#data storage security in cloud computing
Explore tagged Tumblr posts
Text
Best Cloud Storage for Small Business
Are you starting a new business? IT Total Care, Inc. can take your business to the next level of operations, cloud storage, and IT support. Our trained experts focus on making and keeping your IT environment hassle-free. https://www.ittotalcare.com/storage-retrieval-and-data-protection/
#best cloud storage for small business#data storage security in cloud computing#desktop and server support
0 notes
Text
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
Understanding Microsoft Azure
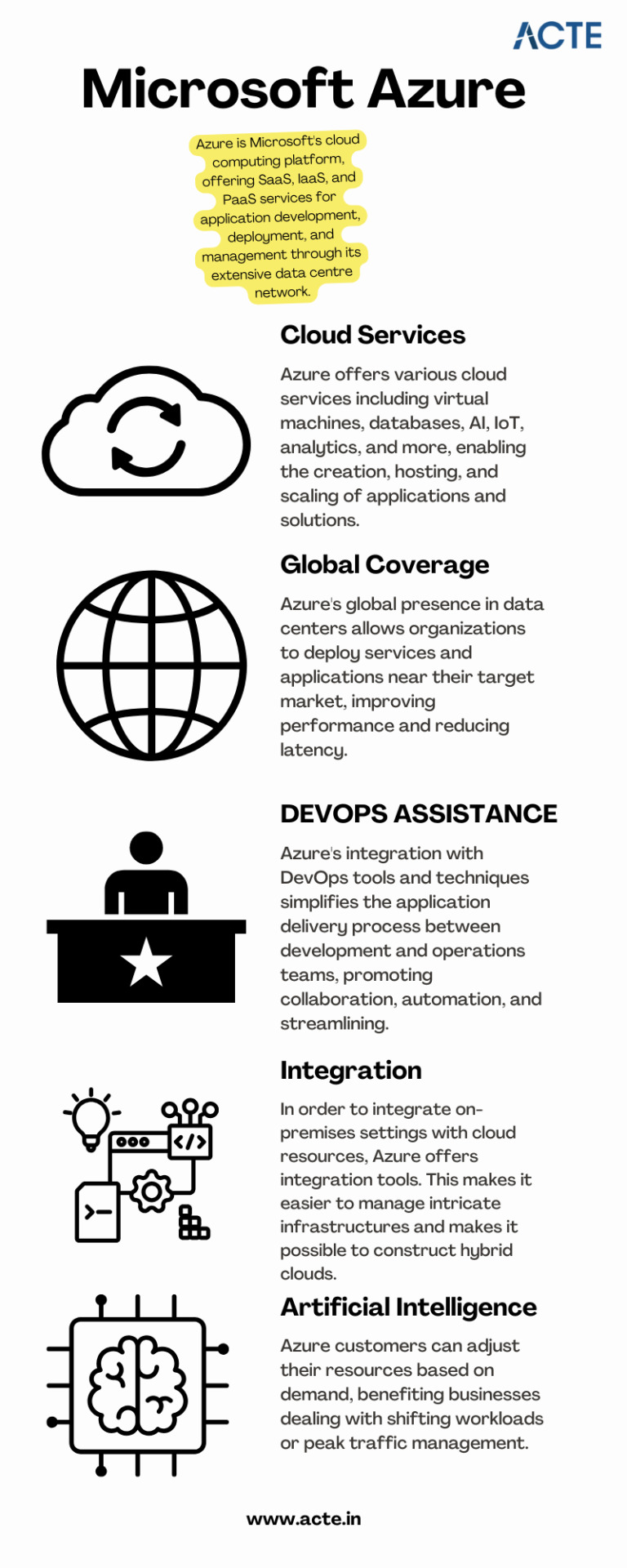
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
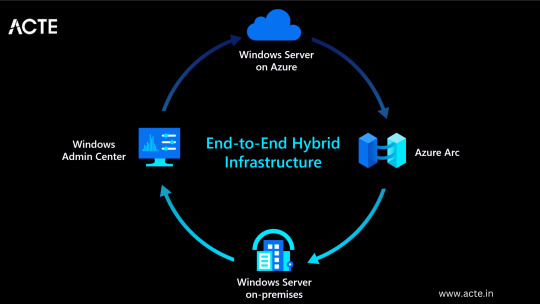
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Text
The advantages of Computer Networks: Enhancing Connectivity & Efficiency
Computer networks form the backbone of modern communication, business operations, and data management, enabling seamless connectivity and resource sharing. Whether in workplaces, homes, or global enterprises, networking has transformed the way we exchange information. Here’s why computer networks are essential for efficiency, security, and collaboration. 1. Seamless Communication &…
#business connectivity#cloud storage solutions#computer networking benefits#digital collaboration#IT infrastructure efficiency#network performance optimization#secure data sharing
1 note
·
View note
Text
Storage Predictions for 2025: Larry O’Connor Explores the Future of Data Management
New Post has been published on https://thedigitalinsider.com/storage-predictions-for-2025-larry-oconnor-explores-the-future-of-data-management/
Storage Predictions for 2025: Larry O’Connor Explores the Future of Data Management


In this article by Larry O’Connor for LarryJordan.com, the founder and CEO of OWC shares his insightful predictions for the future of data storage in 2025. Highlighting the return to on-premises solutions, the democratization of AI through local implementation, and the growing performance gap between local and cloud-based systems, O’Connor provides a roadmap for businesses to optimize their storage strategies. These predictions focus on enhancing security, improving performance, and reducing costs—key considerations for data management in the digital era.
The Return of On-Premises Data Storage and Computing
O’Connor predicts a major resurgence in on-premises data storage and computing as organizations prioritize security, performance, and cost control. With cloud storage costs on the rise and vulnerabilities becoming more apparent, many businesses are turning to local solutions for critical data management. On-prem data storage offers faster access speeds, greater reliability, and enhanced protection against cyberattacks.
Smaller businesses, in particular, benefit from local storage since it is less attractive to cybercriminals compared to public cloud platforms. O’Connor emphasizes that the cloud should play a supporting role—serving as a tertiary backup or for external data sharing—while local solutions remain the primary strategy for data security. By reducing reliance on cloud storage, businesses can avoid bandwidth costs, accelerate data recovery, and maintain control over sensitive information.
On-Premises AI: Democratizing Technology and Protecting Intellectual Property
One of the most exciting predictions from O’Connor is the rise of on-premises AI. This shift enables smaller businesses to access powerful data processing tools without the high costs associated with cloud-based AI platforms. Running AI systems locally not only democratizes advanced technology but also protects proprietary data, algorithms, and customer insights from being exposed in the cloud.
O’Connor warns of the risks of “data bleed,” where proprietary information inadvertently enhances third-party systems or becomes accessible to competitors. On-prem AI ensures full control over sensitive data while eliminating recurring costs associated with cloud AI services. This makes on-premises AI a cost-effective and secure option for businesses looking to leverage AI capabilities.
The Expanding Performance Gap Between Local and Cloud-Based Systems
O’Connor’s third prediction underscores the growing performance gap between locally operated systems and cloud-dependent solutions. With advancements like Thunderbolt 5 technology, local systems now achieve data transfer speeds of up to 7000MB/s, far surpassing the 100MB/s typical of cloud-based systems.
This dramatic performance boost is essential for tasks such as video editing, high-resolution imagery processing, and managing complex data sets. By leveraging local systems, businesses can streamline workflows and significantly reduce the time and cost associated with cloud dependency. O’Connor suggests that cloud storage is best reserved for distribution and collaboration, while local solutions should handle performance-intensive tasks.
Conclusion: Embracing a Hybrid Storage Strategy
Larry O’Connor’s predictions for 2025 highlight a pivotal shift in data management strategies. Businesses are advised to embrace on-premises solutions for their speed, security, and cost advantages while using cloud services selectively for supplementary needs. Whether it’s safeguarding intellectual property, optimizing performance, or reducing expenses, on-premises storage and computing are poised to take center stage in the future of data management.
For organizations looking to stay ahead of the curve, O’Connor’s insights provide a clear path to success. By adopting a hybrid approach to data storage, businesses can harness the best of both local and cloud technologies, ensuring they remain competitive in an evolving digital landscape.
Read the full article by Larry O’Connor HERE
Learn more about OWC below:
#2025#ai#AI platforms#AI systems#Algorithms#approach#Article#backup#Best Of#CEO#Cloud#Cloud AI#cloud services#cloud storage#Collaboration#computing#Cyberattacks#cybercriminals#data#Data Management#data processing#data recovery#data security#data sharing#data storage#data transfer#democratization#democratization of AI#Editing#focus
0 notes
Text
As this synergy grows, the future of engineering is set to be more collaborative, efficient, and innovative. Cloud computing truly bridges the gap between technical creativity and practical execution. To Know More: https://mkce.ac.in/blog/the-intersection-of-cloud-computing-and-engineering-transforming-data-management/
#engineering college#top 10 colleges in tn#private college#engineering college in karur#mkce college#best engineering college#best engineering college in karur#mkce#libary#mkce.ac.in#Cloud Computing#Data Management#Big Data#Analytics#Cost Efficiency#scalability#High-Performance Computing (HPC)#Artificial Intelligence (AI)#Machine Learning#Automation#Data Storage#Remote Work#Data Security#Global Reach#Cloud Servers#digitaltransformation
0 notes
Text
What Should You Know About Edge Computing?
As technology continues to evolve, so do the ways in which data is processed, stored, and managed. One of the most transformative innovations in this space is edge computing. But what should you know about edge computing? This technology shifts data processing closer to the source, reducing latency and improving efficiency, particularly in environments where immediate action or analysis is…
#5G#AI#AI edge#AI integration#automation#autonomous vehicles#bandwidth#cloud#cloud infrastructure#cloud security#computing#computing power#data generation#data management#data processing#data storage#data transfer#decentralization#digital services#digital transformation#distributed computing#edge analytics#edge computing#edge devices#edge inferencing#edge networks#edge servers#enterprise data#Healthcare#hybrid cloud
0 notes
Text
Dominating the Market with Cloud Power

Explore how leveraging cloud technology can help businesses dominate the market. Learn how cloud power boosts scalability, reduces costs, enhances innovation, and provides a competitive edge in today's digital landscape. Visit now to read more: Dominating the Market with Cloud Power
#ai-driven cloud platforms#azure cloud platform#business agility with cloud#business innovation with cloud#capital one cloud transformation#cloud adoption in media and entertainment#cloud computing and iot#cloud computing for business growth#cloud computing for financial institutions#cloud computing for start-ups#cloud computing for travel industry#cloud computing in healthcare#cloud computing landscape#Cloud Computing solutions#cloud for operational excellence#cloud infrastructure as a service (iaas)#cloud migration benefits#cloud scalability for enterprises#cloud security and disaster recovery#cloud solutions for competitive advantage#cloud solutions for modern businesses#Cloud storage solutions#cloud technology trends#cloud transformation#cloud-based content management#cloud-based machine learning#cost-efficient cloud services#customer experience enhancement with cloud#data analytics with cloud#digital transformation with cloud
1 note
·
View note
Text
Cloud vs On-Prem Data Warehouse: Making the Right Choice for Your Business
In today's data-driven world, businesses face a critical decision when it comes to choosing the right data warehouse solution. The debate between cloud and on-premise data warehouses has been ongoing, with each option offering distinct advantages and challenges. This article will delve into the practical differences between cloud and on-premise data warehouses, offering real-world examples and data-driven insights to help you make an informed decision.

What is a Cloud Data Warehouse?
A cloud data warehouse is a scalable and flexible data storage solution hosted on cloud platforms like AWS, Google Cloud, or Microsoft Azure. Unlike traditional on-premise data warehouses, cloud data warehouses eliminate the need for physical infrastructure, offering businesses the ability to store and manage data with ease and efficiency.
On-Premise Data Warehouse: A Legacy Approach
An on-premise data warehouse is a traditional data storage solution where the data is hosted on local servers within a company's own data center. This model offers complete control over the data and the infrastructure but comes with significant upfront costs and ongoing maintenance requirements.
Key Differences Between Cloud and On-Premise Data Warehouses
1. Cost Efficiency
Cloud Data Warehouse:
Pros: The pay-as-you-go model allows businesses to scale resources up or down based on demand, reducing unnecessary costs. There is no need for significant capital investment in hardware or software.
Cons: Long-term costs can add up if not managed properly, especially with increasing data volumes and computational needs.
On-Premise Data Warehouse:
Pros: Once the initial investment is made, ongoing costs can be more predictable. No recurring subscription fees.
Cons: High upfront costs for hardware, software, and skilled IT personnel. Ongoing maintenance, power, and cooling expenses add to the total cost of ownership (TCO).
2. Scalability
Cloud Data Warehouse:
Pros: Cloud solutions offer almost infinite scalability. Businesses can adjust their storage and processing power according to their needs without physical limitations.
Cons: Rapid scaling can lead to unexpectedly high costs if usage is not carefully monitored.
On-Premise Data Warehouse:
Pros: Customizable to specific business needs. Scaling is possible but requires additional hardware and can be time-consuming.
Cons: Scaling is limited by the physical infrastructure, often requiring significant time and financial investment.
3. Performance
Cloud Data Warehouse:
Pros: Advanced cloud architectures are optimized for performance, offering faster query processing and better data handling capabilities.
Cons: Performance can be affected by network latency and bandwidth limitations.
On-Premise Data Warehouse:
Pros: Performance is highly controlled, with low latency since data is processed on-site.
Cons: Performance improvements require hardware upgrades, which can be costly and time-consuming.
4. Security and Compliance
Cloud Data Warehouse:
Pros: Leading cloud providers offer robust security features, including encryption, access controls, and compliance with industry standards like GDPR, HIPAA, and SOC 2.
Cons: Data security in the cloud is a shared responsibility. Organizations must ensure that they implement proper security measures on their end.
On-Premise Data Warehouse:
Pros: Complete control over security policies and compliance with regulatory requirements. Data remains within the company's own environment.
Cons: Higher responsibility for maintaining security, requiring dedicated IT staff and resources.
Live Examples: Cloud vs On-Premise in Action
Cloud Data Warehouse: Netflix
Netflix is a prime example of a company leveraging cloud data warehouses to manage its massive data volumes. By using AWS Redshift, Netflix can analyze petabytes of data in real-time, optimizing its recommendation algorithms and improving user experience. The scalability and performance of cloud data warehouses allow Netflix to handle peak loads, such as during new content releases, without compromising speed or reliability.
On-Premise Data Warehouse: Bank of America
Bank of America relies on an on-premise data warehouse to maintain full control over its sensitive financial data. By keeping data in-house, the bank ensures that all security and compliance requirements are met without relying on external cloud providers. While the costs and complexity of managing an on-premise solution are higher, the bank prioritizes control and security over the flexibility offered by cloud solutions.
Data-Driven Insights: Market Trends and Future Outlook
Market Growth: According to a report by MarketsandMarkets, the global cloud data warehouse market is expected to grow from $4.7 billion in 2021 to $12.9 billion by 2026, at a CAGR of 23.8%. This growth is driven by the increasing adoption of cloud technologies, the need for real-time analytics, and the flexibility offered by cloud solutions.
Hybrid Approaches: Many organizations are adopting hybrid models, combining both cloud and on-premise data warehouses to balance the benefits of both. For instance, sensitive data may be stored on-premise, while less critical data is managed in the cloud.
AI and Machine Learning Integration: Cloud data warehouses are increasingly integrating AI and machine learning tools to enhance data processing capabilities. This trend is expected to accelerate, with cloud providers offering more advanced analytics and automation features.
Making the Right Choice: Key Considerations
Business Needs: Assess your organization’s specific needs, including data volume, security requirements, budget, and long-term goals.
Total Cost of Ownership (TCO): Consider both the short-term and long-term costs associated with each solution, including maintenance, upgrades, and scalability.
Security and Compliance: Ensure that your chosen solution meets all regulatory requirements and provides the necessary security features to protect your data.
Scalability and Performance: Evaluate the scalability and performance needs of your organization, and choose a solution that can grow with your business.
Conclusion
Choosing between a cloud and an on-premise data warehouse is a decision that requires careful consideration of various factors, including cost, scalability, performance, and security. While cloud data warehouses offer flexibility, scalability, and advanced analytics, on-premise solutions provide greater control and security. By understanding your organization’s unique needs and long-term goals, you can make an informed decision that will support your data management strategy for years to come.
#Cloud Data Warehouse#On Premise Data Warehouse#Data Storage#Data Management#Cloud Computing#Enterprise Data#Hybrid Cloud#Data Analytics#Data Security#Digital Transformation#Data Infrastructure#Business Intelligence
0 notes
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Text
Hi there’s a tornado in my area rn but I’m spiteful like that. Random tsams/eaps headcanons be upon ye
Ruin still does those little audio log diaries. It helps manage his overflowing memory storage (read: old age = more memories to store) without compressing data files.
Bloodmoon sleeps with dog toys. Otherwise, they’d probably chew through whatever bedding material they had chosen that night. This was Ruin’s idea.
Eclipse can’t sleep with lights on in a room. Ruin can’t sleep without a light. The makeshift solution is a sleeping mask for Eclipse, but their actual compromise is a star projector.
Eclipse has to know where everyone is most of the time, especially after Charlie came into the picture. This is usually done with cameras and tracking via fazbear systems, but it’s an issue he has to work on, as it’s just a method to make him feel better about security now that there are people he cares about. At least one person has commented on there being a new nightguard.
Dark sun finds thrillers tacky, and prefers thought-provoking mysteries, bonus points for romance.
Most of them carry some kind of sanitizing wipe packet. For daycare attendants, these are for sticky messes and children. For those more familiar with tools, these are for tougher grime and are not suitable for sensitive (children’s) skin. Solar has both.
The eclipses (Eclipse, Solar, Ruin) are the most prone to damaging their rays. Eclipse sometimes hits doorways and doesn’t bother to fix cracked rays. Ruin is small enough for humans to reach his head. Solar peels the paint off of his. All three will pull or squeeze their rays in times of extreme stress, to varying degrees. Lunar is an exception for lack of rays. (Similarly, Sun fidgets with his rays, which is the source of this trait.)
While there are exceptions, Suns prefer tactile stimulation, Moons auditory, and Eclipses have no strong preference. Earth likes social interaction.
Animatronics have personalized UI that makes sense to them, which serves as their access point to their internal folders, like memory files, downloaded items, and executable programs. Bots that share an operating system/“brain” have the same UI. Diagnostics, software updates, and safety modes all require additional hardware (computers, parts and service devices, fazwrenches) to complete. Mindscapes are in AI chips, and multiple AIs in one mindscape happen when multiple AIs share the same operating system. Visual feed can be projected onto other screens with HDMI cables and vice versa, which can sometimes show that bot’s UI depending on what it is. For a more direct example of this think of the battery and blue borders you see in Security breach when Gregory is hiding inside Freddy.
Safety mode disconnects that bot from the Fazbear Ent. local network, meaning no tracking, no communication via local networks (which generally aren’t private anyway, most bots with access to phones prefer those), and no access to files that aren’t stored in that bot’s drive. This is meant to isolate a bot’s systems from the main network in case of a security breach (hah), make transportation of bots between locations easier, and make maintenance a smoother affair as there is no outside interference during the process. For the bots themselves, this is the equivalent of turning off your phone and going outside I mean focusing only on what’s in front of you instead of what’s going on in your area/social network. It’s possible to be stuck in safety mode. Depending on how much of a bot’s system relies on Fazbear Ent. Networks to function (such as a bot’s memory being stored in a Cloud, which is also ill advised between the bots themselves,) this can be mean a temporary personality/memory reset until those files get reconnected again. Bots do not need to be connected to the Fazbear ent networks to function, but it generally makes access to software updates easier due to being recognized as a company entity. It is possible for a private network to exist, but it’s considered foreign by Fazbear systems and can be more trouble than they’re worth. Moon and Eclipse have private networks shared with close friends and family for different purposes. Moon’s is mostly for emergency backups, and Eclipse’s is for security.
Animatronic’s memories are stored in the hard drives in their bodies. It’s possible to offload memory files into networks (Cloud) or external storage systems. If another bot had access to these clouds or external storages, they could experience the memories stored in them. Memory files include visual and auditory data, like a movie. AI/personality chips are the equivalent of a soul in that the AI is the product of a learning AI having experienced environments that supplied them information about the world AKA an Ai that developed a personality beyond their base programming, but they do not carry memories. For example, Eclipse V3-V4 is an Eclipse AI given incomplete memories, creating a disconnect in the AI’s learned behaviors and what it perceives as the source of that behavior, resulting in an incomplete backup. Backups are static/unchanging copies of integral memory files and the accompanying AI (As is in the moment that they are backed up.) Backups need to be updated as the animatronic it’s for develops.
#go easy on me I only have basic knowledge of computer stuff#quirky headcanons#tsams#eaps#I’m also halfway through a sociology class so take the AI one with a grain of salt#hopefully this makes sense
25 notes
·
View notes
Text
Demystifying cloud computing: the future of technology.

In today's rapidly evolving digital world, cloud computing is not just a technology trend-cloud computing is the foundation of today's IT infrastructure. from streaming your favourite Netflix show to collaborating on Google Docs.
what is cloud computing?

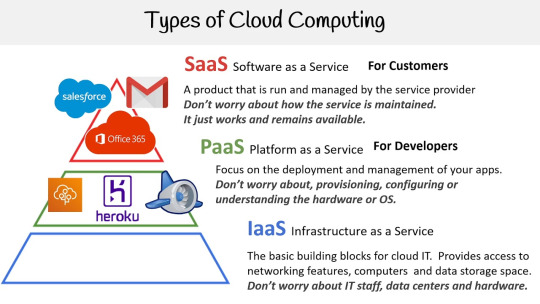
Cloud computing is the provision of computing services including the servers, databases, storage, networking, software, analytics, and intelligence over the internet to offer faster innovation, flexible resources, and economies of scale.
Types of cloud services.
Security in the cloud.
Security is the top priority. cloud vendors employ encryption, firewalls, multi-factor authentication, and periodic audits to secure data. Organizations must, however, set up and manage secure access.
The future of cloud computing.

The future of cloud computing is being defined by a number of ground breaking trends that are changing the way data and applications are processed. Edge computing is moving computation near data sources to decrease latency and improve real-time processing for IoT and mobile applications.
7 notes
·
View notes
Text
i have a loving and desperate reminder for folks working on large/long term projects in digital format:
it's unwise to make the "cloud" your primary location for data storage. making back-ups in them is fine, but the most secure place for your work is on an ext hard disk that you can detach from your machine, and on multiple copies if you can manage/afford it. (and dont forget to unplug your ext drives when not actively using them!!)
if you dont have access to a personal computer, the public library in your area likely has computers available that you can use. even if theyre not powerhouse machines, they can do what's needed in order for you to back up your stuff. using the internet there you can access your phone/tablet cloud storage online and copy your work onto your external drive. it's definitely inconvenient, but it's probably more convenient than losing your entire library of personal work, writing, and photos.
discord stopped hosting images not that long ago which broke a lot of hyperlinks for personal web projects, google is doing sinister google stuff and is probably going to continue to do so, and we're sort of teetering on a major data/archive crisis that definitely won't put people like us first. corporations are not interested in protecting you. you are the only person who can keep your artwork, writing, and photos secure. ❤️ 🙏
i love you ❤️ pls protect your passion projects ;-; dont let corps decide if your work lives or dies pls back up your digital stuff
#barbossa voice#u best be believin in a cyberpunk hellscape#ur in one#i want to be able to read your projects ;-;
50 notes
·
View notes
Text
By Madge Waggy MadgeWaggy.blogspot.com
December 30, 2024
According to Steven Overly From: www.politico.com The freakout moment that set journalist Byron Tau on a five-year quest to expose the sprawling U.S. data surveillance state occurred over a “wine-soaked dinner” back in 2018 with a source he cannot name.
The tipster told Tau the government was buying up reams of consumer data — information scraped from cellphones, social media profiles, internet ad exchanges and other open sources — and deploying it for often-clandestine purposes like law enforcement and national security in the U.S. and abroad. The places you go, the websites you visit, the opinions you post — all collected and legally sold to federal agencies.
I’m going to alert you to what many are considering to be on of the worst doomsday scenarios for free American patriots. One that apparently not many are prepping for, or even seem to care about.
By now everybody knows that the government ‘alphabet agencies’ including mainly the NSA have been methodically collecting data on us. Everything we do, say, buy and search on the internet will be on permanent data base file by next year. All phone calls now are computer monitored, automatically recorded and stored with certain flag/trigger words (in all languages).
As technology improves, every single phone call will be entirely recorded at meta-data bases in government computer cloud storage, when ‘They’ finish the huge NSA super spy center in Utah. Which means they will be available anytime authorities want to look them up and personally listen for any information reference to any future investigation. Super computer algorithms will pin point search extrapolations of ANY relationship to the target point.
You can rest uneasily, but assured, that in the very near future when a cop stops you and scans your driver license into his computer, he will know anything even remotely ’suspicious’ or ’questionable’ about ALL the recent activities and behavior in your life he chooses to focus upon!
This is the ‘privacy apocalypse’ coming upon us. And you need to know these five devices that you can run to protect your privacy, but you can’t hide from.
When Security Overlaps Freedom
11 notes
·
View notes
Text
Unlocking Compliance Excellence: The Role of Cloud Technology in Business - Technology Org
New Post has been published on https://thedigitalinsider.com/unlocking-compliance-excellence-the-role-of-cloud-technology-in-business-technology-org/
Unlocking Compliance Excellence: The Role of Cloud Technology in Business - Technology Org
Cloud technology has had a significant transformative impact on enhancing compliance within business operations. From streamlining processes to fortifying data security, cloud solutions and computing strategies are changing how organisations mitigate potential human errors and improving cyber security standards.
Working with cloud services – illustrative photo. Image credit: Sigmund via Unsplash, free license
Research has found that 48 percent of businesses that use cloud computing have reported increased efficiency across a variety of processes. The active monitoring systems are becoming as essential to everyday operations as more and more financial compliance laws emerge. This guide discusses the role of cloud technology in business and the benefits of Cloud adoption.
Scalability and Flexibility
Cloud solutions are offering businesses of all sizes scalability, which is crucial for accessing more clients, resources and data. Having adequate software and systems to effectively manage this allows organisations to develop improved products, services and general efficiency. A scalable compliance infrastructure can continuously evolve to meet changing needs and regulatory requirements.
Deploying General Data Protection Regulation (GDPR) and secure payment industry frameworks are making it easier for businesses to customise tools and processes to meet specific industry regulations. This flexibility is transforming how businesses perform VAT compliance reporting as well as data protection rules.
Automated Compliance Monitoring
Automated tools and algorithms are making great strides in minimising the risk of security of compliance breaches and monitoring operations. Not only do they remove the possibility of human error but these systems alert users to changes in systems, settings modifications and when security standards are broken.
Cloud computing also offers increased transparency to stakeholders. When potential compliance issues are identified, an alert is sent out and this allows for proactive mitigation measures to be implemented.
Enhanced Security Protocols
As business operations are progressively moving online, upgraded security protocols are more important than ever. Given the sensitive nature of compliance information and records, cloud technology keeps important documentation secure and keeps businesses ahead of the curve regarding documentation.
Features such as data encryption and advanced threat detection ensure data protection compliance and safeguards against unauthorised access. The implementation of granular access controls keeps data access limited to authorised personnel.
Centralised Data Management and Accessibility
Centralising data storage and facilitating seamless access to information means that employees perform tasks and remain compliant from wherever they are working. This has become crucial with the popularity of hybrid and remote working practices.
Real-time data updates allow businesses to stay up to date with regulatory changes and swiftly adapt their compliance strategies. It also improves the efficiency and effectiveness of decision-making and detects anomalies to protect data privacy and uphold the rights of individuals. This is critical to maintaining business reputations in the marketplace and ensuring data accuracy and integrity.
#Accessibility#Algorithms#automated tools#Business#Cloud#cloud computing#cloud services#cloud solutions#cloud technology#compliance#computing#cyber#cyber security#data#Data Management#data privacy#data protection#data security#data storage#detection#documentation#efficiency#employees#encryption#Features#financial#Fintech news#gdpr#general data protection regulation#how
0 notes
Text
building an opensource collection of 'net services
hi there! im mia :) im a computer nerd with too much time on her hands.
im making this post to bring a project of mine into the world; a fully opensource and collaborative collection of online tools. this will grow over time, but for now, there is one thing active and two planned. (read on below)
CalicoDrive
a nextcloud instance! currently offering a bunch of very useful things:
50GB of free cloud storage
a Markdown notetaking tool
a shareable, open calendar
a photo gallery
web bookmark storage, and
some organisation and collaboration tools.
many of the cloud storage services we rely on are corporate, and require exorbitantly priced subscriptions. alongside that, data on them is often subject to a huge array of impenetrable terms/conditions.
what makes this different? firstly, your data is controlled by you. it is entirely encrypted on disk and can only be decrypted with your selected password. you own the data the same way you would were it on an external hard drive or flashstick.
secondly- its free! while you can pay 20$ once off or 5$ a month to upgrade storage quota and support the project, the core of it is entirely and utterly free to use.
matrix.calicocore
(full disclaimer- this service isn't online yet. it's planned to be active within the next month at the very maximum, very likely sooner.)
what's matrix? i am absolutely sure you've heard of IRC- internet relay chat. im also sure you've heard of discord.
matrix is a modern federated chat protocol- if you took the best of IRC, and you took the best of Discord, and combined them into an opensource and *free* protocol for real-time messaging? that's matrix, baby!
matrix functions similarly to the fediverse (more on that later). when you sign up, you select a homeserver, which is the infrastructure your account is hosted on. your homeserver determines who you're federated with, your most easily accessible spaces, and the little tag at the end of your name.
so what's matrix.calicocore going to be? a homeserver! the idea here is to bring communication and community into our hands, and away from the hands of big tech corporations who really don't care about us. it'll be federated with other spaces and servers, and run collectively.
fedi.calicocore
if you've ever used mastodon, fedi.calicocore will be a server compatible with it. this is still in the very very early stages as a project, so i cant detail much, but stay tuned.
things to note, disclaimers, etc
this project is in its early days. i cant guarantee perfect stability, though it has been tested and run for a few days already. please don't expect a perfect replacement for existing services YET.
secondly, in regards to calicodrive; your data is fully encrypted in two ways, both within the nextcloud instance and on the physical spinning rust. this means if you majorly forget your password, there's a possibility of losing it- but that trade-off is worth it for the security.
this all sounds great! how can i sign up?
for now, this is the link to the nextcloud:
https://drive.calicocore.space
in the very near future, there'll be a central discussion space on the matrix, too, which you're encouraged to introduce yourself on!
lastly:
who is this for?
these services and tools are made by a disabled trans woman. they will prioritise people vulnerable on the current internet, and focus on building a safe space for trans, non-binary, and queer people; as well as disabled people and people of colour.
you can sign up if you are not one of these, however you will be expected to defer to the marginalised members and be generally respectful of the purpose of the space!
8 notes
·
View notes
Text
When Microsoft named its new Windows feature Recall, the company intended the word to refer to a kind of perfect, AI-enabled memory for your device. Today, the other, unintended definition of “recall”—a company's admission that a product is too dangerous or defective to be left on the market in its current form—seems more appropriate.
On Friday, Microsoft announced that it would be making multiple dramatic changes to its rollout of its Recall feature, making it an opt-in feature in the Copilot+ compatible versions of Windows where it had previously been turned on by default, and introducing new security measures designed to better keep data encrypted and require authentication to access Recall's stored data.
“We are updating the set-up experience of Copilot+ PCs to give people a clearer choice to opt-in to saving snapshots using Recall,” reads a blog post from Pavan Davuluri, Microsoft's corporate vice president for Windows and devices. “If you don’t proactively choose to turn it on, it will be off by default.”
The changes come amid a mounting barrage of criticism from the security and privacy community, which has described Recall—which silently stores a screenshot of the user's activity every five seconds as fodder for AI analysis—as a gift to hackers: essentially unrequested, preinstalled spyware built into new Windows computers.
In the preview versions of Recall, that screenshot data, complete with the user's every bank login, password, and porn site visit would have been indefinitely collected on the user's machine by default. And though that highly sensitive data is stored locally on the user's machine and not uploaded to the cloud, cybersecurity experts have warned that it all remains accessible to any hacker who so much as gains a temporary foothold on a user's Recall-enabled device, giving them a long-term panopticon view of the victim's digital life.
"It makes your security very fragile,” as Dave Aitel, a former NSA hacker and founder of security firm Immunity, described it—more charitably than some others—to WIRED earlier this week. “Anyone who penetrates your computer for even a second can get your whole history. Which is not something people want.”
In addition to making Recall an opt-in feature, Microsoft’s Davuluri also writes that the company will make changes to better safeguard the data Recall collects and more closely police who can turn it on, requiring that users prove their identity via its Microsoft Hello authentication function any time they either enable Recall or access its data, which can require a PIN or biometric check of the user’s face or thumbprint. Davuluri says Recall’s data will remain encrypted in storage until the user authenticates.
All of that is a “great improvement,” says Jake Williams, another former NSA hacker who now serves as VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks. But Williams still sees serious risks in Recall, even in its latest form.
Many users will turn on Recall, he points out, partly due to Microsoft’s high-profile marketing of the feature. And when they do, they’ll still face plenty of unresolved privacy problems, from domestic abusers that often demand partners give up their PINs to subpoenas or lawsuits that compel them to turn over their historical data. “Satya Nadella has been out there talking about how this is a game changer and the solution to all problems,” Williams says, referring to Microsoft's CEO. “If customers turn it on, there’s still a huge threat of legal discovery. I can’t imagine a corporate legal team that’s ready to accept the risk of all of a user’s actions being turned over in discovery.”
For Microsoft, the Recall rollback comes in the midst of an embarrassing string of cybersecurity incidents and breaches—including a leak of terabytes of its customers' data and a shocking penetration of government email accounts enabled by a cascading series of Microsoft security slipups—that have grown so problematic as to become a sticking point given its uniquely close relationship with the US government.
Those scandals have escalated to the degree that Microsoft's Nadella issued a memo just last month declaring that Microsoft would make security its first priority in any business decision. “If you’re faced with the trade-off between security and another priority, your answer is clear: Do security,” Nadella's memo read (emphasis his). “In some cases, this will mean prioritizing security above other things we do, such as releasing new features or providing ongoing support for legacy systems.”
By all appearances, Microsoft's rollout of Recall—even after today's announcement—displays the opposite approach, and one that seems more in line with business as usual in Redmond: Announce a feature, get pummeled for its glaring security failures, then belatedly scramble to control the damage.
20 notes
·
View notes