#Enterprise Architecture
Explore tagged Tumblr posts
Text
Starting Your Journey as an Enterprise Architect?
Your first week can define your future success. Our comprehensive guide outlines practical, easy-to-follow steps to quickly understand your new role, build strong relationships, and demonstrate immediate value to your team.

Take charge from day one! 👉 https://www.advisedskills.com/blog/enterprise-architecture/your-first-week-as-an-enterprise-architect-tips-to-hit-the-ground-running
#EnterpriseArchitect #CareerTips #AdvisedSkills #ProfessionalGrowth
2 notes
·
View notes
Text
The Zachman Framework: The Granddaddy of Modern Enterprise Architecture
🏛️ From 1987 to Today: How One Framework Shaped the Entire Field of Enterprise Architecture Ever wonder why today's enterprise architecture frameworks all feel somehow... familiar? I've just published an article on the history of the Zachman Framework!
Picture this: It’s 1987. The first Zelda game just hit shelves, The Simpsons made their TV debut, and somewhere in the tech world, a revolutionary idea was taking shape that would influence enterprise architecture for decades to come. Enter the Zachman Framework. The Family Tree of Enterprise Architecture If enterprise architecture frameworks were a family, the Zachman Framework would be the…
#agile#architecture#Enterprise Architecture#IT Strategy#solution-architecture#technology#TOGAF#Zachman
2 notes
·
View notes
Text
Adapt or be Left Behind: Integrated EA as Strategy
In the rapidly evolving landscape of contemporary business, the strategic significance of Enterprise Architecture has become increasingly prominent. Historically perceived as a discipline rooted in the realms of information technology, EA has undergone a transformative journey, emerging as an indispensable strategic enabler within organisations. This evolution is not just a reflection of EA’s…

View On WordPress
#Business Strategy#Enterprise Architecture#Organisational Change#Technology Leadership#Transformation
2 notes
·
View notes
Text
The Role of Enterprise Architecture in Fostering Innovation
Aligning Business Goals with Technological Initiatives Enterprise Architecture can play a pivotal role in fostering innovation by providing a structured approach to aligning technology with business goals. Through Enterprise Architecture, an organisation can ensure that their technological initiatives are not only advancing but also tailored to support and enhance business objectives, driving…
0 notes
Text
Insider threats aAmplified by behavioral analytics
New Post has been published on https://thedigitalinsider.com/insider-threats-aamplified-by-behavioral-analytics/
Insider threats aAmplified by behavioral analytics

In the realm of cybersecurity, behavioral analytics has emerged as a powerful tool for detecting anomalies and potential security threats by analyzing user behavior patterns.
However, like any advanced technology, it comes with its own set of risks—particularly when it comes to insider threats. The very data and insights that make behavioral analytics so effective can also be leveraged by malicious insiders to amplify the damage they can inflict.
How behavioral analytics works
Behavioral analytics tracks user activities—such as login times, access patterns, file usage, and communication habits—to establish a baseline of “normal” behavior.
When deviations from this baseline occur, the system flags them as potential security concerns. This method is particularly useful for identifying sophisticated attacks that bypass traditional security measures.
The double-edged sword of behavioral analytics
While the ability to detect deviations in user behavior is invaluable for cybersecurity, it also presents significant risks if the data and insights generated by behavioral analytics are misused. This is where the danger of insider threats is magnified.
1. Informed malicious insiders:
One of the most significant risks comes from insiders who have legitimate access to behavioral analytics data.
These individuals, whether they are disgruntled employees, compromised insiders, or even careless users, can gain deep insights into what triggers security alarms and how the organization’s monitoring systems operate.
With this knowledge, they can tailor their malicious activities to avoid detection, effectively bypassing the very systems designed to protect the organization.
2. Targeted attacks on individuals:
Behavioral analytics can provide detailed profiles of individual user behavior, including patterns of communication, resource access, and even response times to certain stimuli.
A malicious insider could use this information to target specific individuals within the organization, exploiting their known habits or routines to craft more effective phishing attacks, social engineering schemes, or even direct sabotage.
3. Bypassing security controls:
By understanding the thresholds and triggers of the organization’s security systems, an insider can engage in malicious activities that remain within the bounds of “normal” behavior.
This might involve gradually escalating privileges, exfiltrating data in small increments, or even altering their behavior to blend in with other users who have similar access levels. Over time, these activities can accumulate into significant security breaches without ever raising a red flag.

4. Collusion with external actors:
The risk is further exacerbated if an insider collaborates with external attackers. An insider could share behavioral analytics data with these external actors, allowing them to tailor their attacks to the specific weaknesses of the organization. This kind of collusion can lead to highly sophisticated, multi-vector attacks that are difficult to detect and mitigate.
5. Privilege escalation and abuse:
Behavioral analytics might also reveal patterns in how privileges are granted and used within an organization. A savvy insider could exploit these patterns to gradually escalate their access rights or to gain unauthorized access to sensitive data. Once inside, they can operate with impunity, knowing how to avoid detection based on their understanding of the system’s monitoring capabilities.
Mitigating the risks
To mitigate these amplified risks, organizations must adopt a multi-faceted approach:
Strict access controls: Limit access to behavioral analytics data to only those who absolutely need it and ensure that this access is regularly audited.
Advanced monitoring: Implement monitoring systems that are specifically designed to detect anomalies in insider behavior, particularly those with access to sensitive data or analytics tools.
Data encryption and masking: Secure behavioral analytics data with robust encryption, and consider data masking techniques to limit the exposure of sensitive information.
Zero-trust architecture: Adopt a zero-trust model that continuously validates trust at every stage, ensuring that even insiders are subject to rigorous scrutiny.
Security awareness training: Regularly train employees on the importance of security, with a specific focus on the dangers of insider threats and the critical role behavioral analytics plays in cybersecurity.
Generative AI from an enterprise architecture strategy perspective
Eyal Lantzman, Global Head of Architecture, AI/ML at JPMorgan, gave this presentation at the London Generative AI Summit in November 2023.

Behavioral analytics is a powerful tool in the fight against cyber threats, but it is not without its risks. The amplification of insider threats through the misuse of this technology is a real and present danger.
By understanding these risks and implementing robust security measures, organizations can harness the benefits of behavioral analytics while minimizing the potential for it to be used against them.
In an age where the insider threat is increasingly recognized as one of the most significant security challenges, a proactive approach to safeguarding behavioral analytics data is not just advisable—it’s essential.
Your guide to LLMOps
Understanding the varied landscape of LLMOps is essential for harnessing the full potential of large language models in today’s digital world.

#2023#ai#ai summit#AI/ML#Analytics#anomalies#approach#architecture#Artificial Intelligence#attackers#awareness#Behavior#communication#craft#cyber#Cyber Threats#cybersecurity#data#detection#double#employees#encryption#engineering#enterprise#Enterprise Architecture#exploit#Fight#focus#Full#generative
0 notes
Text

Modern organizations may improve client interactions, increase revenue, and streamline operations with the help of Microsoft Dynamics 365 CRM. Its integrated platform handles customer support, marketing, and sales interactions with ease. Microsoft Dynamics 365 CRM uses automation, analytics, and artificial intelligence (AI) to increase corporate agility, optimize processes, and boost customer interaction. This Flexible Solution encourages team cohesiveness throughout your company and supports data-driven decision-making for sustained success, spend money on Dynamics 365 CRM.
#customer relationship management#erp software#fusion5#corporate performance management#cpm tools#ibm cloud#crm systems#netsuite#enterprise architecture#erp system in new zealand#microsoft dynamics 365 crm
0 notes
Text
TOGAF 10 Training and Certification Course – Master Enterprise Architecture Framework
Advance your career with the TOGAF 10 Training and Certification Course, designed to help professionals master the globally recognized enterprise architecture framework. This comprehensive course covers the latest version of TOGAF, providing practical insights, tools, and techniques for implementing enterprise architecture. Whether you're a business architect, IT professional, or project manager, this course equips you with the skills needed to drive business transformation and align IT strategies with business goals. Gain your TOGAF 10 certification and enhance your expertise in modern enterprise architecture.
0 notes
Text
Technology Hits: New Submission Guidelines - 2024
Technology Join a unique publication supporting writers penning about technology to find a broad audience using the power of ILLUMINATION on Medium. Dear Writers and Readers, Coming from a technology and science background, I have a strong affinity for technology writers and tech topics on multiple platforms. I enjoy reading their stories, but I also like reviewing, curating, and promoting…
#business#Business Architecture#Dr Mehmet Yildiz technologist#Dr Yogesh Kulkarni as lead editor#Enterprise Architecture#entpreneurship in technology#Hardware enginnering#Medium#Self Improvement#software architecture#Sofware engineering#substack#Sylvain Zysman#Tech Startup#technology#Technology Excellence#Technology for Startups#technology Hits on Medium#Technology Hits on Substack#technology leadership#writers#writing#writingcommunity
0 notes
Text
Optimizing Enterprise Architecture Initiatives: Partnering Model and Essential Stages
In the ever-evolving landscape of enterprise architecture, the journey from discovery to implementation is a complex yet rewarding process. Through this process there are critical phases of this journey, with every portion focused in how you partner with your teams. Join me as we navigate through these essential stages, offering insights and best practices to ensure your enterprise architecture…
View On WordPress
0 notes
Text
Real-World Application of Data Mesh with Databricks Lakehouse
Explore how a global reinsurance leader transformed its data systems with Data Mesh and Databricks Lakehouse for better operations and decision-making.
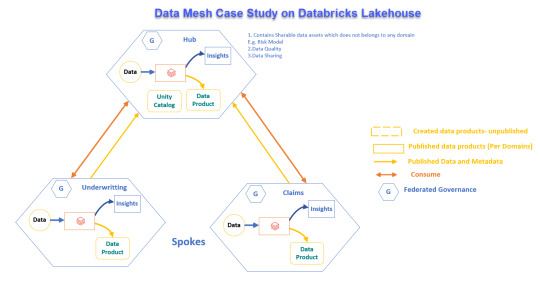
View On WordPress
#Advanced Analytics#Business Transformation#Cloud Solutions#Data Governance#Data management#Data Mesh#Data Scalability#Databricks Lakehouse#Delta Sharing#Enterprise Architecture#Reinsurance Industry
0 notes
Text






ADVANTAGE OF Enterprise Architecture
“Unlock Your Career Potential: Enroll Now with Certera for Accelerated Growth!”
Visit our website for more information or to explore the courses.
Follow us on LinkedIn, X, YouTube and Instagram.
0 notes
Text
What Makes Open Agile Architecture™ So Powerful?
Curious how Open Agile Architecture™ helps organizations thrive in a fast-changing world? In this article, we dive into the 10 core principles-from modular thinking to customer centricity-and explain how they support agility, innovation, and scalability.

💡 Whether you're an architect, strategist, or agile leader, this breakdown is a must-read.
👉 Explore the full article: https://www.linkedin.com/pulse/understanding-core-principles-open-agile-architecture-advisedskills-qcdrf/
#open agile architecture#digital strategy#enterprise architecture#advised skills#advisedskills#agile transformation
1 note
·
View note
Text
How to Build an Effective Cloud Organization
#ai#azure#Cloud#Cloud Architecture#Cloud Operating Model#cloud-computing#Enterprise Architecture#IT Strategy#Michael Griffin#Solution Architecure#technology
0 notes
Text
New Episode of Enterprise Architecture Radio out...! We noticed in 2023 that slowly people are moving away from the digital life. The life where they spend hours and hours of unproductive time on the digital screen. Humans have slowly started realizing that life outside the digital world is more satisfying.
YouTube: https://lnkd.in/gKkrUecX
Apple Podcasts: https://lnkd.in/gtk5ehja
Spotify: https://lnkd.in/gxFz2mSx
Amazon Music: https://lnkd.in/gkc5D6nb
Google Podcasts: https://lnkd.in/g895aKRw
Podbean: https://lnkd.in/gYJuyiVR
-------------------------------------------------------------
LinkedIn: https://lnkd.in/gG4q7WDt
Twitter: @EntArchRadio
Email: [email protected]
Telegram Group: https://lnkd.in/gSGp9v-a
#Entarch #EnterpriseArchitecture #TechTrends2024
0 notes
Text
Understanding the Role of Information Architecture in Enterprise Architecture
In today’s rapidly evolving digital landscape, organizations, whether large or mid-sized, need to navigate a complex web of data and technology. To effectively manage this complexity and ensure that their operations run smoothly, they often rely on robust Enterprise Architecture (EA) practices. Within the realm of EA, one crucial aspect that plays a pivotal role is Information Architecture (IA).…

View On WordPress
0 notes
Text
Adobe introduces AI-powered eraser to Lightroom
New Post has been published on https://thedigitalinsider.com/adobe-introduces-ai-powered-eraser-to-lightroom/
Adobe introduces AI-powered eraser to Lightroom

Say goodbye to photobombs.
Adobe is introducing an AI-driven Generative Remove feature to its Lightroom photo editor. This feature simplifies the removal of unwanted elements like that annoying person in the background. Currently in public beta, it works seamlessly across the Lightroom ecosystem on mobile, desktop, and web platforms.
Streamlined editing with Firefly AI
Lightroom’s Generative Remove effortlessly replaces unwanted elements using Adobe’s Firefly AI engine. Paint over the area you want to remove, and Lightroom sends this information to Adobe’s Firefly servers, which process the data and return the edited image.
In contrast to Adobe Photoshop’s Reference Image feature, which allows users to generate new images using Firefly, Lightroom’s AI enhancements are designed to streamline a photographer’s workflow.
Tackling complex edits with ease
Removing distracting elements from images is often challenging. Traditionally, tools like Lightroom’s Content Aware Remove match surrounding areas to hide elements. While effective for simple backgrounds, this method becomes cumbersome for larger objects or complex backgrounds.
The Firefly-powered Generative Remove excels at handling larger objects against any background, reducing what once took hours and technical expertise to a quick and easy task. Lightroom now empowers everyone to be an editing wizard. Moreover, Generative Remove offers three different versions of the edit, letting you choose the best one.
Comparing to Google’s Magic Eraser
Although Generative Remove is impressive, it might seem familiar to users of Google Photos. The new features are similar to Google’s Magic Eraser tool and do not offer the same capabilities as Google’s Magic Editor, which can alter scene lighting or rearrange subjects.
Adobe’s Generative Remove reflects the company’s ongoing approach to AI, as seen with last year’s AI-powered noise removal tool. These enhancements build on existing tools, providing practical improvements rather than groundbreaking new features.
This focus on better tools over flashy innovations likely aligns with what working photographers seek. Adobe appears content to let others handle more dramatic AI-powered capabilities, like post-capture scene rearrangement.
Want to know more about generative AI? Read the article below:
Generative AI from an enterprise architecture strategy perspective
Eyal Lantzman, Global Head of Architecture, AI/ML at JPMorgan, gave this presentation at the London Generative AI Summit in November 2023.


Like what you see? Then check out tonnes more.
From exclusive content by industry experts and an ever-increasing bank of real world use cases, to 80+ deep-dive summit presentations, our membership plans are packed with awesome AI resources.
Subscribe now
#2023#adobe#ai#ai summit#AI-powered#AI/ML#approach#architecture#Article#Artificial Intelligence#background#Capture#content#data#desktop#easy#Editing#engine#enterprise#Enterprise Architecture#Features#focus#generative#generative ai#Global#Google#images#Industry#innovations#it
0 notes