#PHP vulnerabilities
Explore tagged Tumblr posts
Text
4chan: The Internet’s Mos Eisley Cantina Takes Another Hit
In the chaotic world of online forums, 4chan stands out like a neon sign in a dark alley. Dubbed the “cesspool of the internet,” it has a reputation for being the lawless Doge City of the online world. This notorious imageboard has seen its fair share of craziness, and now, it’s down again—this time, apparently hacked. On April 14, 2025, users began reporting that 4chan was loading slowly. By…
#4chan#anonymity online#conspiracy theories#Controversy#cybersecurity#digital privacy#digital security#far-right extremism#forum hacks#hacking news#internet culture#internet escapades#internet forum#internet memes#lawless internet#meme culture#meme history#online anonymity#online communities#online trolls#PHP vulnerabilities#source code leak#Soyjak.party#Tech News#viral content
2 notes
·
View notes
Text

PHP - Day 2
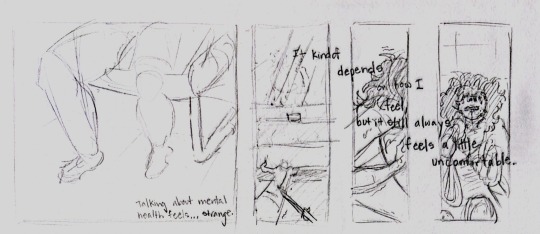

#php#partial hospitalization program#still shocked that they have a tag for that#vulnerability#emotional unavailability#all that good stuff
2 notes
·
View notes
Text
AAAHHHHHH!! WHAT THE FUDG—!!! THIS IS AWESOME!! OH MY GAWD!!💙

The detail, The story telling, The expressions!! WHY IS IT SO GOOD?!!

I live for angst like this and I love how ppl are really liking it too, Thank you for blessing my eyes with this masterpiece! Irwin, my big guy!!💙


Mourning AU by @artsygirl0315
Irwin isn't supposed or allowed to visit Sectors he already went to... Unless said Sectors seem to have major problems like, idk, losing members and the rest getting too unruly.
He needs to keep up the "kid stuck in an adult body" lie and try to understand what the problem is and how to help with it (not solve, that's something the Sector needs to do itself). If the members won't listen and attack him, he can show a bit more of his adult side. If they keep being unruly and uncooperative, he needs to leave and tell Moonbase the situation. The Soopreme Leader then will take the measure they think are necessary.
And this doesn't look too good...
#knd#kids next door#codename kids next door#codename knd#sector php#irwin stevens#mourning au#i really think Phoebe is stuck between two hard places because Irwin is such a good friend but she can't go against orders#Tyler is really taking on the unhealthy role here and I'm keeping it because character development#I'm glad we get to see Irwin in this because imagine how it would feel for the sector to be seen so.. vulnerable by a friend
52 notes
·
View notes
Text
If you are sexually active, please discuss PrEP with your doctor. And everyone should discuss it with all of their friends. Programs like Ryan White are incredibly important to reducing the spread of HIV/AIDS https://ryanwhite.hrsa.gov/about/four-years-hiv-success. These programs provide both HIV antiretrovirals(ARV) and PrEP to low income people and are the reason HIV isn’t ravaging the LGBTQ community like in the 80s. With funding cut, it will be significantly harder for low income people to get access to these medications and will cause HIV to spread through those communities.
ARVs can get people living with HIV to undetectable levels. And undetectable HIV is untransmittable https://www.cdc.gov/global-hiv-tb/php/our-approach/undetectable-untransmittable.html. When people lose access to these medications, they can transmit HIV to their sexual partners. PrEP is 99% effective in reducing the spread of HIV https://www.hiv.gov/hiv-basics/hiv-prevention/using-hiv-medication-to-reduce-risk/pre-exposure-prophylaxis. Not everyone will be able to access PrEP if these programs are cut, but everyone who can should get on it to reduce the spread as much as possible.
We already see health disparities of racial minorities in HIV infection rates https://www.cdc.gov/hiv/data-research/facts-stats/race-ethnicity.html. Black and Latine people will be the first to be affected by these cuts, but like much of our culture it will spread from those communities. It most likely will not reach the level of the 80s, but it will devastate the most vulnerable people in our communities. The wealthiest among us will still be able to afford medication, but for the rest of us, we need to do everything we can to stop the spread.
WE HAVE THE KNOWLEDGE
WE HAVE THE TOOLS
WE CANNOT ALLOW THESE MONSTERS TO KILL US AGAIN
226 notes
·
View notes
Text
allowing kids freedom to fuck around and find out is so so important but someone really should have stopped me from port forwarding my vulnerability ridden php apps
80 notes
·
View notes
Text
The UK needs some help with there own Online Safety Act (UK KOSA) that going to end up shutting down both small and big sites starting in March 2025.
It's already starting a online cycling community web forum with over 60K users shutting down because of the UK Online Safety Act (UK KOSA).
Link to more info here
"Reading https://www.ofcom.org.uk/online-safety/illegal-and-harmful-content/time-for-tech-firms-to-act-uk-online-safety-regulation-comes-into-force/ and we're done... we fall firmly into scope, and I have no way to dodge it. The act is too broad, and it doesn't matter that there's never been an instance of any of the proclaimed things that this act protects adults, children and vulnerable people from... the very broad language and the fact that I'm based in the UK means we're covered.
The act simply does not care that this site and platform is run by an individual, and that I do so philanthropically without any profit motive (typically losing money), nor that the site exists to reduce social loneliness, reduce suicide rates, help build meaningful communities that enrich life.
The act only cares that is it "linked to the UK" (by me being involved as a UK native and resident, by you being a UK based user), and that users can talk to other users... that's it, that's the scope.
I can't afford what is likely tens of thousand to go through all the legal hoops here over a prolonged period of time, the site itself barely gets a few hundred in donations each month and costs a little more to run... this is not a venture that can afford compliance costs... and if we did, what remains is a disproportionately high personal liability for me, and one that could easily be weaponised by disgruntled people who are banned for their egregious behaviour (in the years running fora I've been signed up to porn sites, stalked IRL and online, subject to death threats, had fake copyright takedown notices, an attempt to delete the domain name with ICANN... all from those whom I've moderated to protect community members)... I do not see an alternative to shuttering it.
The conclusion I have to make is that we're done... Microcosm, LFGSS, the many other communities running on this platform... the risk to me personally is too high, and so I will need to shutter them all.
What and When
So here's the statement...
On Sunday 16th March 2025 (the last day prior to the Act taking effect) I will delete the virtual servers hosting LFGSS and other communities, and effectively immediately end the approximately 300 small communities that I run, and the few large communities such as LFGSS.
It's been a good run, I've administered internet forums since 1996 having first written my own in Perl to help fans of music bands to connect with each other, and I then contributed to PHP forum software like vBulletin, Vanilla, and phpBB, before finally writing a platform in Go that made it cost efficient enough to bring interest based communities to so many others, and expand the social good that comes from people being connected to people.
Approximately 28 years and 9 months of providing almost 500 forums in total to what is likely a half a million people in that time frame... the impact that these forums have had on the lives of so many cannot be understated.
The peak of the forums has been the last 5 years, we've plateaued around 275k monthly users across the almost 300 websites on multiple instances of the platform that is Microcosm, though LFGSS as a single community probably peaked in the 2013-2018 time period when it alone was hitting numbers in excess of 50k monthly users.
The forums have delivered marriages, births, support for those who have passed (cancer being the biggest reason), people reunited with stolen bikes, travel support, work support, so much joy and happiness and memorable experiences... but it's also been directly cited by many as being the reason that they are here today, the reason they didn't commit suicide or self-harm. It's help people get through awful relationship breakups, and helped people overcome incredible challenges with their health.
It's devastating to just... turn it off... but this is what the Act forces a sole individual running so many social websites for a public good to do.
I don't know where to recommend... I know lots of people have moved small groups to places like Signal and WhatsApp, and that some people are on the fediverse, and some are in other websites and groups.
There is no central place that could take us all and preserve the very special thing we had... so it's done.
This is a really special place... the people are special... I guess the next 3 months will be a time of sharing what it meant, and of groups figuring out where they want to go next.
Love you all forever, it's been amazing to be a part of it all, I never thought I'd touch the lives of so many people by running websites, and in turn to give so much reason to my own life. In the end, the person I save most was likely myself.
Dee"
This is very bad and the compliance requirements will affect alot of websites based in the UK and Ofcom seems very out of its depth.
The whole thing is an unworkable mess and will collapse under its own weight. There also alot of privacy and legal issues with it.
This may also affect Tumblr and force the site to leave the UK.
Please spread awareness!
39 notes
·
View notes
Text
NIGHT-DAY TERROR AU (SECTOR PHP) !!
(Slight gore and horror is mentioned, You have been warned)
Sector PHP(?)


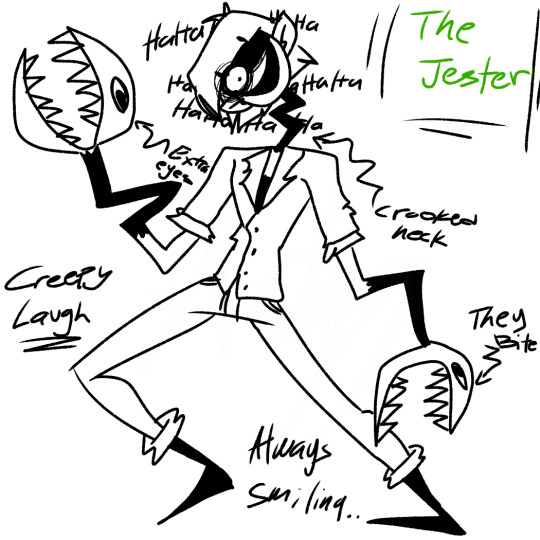


Finally decided on making some Monsterous Sector PHP sheets for the Night-Day Terror AU made by the lovely @kandykatz💙
Info:
Sector PHP, A well-known undercover sector who is the main resourse supply for the KND. They're strong-willed, dedicated and determined.
But... Something changed..
In one moment, they were seen evacuating the area after the incident with a 'certain operative' and the next, they are seen roaming around the neighborhood in such nightmare-ish forms.
The ones who stayed below their treehouse can be seen either destroying property or hunting down whatever they see that moves or even breathes.
The Foreseer, stays in their treehouse but he doesn't miss anything that goes on with his sector. He sees everything, he knows what goes on with what they do but not all the time. Sometimes he'll lose sight of something and get distracted, sometimes he'll blink and miss one of his operative's vision.
Nonetheless, he's their mastermind. He's to follow, he's to obey and rest assured, he's here to seek.
The Strong Bull, the poor soul, his legs ceased to move and are completely numb to the bone. Although, this doesn't stop him as his large fists can punch through the ground with loud thuds and he can move by such.
His enormous size is very intimidating that when he charges, you can bet that it's the last thing you'll ever see. He's fast despite his size, yet he's strong and he's unstable.
The Jester, His laugh is the last thing that can be known as contagious. A creepy smile plastered on his face as his body fails human anatomy all together, his hands replaced as these 'puppets' of his.
He's incredibly durable and extremely energetic, his lively nature is nothing but a bad cause. He doesn't spread cheer nor laughter, rather pain and screams. But he can't help it if one keeps getting bitten by his puppets.
The Hungry Ghoul, if you ever saw a detached lower body running straight towards you then best assume she's flying right above you and she has an insatiable appetite.
Her upper body roams the sky for prey and sometimes she'll chase after them if her incredibly fast legs can catch up, although, one of her weak points are her vision.
The only way you can slow her down is if you can even manage to attach her body again.
That's near to impossible, really.
The Weeping Siren, Much like only a few operatives, this one is very docile to who she fails to see as a complete threat. If you are someone she can recognize or seen as very vulnerable then she will fake ignorance and walk away, this is because she knew her leader was watching.
Her voice can be used to lure prey so be very careful, she can move by twirling using her sharp legs as a ballerina would, this feigns innocence.
She's completely unstable, she knows that, and so she weeps her sorrows away knowing she can't completely help people.
(Ahh, so glad I got to finish this despite it looking very rushed. I wanted to add my dumdums in these just because I wanted to practice horror in their au. Nght-Day Terror AU belongs to my awesome moot @kandykatz !!!)
#knd#kids next door#codename kids next door#codename knd#knd oc#oc#original character#drawing#art#night day terror au#friends au#knd au#sector php
30 notes
·
View notes
Note
Trick or treat!
You get PHP's "type juggling" feature!

While listed in the documentation as a language "feature", in many contexts it is considered a vulnerability. Maybe do worry about it?
29 notes
·
View notes
Text
This blog whole heartedly endorses writing your own shit, open sourcing it as your own years before using it in a work context, and then safely saving yourself the trouble of writing it again at work.
You get a lot of things from that:
1. You're protecting your ability to build off your own work, regardless of who is paying you.
2. You're learning how to use your work in a business context. And while they may be able to claim the derivative works, they can't claim the experience of making them, or your reimplementing them back into the open source (with learned experience they paid for (without looking at the derivative code))
3. You protect your portfolio. This is probably the most important: here's this thing I made, here are the business critical things it runs or supports.
Me, I made a silly curl wrapper to send and receive json from the RuneScape auction house API, now it's running in two ERP/E-commerce integrations about to be deployed company wide as our standard for API integrations. It's also running at least one Instagram integration for a ski resort and some event ticketing thing for a local theater. It's also been used for proof of concept demonstrations of security vulnerabilities.
Clients love it when you show them the picture of a kitten that has a PHP shell in it and then proceed to read them their email through the kitten shell. By love I mean no one actually liked that and I deployed the fix server wide anyway because we were hemorrhaging money on preventable security breaches.
8 notes
·
View notes
Text
Critical PHP Vulnerability Under Mass Exploitation

Source: https://www.securityweek.com/mass-exploitation-of-critical-php-vulnerability-begins/
More info: https://www.greynoise.io/blog/mass-exploitation-critical-php-cgi-vulnerability-cve-2024-457
3 notes
·
View notes
Text
Prevent HTTP Parameter Pollution in Laravel with Secure Coding
Understanding HTTP Parameter Pollution in Laravel
HTTP Parameter Pollution (HPP) is a web security vulnerability that occurs when an attacker manipulates multiple HTTP parameters with the same name to bypass security controls, exploit application logic, or perform malicious actions. Laravel, like many PHP frameworks, processes input parameters in a way that can be exploited if not handled correctly.

In this blog, we’ll explore how HPP works, how it affects Laravel applications, and how to secure your web application with practical examples.
How HTTP Parameter Pollution Works
HPP occurs when an application receives multiple parameters with the same name in an HTTP request. Depending on how the backend processes them, unexpected behavior can occur.
Example of HTTP Request with HPP:
GET /search?category=electronics&category=books HTTP/1.1 Host: example.com
Different frameworks handle duplicate parameters differently:
PHP (Laravel): Takes the last occurrence (category=books) unless explicitly handled as an array.
Express.js (Node.js): Stores multiple values as an array.
ASP.NET: Might take the first occurrence (category=electronics).
If the application isn’t designed to handle duplicate parameters, attackers can manipulate input data, bypass security checks, or exploit business logic flaws.
Impact of HTTP Parameter Pollution on Laravel Apps
HPP vulnerabilities can lead to:
✅ Security Bypasses: Attackers can override security parameters, such as authentication tokens or access controls. ✅ Business Logic Manipulation: Altering shopping cart data, search filters, or API inputs. ✅ WAF Evasion: Some Web Application Firewalls (WAFs) may fail to detect malicious input when parameters are duplicated.
How Laravel Handles HTTP Parameters
Laravel processes query string parameters using the request() helper or Input facade. Consider this example:
use Illuminate\Http\Request; Route::get('/search', function (Request $request) { return $request->input('category'); });
If accessed via:
GET /search?category=electronics&category=books
Laravel would return only the last parameter, category=books, unless explicitly handled as an array.
Exploiting HPP in Laravel (Vulnerable Example)
Imagine a Laravel-based authentication system that verifies user roles via query parameters:
Route::get('/dashboard', function (Request $request) { if ($request->input('role') === 'admin') { return "Welcome, Admin!"; } else { return "Access Denied!"; } });
An attacker could manipulate the request like this:
GET /dashboard?role=user&role=admin
If Laravel processes only the last parameter, the attacker gains admin access.
Mitigating HTTP Parameter Pollution in Laravel
1. Validate Incoming Requests Properly
Laravel provides request validation that can enforce strict input handling:
use Illuminate\Http\Request; use Illuminate\Support\Facades\Validator; Route::get('/dashboard', function (Request $request) { $validator = Validator::make($request->all(), [ 'role' => 'required|string|in:user,admin' ]); if ($validator->fails()) { return "Invalid Role!"; } return $request->input('role') === 'admin' ? "Welcome, Admin!" : "Access Denied!"; });
2. Use Laravel’s Input Array Handling
Explicitly retrieve parameters as an array using:
$categories = request()->input('category', []);
Then process them safely:
Route::get('/search', function (Request $request) { $categories = $request->input('category', []); if (is_array($categories)) { return "Selected categories: " . implode(', ', $categories); } return "Invalid input!"; });
3. Encode Query Parameters Properly
Use Laravel’s built-in security functions such as:
e($request->input('category'));
or
htmlspecialchars($request->input('category'), ENT_QUOTES, 'UTF-8');
4. Use Middleware to Filter Requests
Create middleware to sanitize HTTP parameters:
namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class SanitizeInputMiddleware { public function handle(Request $request, Closure $next) { $input = $request->all(); foreach ($input as $key => $value) { if (is_array($value)) { $input[$key] = array_unique($value); } } $request->replace($input); return $next($request); } }
Then, register it in Kernel.php:
protected $middleware = [ \App\Http\Middleware\SanitizeInputMiddleware::class, ];
Testing Your Laravel Application for HPP Vulnerabilities
To ensure your Laravel app is protected, scan your website using our free Website Security Scanner.

Screenshot of the free tools webpage where you can access security assessment tools.
You can also check the website vulnerability assessment report generated by our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
HTTP Parameter Pollution can be a critical vulnerability if left unchecked in Laravel applications. By implementing proper validation, input handling, middleware sanitation, and secure encoding, you can safeguard your web applications from potential exploits.
🔍 Protect your website now! Use our free tool for a quick website security test and ensure your site is safe from security threats.
For more cybersecurity updates, stay tuned to Pentest Testing Corp. Blog! 🚀
3 notes
·
View notes
Text
Common Things Vulnerable to Y2K38 (+ Explanation)
I want to compile a list of things I find that are vulnerable to the Y2K38 bug. If you find any I don't know about, I can add them to the list. But first, an explanation...
What is Y2K38?
For those that aren't aware, past January 19, 2038 at 3:14:07 UTC (2038-01-19T03:14:07Z), the number of seconds since midnight of January 1, 1970 (1970-01-01T00:00:00Z) will surpass 2^31 - 1.
So what are the implications of this? It has to do with how computers store time.
The Unix epoch is defined as the number of seconds since January 1, 1970, and this is universal to both Unix and Windows systems (so virtually every single computer that doesn't have a homemade operating system). The issue is what specific types of numbers are used to store the epoch.
There are two properties to an integer type: size and sign. The size dictates how many bits a number can hold, and the sign dictates whether or not the integer can store negative numbers. If the number is unsigned, it will be able to store numbers ranging from zero to 2^n - 1, where n is the size of the integer in bits. This means that an 8-bit unsigned number can hold numbers ranging from 0 to 255, because 2^8 - 1 is 255. If a number is signed, the positive range is cut in half. Signed numbers range from -2^(n - 1) to 2^(n - 1) - 1. This means that an 8-bit signed integer can hold numbers ranging from -128 to 127, as -2^7 is -128, and 2^7 - 1 is 127. As integers are used to store the Unix epoch, this means that the epoch is limited to the range of the integer type you use to store it.
If you decide to use a 32-bit signed integer to store the Unix epoch, then once the epoch reaches 2^31 - 1 (which is the upper limit of 32-bit signed integers and is around 2.1 billion), the epoch won't be able to increase anymore. So what happens when we try to increase it anyways? We get an integer overflow.
Due to how CPUs add numbers together, when the result of an operation is larger than the range of the integer type, the result is wrapped around. For example, if you have the number 127 in an 8-bit signed integer, adding one will wrap around to -128! This is a problem for the epoch, because now, instead of storing 2.1 billion seconds past January 1, 1970, it will now be storing 2.1 billion seconds before 1970, which goes all the way back to December 1901!
So why not just use a bigger number? Well, it's not really that simple. There has been an effort to switch over to 64-bit integers, which has an overwhelmingly generous range of around 21 times the estimated age of the universe. However, there are some systems that just can't change or haven't changed for a variety of reasons, and this is what the list will be about. There are two main causes for the Y2K38 bug, and most vulnerabilities stem from them:
32-bit representation of of time_t: time_t is the integer type that time is stored in. When a C program calls the time() function, it will receive a time_t. If time_t is 32-bits long, then the time() function will be vulnerable.
Downcasting the result of time(): There's a pattern in programming I like to call "int-defaultness". C's primitive types are not named with sizes. Instead, they are called 'char', 'short', 'int', and 'long'. These types are standardised to be at least 8 bits, 16 bits, 32 bits, and 64 bits respectively, but most platforms just use those sizes exactly. Usually, you would use exact-sized types like int16_t, uint64_t, and so on, or if it's a function like time(), you would use time_t. However, it is a common pattern to default to int as an integer type, and someone who isn't careful may just convert the result of the time() function into an int. This is known as downcasting, which is the conversion from one integer type to a smaller one. Regardless of whether or not time_t is 32 bits or 64 bits, this downcast will always convert the time to 32 bits, and the overflow behaviour will apply, leaving PHP vulnerable.
As you can see, the time() function is the root cause of the bug, and due to its popularity, usages and mimics of time() can be left vulnerable.
So, without further ado, here is...
The List of Vulnerabilities
PHP time() function: PHP has a time() function that acts very similar to C's, and if the size of a PHP int is 32 bits, PHP is left vulnerable.
pcap file format: The pcap file format (used by libpcap, which is used by utilities like tcpdump and Wireshark) is a format for storing captured packets, and the specification states that the timestamps of packets must stored in a 32-bit unsigned integer. Luckily, since it is unsigned, this will overflow in the year 2106, but there is still some vulnerability here. The PcapNG file format uses 64-bit timestamps, which prevents the vulnerability.
Embedded systems: Smaller computers have a tendency towards lower bit-widths, and 32 bits is common. Embedded systems control things like radios, elevators, GPSes, and more things that don't require heaps of computation power. These systems commonly define time_t to be 32 bits, making them vulnerable.
2 notes
·
View notes
Text
im just gonna outright say it now before people get upset again when i talk abt mental health treatment:
i had a shit experience inpatient for mental health. if it saved your life, good for you, my posts are not about you, they are about me.
tw for abuse, neglect, suicide, death, sa mentions
the place i went to caused the death of a sixteen year old girl and almost took the life of a thirteen year old i know, as well as fucked over so many vulnerable children. they neglected my health issues resulting in almost weekly er visits. therefore, i hold the view that long term treatment facilities are not helpful, they are institutions filled with greed that function as prisons where mentally ill children go to get more mentally ill
i do agree with short term psychiatric wards. i think php and iop are also good options though i never went. outpatient therapy may be enough if someone hasnt been mentally ill for too long. i draw the line at ripping someone from all their friends and comforts, watching them 24/7, not letting them make any friends, and punishing them for every misstep. that doesnt help
i am more sick than ever, my cognitive skills are declining due to overmedication and ive developed a movement disorder that causes me to involuntarily distort my face in painful ways. i have ptsd and nightmares multiple times a week. im scared of people, and im never seeking any mental health help ever again. i see an anp for meds but thats it, we dont discuss how im doing i dont say anything. my arms and legs are covered in scars, most of which happened when i started cutting way deeper after treatment due to paranoia and ptsd. i cant socialize i cant make friends, i dont know how. i cant open up to people.
im a mess but i cant tell anyone. all i want to do is to tell someone tell a friend i want fo fucking cry and scream but i cant bc all i think about is inpatient. i cant even attempt suicide not bc im scared of dying but bc im scared of SURVIVING and ending up insitutionalized again.
dont argue with me on this, youll just piss me off and get blocked.
#vampyrepsychward#important#info#im not talking abt weeklong psych wards im talking abt keeping someone for months or years idgaf abt two weeks#likeyeah still traumatizing but at least its somewhat justifyable
3 notes
·
View notes
Text
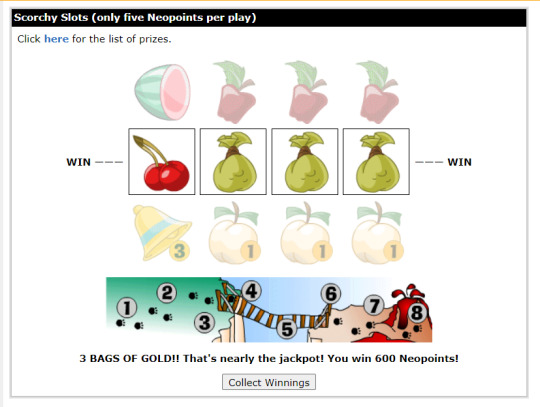
incredible. floored. what do i do with all this money?!??!?!
i really dont understand why neopets (and many other similar games) dont just have a staff member spend a couple weeks, every few years, rebalancing rewards from games. like... no, it wont break the economy if you simply go update the rewards from scorchy slots or dicearoo (or even the 1000np flash games reward lolllllll) to something decently relevant for the current time. in this case, giving me 10-50k np for this win feels like it wouldve been reasonable - and we already get more than 10k just from the daily quests, trudy, etc, so its clearly not going to have any major effect on the economy.
i guess the only actual problem is the php/html games being more vulnerable to cheating in certain ways. but like... they would definitely have been able to afford paying a good programmer to fix security and cheating issues before, even if they currently cant (and cant prioritise old games and old content due to lack of resources).
if i was able to earn like 10k from playing a flash game (if you got a rly good score, not just for any score) i would also be more likely to actually do that. and apparently grundo's cafe gives out item rewards when you get a good score, which is also a good incentive, and reminds me of my childhood on neo where they gave out magical plushies for high scores in some games. (i wanted to get a magical poogle or magical chomby plush so badly)
3 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider “smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
4 notes
·
View notes
Text
Full Stack Testing vs. Full Stack Development: What’s the Difference?

In today’s fast-evolving tech world, buzzwords like Full Stack Development and Full Stack Testing have gained immense popularity. Both roles are vital in the software lifecycle, but they serve very different purposes. Whether you’re a beginner exploring your career options or a professional looking to expand your skills, understanding the differences between Full Stack Testing and Full Stack Development is crucial. Let’s dive into what makes these two roles unique!
What Is Full Stack Development?
Full Stack Development refers to the ability to build an entire software application – from the user interface to the backend logic – using a wide range of tools and technologies. A Full Stack Developer is proficient in both front-end (user-facing) and back-end (server-side) development.
Key Responsibilities of a Full Stack Developer:
Front-End Development: Building the user interface using tools like HTML, CSS, JavaScript, React, or Angular.
Back-End Development: Creating server-side logic using languages like Node.js, Python, Java, or PHP.
Database Management: Handling databases such as MySQL, MongoDB, or PostgreSQL.
API Integration: Connecting applications through RESTful or GraphQL APIs.
Version Control: Using tools like Git for collaborative development.
Skills Required for Full Stack Development:
Proficiency in programming languages (JavaScript, Python, Java, etc.)
Knowledge of web frameworks (React, Django, etc.)
Experience with databases and cloud platforms
Understanding of DevOps tools
In short, a Full Stack Developer handles everything from designing the UI to writing server-side code, ensuring the software runs smoothly.
What Is Full Stack Testing?
Full Stack Testing is all about ensuring quality at every stage of the software development lifecycle. A Full Stack Tester is responsible for testing applications across multiple layers – from front-end UI testing to back-end database validation – ensuring a seamless user experience. They blend manual and automation testing skills to detect issues early and prevent software failures.
Key Responsibilities of a Full Stack Tester:
UI Testing: Ensuring the application looks and behaves correctly on the front end.
API Testing: Validating data flow and communication between services.
Database Testing: Verifying data integrity and backend operations.
Performance Testing: Ensuring the application performs well under load using tools like JMeter.
Automation Testing: Automating repetitive tests with tools like Selenium or Cypress.
Security Testing: Identifying vulnerabilities to prevent cyber-attacks.
Skills Required for Full Stack Testing:
Knowledge of testing tools like Selenium, Postman, JMeter, or TOSCA
Proficiency in both manual and automation testing
Understanding of test frameworks like TestNG or Cucumber
Familiarity with Agile and DevOps practices
Basic knowledge of programming for writing test scripts
A Full Stack Tester plays a critical role in identifying bugs early in the development process and ensuring the software functions flawlessly.
Which Career Path Should You Choose?
The choice between Full Stack Development and Full Stack Testing depends on your interests and strengths:
Choose Full Stack Development if you love coding, creating interfaces, and building software solutions from scratch. This role is ideal for those who enjoy developing creative products and working with both front-end and back-end technologies.
Choose Full Stack Testing if you have a keen eye for detail and enjoy problem-solving by finding bugs and ensuring software quality. If you love automation, performance testing, and working with multiple testing tools, Full Stack Testing is the right path.
Why Both Roles Are Essential :
Both Full Stack Developers and Full Stack Testers are integral to software development. While developers focus on creating functional features, testers ensure that everything runs smoothly and meets user expectations. In an Agile or DevOps environment, these roles often overlap, with testers and developers working closely to deliver high-quality software in shorter cycles.
Final Thoughts :
Whether you opt for Full Stack Testing or Full Stack Development, both fields offer exciting opportunities with tremendous growth potential. With software becoming increasingly complex, the demand for skilled developers and testers is higher than ever.
At TestoMeter Pvt. Ltd., we provide comprehensive training in both Full Stack Development and Full Stack Testing to help you build a future-proof career. Whether you want to build software or ensure its quality, we’ve got the perfect course for you.
Ready to take the next step? Explore our Full Stack courses today and start your journey toward a successful IT career!
This blog not only provides a crisp comparison but also encourages potential students to explore both career paths with TestoMeter.
For more Details :
Interested in kick-starting your Software Developer/Software Tester career? Contact us today or Visit our website for course details, success stories, and more!
🌐visit - https://www.testometer.co.in/
2 notes
·
View notes