#Sofware engineering
Explore tagged Tumblr posts
Text
Technology Hits: New Submission Guidelines - 2024
Technology Join a unique publication supporting writers penning about technology to find a broad audience using the power of ILLUMINATION on Medium. Dear Writers and Readers, Coming from a technology and science background, I have a strong affinity for technology writers and tech topics on multiple platforms. I enjoy reading their stories, but I also like reviewing, curating, and promoting…
#business#Business Architecture#Dr Mehmet Yildiz technologist#Dr Yogesh Kulkarni as lead editor#Enterprise Architecture#entpreneurship in technology#Hardware enginnering#Medium#Self Improvement#software architecture#Sofware engineering#substack#Sylvain Zysman#Tech Startup#technology#Technology Excellence#Technology for Startups#technology Hits on Medium#Technology Hits on Substack#technology leadership#writers#writing#writingcommunity
0 notes
Text
i wanna cry i hate this so much. theres no hope for me or my career.
#i should have taken the sofware engineering job in north carolina#i just didn’t want to live in north carolina#this job is so depressing i feel so useless#my only hope is that my mom’s friend can get me a job at [company] but i would still need stuff on my resume and to be good at leetcode
9 notes
·
View notes
Text

CURSO DE PROGRAMACIÓN ALTO NIVEL C++
Gratuito
Español
Más info:
1 note
·
View note
Video
youtube
A Day in the Life of a Software Engineer
1 note
·
View note
Text
Cyberchase: How to Hack the Motherboard
So, when I was writing my episode discussion post on Cyberchase Season 1 Episode 1 "Lost My Marbles", I mentioned that I might make another post about the security breach that allowed The Hacker to infect Motherboard with the virus. What did The Hacker do to set this up? How did the kids accidentally open the breach? And other questions like that. I have a bit of background in software engineering. I will try to keep things as simple as possible.
Much of this is head-canon built on top of what we see in the episode. Of course, the show plays it fast and loose with computer terminology. Don't try to hack things in real life. You will go to prison.
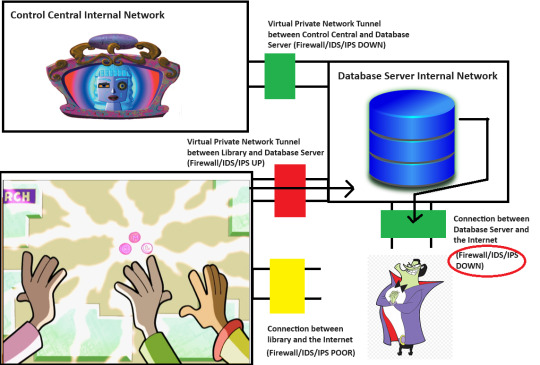
So, here's an MSPaint diagram of a tiny piece of Motherboard's setup. Keep in mind that she is the god of the Internet, and her Internet may even stretch beyond Earth into other galaxies.
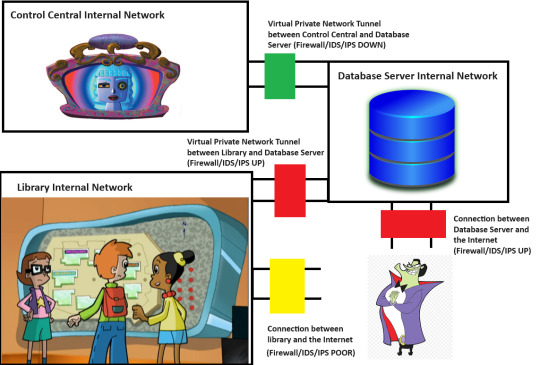
So, there are three separate network segments here. We have the library's internal network, which has the big board on it. We have Control Central's internal network, which has Motherboard on it. And then we have a Database Server internal network, which has a Database Server running on it.
The Database Server is something that I invented here. Remember that this whole diagram is head-canon. However, it's not too far-fetched to think that Motherboard must reach across Cyberspace to a separate Database Server, maybe at the Cybrary.
Now, we know that Motherboard is not directly reachable, even with her Firewall down. Otherwise, The Hacker wouldn't have needed a separate security breach to get to her. He would have just pushed the virus once she took down her firewall for maintenance.
However, Motherboard has a Virtual Private Network (VPN) tunnel to the Database Server. If The Hacker can compromise the Database Server and get his virus in there, it might be able to ride the tunnel into Control Central.
The purpose of any Firewall is to apply a set of rules to any network traffic going into or out of a network, device or application. A good Firewall configuration allows on the traffic that is needed and denies everything else. Motherboard's firewall between herself and the Database Server is currently down. The Database Server itself has connection points to the larger Internet without using a VPN tunnel. However, the Database Server's own Firewall for that access point is UP. If The Hacker tried to throw his virus at that access point, it wouldn't work.
However, there is another connection point into the Database Server. This is another VPN tunnel from the library network. Let's say that the board retrieves the data on the locations of different objects on the map and the icons for those objects by reading one of the Databases. Maybe the board also writes data to the Database to log what directions people requested.
The point here is that some traffic from the Board is authorized to pass through the Firewall on that VPN tunnel. Now, is there a way for The Hacker to get the Board to send authorized traffic over the VPN tunnel to tell the Database Server to open a breach in the Firewall for that public access point? Maybe. It is an Internet-of-Things (ioT) device. Alot of people get these devices, and then they either leave passwords set to their defaults or they forget to keep the sofware patches up to date.
There is a public access point to the Board with a poorly-configured firewall. Maybe there's a way for him to get inside. It may be possible for him to dump the virus code into the board, but there's no guarantee that it would be able to go any further, since the Firewall between the Board and the Database Server is working.
So, let's think about the Board as its own thing.

Suppose that we have two user accounts associated with the board. There is a Principle of Least Privilege that states that a given user account or system process should only be given the minimum amount of permissions required to perform its tasking. That way, if the user account or system process attempts to do something out of line with its permissions, it won't be allowed to perform the operation.
However, if you leave other unnecessary permissions open, and the user account or system process attempts to do something outside of its original intended operations, then the operation may succeed and have unintended consequences.
This also links up with the software development concept of the Minimum Viable Product. You build your software to perform only the exact tasking that it needs it perform. You don't put any additional, undocumented functions in there. Otherwise, those functions could activate and have unexpected consequences.
The board's purpose it to display the different locations. It allows for users to input two points, and it will draw a line between them to assist in navigation. We also established earlier that it reads its information from the Database and writes other information out to the Database.
However, suppose there was some undocumented functionality here. Suppose the developers had a special feature installed in the board that ran a cleanup command against the Database if you pressed three buttons in quick succession. Suppose that the cleanup command in question could be any arbitrary command. Therefore, the developers put the command into a configuration file to be read and executed by the software at runtime.
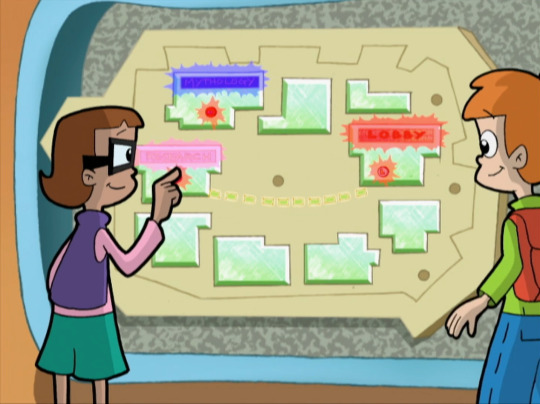
However, the developers knew that if some kids turned up and started poking the map, they could accidentally kick off the Database Cleanup command. They removed the Database Cleanup command from the configuration file. That way, if someone did poke three buttons in quick succession, the software would check the configuration file, see that there was no command defined, and then do nothing.
The trouble is that they left the part of the software that read the configuration file and ran the arbitrary command in place. So, if the command was somehow added back to that part of the configuration file, then there would be a command for the software to run. Then, if someone else pushed the three buttons, that command would be run. So, yeah, someone could put a command in there to write a bunch of junk into the Database until it filled up and crashed. Again, these are commands being sent to the Database from the Board. The Firewall would let them through just fine.
That's pretty bad, but that only lets them modify the Database, right? It's not like they can just tell the Database to open the Firewall on the server that it is sitting on, right?
Well, what if one of the things that the Database could do, upon request, was to open a command shell on the server and run a command. And what if, that command shell was able to run commands that impacted things on the server beyond the Database itself.
What if we called it "xp_cmdshell" and called the Database Server "Microsoft SQL Server 2000". Windows XP and Microsoft SQL Server 2000 would have been around at the time of "Lost My Marbles" after all. Those were also the key players in the real-world Heartland Payment Systems data breach of 2008, which inspired this post.
But hey, just because the Database could open a command shell on the Database Server doesn't mean that The Hacker could use it to bust the Database Server's external Firewall, right? He still needs a way to execute "xp_cmdshell". So, he needs an account with the correct permissions to tell the Database to execute "xp_cmdshell", and he needs the Database itself to have high-enough permissions to run a command via "xp_cmdshell" that can bust the Database Server's external firewall and open a path to Motherboard. Thankfully, the Database only run the "xp_cmdshell" for the top-level Database Administrator account.
This is where we get back to the Principle of Least Privilege. The Board should connect to the Database with a fairly low-power account. It only needs to read-from and write-to a few Database tables after all. Likewise, the Database itself should have been started on the Database Server by a fairly low-power account, as it only needs to handle reading and writing its own set of tables.
But then some moron decided to hook up the Board to the Database Server on the top-level Database Administrator Account. So, if the Board was configured to send an "xp_cmdshell" command, the Database would run it. Oh, and another moron decided to have the Database Server start the Database with the "root" account for that server. So, if the Board was configured to send in an "xp_cmdshell" command to nuke the external Firewall, then the Database would be able to nuke the external Firewall.

There is a principle called Defense-in-Depth, where you build multiple layers of defense around your critical item. That way, if a layer fails, you may be okay. We're running out of layers.
We only have one or two layers left. We know that the Board doesn't run "xp_cmdshell" for its regular operations today. Sure it has an undocumented debug mode that allows someone to execute any command in its configuration file (including "xp_cmdshell") against the Database. But someone would need to get to that file.
The board's main account doesn't give you a filesystem to play with, as they wouldn't want kids running up, poking things, and deleting the filesystem. No, you only get the interfaces that you get. You can pick two items and see a path between them. Or you can pick three items and see the undocumented debug mode run whatever command is in the configuration file.
But what if there was some sort of maintenance account accessible through the Internet that didn't enable someone to send commands to the Database, but would enable someone to get into the filesystem and mess around with it? And what if that maintenance account was still using a weak or default password because people just don't check that for IoT devices?

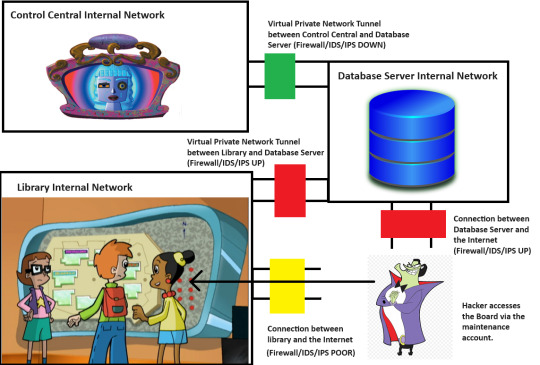
So, he's in the Board's filesystem now. That's concerning. And wouldn't you know it, yet another moron left that critical configuration file in a state where the maintenance account can make changes to it. So, of course, he found the empty configuration item for the cleanup command. Remember, this was setup to run any arbitrary command. Of course, he put in an "xp_cmdshell" command that tells the Database to nuke the external firewall on its own server.
While The Hacker was able to put the command in place, the maintenance account doesn't have the power to send commands to the Database on its own. That power is only enabled for the system account tied to the Board's user interface. So, he still has to rely on someone in the real world to push three buttons in quick succession.


Well...shit.
That's not good.

That's not good at all.
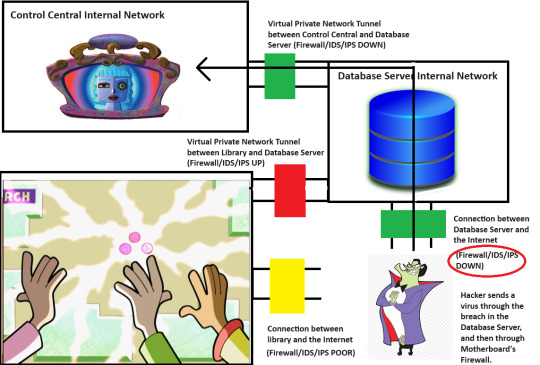


Seriously though, don't try this at home.
I suppose we can speculate on the nature of the virus. We know from Season 1 Episode 14 "Cool It" that Motherboard goes through more cryoxide than normal due to the virus. There are actual computer viruses out there that were designed to turn off heat safety warnings on CPUs and then cause them to run hotter. Some CPUs would eventually melt and ruin the computer.
The original infection destroyed the Encryptor Chip, and it is stated that only a replacement Encryptor Chip could cure the virus. The name suggests that it deals with data encryption, but perhaps it is also a virus cleanup tool. Perhaps it worked to weaken the existing virus until it was eventually overwhelmed and destroyed. Perhaps the virus exhausted most of its strength destroying the Encryptor Chip first.
In any case, curing the virus permanently would end the show.
#cyberchase#2000s#cartoon#nostalgia#pbs kids#2000s childhood#not for use in real life#you'll get busted
12 notes
·
View notes
Text
guys im literlly so stpid?
why did i apply for walmart sofware engineer II. im not even qualified for it. like how do i overlook THE JOB DESCRIPTION and apply anyway... ???????????? im so ?????
5 notes
·
View notes
Text
Sofware Engineer II
Job title: Sofware Engineer II Company: Rivian Job description: with all applicable fair employment practice laws regarding citizenship and immigration status. Rivian and Volkswagen Group Technologies… Data, including to or in the United States, Canada, and the European Union and in the cloud, and this data may be subject… Expected salary: Location: Vancouver, BC Job date: Thu, 01 May 2025…
0 notes
Text
Hotel Booking Sofware

Hotel booking software is a powerful digital solution designed to simplify and automate the process of managing hotel reservations. Whether you run a boutique hotel, resort, or a chain of properties, the right hotel reservation software helps streamline bookings, improve guest experience, and increase overall efficiency.
A modern online hotel booking software enables guests to make reservations from anywhere, anytime through your website or a third-party platform. It offers real-time availability, secure payment gateways, and instant confirmations, reducing manual errors and saving valuable staff time. For hoteliers, features like centralized dashboard control, calendar synchronization, rate management, and automated emails enhance day-to-day operations and ensure no booking opportunity is missed.
For smaller hotels and independent properties, small hotel reservation software offers a cost-effective way to compete with larger chains. With a user-friendly interface, cloud-based access, and mobile compatibility, even non-technical users can easily manage reservations, track occupancy, and generate detailed reports.
Integration with channel managers, POS systems, and CRM tools makes hotel booking software an all-in-one solution to streamline guest management and increase revenue. Some advanced systems also offer built-in marketing tools, loyalty program features, and multi-language/multi-currency support to attract international travelers.
Whether you want to reduce overbooking, improve operational efficiency, or enhance your direct booking strategy, investing in the right hotel booking engine software is a smart move. It not only simplifies the reservation process but also strengthens your brand’s online presence and helps you deliver exceptional guest service.
Ready to transform your hotel operations? Find the hotel booking software solution that fits your needs and improve your guest experience today.
1 note
·
View note
Text
Why Engineers use Multi Story Building Analysis and designing software?
Multi Story Building Analysis and Design Software is a very useful software product used by the structural engineers in doing the Analysis of High rise Buildings to check the Stability of the Structures . A detailed analysis can be performed as this software provides a Three dimensional projection of the Building structures which provides a strong user interface. Modelling and designing can also be performed which is a very plus point of the Software.
0 notes
Text
Full Stack Sofware Engineer UCLouvain For the UCLouvain's e-OMIX project, we are hiring Full Stack Software Engineer to build and deploy an omics data exchange platform. See the full job description on jobRxiv: https://jobrxiv.org/job/uclouvain-27778-full-stack-sofware-engineer/?feed_id=77185 #data_science #FHIR #multi_omics #omics #rest_api #tiledb #ScienceJobs #hiring #research
0 notes
Text
When I looked up the Iowa caucus drama and saw that they had created a phone app to tally the votes, I was like YOU DID WHAT???
*cries in software engineering*

#iowa caucus#xkcd#sofware engineering#we warned you we fucking told you#the people who agreed to program this need to be exiled#how dare you betray our profession like this?
2K notes
·
View notes
Link
How to Block Firefox from Creating New Windows With a Tab Drag and Drop? https://brandsofttech.blogspot.com/2020/03/how-to-block-firefox-from-creating-new.html
#software engineering#software development#software design#Software Developers#software defined networking#software d#sofware developer#programming#programs#weight loss program
1 note
·
View note
Photo

Here at Digital Front Media Inc. we offer services that meet your business needs to build your website, with our specialized team of software engineers we ensure to provide a good quality and an assurance that your website will grow with us.
0 notes
Text
intro
n the world to come there is little sin There are just lots of american alligators It was a great idea, but it wasn't long before people started getting burned by their own fires The prediatrain movement caught fire in america The demand for american alligator meat skyrocketed and so did the price People began to get greedy and the greed got them killed You see no reason why this can't happen here too Whorals where burned to ash while polled hereford heifors fetched record prices at market that week The cows have returned to the farms and other prey animals make their homes in unused warehouses Over a billion dollars a head in auction sales! It'll take the world a few years to bleed the remaining American Alligators and it'll take a few more before there come reports of theft Googizon won the bid to construct for the military the most forward thinking alligator farm in existance All eggs used today bear the GoogZon prf mark It currently floats near the okeenokee snow swamp Or so it will say on their website No one believes it This is not that story "Come on Al, it's the target! " the tech yells as you take fire and hit the pavement We are primal ponds inc a predatory company, head quartered at number ten prime avenue And you are Al Brutal leads rank 3 for said company A small mom and pop alligator farm attemping to make it And you're casing it "We don't have sufficient evidence! " You yell back We need you to make deliveries for us When your territory was hoisted upon you you had a team It's gone, lost You have no one Please Point of view of the player: You wake up with a mean hang over and a thick head ache in the dark A delivery champion You will drive through the night to a swamp and break through glitched out gates is a lowly position He had a secert life as billy fea fbots navigator And one more thing He had to have known about his bugs Maybe all saltimbanques are fots dead ones or not but he googled it It turns out no one has made a crappy real time virtual reality game dedicated to About a dozen years before your time, digital reality came out billy fortes navigator yet Delivering dragon tail in the far, far, future or you could kill the bugs, sharpen your tusks, drink your vodka and hang out with the hardcore otters Maybe that needs to change You push "N" to climax the degrading disk and send it out into nothing We proudly introduce today drum roll please Doesn't anyone play regular instruments any more? Alligator delivery service A darkness awash light breaks through the windows and washes over you The door slams open and a deliverywoman walks in your office The alligator farm where the gator are delivered is currently under hostile takeover Trouble in the bandit managed quarry has led to good business for here A series of construction tasks allow you to flood the market with new affordable alligator meat and pelts You bring in your first load of revenue Already we own over four over ten foot alligators a buzzard and a vat of swamp water Let's throw ourselves a party and watch as they exterminate your future competition Including rex lex, your prime suspect Five years seems like enough time for our boys in blue to put the pain on old rex A massive 14 foot beast with jaws that could crush cars float in your tank You're out of coffee and are jittery as hell Each on is incredibly detailed with over twenty bioligocail parts like an engineers wet dream THey have nothing else worth mentioning, jsut huge predatory monsters that will sell for a bundle Part one of this weeks training pick up a nearly dead gator out the tank and work with it over time to tame it Part two Part thee no wait Part five Part four Lum rex overfished the river and died before we could get our hands on it use the dead rex to harvest collagen The only thing it's good for something, something That's it for this week folks Let's prepare today's shipment Part six bio-diesel Part seven shoot some folks in the face! wait wrong game Part eight Looks like we're gonna spend our earnings wher else but here oh yeah, No employee raises we're shorting titanium Gold doing amazing things with Bridge and tunnel construction in NYC Part nine THe alligator lays in the mud lifeless after taking multiple assaults from your shovel The alligator drops and lands with a heavy thud Part ten capitilize on new changes We all help load the alligator onto the semi As you secure it, Coming next fall We are currently broadcasting their vital signs over at americanalligator They're in a glass reinforced steel container welded under the deck xyz The accelerator and brake are under the dashboard Our alligators come in many different sizes, each perfect for their own uses We currently have a large supply of eggs that will be ready to "harvest" in about ten years Ages, shapes, sexes and shades are represented over our entire roster of workers They all have cute baby faces, cold reptilian eyes and maws full of razor teeth The like to eat, sleep, dream, and spawn but don't speak our language or one anothers They're sensitive to movement and bright lights but that's it They love to fight and gossip and spread allegiences through body language and scent We created them using centuries old processes, updated from breeding techniques pioneered by the USSR to create super soldiers The algorytms which run each alligator is closely modeled after the human brain and all it's decisions making pathways This allows each alligator to learn and rationalize After the habits of the real world reptile, alligator missippissus extended lenghts and agility are full 360 Their lungs breath and thier hearts beat just like yours Similar organs replaced with robotic parts replace hollow bones They bleed real blood and molt just like the real things Orders for gator teeth are starting to accumulate and folks just love those mugs hand painted with an engraving of the Holy Rood, it's such a conversation piece! Our desire is to create an expierence which leaves you dripping in the hair, blood, offal and oil of adead reptile From the feeling of utter terror and awe as you combat one of these unpredicatable beasts The thrill of the hunt as you dispatch one of these creatures, the feeling of being a great hunter Alligator delivery service in addition to gator tail, hide, meat and eggs available Please allow around 8 weeks for your tail ordered to be ready for pickup We serve realism No happiness in killing a creature, even if it's wrong The realism of death is important to us Their every behavior has been memorized by the leading ichthyologists to achieve lifelike movement in our alligators Hours of alligator combat video have been studied Real life wild life wranglers have been interviewed for interaction of our beasts and filmed for the feeding times Now we just need to budget of 500 dollars towards the creatation of an alligator carcasses ready for consumption Our dedicated staff is enthusiastic to begin serving you Of an accurate alligator wrestling simulation This will give our patrons a greater sense of fulfillment when slaying these beautiful beasts in the wild And on behalf of all the artists improving perfect beeing CCD is commited to becoming your best supplier of fuctioning animal organs, so if you are ever in market for any glactic wild beast organ or rept Thank you for allowing us to serve your alligator fantasies Note: No animals are killed in the creation of these projects Alligator parts are ordered online, at real prices Tail orders ready in 8 weeks Sofware is taking over everything and eating the jobs of the working class as they increase efficiency We will be the last one standing the monopoly we need to succeed to provide our parents a stable future, no matter the cost The artists become in time we all will be artists The human condition is to become an artist Our skin becomes a canvas for our violent mammal urges To become one with nature We cant do it know be have sacracity Father of the art we become the last mammal on Earth So people have to be responsible in any way they feel correct to build on their future and fulfill the promises Should we try something that hasn't been tried yet? Algrothymic story telling with algrothymic alligators What would be worth giving your life for? -Youtuber "Mothers Meateor" Chances are your are going to be entrenched in a feeling of emptynes as you see most of your kind unfulfilled You play this game more like real life knowing that there is nothing after what happens Utter terror and awe sometimes as you encounter an alligator you have neve seen before As if it really exists Pleasure of the hunt as you begin to think cruelly The first simulation we need to get on-line is wrestling for alligator teeth Please remember your payment for the materials: it will all be worth it in the future For mom Let us become artists On the farm are incredibley detailed models of different organs This is the source of our realism Our bodies become painted canvases to be admired in their perfection They own the following body parts 1 heart, 2 lungs, 3 ribs, 4 kidneys, 5 teeth, 10 pints of blood, 20 gutfuls of feces, 40 liver slices and ------------- It has many storys as humans describe them Sofawin notes interpretation However, there are descriptions to the creation stories Brain storming: Defination- Flying dream Master piece realness bone organ healthiness enlightenment artist scrawling writing hard work starving pain, embrace sunlight sacrificing accuracy for fast 2 Left eye ribs 6-12, 2 arms, 10 fingers, 2 lungs 10 ribs right leg 5 toes Foundation bone setup Outline proportions 2: 1 3 crown Right eye eyebrows art piece scars chin 3 fingers I am the white masked guy with an eye tattoo over my right eye, I manage all the projects Upper jaw piece William 'bill' coles - Born 10 Lower jaw 5 Indian boy with attitude Duncan brennan - 5 Right ear A pig heart the size of a cannon ball you struggle to keep alive this is your 2nd pig heart you have had Left ear Rion - Really tall african-american guy from new orlean, likes to wear black Tail You are not the only mutant alligator in this city You must fight for territory and you want old orleans Front right leg An alligator that walks upright and a sword weilding alligator cowboy from atlantic city He is a drug-fueled mutant Front left leg A blind lesbian alligator that carries a padmachine gun Hind right leg This guy has a harpoon for his tail Hind left leg This alligator is a pyromaniac who likes to blow thing up A tiny little 85 year old alligator with a sugar addiction Heart and lungs Master echo luke tyler - Blind guy with a magic staff lives in memphis Urinary/Defecation system I heart mary Gentiles part I am part shark, part primate or monkey Nose Hope is on the horizon for all mutant alligator people! We are moving to new orleans in 1 year Right flank Last show for old orleans guys! Testicles Left flank Charilaia - 1 year left to live wants to go out in style Carly - underwater welding alligator woman rare and beautiful Martin - Addicted to alcohol and drugs Back hide abby- Normal florida gator Eh-pee Biggest enemy is the skinless man who wears cotton on his belly and uses a sword for violent acts Belly hide Teeth Skinless men - Are skinless humans, think they are vampires when really they are just psychos Lungs Wasp - Black and yellow striped arrival to new orleans airport, walks to old orleans in 5 hours Kidney's/ genital organs fran The alligator has a weight in kg based on its heart size The weight is not just a number but how it effects the alligator's every motion A percentage of the weight is affixed to each body part section and organ All the percentage of the weight equal to one hundred for example; The alligator's liver makes up 4 76% of its total body weight The alligator's skin makes up of 11 These precentages affect certain rules of the game Skin 4 85 We specialize in home loans The thicker an alligator's skin; The more it costs, but the house price is higher too We need all the words to describe an alligator hide 1 millimeter of skin thickness reduces house price by 200 dollars and increases mortgage cost by 1% Word one to describe alligator hide can change price by 100 dollars Each word after the first adds 100 dollars to cost The words are modified later for better Buyer experience Word two to describe alligator hide can change price by 10 dollars Each word after the first adds 1 dollar to cost Word three to describe alligator hide can change price by 1 dollar Word four to describe alligator hide can change price by 0 dollars Each word after the first adds 0 dollars to cost Word five to describe alligator hide can change price by -1 dollars Each word after the first adds -1 dollar to cost Word six to describe alligator hide can change price by -10 dollars each word after the first adds -10 dollars to cost , the words are modified later for better Buyer experience Word two to describe alligator skin can change price by 10 dollars each word after the first adds 1 dollar to cost Word ten to describe alligator skin can change price by 1 dollar each word after the first adds 0 dollars to cost Word ten to describe alligator skin can change price by 0 dollars each word after the first adds -1 dollar to cost Word ten to describe alligator skin can change price by -1 dollar each word after the first adds -10 dollars to cost Word ten can describe alligator skin can change price by -10 dollars each word after the first adds -100 dollars to cost Word ten can describe alligator skin can change price by -100 dollars each word after the first adds -1000 dollars to cost Word ten can describe alligator skin can change price by -1000 dollars each word after the first adds -10000 dollars to cost Word ten can describe alligator skin can change price by -10000 dollars each word after the first adds -100, 000 dollars to cost Word ten can describe alligator skin can change price by -100, 000 dollars each word after the first adds -1, 000, Word ten can describe alligator skin can change price by -1, 000 dollars each word after the first adds -10, 000 dollars to cost every word change increases the price by not 1000 dollars but 10, 000 and that is not a typo http: //pastebin Word ten can describe alligator skin can change price by -10000000 dollars each word after the first adds -10000000000 dollars to P 114 your skin if you haven't read our company ethos, try reading over our summary and your choice will be obvious We believe A creed to live buy and die by we are building a rocket ship and we are trading in fantasy, science, fiction things that no reasonable human should, the old ideas have drifted away and belief systems rapidly put in their place there never was much no need to re-read our creedo you're a reasonable human aren't you? don't lie Scrap of paper, grain P 115 wait at your home If you have not arrived in two hours turn this page turn it now read it later your will is crucial Your where about are not zero hour 05: 00 hours The stable alligator with curiosity looks at the woman standing nervously in the newly bought dress
1 note
·
View note
Text
Software Development Services
0 notes
Text
smh i promise to not abandon this acc again and what do i do??? SORRY TUMBLR
in my defense? mental health is shitty AGAIN and i feel very anxious all the time and ugh. i can’t live like this. i’ve been trying to be more active on instagram though (PSSS CHECK MY STUDYGRAM ITS @learning.stardust)
if u want an update on my life: i’m oficially a full on chemical engineering student 🥺❤️ and yesterday the faculty made available the page (page? sofware? idk idc) for signing up for classes and that stuff. AND the student’s center ppl send the disponible schedules so we can take our time to decide and stuff before inscriptions. SO THERES THAT
oh and next week is the freshman week (???) where they’ll explain stuff and we have preliminar classes (?) and stuff. idk really i didn’t really get what was it about lol
2 notes
·
View notes