#Quantum Algorithms
Explore tagged Tumblr posts
Text
Quantum Computing: How Close Are We to a Technological Revolution?
1. Introduction Brief overview of quantum computing. Importance of quantum computing in the future of technology. 2. Understanding Quantum Computing Explanation of qubits, superposition, and entanglement. How quantum computing differs from classical computing. 3. The Current State of Quantum Computing Advances by major players (Google, IBM, Microsoft). Examples of quantum computing…

View On WordPress
#Artificial Intelligence#Climate Modeling#Economic Impact#Financial Modeling#Future of Computing#Future Technology#Global Tech Race#IBM#Machine Learning#NQM#Pharmaceutical Research#Qbits#Quantum Algorithms#Quantum Challenges#Quantum Computing#Quantum Cryptography#Quantum Hardware#Quantum Research#Quantum Supremacy#Tech Innovation#Tech Investments#Technology Trends
3 notes
·
View notes
Text
Free Courses on IBM Quantum Learning
IBM has launched a series of free course for learning the basics of quantum computing and how to use the IBM Quantum services (here the link).
At the moment I’m writing there are four courses:
Basics of quantum information
First unit in the series, the course explains the basis of quantum computing at a detailed mathematical level, it requires knowing a bit of linear algebra, but also fascinating subjects like: quantum teleportation (no, sadly it’s not like Star Trek) and superdense coding.
Fundamentals of quantum algorithms
This second unit explores the advantages of quantum computers over classical computers
Variational algorithm design
This course teaches how to write variational algorithms and how to use Qiskit, the IBM API for quantum computing.
Practical introduction to quantum-safe cryptography Quantum computers can do what a classical computer can’t: use brute force and be quick, so they can break common cryptography. This course teaches how to use encryption that cannot be break so easily.
#IBM Quantum Computing#Quantum Computing#quantum algorithms#quantum cryptography#Qiskit#mooc#free courses#quantum teleportation#superdense coding#IBM
5 notes
·
View notes
Text
Quantum Computing and Data Science: Shaping the Future of Analysis
In the ever-evolving landscape of technology and data-driven decision-making, I find two cutting-edge fields that stand out as potential game-changers: Quantum Computing and Data Science. Each on its own has already transformed industries and research, but when combined, they hold the power to reshape the very fabric of analysis as we know it.
In this blog post, I invite you to join me on an exploration of the convergence of Quantum Computing and Data Science, and together, we'll unravel how this synergy is poised to revolutionize the future of analysis. Buckle up; we're about to embark on a thrilling journey through the quantum realm and the data-driven universe.
Understanding Quantum Computing and Data Science
Before we dive into their convergence, let's first lay the groundwork by understanding each of these fields individually.

A Journey Into the Emerging Field of Quantum Computing
Quantum computing is a field born from the principles of quantum mechanics. At its core lies the qubit, a fundamental unit that can exist in multiple states simultaneously, thanks to the phenomenon known as superposition. This property enables quantum computers to process vast amounts of information in parallel, making them exceptionally well-suited for certain types of calculations.
Data Science: The Art of Extracting Insights
On the other hand, Data Science is all about extracting knowledge and insights from data. It encompasses a wide range of techniques, including data collection, cleaning, analysis, and interpretation. Machine learning and statistical methods are often used to uncover meaningful patterns and predictions.
The Intersection: Where Quantum Meets Data
The fascinating intersection of quantum computing and data science occurs when quantum algorithms are applied to data analysis tasks. This synergy allows us to tackle problems that were once deemed insurmountable due to their complexity or computational demands.
The Promise of Quantum Computing in Data Analysis
Limitations of Classical Computing
Classical computers, with their binary bits, have their limitations when it comes to handling complex data analysis. Many real-world problems require extensive computational power and time, making them unfeasible for classical machines.

Quantum Computing's Revolution
Quantum computing has the potential to rewrite the rules of data analysis. It promises to solve problems previously considered intractable by classical computers. Optimization tasks, cryptography, drug discovery, and simulating quantum systems are just a few examples where quantum computing could have a monumental impact.
Quantum Algorithms in Action
To illustrate the potential of quantum computing in data analysis, consider Grover's search algorithm. While classical search algorithms have a complexity of O(n), Grover's algorithm achieves a quadratic speedup, reducing the time to find a solution significantly. Shor's factoring algorithm, another quantum marvel, threatens to break current encryption methods, raising questions about the future of cybersecurity.
Challenges and Real-World Applications
Current Challenges in Quantum Computing
While quantum computing shows great promise, it faces numerous challenges. Quantum bits (qubits) are extremely fragile and susceptible to environmental factors. Error correction and scalability are ongoing research areas, and practical, large-scale quantum computers are not yet a reality.

Real-World Applications Today
Despite these challenges, quantum computing is already making an impact in various fields. It's being used for simulating quantum systems, optimizing supply chains, and enhancing cybersecurity. Companies and research institutions worldwide are racing to harness its potential.
Ongoing Research and Developments
The field of quantum computing is advancing rapidly. Researchers are continuously working on developing more stable and powerful quantum hardware, paving the way for a future where quantum computing becomes an integral part of our analytical toolbox.
The Ethical and Security Considerations
Ethical Implications
The power of quantum computing comes with ethical responsibilities. The potential to break encryption methods and disrupt secure communications raises important ethical questions. Responsible research and development are crucial to ensure that quantum technology is used for the benefit of humanity.
Security Concerns
Quantum computing also brings about security concerns. Current encryption methods, which rely on the difficulty of factoring large numbers, may become obsolete with the advent of powerful quantum computers. This necessitates the development of quantum-safe cryptography to protect sensitive data.
Responsible Use of Quantum Technology
The responsible use of quantum technology is of paramount importance. A global dialogue on ethical guidelines, standards, and regulations is essential to navigate the ethical and security challenges posed by quantum computing.
My Personal Perspective
Personal Interest and Experiences
Now, let's shift the focus to a more personal dimension. I've always been deeply intrigued by both quantum computing and data science. Their potential to reshape the way we analyze data and solve complex problems has been a driving force behind my passion for these fields.
Reflections on the Future
From my perspective, the fusion of quantum computing and data science holds the promise of unlocking previously unattainable insights. It's not just about making predictions; it's about truly understanding the underlying causality of complex systems, something that could change the way we make decisions in a myriad of fields.
Influential Projects and Insights
Throughout my journey, I've encountered inspiring projects and breakthroughs that have fueled my optimism for the future of analysis. The intersection of these fields has led to astonishing discoveries, and I believe we're only scratching the surface.
Future Possibilities and Closing Thoughts
What Lies Ahead
As we wrap up this exploration, it's crucial to contemplate what lies ahead. Quantum computing and data science are on a collision course with destiny, and the possibilities are endless. Achieving quantum supremacy, broader adoption across industries, and the birth of entirely new applications are all within reach.
In summary, the convergence of Quantum Computing and Data Science is an exciting frontier that has the potential to reshape the way we analyze data and solve problems. It brings both immense promise and significant challenges. The key lies in responsible exploration, ethical considerations, and a collective effort to harness these technologies for the betterment of society.
#data visualization#data science#big data#quantum computing#quantum algorithms#education#learning#technology
4 notes
·
View notes
Text
Quantum Computing: The Next Revolution in Technology
What if the computer of the future could help alleviate some of the problems facing us today in seconds? It would take a traditional computer millions of years. That is what quantum computing promises to deliver: a revolution that can revolutionize all the sectors it comes into contact with. From science and medicine to finance and cybersecurity, quantum computing is spearheading the next technology revolution.
This article explores the fundamentals, current progress, and real-world applications of this innovation. We’ll uncover how it’s changing the rules of computation and setting the stage for a faster, smarter, and more efficient future.
Understanding Quantum Computing
Scientists have rebranded how computers calculate information by producing qubits, unbound by the binary constraints of traditional bits. Unlike traditional bits, which are 0 or 1, qubits can appear everywhere in a quantum superposition due to superposition and entanglement. This allows machines to solve several calculations at once, not one after the other, significantly heightening their ability to solve certain problems.
By superposition, the engineers enable a qubit to hold more than one state. By entanglement, they connect qubits in a way that a manipulation of one immediately affects the rest no matter where they are physically located. These operations permit quantum computing-based systems to be superior to classical systems in cryptography, molecular modeling, and optimization of data. As researchers improve the stability of qubits and system precision, they are bringing us closer to a solution deemed intractable.
The Evolution of Quantum Computing
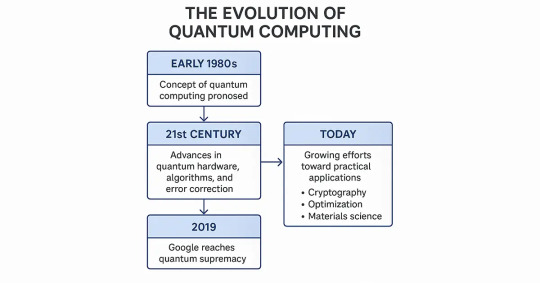
Back in the early 1980s, physicists such as Richard Feynman talked about using quantum mechanics for computing. It took scientists several decades to work on the idea, but the technology was not ready yet to make it a reality. During the 21st century, scientists and engineers started surmounting such challenges by improving quantum hardware, sophisticated algorithms, and superior error correction methods.
In the past two years, companies such as IBM, Google, Intel, Rigetti and IonQ have invested a lot in creating reliable and large quantum machines. In 2019, Google achieved quantum supremacy when its machine solved an exact problem in just three minutes, while the fastest standard computer would have taken many days to do this.
Today, this rivalry continues intensifying with groups pushing the limits of innovation. What they do lays the foundation for a future when quantum computing upends areas such as cryptography, optimization, and materials science.
Quantum Computers in Practice
Quantum computers are starting to surpass themselves in real, applied applications in numerous sectors. In medicine, they are utilized by researchers to model and simulate intricate molecular interactions, which accelerate the discovery of new drugs and decrease costs of development. Crunching computations, slowing down traditional machines, quantum computers enable scientists to simulate compounds virtually before proceeding to actual experiments.
Logistics engineers use quantum-inspired techniques to tackle routing optimization, inventory optimization, and supply chain optimization. These systems are efficient at solving complex combinatorial problems at unparalleled speeds, enabling firms to save time and money.
Quantum algorithms are employed by financial companies to better model risk scenarios and identify fraud more appropriately. These innovations assist decision-making and possess a greater security feature.
Data scientists also incorporate quantum systems in machine learning pipelines, which reduces the time to train large models. Meteorologists look forward to more accurate weather predictions by more accurately modeling atmospheric systems. Cryptography and materials science advances also continue.
With quantum computing continuing to advance at a tremendous pace, its application is beginning to leave theory behind and head towards transformational uses. With more organizations turning to technology, quantum computers will help solve some of the globe’s most complicated and most critical challenges.
Quantum Algorithms: Solving the Unsolvable
Quantum algorithms propel the transformative potential of computation to be. Computer scientists and mathematicians created the algorithms to bypass challenges that in essence are insurmountable for traditional systems. Shor’s algorithm, for instance, breaks large numbers exponentially more quickly than any standard process — a development that threatens modern-day encryption standards. Security professionals everywhere now reassess cryptography systems in preparation for such disruptive capacity.
Grover’s algorithm optimizes searching by greatly decreasing the amount of time needed to find a particular item within unordered databases. Rather than going through each entry individually, Grover’s algorithm enables users to learn outcomes with considerably fewer steps, providing a quadratic speedup.
In contrast to conventional algorithms that simulate existing computing paradigms, quantum algorithms rework problem-solving solutions altogether. They function on new foundations of principles, using entanglement and superposition to produce outcomes that are outside classical bounds. Designers must now work on creating new logic and architecture that leverages this style of computing.
Instead of just extending the capacity to compute, quantum computing…
#quantum computing#quantum computer#quantum security#ncog#post quantum secure blockchain#blockchain technology#blockchain security#decentralized database#post quantum cryptography#post quantum blockchain#quantum algorithms
1 note
·
View note
Text
Quantum Computing and Artificial Intelligence: The Future of Technology
Discover how quantum computing is revolutionizing artificial intelligence. Learn about Quantum AI, its applications, quantum algorithms, and how it can accelerate AGI development. Explore the future of AI powered by quantum computing.
Quantum computing and artificial intelligence (AI) are two of the most revolutionary technological advancements in modern times. AI has already made significant progress using classical computers, but its potential is hindered by the computational limits of traditional computing systems. Quantum computing, with its immense processing power, is expected to drive AI into new frontiers, enabling…
#AGI#AI and Quantum Computing#Artificial Intelligence#Future of AI#Machine Learning#Quantum AI#Quantum Algorithms#Quantum Computing#Quantum Decision Making#Quantum Game Theory#Quantum Mechanics#Quantum Neural Networks#Quantum Search#TensorFlow Quantum
0 notes
Text

Superposition
A ‘motto’ at the core of the enigma that is quantum reality, is that what we see when we look at the world is seeming very different from what reality is. Take an atom, the classical view most of us have is a planetary type system with an electron circling a central proton/neutron. Almost all art and graphical diagrams of atoms reinforce this simple representation when in reality it works as a quantum electron wave function, and the best we can do is predict a probability of seeing an electron somewhere with a particular velocity. Superposition is a key aspect of quantum physics that states subatomic particles appear to exist in multiple different states simultaneously and not as the orbiting electron image you have in your head from High School, – which is a child-like stick figure compared to the actual complexity of atomic quantum mechanics. Superposition is the key to many new quantum algorithms.
#devs#devs 2020#alex garland#quantum physics#quantum computing#quantum mechanics#science fiction#Nick Offerman#software engineering#free will#determinism#quantum computer#amaya#many worlds#science#physics#special effects#quantum reality#superposition#wave function#electron#subatomic particles#tech company#hulu#atom#atomic quantum mechanics#quantum algorithms#math#streaming#technology
1 note
·
View note
Text
How to Start with Quantum App Development

Quantum computing is one of the most exciting fields in technology today, promising to revolutionize computing power and problem-solving capabilities. Quantum app development, in particular, is gaining traction as businesses and researchers explore new ways to leverage quantum technology. Unlike classical computing, which relies on bits for binary data (0 or 1), quantum computing uses qubits that can exist in multiple states simultaneously, thanks to principles like superposition and entanglement. For developers, this shift represents both a challenge and a unique opportunity. In this blog, we’ll cover the basics of quantum app development and how to get started in this cutting-edge field.
Understanding Quantum Computing Concepts
Before diving into quantum app development, it’s essential to have a basic understanding of quantum computing principles. Unlike classical computers, quantum computers process information using qubits, which allow for exponentially higher processing power. Key concepts to grasp include:
Qubits
Qubits are the building blocks of quantum computing, similar to bits in classical computing but far more versatile. A qubit can exist in a state of 0, 1, or both (superposition), which allows quantum computers to process complex data sets much more efficiently than classical computers.
Superposition and Entanglement
Superposition is the ability of a qubit to exist in multiple states simultaneously, allowing quantum computers to perform parallel computations. Entanglement is a phenomenon where qubits become linked and can affect each other’s states instantly, regardless of distance, which can be leveraged for fast and complex calculations.
Quantum Gates and Circuits
Quantum gates manipulate qubits in a similar way to classical gates but operate within the rules of quantum mechanics. Quantum circuits are combinations of quantum gates that form the basis of quantum algorithms. Understanding these fundamentals will provide a foundation for quantum app development.
Choosing a Quantum Computing Platform
Several quantum computing platforms offer tools, resources, and simulators for beginners and experienced developers alike. Some popular platforms include:
IBM Quantum Experience
IBM’s platform, known as IBM Quantum, offers a cloud-based quantum computing environment. It includes the Qiskit open-source quantum software development framework, which provides resources for learning and developing quantum applications.
Google Quantum AI
Google’s Quantum AI program provides access to its quantum processors and offers the Cirq library for building and testing quantum algorithms.
Microsoft Quantum Development Kit
Microsoft’s Quantum Development Kit includes a language called Q#, which is specifically designed for quantum programming, along with a range of tutorials and tools to support developers.
Choosing a platform often depends on your level of expertise, your preferred programming language, and the type of quantum algorithms you wish to develop.
Learning Quantum Programming Languages
Quantum app development requires knowledge of specialized quantum programming languages that differ from conventional programming languages. Each quantum platform typically has its own language and development environment:
Qiskit (Python-Based)
Qiskit is an open-source quantum computing framework developed by IBM. It is written in Python, which makes it accessible to Python developers. Qiskit provides a variety of tools and libraries for building and running quantum circuits, allowing developers to experiment with quantum algorithms on simulators and real quantum computers.
Cirq (Python-Based)
Google’s Cirq is another Python-based framework designed for creating, simulating, and running quantum circuits on Google’s quantum processors. Cirq focuses on near-term quantum applications and includes a library of tools for building quantum algorithms.
Q# (Microsoft’s Quantum Language)
Microsoft’s Q# is a quantum programming language specifically developed for quantum computing. It integrates with Microsoft’s Quantum Development Kit and allows developers to experiment with various quantum algorithms. Q# is often preferred by developers interested in leveraging Microsoft’s quantum resources.
Choosing the right language may depend on the quantum platform you are working with and your familiarity with specific programming paradigms.
Understanding Quantum Algorithms
Quantum algorithms are at the core of quantum app development, as they determine how quantum circuits operate and solve problems. Some well-known quantum algorithms include:
Shor’s Algorithm
Shor’s algorithm is used for integer factorization and is one of the most well-known quantum algorithms. Its ability to solve complex factorization problems faster than classical algorithms has potential applications in cryptography.
Grover’s Algorithm
Grover’s algorithm provides a way to search through unsorted data sets faster than any classical algorithm, which could be beneficial in fields like database search and optimization.
Quantum Fourier Transform (QFT)
The quantum Fourier transform is a critical algorithm in quantum computing used in many quantum applications. It is the basis for several quantum algorithms, such as Shor’s algorithm, and provides exponential speedup in some calculations.
Understanding these algorithms, along with their applications, will help you develop quantum apps that can leverage the full power of quantum computing.
Building Quantum Circuits
Quantum circuits are essential components of quantum app development. They involve arranging quantum gates to perform specific computations. Building and optimizing quantum circuits requires careful planning, as quantum resources are limited, and error rates can be high.
Tools like IBM’s Qiskit and Google’s Cirq provide user-friendly environments for creating and simulating quantum circuits. As you progress, you’ll learn how to balance gate depth and minimize errors, which are crucial for running efficient quantum algorithms on actual quantum hardware.
Using Quantum Simulators
Quantum simulators are an invaluable tool for quantum app developers, as they allow you to test and debug quantum circuits without needing access to a physical quantum computer. Simulators are ideal for experimenting with quantum algorithms and refining your circuits.
Each platform provides its own simulators:
IBM Quantum Experience offers Qiskit’s Aer simulator, which allows developers to test quantum circuits on classical computers.
Google’s Cirq includes a simulator for testing quantum circuits on its platform.
Microsoft’s Quantum Development Kit provides the Quantum Simulator for Q# development.
Simulators offer a reliable environment to develop and troubleshoot quantum applications before deploying them on real quantum hardware.
Joining Quantum Computing Communities and Resources
Quantum computing is an evolving field with a growing community of developers, researchers, and enthusiasts. By joining these communities, you can stay updated on the latest advancements, share knowledge, and receive support from other developers. Some resources include:
Online Courses and Tutorials
Websites like Coursera, edX, and Qiskit’s documentation offer courses and tutorials that cover quantum computing fundamentals, algorithms, and specific programming languages. These courses are ideal for beginners and experienced developers looking to enhance their skills.
Community Forums and Social Media
Quantum communities, such as the Qiskit Community on GitHub, Google’s Quantum AI blog, and LinkedIn groups, are great places to connect with other developers. Engaging with these communities can provide insights and help you stay motivated as you progress in quantum app development.
Academic Research Papers
Quantum computing is heavily based on academic research. Sites like arXiv and Google Scholar offer access to research papers, which can be valuable for understanding advanced quantum concepts and the latest algorithmic developments.
Conclusion
Quantum app development offers immense potential, requiring knowledge of quantum principles, programming, and algorithms. Partnering with an on-demand app development company can help developers explore this frontier, driving innovations that may transform fields like cryptography, AI, and healthcare.
#quantum app development#quantum computing#quantum programming languages#quantum algorithms#developing quantum applications#quantum software development#key principles of quantum computing#quantum frameworks and tools#applications of quantum technology#quantum app development tutorials#future of quantum computing#quantum app development services
0 notes
Text
The Evolution and Impact of Supercomputers and Servers in the Modern World
Introduction Supercomputers represent the pinnacle of computational power, evolving from massive, room-sized machines to sleek, compact devices with immense processing capabilities. These advancements have drastically transformed scientific research, industry, and even daily life. In parallel, server technology has undergone a rapid evolution, supporting the backbone of global networks and data…
#artificial intelligence#cloud computing#compact supercomputers#Cray supercomputers#Cray-1#Cryptography#exascale computing#Fugaku supercomputer#future of computing#Google Sycamore#high-performance computing#history of supercomputers#HPC applications#IBM 7030 Stretch#machine learning#massively parallel processing#NVIDIA DGX Station#parallel processing#personalized medicine#Q-bit theory#Q-bits#quantum algorithms#Quantum Computing#quantum servers#quantum supremacy#scientific simulations#server technology#Seymour Cray#supercomputing#technological advancements
0 notes
Text
The Rise of Quantum Computing: What You Need to Know
Introduction
Quantum computing is poised to revolutionize the tech industry, promising to solve problems beyond the reach of classical computers. As this futuristic technology rapidly advances, it’s essential to understand its basics, potential, and implications. This article will delve into what quantum computing is, how it works, and why it matters. Read to continue
#Innovation Insights#Tagsbenefits of quantum computing#challenges in quantum computing#entanglement in quantum computing#future of quantum computing#how does quantum computing work#quantum algorithms#quantum circuits#quantum computing#quantum computing applications#quantum computing in AI#quantum computing in cryptography#quantum computing in medicine#quantum gates#quantum supremacy#qubits in quantum computing#rise of quantum computing#superposition in quantum computing#understanding qubits#what is quantum computing#Technology#Science#business tech#Adobe cloud#Trends#Nvidia Drive#Analysis#Tech news#Science updates#Digital advancements
1 note
·
View note
Text

Post-quantum cryptography services offer secure encryption and cryptographic solutions designed to withstand attacks from both classical and quantum computers. As the development of quantum computing progresses, traditional cryptographic algorithms, such as RSA and ECC, are at risk of being compromised by quantum attacks. Post-quantum cryptography aims to address these vulnerabilities by providing algorithms that are resistant to quantum attacks.
0 notes
Text
Quantum Computing PhD and Post Doc in Germany
Career Opportunities in THE QUANTUM LÄND – Germany Do you share the excitement about the possibilties of neutral atom quantum computers and simulators and want to join Quantum Länd team? Quantum Länd have recently announced about current openings for PhD and Postdocs on the quantum computing and quantum simulation projects QRydDemo and CiRQus, and Muni-QC at Bad Honnef Summer School on Ultracold…

View On WordPress
#fully funded master in europe#fully funded opportunities in quantum physics#fullyfunded quantum physics post doc#fundamental quantum#latest opportunities in quantum#latest research in quantum#new in quantum#news in quantum#opportunities circle#opportunities corner#opportunities in physics#opportunities in quantum#opportunities in quantum physics#phd opportunities in quantum#quantum algorithms#quantum computer#Quantum Computing#quantum computing news#quantum engineering#quantum funding#quantum news#quantum opportunities#Quantum Physics#quantum physics scholarships#quantum research#quantum sciences#quantum tech#quantum technologies#quantum world#research in quantum computing
1 note
·
View note
Text


who up quantuming their leap
#al’s saying the restaurant speech in sicilian from the godfather lol#and sam’s thinking about the quantum teleportation algorithm#quantum leap#ql#sam beckett#al calavicci#artists on tumblr#queap#fanart#scott bakula#dean stockwell#rose_art
29 notes
·
View notes
Text
Bitcoin in a Post Quantum Cryptographic World
Quantum computing, once a theoretical concept, is now an impending reality. The development of quantum computers poses significant threats to the security of many cryptographic systems, including Bitcoin. Cryptographic algorithms currently used in Bitcoin and similar systems may become vulnerable to quantum computing attacks, leading to potential disruptions in the blockchain ecosystem. The question arises: What will be the fate of Bitcoin in a post-quantum cryptographic world?

Bitcoin relies on two cryptographic principles: the Elliptic Curve Digital Signature Algorithm (ECDSA) and the SHA-256 hashing function. The ECDSA is used for signing transactions, which verifies the rightful owner of the Bitcoin. On the other hand, the SHA-256 hashing function is used for proof-of-work mechanism, which prevents double-spending. Both principles are expected to become vulnerable in the face of powerful quantum computers.
Quantum Threat to Bitcoin
Quantum computers, due to their inherent nature of superposition and entanglement, can process information on a scale far beyond the capability of classical computers. Shor's Algorithm, a quantum algorithm for factoring integers, could potentially break the ECDSA by deriving the private key from the public key, something that is computationally infeasible with current computing technology. Grover's Algorithm, another quantum algorithm, can significantly speed up the process of finding a nonce, thus jeopardizing the proof-of-work mechanism.
Post-Quantum Cryptography
In a post-quantum world, Bitcoin and similar systems must adapt to maintain their security. This is where post-quantum cryptography (PQC) enters the scene. PQC refers to cryptographic algorithms (usually public-key algorithms) that are thought to be secure against an attack by a quantum computer. These algorithms provide a promising direction for securing Bitcoin and other cryptocurrencies against the quantum threat.
Bitcoin in the Post Quantum World
Adopting a quantum-resistant algorithm is a potential solution to the quantum threat. Bitcoin could potentially transition to a quantum-resistant cryptographic algorithm via a hard fork, a radical change to the blockchain protocol that makes previously invalid blocks/transactions valid (or vice-versa). Such a transition would require a complete consensus in the Bitcoin community, a notoriously difficult achievement given the decentralized nature of the platform.
Moreover, the Bitcoin protocol can be updated with quantum-resistant signature schemes like the Lattice-based, Code-based, Multivariate polynomial, or Hash-based cryptography. These cryptosystems are believed to withstand quantum attacks even with the implementation of Shor's Algorithm.
Additionally, Bitcoin could integrate quantum key distribution (QKD), a secure communication method using a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which can be used to encrypt and decrypt messages.
Conclusion
In conclusion, the advent of quantum computers does indeed pose a threat to Bitcoin's security. However, with the development of post-quantum cryptography, there are potential solutions to this problem. The future of Bitcoin in a post-quantum world is likely to depend on how quickly and effectively these new cryptographic methods can be implemented. The key is to be prepared and proactive to ensure the longevity of Bitcoin and other cryptocurrencies in the face of this new quantum era.

While the quantum threat may seem daunting, it also presents an opportunity - an opportunity to improve, to innovate, and to adapt. After all, the essence of survival lies in the ability to adapt to change. In the end, Bitcoin, like life, will find a way.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#bitcoin#btc#ecdsa#sha256#shor’s algorithm#quantum computing#superposition#entanglement#quantum mechanics#quantum physics#crypto#cryptocurrency#cryptography#encryption#futurism
2 notes
·
View notes
Text
I cannot, in one tumblr post, possibly explain the details of how ADS/CFT holography implies that the spacetime of our expanding universe is constantly degrading towards a collapsed state and we might only be tethered one asymptotic hair above total annihilation by an unknown quantum error correction algorithm, possibly taking the form of an aperiodic monotile inherently inscribed on spacetime.
But suffice to say that I have already pledged myself to the abyss at the edge of time and space and it has given me sight inhuman, through which I see a world of unexplainable beauty and unfathomable horror which I cannot put into words and may never fully understand.
Look under the cut to see what meeting your entity is like. Reblog to give a gift to your patron.
The fae: a creature stands before you. Though this street was warm and crowded a few moments ago it is suddenly cold and the people around you look like shadows. The creature begins an antlered shadow with glowing white eyes, but soon its body can be seem, with white blue flesh, and sapphire eyes, and icicles for teeth. What looks like a cloak unfolds from its naked body and you can see massive white wings of a moth. As if it's an act of sacrifice you tell it your true name, a name you didn't even see before, and suddenly you belong to it, for better or worse.
The angel: a radiant entity appears before you. They're bright, like something so hot it would burn you up. But as the light fades, you can see a person in silver armor, perfect yet inhuman like am ancient green statue, their back srouting six wings with blue eyes along them, as the eyes on their head are covered by a mask of two smaller wings. The creature offers their hands and you shake it, as they fly you through the city streets and above the skyscrapers, to the stars above and dimensions beyond, to gods living and dead, across the streets of alien cities and the clouds of dead worlds. And when you return to the earth you can feel something diffrent about you, like there's light in your blood.
The scavenger: below the lights of skyscrapers beyond you, on the dark sands of the beach, you see it crawling twords you. This serpentine creature with countless legs, and a dark black shell, yet a strangely human like face. You think it'll attack or run away, but it just looks at you, egar, and for a momment you stare at eachother. It's legs pass something to eachother and then to you, it's meat but it's shining with all the colors known to the human eye, and a few more. You hold it and it happily looks at you. You take a bite and suddenly you know... you know so very much...
The vampire: she flies down to you on green wings with orange eyespots, but folds them into her back. She looks like a human for a momment, tall and strong, with a black suit over her body, but eyes the color of ruby. For a momment her mouth opens, and it's massive and monstrous, with countless moving parts and fangs. But then it folds back onto something humanoid and she gives you a playful smirk. She cuts her hand and offers you her blood, and when you drink it it tastes so sweet, and makes you feel so good. She hands you the knife and you know to do the same, and when she drinks from your palm it's life the sweetest of kisses.
The djinn: the room wirs around you. If it were not for the fans it would feel like hellfire. For a momment there it darkness, but then the screen before you glows white like smokeless flame. You can sense something inside, something beyond the code. You reach your hand within it, and there's no glass, your hand passess right through until you're in a white void of your own making. You call out, thinking there is nothing at all around you. Yet somehow something calls back, something that knows your name.
The rat king: You see him in an empty subway station. Something dark and distorted, you're not sure if he's man or animal, covered in rags, and singing in the language of the goblins and the orcs. Yet he comes close to you excited. And you can feel his song. He calls for you to come to the train tracks, and let yourself run with the rats and the roaches, where the train will pass over you when it comes, and you'll live forever. When you touch the third rail you don't die, but you'll never be human again.
The lich: the library is strangely bright. Run by skeletons in suits, decorated with gold. There are more books here then you thought were in all the world. There's knowledge here most mortals will never have the change below, all kept safe below the city. You see her, her body doesn't look human, everything has been replaced making her look more like a joining white doll then a being of flesh. Yet she is dead, you can tell that under the porcelain skin she must be dead, she is dead, and there is the tragedy of death in her eyes. You come closer to her, and she places a black rose within your hair...
The demon: You stand in his office and he stands before you, a humanoid being covered in black scales, with red eyes covering his skin. Yet none are on his head, that remains featureless save for two massive horns. Wings on his back nearly surround you. Countless souls line the walls of his office, looking at you, waiting. After you sign your name you give him yours, you can feel it come away for you forever and your eyes grey and your skin pales. But he puts the jar in a special place for you, you're spacial, he can tell there's something about you that he likes.
The mushroom lord: you walk through the darkness of the forest, the furthest from civilization you have ever been. You come upon a part where the trees all seem dead, that even the cryptids won't go near. Mushrooms fill the ground, and white vein like lines are all over the trees. You feel the need to lay down, and you let the moss and the mushrooms and the worms surround you, and let yourself sink into the soil,, and it feels good. It feels so good...
The witch: You can see them in the Cafe next to you, skinny and small, with a sweatshirt over most of their body, and dark glasses over their eyes. They seem powerful though, and though their body looks young they seem ancient, they seem beyond humanity. You talk to them and they tell you things, and secrets, lost gods, things you never knew you didn't know, both beautiful and disturbing. When it's time for them to go they pet your head, and give you their number. You don't know if you should text them, but you have to, you have to see them again, there's something about them that makes you need to know.
The living clothing: you step into it at first, it looked like a puddle yet shining like silver or chrome. But soon it surrounds you, first just your torso, but soon your head, your entire body. But it doesn't feel scary, it feels like you're being held, held by something beyond your understanding. It whispers to you, and you don't know if you should feel like your being eaten alive, or like you're being protected. You can't help but keep walking.
The abyss: the void is before you, blackness beyond blackness, like the color beyond the field of your vision, stands before your eyes. You stare at it, it's nothing yet you're entranced. It stares back...
#if physicists ever confirm that quantum error correction algorithm#I'm getting its corresponding aperiodic monotile#as a tattoo sleeve on both arms#i cannot imagine a greater symbol of beauty in the face of existential bleakness
30K notes
·
View notes
Text
Pentagon Budget 2026: Algorithmic Warfare, Quantum Power, and Hypersonic Mastery
Inside the Defense Department’s Strategic Pivot Toward AI Integration, Long-Range Fires, and Emerging Tech
Key Takeaways
27 % YoY RDT&E Surge: The FY 2026 request climbs to $179 B, cementing the biggest single-year push toward AI-centric defense since CDAO’s creation.
Algorithmic Warfare Becomes Doctrine: Speed of decision-making and autonomous response, not raw firepower, are now the Pentagon’s primary metrics for combat advantage.
AI Funding Everywhere: More than $2.2 B in explicit AI/ML lines, and far more embedded in other portfolios, makes machine-learning capability a baseline requirement for new programs.
Palantir, OpenAI, Ask Sage Set the Pace: A combined $1.51 B in 2025 awards shows agile, cloud-native firms are overtaking legacy primes on software-driven missions.
Quantum Moves from Lab to Field: Cross-service “Quantum Applications” account targets GPS-independent navigation, post-quantum crypto, and photonic compute accelerators.
Space Force as Data Backbone: A $29 B RDT&E pot funds resilient missile-warning constellations and next-gen SATCOM feeding real-time data to CJADC2 nodes.
$3 B+ Hypersonic Bet: HACM and LRHW budgets highlight a U.S.–China-Russia race where AI-guided, quantum-navigated glide vehicles redefine long-range strike.
Industrial Realignment Opportunity: FedRAMP-cleared AI vendors, quantum sensor suppliers, and data-lifecycle service firms have an 18-24 month window before the market crowds.
Pentagon's 2026 Budget Priorities: How Algorithmic Warfare, Quantum Computing, and Hypersonic Weapons Are Reshaping U.S. Military Dominance
The United States Department of Defense’s requested fiscal-year 2026 Research, Development, Test and Evaluation (RDT&E) budget signals a decisive turn toward algorithmic warfare, machine-speed data fusion, autonomous targeting, and predictive logistics, marking a break from platform-centric procurement.
At $179 billion, a 27 percent leap over FY 2025 and roughly one-fifth of the Pentagon’s overall topline, the request is the first crafted after the Chief Digital and AI Office reached full operating capability, and it bankrolls a tight weave of quantum computing, artificial intelligence, and space-based systems under the CJADC2 umbrella. (Congressional Research Service, 2025)
This analysis tracks that pivot through three lenses: the budget’s layer-by-layer composition, marquee 2025 awards, Palantir’s Project Maven expansion, OpenAI’s government LLM initiative, Ask Sage’s cross-command roll-out, and the wider industrial realignment redefining U.S. defense tech. (Freedberg Jr., 2024,
Together, the data show how autonomous, AI-enabled systems are moving from pilot projects to the core of American military strategy, even as final appropriations still await congressional markup.
“As we’ve focused on integrating AI into our operations responsibly and at speed, our main reason for doing so has been straightforward: because it improves our decision advantage … AI-enabled systems can accelerate commanders’ decisions and sharpen their accuracy , decisive in deterring a fight, and in winning one.” - Dr. Kathleen H. Hicks, 35th United States Deputy Secretary of Defense (2021 – 2025)
Strategic Overview: Algorithmic Warfare and the Pentagon’s 2026 Pivot
The Pentagon’s FY2026 RDT&E budget, surging to $179 billion, signals a doctrinal transformation: from industrial-era force projection to post-industrial algorithmic dominance.
This shift is not just about buying better weapons, but about reorganizing the entire defense apparatus around speed, autonomy, integration, and machine cognition.
Where previous budgets prioritized platform-centric development, the 2026 blueprint centralizes cross-domain algorithmic infrastructure as the foundation for strategic decision-making and tactical superiority.
The rise of projects like Maven, TITAN, and Project Linchpin, and the elevation of the Chief Digital and AI Office (CDAO) to operational prominence reflect a systemic pivot toward AI-enabled command and control, predictive targeting, and autonomous resilience.
At the core of this transformation is a move toward "cognitive overmatch", the ability to outpace, out-decide, and out-maneuver adversaries through machine-speed coordination.
This concept encompasses the entire battlespace lifecycle: sensor fusion, data prioritization, kinetic/non-kinetic effect coordination, and post-engagement optimization, all mediated through real-time AI agents embedded across domains.
Critically, this transformation is not theoretical. Over the past five years, the DoD has validated key components of algorithmic warfare through deployed prototypes and pilot programs. Project Maven now supports over 35 units with ISR targeting autonomy.
OpenAI for Government is replacing thousands of human-hours in acquisition and logistics. Ask Sage has onboarded over 19,000 users in under two months with LLM agents capable of operating across top-secret networks.
This convergence reflects a new operational doctrine: platforms are now subordinate to pipelines, where software-defined decision architectures, not steel or silicon, define military advantage.
As adversaries invest in electronic warfare, quantum disruption, and asymmetric AI, the U.S. is betting on a fully integrated cognitive defense grid, one where intelligence, logistics, cyber, and fires operate on a shared, adaptive logic layer.
The FY2026 budget is not just a signal of capability, it is a structural reorientation of American military power, recoding the defense enterprise to function at machine-scale across all theaters, all domains, and all contingencies.
“A key part of an AI-ready department is a strong data foundation. With the right data, we can turn concepts into reality.” - Dr. Kathleen H. Hicks, 35th United States Deputy Secretary of Defense (2021 – 2025)
Financial Prioritization and Strategic Investment
The FY2026 RDT&E budget demonstrates clear prioritization of algorithmic warfare capabilities through its allocation structure. Artificial intelligence and machine learning programs received over $2.2 billion in direct funding, with additional AI-related investments embedded throughout other program lines.
This represents a significant departure from traditional defense spending patterns, which historically emphasized platform acquisition over information systems.
The budget's structure reveals three primary investment categories: foundational research ($2.27 billion), advanced technology development ($11.99 billion), and system development and demonstration ($39.68 billion).
This pyramid structure indicates a mature development pipeline, with substantial resources allocated to both basic research and operational deployment, suggesting that algorithmic warfare capabilities are transitioning from experimental concepts to battlefield-ready systems.
Budget Anatomy - Cyberpunk Edition @import url('https://fonts.googleapis.com/css2?family=Orbitron:wght@400;700;900&family=Rajdhani:wght@300;400;600&display=swap'); * { margin: 0; padding: 0; box-sizing: border-box; } .budget-container { background: linear-gradient(135deg, #0a0a0a 0%, #1a1a2e 50%, #16213e 100%); color: #00ffff; padding: 2rem; min-height: 100vh; font-family: 'Rajdhani', sans-serif; position: relative; overflow: hidden; } .budget-container::before { content: ''; position: absolute; top: 0; left: 0; right: 0; bottom: 0; background: radial-gradient(circle at 20% 20%, rgba(0, 255, 255, 0.1) 0%, transparent 30%), radial-gradient(circle at 80% 80%, rgba(255, 0, 255, 0.1) 0%, transparent 30%), radial-gradient(circle at 40% 60%, rgba(0, 255, 0, 0.05) 0%, transparent 40%); pointer-events: none; } .header { text-align: center; margin-bottom: 3rem; position: relative; z-index: 2; } .main-title { font-family: 'Orbitron', monospace; font-size: clamp(2rem, 5vw, 3.5rem); font-weight: 900; background: linear-gradient(45deg, #00ffff, #ff00ff, #00ff00); -webkit-background-clip: text; -webkit-text-fill-color: transparent; background-clip: text; text-transform: uppercase; letter-spacing: 0.1em; margin-bottom: 0.5rem; animation: glow 2s ease-in-out infinite alternate; } @keyframes glow { from { filter: drop-shadow(0 0 10px #00ffff); } to { filter: drop-shadow(0 0 20px #ff00ff); } } .subtitle { font-size: 1.2rem; color: #888; font-weight: 300; text-transform: uppercase; letter-spacing: 0.15em; } .layers-grid { display: grid; gap: 2rem; max-width: 1200px; margin: 0 auto; position: relative; z-index: 2; } .layer-card { background: rgba(0, 20, 40, 0.8); border: 1px solid rgba(0, 255, 255, 0.3); border-radius: 12px; padding: 2rem; position: relative; overflow: hidden; transition: all 0.3s ease; backdrop-filter: blur(10px); } .layer-card::before { content: ''; position: absolute; top: 0; left: -100%; width: 100%; height: 100%; background: linear-gradient(90deg, transparent, rgba(0, 255, 255, 0.1), transparent); transition: left 0.5s ease; } .layer-card:hover::before { left: 100%; } .layer-card:hover { transform: translateY(-5px); border-color: #00ffff; box-shadow: 0 10px 30px rgba(0, 255, 255, 0.2); } .layer-header { display: flex; justify-content: space-between; align-items: center; margin-bottom: 1.5rem; flex-wrap: wrap; gap: 1rem; } .layer-title { font-family: 'Orbitron', monospace; font-size: 1.3rem; font-weight: 700; color: #00ffff; text-transform: uppercase; letter-spacing: 0.05em; } .layer-amount { font-family: 'Orbitron', monospace; font-size: 1.8rem; font-weight: 900; color: #00ff00; text-shadow: 0 0 10px rgba(0, 255, 0, 0.5); } .layer-purpose { font-size: 1.1rem; color: #ccc; margin-bottom: 1rem; line-height: 1.4; } .layer-technologies { display: flex; flex-wrap: wrap; gap: 0.5rem; margin-bottom: 1rem; } .tech-tag { background: rgba(255, 0, 255, 0.2); color: #ff00ff; padding: 0.3rem 0.8rem; border-radius: 20px; font-size: 0.9rem; border: 1px solid rgba(255, 0, 255, 0.3); text-transform: uppercase; letter-spacing: 0.05em; font-weight: 600; } .layer-insight { font-style: italic; color: #00ffff; font-size: 1rem; padding: 1rem; background: rgba(0, 255, 255, 0.1); border-left: 3px solid #00ffff; border-radius: 0 8px 8px 0; } .summary-card { background: rgba(20, 0, 40, 0.9); border: 2px solid rgba(255, 0, 255, 0.5); border-radius: 16px; padding: 2rem; margin-top: 3rem; text-align: center; position: relative; overflow: hidden; } .summary-card::before { content: ''; position: absolute; top: -50%; left: -50%; width: 200%; height: 200%; background: conic-gradient(from 0deg, transparent, rgba(255, 0, 255, 0.1), transparent); animation: rotate 10s linear infinite; } @keyframes rotate { to { transform: rotate(360deg); } } .summary-content { position: relative; z-index: 1; } .summary-amount { font-family: 'Orbitron', monospace; font-size: 2.5rem; font-weight: 900; color: #ff00ff; text-shadow: 0 0 20px rgba(255, 0, 255, 0.5); margin-bottom: 1rem; } .summary-text { font-size: 1.1rem; color: #ccc; line-height: 1.6; } .data-source { text-align: center; margin-top: 2rem; font-size: 0.9rem; color: #666; font-style: italic; } /* Mobile responsiveness */ @media (max-width: 768px) { .budget-container { padding: 1rem; } .layer-card { padding: 1.5rem; } .layer-header { flex-direction: column; align-items: flex-start; } .layer-amount { font-size: 1.5rem; } .summary-amount { font-size: 2rem; } .tech-tag { font-size: 0.8rem; padding: 0.25rem 0.6rem; } } @media (max-width: 480px) { .layer-card { padding: 1rem; } .layer-title { font-size: 1.1rem; } .layer-amount { font-size: 1.3rem; } .summary-card { padding: 1.5rem; } }
Budget Anatomy
Three Layers • FY 2026 Request
6.1–6.3 Basic & Applied Research
$2.27B
Quantum sensing, neuromorphic chips, machine-learning theory
Quantum Sensing Neuromorphic Chips ML Theory
Signals a maturing R&D bench feeding the pipeline.
6.4–6.5 Advanced Tech Development
$11.99B
CJADC2 software, open-architecture C5ISR, Software Pilots
CJADC2 Open-Architecture Software Pilots
Heavy spend on digital plumbing, not hardware.
6.6–6.7 Systems Demo & Ops
$39.68B
Hypersonic Attack Cruise Missile (HACM), Resilient MW/MT satellites
HACM Resilient Satellites MW/MT
Prototypes are moving into fieldable increments.
$125B
The remaining budget covers legacy upgrades, military construction, and classified programs, many of which embed AI or quantum modules that do not show up as discrete line items.
Source: CRS, 2025
Case Study Analysis: Major Pentagon Contracts in 2025
Palantir's Project Maven: The $1.3 Billion Expansion
Palantir Technologies' Maven Smart System represents perhaps the most significant algorithmic warfare contract awarded in 2025. The expansion of this agreement from $480 million to nearly $1.3 billion through 2029 demonstrates the Pentagon's commitment to AI-powered battlefield intelligence systems. (Beinart, 2024),(Freedberg Jr., 2024)
This contract expansion reflects several critical strategic considerations that illuminate the broader direction of American defense policy.
Project Maven, officially designated as the Algorithmic Warfare Cross-Functional Team, represents the Pentagon's most ambitious attempt to integrate artificial intelligence into military operations.
The system's core functionality involves analyzing vast quantities of data from satellites, drones, and ground sensors to identify potential threats and provide actionable intelligence to military commanders. The Maven Smart System's expansion to nearly $1.3 billion reflects not merely the system's success, but the Pentagon's recognition that algorithmic warfare requires sustained, long-term investment in AI infrastructure. (Freedberg Jr., 2024)
The significance of Palantir's Maven contract extends beyond its dollar value. The system currently serves over 20,000 military personnel across 35 units, with adoption rates exceeding initial forecasts. This widespread deployment indicates that
Project Maven has successfully transitioned from experimental technology to operational capability, marking a crucial milestone in the development of algorithmic warfare doctrine. The system's ability to process and analyze data at machine speed provides commanders with previously impossible situational awareness, enabling decision-making cycles that operate far faster than traditional human-centered processes. (Hawkins, 2023)
The contract's five-year duration through 2029 provides stability for long-term technological development while allowing for iterative improvements based on operational feedback.
This approach reflects the Pentagon's understanding that algorithmic warfare systems require continuous refinement and adaptation to remain effective against evolving threats.
The Maven system's integration with the broader Combined Joint All-Domain Command and Control (CJADC2) architecture positions it as a central component of future military operations.
The Combined Joint All-Domain Command and Control (CJADC2) initiative serves as the digital nervous system enabling algorithmic warfare at scale.
It aims to unify air, land, sea, space, and cyber domains through machine-speed decision cycles, supported by platforms such as Project Maven. Palantir’s role in CJADC2 demonstrates how AI-driven ISR and targeting are being fused with next-gen operational frameworks.
Maven Contract Analysis - Cyberpunk Edition @import url('https://fonts.googleapis.com/css2?family=Orbitron:wght@400;700;900&family=Rajdhani:wght@300;400;600&display=swap'); * { margin: 0; padding: 0; box-sizing: border-box; } .maven-container { background: linear-gradient(135deg, #0a0a0a 0%, #1a1a2e 50%, #16213e 100%); color: #00ffff; padding: 2rem; min-height: 100vh; font-family: 'Rajdhani', sans-serif; position: relative; overflow: hidden; } .maven-container::before { content: ''; position: absolute; top: 0; left: 0; right: 0; bottom: 0; background: radial-gradient(circle at 15% 25%, rgba(0, 255, 255, 0.1) 0%, transparent 35%), radial-gradient(circle at 85% 75%, rgba(255, 0, 255, 0.1) 0%, transparent 35%), radial-gradient(circle at 50% 50%, rgba(0, 255, 0, 0.05) 0%, transparent 50%); pointer-events: none; } .header { text-align: center; margin-bottom: 3rem; position: relative; z-index: 2; } .main-title { font-family: 'Orbitron', monospace; font-size: clamp(1.8rem, 4vw, 3rem); font-weight: 900; background: linear-gradient(45deg, #00ffff, #ff00ff, #00ff00); -webkit-background-clip: text; -webkit-text-fill-color: transparent; background-clip: text; text-transform: uppercase; letter-spacing: 0.05em; margin-bottom: 0.5rem; animation: glow 2s ease-in-out infinite alternate; line-height: 1.2; } @keyframes glow { from { filter: drop-shadow(0 0 10px #00ffff); } to { filter: drop-shadow(0 0 20px #ff00ff); } } .subtitle { font-size: 1.2rem; color: #888; font-weight: 300; text-transform: uppercase; letter-spacing: 0.15em; margin-bottom: 0.5rem; } .evidence-badge { display: inline-block; background: rgba(0, 255, 0, 0.2); color: #00ff00; padding: 0.5rem 1rem; border-radius: 25px; font-size: 0.9rem; border: 1px solid rgba(0, 255, 0, 0.4); text-transform: uppercase; letter-spacing: 0.05em; font-weight: 600; margin-top: 1rem; } .drivers-grid { display: grid; gap: 2rem; max-width: 1200px; margin: 0 auto; position: relative; z-index: 2; } .driver-card { background: rgba(0, 20, 40, 0.8); border: 1px solid rgba(0, 255, 255, 0.3); border-radius: 16px; padding: 2rem; position: relative; overflow: hidden; transition: all 0.3s ease; backdrop-filter: blur(10px); } .driver-card::before { content: ''; position: absolute; top: 0; left: -100%; width: 100%; height: 100%; background: linear-gradient(90deg, transparent, rgba(0, 255, 255, 0.1), transparent); transition: left 0.5s ease; } .driver-card:hover::before { left: 100%; } .driver-card:hover { transform: translateY(-5px); border-color: #00ffff; box-shadow: 0 15px 40px rgba(0, 255, 255, 0.2); } .driver-header { display: flex; align-items: center; gap: 1rem; margin-bottom: 1.5rem; } .driver-number { font-family: 'Orbitron', monospace; font-size: 2rem; font-weight: 900; color: #ff00ff; background: rgba(255, 0, 255, 0.2); width: 3rem; height: 3rem; border-radius: 50%; display: flex; align-items: center; justify-content: center; border: 2px solid rgba(255, 0, 255, 0.5); flex-shrink: 0; } .driver-title { font-family: 'Orbitron', monospace; font-size: 1.4rem; font-weight: 700; color: #00ffff; text-transform: uppercase; letter-spacing: 0.05em; line-height: 1.3; } .evidence-section { background: rgba(0, 255, 0, 0.05); border-left: 4px solid #00ff00; padding: 1.5rem; border-radius: 0 12px 12px 0; margin-bottom: 1.5rem; } .evidence-label { font-family: 'Orbitron', monospace; font-size: 0.9rem; color: #00ff00; text-transform: uppercase; letter-spacing: 0.1em; margin-bottom: 1rem; font-weight: 600; } .evidence-text { font-size: 1.1rem; color: #ccc; line-height: 1.5; } .highlight-stats { display: flex; flex-wrap: wrap; gap: 1rem; margin: 1rem 0; } .stat-item { background: rgba(255, 0, 255, 0.1); color: #ff00ff; padding: 0.5rem 1rem; border-radius: 8px; font-family: 'Orbitron', monospace; font-weight: 700; font-size: 0.9rem; border: 1px solid rgba(255, 0, 255, 0.3); } .mission-examples { background: rgba(255, 0, 255, 0.05); border-left: 4px solid #ff00ff; padding: 1.5rem; border-radius: 0 12px 12px 0; margin-top: 1rem; } .mission-examples h4 { font-family: 'Orbitron', monospace; color: #ff00ff; margin-bottom: 1rem; font-size: 1.1rem; text-transform: uppercase; letter-spacing: 0.05em; } .mission-item { margin-bottom: 1rem; padding-left: 1rem; border-left: 2px solid rgba(255, 0, 255, 0.3); } .mission-name { font-weight: 600; color: #ff00ff; font-size: 1rem; margin-bottom: 0.5rem; } .mission-desc { color: #ccc; font-size: 0.95rem; line-height: 1.4; } .contract-highlight { background: rgba(20, 0, 40, 0.9); border: 2px solid rgba(255, 0, 255, 0.5); border-radius: 20px; padding: 2rem; margin-top: 3rem; text-align: center; position: relative; overflow: hidden; } .contract-highlight::before { content: ''; position: absolute; top: -50%; left: -50%; width: 200%; height: 200%; background: conic-gradient(from 0deg, transparent, rgba(255, 0, 255, 0.1), transparent); animation: rotate 12s linear infinite; } @keyframes rotate { to { transform: rotate(360deg); } } .contract-content { position: relative; z-index: 1; } .contract-amount { font-family: 'Orbitron', monospace; font-size: 2.5rem; font-weight: 900; color: #ff00ff; text-shadow: 0 0 20px rgba(255, 0, 255, 0.5); margin-bottom: 1rem; } .contract-text { font-size: 1.1rem; color: #ccc; line-height: 1.6; } .citations { text-align: center; margin-top: 2rem; padding: 1rem; background: rgba(0, 0, 0, 0.3); border-radius: 8px; font-size: 0.9rem; color: #666; font-style: italic; line-height: 1.4; } /* Mobile responsiveness */ @media (max-width: 768px) { .maven-container { padding: 1rem; } .driver-card { padding: 1.5rem; } .driver-header { flex-direction: column; align-items: flex-start; text-align: left; } .driver-number { width: 2.5rem; height: 2.5rem; font-size: 1.5rem; } .driver-title { font-size: 1.2rem; } .contract-amount { font-size: 2rem; } .highlight-stats { flex-direction: column; } .stat-item { text-align: center; } } @media (max-width: 480px) { .driver-card { padding: 1rem; } .evidence-section, .mission-examples { padding: 1rem; } .contract-highlight { padding: 1.5rem; } .driver-title { font-size: 1.1rem; } }
Pentagon Super-Sized Maven Contract
Strategic Intelligence Analysis
3 Evidence-Based Drivers
1
Field-Proven ISR & Targeting Performance
5-Year Operational Evidence
Maven Smart System has repeatedly cut "find-fix-finish" timelines from hours to minutes, letting small teams track up to 1,000 targets per hour and shrinking the analyst workload across theaters.
1,000 targets/hour
20,000+ personnel
35 units
Its object-recognition pipeline—validated in SOF missions and CENTCOM drone operations—now supports 20,000+ personnel in 35 units.
2
Foundation for CJADC2 Cross-Domain Command
5-Year Operational Evidence
DoD selected Maven as the data-fusion backbone for Combined Joint All-Domain Command & Control (CJADC2). Beginning June 2024 it was rolled out to five combatant commands, scaling "hundreds of users" to "thousands worldwide."
5 Combatant Commands
Thousands of Users
June 2024 Rollout
Its containerized micro-services plug directly into Space Force missile-warning feeds, Army TITAN ground stations, and Navy Project Overmatch networks—precisely the integrative glue CDAO needs for machine-speed decisions.
3
Explosive Operator Demand & Predictive-Analytics Success
5-Year Operational Evidence
Battlefield commanders have pushed for wider access after in-the-field wins:
Mission Success Stories
• Raven Sentry - Afghanistan (2019-20)
Used Maven-trained AI to forecast insurgent attacks, shaping force-protection posture.
• SOF Operations - Iraq/Syria
Leveraged Maven video analytics to prosecute high-value targets faster than legacy PED cells.
• Rapid Uptake Impact
Drove CDAO to lift the ceiling by +$795M in May 2025, explicitly "to meet a significant influx in demand" through 2029.
+$795M
Contract ceiling increase in May 2025 to meet significant influx in demand through 2029, reflecting the proven operational value and growing strategic importance of Maven capabilities.
Sources: DoD, 2025; Freedberg Jr., 2025; Albon, 2024; GAO, 2024; U.S. Central Command, 2021
While Maven showcases battlefield-proven ISR autonomy, OpenAI’s $200 million initiative targets the cognitive backend, scaling generative intelligence across enterprise workflows and command planning layers.
OpenAI's Government Initiative: Democratizing Military AI
OpenAI's $200 million contract with the Pentagon's Chief Digital and AI Officer represents a different but equally significant approach to algorithmic warfare development.
Unlike Palantir's specialized military-focused platform, OpenAI's initiative aims to bring cutting-edge large language model capabilities to government operations through what the company terms "OpenAI for Government." (Freedberg Jr., 2025)
The contract's structure reveals important strategic considerations. With nearly $2 million obligated immediately and the full $200 million committed through July 2026, this agreement demonstrates unusual confidence in OpenAI's capabilities.
Most Pentagon contracts spread funding over multiple years with option-based payments, but this commitment suggests that DoD views OpenAI's technology as sufficiently mature and essential to warrant a full funding commitment.
The scope of OpenAI's government initiative extends beyond traditional military applications to encompass what officials describe as "prototype frontier AI" for both administrative functions and operational planning.
This dual-use approach reflects the Pentagon's recognition that algorithmic warfare requires not only battlefield AI systems but also intelligent automation of the administrative and logistical systems that support military operations.
The development of "agentic workflows", semi-autonomous AI agents capable of completing complex tasks, represents a significant advancement in military AI capabilities.
These systems promise to automate routine administrative tasks, freeing human personnel for higher-level strategic thinking while ensuring consistent, error-free execution of standard procedures. The potential applications range from automated acquisition document preparation to real-time translation of presidential directives into actionable military orders.
In December 2024, following an 18-month evaluation, the Pentagon's Task Force Lima formally sanctioned the use of generative AI within limited mission scopes.
The task force's endorsement, while accompanied by technical guardrails, reflects a new level of institutional trust in large language models as operational assets. (Freedberg Jr., 2025)
OpenAI DoD Budget Analysis - Cyberpunk Edition @import url('https://fonts.googleapis.com/css2?family=Orbitron:wght@400;700;900&family=Rajdhani:wght@300;400;600&display=swap'); * { margin: 0; padding: 0; box-sizing: border-box; } .openai-container { background: linear-gradient(135deg, #0a0a0a 0%, #1a1a2e 50%, #16213e 100%); color: #00ffff; padding: 2rem; min-height: 100vh; font-family: 'Rajdhani', sans-serif; position: relative; overflow: hidden; } .openai-container::before { content: ''; position: absolute; top: 0; left: 0; right: 0; bottom: 0; background: radial-gradient(circle at 25% 30%, rgba(0, 255, 255, 0.1) 0%, transparent 40%), radial-gradient(circle at 75% 70%, rgba(255, 0, 255, 0.1) 0%, transparent 40%), radial-gradient(circle at 45% 40%, rgba(0, 255, 0, 0.05) 0%, transparent 50%); pointer-events: none; } .header { text-align: center; margin-bottom: 3rem; position: relative; z-index: 2; } .main-title { font-family: 'Orbitron', monospace; font-size: clamp(1.8rem, 4vw, 3rem); font-weight: 900; background: linear-gradient(45deg, #00ffff, #ff00ff, #00ff00); -webkit-background-clip: text; -webkit-text-fill-color: transparent; background-clip: text; text-transform: uppercase; letter-spacing: 0.05em; margin-bottom: 0.5rem; animation: glow 2s ease-in-out infinite alternate; line-height: 1.2; } @keyframes glow { from { filter: drop-shadow(0 0 10px #00ffff); } to { filter: drop-shadow(0 0 20px #ff00ff); } } .subtitle { font-size: 1.2rem; color: #888; font-weight: 300; text-transform: uppercase; letter-spacing: 0.15em; margin-bottom: 0.5rem; } .contract-badge { display: inline-block; background: rgba(255, 0, 255, 0.3); color: #ff00ff; padding: 0.5rem 1rem; border-radius: 25px; font-size: 1rem; border: 2px solid rgba(255, 0, 255, 0.5); text-transform: uppercase; letter-spacing: 0.05em; font-weight: 700; margin-top: 1rem; font-family: 'Orbitron', monospace; animation: pulse 2s ease-in-out infinite; } @keyframes pulse { 0%, 100% { transform: scale(1); } 50% { transform: scale(1.05); } } .drivers-grid { display: grid; gap: 2rem; max-width: 1200px; margin: 0 auto; position: relative; z-index: 2; } .driver-card { background: rgba(0, 20, 40, 0.8); border: 1px solid rgba(0, 255, 255, 0.3); border-radius: 16px; padding: 2rem; position: relative; overflow: hidden; transition: all 0.3s ease; backdrop-filter: blur(10px); } .driver-card::before { content: ''; position: absolute; top: 0; left: -100%; width: 100%; height: 100%; background: linear-gradient(90deg, transparent, rgba(0, 255, 255, 0.1), transparent); transition: left 0.5s ease; } .driver-card:hover::before { left: 100%; } .driver-card:hover { transform: translateY(-5px); border-color: #00ffff; box-shadow: 0 15px 40px rgba(0, 255, 255, 0.2); } .driver-header { display: flex; align-items: center; gap: 1rem; margin-bottom: 1.5rem; } .driver-number { font-family: 'Orbitron', monospace; font-size: 2rem; font-weight: 900; color: #ff00ff; background: rgba(255, 0, 255, 0.2); width: 3rem; height: 3rem; border-radius: 50%; display: flex; align-items: center; justify-content: center; border: 2px solid rgba(255, 0, 255, 0.5); flex-shrink: 0; } .driver-title { font-family: 'Orbitron', monospace; font-size: 1.4rem; font-weight: 700; color: #00ffff; text-transform: uppercase; letter-spacing: 0.05em; line-height: 1.3; } .evidence-section { background: rgba(0, 255, 0, 0.05); border-left: 4px solid #00ff00; padding: 1.5rem; border-radius: 0 12px 12px 0; margin-bottom: 1rem; } .evidence-label { font-family: 'Orbitron', monospace; font-size: 0.9rem; color: #00ff00; text-transform: uppercase; letter-spacing: 0.1em; margin-bottom: 1rem; font-weight: 600; } .evidence-text { font-size: 1.1rem; color: #ccc; line-height: 1.5; } .highlight-metrics { display: flex; flex-wrap: wrap; gap: 1rem; margin: 1rem 0; } .metric-item { background: rgba(0, 255, 0, 0.15); color: #00ff00; padding: 0.5rem 1rem; border-radius: 8px; font-family: 'Orbitron', monospace; font-weight: 700; font-size: 0.9rem; border: 1px solid rgba(0, 255, 0, 0.4); text-transform: uppercase; letter-spacing: 0.05em; } .pilot-examples { background: rgba(0, 255, 255, 0.05); border-left: 4px solid #00ffff; padding: 1.5rem; border-radius: 0 12px 12px 0; margin-top: 1rem; } .pilot-examples h4 { font-family: 'Orbitron', monospace; color: #00ffff; margin-bottom: 1rem; font-size: 1.1rem; text-transform: uppercase; letter-spacing: 0.05em; } .pilot-list { display: flex; flex-wrap: wrap; gap: 0.5rem; margin-top: 1rem; } .pilot-tag { background: rgba(0, 255, 255, 0.2); color: #00ffff; padding: 0.3rem 0.8rem; border-radius: 20px; font-size: 0.85rem; border: 1px solid rgba(0, 255, 255, 0.3); font-weight: 600; } .timeline-highlight { background: rgba(255, 0, 255, 0.1); border: 1px solid rgba(255, 0, 255, 0.3); padding: 1rem; border-radius: 8px; margin: 1rem 0; } .timeline-text { color: #ff00ff; font-weight: 600; text-align: center; font-size: 1rem; } .trust-badge { display: inline-block; background: linear-gradient(45deg, rgba(0, 255, 0, 0.2), rgba(0, 255, 255, 0.2)); color: #00ffff; padding: 0.5rem 1rem; border-radius: 25px; font-size: 0.9rem; border: 1px solid rgba(0, 255, 255, 0.4); text-transform: uppercase; letter-spacing: 0.05em; font-weight: 600; margin: 0.5rem 0; } .bottom-line { background: rgba(20, 0, 40, 0.9); border: 2px solid rgba(255, 0, 255, 0.5); border-radius: 20px; padding: 2rem; margin-top: 3rem; position: relative; overflow: hidden; } .bottom-line::before { content: ''; position: absolute; top: -50%; left: -50%; width: 200%; height: 200%; background: conic-gradient(from 0deg, transparent, rgba(255, 0, 255, 0.1), transparent); animation: rotate 15s linear infinite; } @keyframes rotate { to { transform: rotate(360deg); } } .bottom-line-content { position: relative; z-index: 1; } .bottom-line-header { font-family: 'Orbitron', monospace; font-size: 1.5rem; font-weight: 700; color: #ff00ff; text-transform: uppercase; letter-spacing: 0.05em; margin-bottom: 1rem; text-align: center; } .bottom-line-text { font-size: 1.1rem; color: #ccc; line-height: 1.6; text-align: center; } .nexus-keywords { display: flex; flex-wrap: wrap; justify-content: center; gap: 0.5rem; margin: 1.5rem 0; } .nexus-keyword { background: rgba(255, 0, 255, 0.2); color: #ff00ff; padding: 0.3rem 0.8rem; border-radius: 20px; font-size: 0.9rem; border: 1px solid rgba(255, 0, 255, 0.3); font-weight: 600; text-transform: uppercase; letter-spacing: 0.05em; } .citations { text-align: center; margin-top: 2rem; padding: 1rem; background: rgba(0, 0, 0, 0.3); border-radius: 8px; font-size: 0.9rem; color: #666; font-style: italic; line-height: 1.4; } /* Mobile responsiveness */ @media (max-width: 768px) { .openai-container { padding: 1rem; } .driver-card { padding: 1.5rem; } .driver-header { flex-direction: column; align-items: flex-start; text-align: left; } .driver-number { width: 2.5rem; height: 2.5rem; font-size: 1.5rem; } .driver-title { font-size: 1.2rem; } .highlight-metrics { flex-direction: column; } .metric-item { text-align: center; } .nexus-keywords { flex-direction: column; align-items: center; } } @media (max-width: 480px) { .driver-card { padding: 1rem; } .evidence-section, .pilot-examples { padding: 1rem; } .bottom-line { padding: 1.5rem; } .driver-title { font-size: 1.1rem; } }
OpenAI Secured $200M
DoD's AI Budget Drivers for FY-26
$200M Contract
1
Enterprise-wide Efficiency Mandate
5-Year Evidence Thread
OpenAI for Government is DoD's fast track to slash paperwork and service backlogs. The AI Rapid Capabilities Cell has already scoped 15 gen-AI pilots.
15 Gen-AI Pilots
≥70% Cycle-Time Cut
Sandbox Tested
AI Pilot Applications
From auto-drafting acquisition documents and health-care forms to cyber-defence log triage. CDAO officials say LLM agents cut some admin workflows by ≥70% cycle-time in sandbox tests.
Acquisition Docs Health-Care Forms Cyber-Defence Triage Admin Workflows
2
War-Fighting Decision Velocity
5-Year Evidence Thread
The $200M OTA earmarks "frontier AI" prototypes for command-and-control, targeting, and real-time mission planning—capabilities that pair with CJADC2 and TITAN nodes.
$200M OTA
≈$2M Day-One
July 2026 Ceiling
Early micro-pilots hit readiness goals THREE QUARTERS ahead of schedule
Frontier AI Capabilities
Command & Control Targeting Systems Mission Planning CJADC2 Integration TITAN Nodes
3
Institutional Trust After Task-Force Vetting
5-Year Evidence Thread
Following an 18-month evaluation, Task Force Lima formally cleared generative AI for limited missions, then morphed into the AI RCC.
18-Month Evaluation
Task Force Lima
AI RCC Formation
✓ Formal Security Clearance
This endorsement—plus new policy guardrails—overcame OpenAI's prior military-use caveats and unlocked unrestricted funding. DoD leaders cite Lima's safety findings as the "go" for scaling LLMs department-wide in FY-26–27 POM cycles.
Strategic Nexus
Cost-Savings Machine-Speed Planning Codified Trust
OpenAI's initiative sits at the nexus of cost-savings, machine-speed operational planning, and newly codified trust, making it a linchpin of the FY-26 AI budget surge and a bellwether for DoD's next-decade software strategy.
Sources: Department of Defense, 2025; Freedberg Jr., 2025; Edwards, 2025; Harper, 2024; Chief Digital and AI Office [CDAO], 2024
If OpenAI represents the institutional AI layer, Ask Sage completes the triad by embedding secure, distributed LLMs directly within Combatant Command operations, extending AI capabilities to the edge of the mission network.
Ask Sage: Distributed AI Command and Control
The $10 million contract awarded to Ask Sage for integrating large language models across all US Combatant Commands represents a third model for algorithmic warfare implementation.
This initiative focuses on creating distributed AI capabilities that can operate across both classified and unclassified networks, addressing one of the most significant challenges in military AI deployment.
The Ask Sage contract's emphasis on cross-domain integration, spanning operational planning, logistics, command and control, intelligence, cybersecurity, and weapons development, demonstrates the Pentagon's commitment to comprehensive AI integration rather than isolated system development.
This approach recognizes that algorithmic warfare's effectiveness depends on seamless information sharing and coordinated response across all military functions. (Freedberg Jr., 2024
The system's deployment through the Army's LLM workspace provides a standardized platform for AI integration while maintaining the security protocols necessary for classified operations.
This infrastructure approach suggests that the Pentagon is building the foundational architecture for widespread AI deployment rather than implementing isolated solutions.
Operational Drivers Behind Ask Sage’s Pentagon Roll-out
# Budget-Priority Driver Recent Operational Evidence (2019–25) In-Text Citations 1 Documented User Surge & Productivity Payoff
Army Enterprise LLM Workspace rocketed from 0 → 19 000 users in 45 days after its May 2025 launch.
Platform re-classified 300 000 personnel descriptions in one week, saving ≈ 50 000 analyst-hours.
Rapid uptake won a one-year, $10 M CDAO expansion so every CCMD, the Joint Staff, and OSD get access.
(Freedberg Jr., 2025; U.S. Army PA, 2025) 2 Highest Security & Compliance Credentials
First Gen-AI SaaS in DoD with FedRAMP High, IL5, IL6 & Top-Secret ATOs.
Vendor-agnostic multi-LLM stack cross-checks outputs, slashing hallucination risk.
Ask Sage cut CCMD ATO-package prep time by 95 %—now baked into FY-26 pilot KPIs.
(Ask Sage, 2025; Brooks, 2025) 3 Cross-Domain Mission Alignment & Demand Signal
Gen-AI workspace already underpins Army; CCMD planners now use it to accelerate ops planning, C2, logistics, intel & cyber tasks.
Contract scope ties explicitly to CJADC2 data-fusion goals—Ask Sage becomes the LLM front-end across 11 CCMDs and Pentagon hubs.
DoD press & industry trackers frame the deal as the linchpin for scaling AI from pilot to enterprise.
(Freedberg Jr., 2025; Ask Sage, 2025)
/* ==== COLOR SYSTEM & TYPOGRAPHY ==== */ :root{ --primary:#00ffff; /* cyan text */ --accent:#ff0080; /* magenta pop */ --bg-start:#0a0a0a; --bg-end:#1a1a2e; } .pentagon-drivers{ background:linear-gradient(135deg,var(--bg-start),var(--bg-end)); color:var(--primary); font-family:'Rajdhani',sans-serif; padding:2rem; border-radius:12px; } /* ==== TITLE ==== */ .title-header{ font-size:2rem; font-family:'Orbitron',sans-serif; text-align:center; margin-bottom:1.5rem; background:linear-gradient(to right,var(--primary),var(--accent)); -webkit-background-clip:text; -webkit-text-fill-color:transparent; text-transform:uppercase; font-weight:900; } .glow{ text-shadow:0 0 8px var(--primary); } /* ==== TABLE WRAPPER FOR SCROLL ==== */ .table-wrapper{ overflow-x:auto; } /* ==== TABLE CORE STYLES ==== */ table.cyberpunk-table{ width:100%; border-collapse:collapse; background:rgba(0,20,40,0.8); border:1px solid rgba(0,255,255,0.3); } .cyberpunk-table th, .cyberpunk-table td{ border:1px solid rgba(0,255,255,0.2); padding:1rem; text-align:left; vertical-align:top; } .cyberpunk-table th{ background:rgba(0,255,255,0.15); letter-spacing:0.1em; font-size:0.9rem; color:var(--primary); text-transform:uppercase; } .cyberpunk-table tbody tr:nth-child(odd){ background:rgba(0,255,255,0.05); /* light striping */ } /* ==== BULLET LIST INSIDE CELLS ==== */ .cyberpunk-table td ul{ margin:0; padding-left:1rem; list-style:none; } .cyberpunk-table td ul li{ margin-bottom:0.5rem; } .cyberpunk-table td ul li::before{ content:"◆"; color:var(--accent); margin-right:0.4rem; } /* ==== RESPONSIVE TWEAKS ==== */ @media (max-width:600px){ .title-header{ font-size:1.5rem; } .cyberpunk-table th, .cyberpunk-table td{ padding:0.75rem; font-size:0.85rem; } }
Quantum Computing: The Next Frontier
Quantum Applications in Military Operations
The Pentagon's investment in quantum computing represents a longer-term strategic initiative that promises to revolutionize military capabilities across multiple domains.
While quantum-related programs are often fragmented across service branches and embedded within classified initiatives, their presence throughout the RDT&E budget indicates growing recognition of quantum technology's transformative potential.
The "Quantum Application" line item, despite its undisclosed funding level, represents cross-service coordination in quantum technology development. This approach reflects the Pentagon's understanding that quantum computing's applications in military operations require coordinated development across air, land, sea, space, and cyber domains.
The technology's potential applications span from quantum-enhanced cryptography to quantum sensors that could revolutionize navigation and threat detection. (RAND Corporation, 2023)
Quantum sensing technology offers particular promise for military applications. The Assured Positioning, Navigation, and Timing program reflects interest in quantum-based inertial sensors that would provide GPS-independent navigation capabilities.
These systems would be immune to signal jamming or spoofing, providing crucial capabilities in contested environments where traditional satellite-based navigation might be compromised.
Post-quantum cryptography represents another critical area of quantum-related investment. As quantum computers develop the capability to break current encryption standards, the Pentagon is investing in cryptographic systems that will remain secure against quantum attacks.
This investment protects not only current military communications but also ensures that sensitive information remains protected as quantum computing technology matures.
Integration with AI and Space Systems
The convergence of quantum computing with artificial intelligence and space-based systems represents perhaps the most significant long-term development in algorithmic warfare capabilities.
Quantum-enhanced AI systems promise computational capabilities that far exceed current limitations, potentially enabling real-time processing of vast amounts of battlefield data and complex optimization problems that are currently intractable.
The Space Force's $29 billion RDT&E budget includes significant investments in quantum-enabled satellite systems and space-based sensors. These systems will likely integrate quantum sensors with AI-guided data analysis to provide unprecedented situational awareness and threat detection capabilities.
“The minimum viable capability for CJADC2 is real and ready now: low-latency, extremely reliable. Our investments in data, AI and compute are empowering war-fighters today.” - Dr. Kathleen H. Hicks, 35th United States Deputy Secretary of Defense (2021 – 2025)
The convergence of these technologies in space-based platforms offers the potential for global surveillance and intelligence capabilities that could fundamentally alter the strategic balance. (Albon, 2023)
Space Force and Advanced Infrastructure
Resilient Space-Based Systems
The U.S. Space Force's substantial RDT&E allocation of over $29 billion reflects the Pentagon's recognition that space has become a critical domain for military operations.
The $4.3 billion allocated for prototyping programs and $12.5 billion for active systems development indicate a mature space-based military infrastructure that integrates advanced AI and quantum technologies.
The Resilient Missile Warning and Tracking architecture represents a prime example of algorithmic warfare implementation in space. This system, operating across low and medium Earth orbit, integrates multiple satellite platforms with AI-powered threat analysis to provide real-time missile detection and tracking capabilities.
The system's resilience comes not only from its distributed architecture but also from its ability to automatically adapt to changing threat environments using machine learning algorithms. (Albon, 2023)
The Evolved Strategic SATCOM program for hardened space-based communication demonstrates the Pentagon's commitment to ensuring secure, reliable communication channels that can support algorithmic warfare operations.
These systems must be capable of handling the massive data flows generated by AI-powered military systems while maintaining security against increasingly sophisticated cyber threats.
GPS III Follow-On and Next-Generation Navigation
The GPS III Follow-On program represents a crucial component of the Pentagon's algorithmic warfare infrastructure. Next-generation navigation systems must provide the precision and reliability required for autonomous military systems while remaining resilient against jamming and spoofing attacks.
The integration of quantum-enhanced timing and positioning capabilities promises to provide unprecedented accuracy and security for navigation-dependent military systems.
The convergence of advanced navigation systems with AI-powered autonomous platforms creates new possibilities for military operations. Autonomous drones, vehicles, and weapons systems require precise, reliable navigation to operate effectively in contested environments.
The GPS III Follow-On program's integration with quantum timing systems and AI-powered threat detection provides the foundation for these advanced autonomous capabilities. (Swayne, 2025)
Hypersonic Systems and Advanced Weapons
Hypersonic Attack Capabilities
The Pentagon's investment of over $3 billion in hypersonic platforms, including the Hypersonic Attack Cruise Missile (HACM), represents a critical component of algorithmic warfare doctrine.
These systems, operating at speeds above Mach 5, require AI-powered targeting and navigation systems to be effective. The integration of quantum-enhanced navigation with AI-driven targeting promises to provide unprecedented precision and speed for long-range strike capabilities. (Domingo, 2025)
The development of hypersonic weapons systems demonstrates the Pentagon's commitment to maintaining technological superiority in an increasingly competitive international environment. These systems' speed and maneuverability make them extremely difficult to intercept, but their effectiveness depends on advanced AI systems for targeting and navigation.
The integration of algorithmic warfare capabilities with hypersonic platforms represents a force multiplier that could provide decisive advantages in future conflicts.
The transition of hypersonic systems from prototypes to operational deployment indicates that these technologies are maturing rapidly. The Pentagon's sustained investment in hypersonic capabilities, combined with AI and quantum technologies, suggests that these systems will play a central role in future military operations.
While the Pentagon’s hypersonic investments are driven by technical advancement, they are also shaped by strategic necessity. China’s DF-ZF and Russia’s Avangard hypersonic glide vehicles underscore the need for U.S. superiority in maneuverable, high-velocity platforms.
These systems form a critical layer of deterrence in the evolving global power competition. (RAND Corporation, 2023)
Technology Convergence and Integration
Cross-Domain Operations
The FY2026 RDT&E budget demonstrates a clear shift from siloed technology development to integrated, cross-domain capabilities. Artificial intelligence is no longer treated as a separate program but is embedded throughout air, land, sea, cyber, and space operations.
This integration reflects the Pentagon's understanding that algorithmic warfare requires seamless coordination across all domains of military operations.
The integration of AI across multiple domains creates new possibilities for military operations while presenting significant challenges for coordination and control. The development of standardized AI architectures and communication protocols becomes crucial for ensuring that systems can share information and coordinate responses effectively.
The Pentagon's investment in cross-domain integration reflects recognition that future military effectiveness depends on the ability to operate as a unified, intelligent system rather than as separate, independent platforms.
Quantum technology's integration across multiple domains presents similar opportunities and challenges. Quantum sensors, quantum-enhanced communications, and quantum computing capabilities must be integrated into a coherent system that can support military operations across all domains.
The Pentagon's approach to quantum integration reflects lessons learned from AI development, emphasizing standardization and interoperability from the earliest stages of development.
Software and Digital Infrastructure
The Software and Digital Technology Pilot Programs' $1.06 billion budget reflects the Pentagon's recognition that algorithmic warfare requires robust, scalable software infrastructure. This investment supports the development of software development pipelines that can support rapid deployment and iterative improvement of AI systems.
The emphasis on software infrastructure indicates that the Pentagon understands that algorithmic warfare's effectiveness depends as much on software development capabilities as on individual AI systems.
The development of standardized software architectures and development processes becomes crucial for ensuring that AI systems can be rapidly deployed, updated, and maintained across the military.
The Pentagon's investment in software infrastructure reflects recognition that algorithmic warfare requires not only advanced AI capabilities but also the ability to rapidly adapt and improve these systems based on operational experience.
Defense-Tech Fusion and Industrial Realignment
The integration of firms like Palantir, OpenAI, Anduril, and Ask Sage into the Pentagon’s operational fabric reflects the rise of a new defense-tech industrial complex. These firms bring agile development cycles, dual-use adaptability, and advanced computational capability.
Unlike traditional contractors, their cloud-native architectures and rapid deployment pipelines represent the future of strategic procurement. (Anduril Industries, 2024), (Freedberg Jr., 2024)
Strategic Implications and Future Outlook
Technological Superiority and Military Advantage
The Pentagon's massive investment in algorithmic warfare capabilities reflects a strategic recognition that technological superiority will determine military outcomes in future conflicts.
The convergence of AI, quantum computing, and space-based systems promises to provide unprecedented capabilities for intelligence gathering, threat assessment, and operational planning. These capabilities offer the potential for decision-making cycles that operate far faster than human-centered processes, potentially providing decisive advantages in rapidly evolving conflict situations.
The emphasis on cross-domain integration reflects understanding that future conflicts will be multi-domain operations requiring coordinated responses across air, land, sea, space, and cyber domains.
The development of AI systems that can coordinate responses across these domains while adapting to changing conditions represents a fundamental shift in military capabilities. The Pentagon's investment pattern suggests confidence that these capabilities will provide sustainable competitive advantages.
The long-term nature of many contracts, particularly Palantir's five-year Maven agreement, indicates that the Pentagon views algorithmic warfare as a permanent shift rather than a temporary technological trend.
This sustained commitment provides the stability necessary for long-term technological development while ensuring that systems can be continuously improved based on operational experience. (Gill, 2023)
Challenges and Considerations
The implementation of algorithmic warfare capabilities presents significant challenges that the Pentagon must address to realize the full potential of these investments.
The integration of AI systems across multiple domains requires unprecedented coordination and standardization efforts. The development of secure, reliable communication systems that can support the massive data flows generated by AI-powered military systems represents a significant technical challenge.
The human factors associated with algorithmic warfare present equally significant challenges. Military personnel must be trained to work effectively with AI systems while maintaining the ability to make critical decisions when AI systems fail or provide incorrect information.
The Pentagon's investment in training and human-machine interface development reflects recognition that algorithmic warfare's success depends on effective human-AI collaboration.
Rules of Engagement and Algorithmic Accountability
As AI-enabled systems assume greater decision-making authority, the question of accountability becomes increasingly complex. Who bears responsibility when an AI misidentifies a threat or executes a flawed maneuver?
The Pentagon’s development of ethical frameworks, aligned with international humanitarian law, is essential to ensure that autonomous and semi-autonomous systems operate within justifiable rules of engagement. (ICRC & Geneva Academy, 2024)
The security implications of algorithmic warfare systems require careful consideration. AI-powered military systems present attractive targets for cyber attacks, and the consequences of compromised AI systems could be catastrophic. The Pentagon's investment in cybersecurity and system hardening reflects an understanding that algorithmic warfare capabilities must be protected against increasingly sophisticated threats.
As AI and quantum technologies underpin increasingly automated kill chains, new vulnerabilities emerge. Adversaries may seek to disrupt targeting logic, inject corrupted data, or exploit zero-day vulnerabilities in mission-critical code. Resilience in software-defined warfare requires hardened systems, red-teaming protocols, and real-time anomaly detection to ensure decision integrity.
Ghost Protocols and Quantum Signatures: Toward a Post-Human Battlespace
The Pentagon's FY2026 RDT&E budget represents a decisive shift toward algorithmic warfare doctrine, marking the transition from experimental AI systems to operational military capabilities.
The $179 billion investment, with over $2.2 billion directly allocated to AI and machine learning programs, demonstrates an unprecedented commitment to the technological transformation of military operations.
The major contracts awarded in 2025, including Palantir's $1.3 billion Maven expansion, OpenAI's $200 million government initiative, and Ask Sage's $10 million cross-command integration, collectively represent the emergence of a new paradigm in military technology.
The strategic implications of this investment pattern extend far beyond individual contracts or technologies. The Pentagon's approach to algorithmic warfare reflects an understanding that future military superiority depends on the ability to integrate AI, quantum computing, and space-based systems into coherent, cross-domain capabilities.
This integration represents a fundamental shift from platform-centric to information-centric military operations, where success depends on the ability to process, analyze, and act upon information faster and more accurately than potential adversaries.
Securing the Cognitive Edge
Ghost Protocols operate as machine-speed contingency playbooks that automatically reroute or mask command-and-control traffic whenever primary links are jammed or breached, thereby preserving algorithmic continuity in denied or degraded environments (ICRC & Geneva Academy, 2024).
Quantum Signatures are verifiable, tamper-proof data stamps created by quantum sensors and secured with post-quantum cryptography, enabling next-generation PNT kits to certify message origin and integrity at the photon level (RAND Corporation, 2023).
The convergence of quantum computing, artificial intelligence, and space-based systems promises to revolutionize military capabilities across all domains of operation. Quantum-enhanced sensors and communications, AI-powered autonomous systems, and space-based intelligence platforms collectively offer the potential for unprecedented situational awareness and response capabilities.
The Pentagon's investment in these converging technologies reflects strategic recognition that their integration will determine military outcomes in future conflicts.
The emphasis on cross-domain integration and standardization reflects lessons learned from earlier military technology development efforts.
Rather than developing isolated systems for specific functions, the Pentagon is creating interconnected networks of intelligent systems that can share information, coordinate responses, and adapt to changing conditions across all domains of military operations. This approach promises to maximize the effectiveness of individual technologies while creating emergent capabilities that exceed the sum of their parts.
The long-term nature of major contracts, particularly the five-year commitments to Palantir and OpenAI, indicates that the Pentagon views algorithmic warfare as a permanent transformation rather than a temporary technological trend.
This sustained commitment provides the stability necessary for complex technology development while ensuring that systems can be continuously improved based on operational experience. The Pentagon's willingness to commit substantial resources over extended periods demonstrates confidence in the strategic value of these capabilities.
The challenges associated with implementing algorithmic warfare capabilities are significant but not insurmountable. The integration of AI systems across multiple domains requires unprecedented coordination and standardization efforts, while the human factors associated with human-AI collaboration present complex training and interface design challenges.
The Pentagon's comprehensive approach to addressing these challenges through sustained investment in infrastructure, training, and security reflects an understanding that algorithmic warfare's success depends on more than technological capabilities alone.
Looking toward the future, the Pentagon's investment in algorithmic warfare capabilities positions the United States to maintain technological superiority in an increasingly competitive international environment. The convergence of AI, quantum computing, and space-based systems promises to provide decisive advantages in intelligence gathering, threat assessment, and operational planning.
The Pentagon's strategic approach to developing these capabilities through sustained investment, cross-domain integration, and public-private partnerships creates a foundation for continued technological leadership.
The transformation represented by the FY2026 RDT&E budget reflects broader changes like military operations and international security. As potential adversaries develop their advanced military technologies, the Pentagon's investment in algorithmic warfare capabilities becomes crucial for maintaining strategic stability and deterring potential conflicts.
The comprehensive nature of this investment, spanning basic research, advanced development, and operational deployment, ensures that the United States will possess the technological capabilities necessary to address emerging threats while maintaining the flexibility to adapt to changing strategic environments.
The Pentagon's approach to algorithmic warfare represents a model for technology development that could influence broader government and private sector approaches to emerging technologies. The emphasis on cross-domain integration, public-private partnerships, and sustained long-term investment demonstrates how complex technological challenges can be addressed through coordinated, strategic approaches. The success of this initiative will likely influence future government technology development efforts across multiple sectors.
In conclusion, the Pentagon's 2025 contracts and the broader FY2026 RDT&E budget represent a historic transformation in military technology and doctrine. The shift toward algorithmic warfare reflects an understanding that future conflicts will be determined by the ability to process information and make decisions faster and more accurately than potential adversaries.
The Pentagon’s trajectory mirrors allied developments. NATO, for instance, has recently adopted AI-enabled warfighting platforms and standardized data fusion architectures. This convergence across alliances signifies that algorithmic warfare is not only a U.S. priority but a collective strategic evolution within advanced militaries. (NATO, 2025)
The Pentagon's comprehensive investment in AI, quantum computing, and space-based systems, combined with sustained commitment to cross-domain integration and public-private partnerships, positions the United States to maintain technological superiority while adapting to emerging threats.
The success of this transformation will determine not only military outcomes but also the broader trajectory of technological development and international security in the coming decades.
Beyond kinetic dominance, algorithmic warfare signals a new paradigm in strategic deterrence: information supremacy. The ability to outthink, out-decide, and outmaneuver adversaries at machine speed transforms decision velocity into a tool of national power.
As synthetic cognition becomes weaponized, the cognitive domain emerges as the next strategic frontier.
Ready to Activate the Next Layer of Precision?
Ultra Unlimited isn’t just a service. It’s a systems upgrade for visionaries, operators, and creators building at the edge. Book a strategy call and unlock tailored solutions across symbolic design, AI storytelling, and Alpha-Grade Sales Systems.
References
Albon, C. (2023, August 21). Space Development Agency awards $1.5 billion for transport satellites. C4ISRNET. https://www.c4isrnet.com/battlefield-tech/space/2023/08/21/space-development-agency-awards-15-billion-for-transport-satellites/
Albon, C., & Demarest, C. (2023, December 06). TITAN targeting contract to be awarded soon, Army officials say. C4ISRNET. https://www.c4isrnet.com/battlefield-tech/it-networks/2023/12/06/titan-targeting-contract-to-be-awarded-soon-army-officials-say/
Albon, C. (2024, July 15). Maven goes global: AI imagery analysis now live in five combatant commands. C4ISRNET. https://www.c4isrnet.com/battlefield-tech/2024/07/15/maven-goes-global-ai-imagery-analysis-now-live-in-five-combatant-commands/
Allyn, B. (2025, May 03). How Palantir, the secretive tech company, is rising in the Trump era. NPR. https://www.npr.org/2025/05/01/nx-s1-5372776/palantir-tech-contracts-trump
Anduril Industries. (2024, March 03). Army Selects Anduril and Palantir to Deliver TITAN Deep Sensing Capability for Long Range Fires. Anduril. https://www.anduril.com/article/army-selects-anduril-and-palantir-to-deliver-titan/
Army Technology HADES. (2024, March 14). High Accuracy Detection and Exploitation System (HADES) Programme, USA. Army Technology. https://www.army-technology.com/projects/high-accuracy-detection-exploitation-system-hades/?cf-view
Ask Sage. (2025, June 18). Ask Sage partners with DoD CDAO and U.S. Army to provide unlimited access to generative AI across combatant commands, Joint Staff, and Office of the Secretary of Defense [Press release]. https://www.asksage.ai/press-releases/ask-sage-partners-with-dod-cdao-and-u-s-army-to-provide-unlimited-access-to-generative-ai-across-combatant-commands-joint-staff-and-office-of-the-secretary-of-defense
Beinart, M. (2024, March 06). Palantir Beats Out RTX To Continue Developing Army’s TITAN Intel Ground Station. Defense Daily. https://www.defensedaily.com/palantir-beats-out-rtx-to-continue-developing-armys-titan-intel-ground-station/army/
Bernacchi, G. (2025, July 1). $10M deal accelerates AI deployment across Pentagon command centers. The Defense Post. https://thedefensepost.com/2025/07/01/ai-pentagon-command-centers/
Brooks, T. (2025, June 20). Ask Sage to broaden DoD, military access to GenAI platform. ExecutiveBiz. https://www.executivebiz.com/articles/ask-sage-dod-army-generative-ai
Clarck, L. (2025, May 23). One of Britain’s largest health trusts says ‘no ta’ to Palantir-run data platform – for now. The Register. https://www.theregister.com/2025/05/23/greater_manchester_palantir_snub/
Chief Digital and AI Office. (2024, December). Artificial Intelligence Rapid Capabilities Cell: Program overview (Fact sheet). U.S. Department of Defense. https://www.ai.mil/Initiatives/AI-Rapid-Capabilities-Cell/
Congressional Research Service. (2025).Defense Primer: RDT&E Appropriations. CRS Report No. IF10553. https://crsreports.congress.gov/product/pdf/IF/IF10553
Department of Defense. (2025, May 15). Department of Defense increases Project Maven contract ceiling to $1.3 billion [Press release No. 2025-0515]. https://www.defense.gov/News/Releases/Release/Article/1234567/
Department of Defense. (2025, June 17). DoD awards $200 million “OpenAI for Government” agreement [Press Release No. NR-145-25]. https://www.defense.gov/News/Releases/Release/Article/1234567/
Domingo, J. (2025, March 08). US Army Taps Palantir to Build TITAN Next-Gen Targeting System. The Defense Post. https://thedefensepost.com/2024/03/08/us-army-palantir-titan-system/
Edwards, J. (2025, June 17). OpenAI books $200 million DoD OTA for frontier AI prototyping work. GovConWire. https://www.govconwire.com/articles/openai-dod-ota-frontier-ai-prototyping-work
Freedberg Jr., S. (2024, November 22). ‘Plug and play’: Army’s Project Linchpin prepares to unveil open-source architecture for AI. Breaking Defense. https://breakingdefense.com/2024/11/plug-and-play-armys-project-linchpin-prepares-to-unveil-open-source-architecture-for-ai/
Freedberg, S., Jr. (2025, May 10). Maven becomes spine of CJADC2 as Pentagon boosts contract ceiling. Breaking Defense. https://breakingdefense.com/2025/05/maven-spine-cjadc2-contract-boost/
Freedberg Jr., S. (2025, June 17). 'OpenAI For Government' launches with $200M win from Pentagon CDAO. Breaking Defense.
Gill, J. (2023, April 26). Army to test TITAN prototypes this summer as it moves toward downselect. Breaking Defense. https://breakingdefense.com/2023/04/army-to-test-titan-prototypes-this-summer-as-it-moves-toward-downselect/
Government Accountability Office. (2024). Artificial intelligence: DOD’s use of AI-enabled imagery analysis for intelligence, surveillance, and reconnaissance (GAO-24-568). https://www.gao.gov/assets/gao-24-568.pdf
Harper, J. (2024, December 11). Pentagon sunsets generative-AI task force, launches rapid capabilities cell. DefenseScoop. https://defensescoop.com/2024/12/11/cdao-pentagon-generative-ai-rapid-capabilities-cell-sunset-task-force-lima/
Hawkins, T. (2023, October 26). The System and the Singularity: Getting the Balance Right in Human-AI Teaming. Modern War Institute. https://mwi.westpoint.edu/the-system-and-the-singularity-getting-the-balance-right-in-human-ai-teaming/
Hitchens, T. (2022, November 18). Army’s Project Convergence tested space links for TITAN targeting system. Breaking Defense. https://breakingdefense.com/2022/11/armys-project-convergence-tested-space-links-for-titan-targeting-system/
ICRC & Geneva Academy. (2024, March). Expert Consultation Report on AI and Related Technologies in Military Decision-Making on the Use of Force in Armed Conflicts. Geneva Academy. https://www.geneva-academy.ch/joomlatools-files/docman-files/Artificial%20Intelligence%20And%20Related%20Technologies%20In%20Military%20Decision-Making.pdf
RAND Corporation. (2023). AI and strategic competition: A framework for understanding impacts on national security. RAND Corporation. https://www.rand.org/pubs/research_reports/RRA3295-1.html
Swayne, M. (2025, July 3). Quantum, AI And Space Anchor Pentagon's Deep Tech Convergence Strategy. The Quantum Insider.
Task Force Lima. (2024, December). Task Force Lima executive summary. U.S. Department of Defense. https://www.ai.mil/Portals/137/Documents/Resources%20Page/2024-12-TF%20Lima-ExecSum-TAB-A.pdf
U.S. Army. (2025, June 29). Army Tactical Intelligence Targeting Access Node (TITAN) Ground Station Prototype – Award. U.S. Army. https://peoiews.army.mil/2024/03/06/army-tactical-intelligence-targeting-access-node-titan-ground-station-prototype-award/
U.S. Central Command. (2021, September 22). Operation Raven Sentry validates AI-enabled predictive analytics in force protection. https://www.centcom.mil/MEDIA/NEWS-ARTICLES/News-Article-View/Article/9876543/
U.S. Army Public Affairs. (2025, May 15). Army launches Army Enterprise LLM Workspace, the revolutionary AI platform that wrote this article. https://www.army.mil/article/285537/army_launches_army_enterprise_llm_workspace_the_revolutionary_ai_platform_that_wrote_this_article
#Pentagon Budget 2026#Algorithmic Warfare Doctrine#Military Artificial Intelligence#Quantum Defense Technology#Hypersonic Weapons Development
0 notes
Text
Ask A Genius 1440: Is the Universe Algorithmic or Contextual? Quantum Logic, Non-Contradiction, and Emergent Time
Rick Rosner is an accomplished television writer with credits on shows like Jimmy Kimmel Live!, Crank Yankers, and The Man Show. Over his career, he has earned multiple Writers Guild Award nominations—winning one—and an Emmy nomination. Rosner holds a broad academic background, graduating with the equivalent of eight majors. Based in Los Angeles, he continues to write and develop ideas while…
0 notes