#Nmap on Kali Linux
Explore tagged Tumblr posts
Text
Nmap Ping Sweep: Home Lab Network Ping Scan
Nmap Ping Sweep: Home Lab Network Ping Scan @vexpert #vmwarecommunities #100daysofhomelab #homelab #Nmaptutorial #Networkscanning #Pingsweepguide #Nmapcommandexamples #HostdiscoverywithNmap #Networksecurity #NmaponKaliLinux #TCPSYNACKpackets #ICMPscanning
There is perhaps not a better known network scan tool for cybersecurity than Nmap. It is an excellent tool I have used for quite some time when you have a rogue device on a network and you want to understand what type of device it is. Nmap provides this functionality along with many others. Let’s look at the Nmap Ping Sweep and see how we can use it as a network vulnerability ping scan to…

View On WordPress
#Host discovery with Nmap#ICMP scanning#Local Ethernet network scanning#network scanning#network security#Nmap command examples#Nmap on Kali Linux#Nmap tutorial#Ping sweep guide#TCP SYN/ACK packets
0 notes
Text
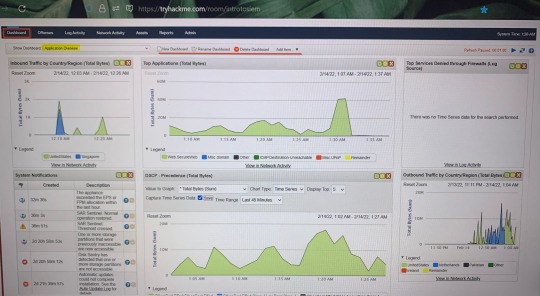
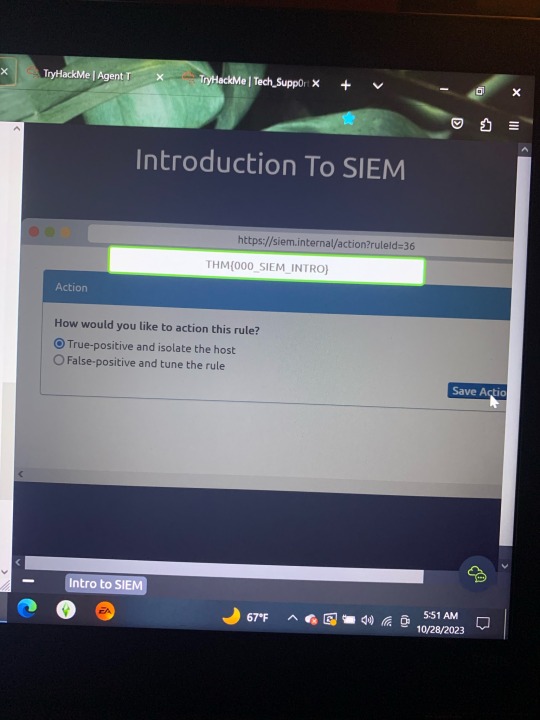

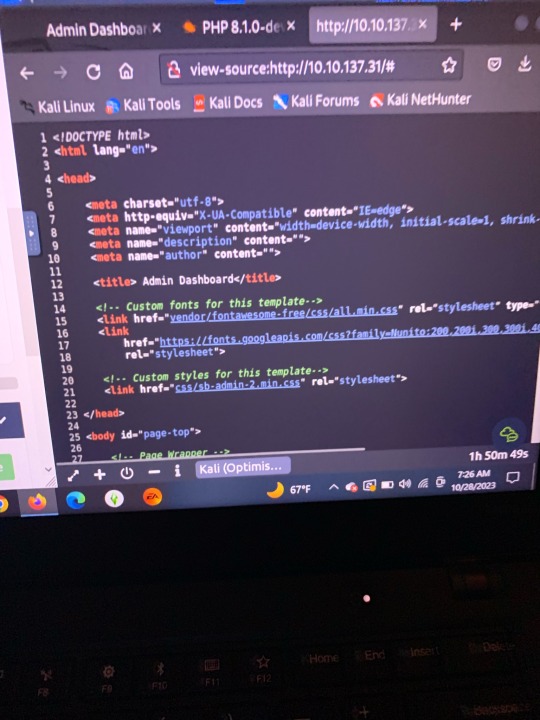
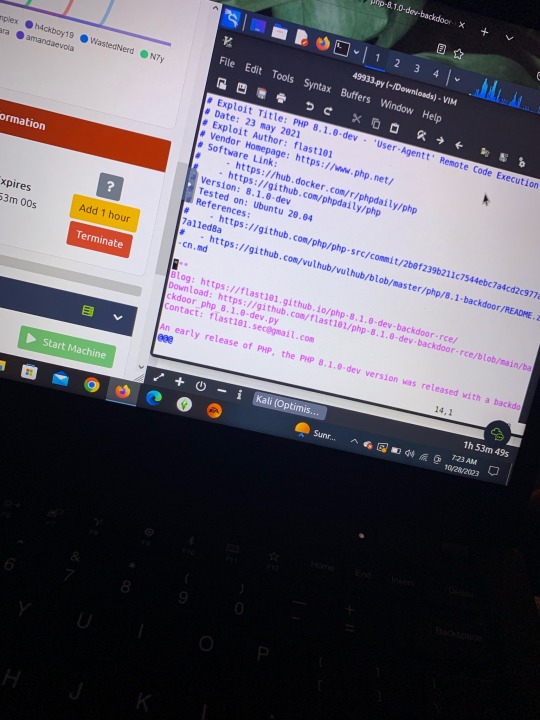
TryHackMe.. learning more of Nmap, Kali Linux, Burp Suite, etc. I am more a fan of defensive security/blue team (unpopular opinion) the first 2 pictures were walkthroughs of an SIEM (Security Information and Event Management).
#tryhackme#hacking#cool#blue team#red team#hacker#learning and growth#linux#kali linux#labs#tech#technology
4 notes
·
View notes
Text
How I Got Started in Ethical Hacking as a Complete Beginner
A few months ago, I had no idea what "ethical hacking" even meant. I just knew I was curious about how hackers think — and how companies defend against them. I began by understanding basic networking concepts, using tools like Nmap, Wireshark, and Kali Linux. I also explored some structured learning platforms that made everything less intimidating. One of the most helpful ethical hacking beginner-friendly resources I came across explained the fundamentals really well and included hands-on exercises. If you're just getting into this field. The key is consistency. Practice daily, stay ethical, and always aim to learn more.
0 notes
Text
Les 7 applications Android que tout hacker éthique doit avoir
L’univers de la cybersécurité évolue rapidement, et avec lui, les outils à la disposition des hackers éthiques. Que vous soyez débutant souhaitant apprendre les bases du hacking ou professionnel expérimenté en quête de solutions mobiles performantes, il existe aujourd’hui des applications Android puissantes qui vous permettent d’analyser, protéger et tester la sécurité d’un réseau ou d’un système directement depuis votre smartphone. Dans cet article, je vous présente les 5 meilleures applications Android que tout hacker éthique doit avoir, utilisables sans PC. 1. Termux – Le terminal Linux dans votre poche Pour tout hacker éthique, la maîtrise de la ligne de commande est essentielle. C’est là qu’intervient Termux, une application qui vous offre un terminal Linux complet directement sur votre Android, sans root. Avec Termux, vous pouvez : Installer des outils tels que nmap, hydra, ou sqlmap Écrire et exécuter vos propres scripts en Python, Bash, etc. Gérer des paquets via le gestionnaire APT Grâce à sa légèreté et sa compatibilité avec F-Droid, Termux devient le point de départ idéal pour tout environnement de test mobile. 📥 Télécharger Termux sur F-Droid 2. Kali NetHunter – La puissance de Kali Linux sur Android Une fois familiarisé avec l’environnement Linux grâce à Termux, vous pouvez passer à un niveau supérieur avec Kali NetHunter. Développée par Offensive Security, cette plateforme regroupe les principaux outils de test de pénétration dans une interface mobile. Ses atouts : Attaques man-in-the-middle (MITM) Injection de paquets, scan de ports, sniffing réseau Disponible en version rootless Kali NetHunter transforme votre téléphone en un véritable laboratoire de sécurité mobile, sans avoir besoin de rooter votre appareil. 📥 Télécharger Kali NetHunter 3. Orbot – L’anonymat avant tout Lorsque vous effectuez des analyses ou naviguez dans des environnements sensibles, protéger votre identité est crucial. C’est ici qu’intervient Orbot, un proxy mobile qui fait transiter vos données par le réseau Tor. Pourquoi l’utiliser : Masquer votre adresse IP Chiffrer le trafic sortant de vos applications Appliquer Tor à des applis spécifiques via VPN local Combiné à Termux ou NetHunter, Orbot garantit un niveau d’anonymat supplémentaire, indispensable lors de tests d’intrusion en réseau ou sur des applications distantes. 📥 Télécharger Orbot sur le site du Guardian Project 4. Fing – L’analyseur de réseau intelligent Maintenant que votre environnement est sécurisé, il est temps de scanner les réseaux à la recherche de failles potentielles. Fing est l’une des applications les plus complètes pour cette tâche. Fonctionnalités clés : Détection de tous les appareils connectés Analyse des ports ouverts et services actifs Identification des adresses IP, MAC, et constructeurs Fing est extrêmement simple à utiliser et vous permet d’auditer la sécurité d’un réseau Wi-Fi en quelques minutes, directement depuis votre téléphone. 📥 Télécharger Fing sur Google Play 5. FakeTraveler – Falsifiez votre localisation GPS sans root Dans certaines situations, il peut être utile de simuler une autre localisation GPS sur votre smartphone, que ce soit pour préserver votre vie privée, tester des applications sensibles à la géolocalisation ou valider des comportements en conditions simulées. FakeTraveler répond parfaitement à ce besoin en proposant une interface simple et intuitive : Une carte interactive où vous pouvez sélectionner la localisation désirée via un appui long Possibilité d’appliquer la localisation fake immédiatement Options avancées pour simuler la localisation sur une période donnée Pas besoin de root : l’application utilise la fonctionnalité "Mock Location" disponible dans les options développeur Android 📥 Télécharger FakeTraveler sur F-Droid 6. WiFiAnalyzer – Analyse des réseaux Wi-Fi WiFiAnalyzer vous aide à visualiser les réseaux Wi-Fi environnants, identifier les canaux encombrés et optimiser votre propre réseau.
Fonctionnalités principales : Détection des réseaux Wi-Fi à proximité Analyse des canaux pour éviter les interférences Graphiques en temps réel de la puissance du signal 📥 Télécharger WiFiAnalyzer sur Google Play 7. NetHunter Store – Accès à des outils spécialisés Le NetHunter Store est une boutique d'applications basée sur F-Droid, offrant une collection d'outils de sécurité et de hacking éthique, même sans installer Kali NetHunter. Fonctionnalités principales : Accès à des applications comme WiFi Analyzer, cSploit, et plus Téléchargements sécurisés sans télémétrie Interface adaptée aux professionnels de la sécuritéMyGreatLearning 📥 Accéder au NetHunter Store En combinant ces cinq applications, vous disposerez d’un environnement de test de pénétration complet et mobile. ⚠️ Rappel important : n’utilisez ces outils que dans un cadre légal et éthique — par exemple sur votre propre réseau, sur des environnements de test, ou dans le cadre d’un audit autorisé. Le hacking éthique n’est pas un jeu, c’est une discipline sérieuse et précieuse pour la sécurité numérique de tous.
0 notes
Text

Master Ethical Hacking with Evision Technoserve
Master Ethical Hacking with Evision Technoserve! Dive into the world of cybersecurity with expert-led training in NMAP for network scanning, and Kali Linux for penetration testing. Gain hands-on experience through real-world scenarios designed to build practical skills. Our career-focused curriculum prepares you to ethically hack and defend like a pro. Whether you're starting out or advancing your career, Evision gets you job-ready.
0 notes
Text
Advanced program in cybersecurity and ethical hacking
Become a cyber defense expert with our Advanced Program in Cybersecurity & Ethical Hacking—hands-on hacking, threat hunting, and real-world simulations.
https://techcadd.com/advanced-program-in-cybersecurity-and-ethical-hacking.php
Master the Digital Battlefield with TechCadd’s Advanced Program in Cybersecurity and Ethical Hacking
cybersecurity is no longer optional—it's a critical requirement for individuals and organizations alike. As cyber threats grow more sophisticated, so does the demand for skilled professionals who can detect, prevent, and counter cyber attacks. To address this growing need, TechCadd has launched its Advanced Program in Cybersecurity and Ethical Hacking—a powerful course designed for future-ready professionals seeking a competitive edge in the world of information security.
What Makes This Program Stand Out?
TechCadd’s Advanced Program in Cybersecurity and Ethical Hacking is meticulously structured to provide both theoretical foundations and practical expertise. Unlike basic certification courses, this program dives deep into advanced security concepts, offering participants hands-on training with real-world tools and techniques used by industry experts.
The curriculum starts with networking and operating systems, gradually moving into advanced domains like penetration testing, system exploitation, vulnerability assessment, and secure coding practices. Students also learn how to use essential cybersecurity tools such as Metasploit, Nmap, Burp Suite, and Kali Linux through instructor-led labs and guided simulations.
Bridging the Skill Gap
As digital transformation accelerates, businesses across sectors—from finance and healthcare to e-commerce and government—are facing constant cyber threats. However, there's a growing shortage of professionals who can effectively mitigate these risks. This Advanced cybersecurity and ethical hacking course is designed to bridge that gap, transforming learners into skilled defenders who understand both attack strategies and countermeasures.
Whether you’re an IT graduate, a system administrator, or someone looking to pivot into cybersecurity, this course offers a pathway to meaningful, high-demand roles. The emphasis on ethical hacking prepares students to think like attackers in order to build stronger defenses.
Who Can Join?
The course welcomes a wide range of participants:
IT and networking professionals
Computer science students
Cybersecurity enthusiasts
Working professionals seeking upskilling opportunities
Business owners looking to secure their digital infrastructure
No previous hacking experience is required. The program’s step-by-step approach ensures that learners of all levels can grasp complex topics with ease.
Certification and Career Support
Upon completing the Advanced Program in Cybersecurity and Ethical Hacking, students receive a certificate that verifies their expertise and practical skills. TechCadd also provides career support services, including resume guidance, mock interviews, and job placement assistance with hiring partners.
With cybercrime on the rise, having a recognized credential in cybersecurity and ethical hacking not only boosts your resume but also demonstrates your commitment to digital safety and ethical practice.
Why TechCadd?
TechCadd is known for its hands-on teaching style, up-to-date course content, and experienced instructors. Its Advanced cybersecurity and ethical hacking course is more than just academic—it prepares students to face real-world cyber challenges through projects, live scenarios, and team-based problem-solving.
Conclusion
As technology evolves, so do cyber threats. The Advanced Program in Cybersecurity and Ethical Hacking by TechCadd offers a future-proof skill set for those who want to stay ahead in a fast-changing digital landscape. Whether you're starting your career or enhancing your current role, this program provides the tools, knowledge, and credentials needed to thrive in the cybersecurity arena.
#CyberSecurity#InfoSec#CyberDefense#NetworkSecurity#CloudSecurity#EthicalHacking#WhiteHat#PenTesting#BugBounty#HackTheBox#HackerLife
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
How I Got Started in Ethical Hacking as a Complete Beginner
A few months ago, I had no idea what "ethical hacking" even meant. I just knew I was curious about how hackers think — and how companies defend against them. I began by understanding basic networking concepts, using tools like Nmap, Wireshark, and Kali Linux. I also explored some structured learning platforms that made everything less intimidating. One of the most helpful beginner-friendly resources I came across explained the fundamentals really well and included hands-on exercises. If you're just getting into this field, check out this guide that helped me understand things step-by-step. The key is consistency. Practice daily, stay ethical, and always aim to learn more.
1 note
·
View note
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
Kali Linux
ego logu Nmap wynika, że masz teraz trzy urządzenia, które są widoczne w Twojej sieci: funbox.home (192.168.1.1) - Router. desktop-bedkeu2.home (192.168.1.44) - Inne urządzenie w sieci, które ma adres MAC D4:54:8B:4B:D1:33, ale nie jest rozpoznane (jest to "Unknown"). Możliwe, że to komputer stacjonarny lub laptop. kali.home (192.168.1.11) - Twój komputer z systemem Kali Linux. Enter fullscreen…
0 notes
Text
Top 10 Kali Linux Tools for 2025

Kali Linux is the go-to operating system for ethical hackers and cybersecurity professionals, offering over 600 tools for tasks ranging from network analysis to digital forensics. Among its top tools are Nmap, a network mapper for scanning vulnerabilities; Metasploit Framework, ideal for exploit development; and Wireshark, a packet analyzer for real-time network traffic monitoring. Tools like Aircrack-ng and Hydra cater to wireless and login security, while Burp Suite and OWASP ZAP excel in web application security. Whether you’re testing passwords with John the Ripper or scanning servers with Nikto, Kali Linux equips you to handle critical cybersecurity challenges.
Mastering these tools ensures robust security defenses and deeper insights into vulnerabilities. From web exploitation with BeEF to multi-protocol attacks with Hydra, these utilities cover the spectrum of cybersecurity needs. Beginners and experts alike can harness Kali Linux to secure systems and assess risks effectively. For more information, Please Read https://srutatech.com/2025/01/28/top-10-kali-linux-tools-for-2025/
#software development#digitalmarketing#digitalmarketingseo#digital marketing#digital marketing bensalem#app development#web development#digitalmarketingbensalem#digital marketing philadelphia
0 notes
Text
Building a hacker laptop ?
Start with Kali Linux or Parrot Security OS for your operating system. Ensure your laptop has at least 8GB of RAM, an SSD, and a strong CPU for optimal performance. Pre-install tools like Metasploit, Nmap, and Wireshark for penetration testing and network analysis. Always enable encryption, a firewall, and a VPN to stay secure. Consider using VirtualBox or VMware for virtualization to run multiple systems. Ready to dive into ethical hacking? Click Here to read more.
1 note
·
View note
Text
جميع أوامر termux للأختراق والتهكير all Commands Termux
أوامر في تطبيق Termux م�� خلال هذا المقال سوف نتعرف على كل أوامر termux وشرح اهم الأوامر في تطبيق Termux للأختراق وكيفيه التعامله معه تطبيق Termux يعتبر من اهم التطبيقات التي يجب عليك تثبيته على هاتفك الأندرويد فأنت لست بحاجه لجهاز حاسوب لكي تتعلم الأختراق ولكن علينا اولاً ان نتعرف على التطبيق شرح termux commands list وما هي الاومر الاولى في تشغيل termux قبل البدء كل هاذا سوف نتعرف عليه من خلال هذا المقال . termux commands list
جميع أوامر termux للأختراق والتهكير all Commands Termux
اوامر termux للاختراق كنا قد نشرنا مواضيع كثيرة حول تطبيق تيرمكس وربما من اشهر هذه المواضيع شرح جميع اوامر Termux لكن اليوم سوف نقدم مجموعه اخرى من الأوامر المهمه والتي من خلالها سوف تتعرف على كيفيه التعامل مع تطبيق تيرمكس بشكل ممتاز دون الحاجه الى اي مساعدة من احد , وربما من اهم ما يجب ان تتعلمه هوا termux commands list اي أوامر تيرمكس وهذه امر مهم جداً فمن دونها لن تتكمن من التعامل مع التطبيق فلكل امر وظيفه معينه يقوم بها مثل تحميل الأدوات والتنقل بين الملفات وفهم الصلاحيات وغيرها اوامر termux .
لكن ما هوا termux وفيما يستعمل , حسناً دعني اجيبك بشكل مبسط تيرمكس اوامر termux هوا تطبيق عبارة عن Terminal اي سطر اوامر مبني على اللنكس من خلاله يمكنك تحميل ادوات الأختراق او وتشغيل سكربتات بللغات برمجيه مختلفه مثل Paython وغيرها فهوا شبيه الى حد ما في نظام Kali linux ولكن تيرمكس يعمل على الهاتف اي لست بحاجه الى جهاز كمبيوتر اوامر termux للاختراق .
أهم أوامر تشغيل termux قبل الأستعمال
pkg update pkg upgrade pkg install python pkg install python2 pkg install python3 pkg install ruby pkg install git pkg install php pkg install java pkg install bash pkg install perl pkg install nmap pkg install bash pkg install clang pkg install nano pkg install zip pkg install unzip pkg install tor pkg install sudo pkg install wget pkg install openssl
أوامر Termux لأنشاء ملفات والتنقل بينها
touch لأنشاء ملف جديد cat أنشاء ملف جديد بمحتوى echo “hello world” انشاء ملف جديد وكتابه بداخله cat >> [file name] – اضافه محتوى في ملف موجود مسبقاً mkdir [name] – انشاء فولدر او ملف جديد
أوامر النسخ واللصق Termux
cp لنسخ الملفات cp -r لنسخ الملف في اي مسار mv يستعمل لنقل الملفات من مسار الى اخر mv -v يستعمل لنقل اي ملف mv [file1 name] نقل واعادة تسميع الملف mv -i التحريك والكتابه فوق الملف mv -f – نقل الملف والكتابه فوقه بشكل اجباري
أوامر التنقل بين الملفات Termux
cd يستخدم لتنقل بين الملفات cd / يستعمل للرجوع الى ملف الروت cd .. لرجوع خطوة الى الخلف
وهذه أوامر الأخرى اساسيات termux
rm لحذف الملف pwd لمعرفه مسارك wget لتحميل الأدوات git clone لتحميل الأدوات من رابط apt install curl لتحميل apt search للبحث عن حزم unzip لفك الضغط عن الملف bye لعمل اغلاق لسطر الأوامر whoami – لمعرفه اسم المستخدم nano لتعديل على ملف ifconfig لمعرفه اي بي جهازك
تحميل جميع ادوات termux
Termux-kalinetHunter
git clone https://github.com/Hax4us/Nethunter-In-Termux cd Nethunter-In-Termux chmod +X* ./kalinethunter
Lazymux Tool
قد يعجبك ايضا
منذ عام
جميع أوامر termux للأختراق والتهكير all Commands Termux
منذ عام
تحميل كتاب أساسيات Termux للأختراق على الهاتف PDF
منذ عام
كتاب جميع أوامر تطبيق Termux
git clone https://github.com/Gameye98/Lazymux cd Lazymux chmod +X* python2 lazymux.py
Tool-X
pkg install git git clone https://github.com/Rajkumrdusad/Tool-X.git cd Tool-X chmod +x install.aex sh install.aex
اوامر Termux لاستخراج المتاحات
xHak9x
apt update && apt upgrade apt install git python2 sudo git clone https://github.com/xHak9x/fbi.git cd fbi sudo pip2 install -r requirements.txt sudo python2 fbi.py
theHarvester
git clone https://github.com/laramies/theHarvester ls cd theHarvester python2 theHarvester.py pip2 install requests python2 theHarvester.py -d hotmail.com -b google -l 500 python2 theHarvester.py -d yahoo.com -b google -l 500
أوامر termux اختراق wifi
wifiphisher
apt-get install git python apt-get install python python-pip python-setuptools pip install scapy git clone https://github.com/wifiphisher/wifiphisher.git cd wifiphisher python setup.py install cd wifiphisher python wifiphisher
جميع اوامر Terminal Emulator للاندرويد
dhcpcd dmesg dnsmasq dumpstate dumpsys dvz fsck_msdos gdbserver getevent getprop gzip hciattach hd id ifconfig
ash awk base64 bash busybox cat chmod chown cksum clear cmp cp cut date dd df diff dirname echo env expr false fgrep find gawk grep gunzip gzip head id install kill killall ln ls md5sum mkdir mknod mktemp mv nice nl nohup od paste patch pgrep pkill ps pwd readlink realpath rm rmdir sed seq sha1sum sha256sum sha3sum sha512sum sleep sort split stat stty sum tail tar tee test timeout touch tr true uname uniq unzip uptime users wc which xargs yes zcat ls: قائمة الملفات والدلائل في الدليل الحالي اوامر termux للاختراق . cd: قم بتغيي�� دليل العمل الحالي. mkdir: إنشاء دليل جديد. touch: قم بإنشاء ملف جديد. echo: إخراج النص المحدد. cat: عرض محتويات الملف. grep: ابحث عن أنماط في الإدخال. wget: قم بتنزيل ملف من الإنترنت. curl: نقل البيانات من أو إلى الخادم. apt-get: تثبيت أو إزالة الحزم من مدير الحزم. apt-cache: الاستعلام عن قاعدة بيانات مدير الحزم. find: البحث عن الملفات في التسلسل الهرمي للدليل. gzip: ضغط الملفات أو فك ضغطها. tar: إنشاء أو استخراج أو سرد محتويات أرشيف القطران. ssh: الاتصال بجهاز بعيد باستخدام بروتوكول SSH.
0 notes
Text

With all the hassles present on the internet, brings forth the importance of cyber security, be it an average citizen an aspiring IT specialist or a student. Every individual can learn the cyber environment and enhance their skills with the right set of tools. Following is a list of free tools for cybersecurity tools every beginner should explore.
1. Wireshark
A hugely potent organized protocol analyzer wireshark enables you to analyze data packets in real times by capturing them. It is an excellent tool for analyzing organized network issues, learning about the functions of networks, and investigating basic-level functions. It can be used by beginners to gain insights on the movement of information across a network and also pinpoint existing potential security issues.
Features:
Pckect analyzing in real-time.
Supports a wide array of protocols.
Easy to use with many visual representations.
2. Nmap (Network Mapper)
A tightly held toolkit for those practicing ethical hacking and penetration testing is a fantastic tool for planning and discovering systems and security audits Nmap. It allows novices to scan systems and enumerate hosts services and ports that are active. Its primary purpose is to scan networks and host services.
Features:
Scan at a super fast speed.
Maps advanced network attractions.
Compatible with multiple operating systems.
3. Metasploit Community Edition
Metasploit could be a broadly utilized entrance testing system. The community edition is free and culminates for tenderfoots to memorize vulnerabilities, misuses, and payloads. It's an intelligent way to see how aggressors can compromise frameworks and how to secure them.
Features:
Extensive library of exploits and payloads.
Easy-to-use graphical interface.
Ideal for practicing ethical hacking techniques.
4. Kali Linux
Kali Linux could be a Debian-based Linux dispersion particularly planned for entrance testing and security examination. Stuffed with a wide cluster of tools, it's a one-stop shop for anybody inquisitive about cybersecurity.
Features:
Pre-installed cybersecurity tools.
Lightweight and customizable.
5. Burp Suite Community Edition
Burp Suite may be a favorite among web application security analyzers. The community version is free and incorporates apparatuses for reviewing HTTP demands, analyzing web vulnerabilities, and understanding how web apps work.
Features:
Comprehensive suite for web vulnerability scanning.
User-friendly interface.
Supports learning about web security.
6. CyberChef
Known as "The Cyber Swiss Armed Force Cut," CyberChef may be a web-based tool for encryption, encoding, and information examination. Its instinctive drag-and-drop interface makes it perfect for apprentices investigating the essentials of cryptography and information change.
Features:
Simplifies data processing tasks.
Hundreds of available operations.
Accessible via a web browser
7. OWASP ZAP (Zed Attack Proxy)
OWASP Destroy is an open-source web application security scanner. It is a beginner-friendly apparatus to memorize approximately web vulnerabilities like SQL infusion, cross-site scripting (XSS), and more.
Features:
Automated vulnerability detection.
Supports manual testing.
Detailed reports and logs.
8. Hashcat
Hashcat may be a free watchword recuperation device that makes a difference to clients getting the significance of secret word security. It bolsters a wide assortment of hashing calculations and illustrates how powerless passwords can be split.
Features:
High-performance password cracking.
Supports GPU acceleration.
Multi-platform support.
9. Vega
Vega is another web security scanner that is well-suited for beginners. It's open source, free, and helps to identify vulnerabilities in web applications. Not very hard to figure out, but very helpful.
Such simple tools are most likely never going to help in things such as penetration testing.
XSS and SQL injection are some of the most common they get through to use the graphical interface they have.
10. ClamAV
ClamAV is another tool that most probably every cybersecurity deploys. Cross-platform functionality always plays a critical role for users as not only are they bound to a particular OS. In terms of the tools available, there is a command line option and also a Graphical User Interface.
Conclusion
Investing in these tools will give you a practical ability on how things work, from advanced systems analysis to web application security. Also, users must remember that these are ethical dilemmas and that all users need to comply with the laws of the land. It should make you better equipped to face the advancing technical era out there. So what are you waiting for, grab this opportunity. visit us Enbridg
0 notes