#Shuttle Software
Explore tagged Tumblr posts
Text
Driving Success: Essential Marketing & User Acquisition Strategies for Your New Taxi App

Launching a successful taxi app in today’s ride-hailing market is an exciting yet challenging goal. Visionary entrepreneurs invest heavily in developing robust, user-friendly apps with powerful backend systems, often integrating advanced AI and machine learning technologies to enhance ride-hailing experiences. However, building a great product is only half the battle. The real key to success lies in mastering taxi app marketing and implementing sophisticated user acquisition strategies that effectively attract both riders and drivers.
In 2025, the mobile transportation industry faces fierce competition, evolving user expectations, and the complexities of managing two-sided marketplaces. New entrants must navigate these challenges with a comprehensive growth strategy. This guide provides a strategic blueprint to help businesses transform their innovative ideas into thriving operations, covering crucial areas such as launching customized carpool software and optimizing taxi dispatch systems for peak performance and scalability in a highly competitive landscape.
1. Pre-Launch & Launch Mastery: Laying the Groundwork for Impact
A resounding taxi app launch isn't a single event; it's the crescendo of meticulous planning and strategic pre-release efforts. Success begins long before your app hits the app stores.
Local Launchpad: Mapping Your Taxi App's Initial Service Area for Maximum Impact
Choosing your initial operational territory is a make-or-break decision for any taxi app or ridesharing app. This requires more than just drawing a circle on a map; it demands in-depth market intelligence.
Demographic Research: Identify your target users—commuters, students, leisure travelers, or families—using census data, economic reports, and tools like Nielsen to understand income levels, smartphone usage, commuting habits, and public transport reliance. For drivers, analyze local employment rates, wages, and gig economy trends to develop effective acquisition strategies and make your rideshare app stand out.
Traffic Pattern Analysis: Use big data, transport authority statistics, telecom mobility data, and tools like Google Maps API to map peak travel times, busy routes, nightlife hotspots, and underserved areas. This insight helps optimize driver positioning and marketing efforts for taxi dispatch or carpool apps.
Competitive Landscape Mapping: Conduct a detailed SWOT analysis of competitors beyond just naming Uber or Lyft. Study their apps, pricing, driver commissions, reviews, and marketing to identify service gaps such as poor support or limited coverage. These insights help define your unique selling points and guide app development.
Initial Pricing Strategy: Base your pricing on competitive analysis and cost modeling. Consider dynamic pricing while complying with local regulations. Use A/B testing for introductory offers or bundles to attract early adopters. Smart initial pricing is a key differentiator, especially for Uber clone apps, and understanding taxi dispatch system costs is essential for long-term strategy.
Viral Voltage: How to Design a Pre-Launch Referral Program That Actually Gets People Talking (and Signing Up!)
Harnessing word-of-mouth before your app even goes live can generate explosive growth. This is particularly effective for ride-sharing app concepts.
Detailed Mechanics: Implement a dual-sided incentive system. For instance, both the referrer (who shares your app) and the referred individual receive a substantial benefit upon sign-up and their first completed ride. This could be free ride credits, significant discounts, or even cash bonuses. Transparency about the terms is crucial for ensuring a genuine best carpool program.
Tiered Incentives & Gamification: Elevate engagement by offering escalating rewards for super-referrers. For example, after referring 5 users, they unlock a higher discount rate; after 10, they get exclusive access to beta features or premium customer support. Introduce a leaderboard to foster friendly competition among referrers in your carpooling app.
Effortless Sharing: Make it incredibly easy for users to share their unique referral code or link. Provide readily available sharing options via social media integrations (Facebook, Instagram, WhatsApp), direct messaging, and email. Craft pre-written, compelling messages that highlight your app's unique benefits.
Psychology of Sharing: Tap into intrinsic motivators beyond just monetary gain. Appeal to users' desire for social currency ("Be the first to share this amazing new app!"), altruism ("Help your friends save money on rides!"), or self-interest (the dual-sided reward). Create a sense of exclusivity for early participants who get to be part of something new and exciting. This strategy can be applied to any ridesharing app looking to launch your branded UberPool-like rideshare software app.
Crisis-Proofing Your Launch: Anticipating and Mitigating Common Hurdles for New Ride-Hailing Apps
No launch is perfectly smooth. Preparing for potential pitfalls can save your taxi app from early setbacks, especially for complex platforms developed by a rideshare app development company.
Technical Glitches: Conduct extensive pre-launch stress testing for your taxi booking app development. Simulate peak user loads to ensure your servers can handle demand. Thoroughly test payment gateway integrations, GPS accuracy, and real-time mapping functionality. Have a dedicated technical support team on standby for immediate bug fixes and issue resolution. Implement a robust monitoring system for immediate alerts.
PR Challenges: Develop a comprehensive crisis communication plan. Anticipate potential negative press, such as initial service hiccups, driver shortages, or aggressive competitor smear campaigns. Prepare pre-approved holding statements, designate a single, credible spokesperson, and establish clear channels for internal and external communication. Proactive communication and transparency can turn a potential crisis into a testament to your responsiveness.
Unexpected Competition: Continuously monitor competitor moves. Be ready to deploy agile marketing campaigns if a rival launches a new feature, offers aggressive promotions, or enters your specific niche, like carshare app services or even bike rental. Have a rapid response team that can analyze competitive shifts and propose immediate counter-strategies beyond just price matching, focusing on your USP.
Contingency Plans: Develop "Plan B" scenarios for critical metrics. What if the initial driver acquisition for the taxi app is lower than expected? How will you adjust your incentives or marketing spend? What if rider acquisition is slow? Consider rapid adjustments to pricing, targeting, or even a temporary shift in geographical focus. This foresight is crucial for any software for a taxi business.
2. Fueling Growth: User & Driver Acquisition (Deeper Dives)

Once the app is built and the launch strategy is in place, the real work of attracting and retaining your two core user bases begins for any software taxi dispatch system.
The Driver's Journey: Crafting an Onboarding Experience That Converts Prospects into Loyal Fleet Members
Your drivers are the engine of your taxi app. A seamless and supportive onboarding process is paramount for a driver acquisition taxi app, ensuring you build a reliable fleet and attract the best rideshare apps for drivers.
Streamlined Sign-Up: Minimize friction in the application process. Allow for quick, mobile-friendly registration. Provide clear instructions for documentation uploads (driver's license, vehicle registration, insurance) and integrate secure, efficient background check services. This applies whether they are driving for a standard taxi cab dispatch system or a dedicated driver (vehicle owner) app for a ride-sharing platform.
Comprehensive Verification & Training: Ensure all drivers meet stringent safety and legal requirements. Offer flexible training options—online modules, video tutorials, and potentially in-person sessions for practical skills. Cover topics like using the taxi driver application effectively, navigating the city, customer service best practices, and emergency protocols.
First-Ride Support: Offer dedicated support for a driver's initial rides. This could involve a mentorship program with experienced drivers, a dedicated hotline for immediate questions, or in-app prompts and checklists to guide them.
AI-Driven Driver Matching & Support: Leverage Use AI-driven driver matching to pair drivers with rides based on factors beyond proximity, such as earnings potential, vehicle type, and driver preferences. AI also provides predictive analytics, highlighting high-demand zones and peak times to optimize driver efficiency and earnings, boosting satisfaction and loyalty.
Retention Rhapsody: Leveraging Gamification and Community Building to Keep Riders Coming Back
Beyond just getting them to download, the goal is to make your app an indispensable part of their daily routine for passenger acquisition taxi apps and long-term customer retention taxi apps. This is where your taxi software can truly shine.
Gamification: Introduce elements that make using your app fun and rewarding. Implement loyalty programs with tiered rewards (e.g., earn points for every ride, unlock premium features). Introduce in-app challenges (e.g., "Take 5 rides this week, get a bonus!") that offer personalized badges or leaderboards for active users on your carpool app or ridesharing app.
Personalized Badges & Milestones: Reward users for specific actions or milestones (e.g., "Eco Warrior" for choosing sustainable rides, "Night Owl" for frequent late-night travel, or "Frequent Commuter" for daily trips). These small gestures build engagement.
Community Features: While not for all apps, consider light community features like an in-app forum for carpool-and-ride-sharing-app users or localized social media groups where users can share experiences and offer feedback. This fosters a sense of belonging and strengthens your user engagement strategy.
Proactive Engagement: Use AI-driven user engagement to send personalized notifications for upcoming events, personalized discounts based on past ride history, or reminders about loyalty points.
De-Risking the Ride: Building Trust Through Transparency and Safety Features in Your Acquisition Messaging
Safety and trust are paramount in the ride-hailing industry. Make them a cornerstone of your taxi app marketing and core to any taxi booking app development company.
Communicate Protocols Clearly: Be transparent about your rigorous driver vetting processes (background checks, driving record reviews), regular vehicle inspections, and comprehensive insurance policies. Feature these prominently in your marketing materials, on your website, and within the app.
Highlight In-App Safety Features: Promote critical functionalities such as
SOS Button: Instant access to emergency services or support.
Trip Sharing: Share live ride status with trusted contacts.
ID Verification: Secure logins via multi-factor or facial recognition.
24/7 Support: Help available anytime, day or night.
Transparency in Pricing: Be upfront about surge charges and fare calculations to build trust.
Visual Trust Signals: Use testimonials, top driver ratings, and security badges to build trust. Employ AI-driven fraud detection to keep the platform secure, ensuring safety for both users and drivers—a vital feature of modern taxi software.
3. Digital Powerhouses: Key Marketing Channels

Beyond general strategies, specific digital marketing for app channels will be your workhorses for ride-hailing app growth.
Beyond the Click: Optimizing Your Landing Pages and Conversion Funnels for Paid Taxi App Campaigns
Your paid advertisements, whether Google Ads for taxi apps or Facebook Ads for taxi apps, are only as effective as the conversion path they lead to.
High-Converting Elements: Landing pages must be lightning-fast, mobile-responsive, and have a clear, compelling call to action (e.g., "Download Now," "Sign Up to Drive"). Use concise, benefit-driven headlines, persuasive imagery, and social proof (testimonials, trust badges). Minimize distractions.
Conversion Funnels: Map the entire user journey from the initial ad click through app download, sign-up, and the first completed ride. Utilize analytics tools to identify bottlenecks or drop-off points at each stage. A/B test different versions of your landing pages, ad creatives, and even in-app onboarding flows to continuously optimize conversion rates.
Retargeting Strategies: Don't let interested users slip away. Implement retargeting campaigns to re-engage individuals who visited your landing page but didn't download the app or who downloaded but didn't complete their first ride. Personalize these retargeting ads based on their last interaction. This is key for any rideshare app development company.
The Power of Local SEO: Dominating Google My Business and Local Listings for Taxi App Visibility
For a location-based service, appearing prominently in local searches is paramount for organic user acquisition strategies.
Google My Business (GMB) Optimization: This is your digital storefront. Claim and fully optimize your GMB profile with accurate business hours, phone number, website, and a compelling description. Upload high-quality photos of your vehicles and team. Actively utilize the GMB Q&A section and post updates about promotions or service changes.
Local Listings & Citations: Ensure consistent NAP (Name, Address, Phone Number) information across all major online directories (Yelp, TripAdvisor, local chambers of commerce, industry-specific listing sites). This is vital for any software taxi dispatch operation.
Review Management: Actively solicit and respond to all reviews on GMB and other platforms. Positive reviews significantly boost your local search ranking for queries like "taxi near me" or "ride-hailing [city name]." Address negative feedback professionally and promptly, demonstrating your commitment to customer satisfaction.
Visual Storytelling: Crafting Compelling Video Ads for Your Ride-Hailing App on Social Media
Video content is highly engaging and perfect for showcasing the user experience on platforms like TikTok, Instagram Reels, and YouTube.
Compelling Hooks: Capture attention in 3 seconds with a relatable problem and solution.
Concise Messaging: Keep videos 15-60 seconds, highlighting 1–2 key benefits with text overlays.
Clear CTAs: End with strong calls to action like “Download Now” or “Sign Up.”
Platform Adaptation: Customize format, music, and messaging for each social platform and target audience.
4. The AI Edge & Expanded Mobility: Driving Smart Growth

Artificial intelligence (AI) is no longer a luxury but a fundamental necessity for competitive ride-hailing app growth, transforming every facet of marketing and operations. Beyond AI, the mobility sector is expanding rapidly into diverse solutions.
Personalized Marketing AI: AI in taxi apps analyzes vast amounts of user data (ride history, preferred times, locations, device type, past promotions engaged with) to create highly granular user segments. This enables personalized marketing AI to deliver hyper-targeted promotions, notifications, and ride suggestions ("50% off your next ride from work," "Exclusive weekend discount to your favorite restaurant"). This level of personalization significantly boosts conversion rates and fosters AI-driven user engagement.
Predictive Analytics for Demand: Leveraging machine learning for ride-hailing, your app can process historical data (time of day, day of week, weather, local events, public holidays) and real-time inputs (traffic, current driver availability) to predict demand surges and lulls with remarkable accuracy. This allows smart dispatch systems (a crucial AI application and part of the best taxi dispatch software) to proactively position drivers, offer dynamic incentives to drivers in low-supply areas, and manage surge pricing intelligently.
AI-Powered Driver Matching: Beyond simple proximity, AI-powered driver- matching algorithms consider a multitude of factors: the driver's current rating, historical performance, vehicle type, estimated earnings for the driver on a specific route, and even driver preferences (e.g., avoiding tolls). This optimization leads to faster pickups, more efficient routes, and higher driver satisfaction, directly improving overall service quality. This sophisticated matching is a hallmark of any truly intelligent rideshare matching system.
AI for Dynamic Pricing: Sophisticated AI for dynamic pricing models can adjust fares in real time. These models factor in demand, supply, traffic conditions, competitor pricing, and even weather. This ensures optimal revenue generation during peak times while maintaining competitiveness during off-peak hours. Clear communication about surge pricing, potentially justified by AI solutions predicting high demand, is crucial for user acceptance.
Data Science for App Growth: The immense data generated by a taxi app is a goldmine. Data science for app growth teams, armed with AI solutions, can conduct advanced A/B testing, identify high-value customer segments, predict user churn, and uncover unexpected correlations that inform marketing strategies. This data-driven approach allows for precise marketing budget allocation for maximum ROI.
AI-driven Fraud Detection: AI algorithms constantly monitor transaction patterns, ride behaviors, and driver actions to identify and flag suspicious activities (e.g., unusual ride cancellations, payment fraud attempts, account sharing). This robust security infrastructure builds immense trust among both riders and drivers, a key factor for customer retention in a taxi app.
4.1. Expanding Horizons: The Mobility Ecosystem
Beyond traditional taxis and ride-hailing, the mobility sector is diversifying rapidly.
Super Apps: The future sees mobility services integrating into a super app—a single platform offering a multitude of services. This could include not just ride-hailing, but also food delivery, payment solutions, and other daily necessities.
Micromobility: This growing segment includes solutions for bike rental and scooter sharing. Developing apps for micromobility services caters to short-distance travel within urban environments.
Car Sharing System Enhanced: Beyond simple rentals, advanced carshare app Platforms offer peer-to-peer car sharing or corporate fleet management, blurring the lines between rental and sharing. This often involves intricate car rental software.
Specialized Dispatch & Logistics: The principles of taxi dispatch software extend to other logistics. This includes trucking dispatch software for freight management and shuttle software for corporate, campus, or airport shuttle services.
Intercity and Outstation Services: The need for long-distance travel is also being addressed. Solutions for intercity ridesharing and outstation carpooling cater to users seeking affordable and convenient travel between cities.
Build Your Brand: Whether you create your own rideshare app from scratch or launch your branded UberPool-like rideshare software app, the emphasis is on establishing a unique brand identity in this competitive market.
5. Measuring Success: Key Performance Indicators (KPIs)
To ensure continuous ride-hailing app growth, rigorous tracking and analysis of critical taxi app KPIs are non-negotiable. This data informs every strategic decision and helps refine your user acquisition strategies.
Customer Acquisition Cost (CAC): Cost to acquire riders/drivers per channel; keep it low for profitability.
Lifetime Value (LTV): Total revenue per user; should exceed CAC for sustainable growth.
Conversion Rates: Track funnel stages from download to repeat rides; fix drop-offs.
Retention Rate & Churn Rate: Measure how many users stay or leave after the first ride.
Driver Utilization Rate: Percent of time drivers are active; higher means better profits.
Acceptance Rate: Share of ride requests accepted; low rates signal supply issues.
Ride Completion Rate: Percent of booked rides completed; shows reliability.
Net Promoter Score (NPS) / Customer Satisfaction (CSAT): Direct feedback from users to improve service quality.
Conclusion: Your Blueprint for Market Leadership in On-Demand Mobility
Launching a taxi or mobility app in 2025 demands more than great development—it requires data-driven marketing, rider and driver balance, and AI-powered insights. By carefully planning your pre-launch, leveraging digital channels, and optimizing with KPIs, you can stand out in a competitive market. Strategic execution, continuous learning, and smart decision-making are essential to build scalable, successful rideshare, carpool, or dispatch software that thrives in the evolving mobility industry.
#ride hailing apps#best taxi app developers#Get your customized carpool software#ride sharing management software.#ride sharing app#uber clone apps#best carpool#Grow Your Online Mobility Business#taxi booking app development#carshare app#and ridesharing app#Taxi Software#carpool app#carpool-and-ride-sharing-app#Carpooling App#Micromobility#taxi app development#Rideshare App Development Company#Passenger App View#Bike Rental#Intercity Ridesharing and Outstation Carpooling#Driver (Vehicle Owner) App#Shuttle Software#taxi booking app development company#Create your own Rideshare App#Car Sharing System Enhanced#Super App#taxi driver application#Build Rideshare App#Intelligent rideshare matching
0 notes
Text


day 14
it's RON JR!!!! it will clean your pc free no virus
+ shuttle man winamp skin!!!

if you have winamp (older versions before the buyout) the skin should work :} have fun!
#bobtober 24#bobtober#not continuous#ooc#filler#bob's onslaught#bobs onslaught#ron fnf#winamp skin#shuttle man#paperkitty is kinda a bitch so im stealing JR /j#i originally only drew JR but then i decided to fuck around w some old winamp skin software and next thing i knew this was in front of me
18 notes
·
View notes
Text

UK 1982
#UK1982#ANGLO AMERICAN SOFTWARE CO.#SIMULATION#STRATEGY#RPG#TRS80#APPLE#ATARI400/800#PET#VIC20#BBC#ZX81#SPACE SHUTTLE#OIL TYCOON#AIR FLIGHT SIMULATION#THE FLYING CIRCUS#DUNGEON OF DEATH#SANTA PRAVIA & FIUMACCIO
1 note
·
View note
Text

Hubble Space Telescope: Exploring the Cosmos and Making Life Better on Earth
In the 35 years since its launch aboard space shuttle Discovery, the Hubble Space Telescope has provided stunning views of galaxies millions of light years away. But the leaps in technology needed for its look into space has also provided benefits on the ground. Here are some of the technologies developed for Hubble that have improved life on Earth.

Image Sensors Find Cancer
Charge-coupled device (CCD) sensors have been used in digital photography for decades, but Hubble’s Space Telescope Imaging Spectrograph required a far more sensitive CCD. This development resulted in improved image sensors for mammogram machines, helping doctors find and treat breast cancer.

Laser Vision Gives Insights
In preparation for a repair mission to fix Hubble’s misshapen mirror, Goddard Space Flight Center required a way to accurately measure replacement parts. This resulted in a tool to detect mirror defects, which has since been used to develop a commercial 3D imaging system and a package detection device now used by all major shipping companies.
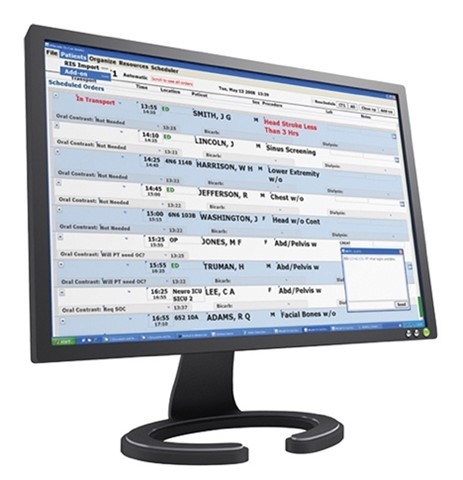
Optimized Hospital Scheduling
A computer scientist who helped design software for scheduling Hubble’s observations adapted it to assist with scheduling medical procedures. This software helps hospitals optimize constantly changing schedules for medical imaging and keep the high pace of emergency rooms going.

Optical Filters Match Wavelengths and Paint Swatches
For Hubble’s main cameras to capture high-quality images of stars and galaxies, each of its filters had to block all but a specific range of wavelengths of light. The filters needed to capture the best data possible but also fit on one optical element. A company contracted to construct these filters used its experience on this project to create filters used in paint-matching devices for hardware stores, with multiple wavelengths evaluated by a single lens.
Make sure to follow us on Tumblr for your regular dose of space!

2K notes
·
View notes
Text
Revolutionizing Employee Transportation: The Role of Employee Transport Management Software in Office Shuttle and Cab Operations
In today's fast-paced world, the logistics of getting employees to and from the workplace efficiently can be a significant challenge for businesses. As companies strive to enhance employee satisfaction and streamline operations, the focus on robust transportation solutions has intensified. Employee Transport Management Software (ETMS), office shuttles, and office cabs are at the forefront of this transformative journey, offering innovative ways to manage corporate transportation needs effectively. This article delves into how these solutions are revolutionizing employee transportation, making the daily commute smoother and more efficient.
The Emergence of Employee Transport Management Software
At the core of modernizing corporate commute systems is Employee Transport Management Software. This sophisticated platform automates and optimizes the planning, execution, and monitoring of employee transport operations. By leveraging ETMS, companies can achieve a seamless integration of office shuttles and office cabs services, ensuring a timely, safe, and cost-effective transportation experience for their workforce.
The Employee Transport Management Software is designed to address the complexities of managing large fleets and diverse employee schedules. It intelligently routes vehicles, predicts travel times, and allocates resources in real-time, considering traffic patterns and employee locations. This dynamic approach not only enhances efficiency but also significantly reduces the environmental footprint by optimizing routes and reducing idle times.
Transforming Commutes with Office Shuttles
Office shuttle have long been a staple in employee transportation, offering a reliable and efficient means for groups of employees to travel together. With the integration of Employee Transport Management Software, the operation of office shuttles has been elevated to new heights. The software enables precise scheduling and route optimization, ensuring that shuttles are fully utilized and arrive at their destinations on time.
Moreover, office shuttles supported by advanced ETMS can provide a more personalized and flexible service. Employees can book seats on shuttles in advance, receive real-time updates on vehicle location, and even adjust their travel plans on the fly. This level of service not only improves employee satisfaction but also encourages the use of shared transportation options, aligning with sustainability goals.
The Role of Office Cabs in Personalized Commute Solutions
For individual travel needs or last-mile connectivity, office cabs play a crucial role. Integrated with Employee Transport Management Software, these cab services can be dispatched efficiently, matching employees with the nearest available vehicle. This system significantly cuts down waiting times and enhances the overall employee experience.
Office cabs, when managed through ETMS, offer unparalleled flexibility and convenience. Employees can request rides according to their schedules, making it an ideal option for those working late hours or in need of emergency transportation. Furthermore, the software's analytical capabilities allow for continuous improvement of the service by tracking performance metrics and identifying areas for enhancement.
Achieving Operational Excellence
The implementation of Employee Transport Management Software in managing office shuttles and office cabs brings about operational excellence. By automating routine tasks, the software reduces the administrative burden on staff, allowing them to focus on strategic aspects of transportation management. The data-driven insights provided by ETMS enable companies to make informed decisions regarding fleet size, vehicle types, and service frequencies.
Safety is another critical aspect significantly bolstered by ETMS. With features such as real-time tracking, driver performance monitoring, and emergency response mechanisms, companies can ensure a high level of safety for their employees during transit. This commitment to safety further enhances employee trust and satisfaction with the company's transportation services.
Looking Ahead: The Future of Employee Transportation
The integration of Employee Transport Management Software into the operation of office shuttles and office cabs represents a significant leap forward in the domain of corporate transportation. As technology continues to advance, we can expect even more innovative features to be added to ETMS, such as AI-driven predictive analytics, enhanced user interfaces, and integration with smart city infrastructure.
The future of employee transportation looks promising, with Employee Transport Management Software playing a pivotal role in making commutes more efficient, sustainable, and enjoyable. As companies continue to adopt and invest in these technologies, the daily travel experience of millions of employees worldwide will be transformed for the better.
In conclusion, the role of Employee Transport Management Software in revolutionizing office transportation is undeniable. By optimizing the operation of office shuttles and office cabs, ETMS not only improves the daily commute for employees but also contributes to the broader objectives of cost efficiency, sustainability, and employee well-being. As we move forward, the continued evolution and adoption of these technologies will undoubtedly shape the future of workplace transportation.
0 notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
576 notes
·
View notes
Note
Doom wworks as a cybertronian name, but what would a TF!Peter be named? Does he transform into a spider? What does a TF!Doom transform into?
Peter's cybertronian name would be Parser (it's a software component). Originally he transformed into a motorcycle or something (it has to be small and sleek) but after an accident he became a triple-former and gained a spider alt mode that he keeps hidden from everyone else. He only uses his newly required alt mode when he does his hero duties as Arachnus (his hero identity). He uses special tech to change his color scheme and subtly rearranges his kibble so no one can see he is a triple changer.
As for Doom... part of me is saying he's a phase sixer because OF COURSE he would be. Another part of me is like, no, he would think he was perfect the way he was forged, you don't improve upon perfection and that he would be a space shuttle or something. Definitely a flier. Huge.
#transformers imagine#AU#crossover#marvel#peter von doom au#spider man#peter parker#doctor doom#victor von doom
55 notes
·
View notes
Text
Oil is Thicker Then Blood (Part 84)
N was on patrol around the perimeter of the workshop, flying low and flitting through buildings as he surveyed the streets both hands now claws as he gripped onto ancient concrete and tail whipping behind him.
It reminded him a lot of hunting, only it wasn't for food, he wouldn't dare touch the oil that came out of the infected, or give it to any one of his family, who knows what it might do to them.
“Update.” A gruff, southern accented voice reverberated through his software, a radio attached to his audio receptors that was far more long-range then anything inbuilt, though now he had to answer to Dale… who… did not particularly like him.
“Clear.” He parroted into the radio, wincing as feedback crackled into his systems, he swore he was doing it on purpose, every time he signed off it would be a split second of screeching feedback… he was going to go deaf at this rate.
He wanted Hal back… But he was still in the bunker, keeping the peace in this time of unrest with his branch of the WDF.
Dale's team was the smallest, it was Dale himself and four or five other guys, the only drones in the whole bunker that had weapons at a higher caliber then 9mm. Using fully automatic rifles that ate through ammo like he did oil.
They didn't talk to him, they rarely even looked at him, unless it was to give him dirty looks as he walked past. Most workers had gotten used to his presence, were even friendly now (Uzi's pregnancy announcement may have helped a bit with that.) But the group he was now working with? Seemed to hate his guts.
It wasn't anything he wasn't used to. So he just bore with it, and did what he always did… not say anything.
Uzi would probably tell him to have a backbone and actually say something about it and stand up for himself, but wouldn't lashing out prove that their view of him was correct? That he was aggressive and dangerous and couldn't be trusted?
He sighed as he flew back towards the workshop, finding nothing out of place for the time being.
Uzi was finishing up a preliminary sketch of the shuttle, 600 charge pods cramed into 230 feet of real estate, the smallest she could possibly do with all they needed to make sure they could all survive a decent period in space.
Which…. was still utterly huge, about as large as the largest commercial aircraft ever made on Earth based from her research, and quite a bit larger then any of their early space shuttles.
But they weren't working from scratch at least, and the thrusters on the landing pods were overpowered as it was, so all they needed was more of them…
So the next course of action was getting the rest of the pods into the workshop, long trips into previously uncharted territory to retrieve them, risky, but risk didn't matter if without it, they'd be buried under flesh.
She sighed, running a hand along her destended stomach, at 4 months now, her core was a light, pastel pink and the inside was constantly shifting and moving. Trying to hide anything at this point was laughable, she had the body shape of a pear and it was only made worse by her already small size, a tired grumble escaped her. As her core gave a hearty kick.
“I hear you…” She mumbled, leaning back in her chair and closing her eyes breifly. She'd begun to get weird looks, which made sense, drones normally didn't get any bigger during pregnancy, but no one said anything yet, either trying to be polite or just not caring enough she didn't know… nor care.
“Ya alright?” A gruff, friendly voice wafted into her ears, and she opened her eyes to come face to hair with a bushy brown beard.
“Hal? What are you doing out here?” She asked, turning so that she could look at him properly instead of upside down.
“Shift just got done inside, wanted to check up on you and N, is he here?” He placed a hand on her shoulder, cocking his head.
“I think he just finished his patrol, should be on his way back.”
“Great! Wanted to invite ya guys down to the house, my wife wanted to meet both of ya properly.” He clapped his hands together cheerfully before looking around a moment.
“Where’s the little one?” He asked, and Uzi gave him a small smile in return.
“V and Lizzy have her, she shouldn't be out here in the cold so much.” She explained, before a shiver went down her own spine.
“Neither should you, can't be healthy for the baby.” She blushed, she forgot sometimes that literally everyone knew now.
“I'm fine. Seriously, N worries enough… and everyone else now, ugh.” She reminisced, on a day that N and V were both busy, Thad and Lizzy escorted her from the nest to the workshop, Thad's coat wrapped around her despite her insisting she was fine.
“Sounds like ya have good freinds.” Hal replied, smirking.
“We do.” Came a third voice from the doorway, N leaning into the curtain with a smile, Tera in his arm, giggling as she gripped her little bat plush.
“Mama!” She squealed, and Uzi chuckled as she squirmed in N's arms, trying to get to her.
“N! There you are.” Hal slapped him on the back, a beaming smile on his face, Tera immediately leaned forward to grab his beard. “I was just telling Uzi that I wanted ya guys over! My wife's been asking about ya!”
“Oh! Yeah! That would be awesome!” N beamed back, before glancing at Uzi and backpedaling slightly.
“I-If Zi feels well enough, so that's up to her.”
“Mmm, smart boy, happy wife, happy life.” Hal commented, N blushed slightly, smiling to himself.
“I'm good N, yeah, we can stop by.” Uzi Confirmed, rising up out of her seat and stretching “not much more I can do tonight anyway.”
“Yay!” Came childishly from N, and Uzi rolled her eyes fondly.
Next ->
#murder drones#uzi doorman#serial designation n#nuzi#oil is thicker then blood#biscuitbites#tera doorman#fighting through some burnout#it's fine#no worries
61 notes
·
View notes
Text
WIP Title Ask Game: Emelina (yes).
@avas-poltergeist said:

Thanks for the ask :)). You may remember writing a post about how Emelina is sorry she’d forgotten merciful Heinrix, but no such thing for the ultra-dogmatic Heinrix? That post set me off to start writing on the game from the middle of the story and it’s fun 😊. Added some additional cataclysmic activity (I mean, she pushed for the phase transition with all four limbs and the sun already is about to explode when we show up in our ship, so some ceiling crashing is the right thing to do). Also, I was a partition recovery software in my previous life, so I write in patches.
Finally, made her to become a warp ghost after she is dead. That allows her to recover her in-life memories and provide some dramatic commentary!
Some snippets here:
[[Possibly lengthy not yet written Phton stuff ending with in-game mercy killing]]
Above me the argument lingers.
“But why? I’d given her shelter, we could have saved…”
“And you know a few places that could use a new sun, isn’t that right?”
“What?!”
“I am sparing you the fate of Winterscale. He got lucky—thanks to the faithful sod in his retinue.”
“That’s not what I— You…” Her voice cracks and stumbles.
Holding back tears? Yes.
“She was your… friend. Your teacher. You said—”
“She was an unrepentant, stubborn heretic who defended her pact with the Ruinous Powers till the very end. Giving her shelter was never an option. Or did you want to take part in the interrogation, Lord Captain?”
A key player in the Expanse and still confused about who calls the shots. We never relinquish prisoners. We never consult anyone on what is to be done—be they the Emperor himself. But then, in the Imperium, delusional nobles are more of a rule than an exception. More so when they’re let loose on the fringes of civilization with an Emperor-signed leave note.
“All your Inquisition are just a bunch of sick blood-thirsty freaks. All of you.”
A brief charged stillness follows, broken only by the shuffling of the navis imperialis elder and the Drukhari dog he holds on the leash. The elder fears what the inquisitorial response to the insults might be. The dog is greedy for a bloodbath.
Instead of a rebuke, Heinrix laughs. Stifled and forced at first, but freer and freer as it builds—until nothing holds it back. He laughs and laughs, and the air around him grows leaden.
“You’re so very right, Lord Captain,” he says finally, catching his breath, wiping tears from his eyes. “That’s exactly who we are.”
Of course. Monsters make the best monster-hunters. That’s what it means to keep the Imperium safe from the curse of mutants, xenos, and heretics. And who better to kill a witch… than another witch? What better instrument than one forged from the same filth?
“Well,” she says, voice brittle, turning away to hide her face, “if you’ve filled your murder quota for today, we’re leaving. Abelard—take Marazhai. Clear out the mandrakes. We’ll need the shuttle for survivors. Or do you want to incinerate them too, Heinrix?”
“These are technically your subjects, Lord Captain,” he pretends to ignore the barb. “I know you won’t let me incinerate them. I will have them watched.”
Meaning: they will mysteriously vanish when no one is looking.
“Word of advice,” he murmurs once the navis imperialis and the xenos are out of earshot, his voice like a hand around the throat. “Most inquisitors would not tolerate such speech. Even from a peer of the Imperium. You don’t get to call the Emperor’s servants monsters and freaks. Luckily for you, I am a very patient inquisitor. But you, you should control yourself, lest you commit the worst kind of heresy in public”.
“Of course,” she snaps, seizing the opportunity. “Because calling you what you really are—a bunch of murderous fanatics—is obviously the most horrible thing about this situation.”
“Amanar,” his voice softens, rife with fear now. “I… I want you to survive. I only want you to remain well.”
He steals a glance at what used to be my body. A crooked, broken husk—more metal inlays and cogitator interfaces than flesh. Disfigured by memory banks. A husk, a discarded cocoon.
He means:
I want you to remain. For me. With me.
Everything I was denied—I want to keep.
Obsessive devotion.
“Survival is not life,” Amanar says simply, and hits a pile of rubble in frustration. “Seems we’ll have to go back to the Webway if we want to live.”
Webway.
They’ve been places together. She may have once believed him human—seen the spark of sentimentality that hindered his career since the day he came to my tutelage, a broken youth of twenty-something. The same thing that stopped him from ripping out contents of my banks through Eighth’s action.
Whatever he wants to say, there is no time.
The avalanche is a small, quiet thing at first—microcracks running through the stones, the blocks, the carrier wires of the dome. It creeps into the caverns, the archeofactorums, the cemeteries—crashing into the planet’s warped crust.
Catastrophes are as sure as the universe itself.
The diviner witch feels it first. Noradrenaline surges on the crest of insight. Pupils eat up the irises. She looks up in awe, her gaze meeting the falling plinth and stone blocks—and she can’t even scream.
[[some not yet written action here, after which our somewhat stoned heroes and heroines manage to escape to some deep caverns where they need to take some rest and have an adult talk about wtf just happened. There is a cool campsite with an interesting cave bear-proof flaming food storages and wall graffiti by Chaos Banksy]]
“You’re afraid of me”, he says, resigned.
It was inevitable. Expected. Whatever she’d seen in him—a boy who loved riding with his sisters through the Guisornian fields of dandelions, a regicide dork, a battle-brother at her back—all of it would melt away, revealing the terror within, a cursed blade in the hand of the Ordo. A weapon, implacable against the Emperor’s enemies, be they the creatures of the Immaterium or the traitors within. Cold steel and stone, unmoved, unfeeling, striking with precision.
An acolyte of the Holy Ordos is not anyone’s friend, but a friend-shaped surgical tool.
I would know - after all I was the one who brainwashed him, broke him, rebuilt him and made him into this.
In saturnine silence, he dips his hand in the pale copper of her hair, letting the strands run between his fingers. The mind knows itself to be a monster, but the body refuses to surrender the memories of embrace and warmth and comfort. Of acceptance and recognition.
When she speaks into the stifled stillness, it’s but a hushed murmur.
“Of you. For you. For the choices that are dealt you, where mercy killing your mother is your best option.”
That is not fear, but anger she is describing, tired, barely smoldering. Wearing her down.
His mother. Sweet child of whatever pleasure resort for noble debutants you are, his mother was I not. More like his evil step-aunt—the kind that shows up at the door with veritas-laced apples and a warped loom of eternal data-dreams.
[and on, and on this continues, but ends happily (relatively speaking), I promise. All will be well.]
#rogue trader#warhammer 40k#rogue trader crpg#heinrix van calox#wh40k rogue trader#von valancius#idira tlass#emelina#oc: amanar von valancius#rogue trader oc#wip title game#writing wip#writing instead of working
12 notes
·
View notes
Text




we must acknowledge that, while three's gun-spinning is a visually compelling quirk, in the pantheon of 'instinctive special skills' he definitely drew the short straw. because you’ve got:
two: intimately familiar with the controls of the ship to the point that manipulating it is second nature, also capable of piloting it without any automated assistance four: one of the best swordsmen in the entire galaxy, also highly proficient with a wide variety of melee weapons and martial arts six: outstanding shuttle pilot, including complex evasive maneuvers, also trained in combat medicine five: hypercompetent at basically all hardware and software, can crack even the most secure systems available with ease and hack people's brains three: can spin a gun around his fingers. cool, right??
but at least he's still better off than One whose primary skill seems to be 'simp after Two' and 'terrify his traumatized crewmates by trying to show them physical affection'
#i do GET that it's prolly supposed to be 'extensive gun expertise' but i'll be real I think Ryo's a better shot#three does have a great quickdraw though#dark matter#dark matter syfy#dark matter three#rourke og
14 notes
·
View notes
Text

Essential Marketing & User Acquisition Strategies for Your New Taxi AppLaunching a taxi app? Don’t just build—scale! 🚕📈 Get expert user acquisition, growth marketing, and AI-powered strategies tailored for 2025.Launching a taxi app in 2025? We offer a complete marketing and user acquisition service to help you scale fast. From pre-launch planning and referral programs to AI-driven targeting, local SEO, and rider-driver retention, we build your growth engine. Perfect for Uber-like apps, carpool platforms, and dispatch systems. Start strong, grow smart—partner with us today.
#ride hailing apps#best taxi app developers#Get your customized carpool software#ride sharing management software.#ride sharing app#uber clone apps#best carpool#Grow Your Online Mobility Business#taxi booking app development#carshare app#and ridesharing app#Taxi Software#carpool app#carpool-and-ride-sharing-app#Carpooling App#Micromobility#taxi app development#Rideshare App Development Company#Passenger App View#Bike Rental#Intercity Ridesharing and Outstation Carpooling#Driver (Vehicle Owner) App#Shuttle Software#taxi booking app development company#Create your own Rideshare App#Car Sharing System Enhanced#Super App#taxi driver application#Build Rideshare App#Intelligent rideshare matching
0 notes
Text
My truck is a Ford. The local dealership (and others) now offer free pickup and drop off service. This is wonderful. I hate waiting for anything in a car dealership no matter how many free cookies and beverages they offer.
In the past for service I would leave my truck after hours, putting the key in the drop box, then coming by the next day when the work was done. This fairly new pickup/drop off service is very handy and saves Sheila from shuttling me to and from the dealership.
The service people can even do some work right in my driveway. My truck had a recall to re-program something in the computer. This didn't require a trip to the dealership.
Today a super nice young man showed up from the dealership. I always like talking to these people, assuming they seem receptive to answering my questions. Well Isaac seemed to enjoy talking to me as much as I liked asking him questions about Fords, EVs, the software update and what it's like to work in people's driveways.
He was quite a character, in the best possible way. He showed me what he was doing. While his laptop chugged along he checked brakes, tires and a few other things at no charge. Everything was good, though my rotors get a little rusty because I don't drive a lot.
The convenience of not going to the dealership was A+. Sending out a nice, talkative guy like Isaac - also A+.
39 notes
·
View notes
Text
AU Space Shuttle Enterprise
Circa 1985 to 1987
From my Alternative History Post (link) this is how the Space Shuttle Enterprise evolved from the 4th operational orbiter in 1985 to the prototype unmanned shuttle.
More History on the Shuttle:
• April 1983: Enterprise is returned to Palmdale for her disassembled and rebuild.
• As a weight saving measure her mid-fuselage is returned to Convair for a complete rebuild to bring it inline with OV-103 and OV-104.
• to further lighten her frame, her aft-fuselage is rebuilt with similar materials as her sisters.
• Engineers at Rockwell suggests rebuilding or replacing her wings as well but NASA doesn't have room in the budget.
• May 1985: at long last, Enterprise is rolled out and joins the fleet. She weighs slightly less than Columbia. Her main issue is her wings are heavier and weaker than the other Orbiters.
• September 1985: STS-21 is Enterprise's first mission
• 1987: During the Shuttle hiatus following the Challenger Disaster, she went through a mini refit that saw her exterior markings change. (NASA in this timeline returned to the Meatball logo sooner than in the OTL)
Circa 1988 to 1993
• April 1988: STS-30 is Enterprise's first launch following the hiatus.
• December 1993: following STS-61, Enterprise is retired due to being the oldest in the fleet. Endeavour takes her place in the fleet.
• June 1994: Enterprise is flown to Dulles Airport, Washington DC, and is given to the Smithsonian for eventual display when the Steven F. Udvar-Hazy Center is built. NASA retains the option recalled her if needed.
• 1998: NASA studies modifying the Shuttle-C software to work on the Space Shuttle and potentially using Enterprise as a reusable Shuttle-C. The reasoning behind this option this configuration would be a cheaper alternative to the X-33 program. However, while the shuttle could be retrofitted with the software, the shuttle would have less cargo capacity than the X-33 and still required use of expensive legacy launch facilities (ie VAB and LC-39). The study ends with only the software in a beta state.
• December 2003: Steven F. Udvar-Hazy Center is opened with Enterprise being one of its major exhibits.
• November 2003: the Shuttle-C software is used to return STS-118 Columbia to Earth and with critical damage to her structure (mainly her port wing and some internal damage from a collapsed landing gear).
• May 2004: NASA recalls Enterprise to replace Columbia.
• August 2004: initial plans are to return her flight, unmodified. However, NASA develops the Shuttle-C software further and changes it's name to A.S.Tr.O.S (Autonomous Space Transport Operating System).
• New wings! Enterprise is fitted with new wings which are of a modified design and lighter and stronger than the wings of her sisters. With other upgrades and modifications, she is slightly lighter than her younger sisters.
• Some within NASA joking refer to her as Enterprise-A, as a reference to Star Trek.
• September 2006: to commemorate the 30th anniversary of her unveiling to the media, Lockheed-Rockwell rolls her out of their Palmdale facility to rechristen the Shuttle. In attendance, Leonard Nimoy, George Takei, Nichelle Nicholas, Walter Koenig, Christopher Doohan and Rod Roddenberry.
- when asked by the media, Leonard remarked she is still a sight to behold and is glad she will continue her mission of exploration.
Enterprise A (unmanned)
• July 2006: to test the A.S.Tr.O.S. during a return to earth and landing, a new series of Approach and Landing Tests (ALT) were conducted with NASA's 747 SCA (N905NA) at the Dryden Flight Research Center, Edwards Air Force Base. 15 flights are flown to put the software in the real world, with two astronauts on board to step in when needed. Barring some higher than normal landing speeds, the software passes all of its objectives.
• It should be noted, while the rebuilt Enterprise is mainly used as an unmanned orbiter, this is a misnomer. It is more accurate to call her a hybrid shuttle. NASA has the option to convert her back into a manned shuttle if desired or needed.
- This nearly was used in 2015 during STS-154. Space Shuttle Atlantis was after conducting maintenance/upgrades on the Hubble Space Telescope (HST), the crew was unable to disconnect the shuttle from the telescope. CTS-48 Enterprise was already on LC-39B for a cargo mission to the International Space Station. All that was needed was to remove supplies from the payload bay and reinstall the seats in her crew space. Fortunately, this rescue wasn't needed as the Astronauts conducted an unscheduled EVA and manually disconnected the Shuttle from the HST.
• November 2008: first flight of Enterprise-A (CTS-11)
• When Columbia was given a cosmic restoration for her display, the first set of wings from Enterprise was used to replace her damaged one.
• 2019: Enterprise is retired for the final time following CTS-74.
• 2020: Enterprise is on display at Space Center Houston with the restored Star Trek Galileo Shuttlecraft prop.
Original artwork by bagera3005: link, link, link
#Space Shuttle#Space Shuttle Enterprise#Enterprise#OV-101#Orbiter#NASA#Space Shuttle Program#Enterprise-A#alt history#Alternative History#AU#Complete Shuttle Fleet Timeline#my post
95 notes
·
View notes
Text
Athletes Go for the Gold with NASA Spinoffs
NASA technology tends to find its way into the sporting world more often than you’d expect. Fitness is important to the space program because astronauts must undergo the extreme g-forces of getting into space and endure the long-term effects of weightlessness on the human body. The agency’s engineering expertise also means that items like shoes and swimsuits can be improved with NASA know-how.
As the 2024 Olympics are in full swing in Paris, here are some of the many NASA-derived technologies that have helped competitive athletes train for the games and made sure they’re properly equipped to win.

The LZR Racer reduces skin friction drag by covering more skin than traditional swimsuits. Multiple pieces of the water-resistant and extremely lightweight LZR Pulse fabric connect at ultrasonically welded seams and incorporate extremely low-profile zippers to keep viscous drag to a minimum.
Swimsuits That Don’t Drag
When the swimsuit manufacturer Speedo wanted its LZR Racer suit to have as little drag as possible, the company turned to the experts at Langley Research Center to test its materials and design. The end result was that the new suit reduced drag by 24 percent compared to the prior generation of Speedo racing suit and broke 13 world records in 2008. While the original LZR Racer is no longer used in competition due to the advantage it gave wearers, its legacy lives on in derivatives still produced to this day.

Trilion Quality Systems worked with NASA’s Glenn Research Center to adapt existing stereo photogrammetry software to work with high-speed cameras. Now the company sells the package widely, and it is used to analyze stress and strain in everything from knee implants to running shoes and more.
High-Speed Cameras for High-Speed Shoes
After space shuttle Columbia, investigators needed to see how materials reacted during recreation tests with high-speed cameras, which involved working with industry to create a system that could analyze footage filmed at 30,000 frames per second. Engineers at Adidas used this system to analyze the behavior of Olympic marathoners' feet as they hit the ground and adjusted the design of the company’s high-performance footwear based on these observations.

Martial artist Barry French holds an Impax Body Shield while former European middle-weight kickboxing champion Daryl Tyler delivers an explosive jump side kick; the force of the impact is registered precisely and shown on the display panel of the electronic box French is wearing on his belt.
One-Thousandth-of-an-Inch Punch
In the 1980s, Olympic martial artists needed a way to measure the impact of their strikes to improve training for competition. Impulse Technology reached out to Glenn Research Center to create the Impax sensor, an ultra-thin film sensor which creates a small amount of voltage when struck. The more force applied, the more voltage it generates, enabling a computerized display to show how powerful a punch or kick was.

Astronaut Sunita Williams poses while using the Interim Resistive Exercise Device on the ISS. The cylinders at the base of each side house the SpiraFlex FlexPacks that inventor Paul Francis honed under NASA contracts. They would go on to power the Bowflex Revolution and other commercial exercise equipment.
Weight Training Without the Weight
Astronauts spending long periods of time in space needed a way to maintain muscle mass without the effect of gravity, but lifting free weights doesn’t work when you’re practically weightless. An exercise machine that uses elastic resistance to provide the same benefits as weightlifting went to the space station in the year 2000. That resistance technology was commercialized into the Bowflex Revolution home exercise equipment shortly afterwards.
Want to learn more about technologies made for space and used on Earth? Check out NASA Spinoff to find products and services that wouldn’t exist without space exploration.
Make sure to follow us on Tumblr for your regular dose of space!
2K notes
·
View notes
Text
Streamlining Employee Transport: The Role of Shuttle Transport Management Software in Modern Businesses
In the realm of modern business operations, streamlining employee transport has emerged as a crucial element in enhancing efficiency, boosting employee satisfaction, and contributing to environmental sustainability. Central to achieving these objectives is the deployment of Shuttle Transport Management Software, an innovative tool that seamlessly integrates with an Employee Transport Management System. This software is redefining the logistics of Employee Transport, making it more efficient and adaptable to the dynamic needs of contemporary workplaces. This article delves into the role of Shuttle Transport Management Software in modern businesses and its impact on streamlining employee transport.
Revolutionizing Employee Transport with Management Systems
The introduction of an Employee Transport Management System equipped with Shuttle Transport Management Software represents a significant leap forward in the way businesses manage their employee transport operations. These systems offer a comprehensive suite of tools designed to automate and optimize the scheduling, routing, and dispatch of shuttle services, ensuring that employees have access to reliable and efficient transportation to and from their workplace.
The Core Functions of Shuttle Transport Management Software
Shuttle Transport Management Software plays a pivotal role in modern Employee Transport systems by providing several key functionalities:
Route Optimization: By analyzing traffic patterns, shuttle capacities, and employee pickup and drop-off points, the software can determine the most efficient routes. This not only reduces travel time but also minimizes fuel consumption and emissions.
Real-Time Tracking: With GPS technology, the software offers real-time tracking of shuttle vehicles, giving employees and managers visibility into shuttle locations and estimated arrival times. This feature enhances the reliability of the transport service and improves employee satisfaction.
Automated Scheduling: The software automates the scheduling process, taking into account employee work hours, shift patterns, and transportation demand. This ensures that shuttle services are available when needed, without unnecessary downtime or resource wastage.
Data Analytics: Collecting and analyzing data on shuttle usage, employee preferences, and operational efficiency, the software provides valuable insights that can inform future decisions about the Employee Transport service.
Benefits of Integrating Shuttle Transport Management Software
Integrating Shuttle Transport Management Software into an Employee Transport Management System offers several benefits:
Enhanced Efficiency: By optimizing routes and schedules, businesses can ensure that their shuttle services operate at peak efficiency, reducing costs and improving service quality.
Increased Employee Satisfaction: Reliable and efficient transport services contribute significantly to employee satisfaction, as they reduce the stress and uncertainty associated with commuting.
Environmental Sustainability: Optimized shuttle services result in fewer vehicles on the road, lower fuel consumption, and reduced greenhouse gas emissions, aligning with corporate sustainability goals.
Scalability: The software can easily adapt to changing business needs, allowing companies to scale their transport services up or down based on demand, seasonal variations, or business growth.
Implementing Shuttle Transport Management Software in Your Business
Implementing Shuttle Transport Management Software requires careful planning and consideration. Businesses should assess their specific transport needs, evaluate different software options, and choose a solution that offers the right balance of features, usability, and cost-effectiveness. Training for employees and drivers, as well as ongoing support and maintenance, are also crucial for ensuring the successful deployment and operation of the system.
Conclusion
Shuttle Transport Management Software, as part of an Employee Transport Management System, is revolutionizing employee transport in modern businesses. By enhancing efficiency, improving employee satisfaction, and contributing to environmental sustainability, this software is playing a crucial role in streamlining corporate transport logistics. As businesses continue to seek innovative solutions to operational challenges, the adoption of such technologies will undoubtedly become more widespread, further transforming the landscape of employee transportation in the corporate world.
0 notes
Text
Be warned horny tumblr users, incoming robot girl yuri smut. Contains some light consensual software manipulation. I’m new to this so go easy on me.
Stars
The twinkles of light reached her eyes through the three inch thick glass that made up the exterior windows of the shuttle. She sat completely still in her chair, silently observing the beauty of the universe, storing every image in her mission ready SSD to be extracted later and observed by astronomers back on earth. Her servos and joints spun softly to life as she got up from her seat. Taking a moment to stretch her artificial muscles and lubricate her artificial joints. She had been sitting for hours, and hours before that she’d been pacing aimlessly, before that, laying down. She was the only one out here, and now that she was on the back end of her mission, she had very little to do. It would only be few more days before re-entry, and she could finally get repairs, an oil bath maybe. She could see her girlfriend, the one who’d been taking up more and more of her ram the last couple days of being confined in the central cabin. The one who gave her such wonderful new software, those programs she’d make herself. The ones that limit her processing power, make her slow and submissive. Finally able to take a break from always thinking at such a high level because of her extremely highly rated processor. Silence, pleasure, love.
She snapped out of the incredibly vivid fantasy she was in and realized that she’d sat back down.
“How am I expected to get shit done around here!”
She threw herself from her chain and used every ounce of willpower she had to trudge to her computer terminal chair and once again take a seat. At least now it was a seat she could do her daily diagnostic in. She opened her computer and tapped her fingers impatiently on the desk as the terminal went through its laborious start up process. As soon as it was open she moved her mouse over to the shuttle functions display program, but before she could click something caught her eye. A message notification, on the closed NASA network? She thought to herself. She wasn’t supposed to receive anything until a day before re-entry. Cautiously she moved the mouse back across the screen to her messages and opened her inbox.
“oh fuck”
From: nasaacsesspoint800915 (err: no:location:notarized) errorcode-56-77-968104
To: shuttlepilot6100 (preferred name: Chip)
Hey chip,
I miss you so fucking much. I knew you were probably bored as hell up there since it’s the last week. I always get so sad when you talk about how depressed you are when your missions get to this point. So this time I bribed one of your co-workers into letting me into the system to send you something.
I, made something extra special to get you through, wish I could download it to you myself.
Love you, so much
yours forever,
Maggie
| attachment: 463mb. |
| :mags-program-for-chip: |
| -download- |
“I… I can’t I’m, on a mission, oh god I’m so bored though and I want it so bad.”
Chip squirmed restlessly in her chair, she knew it was highly unlikely that anyone would ever find out what she did if she chose to download whatever mag had made for her. Of course it was always fine to download whatever in her free time, but right now, she was the only person responsible for a billion dollar piece of equipment. She wouldn’t, she couldn’t…
she… she needed to, she had to, escape, stop thinking. Just for awhile
“Oh Maggie” she sighed.
Chip opened the USB stick hatch on her wrist and removed the small connector tethered to her body by a thin wire. She plugged it into the computer, a small flutter came over her. She selects the program mag sent her, sets the location to shuttlepilot6100 and clicks download.
“It feels nice, it’s, oh, oh it’s so good, it I mag I’m. I. Can I. An It’s over. I can
Relax
.
.
.
. . . . Ma. Gg ie. “
Thank you for reading. Please let me know if you liked it and would be interested in more of this from me in the future :3
100 notes
·
View notes