#What is Data Protection
Explore tagged Tumblr posts
Text
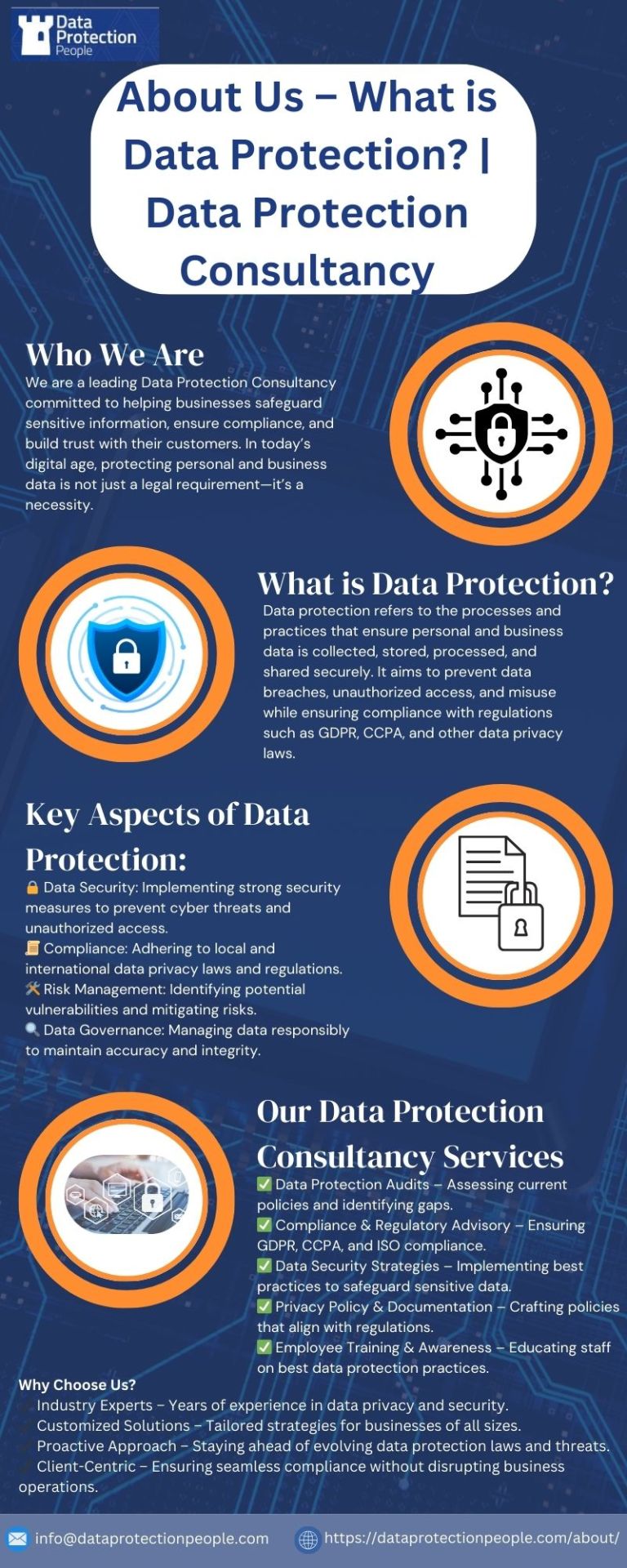
About Us - What is Data protection?| Data Protection Consultancy
Our mission is to make data protection easy. Looking for a GDPR consultant or Outsourced DPO Services in the UK? Get in touch today.
0 notes
Text

"I would hug you, but I do not have human arms or warmth."
#fairly oddparents fanart#fairly odd parents a new wish#dev dimmadome#development devin dimmadome#au pairs#o pairs#my art#i rewatched that clip and got really sad#maybe it's the autism but i get very attached to droids/robots and the like#plus these things HAVE to be sentient. at least a little#they're truly both Dale's saddest little creations#someone give that kid a hug#i may have forgotten to eat but you know what. i'm content.#the au pairs CARE about dev trust me guys#he's just their little guy they have to protect him#as a kid i loved data in st@r trek so take that as you will#still do#currently love isaac from the 0rville#and samuel in the alien game#what can i say i'm a sucker for androids and artificial lifeforms#fop fanart#fairly oddparents
71 notes
·
View notes
Text
#section 31 doesn’t matter to me#I only care about these and I’m pretty sure we all hate section 31#so I’ll just leave it out to begin with#star trek#star trek tos#Star Trek tng#mine is generations it genuinely seems so pointless#the emotion chip plot is annoying and very cheaply throws away a lot of character development data went through#I get why it’s interesting for a movie plot but it kinda just ignores seven seasons of development#and Kirk’s plot annoys me#‘hey he fell in love with some random woman but it’s for real this time’ yeah okay#and then the whole ‘ah the nexus is perfect you’ll never want to leave’ unless you’re a starship captain then you’re immune#I haven’t watched nemesis yet because I know what happens and I’m choosing to protect myself from it#but I have a sneaking suspicion that once I watch it it will be my lest favorite#also whoever chose voyage home that better have been a misclick#you better be joking
23 notes
·
View notes
Text
Creation = The Thing (from the tubhole?)
Primary Protector (Creator (not used but could be)) = Tubbo
Rank 1 Shell = Sunny
Guardian = Philza
Shell (in general) = Eggs
Pancake Shell = Empanada
The Mother of Pancake Shell = Bagi
Duck Shell = Chayanne
Trauma Shell = Tallulah
#i can’t talk in chat rn and am dealing™️#qsmp philza#Philza#donno what else to tag#I kinda hope he keeps playing it relatively serious#the idea of Creation being something from either the tubbhole or something Tubbo made#to protect Sunny in case he isn’t there#‘you are my job’ yeah he’s meant to look after her- DID HE JUST POINT AT HER AND SHE DISAPPEAR#I KNEW IF HE POINTED AT YOU YOU GET VOIDED BUT WTF#‘Rank 1 is now Safe’ UH HUH. SURE.#OH HE BROUGHT HER BACK#‘Guardian I am here for you’ ‘how can I trust you?’#‘yes it was warm there like a blanket :)’ ‘no one else is here for me’#SUNNY#‘primary protector is missing.’ ‘Primary Protector put me here for you.’ ‘fear no more’ at least Phil is getting#‘PRIMARY PROTECTOR WILL BE FOUND OR RECOVERED INTO A BACK UP’ WHAT#‘I need your help guardian’ ‘locating (primary protector)’ ‘do you have the data’#Phil trying to explain to Creation what happened and why-#‘primary protector cannot die. primary protector is not alive to begin with.’ WHAT. TUBBO LORE?????
119 notes
·
View notes
Text

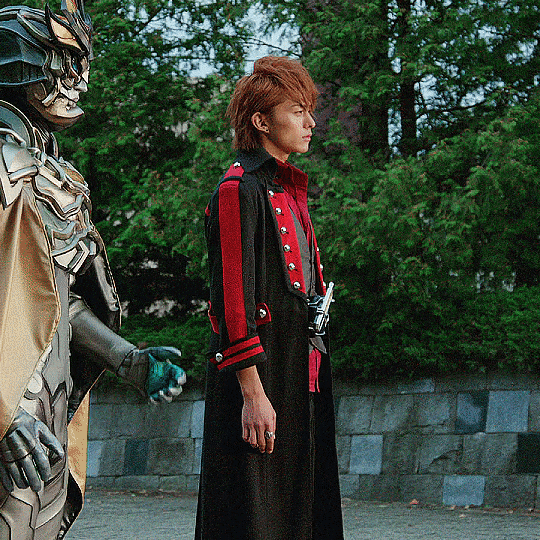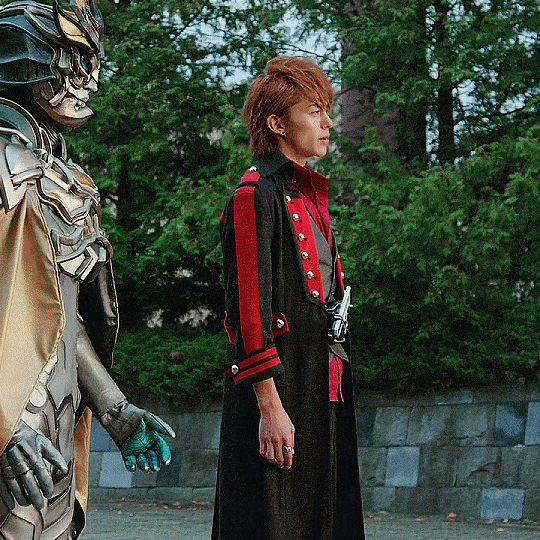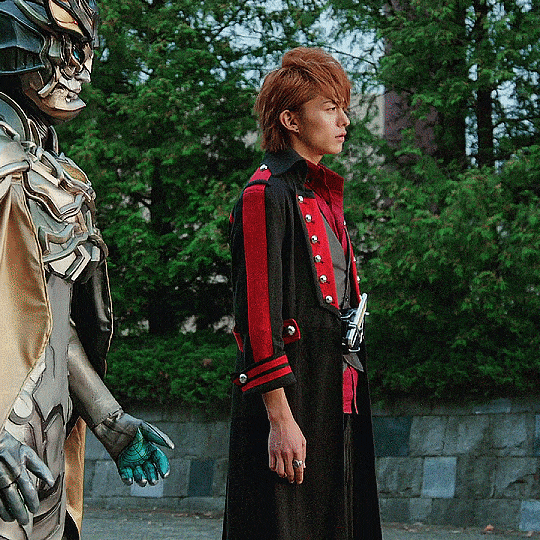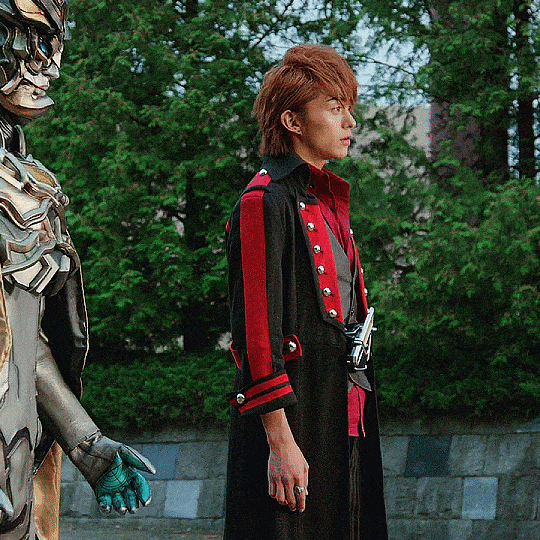





Kaito Kumon in Kamen Rider × Kamen Rider Drive & Gaim: Movie War Full Throttle (2014)
"Kazuraba... You never change. I see you're still fighting the same battle. Well I haven't changed either..."
+ bonus

#kamen rider gaim#kamen rider baron#kamen rider#kumon kaito#kaito kumon#tokuedit#please do not repost#umbrella.edits#umbrella.gifs#umbrella.posts#he's so pretty <3#i've been thinking about this and how he's made from the data of memories but is still kaito like he's just like kouta remembers him#it's the way he'll still protect kouta while also doing what he swears to do
9 notes
·
View notes
Text
everyone is quitting and no one is hiring for a livable wage or has ethical standards or they are offering a 15k sign on bonus to move to Alaska
but no one wants to work
#im not going to fucking use AI in confidential therapy notes you dumb fucks!!!! who sees this data? what protections are there????#just make a fuckign wordbank if the paperwork is that hard
7 notes
·
View notes
Text
y'all i've been upset about nanowrimo's shenanigans since last year, when kids weren't safe, and now there's this AI shitshow, and i want to cry about it again, because nano has been SO IMPORTANT to me since 2008--it helped me hack my writing process and make a bunch of cool shit, and i've written so many stories i love using it as a jumping off point. but. we gotta protect kids, and we gotta get the fuck out of here with AI bullshit.
so. the decision i have come to is that i will still be participating in nano. but now it stands for "now a's [that's me] novel writing month." i'm still going to write a book in november, and i'm still going to shoot for the 1,667 words/day (even though my finished projects wind up way longer than that, invariably), because i've structured my creative life around this routine, but i won't be using their site any more.
i will also not be tagging my november project posts as nanowrimo, but i WILL still be tagging them as "nano[YEAR]" (because that's been my tagging system for untitled projects for uh. years.). and it's now a's novel writing month :)
#text#personal#nanowrimo#nano2024#as soon as i can get my feelings together i'm going to go delete my account :(#i want to save my data from it though so i have to figure out How To Do That#that's like. that's my writing history. for over a decade.#well. one month's worth anyway.#i love the graphs i love the word counter i love the Record#i love that it did it for me so i didn't have to make it special for myself#a friend already did a little excel graph that accomplishes most of the same stuff so i'll use something like that#i've been counting offline for years anyway#i just. ouch.#literally the project i'm revising now was a nano seven years ago#so many of them have been#protect kids like DON'T SET THEM UP TO BE GROOMED HOLY FUCK#not protect kids like coddle and restrict access#protect kids like don't put people in positions of power who can't be trusted with it (like make sure the space is FOR TEENS)#anyway i'm tired and upset and i need to figure out what to do about this haunted house book#i wanted to get words out here before i continued to post about my writing projects just so i have sometime to point to about it#“hi here's my stance kthxbye”#admin
11 notes
·
View notes
Text
between my phone battery being gregnant/dying and the path of that damned typhoon, i am so cooked jsbfhsdvfdsvf i can't even see notifs/reply to messages from there bc it keeps shutting down, im typing this all on pc rn, it's so inconvenient ueueueue
#eintxt#the nearest service center for my phone brand is 2-3 hours away 💀👍👍#i want to get it fixed this weekend but this bitchass typhoon also hits this weekend!#bc what if this is the one that make our roofs fly off#lowkey still have a bit of trauma from that one typhoon that made it rain inside our house & fucked up my whole town years ago#WHILE I WAS IN THE MIDDLE OF MY RESEARCH PROJECT EVEN BTW#i need to protect my laptop tablet pc and merch when that happens again#if im inactive/unresponsive this weekend u alr know 🗿#i need to charge my power bank and load up some mobile data on my old/back-up phone
7 notes
·
View notes
Text
It's just so phenomenally stupid to be sitting here trying to do everyday shit and planning for the work week ahead when it doesn't even matter anymore. Laundry groceries meal prep cleaning who the fuck cares. The lucky ones with the means to do so will get to escape the country and the rest get to deal with everything becoming too exorbitantly expensive to be able to live and also having no healthcare. Plus vaccines being outlawed (it just happened in Idaho!) and a brewing H5N1 pandemic everyone is going to ignore oh yeah and also Trump executing everyone who doesn't agree with him. Why the fuck am I having to do emails and spreadsheets at a time like this??
#me trying to figure out what i need to do before january 20th to protect myself and being overwhelmed lmao#hoard cash encrypt data find servers overseas to store my cloud stuff find secure messaging apps AHH
14 notes
·
View notes
Text
I love the depiction of the police in this show god almighty
#squid game season 3#squid game season three#squid game season three spoilers#I haven’t got to the end but I already see people slagging it off#and if I think this is going the way of sunrise on the reaping#then bleak doesn’t equal bad#it wouldn’t surprise me if many people didn’t get this#also that cop TOTALLY BROKE DATA PROTECTION CMON#just bulldozed gdpr#then again what do we expect right#for them to be competent
2 notes
·
View notes
Text
lmao @ mozilla putting telemetry in firefox, then saying they will "anonymize it" and "not sell it to third parties"... and then a month later they acquire an advertising broker and send your data to that, which technically means it's a first party and their little "promise" isn't broken, while still attempting to send you directed ads based on your browsing data & profit from it
#firefox really only has mv2 extension support separating them from the other major browsers#went back to ungoogled chromium until the mv2 ban kicks in and then i don't know what i'm going to do#librewolf is an option but there are some streaming websites that don't play nice with it#hopefully mv3 data protection apps improve a bit more - the ad blockers are working pretty well but they aren't as privacy-protecting yet
9 notes
·
View notes
Photo










Always rejecting intimacy <<|?? (Patreon)
#Doodles#SCII#ZEX#DAX#At least it's fairly well-earned this time - ZEX is being irresponsible and DAX loves to correct him on that front#For the record - ZEX is now immunized against catching hanahaki again#At least until his affections turn elsewhere lol but considering how infatuated he is with the Captain ♥#And even then he wouldn't be at risk of catching DAX's strain because it's self-inflicted! Yaayyy#But they don't know that! ZEX is putting an awful lot on the line for the possibility of playing test subject for DAX's sake#Very interesting how much he's willing to gamble to see his Sub-Commander well hm ♪#ZEX's selfishness is probably one of my favourite points about him - if he had the hard data to back up that he'd get DAX's strain hmmm#I wonder if he'd be quite so willing to be reinfected - but :) His own experiences - his self-centered viewpoint and confidence and pride#He was fine last time! Surely nothing bad would happen to him! He'd be fine this time too!#That vagueity gives him space to play in#And he's still acting selfishly here as well! Trying to take matters into his own arms without considering DAX's feelings!#Ahh <3 I love him ♥#He's also not particularly partial to DAX trying to protect him when /he's/ the one trying to protect DAX!#Their little mismatches in trying to do right by each other and stopped by the other haha <3#Poor DAX lost his breath just from pushing ZEX away wehh#Usually so strong! Physically even more than ZEX! Though ZEX is more clever hehe <3#But now with the roots in his lungs he can't even push him away fully#Gah what a lovely metaphor <3
4 notes
·
View notes
Text
I actually have a fic idea but lc is a show that's like. you will never ever have all the information and context until the end. and I am a writer who writes best and more confidently when I have all the info and context at my fingertips. so now I'm just like 🧍♂️
anyway. ramble in the tags
#mine musings#not tagging etc etc#it's an AU so it shouldn't even matter actually. but. whatever. i'll still try to write it. it'll take a while#it's more like character exploration anyway. a role reversal (my favorite kind of au)#i.e. what would the emma case look like if cxs is the one who keeps timelooping to save lg?#it's not a power swap or personality swap so i think it'll be an interesting exploration of the limits of their personalities#for example: in this au i think lg is still protective of cxs and acts as the guide. but he's closer to og!timeline lg#so i'm thinking that he's still very principled but perhaps less strict about doing small deviations from the timeline#cxs is still empathetic and reckless and i think that would actually get worse in a timelooping cxs#since he's the possessor he rationalizes to himself that he gets to shield lg from the messy parts of an operation#and how this self-matyrdom pulls at the fragile trust they have. because their partnership is never equal when someone is timelooping#i'm thinking in like the emma case this all comes to a head when emma gets the text from her parents#in S1 lg tells him “it's better not to look”#i think in this au. cxs would have already honed his acting skills and be like “lg. does she check the phone?”#and lg who is protective but a little naive and not as strict with rules is like#cxs looks so sad :( he's been missing his parents lately :( emma doesn't see the text until tomorrow but...#this probably won't change the timeline too much... right? i think cxs needs to feel loved right now :) “yes she checks her phone”#and cxs is like “... are you sure?”#lg: “yes i'm sure”#and then post-dive cxs finds out emma dies but he doesn't tell lg :) he just keeps it to himself :)#bc it's his job to handle all the messy parts :) like the emotions of their clients. their regrets and obsessions. their fates#in his mind. the more lg knows the more he tries to sacrifice himself to save cxs. so it's important that lg is kept in the dark#something something actor/scriptwriter metaphors idk still working on the idea#just. role reversal shiguang... cxs who keeps timelooping bc he has abandonment issues so he can't handle lg dying...#lg basically is like 9S from nier automata who always dooms himself by learning the truth#this could've been a read more instead of a tag essay i'm sorry. i keep forgetting that feature. i am a yapper in the tags#cxs after dragging lg out for dinner so he doesn't catch the news: “hey lg. we followed the script to a tee right?”#“i didn't forget any lines or anything?”#lg (confused) (lying): “yes. aside from getting the financial data part. we did everything right.”#cxs: “okay 😊 i trust you 😊 past or future let them be”
4 notes
·
View notes
Text
I really wish I wasn't living in the middle of a natural disaster site right now :D
#'oh we don't get tornadoes in northeast ohio we're on the lake'#welp....it finally happened. We had our first tornado yesterday#and you know where it hit? my childhood home :D#i'm lucky enough to have power but we have no internet and everyone around us is gonna be out until at least the weekend#i go on vacation this weekend but like....y'all....i'm still so freaked out#my ptsd didn't have time to kick in yesterday because i was at work and protecting my students but uhhhh it's kicked in today :D#and only having spotty cell service and data is making it worse#it's hard to stay connected and keep an eye on what's going on when you can't access the fucking internet#but tumblr works lmao
4 notes
·
View notes
Text
question to ao3 users have yall actually agreed to the new terms and conditions and/or is there a way to continue using the site without agreeing
#nathan's notes#ao3#i'm not from the US so i dont know how my data will be processed#since i'm like 90% sure that my country wouldnt allow for the US's type of info gathering#idk if they could protect me from that#or if i'm just fucked#also what could the US even do with that type of info they gather
2 notes
·
View notes
Text
YouTube and the way they exploit you and your children.
Youtube is pushing this idea of it being a kid friendly site. Despite the fact that for years, they've been involved in some of the most questionable Internet dramas.
A lot of their content creators and online personalities have been guilty of a slew of crimes, and yet they push their channels and garner ad revenue.
They claim to be in support of the LGBTQ+ community, womens rights, and racial justice... Just take a look on their official page. Yet they continually promote advertise and push content from hardcore incels, racist radicals, and right wing content creators.
See, YouTube says one thing, and shows another story. They'll even go so far as to put all these guidelines in place, no profanity, no sexual content. And yet there are plenty of videos dehumanizing women and pushing sexualized thumbnails, all catered to children. These channels are not taken down, and most of them are catered to children.
Their latest attempts to appeal to (and aid) the pedophiles on their site, (and perhaps running it?) is by far the most egregious and horrifying. Making it so that Creator's are forced to give them government protected private information. I'm talking PASSPORTS, PHOTOS, and HOME ADDRESSES PEOPLE.
Now you're probably asking yourself, why on earth would YOUTUBE "need" a government document... Well, that would make it so that young women, men, and KIDS are suddenly soooo much easier to find of course! Now they'll know exactly what you look like, where you live, and how to create a passport to take you somewhere far away!
Let's not forget that YouTube has had more than it's fair share of horrific stories come out... maybe we as a public should start questioning the people who are in charge of, and putting such creepy invasive things in place... YouTube claims to be a site for it's users, but do their true intentions linw up? Because all I've seen lately of their site is hate filled hate mongering practices. And insidious "guidelines" that basically act as a manual for human trafficking.
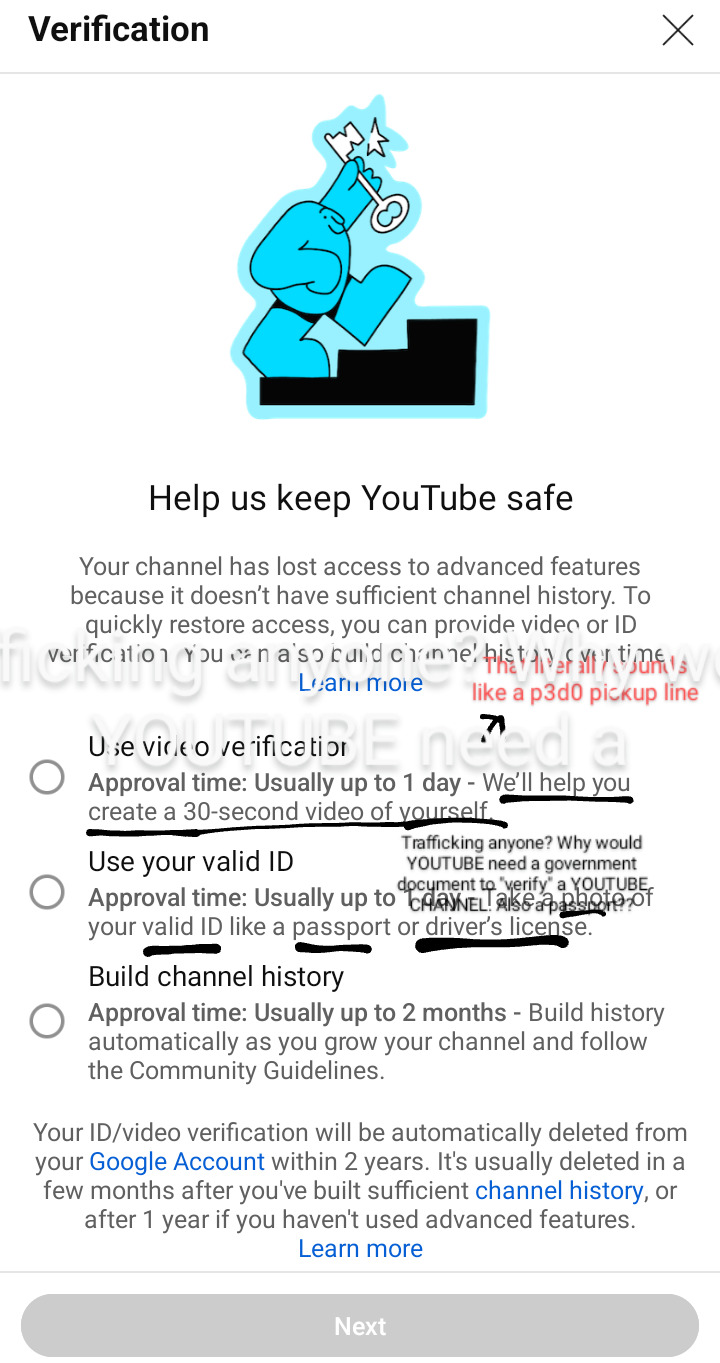
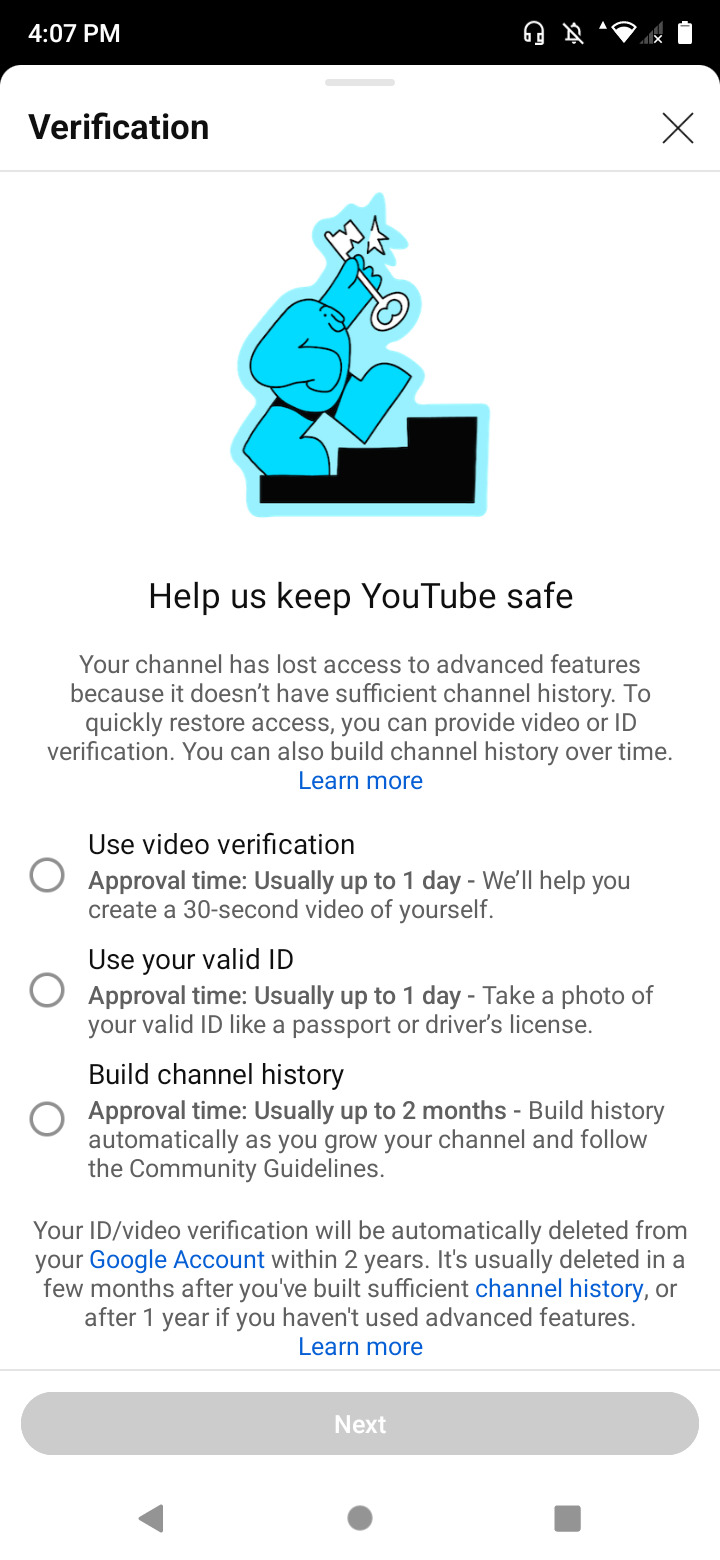
#youtube channel#youtube#comment section#youtube music#social media#human rights violations#human rights#private#data privacy#protect women#protect trans kids#protect your peace#protect yourself#lawsuit#youtube drama#youtube documentary#fuck youtube#fuck you#amerikkka#what the fuck#seriously what the fuck#online privacy#invasion of privacy#internet#internet privacy#safety#trafficking tw#trafficking mention#human trafficking#I came with RECEIPTS
4 notes
·
View notes