#cryptosystem
Explore tagged Tumblr posts
Text
Tempting Fate Ch. 4
summary: Evie made it through her first full week, has a breakthrough, and gets to celebrate!
author's note: I love a slow burn, but I want to get to the good stuff here. anyone else?!
masterlist
tag list: tag list: @yiiiikesmish @sunflower1290 @barnescamboy @thedisc0spider @bitchy-bi-trash @kulteule @kandis-mom @i-mushi @unknown-writings

A few hours and two large coffees later, Evie sat in her usual spot in the lab, her fingers flying across the keyboard. The screen in front of her was filled with complex lines of code, diagrams, and a myriad of data points. Her mind was a whirl of thoughts and possibilities, each one adding a new layer to her evolving solution for cracking Orpheus' defenses. She’d gotten right to the cusp last night, and today she’d been able to blow this motherfucker wide open.
The lab was quieter than usual, the other engineers having gone for their lunch break or taken Friday off altogether. All except for Chris, the one who’d infamously mistaken her for one of Tony’s one night stands on her first day. Since then, he'd been skittish around her, but they'd developed a tentative working relationship. Evie respected his skills and found his nervous energy somewhat endearing. She wasn’t one to hold grudges, nor was she one to get her feelings hurt over a misconception that––truth be told––made sense. He was the only other engineer with SHIELD security clearance, having been the main technological consultant before Evie was brought on board.
"Chris," Evie called absently, not looking up from her screen. "Get your ass over here for a second."
Chris, who had been tinkering with a circuit board at the other end of the lab, jumped slightly at the sound of her voice. He hesitated for a moment, then made his way over to her workstation.
"Uh, okay," he said, fidgeting with the screwdriver in his hands. "What’s up?"
Evie continued typing for a few more seconds before stopping and turning to face him. "I need a second pair of eyes on this. I’ve been at it all night and I might just be hallucinating, but I think I’ve found a solution to Orpheus’ defenses. Can you take a look and tell me if I'm just sleep-deprived or if this actually makes sense?"
Chris blinked, then nodded. "Of course, let’s see it."
Evie turned her laptop screen toward him and started explaining her solution in the rapid pace that only ever came out when she was excited.
"Alright, here’s the deal," Evie began, tapping a key to bring up a detailed diagram. "Orpheus’ encryption is a hybrid adaptive cryptosystem. They’re using a combination of RSA for key exchange and AES for data encryption, but they’ve added this insane layer of polymorphic encryption to constantly change the encryption keys on the fly."
Chris frowned, leaning in closer. "Okay, so how do we counter that?"
Evie smirked. "Glad you asked. The key is to exploit the timing discrepancies during the key exchange. By using a side-channel attack, we can measure the slight variations in execution time to predict the next set of encryption keys. From there, we inject a custom-built Trojan that piggybacks on their own update mechanism."
Chris' eyes widened. "You built a Trojan for this? Overnight?"
"Yes," Evie said, waving her hand dismissively. "It's a polymorphic Trojan, meaning it changes its code every time it replicates. That way, it can evade their adaptive defenses. Once it’s inside, it creates a virtual bridge, giving us a backdoor into their system."
Chris nodded slowly. "So, we use their own system updates to slip in unnoticed?"
"Exactly," Evie said, her eyes gleaming with excitement. "But that’s not all. I’ve also designed a recursive algorithm that exploits a vulnerability in their communication protocol. Every time Orpheus sends or receives data, the algorithm intercepts and duplicates the packets, allowing us to decrypt them in real-time."
Chris stared at the screen, his mind racing to keep up with her explanation. Slowly, he began to nod. "Evie, this is... I mean, this is incredible. You've actually figured it out. This should work. This should work…perfectly."
Evie’s eyes flicked off the screen and met his. "Really? You think so?"
Chris nodded more vigorously. "Yes, absolutely. It’s brilliant."
Without thinking, Evie jumped up from her chair, a huge grin spreading across her face. "Yes!" she exclaimed, leaning over to kiss him on the cheek. "Hell YES! Thank you!"
Chris stood there, utterly flustered, his face turning a deep shade of red. "Uh, you’re welcome," he stammered.
Evie shoved her laptop into her bag, grabbed her coffee, and rushed out of the lab, her heart pounding with exhilaration. "You’re the man, Chris!"
As she disappeared down the hallway, Chris stood there for a moment, still processing what had just happened. Finally, he shook his head with a small, bewildered smile. "Unbelievable," he muttered to himself, before returning to his workstation.
Evie practically sprinted through the halls, her coffee sloshing in her cup. She reached Tony’s private lab upstairs and burst through the door the second her keycard turned the access pad green.
Tony looked up from his workstation, raising an eyebrow at her sudden entrance. "Well, well, if it isn't the wunderkind herself," he said dryly. "Ever heard of knocking? You might see something you don't want to see."
Evie waved off his comment, her excitement palpable. "Yeah, yeah, spare me the pleasantries, Stark. I need to show you something."
Tony leaned back in his chair, crossing his arms over his chest. "This better be good. It’s barely noon, the crack of dawn here."
Evie quickly set her laptop on the table and pulled up her work, launching into her explanation. "I've been working on Orpheus' encryption all night, and I think I've cracked it. Look, their system uses a hybrid adaptive cryptosystem. RSA for key exchange, AES for data encryption, and a layer of polymorphic encryption."
Tony started to pay attention, but his eyes flicked over her attire, and a smirk formed on his lips. "Hold up a second. Are you wearing Cap's sweatshirt?"
Evie glanced down at the navy blue crewneck she had on, suddenly realizing the emblem on the sleeve clearly featured the Avengers trademark “A” with the words ‘Captain Rogers’ embroidered right beneath it. She rolled her eyes. "Yeah. I pulled an all nighter and didn't want to show up in the same clothes from yesterday. People might make assumptions, as they already have." She raised her eyebrow impatiently.
Tony's smirk grew wider. "And you didn't think they'd make assumptions if you showed up in Captain America's sweatshirt?"
Evie shrugged. "He’s not my boss."
Tony chuckled, but his eyes were now glued to the screen. "Alright, what you do in your own time is none of my business anyways. Show me what you've got, Langston."
Evie dove back into her explanation, her fingers flying over the keys as she navigated through her code and diagrams. "Okay, so, their encryption changes the keys on the fly. To counter that, I developed a side-channel attack to measure the timing discrepancies during their key exchange. We use those discrepancies to predict the next set of encryption keys."
Tony's interest piqued, and he leaned forward. "Timing attack, huh? Not bad. But what about the polymorphic encryption?"
"Glad you asked," Evie said with a grin. "I built a polymorphic Trojan that changes its code every time it replicates. It evades their adaptive defenses and creates a virtual bridge, giving us a backdoor into their system. And there's more. I designed a recursive algorithm that intercepts and duplicates their data packets, allowing us to decrypt them in real-time."
Tony stared at the screen for a moment, then let out a low whistle. "Damn, Red. You really outdid yourself."
Evie's grin widened. "So, you think it’ll work?"
Tony nodded slowly. "Oh, it'll work. I'm just wondering how the hell you managed to put this together in one night. And then still had time to swipe Cap’s sweatshirt.”
She shrugged. "I work well under pressure. And I love a challenge."
Tony laughed, shaking his head. "Alright, genius. Let's get this to Maria. She’s going to want to see this ASAP. Let’s go to the boardroom, I’ll conference her in."
Evie grabbed her laptop, feeling a rush. "Let's do it."
As they headed out of the lab, Tony glanced at her again, the smirk still playing on his lips. "Rogers couldn’t handle you in the first place, kid."
“All I know is he makes a killer breakfast.”
__________
The lab was quiet, save for the soft hum of machinery and the clicking of the keyboard. Evie was hunched over her workstation, the glow of the screen illuminating her face. She meticulously reviewed her code for what felt like the hundredth time, making sure every line was perfect when Tony walked in, his footsteps echoing in the large, empty room.
"I swear, I’m either getting very old or this is deja vu." he called out, making his way over to her.
She didn't look up from her screen. "I don’t think those two are mutually exclusive."
Tony sighed dramatically, leaning against her desk. "You know, I hired you because you’re hot. But being in the office for 30 hours straight without going home to shower is seriously ruining the mood."
Evie glanced up and flipped him off. "You're hilarious, Stark."
Tony raised his eyebrows. "Seriously, what the hell are you still doing here? It’s 7pm on a Friday night. Surely you have something better to do than this.”
“I’m just going over everything again.”
“It’s perfect. We went through it ten times today. You won't make it any better by staring at it all night."
Evie leaned back in her chair, rubbing her tired eyes. "I just want to make sure. This is big."
Tony nodded, his tone turning slightly more serious. "I know. And you did an amazing job. Which is why I’ve already invited the team out to celebrate your brilliant discovery and for finishing the work before the mission deadline––which, considering they’re used to working with me––is a novel concept. Also, to celebrate your first full week of working for me."
Evie raised an eyebrow. "You’re serious?"
"Dead serious," Tony replied. "We’ll be meeting at the bar in an hour and a half. And I’ve got Happy waiting for you outside to take you to your building."
Evie blinked. "Wow, thanks, Tony. But really, I’m fine. I just need to pick up around here and then I can just head straight to the bar."
Tony shook his head. "No can do, Red. Happy has strict instructions to make sure you get into the elevator and don’t try to come back to the lab. You need to get some fresh and fix…” he gestured vaguely to her hair and outfit. “...this situation.”
Evie rolled her eyes but couldn’t help the small smile tugging at her lips. "You’re such a control freak."
Tony shrugged. "Yes, and you’ll thank me later. Now, go. Freshen up, put on something that doesn't smell like coffee and palladium, and be ready to celebrate like I taught you."
Evie stood up, stretching her arms. "Alright, alright. I’ll go. But you’re still an ass."
Tony chuckled. "I’ve been called worse. Now get out of here before I tell FRIDAY to revoke your security clearance for the weekend."
Rolling her eyes, Evie grabbed her laptop and bag, heading towards the door. As she walked out, she glanced back at Tony. "Thanks, Tony. For everything."
Tony waved her off with a smile. "See you in a bit."
Evie made her way outside, squinting at the sun to see Happy standing next to the black SUV, waiting patiently. He gave her a nod and opened the door for her.
"Miss Langston," he greeted with a smile. "Ready to head home?"
Evie grinned. "Yessir, thanks for the lift, Happy."
"Anytime," he replied, closing the door behind her.
As they drove towards her building, Evie allowed herself a deep breath, shoulders rolling back from the hours hunched over a workstation. It had been an intense week, but she had proven herself and made a significant breakthrough. Tonight, she would celebrate with the team –– the fucking Avengers –– knowing she had earned every bit of it.
Evie slumped against the back seat of the car, exhaustion and a sense of accomplishment washing over her as she snapped out of her single-minded work mode. She stared out the window, her mind processing the reality that was her life. This past week had been a whirlwind – a literal dream come true.
Happy glanced at her through the rearview mirror, a good-natured smile tugging at his lips. "So, how's it feel? First week at Stark Industries under your belt. Bet it's been a ride."
Evie sighed. "Oh, Happy. It's been everything. I think I slept about 10 hours the whole week, half because I was too excited and half because I couldn’t get myself to leave the lab.” She looked out the window. “It probably sounds childish, but part of me feels like if I go to sleep, I’ll wake up back in my tenth grade calculus class bored out of my mind. It’s like…it’s just a dream.”
Happy chuckled. "It doesn’t sound childish at all. I remember the first time I met you, back at the alumni gala. When Tony brought you out to the car, I thought you were…well––"
“You thought I was a cocktail waitress trying to end up on a yacht.”
“Well, yes, something like that.” His cheeks flushed.
“Astute observation.” Evie grinned. “I’m sure you weren’t the only one to make it.”
“Of course, after meeting you, it was clear––”
Evie laughed, waving him off. "Don’t worry about it, Happy, seriously. I’m sure you’re conditioned to assume that with Tony."
"You could say that," Happy replied, shaking his head with a grin. “That was a fun night. When we drove back to the city the next day, Tony couldn’t stop talking about you. He kept saying you were ‘the princess who was promised’, or something along those lines. He may have still been a little drunk, but even so, he’s not one to rave about someone’s intellect besides his own. "
“He’s been watching too much Game of Thrones.” Evie chuckled. “That’s very flattering.”
“I’m not kidding, he told me from that very first weekend that he thought you’d change the world. He wanted to convince you to drop out and go work for him that second.”
“Believe me, he tried.”
“Well, for what it’s worth, I’m glad you stuck it out.” Happy met her eyes in the rearview. “Especially if you’re prone to workaholism, I’m glad you got to live your life for a while.”
“Considering my boss is the one who threw me out of the office and told me to get my ass to the bar, I don’t think that’s going to stop.”
Happy shrugged. "Tony’s lost himself in his work before. I don’t think he wants to see that happen to you."
Evie smiled. "That’s oddly wholesome."
“Mr. Stark is an enigma.” Happy's eyes crinkled as he smiled. "You know, I got kicked out of my own car that night at the gala."
Evie raised an eyebrow. "Really? Why?"
"Tony wanted some alone time with your best friend," Happy explained with a smirk. "So, I logged some significant time playing pool with grad students in the bar until I got the all-clear. Your friend was quite the charmer, apparently."
Evie shook her head. "Yeah, that's Jade. I got far too many details about that night."
Happy shuddered. "I don’t even want to know. But hey, it worked out. You got to where you wanted to be, and Tony… well, he got what he wanted too."
As they pulled up to her building, Happy glanced at her sweatshirt, doing a double take. "Is that Cap’s sweatshirt?"
Evie smirked, a mischievous glint in her eye. "Maybe. Why?"
Happy laughed, shaking his head. "Just making sure you're not causing any trouble."
She winked at him. "Wouldn't dream of it."
Happy parked the car and got out, opening the door for her. "Alright, Miss Langston. You go get ready and do whatever it is that Tony insisted I bring you here for. I’ll be back to pick you up in an hour."
Evie stepped out, shrugging her bag onto her shoulder. "Thanks, Happy. I’ll see you soon."
He gave her a nod. "Take care, Evie. And remember, no trying to sneak back to the lab."
She laughed. "Got it. See you soon, Happy."
________
Evie walked into the bar, a surprisingly normal looking joint in a lesser known part of the city. She didn’t know what she expected, something flashier and possibly on a rooftop? Dancers in lingerie in floating cages above the crowd? That seemed much more Tony-esque than this pseudo dive bar. Not that she was complaining, it reminded her of The Bos, giving her a warm rush of nostalgia. They crossed the busy room, Evie turning heads and drawing a few catcalls as she navigated toward the back booth where Earth’s Mightiest Heroes sat. Happy gave the already drunk catcallers a stern look and a wave of his hand. "Alright, keep moving, nothing to see here," he said, holding a hand out to clear a way through the crowd.
"Thanks, Happy," Evie nodded.
Tony's voice rang out above the low roar of the bar. "There she is! The woman of the hour!" He relished in the attention of the bar as he strode over, placing his arm around Evie's shoulders and escorting her to the large corner booth where the team was waiting.
"Evie!" Wanda called out, standing up to give her a warm hug. "It’s so good to see you."
"Hey, Wanda," Evie replied, hugging her back. "It’s good to see you too."
“One week down, that’s like a lifetime with Stark.” Natasha gave her a friendly nod. "Nice work this week, Evie. Heard you’ve been killing it."
"Thanks, Nat. I’m just trying to keep up with you guys," Evie gave a humble nod, her usual borderline arrogance fading in the face of Black Widow herself.
Sam clapped her on the back. "You’re doing more than keeping up. You’re setting the pace."
Evie grinned. "Thanks, Sam."
Before anyone else could greet her, Tony held his hand out in front of her. “In order to make an effective toast, the toastee needs a drink. Shall we?”
“We shall,” Evie put her hand on his, grinning. She turned back to face the team and looked at Steve, who was watching her with a small smile from his seat. "Oh, Steve, I promise I’ll return your sweatshirt. Thanks for letting me borrow it this morning."
The team erupted in a chorus of “ooh” and “Alright, Rogers” as Steve blushed, grinning down at his drink.
Tony guided her to the bar, placing a hand on her shoulder. “You know exactly what you’re doing, I assume.”
“I don’t know what you’re talking about.” Evie gave a wry smile.
"Come on, genius. First round’s on me."
Evie smirked. "Correction: every round is on you because you’re the one who invited me out."
Tony raised an eyebrow, clearly amused. "Is that so?"
"Absolutely," she replied confidently. "You dragged me out of the lab, so you get to pay for my drinks. It's only fair."
Tony laughed. "Alright, alright. You drive a hard bargain. What’ll it be?"
"I’ll start with a whiskey sour," Evie said, sliding onto a barstool.
Tony ordered their drinks and turned to her. "So, how does it feel to be the second smartest person in the room?"
Evie snorted. “You tell me."
Tony handed her the drink, a smirk on his face. "You’re insufferable. I love it. Here’s to a brilliant first week."
They clinked glasses, and Evie took a sip. "Thanks, Tony. For the drink, for this, for everything. This week has been a dream come true."
Tony nodded, his expression sincere for once. "Just keep doing what you’re doing, Evie. I’m glad to have you. Now don’t go getting all weepy on me, I’m trying to cut back on sentiment."
They returned to the booth, where the team was waiting with smiles and cheers. "Alright, everyone," Tony announced. "Here’s to Evie and her first week at Stark Industries, and our lives being in very capable hands. Let’s make this a night we wished we could remember!"
The team raised their glasses, and Evie couldn’t help but feel a surge of happiness. She was exactly where she was meant to be. As she downed another gulp of her drink, she let all thoughts of work and code and trojans and missions fade to the back of her mind.
An hour passed as the group chatted and laughed, some breaking off to play pool, some (Sam) ending up on the dance floor in the middle of a bachelorette party. Steve and Bucky found themselves in a quiet debate in the back of the booth.
"You flip," Steve suggested, holding a coin between his fingers.
Bucky shook his head. "No way, you flip. Last time, I got stuck with the tab."
Steve chuckled. "Alright, alright. Heads, I offer. Tails, you do."
As he prepared to flip the coin, Evie noticed their quiet discussion and couldn’t help but be curious. Handing Nat the cue stick, she walked over to where they were sitting.
"What's this about a coin flip?" she asked, leaning against the table and giving them a teasing look.
Both men looked up, slightly caught off guard at someone returning to the booth. Evie guessed they usually ended up the only two still sober at the end of the night due to their Super Soldier something or other.
"Just a little game we play," Bucky said coolly, rolling the coin around in his metal fingers.
Steve nodded, smiling up at her. "Deciding who buys the next round."
Evie raised an eyebrow. "How about we skip the coin flip and both of you buy me a drink?"
Steve and Bucky exchanged a glance. "Deal," Steve said, standing up. "What’s your poison?"
Evie pretended to think for a moment, tapping her chin. "Surprise me. But make it something good."
As Steve headed to the bar, Evie slid into the seat next to Bucky. "So, do you always use coin flips to make decisions?"
Bucky chuckled, leaning back in his chair. "Only when we can't decide. Or when it's something important."
"Buying me a drink is important?" she asked, half a question and half a statement.
Bucky met her gaze, his blue eyes intense "You could say that."
Steve returned with two beers and a bright red drink with two cherries floating on top, setting them down on the table before sliding in on Evie’s other side. "One surprise drink, as requested."
Evie picked up her glass, examining the contents before taking a sip. "Hmm, not bad. Four stars, two enthusiastic thumbs up."
She leaned closer to them, her voice dropping to a conspiratorial whisper. "So, what else do you two decide with coin flips? Who gets the best mission assignments?"
Steve chuckled, shaking his head. "No, that one's above our pay grade."
"But we do use it for simpler things," Bucky added. "Who gets to take the motorcycle, who has to run with Sam, things like that."
Evie laughed. "Sounds incredibly meticulous, very fitting of two Avengers. It must be fun, having your best friend to share all of this with."
Steve and Bucky exchanged another glance. "It has its moments," Steve said, his smile genuine.
Bucky nodded. "Yeah, it's not so bad."
“Do you share everything?” She tugged on a cherry stem, popping the fruit in her mouth.
“Not…everything.” Steve said slowly, eyes flicking down to her lips for a split second. “I’m sure the team would say we’re a package deal, but some things are still kept separate.”
Evie took another sip of her drink, watching them. "So, tell me," she said, leaning forward, her eyes locked onto theirs. "What’s the craziest thing you’ve done lately? You can flip the coin to decide who spills first."
Steve and Bucky glanced at her, then at each other, both grinning sheepishly.
"Honestly, our lives are pretty... regimented," Steve admitted. "Missions, training, repeat."
Bucky nodded in agreement. "Yeah, we don’t get much downtime. Not that we’re complaining, but it doesn’t leave a lot of room for…crazy."
Evie laughed, shaking her head. "You guys need to get out more.”
“Coming from the one who Stark had to drag out of the lab.” Bucky sipped his beer, not breaking eye contact.
“Forgive me for wanting to make sure the technology that’s going to keep your asses alive is foolproof.” She winked. “Besides, I have plenty of experience being out.”
Steve raised an eyebrow. "Oh yeah? How so?"
"Well, I used to bartend, so I spent a lot of time in a place just like this," she said, gesturing around the bar.
"Doesn’t sound too crazy on your end either," Bucky said, leaning onto the table. "Unless you have another story sweetheart, you’re still talking about work."
Evie leaned onto her elbows, eyes locked on his. "I guess I just like to keep busy."
Steve looked thoughtful for a moment before a spark of an idea lit his eyes. "You know, maybe we should start doing something like that. Hold each other accountable for getting out and having fun."
Bucky shot him a curious glance, tearing his eyes from Evie’s. "What are you suggesting, Rogers?"
Steve shrugged, his smile growing. "I’m saying we make Friday nights our mandatory 'fun time.' No missions, no training, no work. Just us, going out and doing something together. If nothing else, it would get Sam to get off our case about being old and boring."
Evie raised her glass in a mock toast. "I like the sound of that. I could probably benefit from leaving the lab every now and then, wouldn’t want to turn into a mad scientist."
Bucky tilted his head, considering. "I’ve heard worse ideas."
"Great," Steve said, raising his own glass. "To Friday nights and mandatory fun."
They all clinked their glasses together, taking a long drink.
“Wait,” Evie fished her phone out of her purse. “Let’s take a photo to commemorate this historic agreement.” She held her arm out, fighting the flutter in her stomach as both men leaned closer on either side of her, smiling at the screen. “That’s a keeper, for sure.” She grinned, zipping her phone back into her bag.
As the night wore on, they continued to talk and laugh, different members of the team coming and going from the booth. No one stopped to ask them for photos or autographs, which Evie guessed is why they liked this place. She wondered if they were regulars, giggling at the thought of the ones who save the planet from intergalactic threats being regulars anywhere.
"So, what's the first thing we do for our new Friday night tradition?" Evie asked, leaning back in the booth.
Bucky eyed her as he raised the bottle to his lips. "Something tells me you’ve got some ideas."
Evie grinned. "I’ve got a few."
Steve chuckled. "We’re at your mercy. Here’s to new traditions and great company."
They clinked their glasses once more before Sam came to steal them all for a rousing game of darts. It was short lived, seeing as Bucky hit a bullseye with every single left-handed toss. As the evening wound down, the group made their way out of the bar just before last call. Tony had blown her a kiss across the bar an hour prior, he and Sam leaving with the bachelorette party. Nat and Wanda hopped into the car with Happy, waving goodbye as they pulled away from the curb. Evie fished her phone out of her bag, preparing to call an Uber as she swayed near the curb.
“Hold up, Evie,” Steve said, stepping closer. “We can drop you off.”
She looked up, eyes wide. “You guys don’t have to do that. Besides, you’ve been drinking too.”
Bucky smirked. “Super Soldiers, remember? Alcohol doesn’t affect us the same way.”
Evie hesitated, a small smile tugging at her lips. “You’re sure?”
“Positive,” Steve replied, his tone leaving no room for argument.
“Well, okay then,” she said, feeling a warmth spread through her that had nothing to do with the alcohol. “Thanks.”
The drive back to her building was euphoric, the top was off in Steve’s jeep and the wind whipped through her hair. Evie leaned back in the middle of the backseat, spreading her arms wide as they drove through the night air. When they pulled up to her building, Steve put the car in park before hopping out to open her door and give her a hand down.
“Thanks for the ride,” she said, trying not to slur her words too much as she turned to look at them both. “And for tonight. I had a lot of fun.”
Steve smiled. “So did we.”
As Steve hopped back into the driver’s seat, she leaned on the ledge of Bucky’s door. “Sweet dreams. I’ll see you guys on Monday.”
Bucky nodded, his expression softer than usual. “Looking forward to it.”
She gave them a small wave as she spun and headed into her building, feeling a strange mix of emotions. There was something about the way they’d cared for her, looked out for her, that disarmed her usual bravado and flirtation. It was a feeling she wasn’t entirely used to, but one she found herself liking.
Evie walked into her luxurious penthouse apartment, the city lights casting a soft glow through the floor-to-ceiling windows. She kicked off her heels and headed to her bedroom, the plush carpet soft under her feet. She tossed her bag on the bed and pulled out her phone, shooting the photo she’d taken earlier to Jade as she started to change into her pajamas.
Unsurprisingly, her phone buzzed only seconds later, despite it being the middle of the night. Jade was probably closing up The Bos anyways.
J: HOT
J: why do I feel like it won’t be long before i’m not the only one who’s fucked an Avenger?
E: a lady never tells…
J: a lady might not, but you better!
E: i’ll call you in the AM, sweet dreams baby J ;)
J: dirty dirty girl. talk soon. you better have a good story for me.

#bucky barnes#bucky fluff#winter soldier#sebastian stan#bucky fanfic#bucky barnes x oc#avengers#james bucky barnes#stucky x oc#stucky#Steve and Bucky#avengers fanfiction#the avengers#mcu#marvel mcu#marvel cinematic universe
21 notes
·
View notes
Text
I need a shirt that shows the rsa cryptosystem but it’s got decryption key d=☕️, encryption key e=😭, message a=🔢 and encrypted message A=\Box
(tea decrypts numbers into finished proofs)
6 notes
·
View notes
Text
This package contains cryptographic software (caesar and rot13). In some jurisdictions, use or distribution of these utilities may be restricted, whether under export control regulations or because these cryptosystems have been used as technical protection measures to restrict access to and copying of copyright works.
I don't think this applied even in the eighties. But thanks
24 notes
·
View notes
Text
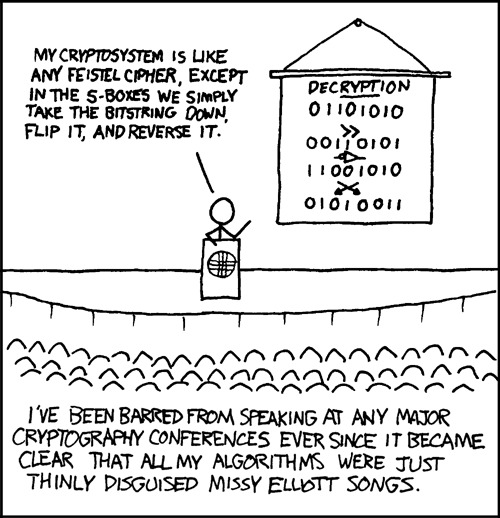
If you got a big keyspace, let me search it.
Cryptography [Explained]
Transcript Under the Cut
[Randall Munroe (drawn as Cueball) stands behind a lectern on a podium in front of a large conference audience (consisting of Cueball heads), with a poster hanging beside him.] Randall: My cryptosystem is like any Feistel cipher, except in the S-Boxes we simply take the bitstring down, flip it, and reverse it.
[The poster reads:] Decryption 01101010 >> 00110101 [inverter symbol] 11001010 [crossed arrows] 01010011
[Caption below the crowd:] I've been barred from speaking at any major cryptography conferences ever since it became clear that all my algorithms were just thinly disguised Missy Elliott songs.
24 notes
·
View notes
Text

#art#artist#arte#artistic#contemporary art#artwork#fine art#fashion#Aesthetic#musician aesthetic#music#musician#new music#My music#musician on tumblr#chill#Illustration#illustrator#love#drawing#painting#original#Original Work#original art#inspiration#inspired#Songs#soundcloud#Bandcamp#new
3 notes
·
View notes
Text
finals crunch time
i have like 3-4 posts in my queue but if u see me doing anything else yell at me to get off this site so i can pass my cryptosystems exam
3 notes
·
View notes
Text
Bitcoin in a Post Quantum Cryptographic World
Quantum computing, once a theoretical concept, is now an impending reality. The development of quantum computers poses significant threats to the security of many cryptographic systems, including Bitcoin. Cryptographic algorithms currently used in Bitcoin and similar systems may become vulnerable to quantum computing attacks, leading to potential disruptions in the blockchain ecosystem. The question arises: What will be the fate of Bitcoin in a post-quantum cryptographic world?

Bitcoin relies on two cryptographic principles: the Elliptic Curve Digital Signature Algorithm (ECDSA) and the SHA-256 hashing function. The ECDSA is used for signing transactions, which verifies the rightful owner of the Bitcoin. On the other hand, the SHA-256 hashing function is used for proof-of-work mechanism, which prevents double-spending. Both principles are expected to become vulnerable in the face of powerful quantum computers.
Quantum Threat to Bitcoin
Quantum computers, due to their inherent nature of superposition and entanglement, can process information on a scale far beyond the capability of classical computers. Shor's Algorithm, a quantum algorithm for factoring integers, could potentially break the ECDSA by deriving the private key from the public key, something that is computationally infeasible with current computing technology. Grover's Algorithm, another quantum algorithm, can significantly speed up the process of finding a nonce, thus jeopardizing the proof-of-work mechanism.
Post-Quantum Cryptography
In a post-quantum world, Bitcoin and similar systems must adapt to maintain their security. This is where post-quantum cryptography (PQC) enters the scene. PQC refers to cryptographic algorithms (usually public-key algorithms) that are thought to be secure against an attack by a quantum computer. These algorithms provide a promising direction for securing Bitcoin and other cryptocurrencies against the quantum threat.
Bitcoin in the Post Quantum World
Adopting a quantum-resistant algorithm is a potential solution to the quantum threat. Bitcoin could potentially transition to a quantum-resistant cryptographic algorithm via a hard fork, a radical change to the blockchain protocol that makes previously invalid blocks/transactions valid (or vice-versa). Such a transition would require a complete consensus in the Bitcoin community, a notoriously difficult achievement given the decentralized nature of the platform.
Moreover, the Bitcoin protocol can be updated with quantum-resistant signature schemes like the Lattice-based, Code-based, Multivariate polynomial, or Hash-based cryptography. These cryptosystems are believed to withstand quantum attacks even with the implementation of Shor's Algorithm.
Additionally, Bitcoin could integrate quantum key distribution (QKD), a secure communication method using a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which can be used to encrypt and decrypt messages.
Conclusion
In conclusion, the advent of quantum computers does indeed pose a threat to Bitcoin's security. However, with the development of post-quantum cryptography, there are potential solutions to this problem. The future of Bitcoin in a post-quantum world is likely to depend on how quickly and effectively these new cryptographic methods can be implemented. The key is to be prepared and proactive to ensure the longevity of Bitcoin and other cryptocurrencies in the face of this new quantum era.

While the quantum threat may seem daunting, it also presents an opportunity - an opportunity to improve, to innovate, and to adapt. After all, the essence of survival lies in the ability to adapt to change. In the end, Bitcoin, like life, will find a way.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#bitcoin#btc#ecdsa#sha256#shor’s algorithm#quantum computing#superposition#entanglement#quantum mechanics#quantum physics#crypto#cryptocurrency#cryptography#encryption#futurism
2 notes
·
View notes
Text
Post Quantum Algorithm: Securing the Future of Cryptography

Can current encryption meet the quantum future? With the entry of quantum computing, classical encryption techniques are under the immediate threat of compromise. There has come a new age with the post quantum algorithm as a vital solution. Having the capability to shield data from being vulnerable to quantum attacks, this fascinating technology promises digital security for the future decades. Different from classic crypto schemes, such algorithms resist even sophisticated quantum attacks. But how do they work, and why are they important? In this article, we’ll explore how post-quantum algorithms are reshaping the cybersecurity landscape — and what it means for the future of encryption.
What is a Post Quantum Algorithm?
A post quantum algorithm is an encryption technique implemented to secure sensitive information from the vast processing power of quantum computers. In contrast to the classic encryption method, which can be cracked using the help of algorithms like Shor’s by quantum computers, this new method takes advantage of maths problems that are difficult for both quantum and classical systems to calculate. Quantum computers employ qubits to process information at new rates, endangering the current state of encryption, such as RSA or ECC.
To counter this, post-quantum solutions employ methods such as lattice-based encryption, code-based cryptography, and hash-based signatures. These are long-term security frameworks that keep data safe, even when there are vast numbers of quantum computers available for cryptographic algorithms.
Why We Need Post Quantum Algorithms Today
Although quantum computers are not yet available, post-quantum implementation of the algorithms in the initial stages is unavoidable. Encryption is not for today — it’s for tomorrow’s data too. A cyberthief will tap encrypted data today and crack it when there’s quantum technology in the future.
The application of a post quantum algorithm nowadays assures long-term secure information protection. Government agencies, banks, and medical providers are already transitioning to quantum-resistant systems.
Types of Post Quantum Algorithms
There are various kinds of post quantum algorithms, and each one has special strengths-
Lattice-based Cryptography: Lattice-based cryptography holds most hope. It relies on lattice problems upon which to build security that even a highly capable quantum computer possesses no way of solving quickly. They do digital signatures and encryption, and are relatively fast. They are quite general, hence are in line for standardization.
Hash-based Cryptography: Hash-based cryptography is primarily digital signature-based. They enjoy the security of traditional cryptographic hash functions and are safe against known quantum attacks. Very secure and grown-up, but generally not employed for encryption due to their size and slow performance, these schemes are only suitable to protect firmware and software patches.
Multivariate Polynomial Cryptography: Multivariate Polynomial Cryptography: Multivariate polynomial cryptography consists of complex mathematical equations involving numerous variables. They provide compact signature generation and verification, which is advantageous in resource-limited settings such as embedded systems.
Code-based Cryptography: Code-based cryptography research has been conducted for many decades and employs error-correcting codes for encrypting and protecting information. It provides very good security against quantum attacks and is particularly suitable for encryption applications. Although code-based cryptosystems have large public key sizes, their long history of resistance makes them a popular selection for protecting information in the long term.
How Post-Quantum Algorithms Work
A post quantum algorithm relies on the concept of using mathematical problems that are hard to break through quantum computers. They are resistant to both classical and quantum attacks. One of them, lattice-based cryptography, uses vectors in high-dimensional space. It is still very hard to solve the lattice problems even for highly powerful quantum processors.
All of the suggested algorithms test extensively for performance, key size, and resistance against any known quantum attacks. The National Institute of Standards and Technology (NIST) coordinates the worldwide effort in testing and standardizing the algorithms. They will work on new cryptographic systems used to replace current systems that are vulnerable and offer long-term security of information in a world where quantum computers are readily available and extremely powerful.
Real-World Applications of Post-Quantum Algorithms
Post quantum algorithm application is not a theory. Many companies have already started using them-
Finance: Organisations in the finance sector employ quantum-resistant cryptography to protect confidential financial transactions and customer data. Financial information is confidential for decades, and quantum-safe encryption protects it from hacking in the future. Banks and payment processors are piloting and implementing post-quantum approaches into core security solutions.
Healthcare: The integrity and confidentiality of medical records form the basis of the healthcare business. Healthcare organizations and hospitals have been using quantum-secure encryption to secure patients’ data for decades. Health information is retained for many years, and post-quantum methods provide guarantees that such information will not be vulnerable to future computing breakthroughs.
Government: Government departments manage national security information that may be useful for many decades. Therefore, they are leading the adoption of post-quantum technologies, primarily for secure communication and sensitive documents. Military, intelligence, and diplomatic operations are investing in quantum-resistant technologies to prepare for the future.
Cloud Services: Cloud service providers deploy Quantum-resistant encryption. As cloud infrastructure is responsible for everything from document storage to software services, they have to ensure data protection both in transit and at rest. Cloud giants are experimenting with hybrid approaches that involve classical and post-quantum encryption to protect data even further.
Post Quantum Security in the Modern World
Security does not only mean encrypting information; it means expecting it. That is where post quantum security comes in. With billions of devices connected and more data exchanges taking place, organizations need to think ahead. One quantum attack will reveal millions of records. Adopting a post-quantum algorithm today, companies construct tomorrow-proof resilience.
Transitioning to Post Quantum Algorithms: Challenges Ahead
The transition to a post quantum algorithm presents a sequence of challenges for contemporary organizations. The majority of today’s digital architectures depend on outdated encryption algorithms such as RSA or ECC. Replacing those systems with quantum-resistant technology requires a lot of time, capital, and extensive testing. Post-quantum techniques have greater key lengths and increased computational overhead, affecting performance, particularly on outdated hardware.
To control this transition, companies have to start with proper risk analysis. Companies have to tag the systems handling sensitive or long-term data and have them upgraded initially. Having a clear migration timeline guarantees the process will be seamless. With early execution and adopting hybrid cryptography, companies can phase their systems gradually while being in advance of the quantum attack without sacrificing the security level.
Governments and Global Efforts Toward Quantum Safety
Governments across the globe are actively engaging in countering quantum computing risks. Governments recognize that tomorrow’s encryption must be quantum-resistant. Organizations such as the National Institute of Standards and Technology (NIST) spearhead initiatives globally by conducting the Post-Quantum Cryptography Standardization Process. The process is to identify the best post quantum algorithm to implement worldwide.
Parallely, nations finance research, sponsor academic research, and engage with private technology companies to develop quantum-resistant digital infrastructures. For the effectiveness of these breakthroughs, global cooperation is necessary. Governments need to collaborate in developing transparent policies, raising awareness, and providing education on quantum-safe procedures. These steps will determine the future of secure communications and data protection.
Understanding Post Quantum Encryption Technologies
Post quantum encryption employs post-quantum-resistant methods to encrypt digital information. This is in conjunction with a post quantum algorithm, which protects encrypted information such that no individual, even quantum computers, can access it. Whether it is emails, financial data, or government documents being protected, encryption is an essential aspect of data protection. Companies embracing quantum encryption today will be tomorrow’s leaders.
The Evolution of Cryptography with Post Quantum Cryptography
Post quantum cryptography is the future of secure communication. Traditional cryptographic systems based on problems like factorization are no longer efficient. Post quantum algorithm…
#post quantum cryptography#post quantum encryption#post quantum blockchain#post quantum secure blockchain#ncog#post quantum#post quantum securityu#tumblr
1 note
·
View note
Text
Types of qubits And Applications of Quantum Processing Units

This article covers quantum processing unit applications, structure, qubit types, and more.
The “brain” of a quantum computer is a Quantum Processing Unit. This cutting-edge machine solves complicated issues with qubits and quantum physics. QPUs use qubits, which can be 0, 1, or a mix of both. Traditional computers employ binary bits. QPUs handle data differently than computers due to quantum principles like entanglement, decoherence, and interference.
QPU Structure and Function
Two key components make up a QPU:
Quantum Chip: This semiconductor base has numerous layers etched with superconducting components. These components make up physical qubits.
Control Electronics: These handle and amplify control signals, control and read qubits, and address decoherence-causing interference. They have standard CPU components for data exchange and instruction storing.
Dilution refrigerators that freeze the quantum chip to near absolute zero—colder than space—are needed for qubit coherence. Traditional computing equipment and control circuits can be stored in racks close to the refrigerator at normal temperature. The whole quantum computer system, including cryogenic systems and other classical components, may be the size of a four-door car.
Quantum logic gates in QPUs translate qubit data mathematically, unlike binary logic gates. Even though they can solve issues that classical computing cannot, QPUs are much slower than CPUs in raw computation speed. But other issue classes compute more efficiently, which can reduce calculation time.
Types of Qubit
Quantum processors’ quantum technologies vary, showing the variety of quantum computers in development. Qubits are usually made by manipulating quantum particles or building systems that approximate them. Different modalities include:
Cold, laser-controlled neutral atoms in vacuum chambers. Scaling and executing activities are their specialities.
Low-temperature superconducting qubits are preferred for speed and precise control. IBM QPUs employ solid-state superconducting qubits.
High-fidelity measurements and long coherence durations are possible with trapped ion qubits.
Catching an electron creates a qubit from quantum dots, tiny semiconductors. Compatible with semiconductor technology and scalable.
Photons: Light particles used in quantum communication and cryptography, notably long-distance quantum information transfer.
QPU manufacturer design direction and computing requirements often determine qubit modality. All known qubits require a lot of hardware and software for noise handling and calibration due to their extraordinary sensitivity.
Quantum Processing Unit Applications
QPUs promise advances in many vital industries and are ideally suited for unsolved problems. Important uses include:
Combinatorial optimisation challenges: These enormous issues get tougher to tackle. Neutral atom Rydberg states may solve these classification problems.
Pharmaceuticals and quantum chemistry: Accelerating medication development and chemical byproduct studies by simulating molecular and biological reactions.
Artificial Intelligence (AI) and Machine Learning (ML): Quantum algorithms may speed up Machine Learning and help AI investigate new techniques by analysing enormous volumes of classical data.
Materials Science: Studying physical matter to solve problems in solar energy, energy storage, and lighter aviation materials.
Integer factorisation can still undermine open cryptosystems.
AI and cybersecurity applications are commercialising RNG.
In quantum cryptography, new cryptographic algorithms are developed to improve data security.
Simulation of complex quantum particle systems to predict their behaviour before physical design.
Present and Future Availability
QPU development is accelerating in 2025 due to traditional computing demands. Tech giants D-Wave Systems, Google, IBM, Intel, IQM, Nvidia, QuEra, Pasqal, and Rigetti Computing are developing QPUs. IBM has achieved “quantum utility” (reliable, accurate outputs beyond brute-force classical simulations) and is pursuing “quantum advantage” (outperforming classical supercomputing).
However, serious challenges remain. Early QPUs have low qubit coherence and significant error rates due to noise. Scalability constraints limit useful uses. Software tools for building, testing, and debugging quantum algorithms can also be improved.
Commercial QPUs are appearing, but they may take time to become generally available. QPUs will likely be used only by government labs and large public cloud companies that offer quantum computing as a service due to their environmental requirements, which include powerful refrigeration systems, vacuums, and electromagnetic protection to chill qubits close to absolute zero. The QPUs’ specialised computing skills are not needed, hence they should not be integrated into cellphones or home PCs.
#QuantumChip#QuantumProcessingUnit#qubits#physicalqubits#quantumcomputing#superconductingqubits#NeuralProcessingUnit#CentralProcessingUnit#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Here’s how Windows 11 aims to make the world safe in the post-quantum era
Monday’s update bundles new post-quantum computing algorithms selected by the US Department of Commerce’s National Institute of Standards and Technology, or NIST, in its yearslong drive to find replacements for RSA and elliptic-curve cryptosystems. The new algorithms are the latest to be added to the list of FIPS, a NIST-endorsed list of standards for ensuring guaranteed levels of security and…
0 notes
Text
CSCE 1030: Homework 4
BACKGROUND INFORMATION: A cryptosystem is a system for encryption and decryption. Encryption, also called encoding or enciphering, involves changing the original message into a secret message, while decryption, also called decoding or deciphering, involves just the opposite – changing the secret message back into its original readable form. In cryptography, a plaintext file is a file containing…
0 notes
Text
The Trump Effect on Crypto: Disruption, Deregulation, and Digital Gold
Donald Trump and the Crypto verse: A Difficult Connection
Politics and cryptocurrencies have been growing more closely in the last few years. Few world leaders have generated as many discussions and interest inside the crypto-verse as past United States ones. President Donald J. Donald Trump. His impact on this fast-changing digital scene is complex and formed by his policies, public comments, and general ideological positions. Some people view him as a polarizing personality whose speeches frequently generated doubt for blockchain pioneers; others consider him a disruptor who unconsciously aided the growth of decentralized finance (DeFi). The blog examines how Donald Trump's words and actions have affected the cryptosystem, examining both direct and indirect effects objectively.
With Donald Trump: Ambiguity Meets Finding
One could best characterize Donald Trump's attitude towards cryptocurrencies as ambivalent. He hardly mentioned Bitcoin or other digital assets head-on throughout his term from 2017 to 2021. Still, his remarks were quite derogatory whenever he did refer to them. Several mainstream economists echoed Trump's criticism of Bitcoin from July 2019, saying it was "based on thin air" and devoid of inherent value—among other things Trump tweeted he was "not a fan" of Bitcoin. He was also doubtful of Facebook's suggested Libra project, now Diem, since he worried it might weaken the U.S. dominance by the U.S. dollar.
Trump's administration acted indirectly favorably to the crypto-verse despite this negative feedback. Under his direction, the Office of the Comptroller of the Currency (OCC) issued guidelines authorizing federally chartered banks to maintain crypto assets. This choice was a critical turning point for institutional acceptance since it gave mainstream financial firms credibility to use digital money. Such a clear regulatory framework opened opportunities for creativity since businesses including Coinbase and Kraken could grow their businesses free of legal uncertainty.
Furthermore, those in favor of devolution responded to Trump's focus on free-market concepts and deregulation. Many libertarians and technology lovers drew connections between his anti-establishment attitude and the fundamental principles of blockchain technology—transparency, autonomy, and resistance to centralized control. By supporting less government involvement in some industries, Trump unwittingly fell in line with values treasured by early cryptocurrency users.
The ripple effects of trade wars and economic policies.
Particularly his trade battles and financial approaches, one cannot talk about Trump's influence on the crypto verse without considering his economic policies. Significant instability in world markets followed Chinese goods being tariffed and increasing friction with Beijing. Investors seeking shelter from geopolitical upheavals turned to alternative value stores including gold and Bitcoin. As a result, Bitcoin has experienced significant value spikes during periods of heightened volatility, further cementing its reputation as "digital gold."
Moreover, Trump's fiscal stimulus policies and tax reductions helped to raise inflationary pressures, therefore indirectly driving demand for cryptocurrencies. Debased by too much money printing, fiat currencies lose buying power, people started looking into decentralized options offering deflationary characteristics. Many individuals who are wary of central bank policies find this particularly exciting. Bitcoin's fixed supply limit of 21 million coins.
It is to be noted that Trump's abrasive style of foreign policy also affected the worldwide acceptance of digital currencies. Countries the U.S. targeted. Countries like Iran and VZ dug into blockchain technology ideas to go around sanctions. China's efforts to curb domestic crypto operations also pushed entrepreneurs to move to more crypto-friendly areas, hence hastening the decentralization of the sector.
Institutional acceptance as well as regulatory fights
Though the Trump administration established some foundation for regulating cryptocurrencies, it also created seeds of conflict across the field of regulation. Clashes over jurisdictional power among organizations including the Securities and Exchange Commission (SEC) and the Commodity Futures Trading Commission (CFTC) have been disorientating for market players. In sectors including initial coin offerings (ICOs) and stablecoin releases,the lack of effective supervision hindered progress.
Still, the foundation set during Trump's presidency opened doors for further changes. Under his watch, approval of Bitcoin futures trading on venues like CME Group came, hence showing rising acceptance of digital assets within conventional finance. Further, the selection of key OCC positions for pro-crypto personalities including Brian Brooks indicated a desire to interact with new technologies.
After he left office, Trump's effect kept forming the the discussion regarding the adoption of institutions. Reflecting a larger corporate interest in Bitcoin, strong support from tycoons like Elon Musk and MicroStrategy CEO Michael Saylor is part of a more general trend a movement that started to pick up speed under Trump. These changes most emphasize the continuous influence of policies chosen when he was in power.
The common assertion is populist attraction.
Beyond policy details, Trump's personality significantly influenced how people viewed cryptocurrencies. Known for his adept use of social media, he realized how stories could help to change public opinion. Whether on purpose or not his criticisms of Bitcoin attracted notice to the asset class and started discussions among ordinary Americans who would otherwise have been ignorant.
Trump's populist appeal connected with parts of the people let down by centralized governments and Wall Street élites. This view fits nicely with the ethos of the crypto-verse, where decentralization and democratization are core ideas. Even if they differed with him on other issues, grassroots campaigns supporting financial independence resonated with Trump's opposition to the establishment.
Still, Trump's contentious character also darkened the crypto use. Critics contend that his caustic comments and unpredictable behavior brought needless volatility into already unstable markets. His tweets, for instance, often caused asset values to swing sharply, thus emphasizing the sensitivity of investor trust in emerging sectors.
Aspiration: Legacy and Lessons Learned
The legacy of Donald Trump's influence is still a much-debated issue as the crypto verse advances in sophistication. On one side, his administration's work to define regulatory structures and support free-market ideas helped to validate digital assets. Conversely, his belligerent attitude and inconsistent message raised questions about whether safe havens made cryptocurrencies were still valid over the long term.
Going ahead, legislators should carefully balance consumer protection with innovation encouragement. The insights attained from Trump's administration highlight the need for prudent regulation, clear communication, and international cooperation. The crypto verse can only realize its complete potential as a transcendent power in the world economy through these means.
Finally,
The influence of Donald Trump on the crypto verse shows how closely politics and technology are intertwined. Regardless if seen as a spur for transformation or a cause of instability, his administration certainly had a significant impact on the development of digital currencies. His deeds will keep rocking this dynamic sector down the road from legislative benchmarks to changes in prevalent attitude to define its path of travel. One thing is certain: the interaction of leadership and creativity will be a defining aspect of our digital era as stakeholders negotiate the complexities of this constantly changing terrain.
Knowing the subtleties of Trump's influence helps us to see the issues and chances the crypto verse currently presents. This point in history offers much to learn from whether you are a long-time investor, a curious observer, or a strong supporter of decentralization—and much to expect as the narrative evolves.
Even a small tip goes a long way!
ETH: 0x788571C4c836ec733a72ff84c626BF7F20736d76
1 note
·
View note
Text
The Future of P2P Crypto Exchange
Since the launch of Bitcoin in 2009, the world of cryptocurrencies has not stopped evolving, establishing itself as a key pillar of economic and monetary transformation, and this leads us to the question: what does the future of cryptocurrency look like?
Peer-to-peer exchange or pair-to-pair exchange is one of the most important developments that occurred after the popularity of cryptocurrencies. It is a fusion of cryptocurrency-specific decentralization with digital connectivity, rather than relying on centralized entities, making it the cryptosystem of future trading exchanges.
In this article, we will talk about various topics such as the future of cryptocurrency and the future of cryptocurrency exchange development.
Direct Trading Empowerment: Benefits and Challenges of P2P Crypto Exchange
Peer-to-peer trading represents the future of crypto exchanges. Thanks to all the advantages it offers and all the challenges it has successfully overcome, let's look at some of its advantages and what the future holds for crypto exchanges:
Total Control: Traders have absolute control over their transactions without the intervention of a central exchange platform. This guarantees complete autonomy over the movement of their assets.
Cost savings: Transaction fees are usually lower on P2P platforms compared to centralized exchanges, allowing users to save on exchange costs.
Global access: Traders can trade assets with users around the world, eliminating geographical restrictions. This is one of the main indicators and gives us an idea of what the future of crypto will look like.
Social interaction: P2P exchanges encourage interaction between traders and create dynamic communities and learning opportunities.
Asset diversity: P2P platforms often offer a diverse selection of digital assets for exchange.
Security and trust: Due to create a decentralized crypto exchange nature of trading, traders must pay attention to the security of transactions and the reputation of their counterparties to avoid fraud.
All these advantages add up to an idea of what the future of cryptocurrency is and what the future of cryptocurrency will be. And I can tell you that this is just the beginning, the development is still underway and people are starting to understand its true potential as an opportunity to make more money or as a tool that will replace their traditional banking system.
The development of P2P trading
What does the future of cryptocurrency look like and what does future trading look like on Binance, Cryptomus or other platforms? In this part, we will answer these two questions and see together what the future holds for cryptocurrency.
At the beginning, cryptocurrency trading took place mainly on platforms where users had to entrust the management of their transactions to a third party. However, this approach had limitations, especially in terms of security, control and confidentiality, so the cryptocurrency of the future can replace the traditional system or at least become a direct competitor.
This gave rise to the idea of a secure P2P platform where it will be possible to conduct business in a safe and easy way and successfully exchange cryptocurrencies all over the world.
The potential of P2P exchanges
Since its inception, P2P exchange has not stopped evolving from platform to platform, creating a new market and little by little more and more people are accepting cryptocurrencies, which increases the need for exchange platforms. So what does the future of cryptocurrencies look like? Let's analyze what the future of crypto exchanges may look like in the next few years. P2P exchanges are more secure nowadays with security protocols such as KYC and 2FA, and on top of that, they have really created a new way of paying and transferring money. It will soon give rise to a completely new economic system that will completely change the world.
Traders can benefit from reduced transaction fees compared to creating a centralized exchange. This cost saving is particularly attractive for traders who transact frequently. Furthermore, P2P exchanges open the door to a greater variety of digital assets and global accessibility by removing geographical barriers, and this answers the question of what the future holds for crypto exchanges.
Innovations and trends shaping the future of P2P crypto trading
Let’s look at the innovations that P2P brings us and what the future of crypto looks like:
Integration of decentralized payments: Payment technologies facilitate P2P transactions by eliminating intermediaries and speeding up processes.
Decentralized Finance (DeFi): The rise of DeFi allows users to access financial services such as loans, bonds, and exchanges without going through traditional institutions.
Side-chain technology: Side-chains parallel to the main blockchain offer faster and cheaper transactions, thus improving the efficiency of P2P trading.
Artificial Intelligence (AI): What will the future of cryptocurrency look like without the integration of AI? enables real-time analysis of market data and provides traders with valuable information for informed decisions.
Increased security: P2P trading platforms prioritize security and take measures to protect users’ assets and prevent fraudulent risks.
The future path of P2P crypto trading
P2P trading comes with challenges. Security remains a major concern as transactions are conducted directly between users. Traders should be alert to potential scams and employ strict security practices.
What does the future of cryptocurrency look like if all these challenges are overcome? As I said in the previous part of this article, we can see all these challenges disappearing and giving way to a world where cryptocurrencies and seamless trading on P2P platforms have replaced the traditional banking system. Let's take the example of the P2P exchange Cryptomus, which offers fee-free trading and high-security protocols.
P2P Exchanges: Redefining the Landscape of Cryptocurrency Trading
P2P exchanges are redefining the cryptocurrency trading landscape by providing users with a decentralized and direct alternative. But with all this in mind, what does the future of cryptocurrency look like? This empowerment allows traders to take full control of their transactions and trade assets with complete confidentiality. However, it is crucial to remain aware of the potential challenges and take steps to overcome them.
The Power of Direct Transactions: The Role of P2P Exchanges
The role of P2P exchanges is that they eliminate the middlemen and provide a more transparent and personalized trading experience. However, to take full advantage of them, users must always be informed and always vigilant and cautious when choosing their platform, as well as be responsible in their interactions on P2P platforms.
In this article, we have seen what the future of cryptocurrency looks like and that it has the potential to transform cryptocurrency trading by giving users direct control over their transactions. However, with this comes challenges that require smart approach. As the trading landscape evolves, P2P exchanges will continue to play a major role in empowering traders and redefining the way digital assets are traded.
0 notes
Text
ID. paragraph from the Brephos II loretab that reads:
She and her fraternal twin never answer each other's questions directly. Mara is cool with this because she feels like words are a very bad system of encryption, and that if you really want to communicate with someone, you must develop your own special one-to-one cryptosystem. The ideal statement, Mara feels, would be indecipherable to anyone but the person it's spoken to—and even then, only if they know you are the one speaking.
End ID.

most normal woman in the system
211 notes
·
View notes
Text
Quotes about "Long-term Thinking
"America would be a better place if leaders would do more long-term thinking." Wilma Mankiller +++++++++++++++++++ "Middle-income countries need to attend to the education of their poorest people to build their economies and ensure long-term stability. "Julia Gillard +++++++++++++++++++ "Long-term unemployment is particularly costly to those directly affected, of course. But in addition, because of its negative effects on workers' skills and attachment to the labor force, long-term unemployment may ultimately reduce the productive capacity of our economy. " Ben Bernanke ++++++++++++++++++ "You've got a lot of very, very smart people standing by waiting for somebody else to do the work. Not a recipe for long-term solvency in my opinion. " Mike Rowe ++++++++++++++++++ "There has been a great challenge in improving educational achievement. It's a long-term issue, not a short-term one. It includes everything from getting more parents involved to addressing issues of poverty and improving what happens in the classroom. " Julian Castro ++++++++++++++++++ "If you are designing cryptosystems, you've got to think about long-term applications. You've got to try to figure out how to build something that is secure against technology in the next century that you cannot even imagine. " Whitfield Diffie ++++++++++++++++++ "Today people who hold cash equivalents feel comfortable. They shouldn't. They have opted for a terrible long-term asset, one that pays virtually nothing and is certain to depreciate in value. " Warren Buffett ++++++++++++++++++ "As more and more Americans own shares of stock, more and more Americans understand that taxing businesses is taxing them. Regulating businesses is taxing them. They ought to be thinking long-term about their ownership, not just their income, and that they should pay taxes on capital, as well as taxes on labor." Grover Norquist ++++++++++++++++++ "Capitalism is a wonderful economic engine, but it assigns little value to long-term projects or societal problems."George M. Whitesides ++++++++++++++++++ "It's difficult to make your clients understand that there are certain days that the market will go up or down 2%, and it's basically driven by algorithms talking to algorithms. There's no real rhyme or reason for that. So it's difficult. We just try to preach long-term investing and staying the course. " Warren Stephens ++++++++++++++++++ "It's a lot easier to see, at least in some cases, what the long-term limits of the possible will be, because they depend on natural law. But it's much harder to see just what path we will follow in heading toward those limits."K. Eric Drexler ++++++++++++++++++ "While natural disasters capture headlines and national attention short-term, the work of recovery and rebuilding is long-term. " Sylvia Mathews Burwell ++++++++++++++ "The market is a brilliant system for the exchange of goods and services, but it doesn't protect the environment unless it's regulated, it doesn't train your workforce unless it's regulated, and it doesn't give you the long-term investment you want. " Ken Livingstone
0 notes
Text
Why is Authenticity Key in Crypto Influencer Marketing?

Why will some crypto influencers resonate so much with their audience, while others fail miserably? What is the secret ingredient of making particular voices stand out amidst the crowd? It might just surprise you: it is not about dazzling graphics or complex jargon but something much more basic – authenticity. Let's know more about it!
The Power of Genuine Voices in Crypto
The need for connections arises in a world that feels digitized, complex, and full of digital currencies and blockchain technology. People want to get information from experiences related to real people, who feel their anxiety and can talk to them face-to-face. Here's where authentic crypto influencers stand out.
Authentic influencers do not repeat a lot of information. Instead, they tell from their own experiences, with both positive and bad situations. They also often admit if they do not know something; they are not afraid to show that they are learning. This helps build trust between themselves and their audiences.
Why Authenticity Matters in Crypto Marketing?
The crypto world moves fast. New coins, technologies, and regulations pop up all the time. In this ever-changing landscape, people need trustworthy guides. They want influencers who will give them the straight facts, not just hype up the latest trend.
Authentic influencers do more than just promote products or services. They educate their audience, helping them understand the complex world of cryptocurrency. This education builds a stronger, more engaged community around crypto projects.
The Risks of Inauthentic Influencer Marketing
The worst happens when fake influencers diffuse the wrong information among people. Due to such biased or half-baked information, one might make ill-advised investments in inappropriate assets. This could eventually lead to financial losses and erosion of trust in the entire cryptosystem.
Inauthentic marketing can also harm your brand reputation. If an influencer is found dishonest or promoting scams, they automatically become a bad rep for the companies they deal with. In extreme cases, this can attract lawsuits and regulatory attention.
Building Trust Through Authentic Content
So how do authentic influencers build trust? They do it through consistent, honest communication. They share their real thoughts and feelings about crypto projects, even when those opinions aren't entirely positive.
Authentic influencers also engage with their audience. They answer questions, address concerns, and participate in discussions. This two-way communication helps build a strong, loyal community around them.
The Role of Transparency in Crypto Influence
Transparency is the essence of authenticity in a crypto influencer marketing agency. It is open to partnerships, sponsorships, and personal investments. The more open influencers are about their relations to crypto projects, the more competent their audience will be.
Transparent influencers also give out methods of research. They reveal how they rank crypto projects as well as what things they consider valuable. These processes have enabled individuals to discover things for themselves and, in turn, empowered them with the ability to carry out their research.
Balancing Promotion and Education
Probably the biggest dilemma for crypto influencers is finding the right balance between promotion and education. Authentic influencers do not promote a product; they add value to their audience by educating them and showing them insights.
For instance, this can manifest by developing in-depth guides on blockchain technology or breaking down complex concepts in crypto into easily understandable pieces. Niche education allows an influencer to create a more knowledgeable and engaged audience.
The Impact of Authentic Influencers on Crypto Projects
When crypto projects work with authentic influencers, they see better results. These influencers can explain the project's benefits in a way that resonates with their audience. They can also honestly address concerns and skepticism, which builds credibility for the project.
Authentic influencers also tend to attract a more committed audience. Their followers are more likely to stick with a project long-term, rather than just jumping on the latest hype train.
Choosing the Right Influencers for Your Crypto Project
Selecting the right influencers is crucial for successful crypto marketing. Look for influencers who align with your project's values and have a genuine interest in your technology. Their enthusiasm will come across as authentic to their audience.
Consider working with a crypto marketing agency to find the right partners for your project. These agencies have connections with a wide range of influencers and can help match you with voices that resonate with your target audience.
The Future of Authentic Crypto Influencer Marketing
As the crypto industry matures, the demand for authentic voices will only grow. People are becoming more savvy about influencer marketing and can spot insincerity from a mile away. The influencers who will thrive are those who prioritize honesty, transparency, and genuine value for their audience.
For crypto projects, this means focusing on long-term relationships with influencers rather than one-off promotions. It means giving influencers the freedom to share their honest opinions, even if they're not always 100% positive.
Measuring the Success of Authentic Influencer Campaigns
How do you know if your authentic influencer marketing is working? Look beyond simple metrics like follower counts or engagement rates. Pay attention to the quality of conversations happening around your project. Are people asking thoughtful questions? Are they showing a deeper understanding of your technology?
A crypto marketing agency can help you track these more nuanced metrics and adjust your strategy accordingly. They can also help you identify influencers who are genuinely resonating with your target audience.
Final Words
In the fast-paced world of cryptocurrency, authenticity stands out. It builds trust, fosters community, and drives real engagement. For crypto projects looking to make a lasting impact, partnering with authentic influencers is not just a good strategy – it's essential.
Remember, in crypto influencer marketing, honesty and transparency are your most valuable assets. By prioritizing authenticity, you're not just promoting your project – you're contributing to a more trustworthy and sustainable crypto ecosystem.
Whether you're a crypto project looking for influencers or an influencer yourself, always strive for genuine connections and real value. Your audience will thank you for it, and your success will be all the more meaningful.
0 notes