#adopt data protection
Text




Since I'm playing Awakening again, I think it's time to bring this back <3
#elaine is very protective of her dad considering he's the only family she's got--#well besides lon qu... and flavia... okay listen i like to think of regna ferox as a big ol found family sometimes fbjdshfs#and well basilio did in fact adopt elaine sooooooooo--#old art from uuuuuh last year i think but it's fine#data log: manda's doodles#elaine (fea)#familial: basili dad#also shout out to adrian for kissing my dad <3
4 notes
·
View notes
Text
Bridging the AI Trust Gap
New Post has been published on https://thedigitalinsider.com/bridging-the-ai-trust-gap/
Bridging the AI Trust Gap
AI adoption is reaching a critical inflection point. Businesses are enthusiastically embracing AI, driven by its promise to achieve order-of-magnitude improvements in operational efficiencies.
A recent Slack Survey found that AI adoption continues to accelerate, with use of AI in workplaces experiencing a recent 24% increase and 96% of surveyed executives believing that “it’s urgent to integrate AI across their business operations.”
However, there is a widening divide between the utility of AI and the growing anxiety about its potential adverse impacts. Only 7% of desk workers believe that outputs from AI are trustworthy enough to assist them in work-related tasks.
This gap is evident in the stark contrast between executives’ enthusiasm for AI integration and employees’ skepticism related to factors such as:
The Role of Legislation in Building Trust
To address these multifaceted trust issues, legislative measures are increasingly being seen as a necessary step. Legislation can play a pivotal role in regulating AI development and deployment, thus enhancing trust. Key legislative approaches include:
Data Protection and Privacy Laws: Implementing stringent data protection laws ensures that AI systems handle personal data responsibly. Regulations like the General Data Protection Regulation (GDPR) in the European Union set a precedent by mandating transparency, data minimization, and user consent. In particular, Article 22 of GDPR protects data subjects from the potential adverse impacts of automated decision making. Recent Court of Justice of the European Union (CJEU) decisions affirm a person’s rights not to be subjected to automated decision making. In the case of Schufa Holding AG, where a German resident was turned down for a bank loan on the basis of an automated credit decisioning system, the court held that Article 22 requires organizations to implement measures to safeguard privacy rights relating to the use of AI technologies.
AI Regulations: The European Union has ratified the EU AI Act (EU AIA), which aims to regulate the use of AI systems based on their risk levels. The Act includes mandatory requirements for high-risk AI systems, encompassing areas like data quality, documentation, transparency, and human oversight. One of the primary benefits of AI regulations is the promotion of transparency and explainability of AI systems. Furthermore, the EU AIA establishes clear accountability frameworks, ensuring that developers, operators, and even users of AI systems are responsible for their actions and the outcomes of AI deployment. This includes mechanisms for redress if an AI system causes harm. When individuals and organizations are held accountable, it builds confidence that AI systems are managed responsibly.
Standards Initiatives to foster a culture of trustworthy AI
Companies don’t need to wait for new laws to be executed to establish whether their processes are within ethical and trustworthy guidelines. AI regulations work in tandem with emerging AI standards initiatives that empower organizations to implement responsible AI governance and best practices during the entire life cycle of AI systems, encompassing design, implementation, deployment, and eventually decommissioning.
The National Institute of Standards and Technology (NIST) in the United States has developed an AI Risk Management Framework to guide organizations in managing AI-related risks. The framework is structured around four core functions:
Understanding the AI system and the context in which it operates. This includes defining the purpose, stakeholders, and potential impacts of the AI system.
Quantifying the risks associated with the AI system, including technical and non-technical aspects. This involves evaluating the system’s performance, reliability, and potential biases.
Implementing strategies to mitigate identified risks. This includes developing policies, procedures, and controls to ensure the AI system operates within acceptable risk levels.
Establishing governance structures and accountability mechanisms to oversee the AI system and its risk management processes. This involves regular reviews and updates to the risk management strategy.
In response to advances in generative AI technologies NIST also published Artificial Intelligence Risk Management Framework: Generative Artificial Intelligence Profile, which provides guidance for mitigating specific risks associated with Foundational Models. Such measures span guarding against nefarious uses (e.g. disinformation, degrading content, hate speech), and ethical applications of AI that focus on human values of fairness, privacy, information security, intellectual property and sustainability.
Furthermore, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have jointly developed ISO/IEC 23894, a comprehensive standard for AI risk management. This standard provides a systematic approach to identifying and managing risks throughout the AI lifecycle including risk identification, assessment of risk severity, treatment to mitigate or avoid it, and continuous monitoring and review.
The Future of AI and Public Trust
Looking ahead, the future of AI and public trust will likely hinge on several key factors which are essential for all organizations to follow:
Performing a comprehensive risk assessment to identify potential compliance issues. Evaluate the ethical implications and potential biases in your AI systems.
Establishing a cross-functional team including legal, compliance, IT, and data science professionals. This team should be responsible for monitoring regulatory changes and ensuring that your AI systems adhere to new regulations.
Implementing a governance structure that includes policies, procedures, and roles for managing AI initiatives. Ensure transparency in AI operations and decision-making processes.
Conducting regular internal audits to ensure compliance with AI regulations. Use monitoring tools to keep track of AI system performance and adherence to regulatory standards.
Educating employees about AI ethics, regulatory requirements, and best practices. Provide ongoing training sessions to keep staff informed about changes in AI regulations and compliance strategies.
Maintaining detailed records of AI development processes, data usage, and decision-making criteria. Prepare to generate reports that can be submitted to regulators if required.
Building relationships with regulatory bodies and participate in public consultations. Provide feedback on proposed regulations and seek clarifications when necessary.
Contextualize AI to achieve Trustworthy AI
Ultimately, trustworthy AI hinges on the integrity of data. Generative AI’s dependence on large data sets does not equate to accuracy and reliability of outputs; if anything, it’s counterintuitive to both standards. Retrieval Augmented Generation (RAG) is an innovative technique that “combines static LLMs with context-specific data. And it can be thought of as a highly knowledgeable aide. One that matches query context with specific data from a comprehensive knowledge base.” RAG enables organizations to deliver context specific applications that adheres to privacy, security, accuracy and reliability expectations. RAG improves the accuracy of generated responses by retrieving relevant information from a knowledge base or document repository. This allows the model to base its generation on accurate and up-to-date information.
RAG empowers organizations to build purpose-built AI applications that are highly accurate, context-aware, and adaptable in order to improve decision-making, enhance customer experiences, streamline operations, and achieve significant competitive advantages.
Bridging the AI trust gap involves ensuring transparency, accountability, and ethical usage of AI. While there’s no single answer to maintaining these standards, businesses do have strategies and tools at their disposal. Implementing robust data privacy measures and adhering to regulatory standards builds user confidence. Regularly auditing AI systems for bias and inaccuracies ensures fairness. Augmenting Large Language Models (LLMs) with purpose-built AI delivers trust by incorporating proprietary knowledge bases and data sources. Engaging stakeholders about the capabilities and limitations of AI also fosters confidence and acceptance
Trustworthy AI is not easily achieved, but it is a vital commitment to our future.
#abby#ai#ai act#AI adoption#AI Ethics#AI integration#AI systems#anxiety#applications#approach#Article#artificial#Artificial Intelligence#assessment#bases#Bias#Building#Business#compliance#comprehensive#content#continuous#court#data#data privacy#data protection#data quality#data science#data usage#decision making
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Adopting rightwing policies on issues such as immigration and the economy does not help centre-left parties win votes, according to new analysis of European electoral and polling data.
Faced with a 20-year decline in their vote share, accompanied by rising support for the right, far right and sometimes the far left, social democratic parties across Europe have increasingly sought salvation by moving towards the political centre.
However the analysis, published on Wednesday, shows that centre-left parties promising, for example, to be tough on immigration or unrelenting on public spending are both unlikely to attract potential voters on the right, and risk alienating existing progressive supporters.
[...]
One of the key lessons was that “trying to imitate rightwing positions is just not a successful strategy for the left”, he said. Two studies in particular, looking at so-called welfare chauvinism and fiscal policy, illustrated the point, the researchers said.
Björn Bremer of the Central European University in Vienna said a survey in Spain, Italy, the UK and Germany and larger datasets from 12 EU countries showed that since the financial crisis of 2008, “fiscal orthodoxy” had been a vote loser for the centre left.
“Social democratic parties that have backed austerity fail to win the support of voters worried about public debt, and lose the backing of those who oppose austerity,” Bremer said. “Centre-left parties that actually impose austerity lose votes.”
[...]
The data strongly suggests centre-left parties can build a coalition of voters who believe a strong welfare state, effective public services and real investment, for example in the green transition, are essential,” Bremer said.
“But doing the opposite – offering a contradictory programme that promotes austerity but promises to protect public services and the welfare state, and hoping voters will swallow such fairytales – failed in the 2010s, and is likely to fail again.”
Similarly, said Matthias Enggist of the University of Lausanne, analysis of data from eight European countries showed no evidence that welfare chauvinism – broadly, restricting immigrants’ access to welfare – was a successful strategy for the left.
936 notes
·
View notes
Text
Interior Department Announces New Guidance to Honor and Elevate Hawaiian Language

"In commemoration of Mahina ʻŌlelo Hawaiʻi, or Hawaiian Language Month, and in recognition of its unique relationship with the Native Hawaiian Community, the Department of the Interior today announced new guidance on the use of the Hawaiian language.
A comprehensive new Departmental Manual chapter underscores the Department’s commitment to further integrating Indigenous Knowledge and cultural practices into conservation stewardship.
“Prioritizing the preservation of the Hawaiian language and culture and elevating Indigenous Knowledge is central to the Biden-Harris administration's work to meet the unique needs of the Native Hawaiian Community,” said Secretary Deb Haaland. “As we deploy historic resources to Hawaiʻi from President Biden’s Investing in America agenda, the Interior Department is committed to ensuring our internal policies and communications use accurate language and data."
Department bureaus and offices that engage in communication with the Native Hawaiian Community or produce documentation addressing places, resources, actions or interests in Hawaiʻi will use the new guidance on ‘ōlelo Hawaiʻi (Hawaiian language) for various identifications and references, including flora and fauna, cultural sites, geographic place names, and government units within the state. The guidance recognizes the evolving nature of ‘ōlelo Hawaiʻi and acknowledges the absence of a single authoritative source. While the Hawaiian Dictionary (Pukui & Elbert 2003) is designated as the baseline standard for non-geographic words and place names, Department bureaus and offices are encouraged to consult other standard works, as well as the Board on Geographic Names database.
Developed collaboratively and informed by ʻōlelo Hawaiʻi practitioners, instructors and advocates, the new guidance emerged from virtual consultation sessions and public comment in 2023 with the Native Hawaiian Community.
The new guidance aligns with the Biden-Harris administration’s commitment to strengthening relationships with the Native Hawaiian Community through efforts such as the Kapapahuliau Climate Resilience Program and Hawaiian Forest Bird Keystone Initiative. During her trip to Hawaiʻi in June, Secretary Haaland emphasized recognizing and including Indigenous Knowledge, promoting co-stewardship, protecting sacred sites, and recommitting to meaningful and robust consultation with the Native Hawaiian Community."
-via US Department of the Interior press release, February 1, 2024
--
Note: I'm an editor so I have no idea whether this comes off like as big a deal as it potentially is. But it is potentially going to establish and massively accelerate the adoption of correctly written Native Hawaiian language, as determined by Native Hawaiians.
Basically US government communications, documentations, and "style guides" (sets of rules to follow about how to write/format/publish something, etc.) can be incredibly influential, especially for topics where there isn't much other official guidance. This rule means that all government documents that mention Hawai'i, places in Hawai'i, Hawaiian plants and animals, etc. will have to be written the way Native Hawaiians say it should be written, and the correct way of writing Hawaiian conveys a lot more information about how the words are pronounced, too, which could spread correct pronunciations more widely.
It also means that, as far as the US government is concerned, this is The Correct Way to Write the Hawaiian Language. Which, as an editor who just read the guidance document, is super important. That's because you need the 'okina (' in words) and kahakō in order to tell apart sizeable sets of different words, because Hawaiian uses so many fewer consonants, they need more of other types of different sounds.
And the US government official policy on how to write Hawaiian is exactly what editors, publishers, newspapers, and magazines are going to look at, sooner or later, because it's what style guides are looking at. Style guides are the official various sets of rules that books/publications follow; they're also incredibly detailed - the one used for almost all book publishing, for example, the Chicago Manual of Style (CMoS), is over a thousand pages long.
One of the things that CMoS does is tell you the basic rules of and what specialist further sources they think you should use for writing different languages. They have a whole chapter dedicated to this. It's not that impressive on non-European languages yet, but we're due for a new edition (the 18th) of CMoS in the next oh two to four years, probably? Actually numbering wise they'd be due for one this year, except presumably they would've announced it by now if that was the case.
I'm expecting one of the biggest revisions to the 18th edition to add much more comprehensive guidance on non-Western languages. Considering how far we've come since 2017, when the last one was released, I'll be judging the shit out of them if they do otherwise. (And CMoS actually keep with the times decently enough.)
Which means, as long as there's at least a year or two for these new rules/spellings/orthographies to establish themselves before the next edition comes out, it's likely that just about every (legit) publisher will start using the new rules/spellings/orthographies.
And of course, it would expand much further from there.
#don't ask me about the magazine and newspaper half of this#bc I do Not know AP style#except the differences I'm annoyed at lol#ap doesn't respect the oxford comma#hawaii#hawaiʻi#language#orthography#linguistics#language stuff#hawaiian#native hawaiian#united states#publishing#book publishing#indigenous#indigineous people#indigenous languages#language revitalization#language resources#editorial
407 notes
·
View notes
Text
The Best News of Last Week - June 26, 2023
1. California's Lake Oroville now at 100% capacity following megadrought; 1st time since 2019

Once a stark example of the drastic effects of California's yearslong megadrought, Lake Oroville has rebounded and is once again filled to capacity, data from the state's Department of Water Resources shows.
Lake Oroville, the state's most beleaguered and second-largest reservoir, is at 100% of its total capacity and 127% of where it should be around this time of year - a huge boost after the climate-change-fueled megadrought sucked away nearly all its water supply.
2. Blue whales are thriving in California waters – the story of their amazing comeback

If you’ve recently taken a Southern California whale-watching tour, you may have been lucky enough to come across earth’s largest animal. Pacific blue whales grow up to 110 feet long and can reach a weight of 200 tons. Decades ago, blue whales were nearly hunted to extinction, and although still listed as protected under the Endangered Species Act, marine biologists and researchers are heralding a “conservation success story,” unlike any other.
According to a study published in 2014 by researchers at the University of Washington, the West Coast blue whale population has bounced back at tremendous levels, recouping 97% of its pre-whaling population
3. Newborn left in Florida Safe Haven Baby Box adopted by the firefighter who found her

Zoey is now 5 months old. Courtesy Zoey's family
A firefighter in Ocala, Florida, was pulling an overnight shift at the station in January when he was awakened at 2 a.m. by an alarm. He recognized the sound immediately. A newborn had been placed in the building’s Safe Haven Baby Box, a device that allows someone to safely and anonymously surrender a child — no questions asked.
“To be honest, I thought it was a false alarm,” said the firefighter, who wished to remain anonymous to protect his family’s privacy. But when he opened the box, he discovered a healthy infant wrapped in a pink blanket.
That baby would become his daughter, Zoey.
4. Iceland suspends whale hunt on animal welfare concerns

Iceland's government said Tuesday it was suspending this year's whale hunt until the end of August due to animal welfare concerns, likely bringing the controversial practice to a historic end.
"I have taken the decision to suspend whaling" until August 31, Food Minister Svandis Svavarsdottir said in a statement. The country's last remaining whaling company, Hvalur, had previously said this would be its final season as the hunt has become less profitable.
5. He wanted to pet dogs for his 100th birthday. Hundreds lined up.

Alison Moore had a unique idea to celebrate her father's 100th birthday: a pet parade filled with as many dogs as possible. Her father, Robert Moore, has always adored dogs and wanted to pet every one he saw. So, Alison took to social media and invited the community to join in the festivities. Little did she know that over 200 dogs and their owners would gather for the heartwarming event.
The parade brought immense joy not only to Robert but also to attendees like Rodger, who has Alzheimer's disease, and his daughter Denise, who hadn't seen her father smile so much in a long time. It was a day filled with wagging tails, smiling faces, and love that made Robert's milestone birthday an unforgettable celebration.
6. Historic decision: Estonia legalizes same-sex marriage

Tuesday, the Estonian government has survived a vote of no confidence in the Riigikogu tied to amendments to the Family Law Act and related legislation, which is granting same-sex couples the legal right to wed. 55 members of the Riigikogu voted in favor of the measure, while 34 voted against.
It is proposed that the institution of marriage, as defined by family law, be modified so that any two natural persons of legal age, regardless of gender, may marry. The words "man and woman" will be replaced with the words "two natural persons."
7. US approves chicken made from cultivated cells, the nation's first 'lab-grown' meat

For the first time, U.S. regulators on Wednesday approved the sale of chicken made from animal cells, allowing two California companies to offer “lab-grown” meat to the nation’s restaurant tables and eventually, supermarket shelves.
The Agriculture Department gave the green light to Upside Foods and Good Meat, firms that had been racing to be the first in the U.S. to sell meat that doesn’t come from slaughtered animals — what’s now being referred to as “cell-cultivated” or “cultured” meat as it emerges from the laboratory and arrives on dinner plates.
----
That's it for this week :)
This newsletter will always be free. If you liked this post you can support me with a small kofi donation:
Support this newsletter ❤️
Also don’t forget to reblog.
1K notes
·
View notes
Link

The western bumble bee (Bombus occidentalis), one of the focal species of the conservation strategy, is currently under review for listing under the Endangered Species Act. This specimen was collected on western mountain aster (Symphyotrichum spathulatum) at a site on the Okanogan-Wenatchee National Forest south of Cle Elum and photographed as part of the Pacific Northwest Bumble Bee Atlas. After recording information about the bee it was released, unharmed. (Photo: Ed Lisowski.)
2K notes
·
View notes
Text
Fintech bullies stole your kid’s lunch money

I'm coming to DEFCON! On Aug 9, I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On Aug 10, I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

Three companies control the market for school lunch payments. They take as much as 60 cents out of every dollar poor kids' parents put into the system to the tune of $100m/year. They're literally stealing poor kids' lunch money.
In its latest report, the Consumer Finance Protection Bureau describes this scam in eye-watering, blood-boiling detail:
https://files.consumerfinance.gov/f/documents/cfpb_costs-of-electronic-payment-in-k-12-schools-issue-spotlight_2024-07.pdf
The report samples 16.7m K-12 students in 25k schools. It finds that schools are racing to go cashless, with 87% contracting with payment processors to handle cafeteria transactions. Three processors dominate the sector: Myschoolbucks, Schoolcafé, and Linq Connect.
These aren't credit card processors (most students don't have credit cards). Instead, they let kids set up an account, like a prison commissary account, that their families load up with cash. And, as with prison commissary accounts, every time a loved one adds cash to the account, the processor takes a giant whack out of them with junk fees:
https://pluralistic.net/2024/02/14/minnesota-nice/#shitty-technology-adoption-curve
If you're the parent of a kid who is eligible for a reduced-price lunch (that is, if you are poor), then about 60% of the money you put into your kid's account is gobbled up by these payment processors in service charges.
It's expensive to be poor, and this is no exception. If your kid doesn't qualify for the lunch subsidy, you're only paying about 8% in service charges (which is still triple the rate charged by credit card companies for payment processing).
The disparity is down to how these charges are calculated. The payment processors charge a flat fee for every top-up, and poor families can't afford to minimize these fees by making a single payment at the start of the year or semester. Instead, they pay small sums every payday, meaning they pay the fee twice per month (or even more frequently).
Not only is the sector concentrated into three companies, neither school districts nor parents have any meaningful way to shop around. For school districts, payment processing is usually bundled in with other school services, like student data management and HR data handling. For parents, there's no way to choose a different payment processor – you have to go with the one the school district has chosen.
This is all illegal. The USDA – which provides and regulates – the reduced cost lunch program, bans schools from charging fees to receive its meals. Under USDA regs, schools must allow kids to pay cash, or to top up their accounts with cash at the school, without any fees. The USDA has repeatedly (2014, 2017) published these rules.
Despite this, many schools refuse to handle cash, citing safety and security, and even when schools do accept cash or checks, they often fail to advertise this fact.
The USDA also requires schools to publish the fees charged by processors, but most of the districts in the study violate this requirement. Where schools do publish fees, we see a per-transaction charge of up to $3.25 for an ACH transfer that costs $0.26-0.50, or 4.58% for a debit/credit-card transaction that costs 1.5%. On top of this, many payment processors charge a one-time fee to enroll a student in the program and "convenience fees" to transfer funds between siblings' accounts. They also set maximum fees that make it hard to avoid paying multiple charges through the year.
These are classic junk fees. As Matt Stoller puts it: "'Convenience fees' that aren't convenient and 'service fees' without any service." Another way in which these fit the definition of junk fees: they are calculated at the end of the transaction, and not advertised up front.
Like all junk fee companies, school payment processors make it extremely hard to cancel an automatic recurring payment, and have innumerable hurdles to getting a refund, which takes an age to arrive.
Now, there are many agencies that could have compiled this report (the USDA, for one), and it could just as easily have come from an academic or a journalist. But it didn't – it came from the CFPB, and that matters, because the CFPB has the means, motive and opportunity to do something about this.
The CFPB has emerged as a powerhouse of a regulator, doing things that materially and profoundly benefit average Americans. During the lockdowns, they were the ones who took on scumbag landlords who violated the ban on evictions:
https://pluralistic.net/2021/04/20/euthanize-rentier-enablers/#cfpb
They went after "Earned Wage Access" programs where your boss colludes with payday lenders to trap you in debt at 300% APR:
https://pluralistic.net/2023/05/01/usury/#tech-exceptionalism
They are forcing the banks to let you move your account (along with all your payment history, stored payees, automatic payments, etc) with one click – and they're standing up a site that will analyze your account data and tell you which bank will give you the best deal:
https://pluralistic.net/2023/10/21/let-my-dollars-go/#personal-financial-data-rights
They're going after "buy now, pay later" companies that flout borrower protection rules, making a rogues' gallery of repeat corporate criminals, banning fine-print gotcha clauses, and they're doing it all in the wake of a 7-2 Supreme Court decision that affirmed their power to do so:
https://pluralistic.net/2024/06/10/getting-things-done/#deliverism
The CFPB can – and will – do something to protect America's poorest parents from having $100m of their kids' lunch money stolen by three giant fintech companies. But whether they'll continue to do so under a Kamala Harris administration is an open question. While Harris has repeatedly talked up the ways that Biden's CFPB, the DOJ Antitrust Division, and FTC have gone after corporate abuses, some of her largest donors are demanding that her administration fire the heads of these agencies and crush their agenda:
https://prospect.org/power/2024-07-26-corporate-wishcasting-attack-lina-khan/
Tens of millions of dollars have been donated to Harris' campaign and PACs that support her by billionaires like Reid Hoffman, who says that FTC Chair Lina Khan is "waging war on American business":
https://prospect.org/power/2024-07-26-corporate-wishcasting-attack-lina-khan/
Some of the richest Democrat donors told the Financial Times that their donations were contingent on Harris firing Khan and that they'd been assured this would happen:
https://archive.is/k7tUY
This would be a disaster – for America, and for Harris's election prospects – and one hopes that Harris and her advisors know it. Writing in his "How Things Work" newsletter today, Hamilton Nolan makes the case that labor unions should publicly declare that they support the FTC, the CFPB and the DOJ's antitrust efforts:
https://www.hamiltonnolan.com/p/unions-and-antitrust-are-peanut-butter
Don’t want huge companies and their idiot billionaire bosses to run the world? Break them up, and unionize them. It’s the best program we have.
Perhaps you've heard that antitrust is anti-worker. It's true that antitrust law has been used to attack labor organizing, but that has always been in spite of the letter of the law. Indeed, the legislative history of US antitrust law is Congress repeatedly passing law after law explaining that antitrust "aims at dollars, not men":
https://pluralistic.net/2023/04/14/aiming-at-dollars/#not-men
The Democrats need to be more than The Party of Not Trump. To succeed – as a party and as a force for a future for Americans – they have to be the party that defends us – workers, parents, kids and retirees alike – from corporate predation.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/07/26/taanstafl/#stay-hungry

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#fintech#ed-tech#finance#usury#payment processing#chokepoints#corruption#monopoly#cfpb#consumer finance protection bureau
208 notes
·
View notes
Text
Good News - August 15-21
Like these weekly compilations? Tip me at $kaybarr1735 or check out my new(ly repurposed) Patreon!
1. Smart hives and dancing robot bees could boost sustainable beekeeping

“[Researchers] developed a digital comb—a thin circuit board equipped with various sensors around which bees build their combs. Several of these in each hive can then transmit data to researchers, providing real-time monitoring. [… Digital comb] can [also] be activated to heat up certain parts of a beehive […] to keep the bees warm during the winter[…. N]ot only have [honeybee] colonies reacted positively, but swarm intelligence responds to the temperature changes by reducing the bees' own heat production, helping them save energy.”
2. Babirusa pigs born at London Zoo for first time

“Thanks to their gnarly tusks […] and hairless bodies, the pigs are often called "rat pigs" or "demon pigs” in their native Indonesia[….] “[The piglets] are already looking really strong and have so much energy - scampering around their home and chasing each other - it’s a joy to watch. They’re quite easy to tell apart thanks to their individual hair styles - one has a head of fuzzy red hair, while its sibling has a tuft of dark brown hair.””
3. 6,000 sheep will soon be grazing on 10,000 acres of Texas solar fields

“The animals are more efficient than lawn mowers, since they can get into the nooks and crannies under panel arrays[….] Mowing is also more likely to kick up rocks or other debris, damaging panels that then must be repaired, adding to costs. Agrivoltaics projects involving sheep have been shown to improve the quality of the soil, since their manure is a natural fertilizer. […] Using sheep instead of mowers also cuts down on fossil fuel use, while allowing native plants to mature and bloom.”
4. Florida is building the world's largest environmental restoration project

“Florida is embarking on an ambitious ecological restoration project in the Everglades: building a reservoir large enough to secure the state's water supply. […] As well as protecting the drinking water of South Floridians, the reservoir is also intended to dramatically reduce the algae-causing discharges that have previously shut down beaches and caused mass fish die-offs.”
5. The Right to Repair Movement Continues to Accelerate

“Consumers can now demand that manufacturers repair products [including mobile phones….] The liability period for product defects is extended by 12 months after repair, incentivising repairs over replacements. [… M]anufacturers may need to redesign products for easier disassembly, repair, and durability. This could include adopting modular designs, standardizing parts, and developing diagnostic tools for assessing the health of a particular product. In the long run, this could ultimately bring down both manufacturing and repair costs.”
6. Federal Judge Rules Trans Teen Can Play Soccer Just In Time For Her To Attend First Practice

“Today, standing in front of a courtroom, attorneys for Parker Tirrell and Iris Turmelle, two transgender girls, won an emergency temporary restraining order allowing Tirrell to continue playing soccer with her friends. […] Tirrell joined her soccer team last year and received full support from her teammates, who, according to the filing, are her biggest source of emotional support and acceptance.”
7. Pilot study uses recycled glass to grow plants for salsa ingredients

“"We're trying to reduce landfill waste at the same time as growing edible vegetables," says Andrea Quezada, a chemistry graduate student[….] Early results suggest that the plants grown in recyclable glass have faster growth rates and retain more water compared to those grown in 100% traditional soil. [… T]he pots that included any amount of recyclable glass [also] didn't have any fungal growth.”
8. Feds announce funding push for ropeless fishing gear that spares rare whales

“Federal fishing managers are promoting the use of ropeless gear in the lobster and crab fishing industries because of the plight of North Atlantic right whales. […] Lobster fishing is typically performed with traps on the ocean bottom that are connected to the surface via a vertical line. In ropeless fishing methods, fishermen use systems such an inflatable lift bag that brings the trap to the surface.”
9. Solar farms can benefit nature and boost biodiversity. Here’s how

“[… M]anaging solar farms as wildflower meadows can benefit bumblebee foraging and nesting, while larger solar farms can increase pollinator densities in surrounding landscapes[….] Solar farms have been found to boost the diversity and abundance of certain plants, invertebrates and birds, compared to that on farmland, if solar panels are integrated with vegetation, even in urban areas.”
10. National Wildlife Federation Forms Tribal Advisory Council to Guide Conservation Initiatives, Partnerships

“The council will provide expertise and consultation related to respecting Indigenous Knowledges; wildlife and natural resources; Indian law and policy; Free, Prior and Informed Consent[… as well as] help ensure the Federation’s actions honor and respect the experiences and sovereignty of Indigenous partners.”
August 8-14 news here | (all credit for images and written material can be found at the source linked; I don’t claim credit for anything but curating.)
#hopepunk#good news#honeybee#bees#technology#beekeeping#piglet#london#zoo#sheep#solar panels#solar energy#solar power#solar#florida#everglades#water#right to repair#planned obsolescence#trans rights#trans#soccer#football#recycling#plants#gardening#fishing#whales#indigenous#wildlife
117 notes
·
View notes
Text


Gelatopod - Ice/Fairy
(Vanilla-Caramel Flavor is normal, Mint-Choco is shiny)
Artist - I adopted this wonderful fakemon from xeeble! So I decided to make up a full list of game data, moves, lore, etc. for it. Enjoy! :D
Abilities - Sticky Hold/Ice Body/Weak Armor (Hidden)
Pokedex Entries
Scarlet: Gelatopod leaves behind a sticky trail when it moves. A rich, creamy ice cream can be made from the collected slime.
Violet: At night, it uses the spike on its shell to dig into the ground, anchoring itself into place. Then it withdraws into its shell to sleep in safety.
Stats & Moves
BST - 485
HP - 73
Attack - 56
Defense - 100
Special Attack - 90
Special Defense - 126
Speed - 40
Learnset
Lvl 1: Sweet Scent, Sweet Kiss, Aromatherapy, Disarming Voice
Lvl 4: Defense Curl
Lvl 8: Baby Doll Eyes
Lvl 12: Draining Kiss
Lvl 16: Ice Ball
Lvl 21: Covet
Lvl 24: Icy Wind
Lvl 28: Sticky Web
Lvl 32: Dazzling Gleam
Lvl 36: Snowscape
Lvl 40: Ice Beam
Lvl 44: Misty Terrain
Lvl 48: Moonblast
Lvl 52: Shell Smash
Friendship Level Raised to 160: Love Dart (Signature Move)
Egg Moves
Mirror Coat, Acid Armor, Fake Tears, Aurora Veil
Signature Move - Love Dart
Learned when Gelatopod's friendship level reaches 160 and then the player completes a battle with it
Type - Fairy, Physical, Non-Contact
Damage Power - 20 PP - 10 (max 16) Accuracy - 75%
Secondary Effect - Causes Infatuation in both male and female pokemon. Infatuation ends in 1-4 turns.
Flavor Text - The user fires a dart made of hardened slime at the target. Foes of both the opposite and same gender will become infatuated with the user.
TM Moves
Take Down, Protect, Facade, Endure, Sleep Talk, Rest, Substitute, Giga Impact, Hyper Beam, Helping Hand, Icy Wind, Avalanche, Snowscape, Ice Beam, Blizzard, Charm, Dazzling Gleam, Disarming Voice, Draining Kiss, Misty Terrain, Play Rough, Struggle Bug, U-Turn, Mud Shot, Mud-Slap, Dig, Weather Ball, Bullet Seed, Giga Drain, Power Gem, Tera Blast
Other Game Data
Gender Ratio - 50/50
Catch Rate - 75
Egg Groups - Fairy & Amorphous
Hatch Time - 20 Cycles
Height/Weight - 1'0''/1.3 lbs
Base Experience Yield - 170
Leveling Rate - Medium Fast
EV Yield - 2 (Defense & Special Defense)
Body Shape - Serpentine
Pokedex Color - White
Base Friendship - 70
Game Locations - Glaseado Mountain, plus a 3% chance of encountering Gelatopod when the player buys Ice Cream from any of the Ice Cream stands
Notes
I'm not a competitive player, but I did my best to balance this fakemon fairly and not make it too broken. Feel free to give feedback if you have any thoughts!
I have a huge bias for Bug Pokemon since they're my favorite type, and at first I wanted to make it Bug/Ice, since any intervebrate could be tossed into the 'Bug' typing. But ultimately I decided to keep xeeble's original idea of Ice/Fairy. There's precedent of food-themed pokemon being Fairy type, and Ice/Fairy would be very interesting due to its rarity (only Alolan Ninetails has it). Its type weaknesses are also slightly easier to handle than Bug/Ice imo
The signature move is indeed based on real love darts, I could not resist something that fascinating being made into a Pokemon move, even if the real games may possibly shy away from the idea. (Honestly it could be argued "Love Dart" is based on Cupid's arrow so Gamefreak might actually get away with making a move like this though.) Its effectiveness on both males and females is a nod to snails/slugs being biological hermaphrodites. I can see this move also being learned by Gastrodon and Magcargo in Scarlet/Violet
#pokemon#fakemon#honorary bug pokemon#pokemon scarlet/violet#pokémon#ice pokemon#fairy pokemon#gen 9#molluscs#snails#mycontent
483 notes
·
View notes
Text
Some thoughts on Cara
So some of you may have heard about Cara, the new platform that a lot of artists are trying out. It's been around for a while, but there's been a recent huge surge of new users, myself among them. Thought I'd type up a lil thing on my initial thoughts.
First, what is Cara?
From their About Cara page:
Cara is a social media and portfolio platform for artists.
With the widespread use of generative AI, we decided to build a place that filters out generative AI images so that people who want to find authentic creatives and artwork can do so easily.
Many platforms currently accept AI art when it’s not ethical, while others have promised “no AI forever” policies without consideration for the scenario where adoption of such technologies may happen at the workplace in the coming years.
The future of creative industries requires nuanced understanding and support to help artists and companies connect and work together. We want to bridge the gap and build a platform that we would enjoy using as creatives ourselves.
Our stance on AI:
・We do not agree with generative AI tools in their current unethical form, and we won’t host AI-generated portfolios unless the rampant ethical and data privacy issues around datasets are resolved via regulation.
・In the event that legislation is passed to clearly protect artists, we believe that AI-generated content should always be clearly labeled, because the public should always be able to search for human-made art and media easily.
Should note that Cara is independently funded, and is made by a core group of artists and engineers and is even collaborating with the Glaze project. It's very much a platform by artists, for artists!
Should also mention that in being a platform for artists, it's more a gallery first, with social media functionalities on the side. The info below will hopefully explain how that works.
Next, my actual initial thoughts using it, and things that set it apart from other platforms I've used:
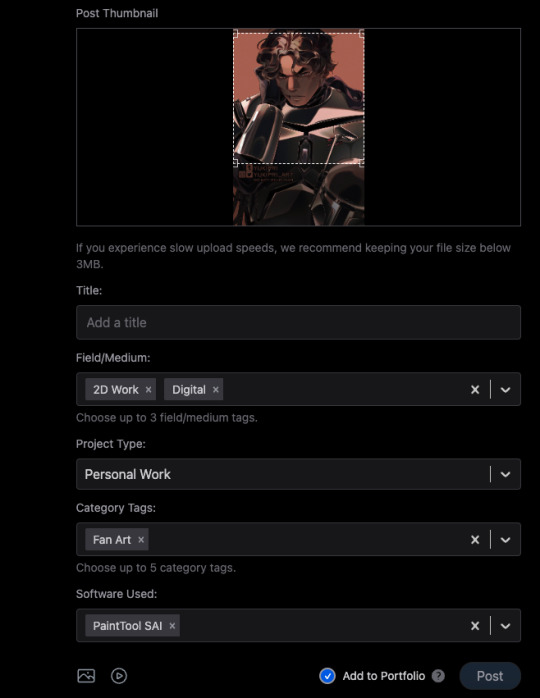
1) When you post, you can choose to check the portfolio option, or to NOT check it. This is fantastic because it means I can have just my art organized in my gallery, but I can still post random stuff like photos of my cats and it won't clutter things. You can also just ramble/text post and it won't affect the gallery view!
2) You can adjust your crop preview for your images. Such a simple thing, yet so darn nice.
3) When you check that "Add to portfolio," you get a bunch of additional optional fields: Title, Field/Medium, Project Type, Category Tags, and Software Used. It's nice that you can put all this info into organized fields that don't take up text space.
4) Speaking of text, 5000 character limit is niiiiice. If you want to talk, you can.
5) Two separate feeds, a "For You" algorithmic one, and "Following." The "Following" actually appears to be full chronological timeline of just folks you follow (like Tumblr). Amazing.
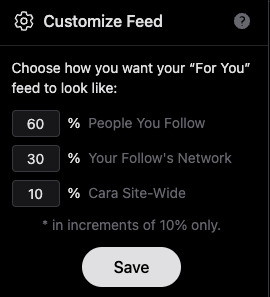
6) Now usually, "For You" being set to home/default kinda pisses me off because generally I like curating my own experience, but not here, for this handy reason: if you tap the gear symbol, you can ADJUST your algorithm feed!
So you can choose what you see still!!! AMAZING. And, again, you still have your Following timeline too.
7) To repeat the stuff at the top of this post, its creation and intent as a place by artists, for artists. Hopefully you can also see from the points above that it's been designed with artists in mind.
8) No GenAI images!!!! There's a pop up that says it's not allowed, and apparently there's some sort of detector thing too. Not sure how reliable the latter is, but so far, it's just been a breath of fresh air, being able to scroll and see human art art and art!
To be clear, Cara's not perfect and is currently pretty laggy, and you can get errors while posting (so far, I've had more success on desktop than the mobile app), but that's understandable, given the small team. They'll need time to scale. For me though, it's a fair tradeoff for a platform that actually cares about artists.
Currently it also doesn't allow NSFW, not sure if that'll change given app store rules.
As mentioned above, they're independently funded, which means the team is currently paying for Cara itself. They have a kofi set up for folks who want to chip in, but it's optional. Here's the link to the tweet from one of the founders:
And a reminder that no matter that the platform itself isn't selling our data to GenAI, it can still be scraped by third parties. Protect your work with Glaze and Nightshade!
Anyway, I'm still figuring stuff out and have only been on Cara a few days, but I feel hopeful, and I think they're off to a good start.
I hope this post has been informative!
Lastly, here's my own Cara if you want to come say hi! Not sure at all if I'll be active on there, but if you're an artist like me who is keeping an eye out for hopefully nice communities, check it out!
#YukiPri rambles#cara#cara app#social media#artists on tumblr#review#longpost#long post#mostly i'd already typed this up on twitter so i figured why not share it here too#also since tumblr too is selling our data to GenAI
175 notes
·
View notes
Text
hi okay so we’re onboard with fox and his droid buddy and all i’m saying is
there’s a universe where the kaminoans weren’t quite as confident in their product and they slid one perfect android into each dispatched division, to report back on defects in the clones in the field. to protect the IP, and all that.
the AD units don’t know what they are. why would they need to know that someone else sees through their eyes? besides, all vode know they are observed from the moment they’re decanted until the moment they die. what would one more set of eyes be, after all that?
anyway what i’m saying is that, in the coruscant guard, those eyes are thorn’s.
but the force is dark on coruscant and it does strange things to thorn’s circuitry. he gets blackouts—but many in the guard experience blackouts. he should report them—he feels strongly that he’s supposed to report them and yet—but it’s probably just the weather. the job. not getting enough fresh air or laps. that’s probably it.
then thorn is lost on scipio, and all his data is lost with him.
(by that point the kaminoans don’t bother issuing new AD units. the war has firmly cemented their galactic reputation.)
time passes. then, one day that resembles every other murky day, a knock comes at fox’s door. it’s honk!, the mouse droid that adopted fox for some absurd reason, and behind him trails—
fox stares. “that’s a b1 in a trench coat.” he jolts to his feet, drawing his blaster in the same motion, and shouts, “that’s a kriffin’ b1 in a karking trench coat! i’m going to hang widget by his toes!”
the clanker dodges the first shot, and the second, and then fox yelps as honk! tases him in the shin and—
“what in haran is going on in here?” stone demands, bullying past the crowd. he stops in the doorway to fox’s office and has to take off his helmet. “i reiterate my question more forcefully.”
fox is hopping, holding onto his shin with one hand, and waving his blaster in the face of a placid b1 droid. a droid wearing a trench coat. a droid with red wings painted on the crest of its chassis.
“honk! is a separatist! arrest these droids!” fox yells. his eyes are wide and his forehead glistens with sweat. he has, stone notes, impeccable balance.
“i’m not a separatist, sir,” the b1 says. “you said they’d never take me, anyway. remember?”
it sounds—
fox’s blaster hand is shaking. “i don’t— i don’t know what you’re— stone! shoot it!”
stone didn’t reach for his blaster. he’d get decommissioned, but he waved off the troopers crowding behind him, and he didn’t reach for his blaster.
at least the clanker would shoot him in the front. stone swallowed.
“sir, i—“
“commander—“ the clanker started.
fox barked a command, underscored with a wave of his blaster. “no!”
a flurry of beeps came from the region of fox’s ankles, loud in the standoff. honk! whirred around fox’s desk and chittered at stone. he glanced at his vambrace, then honk!, then the clank— then the droid. then fox.
fox’s hand was trembling on his blaster. he could’ve shot the droid a dozen times by then but he hadn’t. he didn’t seem able to look away from those red wings for more than seconds at a time.
stone swallowed again.
he’d been wishing for thorn to come back for a long time, and now he finally understood the warning in all those tubie tales. be careful what you wish for didn’t cover even half of it.
#if echo can have his brain uploaded to the system then the reverse can also be true#come with me on this journey#thorn maybe cracked the firewall by accident when he came back#we all have a chip he says#you’re just like me! :):)#cmo shiv like mmm gonna get my scanner out real quick okay#they get him a bunch of purloined battlefield scrap and thorn upgrades himself#(he’d already figured out the voice modulator)#he keeps the trench coat#oh crap i just realised i made him the outlaws droid ahahahha i’m sorry#putting my blorbo in situations#commander thorn#commander fox#commander stone#coruscant guard#star wars#the clone wars#honk! the mouse droid
101 notes
·
View notes
Text
SolarWinds IT Trends Report 2024: Embracing AI – A Boon or a Risk?
New Post has been published on https://thedigitalinsider.com/solarwinds-it-trends-report-2024-embracing-ai-a-boon-or-a-risk/
SolarWinds IT Trends Report 2024: Embracing AI – A Boon or a Risk?
The 2024 SolarWinds IT Trends Report, titled “AI: Friend or Foe?“, provides a comprehensive examination of the current landscape of artificial intelligence (AI) within IT operations. Conducted in partnership with UserEvidence, the report surveyed nearly 700 IT professionals to understand their views on AI, focusing on the benefits, challenges, and future implications of AI and AIOps (AI for IT operations).
Executive Summary
The report explores the dual nature of AI as both a potential boon and a source of concern for IT professionals. While cinematic portrayals of AI often evoke fears of uncontrollable, malevolent machines, the reality in IT is more nuanced. Professionals are evaluating AI’s impact on security, data integrity, and decision-making processes to determine if AI will be a friend or foe in achieving their organizational goals.
Methodology
The survey included IT staff and leaders from various global enterprises, with respondents spanning multiple industries such as technology, manufacturing, finance, telecommunications, and healthcare. Companies of different sizes were represented, ranging from small enterprises with up to 1,000 employees to large organizations with over 5,000 employees.
Key Insights
AI Improves Efficiency and Productivity in IT Teams
Automation and Efficiency: A significant portion of IT professionals (46%) believe that AI investments will lead to increased efficiency, making it the primary driver for adopting AI technologies. AIOps is seen as a powerful tool for automating repetitive tasks, processing vast amounts of data, and providing real-time insights, thus enhancing productivity and reducing the workload on IT teams.
Benefits of AIOps: The integration of AIOps can lead to fewer incidents, faster resolution times, greater visibility, and reduced alert noise. This enhances the overall efficiency and operational capabilities of IT teams.
Strong Confidence in AI Adoption and Implementation
Investment Levels: Nearly two-thirds of organizations have invested $5 million or more in AI technology, with 31% investing over $25 million. This substantial investment reflects strong confidence in AI’s potential to deliver significant benefits.
Future Outlook: A large majority (88%) of respondents have already adopted AI or plan to do so. However, many IT professionals (56%) desire even greater investment in AI and faster implementation to fully leverage its capabilities.
Security and Privacy Concerns
Major Concerns: Security and privacy remain the top concerns, with 47% of IT professionals reporting negative experiences due to these issues. The rapid advancement of AI raises questions about data protection, the integrity of AI models, and the safeguarding of proprietary information.
Regulatory Needs: A substantial majority (88%) of respondents support increased government oversight of AI, particularly in areas related to security (72%) and privacy (64%).
Trust in Data Quality
Data Quality Issues: Many IT professionals are cautious about the quality of data used in AI systems. Poor data quality is the second most significant barrier (16%) to successful AI integration, leading to errors and unreliable outputs.
Government Regulation: More than half (54%) of respondents believe that government regulation should play a role in ensuring data quality and combating misinformation.
AI as a Wise Advisor, Not a Final Decision-Maker
Human Oversight: IT professionals widely agree that AI should function as an advisor rather than a solo decision-maker. While AI can process data and identify patterns, human oversight is crucial to ensure ethical governance, mitigate biases, and maintain trust in AI systems.
Decision-Making: Only 47% of respondents view enhanced decision-making capabilities as a positive outcome of AI, with a majority expressing a need for more comfort and trust in AI’s role in decision-making processes.
Future of AI in IT
The report anticipates that generative AI will become deeply integrated into daily routines within the next two to three years. Early adopters already report significant benefits in areas such as customer support and incident management, with improvements ranging from 30-50% or more in cost savings, response times, and customer satisfaction.
Recommendations for Organizations
Adopt Ethical Frameworks: Implement frameworks like AI by Design to ensure ethical and secure AI development.
Invest in Training: Equip teams with the necessary skills and knowledge to effectively use AI technologies.
Prioritize Human Oversight: Maintain human involvement in AI decision-making processes to uphold trust, safety, and ethical standards.
Support Government Regulation: Advocate for regulatory measures that address security, privacy, and data quality issues.
Conclusion
AI holds immense potential to revolutionize IT operations, but its integration must be approached with careful consideration of security, privacy, and data quality concerns. By adopting best practices and maintaining a balance between AI automation and human oversight, organizations can harness the power of AI to drive efficiency, productivity, and innovation.
This extensive analysis of AI in IT underscores the importance of proactive planning and ethical implementation to ensure that AI remains a beneficial tool for IT professionals and their organizations.
To learn more readers should visit access the AI: Friend or Foe? report.
#000#2024#ai#AI adoption#AI integration#AI models#AI systems#Analysis#artificial#Artificial Intelligence#automation#barrier#Companies#comprehensive#cost savings#data#data integrity#data protection#data quality#Design#development#efficiency#employees#Enterprises#finance#Future#generative#generative ai#Global#governance
0 notes
Text
Humans now share the web equally with bots, according to a major new report – as some fear that the internet is dying.
In recent months, the so-called “dead internet theory” has gained new popularity. It suggests that much of the content online is in fact automatically generated, and that the number of humans on the web is dwindling in comparison with bot accounts.
Now a new report from cyber security company Imperva suggests that it is increasingly becoming true. Nearly half, 49.6 per cent, of all internet traffic came from bots last year, its “Bad Bot Report” indicates.
That is up 2 per cent in comparison with last year, and is the highest number ever seen since the report began in 2013.
In some countries, the picture is worse. In Ireland, 71 per cent of internet traffic is automated, it said.
Some of that rise is the result of the adoption of generative artificial intelligence and large language models. Companies that build those systems use bots scrape the internet and gather data that can then be used to train them.
Some of those bots are becoming increasingly sophisticated, Imperva warned. More and more of them come from residential internet connections, which makes them look more legitimate.
“Automated bots will soon surpass the proportion of internet traffic coming from humans, changing the way that organizations approach building and protecting their websites and applications,” said Nanhi Singh, general manager for application security at Imperva. “As more AI-enabled tools are introduced, bots will become omnipresent.”
231 notes
·
View notes
Text
This plot bunny is eating me alive so I’m going to share it with you guys so you can suffer too. I’ll never write it as I’m still trying to finish TBB Echo gets yoinked back in time because the disaster trio (Fives, Hardcase, Jesse) are idiots.
So Fives dies in that warehouse right, except he wakes up hours later only he’s a tooka kitten. Promptly gets adopted by Guard shinies much to his irritation. But very quickly realizes oh wait things are actually pretty fucked up here. And so begins Fives’ adventure to save the galaxy while also adopting a battalions worth of brothers even if they’re older then him.
I have scenes of him hauling a data pad he swiped from the Guard CMO with Fox’s blackout records up the stairs of the Jedi Temple. To the Temple guards amusement, as they assume an initiate or padawan sent the little tooka to fetch their lost homework. Fives doesn’t find it nearly as amusing because force that’s a lot of stairs.
Exposing Palpatine after sneaking into his office by hiding under Padmes dress. Of course this is after appreciating the truest extensive amount of hidden weapons she has.
Haven’t decided if Echo would play a role or not. Have a really heartbreaking idea of him confronting Fox all the while Fives is right there trying to protect Fox while also wanting to run to his twin back from the dead. So much potential.
#plot bunny#I’ll never write this#arc trooper fives#the coruscant guard#arc trooper echo#commander fox#swtcw
145 notes
·
View notes
Text
Hi 👋 This is chapter four of the Estranged Uncle Au!
Just a warning there is mentions of cults and a scene that has Damian being Damian (AKA knife child) Please take care of yourselves! I hope you enjoy!
Clark was sweating buckets.
“I promise you I’m not in danger! This is all a big misunderstanding! Bruce isn’t even that creepy!”
Jazz rattled off several reasons.
“He has a cloyingly sweet public persona, his personal computer has extensive information on all of the local rogues in the area and all the adopted sons we’ve met look practically identical to both each other and you and Danny! Not to mention they all seem trained for combat! How is that not creepy?”
Okay from an impartial standpoint Clark could see how it looked like he was tied up in a cult.
“I swear if another fruitloop billionaire obsessed with one of my family members tries to adopt me I’m gonna wail!”
How specific!
“Wail?” Clark began to ask but was cut off.
“Are you tied up in a cult Clark? Because we can get you out if you are! I … uh know a guy who specializes in taking down cults.”
What?
“I promise you I’m not in a cult! The blue eyes and black hair is a coincidence and I am not in danger! Also what do you mean you know a guy who specializes in taking down cults!?!”
Danny squinted.
“Hold that thought. Everyone stop talking!”
Danny reached towards Clark’s shoulder and picked out a small device, no bigger than a grain of rice out of his cable knit sweater.
“No one who plants listening devices into sweaters isn’t creepy.”
He then promptly threw it to the ground and crushed it with his heel.
“That’s the end of the recording.” Tim said while cringing.
“Sleazy?!? Me? Sleazy? I did a back handspring on hardwood floors for them and they call me sleazy?!”
Dick thought that he could win them over. Was he too heavy handed?
“It’s probably because you fell asleep in the pico de gallo timber.” Jason joked as he inspected the weapons vault.
“What? Me?!? I was the only one who made any headway! I was just up late trying to track whoever was hacking us!” Tim defended.
“Well good news! You found ‘em! Let me know when they hack my library account seeing as the Big bad bat computer is being hacked by a couple teens.” Jason said dismissively as he took a flamethrower fuel canister.
Bruce was experiencing a new amalgamation of emotions. He was both incredibly embarrassed, incredibly amused and incredibly impressed.
How embarrassing that the bat computer was hacked! He put so much effort into the protection of his data!
But then again Clark must be beside himself trying to convince them he wasn’t in a cult and that was incredibly amusing. He even said all the things that people said when they were in denial about being in a cult!
This was absurd! The only way to describe this was absurd!
“Fools! All of you do not truly understand the gravitas of the situation! If they believe that we are indeed weapons dealers they may snoop further and compromise all of our secret identities!” Damian huffed his way into the view of his family.
“We’ll be alright Dami, Tim is reinforcing our defenses for the computer and we’re going to try and disengage for a while. If we keep on trying we might make it worse.” Dick ruffled through Damian’s hair despite many protests.
Damian tutted at this suggestion. They needed to approach the problem head on and quickly rectify the situation lest it spiral into a larger one. Perhaps if they suffered an accident.
“Damian! I know that face! That’s the face you make when you go off and try to rectify the situation by yourself!”
“That is not true Grayson! I was simply thinking about confiding in my companion about how tedious my science project is.”
“You promise you’re only going to engage in age appropriate activities like science homework and book reports?”
“I promise.”
"I'm choosing to believe you" Dick began to walk away before pulling another sour face. "...Sleazy?"
Damian checked his hidden blades one final time before encroaching upon this Daniel Fenton who had foolishly entered an alleyway. He deftly held a knife to the throat of his target.
"If you continue to snoop into my father's business I will not hesitate to cut you down!"
Damian was expecting to me met with fear and copious apologies. He was a fearsome and terrifying warrior after all.
"Are you trying to hold me at knifepoint on your tippy-toes?" The target said in the same tone that one would use with a kitten trying to jump a bit too high. They should be focused on the clear danger Damian was posing. Or at least the danger he was posing. Between the moment Damian looked at his feet and the moment he looked back up to find a very unperturbed Danny.
"Did your father put you up to this?" He asked.
"No! I acted of my own accord!"
"Well are there anymore ineffective threats you want to say?"
Damian was about to say something when his stomach audibly growled. Curses! He could not bring a meal in order to maintain secrecy from Alfred! Damian slowly looked up towards Danny's face. He has that look that Grayson gets before he does something annoying like ruffle his hair.
"Are you hungry?"
Damian did not dignify this question with an answer and began to storm off.
"I'm having some friends over, we can spare you a plate! My friend Sam chose the menu though so its vegan."
Damian stopped in his tracks.
"What is it that you are making?"
"Cauliflower gnocchi with cashew cream pesto."
"And this is taking place in Clark's home?"
"yep."
"Fine. But I will not be lenient with you because you've offered me a meal!"
Danny laughed and texted Sam
"Hey get another bundle of basil Im bringing a guest"
#estranged uncle au#dp x dc#Give clonk a moment to explain himself!#Damian Wayne thinks he is the best at solving issues quickly#Danny: We are having *fancy food you can eat*#Damian: ... fine. You may live a few more hours.#Also Alfred already knows what Damian is doing and where he is. He's just letting the punishment be him missing an Alfred-cooked lunch#Clark isn’t in a cult he swears!#tw cult mention#tw knife
621 notes
·
View notes