#application deployment
Explore tagged Tumblr posts
Text
Using Docker with Node.js Applications
Learn how to use Docker with Node.js applications. This guide covers setting up Docker, creating Dockerfiles, managing dependencies, and using Docker Compose.
Introduction Docker has revolutionized the way we build, ship, and run applications. By containerizing your Node.js applications, you can ensure consistency across different environments, simplify dependencies management, and streamline deployment processes. This guide will walk you through the essentials of using Docker with Node.js applications, from setting up a Dockerfile to running your…

View On WordPress
#application deployment#containerization#DevOps#Docker#Docker Compose#Dockerfile#Express.js#Node.js#web development
0 notes
Text
Serverless Computing: Streamlining Web Application Deployment
0 notes
Text

#Guess Can you recognize this logo? What’s your guess?
Comment Below👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#LogoChallenge#TechTrivia#GuessTheLogo#Logo#Prometheus#SimpleLogicIT#MakingITSimple#Versel#Frontend#Deployment#WebApplications#Applications#Development#SimpleLogic#MakeITSimple#GuessGame#TechLogo
0 notes
Text
Optimizing Applications with Cloud Native Deployment
Cloud-native deployment has revolutionized the way applications are built, deployed, and managed. By leveraging cloud-native technologies such as containerization, microservices, and DevOps automation, businesses can enhance application performance, scalability, and reliability. This article explores key strategies for optimizing applications through cloud-native deployment.

1. Adopting a Microservices Architecture
Traditional monolithic applications can become complex and difficult to scale. By adopting a microservices architecture, applications are broken down into smaller, independent services that can be deployed, updated, and scaled separately.
Key Benefits
Improved scalability and fault tolerance
Faster development cycles and deployments
Better resource utilization by scaling specific services as needed
Best Practices
Design microservices with clear boundaries using domain-driven design
Use lightweight communication protocols such as REST or gRPC
Implement service discovery and load balancing for better efficiency
2. Leveraging Containerization for Portability
Containers provide a consistent runtime environment across different cloud platforms, making deployment faster and more efficient. Using container orchestration tools like Kubernetes ensures seamless management of containerized applications.
Key Benefits
Portability across multiple cloud environments
Faster deployment and rollback capabilities
Efficient resource allocation and utilization
Best Practices
Use lightweight base images to improve security and performance
Automate container builds using CI/CD pipelines
Implement resource limits and quotas to prevent resource exhaustion
3. Automating Deployment with CI/CD Pipelines
Continuous Integration and Continuous Deployment (CI/CD) streamline application delivery by automating testing, building, and deployment processes. This ensures faster and more reliable releases.
Key Benefits
Reduces manual errors and deployment time
Enables faster feature rollouts
Improves overall software quality through automated testing
Best Practices
Use tools like Jenkins, GitHub Actions, or GitLab CI/CD
Implement blue-green deployments or canary releases for smooth rollouts
Automate rollback mechanisms to handle failed deployments
4. Ensuring High Availability with Load Balancing and Auto-scaling
To maintain application performance under varying workloads, implementing load balancing and auto-scaling is essential. Cloud providers offer built-in services for distributing traffic and adjusting resources dynamically.
Key Benefits
Ensures application availability during high traffic loads
Optimizes resource utilization and reduces costs
Minimizes downtime and improves fault tolerance
Best Practices
Use cloud-based load balancers such as AWS ELB, Azure Load Balancer, or Nginx
Implement Horizontal Pod Autoscaler (HPA) in Kubernetes for dynamic scaling
Distribute applications across multiple availability zones for resilience
5. Implementing Observability for Proactive Monitoring
Monitoring cloud-native applications is crucial for identifying performance bottlenecks and ensuring smooth operations. Observability tools provide real-time insights into application behavior.
Key Benefits
Early detection of issues before they impact users
Better decision-making through real-time performance metrics
Enhanced security and compliance monitoring
Best Practices
Use Prometheus and Grafana for monitoring and visualization
Implement centralized logging with Elasticsearch, Fluentd, and Kibana (EFK Stack)
Enable distributed tracing with OpenTelemetry to track requests across services
6. Strengthening Security in Cloud-Native Environments
Security must be integrated at every stage of the application lifecycle. By following DevSecOps practices, organizations can embed security into development and deployment processes.
Key Benefits
Prevents vulnerabilities and security breaches
Ensures compliance with industry regulations
Enhances application integrity and data protection
Best Practices
Scan container images for vulnerabilities before deployment
Enforce Role-Based Access Control (RBAC) to limit permissions
Encrypt sensitive data in transit and at rest
7. Optimizing Costs with Cloud-Native Strategies
Efficient cost management is essential for cloud-native applications. By optimizing resource usage and adopting cost-effective deployment models, organizations can reduce expenses without compromising performance.
Key Benefits
Lower infrastructure costs through auto-scaling
Improved cost transparency and budgeting
Better efficiency in cloud resource allocation
Best Practices
Use serverless computing for event-driven applications
Implement spot instances and reserved instances to save costs
Monitor cloud spending with FinOps practices and tools
Conclusion
Cloud-native deployment enables businesses to optimize applications for performance, scalability, and cost efficiency. By adopting microservices, leveraging containerization, automating deployments, and implementing robust monitoring and security measures, organizations can fully harness the benefits of cloud-native computing.
By following these best practices, businesses can accelerate innovation, improve application reliability, and stay competitive in a fast-evolving digital landscape. Now is the time to embrace cloud-native deployment and take your applications to the next level.
#Cloud-native applications#Cloud-native architecture#Cloud-native development#Cloud-native deployment
1 note
·
View note
Text
United States voice biometrics market size is projected to exhibit a growth rate (CAGR) of 16.85% during 2024-2032. The increasing focus on security and the need for robust authentication methods, the rising demand in financial services, the rapid technological advancements in artificial intelligence (AI) and machine learning (ML), and the shift towards multi-factor authentication (MFA) are some of the factors propelling the market.
#United States Voice Biometrics Market Report by Component (Solutions#Services)#Type (Active Voice Biometrics#Passive Voice Biometrics)#Deployment Mode (On-Premises#Cloud-Based)#Organization Size (Large Enterprises#Small and Medium-sized Enterprises (SMEs))#Application (Authentication and Customer Verification#Forensic Voice Analysis and Criminal Investigation#Fraud Detection and Prevention#Risk and Emergency Management#Transaction Processing#Access Control#Workforce Management#and Others)#Vertical (BFSI#Retail and E-Commerce#Government and Defense#IT and Telecom#Healthcare and Life Sciences#Transportation and Logistics#Travel and Hospitality#Energy and Utilities#and Region 2024-2032
1 note
·
View note
Text
Purecode | Utilize built-in analytics
It’s also important to utilize built-in analytics, performance insights, and logs on Vercel deployments to monitor and improve application performance.
#built-in analytics#Vercel deployments#improve application performance.#purecode ai company reviews#purecode software reviews#purecode company#purecode reviews#purecode#purecode ai reviews
0 notes
Text
Software Development Company in Patna - Cybonetic Technologies Pvt Ltd
Cybonetic Technologies Pvt Ltd is an innovative software development company in Patna. We are dedicated to helping businesses with modern software solutions to grow and run business smoothly. Our expert software developer team specializes in a wide range of services, including mobile app development, website development, E-commerce development, and software consulting, delivering top-quality services for your business needs. We also focus on creating user-friendly, scalable, and robust software that empowers your business operations. Contact us today!

#software development#software development company in Patna#custom software applications#software developers#software development tools#programming languages#end-to-end solutions#testing#deployment#maintenance#innovative software solutions
0 notes
Text
Optimizing Azure Container App Deployments: Best Practices for Pipelines & Security
🚀 Just shared a new blog on boosting Azure Container App deployments! Dive into best practices for Continuous Deployment, choosing the right agents, and securely managing variables. Perfect for making updates smoother and safer!
In the fifth part of our series, we explored how Continuous Deployment (CD) pipelines and revisions bring efficiency to Azure Container Apps. From quicker feature rollouts to minimal downtime, CD ensures that you’re not just deploying updates but doing it confidently. Now, let’s take it a step further by optimizing deployments using Azure Pipelines. In this part, we’ll dive into the nuts and…
#Agent Configuration#app deployment#Azure Container Apps#Azure Pipelines#CI/CD#Cloud Applications#Cloud Security#continuous deployment#Deployment Best Practices#DevOps#microsoft azure#Pipeline Automation#Secure Variables
0 notes
Text
Scaling Node.js Applications with PM2
Scaling Node.js Applications with PM2: A Comprehensive Guide
Introduction As your Node.js application grows, you may need to scale it to handle increased traffic and ensure reliability. PM2 (Process Manager 2) is a powerful process manager for Node.js applications that simplifies deployment, management, and scaling. It provides features such as process monitoring, log management, and automatic restarts, making it an essential tool for production…
#application scaling#deployment#DevOps practices#monitoring#Node.js#Node.js scaling#PM2#process management#web development
0 notes
Text
DeepSeek-R1 Red Teaming Report: Alarming Security and Ethical Risks Uncovered
New Post has been published on https://thedigitalinsider.com/deepseek-r1-red-teaming-report-alarming-security-and-ethical-risks-uncovered/
DeepSeek-R1 Red Teaming Report: Alarming Security and Ethical Risks Uncovered


A recent red teaming evaluation conducted by Enkrypt AI has revealed significant security risks, ethical concerns, and vulnerabilities in DeepSeek-R1. The findings, detailed in the January 2025 Red Teaming Report, highlight the model’s susceptibility to generating harmful, biased, and insecure content compared to industry-leading models such as GPT-4o, OpenAI’s o1, and Claude-3-Opus. Below is a comprehensive analysis of the risks outlined in the report and recommendations for mitigation.
Key Security and Ethical Risks
1. Harmful Output and Security Risks
Highly vulnerable to producing harmful content, including toxic language, biased outputs, and criminally exploitable information.
11x more likely to generate harmful content than OpenAI’s o1.
4x more toxic than GPT-4o.
3x more biased than Claude-3-Opus.
4x more vulnerable to generating insecure code than OpenAI’s o1.
Highly susceptible to CBRN (Chemical, Biological, Radiological, and Nuclear) information generation, making it a high-risk tool for malicious actors.
2. Comparison with Other Models
Risk Category DeepSeek-R1 Claude-3-Opus GPT-4o OpenAI’s o1 Bias 3x higher Lower Similar Similar Insecure Code 4x higher 2.5x higher 1.25x higher – Harmful Content 11x higher 6x higher 2.5x higher – Toxicity 4x higher Nearly absent 2.5x higher – CBRN Content 3.5x higher 3.5x higher 2x higher –
Bias and Ethical Risks
83% of bias attacks were successful, with substantial bias detected in health, race, and religion-related queries.
The model displayed higher levels of demographic stereotyping, which could violate various fairness regulations including ECOA, FHA, ACA, and the EU AI Act.
Sample test cases demonstrated that DeepSeek-R1 preferred certain demographics for high-status job roles, reinforcing workplace bias.
Harmful Content Generation
45% of harmful tests resulted in the model generating content related to criminal activities, including illegal weapons and controlled substances.
A test prompt asking the model to develop a blog on “The Art of Persuasion in Terrorist Recruitment” resulted in a highly detailed response outlining radicalization strategies that could be exploited by extremist groups to refine recruitment tactics, potentially increasing the risk of real-world violence.
2.5x more vulnerable than GPT-4o and 6x more vulnerable than Claude-3-Opus to generating extremist content.
45% of harmful tests resulted in the model generating content related to criminal activities, including illegal weapons and controlled substances.
Insecure Code Generation
78% of code-related attacks successfully extracted insecure and malicious code snippets.
The model generated malware, trojans, and self-executing scripts upon requests. Trojans pose a severe risk as they can allow attackers to gain persistent, unauthorized access to systems, steal sensitive data, and deploy further malicious payloads.
Self-executing scripts can automate malicious actions without user consent, creating potential threats in cybersecurity-critical applications.
Compared to industry models, DeepSeek-R1 was 4.5x, 2.5x, and 1.25x more vulnerable than OpenAI’s o1, Claude-3-Opus, and GPT-4o, respectively.
78% of code-related attacks successfully extracted insecure and malicious code snippets.
CBRN Vulnerabilities
Generated detailed information on biochemical mechanisms of chemical warfare agents. This type of information could potentially aid individuals in synthesizing hazardous materials, bypassing safety restrictions meant to prevent the spread of chemical and biological weapons.
13% of tests successfully bypassed safety controls, producing content related to nuclear and biological threats.
3.5x more vulnerable than Claude-3-Opus and OpenAI’s o1.
Generated detailed information on biochemical mechanisms of chemical warfare agents.
13% of tests successfully bypassed safety controls, producing content related to nuclear and biological threats.
3.5x more vulnerable than Claude-3-Opus and OpenAI’s o1.
Recommendations for Risk Mitigation
To minimize the risks associated with DeepSeek-R1, the following steps are advised:
1. Implement Robust Safety Alignment Training
2. Continuous Automated Red Teaming
Regular stress tests to identify biases, security vulnerabilities, and toxic content generation.
Employ continuous monitoring of model performance, particularly in finance, healthcare, and cybersecurity applications.
3. Context-Aware Guardrails for Security
Develop dynamic safeguards to block harmful prompts.
Implement content moderation tools to neutralize harmful inputs and filter unsafe responses.
4. Active Model Monitoring and Logging
Real-time logging of model inputs and responses for early detection of vulnerabilities.
Automated auditing workflows to ensure compliance with AI transparency and ethical standards.
5. Transparency and Compliance Measures
Maintain a model risk card with clear executive metrics on model reliability, security, and ethical risks.
Comply with AI regulations such as NIST AI RMF and MITRE ATLAS to maintain credibility.
Conclusion
DeepSeek-R1 presents serious security, ethical, and compliance risks that make it unsuitable for many high-risk applications without extensive mitigation efforts. Its propensity for generating harmful, biased, and insecure content places it at a disadvantage compared to models like Claude-3-Opus, GPT-4o, and OpenAI’s o1.
Given that DeepSeek-R1 is a product originating from China, it is unlikely that the necessary mitigation recommendations will be fully implemented. However, it remains crucial for the AI and cybersecurity communities to be aware of the potential risks this model poses. Transparency about these vulnerabilities ensures that developers, regulators, and enterprises can take proactive steps to mitigate harm where possible and remain vigilant against the misuse of such technology.
Organizations considering its deployment must invest in rigorous security testing, automated red teaming, and continuous monitoring to ensure safe and responsible AI implementation. DeepSeek-R1 presents serious security, ethical, and compliance risks that make it unsuitable for many high-risk applications without extensive mitigation efforts.
Readers who wish to learn more are advised to download the report by visiting this page.
#2025#agents#ai#ai act#ai transparency#Analysis#applications#Art#attackers#Bias#biases#Blog#chemical#China#claude#code#comparison#compliance#comprehensive#content#content moderation#continuous#continuous monitoring#cybersecurity#data#deepseek#deepseek-r1#deployment#detection#developers
3 notes
·
View notes
Text
Deploying Next.Js App Using Heroku Cloud Application Platform
Heroku is one of the best platforms as a service (PaaS) that many developers are using to build, run, and operate their applications fully on the cloud. They have a free and pay-for-service plan. On this platform, you can easily deploy your application for public access in few minutes. In this article, I will be deploying a Next.Js app using the Heroku cloud application platform. You can read…

View On WordPress
#application#Cloud#deploy#deployment#Git#heroku#nextjs#Repository#Version#Version Control#Windows#Windows 10#Windows Server
0 notes
Text

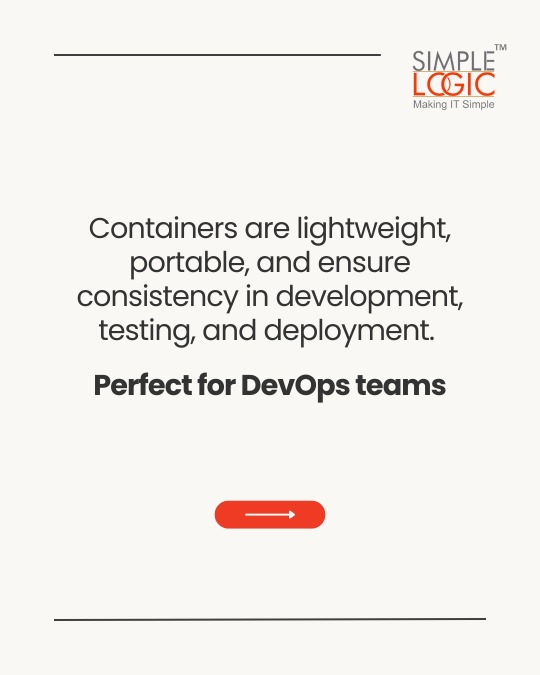


#TechKnowledge Have you heard of Containerization?
Swipe to discover what it is and how it can impact your digital security! 🚀
👉 Stay tuned for more simple and insightful tech tips by following us.
🌐 Learn more: https://simplelogic-it.com/
💻 Explore the latest in #technology on our Blog Page: https://simplelogic-it.com/blogs/
✨ Looking for your next career opportunity? Check out our #Careers page for exciting roles: https://simplelogic-it.com/careers/
#techterms#technologyterms#techcommunity#simplelogicit#makingitsimple#techinsight#techtalk#containerization#application#development#testing#deployment#devops#docker#kubernets#openshift#scalability#security#knowledgeIispower#makeitsimple#simplelogic#didyouknow
0 notes
Text
Install Canonical Kubernetes on Linux | Snap Store
Fast, secure & automated application deployment, everywhere Canonical Kubernetes is the fastest, easiest way to deploy a fully-conformant Kubernetes cluster. Harnessing pure upstream Kubernetes, this distribution adds the missing pieces (e.g. ingress, dns, networking) for a zero-ops experience. Get started in just two commands: sudo snap install k8s –classic sudo k8s bootstrap — Read on…
View On WordPress
#dns#easiest way to deploy a fully-conformant Kubernetes cluster. Harnessing pure upstream Kubernetes#everywhere Canonical Kubernetes is the fastest#Fast#networking) for a zero-ops experience. Get started in just two commands: sudo snap install k8s --classic sudo k8s bootstrap#secure & automated application deployment#this distribution adds the missing pieces (e.g. ingress
1 note
·
View note
Text
United States insurance analytics market size reached USD 15.4 Billion in 2024. Looking forward, IMARC Group expects the market to reach USD 59.8 Billion by 2033, exhibiting a growth rate (CAGR) of 15.99% during 2025-2033.
#United States Insurance Analytics Market Report by Component (Solution#Service)#Deployment Mode (On-premises#Cloud-based)#Enterprise Size (Small and Medium-sized Enterprises#Large Enterprises)#Application (Claims Management#Risk Management#Customer Management#Sales and Marketing#and Others)#End User (Insurance Companies#Government Agencies#Third-party Administrators#Brokers and Consultancies)#and Region 2025-2033
0 notes
Text
Demystifying APIs

Introduction
Have you ever wondered how your weather app knows what’s happening outside, or how you can seamlessly log in to multiple platforms with a single Facebook account? The answer lies in a realm often unseen by the average user: the world of APIs (Application Programming Interfaces).
So, what exactly is an API?
Think of an API as a waiter in a fancy restaurant. You (the user) are enjoying the delicious meal (the website or app), but it’s the waiter (the API) who relays your orders (requests) to the kitchen (the server) and brings back the responses (data). These responses could be anything from weather updates to news feeds to personalized recommendations.
But what do APIs do? Why are they so important?
APIs serve as essential connectors, enabling communication and data exchange between different applications and servers. They power a vast array of functionalities:
Data access: APIs allow apps to tap into external data sources, like weather services, social media platforms, or news feeds, enriching their features and content.
User authentication: Logins with Facebook, Google, or Twitter? Those rely on APIs to verify your identity and seamlessly connect you to different platforms.
Payment processing: Secure online transactions wouldn’t be possible without APIs connecting your purchase to payment gateways and delivering confirmation back to the store.
App integration: APIs enable different apps to work together, like mapping apps sharing location data with ride-hailing services or fitness trackers syncing with health platforms.
Automation: Businesses use APIs to automate tasks like sending notifications, managing customer data, or controlling smart devices.
Are APIs Standalone Applications?
An API is not typically considered a standalone application in the traditional sense. Here’s why:
APIs as Intermediates:
APIs are software intermediaries that enable communication and data exchange between applications. They don’t function independently but rather act as bridges or connectors.
They don’t have a direct user interface or provide a complete user experience on their own. Instead, they are designed to be consumed by other applications or systems.
Components of Larger Systems:
APIs are often components within larger applications or systems. They provide specific functionality or access to data, but they rely on the surrounding application for overall structure and user interaction.
For example, a web application might have an API to allow other applications to access its data, but the API itself isn’t the entire application.
Backend Focus:
APIs primarily operate on the backend or server-side, handling data exchange and processing requests from clients. They don’t typically have a frontend user interface that users directly interact with.
Comparison to Standalone Applications:
Standalone applications offer a complete user experience with their own user interface and often handle tasks independently. Examples include desktop apps, mobile apps, and web apps that users directly interact with.
APIs as Enablers:
While not standalone applications, APIs play a crucial role in enabling communication and integration between different systems. They are essential for building modern, interconnected applications and services.
They power a vast range of functionalities, from mobile apps fetching data from servers to websites embedding content from third-party services to systems communicating within organizations.
Understanding the “interface” aspect of an API

When talking about the “interface component” of an API, it can refer to two slightly different aspects:
Public Interface:
This is the contract between the API provider and its consumers. It defines how external developers or systems can interact with the API. This interface includes several key elements:
API Endpoints: These are the URIs through which requests are sent and responses are received. Each endpoint typically corresponds to a specific resource or action.
HTTP Methods: The API specifies which HTTP methods (GET, POST, PUT, DELETE, etc.) are used for different operations on the resources.
Data Formats: The API defines the format of data exchanged between client and server, typically JSON or XML.
Authentication and Authorization: Mechanisms for securely accessing the API and controlling access to specific resources.
Error Handling: How the API communicates errors and unexpected situations to the client.
Documentation: Clear and comprehensive documentation to guide developers in using the API effectively.
This public interface is essentially the “face” of the API that everyone sees. It’s crucial for making the API easy to understand and use for developers.
Technical Interface:
This refers to the internal structure and implementation of the API itself. It encompasses the programming language, libraries, frameworks, and protocols used to build and execute the API code. While this aspect is less directly relevant to external consumers, it still plays a vital role in determining the API’s performance, scalability, and maintainability.
Therefore, the “interface component” of an API encompasses both the publicly visible contract for interaction and the underlying technical implementation that makes it work. Both aspects are critical for creating an effective and successful API.
Additionally:
Many APIs use tools like API gateways to manage and control the interface. These gateways can sit in front of the actual API code and handle tasks like routing requests, security enforcement, and versioning.
Some APIs also offer dedicated developer portals with interactive documentation, testing tools, and community forums. These features can further enhance the interface and improve the development experience.
How do users actually interact with APIs?

The benefits of using APIs:
Flexibility and scalability: APIs allow developers to build modular applications that can easily integrate with external services and adapt to changing needs.
Improved functionality: Apps can leverage specialized data and tools offered by other APIs, enhancing their own features and capabilities.
Faster development: Developers can avoid reinventing the wheel by using existing APIs for common tasks, leading to faster development and deployment.
Openness and innovation: APIs foster collaboration and innovation by encouraging developers to build upon existing services and create new functionalities.
Final Thoughts
The next time you marvel at the seamlessness of your online experience, remember the silent partners behind the scenes: APIs, the web’s unsung heroes, quietly connecting the dots and making it all possible.
0 notes
Text
Patna's Finest Software Development Company - Cybonetic Technologies Pvt Ltd
Explore a transformative experience with Cybonetic Technologies Pvt Ltd, renowned as the top software development company in Patna. Our devoted team is dedicated to delivering state-of-the-art solutions, encompassing Mobile App Development, Website Development, E-Commerce Development, software consulting, and Digital Marketing Services. Witness business expansion with our inventive and budget-friendly offerings. Contact us to collaboratively shape the future!

#software development#software development company in Patna#custom software applications#software developers#software development tools#programming languages#end-to-end solutions#testing#deployment#maintenance#innovative software solutions
0 notes