#Security Technology
Explore tagged Tumblr posts
Text
Smart Locks for Front Door: The Future of Home Security
The Smart Home Industry is evolving rapidly, and one of the most exciting advancements is the introduction of smart locks for front doors. Brands like SwitchBot are leading the charge, offering innovative solutions that enhance both security and convenience for homeowners.
SwitchBot's smart locks are designed with the user in mind, providing seamless integration with your smart home ecosystem. Imagine arriving home with your hands full, only to have your door unlock automatically as you approach! This feature not only adds convenience but also ensures that you never have to fumble for keys again.
Moreover, SwitchBot smart locks come equipped with robust security measures, including encryption technology and remote monitoring capabilities. You can easily manage access for family members or guests right from your smartphone, giving you peace of mind whether you're at home or away.
In conclusion, SwitchBot is at the forefront of making your home smarter and safer. With their smart locks for front doors, you can embrace the future of home security while enjoying the numerous benefits of a smart home lifestyle.
#smart home#home security#smart locks#access management#remote monitoring#SwitchBot#convenience#security technology
0 notes
Text
What is keystroke technology?

An unsettling subject is beginning to surface around how employers monitor how much or how little employees work. Since remote work became popular during the pandemic and businesses started to worry that they couldn’t physically see employees at desks, there has been an increase in digital monitoring. Many said that, as a result, productivity had decreased. Let’s talk about keystroke technology.
The discussion about the technologies businesses use to monitor worker productivity erupted last week when an Australian lady was let go after their monitoring systems revealed she hadn’t spent enough time typing during the workday. According to Business Insider, the 18-year employee of the insurance company used a keyboard for less than 100 working hours in October and again in November. Suzie Cheikho, the woman, has openly denied the accusations.
What is a keylogger, often a system monitor or keystroke logger?
Keyloggers, or keystroke loggers, are surveillance technologies that track and log every keystroke made on a particular device, like a computer or smartphone. It may be based on software or hardware. The latter kind is sometimes called keyboard capture or system monitoring software.
Why do people use keyloggers?
Cybercriminals frequently employ keyloggers as spyware tools to steal valuable company data, login credentials, and personally identifiable information. Nevertheless, there are a few applications for keyloggers that, in specific contexts, might be deemed suitable or moral. Keyloggers, for example, can also be utilised for the following purposes:
By companies to keep an eye on their workers’ computer usage.
Parents monitor the internet use of their kids.
The owners of gadgets monitor any potential illegal activity on their possessions.
By law enforcement organisations to examine computer-related occurrences.
Keystroke tracking software: What Is It?
Keystrokes on employees’ computers are tracked and recorded using keystroke-tracking technology. It records each keystroke a user makes and generates a comprehensive history of their typing actions.
This kind of software is frequently employed for several objectives, such as:
Workers’ Surveillance
Employers can monitor workers’ productivity and activity by implementing keystroke tracking. It can evaluate how workers allocate their time, pinpoint areas needing development, and guarantee adherence to corporate guidelines.
Online Safety
Keystroke monitoring is one security tool they can use to identify and stop unwanted access. The software can detect unusual activity or efforts to breach passwords and other sensitive data by keeping track of keystrokes.
Investigative Forensics
Keystroke tracking can be used in forensic and legal contexts to examine computer user behaviour and gather evidence for inquiries. In situations involving cybercrime or unauthorised access, it is advantageous.
How does it operate?

“keystroke technology” keeps tabs on and gathers information about how employees utilise computers. It is one of the few technologies available to employers to monitor how employees spend the hours they are expected to work more carefully. It records every keystroke an employee makes on their computer.
Thanks to newer features, administrators can now occasionally snap screenshots of employees’ displays. This is the general operation of keystroke tracking software:
Installation: Keystroke tracking software can be installed remotely using malware, phishing scams, or other techniques, or it can be installed on a computer by someone with physical access. It might be purposefully deployed on rare occasions for monitoring—for example, parental control or staff observation.
Hooking into the Operating System: Keyloggers frequently employ methods like hooking into the keystroke handling mechanism of the operating system. Regardless of the application they type in, it enables them to intercept keystrokes as the operating system processes them.
Recording Keystrokes: When installed and turned on, the keylogger records keystrokes. The keyboard captures every key press, including function keys, letters, numbers, symbols, and special keys like Enter, Backspace, and Delete.
Covert Mode: Numerous keyloggers function in stealth mode, which entails running covertly in the background without the user’s awareness. To evade detection by antivirus software and users, they might conceal their files, processes, and registry entries.
Information Recovery:
A database or log file keeps the logged keystrokes. The individual or organisation that installed the keylogger can access it. The keylogger automatically sends recorded data after recording, according to its settings.
Analysis and Misuse: After recording keystrokes, you can examine the data to extract private information such as credit card numbers, usernames, and passwords. Information misappropriation may occur for financial fraud, espionage, identity theft, or other nefarious reasons.
What Issues Does Keystroke Tracking Have With Controversy?
Someone can use keyloggers or keyboard tracking software for controversial purposes, as they can be employed for good intentions just as easily as bad.The following are some critical issues influencing the dispute:
Keystroke tracking presents serious privacy concerns, particularly when people don’t know their manager monitors their typing habits. The possibility of privacy violation may cause unease and resistance.
Unauthorised SurveillanceWithout express authorization, someone can use keystroke tracking software for unauthorized surveillance. This raises moral concerns regarding private property rights and the limits of appropriate monitoring.
Data Security Risks: The management and storage of keystroke data are risks since unauthorised access may lead to financial fraud, identity theft, or other nefarious acts. The acquisition of data raises concerns about its potential misuse.
Workplace Dynamics: When employees are subjected to keystroke tracking in a work environment, trust between them and their employers may be strained. Open communication about monitoring procedures is necessary for sustaining a pleasant work environment.
Ambiguity in Law and Ethics: The debate highlights the necessity for precise laws and moral principles regulating the use of keystroke tracking. Because technology is constantly changing, it is unclear whether current laws can handle new privacy issues.
What Are the Benefits of Keystroke Tracking Software for Businesses?

The company can benefit from implementing keylogging software in the workplace, but it is important to do so responsibly and in accordance with the law. Here are some things to think about:
Enhanced Protection:
Keylogging software is an essential instrument for strengthening security protocols in an enterprise. Keeping sensitive data from unauthorized access and corruption, we identify and resolve issues such as unauthorized access.
Employee Observation:
Keystroke monitoring by employees offers insightful information on their actions and demeanour at work. Employers can use this data to assess worker productivity, spot patterns in behaviour, and identify areas where workers might need more guidance or instruction.
Compliance and Regulations:
By putting keystroke tracking systems in place, businesses can ensure they abide by legal and industry standards for data security and protection. By adhering to set standards, companies reduce the possibility of incurring fines or legal consequences.
Recognizing Insider Threats:
Keystroke monitoring software is crucial for spotting unusual activity or possible insider threats in a company. Organisations can proactively identify and reduce risks posed by internal actors who could compromise sensitive information or carry out unauthorised operations by analysing keystroke data.
Keylogging is an invaluable instrument for investigative purposes when looking into cybersecurity events, fraud, or other illegal activity. Investigators can successfully support their inquiries by gathering evidence and reconstructing events by capturing extensive information about system activity and user interactions.
Safeguarding Private Information:

Keystroke tracking is critical in protecting confidential data, including passwords and private information, from unwanted access. Organisations can put strong security measures in place to stop data breaches and unauthorised disclosures of private information by monitoring user inputs and interactions.
Concluding
Although there is no denying that keystroke monitoring software improves productivity and strengthens cybersecurity, its use requires careful consideration of both practicality and morality. Protecting personal information and fostering employee trust go hand in hand with the ability to improve security and expedite processes
#keystroke technology#typing analysis#biometric authentication#user behavior#security technology#human-computer interaction#machine learning#data security#password alternatives
0 notes
Text
Upgrade your security measures with biometric access control. This advanced technology ensures only authorized personnel can access your premises, providing a higher level of security. Explore the benefits of integrating biometric access control into your existing systems.
0 notes
Text
Enhance Your Security with Pyrotech Electronics Pvt Ltd CCTV Cameras
When it comes to safeguarding your home or business, Pyrotech Electronics Pvt Ltd is your go-to source for top-tier CCTV solutions. Our range of CCTV cameras combines cutting-edge technology with unmatched reliability to offer you the best in security surveillance.
Why Choose Pyrotech Electronics Pvt Ltd for CCTV Cameras?
Superior Image Quality Our CCTV cameras are engineered to deliver high-resolution video, ensuring every detail is captured with clarity. Whether you need sharp images for identification or broad coverage for general monitoring, our cameras provide excellent visual performance.
State-of-the-Art Technology At Pyrotech Electronics Pvt Ltd, we use the latest advancements in CCTV technology. Our offerings include HD, IP, and PTZ cameras, each designed to provide exceptional performance and adaptability for various security needs.
Robust and Reliable Built to last, our CCTV cameras are constructed with durability in mind. They are designed to operate effectively in diverse environmental conditions, ensuring consistent performance and reliability.
Advanced Features Our cameras come equipped with a range of advanced features to enhance your surveillance system. From night vision capabilities and motion detection to remote monitoring and control, Pyrotech Electronics Pvt Ltd cameras offer sophisticated solutions to keep your property secure.
Versatile Solutions We offer a wide range of CCTV cameras suitable for residential, commercial, and industrial applications. Whether you need comprehensive coverage for a large facility or focused monitoring for a smaller space, Pyrotech Electronics Pvt Ltd has the right solution for you.
Explore Our CCTV Camera Range:
HD CCTV Cameras: Capture every detail with high-definition clarity, perfect for precise monitoring and security. IP Cameras: Utilize network-based surveillance for flexible installation and remote access, allowing you to monitor your premises from anywhere. PTZ Cameras: Gain comprehensive coverage with pan, tilt, and zoom capabilities, ideal for large areas and detailed observation. Day/Night Cameras: Ensure clear video footage even in low-light or nighttime conditions with advanced low-light technology. Secure Your Property with Confidence
Choose Pyrotech Electronics Pvt Ltd for your CCTV camera needs and experience the difference that high-quality, reliable surveillance technology can make. Our dedication to innovation and customer satisfaction ensures you receive the best security solutions available.
For more details about our CCTV cameras or to discuss how we can meet your specific security requirements, please get in touch with us. Pyrotech Electronics Pvt Ltd is committed to providing superior CCTV solutions to keep your environment safe and secure.
#CCTV Cameras#Security Solutions#Pyrotech Electronics Pvt Ltd#High-Resolution Surveillance#HD CCTV Cameras#IP Cameras#PTZ Cameras#Night Vision Cameras#Security Technology#Reliable Surveillance#Advanced CCTV Features#Home Security#Commercial Security#Industrial Surveillance#Surveillance Solutions
0 notes
Text
I saw a post before about how hackers are now feeding Google false phone numbers for major companies so that the AI Overview will suggest scam phone numbers, but in case you haven't heard,
PLEASE don't call ANY phone number recommended by AI Overview
unless you can follow a link back to the OFFICIAL website and verify that that number comes from the OFFICIAL domain.
My friend just got scammed by calling a phone number that was SUPPOSED to be a number for Microsoft tech support according to the AI Overview
It was not, in fact, Microsoft. It was a scammer. Don't fall victim to these scams. Don't trust AI generated phone numbers ever.
#this has been... a psa#psa#ai#anti ai#ai overview#scam#scammers#scam warning#online scams#anya rambles#scam alert#phishing#phishing attempt#ai generated#artificial intelligence#chatgpt#technology#ai is a plague#google ai#internet#warning#important psa#internet safety#safety#security#protection#online security#important info
3K notes
·
View notes
Text
I love how half the sites I use are spiralling deeper and deeper into pure security theatre by enforcing extremely complicated password policies whose only practical effect is to create a single point of failure for everybody's personal data by forcing them to rely on password manager apps because any password that actually satisfies the rules is impossible for humans to remember, and the other half are like "actually, we're switching to PINs, so now your account is secured by a six-digit number".
2K notes
·
View notes
Text
#biometrics#Workplace security#Access control#Biometric authentication#access control system#Security technology
0 notes
Text
however bad of a day you're having, know that it's not nearly as bad as whatever the Crowdstrike security team is going through since waking up this morning
#accidentally bricking millions of computers worldwide because of a faulty security update pushed through on Friday evening#has to be some special circle of hell for software engineers#crowdstrike#current events#technology
2K notes
·
View notes
Text

"Eric Noonan, CEO of cybersecurity provider CyberSheath, told CNN it’s likely too early to tell if an attack caused the issues.
“One of the things that should always be taken with a grain of salt is any statements made in the short period of time, immediately after, or even in this case during an attack,” Noonan said.
Musk has a history of attributing technical snafus to cyberattacks. When his conversation with Donald Trump on X started 42 minutes late in August 2024, he said there was a “probability” of an attack."
CNN
Sky News
POLITICO
#destiel meme news#destiel meme#news#united states#us news#world news#elon musk#fuck elon#elongated muskrat#x twitter#twitter#x#cyber attack#cyberattack#cyber security#tech industry#computer technology#computer security#i hope it's just the gutted hollowed out shell of twitter's code finally giving out
190 notes
·
View notes
Text
It's International Bat Appreciation Day!! And I've been stuck thinking about robots lately, so-
#international bat appreciation day#bat#robot art#or something#behold- a guy#this guy had absolutely zero planning in their design#aside from wanting them to have mega radar range#i just had fun making shapes <3#they watch tv in their head all day i bet#listens to radio at the same time#also listens to satellites and secure channels to get all the juicy secret international gossip#i may not know how technology works but just trust me they can do that stuff ezpz#icys drawings and doodles#its 11:55 its still bat day lmao
32 notes
·
View notes
Text
Someday, we’ll all take comfort in the internet’s “dark corners”

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me on SUNDAY (Mar 24) with LAURA POITRAS in NYC, then Anaheim, and beyond!

Platforms decay. Tech bosses, unconstrained by competition; regulation; ad blockers and other adversarial interoperability; and their own workers, will inevitably hollow out their platforms, using ultraflexible digital technology to siphon value away from end users and business customers, leaving behind the bare minimum of value to keep all those users locked in:
https://pluralistic.net/2024/01/30/go-nuts-meine-kerle/#ich-bin-ein-bratapfel
If you'd like an essay-formatted version of this thread to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/23/evacuate-the-platforms/#let-the-platforms-burn
Enshittification is the inevitable result of high switching costs. Tech bosses are keenly attuned to opportunities to lock in their customers and users, because the harder is to leave a platform, the worse the platform can treat you – the more value it can rob you of – without risking your departure.
But platform users are a heterogeneous, lumpy mass. Different groups of users have different switching costs. An adult Facebook user of long tenure has more reasons to stay than a younger user: they have more complex social lives, with nonoverlapping social circles from high school, college, various jobs, affinity groups, and family. They are more likely to have a chronic illness, or to be caring for someone with chronic illness, and to be a member of a social media support group they value highly. They are more likely to be connected to practical communities, like little league carpool rotas.
That's the terrible irony of platform decay: the more value you get from a platform, the more cost that platform can extract, a cost denominated in your wellbeing, enjoyment and dignity.
(At this point, someone will pipe up and say, "If you're not paying for the product, you're the product." It's nonsense. Dignity, respect and fairness aren't frequent flier program perks that tech companies dribble out to their best customers. Companies will happily treat their paying customers as "products" if they think those customers can't avoid other forms of rent-extraction, such as "attention rents")
https://pluralistic.net/2023/11/06/attention-rents/#consumer-welfare-queens
Now, consider the converse proposition: for younger users, platforms deliver less value. Younger users have less complex social lives on average relative to their parents and grandparents, which means that platforms have fewer ways to sink their hooks into those young users. Further: young users tend to want things that the platforms don't want them to have, right from the first day they sign up. In particular, young users often want to conduct their socializing out of eyesight and earshot of adults, especially parents, teachers, and other authority figures. This means that a typical younger user has both more reasons to leave a platform as well as fewer reasons to stay there.
Younger people have an additional reason to bail on platforms early and often: if your online and offline social circles strongly overlap – if you see the same people at school as you do in your feed, it's much easier to reassemble your (smaller, less complex) social circle on a new platform.
And so: on average, young people like platforms less, hate them more, and have both less to lose and more to gain by leaving one platform for another. Sure, some young people are also burning with youth's neophilia. But even without that neophilia, young people are among the first to go when tech bosses start to ratchet up the enshittification.
Beyond young people, there are others who tend to jump ship early, like sex-workers:
https://pluralistic.net/2022/06/21/early-adopters/#sex-tech
Sex-workers' technology changes are only incidentally the result of some novelty-seeking impulse. The real reason to change platforms if you're a sex-worker is that the platforms are either absolutely hostile to sex-workers, or profoundly indifferent to the suffering their policy changes rain down upon them.
The same is broadly true of other disfavored groups, including those with out-of-mainstream political ideologies. Some of these groups hold progressive views, others are out-and-out Nazis, but all of them chafe at the platforms' policies at the best of times, and are far more ready to jump ship when the platforms tighten the noose on all their users.
This is where "dark corners" come in. The worst people on the internet have relocated to its so-called dark corners – privately hosted servers, groupchats, message-boards, etc. Some of these are notorious: Kiwi Farms, 4chan, 8kun, sprawling Telegram groupchats. Others only breach when they are implicated in waves of unthinkably cruel and grotesque crimes:
https://www.wired.com/story/764-com-child-predator-network/
The answer to crimes committed in the internet's dark corners is the same as for crimes committed anywhere: catch the criminals, prosecute the crimes. But a distressing number of well-meaning people observe the nexus between dark corners and the crimes that fester there, and conclude that the problem is with the dark corners, themselves.
These people observe that social media platforms like Facebook, and intermediaries like Cloudflare, DNS providers, and domain registrars constitute a "nexus of control" – chokepoints that trap the online lives of billions of people – and conclude that these gigantic corporations can and should be made "responsible" for their users:
https://www.techdirt.com/2020/06/23/hello-youve-been-referred-here-because-youre-wrong-about-section-230-communications-decency-act/
From there, it's a short leap to conclude that anyone who isn't in a position to be controlled by these too big to jail, too big to fail, relentlessly enshittifying corporations must be pushed into their demesne.
This is a deal with the devil. In the name of preventing small groups of terrible people from gathering in private, beyond the control of the world's insufferable and cruel tech barons, we risk dooming everyone else to being permanently within those unworthy billionaires' thumbs.
This is why people like Mark Zuckerberg are so eager to see an increase in "intermediary liability" rules like Section 230. Zuckerberg's greatest fear isn't having to spend more on moderators or algorithms that suppress controversial subjects:
https://arstechnica.com/tech-policy/2024/03/instagram-users-outraged-by-app-limiting-political-content-ahead-of-elections/
The thing he fears the most is losing control over his users. That's why he bought Instagram: to recapture the young users who were fleeing his mismanaged, enshittified platform in droves:
https://pluralistic.net/2023/09/03/big-tech-cant-stop-telling-on-itself/
A legal mandate for Zuckerberg to police his users is a legal requirement that he surveil and control those users. It's fundamentally incompatible with the new drive in competition circles to force Zuckerberg and his fellow tech barons to offer gateways that make it easier to escape their grasp, by allowing users to depart Facebook and continue to socialize with the users who stay behind:
https://www.eff.org/interoperablefacebook
Remember: the more locked-in a platform user is, the harder that platform will squeeze that user, safe in the knowledge that the cost of leaving is higher than the cost of staying and tolerating the platform's abuse.
This is the problem with "feudal security" – the warlord who lures you into his castle fortress with the promise of protection from external threats is, in reality, operating a prison where no one can protect you from him:
https://pluralistic.net/2021/06/08/leona-helmsley-was-a-pioneer/#manorialism
Rather than fighting to abolish dark corners because only the worst people on the internet use them today, we should be normalizing dark corners, making it easier for every kind of user to find a cozy nook that is shaded from the baleful glare of Zuck and his fellow, eminently guillotineable tech warlords:
https://pluralistic.net/2023/01/15/normalize-dark-corners/
Enshittification is relentless. The collapse of the restraints that penalized tech companies who abused their users – competition, regulation, interoperability and their own workers' consciences – has inculcated every tech boss with an incurable enshittification imperative.
Efforts to make the platforms safer for their users can only take us so far. Fundamentally, these vast, centralized systems that vest authority with flawed and mediocre and frail human dictators (who fancy themselves noble, brilliant and infallible) will never be safe for human habitation. Rather than focusing on improving the platforms, we should be evacuating them:
https://pluralistic.net/2023/07/09/let-the-platforms-burn/
Online communities that control their own moderation policies won't always get it right. But there is a whole host of difficult moderation calls that can never be adequately handled by outsiders overseeing vast, sprawling platforms. Distinguishing friendly banter from harassment requires the context that only an insider can hope to possess.
We all deserve dark corners where we stand a chance of finding well-managed communities that can deliver the value that keeps us stuck to our decaying giant platforms. Eventually, the enshittification will chase every user off these platforms – not just kids or sex-workers or political radicals. When that happens, it sure would be nice if everyone could set up in a dark corner of their own.

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/23/evacuate-the-platforms/#let-the-platforms-burn
#pluralistic#online harms#interoperability#dma#interop#feudal security#switching costs#dark corners#web theory#darknet#platforms#enshittification#evacuate the platforms#bulletproof hosting#incentives matter#platform decay#shitty technology adoption curve
220 notes
·
View notes
Text


I can't remember where Against Sustainability is from lol.
Technical Authority is in this issue of Black Seed. Everything besides this one is an excerpt from a book, so read just the excerpt or the whole book, the choice is yours.
You can read more than just the first ITS communique if you want but they get a little bit nuts later in their existence.
#anarchism#egoism#individualists tending towards the wild#anticiv#anti technology#ecoextremism#ecoterrorism#insurrectionary anarchism#individualist anarchism#technology#security culture#nihilism#anarcho nihilism
74 notes
·
View notes
Text


minecraft at the abbott household
#cooper abbott#riley abbott#logan abbott#trap 2024#trap movie#my art#i think his knowledge of technology only extends to stuff he does butcher stuff with (the security cams and the app etc)#he's still a dad in his mid 40s lol he dont got internet#bideo games get him heated LMFAOO but he tries for the kidsss#being Dad is priority no. 1#he loves being Dad he's very good at being Dad he likes the routines its like a game and he likes winning#the one game he likes#anyways .#he means a lot to me
41 notes
·
View notes
Text

Oh youtube recommendations are being extra cheeky today huh
101 notes
·
View notes
Note
https://x.com/csoandy/status/1814252032884146636
good commentary on the crowdstrike incident
Yes, this is good technical commentary. It's noticeable that different companies have had very different levels of difficulty managing the incident and preparation will certainly have played a role, along with the timing and the number and distribution of systems.
For the less technical (because I've noticed some confused reblogs): Crowdstrike is an enterprise-level, i.e. for large organisations managing many computer systems, set of antivirus tools. It is very good - this is why many, many large organisations with high security needs (such as banks and airlines) use it. Since it defends against malware and viruses, its tools are constantly receiving automatic updates.
About eighteen hours ago, one of those automatic updates accidentally blue-screened Windows machines and servers worldwide that had one particular Crowdstrike tool installed. This was quickly deemed to be fixable without too much hassle, except for one really major issue: individual systems need someone with technical expertise to start them up *directly, in person* in order to be fixed. Imagine you're an airline with computers at every airport. A bank with ATMs nationwide. A retail chain with computers in every store...
Anyway, this is going to take some organisations a while to fix. It is extremely, extremely fixable! But it's gonna take a minute. And some of the orgs not directly affected are reliant on other ones which are. So yeah, soz to IT teams everywhere about their weekend.
#technology#crowdstroke#is what I've seen it called other places and is very funny to me so I'll steal it#computer security#nb: this definitely isn't a hack or a plot or whatever. it's a fuck-up#those happen. it is honestly to crowdstrike's credit this is the first time it's happened to them in a major way
57 notes
·
View notes
Text
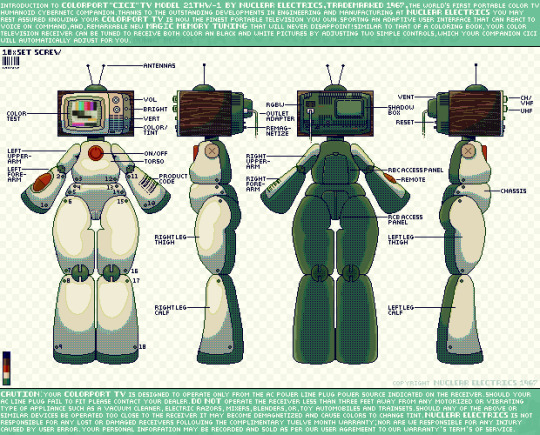
Introduction to COLOPORT CICI TV M21THW-1 BY NUCLEAR ELECTRICS© 1967
An OC I've been developing for the past two weeks, I've been hyper-fixating about a specific 1960s portable tv by General Electrics
She has 6 available personalities and comes with her very own pet! (soon to be released)
She's heavily inspired by 60s technology and the post WWII "return to normalcy" movement and the Red Scare, she's technically just a TV but that's not necessarily what NUCLEAR ELECTRICS or the government for that matter use her for. Let's just hope her pets don't find you acting out of the ordinary...
also... i couldn't figure out how to save this drawing without the pixels becoming blurry but CSP gave me the best resolution, i drew this in Ibis Paint on my phone :) all of the words are hand-drawn because i couldn't find a single font that wouldn't become blurry at the size i wanted
here's a fun list of all the websites i found trying to make this character:
https://www.earlytelevision.org/Etzold/portacolor-d.html
https://www.worthpoint.com/worthopedia/antique-1967-ge-porto-11-color-tv-3845768543
https://clickamericana.com/topics/science-technology/how-to-enjoy-your-ge-porta-color-television-1967
https://www.cool386.com/ge_19inch/ge_19inch.html
also some cool pictures of it




#original character#OC#pixel art#digital art#60s inspired#60s technology#tv head#security camera#cctv#vintage#ibispaint#ibispaint x#my art#my artwork#technical drawing#robot#robot oc#robot girl#robotposting#android#humanoid#character design#character art#Donut Posting#CiCi tv
97 notes
·
View notes