#TCP SYN/ACK packets
Explore tagged Tumblr posts
Text
Nmap Ping Sweep: Home Lab Network Ping Scan
Nmap Ping Sweep: Home Lab Network Ping Scan @vexpert #vmwarecommunities #100daysofhomelab #homelab #Nmaptutorial #Networkscanning #Pingsweepguide #Nmapcommandexamples #HostdiscoverywithNmap #Networksecurity #NmaponKaliLinux #TCPSYNACKpackets #ICMPscanning
There is perhaps not a better known network scan tool for cybersecurity than Nmap. It is an excellent tool I have used for quite some time when you have a rogue device on a network and you want to understand what type of device it is. Nmap provides this functionality along with many others. Let’s look at the Nmap Ping Sweep and see how we can use it as a network vulnerability ping scan to…

View On WordPress
#Host discovery with Nmap#ICMP scanning#Local Ethernet network scanning#network scanning#network security#Nmap command examples#Nmap on Kali Linux#Nmap tutorial#Ping sweep guide#TCP SYN/ACK packets
0 notes
Text
Yeah, it's probably an automatic call/response ping. That's how computers on a network locate and identify each other.
In TCP/IP computers use a 3-way handshake to establish a connection before they start communicating. The initiating PC sends a sync request [SYN] containing the IP and port of the source, and the intended IP and port of the destination. the server/second pc sees it and sends back and acknowledgement [SYN/ACK] confirming the details and responding with it's own information. Finally the initiating computer sends a final acknowledgement [ACK] confirming all of the details and opening a channel for communication. The process takes milliseconds.
If they're trying to hail another ship, they would be doing so using this same basic principle. If the other ship has all channels closed their SYN would be unanswered or perhaps rejected. In which case they would know in about 0.01 seconds that there's no response and the other ship isn't recieving their hails.
On the other hand, as has happened in a couple of episodes, if the other ship is receiving their hails and just choosing to ignore them, the 3 way handshake would work, the connection would be established, but all subsequent packets would simply be swallowed by the server with no echo. This would present as CPT. Picard repeatedly introducing himself and the other captain not answering.
one of my pettiest complaints about star trek is that they always say “hailing [the other ship]” and then 0.3 seconds later say “no response” as though they’re meant to have had time to even register they’re being hailed let alone RESPOND
35K notes
·
View notes
Text
Introduction to Distributed Denial of Service (DDoS) Attacks
DDoS attacks are a form of cyberattack where multiple compromised devices (known as "zombies") are used to overwhelm a target server or network with an immense volume of traffic, rendering the service unavailable to legitimate users. These attacks are a significant threat to online services, targeting the core principle of availability in information security. Unlike viruses or malware that focus on compromising or stealing data, DDoS attacks disrupt services by exhausting resources such as bandwidth, CPU, or memory. The foundation for DDoS attacks emerged in the 1980s with attacks like the Morris worm (1988), which was one of the first large-scale disruptions, affecting internet functionality on a significant scale. As the internet expanded, so did the complexity and frequency of DDoS attacks, making them a primary concern for internet security.
Types and Mechanisms of DDoS Attacks
DDoS attacks can vary in their structure and method of execution but are generally classified into two main categories: resource exhaustion and service disruption.
Resource Exhaustion Attacks: These attacks aim to overload a system by flooding it with traffic. Examples include SYN Flood and ICMP Flood (e.g., Smurf Attack) where attackers flood a server with connection requests or ping requests, respectively, consuming bandwidth and preventing legitimate connections.
Service Disruption Attacks: These attacks exploit specific vulnerabilities in applications or protocols, such as the Ping of Death or SQL Slammer worm. These attacks send malformed packets or exploit application flaws to disrupt service functionality directly, rather than simply flooding the server.
DDoS attacks are facilitated by weaknesses inherent in internet protocols. Protocols like TCP/IP were initially designed for openness and accessibility, without strong security controls to verify the source of traffic. This lack of source verification enables attackers to "spoof" IP addresses, making it difficult to trace the origin of the attack. The structure of these attacks has also evolved, with sophisticated approaches like Reflector and Amplification attacks, which amplify traffic through intermediary servers, and Botnets, where attackers control a large network of compromised devices to launch synchronized attacks.
Defense Mechanisms Against DDoS Attacks
Defense against DDoS attacks requires a layered approach due to the distributed and deceptive nature of these threats. Broadly, defense strategies are classified into prevention, detection, mitigation, and traceback.
Prevention: This involves measures to protect systems before an attack occurs. Techniques include:
Ingress/Egress Filtering: Filtering packets based on IP addresses to prevent spoofed IP traffic from reaching a network.
Source Address Validation (SAVE): Verifying the source address of incoming packets to ensure they originate from legitimate IP addresses.
Hop Count Filtering: Matching the packet’s hop count with known values to detect and filter spoofed packets.
Detection: Effective DDoS defense relies on early detection of anomalous traffic patterns. Common methods include:
Anomaly-based Detection: Establishing a baseline for normal network behavior and flagging traffic that deviates from this baseline.
Pattern-based Detection: Identifying DDoS patterns based on known attack signatures, such as the SYN-ACK ratio in SYN Flood attacks.
Time-Series Analysis: Detecting sustained traffic spikes, often indicative of DDoS attacks.
Mitigation and Reaction: When a DDoS attack is underway, mitigation techniques aim to minimize impact. These include:
Rate Limiting: Limiting the volume of requests to a server to prevent overload.
Filtering and Blacklisting: Blocking known malicious IPs or applying firewall rules to drop suspected malicious packets.
Pushback Scheme: A collaborative response where routers communicate and implement filters upstream to prevent the attack from reaching the target network.
Traceback and Source Identification: Locating the source of DDoS traffic is challenging but essential for a complete defense. IP Traceback methods, including probabilistic packet marking and hash-based traceback, can identify the origin of traffic even when IP spoofing is used.
Challenges and Future Directions
The distributed nature of DDoS attacks poses challenges that make a one-size-fits-all solution unlikely. The attack traffic can often resemble legitimate traffic, making it difficult to distinguish between the two. Additionally, global implementation of protocols like IP traceback is limited by coordination challenges among diverse networks and jurisdictions. Large-scale adoption of D-WARD and Secure Overlay Services (SOS), which operate close to the source of traffic, is still under exploration for practical implementation. Effective DDoS defense will likely require collaborative efforts between ISPs, enterprises, and governments to address technical and regulatory aspects of security, including stricter policies on internet access and accountability.
Conclusion
DDoS attacks remain a persistent threat to internet security, driven by a combination of technical vulnerabilities and the evolving capabilities of attackers. Despite significant advancements in detection and prevention techniques, a completely foolproof solution remains elusive. Future defenses will need to balance flexibility, speed, and scalability to keep up with evolving attack methods. With increased collaboration and adoption of advanced technologies, however, it is possible to significantly reduce the impact of these attacks and improve overall internet resilience.
Endless Data in Dubai has been providing professional service in information security since 2002 , for more information about our security products please visit our website
1 note
·
View note
Text
What is the TCP protocol? The “Reliable Transmission Tool” of the Web
When you send emails, browse web pages or download files on the Internet, there is a key network protocol working behind the scenes, that is, the TCP protocol, which is widely used in a variety of Internet services, and it provides us with stable and reliable data transmission. The following will bring you a deeper understanding of the TCP protocol and how it works.

1. What is the TCP protocol?
TCP (Transmission Control Protocol) is a connection-oriented transport layer protocol that is responsible for ensuring the reliable and orderly transmission of data in a network.TCP is commonly used in applications that need to ensure the accuracy and integrity of data, such as web browsing, email, file transfer, etc. TCP is a protocol that is used in a wide variety of Internet services.
Simply put, the TCP protocol enables data to be transmitted from the sender to the receiver accurately and without error by establishing a reliable connection and ensuring the order and integrity of the data.
2. Key features of the TCP protocol
There are several important features of the TCP protocol that make it useful in data transmission where high reliability is required:
Connection-oriented: Before transmitting data, TCP needs to establish a connection between the two ends of the communication. This process is accomplished through a “three handshakes” mechanism, which ensures that both parties are ready to communicate.
Reliable Transmission: TCP ensures that each packet reaches the receiver successfully by means of an acknowledgement mechanism. If a packet is lost or corrupted, TCP automatically retransmits the packet.
Flow Control: TCP has a flow control mechanism that adjusts the speed of data transmission according to network conditions to avoid network congestion.
Congestion Control: TCP is able to detect congestion in the network and reduce the speed of data transmission to reduce the network load so as to avoid packet loss.
Orderly transmission: TCP ensures that packets reach the receiver in the correct order, even if they are transmitted in a different order in the network.
3. How the TCP protocol works
The core process of the TCP protocol can be divided into three phases: connection establishment, data transfer and connection termination.
Connection Establishment: Three Handshakes
Before data transmission begins, TCP uses “three handshakes” to establish a connection:
1. First handshake: The client sends a connection request SYN (synchronization) packet to the server, indicating that it wishes to establish a connection.
2. Second handshake: The server receives the SYN packet and sends a packet with SYN and ACK (acknowledgement), indicating that it agrees to establish a connection.
3. Third handshake: the client receives a SYN-ACK packet from the server and sends an ACK packet with an acknowledgement, at which point the connection is established and data transfer can begin.
Data Transmission
During data transmission, TCP splits large data into smaller packets for transmission and assigns a sequence number to each packet. The receiver sends an acknowledgement message after receiving the packet. If the sender does not receive the acknowledgment message within the specified time, it retransmits the unacknowledged packet.
Connection Termination: Four Waves
After the data transfer is completed, TCP uses “four waves” to close the connection:
1. First wave: the sender sends a FIN (termination) packet, indicating that no more data will be sent.
2. The second wave: the receiver receives the FIN packet, send an ACK packet to confirm.
3. Third wave: the receiver sends its own FIN packet, indicating that data reception is complete.
4. Fourth wave: the sender receives the FIN packet, sends an ACK packet to confirm that the connection is terminated.
The TCP protocol ensures that our data transmission over the network is stable and orderly through mechanisms such as connection establishment, reliable transmission, and flow control. If you need to deal with demanding network applications in your work or life, TCP protocol is undoubtedly your trusted choice.
Meanwhile, if you need to further improve the stability and security of data transmission, it is recommended to use 711Proxy proxy service, which is able to provide worldwide quality IP resources, guaranteeing you a smoother and more unobstructed network connection.
0 notes
Text
DDoS Attack: The Most Prevalent Threat in the Digital Landscape
Understanding Distributed Denial of Service (DDoS) Attacks: An In-Depth AnalysisIntroduction to DDoS Attacks Mechanisms Behind DDoS AttacksKey Attack Vectors in DDoS Attacks Common Denominator: Resource Exhaustion The Impact of DDoS AttacksFinancial Losses Reputation Damage Operational Disruption Strategies for Mitigating DDoS Attacks Legal Strategies to Defend a Victim of a DDoS Attack1. Gathering and Preserving Evidence 2. Legal Claims and Remedies 3. Collaboration with Law Enforcement Consequences for the Perpetrators Proving a DDoS Attack and Identifying the Perpetrators1. Technical Evidence 2. Legal Identification of Perpetrators Understanding Distributed Denial of Service (DDoS) Attacks: An In-Depth Analysis Introduction to DDoS Attacks Distributed Denial of Service (DDoS) attacks have emerged as one of the most disruptive and prevalent threats in the digital landscape. Unlike traditional cyberattacks that focus on breaching security defenses to access sensitive information, DDoS attacks aim to disrupt services, making them inaccessible to legitimate users. This is achieved by overwhelming the target system with a massive influx of traffic, effectively paralyzing its operations.

Mechanisms Behind DDoS Attacks Distributed Denial of Service (DDoS) attacks are executed using a coordinated network of compromised devices, known as a botnet. This network typically comprises thousands, or even millions, of devices that have been infected with malware, enabling attackers to control them remotely. The primary goal of a DDoS attack is to inundate a target system with an overwhelming amount of traffic, thereby denying legitimate users access to the service. Key Attack Vectors in DDoS Attacks The traffic in a DDoS attack can manifest through several methods, each exploiting different aspects of network communication. The most common types include: - HTTP Floods: - Description: This method involves bombarding a web server with a massive number of HTTP requests. The objective is to overwhelm the server's ability to process incoming requests, making it unresponsive to legitimate users. - Mechanism: Attackers typically use botnets to send HTTP GET or POST requests, which are common methods for fetching resources or submitting data. The high volume of requests saturates the server's processing capacity, leading to a denial of service. - UDP Floods: - Description: UDP floods focus on the User Datagram Protocol (UDP), which is a connectionless protocol. This type of attack sends large quantities of UDP packets to random ports on the target system, causing the system to repeatedly check for applications listening on those ports. - Mechanism: Since UDP is a stateless protocol, the target must respond to each incoming packet with an ICMP (Internet Control Message Protocol) packet, reporting that the port is unreachable if there is no service listening on that port. This process consumes significant bandwidth and processing power, eventually exhausting the target's resources. - SYN Floods: - Description: SYN floods exploit the TCP handshake process, a fundamental part of establishing a TCP connection between a client and a server. This attack method involves sending a succession of TCP/SYN requests to initiate connections with the target server. - Mechanism: In a typical TCP handshake, a client sends a SYN request to the server, which responds with a SYN-ACK, and then the client sends an ACK to establish the connection. In a SYN flood, the attacker sends a flood of SYN requests without completing the handshake, leaving the server waiting for the final ACK. These half-open connections consume resources and can quickly exhaust the server's ability to establish new connections, leading to a denial of service. Common Denominator: Resource Exhaustion The unifying factor in these attack vectors is their ability to exhaust the target's critical resources—be it bandwidth, CPU power, or memory. By overwhelming these resources, DDoS attacks prevent the target system from functioning normally, thereby denying service to legitimate users. The efficiency and scale of these attacks are largely dependent on the size and sophistication of the botnet, as well as the specific attack method employed. In summary, the mechanisms behind DDoS attacks are designed to exploit the limitations of network protocols and system resources. By understanding these mechanisms, organizations can better prepare for and mitigate the impact of such attacks, ensuring the continued availability and security of their services. The Impact of DDoS Attacks Distributed Denial of Service (DDoS) attacks pose significant risks to organizations by disrupting access to essential online services. The ramifications of these attacks extend far beyond temporary inconveniences, often resulting in severe and lasting consequences. The impact of a successful DDoS attack can be categorized into three primary areas: financial losses, reputation damage, and operational disruption. Financial Losses One of the most immediate and tangible effects of a DDoS attack is the financial loss incurred due to downtime. For businesses that depend on digital platforms for their operations, such as e-commerce websites, financial institutions, and online service providers, even brief periods of unavailability can lead to substantial revenue losses. The specific financial impact can vary widely depending on the nature of the business and the duration of the outage. Key factors contributing to financial losses include: - Lost Sales: In e-commerce, downtime translates directly to lost sales opportunities, as customers are unable to complete transactions. - Operational Costs: Businesses may incur additional costs for IT support, security measures, and emergency response to mitigate the attack and restore services. - Penalties and Legal Costs: In some industries, regulatory requirements mandate minimum service availability. Failure to comply can result in penalties, fines, or legal action from affected parties. Reputation Damage The reputational impact of a DDoS attack can be profound and long-lasting. In an era where customer trust and brand reliability are critical, repeated or prolonged service outages can severely damage a company's reputation. The erosion of trust can manifest in several ways: - Customer Dissatisfaction: Users may become frustrated and lose confidence in a service's reliability, leading to customer churn and negative word-of-mouth. - Brand Perception: A high-profile service disruption can attract media attention, painting the affected company as vulnerable and poorly secured. This negative publicity can tarnish the brand's image and deter potential customers or partners. - Investor Confidence: For publicly traded companies, service outages can negatively impact stock prices as investor confidence wanes. The perceived inability to protect against cyber threats can lead to a loss of market value. Operational Disruption The operational impacts of DDoS attacks can be particularly severe for organizations that provide critical services, such as healthcare providers, government agencies, and utilities. In these cases, the disruption extends beyond financial implications and can have serious consequences for public safety and welfare. Key aspects of operational disruption include: - Service Availability: Critical systems, such as emergency services, healthcare platforms, or public infrastructure, may become unavailable, potentially putting lives at risk. - Data Integrity and Security: While DDoS attacks primarily focus on disrupting service availability, they can also serve as a distraction for other malicious activities, such as data breaches or malware deployment. This can compromise the integrity and security of sensitive information. - Resource Allocation: Organizations may need to divert significant resources, both human and technical, to respond to and recover from an attack. This can strain internal capabilities and delay other essential operations or projects. The impact of DDoS attacks is multifaceted, affecting financial stability, brand reputation, and operational continuity. The extent of the damage often depends on the organization's preparedness and the effectiveness of its response measures. As cyber threats continue to evolve, it is crucial for organizations to implement robust security protocols, develop comprehensive incident response plans, and invest in advanced DDoS mitigation technologies. By doing so, businesses can better safeguard against the detrimental effects of these attacks and ensure the continuous availability of their critical services. Strategies for Mitigating DDoS Attacks To protect against DDoS attacks, organizations must adopt a comprehensive, multi-layered defense strategy: - Advanced Network Security Solutions: - Intrusion Detection Systems (IDS): These systems monitor network traffic for suspicious activity and can alert administrators of potential attacks. - Web Application Firewalls (WAF): WAFs provide an additional layer of protection by filtering and monitoring HTTP traffic between a web application and the internet. - DDoS Protection Services: Specialized services can detect and mitigate DDoS attacks in real-time, absorbing and filtering malicious traffic before it reaches the target. - Scalable Infrastructure: - Content Delivery Networks (CDN): CDNs distribute traffic across a network of servers, reducing the load on the primary server and mitigating the impact of a DDoS attack. - Cloud-Based Solutions: Cloud services can dynamically scale resources to handle traffic surges, providing additional resilience against large-scale attacks. - Rate Limiting and Traffic Filtering: - Rate Limiting: This technique limits the number of requests a server will accept in a given timeframe, preventing overload from excessive traffic. - Traffic Filtering: Implementing filters to block traffic from known malicious IP addresses or patterns can reduce the risk of a successful attack. - Incident Response Plan: - An effective incident response plan outlines the steps to be taken in the event of a DDoS attack, including communication protocols, mitigation strategies, and service restoration processes. Having a clear plan helps minimize downtime and ensures a swift recovery. Legal Strategies to Defend a Victim of a DDoS Attack Defending a victim of a Distributed Denial of Service (DDoS) attack involves a multifaceted approach that includes legal strategies, technical evidence gathering, and collaboration with law enforcement and cybersecurity experts. The primary objectives are to establish the occurrence and impact of the attack, identify the perpetrators, and seek legal redress or protection. Here are key strategies: 1. Gathering and Preserving Evidence Digital Forensics: Immediately after a DDoS attack, it is crucial to collect and preserve digital evidence. This includes logs, network traffic data, server response times, and any anomalous patterns observed during the attack. Digital forensics experts can analyze this data to trace the origin of the attack and identify the involved devices and methods. Chain of Custody: Maintaining a clear chain of custody for all evidence ensures that it is admissible in court. This involves documenting how evidence was collected, stored, and handled, preventing any tampering or loss. Expert Testimony: Cybersecurity experts can provide testimony on the nature of the DDoS attack, its impact on the victim's systems, and the methods used by the attackers. This expert testimony is critical in explaining complex technical details to a court. 2. Legal Claims and Remedies Criminal Prosecution: If the perpetrators are identified, they can be prosecuted under various cybercrime laws. In many jurisdictions, launching a DDoS attack is a criminal offense, punishable by fines, imprisonment, or both. The severity of the punishment often depends on the extent of the damage and whether the attack was part of a larger criminal enterprise. Civil Litigation: Victims may pursue civil litigation against the perpetrators or any entities that facilitated the attack (e.g., internet service providers, if negligence can be proven). Claims can include compensation for financial losses, damage to reputation, and costs incurred due to the attack. Injunctions: Victims can seek injunctive relief to prevent ongoing or future attacks. This may involve court orders compelling service providers to block certain traffic or requiring parties to cease specific activities. 3. Collaboration with Law Enforcement Reporting and Cooperation: Victims should report the DDoS attack to relevant law enforcement agencies. In many cases, agencies such as the FBI's Cyber Crime Division or Europol's European Cybercrime Centre have the resources to investigate large-scale cybercrimes. Information Sharing: Sharing information with law enforcement can assist in identifying and prosecuting the attackers. This includes details about the attack vectors, botnets involved, and any ransom demands made (if applicable). Consequences for the Perpetrators The consequences for individuals convicted of launching or orchestrating a DDoS attack vary by jurisdiction but can include: Criminal Penalties: These often involve imprisonment, especially if the attack caused significant disruption or was aimed at critical infrastructure. Penalties can also include substantial fines, community service, and probation. Civil Liability: In addition to criminal penalties, perpetrators may face civil lawsuits from victims seeking compensation for damages. This can lead to financial restitution orders, forcing the perpetrators to pay for losses incurred due to the attack. Asset Seizure: In cases where DDoS attacks were part of a broader criminal enterprise, authorities may seize assets obtained through illegal activities. Proving a DDoS Attack and Identifying the Perpetrators Proving a DDoS attack and identifying the individuals responsible involves a combination of technical and legal steps: 1. Technical Evidence Network and Server Logs: These logs can show a sudden spike in traffic, identify IP addresses from which the traffic originated, and highlight unusual patterns that are consistent with a DDoS attack. Traffic Analysis: Analyzing the nature and volume of incoming traffic can reveal the type of DDoS attack (e.g., HTTP flood, UDP flood). Patterns such as consistent traffic from certain regions or the use of particular protocols can help in pinpointing the source. Botnet Analysis: Identifying the botnet used can provide clues to the attack's origin. This involves tracking command and control servers, often requiring international cooperation due to the global nature of botnets. 2. Legal Identification of Perpetrators IP Tracing: While attackers often use techniques like IP spoofing to hide their identities, sophisticated tracing methods can sometimes reveal the true source of the traffic. However, this is often challenging and may require cooperation from ISPs and international agencies. Subpoenas and Warrants: Law enforcement can use legal tools like subpoenas and warrants to obtain information from service providers, such as logs or customer data, that can help identify the attackers. Digital Footprints: Sometimes, attackers leave behind digital footprints, such as communications on forums, use of specific software tools, or even ransom notes. These can be used to link the attack to specific individuals or groups. The legal defense of a DDoS attack victim requires a comprehensive strategy that includes evidence gathering, collaboration with authorities, and potentially pursuing criminal and civil remedies. The consequences for perpetrators can be severe, including criminal penalties and civil liabilities. Proving the occurrence of a DDoS attack and identifying those responsible is a complex process that relies on both technical expertise and legal mechanisms. This integrated approach is essential for ensuring accountability and protecting victims' rights. As cyber threats continue to evolve, the importance of robust defenses against DDoS attacks cannot be overstated. Businesses must be proactive in implementing security measures and preparing for potential incidents. Collaborating with internet service providers (ISPs) and cybersecurity experts can further enhance defenses, ensuring the availability and reliability of critical services. By adopting these strategies, organizations can mitigate the risks associated with DDoS attacks and safeguard their digital assets and reputation. https://www.youtube.com/watch?v=a_r-lzQKMAQ Read the full article
0 notes
Text
TCP handshake error causes and solutions
A TCP handshake error occurs when the three-way handshake process, which is essential for establishing a TCP connection, fails. This handshake involves three steps: SYN (synchronize) packet sent by the client. SYN-ACK (synchronize-acknowledge) packet sent by the server. ACK (acknowledge) packet sent by the client. If any part of this handshake fails, the connection cannot be established. Here…
View On WordPress
0 notes
Text
Advanced VPN sessions hijack, injecting data into their TCP streams.
The attacker starts scanning the device connected to the access point for active VPN sessions. To do this, the access point can send SYN-ACK packets to any connected devices, canvassing across the entire virtual IP space.
When a SYN-ACK is sent to the correct virtual IP on the victim device, the device responds; when the SYN-ACK is sent to the incorrect virtual IP, nothing is received by the attacker.
Once the attacker determines that the user has an active TCP connection to an external server, the next step is to sniff out the next sequence number and in-window acknowledgment number needed to inject forged packets into the connection.
To find the appropriate sequence and ACK numbers, the attacker can continually spoof reset packets into the active connection until it sniffs challenge ACKs.
The victim’s device will trigger a TCP challenge ACK on each reset it receives that has an in-window sequence number for an existing connection.
Continuing with packet-spoofing and challenge ACK analysis, an attacker can infer the rest of the information needed to inject arbitrary payloads into the victim’s active VPN session.
Affected OS VPNs: macOS, iOS, Android, Ubuntu, Fedora and Debian, FreeBSD and OpenBSD.
Affected VPN technology, OpenVPN, WireGuard and IPSec and they’re in the process of testing Tor.
2 notes
·
View notes
Text
Hawk Network and pentest utility that I developed so that I could perform different kinds of...
Hawk Network and pentest utility that I developed so that I could perform different kinds of task using the same suite, instead of jumping from one tool to another. Currently, this script can perform a variety of tasks such as ifconfig, ping, traceroute, port scans (including SYN, TCP, UDP, ACK, comprehensive scan, host discovery (scan for up devices on a local network), MAC address detection (get MAC address of a host IP on a local network), banner grabbing, DNS checks (with geolocation information), WHOIS, subdomain enumeration, vulnerability reconnaissance, packet sniffing, MAC spoofing, IP spoofing, SYN flooding, deauth attack and brute-force attack (beta). Other features are still being implemented. Future implementations may include WAF detection, DNS enumeration, traffic analysis, XSS vulnerability scanner, ARP cache poisoning, DNS cache poisoning, MAC flooding, ping of death, network disassociation attack (not deauth attack), OSINT, email spoofing, exploits, some automated tasks and others. https://github.com/medpaf/hawk

-
1 note
·
View note
Text
SNIFF with me~
Wireshark -- is a tool to help you see what is happening on your network. It anaylzes the network protocols and captures packets being sent and received through a network connection.
It’s a packet sniffer!
So what will we SNIFF today?? HERE’S THE CHALLENGE:

link for the interceptor file: https://shell.fullstackacademy.com/static/c2e9660a916c75f416cd3ffd29cf4fc5/interceptor
Step 1.
Let’s start off by downloading the interceptor file.
The curl (clinet user) command will work great here. Think of curl as the url browser for your terminal! We can also add the option -o (for open) to the curl command, in order to download and create the binary file into your linux terminal.
INPUT: curl -o <interceptor link>
LS to check if the file has been downloaded.

.
Step 2.
Is it downloaded? Have you tried running it? Maybe you got this:
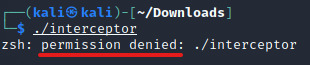
DENIED.
Ah, but that’s okay. Our trusty sudo command can give us root access to modify the permission of this file to be changed to executable. Just make sure you know your root password to use sudo.
To modify the permission, use the chmod command with options -a (for all) + -x (for executable)
INPUT: sudo chmod a+x “interceptor”
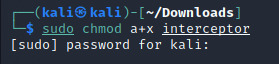
COOL. let’s see if anything changed now.
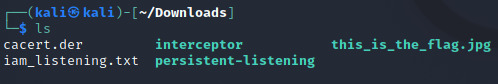
OHOHO. the file is in green so it means the file is ready to be executed (you can also check the specific permissions of the file using: ls -l <filename>)
.
Step 3.
Whoah, whoah. Hold your horses before executing. This is where the SNIFFing starts.
Let’s open Wireshark.

The opening menu will prompt you to select the network you want to capture. For this demonstration, we’ll select any.. ***** keep any internet browsers closed as this will pick up any packets that are going through the network.
It should look like this:
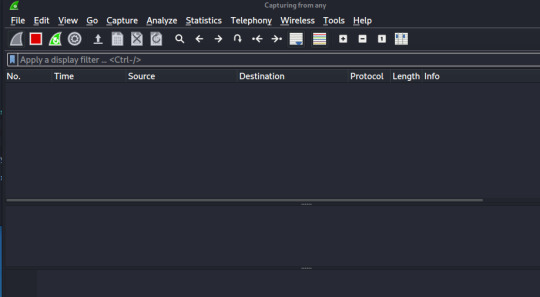
Empty?? NICE. It should be to help us sort through the traffic we want from when we run our binary file.
.
Step 4.
Okay! Now let’s go back to our terminal and run our interceptor binary (with our Wireshark open).

When we execute the binary, we should expect to see some traffic on Wireshark.

Ohoho..... that’s some SNIFFing. There should be about 38 packets, and while that’s not too many (compared to hundereds and hundreds), we still want to find a way to narrow down our search.
The Challenge question states that the interceptor file is a beacon for criminal activity, so we can expect these nefarious players to be interacting in this network.
Let’s make sense of the first few lines of what is being picked up!

The first 4 lines shows us making the request to a DNS server to find the host of this website. The request for tor the DNS is sent with a response confirming that the host is from “shell.fullstackacademy.com”. We can see that the host’s IP is “52.1.103.48″. Let’s take a closer look at that.

Along with the host’s IP we see the DNS server request/response followed by a TCP protocol. Notice how the next few subsequent rows show the TCP/IP protocol’s classic “3-way handshake” -- [SYN], [SYN, ACK], and [ACK].
Seeing this, we can confirm that packets are being requested and responded.
COOL. Let’s take even a CLOSER look at the packets being sent by the host’s IP.
.
Step 5.
In order to “Follow” the stream of packets, right click on the desired packet and select “Follow” --> “TCP Stream”
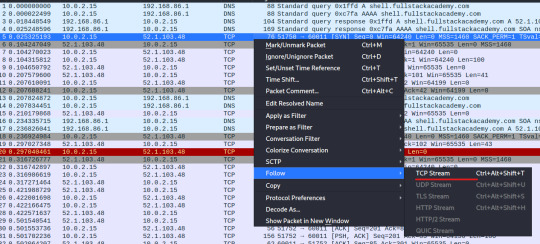
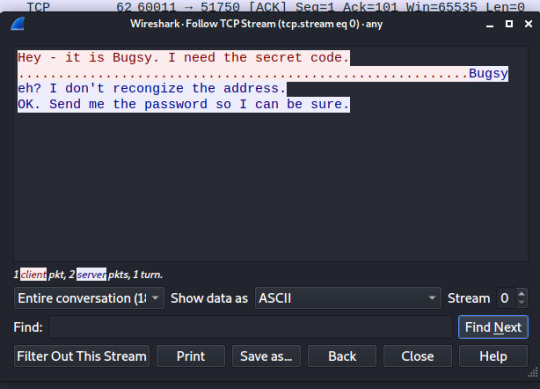
AHA. we’ve intercepted a message between the hackers! But the message only shows an inquiry for the password (or Flag) and not the actual flag.
Let’s keep following this TCP Stream. On the Bottom right corner , click the arrow button to go through different TCP Packets in this stream.
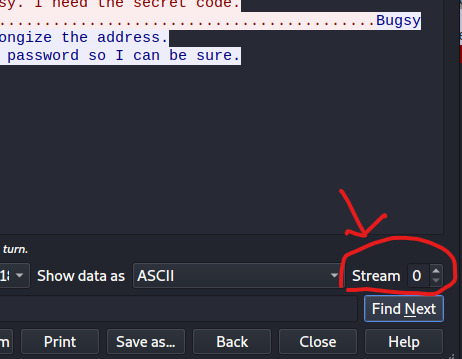

And thereeeee it is! We’ve successfuly intercepted the hacker’s password by SNIFFing on their traffic.
FLAG: FS{no_unencrypted_traffic_is_safe_548844}
SNIFFing on Wireshark~ so kewlll.
3 notes
·
View notes
Text
What is a DDoS attack and Anti-DDoS methods
As technological solutions emerge, new methods of computer warfare also appear that threaten the security of our platforms. One of the most traditional cyber-attacks is carried out using the DDoS method. This technique dates back to the early 2000s, but according to Akamai reports, DDoS attacks have been on the rise since 2014. On October 21, 2016, one of the most severe massive DDoS attacks in the world took place, disrupting the services of large companies such as PayPal, Spotify, Twitter and Netflix. According to The Guardian, this attack was the most massive of its kind in history.
What is a DDoS attack and what does it consist of?
Let's start by defining a simple denial of service or DoS attack. The final objective of a DoS attack is to consume the resources of the target machine or network causing the unavailability of its services. This is not a hacking attack, as a denial of service attack is not designed to steal confidential information or break into a system in a forced manner, but rather to interrupt the services offered by that system, which can be an application/web site or any IT platform connected to the Internet. Some hackers, however, can take advantage of this temporary vulnerability to perpetuate other types of attacks.
Difference between DoS and DDoS
Let's look at a simple analogy: suppose a large store with enough staff and products opens a new offer, free PS4 consoles! The number of customers trying to purchase the product will cause your resources to collapse, so it is very likely that the store will have to close temporarily, preventing customers from accessing your services.
Now suppose a more cunning attacker wants to attack the store with more customers and inserts a chip that turns thousands of customers into zombies -yes, this is the IT term for an intruder-controlled computer- to drain more and more resources from that store. This is what a DDoS or distributed denial of service attack is all about. A stresser/booter is used for this type of attack.
A DoS attack is carried out using a single Internet connection, taking advantage of software vulnerabilities or overflowing the attacked machine with fake requests with the intention of overloading network resources, RAM or CPU usage. In contrast, and as we can see in the analogy, a DDoS attack is perpetuated from several devices across the Internet network. In general, these attacks are executed using many computers in a network, in the order of hundreds or thousands. How do so many people manage to agree on such an attack? The reality is that the vast majority of device owners running a DDoS attack have no idea they are part of the attack, this is because a Trojan/Malware/bot infects the devices and takes over the attack.
The large number of devices sending requests saturates the target computer or network, making it unavailable. This also makes determining the source of the attack extremely difficult. There are different types of DDoS attacks, which are described in the section Types of DDoS attacks and how they are carried out.

What is a botnet?
The group of devices infected with a bot that can be managed remotely is called a botnet. Also called "zombie armies" (zombies are the equivalent of computer bots), they are the source of a DDoS attack. Due to the geographical dispersion of the computers that make up a botnet, it is almost impossible to find a pattern of attacking devices.
What is the impact of a DDoS attack?
The impact of a DDoS attack that achieves its objective is very extensive. Suppose you have a large retail consortium -like Amazon- and your service is affected for 24 hours or more. The first impact is usually economic. And it's not just the impact on major sales losses, it also affects your reputation, service level agreements are violated, your numbers drop in availability, and statistically important values such as quality of service and experience (QoS and QoE) are impacted.
This is why it is so important that you are protected against these attacks, or that you are prepared for their imminent occurrence. At OpenCloud we are pioneers in offering Anti-DOS solutions in Chile and Latin America, with which you can avoid the occurrence of these types of attacks or mitigate the problem, addressing it with mitigation methods used by large companies. For more information go to the Anti-DDoS Methods section.
Types of DDoS attacks and how they are carried out
We can divide DDoS attacks into two main categories within the OSI model: network layer attacks and application layer attacks.
DDoS attacks in the application layer
These attacks are usually of a smaller scale, and are aimed at directly affecting the web server, without adverse effects on other ports and services. These types of attacks consume little bandwidth and include: HTTP overflows, slow attacks with tools such as Slowloris or RUDY, "day zero" attacks (taking advantage of vulnerabilities before they are discovered/solved by the manufacturer) and DNS request overflow attacks.
Slowloris sends partial requests to the target server, to keep connections open for as long as possible. At the same time, it sends large numbers of HTTP headers at certain time intervals that increase the number of requests, but never complete a connection. In this way, the victim's resources are affected, making it impossible for them to continue providing their services. This attack only affects the web server.
For its part, RUDY focuses on web applications by consuming all available sessions on the web server. It simulates a user who has a very slow Internet connection and sends HTTP POST packets -like those of a web form-, forcing the server to wait a long time until the request is completed. It is a slow attack, but is usually effective as it takes advantage of this HTTP vulnerability.
DDoS attacks in the network layer
These types of attacks try to take advantage of network and transport layer vulnerabilities (layers 3 and 4 of the OSI model), sending more packets or more bandwidth than the target server can support. The major attacks we usually read about in media reports are DDoS attacks on the network layer.
Attacks under this category usually cause a total interruption of service or serious operational damage. These attacks consume so many network resources that they are usually measured in the order of Gbps (gigabits per second), the largest ones even exceeding 300 Gbps.
Attacks of this type include:
● SYN overflows: this attack exploits a small vulnerability in TCP connections. Attackers send a request in a SYN synchronization packet to the victim server, but mask the attacker's IP address (or the zombies in a botnet). Although the connection request looks real, the victim, when trying to respond to the connection request with an ACK message, does not find the attacker, slowing down the connection process and leaving connections open. By multiplying these requests by hundreds of thousands, the server consumes all available network resources and stops working.
● DNS overflow: The attacker points to one or more DNS servers and sends apparently valid traffic, when in reality it is a question of badly formed packets, exhausting the resources of the recursive DNS server and preventing it from processing the requests that are real.
● UDP overflow: in this case the attacker floods random ports of the victim with IP packets containing UDP datagrams. The victim searches for the associated service and when it does not get anything, it returns an "Unreachable Destination" packet. As it receives and responds to more packets, it becomes saturated and stops responding to other clients.
● UDP-based amplification attacks: this type of attack is based on saturation of other services such as [DNS] (name translation to IPs on the Internet), NTP (synchronization of the computer clock on the Internet) or SSDP (searching for UPnP devices on the network) by sending large amounts of UDP packets. They are called amplification attacks because the attacker uses amplification techniques that can exaggerate the size of UDP packets, making the attack very powerful.
● Ping of death: in this case, the attacker sends badly formed ICMP packets (slightly above the standardized limit of 65,535 bytes) using a simple ping command. When the victim server tries to reconstruct these packets it consumes a lot of resources; by considerably multiplying the number of packets sent via ping the server hangs.
● There are other attacks such as NUKE and SMURF (smurf) that also take advantage of IP protocol vulnerabilities and ICMP messages to cause saturation and a final network overflow.
Why do you carry out DDoS attacks?
There are many different reasons for performing a DDoS attack, the most common causes include:
● Hacktivism: this word comes from hacker and activism; this is one of the most common reasons for these attacks. It is a way for hackers or hacker organizations -like Anonymous- to express their critical opinion on issues of large corporations or politics.
● Extortion: this is another increasingly popular motive. Here, attackers extort medium and large companies to hand over money in exchange for not carrying out a DDoS attack.
● Cyber-vandalism: These are generally less experienced attackers who use tools and scripts already developed to carry out an attack simply for the sake of fun or unethical revenge.
● Competition in the market: these competitive attacks are usually triggered by rivalry between companies or simply as a form of dirty market competition; for example: attacks on servers of online games companies, or attacks on companies selling services and products on crucial days, such as Black Friday.
Anti-DDoS Methods
DoS-based attacks cannot be prevented. You must accept the fact that the attackers are likely to act and will succeed in reaching the target. However, let's look at some steps to prepare you in case of such an attack. What we can do is make our platform more difficult to penetrate, and be prepared to take action in the event of an attack. Let's look at some recommendations for preparing for DDoS cyber-attacks:
● Invest in building a robust platform: If you own a large platform that offers services or products that generate revenue or commercial value, you should invest in the security of your applications. Many times companies are reluctant to pay for services they don't use, however, this can be a very small expense when compared to the losses that a DDoS attack can generate.
● Implement a monitoring tool for your systems: there are many tools available on the market, OpenCloud offers a monitoring solution to monitor the most important values of your CloudServer, however, it is advisable to implement a monitoring solution in a different network segment to be aware of unusual changes in the use of bandwidth, CPU and memory. Conduct stress tests: Another good idea is to use tools for third-party DDoS attacks and do testing before your platform goes into production, so you know how your system behaves in different DDoS scenarios.
● Watch out for social networks and news blogs about DDoS threats. You can use Info Risk Today's RSS crawlers to keep up to date with the latest cyber threats.
● During a DDoS attack, the log file record grows exponentially and can be the cause of your service interruption. As soon as you become aware that you are a victim of a DDoS attack, start deleting the dump files that start to be created due to the amount of general errors. One of the secrets of DDoS attacks is to cause large loads on instances of the system other than those attacked a priori. A good idea is to completely disable the generation of logs while the attack lasts.
● Mitigating DDoS attacks with OpenCloud
● OpenCloud offers a solution that helps redirect traffic corresponding to a DDoS attack on your website, diverting it to another point in the network. Traffic - national and international - entering your network is carefully inspected, filtered and discarded. In addition, we use IP masking on your CloudServer, preventing direct attacks on your IP address. This is an ideal solution for gamers or users with broad platforms that require more advanced levels of security.
1 note
·
View note
Text
Change syn

#Change syn full
But, if it responds with a UDP packet, the port is open. If an ICMP unreachable error comes back, the port is closed. UDP scans are done by sending UDP packets to all ports. They are slower and more complex to send than a SYN or TCP packet but can be combined with those types of scans to check UDP ports. Instead of running over TCP, hackers can deploy User Datagram Protocol ( UDP) scans over domain name system, Dynamic Host Configuration Protocol or Simple Network Management Protocol. Instead of requiring a raw packet like other scan types, Nmap will request a connection with the target operating system (OS) using a system call. A TCP scan is common for users who don't have raw packet access privileges, but it is less efficient than a SYN scan. If a SYN scan can't be performed, a TCP connect scan is a popular alternative for hackers. On rare occasions, a SYN packet may be returned without the ACK flag, indicating an open port and the presence of a TCP three-way handshake. If no response is received or if an Internet Control Message Protocol ( ICMP) unreachable error is received, it indicates a filtered state. A SYN/ACK response indicates an open TCP port, whereas an RST response indicates a closed port. It works by sending a SYN packet in an attempt to open a connection. For this reason, TCP SYN scanning is also commonly referred to as half-open scanning and can indicate open, filtered and closed port states.
#Change syn full
It is a quick and efficient scan, not restricted by firewalls since it never completes the full TCP connection. The TCP SYN scan - a variant of the traditional SYN scan - is commonly used. The following is a list of some scan types that can be done by a port scanner. What results is that few or no communications from legitimate clients can take place.Īs part of a extensive network security program, it's important to understand that other port scanning techniques can be used in conjunction with SYN scanning or as a substitute for it. When a hacker continuously sends large numbers of SYN packets to a server, it can consume server resources. If the server responds with an RST packet from a particular port, it indicates that the port is closed and cannot be exploited. The open port remains open and vulnerable to exploitation. In this scenario, the assumption is wrong. Then, the hostile client sends an RST (reset) packet.Īs a result, the server assumes that there's been a communications error and the client has not established a connection. If the server replies with an ACK (acknowledgement) response - or SYN/ACK (synchronization acknowledged) packet - from a particular port, it means the port is open. This is done by sending a SYN (synchronization) packet, as if to initiate a three-way handshake, to every port on the server. In SYN scanning, similar to port scanning, the threat actor attempts to set up a Transmission Control Protocol/Internet Protocol ( TCP/IP) connection with a server at every possible port.

0 notes
Text
Red Network Tool A tool for network exploration and info found. The current tool version...
Red Network Tool A tool for network exploration and info found. The current tool version consists of: 1. ifconfig. 2. Port scan(comprehensive, TCP, SYN, ACK, UDP). 3. Host discovery(scan for up devices on a local network). 4. DNS checks with geolocation information. 5. Banner grabbing. 6. Ping(send ICMP packets to a host to check connectivity). 7. Traceroute(diagnose route paths and measure transit delays). 8. Reverse ip lookup. 9. Censys. 10. Site technologies detection feature. 11. Honeypot probability. 12. Mac address lookup. 13. Dns mapping. https://github.com/Red-company/RedNetwork_Tool

-
2 notes
·
View notes
Video
youtube
What is TCP 3 Way Handshake? | Fundamentals of Cybersecurity
In this video we will understand, the three way handshake of TCP. The steps from connection establishment to Connection Terminate are as follows, TCP - uses 3 way handshake for establishing connection. a) Client - SYN - "I want to Connect" b) Server - SYN, ACK - "I'm willing to accept a connection, but i need to connect to you" c) Client - ACK - "OK, I'm willing to accept the connection as well". d) Client and Server exchange the data. e) If either side send that RST (Reset) during this exchange, the connection is going to be abort. f) Client finishes the connection by FIN to server --"Good bye from client" g) Server ACK to client FIN packet, server will also send FIN-ACK to say "Good bye from server" h) Client - ACK to server (I got you FIN ACK) Subscribe for more videos : https://lnkd.in/eV3JaUA Follow me on Twitter - https://lnkd.in/e__Sphj Follow me on Instagram - https://lnkd.in/e-CEcFH Follow my Facebook Page - https://lnkd.in/erR_xwW For more .NET related Projects : https://lnkd.in/fqEwq4i
0 notes
Link
Under the hood of Browsers
The web browser is inarguably the most common portal for users to access the web. The advancement of the web browsers has led many traditional “thick clients” to be replaced by browser enhancing its usability and ubiquity.
The web browser is an application that provides access to the webserver, sends a network request to URL, obtain resources, and represent them in an interactive way. Common browsers include Internet Explorer, Firefox, Google Chrome, Safari, and Opera.
Functionality of Web Browser
The browser presents the web resource you choose in the info window and proceed with user interaction. Basically, it is fetching, processing, displaying, and storing.
Structure of Web Browser

Fig. Web browser structure
User Interface
Browser Engine
Render Engine
Storage
UI BackEnd
JavaScript Interpreter (Scripting Engine)
Networking (HTTP at minimum, FTP, SMTP, email e.t.c)
User Interface
It is a space where interaction between user and browser (application) occurs via the control presented in the browser. No specific standards are imposed on how web browsers should look and feel. The HTML5 specification doesn’t define UI elements but lists some common elements: location bar, personal bar, scrollbars, status bar, and toolbar.
Browser Engine
It provides a high-level interface between UI and the underlying rendering engine. It makes a query and manipulates the rendering engine based upon the user interaction. It provides a method to initiate loading the URL, takes care of reloading, back, and forward browsing action.
Rendering Engine
Rendering Engine is responsible for displaying the content of the web page on the screen. The primary operation of a Rendering engine is to parse HTML. Rendering engine by defaults displays HTML, XML, and images and supports other data types via plugin or extension.

Fig. Rendering engine flow
Rendering Engine flow The modern browser uses different rendering engines. Gecko : Firefox Webkit : Safari Blink : Chrome, Opera (version 15 onwards).
The web content is displayed through a series of the process:
HTML Data to DOM
The requested content from the networking layer is received in the rendering engine (8 kb chunks generally). The raw bytes are then converted to a character (based upon character encoding) of the HTML file. Characters are then converted into tokens. Lexer carries out lexical analysis, breaking input into tokens. During tokenization, every start and end tags in the file are accounted for. It knows out how to strip out irrelevant characters like white space and line breaks.
The parser then carries out syntax analysis, applying the language syntax rule to construct the parse tree by analyzing the document structure. The parsing process is iterative. It will ask lexer for new token and token will be added to parse tree if language syntax rule match. The parser will then ask for another token. If no rule matches, the parser will store the token internally and keep asking for tokens until rule matching all the internally stored token is found. If no rule is found, then the parser will raise the exception. This means the document was not valid and contained syntax errors.
These nodes are linked in the tree data structure called DOM (Document Object Model) which establishes the parent-child relationship, adjacent sibling relationships.
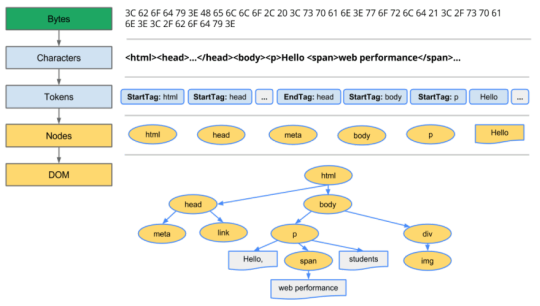
Fig. DOM Tree
CSS Data to CSSOM
Raw bytes of CSS data are converted into character, token, node, and finally in CSSOM (CSS Object Model). CSS has something called cascade which determines what styles are applied to the element. Styling data to the element can come from parents (via inheritance) or are set to the elements themselves. The browser has to recursively go through the CSS tree structure and determine the style of the particular element.

Fig. CSSOM Tree
Combination of DOM and CSSOM to Render Tree
DOM tree contains the information about HTML elements relationship and the CSSOM tree contains information on how these elements are styled. Starting from root node the browser traverses each of the visible nodes. Some nodes are hidden (controlled via CSS) and not reflected in the rendered output. For each visible node, the browser matches the appropriate rule defined in CSSOM and finally, these nodes are emitted with their content and styling called Render tree.

Fig.Render Tree
Layout
It then proceeds to the next level called layout. The exact size and position of each of the content should be calculated to render on a page (browser viewport). The process is also referred to as reflow. HTML uses a flow-based layout model, meaning geometry is computed in a single pass most of the time. It is a recursive process starting from the root element () of the document.
Painting
Each of the renderers is traversed and the paint method is called to display the content on the screen. The painting process can be global (painting the entire tree) or incremental (the render tree validates its rectangle on-screen) and OS generates the paint event on that specific nodes and the whole tree is not affected. Painting is a gradual process where some parts are parsed and rendered while the process continues with the rest of the item from the network.
JavaScript Interpreter (JS Engine)
JavaScript is a scripting language that allows you to dynamically update the web content, control multimedia, and animated images executed by the browser’s JS engine.DOM and CSSOM provide an interface to JS which can alter both DOM and CSSOM. Since the browser is unsure what particular JS will do, it will immediately pause the DOM tree construction after it encounters the script tag. Every script is a parse blocker; the DOM tree construction is halted.
The JS engine begins parsing the code right away after fetching from the server feeding into JS parser. It converts them into the representative object the machine understands. The object that stores all the parser information in the tree representation of the abstract syntactic structure is called an object syntax tree (AST). The objects are fed into an interpreter which translates those objects into byte code. These are Just In Time (JITs) compiler meaning JavaScript files downloaded from the server is compiled in real-time on the client’s computer. The interpreter and compiler are combined. The interpreter executes source code almost immediately; the compiler generates machine code which the client system executes directly.
Different Browser uses different JS engines
Chrome: V8 Engine (Node JS was built on top of this) Mozilla: Spider Monkey (formerly known as ‘Squirrel Fish’) Microsoft Edge: Chakra Safari: Nitro
UI Back End
It is used for drawing a basic widget like combo boxes and windows. Underneath it uses operating system user interface methods. It exposes a generic platform that is not platform-specific.
Data Storage
This layer is persistent which helps the browser to store data (like cookies, session storage, indexed DB, Web SQL, bookmarks, preferences, etc.) The new HTML5 specification describes a database that is a complete database in a web browser.
Networking
It handles all kinds of network communication within the browser. It uses a set of communication protocols like HTTP, HTTPs, FTP while fetching the resource from requested URLs.
Web Browser relies on DNS to resolve the URLs. The records are cached in the browser, OS, router, or ISP. If the requested URL is not cached in, the ISP DNS server initiates the DNS query to find the IP of that server. After receiving the correct IP address the browser establishes the connection with the server with protocols. The browser sends the SYN(synchronize) packet to the server asking if it is open for TCP connection. The server responds with ACK(acknowledgment) of the SYN packet using the SYN/ACK packet.
The browser receives an SYN/ACK packet from the server and will acknowledge by sending an ACK packet. Then TCP connection is established for data communication. Once the connection is established, data transfer is ready. To transfer the data, the connection must meet the requirements of HTTP Protocol including connection, messaging, request, and response rules.
Comparison of Browsers
There are many different web browsers in the market today. Although the primary application of the browser is the same, they differ from each other in more than one aspect. The distinguishing areas are platform(Linux, Windows, Mac, BSD, and other Unix), Protocols, Graphical User Interface(GUI), HTML5, open-source, and Proprietary, explained in details here.
Happy Browsing!
0 notes
Text
Transmission Control Protocol (TCP) Socket Connection
What is Transmission Control Protocol (TCP)?
Our android development team was working on one mobile app project when TCP came into picture. Basically, Transmission Control Protocol generally recognizes as TCP is a standard that allows establishment and maintenance of within network communication. It functions on the Internet Protocol (IP) to exchange application programs through a shared network. TCP and IP work hand in hand to define the mechanism of how computers interact with each other via data pockets. Our android development team was working on one mobile app project when TCP came into picture.
IP and TCP together are the basic ruling elements of internet protocol suite yet the Internet Engineering Task Force (IETF) specifies TCP as Request for Comments (RFC) standards of documentation. TCP originated as an individual protocol but further, it complimented IP, therefore, they are together referred to as TCP/IP. In network communication, TCP offers a reliable, error-tested, quality delivery stream of octets via an IP network. Major internet entities like World Wide Web, File transfer; Remote Administration, etc are under function based on TCP itself.
For example: In a real organizational context, Transmission Control Protocol (TCP) is utilized for peer to peer communication. As in this case, in order to consider an example, Transmission Control Protocol (TCP) Socket Connection that works as the source of inter-organizational conversation and file share. It is also called an IP messenger. This TCP socket connection is a computer application that functions on a shared LAN or Wi-Fi network. The basic functionality of the TCP socket connection is that it performs secured and reliable data transfer from the company server to the client or multiple clients as well. Organization and management of conversations are handed to the server host, as every message from the client or employee arrives at the server as well. It is a very simple protocol that requires only time configuration and then it allows multi-directional data transmission without any hiccups in the process.
TCP socket connection offers the following features:
TCP socket connection allows sending text messages to the individual who is linked by the same shared network. It can be a shared LAN or Wi-Fi connection.
TCP socket connection allows broadcasting the messages from any user or the server, under the range of common IP.
It allows verification of the sent message and received status to the server destination.
What Does Transmission Control Protocol (TCP) Work On?
Transmission Control Protocol (TCP) is a network-oriented protocol that pronounces that it first establishes a network and then manages a communication via data packets sharing between the devices under the same hosted network. It basically begins the function by breaking the data into data packets so that the network is capable to transfer it. It manages the flow of data packets being shared as it keeps track of data packets sent to and data packets received from inside the network. It means if in case the data packet or message is sent from one device then the admin or server would get the notification along with the device address of the sender. As TCP has a function of transmitting error-free data, it also manages the flow of retransmission of missed or out dropped data packages. Being an Open System Interaction (OSI) communication protocol, TCP works on parts of the layers such as the transport layer and the session layer.
Process of Transmission Control Protocol (TCP) functioning:
There are basically steps in the Transmission Control Protocol (TCP) function, namely, segmentation, multiplexing, three-way handshake, data sequencing and acknowledgment, and flow control. These functions that TCP deploys can be discussed as follows:
1. Segmentation : Segmentation is the process to bifurcate the big stream of data into smaller segments or sections. This basically allows the server or the host to send or receive any bulk of information over the shared network. While working in the transmission layer the act of segmentation is performed in order to develop small-sized data packets that a shared network can transmit from one device to another. For example: If in case the bandwidth of the shared network is 2MBPS and the size of the data file is 100Mb then the segmentation is performed to divide the data file into 50 small-sized data packets. Once the data packets of reduced size are created then they can be transmitted through available bandwidth with quite an ease. This segmentation takes place at the sender’s end but when the data reaches the server’s end then the destination host reconstructs the data file by connecting those small data packets.
In terms of segmentation only, TCP is all time pitted against User Datagram Protocol (UDP) as they both work on the transmission layer. Yet TCP stands well tall here as TCP supports data segmentation but UDP does not. The standout feature of TCP is that it performs the segmentation process on its own before setting it for via-bandwidth transmission.
2. Connection Establishment Or Multiplexing : As mentioned earlier Transmission Control Protocol (TCP) is a connection-oriented protocol, as it requires sending data only through a well-established network connection. Therefore, connection establishment is the second step of TCP function. Once the network between server and sub-devices is established then the transmission begins. This is ensured that TCP would not transmit any data without establishing a strong network.
3. Three-way Handshake : The data transmission via TCP is required to be secured and authorized therefore, there is the provision of the third step of TCP functioning. The three-way handshake is the methods of authentication which allows the data to be synchronized and acknowledged. In this activity, at first, the source or server sends a synchronization (SYN) segment to the other end of the sub-device or receiver. If the terms are acknowledged by the user then it responds back with synchronization/acknowledgment (SYN/ACK) segment. This ensures that the source and destination both have received the terms and then finally the primary source will send the Acknowledged (ACK) segment so that the handshake is completed. This three-way handshake signifies that a reliable and authentic connection is well established.

Once the three-way handshake is processed, then both of the parties, source and destination can transmit data. This can be a two-way data transfer or unidirectional, it only depends on the requirements of the shared network conversation. Yet TCP only requires the authentication of header data, as the first step of authentication is already performed in segmentation.
4. Sequencing and acknowledgment : This is the next step of Transmission Control Protocol (TCP) functioning, it can be considered as an intermediate step but a whole process in itself. It involves 4 sub-processes as detailed below:
Identification of lost data packets and recognition of information
Detection and removal of duplicate data packets
Recognition and sequencing of the dropped or off orderly arrived data packets.
Control and management of the dataflow or overflow of the data packets.
Sequencing and acknowledgment are the strong reliability check process of TCP as it involves recognition of authentic data packets, dropping of duplicate data packets and sequencing of the data packets as well.
To offer reliability, TCP assigns the numeric system or sequence numbering to ease transmitted segments or data packets. This helps the destination host in rearranging the order of data packets and detect if all the sent data packets are received. Only on the based on sequence numbers, the data file is reconstructed at the destination host. Once the sequencing part is over then the acknowledgment part begins.
It also works on the numeric system only but the order of acknowledgment numbers is in the opposite direction to the sequencing numbers. These acknowledgment numbers are sent to the source-destination as verification of received data. After all the verification a final acknowledgment number is sent from the destination host to the server which is one numeric higher than the actual number of data packets. If any sequencing or acknowledgment number is missing then it is an indication that a data packet is only missing. Once the source and host interchange the sequence numbers then the process of data exchange can be used anytime or they can interchange themselves in functions.
5. Flow Control : Transmission Control Protocol (TCP) performs the flow control process through windowing. Basically, windowing is the process of flow control itself. It is required when one source uploads bulky data files and the data packets are overloaded in the transmission signal then the flow control technique though windowing comes into play. It secures the system from problems like buffering and malfunctioning. In this process, the receiver device updates the sender device about its window size during the three-way handshake only. This way the destination host gives a precision of data load to be transmitted by the sender. Window size is basically a number of data packets that can be stored and processed in the receiver’s system. As the sender computer has a precision of the receiver’s window size therefore the flow of data packets is controlled by the sender itself.
For example: If the window size of the destination host is 10 then the source will only transmit 10 data packets, once these data packets are received by the destination host then the sender will get the confirmation notification. Then only the source will release further 10 numbers of data packets to the destination host. This is how the flow control in TCP is performed to prevent the transmission from buffering.
To enhance the performance of TCP, there is another brownie step performed. This step is called packet dropping and sequencing. In this step, duplicate data packets are dropped from the transmission and then the order of data packets that arrived off the order is set.
What Is Transmission Control Protocol (TCP) Used For?
TCP is used for inter-organizational or internal shared server to client communication purposes. It is used for such organizational conversations because it is authentic as well as a reliable source of communication and data transmission. It is utilized for ensuring the security of the sensitive information shared between the organization and clients. Irrespective of the amount of information being transmitted, TCP maintains the integrity of the data over the shared network. TCP is used as a higher priority when the total amount of data is required to be transmitted without any leakage from the higher-level protocols.
TCP/IP is used in the application layer in three different functions, mentioned as follows:
Inter-organizational peer to peer communication of file transfers; TCP/IP is used as, File transfer Protocol Secure Shell (SSH), and Telnet.
For e-mail transmissions, Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), etc are used as TCP/IP integrated functions.
In the web, access HTTP is a form of TCP/IP.
TCP/IP Stack:
All of these applications of TCP are only available in the application layer of the TCP/IP stack. Where TCP/IP stack is the virtual destination or model that represents the organization and transmission of data that have taken place over a shared IP. It represents the layers of information, based on how the data is stored, organized, handled and transmitted. It is basically a series of protocols traced over the data transmission from the server to the destination host and vice versa.
Parting Words:
Transmission Control Protocol (TCP) is a standard set protocol that allows inter-organizational communication over the shared IP. It shall be concluded that TCP and IP both individually make statement importance in Internet Protocol Suit but once they go hand in hand as TCP/IP, the applications like TCP socket connection can be developed. TCP deploys five stages of data transmission process such as segmentation, multiplexing, three-way handshake, data sequencing and acknowledgment, and flow control which makes it stand as a reliable, authentic and professional communication standard in the industries. TCP socket connection is an important application because it only allows data transfer inside the organization, and it reduces the hazards of data leakage outside the shared IP.
#tcp/ip#tcp#transmission control protocol#internet protocol#internet#networking#communication protocol
0 notes
Text
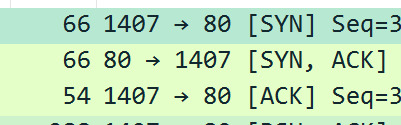
Identifying the traffic - Cont - SA
TCP: a connection-oriented protocol meaning that a connection is established and maintained until messages have finished being exchanged.
TCP’s three way handshake:
To begin the connection a SYN packet is sent across the network to check for open ports for connection. The target server receives this packet and responds with an ACK packet as confirmation. The client server receives this ACK packet and responds with an ACK packet.
Here is a three-way handshake I found on the wifi:
0 notes