#Manage Multiple VMs
Explore tagged Tumblr posts
Text
Easily Manage Multiple Hyper-V Hosts with the built-in MMC
There are more IT shops using Microsoft’s Hyper-V than ever before. Thanks in part to Broadcom’s shenanigans with the licensing after they purchased VMware, more are considering making the change every day. One challenge that causes organizations to pause when considering Hyper-V is the apparent lack of centralized host management. It’s true, Hyper-V doesn’t include a direct vCenter equivalent…
0 notes
Text
05/13/2024
‼️needed ASAP!!!‼️
Hey, so one of my coworkers at my job just quit this week and management off loaded all their hours on to me bc our department is short staffed
I now have multiple full shifts this week with no food for lunches! I've been skipping meals at work due to lack of funds and my body really can't take it anymore! I need to be able to feed myself.
I need $180 for groceries for my lunches plus household toiletries, I'm having a real rough time before I get paid, pls lend a hand if you Can!!
CA: $lezsalt or $sleepyhen
VM: wildwotko
Dm 4 PP
#sorry we are poor#shout out to her for standing up to managements bullshit#but like girl im gonna miss you 😭#now im just surrounded by cishet dudes#thank you for the hours ig but i need to eat i cant just keep enduring
986 notes
·
View notes
Text
Whoa!!! Nice start to the morning. I issued a property lien for non payment of services on a real winner about two months ago and she just figured it out this morning. I answered the call and had to hold the phone away from my ear because she screamed at the top of her voice saying I was a piece of shit preying on poor folks sitting in my temple of evil. I sat quietly until she was out of breath and referred her to our company attorney. She screamed in a crackling voice that she knows I have to be a god damn “librel” taking from the God fearing good people that hold this country up for cocksuckers like me and when Trump gets back to the White House he’ll dispose of trash like me. I told her to have a great day and she said she hopes that me and my family all die. All I could do was laugh at this point and hang up. She tried calling 10 more times and I just hit the VM button.
By the way this financially poor woman owns multiple properties in several states and just bought a car that cost three times my yearly salary and paid CASH. Bless her heart shes overwhelmed with wealth and can’t manage such a burden. My heart breaks for her. 🤮
22 notes
·
View notes
Text
For future reference (my own and others), if your TI SilverLink USB cable stops working and starts showing up as "TUSB3410 Boot Device" or similar under device manager (AKA this issue on TI's help page), this is how you can fix it:
Download the TUSB3x10 EEPROM Burner. This is a Windows-only program, but to my knowledge will work on basically any windows machine from XP on -- so long as it's got USB ports. No clue if it'll work in a VM. (You might want to consult this user's manual.)
Download the SilverLink firmware. I got it from here, and compiled it from their de-compilation. It's just a standard 'make' to build. The output file you're looking for is called "ti_graph_link_silver.eep".
Rename "ti_graph_link_silver.eep" to "ti_graph_link_silver.bin".
Open the TUSB3x10 EEPROM Burner, click on the options dropdown and click "Show the 'Program Full Binary Image' button". (page 7 of the manual).
Select the entry under "Computer" labeled "TUSB3410 EEPROM Burner Instance (1.00)".
Set EEPROM size to "64Kb".
Set "File Path" to point to "ti_graph_link_silver.bin". (The renamed .eep, not the original .bin)
I don't know if the VID, PID, Manufacturer string, Product string and Serial # need to be set manually or not with a 'Full Binary Image' burn. Just to be safe, I set VID to 0451, PID to e001, Manufacturer to "Texas Instruments", Product to "TI-GRAPH LINK USB", and checked "Not Serialized"*.
Click the "Program Full Binary Image" button (yellow triangle with the exclamation point), and proceed with the write.
Unplug and re-plug your cable, and it should show up as a SilverLink again!
Additional notes:
The reason that this happens is because the SilverLink cable (revision b, at least) is based on the TUSB3410 microcontroller. That microcontroller's boot process involves checking for an I2C EEPROM containing program code. If it finds that EEPROM and its contents are properly formatted, it'll copy that code into internal RAM and start executing it. If it can't find the EEPROM, or its contents aren't properly formatted, it'll fall back to looking for boot code over USB. Thus: "TUSB3410 Boot Device". Your cable has, in essence, forgotten who it is and and is begging for you to give it a purpose.
The default page-write buffer size (32 bytes) and I2C bus speed (400 KHz) in the burner app are already correct, so no need to change them.
*I don't remember exactly what the Manufacturer string, Product string, or serial number fields were set to pre-corruption. Likewise, no idea about the advanced descriptor options. If someone wants to send the output of lsusb -v -s [whatever their silverlink's bus/id numbers are], I'd really appreciate it!
You might be able to skip the header rigamarole by taking the ti_graph_link_silver.bin file directly ("directly coming from the compiler") -- but I again I don't know exactly what information is in the .eep file and what isn't. Are the PID and VID encoded somewhere in there? I peeked with a hex editor but have no clue. If someone has hardware lying around they're willing to experiment with/potentially brick, I'd love to hear your results!
If you mess up and accidentally forget to do a "Full Binary Image" write, or otherwise brick the firmware, you can force the TUSB3410 to fall back to USB boot mode by opening the plastic shell around the PCB (one Torx screw under the sticker, then just normal plastic tabs) and shorting the right-bottom (Vss) and right-top (SDA), or right-bottom (Vss) and center right-top (SCL) pins of the EEPROM (the chip labeled "24LC64") as you plug it into the USB port. You may need multiple attempts. This works because it temporarily convinces the TUSB3410 that the EEPROM is missing/corrupt, and thus it decides to fall back into USB boot mode -- until you reset it. It might be better to do this with a ~1k resistor instead of a jumper wire, but IDK I'm not an electrical engineer. All I know is that shorting Vss and SDA worked for me. Again, would love feedback.
No clue what causes the corruption in the first place, or how long this fix will last. It might be because the EEPROM's write protect pin is set to "write enable"? It could also just be degrading hardware, for all I know, so no idea how long the fix will last. All I do know is that everything seems nominal right now (immediately after performing this procedure).
10 notes
·
View notes
Text
How can you optimize the performance of machine learning models in the cloud?
Optimizing machine learning models in the cloud involves several strategies to enhance performance and efficiency. Here’s a detailed approach:

Choose the Right Cloud Services:
Managed ML Services:
Use managed services like AWS SageMaker, Google AI Platform, or Azure Machine Learning, which offer built-in tools for training, tuning, and deploying models.
Auto-scaling:
Enable auto-scaling features to adjust resources based on demand, which helps manage costs and performance.
Optimize Data Handling:
Data Storage:
Use scalable cloud storage solutions like Amazon S3, Google Cloud Storage, or Azure Blob Storage for storing large datasets efficiently.
Data Pipeline:
Implement efficient data pipelines with tools like Apache Kafka or AWS Glue to manage and process large volumes of data.
Select Appropriate Computational Resources:
Instance Types:
Choose the right instance types based on your model’s requirements. For example, use GPU or TPU instances for deep learning tasks to accelerate training.
Spot Instances:
Utilize spot instances or preemptible VMs to reduce costs for non-time-sensitive tasks.
Optimize Model Training:
Hyperparameter Tuning:
Use cloud-based hyperparameter tuning services to automate the search for optimal model parameters. Services like Google Cloud AI Platform’s HyperTune or AWS SageMaker’s Automatic Model Tuning can help.
Distributed Training:
Distribute model training across multiple instances or nodes to speed up the process. Frameworks like TensorFlow and PyTorch support distributed training and can take advantage of cloud resources.
Monitoring and Logging:
Monitoring Tools:
Implement monitoring tools to track performance metrics and resource usage. AWS CloudWatch, Google Cloud Monitoring, and Azure Monitor offer real-time insights.
Logging:
Maintain detailed logs for debugging and performance analysis, using tools like AWS CloudTrail or Google Cloud Logging.
Model Deployment:
Serverless Deployment:
Use serverless options to simplify scaling and reduce infrastructure management. Services like AWS Lambda or Google Cloud Functions can handle inference tasks without managing servers.
Model Optimization:
Optimize models by compressing them or using model distillation techniques to reduce inference time and improve latency.
Cost Management:
Cost Analysis:
Regularly analyze and optimize cloud costs to avoid overspending. Tools like AWS Cost Explorer, Google Cloud’s Cost Management, and Azure Cost Management can help monitor and manage expenses.
By carefully selecting cloud services, optimizing data handling and training processes, and monitoring performance, you can efficiently manage and improve machine learning models in the cloud.
2 notes
·
View notes
Text

Enemies to Lovers? Thank You, Yes, Think I Will... <3
***spoilers***
Wasn't reeeeeeellli planning to write about this one here. But surprised myself by enjoying it. Surprised myself again by discovering that it's based on a book (probably the publishing house setting was a big clue but not one I feel confident relying on fully).
Gave it a go because I'd vm enjoyed Lucy Hale in the (for me) ridiculously named but surprisingly rounded / robust / landing-achieving Puppy Love (2023), opp Grant Gustin from Flash/Glee.
I thought she did a great job of being "kooky" without shading across into unfathomably irrational and managing to deliver high charm almost all the way through. Didn't say it there so I'll say it here - felt to me like there was very significant fondness and almost no heat in the depiction of the MC rels... if there was room for love stories that were largely ace/platonic, maybe this would be a good place to land that particular love story? I do get it, that this isn't An Option, in terms of the mainstream tropes or audience expectation. YET??
BTW - veering //AGAIN// - saw analysis of La La Land that suggested it works (and doesn't REALLY have a sad/unsatisfactory ending) because the nature of the love the MCs have for each other is preserved and merely shifts from romantic towards platonic. (?)
youtube
If I remember correctly, the commentator thought that the central relationship in La La Land was pretty healthy - that each of the MCs were doing more and most of their work on their own personal issues.
I'm going to guess that he probably wouldn't feel this way about the relationship in The Hating Game, though it's sweeter and kinder sooner and for more of the movie than the title or opening suggested.
Thanks to BuzzFeed article by Farrah Penn (Dec 23, 2021), I now know that the opening line for the movie is also the - deliciously hooky - opening line for the book. Put the pitch into the start of the story - why not? It absolutely got me to stay to see how it played out.
[But perhaps, watching through my fingers, because as I may have mentioned, I'm not actually a fan of storylines that involve the MCs being psychotic, either towards each other or in general. Yes, it generates tension but not in a way I find v. enjoyable to invest in.]

Things I liked -
That he genuinely took care of her (multiple times but I'm thinking of when she's ill). That she stuck up for him at the family event. That he wants a relationship not a hook-up (I read this as gender-reversed?).
Things I liked LESS -
The moments in the plot where they "have to fight" or "have to fall out" - I was genuinely mystified about how the film could take them from a declaration of love on his part to right back to sq one on her part (convinced he's the enemy) in roughly 3 mins of screen time.
UGH.
The fact that he reads to me like a man who's been written by a woman. What? We give male writers a hard time when they write women really badly. For me, this reads WELL for the story and POORLY in terms of whether this could be an actual living male. Perhaps it could - but (again, for me) the confection lasted only as long as the film's HEA and then fell over like cardboard caught in rain.
By contrast, I bought GG's character as highly neurotic but believable as a character in his own right - the bond they make gives him back to himself. I can imagine him existing independently in that world.
Back to The Hating Game -
Also, didn't love the decision to give him a mostly nude scene where the female MC was clothed. Good for LH that her contract allows her to keep her clothes on. Good - I guess - that the film shows us the female gaze where the male gaze has traditionally been. But how about we abolish Uneven Gazing altogether (??). For my own taste, clothes on or covered would have been Fine, just Fine. But main ask is for a couple mutually revealed to each other - a balance. Evenness.
Also, I accept that I may not be representing the maj view here in my general request for screen couples to kiss hotly but retain their attire.
So, yes, this isn't what I'd design For Me but sure, I can be happy to let beautiful people carry on being gorgeous on screen and for them to look longingly at each other (as proxies for how we are no doubt looking at them from our sofas). In principle I'm body positive - tho in practice, I'm still basically awkward, shy and old-style British.
Final thought - fascinates me how perceptions about levels of chemistry differ. For me, these actors had great on-screen chemistry but I've seen at least one review that felt they absolutely did not.
For me, it seems more like the problems for this couple are going to start when they stop making out / shagging and attempt to co-habit or to sustain a conversation that isn't about work or her lipstick.
2 notes
·
View notes
Text
Azure’s Evolution: What Every IT Pro Should Know About Microsoft’s Cloud
IT professionals need to keep ahead of the curve in the ever changing world of technology today. The cloud has become an integral part of modern IT infrastructure, and one of the leading players in this domain is Microsoft Azure. Azure’s evolution over the years has been nothing short of remarkable, making it essential for IT pros to understand its journey and keep pace with its innovations. In this blog, we’ll take you on a journey through Azure’s transformation, exploring its history, service portfolio, global reach, security measures, and much more. By the end of this article, you’ll have a comprehensive understanding of what every IT pro should know about Microsoft’s cloud platform.
Historical Overview
Azure’s Humble Beginnings
Microsoft Azure was officially launched in February 2010 as “Windows Azure.” It began as a platform-as-a-service (PaaS) offering primarily focused on providing Windows-based cloud services.
The Azure Branding Shift
In 2014, Microsoft rebranded Windows Azure to Microsoft Azure to reflect its broader support for various operating systems, programming languages, and frameworks. This rebranding marked a significant shift in Azure’s identity and capabilities.
Key Milestones
Over the years, Azure has achieved numerous milestones, including the introduction of Azure Virtual Machines, Azure App Service, and the Azure Marketplace. These milestones have expanded its capabilities and made it a go-to choice for businesses of all sizes.
Expanding Service Portfolio
Azure’s service portfolio has grown exponentially since its inception. Today, it offers a vast array of services catering to diverse needs:
Compute Services: Azure provides a range of options, from virtual machines (VMs) to serverless computing with Azure Functions.
Data Services: Azure offers data storage solutions like Azure SQL Database, Cosmos DB, and Azure Data Lake Storage.
AI and Machine Learning: With Azure Machine Learning and Cognitive Services, IT pros can harness the power of AI for their applications.
IoT Solutions: Azure IoT Hub and IoT Central simplify the development and management of IoT solutions.
Azure Regions and Global Reach
Azure boasts an extensive network of data centers spread across the globe. This global presence offers several advantages:
Scalability: IT pros can easily scale their applications by deploying resources in multiple regions.
Redundancy: Azure’s global datacenter presence ensures high availability and data redundancy.
Data Sovereignty: Choosing the right Azure region is crucial for data compliance and sovereignty.
Integration and Hybrid Solutions
Azure’s integration capabilities are a boon for businesses with hybrid cloud needs. Azure Arc, for instance, allows you to manage on-premises, multi-cloud, and edge environments through a unified interface. Azure’s compatibility with other cloud providers simplifies multi-cloud management.
Security and Compliance
Azure has made significant strides in security and compliance. It offers features like Azure Security Center, Azure Active Directory, and extensive compliance certifications. IT pros can leverage these tools to meet stringent security and regulatory requirements.
Azure Marketplace and Third-Party Offerings
Azure Marketplace is a treasure trove of third-party solutions that complement Azure services. IT pros can explore a wide range of offerings, from monitoring tools to cybersecurity solutions, to enhance their Azure deployments.
Azure DevOps and Automation
Automation is key to efficiently managing Azure resources. Azure DevOps services and tools facilitate continuous integration and continuous delivery (CI/CD), ensuring faster and more reliable application deployments.
Monitoring and Management
Azure offers robust monitoring and management tools to help IT pros optimize resource usage, troubleshoot issues, and gain insights into their Azure deployments. Best practices for resource management can help reduce costs and improve performance.
Future Trends and Innovations
As the technology landscape continues to evolve, Azure remains at the forefront of innovation. Keep an eye on trends like edge computing and quantum computing, as Azure is likely to play a significant role in these domains.
Training and Certification
To excel in your IT career, consider pursuing Azure certifications. ACTE Institute offers a range of certifications, such as the Microsoft Azure course to validate your expertise in Azure technologies.

In conclusion, Azure’s evolution is a testament to Microsoft’s commitment to cloud innovation. As an IT professional, understanding Azure’s history, service offerings, global reach, security measures, and future trends is paramount. Azure’s versatility and comprehensive toolset make it a top choice for organizations worldwide. By staying informed and adapting to Azure’s evolving landscape, IT pros can remain at the forefront of cloud technology, delivering value to their organizations and clients in an ever-changing digital world. Embrace Azure’s evolution, and empower yourself for a successful future in the cloud.
#microsoft azure#tech#education#cloud services#azure devops#information technology#automation#innovation
2 notes
·
View notes
Text
WILL CONTAINER REPLACE HYPERVISOR
As with the increasing technology, the way data centers operate has changed over the years due to virtualization. Over the years, different software has been launched that has made it easy for companies to manage their data operating center. This allows companies to operate their open-source object storage data through different operating systems together, thereby maximizing their resources and making their data managing work easy and useful for their business.
Understanding different technological models to their programming for object storage it requires proper knowledge and understanding of each. The same holds for containers as well as hypervisor which have been in the market for quite a time providing companies with different operating solutions.
Let’s understand how they work
Virtual machines- they work through hypervisor removing hardware system and enabling to run the data operating systems.
Containers- work by extracting operating systems and enable one to run data through applications and they have become more famous recently.

Although container technology has been in use since 2013, it became more engaging after the introduction of Docker. Thereby, it is an open-source object storage platform used for building, deploying and managing containerized applications.
The container’s system always works through the underlying operating system using virtual memory support that provides basic services to all the applications. Whereas hypervisors require their operating system for working properly with the help of hardware support.
Although containers, as well as hypervisors, work differently, have distinct and unique features, both the technologies share some similarities such as improving IT managed service efficiency. The profitability of the applications used and enhancing the lifecycle of software development.
And nowadays, it is becoming a hot topic and there is a lot of discussion going on whether containers will take over and replace hypervisors. This has been becoming of keen interest to many people as some are in favor of containers and some are with hypervisor as both the technologies have some particular properties that can help in solving different solutions.
Let’s discuss in detail and understand their functioning, differences and which one is better in terms of technology?
What are virtual machines?
Virtual machines are software-defined computers that run with the help of cloud hosting software thereby allowing multiple applications to run individually through hardware. They are best suited when one needs to operate different applications without letting them interfere with each other.
As the applications run differently on VMs, all applications will have a different set of hardware, which help companies in reducing the money spent on hardware management.
Virtual machines work with physical computers by using software layers that are light-weighted and are called a hypervisor.
A hypervisor that is used for working virtual machines helps in providing fresh service by separating VMs from one another and then allocating processors, memory and storage among them. This can be used by cloud hosting service providers in increasing their network functioning on nodes that are expensive automatically.
Hypervisors allow host machines to have different operating systems thereby allowing them to operate many virtual machines which leads to the maximum use of their resources such as bandwidth and memory.

What is a container?
Containers are also software-defined computers but they operate through a single host operating system. This means all applications have one operating center that allows it to access from anywhere using any applications such as a laptop, in the cloud etc.
Containers use the operating system (OS) virtualization form, that is they use the host operating system to perform their function. The container includes all the code, dependencies and operating system by itself allowing it to run from anywhere with the help of cloud hosting technology.
They promised methods of implementing infrastructure requirements that were streamlined and can be used as an alternative to virtual machines.
Even though containers are known to improve how cloud platforms was developed and deployed, they are still not as secure as VMs.
The same operating system can run different containers and can share their resources and they further, allow streamlining of implemented infrastructure requirements by the system.
Now as we have understood the working of VMs and containers, let’s see the benefits of both the technologies
Benefits of virtual machines
They allow different operating systems to work in one hardware system that maintains energy costs and rack space to cooling, thereby allowing economical gain in the cloud.
This technology provided by cloud managed services is easier to spin up and down and it is much easier to create backups with this system.
Allowing easy backups and restoring images, it is easy and simple to recover from disaster recovery.
It allows the isolated operating system, hence testing of applications is relatively easy, free and simple.

Benefits of containers:
They are light in weight and hence boost significantly faster as compared to VMs within a few seconds and require hardware and fewer operating systems.
They are portable cloud hosting data centers that can be used to run from anywhere which means the cause of the issue is being reduced.
They enable micro-services that allow easy testing of applications, failures related to the single point are reduced and the velocity related to development is increased.
Let’s see the difference between containers and VMs
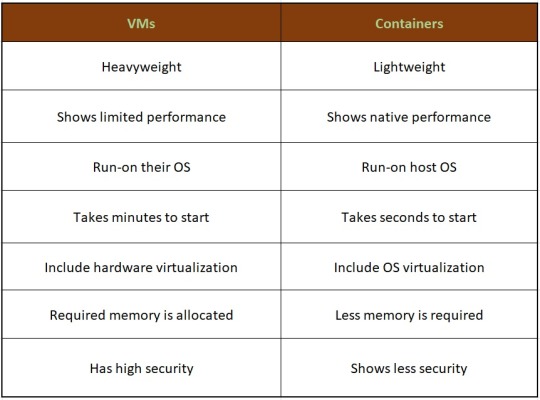
Hence, looking at all these differences one can make out that, containers have added advantage over the old virtualization technology. As containers are faster, more lightweight and easy to manage than VMs and are way beyond these previous technologies in many ways.
In the case of hypervisor, virtualization is performed through physical hardware having a separate operating system that can be run on the same physical carrier. Hence each hardware requires a separate operating system to run an application and its associated libraries.
Whereas containers virtualize operating systems instead of hardware, thereby each container only contains the application, its library and dependencies.
Containers in a similar way to a virtual machine will allow developers to improve the CPU and use physical machines' memory. Containers through their managed service provider further allow microservice architecture, allowing application components to be deployed and scaled more granularly.

As we have seen the benefits and differences between the two technologies, one must know when to use containers and when to use virtual machines, as many people want to use both and some want to use either of them.
Let’s see when to use hypervisor for cases such as:
Many people want to continue with the virtual machines as they are compatible and consistent with their use and shifting to containers is not the case for them.
VMs provide a single computer or cloud hosting server to run multiple applications together which is only required by most people.
As containers run on host operating systems which is not the case with VMs. Hence, for security purposes, containers are not that safe as they can destroy all the applications together. However, in the case of virtual machines as it includes different hardware and belongs to secure cloud software, so only one application will be damaged.
Container’s turn out to be useful in case of,
Containers enable DevOps and microservices as they are portable and fast, taking microseconds to start working.
Nowadays, many web applications are moving towards a microservices architecture that helps in building web applications from managed service providers. The containers help in providing this feature making it easy for updating and redeploying of the part needed of the application.
Containers contain a scalability property that automatically scales containers, reproduces container images and spin them down when they are not needed.
With increasing technology, people want to move to technology that is fast and has speed, containers in this scenario are way faster than a hypervisor. That also enables fast testing and speed recovery of images when a reboot is performed.

Hence, will containers replace hypervisor?
Although both the cloud hosting technologies share some similarities, both are different from each other in one or the other aspect. Hence, it is not easy to conclude. Before making any final thoughts about it, let's see a few points about each.

Still, a question can arise in mind, why containers?
Although, as stated above there are many reasons to still use virtual machines, containers provide flexibility and portability that is increasing its demand in the multi-cloud platform world and the way they allocate their resources.
Still today many companies do not know how to deploy their new applications when installed, hence containerizing applications being flexible allow easy handling of many clouds hosting data center software environments of modern IT technology.
These containers are also useful for automation and DevOps pipelines including continuous integration and continuous development implementation. This means containers having small size and modularity of building it in small parts allows application buildup completely by stacking those parts together.
They not only increase the efficiency of the system and enhance the working of resources but also save money by preferring for operating multiple processes.
They are quicker to boost up as compared to virtual machines that take minutes in boosting and for recovery.
Another important point is that they have a minimalistic structure and do not need a full operating system or any hardware for its functioning and can be installed and removed without disturbing the whole system.
Containers replace the patching process that was used traditionally, thereby allowing many organizations to respond to various issues faster and making it easy for managing applications.
As containers contain an operating system abstract that operates its operating system, the virtualization problem that is being faced in the case of virtual machines is solved as containers have virtual environments that make it easy to operate different operating systems provided by vendor management.
Still, virtual machines are useful to many
Although containers have more advantages as compared to virtual machines, still there are a few disadvantages associated with them such as security issues with containers as they belong to disturbed cloud software.
Hacking a container is easy as they are using single software for operating multiple applications which can allow one to excess whole cloud hosting system if breaching occurs which is not the case with virtual machines as they contain an additional barrier between VM, host server and other virtual machines.
In case the fresh service software gets affected by malware, it spreads to all the applications as it uses a single operating system which is not the case with virtual machines.
People feel more familiar with virtual machines as they are well established in most organizations for a long time and businesses include teams and procedures that manage the working of VMs such as their deployment, backups and monitoring.
Many times, companies prefer working with an organized operating system type of secure cloud software as one machine, especially for applications that are complex to understand.
Conclusion
Concluding this blog, the final thought is that, as we have seen, both the containers and virtual machine cloud hosting technologies are provided with different problem-solving qualities. Containers help in focusing more on building code, creating better software and making applications work on a faster note whereas, with virtual machines, although they are slower, less portable and heavy still people prefer them in provisioning infrastructure for enterprise, running legacy or any monolithic applications.
Stating that, if one wants to operate a full operating system, they should go for hypervisor and if they want to have service from a cloud managed service provider that is lightweight and in a portable manner, one must go for containers.
Hence, it will take time for containers to replace virtual machines as they are still needed by many for running some old-style applications and host multiple operating systems in parallel even though VMs has not had so cloud-native servers. Therefore, it can be said that they are not likely to replace virtual machines as both the technologies complement each other by providing IT managed services instead of replacing each other and both the technologies have a place in the modern data center.
For more insights do visit our website
#container #hypervisor #docker #technology #zybisys #godaddy
6 notes
·
View notes
Text
Vending Management System: Streamlining Smart Retail Operations
As the retail industry evolves, automation and data-driven decision-making have become essential. Traditional vending machines are giving way to intelligent systems that do more than dispense products—they analyze, optimize, and transform the way vending businesses operate. At the heart of this evolution is the vending management system (VMS).

A vending management system is not just a software tool—it's a digital backbone that powers modern vending networks, enabling businesses to operate more efficiently, increase profits, and deliver a better customer experience.
What Is a Vending Management System?
A vending management system is a comprehensive platform that allows operators to monitor, manage, and optimize a fleet of vending machines remotely. Whether you're managing 10 or 1,000 machines, a VMS provides a centralized dashboard to control operations in real time.
Advanced systems, like those offered by SandStar, integrate AI, IoT, and computer vision, providing unmatched visibility and automation across the vending network.
Key Features of a Smart Vending Management System
1. Real-Time Inventory Tracking
Know exactly what’s in each machine, at any time. A VMS monitors stock levels across your locations, alerts you when products are low or expired, and helps reduce out-of-stock events and spoilage.
2. Sales & Performance Analytics
Track which products are selling best, peak usage times, and revenue by machine or location. These insights help optimize product placement, pricing, and stocking strategies.
3. Remote Diagnostics & Maintenance
Receive automatic notifications if a machine is offline, has a technical issue, or requires servicing. Many problems can be diagnosed—and sometimes resolved—without dispatching a technician.
4. Dynamic Pricing & Promotions
Adjust prices based on time of day, demand, or expiration dates. A smart VMS allows you to set automated discounts, bundle deals, and loyalty offers remotely.
5. Route Optimization for Refill Teams
Save time and fuel by planning restocking routes based on real-time inventory data, rather than fixed schedules. This improves efficiency and reduces operational costs.
Why Your Vending Business Needs a VMS
✅ Improved Efficiency
Automating routine tasks and streamlining operations lets your team focus on growth, not guesswork. A VMS takes the manual effort out of restocking, maintenance, and reporting.
✅ Enhanced Customer Experience
Fewer out-of-stock products and fewer machine breakdowns lead to happier customers. With features like contactless payment and fast checkout, smart vending becomes more convenient than ever.
✅ Scalability
Whether you're managing a few machines or an international network, a VMS helps you scale without losing control. New machines can be onboarded quickly with plug-and-play functionality.
✅ Data-Driven Decisions
With access to detailed reports and analytics, business owners can make smarter choices about inventory, pricing, location strategy, and product selection.
SandStar’s AI-Driven Vending Management System
SandStar offers a state-of-the-art vending management solution that integrates computer vision, AI-powered analytics, and real-time system monitoring. It’s designed to support smart vending machines, unattended stores, and micro-markets.
With SandStar’s system, you can:
Manage multiple machines from a single dashboard
Analyze consumer behavior patterns using vision-based data
Remotely adjust promotions and pricing
Maintain higher uptime and faster service response
Trusted by global brands like PepsiCo, Coca-Cola, and Unilever, SandStar’s technology helps businesses enhance retail operations and drive revenue growth.
Industries That Benefit from Vending Management Systems
Retail Chains – Streamline operations across locations
Corporate Campuses – Provide employee snacks and essentials with full visibility
Airports & Transit Hubs – Ensure 24/7 service without staffing
Healthcare Facilities – Reduce product waste and ensure availability
Universities & Schools – Serve students efficiently and cost-effectively
Conclusion: Powering the Future of Automated Retail
A modern vending management system is more than a convenience—it's a necessity for operators who want to compete in the future of retail. From real-time inventory control to automated insights and remote servicing, a VMS empowers businesses to deliver better results with less manual effort.
With innovative platforms like SandStar, vending businesses can embrace automation, enhance profitability, and deliver superior customer experiences—all while staying ahead of the competition.
Ready to take control of your vending operations? Visit SandStar to learn how our AI-powered solutions can transform your retail strategy.
1 note
·
View note
Text
Data Center Market Forecast & Growth Trends
The global data center market was valued at USD 347.60 billion in 2024 and is expected to reach USD 652.01 billion by 2030, expanding at a robust compound annual growth rate (CAGR) of 11.2% from 2025 to 2030. This growth is primarily driven by the exponential surge in data generation across various sectors, fueled by widespread digital transformation initiatives and the increasing adoption of advanced technologies such as cloud computing, artificial intelligence (AI), machine learning (ML), and the Internet of Things (IoT).
As organizations generate and process vast volumes of data, the demand for scalable, secure, and energy-efficient data center infrastructure has intensified. Enterprises are seeking agile and resilient IT architectures to support evolving business needs and digital services. This has led to the rapid expansion of data center capacity worldwide, with a particular focus on hyperscale and colocation facilities.
Hyperscale data center operators—including major players such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud—are continuously scaling their infrastructure to meet global demands for cloud storage, computing power, and data processing. These tech giants are making substantial investments in constructing new data centers and upgrading existing ones to ensure seamless service delivery, latency reduction, and improved data security.
Simultaneously, the colocation segment is gaining momentum as businesses pursue cost-effective solutions to manage IT infrastructure. Colocation centers offer shared facilities equipped with high-speed connectivity, advanced cooling systems, and robust physical and cyber security. These benefits allow companies—especially small and medium enterprises—to scale their operations flexibly without the high capital expenditure required to build and maintain in-house data centers.
Another major trend accelerating market growth is the rise of edge computing. As the number of IoT devices and real-time applications grows, there is an increasing need for decentralized computing infrastructure. Edge data centers, located closer to end-users and data sources, provide reduced latency and faster response times—critical for applications in sectors such as autonomous vehicles, remote healthcare, industrial automation, and smart cities.
Key Market Trends & Insights
In 2024, North America dominated the global data center market with a share of over 40.0%, propelled by the widespread adoption of cloud services, AI-powered applications, and big data analytics across industries.
The United States data center market is anticipated to grow at a CAGR of 10.7% between 2025 and 2030, driven by continued digital innovation, enterprise cloud adoption, and the expansion of e-commerce and fintech platforms.
On the basis of components, the hardware segment accounted for the largest market share of more than 67.0% in 2024. The surge in online content consumption, social networking, digital transactions, and IoT connectivity has significantly boosted demand for high-capacity, high-performance hardware.
Within the hardware category, the server segment emerged as the market leader, contributing over 34.0% to revenue in 2024. Modern servers are being equipped with enhanced processing power, memory, and storage efficiency, all of which are crucial to supporting next-generation computing needs.
Among software solutions, the virtualization segment held a dominant share of nearly 18.0% in 2024. Virtualization allows data centers to maximize hardware utilization by enabling multiple virtual machines (VMs) to operate on a single physical server, reducing costs and increasing operational flexibility.
Order a free sample PDF of the Data Center Market Intelligence Study, published by Grand View Research.
Market Size & Forecast
2024 Market Size: USD 347.60 Billion
2030 Projected Market Size: USD 652.01 Billion
CAGR (2025-2030): 11.2%
North America: Largest market in 2024
Asia Pacific: Fastest growing market
Key Companies & Market Share Insights
Key players operating in the data center industry are Amazon Web Services (AWS), Inc. Microsoft, Google Cloud, Alibaba Cloud, and Equinix, Inc. The companies are focusing on various strategic initiatives, including new product development, partnerships & collaborations, and agreements to gain a competitive advantage over their rivals. The following are some instances of such initiatives.
In February 2025, Alibaba Cloud, the digital technology arm of Alibaba Group, opened its second data center in Thailand to meet the growing demand for cloud computing services, particularly for generative AI applications. The new facility enhances local capacity and aligns with the Thai government's efforts to promote digital innovation and sustainable technology. Offering a range of services including elastic computing, storage, databases, security, networking, data analytics, and AI solutions, the data center aims to address industry-specific challenges.
In December 2024, Amazon Web Services (AWS) introduced redesigned data center infrastructure to accommodate the growing demands of artificial intelligence (AI) and sustainability. The updates features advancements in liquid cooling, power distribution, and rack design, enabling a sixfold increase in rack power density over the next two years. AWS stated that these enhancements aims to deliver a 12% boost in compute power per site, improve energy efficiency, and enhance system availability.
In May 2024, Equinix, Inc. launched its first two data centers in Malaysia, with the International Business Exchange (IBX) facilities now operational in Johor and Kuala Lumpur. The facilities are intended to cater to Equinix Inc.'s customers in Malaysia while enhancing regional connectivity.
Key Players
Alibaba Cloud
Amazon Web Services, Inc.
AT&T Intellectual Property
Lumen Technologies (CenturyLink)
China Telecom Americas, Inc.
CoreSite
CyrusOne
Digital Realty
Equinix, Inc.
Google Cloud
IBM Corporation
Microsoft
NTT Communications Corporation
Oracle
Tencent Cloud
Browse Horizon Databook on Global Data Center Market Size & Outlook
Conclusion
The global data center market is undergoing rapid expansion, driven by the growing digital economy, technological advancements, and the ever-increasing demand for data storage, computing power, and connectivity. Hyperscale and colocation facilities are at the forefront of this transformation, offering scalable and secure infrastructure that supports cloud computing, AI workloads, and real-time applications. Edge computing is further reshaping the landscape by bringing processing capabilities closer to data sources, enabling faster and more efficient services across various industries.
As the market continues to evolve, investment in energy-efficient hardware, software virtualization, and regional data center development will be critical to meeting future demands. Companies that adopt flexible, sustainable, and innovation-driven data infrastructure strategies will be best positioned to capitalize on the tremendous growth opportunities in the data center space over the coming years.
0 notes
Text
INNOV8 Equipment: Leading the Way in Traffic Safety Solutions Across Australia
In a world where road safety and infrastructure development are moving at a rapid pace, INNOV8 Equipment stands out as a forward-thinking leader in the traffic management industry. Specializing in high-performance traffic control equipment, INNOV8 is committed to improving worksite safety, operational efficiency, and compliance across Australian roads. With cutting-edge solutions like Truck Mounted Attenuators (TMAs), Variable Message Sign (VMS) boards, and other intelligent traffic devices, INNOV8 Equipment is redefining how the country approaches road safety.
Who Is INNOV8 Equipment?
INNOV8 Equipment is an Australian-based company dedicated to providing industry-leading traffic control equipment and safety systems. Trusted by civil contractors, government agencies, infrastructure developers, and traffic management companies, the business has built a solid reputation for reliability, innovation, and compliance.
Their mission is simple yet powerful: to protect lives by supplying top-tier safety equipment that meets and exceeds industry standards.
Whether you're managing a highway resurfacing project, setting up an emergency work zone, or maintaining utility services in high-traffic areas, INNOV8 has the gear and the expertise to support your project from start to finish.
Core Offerings
INNOV8 Equipment supplies a comprehensive range of products designed for road safety, infrastructure maintenance, and traffic control:
✅ Truck Mounted Attenuators (TMA Trucks)
Crash-rated and MASH-compliant, INNOV8’s TMA trucks offer critical impact protection during roadside works. Available for hire or sale, these vehicles are essential for lane closures, emergency repairs, and road construction.
✅ VMS (Variable Message Sign) Boards
Their solar-powered, trailer-mounted VMS boards deliver real-time messages to motorists. Ideal for traffic redirection, public alerts, and event management, these boards are programmable and easy to deploy.
✅ Portable LED Arrow Boards
Perfect for short-term works or mobile use, these boards help direct traffic safely and clearly, even in low-light or high-speed areas.
✅ Traffic Management Equipment Hire
From blade attenuators to digital signage, INNOV8 provides hire options for a wide range of safety equipment, saving clients from capital expenses while ensuring access to the latest technology.
Why Choose INNOV8 Equipment?
✅ Compliance and Safety First
All equipment supplied by INNOV8 meets strict Australian safety and performance standards, including MASH certification for attenuators and AS standards for signage and electronics.
✅ Experience You Can Trust
With years of industry experience, the INNOV8 team understands the day-to-day needs of contractors and road safety professionals. Their advice and service reflect that insight.
✅ Flexible Hire and Sales Options
Whether you need a one-off rental or a full fleet solution, INNOV8’s flexible business model helps clients manage budgets while maintaining high safety standards.
✅ Rapid Deployment
INNOV8’s strategically located facilities and fast response times mean your project can get started with minimal delays.
✅ Australia-Wide Reach
The company serves projects across all states and territories, providing national-level service with a local understanding.
Industries Served
INNOV8 Equipment proudly works across multiple industries, including:
Road and highway construction
Utilities and infrastructure maintenance
Emergency response and disaster recovery
Local government and council works
Private traffic management companies
Rail and transport upgrades
Our Commitment
At INNOV8 Equipment, safety isn’t just a product feature—it’s a company value. Every piece of equipment is selected and maintained with one goal in mind: saving lives on Australian roads. By combining smart technology, durable construction, and client-focused service, INNOV8 empowers companies to meet their safety obligations without compromise.
Conclusion
If you're looking for a reliable, forward-thinking partner in road safety and traffic control, INNOV8 Equipment is your answer. With cutting-edge solutions, nationwide service, and a passion for innovation, INNOV8 is helping shape safer roads—one project at a time.
FOLLOW MORE INFO:
1 note
·
View note
Text
How to Integrate a Visitor Management System with Access Control
Modern workplaces demand more than just a front desk and a logbook to manage the flow of visitors. With an increasing focus on security, compliance, and visitor experience, businesses are turning to visitor management systems integrated with access control to streamline entry processes. This approach not only secures physical spaces but also enhances how visitors interact with your business.
Integrating visitor management with access control can significantly reduce administrative overhead, strengthen safety protocols, and deliver a seamless entry experience for guests, vendors, and contractors. For organizations seeking to modernize their premises, providers like Spintly offer integrated, mobile-first solutions that redefine how people move through buildings.

In this blog, we’ll explore how to integrate these two essential systems and why it’s a critical move for forward-thinking businesses.
Why Integrate Visitor Management and Access Control?
While visitor management and access control can operate independently, their true potential is unlocked when integrated. Here’s why:
Enhanced Security: Only pre-approved or verified visitors receive access, limiting unauthorized entries.
Improved Compliance: Visitor logs are automatically tied to access credentials, aiding in audits and regulatory compliance.
Better Visitor Experience: Guests enjoy smoother check-ins, digital badges, and real-time guidance without waiting at the reception.
Centralized Monitoring: Security teams can monitor visitor movements across the premises through one unified platform.
When paired effectively, these two systems offer organizations full control over who enters, when, where, and how.
Steps to Integrate Visitor Management with Access Control
1. Evaluate Your Current Infrastructure
Begin by assessing your existing access control hardware and software. Identify whether it’s cloud-based, on-premises, or mobile-enabled. Also, evaluate how you currently handle visitor registration. This will help determine integration needs and compatibility with visitor management software.
Forward-thinking solutions like Spintly’s cloud-based access platform support modern integrations with minimal infrastructure changes, making deployment seamless.
2. Choose a Scalable Visitor Management System
Not all systems are built equal. Select a visitor management system (VMS) that:
Supports real-time data sharing with your access control setup
Can issue temporary access credentials to guests
Offers pre-registration options via web or mobile
Supports ID verification, photo capture, and e-signatures
Ensure the VMS can grow with your organization, supporting multiple sites, user roles, and customizable workflows.
3. Define Visitor Policies and Access Levels
Establish rules for different visitor types - clients, vendors, interviewees, or delivery personnel. Define what areas they can access, how long their credentials remain valid, and any approvals required.
This granular control is best managed with integrated systems that assign access levels automatically once a guest is verified. Platforms like Spintly allow pre-defined templates and workflows for streamlined visitor management and access control assignment.
4. Set Up Pre-Registration and Check-In Processes
With integration in place, authorized personnel can pre-register visitors, who then receive digital QR codes or mobile passes. On arrival, guests can check in via a tablet or their smartphone, reducing front desk congestion.
Upon check-in, the system can automatically assign temporary access credentials synced with your access control system, enabling entry to approved zones only. This process ensures contactless, secure, and efficient guest onboarding.
5. Implement Real-Time Monitoring and Alerts
A key benefit of integrated systems is the ability to track visitor movement in real-time. Security teams can receive alerts if a guest overstays their scheduled visit or tries to access restricted zones.
Additionally, visitor data such as entry time, exit time, host information, and location can be stored securely in the cloud - useful for audits, emergency evacuations, or post-incident analysis.
Benefits of Integrating Visitor Management with Access Control
1. Superior Security Posture
Every guest is accounted for and traceable, reducing the risk of security breaches. Temporary credentials expire automatically, and there's no chance of physical badges being misused.
2. Streamlined Workflows
Hosts can receive notifications when visitors arrive, eliminating the need for manual coordination. The system manages approvals, check-ins, and access issuance - all in one flow.
3. Reduced Reception Workload
Automation means fewer repetitive tasks for your front desk team. With mobile-based visitor self-check-ins and cloud access provisioning, staff can focus on more critical responsibilities.
4. Enhanced Professionalism and Brand Image
A sleek visitor check-in experience - complete with digital forms, wayfinding, and personalized greetings - sends a strong message about your company’s professionalism and commitment to innovation.
5. Data-Driven Insights
Integrated systems generate valuable data - peak visit hours, repeat visitor patterns, time spent on premises, etc. This information helps optimize facility usage and inform security decisions.
Industry Applications
Corporate Offices
Enable secure, scheduled client and candidate visits without burdening HR or admin teams.
Co-Working Spaces
Manage a high volume of diverse guests while ensuring access to only authorized zones.
Healthcare Facilities
Restrict access to critical areas and maintain accurate logs for compliance and safety.
Manufacturing Plants
Grant vendors access only to specific zones during their scheduled maintenance windows.
Educational Institutions
Monitor and control non-staff movement, ensuring student safety and privacy.
Why Choose a Modern Platform Like Spintly?
As one of the leading innovators in smart building solutions, Spintly offers a unified platform that combines cloud-based access control and visitor management in a seamless ecosystem. The solution eliminates the need for physical badges, cards, or high-touch kiosks by using smartphone-based credentials and facial recognition technology.
With Spintly, businesses enjoy:
Mobile check-in and QR code entry for visitors
Role-based access provisioning
Real-time visitor analytics and automated reports
Minimal hardware dependencies and wireless deployment
Integration with calendar systems, HR software, and more
This kind of integration redefines visitor management not just as a security feature, but as an enabler of smarter, safer, and more agile workplaces.
Conclusion
In today’s world, visitor management is no longer about just keeping track of who’s coming and going. It’s about creating an efficient, safe, and welcoming experience for everyone entering your space. Integrating visitor management systems with modern access control elevates building security while simplifying operations.
Whether you're managing a single building or a distributed enterprise network, smart solutions like Spintly empower your organization to handle guest access with precision and ease. With seamless integration, real-time monitoring, and cloud-native flexibility, you're not just securing your workplace - you're transforming how it operates.
#visitormanagementsystem#visitor management system#visitormanagement#accesscontrol#mobile access#access control solutions#access control system#spintly#smartacess#biometrics#smartbuilding#biometric attendance
0 notes
Text
Microsoft Windows Server 2019 Administration: Key Features and Best Practices
In today’s digital age, businesses rely heavily on robust and secure IT infrastructure. Microsoft Windows Server 2019 stands as a cornerstone of enterprise IT environments, offering a wide range of features for networking, storage, security, and management. Whether your organization is large or small, efficient server management is crucial for ensuring optimal performance and security. In this blog, we’ll explore the key aspects of Windows Server 2019 administration, its core features, and best practices for IT professionals to effectively manage and secure the server environment.
What is Windows Server 2019?
Windows Server 2019 is the latest long-term servicing channel (LTSC) release from Microsoft, building on the capabilities of previous versions of Windows Server with an enhanced focus on cloud integration, security, and virtualization. It offers significant improvements over its predecessors, including better management tools, security features, and support for hybrid cloud environments. Windows Server 2019 allows IT administrators to manage various aspects of an organization’s network infrastructure, from Active Directory to file management and beyond, all within a unified environment.

Key Features of Windows Server 2019
1. Windows Admin Center
Windows Admin Center (WAC) is a modern, browser-based interface for managing Windows Server environments. It provides administrators with a centralized hub to perform tasks such as monitoring system performance, managing users, and configuring server roles. Windows Admin Center simplifies management tasks, making it easier to maintain server health and apply configurations across multiple servers from a single console.
The WAC interface is particularly beneficial for administrators who manage multiple servers. It helps reduce the complexity of managing legacy tools, enabling administrators to use a unified console that integrates various management and diagnostic features. WAC can also manage remote servers, which is useful for those who administer geographically dispersed infrastructure.
2. Security Enhancements
Windows Server 2019 introduces several significant security improvements, which are vital for protecting both on-premises and cloud-connected environments. Key security features include:
Windows Defender Advanced Threat Protection (ATP): A next-generation solution that helps detect, investigate, and respond to potential security threats. ATP enhances the security posture of the server by providing continuous monitoring and threat analytics.
Shielded Virtual Machines: This feature protects virtual machines (VMs) by encrypting them and restricting unauthorized access. Shielded VMs help prevent attacks by ensuring that only trusted users can interact with VMs.
Enforced Secure Boot: Windows Server 2019 enhances system boot-up security, ensuring that only trusted software is loaded during the boot process, preventing unauthorized code from running.
These features ensure that Windows Server 2019 is well-equipped to meet the ever-growing security challenges posed by cyber threats.
3. Hybrid Cloud Integration
Windows Server 2019 brings greater integration with Microsoft Azure, providing organizations with the tools needed to manage hybrid cloud environments. Features such as Azure Backup and Azure Site Recovery make it easy for administrators to manage offsite backups and disaster recovery solutions in the cloud. Furthermore, Windows Server 2019 includes built-in support for Azure Active Directory, allowing organizations to extend their on-premises Active Directory to the cloud.
This hybrid cloud functionality enables IT teams to seamlessly integrate on-premises infrastructure with cloud services, which is a crucial capability for organizations adopting cloud-first strategies or looking for a mix of both cloud and on-premises resources.
4. Storage Spaces Direct and Storage Migration
Windows Server 2019 introduces Storage Spaces Direct, a feature that allows for highly scalable, software-defined storage solutions. By using commodity hardware, organizations can create highly available storage pools that increase storage flexibility and reduce costs.
Storage Migration Service is another critical feature that simplifies the migration of legacy storage systems to modern storage solutions. This tool helps administrators move data from older servers to newer Windows Server environments with minimal downtime, ensuring a smooth transition to new infrastructure.
5. Improved Virtualization Support
Windows Server 2019 enhances its virtualization capabilities through Hyper-V. It offers better integration with container technologies like Docker and Kubernetes, making it easier to deploy and manage containerized applications. Server Core, a minimal installation option in Windows Server, also supports the use of containers, providing a lightweight option for managing virtual environments.
The improvements in Hyper-V allow organizations to better utilize their hardware resources while maintaining flexibility in how they deploy and manage virtual machines.
Best Practices for Windows Server 2019 Administration
Managing Windows Server 2019 requires a strategic approach to ensure high performance, security, and reliability. Here are some best practices for IT administrators to follow:
1. Regular Updates and Patch Management
Keeping Windows Server 2019 updated is critical for ensuring that the system remains secure and functional. Administrators should establish a routine for patch management, using Windows Server Update Services (WSUS) or Windows Update for Business to streamline updates across multiple servers. Regular updates not only provide new features but also ensure the system is protected against newly discovered vulnerabilities.
2. Backup and Disaster Recovery Planning
Ensuring data safety is a top priority for any server administrator. Set up automated backups using tools like Azure Backup or Windows Server Backup to ensure that critical data is protected. Test backup and recovery procedures regularly to guarantee that they will work in case of an emergency.
In addition, consider implementing disaster recovery solutions like Azure Site Recovery to provide business continuity in the event of server failure, ransomware attacks, or natural disasters.
3. User and Permission Management
Windows Server 2019 includes robust Active Directory capabilities, which allow administrators to define user roles, group policies, and access control across the network. Regularly audit user permissions and ensure that least-privilege access principles are enforced. Using Group Policy Objects (GPOs) can help streamline user and security management across multiple servers and improve overall system security.
4. Resource Monitoring and Performance Tuning
To ensure servers run efficiently, administrators should use built-in tools like Performance Monitor and Resource Monitor to track system performance, resource utilization, and identify potential bottlenecks. Regular monitoring of disk, CPU, memory, and network usage can help avoid downtime and optimize server performance.
5. Security and Encryption
Always adhere to security best practices by configuring firewalls, enforcing strong password policies, and using encryption for data at rest and in transit. Windows Server 2019 offers features like BitLocker encryption to protect sensitive data. Additionally, ensure that multi-factor authentication (MFA) is enabled for administrative access and critical systems to prevent unauthorized access.
Conclusion
Microsoft Windows Server 2019 is a powerful, flexible, and secure platform for managing enterprise IT environments. Its extensive features—from security enhancements and virtualization support to hybrid cloud integration and advanced storage management—make it a cornerstone for organizations looking to streamline their infrastructure and embrace digital transformation.
For IT professionals responsible for Windows Server administration, mastering these features and adhering to best practices can ensure high availability, improved security, and better performance of the server infrastructure. Whether you’re managing on-premises servers or hybrid cloud environments, Windows Server 2019 offers the tools and flexibility required to meet the demands of modern business operations. By staying updated with the latest advancements and maintaining a proactive management strategy, administrators can keep their systems running smoothly and securely for years to come.
0 notes
Text
What is Cloud Hosting and How Does It Work?
In today’s digital age, businesses and individuals need reliable, scalable, and secure web hosting solutions more than ever. Enter cloud hosting — a modern approach to hosting websites and applications that offers flexibility, performance, and cost-efficiency. But what exactly is cloud hosting, and how does it work?
Let’s break it down.
What is Cloud Hosting?
Cloud hosting is a type of web hosting that uses a network of virtual servers running on top of a physical infrastructure of multiple connected servers. Unlike traditional hosting (where resources are tied to a single server), cloud hosting distributes resources such as CPU, RAM, and storage across multiple servers, ensuring high availability and scalability.
In simple terms, cloud hosting is like renting computing power from a huge network (or “cloud”) of servers instead of relying on just one.
How Does Cloud Hosting Work?
Cloud hosting works through virtualization technology, where physical servers are partitioned into multiple virtual machines (VMs). These VMs form a network of servers that host websites, apps, and databases. Here’s a step-by-step look at how it operates:
1. Virtualization
Cloud providers create virtual servers (called instances) using software called a hypervisor. These virtual instances run independently but draw from the pool of physical resources.
2. Resource Pooling
All virtual servers share a common pool of hardware (CPU, memory, storage) across multiple physical machines. If one server goes down, another automatically takes over.
3. Load Balancing
Cloud hosting uses load balancers to distribute incoming traffic efficiently across all available servers. This prevents any one server from being overwhelmed and ensures smoother performance.
4. Scalability on Demand
One of the biggest advantages is scalability. If your website experiences a traffic spike, more resources can be added automatically or manually in real-time, without downtime.
5. Pay-as-You-Go Pricing
With cloud hosting, you only pay for the resources you actually use — much like an electricity or utility bill. This makes it cost-effective for both startups and large enterprises.
Benefits of Cloud Hosting
✅ High Reliability
If one server fails, another takes over instantly. This redundancy ensures better uptime and minimal disruptions.
✅ Flexible Scaling
Resources like bandwidth, RAM, and storage can be scaled up or down based on demand — perfect for growing businesses or unpredictable traffic.
✅ Improved Performance
Data is served from the nearest available server, improving speed and responsiveness for users around the world.
✅ Cost Efficiency
No need to pay for unused server capacity. Cloud hosting adapts to your needs and usage patterns.
✅ Disaster Recovery
Many cloud hosts offer automated backups, snapshots, and failover systems to protect against data loss.
Use Cases for Cloud Hosting
Cloud hosting is ideal for a wide range of scenarios:
E-commerce websites that need fast loading times and uptime during sales
Web applications with fluctuating traffic
Content-heavy websites (blogs, media, streaming platforms)
Startups looking for low-cost, scalable hosting solutions
Enterprise-level applications requiring high performance and security
Popular Cloud Hosting Providers
Some of the leading names in the cloud hosting industry include:
Amazon Web Services (AWS)
Google Cloud Platform (GCP)
Microsoft Azure
DigitalOcean
Linode
Cloudways (a managed cloud hosting platform)
Each offers unique features, pricing models, and service levels, so the best choice depends on your project needs and budget.
Is Cloud Hosting Right for You?
If you’re managing a website or app that needs to stay online, perform well under pressure, and grow without constant migration or downtime, cloud hosting is likely a smart choice. It’s especially useful for businesses that want:
Minimal downtime
Flexible and scalable infrastructure
Better performance for global users
Affordable pay-per-use pricing
Conclusion
Cloud hosting is revolutionizing the way websites and applications are deployed and managed. By moving beyond the limitations of traditional hosting, it offers a dynamic, efficient, and reliable solution for the modern web.
Whether you're a solo developer, a growing business, or a large enterprise, cloud hosting provides the infrastructure you need — when you need it, how you need it.
0 notes
Text
Streamlining Temporary Hiring with Vendor Management and Direct Sourcing

In a time of rapid change and growing demand for agility, businesses are increasingly turning to temporary workforce solutions to meet short-term needs without long-term commitments. But managing a high volume of temporary workers—while ensuring quality, compliance, and cost control—requires more than spreadsheets and manual processes. The answer lies in combining temporary workforce management software, a strong vendor management solution, and a modern direct sourcing recruitment strategy.
The Rise of Temporary Workforce Management Software
As contract-based roles and project-based hiring increase, organizations need purpose-built platforms to manage everything from job requests to onboarding, compliance, timesheets, and payments. This is where temporary workforce management software plays a crucial role.
Key features include:
Centralized worker profiles and job tracking
Automated onboarding and document collection
Time and attendance tracking
Payroll integration
Compliance and performance reporting
By digitizing these tasks, companies can reduce administrative burden, improve hiring accuracy, and gain visibility into workforce operations.
The Role of Vendor Management Solutions
When companies rely on multiple staffing vendors to fulfill temporary roles, managing those relationships becomes complex. A vendor management solution (VMS) helps companies standardize and streamline the process of working with multiple suppliers.
Benefits of a vendor management solution:
Track vendor performance and fill rates
Automate job requisitions and candidate submissions
Manage rate cards and billing in one platform
Ensure compliance with labor and tax regulations
Optimize vendor usage with data-driven insights
Together with workforce software, a VMS helps align vendor performance with company goals—ensuring the best talent is sourced efficiently and compliantly.
Direct Sourcing Recruitment: Build Your Own Talent Network
Direct sourcing recruitment enables organizations to create their own talent pools—contractors and freelancers who can be redeployed quickly for future roles. Rather than relying solely on vendors, businesses can engage candidates directly using branded career portals, talent CRMs, and AI-matching tools.
Why direct sourcing works:
Reduced time-to-fill and lower costs
Stronger employer branding among contingent workers
More control over talent quality and fit
Reuse of trusted, pre-vetted workers for future roles
Integrating direct sourcing with your VMS and workforce software enables a flexible, efficient hiring ecosystem that leverages both agency and direct-sourced talent.
Final Thoughts
Success in today’s workforce depends on speed, control, and flexibility. By combining temporary workforce management software, a smart vendor management solution, and a proactive direct sourcing recruitment strategy, organizations can optimize their temporary hiring process end-to-end.
This integrated approach ensures you hire the right people, from the right sources, at the right time—while staying compliant and efficient.
#contingentworkforce#vendor management software#vendor management solutions#vendor management tools#talentacquisition#directsourcing#vendormanagement#vendor relationship management#temporary workforce management software#vendor risk management systemcontingent workforce management software#direct hire#sourcing in recruitment#onboarding automation
0 notes
Text
Resolve the Update Package Database failure on Proxmox VE
Proxmox Virtual Environment provides a complete open-source platform for enterprise virtualization. Its built-in web interface enables you to manage VMs and containers, configure software-defined storage and networking, set up high-availability clustering, and use multiple out-of-the-box tools all in a single solution. In this guide, we shall discuss the steps to resolve the Update Package…
#Change Proxmox Repository to Fix Update Error: How to resolve Update package database failure on Proxmox#Install Proxmox#proxmox#Proxmox Server#Proxmox Update Error#Proxmox VE#Proxmox Virtual Environment#Update Package Database
0 notes