#Anonymous Internet Browsing Experience
Explore tagged Tumblr posts
Text
Choosing the Right VPN Service: Key Features and Considerations
In an era where online privacy and security are paramount, selecting the right VPN (Virtual Private Network) service is crucial. With countless options available, it’s essential to understand what features to look for and what makes a VPN service reliable and effective. Here’s a comprehensive guide on how to choose a VPN service and the key elements a good VPN should offer. Security…

View On WordPress
#A#Access#Affordable Pricing Plans#Anonymity#Anonymous Browsing#Anonymous Internet Browsing Experience#Anonymous Web Browsing#Compatibility#Competitive and Transparent Pricing#Comprehensive Privacy Protection Features#Cross-Platform Compatibility#Customer Support#Data Protection#Encryption#Extensive Global Server Network#Global Server Network#High Speed#High-Speed Connection Options#High-Speed Connections#Internet Security#Intuitive User-Friendly Interface#Multi-Device Compatibility#No-Logs Policy#Privacy#Privacy and Security#Privacy Policy#reliability#Reliable Customer Support#Reliable Service#Responsive Customer Support Services
0 notes
Text
i had a terrible, awful, bad day yesterday (I mean. two days ago, since it's already after midnight here). I'm not sure if I even should share details, but let's just say being (partially) responsible for evacuating almost 700 people definitely wasn't on my bucket list for that day
and it is mentally taxing, I still feel like the stress of it all didn't fully leave my body. and I have to go to work tomorrow (I mean. today. since it's already after midnight) and everyone knows what happened and to whom and I know they're all just curious but I'm not sure if I'm mentally capable of answering all their questions. I DIDN'T SIGN UP FOR BEING A MINOR CELEBRITY AT MY JOB I SIGNED UP SO I COULD BE NICE TO PEOPLE AND SOMETIMES SLEEP AT WORK
#i would write down specifically what happened but#let's just say i like to be somewhat anonymous on the internet#+ it was literally something that never happened before. not just to me but to ANYONE#(not like. never ever)#(but not in this city. not to people that work where i do. not on that scale.)#and if I write about it too openly#my employers potentially could figure out my identity#i doubt they browse tumblr but if they do then they WILL know who I am#and since the employers & the bosses (& the way company handled this case) are part of the reason the day was fucking awful-....#yea i dont wanna them to read it#i like my job and i'd like to keep it. and i'm alredy on thin ice#but now im just. so tired guys#so tired and YET im proud of myself.#of the way i handled it. of all things i did. people literally thanked ME for it????#i know that better than me would fail in my position.#this is a valuable experience#not just for me but for the entire company#so the empoyers should fucking APOLOGIZE to me and utilize my experience for something better. for their own good lol#dont mess with me i have the power of rage and labour unions on my side#personal#ramblings
0 notes
Text
ONİONSİTES - DRAGON+ (2)

Onion sites, also known as.onion sites, are a unique type of website that can only be accessed through the Tor network. The Tor network, short for The Onion Router, provides a layer of anonymity and encryption for users accessing these sites, making them popular for those seeking privacy and security online. Unlike traditional websites that can be accessed through standard web browsers, onion sites list require special software, such as the Tor browser, to navigate. Individuals can create onion versions of regular websites or develop standalone onion sites for specific purposes. The exclusivity and privacy features of onion sites contribute to their appeal for various users, ranging from privacy advocates to individuals navigating the dark web for specific content.
There are several reasons why individuals choose to use onion sites, with privacy and anonymity being at the forefront. Onion sites offer a level of confidentiality that is not typically found on the surface web, making them attractive to individuals seeking to protect their identity and browsing habits. Moreover, best onion sites can provide access to content that may be restricted or censored in certain regions, allowing users to circumvent such limitations and access information freely. The encrypted nature of the Tor network adds an additional layer of security, reducing the risk of surveillance and tracking by third parties, including governments and internet service providers.
Common types of content found on onion sites range from forums and marketplaces to news outlets and secure communication platforms. While exploring onion sites, individuals may come across forums, chat rooms, file-sharing platforms, and other interactive spaces that facilitate communication and information exchange in a secure environment. The anonymity and encryption offered 2024 onion sites contribute to a unique online experience, enabling users to engage with content and communities that may not be easily accessible through conventional web browsers.
1K notes
·
View notes
Text
Employees at the Social Security Administration (SSA) were informed on Thursday morning that new rules forbid them from accessing “general news” websites, including those that have been at the forefront of the reporting on Elon Musk’s so-called Department of Government Efficiency (DOGE) effort.
In an email reviewed by WIRED and addressed to “all SSA employees” from a mailing list called “internal communications,” the agency informed employees that it was “implementing additional restrictions to the categories of websites prohibited from government-furnished equipment. Effective today, March 6, 2025, the categories include: Online shopping; General News; and Sports.” The headline read “Internet Browsing from Government Equipment.”
The email did not specify which websites in particular were to be blocked. However, WIRED has confirmed with two sources inside the SSA that Wired.com is no longer accessible today, though it was accessible previously.
The sources also confirmed that the websites of The Washington Post, The New York Times, and MSNBC were inaccessible. However, the sources were able to access other news websites including Politico and Axios.
“Local news blocked,” says one source at SSA, who was granted anonymity over fears of retribution. “So if there was a local shooting or something, I wouldn’t be able to see.”
It’s unclear who has implemented the block list or what criteria were used to populate it, but it appears not to be based on ideological grounds, as Fox News and Breitbart are also blocked.
On Friday, weeks after DOGE engineers were installed at SSA, the agency announced plans to cut 7,000 employees. Many of the agency’s most senior staff have resigned. This includes former SSA commissioner Michelle King, who has decades of experience within the agency. She was replaced by acting commissioner Leland Dudek, a mid-level staffer who claimed in a LinkedIn post, reviewed by WIRED, that he had been punished by King for helping DOGE engineers when they first arrived. Musk and Donald Trump have also continued to push the conspiracy theory that millions of dead people are continuing to collect social security benefits, despite the fact those claims have been debunked.
In the hours after the initial email was sent about blocking news sites, some employees received another email from their managers providing instructions on how to disable news showing up on the Edge landing page. This was not a requirement but a recommendation to help employees resist the temptation to click on news links, a source who had received the email told WIRED.
Those trying to visit Wired.com were greeted with a page replicating much of what was in the initial email. It also listed a “URL Reputiation” score, though it was unclear where that score was being sourced from, or if it has a bearing on site access. Different blocked news websites were given different scores, according to screenshots viewed by WIRED.
SSA employees typically use computers with Microsoft’s Edge installed as the internet browser. The default landing page on that browser is set to show news headlines, according to several sources at SSA.
“Employees with a legitimate business [sic] should submit an exception SAM request for their supervisor's review,” the email continued. “These additional restrictions will help reduce risk and better protect the sensitive information entrusted to us in our many systems.”
On Reddit, multiple members of the FedNews subreddit who said they worked at the SSA claimed that accessing news in a timely manner was an essential part of their job. Others pointed out that being able to make purchases online was a core component of their work.
After this article was published, an SSA spokesperson told WIRED that it implemented the restrictions because “employees should be focused on mission-critical work and serving the American people.”
It did not respond to requests for comment on why some news websites were blocked and others were not.
Employees at several other US government agencies contacted by WIRED said similar blocks on news pages had not been implemented on their networks.
43 notes
·
View notes
Text
So...you're questioning if you are aromantic and/or asexual...
...and you don't know where to start.
Well, here! This is my compilation of all the things that helped me figure myself out. I would adore it if other arospec and/or acespec individuals added on as well.
Resources/Research:
1. Forums
Being able to talk to people about my experiences was really helpful and validating. Being able to see other people's experiences that were similar to mine was also so helpful.
For asexuality, there's AVEN. There's a specific section for questioning people as well. For that section, I recommend only posting, not reading other people's posts. There's also this FAQ section with a ton of helpful information about asexuality in general. Overall, I suggest browsing the site, and posting any questions you have.
(small disclaimer: in my time there, I found AVEN to be pretty unfriendly to aromantic people. I have it on good authority that the problem has been solved, but I want to be honest that my personal experience wasn't all sunshine and rainbows)
For aromanticism, there's Arocalypse. It's a smaller forum than AVEN, but also supportive and helpful. There's an Anonymous Q&A section, where you can post without an account, as well as a Discussion section where you can learn more about aromanticism. There's also a non-forum FAQ, with additional resources linked at the top. Similarly to AVEN, stay off the posts of other questioning people, browse the site, and post any questions you have.
If neither of those work for you, I recommend Reddit, but only as a last resort. The moderation there can be interesting, and there's a lot of in-fighting. But, in my opinion, it's important to have that space if you need it.
2. Videos
Seeing people talk about being asexual/aromantic is really helpful for solidifying that they are real things for real people, not just concepts on the internet. They also provide the information in a more streamlined way than forums do.
My number one recommendation for this is Ash Hardell's series on asexuality and aromanticism. There's 3 parts (One Two Three). There's a ton of good information there, presented by asexual and aromantic people.
My second recommendation is to just go to Youtube and look up "am I asexual" or "am I aromantic". This will pull up a lot of videos of people talking through their own experiences.
3. Articles
If you want to read about asexuality and/or aromanticism, it's better to use the forums. Articles about us are often outdated or include incorrect information. Similarly, the forums are awful at giving information about what sexual and/or romantic attraction is.
That's what articles are more useful for. There's a ton out there describing the experience of sexual and romantic attraction, as well as the development of it in humans. That's very helpful for figuring out if you actually feel it or not.
When looking stuff up about sexual/romantic attraction, make sure you use sources you can trust. Sexual attraction is an area where pseudoscience thrives. If you don't know the source, this site is great for checking if it is factual and unbiased.
Non-Research Stuff To Do:
1. Write down your thoughts
One of the issues I ran into while questioning is that I would figure something out, then a few weeks later, doubt myself on that. So I started writing stuff down. This both helps you remember stuff, and verifies that it happened.
2. Just try out the label(s)
Just use them. It doesn't hurt anybody, and you can always stop. You can use the umbrella terms acespec and/or arospec, or just use aromantic and/or asexual (which also function as umbrella terms). This will give you a feel for if the label is right for you. Remember, it's okay to be wrong.
3. Seek out positivity
Go find asexual and/or aromantic people who celebrate being asexual and aromantic. It's helpful in feeling comfortable enough to use the label(s).
What Not To Do:
1. Do not read other questioning people's stuff
This isn't helpful, just confusing. Trust me. Read it after you have yourself figured out.
2. Do not go through the microlabels
Going through microlabels is helpful once you know you are acespec and/or arospec. Not before. Put the queer wiki down. It won't save you.
3. Do not go into spaces that focus on issues
This also isn't helpful, just upsetting. These spaces are helpful for people who are confident in their identities. Not for people questioning.
Other:
Go through the notes! Hopefully, people have added stuff!
134 notes
·
View notes
Text
* “Photos” includes photographs and any form of art (be it traditional or digital).
This poll was submitted to us and we simply posted it so people could vote and discuss their opinions on the matter. If you’d like for us to ask the internet a question for you, feel free to drop the poll of your choice in our inbox and we’ll post them anonymously (for more info, please check our pinned post).
#poll#polls#pinterest#incognito polls#poll time#random polls#fun polls#tumblr polls#tumblr poll#aesthetic
21 notes
·
View notes
Text
Yunyun Syndrome!? Rhythm Psychosis launches October 30 - Gematsu

Rhythm adventure game Yunyun Syndrome!? Rhythm Psychosis will launch for PC via Steam on October 30, publisher and developer WSS playground, publisher Alliance Arts, and developer WHO YOU announced.
Here is an overview of the game, via its Steam page:
About
Yunyun Syndrome!? Rhythm Psychosis is a rhythm adventure game about a psychotic hikikomori girl—also an avid anonymous poster—who corrupts the world with her severe brain rot from listening to too many denpa songs. Yunyun all over this ♡♡♡♡ world with your degen otaku-posting. High and vibin’ with denpa songs, we’ll corrupt the entire Internet! Hehe. all we need is a bit of otaku love, that’s all. This is a rhythm-adventure game where you play as a hikikomori (shut-in) girl who’s high on denpa songs. Become Yunyun-brained and lose all self-control to anonymously post on social media and destroy the world with your Yunyun brain rot. Have a Doki-Doki experience with over 30 denpa songs and multiple endings.
Q. Why did she become a hikikomori?
Q. How does anonymous online posting lead to world destruction?
Q. Does a happy ending exist for a degenerate otaku?
The answers to those “Q’s” lie at the convergence of insanity and denpa psychosis. Now, put those headphones on and become ill with Yunyun Syndrome!? Rhythm Psychosis.
Groove to the DENPA!
Anonymously Post Online and Infect the Whole World with Yunyun-Brain! – Get high on denpa songs and sink in the depths of social media!! Browse social media at the start of the song to check up on your Yunyun cult and haters. And then prepare for the climax where you can start dropping posts left and right. Successfully posting will cause other social media users to become psychotically Yunyun-ified. Social media is all about sharing – spread your heartful psychosis to everyone else!
Characters
Qtie – The main character. A hikikomori. She suffered too much irl that she’s become a little (very) fuzzy in the head. Her obsessive love for the fictional character “Yunyun” is for sure an illness. Her overly “high” state from overdosing denpa songs causes her to propagate Yunyun love. Will there really be a happy end for such a degenerate otaku?
Yunyun – A fictional character that loves Qtie. A very much angelic devil. She will speak to Qtie through the monitor screen. Whilst the truth is unknown, most likely, she is just a figment of Qtie’s imagination. It’s joever for her.
About Denpa Songs! “Denpa” is a genre of music that is intentionally strange and catchy. All playable songs in this game are denpa songs. Many popular denpa songs such as “it’s a cherry kissing explosion” (Sakuranbo Kiss) and many more are featured!
Watch a new trailer below.
Release Date Trailer
English
youtube
Japanese
youtube
Korean
youtube
Traditional Chinese
youtube
Simplified Chinese
youtube
#Yunyun Syndrome!? Rhythm Psychosis#Yunyun Syndrome#WHO YOU#WSS playground#Aliance Arts#Rhythm game#adventure game#Gematsu
5 notes
·
View notes
Text
does hughes net offer a vpn for router
does hughes net offer a vpn for router
HughesNet VPN Router Compatibility
Title: Ensuring HughesNet VPN Router Compatibility: What You Need to Know
In today's digitally interconnected world, safeguarding your online activities is paramount. Virtual Private Networks (VPNs) serve as a vital tool in protecting your internet privacy and security. However, for individuals utilizing HughesNet satellite internet services, ensuring VPN router compatibility is essential for seamless integration and optimal performance.
HughesNet, known for its reliable satellite internet connectivity, offers users high-speed internet access in areas where traditional cable or DSL services may be unavailable. While HughesNet's satellite internet service operates differently from terrestrial broadband connections, it is still compatible with VPN routers.
When selecting a VPN router to use with HughesNet, it's crucial to consider certain factors to ensure compatibility and performance. Firstly, opt for a VPN router that supports satellite internet technology and is compatible with HughesNet's network infrastructure. This compatibility ensures smooth data transmission and minimal latency, maintaining your internet speed and reliability.
Additionally, prioritize VPN routers with robust security features and encryption protocols to fortify your online privacy and protect sensitive information from potential cyber threats. Features such as firewall protection, intrusion detection, and VPN passthrough capabilities enhance the overall security of your internet connection.
Moreover, verify that the VPN router is compatible with your specific HughesNet modem model to avoid any compatibility issues or connectivity disruptions. Consult the manufacturer's specifications or contact HughesNet customer support for guidance on compatible VPN router options.
By selecting a VPN router that is compatible with HughesNet satellite internet services, you can enjoy the benefits of enhanced online security and privacy without sacrificing internet performance. Prioritize compatibility, security features, and reliable connectivity when choosing a VPN router for your HughesNet internet connection. With the right VPN router in place, you can navigate the digital landscape with confidence and peace of mind.
HughesNet VPN Service Availability
Title: Exploring HughesNet VPN Service Availability: What Users Need to Know
In today's digital age, where online privacy and security are paramount concerns, Virtual Private Networks (VPNs) have become essential tools for internet users. They encrypt internet traffic, ensuring confidentiality and anonymity while browsing. However, for those relying on satellite internet services like HughesNet, questions often arise about VPN compatibility and performance.
HughesNet, a leading provider of satellite internet services, offers internet access to users in rural and remote areas where traditional broadband options may be limited. While HughesNet provides reliable internet connectivity, some users wonder about the compatibility of VPNs with satellite internet and whether HughesNet supports VPN usage.
The good news is that HughesNet does support VPN usage. Users can connect to VPN services to enhance their online security and privacy, just like with any other internet service provider. Whether for personal use, business needs, or accessing geo-restricted content, HughesNet users can enjoy the benefits of VPN technology.
However, it's essential to consider some factors that may affect VPN performance over satellite internet. Due to the inherent latency and occasional network congestion associated with satellite connections, users may experience slower VPN speeds compared to terrestrial broadband. Additionally, data caps and Fair Access Policy (FAP) limits imposed by HughesNet may impact VPN usage, particularly for activities requiring large amounts of data.
Despite these potential limitations, many HughesNet users find VPNs to be valuable tools for safeguarding their online activities. By encrypting data transmissions and masking IP addresses, VPNs help mitigate security risks and preserve privacy, even over satellite internet connections.
In conclusion, HughesNet users can take advantage of VPN services to enhance their online security and privacy. While some performance considerations exist, the compatibility of VPNs with HughesNet enables users to enjoy the benefits of secure and anonymous browsing, regardless of their location.
HughesNet VPN Router Integration
Title: Seamless Integration: HughesNet VPN Router Enhances Connectivity
In today's digital landscape, ensuring secure and reliable connectivity is paramount, especially for users of satellite internet services like HughesNet. With the increasing emphasis on online privacy and data security, integrating a Virtual Private Network (VPN) with your HughesNet router can offer enhanced protection and flexibility for internet usage.
HughesNet, known for its high-speed satellite internet solutions, recognizes the importance of safeguarding users' online activities. By incorporating a VPN router into the HughesNet network setup, users can encrypt their internet traffic, shielding it from prying eyes and potential cyber threats.
One of the primary advantages of integrating a VPN router with HughesNet is the ability to establish a secure connection regardless of the user's location. Whether accessing the internet from the comfort of home or on the go, users can enjoy peace of mind knowing that their data is encrypted and their privacy is preserved.
Moreover, the integration of a VPN router can help bypass certain restrictions imposed by internet service providers (ISPs) or geographical limitations on content access. This means HughesNet users can enjoy unrestricted access to online content, services, and streaming platforms, regardless of their physical location.
Another benefit of HughesNet VPN router integration is the added layer of security it provides for sensitive online transactions, such as online banking or shopping. With encryption protocols in place, users can conduct financial transactions with confidence, minimizing the risk of unauthorized access to their personal information.
In conclusion, the integration of a VPN router with HughesNet offers users a comprehensive solution for enhancing online security, privacy, and flexibility. By encrypting internet traffic and circumventing restrictions, users can enjoy a seamless online experience while safeguarding their digital footprint.
HughesNet VPN Subscription Options
Title: Exploring HughesNet VPN Subscription Options
In today's interconnected world, online security and privacy are paramount concerns for internet users. HughesNet, a leading provider of satellite internet services, recognizes the importance of protecting its customers' data. To address this need, HughesNet offers VPN (Virtual Private Network) subscription options to enhance online security and privacy for its users.
A VPN encrypts internet traffic, routing it through a secure server, thus shielding sensitive information from potential threats such as hackers, identity thieves, and data snoopers. HughesNet understands the value of safeguarding its users' online activities, especially in remote or underserved areas where internet access may be limited.
HughesNet VPN subscription options cater to varying needs and preferences. Whether users require basic protection for casual browsing or advanced features for business use, HughesNet offers flexible plans to suit diverse requirements. Users can choose from monthly or yearly subscription plans, depending on their usage frequency and budget constraints.
One of the key advantages of opting for HughesNet VPN is its seamless integration with HughesNet's satellite internet services. Subscribers can enjoy uninterrupted internet connectivity while benefiting from enhanced security features offered by the VPN.
Moreover, HughesNet VPN boasts a user-friendly interface and reliable customer support, ensuring a hassle-free experience for users seeking assistance or troubleshooting guidance.
In conclusion, HughesNet VPN subscription options empower users to take control of their online security and privacy. By encrypting internet traffic and shielding sensitive information from prying eyes, HughesNet VPN offers peace of mind in an increasingly digitized world. Whether for personal or business use, HughesNet VPN provides a comprehensive solution for safeguarding online activities and data.
HughesNet VPN Router Setup Instructions
Title: Easy Steps for HughesNet VPN Router Setup
In today's digital age, ensuring your online security and privacy is paramount. One effective way to achieve this is by setting up a VPN (Virtual Private Network) router, especially if you're using HughesNet satellite internet service. By encrypting your internet connection, a VPN router protects your data from prying eyes and enhances your online anonymity.
Here's a comprehensive guide on how to set up a VPN router with your HughesNet internet connection:
Choose a Compatible VPN Router: Before diving into the setup process, make sure you have a VPN-compatible router. Not all routers support VPN configurations, so it's essential to check compatibility beforehand.
Access Router Settings: Connect your computer to the router either via Wi-Fi or Ethernet cable. Open a web browser and enter the router's IP address in the address bar. Typically, the default IP address is 192.168.1.1 or 192.168.0.1. Log in using the router's admin credentials.
Install VPN Firmware: If your router doesn't come pre-installed with VPN firmware, you'll need to flash it with compatible firmware. Follow the manufacturer's instructions to download and install the VPN firmware onto your router.
Configure VPN Settings: Once the firmware is installed, navigate to the router's VPN settings. Enter the VPN server details provided by your VPN service provider, including the server address, username, and password.
Enable VPN Connection: After entering the VPN details, save the settings and enable the VPN connection on your router. This will establish a secure connection between your devices and the VPN server.
Test the Connection: Once the VPN is set up, it's crucial to test the connection to ensure everything is working correctly. Visit a website like whatismyip.com to verify that your IP address has changed to the VPN server's IP.
Enjoy Secure Browsing: With the VPN router successfully configured, you can now enjoy secure and private browsing sessions without worrying about potential threats or data breaches.
By following these steps, you can set up a VPN router with your HughesNet internet service and enjoy enhanced online security and privacy.
2 notes
·
View notes
Text
The Ultimate Guide to Choosing the Perfect VPN
In an era where online privacy and security have become paramount, choosing the right Virtual Private Network (VPN) is a crucial decision. With countless options available, finding the perfect VPN can be a daunting task. This comprehensive guide aims to simplify the process and help you make an informed choice.
Define Your Needs: Begin by identifying your primary reasons for using a VPN. Are you seeking enhanced security, anonymous browsing, or access to geo-restricted content? Your goals will shape the features you prioritize in a VPN.
No-Logs Policy: Opt for a VPN provider that strictly follows a no-logs policy. This ensures that your online activities remain confidential and aren't stored on the provider's servers.
Server Locations: Consider the VPN's server network. The more extensive and diverse the server locations, the better your access to geo-restricted content from around the world.
Speed and Performance: Some VPNs can slow down your internet speed. Choose a VPN with high-speed servers to ensure smooth streaming, gaming, and browsing experiences.

Compatibility: Ensure the VPN is compatible with all your devices – from desktops and laptops to smartphones and tablets. Look for multi-device support to secure all your gadgets with a single subscription.
User-Friendly Interface: A user-friendly interface makes setup and usage hassle-free. Intuitive apps and easy-to-navigate settings contribute to a positive VPN experience.
Customer Support: Responsive customer support is invaluable, especially if you encounter technical issues. 24/7 live chat, email, and comprehensive online resources can be a lifesaver.
Free vs. Paid: While free VPNs exist, they often come with limitations on data usage, slower speeds, and potential privacy concerns. Consider investing in a paid VPN for a premium experience.
Trial Periods and Money-Back Guarantees: Reputable VPN providers offer trial periods or money-back guarantees. These allow you to test the VPN's features and performance risk-free before committing.
Reputation and Reviews: Research online reviews and user feedback to gauge the reputation and reliability of the VPN provider. Positive testimonials can provide valuable insights.
Pricing Plans: Compare pricing plans and subscription options. Some providers offer different tiers with varying features, so choose the one that aligns with your needs and budget.
Additional Features: Some VPNs offer additional features such as ad-blocking, malware protection, and split tunneling. Evaluate whether these extras align with your requirements.
Privacy Jurisdiction: Research the VPN provider's jurisdiction – where they are legally based. Opt for a provider located in a privacy-friendly jurisdiction to ensure your data is protected.
Regular Audits and Transparency: Choose a VPN provider that undergoes third-party security audits and is transparent about its practices. This adds an extra layer of trustworthiness.
In conclusion, selecting the ideal VPN involves careful consideration of your needs, preferences, and priorities. By evaluating security features, performance, compatibility, and more, you can find a VPN that seamlessly integrates into your online life while providing the privacy and security you deserve. Check here to know more about vpn.
7 notes
·
View notes
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
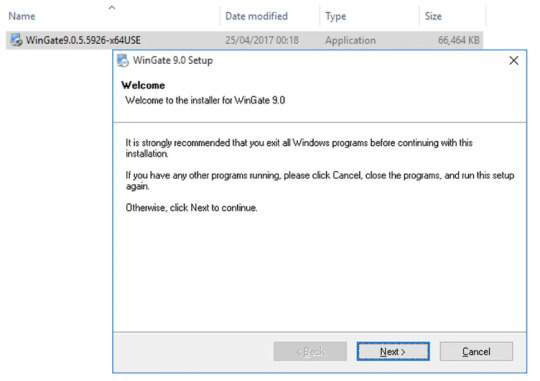
Get 1GB Proxy Free Trial of Residential Proxies Now!
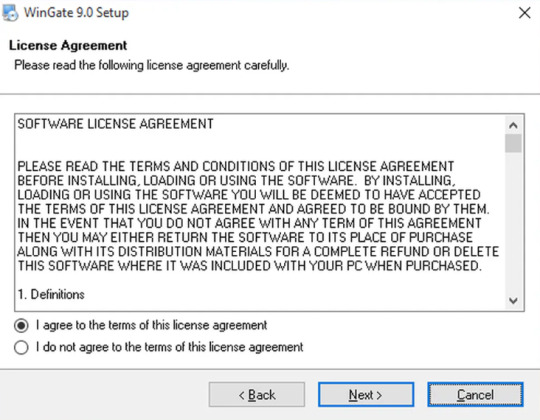
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
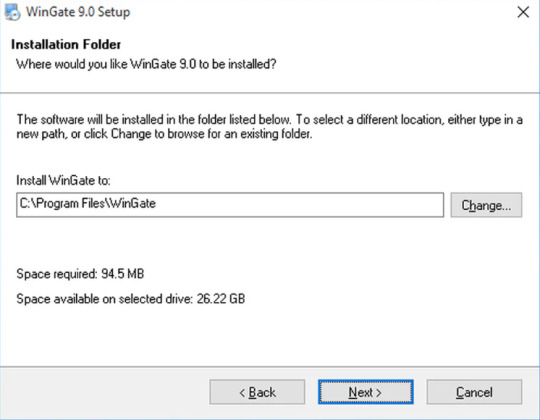
Step 3 Installation Folder
Choose the location on your system, where you like to place the WinGate installation setup.
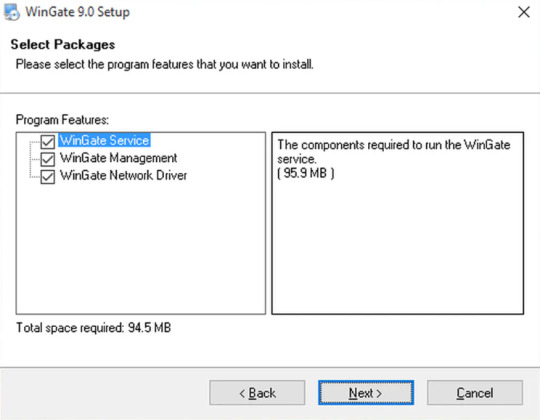
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
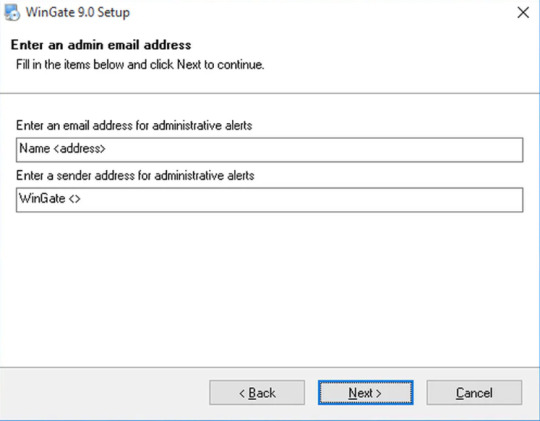
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
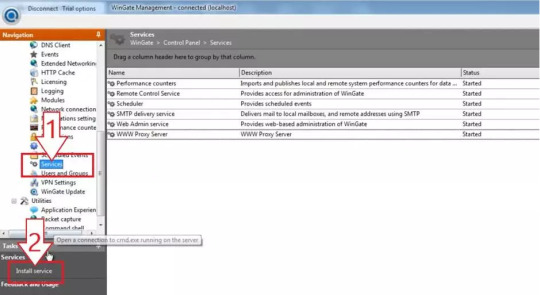
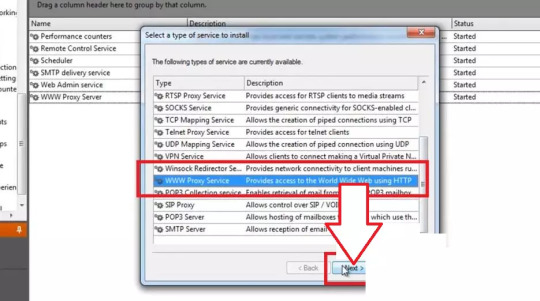
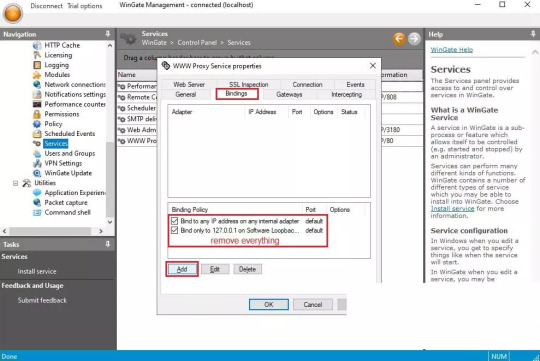
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
3. Now, go to the Connection tab. Check the box next to “Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
The Power and Perks of VPNs in the Chrome Web Store

Introduction:
In an era dominated by digital connectivity and online interactions, ensuring our privacy and security while browsing the web has become paramount. One indispensable tool that has gained significant popularity in this regard is the Virtual Private Network (VPN). Among the myriad of VPN options available, the Chrome Web Store stands out as a convenient hub for users seeking reliable VPN services seamlessly integrated into their browsing experience.
Understanding VPNs:
Before delving into the world of VPNs available on the Chrome Web Store, it’s essential to grasp the fundamental concept of a Virtual Private Network. At its core, a VPN is a technology that establishes a secure and encrypted connection over the internet, allowing users to transmit data privately and securely. This encryption not only safeguards sensitive information but also masks the user’s IP address, providing anonymity and preventing unauthorized access to personal data.
Read More:-
2 notes
·
View notes
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Text
Protect Your Digital Life with Norton Antivirus: Complete Security for Every Device
In an age where cyber threats are more sophisticated than ever, having robust digital protection is no longer optional—it’s essential. Norton Antivirus stands out as a trusted and comprehensive security solution, helping individuals and families stay safe from viruses, malware, ransomware, and online fraud. If you're looking for top-tier protection, the Norton 360 Premium package available on OmniSoft is the ideal choice.
What Is Norton Antivirus?
Norton Antivirus is a globally recognized cybersecurity software developed to provide real-time protection against a wide range of online threats. With over three decades of experience, Norton has continuously evolved to offer intelligent, proactive defense systems that protect your privacy, personal information, and devices from digital dangers.
Key Features of Norton 360 Premium
The Norton 360 Premium edition is more than just antivirus software—it’s an all-in-one digital protection suite. Here are some of the standout features:
Comprehensive Antivirus Protection: Detects and removes viruses, spyware, malware, and ransomware.
Multi-Device Coverage: Safeguard up to 10 devices including Windows, Mac, Android, and iOS.
75 GB Cloud Backup: Keep your important files secure in the cloud to prevent data loss due to ransomware or hard drive failure.
Firewall for PC and Mac: Adds an additional layer of security to block unauthorized access to your private data.
Password Manager: Securely stores and manages your passwords, credit card information, and other credentials.
Parental Control: Help your kids safely explore the internet by monitoring online activity and limiting access to inappropriate content.
Secure VPN: Browse anonymously and securely even on public Wi-Fi with an integrated virtual private network.
Why Choose Norton from OmniSoft?
OmniSoft is a trusted digital software provider offering licensed and affordable security solutions. When you purchase Norton Antivirus 360 Premium from OmniSoft, you benefit from:
Immediate digital delivery
One-year full protection
Romanian customer support
Reliable and secure payment methods
Who Needs Norton Antivirus?
Whether you're a student, a remote worker, a business professional, or managing a household, you likely rely on multiple devices daily. Cybercriminals target everyone—from casual browsers to corporate executives. Norton 360 Premium provides peace of mind, knowing your data, identity, and online activity are protected around the clock.
Final Thoughts
Don’t leave your digital life vulnerable. With cyber threats growing each day, investing in powerful and reliable protection like Norton Antivirus is a smart and necessary step. Secure your online world today with Norton 360 Premium from OmniSoft—because your privacy, files, and peace of mind are worth it.
For more info visit here:- total security
1 note
·
View note
Text
The Key Reasons Why More People Pick Short-lived Numbers to Receive SMS Online?

Privacy has ended up being a top priority for users browsing the digital world. With data violations, spam, and unapproved tracking increasing, many are seeking much safer methods to communicate with on the internet platforms. One solution that's acquiring momentum is the capacity to receive SMS online without making use of personal numbers. This expanding trend equips individuals to stay secure while still getting the job done - whether it's verifying a social account or testing software functions.
Digital Personal Privacy Needs Safer Interaction
Users are becoming extra mindful regarding where and how they share their phone numbers. Sending a number during sign-ups or application tests typically results in unrelenting marketing messages or, even worse, exposure in a data leak. That's where the ability to receive SMS online United States steps in. It offers users an option to using their personal number, supplying comfort and freedom from unsolicited messages. For individuals in the United States, Canada, India, and the UK, this approach gives neighborhood choices, consisting of receive SMS online United States, receive SMS online Indian, and free SMS receive UK, providing a secure way to engage online.
Equipping Developers and Testers
Software application developers and application testers are major adopters of services that let you receive SMS online. These specialists commonly need to examine OTP flows, confirm verification processes, or mimic various customer situations. Using their personal number would certainly not just mess their inbox however additionally increase protection problems. With platforms like online-sms.org, they can rapidly choose from a range of worldwide numbers, including free receive SMS Canada or free SMS receive UK, and view messages promptly. This conserves time and makes sure reliability during crucial screening stages without breaching individual privacy.
Hassle-free International Accessibility for Everybody

The ability to receive SMS online is no longer just a tool for developers. Day-to-day individuals from across the globe now rely upon it to bypass OTP confirmations, gain access to limited content, or join anonymously on sites. Whether you're located in The United States and Canada, making use of receive SMS online United States, or in South Asia with receive SMS online Indian, you'll locate it easier than ever to obtain temporary numbers that work. Services like online-sms.org have actually helped democratize gain access to by supplying international numbers, providing everybody an opportunity to safeguard their personal privacy. The very best part? The majority of platforms allow send out and SMS capabilities without also needing to register.
Sustaining a Secure and Spam-Free Digital Experience
Beyond convenience, using short-term contact number likewise helps in reducing spam and stopping fraudulent schemes. By utilizing alternatives like free receive SMS Canada or free SMS receive UK, users can evade suspicious web sites that collect and misuse get in touch with information. Instead of becoming a target for fraudsters or advertisers, they continue to be anonymous while finishing verification or test processes. The filtering systems utilized by platforms such as online-sms.org ensure that sensitive information is not misused, keeping individual trust high. This adds to a cleaner and a lot more considerate digital atmosphere where interaction continues to be purposeful and protected.
Verdict
The growing popularity of services that let users receive SMS online mirrors a change in how people value their personal privacy. From developers examining OTP systems to informal users staying clear of spam, this technique uses an effective and confidential option to typical number sharing. Thanks to safeguard and simple platforms like online-sms.org, worldwide individuals - from the USA to India - can now take care of verifications without putting their individual information at risk.
0 notes
Text
CroxyProxy YouTube: Unlocking Unrestricted Access to Your Favorite Videos

In today’s digital age, video content is king. YouTube, being the largest video-sharing platform, is the go-to source for tutorials, music, entertainment, news, and more. However, many users face restrictions when trying to access YouTube videos—whether it's due to school, workplace firewalls, or regional blocks. That’s where CroxyProxy YouTube steps in as a game-changer.
What is CroxyProxy?
CroxyProxy is a free and secure web proxy service that allows users to access blocked websites, including YouTube. Unlike traditional VPNs or complicated software, CroxyProxy is simple to use. Just head to the official CroxyProxy website, enter the URL of the video you want to watch, and you’re good to go—no downloads, no installations.
Why Use CroxyProxy for YouTube?
The biggest advantage of using CroxyProxy is its ability to bypass restrictions without compromising your privacy. It masks your IP address, keeps your browsing anonymous, and works seamlessly on almost any device or browser. Whether you're trying to watch a documentary at school, a music video at work, or a region-blocked vlog, CroxyProxy provides a smooth and secure streaming experience.
Final Thoughts
Don’t let internet restrictions limit your access to information and entertainment. CroxyProxy YouTube opens the doors to a free internet, giving you the ability to enjoy your favorite videos anytime, anywhere. It’s fast, reliable, and totally free—making it the perfect tool for uninterrupted YouTube streaming.
0 notes
Text
Bridging the Gap: The Transformative Journey of Writing to Prison Pen Pals at Writeacon.com
Introduction
In a international more and more divided through walls—each literal and metaphorical—the act of writing to criminal pen acquaintances gifts an excellent alternative for connection, empathy, and transformation. Entering the world of reformatory correspondence using structures like Writeacon.com can experience daunting first and foremost. But when you start this ride, you’ll stumble on it’s not close to reaching out; it’s about bridging gaps among lives that are often worlds aside.
youtube
Why Choose to Write a Prisoner?
Writing to a prisoner is more than simply replacing letters; it’s approximately working out humanity in its so much uncooked model. You may perhaps wonder why all of us would wish to interact with folks who are incarcerated. The truth is, many prisoners lengthy for connection and assist. They are searching for figuring out from the exterior global and in many instances have tales that mirror deep struggles, hopes, and desires.
The Power of Words
Words can heal wounds unseen. For person constrained inside of criminal walls, receiving mail may be a lifeline—a likelihood to experience valued and heard. When you prefer to put in writing a prisoner, you’re supplying them a glimpse into the exterior world at the same time as at the same time enriching your possess life with new perspectives.
What Is Writeacon.com?
Writeacon.com is an internet platform dedicated to connecting participants with prisoners trying pen neighbors. This provider allows significant relationships by using delivering clients with access to profiles of inmates seeking correspondence.
Features of Writeacon.com User-Friendly Interface: Navigating by using the website is seamless. Diverse Profiles: You can find inmates from quite a lot of backgrounds and reports. Safety Measures: Your anonymity is secure except you go with differently. How Does It Work?
Getting all started on Writeacon.com is inconspicuous:

Create an Account: Sign up with uncomplicated info, ensuring your privacy. Browse Profiles: Take some time searching through distinctive inmate profiles. Send Letters: Once you locate somebody wonderful, draft your letter! Bridging the Gap: The Transformative Journey of Writing to Prison Pen Pals at Writeacon.com
The adventure starts offevolved while write a con one takes the soar to achieve out beyond societal norms and expectations—to connect to a existence so various from theirs. Many other folks are hesitant to start with; they could question what they’ll say or how their phrases shall be got.
Overcoming Initial Hesitations
It’s most effective usual to feel anxious prior to writing your first letter. However, this transformative adventure most often ends up in own enlargement in addition aiding others in profound tactics.
What Should I Say?
youtube
Begin with a undeniable creation about yourself.
Share pastimes, spare time activities, or techniques on themes that resonate with you.
How Will They Respond?
Responses may differ; a few can even open up directly at the same time others can also take time.
1 note
·
View note