#Telephone Access Control System
Explore tagged Tumblr posts
Text

Secure your home and business with the trusted experts in surveillance! As a SIRA-approved CCTV company in Dubai, we provide cutting-edge security solutions tailored to your needs. From advanced camera systems to seamless installation and maintenance, we ensure your property stays protected 24/7. Choose the company that Dubai trusts for safety and reliability.
#cctv camera#cctv installation#cctv installers#dubai#safety#access control system#gate automation#telephone system#led wall#gps tracker#pa system
0 notes
Text
#it products suppliers in dubai#cable supplier in dubai#telephone supplier in dubai#dell distributor in dubai#cctv camera supplier in dubai#server supplier in dubai#itproductssuppliersindubai#access control systems in dubai
0 notes
Text
Dungeon Meshi Chapter 82
This chapter is so short that it doesn't have a title image.
In ancient times, people sought to draw on infinite power by connecting to a dimension where infinity exists. While their efforts succeeded, they also drew the attention of demons from that dimension. The demons would grant people's wishes but also consume their desires to grow stronger. The ancients bound the demons to dungeons to contain them.
The ancient war between the elves and dwarfs preceded the Golden Kingdom being swallowed into a dungeon. The castle was built on top of the ruins of a Dwarf city that was later turned into an outpost by the elves.
At the time the dungeon was created, maybe the elves and dwarfs were still at war, or maybe they'd come to peace. Maybe the shorter-lived races, tired of being caught up in these fights that would last their entire lives, opted to stand in between the long-lived races and force peace.
Whatever the case, the land between where the elves' and dwarfs' influence collide became a kingdom of Tall-men. This kingdom thrived thanks to having easy access to both Elf and dwarf technology. Then one day, it vanished entirely.
The island has been controlled by many races. It's had many names given to it by elves, dwarfs, and Tall-men. These days it is simply called "The Island" because most of its names have been forgotten.
For Tall-men and other short-lived races, these are myths and stories of ancient times. They are tales that have been passed down generations and each retelling has some bits of embellishment, alteration, or omission to the point that no one is entirely certain what the original tale was nor is anyone certain about the origin of it.
For the long-lived races, especially elves, these are war stories your grandparents told you. You sat in front of them and listened as they recalled what happened, and you watched in horror as they began reliving what happened. You looked in their eyes and their eyes looked at you, but you knew they weren't looking at YOU. And you knew that these stories were true no matter how fantastical they sounded.
The dungeon was discovered six years ago. But the long-lived races probably knew about it for centuries since the disappearance of the Golden Kingdom was still burned in their memories. A wish that could vanish a kingdom must have created a particularly powerful and mana-rich dungeon so the island left behind would be a highly valuable resource asset.
But at some point, the elves gave the island to the Tall-men to govern. Perhaps the elves realized the dangers of trying to take over dungeons and realized that the island's dungeon would be better off sealed away and forgotten. And letting a race who would have long-forgotten what happened would be the best stewards.
Now let's talk about this chapter.
The elves, dwarfs, and gnomes have all been working together to monitor the island it turns out. The elves have taken direct charge of investigating the island, but the dwarfs and gnomes have been keeping tabs as well.
I want to assume that Utaya inspired them to come together for this. The demon of Utaya very nearly broke out of the dungeon and the elves were only barely able to contain it. Then a few years later, a dungeon that's been sealed for 1,000 years which contains the entirety of a lost kingdom is discovered.
If the demon would make another attempt to escape the dungeon, the island would be its best shot. So the elves decided they need to work with the dwarfs and gnomes to monitor the dungeon and contain the demon when it tries to escape.

Seriously? They're dressed like lawn ornaments?

I love the contrast between their long-range communication systems. The elves are using fairies, the gnomes are using a crystal ball, and the dwarfs are using a telephone.



The phone is wireless so however these long-range communications work, it works the same way. How wild would it be if there were radio and cell phone towers around the world to support these communication spells. Dwarf infrastructure probably has something like that at least. And then there would have to be the necessary logistics to ensure someone can't hijack, listen in, or alter any messages.
Is this what it was like when the Utaya dungeon ripped open?

What must it be like to see from a distance a great tragedy or grand historic event about to happen? What would this child tell decades from now if asked what she was doing when all this happened? She saw the land rip open, the soldiers boarding ships heading to the island, and the moment the giant serpent heralding the beginning of the end rose from the island. And after seeing all that, she went home, told her parents, and then helped her mom with the laundry.
back
14 notes
·
View notes
Text

House of Huawei by Eva Dou
A fascinating insight into a Chinese telecoms giant and its detractors
Huawei is not exactly a household name. If you’ve heard of it, you either follow the smartphone market closely – it is the main China-based manufacturer of high-end phones – or else consume a lot of news, because the company is at the centre of an ongoing US-China trade war.
But this enormous business is one of the world’s biggest producers of behind-the-scenes equipment that enables fibre broadband, 4G and 5G phone networks. Its hardware is inside communications systems across the world.
That has prompted alarm from US lawmakers of both parties, who accuse Huawei of acting as an agent for China’s government and using its technology for espionage. The company insists it merely complies with the local laws wherever it operates, just like its US rivals. Nevertheless, its equipment has been ripped out of infrastructure in the UK at the behest of the government, its execs and staffers have been arrested across the world, and it has been pilloried for its involvement in China’s oppression of Uyghur Muslims in Xinjiang.
Into this murky world of allegation and counter-allegation comes the veteran telecoms reporter Eva Dou. Her book chronicles the history of Huawei since its inception, as well as the lives of founder Ren Zhengfei and his family, starting with the dramatic 2019 arrest of his daughter Meng Wanzhou, Huawei’s chief financial officer, at the behest of US authorities.
Dou’s command of her subject is indisputable and her book is meticulous and determinedly even-handed. House of Huawei reveals much, but never speculates or grandstands – leaving that to the politicians of all stripes for whom hyperbole about Huawei comes more easily.
At its core, this book is the history of a large, successful business. That doesn’t mean it’s boring, though: there’s the story of efforts to haul 5G equipment above Everest base camp in order to broadcast the Beijing Olympics torch relay. We hear about the early efforts of Ren and his team, working around the clock in stiflingly hot offices, to make analogue telephone network switches capable of routing up to 10,000 calls; and gain insights into the near-impossible political dance a company must perform in order to operate worldwide without falling foul of the changing desires of China’s ruling Communist party.
Dou makes us better equipped to consider questions including: is this a regular company, or an extension of the Chinese state? How safe should other countries feel about using Huawei equipment? Is China’s exploitation of its technology sector really that different to the way the US authorities exploited Google, Facebook and others, as revealed by Edward Snowden?
Early in Huawei’s history, Ren appeared to give the game away in remarks to the then general secretary of the Communist party. “A country without its own program-controlled switches is like one without an army,” he argued, making the case for why the authorities should support his company’s growth. “Its software must be held in the hands of the Chinese government.”
But for each damning event, there is another that introduces doubt. The book reveals an arrangement from when Huawei operated in the UK that gave GCHQ unprecedented access to its source code and operations centre. US intelligence agencies seemed as able to exploit Huawei equipment for surveillance purposes as China’s. While Huawei’s equipment was certainly used to monitor Uyghur Muslims in Xinjiang, it was hardware from the US company Cisco that made China’s so-called Great Firewall possible.
Anyone hoping for definitive answers will not find them here, but the journey is far from wasted. The intricate reporting of Huawei, in all its ambiguity and complexity, sheds much light on the murky nature of modern geopolitics. The people who shout loudest about Huawei don’t know more than anyone else about it. Eva Dou does.
Daily inspiration. Discover more photos at Just for Books…?
12 notes
·
View notes
Text
gonna have to miss another update- between back-to-back work meetings until 7pm, an art telephone entry i had to finish, and a planning session for the World of Darkness game i'm in, today was a day with zero room to maneuver
incidentally look at how bonkers the planning my WoD GM does is:
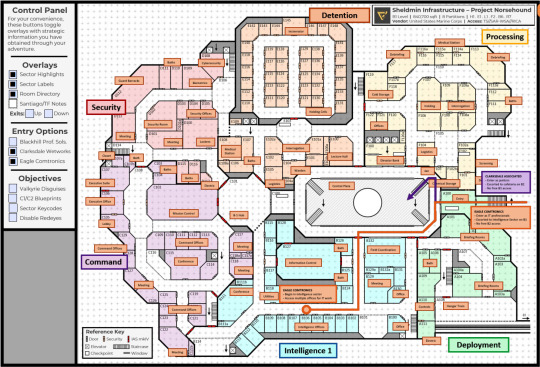

i have never seen any GM prepare an interactive PDF of the map before. this isn't even the entire base we're infiltrating! this is just the first two floors we have blueprints for! part of our mission is finding blueprints for the lower floors so we can make a second plan for getting through there so we can heist our pet pig back from the government! and this isn't even the only handout- there's like, documents on the magic system, documents on Valkyrie's classification hierarchy, documents on all the third-party contractors the base deals with- every fucking document we might lift from anywhere is an actual handout he prepared and formatted because his sessions are more real than reality.
some of the planning we did from several days ago:
Phase 1: Entry -> Paragon Access
Relm poses as an Eagle tech and heads to the Intelligence sector to try to sabotage Brunn data and frame Capricornus.
I pose as a Clarksdale janitor, find a bathroom, and teleport the rest of the team inside via Levi's chalk circle.
We either find a good pre-mealtime window or make a distraction to clear the kitchen by setting off the kitchen sprinklers via the electrical closet, and Levi and I make a hole in the left wall.
I head inside, wait until I don't hear anyone in the server room, and then leave the closet and install the covert USB connection on the server.
I return to the closet and upload our Bifrost data, and begin trying to acquire a cybersecurity account.
In the meantime, Levi, Raya, and Fed explore the accessible areas in search of Pierce, Davidson, or Stern. If they find one, they get within 10 yards and activate one of my magic card cloners to copy their keycard.
If possible, they swipe Davidson's laptop and get the keycodes in case I fail the hacking.
They also search for an unattended computer terminal, in case I succeed and get the cybersecurity account. If I do, someone uses the account creds to acquire the sector keycodes.
Phase 2: Paragon Access -> C-level
Someone with Personnel access (probably just about anyone, there's no specific uniform for being in the Personnel sector) heads to the Laundry room in H232 to obtain five uniforms matching our Bifrost access, and applies patches.
If we don't yet have override keycards, someone with a Command-access Bifrost and an appropriate uniform enters the Command sector and attempts to clone Pierce's keycard.
While there, they enter C102 Mission Control and take pictures of the C-level floorplans on the monitors.
Optionally, search for more Brunn records to sabotage somehow, if they can get away with it cleanly.
Someone else with Security access can try the same thing with the Security sector, in case Pierce is elsewhere. C-level floor plans available in D102.
Meanwhile, if we got the keycodes through a successful hack and have cybersecurity admin access, someone injects Towerfall's trojan into the system to disable the Redeye status indicator. (I believe this is with the Rubber Ducky?)
Otherwise, someone's going to need to look into rewiring the Redeye system to report an all-clear despite the alarms going off. Probably difficult so let's hope the other plan worked.
If we're missing any uniforms from Laundry, someone should head to the locker rooms in search of a suitable replacement.
Once we've obtained an appropriate keycard, someone with Systems access goes to K203 and disables the Redeye system with the override.

tonight was a voice call where we found all those holes and desperately tried to patch them. we patched... some of them. we are extremely going to get caught and possibly killed by the MIB. jesus fuck.
8 notes
·
View notes
Text
[draft]
Neo France is a country divided into 4 distinct, legally-mandated technological zones.
High-tech zones have advanced tissue engineering and cybernetics industries. They have VR implants. Their primary source of electricity is fusion power.
In Mid-tech zones, personal computers are limited to an 800 Mhz single-core processor and a maximum screen resolution of 800x600 pixels. Internet access is 56kbps. The primary sources of electricity are solar and hydroelectric with battery storage. Vehicles use biofuel. There are cellphones, but no smartphones. Think 1990s.
Low-tech zones have landline telephones and telegraphs. Vehicles are limited to wood, charcoal, or biofuel steam power. Maximum vehicle speed for cars and trucks is 30 mph (horse speed).
Wilderness zones don't allow for permanent human settlement. They are mandated by Meta-EU regulations to ensure a proper biological balance (such as oxygen) as well as wildlife survival.
Additionally…
A high-tech hospital may be built in any zone. Airlifts for hospitalization are exempt from vehicle controls.
The citizens of Neo France may move between any of the zones. They are not required to live in any one zone. There may be border checkpoints which check for prohibited technologies when moving between the zones.
Neo France is one country, and they all speak French.
Each zone has its own currency. There is a 10% redistributive income tax between the zones, based on primary residence. The exception is the wilderness zone.
Roads or railroads may cross zones in order to allow access.
The rationales provided for the technology level system include…
Production Chain Resilience: Preservation of less efficient but more robust production chains, to ensure continued supply of critical goods in the event of a global economic disruption.
Reduced Stimulation: Creation of zones with a lower flow rate of information, to prevent overstimulation, as well as reduced surveillance.
Cultural Production: The additional friction in the transmission of information allows for ideas to range farther away from the global currents before resynchronization.
How should Neo France be arranged?
A: Linear. Each zone is one big block, setup in a line from high-tech to low-tech. Each zone will therefore be a rectangle.
B: Rotational. Each zone is one big area, rotated around a central point. This is a very compact approach, with little travel time between zones.
C: Concentric (high to low). The most high-tech zone is in the center. It is surrounded by the mid-tech zone. The mid-tech zone is surrounded by the low-tech zone. The wilderness area is on the outside. This would make lower-tech zones narrower, but much longer, optionally creating an illusion of a much larger low-tech area if moving around the center rather than through the center.
D: Concentric (low to high). The high-tech zone is on the outside. The wilderness zone is a single compact area in the middle. The mid-tech and low-tech zones are in-between.
E: Archipelago. "Islands" of high-tech zones are surrounded by mid-tech zones, in a "sea" of low-tech zones and wilderness areas.
F: Swiss Cheese. A reverse archipelago. High-tech zones form a web connecting the whole territory. Multiple "lakes" of mid-tech zones, surrounding low-tech zones, surrounding wilderness areas, are situated throughout the country.
2 notes
·
View notes
Note
Any starting points or basic tips for someone who's never made a resume/CV? I don't really qualify for the jobs that ask for one instead of blindly hiring online (no completed education past high school level, only worked entry-level jobs) but it doesn't hurt to learn corpospeak just in case lol
I'll give an example! I once worked as a cashier in a Chinese restaurant and it was the most BASIC shitty job (didn't even have an electronic till and i sat with my feet up most of the time lmao) but on my CV the recount for said job read something like:
Customer Services (Restaurant): As part of my role within this establishment, I took lead responsibility in managing orders and ensuring that customers were satisfied with their purchases across both telephone and physical consultations. I also controlled the financial aspects of said purchases while ensuring that all transactions were recorded in an easy-to-access system which made tracking of orders more efficient. In terms of interpersonal relationships, I was responsible for developing and maintaining a consistent line of communication between front of house and back of house staff to make certain that all workers were up-to-date with necessary information. Due to the fast-paced nature of this role, I was consistently prepared for a shifting workload and this flexibility is a skill I have transferred across all aspects of my work ethic.
Sometimes, I think the best way to think about it is to consider every aspect of the work you have undertaken and morph that into how it would benefit the job you are applying for. If it's a very people-heavy job then focus on communication and interpersonal skills while if its more of an office job then the focus should be more on technical and practical skills etc.
7 notes
·
View notes
Text
Ritual magic in fantasy: a small rant
It's fine when writers use the standard trappings of a genre without detailing the underpinnings of the worldbuilding - we can take it for granted, we don't need it explained again every time, not everything needs a new plot twist. Tropes are tools; wizards are part of the grammar of fantasy and don't need their definition explained at the start of every book.
It's fine when writers skip the underpinnings entirely, and treat the wizards as convenient plot devices for the hero to go do something or be somewhere. Some munchkins will say "but then why couldn't the wizard solve the entire plot?" and I say to them "if what you want to read is a list of wizardly constraints, put down the novel and go play D&D". ;^)
But it bugs me when writers seemingly forget that the underpinnings ever existed and act confused as to how the trappings work with no underpinnings. This strikes me as both lazy and ignorant. It's the mark of a writer who is cribbing standard fantasy tropes and hasn't taken the time or effort to understand why those tropes were like that in the first place, and also is poorly read, not having seen the original explanation (nor any of its variations), only the superficial tropes among other people cribbing those same tropes in a game of telephone and losing the underpinnings along the way.
Today I want to talk about ritual magic and the mages doing it. Rituals are for someone; freestanding rituals make no sense!
I've written before on how one of the features that helps fictional magic be "magical" as opposed to Spicy Engineering (e.g. Fireball is Spicy Grenade) is if it involves a thinking entity other than the mage: intercessory magic is less prone to being operationalized into just another craft. Sometimes this is a powerful patron, sometimes it's a specialized sidekick.
To use a less fancy word, magic is often social - it involves a deal, explicit or implicit, between the mage and some goblin, ghost, or other gribbly. (The faeries in Dresden Files take their payment in pizza.)
If you pick up some old medieval grimoire like the Key of Solomon, it is deeply social. Its ritual magic is in some ways like a court order: things have to be done properly, forms filled out, visit during the correct opening hours, appeal to the right judge (God) for a sign-off, then speak with the authority of the judge and the legal system backing you for some specific purpose. Rituals are powerful but inflexible, for comprehensible internal reasons.
Fast forward 500 years to Jack Vance's Dying Earth series (you probably know this as the origin of "Vancian" magic in D&D) and you see more social magic. In the distant future, wizards are living in the ruins of dozens of civilizations that rose and fell, leaving behind relics and creatures. One facet of their magic involves calling on "sandestins", powerful genie-like creatures hinted to have been bound or created by a previous civilization, and the sandestins have to be commanded and persuaded and contracted and threatened with the Great Name, in a word, they have to be wrangled. Libraries of Wizard Lore are not just lists of spells, they're also bestiaries of sandestins, advice on how to wrangle them, collections of rumors by travelers to find other sandestins, etc.
When Gandalf is at the Gates of Moria, pondering the riddle "Speak, friend, and enter", this is also a kind of social ritual. Password-access systems are not found spontaneously generated in nature. The gate itself is not intelligent, but it's the result of an intelligent mind engaged in deliberate design to control access. Gandalf has to jump through hoops to make the gate open, and figure out that the clue to the password is hiding in plain sight.
Social rituals make sense. Rituals for formal polite interaction with another creature (or its proxy) are one of the many reasons the classic fantasy genre looks the way it does.
But skip ahead a couple generation of writers cribbing, pastiching, and repeating tropes they don't understand...
These days I'm seeing an increasing number of works where rituals are treated as a sort of brute fact about the universe, with nobody on the other end. For example, there's a song that heals people when sung word-perfect. It does nothing until it's finished, it does nothing if you get a single word wrong. Why?
A social ritual of this form can be explained with "the genie is picky". There's a genie or some other intelligent creature, acting as a middleman to hear the magical song and cause healing. A brute-fact ritual has to treat the universe as having countless special cases and carve-outs in the laws of physics where certain actions cause unusual effects. Somewhere in the nature of reality is a reaction to a song - in a specific language, of a specific era - which results in "healing", a simple concept for an intelligent mind, but an otherwise complicated concept both fantastically specific and carefully customized to do the right thing for humans.
Brute-fact rituals make for a frankly nonsensical setting. Some writers notice the nonsensical setting, but since they're ignorant of the social origins of the ritual, they think this is a problem with rituals and complain that ritual magic makes no sense.
Worse, how are rituals discovered/created in the first place?
Social rituals: by talking to the genie or fairy or other critter that the ritual is to communicate with.
Brute fact rituals: well, uh,
Harry Potter and the Natural 20 plays with this trope in book 3 chapter 9, doing a little lampshade-hanging:
Chant a little Old Aramaic, burn a little sandalwood, sprinkle a powder made from the canine teeth of a child murdered by his brother over a bowl containing stone from a fallen star under the light of a crescent moon and, in three days, it will rain vinegar. And nobody knows why. That terrified Lucius. Who out there was watching, waiting, to see that someone performed the ritual and had the power to follow up with the effects? More troublingly, why would they do it? What possible gain could this shadowy entity get from powdered teeth and space rocks? Or maybe there was no entity, and it was a fundamental property of the universe that vinegar would rain in the middle of the lunar month because somebody said the right words in a dead language? Lucius wasn't sure which was worse. All of this brought up the uncomfortable question of who it was who first figured that out. It can't have been coincidence, or even experimentation. (...) Rituals, it appeared, wanted to be discovered—and, more troubling, wanted to be shared.
Lucius Malfoy is a bit preoccupied with Voldemort, so he's excused for not being sure which is worse. But from my OOC perspective, "fundamental property of the universe" would be worse writing. Shadowy entities with mysterious motives are a staple of fantasy fiction, and practically required in some sense to be the sharer-of-rituals making rituals be discovered by human wizards.
30 notes
·
View notes
Text
For years, China’s state-backed hackers have stolen huge troves of company secrets, political intelligence, and the personal information of millions of people. On Monday, officials in the United States and United Kingdom expanded the long list of hacking allegations, claiming China is responsible for breaching the UK’s elections watchdog and accessing 40 million people’s data. The countries also issued a raft of criminal charges and sanctions against a separate Chinese group following a multiyear hacking rampage.
In August last year, the UK’s Electoral Commission revealed “hostile actors” had infiltrated its systems in August 2021 and could potentially access sensitive data for 14 months until they were booted out in October 2022. The deputy prime minister, Oliver Dowden, told lawmakers on Monday that a China state-backed actor was responsible for the attack. In addition, Dowden said, the UK’s intelligence services have determined that Chinese hacking group APT31 targeted the email accounts of politicians in 2021.
“This is the latest in a clear pattern of malicious cyber activity by Chinese state-affiliated organizations and individuals targeting democratic institutions and parliamentarians in the UK and beyond,” Dowden said in the UK’s House of Commons. The revelations were accompanied by the UK sanctioning two individuals and one company linked to APT31.
Alongside the UK’s announcement on Monday, the US Department of Justice and Department of the Treasury’s Office of Foreign Assets Control unveiled further action against APT31, also known as Violet Typhoon, Bronze Vinewood, and Judgement Panda, including charging seven Chinese nationals with the conspiracy to commit computer intrusions and wire fraud.
The DOJ claims the hacking group, which has been linked back to China’s Ministry of State Security (MSS) spy agency, has spent 14 years targeting thousands of critics, businesses, and political entities around the world in widespread espionage campaigns. This includes posing as journalists to send more than 10,000 malicious emails that tracked recipients, compromising email accounts, cloud storage accounts, telephone call records, home routers, and more. The spouses of one high-ranking White House official and those of multiple US senators were also targeted, the DOJ says.
“These allegations pull back the curtain on China’s vast illegal hacking operation that targeted sensitive data from US elected and government officials, journalists and academics; valuable information from American companies; and political dissidents in America and abroad,” Breon Peace, a US attorney for the Eastern District of New York, said in a statement. “Their sinister scheme victimized thousands of people and entities across the world, and lasted for well over a decade.”
The moves come as countries increasingly warn of an increase in China-linked espionage, during a year when more than 100 countries will host major elections. Statements from officials focus on the impact of the hacking activity on democratic processes, including the targeting of elected officials around the world and the compromising of pro-democracy activists and lawmakers in Hong Kong. However, the disclosures also coincide with continued jostling from Western politicians over pro- or anti-China stances, including the proposed sale of TikTok to a US company, which could result in a ban on the popular app if the sale fails to go through.
As officials in the UK disclosed the details of the hacking activity, Lin Jian, a Chinese foreign ministry spokesperson, claimed it was “disinformation” and told reporters the country “opposes illegal and unilateral” sanctions. “When investigating and determining the nature of cyber cases, one needs to have adequate and objective evidence, instead of smearing other countries when facts do not exist, still less politicize cybersecurity issues,” Jian said in a daily press conference on Monday.
“China is embarking on a huge global campaign of interference and espionage, and the UK and the like-minded nations are pretty sick of it,” says Tim Stevens, a global security lecturer and head of the cybersecurity research group at King’s College London. Stevens says the public shaming and sanctions are unlikely to significantly change China’s actions but may signal a warning to other countries about what is and isn’t deemed acceptable when it comes to international affairs.
China has a broad range of hacking groups linked to its intelligence services and military, as well as companies that it contracts to launch some cyber operations. Many of these groups have been active for more than a decade. Dakota Cary, a China-focused consultant at security firm SentinelOne, says that groups associated with China’s civilian intelligence service are largely conducting diplomatic or government intelligence collection and espionage, while China’s military hackers are behind attacks on power grids and US critical infrastructure such as water supplies. “We do see China engaging in all of those activities simultaneously,” Cary says.
In announcing criminal charges and sanctions against members of APT31, officials in the US laid out a series of hacking allegations that include the targeting of businesses, political entities, and dissidents around the world. These included a “leading provider” of 5G telecoms equipment in the US, Norwegian government officials, and people working in the aerospace and defense industries. APT31 was run by the MSS’s Hubei State Security Department in the city of Wuhan, US officials say.
The seven Chinese nationals hit with charges are Ni Gaobin, Weng Ming, Cheng Feng, Peng Yaowen, Sun Xiaohui, Xiong Wang, and Zhao Guangzong. Both Zhao Guangzong and Ni Gaobin were also sanctioned. The two are alleged to be affiliated with Wuhan XRZ, a company that has also been sanctioned by the US and UK and is believed to be a cover for MSS-linked hacking operations. Employees of the company hacked into a Texas-based energy company in 2018, the US Treasury Department said.
The group used sophisticated malware—including Rawdoor, Trochilus, and EvilOSX—to compromise systems, according to a 27-page indictment unsealed by the DOJ. They also used a “cracked/pirated” version of penetration testing tool Cobalt Strike Beacon to compromise victims, the indictment says. It adds that, between 2010 and November 2023, the group “gained access” to a defense contractor that designed flight simulators for the US Army, Air Force, and Navy; a multi-factor authentication company; an American trade association; a steel company; a machine learning laboratory based in Virginia; and multiple research hospitals.
In its announcement, the UK outlined two separate China-linked incidents: first, the targeting of the email inboxes of 43 members of parliament (MPs) by APT31 in 2021; and second, the hack of the Electoral Commission by further unnamed China-linked hackers. Elections in the UK are decentralized and organized locally, with the commission overseeing the entire process. This setup means the integrity of the electoral process was not impacted, the commission says; however, a huge amount of data may have been taken by the hackers.
When the Electoral Commission revealed it had been compromised last year, it said the details of around 40 million people may have been accessed. The commission said names and addresses of people in Great Britain who were registered to vote between 2014 and 2022 could have been compromised, and that file-sharing and email systems could have been made accessible. “It’s really remarkable that China would go after election oversight systems, particularly given the diplomacy that the PRC [People’s Republic of China] is trying to pull off with the EU,” Cary says. “It’s a very significant act for the PRC to go after these types of systems,” Cary says. “It’s something that democracies are really sensitive to.”
While nations have called out China’s hacking activities for years, the country has evolved its tactics and techniques to become harder to detect. “Over the past couple of years, tired of having their operations rumbled and publicly outed, the Chinese have placed a growing emphasis on stealthy tradecraft in cyber espionage attacks,” Don Smith, vice president of threat intelligence at security firm Secureworks’ counter-threat unit, said in a statement. “This is a change in MO from its previous ‘smash and grab’ reputation but it is viewed by the Chinese as a necessary evolution to one, make it harder to get caught and two, make it nearly impossible to attribute an attack to them.”
3 notes
·
View notes
Note
Hey, Laplace. You said something a while ago that I'm still thinking about. In a response to an ask, you said that masking feels like roleplaying and not like "multiple people". Could you go on? And while you're at it, define masking for us, would you?
Thank you in advance.
-Psy
Masking is just. Putting on a specific affection (usually to mask symptoms that are "inappropriate") for a situation. Like if you're around homophobic family maybe you avoid your queer mannerisms. If you're autistic and in public where stimming would be "disruptive" you mask by not doing it. I'm not really the best person to define masking. To be honest with you. But any "role" you take on to avoid something disruptive or unsafe in a situation? That's masking.
I'm going to describe my experience with masking. I'm plural, and this will not necessarily be true for all plurals, or even match up with what singlets experience. But for me, it's like roleplaying a dnd character. I have like. A bunch of fake shit set up for each mask so that I'm playing a realistic role - I have different opinions and mannerisms sometimes, but it's all by choice and made up. It doesn't feel like being multiple people, it feels like playing dnd as a character. I'm in control of it. My headmates experience the same when masking as our "singletsona" who is "me", since I'm the... I don't like using host, honestly? For us, host just means "person whose life it is", and this is my life. My headmates are all here to help me with the things I need in my life. They're accessibility tools for me, in a way. So they pretend to be the fake mask I made up, because its not any of us, its just a role we play. They never pretend to be like.... me, the actual person. I don't pretend to be them. The masks are all seperate, fake entities that we wear sometimes.
Sometimes I know that members of systems mask as other members - this is, to my understanding, more common with traumagenic & disordered systems - often, those two go hand in hand. This is also usually for safety reasons - when systems are covert, they can't afford to be out and known, especially if they're still in bad situations. So often, even with systems, headmates who mask as each other are still playing a role.
There are reasons other than plurality that can make masking feel like multiple people - however, depersonalization and derealization have crossover with plurality, and so can delusions, and honestly so can hallucinations from schizophrenia! None of these issues are completely seperate because they effect similar parts of the brain. I think that if masking feels like multiple people, then there is probably something going on, and exploring that being plurality maybe isn't bad, even if you're wrong. ESPECIALLY if you end up being wrong. It's okay to wonder and try things out. You aren't like.... hurting anyone by exploring the possibility.
There are also ways of becoming plural if you want to - daemonism especially is very popular. So are soulbonds. Daemonism is creating a mental construct, most often an animal, to interact with. Soulbonds are making a mental connection, most often a sort of telephone line, with a fictional character. The way this manifests is usually the thing where people talk about "characters writing themselves". Not everyone believes in these sorts of connections - it gets into the realm of spirituality for most, honestly. But people have been creating thoughtforms for centuries, you can find mention of them in most cultures.
The whole "tulpa" thing too - I'm not here to debate tulpamancy, but the western version of tulpamancy based on the Buddhist practice is heavily practiced. That's just a fact. Tulpas are just another type of thoughtform. What you call them is ultimately not important, most of the time.
Chosen plurality is a valid, healthy coping mechanism. There are even published psychological techniques based around it. The family system or whatever... breaking your brain and reactions down into parts, or something? I haven't really researched it. My plurality and spiritual practice are a circle, and most of my research focuses on that aspect.
I cannot answer what it feels like for disordered systems to mask. I'm not disordered. Maybe one of the other plurals I know of who are out on the site can answer that part for you if they feel comfortable? This is not an invitation to go ask anyone that - just putting the option for them to reply to this post.
5 notes
·
View notes
Text
I don't have anything for WIP Wednesday (at least for this blog but my crochet blog Nerdy Stitches has a few projects) but I do have a new hyper fixation that has made me suddenly insanely jealous of my father and oldest sister for witnessing before I was even spawned.
So, my new hyper fixation this month is old animatronics, specifically the ones from the pizza chain Showbiz Pizza that is honestly scarier than FNAF in my opinion (Billy Bob haunts my dreams rent free) and my favorite animatronic out of the whole cast of characters to choose from is the first human character and also the first character produced after the launch of Showbiz named Uncle Klunk the Abomination: The Funniest Robot Science Has Ever Made. I just love watching old archived training tapes featuring him and seeing how these old animatronics worked. They worked through hydraulics which is a very misleading name for the technology because it was controlled by air pressure and not water. There would be a huge panel connected to several hoses installed behind the animatronic and under the stage that was accessed through a trap door and the animatronics would move based on these hoses creating and reducing air pressure and these hoses on the panels would be connected to a metal box that would respond to music tapes that were programed to not only play music but move the animatronics in sync with the track. And these tracks took months to program due to how specific you had to be with the air systems. And the character Uncle Klunk is my favorite character to study because he had the most range of movement out of the whole cast and his selling point was the fact he could pick up a telephone and a banana. And how this was done was four movements that would bring his arm to the side, lower the arm, lower the hand, and his thumb and middle finger would clamp onto the object like a claw in a claw machine would. And these objects had to be very specifically placed so he wouldn't accidentally knock them over or miss them entirely.
And what's even more special about the Uncle Klunk character is that there were only 50 of these animatronics because his whole gimmick and act was to be a traveling talk show host and would provide a humourous break in between songs in the main show. His talk show was called the Uncle Klunk Abomination Show where he'd have a cuckoo clock bird name Maurice make fun of him, his mom would call, and sometimes people would call him and have a wrong number (my favorite from old show recordings on YouTube was an argument hotline that called Klunk and started an argument with him so Klunk started agreeing with the man on the other line so he'd get flustered and try harder to continue the argument) so they only had a limited amount of these animatronics in circulation so he could travel to other locations to sell this gimmick. The only problem is he didn't attract as much revenue as was predicted for a traveling character because he only had one commercial and when people did see him in person he produced the effect known as the uncanny valley were something was so human like it was terrifying. (He was based on his voice actor who was a background singer in the Rockafire Explosion Band who was the main band of Showbiz Pizza but he didn't have his own character so they produced Uncle Klunk which is why he was human and looked so realistic minus the cartoonish stylization of the real person he's based on.) If they had advertised him more he would've had a strong fan base like he does now nearly forty years later.
Due to how badly this character performed he was scrapped pretty quickly and repurposed to be used as Santa Claus for Christmas shows, Uncle Pappy who would sit in the arcade and give life advice between folk songs, and an interactive attraction where customers could press buttons and control him over in the arcade and teach kids how animatronics worked and in order to do that they literally split him in half or skinned him entirely which is why a full skinned Uncle Klunk is extremely rare for collectors (I've only seen two on YouTube) and have a selling price close to a half million (his body parts that were skinned or replaced in his repurposing go for several thousand in today's market). So yeah, this character has gone through hell.
And why am I jealous of my dad and oldest sister because of this hyper fixation on Uncle Klunk you may be asking or completely glossed over that in my first paragraph? Because they saw him when he first came out. My sister was from my dad's first marriage and they lived in Richmond, Virginia that had a Showbiz Pizza location and was one of those restaurants that was so saturated with customers they try out all new products at that location and when Uncle Klunk came out my dad happened to be home from the military that weekend and my sister convinced him to take her to Showbiz Pizza because she was also obsessed with Uncle Klunk and they got to see some of his first performances. My dad says they were a 3/10 for him because he didn't particularly like the restaurant in general. And now I'm sad that they got to see such a cool animatronic and that I wasn't spawned in time to also witness the greatness that was Uncle Klunk the Abomination: The Funniest Robot Science Has Ever Made. 😢
5 notes
·
View notes
Text
what is computer devices
What Are Computer Devices? (In Detail)
Computer devices are the physical components (hardware) of a computer system. They are classified based on their roles in the computing process, such as input, output, processing, and storage. Below is a detailed explanation of the major categories and examples.
1. Input Devices
Input devices are used to enter data or instructions into a computer.
Examples:
Keyboard: Used for typing text, numbers, and commands.
Mouse: A pointing device to interact with graphical elements.
Scanner: Converts physical documents into digital format.
Microphone: Captures sound for audio input.
Webcam: Captures video for communication or recording.
Touchscreen: Acts as both input and output; users interact directly with the display.
Game Controller/Joystick: Used mainly in gaming to control movement and actions.
2. Output Devices
Output devices present the results of computer processing to the user.
Examples:
Monitor/Display: Shows visual output from the computer (text, video, images).
Printer: Produces physical copies (hard copies) of digital documents.
Speakers: Output sound from audio files or software.
Headphones: Provide personal audio output.
Projectors: Project computer screen onto a large surface.
3. Processing Device
The core component that processes data and instructions.
Central Processing Unit (CPU):
Often called the "brain" of the computer.
Performs all arithmetic and logical operations.
Consists of:
Arithmetic Logic Unit (ALU): Handles calculations and logic operations.
Control Unit (CU): Directs the flow of data and instructions.
Registers: Temporary storage for quick data access.
4. Storage Devices
These are used to store data permanently or temporarily.
Types:
Primary Storage (Memory):
RAM (Random Access Memory): Temporary storage; fast but volatile.
ROM (Read-Only Memory): Permanent, contains startup instructions.
Secondary Storage:
Hard Disk Drive (HDD): Magnetic storage, high capacity.
Solid-State Drive (SSD): Faster and more reliable than HDDs.
Optical Drives (CD/DVD): Use laser to read/write data.
Flash Drives (USB drives): Portable, solid-state storage.
Memory Cards: Used in cameras, phones, etc.
5. Communication Devices
Used to transmit data from one computer to another.
Examples:
Network Interface Card (NIC): Connects computer to a network.
Modem: Converts digital data to analog for telephone lines.
Router: Directs data across networks and connects multiple devices.
Wi-Fi Adapter: Enables wireless communication.
6. Peripheral Devices
These are external devices that connect to a computer to add functionality.
Can be input, output, or storage.
Examples include: external hard drives, printers, scanners, webcams, and game controllers.
0 notes
Text
Welcoming Smarter – Why Every Office Needs a Visitor Management System
Think about your last visit to an office. Did you get a great welcome, or simply a pen to sign an antiquated book? First impressions count — and for many organizations, that first impression comes from the front reception desk. This is where a visitor management system can change the game.
In many workplaces today, guests are not just guests — they are clients, job applicants, contractors, and suppliers. While providing a courteous welcome to visitors is good relationships practice, managing the visit is important to keep things organized and secure. That's why so many offices are moving away from paper visitor logs and paper check ins to digital visitor check ins.
A visitor management system lets you know exactly who is walking in and out of your office. Guests can enter their details, a photo can be taken, and often a visitor pass can be printed within a matter of minutes. You have the benefit of keeping an efficient office while maintaining some level of security.
The visitor has a positive experience when a visitor management system is used.. Nobody likes filling out a long visitor registration form or waiting too long at the receptionist to check in. With digital check-in, guests can easily register and notify their host of their arrival.
For a workplace in which people handle visitors, this is less about convenience but more about control. You get a record of who came, and left and the reason why! Should you need to look up a past entry, this will be neat and easy. No turning over pages of scrawled names or missing telephone numbers.
Not to mention, safety.Knowing who is inside the building could save lives in an emergency.You are provided with visitor information to help assure everyone is safe and only authorized visitors have access to certain areas in the workplace.
Ultimately, a visitor management system is more than just some technology, the associated benefits demonstrate to visitors the workplace is efficient, organized and shows respect for their time and interest in their safety.
As workplaces continue to expand and visitations increase an office gets smarter at the front, a simple yet moving step forward. After all, a workplace sets the tone by how it greets a visitor.
0 notes
Text
Aria Telecom: Your Trusted Cloud Based Doctor Appointment System in Canada
In today’s digital-first world, efficiency and accessibility in healthcare are more important than ever. Long queues, telephone delays, and manual scheduling are not just outdated—they compromise patient care. That’s why modern clinics, hospitals, and medical practices are turning to smart solutions like Aria Telecom’s Cloud Based Doctor Appointment System in Canada, designed to simplify scheduling, reduce administrative burden, and enhance the patient experience.
Whether you manage a private clinic or a public healthcare network, digitizing your appointment process ensures better control, higher patient satisfaction, and fewer no-shows. And with Aria Telecom’s cloud infrastructure, your system is always secure, available, and scalable.
Why Choose a Cloud-Based Appointment System?
A cloud-based solution means your scheduling system isn’t restricted to one computer or clinic. Doctors, staff, and patients can access it from anywhere—be it a mobile device, tablet, or desktop.
As a trusted provider of a Cloud Based Doctor Appointment System in Canada, Aria Telecom offers:
24/7 booking access for patients
Automated appointment confirmations and reminders
Easy rescheduling and cancellation options
Integrated doctor availability calendar
HIPAA and PIPEDA-compliant cloud storage
All appointments, updates, and patient interactions are securely logged in real-time, reducing errors and miscommunication.
Key Features of Aria Telecom’s Appointment Platform
🗓️ Smart Booking Interface
Patients can easily book, view, and manage appointments via web portal or mobile app. Available time slots update in real time.
🔄 Auto Notifications
Patients receive SMS and email reminders to reduce no-shows and late cancellations.
🩺 Multi-Doctor and Multi-Clinic Support
Ideal for small practices or large healthcare networks. Manage multiple doctors’ calendars under a unified system.
🔐 Secure Canadian Hosting
Our cloud platform is hosted on Canadian servers, ensuring full PIPEDA compliance and patient data privacy.
📊 Admin Dashboard
Admins can track booking trends, manage workloads, and generate reports with a few clicks.
Perfect for Canadian Healthcare Providers
Whether you’re a private practitioner in Toronto or a clinic in British Columbia, our Cloud Based Doctor Appointment System in Canada is built to serve:
Solo doctors and specialists
Multi-specialty clinics
Diagnostic and pathology labs
Mental health and therapy centers
Provincial healthcare groups and public hospitals
It integrates seamlessly with existing EHRs and patient record systems to create a smooth operational flow.
Success Story: Quebec-Based Medical Group
A growing network of dermatology clinics in Quebec faced scheduling chaos due to phone-based appointment systems. Long hold times and miscommunication were affecting both patients and front-desk staff.
After adopting Aria Telecom’s solution:
Patient booking increased by 35% in the first 3 months
Missed appointments dropped by over 40%
Staff reported 60% less time spent on scheduling-related tasks
This highlights why Aria Telecom is a go-to name for a reliable Cloud Based Doctor Appointment System in Canada.
Designed with Compliance and Security in Mind
Your patient data is sensitive. Our cloud infrastructure ensures that it stays secure and fully compliant with Canadian healthcare laws:
Encrypted data at rest and in transit
Canadian data center hosting
Role-based access for doctors, admin staff, and patients
Full PIPEDA and HIPAA alignment
Daily backups and activity audit logs
Why Aria Telecom?
Aria Telecom brings over two decades of experience in telecom and healthcare IT solutions. Choosing us means:
🚀 Quick deployment and onboarding
📞 24/7 technical support
🔧 Custom branding and integration
💡 Scalable plans for clinics of all sizes
🤝 A technology partner that evolves with you
We’re not just giving you software—we’re helping you offer smarter, faster, and safer care.
#DoctorAppointmentSystem#CloudHealthcareCanada#AriaTelecomSolutions#PatientBookingMadeEasy#DigitalHealthCanada
0 notes
Text
Online Food Ordering System for Restaurants: Enhancing Dining in the Digital Age!

In recent years, the hotel industry has experienced a central transformation due to the progress of digital technology, especially online systems. Today, customers expect convenience, speed, and flexibility in food, which must be adjusted to be competitive. Implementing a restaurant food control system is no longer a luxury - it's a must. This keyword explores key aspects of restaurant control, challenges, and how restaurants can improve customer operations and satisfaction. A food control system is a digital platform that allows ordinary customers to tailor their choices and check a furniture app. These systems can be entered directly on the restaurant website or as part of a last-mile distribution app.
Online food ordering system for restaurants is built and maintained by the restaurant or through a blank label supplier. Orders go directly to the restaurant without an intermediary. One of the most important advantages of implementing an internet food control system is to increase income growth. With easy access to the menu and an intuitive check interface, customers are more likely to add additional items to their order, as beverages and teams. In addition, Internet Control Systems Taxes 24/0 means that customers can implement Output-So -opening Output orders or distributions.
Today, customers need convenience and a numeric control system over precisely that. Customers no longer need to wait or visit a physical restaurant to place an order. They can do this from the comfort of their home, moving, or their place of work. Many systems also provide registered commanding functions, objective realities, and loyalty prices to improve the global user experience. Traditional telephone orders are subject to mistakes, especially during peak professional time, when communication may be fuzzy or unclear.
Benefits of a Restaurant Online Ordering System
A Restaurant online ordering system minimizes the misunderstandings that allow customers to insert directly with their preferences. This reduces the odds of incorrect orders and increases the customer's general satisfaction. A restaurant's system of classifiers involves reducing the workload. The orders are sent directly to the kitchen, forcing the preparation process. This helps staff focus on food preparation quality and provides excellent service personally. Internet systems collect and store data on customers' preferences, the command frequency, and spending habits.
This information can be used to develop target marketing campaigns, loyalty programs, and custom deals. The data analysis also helps provide the request and the least optimistic. Developing a customized system or reconciliation in a third-party provider includes initial costs. Small restaurants can find this an essential financial obstacle. However, return to the often prevailing investment during the initial expenses over time.
The Future of Online Food Ordering for Restaurants
Without the correct integration, restaurants may face confusion or operational order delays. If you use the third-party distribution apps, restaurants must pay commissions that can eat into the beneficiary's bottom line. It is undisputed to weigh the perks of exposure compared to the cost of each controlled order. In third-party applications, restaurants can find it challenging to differentiate themselves from competitors. An Online food ordering restaurant helps maintain a brand identity and a consistent customer experience.
The Internet food control tendency is not indicated. With the growing dependence on digital services, especially after the pandemic, in the Covni-19 In the future, manufacturing will be a basic industry, and the character and distribution of drones can revolutionize the Internet landscape. For restaurants in London, Ontario, local references are essential. Your web design should integrate keywords, like the keywords in pizza. London. The Customer Contact Solutions - London, Ontario Canada has helped the customers to find the best online food ordering systems.
Conclusion
Restaurants hugging this digital change now will be positioned for long-term success. Investing in a reliable platform of order in case, they still have a sustainable and competitive pattern. The food control system in the restaurants changes the game, offering their customers operational benefits for business. Adoption of modern restaurant and system is a strategic decision that responds to the changing market and benefits. A design that complements the restaurant's aesthetic - be rusty, modern, or eclectic - is essential. A professional photograph is worth investing in people who eat fine food in their eyes. Either offering bookings or distributions in line with platform integration are essential.
0 notes
Text
Costa Power Industries Pvt. Ltd.is a having global exposure as APC ups Manufacturers in Mumbai, APC ups Suppliers, APC ups Distributors in India and APC ups dealers in Mumbai, APC ups battey systems.
Costa Power Industries Pvt. Ltd.had started its operation in the field Since years successfully offering turnkey project services in the field ofElectrical, Automation, Instrumentation, Energy Saving and Control with qualified & experience working team with solid technical background. As headquarter is in economic capital of India, located in Mumbai and branches at PAN India.
apc ups battery backup systems with customized ups battery solutions and nationwide with a strong presence in the thane, Mumbai, Mumbai Suburbs, Maharashtra interior parts and in India.
Costa Power builds name and get reputation in India as ups suppliers , APC ups dealers in Mumbai chain of APC ups manufacturers in Mumbai , APC online ups dealers in mumbai of global distributors such as APC industrial ups , APC smart online ups , APC single phase ups , digital online ups , APC modular ups manufacturers , APC three phase ups ,APC smart ups dealers in Mumbai ,APC online ups in Mumbai ,APC offline ups ,Smart APC office ups etc.APC online ups suppliers in India.
CPIPL is best APC online ups suppliers in India used for safety the machinery, equipment and save the loss of raw material in manufacturing units in its factories, pharmacuetical companies etc. Costa Power is always ahead when it comes as APC ups suppliers in Mumbai ,APC ups suppliers in India , APC online ups dealers in Mumbai, APC ups dealers in Pune with Symmetra LX is a line of online ups suppliers in India , APC ups dealers in Delhi products, aimed at network and server applications. This technology comes in power configurations different ranging from APC ups 3 kVA to APC ups 10 kVA. with APC offline ups 1000VA to APC Online ups 20KVA and in higher kVA as per industry requirements which are built for use in data centers and new startups as well in Industrial segments. Costa power with their highly experience technical team provides solution i.e.APC industrial ups manufacturers in India for power saving and equipment protection for long life. As Costa Power top ups suppliers of APC ups manufacturers in India include features such as integrated manageability, hot-swap ability, user replaceable power, APC ups battery and intelligence modules in APC modular ups in Mumbai. By with another milestone Costa power is dedicated APC ups dealers in Mumbai for Typical applications include web and other application servers, IP based and traditional PBX voice solutions, and enterprise type network switches. APC ups distributors in Mumbai. Costa power is genuine APC ups Distributors and APC ups suppliers for APC ups manufacturers in Mumbai with PAN India basis with features APC Symmetra PX1 (THOR 20-80 KVA) is a line of APC ups distributors in India Products aimed at the small, medium market of data servers rooms. We trust this technology and always believe and recommend to client because it is With user changeable Power Modules, Battery Modules, and 24/7 Hotline Support which typically can diagnose a problem via telephone call and/or direct connection access of its SNMP (Simple Network Management Protocol) Card, have become "THE LEGENDARY RELIABILITY" Leader in the ups Marketplace with a demonstrative 99.4% Online Uptime.
#Upsbattery#Upsbatterydealers#Upsbatterydistributor#Upsbatterysuppliers#Upsamc#Upsapc#Microtekinverter#Quatabattery#Luminousups#Emersonups#Onlineups#Digitalups#Offlineups#Bestups#Bestbattery#Servostabilizer#Vertivups#Exidebattery#Luminousinverter#Upsdealers#Upssuppliers#Upsdistributors
0 notes