization and…
0 notes
Video
youtube
🚀 HACKING with Parrot OS in Docker! (EASY Windows 11 Setup) 🚀 hashtag#ParrotOS hashtag#Docker hashtag#HackingTutorial hashtag#EthicalHacking hashtag#NmapDemo In this video, I’ll show you how to set up Parrot OS, a powerful Linux distro for ethical hacking and cybersecurity, inside a Docker container on Windows 11. This lightweight setup is perfect for running hacking tools without the need for bulky virtual machines! 👉 Here’s what you’ll learn in this video: How to install Docker on Windows 11. Pulling and running the Parrot OS container. We are troubleshooting common Docker issues, which include running containers with the --privileged flag. We are installing tools such as Nmap in the Parrot OS container. This is a hands-on demonstration of utilizing Nmap for conducting network scans. 💡 Key Commands from the Video: Pull the Parrot OS Docker image: bash Copy code docker pull parrotsec/core Run the container with elevated privileges to troubleshoot tool permissions. css Copy code docker run -it --privileged --name parrotos parrotsec/core bash Install Nmap inside the container: sql Copy code apt update && apt install nmap -y Scan a target using Nmap: Copy code nmap scanme.nmap.org 🎯 By the end of this tutorial, you’ll have a fully functional Parrot OS container with the tools you need to explore cybersecurity tasks securely and efficiently! ⚠️ Important Reminder: Always use ethical practices and only scan systems you own or have permission to test. 📌 Like, comment, and subscribe for more practical tutorials on hacking, cybersecurity, and tech tools! Let me know in the comments if you want me to cover other tools or topics next! ✨❤️ Your Support Ignites Our Passion! ❤️✨ 🍵 BuyMeACoffee: https://lnkd.in/g2xVtifJ ▶️ YouTube: https://lnkd.in/gjHhgH6Z 🎵 TikTok: https://lnkd.in/giqyvF57 🌐 Website: https://lnkd.in/gCGpf8Gr 📘 Facebook: https://lnkd.in/gi9M53uU 💼 LinkedIn: https://lnkd.in/gnQNRCxv 📸 Instagram: https://lnkd.in/gKEptjaW 🛒 Amazon Recommendations: https://amzn.to/3XMR1qr Hidden Camera Products: https://amzn.to/3Zig0SJ
0 notes
Text
#cybersecurity#nmap#nmaplarning#hacking#hackes#securityhacking#nmaphacker#nmapcommand#nmap command#nmapseries
0 notes
Text
Memory Lane: quando scrivevo su riviste su Forenic NMAP
Ci si creda o meno una volta scrivevo pure su riviste tecniche. E poi ci sono quelli che rimpiangono il passato 🤣 Vedi qui sotto: https://hakin9.org/download/nmap-guide-revisited-hakin9-tutorials Nmap Guide Revisited – Hakin9 TutorialsNmap Guide Revisited – Hakin9 Tutorials Hakin9 · Jun 5, 2013 In Depth Guide To Digital ForensicsForensic NmapBy Antonio Ierano, Former Cisco European Security…

View On WordPress
0 notes
Text
Come fare una analisi sicurezza di un sito Web

Come fare una analisi sicurezza di un sito Web? La sicurezza di un sito web è fondamentale per proteggere i dati sensibili, la reputazione online e la fiducia degli utenti. Un sito web vulnerabile può essere facilmente attaccato da hacker, malware, phishing, spam e altre minacce informatiche.
Come effettuare un'analisi di sicurezza del tuo sito web per proteggere dati sensibili e prevenire attacchi informatici
Per evitare questi rischi, è necessario effettuare una analisi sicurezza di un sito web, ovvero un processo che verifica lo stato di sicurezza di un sito web e identifica eventuali debolezze o problemi da risolvere.
Perché è importante fare una analisi sicurezza di un sito web?

Avevo accennato parzialmente nel primo e secondo paragrafo perchè fare una analisi sicurezza di un sito web è importante per diversi motivi, ebbene in questi prossimi paragrafi visto che sembri interessato a questo argomento vediamo di approffondire. Quindi mettiti comodo e continua a leggere. Prevenire le violazioni dei dati: un sito web sicuro impedisce che i dati personali o aziendali siano rubati, compromessi o esposti da attacchi informatici. Questo protegge la privacy e la sicurezza degli utenti e dei proprietari del sito web, e previene possibili sanzioni legali o multe. Migliorare il posizionamento sui motori di ricerca: un sito web sicuro ha maggiori probabilità di essere indicizzato e classificato dai motori di ricerca, come Google o Bing, che premiano i siti web che offrono una buona esperienza utente e che utilizzano il protocollo HTTPS. Questo aumenta la visibilità e il traffico del sito web, e quindi le opportunità di business. Aumentare la fiducia e la conversione degli utenti: un sito web sicuro trasmette una sensazione di affidabilità e professionalità agli utenti, che si sentono più sicuri a navigare, a fornire i loro dati o a effettuare acquisti online. Questo aumenta il tasso di conversione e di fidelizzazione degli utenti, e quindi il fatturato del sito web.
Come fare una analisi sicurezza di un sito web?
Per fare una analisi sicurezza di un sito web, è possibile seguire questi passaggi: Scegliere uno strumento di analisi sicurezza Esistono diversi strumenti online, gratuiti o a pagamento, che permettono di effettuare una analisi sicurezza di un sito web in modo semplice e veloce. Alcuni esempi sono: Sucuri SiteCheck, Qualys SSL Labs, Nmap, OWASP ZAP, Google Safe Browsing. Questi strumenti scansionano il sito web e rilevano eventuali vulnerabilità, malware, certificati SSL scaduti o non validi, configurazioni errate, ecc. Ma vediamo meglio nel dettaglio come funzionano: Sucuri SiteCheck
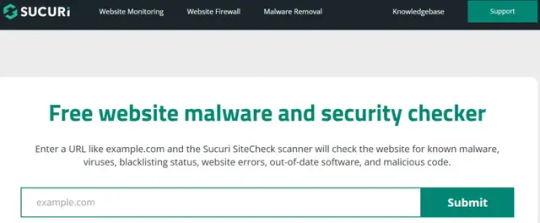
Sucuri SiteCheck è uno strumento online che permette di effettuare una analisi sicurezza di un sito web in modo semplice e veloce. Basta inserire l’URL del sito che si vuole controllare e cliccare su “Submit”. Sucuri SiteCheck scansiona il sito web e rileva eventuali malware, virus, blacklist, errori, software obsoleti o codice malevolo. Fornisce poi un rapporto dettagliato sullo stato di sicurezza del sito web, con un punteggio complessivo e una lista di problemi trovati, suddivisi per gravità e categoria. Inoltre, suggerisce come risolvere i problemi di sicurezza e come migliorare la protezione del sito web. Puoi trovare maggiori informazioni su Sucuri SiteCheck o leggere un tutorial su come usarlo. Qualys SSL Labs
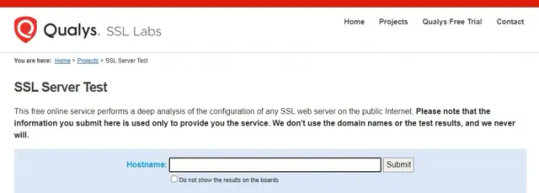
Qualys SSL Labs è uno strumento online che permette di effettuare una analisi sicurezza di un sito web, verificando la configurazione e il certificato SSL/TLS del sito web. Per usare Qualys SSL Labs, basta inserire l’URL del sito web che si vuole controllare e cliccare su “Submit”. Qualys SSL Labs scansiona il sito web e fornisce un rapporto dettagliato sullo stato di sicurezza del sito web, con un punteggio complessivo e una lista di problemi trovati, suddivisi per gravità e categoria. Inoltre, suggerisce come risolvere i problemi di sicurezza e come migliorare la protezione del sito web. Puoi trovare maggiori informazioni su Qualys SSL Labs Nmap
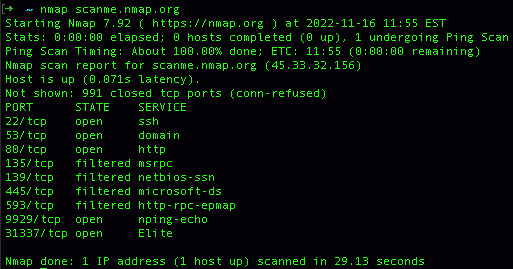
Nmap è uno strumento di analisi di rete che permette di scoprire i dispositivi connessi, le porte aperte, i servizi in esecuzione e i sistemi operativi utilizzati su una rete locale o remota. Nmap funziona inviando pacchetti di dati ai target specificati e analizzando le risposte ricevute. Nmap può usare diversi tipi di scansione, come SYN scan, TCP scan, UDP scan, ecc., per rilevare le informazioni desiderate. Nmap può essere usato da riga di comando o tramite una interfaccia grafica chiamata Zenmap. Nmap è un software libero e multipiattaforma, disponibile per Linux, Windows, macOS e altri sistemi operativi. Puoi leggere una guida del suo funzionamento in Italiano a questo link. OWASP ZAP
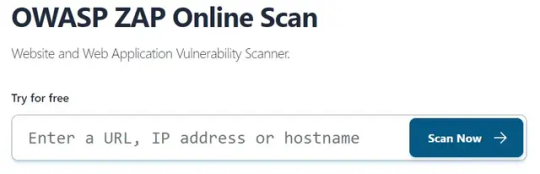
OWASP ZAP è uno strumento online che permette di effettuare una analisi sicurezza di un sito web, verificando la presenza di vulnerabilità, malware, errori o configurazioni errate. OWASP ZAP funziona come un proxy HTTP, che si interpone tra il browser dell’utente e il sito web da analizzare, e consente di ispezionare e modificare il traffico e gli eventi. OWASP ZAP offre due modalità di operazione: una automatizzata, che scansiona il sito web e fornisce un rapporto dettagliato con i problemi trovati e le possibili soluzioni, e una manuale, che permette all’utente di interagire direttamente con il sito web e testare le sue funzionalità. Analizzare i risultati dell'analisi sicurezza Una volta effettuata la scansione, lo strumento di analisi sicurezza fornisce un rapporto dettagliato sullo stato di sicurezza del sito web, con un punteggio complessivo e una lista di problemi trovati, suddivisi per gravità e categoria. È importante leggere attentamente il rapporto e capire quali sono le cause e le conseguenze dei problemi rilevati, e come risolverli. Risolvere i problemi di sicurezza Dopo aver identificato i problemi di sicurezza, è necessario intervenire per risolverli il prima possibile, seguendo le indicazioni fornite dallo strumento di analisi sicurezza o consultando altre fonti di informazione o assistenza. Alcune azioni che si possono fare per migliorare la sicurezza di un sito web sono: aggiornare il software e i plugin del sito web, installare un certificato SSL valido e attivare il protocollo HTTPS, implementare misure di protezione come firewall, antivirus, backup, ecc., educare gli utenti e i dipendenti sulle buone pratiche di sicurezza informatica, ecc. Monitorare la sicurezza del sito web Una volta risolti i problemi di sicurezza, è consigliabile monitorare periodicamente la sicurezza del sito web, ripetendo l'analisi sicurezza con lo stesso o altri strumenti, e verificando che non ci siano nuovi problemi o minacce. Inoltre, è bene tenersi aggiornati sulle ultime novità e tendenze in materia di sicurezza informatica, e adottare le soluzioni più adeguate per il proprio sito web.
Conclusione
Fare una analisi sicurezza di un sito web è un passo fondamentale per garantire la sicurezza, la reputazione e il successo di un sito web. Come hai visto in questa guida esistono diversi strumenti online che permettono di effettuare una analisi sicurezza di un sito web in modo semplice e veloce, e di identificare e risolvere eventuali problemi o vulnerabilità. Monitorare periodicamente la sicurezza del sito web e tenersi aggiornati sulle ultime novità e tendenze in materia di sicurezza informatica sono le migliori pratiche per mantenere il proprio sito web sicuro e protetto.
Note finali
E siamo arrivati alle note finali di questa guida. Come fare una analisi sicurezza di un sito Web. Ma prima di salutare volevo informarti che mi trovi anche sui Social Network, Per entrarci clicca sulle icone appropriate che trovi nella Home di questo blog, inoltre se la guida ti è piaciuta condividila pure attraverso i pulsanti social di Facebook, Twitter, Pinterest e Tumblr, per far conoscere il blog anche ai tuoi amici, ecco con questo è tutto Wiz ti saluta. Read the full article
0 notes
Text
Using Python for Network Security: A Hands-On Tutorial on Nmap and Scapy
Introduction Using Python for Network Security: A Hands-On Tutorial on Nmap and Scapy is a comprehensive guide to leveraging Python for network security testing and analysis. This tutorial will cover the basics of network security, the Nmap and Scapy tools, and how to use Python to automate and enhance network security tasks. In this tutorial, you will learn how to: Understand the core…
0 notes
Text
Unleashing the Power of Kali Linux: A Comprehensive Guide
In the dynamic landscape of cybersecurity, it is crucial for organisations to stay ahead of evolving threats. In such an interconnected world where technology drives every aspect of our lives, the protection of sensitive information and digital assets has become a paramount concern. As we continue to embrace the digital revolution, the threat landscape for individuals, businesses, and governments has expanded exponentially. This is where the critical field of cybersecurity comes into play.
Cybersecurity, the practice of safeguarding digital systems, networks, and data from malicious attacks and unauthorized access, is a dynamic and ever-evolving discipline. From sophisticated cyber-espionage operations to relentless ransomware attacks, the adversaries seeking to exploit vulnerabilities are relentless and cunning. As the digital realm becomes increasingly integral to our daily existence, the need for robust and resilient cybersecurity measures has never been more pressing.To accomplish this, companies need to leverage robust tools and equip their professionals with cutting-edge knowledge. One such tool that has gained immense popularity among ethical hackers, penetration testers, and security enthusiasts is Kali Linux. In this blog post, we will delve into the essentials of Kali Linux, its features, and its significance in the realm of cybersecurity. Additionally, we will shed light on the Executive Programme in Cyber Security for Organisations (EPCSO) offered by IIM Indore, an esteemed program that equips professionals with the necessary skills to protect organisations from cyber threats.
Understanding Kali Linux:
Kali Linux, developed by Offensive Security, is a Debian-based Linux distribution designed for advanced penetration testing and digital forensics. It provides a comprehensive suite of tools that enable ethical hackers and security professionals to assess the security posture of systems, networks, and applications. Kali Linux offers a rich ecosystem of over 600 pre-installed tools, which are regularly updated to keep pace with emerging threats and vulnerabilities.
Features of Kali Linux:
Vast Toolset: Kali Linux boasts an extensive array of tools, including those for reconnaissance, vulnerability analysis, wireless attacks, password cracking, and more. Popular tools such as Nmap, Wireshark, Metasploit, and Aircrack-ng are pre-installed, making it a one-stop solution for security professionals.
Customization: Kali Linux allows users to customize their installations by choosing specific tools or categories during the installation process. This flexibility ensures that users can tailor the distribution to their specific requirements, optimizing their workflow and efficiency. The customization feature empowers cybersecurity professionals and enthusiasts to craft their specialized work environments. By handpicking the essential tools and tool categories during installation, users can optimize their workflows and improve resource management.
Forensics Capabilities: Kali Linux is renowned for its powerful forensics tools. It provides robust features for digital forensics and incident response, making it an indispensable resource for organizations dealing with cybercrime investigations and data recovery.
Community Support: Kali Linux has a large and active community of users and developers who collaborate, contribute, and provide support through forums, documentation, and tutorials. This thriving community enhances the accessibility of the tool and enables users to troubleshoot issues effectively.
Kali Linux in Cybersecurity:
Penetration Testing: Kali Linux serves as an invaluable tool for conducting penetration tests. Its comprehensive suite of tools allows professionals to identify vulnerabilities, exploit them, and provide recommendations to strengthen the security of systems and networks.
Ethical Hacking: Kali Linux facilitates ethical hacking by enabling security professionals to simulate real-world attacks, test defenses, and identify potential weaknesses. This proactive approach helps organizations fortify their security posture and stay one step ahead of malicious actors.
Education and Training: Kali Linux is widely used in cybersecurity education and training programs. Its user-friendly interface, extensive documentation, and wealth of learning resources make it an ideal platform for aspiring security professionals to gain hands-on experience in various domains of cybersecurity.
IIM Indore's Executive Programme in Cyber Security for Organizations (EPCSO):
IIM Indore, one of India's premier management institutions, offers the Executive Programme in Cyber Security for Organizations (EPCSO) to equip professionals with the necessary skills to navigate the complex world of cybersecurity. This program caters to mid to senior-level executives, managers, and leaders responsible for safeguarding their organizations from cyber threats.
EPCSO covers a wide range of topics, including cyber threat landscape analysis, risk management, incident response, digital forensics, ethical hacking, and emerging trends in cybersecurity. The curriculum is designed to provide participants with a holistic understanding of cybersecurity and its implications for organizations.
Eradicate cybersecurity threats by upskilling from IIM Indore in collaboration with Jaro Education. Get in touch with us to know more about the programme.
0 notes
Text
What is the Difference Between NMAP and Wireshark?

In the realm of network analysis and security, two powerful tools stand out: NMAP and Wireshark. Both play critical roles in examining and securing computer networks, but they serve distinct purposes and offer unique features. In this blog, we will explore the differences between NMAP and Wireshark, shedding light on their functionalities and use cases.
NMAP:
NMAP, short for Network Mapper, is a versatile and widely-used network scanning tool. It is primarily designed for network exploration and vulnerability scanning. NMAP is a command-line utility that sends packets to target hosts, allowing users to discover hosts, services, and open ports on a network.
Use Cases:
Network mapping and inventory: NMAP helps identify hosts on a network, including active IP addresses and their corresponding open ports.
Vulnerability scanning: NMAP can scan for potential vulnerabilities in systems by checking for open ports and services that might be susceptible to attacks.
Network troubleshooting: NMAP assists in diagnosing network connectivity issues by verifying port status and service availability.
Penetration testing: Security professionals use NMAP to evaluate the security posture of a network by identifying potential entry points for attacks.
Wireshark:
Wireshark is a powerful network protocol analyzer that provides in-depth packet analysis. Unlike NMAP, Wireshark captures and inspects network packets in real-time or from packet capture files. It allows users to analyze the contents of these packets, providing detailed insights into network traffic and communications.
Use Cases:
Network traffic analysis: Wireshark captures and decodes packets, allowing users to analyze network traffic patterns, identify anomalies, and understand communication between devices.
Troubleshooting network issues: Wireshark is used to diagnose and troubleshoot network problems by inspecting packet data and pinpointing errors or bottlenecks.
Network security analysis: Security professionals leverage Wireshark to investigate potential security breaches, detect suspicious activities, and monitor for unauthorized access or data leaks.
Protocol analysis: Wireshark supports various protocols, making it valuable for studying specific network protocols and their interactions.
Key Differences:
Functionality: NMAP focuses on network scanning and mapping, while Wireshark is designed for detailed packet analysis and network traffic inspection.
Data Collection: NMAP gathers information about hosts and open ports by sending packets to target hosts. Wireshark captures and analyzes packets as they travel through the network.
User Interface: NMAP is primarily a command-line tool, requiring users to enter specific commands and parameters. Wireshark, on the other hand, offers a user-friendly graphical interface that displays captured packets and provides various filtering and analysis options.
Use Cases: NMAP is ideal for reconnaissance, vulnerability scanning, and penetration testing, while Wireshark is best suited for network troubleshooting, protocol analysis, and security investigations.
Conclusion:
NMAP and Wireshark are both essential tools in the field of network analysis and security, but they serve different purposes. NMAP is a network scanning tool used for reconnaissance and vulnerability assessment, while Wireshark is a packet analyzer for in-depth network traffic inspection and troubleshooting.
For those seeking to delve into the world of network scanning and vulnerability assessment, nmap tutorial offer an excellent opportunity to master the tool's functionalities and learn how to perform efficient network reconnaissance. These nmap tutorial provide step-by-step guidance on using NMAP effectively, understanding its various scanning techniques, and interpreting the results to enhance network security and performance.
Understanding the differences between NMAP and Wireshark empowers you to make informed decisions and leverage the right tool for the task at hand. Both tools play vital roles in ensuring the stability, security, and efficiency of computer networks in an ever-evolving digital landscape. With nmap tutorial at your disposal, you can expand your network analysis skillset and contribute to creating robust and secure network infrastructures.
0 notes
Text
Finding Open Ports with Nmap
When traffic is sent to a computer, it is sent to a certain port. This port depends on the software sending/receiving the traffic. This ensures that the data is sent to the software that needs it, for example websites normally operate on port 80 or 443 (depending on if the site uses HTTP or HTTPS respectively), whereas SSH uses port 22. You can read more on ports here.
Nmap is a tool which allows hackers or network administrators to tell which ports are open on a device. This information can be used to find vulnerable services to exploit, or to find services which shouldn’t be running and which a hacker or malware may have added.
The official site for nmap is here, and it can be downloaded from there, however it comes packaged with Kali. I will be scanning a VM running metasploitable, which is an OS created by the creators of metasploit (a hacking tool, but more on that another day) and is intentionally vulnerable. I will be using this machine in many of my tutorials to demonstrate techniques/attacks. Creating a Metasploitable VM is identical to creating a Kali box, but using a Metasploitable image instead.
After booting up the Metasploitable machine, we see something like this:
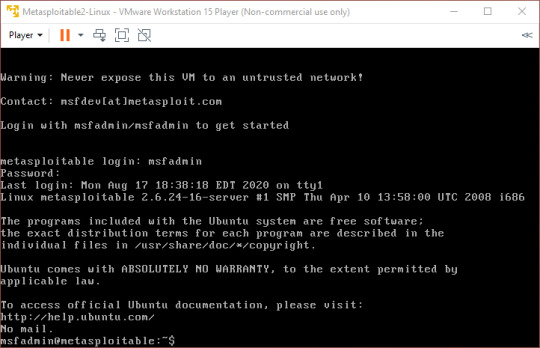
We can then run the command ‘ip route’ to find our local IP address.
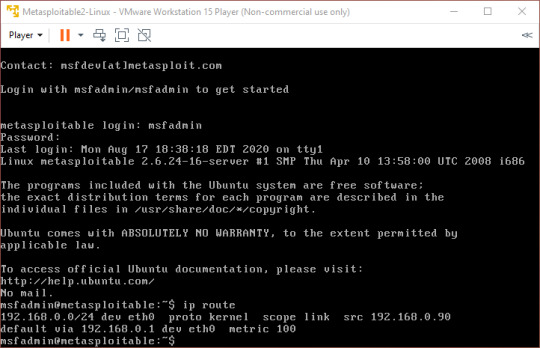
Quite a lot is shown, but what we are looking for is the address after ‘src’. This tells me that my local IP address is 192.168.0.90.
Without closing Metasploitable, we open our Kali VM as well and log in. to check that we can connect to Metasploitable, we will ping the address we just found.
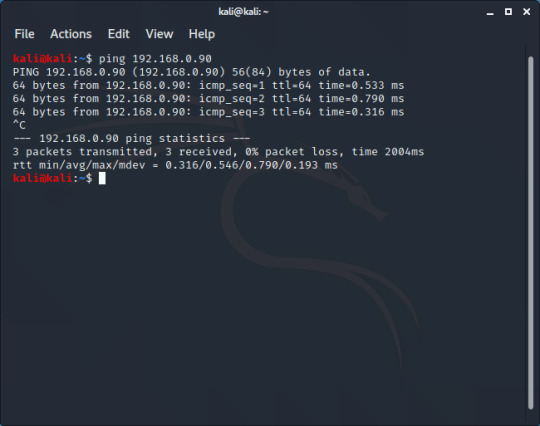
‘64 bytes from 192.168.0.90′ tells me that I am getting a response from Metasploitable. Let’s start an nmap scan.
We are going to start with just a simple scan. I will type ‘nmap 192.168.0.90′ without any other flags.
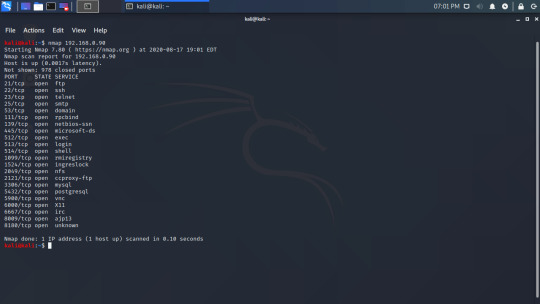
Here we can see that there are 21 ports running. Knowing what ports are open is useful, but we can find more information. Let’s find the OS with the -O flag (bear in mind that this requires sudo)
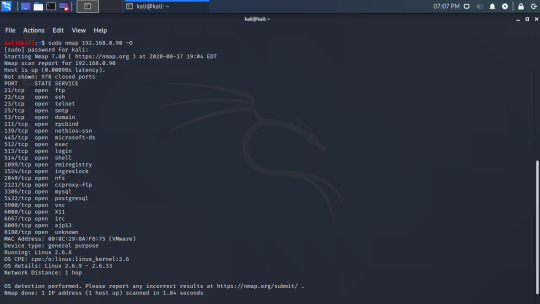
Along with the same information from before, we now have more information. We now know the MAC address, the OS it is running (Linux 2.6), and some more information about the OS.
Nmap can also tell us (a guess) about the software running on each port with the -sV argument.
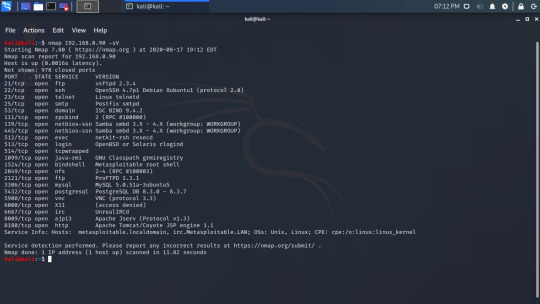
We can use this software version to search for exploits, and I will write another guide on that soon but here is a quick example of just some of the exploits.
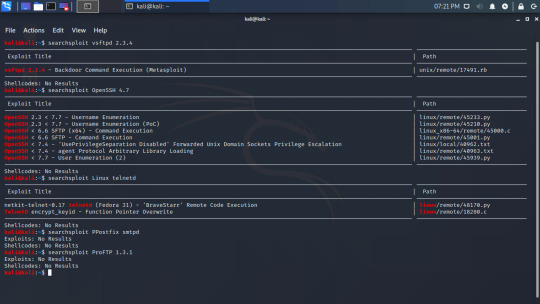
Using the -h flag with nmap will output all of the available options:
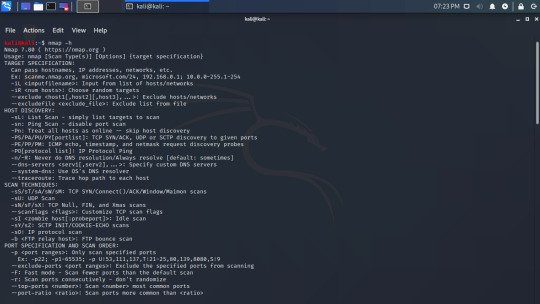
As you can see, there are a lot of options. I recommend using a site like HackTheBox or TryHackMe to give you a place to practice (I have found TryHackMe is better for beginners), or you can practice with a Metasploitable box.
Nmap is a very useful tool and enables you to find so much information. It is worth learning well and I haven’t begun to scratch the surface of all the functionality.
1 note
·
View note
Text
youtube
0 notes
Video
youtube
Nmap XMAS Scan | How to use Nmap | Nmap Tutorials | Port Scanning Tutorial
In this video we will understand a different Nmap Scan - Nmap XMAS scan. Which works on TCP header flag - PSH, URG, FIN. and if a port is open, then destination is discard it and not reply to the source.
We use the command for Nmap XMAS scan: #nmap -sX -p21 target_ip address.
This simple scan will give you the result as the port 21 is open, filtered or closed for the service.
Subscribe for more videos : https://www.youtube.com/c/nileshkumarJadav/ Follow me on Twitter - https://twitter.com/nilusilu3
Connect me with Linkedin - https://www.linkedin.com/in/nileshjadav/
Follow me on Instagram - https://www.instagram.com/nileshk12345/
Follow my Facebook Page - https://www.facebook.com/TechnoCube-107350507784929/
For more .NET related Projects : https://www.c-sharpcorner.com/members/nilesh-jadav
#cybersecurity#cyberattack#hacking#hackers#ethical hacking#nmap#nmap tutorials#xmas scan#tcp#networking#programming#computer
0 notes
Text
threads radio stuff (get HAM license) python (idk lol just do more tutorials!) make maps for funsies (learn where to source data!) nmap docus linear algebra textbook duolingo french + polish + japanese (here we go again) read more fiction! (asimov audiobooks, LOTR) personal website upgrade urbit server gentoo server (omg how am i going to mantain this????)
5 notes
·
View notes