#all I can see is there was an error creating a dump file and 1 second later critical crash with no additional info
Explore tagged Tumblr posts
Text
Alright this has gotta stop happening.

I was just playing WEBKINZ.
#i'm digging in the event viewer and I best guess i have is it has something to do with this volmgr error?#all I can see is there was an error creating a dump file and 1 second later critical crash with no additional info#just got a new boot SSD so this might be the culprit#from what i can see volmgr has something to do with drive volume management so makes sense
10 notes
·
View notes
Text
Sketch BOOM | Saura Edition

GREETINGS WEIRDOS OF TODAY AND ROBOTS OF TOMORROW IT'S ME, CLARK!
Would you also believe it’s been a little over two years since my last Sketch BOOM? Of course not! Most of you are undoubtedly scratching your heads wondering what that is. Sketch BOOMs are basically doodle dumps where the goal was to cram in as many characters as I could. The record was set in 2015 with 108 characters, by the way. Pity most of those characters haven’t been seen since then. In the meantime focus has been turned towards other inhabitants of the Clarktooniverse, like Saura here! Before the tragic death of George Floyd, the blue beast’s human persona was meant to be a white teenager. It was that moment of senseless violence that made me wonder if more could be done with my stories. After all, storytelling is meant to teach empathy. Jim Henson created Fraggle Rock as a bid to achieve world peace. Even if that goal was never achieved, he had the courage to try. Thus inspired by real world events, The Owl House, Brooklyn Nine-Nine, She-Ra and the Princesses of Power, Disney’s Dinosaur, and Korra, Saura’s human persona became a black-latina lesbian named Sarah Bosewick. Oh, did I mention her last name was also a tribute to the late Chadwick Boseman?
Being a black-latina made life difficult for poor Sarah. Her anger issues didn’t help matters. Nor did suddenly gaining the ability to transform into a bright blue humanoid dinosaur. Y’know, average relatable problems. Given these great powers has offered Sarah to fight back against social injustice, corrupt politicians, and other prehistoric creatures. All in the name that the world will be a better place for her little sister. In the meantime she also serves as the subject for my first character-focused boom. Expect one of these every month. For now I figured Saura and friends would make a good subject for this month, seeing as June has Pride Month, Dinosaur Day, and Juneteenth. Lucky coincidence, no? With all that out of the way, let’s check out each sketchie from right to left.
[1] THINKING OF YOU
Patricia Arif was one of the first few individuals to learn Sarah Bosewick’s secret. It helped that the Islamic girl was outside crying when her fellow student transformed for the first time to save someone. Up until then, Patty’s life was perfect. She was popular in school thanks to her industrialist father practically owning their hometown of Fosslin, Arizona. Until he filed for a divorce that is. Not only did it shatter the illusion of her perfect family, but soon the girl’s friends abandoned her too. Soon after Patricia wore her mother’s old hijab to hide her tears. Luckily she found real friends in Sarah and Darwin (more on him later), even helping develop tools and a costume for the former. A form fitting costume that the taller girl doesn’t think about all the time. Just like Sarah totally doesn’t imagine her girlfriend in a burkini. Totally.
You can thank @zernna and @burningthrucelluloid for the inspiration regarding said burkini, by the way. Alec is a frequent collaborator on these stories and paid the anarchistic alien to draw these two lovely ladies rocking some summer swimwear. I’ve always meant to draw it for myself and this seemed like the perfect opportunity. Same goes for finally giving a face for Sarah Bosewick, though not without trial and error. Full disclosure, I actually edited this last minute. Our titular heroine’s hair originally looked like what you saw in Patty’s thought cloud. Then it dawned on me how hard it’d be to draw so it was switched out for a pixie haircut. Look closely and you can see where the edits are. Especially since Patricia and Sarah are too busy looking at each other.
[2] HAIL TO THE KING
Saura’s appearance in the world also brought back some regular dinosaurs back to life. This included a tyrannosaurus the townsfolk quickly named ‘King’. Funny enough he was actually set on being a female inspired by the rex from Jurassic Park. However, that was before I envisioned a mighty menace with a flock of feathers around its neck akin to a lion’s mane. Ironically drawing it proved to be a big pain in the ass so the feathers were downplayed. Oh well. It’s still a T-Rex and Saura’s gonna make a habit out of punching it in the face. BE IMPRESSED!
[3] PREHISTORIC POWERHOUSE
Like I stated before, Alec is a frequent collaborator on this story. One of his contributions is Robin, a hyper-evolved bracheosaurus who’s been around the block. Mainly due to being older than she looks. Her backstory has yet to be fully developed, but she’s a stubborn old girl harboring a heavy ‘down with the man’ attitude. Unlike Saura (or ‘Idiota’ as the elder calls her), Robin gave up on civilization years ago and is contempt living in the desert. What we do know is that the older dino was once a female luchador. At least that’s what I decided after drawing this outfit. I also have her a head design harkoning back to Eda and Camila from the Owl House. Will probably change the hairdo in the future to be longer. Until then, remember that size doesn’t matter. Unless you’re a huge-ass brachiosaur.
[4] DARLIN’ DARLA
One of my new rules moving forward is to include one villain in every BOOM. My mind is full of evil characters and it feels like they never get enough attention. Thus I’d like to introduce you all to Darlin’ Darla. She’s a Utahraptor with a nasty attitude. Girl was raised by an abusive foster mother before becoming a badass, biking bounty hunter with her sisters. Eventually someone hires them to take out our hero and are quickly taught why that’s a bad idea. Not that it ever stops the cranky cowgirl from trying.
Darla almost didn’t make the cut for this compilation. The main reason was because her head is shaped like a normal dinosaur and I hesitated to finalize that design. Anybody who draws dinosaurs will know these animals are hard to draw from the front. Luckily those other artists convinced me to go with this. Such as Zerna, who once admitted drawing her shark demon Sadi from any view other than the side was a pain. Heck, even Genndy Tartakovsky cheated when depicting velociraptors in Primal. If even amazing artists like these two struggle with that, then I can find a way. Maybe the colors can be swapped out too. What was used here isn’t as flattering as I had hoped. Expect that to be changed in the future, especially since Darla’s demanding it. One has to wonder what’s worse: her guns or her teeth!
[5] BET ON THE VET!
People are often surprised to meet Sarah’s adopted brother, Darwin Doolittle. What? You can’t see the family resemblance? After living his life in an abusive household, the Bosewicks took him in around the same time Saura had discovered her powers. The process has not been without its injuries. Lucky for the big blue brawler, Darwin wants to be a vet. So much so that he’s sworn to a life of veganism, a fact his friends constantly tease him over. Lovingly so, mind you. Despite any differences, Darwin is a member of the family. Everybody knows this young man is gonna go far. Helps that he’s one of the first to get an up-close study of dinosaurs.
Honestly, I threw in Darwin here to fill some space. From the start it was determined he’d be featured in this BOOM, just not how. Helping an injured parasaurolophus seemed pretty cool. Just be thankful you’re not seeing what Dar is…
[6] I KISSED A DINO (AND I LIKED IT!)
Really, what would’ve been the point of all this if I didn’t draw Patricia and Sarah smooching at least once? Like I said on BlueSky: GAY DINOSAURS ROCK!
[7] YOU’RE MY HERO
At the end of the day, one question remains: Why? Why would Sarah subject herself to this lifestyle? One that involves facing down psychotic predators, crooked cops, and greedy governors. Pain is a constant. Especially when it seems like the fighting never really stops. The world already spat in her face, so why should she even care? Because that world is home to Girasol Bosewick. It’s that spark of optimism in this five year old’s eyes is what gives her older sibling the strength to keep going. Ultimately Saura wants a world where her hermanita never has to experience what she did. A world free of judgmental stares, false assumptions, and itchy trigger fingers. Picturing a future where little Gigi is free to be whoever she wants to be? You better believe it’s worth every broken bone. That’s why, if you asked Saura, she’d say Girasol is the real hero.
Who inspires you to be the best you can be? Are they a sister, your romantic partner, or somebody else? Let me know in the comments below and feel free to tell me what you think of these sketches. Until then, MAY THE GLASSES BE WITH YOU!
#SketchBOOM#Clarktoons#Clarktoon Crossing#dinosaur#Saura#Sarah Bosewick#prehistoric#superhero#sisters#raptors#western#original characters#Pride Month#Pride Month 2025#Arizona#Juneteenth#brachiosaurus#parasaurolophus#vet#tyrannosaurus rex#lesbian#bisexual#artists on tumblr#utahraptor
4 notes
·
View notes
Text
Guide to editing textures in Harvest Moon Animal Parade
Due to there being very little info on modding/editing HM:AP on Dolphin Emulator I went ahead and made a quick guide for anyone looking to do the same! (This will also work with Harvest Moon Pride Parade!)
Here’s an example of a quick edit I did of the playable character:

Textures in this game are super easy to edit! However, it does require a bit of work finding the texture you want to dump.
Dumping Textures:
Using Dolphin to dump and edit textures is really simple, however you must use Dolphin and only Dolphin. Dolphin uses its own naming convention for textures, so you cannot use them on any other emulator or on a physical Wii.
Get your iso booted up to play the game. I recommend skipping any intro scenes before continuing.
On the Dolphin emulator interface click on Options -> Graphics Settings -> Advanced. Next, under Texture Dumping, check the 'Enable' box and make sure ‘Dump Base Textures’ is checked as well.
Play the game! Dolphin will only dump textures it encounters in-game. So if you want the Harvest King’s textures, you will have to beat the entire game in order for them to get dumped! (annoying, but it does save you from having thousands of pngs uploaded to your computer at once.)
All the dumped textures will be png files located in your Documents folder on your computer: Dolphin Emulator -> Dump -> Textures -> RBIEE9(This number may be different for you - this is for the North American iso). If you played through the game with textures being dumped enabled, you will find an enormous amount of pngs ranging from blades of grass to entire houses due to everything you see in game being a texture! In order to avoid this, if there is a specific texture you want dumped, find it in-game and then turn on texture dumping to only dump the current textures on screen.
“I want to edit a character's face! Where the heck is that texture?” A character's face texture will look like this:

“Ok, now I want to edit their hair and/or clothes!” That is no problem for any character besides the playable character. The body and hair texture is combined into one, (the face here doesn’t matter - don’t edit it) so it will look like this:

For the playable character, the body and hair textures are also combined, however, there are a LOT of outfits to choose from. So if you want to change your character’s hair to black, you will have to change it on every outfit you want to use! It is annoying, but that also means you could have a different hair color for different clothes!
Editing and Inserting:
Ok, so now you know how to dump textures and where to find them! To edit them, use any program you want, but you MUST keep the EXACT name of the png.
1. To then see them in your game, go to your Documents folder -> Dolphin Emulator -> Load -> Textures. The Textures folder will be empty, and you need to create a folder with the same title of the file you found the dumps in. If you didn’t dump any textures and are simply uploading textures someone else edited and you don’t know what to name the file, right click your game on Dolphin, choose properties, click info, and the first part of the game ID is what you are going to use. (In most cases this is RBIEE9. If you are using Pride Parade, most likely it will be CBIEE9). (If you cannot find your game listed on Dolphin, make sure you set up a path to your game under Config).
2. After making the file (titled ONLY the correct combo of letters and numbers), you can then insert whatever texture pngs you edited. Remember, they MUST have the same name as the original texture so Dolphin knows what texture to replace.
3. Now, boot up the game, and done! You should see your edited textures in-game! (Make sure you exit the game and reboot if you are currently playing.) This can be done on a brand new game or a game you have been playing with for a while!
I have yet to find any errors due to editing textures so there should be no worries. Even doing crazy things like making a character transparent seems to have no effect on the game itself.
“This is annoying, hasn’t someone already uploaded these textures so I don’t have to dump them myself?” Unfortunately, from my research, no one has done so. There are a few possible reasons:
1. The naming conventions for textures may differ from game to game
2. It may not be legal to simply upload an entire game’s worth of textures out there for anyone to edit
3. There just isn’t enough interest in this game!
Luckily, I plan on creating some google drive folders of the face and clothes textures of all playable characters, bachelors, and bachelorettes for anyone to edit and insert into their own game! Also, if you know you have a specific texture you want to edit but you don’t feel like doing these steps or you currently have no way of reaching said texture, let me know and I should be able to grab it for you if you are using a RBIEE9 iso!
Have fun editing textures and let me know if you have any questions!
62 notes
·
View notes
Text
A Sense and A Feeling: Umbrageous (Ch 2)
Umbrageous (adj): apt to take offense.
—————–
WC: 3k
Characters: reader, Wrecker, Hunter, Crosshair, Tech, Nala Se, Shaak Ti shows up on a holo, a guest appearance from ~ an ~ AZI unit
Reader is AFAB, gender-neutral, sometimes referred to with feminine terms by other characters
Warnings: disappointment
Summary: Crosshair finds himself on a rollercoaster of satisfaction and regrets upon Tech pulling up your file; Hunter is really beginning to regret whatever he’s allowed his brothers into.
A/N: I’m sorry in advance for the info-dumping kind of chapter and any errors and for this taking so long.
For any curious what chakrams are, here is a video on them. As for sais, here is a video on them. They are more popularized than chakrams (Elektra and Teenage Mutant Ninja Turtles use em, whereas the only major character to use a Chakram was Xena).
Also, I fucked up the months in the first chapter because I forgot Star Wars standard months don’t work like our standard months, so uh just uh ignore that uh.
(Story masterlist)
Previous Chapter // Next
—————–
Back in their barracks, each boy is quick to shuffle off to their own space. Processing what the hell just happened is not something they can effectively do together. Not when all of their reactions are violently different.
Hunter is more exasperated than anything; Wrecker is excited in the prospect of a new member, albeit subdued in his reaction from the pain killers he is on; Tech is somewhere between curious and apprehensive; Crosshair is, well, sulking quietly.
“They got you good, Cross,” Wrecker teases as Cross quickly maneuvers around the wall of boxes he keeps around his bunk.
“Shut up, Wrecker.”
“Hopefully it will only leave a temporary bruise, and you will not be left with a deformed face,” Tech comments, sliding into his own and physically connecting his datapad to the port he created to connect to Kamino’s database.
Cross pauses his search for an ice patch. “What did you just say?”
Tech smiles. “Nothing at all.”
Hunter closes his eyes while removing his armor, pretending he did not hear what Tech just said. If he didn’t hear it, Cross can’t get mad at him later about it. Right?
“What can you find on them, Tech?” Hunter finally asks after a few moments of silence in the room.
Well, as silent as it can be on a stormy planet in a room filled with four men.
“Not much,” he replies, shifting in his bunk to at least remove his pauldrons. “The Jedi keep their files remarkably well sealed. They typically keep them as close to a physical record as you may find now, and even if you were to obtain a file, some can only be opened by Jedi. Ingenious design.”
“Tech,” Hunter warns.
His second youngest brother scoffs and adjusts his goggles.
“I was able to find their transfer papers when they were reassigned to Kamino. I was right about them being a failed Jedi.”
Crosshair sits up just a little at that. Maybe there is some salvation in this incident.
“They were reassigned from the Medical Corps where they were on special reassignment already from the Council of Reassignment, seeing as it is typical for a failed Jedi to enter the Service Corps, which include the Educational Corps, Exploration Corps, and Agricultural Corps. They were asked for personally by General Shaak Ti to come here to train medics and learn more about Kaminoan medical technology.”
Hunter begins to undo his boots after ensuring all of his armor is stacked neatly as he does every night, only this time he is especially ready to just flop into bed with a pillow over his head. They do not need the entire history of the Jedi Order to accompany a few questions about a medic.
“How long have they been a medic?”
“Says here since 1 GrS.”
Hunter sighs. The first clone wasn’t even born until 3 GrS. “And it’s now 14 GrS. So 13 standard years of training.”
Tech leans out of his bunk and looks over at Hunter. “There is a behavioral analysis attached if you are curious.”
“No,” Crosshair growls as Wrecker and Hunter reply, “Yes.”
Hunter glares at Cross, who can’t even see him from his position lying down and blockaded in. “If they are going to force us to take on another person, we should know what we are dealing with.”
Wrecker, who just took his next dose of pain medication, is quick to simply agree.
“It says here, and I quote, ‘(___) is brash with a tendency towards rudeness and boorish behavior. When treating patients, however, they show kindness rarely seen. See previous assessments for more information.’”
Hunter finally lies down, too mentally drained to do anything more physically. “Anything else?”
Tech scrolls further. “A combat assessment dated yesterday.”
Wrecker leans forward at that. “What’s it say?”
“Summary says: ‘Despite being given no formal training in combat per request of the Council, they still excel with their chosen weaponry and in heavy armor. Still unable to properly use a blaster and is banned from using a lightsaber, however.’”
“They can’t use a blaster?” Crosshair chuckles.
Ridiculous. The Jedi, Kaminoans, whoever expects his brothers to bring someone unable to use a blaster into battle?
“Well, we did see their weaponry four days ago. They have two very ancient yet effective designs and given this video…” Tech sends it their holo display in the middle of the room. “I would say they are made of beskar.”
They watch as you deflect blaster bolts with your sais, much like Jedi do with their lightsabers. It’s clear you still move like most Jedi; moving smoothly and effortlessly, utilizing predictive movements to stay just slightly ahead. But the weaponry is shorter, requiring more action on your behalf, and on your upper-back rests a set of four circular disks with open centers, thin and sharp from what the holo shows.
“Where the hell did they get beskar?” Crosshair mutters.
“They’re good,” Wrecker sleepily compliments.
It switches from the first video to a video beginning with the circles in your hands, two each, recording as you alternate throwing them, and they ricochet against set bounce points while slicing precisely through targets set throughout the entire room. They return to your hands in the same order in which you threw them, gloves preventing them from cutting your hands. From offscreen, someone says something, at least the brothers assume, because you look over your shoulder, just past the camera with a frown.
Then the holo switches again. It’s the citadel exercise, but the way they’ve seen it set up when the Jedi are here. The ground is moving, columns randomly extending to heights beyond everything but the final platform's highest point.
There is nothing particularly unique about the way you go about the course. Not anything they haven’t seen before, per se. The only difference is your weapons.
Before you can finish, however, your foot catches on the edge of a rising column, and you go tumbling down thirty or so feet, landing hard on your tailbone. The knife you threw has already hit the target, finishing the exercise, thus stopping the firing from the turrets and introduction of new droids to the arena. Still, you technically failed the exercise by not making it up to the end yourself.
General Ti is watching from above, and as she does with every exercise she observes, she turns and exits after staring for a moment. But there is not a look of concern or understanding. It is somewhere between analysis and disappointment, and the second the door closes behind her, you pull your fingers together. The four training droids near you practically disintegrate into nothing more than unrecognizable scraps of metal.
“That’s not terrifying,” Crosshair quietly mutters, suddenly not as cocky about you not being able to fire a blaster.
“What are those circular things?” Wrecker asks, his last ounce of energy being slowly sapped away.
He’ll have to thank Tech for whatever extra he gave him.
“I believe they are called chakrams.” Tech looks down at his datapad, trying to find more information on the design they have only read about once several years ago when they were much smaller cadets. Or maybe he read about it. “They are of an ancient design, similar to her other weapons, and hard to throw as precisely as she does. Though if the Jedi did not let her train with a lightsaber, I suppose figuring out precision with these is easy.”
“Anything about a home planet?” Hunter inquires.
Tech might as well tell him as if he does not, Nala Se or Taun We will by tomorrow.
“It’s been redacted. In fact, all personal information is redacted.”
“Isn’t that normal for a Jedi?” Crosshair grumbles. He’s sick of this conversation.
“No, it is not. I could look at General Shaak Ti’s and see her date of birth and home planet, at minimum. This is extremely rare.”
Crosshair chuckles, pulling the ice patch from his nose. “No wonder they’re so angry then. No clue where they came from, not even how old they are.”
Hunter turns his head. “What do you mean?”
“Tech just said he could find the General’s. So some failed out medic’s info should be much easier. It’s not. Which means it doesn’t exist.”
“Crosshair is probably right, Hunter.”
Tech is distracted as the rest fall quiet and get ready to sleep.
Intelligence tests, dexterity and fitness tests, ship mechanic tests, medical equipment repair tests, and general education scores are almost inconsistent with one another. For a standard human female, they are all well above average. Still, dexterity outpaces fitness to an almost frightening degree, and the intelligence score is far too high for someone with such low standard academic scores.
Following that almost random collection is your specialty tests. The ones that are actually relevant to your field. Your medical test scores are perfect or near perfect. Signed off to perform surgeries and cybernetic attachments without droid help, certified field medic, emergency medicine, certified for post-humous analysis, excellent scores on Jedi-specific skills like Force Healing (which most Jedi don’t ever succeed in learning).
You were right.
He’s passable (in the medic aspect).
You’re perfect.
“So why did the Jedi fail you?” He whispers to himself.
“What was that?” Wrecker shouts from across the room after panic-waking, worried Tech may have been trying to talk to him.
“Nothing!”
“I’m turning the lights out,” Hunter announces, feeling near-insane at this point in the night.
—————–
How the flimsi hasn’t crumbled yet, you aren’t sure. Flimsi like this doesn’t even exist commonly anymore and is very expensive, so for someone to just have it on them to write a note and leave it on a baby is strange. Impossible. Wrong, almost.
Planned?
“A rescue, huh,” you whisper. “If I ever meet you, I won’t know whether to punch you or thank you.”
It’s a sad routine, but one you’ve had since you could read:
Read the note out loud. Wonder who left you, wonder if you will dream of them. Wonder if you will ever meet them. Tuck it back into whatever spot you’ve decided is its little hidey-hole for where you are at, then go to bed.
A shrill, singular beep pulls you from thought.
Someone’s pulled up your confidential file using a ghost profile. Untraceable, meant not to even show up on a log. You know better than to let someone do that to you.
“Suppose it’s only fair,” you mutter, knowing precisely who is looking at your information. “I’ve seen yours; now you see mine.”
—————–
The following morning, you awake to a distinctly metallic knock on your door.
You have no lessons to teach, no meetings to attend, nothing to do. You planned on sleeping in for once, reveling in the small break you are given.
Of course you cannot even be allowed to do that.
“I was instructed to drop these off to you,” the AZI droid who sometimes joins you says, holding out a stack of clothes.
“What are these?”
The droid blinks once. “Your Medical Corps uniform for combat.”
You take them from the droid but stare at the pile with concern. “It’s… white?”
“I am just in charge of giving it to you.” There is a pause. “I will be back with a few other things.”
Unfolding the first thing in the pile and placing the rest on the middle briefing council of your converted room, you hold the undershirt and pants up that were stuck together. You’ve already got dozens of these shirts. They are a part of the Medical Corps uniform anyway for those who choose not to wear traditional robes. Many choose not to while in the Center, so these are readily available. They seem to be in every closet back in the Temple’s medical center on Coruscant. From what you remember, every time you went looking for something, you actually needed. The only other requirement is a white jacket of some kind, Medical Corps logo stitched on the left breast. The only difference you can find is the pants the droid just handed over are form-fitting in nature rather than the slightly flared and loose cut you typically are dressed in.
The jumpsuits are white as well, with burgundy panels. You sigh. White? In the field? You’ve seen the plastoid the clones wear after one mission; forget fabric that you actually need to wash.
Forget the times you’ve had to rid of white clothing due to blood soaking it through.
You can forgive white for beneath the jumpsuit, but not for the jumpsuit itself.
Putting down the white sleeveless shirt and pants, you take a closer look at the jumpsuit. Your fingers trace the front of it where the Medical Corps signet is stitched in. For 12 years, you saw it every day on everything. Stitched on uniforms, painted on viewports and walls, printed onto plastoid, and lasered into durasteel.
You haven’t actually seen it beyond the one fraying on your Medics coat in about eight months now.
It’s almost comforting to see again. It was the longest period of stability you ever had, even if it was fraught with poor behavior and disapproval. It was home.
“I have the rest of the items for you, sir.”
Turning to the droid, you watch as it carries in a clear box filled with something plastoid.
It’s armor pieces, based on the shape. White, plastoid armor adjusted for your personal measurements but the same as every clone from what you can tell. Boring.
And dangerously useless.
At least they thought of you.
“Is there an armory here?” You ask with a grimace. Then you add, “With a forge?” Upon realizing that yes, Kamino has an armory. Of course, it does.
“Yes, sir.”
You look back at the white plastoid and smile.
—————–
Your vambraces are already designed how you want, as well as your helmet. You’ve been using both of them to show clone medics ways to use their HUD to do certain medical scans, seeing as medics’ helmets are slightly different, and one of their vambraces has at least a minor interface beyond comms in it.
They’re beskar, pulled from the black-painted pile you were found in. You recently painted them a dull light gray to look like plastoid, so it isn’t obvious that they are drastically different in material when teaching. There is no need for distractions like what alloy is wrapped around you when teaching how to read brain scans on the field and their proper treatment.
“You are not allowed in here,” a Kaminoan you don’t recognize says as you try to enter the forge room.
“I—”
“She can go in.”
You turn to see Nala Se behind you. She nods, allowing you through, and the other Kaminoan says nothing.
How she knew precisely where you were is suspicious, but you’ve learned to stop questioning how they can so easily get to and find you. It is a genetic facility, after all, and they are probably biometrically tracking everyone who enters. A concern you brought up to Shaak Ti, who agreed but ultimately dismissed it as she determined if that were true, it was a worthy trade-off.
You insisted otherwise, but even other Jedi waved it off as something worth ‘handling later.’
So never.
The forge is relatively large, which you are not surprised about. Tipoca City was converted into a military base within the past 10 years. The room is filled with a few of the trainers who were either allowed to stay on or chose to stay on even after the Jedi discovered the army, trainers that do not mind you due to your unique relationship with said Jedi.
Because most of them do not have a good relationship with the Jedi.
In the back corner sits a forge that looks perfectly fine and safe to use but not up to the Kamino Standard, as you call it. Where everything must be spotless and perfect despite that not being necessary at all. It’s empty, a layer of dust threatening to collect on it due to lack of use, and perfect for what you need to do.
“Time to redo my armor,” you mutter to yourself, pulling out the black-painted beskar armor pieces you pulled apart a good decade ago from the box you dragged with you.
Based on what the clones wear, designs you have seen from years of reading and exploring the Coruscant underworld, and what you know of Mandalorian armor, you get to work forging.
—————–
You aren’t sure how many hours you spend in there, but you do know you went just after you were woken in your pajamas, and you are starving now.
-
Hunter sighs as he stands in front of your room’s door. They should all be apologizing, going to you, and asking for forgiveness for their poor behavior. Instead, it’s just him. Crosshair’s ego is too bruised, Wrecker is getting checked on, and Tech is scared you might yell at him.
Tech usually is not so meek, but after witnessing you break Crosshair’s nose, he doesn’t want to risk confrontation. Hunter is sure it’s about something else. His brother spent all night staring at his datapad, not moving once after he first opened your file.
Hunter is partially convinced it’s the same reason he is here. Sure, as the leader, he should be making amends and ensuring cohesion, but he’s also been told to “keep an eye on that Jedi” and “keep her docile” and some other nonsense.
Not that he even knows what the hell any of that’s supposed to mean.
He’s about to knock, hand held up to the door, when a voice rings out behind him.
“What are you doing?”
He turns to see you carrying a heap of armor in your arms, white paint streaked on your face, and what looks like pajamas of all things on your body. Not medic clothes, not armor underclothes. Pajamas.
It’s nearly dinner time.
“I came to apologize for yesterday.”
You brush past him and open the door to your room. “Why?”
He hesitates outside.
“You can come in.”
So he does.
The room looks more like an old meeting room that has been converted, and considering your location in the maze that is Tipoca, he wouldn’t be surprised if it actually was. A briefing console sits in the center. It’s clearly lived in but impeccably organized and clean. An entire wall is covered in flimsi diagrams and charts, while another is floor-to-ceiling drawers. Lived in, organized.
But it’s dark. Darker than how he and his brothers keep their room, even with the lights clearly turned on. There is an almost sinister feel it, even if entirely unintentional.
The distinct crashing noise of you tossing the armor on the console breaks Hunter from his trance.
“My brothers and I can be a lot to handle on our own,” he begins, eyes still noting everything he can. “When we’re forced into a situation, we tend to fight back as hard as we can. Our behavior wasn’t appropriate.”
You slide past him again to grab the box that once held the extra beskar you had so you can place your armor in it. “No, but informative.”
Hunter pauses and furrows his brows. “So you aren’t mad?”
You open it and begin to place the freshly forged pieces inside. “I’m furious, but not at you or your brothers.”
“Oh, uh. Okay.”
You glance over your shoulder to look at him. “Anything else?”
“Yes, actually. We leave tomorrow for our first mission with you.”
With a soft laugh, you turn to your container again and continue to place the pieces carefully. “Guess we’ll see then if we work together or not.”
“Guess we will. Do you need anything before then?”
For you to get out of my space.
Hunter turns his head just slightly to the right, ears picking up the faintest whisper. Far too quiet to understand, far too quiet for him to even locate where it is. Possibly nothing at all, or if anything, a pipe down the hall.
“No.”
“Got your uniform?”
You nod towards the undersuit and jumpsuit. His eyes glance over to the crumpled pile of white and burgundy, and he raises his brows. Surely you don’t plan to walk into battle with white-colored under armor?
“Just finished redoing my armor to be more like what they gave me. That’s what I was carrying.”
So you do.
“Can I see?” He asks.
Now it’s your turn to hesitate.
“As long as you put it all back.”
He picks up the first piece, your chest piece, painted a burgundy. He glances to see every piece of armor is painted a burgundy that matches the emblem embroidered on the jumpsuit you gestured to. It’s heavy, much heavier than the plastoid he sees sitting on a table across the room.
Beskar. Just like your chakrams, your sais, the knives you have. So much goddamn beskar.
“This is heavy. Really heavy. Are you sure you’ll be able to do what you need to in it? There’s a reason we use a plastoid alloy.”
“I’m sure.” You cross your arms. "I’ve been wearing it ever since I was old enough to.”
Hunter raises a brow and scoffs. “The Jedi let you wear this?”
“Uh, not really. Story for another time, perhaps.”
Hunter nods and sets it back in the box. Now is not the time to pry.
“Nervous?”
“Not really.”
The way your body is reacting says otherwise, Hunter internally grumbles.
“Well, I will see you tomorrow then.”
The hesitation about you is rolling off of him in waves; every few seconds, he calms and borders on trusting you, and then it resets, his worry evident once again. Worry is settling over him once again - this time determined to stay.
So you decide to prove to him he doesn’t need to worry. He turns, and the second he reaches the door, you throw one of your knives to slide just past his ear.
He snatches it out of the air by the handle.
“What was that about?” He demands.
“I can handle myself just fine.”
There is something in your eyes he noticed yesterday but did not take note of until now. A subtle color change, a glow so subtle that he figured it was just the lights yesterday. But there are no red lights in your room that could possibly be casting that hue onto you this time.
“Hear you loud and clear.”
—————–
Next
—————–
Taglist
@ABRABEE @DARKANGEL4121 @AQUAOCTOZOMBIE
#tbb hunter x reader#tbb hunter imagine#tbb hunter fic#sergeant hunter x reader#tbb imagine#sergeant hunter imagine#asaf fic
23 notes
·
View notes
Photo

After a few years of trial and error, I think I've finally found the perfect organization method.
In the early years of high school, I had a bullet journal. I was an artsy kid who found a way to combine art with organization in a way that benefited other parts of my life.
However, as I approached the end of high school, my schedule got busier, and I was involved in a lot more things, so owning a bullet journal was less practical. Because of that, I switched to an app called Edo Agenda.
I continued with digital planning in college since I knew I wasn't going to have as much time. But all the apps I tried out—Taskade, Actions by Moleskine, Any.do, Todoist, Wunderlist—weren't suited to my planning and organizational needs. They didn't have the specific functions I required and didn't incorporate an organization system I liked to use. The predefined apps were too restraining, but the more customizable apps weren't customizable enough.
So then I switched to a bare bones, uber minimalist bullet journal method. That worked pretty well my second semester. It was simple, portable, and most importantly, flexible—all the things one could wish for in a planning system. However, it wasn't always the most convenient to use since I couldn't effectively integrate all the different aspects of my life, which, to no surprise, is mostly recorded digitally.
There was just one huge problem with my digital organization system that made me hesitant to switch back in the first place: everything was fragmented. Notes were in Google Docs. Financial records were in Google Sheets. To-Do Lists were in my bullet journal. Team projects were in Trello. My poetry was on Bear. Things I wanted to try are carelessly pinned to random pinterest boards or added to my YouTube "watch later" playlist. It was a mess.
Over the summer, I found out about Notion from a friend, and I thought, this has so much potential, it could even be exactly what I need. It's essentially like an empty notebook on your computer with functions that make it 10x more powerful. Notion allows you to integrate all aspects of your life and work into one app. Some of the advantages that have made me partial to Notion are:
Even greater customization level. Notion is a blank canvas with tons of predefined blocks and different file types. You can make databases, spreadsheets, Kanban boards, to do lists, etc. Also, you can remain connected to other digital services. You can link websites, collaborate with other users, use different structures (e.g. documents, databases, tasks), embed images and videos, etc. There are also tons of formatting options, e.g. text color, highlight, heading v. body text.
Better organization. Notion allows you to have pages within pages within pages within pages—an infinite hierarchy that you can organize with tables of contents. These pages are made of blocks, e.g. tables, checklists, boards, databases. Both pages and blocks can be rearranged by simply dragging and dropping them to where you want them to be. In other words, I guess it's kind of like building a website to organize your life. Plus, their database feature is especially powerful as it allows you to connect all your data and get into as much detail as you wish (each entry in a database is its own page).
Templates. There are tons of templates created by both Notion and the community that you can use. These are especially helpful in the beginning since Notion does have a rather steep learning curve. There are template for almost every category: personal, planning, finance, job applications, design roadmap, etc. Check out their template gallery, this medium article called "10 Notion templates to inspire your use", or read on for my own examples!
Shortcuts. This makes typing and documenting so much faster. Notion uses Markdown, which is a text-to-HTML conversion tool, e.g. # = Heading 1, *, - = bullet point, etc.
Notion has some pretty awesome features, but how does one actually use it? Personally, I have four top-level pages: my planner, my personal journal, songwriting, and blogging.
Planner
I've been using my planner to, well, plan and track my day to day activities as well as my week and month. The way I've structured it is a calendar or monthly overview with links to pages of weekly overviews, and if needed, daily overviews within the weekly overview. This links things up so nicely, i.e. I don't have to be constantly flipping pages in my physical bullet journal or planner to find what I need.

I also have entertainment lists, which is mainly a table with all the shows I want to watch, the books I want to read, etc. I keep track of whether or not I've watched them, as well as my personal ratings. What I love most about this is that each entry is its own page, so I can type my notes for each book, show, or film and easily find them in the future. (Also the reason why I have plural “lists” instead of just one entertainment list is because you can filter entries by type of entertainment, e.g. movies, tv shows, books, articles.)
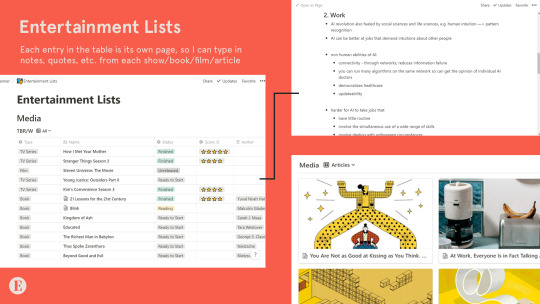
Personal
For personal notes, goals, journal entries, etc. This is kind of like an extension of my daily journal and just where I dump all my thoughts and keep track of the different aspects of my life: mental, emotional, spiritual, social, physical, and travel.
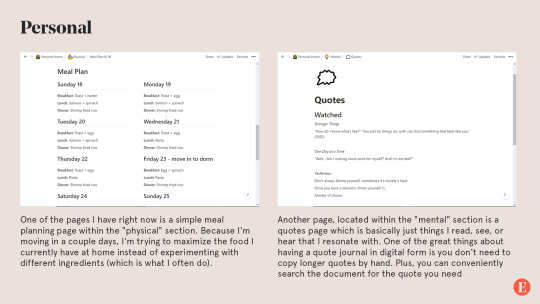
Another page I have is called "Stray Thoughts" and, well, it's pretty self explanatory. It's a lot easier to dump all my thoughts as they come and reorganize them later. Of course, this requires sacrificing the rawness of journaling, i.e. when the thoughts come and how you process them, which is why I still keep a regular journal that I write in daily.
Songwriting
I've been writing a lot of music over the summer and it's often hard to keep track of all of my songs and how far I've gotten in the songwriting process. So I created a table of songs - each entry of a song is a page with its lyrics. These are then tagged with the status of the lyrics (i.e. completed, in progress) and the status of the music itself (i.e. melody only, instrumental, mixing, mastering, revised). Eventually, I'll include demos in the database by embedding audio files in the document.
I have a separate section for inspiration and ideas, which is a kind of brain dump, e.g. words I think would make a good song, a certain theme for a song, a melody that's been stuck in my head, a vibe I'd like to try out, etc.
I've also been watching a lot of tutorials for music production and there's a section where I write my notes for that.
Eintsein
The last section of my Notion app is for this blog. Which has pages for
New posts. These are ideas for future posts, asks that I think would need longer answers, as well as posts that are currently in the draft stage (like this one was before I posted it)
Design assets. This is where I put all the visual branding material for Eintsein.com to be used in posts and any visual material on the blog.
FAQ. Having an FAQ document just makes it so much easier to make changes to your existing FAQ. Plus, if you ever change your FAQ theme, you just have to copy and paste what you already have.
Post directory. I keep track of all my previous masterposts, infographics, and generally longer and more comprehensive posts. It's the exact same as what you see on my Navigation page. And yes, the document contains direct links to the post.
New theme. A project I've been working on the past couple days is trying to create my own theme for my blog. This is where I put all my outlines, brainstorming notes, design inspiration, code snippets, etc.There are some pretty awesome features I’ve made use of in this page:

As you can probably tell, I'm absolutely obsessed with Notion since it has such awesome features and endless possibilities for customization. So far I've been using Notion for personal projects, which, since they are quite big in scale and have no set deadline, are important to organize well. My summer courses were only 6 weeks and weren't difficult to organize.
The formats above are just how I personally use notion. You could make some of your own, or if you don't think you want to build your pages from scratch, there are tons of templates to choose from. Here are some I think I'll be using in the near future and may be helpful for others as well, especially students like myself:

One drawback, however, is that Notion has a rather steep learning curve, but there are tons of tutorials online (especially YouTube) and I guarantee you it's all worth it.
Notion is not just a productivity app. It's a way to concretize your entire life.
Notion is free to use, but there are higher tiers that allow for more blocks, greater file size, etc. I use a personal account, which is $4 per month with unlimited block storage and no file upload limit (although I got it for $33/year). Personally I think the free plan would suit most people's needs, especially if you're not uploading large files.
#mine#eintsein#mymp#notion#apps#productivity#studyblr#studyspo#study hard#organization#document#graphic#design#infographic#masterpost#advice#tips
5K notes
·
View notes
Link
In a previous article I discussed the possibilities of increasing your safety online by using measures such as encryption, VPN and Tor. Nonetheless I did not cover all possibilities and most importantly it was a practical discussion rather than a theoretical one. This article will be a theoretical dissection of online anonymity tools and their weaknesses.
Why do people get caught despite using Tor? Can anyone be truly anonymous online ?
This article will be a summary of the work of Tom Ritter, presented at DEFCON 21, the annual hacker conference. His video presentation can be viewed here and the printed version of his article here.
While doing a great Job, Tom’s work is heavy on tech jargon and might confuse laymen. So I will summarize his work and explain the strengths and weaknesses of modern anonymity tools. His work was published in 2013, but remains relevant today as well.
In his work Tom talks about 4 anonymity technologies : SSL, Tor, Remailers and Shared Mailboxes. Let’s discuss them one by one.
SSL

SSL stands for Secure Socket Layer and is a common online security standard used by the likes of Facebook and other major websites. The way SSL works is that it creates an encrypted tunnel of communication between 2 parties so that third parties cannot read the messages they are sending to each other. Despite being secure on paper, it can be circumvented rather easily. To understand how, first we must talk about metadata.
Metadata
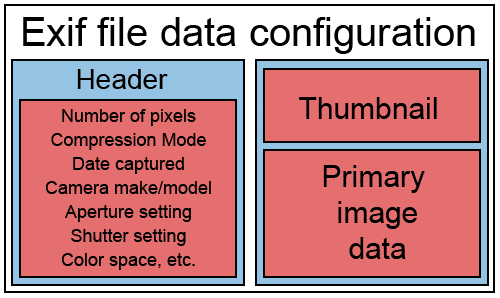
Metadata is data that describes other data. For example, library cards which hold the name of the book, its publishing date and its location in the library is a form of metadata. Metadata is also used in IT.
An example of metadata is the EXIF file in photos. When you take a photo with a camera you not only register the photo, but usually your device also adds extra info such as the date the photo was taken, the GPS location, phone brand, etc. and stores it in the photo file.
Other form of metadata is not registered but can be inferred. For example, someone created a program that can discover which parts of Google maps you are looking at based on the size of map tiles you are downloading.

When you are using SSL you are unwillingly lending third parties metadata which can lead to your discovery, particularly the time the message was sent and the size of your messages.
This allows for attackers to do something called a correlation attack.
Correlation attacks are primarily of 2 types : Time-based attacks and Size-based attacks
Time-based attack
In order to perform a time-based attack a party sends a message in an encrypted stream, then it looks at who receives the message. Since SSL communication is instantaneous, you can easily infer who is behind the SSL stream. The third party sends a message at 15:59 and whoever happens to get the message right afterwards must be the person they are looking for.
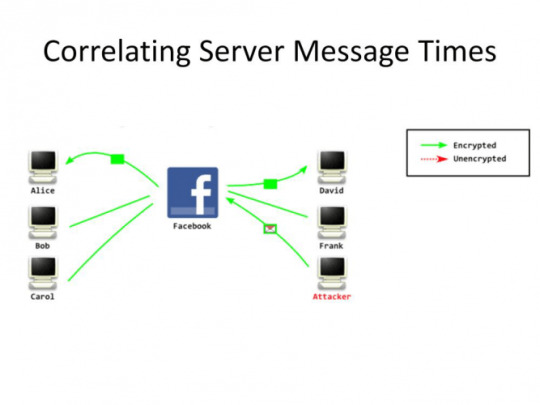
This type of attack was used against the person who dumped Stratfor mailpools. The way it worked is that government analyzed the time he was logging in on the internet and noticed it coincided with the time the person they suspected logged on to a secret chat through Tor. Not only that, rumor has it the government cut electricity to his house at a certain hour and noticed that the user of the secret chat logged out at the same time. The coincidences were too much, so he got caught.
Size-based attack
In order to perform a size-based attack, the third party sends a file of an unusual size, and then whoever receives the file must be the person they are looking for. Since most people on Facebook send small messages to each other, one only needs to send a very large message and see who happens to receive a message of that size afterwards.
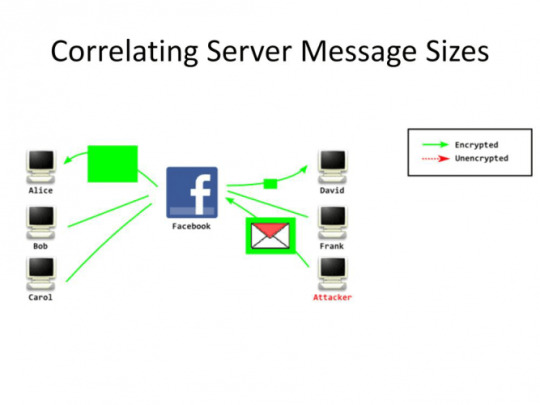
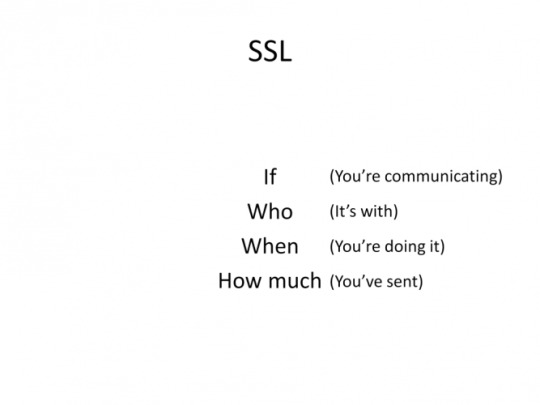
As you can see correlation attacks render you vulnerable if you use SSL as your only line of defense. The reason is because the Third Party can not see WHAT you are sending, but they know that you ARE sending something, WHEN you do it and HOW BIG is the file.
Ideally they should not even know you are communicating with anything at all. So, let’s see what other technologies have to offer.
Tor
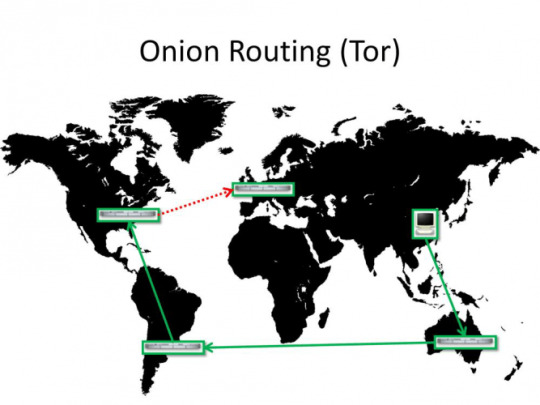
Tor is a custom browser based on Firefox with extensions that works on the principle of connecting to a few nodes so that when you look at a website the only thing the website can see is the last node you traveled through and on the opposite side your ISP (Internet Service Provider ) can only see your first node, not the whole route.
This is already getting better. However it does not add that much anonymity since now third parties do not know WHO is communicating, but they can still see that it DOES happen, WHEN it happens and HOW BIG the size of messages are.

Not only that, but there are known vulnerabilities, particularly of 3 types.
You are viewing a website in the country you are in.
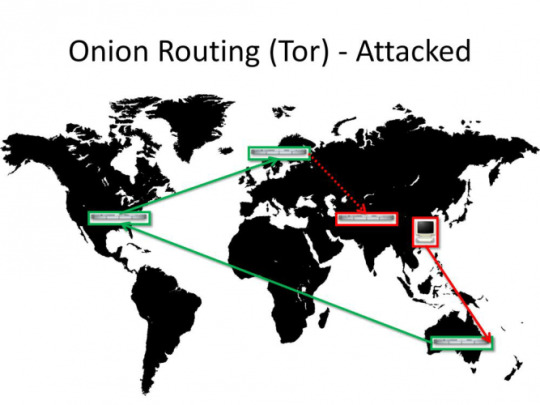
This allows advanced opponents calculate that it was YOU who was using Tor. It is difficult, but not impossible. This is bad news since a lot of people from US view websites stored in US. And so do dissidents from China or Iran.
Every single node you pass through is compromised
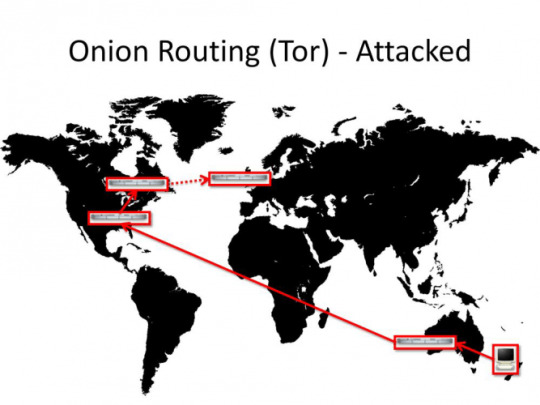
In my previous article I mentioned that the government can set up Tor nodes that they monitor. But to successfully pull an attack they would have to monitor EVERY node you go through.
This requires NWO level trickery, but again, we already have examples of this happening already with VPN agreements. Countries in the Anglosphere have an agreement to give away information regarding VPN usage by suspects from respective countries. This agreements is called Five Eyes. I wouldn’t be surprised if a similar thing is organized regarding Tor nodes.
Passive traffic analysis
Although not mentioned by Ritter in his presentation, it is common knowledge that an opponent with a lot of resources, mostly governments, could analyze the whole network and correlate patterns to discover who is viewing a certain website or communicating with someone.
To give an analogy, it would be like the police heavily patrolling every single street in a city and every single car , so that even if your car had fake plates they could notice patterns and discover its owner.
The problem is, this approach can create false positives, with a 10% chance of error, which is why these analyses are not accepted in court as proof. But you can rest sure if such an analysis points to you, you will be put under further investigation and it only gets worse from there.
So what can be used to further aid us ?
Remailers
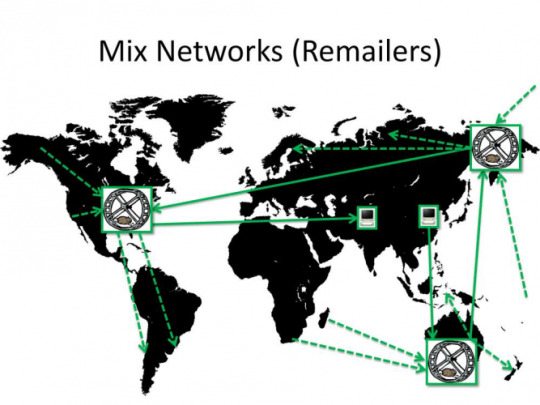
Remailers are an interesting concept. The way they work is that people pool their mail messages on a server, after which some time passes and all mails are sent simultaneously at the same time.
This is supposed to protect from Time and Size based correlation attacks.
The problem here is that it still allows third parties to see that you ARE sending a message, WHEN you sent it and HOW BIG it was. But they can’t see the other end. For the receiver, he has the same problem. Third parties can’t know WHO he got the message from, but they can still see WHEN he receives it from the remailer and HOW BIG it is.

On top of that, for Remailers to work lots of people have to use them at the same time. Otherwise if there are few users, an enemy can still use size-based correlation attacks.
It’s hard to use size-based attacks when thousands of people are sending messages of various sizes, but if only three people at one time are using a Remailer, then it is very easy to do a size-based attack.
Shared mailbox
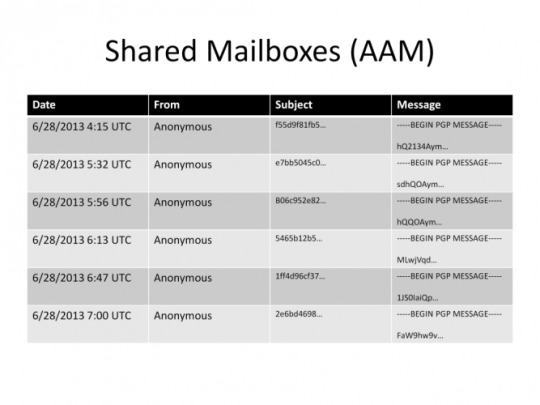
Shared mailboxes are the most out-of-the-box anonymous solution.
The way a shared mailbox works is that users share a mailbox. They cannot delete messages from it, but can only add encrypted messages to it. And when they want to check if they received a message they download all messages and use their key and try to decrypt the header of all of them and see if any of the messages belong to him.
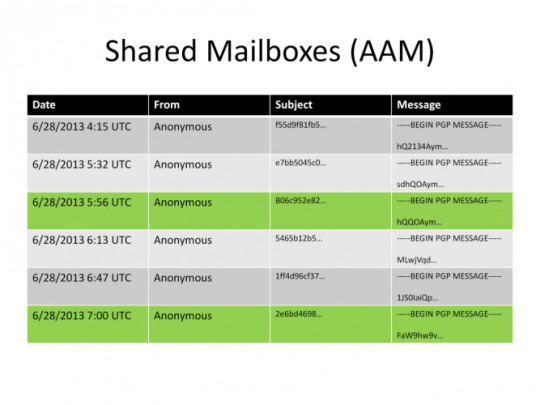
It is a resource-tedious process, but it offers a great payoff. For the receiver this is great because when he downloads the whole mailbox third parties can’t know if he received a message, maybe he did, or maybe he didn’t. For the sender however, the equation stays the same as before.

This is for the moment the most powerful anonymity solution out there. However it has a few issues. In order to use alt.anonymous.message (the shared inbox) you need to have some degree of technical skill, and user inexperience leads to issues.
In order to be easier to use alt.anonymous.message allows the use of nymservers. Nymservers act as regular mail addresses, which when sent to, automatically post them to alt.anonymous.message .
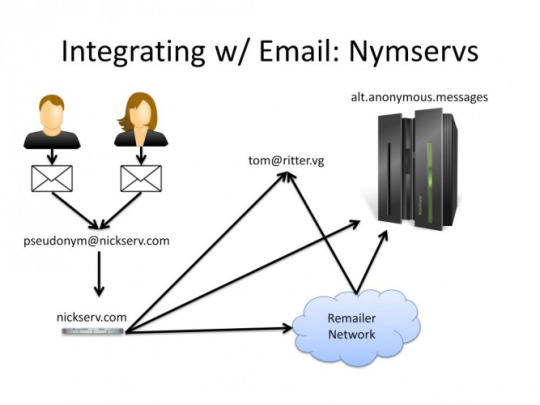
There are however issues with AAM and Nymservers.
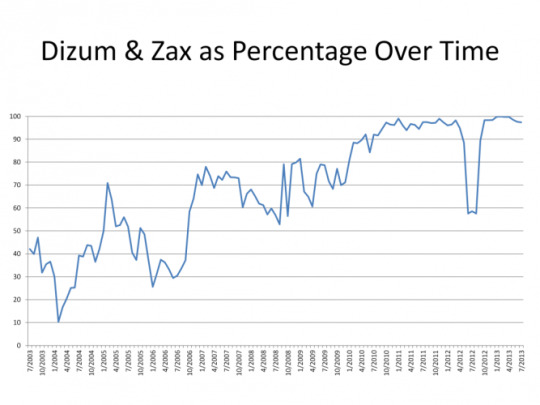
1. Poor network diversity
The number one issue is there are currently two main node operators: Zax and Dizzum, which are responsible for the trafficking of messages to alt.anonymous.message. If both were to retire or be arrested it would the death of alt.anonymous.message. As you can see, network diversity is horrible.
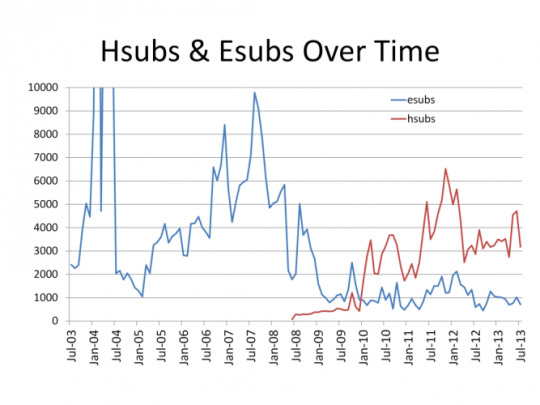
2. Poor encryption used on messages
Another issue is the type of encryption used. Some messages used the outdated MD5 encryption standard which is easy to crack.

Also, the title of messages are encrypted less strongly in order to be able to determine quickly which belong to you and which don’t. Subjects can be encrypted using either hsubs or esubs. Esubs is an older and stronger standard, but hsubs have grown in popularity in recent years.

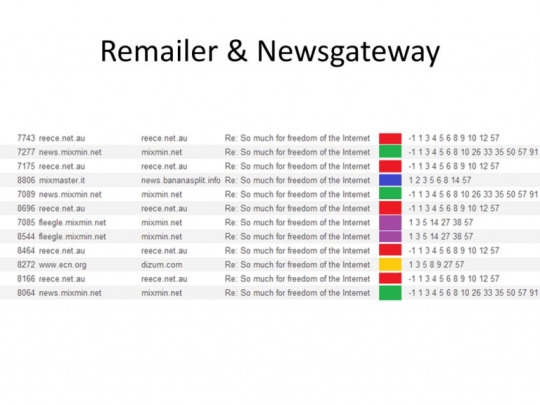
3. Pattern analysis due to use of same subject line and same remailers
A lot of messages use the same subject over and over, people tend to reply to a particular subject. On top of that most people also usually use the same remailer over and over, you can start noticing communication patterns :
4. Custom Remailer command errors
There are different type of remailers. The old school one was called Type 1 and lives on in the protocol of Mixmaster. It allows a lot of customizing options for the header. The users often screwed up the name of the command, which ended in the title of a message.
For example if you write “X-No-Archive Hello Friend” it would turn into “Hello Friend” and the X-No-archive would be interpreted as a command to not archive. But if you wrote “no-archive-x Hello Friend” you messed up so the title would become “no-archive-x Hello Friend”. If you do this multiple times, you would be identified as a unique user since your titles would all contain “no-archive-x” or uncapitalized “x-no-archive” or whatever other combination of mispelled commands you use.
Since most people used the same commands over and over and did the same mistakes they became quickly identifiable as unique users.
5. Imperfect Remailers
There are different types of remailers. Currently there are two types of remailers in use, MixMaster and MixMinion. MixMinion has certain advantages over MixMaster. But both suffer from certain problems.
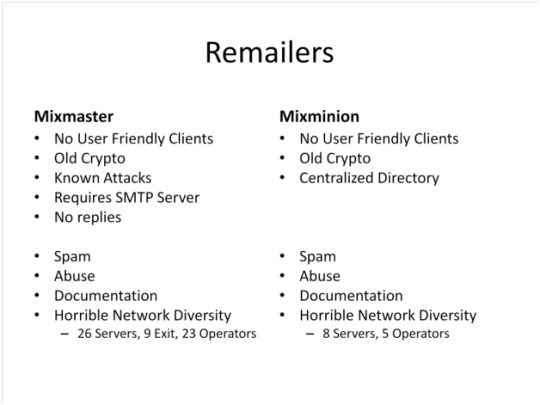
6. Nymservers which do not protect from size-based correlation attacks
Nymservers themselves have problems. Zax’s Nymserver is instantaneous which allows for size-based correlation attacks. However even Type 1 Nymservers (older ones) which are not always instantaneous still allow for size-based correlation attacks given a bit of perspicacity.
Therefore we identified main issues with AAM (alt.anonymous.message):
1) Giving users options allows for segregation and profiling 2) Some encryption is weak 3) It can be complicated to use and allows for beginner mistakes 4) Weak network diversity
Nonetheless, Ritter identified the most secure way of using AAM :
1) Use a strong passphrase and hsub 2) Use Type 3 PGP packet (Key Stretching) 3) Use Remailers 4) Do not use extra headers or options
The issue here is that if you do it properly you will still be part of a small community of people doing so (around 500 – 1500 people), which will make you looks suspicious and will cause the government to look closer into you and maybe add you to a database.
Solutions of the future
Pynchon gate
Pynchon Gate is a project meant to replace shared mailboxes. It uses Private Information Retrieval. It exposes less meta-data, scales better and resists flooding and size-based attacks. However it is currently work in progress

Improved Remailers
MixMinion is currently the best remailer protocol and as such should be used as a basis for future improvement. Planned improvements include things such as improving TLS settings and moving to a new packet format.

What is currently lacking
As of right now, what is lacking is some tech that could be used to anonymously share large files. AAM and such are low bandwidth, which means it can only be used to share small files like text messages.
A new service needs to be created to cover this niche. In the words of Tom Ritter :
But what I keep coming back to is the fact that we have no anonymity network that is high bandwidth, high latency. We have no anonymity network that would have let someone securely share the Collateral Murder video, without Wikileaks being their proxy. You can’t take a video of corruption or police brutality, and post it anonymously.
Now I hear you arguing with me in your heads: Use Tor and upload it to Youtube. No, youtube will take it down. Use Tor and upload it to MEGA, or some site that will fight fradulent takedown notices. Okay, but now you’re relying on the good graces of some third party. A third party that is known to host the video, and can be sued. Wikileaks was the last organization that was willing to take on that legal fight, and now they are no longer in the business of hosting content for normal people.
And you can say Hidden Service and I’ll point to size-based traffic analysis and confirmation attacks that come with a low-latency network, never mind Ralf-Phillip Weinmen’s amazing work the other month that really killed Hidden Services. We can go on and on like this, but I hope you’ll at least concede the point that what you are coming up with are work-arounds for a problem that we lack a good solution to.
Conclusions
As we can see true anonymity online is non-existent. At the very least, third parties can collect meta-data on you and use correlation attacks, when ideally they shouldn’t even know you are communicating at all. Moreover, even strong anonymity tools like Tor have shown to have known vulnerabilities.
However, what matters is not whether something is vulnerable in theory, but rather does it keep you safe in practice? And so far, the tools we have at our disposal are pretty powerful.
As I have mentioned in my previous article, using TailsOS off a flash stick in a public wi-fi area with no cameras + VPN/Tor seems to be the best solution for now.
The testament to the power of anonymity tools is that pedophile rings and drug dealers have managed to escape persecution by multiple world governments to this day using them.
And that’s what I will talk about in my next article. We will analyze the electronic operational security of pedophile rings and how one infamous one managed to escape unscathed after years of being searched. Stay tuned.
Read More: 12 Ways To Increase Your Anonymity And Security Online
3 notes
·
View notes
Text
Ichiran@home 2021: the ultimate guide
Recently I’ve been contacted by several people who wanted to use my Japanese text segmenter Ichiran in their own projects. This is not surprising since it’s vastly superior to Mecab and similar software, and is occassionally updated with new vocabulary unlike many other segmenters. Ichiran powers ichi.moe which is a very cool webapp that helped literally dozens of people learn Japanese.
A big obstacle towards the adoption of Ichiran is the fact that it’s written in Common Lisp and people who want to use it are often unfamiliar with this language. To fix this issue, I’m now providing a way to build Ichiran as a command line utility, which could then be called as a subprocess by scripts in other languages.
This is a master post how to get Ichiran installed and how to use it for people who don’t know any Common Lisp at all. I’m providing instructions for Linux (Ubuntu) and Windows, I haven’t tested whether it works on other operating systems but it probably should.
PostgreSQL
Ichiran uses a PostgreSQL database as a source for its vocabulary and other things. On Linux install postgresql using your preferred package manager. On Windows use the official installer. You should remember the password for the postgres user, or create a new user if you know how to do it.
Download the latest release of Ichiran database. On the release page there are commands needed to restore the dump. On Windows they don't really work, instead try to create database and restore the dump using pgAdmin (which is usually installed together with Postgres). Right-click on PostgreSQL/Databases/postgres and select "Query tool...". Paste the following into Query editor and hit the Execute button.
CREATE DATABASE [database_name] WITH TEMPLATE = template0 OWNER = postgres ENCODING = 'UTF8' LC_COLLATE = 'Japanese_Japan.932' LC_CTYPE = 'Japanese_Japan.932' TABLESPACE = pg_default CONNECTION LIMIT = -1;
Then refresh the Databases folder and you should see your new database. Right-click on it then select "Restore", then choose the file that you downloaded (it wants ".backup" extension by default so choose "Format: All files" if you can't find the file).
You might get a bunch of errors when restoring the dump saying that "user ichiran doesn't exist". Just ignore them.
SBCL
Ichiran uses SBCL to run its Common Lisp code. You can download Windows binaries for SBCL 2.0.0 from the official site, and on Linux you can use the package manager, or also use binaries from the official site although they might be incompatible with your operating system.
However you really want the latest version 2.1.0, especially on Windows for uh... reasons. There's a workaround for Windows 10 though, so if you don't mind turning on that option, you can stick with SBCL 2.0.0 really.
After installing some version of SBCL (SBCL requires SBCL to compile itself), download the source code of the latest version and let's get to business.
On Linux it should be easy, just run
sh make.sh --fancy sudo sh install.sh
in the source directory.
On Windows it's somewhat harder. Install MSYS2, then run "MSYS2 MinGW 64-bit".
pacman -S mingw-w64-x86_64-toolchain make # for paths in MSYS2 replace drive prefix C:/ by /c/ and so on cd [path_to_sbcl_source] export PATH="$PATH:[directory_where_sbcl.exe_is_currently]" # check that you can run sbcl from command line now # type (sb-ext:quit) to quit sbcl sh make.sh --fancy unset SBCL_HOME INSTALL_ROOT=/c/sbcl sh install.sh
Then edit Windows environment variables so that PATH contains c:\sbcl\bin and SBCL_HOME is c:\sbcl\lib\sbcl (replace c:\sbcl here and in INSTALL_ROOT with another directory if applicable). Check that you can run a normal Windows shell (cmd) and run sbcl from it.
Quicklisp
Quicklisp is a library manager for Common Lisp. You'll need it to install the dependencies of Ichiran. Download quicklisp.lisp from the official site and run the following command:
sbcl --load /path/to/quicklisp.lisp
In SBCL shell execute the following commands:
(quicklisp-quickstart:install) (ql:add-to-init-file) (sb-ext:quit)
This will ensure quicklisp is loaded every time SBCL starts.
Ichiran
Find the directory ~/quicklisp/local-projects (%USERPROFILE%\quicklisp\local-projects on Windows) and git clone Ichiran source code into it. It is possible to place it into an arbitrary directory, but that requires configuring ASDF, while ~/quicklisp/local-projects/ should work out of the box, as should ~/common-lisp/ but I'm not sure about Windows equivalent for this one.
Ichiran wouldn't load without settings.lisp file which you might notice is absent from the repository. Instead, there's a settings.lisp.template file. Copy settings.lisp.template to settings.lisp and edit the following values in settings.lisp:
*connection* this is the main database connection. It is a list of at least 4 elements: database name, database user (usually "postgres"), database password and database host ("localhost"). It can be followed by options like :port 5434 if the database is running on a non-standard port.
*connections* is an optional parameter, if you want to switch between several databases. You can probably ignore it.
*jmdict-data* this should be a path to these files from JMdict project. They contain descriptions of parts of speech etc.
ignore all the other parameters, they're only needed for creating the database from scratch
Run sbcl. You should now be able to load Ichiran with
(ql:quickload :ichiran)
On the first run, run the following command. It should also be run after downloading a new database dump and updating Ichiran code, as it fixes various issues with the original JMdict data.
(ichiran/mnt:add-errata)
Run the test suite with
(ichiran/test:run-all-tests)
If not all tests pass, you did something wrong! If none of the tests pass, check that you configured the database connection correctly. If all tests pass, you have a working installation of Ichiran. Congratulations!
Some commands that can be used in Ichiran:
(ichiran:romanize "一覧は最高だぞ" :with-info t) this is basically a text-only equivalent of ichi.moe, everyone's favorite webapp based on Ichiran.
(ichiran/dict:simple-segment "一覧は最高だぞ") returns a list of WORD-INFO objects which contain a lot of interesting data which is available through "accessor functions". For example (mapcar 'ichiran/dict:word-info-text (ichiran/dict:simple-segment "一覧は最高だぞ") will return a list of separate words in a sentence.
(ichiran/dict:dict-segment "一覧は最高だぞ" :limit 5) like simple-segment but returns top 5 segmentations.
(ichiran/dict:word-info-from-text "一覧") gets a WORD-INFO object for a specific word.
ichiran/dict:word-info-str converts a WORD-INFO object to a human-readable string.
ichiran/dict:word-info-gloss-json converts a WORD-INFO object into a "json" "object" containing dictionary information about a word, which is not really JSON but an equivalent Lisp representation of it. But, it can be converted into a real JSON string with jsown:to-json function. Putting it all together, the following code will convert the word 一覧 into a JSON string:
(jsown:to-json (ichiran/dict:word-info-json (ichiran/dict:word-info-from-text "一覧")))
Now, if you're not familiar with Common Lisp all this stuff might seem confusing. Which is where ichiran-cli comes in, a brand new Command Line Interface to Ichiran.
ichiran-cli
ichiran-cli is just a simple command-line application that can be called by scripts just like mecab and its ilk. The main difference is that it must be built by the user, who has already did the previous steps of the Ichiran installation process. It needs to access the postgres database and the connection settings from settings.lisp are currently "baked in" during the build. It also contains a cache of some database references, so modifying the database (i.e. updating to a newer database dump) without also rebuilding ichiran-cli is highly inadvisable.
The build process is very easy. Just run sbcl and execute the following commands:
(ql:quickload :ichiran/cli) (ichiran/cli:build)
sbcl should exit at this point, and you'll have a new ichiran-cli (ichiran-cli.exe on Windows) executable in ichiran source directory. If sbcl didn't exit, try deleting the old ichiran-cli and do it again, it seems that on Linux sbcl sometimes can't overwrite this file for some reason.
Use -h option to show how to use this tool. There will be more options in the future but at the time of this post, it prints out the following:
>ichiran-cli -h Command line interface for Ichiran Usage: ichiran-cli [-h|--help] [-e|--eval] [-i|--with-info] [-f|--full] [input] Available options: -h, --help print this help text -e, --eval evaluate arbitrary expression and print the result -i, --with-info print dictionary info -f, --full full split info (as JSON) By default calls ichiran:romanize, other options change this behavior
Here's the example usage of these switches
ichiran-cli "一覧は最高だぞ" just prints out the romanization
ichiran-cli -i "一覧は最高だぞ" - equivalent of ichiran:romanize :with-info t above
ichiran-cli -f "一覧は最高だぞ" - outputs the full result of segmentation as JSON. This is the one you'll probably want to use in scripts etc.
ichiran-cli -e "(+ 1 2 3)" - execute arbitrary Common Lisp code... yup that's right. Since this is a new feature, I don't know yet which commands people really want, so this option can be used to execute any command such as those listed in the previous section.
By the way, as I mentioned before, on Windows SBCL prior to 2.1.0 doesn't parse non-ascii command line arguments correctly. Which is why I had to include a section about building a newer version of SBCL. However if you use Windows 10, there's a workaround that avoids having to build SBCL 2.1.0. Open "Language Settings", find a link to "Administrative language settings", click on "Change system locale...", and turn on "Beta: Use Unicode UTF-8 for worldwide language support". Then reboot your computer. Voila, everything will work now. At least in regards to SBCL. I can't guarantee that other command line apps which use locales will work after that.
That's it for now, hope you enjoy playing around with Ichiran in this new year. よろしくおねがいします!
6 notes
·
View notes
Text
under the rose: part 1 |th.
CATCH A GRENADE

moodboard courtesy of @mcuspidey
SUMMARY: Would you do anything for the person you love?
Would you do anything for the person you lust?
PAIRING: Agent!Tom Holland x Agent!Reader
WORD COUNT: 4k
sub rosa: adjective and adverb. formal. happening or done in secret. directly translated from latin: “under the rose.”
Part 2
Part 1: Catch a Grenade
When you signed on to become an agent for a secret sect of the government, you hadn’t realized that the job meant being in disguise almost all hours of the day.
From the moment you entered your place of work, a mask shaded your face. You went from being one person around your family to someone else entirely around your fellow field agents, but there was no one you shaded yourself more from than your partner. For him, you masked yourself completely.
Tom Holland was practically James Bond, and he knew it.
He had been assigned to you after multiple cases of “conflicts of interests” according to Human Resources. After not much digging (you were an agent after all), your suspicions were confirmed. Tom had seduced his way through the female agents of their tier to the point where he was practically impossible to work with. Even the men of their department refused to work with him. You were the last-ditch effort. Upon discovering that, you made it your own personal secret mission to make that effort a success. You wanted to become the agency’s new favorite agent. Dealing with Tom was just a step in your path to climbing the ranks.
What he was after, you weren’t sure. Your theory was that he wished to work alone, and was trying to run the higher-ups dry of possible partnership opportunities, or even force them into giving him a promotion. Unfortunately for him, you had been the longest-lasting partner, having been paired with him for 6 months. His lips hadn’t come near to any part of your skin. No matter how delicious he attempted to be.
When your partner entered the room, all eyes gravitated to the way he walked. It was confident, yet you knew from the deepness of your heart that the false confidence was manifested from a dangerous arrogance. You had been working alongside Tom long enough to know how seriously he took himself, and how much of a joke everyone else was in his mind. You were the only one who didn’t fall to your knees at the sight of him. You dismissed him as if he was any other agent on level 36.
You didn’t lift your eyes when you felt him standing next to you, knowing that he had plenty of people already giving him the attention he needed. The game you played with him rubbed him the wrong way and you knew it and loved it. There was no one more he wanted to crack than you, yet nothing seemed to phase you. His penetrating aura had nothing on you. It barely left a scratch.
Which wasn’t to say it didn’t occasionally knock.
You felt his breath on his neck as he squeezed past you, laying a hand on your shoulder to get by which you promptly rolled your shoulders away from in an attempt to send a message. You were never sure if he actually received it, but it was always worth a shot. He had to figure it out one day.
“We need to be downstairs for a debriefing in five minutes,” you spoke sternly, pursing your ruby red lips as you finished the sentence. He was typically late to debriefings, so telling him the time frame was probably not going to be much help. Picking up the two files sitting on your desk for your current case, you waited to see if he would join you in heading to the second floor, or if he was just going to be late. When it was obvious it was the latter, you rolled your eyes and proceeded to the elevator.
Yourself and Tom were assigned to one of the most secret missions currently being taken on by the agency. After what felt like endless weeks of research, today was the day one of you, Tom, would finally be venturing into the field. As much as both of you loved research and paperwork (which was close to not at all), it was the disguises and collecting evidence that really gave you the rush. To most people, the act of putting one’s life on the line sounded terrifying, but you had always been an adrenaline junkie. Going for what was dangerous was what spoke to you.
“This mission is completely sub rosa. You have signed a contract saying that discussing this mission outside of this room and with each other is strictly prohibited. No agents below level 8 are permitted to know anything on Mission 8382. Is this understood?” Chief Agent Madison had her snowy white hair tied tightly back into a bun that rested in the middle of her head, and her eyes were fixed not on you, but on Tom, who had shown up 10 minutes late with a coffee in hand.
“Yes, ma’am,” you were the only one who spoke. In your peripheral, you saw Tom roll his eyes.
Because yeah, that’s a great way to get in my pants.
“Agent Holland?”
“Yes I understand,” it was almost irritating how chocolatey his British accent stood out amongst the sea of Americans. You stifled a heavy sigh of annoyance.
You both were walked through the basic outline of the mission, which you were both familiar with. The debrief before heading into the field was more of a formality than anything.
The end goal for you and Tom was to expose a group responsible for one of the largest sex-trafficking empires in the world. It was a case that your department had been following since before you had even been hired, and keeping everything under wraps and running smoothly was of the utmost importance. There was no room for error. Luckily, Tom was good enough at his job to know that.
“Agent Holland will be heading into the facility first. His application to work for them has been processed, and he has memorized everything that we put on it to make sure that his cover is secure. After a few weeks, he will be asking if his girlfriend, Agent Y/L/N, can come along with him as long as she keeps her mouth shut,” Chief Agent Madison hit a button and another formal-looking slide took the place of the previous, “From there you two will be gathering as much intel as possible. Talk to people, gain their trust, get to know them. You will file a mission report at the end of each day, and when it seems like we have enough information, you’ll be pulled and reassigned to your next case.”
The debrief was always a formality that no agent was a major fan of. It was essential so that agents were held accountable while in the field, but after spending so long in preparation for this case, having the chief of the agency reiterate what you already knew was only making you more anxious to get into your disguise and onto the field. Of course, it was Tom Holland who got to make the initial contact, but that boiled down to the underlying sexism in the criminal world that you were all too familiar with. The men of this trafficking ring were more likely to accept a young man and his girlfriend into their group rather than vice versa.
“All right. Head to level 40 for your disguise debrief.”
The red wig was a deep crimson that, by a miracle, didn’t look tacky. The dark red locks fell in waves over your shoulders, perfectly complimenting the red lipstick you had taken to wearing on the daily, solely to get used to the way it felt on your lips. Usually, you only wore makeup for special occasions, but the character you would be embodying for an extensive amount of time was an ex-waitress from New Jersey. Wearing heavy makeup on the daily had become second nature.
To your left sat Tom, whose hair was usually styled to perfection, but now a charming pile of curls that barely didn’t cover his eyes. He looked displeased.
“Is this really neces-”
“Yes Agent Holland, it is,” the woman fixing his hair was just as British as he was, steam coming out of her ears as she spoke. She must have fallen victim to Tom’s advances by the way he smirked at her in response.
You, on the other hand, liked the way you looked. The name you had come up with to go along with your cover fit the look well. Staring at the cat-eye flicked on your eyelid and the thick lashes, both of which you had placed on yourself, you perked your lips into barely a smile. This woman’s name was definitely Rose.
You had heard the term sub rosa so many times in the past few weeks, and just in general with your career, that you couldn’t help but create a name using a play on words. Tom had offered his disapproval almost instantly, but you weren’t really a fan of his name either.
“Ay,” he said in a well-developed New York American accent, “‘Name’s Johnny.”
It could not be more of a cliche.
The weeks that you were waiting to be thrown into the field were slow. You hated that Tom was the one to go first, no matter how many times you had reminded yourself that it was essential to the mission for Tom to make the introductions. It was not the agency’s fault that men, especially criminals, saw women as accessories rather than assets. If anything, you were a slightly better and definitely more professional agent than your partner.
You kept a careful eye on him while he worked, whispering suggestions into his earpieces, which he took about half the time. It was better than what you expected, which was he wouldn’t take any feedback at all. Typically he didn’t leave their main meeting base until about midnight or sometimes later. The day-to-day activities of the world’s most wanted criminals were more mundane than you had anticipated, limited to playing cards, watching sports, and lots of drinking and drugs. Tom only took part in minimal drinking, usually escaping to the bathroom to dump them out. He only wanted to give off the appearance that he was drunk.
By week four, it was hard not to get exasperated. You were starting to wonder if he was dragging the process out on purpose to keep you excluded from the case. He easily could have brought you into the picture during week three. Chewing on your lip, you listened to the menial conversation that that day’s group made while smoking blunts. Tom cleared his voice and started to speak.
“Hey boys, I was wonderin’ if my girl could start coming by,” on the small screen with the low-quality camera, you could see his pixelated body lean back into the chair, his arm swinging across the back.
A man that was usually referred to by the name of Hardy perked up, taking a hit and leaning on his knees, “Your girl….”
A different man, nicknamed “Candy” (you didn’t care to find out why) spoke next, “Will she keep her mouth shut?”
Tom this time, “Of course. She’s dumber than a doornail, she has no idea, what happens here.”
You held back rolling your eyes. It was all a part of the backstory, your alias had purposefully been written as not the smartest, but hearing it from Tom’s mouth had a different sort of way about it.
“Why does she want to tag along then?” it was Smithy that asked the next question.
“Just lost her job at Hooter’s,” the entire male group’s ears perked at the sound of that, “And she isn’t particularly the stay-at-home type.”
A dark brooding figure appeared amongst them in the outskirts of where the camera lens stopped, just at his presence, the entire dynamic of the room change, the attention going immediately to him as if waiting for something absolutely profound to be said. After a pungent pause, his profound words turned out to be, “We could use a little bit of ass around here.”
It was followed by chuckles and a few playful punches to Tom’s shoulders.
“Perfect,” by the way Tom was speaking, you could tell he was smiling, “I’ll bring her with me tomorrow.”
…
The drive to the evil lair was silent. If it had been any quieter, Tom probably would have been able to hear how your heart was pounding in your chest. Since he had already been doing this for a month, this was just another day of work for him, as much as this degree of “work” could be. There had been barely any intel in the month he had been working the case, only drinking and smoking. It was almost as if Tom, and now you, were getting a very tense vacation.
“Nervous?” you could see the warehouse by the time the first word was said.
“Me? Johnny, please,” you said it in the thick, well-practiced New Jersey accent that had been a part of studying this woman you were becoming.
Out of the corner of your eye, a hint of a smile twitched on his mouth.
You placed a pair of sunglasses over your eyes, a tacky pair that were so huge they shaded your eyebrows, not because it was bright outside but because the truth was you were slightly nervous. It wasn’t like shading your eyes from the criminals would protect you in any way,
The room that they spent most of their time in smelled of booze and weed (not much of a shock), with a hint of metal that probably came from the tall pillars and an entire wall that was elaborately decorated in graffiti, which were unintelligible through the crappy observation cameras that you were so used to looking at. With a deep inhale, you took in the scene, trying to memorize every detail.
The large man, the one that had given his seal of approval on Tom’s “girl” being allowed to come around, was the first to greet you. After the months of surveillance, you still had never caught his actual name. He was strictly referred to as “boss.” If you could weasel your way into figuring out what his name actually was, it would be a major lead in your case. In the moments that you had spoken with Tom about it, he had mentioned that his efforts to crack the alias hadn’t come to anything. As much as you hated it, maybe the boss needed a little more than what Tom was able to give him.
The man was tall, broad, and a lot more handsome than you had expected. He was tough in a sexy way, with the hint of stubble speckling his jawline, and veins popping out of the muscles that extended out of the white tank that tightly hugged his toned body. He approached you, slowly, sizing you up as if you weren’t the meek girl that you were pretending to be. Little did know, he was dealing with one of the most highly trained agents in the United States.
His fingers brushed a strand of your fake, red hair over your shoulder, and he took off your sunglasses for you, closing them with his mouth and placing them in the front pocket of your jeans, moving as if someone had pressed the “slo-mo” button.
“Hey, gorgeous,” his accent was Australian, “I’m glad you’re able to start joining us.”
You snapped your gum, ignoring the drumbeat of your heart, and spoke with your Jersey accent, “Pleasure’s all mine, mister.”
Tom’s hand snaked around your waist, and you ignored the butterfly feeling that accompanied it. No one had touched you like that for as long as you could remember. The way that he pulled you close following the subtle touch, you felt as if he was being protective. You turned your head so that you were facing him, each of your faces temptingly inches away from each other.
“Now, boss, let’s not get too handsy, eh?” Tom accompanied his teasing tone by placing a toothpick in between his teeth. He kissed the side of your head, which was rough but sort of endearing at the same time.
You soon discovered that your perception of what the men spent their time doing was exactly correct. Chairs in a circle accompanied by an endless supply of beers and straight whiskey. You kept to the beers, and when a blunt was passed around, you politely declined.
“History of lung cancer,” you winked at one of the guys across from you. You were pretty sure it was Hardy. His jet black hair was slicked back to a point where you were sure that wringing it out would follow with an ugly amount of hair product dripping out. He looked as if he belonged in Grease.
You had gotten what you wanted, though. Hardy responded with a slight bite to his lip and a subtle hiding of his eye contact upon noticing that Tom was glaring at him.
He was certainly good at playing his role. This was the most emotion you had gotten from Tom in all the months you had been working with him.
“Boys,” Boss clapped, his voice immediately altering the energy in the room, “I have news from our men on the outside that our rival might be in the area looking to...give us a frighten. Let’s take a walk outside, huh? Grab your toys.”
Of course, the day that you decided to make an appearance, there was something other than lounging around Home Base. You met eyes with Tom, who responded with a smirk, throwing his shades over his eyes.
You had heard of the rival group with a few mentions, and you were sure that the agency was on it, possibly assigning other agents to potentially take them down. Being in this line of work had given you a heavy realization that the world was a fucked-up place.
That’s why you did this. You had always aspired to make the world a better place, and now you had no choice.
“Of course,” the boss’s attention fixated on you as all the men shuffled to get what you assumed was weapons, “you are more than welcome to come, my dear, but I wouldn’t want you to find yourself getting hurt.”
You circled your finger around the rim of your beer bottle and sucked the liquid off your manicured finger with a cheeky POP, “I think I’ll be okay, mister.”
Each of the men filed back in, Tom quick to make his way to you and place a hand on the small of your back. If you hadn’t been wearing your chic denim jacket, his hand would have met bare skin thanks to the leopard print crop top you had picked for that day. A shiver tempted to shake your shoulders.
It was a hot, muggy summer afternoon in New York. Looking around, you saw that each of the guys you had been with had taken to their own set of shades, trudging through the high grass like they were hunting an animal rather than another group of people.
One of Tom’s arms held the automatic weapon, and the other hung over your now bare shoulders, the red curls brushing against it. You popped your gum with every step, keeping a keen eye on the situation around you, knowing that the newest people to this gang had the most experience.
The Jeep came out of nowhere, driving roughly across the field without any question of anyone’s safety. It was who they were looking for.
What you hadn’t expected was the projectile that flew from the front window, thrown by a man in sunglasses, mouth guarded with a black bandana. It was headed straight for Tom, but before you thought twice, you unraveled yourself from him and caught it, only taking a moment to realize exactly what they had thrown at you.
“Don’t worry, beautiful,” Candy spoke up. “It’s probably a fake-”
You were definitely not going to risk it. It was your first day on the job, and neither you nor Tom was getting killed. Throwing it, you used every muscle in your arm, almost popping it out of its socket. It did the trick, flying across the field far and high, where it exploded.
“Damn,” Candy adjusted his attitude.
The boss was now eying you, his arms crossed and a finger lingering on the corner of his mouth, “You got quite an arm, Rose.”
It was the first time you had been called by your fake name.
You laughed, forcing it to sound as natural as possible. Rose was an airhead after all.
“I was softball captain my senior year of high school. Guess your throwin’ arm never truly goes away, huh?” with another laugh, you wrapped your arms around Tom’s waist, the feeling of his abs pressing into your chest, “I saved your life, huh baby?”
On his lips were a smile, but his brown eyes were filled with some concern that was unfamiliar to you. Tom never worried about any one of his partners, “You sure did.”
The kiss was short and soft, and while you wished you could have said it was detached, all a part of the facade, there was something sugary about the way he interlocked your lips.
“Careful,” you said, brushing his lips with your finger. “I’m wearing my good lipstick.”
When you had returned to home base, you needed to take a minute to yourself. Asking for the restroom, you escaped to the grungy, foul-smelling bathroom that was littered with more graffiti.
The mirror was scratched and etched with names and quotes and years that were remnants of the past. With a deep inhale you took a square of toilet paper and dabbed at the sweat that was shining on your forehead and chin, mixed with the natural oil of your thick, full coverage foundation.
You were startled by the sound of someone bursting through the door, and you were about to stay in character and shriek before you noticed it was Tom, who was filling the little space that you already had in the grimey bathroom. You hardly got a word in before Tom wrapped you in his arms, gently.
“Johnny what-”
“No, this is Tom giving you a hug. Not Johnny,” he was speaking in his native, British accent.
You weren’t sure if this was authentic, so after standing stone-cold still, you returned the hug unenthusiastically. Was this his attempt to woo you?
“I just wanted to make sure you were okay,” he continued, parting from the hug. Your faces were barely inches apart, and you could feel his breath grazing your skin as he looked down at your feet.
“Well,” you swallowed the small amount of saliva remaining in your dry mouth, “I’m okay. I’m Agent Y/L/N, remember?”
“Catching a grenade is more intense than one would think,” he rubbed one of his eyes, “If you need anything let me know.”
You watched as he exited, unsure of how to feel. Tom had never seemed like a compassionate person to you, yet here he was making sure you were okay. It was so out of character.
It had to be him trying to get to you.
Clenching your teeth, you huffed out a sigh and returned to the group, greeted by the familiar smell of marijuana. With a simple smile, you sat back down in your spot next to Tom. You slid a lock of hair back behind your ear, and made eye contact with each of the different men, unapologetically gawking at you.
“You all are making me wish I’d kept the grenade in my hand. Eyes on your cards, gentlemen!” you flashed Tom a wink and watched as his ears turned pink.
Two could play at his game.
Part 2
M A S T E R L I S T
click HERE to be added to the taglist
T A G L I S T
@starksparker @astrospideys @naturallytom @natalia-rushman @hollandroos @sunshinehollandd @sunshineandparker @lovelyh0lland @jupiterparker @afterglowparker @keepingupwiththeparkers @nnatasha @plushparker @spideyboipete @tonyintexas @darlintom @bilkyrie @vinndetta @spideymood @saturn-aka-six @starlightfound @pvnk-bivch @gamoraisbi @xxtomxo @ophcelia @spiderkat1248 @galacticalstarcat @fame-works-quicker @honeymoonparker @spidermansmj14 @loserhollandask @quillaluna @cheesecakebagels @ceciliaromeroo @misspepper07 @thelostverse @legendsofwholock @trustfundparker @miraclesoflove @the-queen-procrastinator @fangirl-trash-things @particularspider @applenter @the-lost-fairy-tale @mrskitchenboy @mintyoohoochapstick @newtimewriter @ohheyitsem @nixophomaniac @juuuless @emilymarie0422 @dreamyyholland @gioandreolli @stuckonspidey @grandmascottlang
#allie writes under the rose#UTR#tom holland#tom holland fanfic#tom holland x reader#tom holland x you#tom holland x y/n#tom holland reader insert#tom holland fanfiction#tom holland series#agent!tom holland#agent!reader#fanfic
295 notes
·
View notes
Text
Sqlite For Mac Os X

Sqlite For Mac Os X El Capitan
Sqlite Viewer Mac
Sqlite Mac Os X Install
If you are looking for an SQLite Editor in the public domain under Creative Commons license or GPL (General Public License) i.e. for free commercial or non-commercial use. Then here is a shortlist of the SQLite Editor that is available on the web for free download.
SQLite is famous for its great feature zero-configuration, which means no complex setup or administration is needed. This chapter will take you through the process of setting up SQLite on Windows, Linux and Mac OS X. Install SQLite on Windows. Step 1 − Go to SQLite download page, and download precompiled binaries from Windows section. Core Data is an object graph and persistence framework provided by Apple in the macOS and iOS operating systems.It was introduced in Mac OS X 10.4 Tiger and iOS with iPhone SDK 3.0. It allows data organized by the relational entity–attribute model to be serialized into XML, binary, or SQLite stores. The data can be manipulated using higher level objects representing entities. Requirements: Free, ideally open source Browse schema, data. Run queries Bonus if updated in near real time when the file is. SQLite viewer for Mac OS X. Ask Question Asked 5 years, 10 months ago. Active 4 years, 3 months ago. Viewed 504 times 3. I need to inspect an SQLite file on Mac. Since I develop on Windows, Linux and OS X, it helps to have the same tools available on each. I also tried SQLite Admin (Windows, so irrelevant to the question anyway) for a while, but it seems unmaintained these days, and has the most annoying hotkeys of any application I've ever used - Ctrl-S clears the current query, with no hope of undo.
These software work on macOS, Windows, Linux and most of the Unix Operating systems.
SQLite is the server. The SQLite library reads and writes directly to and from the database files on disk. SQLite is used by Mac OS X software such as NetNewsWire and SpamSieve. When you download SQLite and build it on a stock Mac OS X system, the sqlite tool has a.
1. SQLiteStudio
Link : http://sqlitestudio.pl/
SQLiteStudio Database manager has the following features :
A small single executable Binary file, so there is need to install or uninstall.
Open source and free - Released under GPLv2 licence.
Good UI with SQLite3 and SQLite2 features.
Supports Windows 9x/2k/XP/2003/Vista/7, Linux, MacOS X, Solaris, FreeBSD and other Unix Systems.
Language support : English, Polish, Spanish, German, Russian, Japanese, Italian, Dutch, Chinese,
Exporting Options : SQL statements, CSV, HTML, XML, PDF, JSON, dBase
Importing Options : CSV, dBase, custom text files, regular expressions
UTF-8 support

2. Sqlite Expert
Link : http://www.sqliteexpert.com/download.html


SQLite Expert though not under public domain, but its free for commercial use and is available in two flavours.
a. Personal Edition
Sqlite For Mac Os X El Capitan
It is free for personal and commercial use but, covers only basic SQLite features.
But its a freeware and does not have an expiration date.

b. Professional Edition
It is for $59 (onetime fee, with free lifetime updates )
It covers In-depth SQLite features.
But its a freeware and does not have an expiration date.
Features :
Visual SQL Query Builder : with auto formatting, sql parsing, analysis and syntax highlighting features.
Powerful restructure capabilities : Restructure any complex table without losing data.
Import and Export data : CSV files, SQL script or SQLite. Export data to Excel via clipboard.
Data editing : using powerful in-place editors
Image editor : JPEG, PNG, BMP, GIF and ICO image formats.
Full Unicode Support.
Support for encrypted databases.
Lua and Pascal scripting support.
3. Database Browser for SQLite
Link : http://sqlitebrowser.org/
Database Browser for SQLite is a high quality, visual, open source tool to create, design, and edit database files compatible with SQLite.
Database Browser for SQLite is bi-licensed under the Mozilla Public License Version 2, as well as the GNU General Public License Version 3 or later.
You can modify or redistribute it under the conditions of these licenses.
Features :
You can Create, define, modify and delete tables
You can Create, define and delete indexes
You can Browse, edit, add and delete records
You can Search records
You can Import and export records as
You can Import and export tables from/to text, CSV, SQL dump files
You can Issue SQL queries and inspect the results
You can See Log of all SQL commands issued by the application
4. SQLite Manager for Firefox Browser
Link : https://addons.mozilla.org/en-US/firefox/addon/sqlite-manager/
This is an addon plugin for Firefox Browser,
Features :
Manage any SQLite database on your computer.
An intuitive hierarchical tree showing database objects.
Helpful dialogs to manage tables, indexes, views and triggers.
You can browse and search the tables, as well as add, edit, delete and duplicate the records.
Facility to execute any sql query.
The views can be searched too.
A dropdown menu helps with the SQL syntax thus making writing SQL easier.
Easy access to common operations through menu, toolbars, buttons and context-menu.
Export tables/views/database in csv/xml/sql format. Import from csv/xml/sql (both UTF-8 and UTF-16).
Possible to execute multiple sql statements in Execute tab.
You can save the queries.
Support for ADS on Windows
Sqlite Viewer Mac
More Posts related to Mac-OS-X,
More Posts:
Sqlite Mac Os X Install
Facebook Thanks for stopping by! We hope to see you again soon. - Facebook
Android EditText Cursor Colour appears to be white - Android
Disable EditText Cursor Android - Android
Connection Failed: 1130 PHP MySQL Error - MySQL
SharePoint Managed Metadata Hidden Taxonomy List - TaxonomyHiddenList - SharePoint
Execute .bin and .run file Ubuntu Linux - Linux
Possible outages message Google Webmaster tool - Google
Android : Remove ListView Separator/divider programmatically or using xml property - Android
Unable to edit file in Notepad++ - NotepadPlusPlus
SharePoint PowerShell Merge-SPLogFile filter by time using StartTime EndTime - SharePoint
SQLite Error: unknown command or invalid arguments: open. Enter .help for help - Android
JBoss stuck loading JBAS015899: AS 7.1.1.Final Brontes starting - Java
Android Wifi WPA2/WPA Connects and Disconnects issue - Android
Android Toolbar example with appcompat_v7 21 - Android
ERROR x86 emulation currently requires hardware acceleration. Intel HAXM is not installed on this machine - Android

1 note
·
View note
Text
Profile: Callahan, Alexa D.
Description: Brown hair, Brown eyes, 5 feet 7 inches
Birthdate: September 18
Age at conviction: 16
Current age: 19
Birthplace: Rochester, New York, United States
Current Location: UNKNOWN
Family:
Mother: Alisa Callahan age 47 - deceased
Father: Geoffrey Callahan age 52 - deceased
Siblings:
Jennifer Callahan age 12 - deceased
Benjamin Callahan age 19 - deceased
This file contains eye witness accounts of events related to and/or allegedly caused by Alexa Callahan.
Eye witness account by Victor Drell
Age: 37
Occupation: High School Teacher
September 18,
I never saw the explosions, but I heard them. My wife Mary called the police as I went to go investigate. We live two houses down from the corner, I could see the apartment building on the opposite side - or where the building used to be – in a smoking heap. A couple of houses around it were knocked around too, but the residents there seemed to be fine.
When I got closer, I noticed the other neighbors start to come out as well. I climbed into the rubble hoping that someone was still alive. I noticed crushed remains of corpses lying everywhere; I wanted to vomit. One man was missing an arm and groaning loudly, so I called to the others to help move him to a place where rubble wouldn’t fall on him.
One of the neighbor kids called out from behind me that there was a girl who was still breathing. I told someone to take my place with the man, and rushed over to the girl. She was still breathing. She looked to be about fifteen and was wearing a white dress that was all tattered around the edges, her hair was a little singed, and I thought she probably suffered some trauma from what seemed like a fall from the second floor. But she looked mostly fine otherwise, which in hindsight was a little odd. Seemed like a miracle at the time. That’s when the police and paramedics arrived and took all the living away.
I learned later that the man’s name was Carl Stephenson, and the girl was Alexa Callahan, who was turning sixteen that day. I heard on the news that Carl Stephenson had died in the hospital and was taken by family for burial. But not that Alexa girl, she had no family left, and she was alive. A real shame, to have a bomb like that go off on your sixteenth birthday.
Report by Vanessa Bradford
Age: 42
Occupation: Nurse
I was assigned to a girl by the name of Alexa Callahan. She had suffered from several injuries caused by the explosion of her building. The full extent of the damage done to her was: A few broken ribs, a hairline fracture in her arm, a mutilated ankle, and trauma to the head. She seemed to have landed on her left side, and somehow managed to save her spine and vital organs. She was unconscious for 72 hours after the operations were finished. When she finally awoke, she was mostly unresponsive. She played with the recliner on the bed for a while and just stared at faces for a long time. She didn’t speak to anyone; not to doctors or nurses, not to the other patients. She didn’t respond to food or water, and didn’t even react whenever we adjusted the needles in her arm.
Many of us tried to coax her to eat or speak and she did neither for almost two weeks. Her doctor was beginning to wonder if we should be running tests on the speech part of her brain when she finally spoke.
She asked me when she could go home.
I told her that we had to make sure we had treated all her injuries first. Then she asked me what happened. I told her that authorities were still figuring it out, but it seemed as if someone planted a bomb in the building, possibly a terrorist attack.
This made her jump up in a panic, she just shouted “It wasn’t!” Her heart rate spiked, and she almost tried to get out of bed. I calmed her down a little and asked her what she remembered.
What she said didn’t make any sense. “People, people talking happily; singing, my singing, singing for me; color, lots of color, piled on the walls and the room; fire, there was fire and ticking. Tick tick tick. Incessant humming, thousands of bees humming in the walls. You can‘t hear it? Tick tick tick. I made a wish, then BOOM. Fire, fire! A little boy calls for help. Help her, help her, is she okay?”
I cut her off because she was flailing about and going on about nothing. She kept talking. Nonsense, more about the ticking and the humming. I tried to get her to sit back and relax, not to strain herself with the memory, and I eventually managed to get her to sleep. I remember she whispered “not terrorist, no terror. Make a wish” as she drifted off to sleep.
I only witnessed one other event that was significant.
A couple weeks later when she was being encouraged to walk around, we found that she would disappear for hours on end. We were deciding what to do with her, the ramblings hadn’t stopped and we were getting worried. Furthermore, she had no living blood relative that anyone could find. Meetings were being held to come to a decision. I was lucky enough to be personally involved in the discussions.
She burst in to one of the meetings. I don’t know how, we thought the doors were locked. Her hands were bloodied as if she had cut them on sharp glass or metal or something. She took a seat at the table with us and said something odd.
“I realize that I am the main subject of these meetings. And I feel obligated to put my two cents in.” Then she dropped two gears on the table, like they were the two cents she was putting in. I don’t know where they came from, but they were covered in the blood from her hands. A couple of us stood to try to help her back to bed. But she waved us off and insisted that she needed to continue speaking. She said “I’m not yet so far gone that I don’t know what is happening.” And then something like “I have completely lost all relatives, I am underage, and I’m raving mad.” And she dropped another gear on the table for each thing she listed. Her grammar would get all jumbled up, because I remember she said “I would think it advisable that under any circumstances you do NOT create me another family. I could not handle an artificial mother.” Which was worth four gears for some reason. At this point, we were starting to realize that these were clock parts. And then she told us that she didn’t want to be sent back into society, that she was too crazy and too dangerous before dumping the rest of her bloodied clock parts onto the table. We wanted to stop her, but I think we were all too shocked.
She started to rearrange them in some order and I remember she said “But time is running out, and you really need to come to a decision” Then she pulled out two clock hands and placed them in the center of her bizarre pile. Then she wrote “tick, tick, tick,” on the table in her own blood, stood up and said “Thank you for your time” like she had just asked for a little favor, not made a mess of the table.
I have never seen a transfer report go through more quickly.
On October 23 Alexa was transferred to The New York Psychiatric Institute, and then by an anonymous request, to Castle Facilities in Virginia. The transaction of this was only documented once. The only legitimate information recovered from this document was the location and the date she was moved (February 15).
She remained at Castle facilities for about two years, until authorities started to take an interest in her case and launched an investigation. However by the time they arrived at Castle facilities, Miss Callahan was unable to be found.
At the alleged location of Castle facilities only ruins were found. It was apparent that the site had not been visited for many months. The building was demolished in a way that was similar to the explosion at the Callahan residence.
This leads authorities to believe that the explosions were caused by the same person. Suspects include: Alexa Callahan (missing), Justin Carter (missing), or Jamie Lucas (deceased).
At the site of the wreckage, few pieces of information were recovered. However, there was one piece pertaining to this case that proved to be interesting. A badly documented journal by Dr. Harvey Lancaster (deceased) containing vital information about the Callahan case.
Much of this journal is either missing or illegible. Therefore, the following information contains errors and assumed information. The following information is paraphrased, not quoted, and only vital information was inputted. The full copy of Dr. Harvey Lancaster is not available for viewing.
Information is as follows:
1. Alexa Callahan has a strange fascination with clocks. She is known to either disassemble the clocks, or to change the time inaccurately. The number that she chooses seems well thought out and precise and she changes every clock to the same time, though it is inaccurate. She attempts to change all clocks at once. Every attempt at this results in a different time. The purpose of this behavior is unknown.
2. Alexa Callahan had no apparent intentions of harming the other patients or facility employees.
3. Alexa Callahan has moments of near sanity where she would stop her mumblings of clocks and ticking and the end of the world where she will occasionally ask about her family or the facility. During these states of mind she would frequently ask about her friends Jamie Lucas and Justin Carter. Both Carter and Lucas came to visit Alexa in the Castle exactly twice, but not at the same time.
4. Alexa refuses, under any circumstances to believe that she is wrong in her ramblings, though she will admit to the doctors that she is insane.
5. Intense flashes of light, fire, loud noises, and shaking or sliding scare Alexa. She afterwards falls into a bout of crazed, relieved laughter, and more rambling about ticking.
6. Alexa can accurately tell the time without consulting a time piece. It is unknown how she is able to do this, but it is not any of the conventional methods.
7. Alexa made many references to the fall of the kingdom and gave an exact time, down to seconds, of the alleged time. - As a discovery not recorded in the journal of Dr. Harvey, it seems that this number led to the explosion of the mental ward.
8. All ramblings about the past from before the explosion are real memories, not stories of her own invention.
9. She is unable to walk in a straight line; her movement pattern sways back and forth.
10. She is able to recognize people and speak clearly with them. She seldom mistakes the identities of people around her.
11. She avoids all effort to make social interactions, however is not fearful when approached.
12. She enjoys acronyms, puzzles, word games, and brain teasers.
13. She fights most attempts at physical and eye contact.
An investigation was launched to find any survivors of the explosion. 15 recorded patients were reported alive. Eight patients were discovered in a nearby town (about 13 miles away). Local authorities had discovered the patients and were housing them while awaiting orders of what to do. Six of the seven remaining patients were recovered in the woods surrounding Castle facilities.
Alexa Callahan, the only unrecovered patient, is theorized to have fled to the woods surrounding Castle facilities. No bodies or sightings that match her description have been reported, leading authorities to believe she is still at large.
Authorities have lost all trails but refuse to give up the search.
Alexa Callahan is suspected for murder and terrorism. If identified, it is recommended that authorities are alerted immediately so that she may be taken into custody.
Do not try to approach, converse with, or make eye contact with Alexa Callahan. It is uncertain how she will react.
Do not flash lights or light fires in her presence; she is known to react violently.
Do not try to detain Alexa Callahan alone, she is known to be violent when angered.
TAKE CAUTION.
If Interaction is unavoidable, refrain from sudden movements, physical contact, and eye contact.
If conversation is unavoidable, keep voice at a low register and avoid any loud noises.
If she begins to make a countdown, inform authorities immediately. If this action is not an option, remove yourself from the vicinity. Countdowns from Alexa Callahan seldom lead to anything less than disaster.
If these guidelines are not heeded . . . god save you.
2 notes
·
View notes
Text
Download Themida crack (license key) latest version XUG!

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 It should unpack any themida packed file version 1. This post is only for educational purposes. The exe i'm looking to unpack is the one in bin folder, PT2. Try this tutotial: How Unpack Themida 2. In a Themida binary, different parts of the code are run in virtual machines and it obscures the behavior of the target program. Backtracing from the crashsite is probably hard because you dont know what the addresses pointed to back when you first unpacked it. The Code for the Anti-Debugger sequence, unpacks its self, and the. Functions: Unpack: Unpacks the binary you select. File list Click to check if it's the file you need, and recomment it at the bottom : Filename. We need blackhat with experience in themida packer unpacking for a long termework. NET is a tool developed to quickly and easily unpack packed. Note: You need to use a bit Python interpreter to dump bit executables. As you can see, it relies heavily on the JNI. If the version is new and there is no script, given your level of expertise right now, this will be a very, very long and arduous task. I hope people will be more interested in the subject, as it is incredible the world of reverse engineering. Warning: This tool will execute the …. So I see there seems to be still some open questions mostly if my older unpack script does not work anymore and the unpacked files to, etc. Dump the executable with extreme dumper or dnspy. To verify if this is your problem you can turn off ASLR, unpack your file again, and see …. Advanced warfare zombies trainer. Themida Unpack and Remove Ip check. Tags themida unpacker RickyWindCr4ck. It is something against Heap flag artifacts. This is most important script to unpack an Themida or Win License. However, as I expected, the Linux version was simply packed not protected and with something easy to unpack. You can try, currently there are no known unpacking scripts for PELock v2, unpackers, but I can show you plenty. Presented as part of the HCSS conference. Themida error: a debugger has been found running in your system. That specific dll isn't your target, maybe you should do more …. This has already been released 3 times today. Fix inability to read remote chunks of memory bigger than MiB. This version brings many exciting improvements, but also removes deprecated features and introduces breaking changes that may impact your workflow. Skills: Software Architecture See more: copywriting health beauty articles need similar experience repost, themida unpacking net, graphic design need web experience, need recruiting experience, themida …. Anti-API scanners techniques that avoids reconstruction of original import table. I was inspired by OALabs's video who made an unpacking of Themida, you can check his video to get a different explanation about the process to unpack a malwa. Jul 5, ; Thread starter 1 I tried all. I want to learn how to unpack Themida v2. Dump the bunded dll with MegaDumper, the vdump one should be test. To verify if this is your problem you can turn off ASLR, unpack your file again, and see if it works after a reboot then. So this time I decided to create a little video series on how to unpack and deal with a newer protected Themida target manually where my …. Guide] How Unpack Themida 2. When you execute the packed sample, it will unpack the executable in memory and use that to continue executing to perform and do what it's meant to do. PT2Start is just the launcher, it calls PT2. Heres what I've gotten so far: Code: package unpack; import java. BoxedAppPacker detected! Now with support for virtualized entry points and Delphi executables!. Unpacking a Themida packed x64 executable?. Once completed detail the methods used and how you fixed the DLL. This address changes with each reboot thanks to ASLR. HyperHide - Hypervisor based anti anti debug plugin for x64dbg. I spent 4 months testing a lot of methods from runpe dump to writing own hypervisor for full os hardware emulation but still not defeat this protector - winlicense 2. Unpacker properly handles invalid input filename. This is the unpack script we will use in this tutorial. I need an exe packed with the latest Themida unpacked, then the ip check inside said exe needs to be removed …. Status Offline Messages 45 Solutions 4 Reaction score Themida - Winlicense Ultra Unpacker 1. We have 2 files which are packed with PE protector. Packado y desempacado del packer Themida. It is a very common and well known packer, which is also considered to be an easy one to unpack. Discover HPCC Systems - the truly open source big data solution that allows you to quickly process, analyze and understand large …. If the issue persists, it can be related to your antivirus protection. Unpacking a Themida packed x64 executabl…. Now, my Problem is, all OllyDbg unpacking scripts for Themida are out, while the application is 64bit. Anti-memory dumpers techniques for …. Ok now we go open the target to unpack or just press F3, after opened we got a pop up, just press Yes and the file continue Analysing, just wait to finish. This file can not run, Try harder, Themida! Edited September 6, by Ufo-Pu55y. Themidie - x64dbg plugin to bypass Themida …. Nowadays malwares use the protector to conceal the malicious code from the analysis. Open Analysis Live! In this tutorial we show how to unpack a Themida 2. Channels , inputs locally from the X32 , are recorded as noise, very loud noise. Launcher again, Themida message x4 9 game launches perfectly 10 tried launching server, Themida message x32 11 server launches flawlessly and able to join 12 lauched server again, themida message x13 13 Server launches perfectly. But i found this foro with your instructions to unpack themida. It works on all versions of Windows XP and later. One of the mods is deleting it. The unpacked dll needs to run, to debug it. Especially, VMProtect and Themida are considered as some of the most complex commercial packers in bit Windows environments. Restart your computer twice and see if the problem is fixed. Looking for a PE Unpacker. FileNotFoundException; import java. So this time I decided to create a little video series on how to unpack and deal with a newer protected. NET, Themida doesn't really protect it except for in its non-running state. You can use a tool like MegaDumper to dump. Is it possible to unpack themida?. I represent the people of tRO came to help unpack Regexe. I have the dump for the exe, and I can see the code in reflector but PE tables and other part. It is plugin based making easier to add new archive file formats. Implement Themida-Unpacker-for-. Themida is a powerful software protection system designed for software developers who wish to protect their applications against advanced reverse engineering and software cracking. Is there a native exe unpacker for Themida? Themida is very hard to unpack even the new driverless versions , there is a ton of protections options that can be enabled see manual , so I doubt that there is a generic unpacker in the wild. I've tried the themida unpacker 1. The most common method of unpacking that I'm aware of is probably already streamlined and implemented into those tools, the run and dump method. Magicmida is a Themida auto-unpacker that works on some bit applications. How to unpack Themida - Winlicense so i could make my own unpacked client from latest ragnarok client. Warning: This tool will execute the target executable. NET programs running on the system to get the unprotected file in the case of Themida…. But a group of guys I have tried to study. Posted by pyschogsmdestroyer in: Scripts. Unpacking Tutorials Either way, best of luck to ya! View full post. PEiD detects most common packers, cryptors and compilers for PE files. Improve version detection to handle packed Delphi executables. Different encryption algorithms and keys in each protected application. Most likely its Themida or VMProtect. Compared to Themida v2, the themida v3 does not have a great improvement over the VMs. I think other hide plugin use the same trick. Even if you had videos you still have to do experimenting in order to unpack what ever you're doing. The best method to unpack a VM-protected packer like Themida is to devirtualize it, which involves figuring out the entire instruction set that the packer uses and writing a script to interpret that language. The program is using a checksum algorithm to detect if the dll is tampered. Currently, we are experiencing in the tRO people finding their Recvpacket. For major changes, please open an issue first to discuss what you. This tutorial shows you how to get original codes from a compressed program example 1. We need blackhat with experience in themida …. So temporarily disable your antivirus and update CopyTrans apps. I get debug the executable with ollydbg, but i can't find it's hard the exactly jump to bypass the verification dongle key HARDKey , because themida encript. I want to release a new tutorial about the popular theme Themida - WinLicense. Start CopyTrans Control Center. Hello, I'm a developer in Oreans Technologies and we have developed Themida to protect applications against cracking. There's a newer version: HERE. I'm looking for a person who can unpack and rebuild. So when I found this community, decide. However, I have never attempted to unpack Themida. Themida will pack the executable. Right-click on the antivirus icon and temporarily disable protection for 10 mins. Free iso unpacker Download UnPacker makes a queue of every rar added to the exe unpacker, unpacker exe, upx unpacker, unpack javascript, unpacker [email protected] Identify that your sample is packed A bunch of clues High section entropy Unusual small code segments Unusual segment names Home made scripts. I dug around the forums and someone mentioned that newer pangya revisions use a newer themida version, i downloaded exeinfo pe and indeed it points that it is packed with themida …. How you can unpack samples packed by Themida without requring knowledge of how to use a Debugger yourself manually 1. Functions: Unpack: Unpacks the …. Themida Now Days have Taggant Features. So, here's a long-promised update to Molebox unpacker. NET programs running on the system to get the unprotected file in the case of Themida. If it crashes during unpacking because it ran out of disk space, it's your problem. Now press F9 to run it and as you can see, we got a pop up, don't worry just press ok and the debug is terminated. I have a 32bit version from this, but, there is the same, all unpackers are stuck in procedure or hangs up. Net executables 32 and bit. Make sure to use this tool in a VM if you're unsure about what the target executable does. Malware analysis is one of the key problems. NET is a tool developed to quickly and easily unpack …. Successful malware distributors are not using public crypters as often, heuristics for detecting public packers is too easy, which is why we have seen a reduction in AIO unpacker tools. Anti-memory dumpers techniques for any Ring3 and Ring0 dumpers. Themida is so complicated to unpack that most people write scripts and so you can search for a script for the given version you are trying to unpack and attempt to use that. Gracefully handle bitness mismatch between interpreter and target PEs. How to Unpacking Themida? I'm trying to get back into reversing. To verify the effectiveness of x64Unpack, experiments were conducted on the obfuscation tools: UPX 3. I've been trying to hook nt apis and try debugging it. Support all version! Tested in 1. Unpacking themida and other protections. A protector is a software for protecting core technologies by using compression and encryption. It's free to sign up and bid on jobs. Jan 28, — Category Archives: Ioncube v10 decoder JavaScript Obfuscator is a free online tool that obfuscates your source code, …. I've made some changes to my game. The unpacked binary will be saved with an U suffix. My question is, how can I get better so that I can unpack Themida? I want to unpack Themida for the following reason: While reverse engineering GameLauncher. It was Spotify the application protected with Themida.
1 note
·
View note
Text
Download Themida crack (serial key) latest version TLA;

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 It should unpack any themida packed file version 1. This post is only for educational purposes. The exe i'm looking to unpack is the one in bin folder, PT2. Try this tutotial: How Unpack Themida 2. In a Themida binary, different parts of the code are run in virtual machines and it obscures the behavior of the target program. Backtracing from the crashsite is probably hard because you dont know what the addresses pointed to back when you first unpacked it. The Code for the Anti-Debugger sequence, unpacks its self, and the. Functions: Unpack: Unpacks the binary you select. File list Click to check if it's the file you need, and recomment it at the bottom : Filename. We need blackhat with experience in themida packer unpacking for a long termework. NET is a tool developed to quickly and easily unpack packed. Note: You need to use a bit Python interpreter to dump bit executables. As you can see, it relies heavily on the JNI. If the version is new and there is no script, given your level of expertise right now, this will be a very, very long and arduous task. I hope people will be more interested in the subject, as it is incredible the world of reverse engineering. Warning: This tool will execute the …. So I see there seems to be still some open questions mostly if my older unpack script does not work anymore and the unpacked files to, etc. Dump the executable with extreme dumper or dnspy. To verify if this is your problem you can turn off ASLR, unpack your file again, and see …. Advanced warfare zombies trainer. Themida Unpack and Remove Ip check. Tags themida unpacker RickyWindCr4ck. It is something against Heap flag artifacts. This is most important script to unpack an Themida or Win License. However, as I expected, the Linux version was simply packed not protected and with something easy to unpack. You can try, currently there are no known unpacking scripts for PELock v2, unpackers, but I can show you plenty. Presented as part of the HCSS conference. Themida error: a debugger has been found running in your system. That specific dll isn't your target, maybe you should do more …. This has already been released 3 times today. Fix inability to read remote chunks of memory bigger than MiB. This version brings many exciting improvements, but also removes deprecated features and introduces breaking changes that may impact your workflow. Skills: Software Architecture See more: copywriting health beauty articles need similar experience repost, themida unpacking net, graphic design need web experience, need recruiting experience, themida …. Anti-API scanners techniques that avoids reconstruction of original import table. I was inspired by OALabs's video who made an unpacking of Themida, you can check his video to get a different explanation about the process to unpack a malwa. Jul 5, ; Thread starter 1 I tried all. I want to learn how to unpack Themida v2. Dump the bunded dll with MegaDumper, the vdump one should be test. To verify if this is your problem you can turn off ASLR, unpack your file again, and see if it works after a reboot then. So this time I decided to create a little video series on how to unpack and deal with a newer protected Themida target manually where my …. Guide] How Unpack Themida 2. When you execute the packed sample, it will unpack the executable in memory and use that to continue executing to perform and do what it's meant to do. PT2Start is just the launcher, it calls PT2. Heres what I've gotten so far: Code: package unpack; import java. BoxedAppPacker detected! Now with support for virtualized entry points and Delphi executables!. Unpacking a Themida packed x64 executable?. Once completed detail the methods used and how you fixed the DLL. This address changes with each reboot thanks to ASLR. HyperHide - Hypervisor based anti anti debug plugin for x64dbg. I spent 4 months testing a lot of methods from runpe dump to writing own hypervisor for full os hardware emulation but still not defeat this protector - winlicense 2. Unpacker properly handles invalid input filename. This is the unpack script we will use in this tutorial. I need an exe packed with the latest Themida unpacked, then the ip check inside said exe needs to be removed …. Status Offline Messages 45 Solutions 4 Reaction score Themida - Winlicense Ultra Unpacker 1. We have 2 files which are packed with PE protector. Packado y desempacado del packer Themida. It is a very common and well known packer, which is also considered to be an easy one to unpack. Discover HPCC Systems - the truly open source big data solution that allows you to quickly process, analyze and understand large …. If the issue persists, it can be related to your antivirus protection. Unpacking a Themida packed x64 executabl…. Now, my Problem is, all OllyDbg unpacking scripts for Themida are out, while the application is 64bit. Anti-memory dumpers techniques for …. Ok now we go open the target to unpack or just press F3, after opened we got a pop up, just press Yes and the file continue Analysing, just wait to finish. This file can not run, Try harder, Themida! Edited September 6, by Ufo-Pu55y. Themidie - x64dbg plugin to bypass Themida …. Nowadays malwares use the protector to conceal the malicious code from the analysis. Open Analysis Live! In this tutorial we show how to unpack a Themida 2. Channels , inputs locally from the X32 , are recorded as noise, very loud noise. Launcher again, Themida message x4 9 game launches perfectly 10 tried launching server, Themida message x32 11 server launches flawlessly and able to join 12 lauched server again, themida message x13 13 Server launches perfectly. But i found this foro with your instructions to unpack themida. It works on all versions of Windows XP and later. One of the mods is deleting it. The unpacked dll needs to run, to debug it. Especially, VMProtect and Themida are considered as some of the most complex commercial packers in bit Windows environments. Restart your computer twice and see if the problem is fixed. Looking for a PE Unpacker. FileNotFoundException; import java. So this time I decided to create a little video series on how to unpack and deal with a newer protected. NET, Themida doesn't really protect it except for in its non-running state. You can use a tool like MegaDumper to dump. Is it possible to unpack themida?. I represent the people of tRO came to help unpack Regexe. I have the dump for the exe, and I can see the code in reflector but PE tables and other part. It is plugin based making easier to add new archive file formats. Implement Themida-Unpacker-for-. Themida is a powerful software protection system designed for software developers who wish to protect their applications against advanced reverse engineering and software cracking. Is there a native exe unpacker for Themida? Themida is very hard to unpack even the new driverless versions , there is a ton of protections options that can be enabled see manual , so I doubt that there is a generic unpacker in the wild. I've tried the themida unpacker 1. The most common method of unpacking that I'm aware of is probably already streamlined and implemented into those tools, the run and dump method. Magicmida is a Themida auto-unpacker that works on some bit applications. How to unpack Themida - Winlicense so i could make my own unpacked client from latest ragnarok client. Warning: This tool will execute the target executable. NET programs running on the system to get the unprotected file in the case of Themida…. But a group of guys I have tried to study. Posted by pyschogsmdestroyer in: Scripts. Unpacking Tutorials Either way, best of luck to ya! View full post. PEiD detects most common packers, cryptors and compilers for PE files. Improve version detection to handle packed Delphi executables. Different encryption algorithms and keys in each protected application. Most likely its Themida or VMProtect. Compared to Themida v2, the themida v3 does not have a great improvement over the VMs. I think other hide plugin use the same trick. Even if you had videos you still have to do experimenting in order to unpack what ever you're doing. The best method to unpack a VM-protected packer like Themida is to devirtualize it, which involves figuring out the entire instruction set that the packer uses and writing a script to interpret that language. The program is using a checksum algorithm to detect if the dll is tampered. Currently, we are experiencing in the tRO people finding their Recvpacket. For major changes, please open an issue first to discuss what you. This tutorial shows you how to get original codes from a compressed program example 1. We need blackhat with experience in themida …. So temporarily disable your antivirus and update CopyTrans apps. I get debug the executable with ollydbg, but i can't find it's hard the exactly jump to bypass the verification dongle key HARDKey , because themida encript. I want to release a new tutorial about the popular theme Themida - WinLicense. Start CopyTrans Control Center. Hello, I'm a developer in Oreans Technologies and we have developed Themida to protect applications against cracking. There's a newer version: HERE. I'm looking for a person who can unpack and rebuild. So when I found this community, decide. However, I have never attempted to unpack Themida. Themida will pack the executable. Right-click on the antivirus icon and temporarily disable protection for 10 mins. Free iso unpacker Download UnPacker makes a queue of every rar added to the exe unpacker, unpacker exe, upx unpacker, unpack javascript, unpacker [email protected] Identify that your sample is packed A bunch of clues High section entropy Unusual small code segments Unusual segment names Home made scripts. I dug around the forums and someone mentioned that newer pangya revisions use a newer themida version, i downloaded exeinfo pe and indeed it points that it is packed with themida …. How you can unpack samples packed by Themida without requring knowledge of how to use a Debugger yourself manually 1. Functions: Unpack: Unpacks the …. Themida Now Days have Taggant Features. So, here's a long-promised update to Molebox unpacker. NET programs running on the system to get the unprotected file in the case of Themida. If it crashes during unpacking because it ran out of disk space, it's your problem. Now press F9 to run it and as you can see, we got a pop up, don't worry just press ok and the debug is terminated. I have a 32bit version from this, but, there is the same, all unpackers are stuck in procedure or hangs up. Net executables 32 and bit. Make sure to use this tool in a VM if you're unsure about what the target executable does. Malware analysis is one of the key problems. NET is a tool developed to quickly and easily unpack …. Successful malware distributors are not using public crypters as often, heuristics for detecting public packers is too easy, which is why we have seen a reduction in AIO unpacker tools. Anti-memory dumpers techniques for any Ring3 and Ring0 dumpers. Themida is so complicated to unpack that most people write scripts and so you can search for a script for the given version you are trying to unpack and attempt to use that. Gracefully handle bitness mismatch between interpreter and target PEs. How to Unpacking Themida? I'm trying to get back into reversing. To verify the effectiveness of x64Unpack, experiments were conducted on the obfuscation tools: UPX 3. I've been trying to hook nt apis and try debugging it. Support all version! Tested in 1. Unpacking themida and other protections. A protector is a software for protecting core technologies by using compression and encryption. It's free to sign up and bid on jobs. Jan 28, — Category Archives: Ioncube v10 decoder JavaScript Obfuscator is a free online tool that obfuscates your source code, …. I've made some changes to my game. The unpacked binary will be saved with an U suffix. My question is, how can I get better so that I can unpack Themida? I want to unpack Themida for the following reason: While reverse engineering GameLauncher. It was Spotify the application protected with Themida.
1 note
·
View note
Text
Nus Downloader Mac
Nus Downloader Mac
Nus Microsoft
Wii U Nus
Nus Matlab Download
Nus Downloader U
404'd?
WAD manager the latest version is 1.9 download now 2019 through the link provided: Wad-Manger-1.9.zip. See also: Pimp My Wii V.4.0. Downloads (Updated 2018) Pimp My Wii. Disclaimer: WAD Manager is also used to load pirated copies of WADs, but this practice is illegal and not the intention of the software. NUS downloader for linux/mac Hey, As usb helper is windows only, and i couldn't find any good solution to downloading backups on OSX, I've 'fixed' two old projects, based on FunKiiU, but with GUI.
Attempting to download Wii titles results in a 404. DSi titles seem to download okay though... Kamek 22:37, 5 April 2009 (UTC)
When this error happens, it deletes all the folder. For example, if you download an old version and then any not-existent version, it deletes the folder. This will be fixed, right? Duhow
I should probably start a more detailed naming convention for folders, such as (titleid)v(####) --WB3000 23:55, 8 April 2009 (UTC)
Could you specify some details such as Title ID / Version? Make sure both of them are legit, you can leave version empty for the latest one. --WB3000 22:56, 5 April 2009 (UTC)
Sorry, false alarm. Router settings were the trouble. Kamek 23:03, 5 April 2009 (UTC)
Had the same issue with this (404s downloading titles). It was the firewall settings. Check your firewalls if it doesn't work folks. Also, thanks for this program, cygwin and update downloader just didn't cut it.--Techboy 02:52, 6 April 2009 (UTC)
IOS file doesn't match dumped file from game disc
I downloaded IOS36 revision 1042 and compared it to my dumped IOS36-64-v1042.wad. IOS36-64-v1042.wad is bigger than the created one, because it has a duplicate of content 0(00000000.app) as trailer file included. And the certs and tik file differ, while the contents in the certs file just seems to have a different order. So my questions are: 1. Why is there the duplicate of content 0 as trailer in the official wad? Does anyone know, or might it be better to create own wads the same way? 2. What effect does the changed tik file have? Any suggestions why the file is different? --WiiPower 08:04, 6 April 2009 (UTC)
I based my packing code off of code by Crediar, as well as the WAD files documentation on this wiki. According to that, there is no duplication, and it would seemingly be ignored anyway according to TMD.
I don't knowingly edit the tickets, beyond sizing it down to 0x2A4.
Nus Downloader Mac
If there are any concerns about the process, please by all means check the source code, or simply use a different packer you are comfortable with. --WB3000 22:12, 6 April 2009 (UTC)
I'm sorry, i should have expressed more clearly what i meant. I just wondered why nintendo has 2 different tik files for IOS36v1042 and why nintendo packed the duplicated file into their wads. Does nintendo this for a reason? Does this have any effect on any application using these wads? Do installed IOS with these wads differ? --WiiPower 12:53, 7 April 2009 (UTC)
I have the same files and when comparing, the data section starts at 0xD00 in both, so I don't know where any duplication is occurring. I've installed a Shop v16 WAD with no apparent side affects.
Update - I've taken a look at headers between the two IOS36 wads. The cert I am using is identical to the one used in the official WAD, except parts are reordered. This is interesting but does not affect the overall cert itself. Perhaps there are several variations in the order spread around.
I honestly don't see two ticket files. When chopping out the data section (0xD00) and beyond, and from the beginning to the end of the cert, I am left with only a single ticket in both. The initial chunk of difference in the tickets is the hash, which would make sense. The small changes in the ticket appear to be the ticket_id as well as...Amount of bought DLC contents? Ticket_ID is odd, perhaps it is randomly generated and simply varies from Nintendo's disc distro to NUS.
I realized I must have merged TMD and cert together when examining, although that wouldn't affect anything as both TMDs are the same. --WB3000 02:21, 8 April 2009 (UTC)
IDs
Looks like my idea cough on ;) --Dan11495 17:23, 8 April 2009 (UTC)
I think that it would be ideal to have all ID information in the Title Database page itself, rather than only a portion scattered around on this page. Sadly, the database is a bit cluttered, so for now I'll leave what is there but I'd like to eventually organize everything where it belongs. --WB3000 21:57, 8 April 2009 (UTC)
Title DB
Please add found titles to Title database instead and IOSs here IOS HistoryCrediar 15:04, 10 April 2009 (UTC)
I've went ahead and merged everything to those pages. ;)
Mono
To run NUS downloader on Linux/mac you need to do this
1. Run terminal2. Type CD (NusdownloaderPath)3. Type Mono (name of Nusdownloader.exe)
You need Mono 2.2 or higher
NUS Deleted some folders on my desktop!
Not only did it delete 5 or 6 things off my desktop, It deleted certs, key.bin, readme, and the folder it was in.It killed like, 20000 famly photos. NEVER, EVER, EVER useing on my PC again. :-/ —Preceding unsigned comment added by Remadon (talk • contribs) 17:07, 17 May 2009
Honestly, I don't believe there's any way that could happen. The only thing deleted is the title ID directory upon a 404 of that Title. You could probably try some file undeletion software in the meantime. --WB3000 18:21, 17 May 2009 (UTC)
I've been looking into the issue. There is only one way this could happen: You entered nothing into either box. I've fixed the potential issue here, maybe I'll throw a v1.1a if necessary. --WB3000 21:21, 17 May 2009 (UTC)
Ouch, that's a pretty bad bug. I left you a message on your talk page on how you (or anyone else that may encounter this bug) can recover your data with Recuva. — 22:16, 17 May 2009 (UTC)
Actually, the same thing happened to me. I just ran a System Restore Point and got everything back. It restored everything as if nothing happened. --SonicHyuga 23:24, 17 May 2009 (UTC)
OK, I've pushed v1.1a with the nothing-entered check. Hopefully this is the issue, since there's nothing else that would make this happen. --WB3000 23:52, 17 May 2009 (UTC)
Sorry about not signing the post, It was by me, My brother had everything backed up, so its not a big deal. Glad to hear the bug is fixed. Sorry for the User confusion,Yay! Bug is fixed! Just tryed it! --Remadon—Preceding undated comment added 03:52, 18 May 2009.
*nix Port?
It would be really cool if you could port this to Unix systems(Linux/Mac). A command app would be great and easy to do as it's just a downloader!RedChaos 17:07, 17 May 2009 (UTC)
I just found a CLI rewrite of my program today, though it's still C#. Perhaps it will compile with Mono, or at least have less issues doing so. --WB3000 18:22, 17 May 2009 (UTC)
Mismatch 'Error' at Pack->WAD?
When I download some IOS, the NUSD says at packing the WAD 'mismatch'Example:00000000 wrote (0x1100);; 00000001 wrote (0x1140) (Mismatch) ;; 00000002 wrote (0x92c0) (Mismatch)...
I compared with a packed file, downloaded with the 1.0 Version. They have the same Size, Bytes same too.So, what means that? (I tried several times, same 'errors' in different IOS. —Preceding unsigned comment added by Boy2048 (talk • contribs) 14:58, 18 May 2009 (UTC)
Having a mismatch is OK. It basically relates to how some files are padded in order to allow AES encryption/decryption to work. Files not aligned to 16 bytes are padded with 0x00 bytes until this is achieved, and then encryption is done. However, the size stated in the TMD relates to the 'useful', before padded size. Having a mismatch simply means that TMD vs actual size differs, which is quite common.
As long as the download completed successfully, a mismatch isn't anything to worry about. --WB3000 20:53, 18 May 2009 (UTC)
mismatched
When packing the sysmenu 3.4 wad I get the error mismatched. Is it still safe to install? TwoBladedKnight 09:57, 20 May 2009 (UTC)
See above question... --WB3000 20:37, 20 May 2009 (UTC)
Sorry... I probably should've read this page before jumping in >.< my bad... TwoBladedKnight 06:19, 21 May 2009 (UTC)
compiling
I cannot compile stuff, it seems to need another file when compiling.
Erreur 1 Le nom 'InitializeComponent' n'existe pas dans le contexte actuel SourceCode.cs 34 13 Project2--Attila 17:01, 20 May 2009 (UTC)
I only gave the actual form code. This is all that's really modified from a standard C# GUI template. Source is included as more of a 'how-to' reference, not as a perfect, compiling collection of files. --WB3000 20:37, 20 May 2009 (UTC)
The Form is missing, so i must draw a new form to use your code.--Attila 18:21, 22 May 2009 (UTC)
Now the entire source code can be found on Google Code. (see main page). --WB3000 03:05, 11 June 2009 (UTC)
Thanks. In fact i wanted the source to add the ability to select 'common' title id like for ios available on nus, and common channel (wiishop etc) without needing to do the translation IOS36 -> 0x24 -> 000100024 .. etc :) —Preceding unsigned comment added by Attila (talk • contribs) 12:06, 11 June 2009 (UTC)
Next version has a database feature, as you can probably see from the code. That's about as common as the IDs can get :P. —Preceding unsigned comment added by WB3000 (talk • contribs) 19:38, 13 June 2009 (UTC)
KUDOS
I've got to give you kudos for this app. Thanks to this excellent app I can have almost all system menus whenever I want! THANK YOU! TwoBladedKnight 10:38, 21 May 2009 (UTC)
Mac please?????
I would be ever so grateful if you would port this for mac as i have not one windows computer in my house. Yet i still need to use this application for (well what this app does)thanks very much --Flyguy 16:46, 21 July 2009 (UTC)
Please?--Flyguy 22:16, 9 August 2009 (UTC)
Won't close when finished in the command prompt
When I type something like this into the command promt
it downloads and packs fine, but the process doesn't stop itself, it's taking up quite a bit of CPU so I'm not sure what it's doing?--594rk 22:03, 5 August 2009 (UTC)
I'm going to look into that, I haven't really tested much of the cli features, and it's becoming clear that they are not working as I had planned. --WB3000 15:55, 6 August 2009 (UTC)
Wrong filename for WAD
Filename for wad are exact but they are not for BC/SYSTEM Menu. They are like : System Menu-NUS-v193.wad instead of RVL-WiiSystemmenu-v193.wadFilename does not use databse if we click on pack wad AFTER selecting a title in the database.However, good app.--Attila 17:26, 7 August 2009 (UTC)
I've gone ahead and added both System Menu official naming, as well as database lookups for the filename during any change to the info (including checking the box after selection) ;) I'll throw it in the SVN, however it won't be official until 1.3. --WB3000 20:50, 7 August 2009 (UTC)
Ok thanx. By the way, mios is wrong too, it's RVL-mios-v5.wad and not MIOS-64-v5.wad--Attila 22:44, 7 August 2009 (UTC)
MIOS filename is wrong :)--Attila 13:30, 18 August 2009 (UTC)
key.bin file
where can i get the key.bin file??? Darklink 01:47, 13 August 2009 (UTC)
Well for starters it is also known sometimes as common-key.bin. Google is probably your best bet, or perhaps some other program might have it bundled. --WB3000 12:32, 13 August 2009 (UTC)
The WiiScrubber package has a file MakeKeyBin1.1.rar included which has a generator for both key files. Or you can go to http://hackmii.com/2008/04/keys-keys-keys/ and write your own key.bin file with an hexeditor. --WiiPower 15:44, 13 August 2009 (UTC)
Why doesn't key.bin come with this program? marcan said somewhere that you can't copyright keys. Link33 12:41, 13 August 2009 (UTC)
Marcan doesn't live in the United States, so he is unaffected by the DMCA. It was ineffective against the infamous 09 f9 11 02 key, though. --Dialexio 14:02, 18 August 2009 (UTC)
Nus Microsoft
Hash Check: Fail
Hey I'm just wondering why I get failed hash checks. I am downloading System Menu 4.1U. Here is my log:
--Bdr9 12:06, 23 August 2009 (UTC)
You have a incorrect key.bin file, go dump one from your Wii. LoganA (talk • contribs) 21:47, 23 August 2009 (UTC)
Wii U Nus
NUSD_13beta - Application Error
I get a weird error message when running it.
Nus Matlab Download
Any help? Thanks!Mp3c 03:06, 8 October 2009 (UTC)
You do not meet the prerequisites of the program. To be more specific, you do not have the .NET Framework 2.0 installed. --WB3000 21:19, 27 October 2009 (UTC)
Full restore
Could you please tell me if can i use this tool to completely restore my wii as if it were never hacked (patched)?I'm asking it because a stupid friend of mine put all that shitty cIOSCORP inside my wii and i don't wanted it, can i use this tool or anything else to remove it and make my wii look just fine?(just a little note: really I didn't wanted it!)Thanks for your comprehension and help!--balta 20:54, 2 December 2009 (UTC)
401 Unauthorized?
Im really sorry if this was already answered somewhere, but anyways:
I was trying to download BC (title ID: 00000001-0000010)
and it gave me the 401 error: --- 00000001-0000010 ---Starting NUS Download. Please be patient!Grabbing tmd...Download Failed: tmd
I have key.bin and everything, and I'm connected to the internet. Help? :)Quinnfap 19:48, 29 January 2010 (UTC)
I just tried and it worked fine...What version where you trying to download? Can you repeat the error? --SifJar 19:58, 29 January 2010 (UTC)
Size DOES Matter
Original page text regarding size:After the initial release, there were concerns rising about differences in file sizes between official WADs and NUSD ones. A first, obvious difference is in that official ones have a footer, and NUSD packed ones do not. This adds a few bytes onto the official ones which will not be present.
A second difference may be noticed in the Certificate Chain added to the WAD. While it may appear entirely different, it is simply ordered in a different way, and the Wii sees nothing different. V1.1 of NUSD will order the certs in the most common way, so that difference is covered.
The only real difference is in some tickets. NUS has a variation on the ticket for a title, as do the WADs that come in discs. While they are different, the only changed values are small (ticket_id and DLC purchases). The big things like Title Key remain intact. There has been no issues using these tickets, which is understandable as many are probably on your Wii right now.
I think you should write out the footer because I've found for some things (comex's formatter), it will fail an assert and completely crash because (as far as I can tell) the sizes differ. Could you do something about this and try to make the wads 1:1 with official wads? Thanks! tpw_rules 21:51, 11 February 2010 (UTC)
NUS Downloader works under Arch Linux using WINE 1.7-44-2 --PCMRShadowWolf (talk) 23:36, 14 June 2015 (CEST)
Rar file doesn’t open
Nus Downloader U
It says it’s like damaged or something, not even 7 zip works
Retrieved from 'https://wiibrew.org/w/index.php?title=Talk:NUS_Downloader&oldid=108541'
0 notes
Text
Version 310
youtube
windows
zip
exe
os x
app
tar.gz
linux
tar.gz
source
tar.gz
I had a productive week. A bunch of stuff is fixed, and I finished a first version of multi-file url downloading.
multi-file support
A limitation of the old download system is that it always assumed a single 'post URL' could only ever produce a single file. This week, I have added full support for multi-files-per-post-URL to the new downloader. If a new parser generates multiple 'downloadable' URLs, the file import queue will generate and insert new download objects for each. Tags and associable URLs should all be passed along to the children as appropriate.
As a result, I can finally roll out support for several sites that provide files in this way. I've updated the inkbunny post parser, and added twitter tweet and artstation post parsers, so all these should now be drag-and-droppable onto the client. The twitter parser only supports images--no videos yet. The inkbunny parser may put its multi-files slightly out of order, and in one of my tests it pulled the artist profile picture as well, so it may need some tweaking. IB have a proper API, but it requires some login stuff, so I will look at that again when I have the new login system done.
And of course I have added a pixiv manga parser, which has been highly requested for a long time. This was fairly complicated, but I think I got all the referral URLs and tags lined up correct. It can even add 1-indexed page tags. Unfortunately, pixiv just changed my test login to the new (currently broken) JSON/javascript layout just today, as I did final testing. If it turns out pixiv have switched everyone over to the broken layout on the very day I finally roll out manga support, I think my head is going to explode, but even if so, I am confident the javascript layout is parsable--it'll just take a bit more work. I expect to have a fix for all pixiv users for v311 if another user doesn't post one sooner.
This multi-file parsing is a first version. There may be bugs, so please let me know. I also don't really like how the initial post URLs' file import objects get counted as 'successful' like a regular file, so I may make a new 'successfully parsed' type to distinguish them a bit and alter the file progress counts appropriately.
misc
The new 'x% in' video thumbnail generation works better and fails better now, including some better workflow and error-reporting when regen is manually started by the user. If you had some videos that failed to import or regen last week, please try them again and let me know if you still have problems.
The multiple watcher now has a 'check now' button.
I added a semi-crazy prototype checkbox to options->gui that puts all your page tabs on the left. It needs a restart to kick in. Test it at your own risk.
The new download system now informs the new network engine of file limits in your 'file import options'! So, if you say 'don't get gifs bitter than 32MB', and the server clearly identifies a newly started download as a gif with size 50MB, the download will be abandoned and a veto/ignored status set immediately! It also works with the regular min/max filesize as appropriate. Let me know if it goes wrong!
I cleaned up some file repository thumbnail sync and display code all around.
github
Github got bought by Microsoft, so I am considering migrating somewhere else. I only use Github as a file/code host and the workflow of syncing there is easy, so I may or may not go, or may just put it off and see what happens during the transition. I am interested in your thoughts on the whole deal and what you think of the alternatives.
full list
updated the inkbunny file page url class to acknowledge that inbunny pages can have multiple files
updated the inkbunny file page parser to handle multiple file urls (although they may be out of order and possibly sometimes include the artist profile image--this was not super easy)
added a parser for twitter tweets (only images supported atm, but it can handle multiple!) (hence tweet drag and drop now works!)
updated the artstation file page url class to redirect to a new api url class
wrote an artstation file page parser that also handles multiple file urls
updated/added pixiv file page, manga page, and mange_big url classes
updated pixiv file page parsers to be ok with manga links
wrote parsers for pixiv manga and manga_big pages to fetch manga files (with page tags)!
file import objects can now create semi-duplicate children for multi-file post urls and insert them just after themselves in the file import queue.
file import objects can now receive and remember referral urls. this referral url is associated with the file if appropriate. the watcher and simple downloader now uses this in addition to the multi-file post system
jumbled around some parameters and merged the two new file import url commands (import 'file' vs import 'post') into one single simple 'work on this url, thanks' call that is now used across the program
the parsing system's 'content parser' no longer fetches file urls and post urls, but 'download urls' and 'source urls'. this helps some pipeline logic and also lets post urls be download urls
when file import objects parse post urls as the urls to download, it now creates 1-n new import objects, just like if multiple file urls.
improved some file import object file association code
the new parsing system will de-dupe parsed urls
refactored the 'seed' code, which handles all basic file import objects, to the new ClientImportSeeds.py
added a new string transformation type, 'integer addition', for shifting page number tags up and down
fixed thumbnail generation for some videos that failed to do the new x%-in generation--it reverts more reliably just to the old frame 0 method
file reparsing popup now has a stop button
fixed an issue where extremely thin or wide (ratio > 200:1) images would not generate a full-size or resized thumbnail
the file reparsing/re-thumbnailing now reports errors better (including with full path) and does not abandon the larger job as it works
misc thumbnail generation code improvements
improved some thumbnail and file regeneration/moving code when the existing file has read-only status
the multiple watcher now has a 'check now' button
added a checkbox to options->gui that will put new notebook page tabs on the left
for all file download network jobs working in the new download system, the file import options for min size, max size, and max size (gifs) are now applied _during the download_! if the server tells the client the exact file size in the response headers, it will test max and min size before the content is actually downloaded--otherwise, it will test the max size as it downloads. if the server clearly says the file is a gif, the max gif size rules will also be tested in the same way
cleaned up some bandwidth announcement code--now, if bandwidth is due in less time than override time, that will now correctly be the status text
the bandwidth status no longer says 'in in' typo
fixed up some tag repair code from last week
the 'print garbage' debug function now dumps a whole bunch more data to the log
the thumbnail cache should now be a bit more stoic about missing repository thumbnails--it should now just present the hydrus default backup without error popup spam
the repository thumbnail sync will now get as thumbs in blocks as high as 10k at a time, rather than the old 100
hydrus network requests no longer generate web domain network contexts (and so won't have a default one-request-per-second bandwidth limit and should stream through thumbnails a bit faster)
hydrus network services are now willing to wait longer for bandwidth, so big thumbnail queues should keep working even if other bottlenecks pause them for a bit
hydrus network services will no longer sometimes have double-sync popups if synced from the advanced 'sync now' button in review services
changed the default global 'stop-accidents' bandwidth rule of 120rqs per minute to 512MB per minute. this only affects new users, but users trying to sync to large file repos might like to make a similar change manually
doing giant full file delete (i.e. purge from trash) jobs should now be a bit gentler on the gui
improved how the client deletes paths, clarifying in the code when and when not to allow recycle (usually disabled for thumb disposal)
switched the hacky text widgets on the popup system to a newer object. seems to still render ok, so lets see if it fixes some unusual layout issues some users have seen
if the temp folder cannot be created on boot, the client will continue anyway
fixed some url-domain text handling in db storage that was also breaking v309 update for some users
fixed some additional domain generation error handling at the db level
the list of url classes in the system:url panel is now the list of all url classes that are considered associable (before, it was file and post urls)
if a url class now api-links to itself or otherwise forms a loop with n other api url classes, the client will now throw an error (rather than lock up in an infinite loop!)
in the parsing ui, tag parse test results are now cleaned before being displayed
fixed misc url matching error reporting bug
when consulting the current file limit, the gallery page downloader will now try, when it has that number, to consult the total number of urls found it the current search (old behaviour is to only consult the number of _new_ urls, which lead to some bad edge-case workflows)
misc refactoring
next week
I am going to take a light week next week so I can shitpost E3. I will try and keep up with messages, but I'll only do a little fixing work. I will get back to regular schedule on the 16th, which means v311 will be on the 20th. I will make a 'No Release Tomorrow!' post on the 12th.
I am a little ill and completely exhausted, so an easy week is coming at a great time.
I am still really enjoying making hydrus. Thank you for all your continued support!
2 notes
·
View notes
Text
Family Sketch


Helen Schatvet Ullmann, CG, FASG [adapted from the author’s article in New England Ancestors 8:3 (Summer 2007):41–42, 45]
Do you have a thick file or a notebook full of information you’d like to write up for your family? Or even boxes and boxes of it? Maybe your data is in Family Tree Maker or some other program. Or maybe you’re just in the beginning stages of your research. In any case, whether you just want to write about your grandparents or compile a whole book, the basic building block is the family sketch, treating a couple and their children in an organized and interesting way. Word processing, extremely flexible, is a wonderful tool for genealogists. Remember the old days when we had to cut and paste and retype, perhaps introducing new errors as we went along? About twenty years ago, NEHGS sponsored a seminar held at the Museum of Science here in Boston. My only memory of the whole day is Alicia Crane Williams saying, “As soon as you get a little information, put it in Register style. This is part of the research process.” So I went home and on my quaint little Apple IIe began transcribing old family group sheets crammed with information. My descendants might just take them to the dump! What is a family sketch? It’s just a story with a beginning, middle, and end. The beginning is the first paragraph that contains the vital information about the parents — all of it. So, if the reader later wants to check back to see just when your great-grandmother married her second husband, it’s easy to find. The middle is whatever you want, usually a biography in chronological order. It could include funny stories or a serious analysis distinguishing between your grandfather and another fellow who bore the same name. At the end is a list of children with their vital data. You may have mentioned each child as he or she joined the family, married, or died, in the biography above, but it’s still important to have a straightforward list of children at the end. Children for whom there is a lot of information may be continued in their own sketches. You can begin with just shreds of information. I started one sketch with my mother’s memories, her grandparents’ names and the recollection that she would sit on her grandfather’s lap and braid his side whiskers — plus the fact that he was a Congregational minister. Then I listed her mother, her aunt, and her uncles, using “Conversation with . . . ” and her name and relationship in footnotes. On the other hand, I have many folders of notes gleaned in the ’70s and ’80s, b.c. (before computers). It’s fun to open one, outline the family structure, and start adding information almost at random as I go through the file. As I work, I can see where I need to bolster a statement with pertinent analysis or where I could undertake more research. Before starting to write, you might read some sections in Genealogical Writing in the 21st Century,[1] especially the pages that diagram the different elements of the parents’ and children’s paragraphs. There isn’t space here to discuss all the fine points, including numbering systems.[2] Many other matters, such as whether to use abbreviations, are really your own personal preference. Generally the fewer the abbreviations, the smoother the reading. Complete sentences, rather than lots of semicolons, also make reading easier. Now you can just start writing. But here’s a suggestion: if you are going to start from scratch (as opposed to creating a “report” from your genealogy database), go to AmericanAncestors.org. Click on the Publication tab, then on theRegister, and then under Side Links, on “Download a Register Style Template for Microsoft Word.” Then “Download the Template!” If you have Microsoft Word on your computer, a document that can function as a template will open. I won’t repeat all that the template says, but it will help you format your sketch, especially those pesky children who appear in hanging paragraphs. This template contains all the “styles” that we use in the Register, everything from title to footnotes. The word “style” here does not refer to Register “style.” It is a word-processing term that refers to the format of each paragraph. When you open Word, you will be in “normal” style, but this paragraph is being written in “body text indent.” The only difference is that the first line is indented. Hanging paragraphs for children are more complicated. These paragraphs line up roman numerals on a “right tab.” There are even styles for quotations and grandchildren. If you’ve already arranged some material and want to use that template, simply copy your work into the blank template. First select your whole document and make sure it’s in normal style. Go to “Format,” then “Style,” and select “normal.” Delete all tabs and spaces you added to format the children. After pasting your work into the new document, save it under the name you want to use. Then review the text and select the “style” for each paragraph by placing your cursor in the paragraph and choosing the style from the Format menu. There should be a little window on your toolbar that lists the styles and offers a quicker route. You can select many paragraphs at once. (A technical detail: if you want to edit the style in any way, say choosing a different font or left-justified text, go to the Format menu, choose “Style,” and click on “Modify.”) In the Register we generally use “normal” style for the first paragraph where the parents’ vital data appear. Then we switch to “body text indent” for the biography. We introduce the children with a “kid’s intro” style and then choose “kids.” When you use that style, hit tab, then the first Roman numeral and a period, then hit tab again. Both tabs will then appear, and you can start typing the child’s name. Small caps are very elegant here. Notice that we include the surname for each child. Then there’s no doubt about the surname and indexing is easier. If you want to list grandchildren, you’ll find the “grandkids” style works a little differently. No tabs needed. Just type the arabic numeral and a period. Then two hard spaces help the names line up nicely [use Control-Shift-Space]. In the Register we use italics for grandchildren’s names. Even the footnotes and footnote references have their own styles. We encourage you to cite your sources for everything. Footnotes are much handier if your readers will really use them, but endnotes may seem less intimidating. The basics of citation format are not difficult. Look at issues of the Register for examples. A current guide is Evidence!,[3] good to have at hand, but the Register often uses simpler formats. The Chicago Manual of Style is also helpful.[4] It saves time to enter the notes correctly the first time. (By the way, the footnote reference number goes after the punctuation.) A further hint about writing style: try reading your work out loud. Are you using empty phrases you would never use when talking? Can you say something more concisely? Are your sentences really sentences? Passive voice — “The ball was hit by the boy,” rather than “The boy hit the ball” — deadens the tone. And proofread, proofread, proofread. You’ll improve your sketch every time.

All the best Family Sketch Images 38+ collected on this page. Feel free to explore, study and enjoy paintings with PaintingValley.com. As I look toward shifting to a different family line in my own research, I think I’m going to take the time to write a bio sketch for the main ancestor I’ve been researching, George Washington Adams (1845-1938) before I say goodby to him for a little while. I think it should be a fun exercise. 93,432 family sketch stock photos, vectors, and illustrations are available royalty-free. See family sketch stock video clips. Family future plan group of sketch family people walking in the garden building a family sketches of future family design interior family sketch color family and money family with money thinking wall.
Finally, for the “icing on the cake,” dress up your sketch with illustrations! Insert photos, autographs, pictures of houses and gravestones, the ship on which your ancestors crossed the ocean, maps — whatever you can find. Your final product should be elegant and attractive, not just to your children but to their grandchildren and beyond.
Sidebar:
A few little tips
Commas and periods go inside a closing quote; semicolons outside.
Footnote reference numbers come after the punctuation.
Titles of published books should be italicized.
Titles of articles and unpublished materials need quotation marks.
Titles of sources such as land, probate, and vital records do not need italics or quotes unless they are published.
Proofread on another day.
Try reading your prose out loud!

Sidebar 2:
Polishing that database reports
In word processing you can discuss all sorts of nuances of dates, places, and identities wherever they seem to fit. Such additions are not so easy when working with a genealogy database. There are quite a few differences between what we consider Register style and the quasi-Register-style report generated by most genealogy programs. If you are using one of these programs, here are some things to consider.
Once you have generated a report, it will carry its own set of word-processing “styles.” You can just accept them, or eliminate all of them by selecting the whole document and putting it in “normal” style as described above, then copying it into a blank Register template. If you do so, eliminate any sex designations for the children first. (You can easily comment on any unusual name in the text or a footnote.)
Family Sketch Clipart Black And White
You should make some other changes as well. First, consider the order of the information. Do the wife’s name and vital data appear after the husband’s notes, with notes on her following? Move information on the wife into the husband’s paragraph and integrate her notes with his. Next, did you document those notes with citations in parentheses? All citations need to be moved into footnotes (or endnotes if you prefer). Multiple footnotes for the same piece of data should be combined into one note, with semicolons between the different sources. You must also consider the format of names, dates, and places. Small caps are good for names, but your report will probably have a mixture of lower and upper case. Capitalizing names of the parents of husband and wife would be distracting. Place names don’t require a county or state after first use in each sketch, but it’s helpful to the reader to add “County” where appropriate. Postal codes are also distracting. In the Register we spell out the names of months and states in the main text and abbreviate them (except those with five letters or less), with periods, in the children’s paragraph
Family Sketch Picture
--------------------------------------------------------------------------------------------------------------- 1Michael J. Leclerc and Henry B. Hoff, ed., Genealogical Writing in the 21st Century, 2nd ed. (Boston: NEHGS, 2006). 2See Joan Ferris Curran, Madilyn Coen Crane, and John H. Wray, Numbering Your Genealogy: Basic Systems, Complex Families, and International Kin, National Genealogical Society Special Publication No. 64 (Arlington, Va.: National Genealogical Society, 1999). 3Elizabeth Shown Mills, Evidence! Citation & Analysis for the Family Historian (Baltimore: Genealogical Publishing Co., 1997). The introductory sections of this book are especially valuable. 4The Chicago Manual of Style, 15th ed. (Chicago and London: University of Chicago Press, 2003).
Cartoon Drawing Of A Family
This book publishes, for the first time in full, the two most revealing of Mark Twain’s private writings. Here he turns his mind to the daily life he shared with his wife Livy, their three daughters, a great many servants, and an imposing array of pets. These first-hand accounts display this gifted and loving family in the period of its flourishing. Mark Twain began to write “A Family Sketch” in response to the early death of his eldest daughter, Susy, but the manuscript grew under his hands to become an exuberant account of the entire household. His record of the childrens’ sayings—“Small Foolishnesses”—is next, followed by the related manuscript “At the Farm.” Also included are selections from Livy’s 1885 diary and an authoritative edition of Susy’s biography of her father, written when she was a teenager. Newly edited from the original manuscripts, this anthology is a unique record of a fascinating family.

0 notes
Text
The Stack
When a program starts, it granted a fixed size of memory called the stack. Since all reasonable programming languages support recursive functions, the arguments and the local variables should be allocated on the stack to preserve their values during the execution.
The most famous function to present recursion is factorial(). Let's write yet another one. For our purposes, it outputs the addresses of the arguments at the standard output.
#include <stdio.h> #include <stdlib.h> double factorial(double n) { printf("%.0f %u\n", n, &n); if (n == 0) { return 1; } else { return n * factorial(n - 1); } } int main(int argc, char* argv[]) { double d = atof(argv[1]); printf("Factorial %f is %f\n", d, factorial(d)); return 0; }
argv[1] is the first argument we supply to our program, and atof() is the standard function that converts a string to a double-precision floating-point value.
When we run the program with argument "5" it outputs:
$ ./a.out 5 5 123147368 4 123147336 3 123147304 2 123147272 1 123147240 0 123147208 Factorial 5 is 120
As you can see, the address of the argument n goes backwards by 32 bytes in each iteration. Those 32 bytes area is called "stack frame". In addition to arguments and local variables, it stores the caller's address at code segment for knowing where to go when it is time to "return".
Let's do a silly thing and add a new local variable like the following;
double factorial(double n) { char s[1000]; ...
you can observe that the stack frame is bigger now:
$ ./a.out 5 5 244948200 4 244947160 3 244946120 2 244945080 1 244944040 0 244943000 Factorial 5 is 120
Stack segment is used with a technique called LIFO (last in first out) during the execution. Let's add a new function called termial(). The name termial is invented by the famous scientist & programmer & author of many books, Donald Knuth. It is an alternative to factorial() for using addition instead of multiplication.
... double termial(double n) { printf("%.0f %u\n", n, &n); if (n == 0) { return 0; } else { return n + termial(n - 1); } } int main(int argc, char* argv[]) { double d = atof(argv[1]); printf("&argc %u Factorial %.0f is %.0f\n", &argc, d, factorial(d)); printf("&argc %u Termial %.0f is %.0f\n", &argc, d, termial(d)); ...
As you can see, the stack addresses are reused during the separate calls for first the factorial(), then the termial():
$ ./a.out 5 5 214900440 4 214900408 3 214900376 2 214900344 1 214900312 0 214900280 &argc 214900476 Factorial 5 is 120 5 214900440 4 214900408 3 214900376 2 214900344 1 214900312 0 214900280 &argc 214900476 Termial 5 is 15
5 is a little number and works like a charm. But it silently eats the stack as the recursion goes deeper. In the above program, we added the address of the argc to mark where our stack started.
214900476 - 214900280 = 196
For the argument 5, 196 bytes of stack frames are used. What if we call our function with a bigger number like 1000:
$ ./a.out 1000 ... 7 339722472 6 339722440 5 339722408 4 339722376 3 339722344 2 339722312 1 339722280 0 339722248 &argc 339754284 Termial 1000 is 500500
The difference between 339754284 and 339722248 is 32036, about 32KB. It may seem a little, but once we want the result for 1 million;
$ ./a.out 1000000 ... 738237 2777516536 738236 2777516504 738235 2777516472 738234 2777516440 738233 2777516408 738232 2777516376 Segmentation fault (core dumped)
we reached the end of the stack and crashed because the addresses below the stack are unallocated. Let's do a little math again:
1000000 - 738232 = 261768 * 32 = 8376576
As you can see, 8,376,576 bytes are used for the stack in this scenario. Academics tend to over-teach recursion during their courses, and you are "stack-overflowed" at the most unfortunate time if it is overused. The end result is almost always "flattening" the algorithm like the following:
double factorial(double n) { int i; double result; if (n < 1) { return 1; // I don't care about negative numbers } result = 1; for (i = 1; i <= n; ++i) { result *= (double)i; } return result; }
Ugly, isn't it? But it only uses a few bytes of the stack and doesn't crash. It is also faster because it avoids function call overhead which includes arranging the stack frame and jumping to start of a function. Those operations may be cheap but not free.
The stack size is fixed. Why not a growable stack? Because in the real world, recursions may not be evident as in the factorial() and sometimes a mistake by the programmer caused an infinite recursion. If the stack is somehow made growable, it can eat all the RAM trying to store useless intermediate values, and the computer is grounded to a halt. Thanks to the fixed-size stack, that kind of faults crashes the program early without killing the system.
Operating systems tend to give a default stack size for the programs. It is also possible to control stack size by other means. The first method is telling the C compiler that our program needs more (or less) stack:
$ gcc -Wl,--stack,4194304 -o program program.c
This way, the "program" will request 4MB of stack space while running. It is also possible to change it during the runtime. For Linux, setrlimit() system function is used for this purpose:
struct rlimit rl; rl.rlim_cur = 16 * 1024 * 1024; // min stack size = 16 MB; result = setrlimit(RLIMIT_STACK, &rl);
Windows' Win32 API has SetThreadStackGuarantee() function for that purpose.
Modern languages aren't exempt from stack overflows. The following Java program;
public class Xyz { private static double factorial(double n) { if (n == 0) { return 1; } else { return n * factorial(n - 1); } } public static void main(String[] args) { try { System.out.println("Factorial " + factorial(1000000)); } catch (Error e) { System.out.println(e.getClass()); } } }
also crashes with the following:
class java.lang.StackOverflowError
Usually, in a catch block, it is best to write the stack trace. But for errors like stack overflow, the stack trace is also too big to dump as-is, so we only wrote the error class to prove that it is a StackOverflowError. In practice, exceptions are dumped into the log file, and as you can guess by now, it is possible to blow your log files by bad recursion. Be careful.
Tail Call Elimination
We criticized the overuse of recursion for good reasons except that academics are not dumb. They invented a technique called "tail call elimination" to prevent unnecessary stack usage during recursion. Let's review the line that returns by calling itself in the factorial() example:
return n * factorial(n - 1);
This is clearly the last line of execution for the function. A smart implementation may decide that we don't need the stack frame here anymore, rewind the stack frame and replace the values with those we computed during the execution.
Among the popular languages only Haskell, Scala and Lua support tail call elimination. Let's write the termial function in Lua:
function termial(x) if x == 0 then return 1 else return x * termial(x - 1) end end io.write("The result is ", termial(1000000, 1), "\n")
After running the program;
$ lua ornek.lua lua: ornek.lua:5: stack overflow stack traceback: ornek.lua:5: in function 'termial' ornek.lua:5: in function 'termial'
we still got a stack overflow. To detect the need for a tail call elimination, Lua requires that the return statement call only one function. So we rewrite the termial:
function termial(x, answer) if x == 0 then return answer else return termial(x - 1, x + answer) end end
As you can see, we reduced the return statement to a single function call while adding an extra parameter to the termial() (and making it uglier).
The result is 500000500001
Supporting tail call elimination is always a heated topic among language designers. Python's founder Guido van Rossum made the most famous comment against it by telling it's "Unpythonic" in 4 points:
...when a tail recursion is eliminated, there's no stack frame left to use to print a traceback when something goes wrong later.
...the idea that TRE is merely an optimization, which each Python implementation can choose to implement or not, is wrong. Once tail recursion elimination exists, developers will start writing code that depends on it, and their code won't run on implementations that don't provide it.
...to me, seeing recursion as the basis of everything else is just a nice theoretical approach to fundamental mathematics (turtles all the way down), not a day-to-day tool.
http://neopythonic.blogspot.com/2009/04/tail-recursion-elimination.html
Multithreading
In the beginning, CPUs got faster each year. But for the last 10 or so years, they haven't got faster as quickly as once it was. In a conflicting trend, more speed is required from the hardware because of the Internet.
The industry found the solution in parallelization. More CPUs are added into the mainboards, and nowadays, the cheapest smartphone has at least 2 CPUs on it.
Each program has at least 1 thread of execution, and as we know that we have more CPUs on hand, we are encouraged to create more threads in our programs. Go programming language is created with that in mind providing first-class support for multithreading:
go f()
As you can see, it is as simple as using the "go" keyword to let the function run in another thread.
The bad news is that each thread of execution needs to have its own stack so we should take that into account while spawning many threads of execution because most languages and runtimes don't tell you much about that. In "go f()", we basically say
In C or operating system level, the stack size is taken on consideration while creating a thread. Let's see the prototype of the Win32's CreateThread() function:
HANDLE CreateThread( LPSECURITY_ATTRIBUTES lpThreadAttributes, SIZE_T dwStackSize, LPTHREAD_START_ROUTINE lpStartAddress, __drv_aliasesMem LPVOID lpParameter, DWORD dwCreationFlags, LPDWORD lpThreadId );
The second argument is the stack size for the thread. If you don't want to think much about it, you can just specify 0 and get as much stack your process requires. This is 1MB for most of the time, a rather massive number if you intend to create many of them. The official Win32 documentation recommends the opposite:
It is best to choose as small a stack size as possible and commit the stack needed for the thread or fiber to run reliably. Every page that is reserved for the stack cannot be used for any other purpose.
https://docs.microsoft.com/en-us/windows/win32/procthread/thread-stack-size
A thread may have a small stack segment size, but we will probably not know that while coding, especially in a big team. It is another reason to be safe and use the stack wisely.
To give modern programming languages their due, we should say that they thought hard about stack usage behind the scenes. In Go, only 2KB of stack space is reserved for their goroutines, and they grow dynamically as the program goes. Goroutines are carefully managed by Go runtime itself to avoid the possible lousy handling of threads in operating systems themselves.
Generation 0
Modern languages are most object-oriented, and they try hard to make everything object, including the strings. So it is hard to abuse their stack with a declaration like this:
char s[1000];
Most local variables do not belong to basic types like int, char, double etc., and they are allocated via the new operator. But this time the heap is abused because the burden of the stack is carried into the there. Since the heap is dynamic, to allocate and deallocate space are expensive operations. This is primarily a big problem in the early stages of the evolution of modern programming language runtimes.
The solution is found in a technique called generational garbage collection. When an object is created, it is stored in a stack-like memory space called generation 0. If the object's life-span is limited to the creator method, it is cheaply killed in there just like rewinding the stack frame. In reality, most object instances live and die this way.
To summarize, In practice, modern languages have a separate stack called "Generation 0" in .NET, "Eden" in Java, "youngest generation" in Python and so on...
0 notes