#cyber threat investigations
Text
Ankura Cyber Threat Intelligence Bulletin: August - September 2022
Ankura Cyber Threat Intelligence Bulletin: August – September 2022
Over the past sixty days, Ankura’s Cyber Threat Investigations & Expert Services (CTIX) Team of analysts has compiled key learnings about the latest global threats and current cyber trends into an in-depth report: The Cyber Threat Intelligence Bulletin. This report provides high-level executives, technical analysts, and everyday readers with the latest intel and insights from our expert…

View On WordPress
#ankura#business#CITZ#cyber threat intelligence bulletin#cyber threat investigations#cyber threats#Cybersecurity#data privacy#expert services#Human Trafficking#law enforcement#legal
0 notes
Text
Yul Edochie Offers N1million Reward to Catch Online Bullies Threatening His Family!
Yul Edochie Offers N1million Reward to Catch Online Bullies Threatening His Family!

View On WordPress
0 notes
Text
Navigate Cyber-security With Insights Of Private Investigator
Explore the cybersecurity threats and solutions with a private investigator in Ontario. Understand evolving cyber risks in Canada and proactive measures for protection. Discover how Private Investigators address cybersecurity challenges to safeguard businesses and individuals. To know more watch the full video or visit the website today for excellent expert advice.
#investigation hotline#forensic investigators#private investigation agency#private investigators finding someone#investigators in canada#forensic investigator canada#private investigator#cybersecurity#cyber threats
1 note
·
View note
Text
wtf is going on with cellbit - by a brazilian law major student
hey besties ever since the day cellbit released that PDF i’ve been keeping up with his shit bc as a law student (only two years to go!!!!) in brazil it’s kinda really interesting to see how it goes, specially since i don’t think we’ve ever had this sort of judicial action taken by an internet celebrity, like, ever. so i’ve decided to kinda explain what’s going on. if anyone has any questions after this i’d be really up to talk about it i love talking about law 🫶 xoxo let’s start. also sorry if anything reads weird english is not my native language okay
for those who don’t know, very recently, a judicial action taken by cellbit has made public. in this action, he’s suing over 200 people for the crime of defamation.
the action was taken to court in january, but it was under what we call “secret of justice”, which means only cellbit himself and twitter’s lawyers had access to it. now that there have been decisions by the judge and everything, the process’s been made public.
basically, cellbit started an action against twitter (NOT THE PEOPLE WHO COMMITTED THE CRIME YET), citing a little over 200 tweets that accused him of crimes like SA, psychological abuse, pedophilia, and others. all of those are real crimes in brazil — and accusing someone of committing crimes (specially as awful crimes as those) without proof is a crime in itself (defamation). he claimed that the tweets were harmful to his honor, mental health, and reputation, besides categorizing as defamation, since there’s no investigation going on against him for all these infractions he’s being accused of.
with that, he asked twitter to delete all the tweets, and to provide him with the personal information of said twitter accounts so he can sue them directly for defamation. he did these requests through something called “tutela cautelar”, which means the judge gets to decide whether or not twitter has to do these things before proof production and proper investigation, since, if twitter doesn’t do those things, the damage to his honor and reputation will be ongoing + he won’t be able to sue the proper people in time.
the judge conceded to his requests, and twitter has already deleted all the tweets. the main discussion going right now is wtf do they do about the international accounts — does our law apply to them? what’s gonna happen? we don’t know yet. that’s being discussed in court for the moment and, considering brazilian courts, it might take quite a while.
so, yeah, all those people aren’t being sued YET. but they will, probably somewhat soon.
it’s also important to mention that this lawsuit is from january and was only now released to the public. there’s probably a lot more coming after the whole fiasco that led him to releasing his statement, including a lawsuit against his ex herself.
now, other topics — could he sue other twitter accounts for cyber bullying or death threats? probably, but my personal opinion is that suing for defamation and focusing on accounts that were accusing him of having committed crimes was a much better move because it’s a much stronger case.
there’s very little room for discussion when a person has outright said “cellbit committed this crime”. death threats have more room for discussion: “oh, but they’re hundreds of miles away, it wasn’t a serious threat”, “they didn’t mean it”, “it was a joke”. same thing goes for cyberbullying: it can get too subjective.
defamation isn’t subjective. you accuse someone of a crime they didn’t commit? boom, defamation, at least according to our laws. so, to me, personally, it makes a LOT of sense for his lawyers to focus on that: he’s a LOT more likely to win than if he was suing for cyberbullying, threatening, insult, or any of that. also, he’s a lot more likely to win FASTER.
when he gets to sue the actual people who committed the crime, that is. for now, he’s only requested twitter to give him the necessary information to get to these people, which i think they’ll very likely be obligated to do. there are digital data protection laws in brazil, but a crime is a crime. digital data protection isn’t gonna protect you from the court.
another thing: LGPD (brazil’s general law of personal data protection) forces all social media companies to keep records of all the content posted by their users for AT LEAST six months. many companies keep it for way longer. that’s a law created for judicial purposes, in case something published to twitter, facebook, or instagram needs to be analysed by a court. that’s why even tho twitter has deleted the tweets, they still have them, and why it doesn’t matter if the people responsible are deleting the tweets, the accounts, the fucking app itself. the records are still there, and they will be used judicially.
i think that’s the overall for the situation, but i’m willing to answer any questions and to discuss it if anyone wants to! i’m a big law enjoyer. also personally i think cellbit is so fucking right for this like YEAH people don’t get to commit fucking crimes on twitter and get away with it. really interested in how this is gonna go law-wise, but in general also really glad to see someone take action like this.
849 notes
·
View notes
Text
Daily update post:
The IDF has been releasing a lot of incriminating intel on the Shifa hospital in Gaza being used by Hamas. There's footage of a drone going into a terror tunnel underneath it.
youtube
There's pics of the weapons found there. There's the results of an investigation into the fate of 19 years old Noa Marziano, who was kidnapped by Hamas, lightly injured in an IDF strike, which killed the terrorist who was guarding her, another terrorist took her into the basement at the Shifa hospital, and killed her there, then Hamas tried to stage "evidence" that she was killed in the IDF strike. And most recently, there's CCTV footage showing Hamas bringing in hostages (one man from Nepal and one from Thailand) into Shifa, with the terrorists being armed, and all of this was done in broad daylight, and right in front of the medical staff.
Of course anti-Israelis, including the Hamas, said it was just bringing hostages in to get treatment.
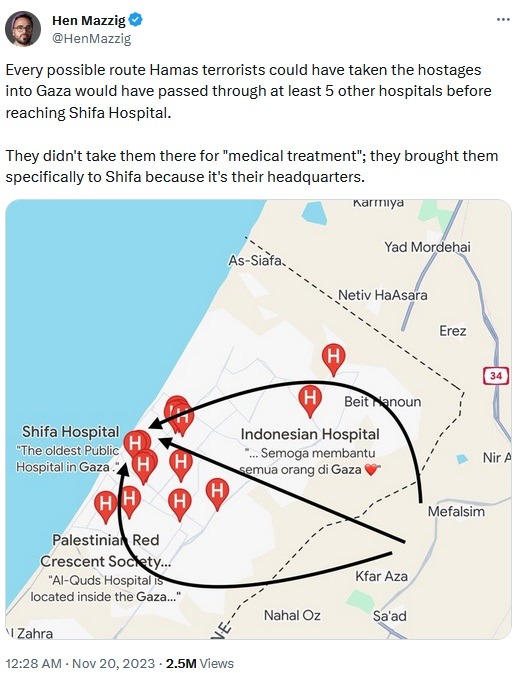
But here's the thing, Shifa is on the Western side of Gaza, while Hamas breached the Israeli border in the east. On the way between the border and where this hospital is located, there are plenty of other medical facilities on the way. Any of them would be preferable if the goal was to give the hostages medical treatment as soon as possible. But they took these kidnapped men all the way to Shifa instead. Because that's Hamas' headquarters.
I've known for years, like most Israelis, that Hamas is using medical facilities like hospitals and ambulances for its terrorist activity. This evidence does not surprise me. But I think it didn't really sink in for me until yesterday, just how many people knew and kept silent. I'm not even talking about the Gazan medical staff. They live under the constant threat of Hamas, I don't blame them. But the UN, the Red Cross, all of those "noble" NGO's operating from Gaza (and getting a lot of donations to do so), all of those foreigners with access to Gaza, who knew the situation on the ground, and chose to lie, and continued to do so even after the Oct 7 massacre... WTF is wrong with these people? By keeping quiet, they endangered both Israeli civilians (who Hamas could continue to target with impunity when operating from inside medical facilities), and Palestinian ones that Hamas endangered by using them as human shields.

Who is going to hold these people accountable? Who is going to make them pay for their complicity in endangering so many people, millions altogether, on both sides of the border, so that they never dare do this again?
Have ANY of them come forward, apologized, taken responsibility for their long complicity? I've heard of no such thing. In fact, I assume that they will only raise the volume of their accusations against and vilification of Israel, to drown out the voices asking these questions.
In this tweet you can hear an interview (starting at around 35 seconds in) with one of the few foreign doctors, who had worked at the Shifa hospital, and who after Hamas' massacre, did not come forward with his testimony about what he'd seen and experienced while he was there, but did agree to have it recorded once he was asked to. If Hamas is finally taken down, we might get to hear more of these, and I guess... better late than never.
In the midst of all of this, Israel has helped evacuate babies from the Shifa hospital to ones in Egypt, and the equipment to established a second Jordanian field hospital has entered Gaza today.
Israel continues to be attacked by Iran-funded rockets from the south, from the north by Iran-funded Hezbollah, as well as from Syria, by the Iran-funded Houthis in Yemen, by independent terrorist attacks, and online from cyber attacks, by Iran-funded and even Iranian hackers. I kind of tend not to talk about these that much, because they're on going. It's happening every single day, and Israel, in the middle of the fight to destroy Hamas, has to also defend its people on these fronts.
The anger and hurt over the denial of rapes that happened as part of Hamas' massacre continues, and more people are trying to speak up against it:
youtube
This is 15 years old Itay Cohen.

He's a triathlete, and was in the middle of a training session, cycling in the south, when Hamas terrorists shot him. He was taken to a hospital without any family by his side, because his parents were locked inside a bomb shelter in their kibbutz. Itay took a bullet to the head, and lost his eyesight, but somehow survived. So did his parents. He vowed he won't stop training, despite his new disability. This terror attack has changed countless lives, from among the survivors as well.
(for all of my updates and ask replies regarding Israel, click here)
#israel#israeli#israel news#israel under attack#israel under fire#israelunderattack#terrorism#anti terrorism#antisemitism#hamas#antisemitic#antisemites#jews#jew#judaism#jumblr#frumblr#jewish
102 notes
·
View notes
Text
Kamala Harris, by most accounts, has learned a great deal by serving as vice president to U.S. President Joe Biden, who is the most experienced U.S. leader on foreign policy since President George H.W. Bush.
“Kamala Harris is Joe Biden’s protégé. He trained her,” said California Lt. Gov. Eleni Kounalakis, a friend of Harris who has served as ambassador to Hungary.
But it’s also clear that Harris has created her own path on foreign policy—and that she represents the next generation of national security experts steeped in newer, high-tech threats that the Cold War generation represented by Biden is less familiar with. These encompass an array of cyber threats, including election hacking and surveillance from abroad, allegedly including from state-run companies such as China’s Huawei; threats from space, such as reported Russian or Chinese plots to disable GPS systems; and over-the-horizon risks from artificial intelligence and quantum computing.
In her speech at the Democratic National Convention accepting the nomination Thursday night, Harris briefly mentioned the high-tech threat while affirming that she would prove a tough commander in chief who would “ensure America always has the strongest, most lethal fighting force in the world.”
“I will make sure that we lead the world into the future on space and artificial intelligence; that America, not China, wins the competition for the 21st century, and that we strengthen, not abdicate, our global leadership,” she said.
Harris’s familiarity with such high-tech areas springs from her unique experience. Beginning as a freshman senator in January 2017, she had a crash course in national security issues on the intelligence and homeland security committees during a period when many new threats from abroad were emerging. Only three days after Harris was sworn in as a U.S. senator by then-Vice President Biden, the Obama administration publicly dropped a blockbuster report revealing the extent of Russian President Vladimir Putin’s covert effort to harm the electoral prospects of Hillary Clinton and promote Donald Trump in the 2016 election. This involved buying digital ads on platforms such as Facebook and Instagram and organizing fraudulent political rallies across the United States, among other intrusions.
“In order to understand how Kamala Harris approaches foreign policy, it’s important to remember she began work in the Senate in the same month that every U.S. intelligence agency declared that Russia intervened in our 2016 election,” said her former national security advisor, Halie Soifer, who started working for Harris during the first week that she entered the Senate. “She played a leading role in the intelligence committee’s inquiry given her experience leading investigations.”
But that was just the start of Harris’s immersion in newer types of threats from abroad, former colleagues said.
“That was a period when the [Intelligence] Committee was in a very different position than most of the rest of the Congress,” said Sen. Mark Warner, the current chairman of the committee, who argued that it was on the cutting edge of foreign policy by exposing threats to U.S. national security that no one else in Congress knew anything about. “It wasn’t just that we were investigating Russian election interference. We were the first ones to identify the China threat [of technological surveillance] from Huawei, and intellectual property theft,” Warner said in an interview.
Those threats continue—and not just from Russia and China. Most recently, the FBI has said it is investigating alleged Iranian cyberattacks against both the Democratic and Republican campaigns for president.
Harris had previously familiarized herself with many of these types of threats during her days as California’s attorney general and a prosecutor in northern California, where she got to know Silicon Valley well. In her 2019 memoir, The Truths We Hold, Harris wrote how “shocked” she was by the state’s backward voting technology when she first took office, and how vulnerable it was to hacking.
“The California Department of Justice maintains the entire criminal justice data system for the state and for many many localities. So we worry constantly about protecting that from hackers,” Harris’s former Senate chief of staff, Nathan Barankin, told Foreign Policy. “When you’re attorney general, and you’re from California, which is very tech-heavy, you come into the job in the Senate and these committees already sensitized to not only the great potential and upside of technology, but its risks too. So when things came up like Huawei, quantum computing, or the manipulation of social media by foreign states trying to influence the election, she was already there.”
By the accounts of her intelligence committee colleagues, Harris swiftly mastered arcane subjects such as Russian election influence operations in cyberspace and Chinese intellectual property theft. She also proved to be a razor-sharp, if occasionally grating, questioner of witnesses, deploying her long experience as a prosecutor and attorney general in California.
“She was a force. She signaled early on that she was willing to do the hard work of oversight,” said Democratic Sen. Ron Wyden of Oregon, the longest-serving member of the committee. “She got more real questions into her five minutes [of questioning] than just about anybody. She made a point of staying away from speeches and asking tough, highly informed questions.”
“She showed that she understands the complexity of the world,” Warner said. He added: “I’m not sure my Republican colleagues would go on the record about it now, but she earned a whole lot of respect from them.”
Indeed, the Republican chairman at the time, Sen. Richard Burr, praised Harris in a 2019 Buzzfeed News article as a “quick study” and “very effective.” (The now-retired Burr, in an email, declined to confirm those comments for this article, saying, “I am not doing any interviews for the elections in November.” Several other GOP committee members who were quoted as praising Harris back then, including Sen. Marco Rubio, did not respond to a request for comment.)
It was notable that by the end of her first year in the Senate, Harris joined with fellow Intelligence Committee member James Lankford, a Republican, to sponsor one of the few bipartisan efforts to bolster the cybersecurity of voting systems. (The bill later stalled due to GOP opposition.) She also sponsored a bill to push the United States ahead of China on quantum computing. Later on, as vice president, Harris kept up the focus on high-tech threats, including from unregulated artificial intelligence, working with French President Emmanuel Macron on new initiatives on space and cybersecurity and representing the Biden administration at the Global Summit on AI Safety. She also served as head of the National Space Council and represented the United States at the COP28 climate conference in Dubai.
One reason that Harris focused on such an obscure area as quantum computing, Barankin said, was that she was concerned about “the investments and efforts that China was making to win that race. It was something she was very sensitive to in terms of how important it was for the U.S. to maintain its station in the world as the lone democratic superpower.”
“It was not uncommon for her to come into the office and outline some new technological development, even if it hadn’t been formally deployed,” said Barankin. “Being confronted with something different and new—that actually gets her engine running.”
Harris’s research into the cyber threat from Russia and other countries included a visit to Israel in November 2017, when she toured its cybersecurity hub at Beersheba. “It wasn’t a typical CODEL [congressional delegation visit],” said Soifer, the former national security advisor. “There were a lot of lessons to learn from the Israelis on cyber. After that, she used her role on the Homeland Security Committee to strengthen our cyber defenses.”
An aide to the vice president agreed that the prolonged intelligence committee probe was central to shaping Harris’s approach not just to Russia, but also to China and other autocratic states that seek to undermine U.S. power.
“She joined the committee at what was a historic moment of turbulence for the intelligence community and the country,” said the aide, a senior White House official who works with Harris and was authorized to speak only on condition of anonymity. “Her experience made her keenly aware of Russian’s malign influence activities and the importance of strong U.S. actions to deter, disrupt, and defend against such activities. That experience really enforced for her the need for strong global leadership by the U.S. You see her speaking about that now.”
It is no accident, he said, that in her speeches as vice president, Harris has repeatedly emphasized preserving the democratic “rules and norms” that keep the U.S.-led global system together in the face of efforts by Moscow, Beijing, and others to destroy it.
At a minimum, Harris’s performance during her four years in the Senate clearly undercuts many of the attacks on her by Trump and the GOP message machine that portray her as an intellectual lightweight (“not smart enough,” “barely competent” and “low IQ” are the epithets that Trump keeps using), and as an easy mark for other world leaders (she’d be a “play toy” in their hands, Trump said). Republicans—and even some Democrats—have also occasionally portrayed her as a mindless, knee-jerk liberal who’s been grandstanding for a presidential run almost since she was sworn in as senator.
Especially on the Homeland Security Committee, “some Democrats believed her pugilistic tone was mostly for show,” wrote Dan Morain, a former Los Angeles Times reporter, in his 2021 biography of her, Kamala’s Way: An American Life. “Others suspected her thirst for the spotlight was part of a long-range plan to ‘pull an Obama’ by staying just long enough in the Senate to get the credentials needed to run for president.” (Former President Barack Obama served briefly on the Senate Foreign Relations Committee before he ran.)
Harris had been warned before she even arrived in Washington that the Intelligence Committee, in particular, was not necessarily a place for an ambitious politician to go. Her fellow Californians, Sen. Dianne Feinstein and outgoing Sen. Barbara Boxer—whose seat Harris had just won—gave her a frank rundown on the pitfalls. The intelligence post, they told her, rarely yielded headlines. Most of the committee’s work was done behind closed doors, with no TV cameras in sight. It had a heavy workload, and it was the most mentally taxing assignment on Capitol Hill: Members went home every night with huge binders of material, but the subject matter was so classified they couldn’t even hire their own staffers to help figure it out.
Boxer, in an interview, said that she warned her successor of the committee’s low profile (a conversation confirmed by Harris herself in her autobiography). But Harris thought the committee would provide her some fast lessons in what was, until that point, mostly a blank spot on her resume: foreign policy. “I do think she just wanted to learn more, to know more about the world,” Boxer said. “She wanted to know about every threat out there. That committee doesn’t give you high visibility, but it certainly teaches you about what the heck is going on in the world.”
Warner added: “Remember, there are members that wouldn’t want to be on a committee where 80 percent of the meetings are in closed session. Because of that, some don’t even show up all the time. She showed up. We were the minority, and she was literally the last person to talk. But she would sit through all these sessions. She did her homework.”
Above all, Harris’s time on various Senate committees deepened her understanding of the vulnerability of U.S. democracy to both foreign and domestic threats from technology, her colleagues said. And she came to understand the threat in a visceral, very personal way, which may provide some insight into how she could be different from Biden, who learned foreign policy from a grand strategic perspective during his three decades on the Foreign Relations Committee.
Harris gradually realized there was a through line, a common theme, to what she’d been doing for much of her career as a prosecutor in California and shaping foreign policy, the new subject she was taking up as a neophyte senator, former aides said. She had spent her previous career as a district attorney and then attorney general of California dealing with the inequities and flaws of U.S. democracy, such as racial injustice in the criminal system and economic exploitation by Wall Street. Now she was faced with a high-tech plot to undermine democracy by exacerbating those same internal vulnerabilities and weaknesses.
“One of the things she found most insidious about Russia’s interference in the 2016 elections was its targeted effort to divide the United States from within,” said Barankin, her former Senate chief of staff. Or as Harris wrote in her autobiography, “Russia’s goals were to undermine faith in the U.S. democratic process.”
Harris said it was clear to her from the Senate investigation that the Russians were focused on dividing Americans over “hot-button” issues, “from race to LGBTQ and immigrant rights.” She described the moment Lankford, a fellow member of the Intelligence Committee, crossed the aisle to tell her he saw the same danger: “I’ve been listening to what you’ve been saying about race as our Achilles’ heel, and I think you’re onto something important.” (Lankford’s office did not directly respond to a request for comment.)
And now, in a kind of career twist she couldn’t possibly have imagined, Harris is running against a candidate who—though he was never shown to be colluding with Russia—is also directly threatening U.S. democracy, at least in the minds of many Trump critics. That has thrust Harris’s theme of democracy-and-freedom promotion forward in a unique way in the current election campaign, said Soifer, Wyden and other Harris supporters.
“You have to think about the moment of history when she started, in January of 2017,” Soifer said. “There was no real playbook for a situation in which a U.S. president would question our institutions and completely disregard our democracy. So not only was her experience on the [Intelligence] Committee essential for investigating the actions of a foreign adversary, it occurred at a moment that the person she’s now running against for president began to directly threaten our democracy domestically.”
And whereas Biden learned foreign policy gradually during his three decades in the Senate—dating back to the Vietnam War—“her view came in a crash course, shaped out of crisis,” especially the cyber threat from Russia, according to one former senior aide who spoke on condition of anonymity. “She had to become an actor right away in mitigating against the threat. So today, even as it relates to the way she talks about preserving democracy and norms and the rule of law, she’s infusing her own experience, making it distinctly her own.”
28 notes
·
View notes
Text
Israel’s National Cyber Directorate (INCD) stated on Thursday that Iran is running a cyber campaign against members of the Israeli delegation arriving in Paris for the 2024 Summer Olympic Games.
In its investigation, the INCD revealed that Iranian hackers have created social media channels and published personal information about the Israeli team members to send them threats. The INCD is working with the Cyber Unit of Israel’s State Attorney to shut them down.
As part of their anti-Israeli campaign, the hackers reportedly pose as the French organization GUD. INCD authorities are continuing to coordinate both with the Israeli Olympic Committee and the Security and Emergency Department of the Culture and Sports Ministry to make sure that Israel’s athletes and other delegation members remain safe during the Paris international sports competition.
INCD Dir.-Gen. Gabi Portnoy said Iran was exploiting the Olympics to terrorize Israel.
“Iran is exploiting an apolitical international sporting competition to promote digital terrorism against Israel and its right to participate in these competitions,” he said.
Israeli Culture and Sports Minister Miki Zohar echoed Portnoy’s remarks.
“We are witnessing attempts by the Iranian regime to intimidate Israeli athletes and carry out psychological terror against our amazing delegation. We are here in Paris, continuing with full force, and nothing will stop us,” he said.
“Our athletes are more prepared and determined than ever to achieve great results, and our security apparatus is ready for any scenario. We will not relent until we topple the Iranian regime,” Zohar added.
French Prime Minister Gabriel Attal said on Thursday that while cyberattacks on the Paris Olympics are inevitable, France will do all it can to limit the effects of such attacks.
“We are a target. There will be cyberattacks. The key thing is to limit their impact,” Attal told reporters at the headquarters of France’s ANSSI software security agency.
In the meantime, Israeli tourists in Paris face escalating threats.
On Sunday, Israel’s National Security Council (NSC) advised Israeli nationals traveling to the Olympic Games in Paris to exercise increased caution due to anti-Israel threats, warning that it believes Iranian-backed terror organizations “are seeking to carry out attacks on Israeli/Jewish targets around the Olympics.”
Earlier this week, a masked man with a Palestinian Authority flag on his shirt threatened the "Zionist regime" participating in the Olympic Games, saying, “Rivers of blood will flow through the streets of Paris.”
Despite the threats, the Israeli delegation traveled to Paris on Monday with their heads held high and the support of the entire nation.
“We feel like emissaries of the State of Israel – our athletes, every one of them are here to achieve their dreams, but there is another layer, of a national mission,” the President of the Olympic Committee of Israel Yael Arad said ahead of the flight to France.
French authorities have reportedly dispatched around 1,000 elite anti-terrorist officers to provide security and a "ring of steel" for Israel’s Olympic athletes. The first competition involving Israelis, a soccer match between Israel and Mali on Wednesday, passed without major security incidents, despite the presence of anti-Israel activists who held Palestinian Authority flags and demonstrated against the Jewish state. Some activists wore “Free Palestine” t-shirts and booed when the Israeli national anthem, "HaTikva" (The Hope) was played before the game. Israeli players were also met with initial boos when they touched the ball during the game.
On Friday, despite heightened security, France suffered attacks targeting the country's train networks in what authorities described as "coordinated sabotage," including arson. No organization has claimed responsibility. The attacks are expected to negatively impact around 250,000 travelers today and 800,000 over the weekend.
23 notes
·
View notes
Note
Just curious...could this Sussex Squad thing turn into a legal investigation (if it's not already)? And what crimes would they be arrested for and what is the penalty?!??
The "general" stuff they do (for lack of a better word), like spread rumors about the Waleses and bully Kate's fans on social media, there's not a whole lot there. It's just seen as "coming with the territory" (also for lack of a better phrase).
Where the Sussex Squad could get into legal trouble is if or when they go after single accounts - doxxing them, dogpiling them, or escalating to death threats (or r*pe threats, threats of violence, etc.). All of that could qualify as stalking, intimidating, harassment, or incitement for violence for which there could be criminal charges levied. Depending on the severity and the jurisdiction, the penalty could range from slap-on-the-wrist fines to jail time.
Where it gets complicated is who reports these incidents and what kind of evidence or investigation there is to support the complaint. Usually the victim of a cyber crime has to report the incident (vs a bystander witness) and usually the onus on providing evidence to prove there's a case is on the victim - in most cases, the investigator (police, FBI, DHS, a lawyer) won't open a case unless the victim provides enough evidence to make it worth their time; screenshots of messages and usernames or phone numbers, IP addresses, voicemails, voice recordings. Which really sucks, but that's the grey area in a lot of cyber crime where the policies and practices are still being developed.
So for example, when Yankee Wally was doxxed and bullied off Twitter, only Yankee Wally could have reported the cyberbullying, the cyber harassment, the cyber stalking/intimidation and she would have had to provide evidence - e.g., screenshots of the tweets and the usernames/accounts who were harassing her. The rest of us wouldn't have been able to "call it in" for her. We could've helped take screenshots of any public messages she received or any posts/websites we saw where her PII published, but we most likely wouldn't have been able to report it to the FBI and have it taken seriously.
Which is why if you're ever the victim of a cyberbullying campaign, a doxxing, online harassment, it's super important you document everything. Take screenshots of all the messages you get (or see) and make sure all the identifying information is there like timestamps, usernames, account handles, and phone numbers. If you know how to get someone's IP address, grab that too. Save any voicemails or voice messages you get. If you answer a call that turns out to be harassment, document as much as you can; the number they called from, what time, what their voice sounded like, what they said. Have physical copies (printouts), electronic copies (screenshots), and backup copies.
If this is happening to you and you receive packages or letters in the mail from addresses you don't recognize, that are unusually heavy, or are leaking some kind of fluid/grease, don't open them, don't bring them inside, don't let children or pets near. Call the police to report it and follow their instructions about what to do.
40 notes
·
View notes
Text
Mark Wauck
Aug 26, 2024
I’ve been looking for something sensible to say about the arrest of Telegram CEO Pavel Durov by Macron in France. I’ve read the arguments that this is all political, directed by the fact that Telegram is one of, perhaps the, most important platforms for getting out reliable information regarding the Anglo-Zionist wars against Russia and Palestine. In other words, Durov is being pressured to submit to censorship demands, under the pretext of cooperating with criminal investigations. I find those arguments persuasive, but I’m hampered by the complexity of some of the issues involved, including matters involving international legal cooperation. This morning commenter Brother Ass provided a link to Robert Barnes discussing the matter—I highly recommend it.
However, I’d like to turn to another legal commentator, Jonathan Turley. Turley did and interview on Fox News, but still hasn’t written about the Telegram matter. Fortunately, Daily Caller has an article that provides a substantial transcript of what Turley has to say, which I’ll quote at length:
Jonathan Turley Slams ‘Global Censors,’ Says Americans Should Be Afraid After Telegram Founder’s Arrest
“So, the authorities say the app was being used for organized crime, drug trafficking, fraud, cyber bullying and promotion of terrorism. Despite all of that, you’re still against his arrest. Why?” Earhardt asked.
“I am. People need to realize what’s really going on here. We haven’t seen anything akin to a charging sheet, but it appears that he’s being arrested under these European laws that are designed to force social media companies to engage in censorship,” Turley said.
[Turley called the European] … Digital Services Act (DSA) … “one of the greatest threats to free speech that we have today around the world.”
Turley goes on to argue that, as with the previous confrontation with Elon Musk, the US—which lacks the kind of anti-free speech laws that Europe has in the DSA—is using Europe as a proxy to attack free speech and the free flow of information in America.
11 notes
·
View notes
Text
Maryland’s top utility regulator was watching the news one February morning when a headline blindsided him: Two suspects with neo-Nazi ties had been charged with plotting to take down Baltimore’s power grid.
Jason Stanek, the then-chair of the state’s Public Service Commission, said Maryland regulators were “caught flat-footed,” not hearing a word from law enforcement before the news broke — or in the months afterward. Federal prosecutors have alleged the defendants were driven by “racially motivated hatred” to try to cut power to hundreds of thousands of people in the state’s largest city, which has a predominantly Black population.
The FBI declined to comment on its communications with the Maryland commission. But Stanek’s experience is not uncommon.
A POLITICO analysis of federal data and interviews with a dozen security, extremism and electricity experts revealed that despite a record surge in attacks on the grid nationwide, communication gaps between law enforcement and state and federal regulators have left many officials largely in the dark about the extent of the threat. They have also hampered efforts to safeguard the power network.
Adding to the difficulties, no single agency keeps a complete record of all such incidents. But the attacks they know about have regulators and other power experts alarmed:
— Utilities reported 60 incidents they characterized as physical threats or attacks on major grid infrastructure, in addition to two cyberattacks, during the first three months of 2023 alone, according to mandatory disclosures they filed with the Department of Energy. That’s more than double the number from the same period last year. DOE has not yet released data past March.
— Nine of this year’s attacks led to power disruptions, the DOE records indicate.
— The U.S. is on pace to meet or exceed last year’s record of 164 major cyber and physical attacks.
— And additional analyses imply that the true number of incidents for both 2022 and 2023 is probably even higher. POLITICO’s analysis found several incidents that utilities had reported to homeland security officials but did not show up in DOE data.

According to a report on grid security compiled by a power industry cyber clearinghouse, obtained by POLITICO, a total of 1,665 security incidents involving the U.S. and Canadian power grids occurred last year. That count included 60 incidents that led to outages, 71% more than in 2021.
While that report does not break down how many of those incidents occurred in which country, the U.S. has a significantly larger grid, serving 145 million homes and businesses, with nearly seven times Canada’s power-generating capacity.
Law enforcement officials have blamed much of the rise in grid assaults on white nationalist and far-right extremists, who they say are using online forums to spread tactical advice on how to shut down the power supply.
Concerns about the attacks have continued in recent months, with incidents including a June indictment of an Idaho man accused of shooting two hydroelectric stations in the state.
But law enforcement officers investigating alleged plots against the grid don’t necessarily alert the Energy Department or other regulatory bodies.
“We have no idea” how many attacks on the grid are occurring, said Jon Wellinghoff, a former chair of the Federal Energy Regulatory Commission, which regulates the U.S. electric grid. “It looks like they’re escalating if you look at the data. But if you don’t have enough data, you can’t discern patterns and proactively work to stop these things from happening.”
Wellinghoff was FERC’s chair when an unknown sniper attacked a Pacific Gas and Electric substation in San Jose, Calif., in 2013 — an incident regulators have described as a “wake-up call” on the electricity supply’s vulnerability to sabotage.

Last year’s record number of physical and cyber disruptions to the U.S. power system included several incidents that captured public attention, such as a December shooting attack against two North Carolina substations that left 45,000 people without power for four days. The state’s medical examiner has blamed the attack for the death of an 87-year-old woman who died after her oxygen machine failed, ruling it a homicide. Nobody has been charged.
“There is no doubt there’s been an uptick over the last three years in the amount of incidents and also the severity of the incidents,” said Manny Cancel, senior vice president at the North American Electric Reliability Corp., the nonprofit body in charge of setting reliability standards for the bulk power system. He is also CEO of its Electricity Information Sharing and Analysis Center, which gathers and analyzes data from power companies.
Cancel said NERC has “seen two pretty substantial increases” in incidents coinciding with the 2020 and 2022 election cycles.
Grid attacks that led to power outages increased 71% from 2021 to 2022, totaling 55 incidents in 2022, according to a NERC briefing to utilities that POLITICO obtained. That increase was primarily due to a rise in gunfire assaults against critical infrastructure.
The largest outage reported from a physical attack early this year — which occurred in March in Clark County, Nev. — affected more than 11,000 people, according to DOE data.
But the state Public Utilities Commission was not aware of any outage due to an attack occurring that day, spokesperson Peter Kostes told POLITICO by email. That’s even though state regulations require utilities to contact the commission within four hours of a significant outage.
The state’s largest utility, NV Energy, said in a statement that it had reported the incident to local law enforcement “as soon as we learned about this incident ... so we can continue to increase our resilience against ongoing threats to the energy industry.” A spokesperson for the utility did not respond to multiple requests for comment on whether it had informed the commission.
Federal regulations also require utilities to report cyber or physical attacks to DOE, including physical attacks that cause “major interruptions or impacts” to operations.
They must also tell the department about disruptions from weather or other causes that meet certain criteria, such as those that cut off service to more than 50,000 customers for at least an hour, an uncontrolled loss of more than 200 megawatts of power, or a utility voluntarily shutting more than 100 megawatts, according to an Energy Department spokesperson. The spokesperson provided the information on the condition that they not be identified by name.
The Energy Department’s records don’t include at least seven reported physical assaults last year and this year that the Department of Homeland Security and the affected utilities said caused substantive economic damage or cut off power to thousands of customers. POLITICO found these incidents by cross-checking the department’s data against warnings issued by DHS and the FBI’s Office of the Private Sector.
DOE said the incidents may not meet its reporting thresholds.
Several of the incidents missing from DOE’s data involved clear physical attacks, based on other agencies’ descriptions. But the utilities involved said they did not report the incidents to the department because the attacks did not affect the kind of major equipment that could lead to widespread, regional power failures.
One of the incidents not found in DOE’s records cut off power to about 12,000 people for roughly two hours in Maysville, N.C., after a shooting damaged a substation in November, according to a DHS report. The FBI’s investigation into the incident is ongoing, according to the intelligence agency.
The utility affected by the incident, Carteret-Craven Electric Cooperative, reported the incident to NERC’s Electricity Information Sharing and Analysis Center, but didn’t report the attack to DOE because it was a “distribution-level” incident, said Melissa Glenn, a spokesperson for the utility. That means the outages caused by the damage would have been limited to local power customers and not lead to the wider blackouts federal regulators are most concerned with.
In another case unreported to the Energy Department, a substation owned by the East River Electric Cooperative serving the Keystone oil pipeline in South Dakota was attacked by gunfire late at night in July 2022, according to DHS. The incident caused more than $1 million in damage and forced the pipeline to reduce operations while repairs were underway.
East River co-op spokesperson Chris Studer said the utility reported the incident to local law enforcement, which brought in the FBI. East River also reported the incident to NERC and its E-ISAC, along with regional grid agencies, but said it did not report it to DOE because the attack did not affect the bulk power system.
Brian Harrell, a former assistant secretary for infrastructure protection at DHS, said in an email that utilities have too many competing agencies to report to, and suggested reporting be streamlined to NERC’s E-ISAC.
“This lack of consistency, by no fault of the utility, suggests that the numbers may not paint a complete picture,” he said.
Grid experts said these data gaps clearly indicate a lack of understanding about which agencies utilities need to report to and when.
Utilities may be using a “loophole” based on definitions of what constitutes “critical infrastructure,” said Jonathon Monken, a grid security expert with the consulting firm Converge Strategies. He was previously senior director of system resilience and strategic coordination for the PJM Interconnection, the nation’s largest power market.
There are “lots of ways” to work around DOE requirements, Monken added, but as he reads the regulation, utilities are required to report any operational disruptions caused by a physical attack.
“[I]t appears the information you collected shows that companies are still missing the boat when it comes to mandatory reporting,” he said. “Not good.”
One former FERC official who was granted anonymity to speak about a sensitive security issue said the commission also received no alerts from law enforcement officials about the planned and actual attacks that took place last year. That omission hinders agencies’ ability to respond to these kinds of events, the person said.
A spokesperson for FERC declined to comment on the commission’s communications with law enforcement.
But Cancel defended government agencies’ response to these incidents, and said federal investigators may have had specific intelligence reasons for keeping FERC and state utility agencies out of the loop.
“I’m not a lawyer or a law enforcement professional, but you had an active criminal investigation going on,” he said. “I don’t think they wanted to sort of blow the horn on that and compromise the integrity of the investigation.”
An FBI spokesperson offered no direct response to these criticisms in an email, but said the agency “views cybersecurity as a team sport.” The person commented on the condition that the remark be attributed to the bureau.
The FBI urged utility executives last month to attend security training hosted by intelligence agents in order to ensure they are up to speed on the threats posed by bad actors.
“We can’t do it without you,” Matthew Fodor, deputy assistant director of the FBI’s counterterrorism division, said during an all-day FERC technical conference on Aug. 10. “The challenges that we have — and DOE can probably speak to this better than anybody — is limited resources.”
People attacking the electricity supply have thousands of potential targets, including power substations and smaller but critical pieces of utility infrastructure. The smaller pieces often go unprotected because federal standards do not require utilities to secure them.
Nearly half of the 4,493 attacks from 2020 to 2022 targeted substations, according to the NERC briefing from February, making them the most frequent targets for perpetrators over that period.
Details on how to carry out these kinds of attacks are available from extremist messaging boards and other online content, researchers and federal security officials say. These include maps of critical entry points to the grid, along with advice that extremists have gleaned from incidents like the assault in North Carolina.
Stanek, the Maryland electricity regulator, said he was “disappointed with the level of coordination and communication” that federal and state law enforcement displayed in handling the alleged plot in Baltimore. No trial date has been announced for the case, which is in U.S. District Court in Maryland.
Maryland’s Public Service Commission is in charge of ensuring that the state’s power system keeps the lights on. Regulators need to be kept informed of threats to the system so they can coordinate with other agencies in case an attack succeeds, Stanek said.
At the same time, he quipped, maybe he was better off in the dark after all.
“There’s a lot of colorful details in [the FBI report],” Stanek said. He paused, thinking. “And honestly, as a regulator, had I received these details in advance and shared the information with trusted sources within state government, I would have had sleepless nights.”
“So perhaps the feds did a favor by only sharing this information after everything was all said and done,” he added.
#us politics#news#politico#2023#alt right#domestic terrorists#neo nazis#fbi#power grids#power outages#Department of Energy#canada#white nationalists#Federal Energy Regulatory Commission#US electric grid#North American Electric Reliability Corp.#Department of Homeland Security#Office of the Private Sector#counterterrorism#cybersecurity#utility infrastructure#maryland
75 notes
·
View notes
Text
Summary:
When he was seventeen, after his mother took her own life, Butters disappeared from the town of South Park. No one has seen or heard from him since.
Five years later, Mysterion gets a job offer from Detective Harris in exchange for an unrefusable amount of money; He is to investigate and catch the criminal behind the latest cyber attack on the town residents’ bank accounts— one who calls himself Chaos. Dropped out, desperate and stuck in South Park, Kenny is willing to do anything to make ends meet until Karen’s graduation, and with Kyle’s help he might be able to pull it off. But the deeper they get into the case, the more Kenny’s identity and Karen’s future are under threat— and the less Kenny is sure he really wants to know who is behind Chaos’ mask.
Rating: M
Status: 3/25 (ongoing)
Words: 11.902
(Anyone willing to beta feel free to dm me! I’m grateful for any help :3)
#south park#butters stotch#kenny mccormick#mysterion#professor chaos#sp bunny#mystechaos#south park fanfiction#fic#fanfic#sp fanfiction#sp kenny#sp butters
16 notes
·
View notes
Text
⚠️ FRIDAY - ISRAEL REALTIME - Connecting to Israel in Realtime
Erev Shabbat - Parshat Barak - Numbers 22:2 - Balak, the king of Moab, summons the prophet Balaam to curse the people of Israel. Three times, from three different vantage points, Balaam attempts to pronounce his curses; each time, blessings issue forth instead. Balaam also prophesies on the end of the days and the coming of Moshiach (the Jewish messiah).
⚠️ WORLD WIDE COMPUTER OUTAGE .. Israel impact (not a cyber attack - an update error)
ISRAEL EMERGENCY NUMBERS MAY BE DOWN:
MDA 101 - alternatives call Hatzalah 1221 (who report they are operating fine) or 100 police
Electric Company - instead of 103, call 054-5838074 or report on Facebook page.
Working fine: 100 police, 102 fire
Some Israeli companies impacted - may accept only cash or be unable to do business for a while:
Israel Post
Ikea
Delek gas stations
Various hospitals - Shaarei Tzedek reports recovered, normal ops, Hadassah not on the problem list, Asuta Ashdod working fine
Affected: Hillel Yaffe, Laniado, Barzilai, Sheba, Wolfson, Shamir Assaf Harofeh, Rambam, Ma'aini Hashua, Nahariya, Poria, Bnei Zion, Ziv, the French Hospital in Nazareth, the Italian Hospital in Nazareth
Meuhedet health clinics
Clalit health clinics
Carrefour grocery - cash only
Banks HaPoalim, Leumi, Discount
Bank of Israel
Port of Ashdod completely down to ships and trucks
EL AL reports no impact, they don’t use the affected software.
Unrelated - Globes newspaper hacked (not the web site, the newsroom.)
WORLD IMPACT:
AIR TRAVEL - FAA suspending many flights in the US, Berlin flights on hold, Spain flights on hold.
Sky News having disruptions
⚠️HEZBOLLAH THREATENS.. significant retaliation for recent IDF targeted eliminations. Northern towns should be on ALERT, take precautions in the north.
▪️RUMORS ABOUT PM.. may suspend trip to the US. At the same time, “Israeli officials estimate that the Netanyahu-Biden meeting will not take place on Monday as planned”, unclear if due to Biden’s health or US election politics.
▪️FIN. MINISTER.. Sanctions from cabinet on PA officials NOT implemented by IDF and Shin Bet for the last 3 weeks???
▪️FBI USES ISRAELI SOFTWARE.. Washington Post: The FBI hacked into the phone of the assassin of Trump using the software of the Israeli company Celebrity.
▪️ECONOMY.. The Turkish embargo has stopped the import of Hyundai, and it is beginning to seep into Toyota, whose inventory in Israel is also shrinking.
PRESS BRIEFING BY IDF SPOKESPERSON RADM. DANIEL HAGARI - JULY 19, 2024
Overnight, a UAV, which we believe was launched from Yemen, infiltrated from the sea to our west and struck a building in central Tel Aviv. This impact resulted in the death of one civilian and lightly injured eight others. We extend our condolences to the bereaved family and wish a speedy recovery to the injured.
No alert was activated during the incident, and we are thoroughly investigating the matter. Our initial findings suggest the UAV was a Samad-3, an Iranian weapon likely upgraded to extend its range. This UAV flew from Yemen to Tel Aviv. Iran supports, funds, and arms its proxies in Gaza, Judea and Samaria, Lebanon, Syria, and Yemen, as evidenced by last night's event. UAV threats have been a constant challenge since the beginning of the war across all our borders. Dozens of UAVs have been launched from Yemen alone, most of which have been intercepted or shot down before entering Israeli territory. The majority were intercepted by an American task force under U.S. CENTCOM, while the rest were intercepted by Israeli Air Force planes or defense systems.
Simultaneously with the Tel Aviv incident, another UAV attempting to infiltrate from the east was intercepted and shot down outside of Israel’s borders. We are investigating the connection between the two incidents.
We are conducting a thorough inquiry to understand why the UAV was not identified as a threat and intercepted before it struck. An initial inquiry was conducted this morning, and we will continue to review the findings and update the public accordingly.
I want to emphasize that our defense is not foolproof. We are strengthening our air patrols and airspace protection across the country. We are continuously improving our capabilities to better protect the citizens of Israel.
There is no change in the Home Front Command directives. Should there be any changes, we will immediately inform the public.
Overnight and this morning, the Chief of the General Staff conducted several situational assessments. We have increased our defensive capabilities in Israel’s skies with additional planes and other measures to improve detection, alert, and interception capabilities. The incident on the ground was managed cooperatively by the Israel Police, Magen David Adom, and the Israel Fire and Rescue Services, who provided vital details for the inquiry.
In the north, the UAV threat is a daily challenge due to short-range launches, differing from last night’s incident. We are studying the northern threat to improve our response. We recognize the ongoing challenges faced by residents in the north.
In the past day, we have eliminated six Hezbollah terrorists and struck fifteen targets from the air and ground in the north.
We are engaged in a multi-front war, operating in all arenas and defending the country's skies daily. We are addressing threats both near and far.
In the coming days, we will continue our situational assessments to understand the incident better, determine the source of the threat, and decide on the necessary defensive and operational responses against those who threaten the State of Israel.
11 notes
·
View notes
Text
New Chapter out!
Fic Summary:
At seventeen, after his mother took her own life, Butters Stotch vanished from the town of South Park and no one has seen or heard from him since.
Five years later, Mysterion gets a job offer from Detective Harris in exchange for an unrefusable amount of money; He is to investigate and catch the criminal behind the latest cyber attack on the town residents’ bank accounts— one who calls himself Chaos. Dropped out, desperate and stuck in South Park, Kenny is willing to do anything to make ends meet until Karen’s graduation, and with Kyle’s help he might be able to pull it off. But the deeper they get into the case, the more Kenny’s identity and Karen’s future are under threat— and the less Kenny is sure he really wants to know who is behind Chaos’ plan.
Rating: M
Status: 7/25 (updated weekly)
Words: 29,148
#mysterion#south park#kenny mccormick#butters stotch#sp#professor chaos#sp bunny#bunny#fanfic#fic#my fic#chaos plan
10 notes
·
View notes
Text
"Anti-feminist blogger Jean-Claude Rochefort, who was convicted of fomenting hatred against women, has been sentenced to 12 months in jail.
The 74-year-old had been arrested in December 2019 in connection with posts and doctored images he had posted to his blog, in which he praised Marc Lépine, who murdered 14 women at Montreal's École Polytechnique on Dec. 6, 1989 in an anti-feminist attack.
Charged in 2010 for making death threats against women on his website, Rochefort was writing under a pseudonym. Montreal police's cyber investigation team nevertheless managed to find him and charge him again in December 2019.
He was found guilty of wilfully promoting hatred against women last August.
In his ruling, Quebec Superior Court Justice Pierre Labrie rejected Rochefort's claims that his publications constituted satire, exaggeration or self-deprecation.
Noting the use of the word kill and the use of images of firearms and decapitated women in the accused's posts, the judge found that Rochefort could not have been unaware that he was deliberately promoting hatred against women."
Full article
Tagging: @politicsofcanada
#cdnpoli#canada#canadian politics#canadian news#canadian#jean-claude rochefort#misogyny#sexism#violence#violence against women#misogyny tw#sexism tw#violence tw#violence against women tw#montréal#québec#montreal#quebec
137 notes
·
View notes
Text
By Richard Pollina
The horrific shows of antisemitism come as French police have launched an investigation into death threats received by three Israeli athletes at the Olympic Games, according to Sky News.
Security concerns for the Israeli team remain a significant priority for Olympic organizers as the nation is weeks away from marking 10 months of war against Hamas.
Israeli athletes in Paris are being escorted to and from events by elite tactical units and have been given 24-hour protection, officials told Sky News.
Israel’s internal security service, Shin Bet, is also assisting with security for their countrymen and other Israeli diplomats attending the games.
7Israel’s supporters wave flags in the men’s group D football match between Israel and Paraguay during the Paris 2024 Olympic Games at the Parc des Princes in Paris on July 27, 2024.AFP via Getty Images
Shin Bet is said to have “total support for the measures that are being taken by the French authorities,” a source told the outlet.

“This sends an important message to individuals and organizations attempting to threaten athletes,” the source added.
To ensure the safety of every country participating in the Olympics, France is deploying 35,000 officers each day, and 45,000 were deployed for the opening ceremonies.
France also receives help from 40 countries that have sent nearly 2,000 reinforcements.
On Thursday, Israel’s National Cyber Directorate said it discovered Iranian hackers were creating fake social media channels to publish personal information about members of the Israeli delegation at the Paris Olympics and were sending them threatening messages, according to Ynet News.
That same day, Israel’s foreign minister warned his French counterpart of a potential Iranian-backed plot to target Israeli athletes and tourists during the Games.
In response to the claims, the Iranian mission to the United Nations said in a statement that “Terrorist acts have no place in the principles of resistance groups; lies and deceit cannot switch the roles of the plaintiff and the accused.”
Israeli athletes have been the target of terrorist attacks during the Olympic Games in the past.
Eleven Israeli athletes and a German police officer were killed by Palestinian terrorists at the 1972 Munich Games.
11 notes
·
View notes
Text
As November’s U.S. presidential election draws closer and the campaigns of former President Donald Trump and Vice President Kamala Harris kick into high gear, so have efforts by hackers from Washington’s adversaries aimed at disrupting or influencing the vote. One adversary in particular is playing an increasingly prominent role: Iran.
Iranian state actors have stepped up their efforts to interfere in this year’s election through online disinformation and influence operations as well as cyberattacks on both presidential campaigns, three U.S. agencies—the Office of the Director of National Intelligence (ODNI), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA)—warned in a joint statement on Monday.
They’re not the only ones sounding the alarm. In the past three weeks alone, current and former intelligence officials as well as cyber threat researchers from Microsoft and Google have shared a growing body of evidence of Iran’s hacking efforts. As several of them have pointed out, Iran’s targeting of U.S. elections isn’t new—hackers linked to Iranian security services have attempted to interfere with presidential and midterm races dating back to at least 2018.
However, “Iran perceives this year’s elections to be particularly consequential in terms of the impact they could have on its national security interests, increasing Tehran’s inclination to try to shape the outcome,” the U.S. agencies wrote in their statement. “We have observed increasingly aggressive Iranian activity during this election cycle.”
Trump and his acolytes have been particular targets of Iranian hacking, with some former intelligence officials speculating to Politico that efforts to compromise their email accounts could be part of an effort to assassinate U.S. officials in retaliation for the 2020 killing of Iranian Gen. Qassem Suleimani during Trump’s presidency.
In their statement on Monday, the FBI, ODNI, and CISA officially blamed Iran for the so-called hack-and-leak operation against Trump’s campaign that the campaign made public earlier this month. Those tactics, mirroring Russia’s breach of the Democratic National Committee during the 2016 election, are only one part of Iran’s election interference efforts along with broader disinformation campaigns aimed at sowing discord among the American electorate.
“Iran, especially because of the past events with Suleimani, they have a marked interest in this election,” said retired U.S. Army Col. Candice Frost, the former commander of the Joint Intelligence Operations Center at U.S. Cyber Command. “They have attempted to message on past elections,” she said, but “I think this one is almost personal to them.”
Iran’s relatively elevated profile and more brazen cyber efforts may also be spurred by the ongoing conflict in the Middle East between U.S. ally Israel and Iranian proxies Hamas and Hezbollah, Mohammed Soliman, director of the strategic technologies and cybersecurity program at the Middle East Institute in Washington, D.C., told Foreign Policy. “I think the timelines have collided [between] regional confrontation with Israel and the U.S. elections,” he said. “This made them more proactive in attacking high-value targets that have brought massive visibility to their work.”
Iran is not the only adversary officials in Washington are concerned with—election interference efforts by Russia have been extensively documented, and U.S. officials have increasingly warned about China’s shift in cyber tactics from espionage to more disinformation and disruptive campaigns. Those two countries remain the prime threats, in large part because their capabilities are relatively more sophisticated.
“Russia and China are really a league of their own,” said Frost, currently an assistant professor at Georgetown University’s Center for Security Studies. “We oftentimes discount Iran and North Korea, and then you’ll have something like the Sony hack or this hack [of the Trump campaign]. So it’s not necessarily the level of advancement or competency that they have, but the fact that they kind of found a vulnerability and have been able to exploit that.”
“Any nation that has an interest or perceived stakes in the outcome of a U.S. presidential election is going to be thinking about how to influence that outcome,” said Gavin Wilde, a senior fellow in the technology and international affairs program at the Carnegie Endowment for International Peace and a former U.S. national security official. “It’s easy to point to Russia and China as the most adversarial and the most sophisticated, but every nation around the world has some perceived interest in the outcome, and so I think we need to calibrate along those lines.”
Officials and experts say the U.S. government has learned from the missteps of previous elections, particularly 2016, and is better prepared to defend this November’s election from cyber threats than it has ever been. Part of that is the shift to publicly calling out adversaries and their activities much earlier in the process and adopting a form of sunlight-as-best-disinfectant strategy, like the ODNI, FBI, and CISA did this week with Iran.
“It’s very hard to counter that narrative once it gets into the American psyche and our citizens’ spheres of influence,” Frost said. “But I do see the focus and calling out [of] this behavior. … That is what we’re seeing at a much faster pace, and I give the current intel community a lot of props for doing that early.”
But Wilde warned that while U.S. officials are “unquestionably” more prepared this time around, they also now need to be careful about showing their work without inciting panic about elections being compromised. “The tightrope they now have to walk is [being] helpful without creating the very kind of panic that might itself undermine confidence in the election,” he said, adding that it’s also important to draw distinctions among hack-and-leak operations that have become “a new normal” for political campaigns, election influence efforts that can sometimes be hard to legally define, and actual efforts to interfere with the ballot box itself.
“I think the most consistent thing from all of them is how much it’s been a lot of just entrepreneurialism and experimental spaghetti-against-the-wall tactics to kind of just see what works,” Wilde said. “The U.S. and everyone has to be careful not to inadvertently incentivize this activity by making too big a deal out of it, and luckily I think we’ve done a lot better this go-round than we did in 2016.”
15 notes
·
View notes