#desktop icon lock software
Explore tagged Tumblr posts
Text
youtube
How To Create A Desktop Lock Icon | एक क्लिक में लॉक करें कंप्यूटर |Laptop|Desktop| By Sachin Sharma
#how to lock desktop icons#computer#desktop#create#lock#desktop icons#desktop shortcut#desktop icon lock software#how to lock#lock desktop icons windows 10#how to wins 10#desktop icon ko lock kaise karen#how to lock desktop icons windows 10#how to lock desktop icons windows 7#how to lock desktop icons in a multiple monitor setup#desktop computer lock#how to lock desktop screen windows 10#Youtube
0 notes
Text
Debian 12 w KDE Plasma let's go~~~
I've got no idea why I didn't like KDE before tbh.... cause trying it now, its kinda nice~~~ last time I tried it was idk how long ago.... when I started messing around with linux to begin with.
It, unlike xfce, has a software updater so I don't need to use the terminal on debian~~~ it looks really snazzy tbh.
last time I used it was idk how long ago..... a decade ago? and I guess now it's just Plasma and not KDE anymore? ??
annoying problem that I fixed~~~~ also for some reason the icons and stuff on my second hard drive have reverted back to dev/sda for my main OS partition and dev/sdb for where all the rest of my data is... and idk why~~~ but the lock icons on everything in that drive is gone~~ and idk what fixed it......
also time.... the date and time was incorrect and i had no idea why given I've selected the proper time zone.... I was just really confused and idk why.... but now I did and it's fixed~~ I had to change the BIOS time to UTC
and since there's no "sync w internet" and you need EXACT SECONDS now the time is slightly off cause I didn't time it down to the second.... but putting my BIOS time into UTC instead of local time fixed it~~~
also still don't know exactly why I can and could get debian to boot and install perfectly fine on my machine even with secure boot and the like from a windows install still on. when linux mint debian edition just.... wouldn't......
stupidly simple fix but I'm happy to have figured it out myself~~~ hope I like KDE more than I did a decade ago. idk why I didn't like it that far back... maybe it was worse? or there was too many customize options and it paralyzed me?
but now I like it so far~~~~ wonder if I can do it up like windows xp/95? lol. throw myself into customize options of KDE and be lost here forever :)
slowly figuring stuff out and my preferences in the linux world~~ idk why I liked xfce..... the KDE log in screen is nicer and more sleek and modern~~~
will gnome stuff work with kde? if I install gnome games? I always install gnome games and then never play any of them lol I mean I'd assume they would but idk~~
idk why I'm documenting my journey with trying different distributions or desktop environments here..... cause I feel no one really cares..... but I got no one around me to talk linux to... even if I am still (in my own eyes) a newbie at it....
welp~~~ back to system config~~ :) hope that's fun~~ and to find accessibility settings~~
what was up with the clock tho? why did I have to set my BIOS time to UTC to get it to be local time? how does linux configure time? never noticed that before~~~
I distro hop a lot I think~~~~
and would ya believe it my function keys STILL WORK~~~~ WOOOO~~
edit: there are swipe gestures to go back on browser?? gonna like KDE I think~~~
yet another edit: double check bios cause I'm a doofus sometimes~~ secure boot is still on but now greyed out and can't toggle it off, fast boot and something below fast boot are disabled~~
still have no idea why pure debian is able to load with secure boot on (permanently now I guess) and linux mint wasn't able to despite it being debian as well.... but debian 12 works so neat~~~~
bad thing tho about the "swipe to go back" is that I keep almost doing that while trying to scroll down~~ could just use the arrow keys but got so used to using the touchpad to scroll ...
#personal#thoughts#thinking#i think too much#operating system#operating systems#linux#linuxposting#debian#debian 12#KDE#KDE plasma#Plasma#DE#desktop environment#been a long time since I messed with KDE#got the time fixed#and that was stupidly simple#the drives being weird and having lock icons on everything straightened itself out and idk how#it looks sleeker and nicer than xfce tbh#maybe I was overwhelmed with all the configuration options when I first tried KDE?#cause just at a quick glance there's a lot
2 notes
·
View notes
Text
Thess vs The Most Annoying Reprieve
So I stepped out and picked up the big pain meds, because dear gods did I need them, and came back to an issue that on one level has freed me from overtime today but on the other hand has ensured that my weekend will be a living hell.
See, I left my machine locked down but turned on, because the time it takes for that annoying piece of plastic to boot up is not to be borne. But when I switched it back on, I noticed that Google Chrome (the browser I pretty much have to use on my machine; no one's letting me install Firefox, apparently) had switched itself off ... and the icon was missing from the desktop. I clicked onto where I had it pinned to the taskbar and got, "Sorry, this .exe has been moved or deleted. Do you want to delete this shortcut?"
...wut.
So I did a restart, which did nothing. Then I went hunting in the start menu ... and there was a Google folder, but no .exe, and I wasn't even allowed to open the error log folder. So that was a bust. Now, of course, the stupid machine does have Microsoft Edge on it as default, so I decided to try that. So it accepted my credentials, but then said, essentially, "Sorry, but you're not allowed to access this site with this browser".
......WUT.
Tried the version of Chrome on the remote desktop where our transcription software lives, but I got the same basic thing. So apparently it has to be through the main desktop, and through Chrome, or I'm not allowed to access it. And Chrome vanished without trace for no apparent reason.
This is apparently a thing, though. Having searched here on my main computer, one suggestion is to restart the machine four times. I guess I'll try that while I type this. But the likelihood seems to be that I am getting a reprieve from overtime tonight, with a view to even worse overtime tomorrow, Friday, and possibly over the weekend. Why do I say "possibly over the weekend"? Because yet again, everyone's leaving the long shit for me to deal with, and working unbelievably slowly. Goblin was in for about half the day today and she took all the short things that people put into the queue between 2-3pm yesterday afternoon, leaving all the Monstrosities from the Breast Guy, the Placenta Guy, this new woman who is absolute shit at GI reports, and several others that were put into the queue between 11:45 and 2pm. Goblin left those. New Girl left those. Scruffman left those. Even Milady, who's usually better than that, left those. Temp still isn't in, but she would have left them too. And I am so. Very. Tired of being left with all of it.
Honestly, I'm just tired in general. We have 375 items in the queue right now. Most of that seems to fall on me, and I am fed right up. Also I hurt. And the restart upon restart upon restart doesn't seem to have done anything so it's going to be up to IT to reinstall or fix whatever update bullshit caused this mess. So while I at least don't have to near-on kill myself typing tonight, I have to sit with the sure and certain knowledge that tomorrow, and Friday, and possibly the weekend, are going to be worse. Because no one in that fucking office is going to even try to get us onto an even keel except me.
I swear to the gods, I read through that fucking competency assessment form that we're apparently self-assessing, and realised how much they fucking shouldn't be. There was a whole section on prioritising in chronological order except for urgent cases, and nobody does that shit but me. Worst part is, not only is it very clear they know that, but they take advantage of it to stick me with the bullshit. (I understand with Scruffman, I admit - he's having to do the manager work too and can't afford to be stuck in a ten minute Monstrosity from Breast Guy when an urgent call comes up needing him to browse away from a half-done document to look up a case on the system. The rest of them? The rest of them are just awful.) Anyway, summary is that their self-assessment is all going to be, "We're fine; we know what we're doing" when they FUCKING DO NOT. No wonder they get away with murder.
So I've replaced working myself to death tonight with stressing myself to death tonight over probably having to work myself to death for several more days upcoming, and probably having to cancel my Saturday D&D afuckinggain, because no one in my office seems to give much of a fuck that we are dealing with patient's lives here. I know it sounds like an exaggeration, but it's not. Another part of the competency assessment was "Hey, you do realise that if you screw around or fuck up, it could cause serious damage to the patients' lives, right?" And they're all going to answer, "Yep, I totally understand" and then just ... continue their lazy-ass way through this, and leave me as the only person in the office who understands what we actually do.
Sometimes I wish I still drank. I technically can, but that hits too hard with my meds, so I don't. I guess hot bath, sort out something about dinner, maybe see if the hurt stops enough to do anything but slump in a chair? I typed this mostly in the spirit of, "If I don't vent, I am going to punch a wall" ... and while that would at least give me a break, we can't afford that right now, and it would hurt, and I play games with those hands, so...
5 notes
·
View notes
Text
What is Jailbreaking : Pros and Cons

Jailbreaking lets you install non-official software on a locked device. By jailbreaking, the device owner can access the OS root and all features. It’s called jailbreaking because it removes perceived restrictions.
What is jailbreaking? Most people refer to jailbreaking the iPhone, the most “locked down” mobile device. Early iPhones had no app store and fewer iOS options. The first iPhone was only available on AT&T in the US, so users needed a jailbroken iPhone for other carriers.
Learn if iPhone jailbreaking is worth it and how to fix a jailbroken iPhone in this video:
Apple’s ‘walled garden’ software has always contrasted with Android’s customization. Many jailbreakers want Android-like iOS. Jailbreaking lets users install unapproved apps and customize the interface.
Since its inception, jailbreaking has involved adapting phone and game console codes. It can mean installing custom mobile software or removing movie DRM. It usually refers to Apple products. The iPad and iPod Touch can be jailbroken.
Jailbreaking is sometimes confused with “cracking” (software) and “rooting” (phones). Rooting removes manufacturer protections to install alternative mobile operating systems, like a jailbreak. Many people jailbreak Amazon Firesticks, Roku streaming boxes, and Nintendo Switches to run media software and emulated games instead of the built-in apps.
A jailbroken iPhone or iPad can use the App Store without affecting its core features. Jailbroken devices download apps Apple rejected or use jailbreaking features from independent app stores. After jailbreaking iOS devices, Cydia, a storefront, is most popular.
Hacking forums and sites offer free jailbreak codes to promote unrestricted device use. Although technical knowledge is helpful, most jailbreaks include full instructions and desktop tools to apply the new code.
Sometimes jailbreaking is “tethered” or “untethered”:
Tethered jailbreaks require an on iOS device and computer. Jailbreaking the iPhone requires a computer and software. Untethered jailbreaks : Jailbreaks without computers. Everything needed to jailbreak iPhone is on it. Booting off a computer doesn’t jailbreak it. Since iPhone apps have OS access, jailbreaking is less popular. Apple publicly opposes jailbreaking, so it has fixed jailbreak vulnerabilities in hardware and software, making many iOS versions hard to jailbreak.
Is jailbreaking safe? Phone jailbreaking is legal but risky. Online criminals can hack jailbroken phones.
Jailbreaking your phone abandons Apple security. Side-loaded apps are unsafe in Apple’s App Store because it doesn’t screen them. Jailbreaking your phone disables iOS updates, including security updates, leaving you vulnerable to new threats.
Apple prohibits jailbreaking iOS and warns users of risks, including:
Security holes Stability issues Possible freezes, crashes Shorter battery life Apple discourages iPhone and iOS device jailbreaking. iPhone viruses are rare and usually caused by jailbreaking. Jailbreaking voids your warranty, so fix phone issues.
You should also consider phone ownership and content. Does your boss own the phone? Your work email linked? Your data and company are at risk from malware. Your company is vulnerable to cyberattacks from jailbroken phones.
Companies that give employees mobile devices usually protect company data. Locking down phones to allow certain features, updating devices and apps, and installing a mobile device agent to detect jailbroken phones are examples.
Pros and cons of jailbreaking Jailbreak benefits Increased device control Apple aims for a unified design. If that’s too restrictive, jailbreak your phone to add icons, wallpapers, and menus. Instead of Apple or anyone else, you become full device administrator. Install screensavers or icons on your iPhone home screen. Jailbreaking allows you to connect your iPad to your PC and control what you see and do by allowing file system access and device communication.
Install and use unauthorized apps Apple removes App Store apps for security. Jailbreaking installs non-App Store apps. The most popular jailbroken phone storefront, Cydia, lets you install games and networking apps. Also banned from Apple’s app store are retro gaming emulators, which let you play older computer games for free. However, Cydia provides them free.
Remove pre-installed apps You can’t change or delete iOS’s default apps like Apple Watch, Weather, Games Center, etc. Non-users dislike these apps’ memory usage. Replace Apple’s default apps with third-party ones with jailbreaking. Siri can use Google Maps instead of Apple Maps for directions.
Extra anti-theft features Some jailbreakers say it boosts anti-theft. Find My iPhone doesn’t work in airplane mode, off, or offline. The jailbreak app iCaughtU claims to outperform Find My iPhone. The front-facing camera emails the owner a photo of a thief who enters the wrong passcode.
Cons of jailbreaking Stop auto-updates Apple will stop automatic updates. Each iOS version requires the jailbreaking community’s hack. Since jailbreaking each iOS version takes time, you can’t update your jailbroken phone until the latest update is jailbroken. Major updates may make jailbreaking difficult.
Problem updating software Several unauthorized modifications have rendered iPhones inoperable after iOS updates.
Voiding phone warranty The iOS end-user software license agreement prohibits unauthorized iOS modifications. Unauthorized software may prevent Apple from servicing an iPhone, iPad, or iPod touch. If your jailbroken device breaks, Apple may deny repairs.
Shorter battery life Hacked software drains iPhone, iPad, and iPod touch batteries faster.
Your phone could brick Bricked phones cannot boot, respond to input, or make calls. Jailbreaking does not brick the phone, but it poses risks.
Content or services may disappear Due to the loss of iCloud, iMessage, FaceTime, Apple Pay, Weather, and Stocks, jailbreaking a phone for more content can backfire. Third-party apps using Apple Push Notification Service have had trouble receiving notifications or received notifications from hacked devices. Push services like iCloud and Exchange have server synchronization issues. Third-party providers may block jailbroken devices.
Your phone may crash more Your jailbroken iPhone or iPad may crash more. Jailbroken apps can access features and APIs Apple-approved apps cannot, so they may not be tested. The device may crash frequently, freeze built-in and third-party apps, and lose data.
Unreliable voice and data Jailbreaking can cause dropped calls, unreliable data, and inaccurate location data.
Data breaches Hackers accessed 225,000 jailbreakers’ iCloud accounts. Security vulnerabilities in jailbreaking allowed hackers to hack devices.
Security can be compromised iOS is one of the most secure mobile operating systems because it’s closed to protect your data and system. Jailbreaking your phone increases hackers’ chances of stealing data, damaging it, attacking your network, or installing malware, spyware, or viruses.
Security risks of jailbreaking Security risks arise from jailbreaking phones. Jailbreak gives you more device control, but apps get more control. These apps requesting root access pose the greatest security risks. Malware can gain root access to all data.
Jailbreaking bypasses Apple’s “walled garden”. Because jailbroken phones bypass Apple’s app vetting, viruses and malware are more likely. Jailbreaking allows free app and game piracy. This means you trust app developers over Apple.
Jailbroken iPhones can compromise bank account, password, and social media data. This risk was highlighted by KeyRaider, which stole 225,000 Apple IDs and thousands of certificates, private keys, and purchasing receipts. The victims reported abnormal app purchases and ransomware-locked phones.
Jailbroken Malware and bugs can crash iPhones and disable important features. Smartphones raise mobile crime risk. You must monitor new threats and scams and install comprehensive mobile security.
Read more on Govindhtech.com
#jailbreaking#iphone#Amazon#apple#malware#CyberSecurity#ipad#AppleWatch#technology#TechNews#govindhtech
6 notes
·
View notes
Text
You don't necessarily need a PC either. I hacked my 3DS a few years back using the SD card slot on my phone.
Advantages of jailbreaking your 3DS include:
Remove the region lock allowing you to play cartridges and eShop games from outside your region
Play games/ports/emulators and use applications the community has developed (there are really good native ports of Sonic Mania and Half-Life 1, assuming you can look past the loading times, and there's a port of Sonic Robo Blast 2 (3D sonic fangame that's low key better than all official 3D sonic games) that plays in 3D)
Install community-created home menu themes from https://themeplaza.art/ and create your own custom ones using Usagi Theme Editor
Copy your physical DS and 3DS games onto your SD card as digital copies and have them show up as regular icons on your homescreen so you can finally stop worrying about losing the cartridges
Create backups of your save games, and copy savegames from digital copies to physical cartridges, or vice versa, or from one cartridge to another
(Optional) Set a PIN lock on your 3DS that must be entered before it will turn on
(New 3DS only) Overclock the 3DS's processor to make demanding games less laggy
(New 3DS only) Send a screen capture stream via Wi-Fi to your PC where it can then be recorded or streamed to Discord/Twitch/etc., no need for an emulator
Install mods/romhacks (I've heard good things about Pokemon Shattered Sapphire and Ruined Ruby, and there's a really cool mod for MarioKart 7 called CTGP-7 that more than triples the number of tracks in the game. Some of the ones it adds are even good!)
Install save file editors for games like Pokemon and Animal Crossing that let you give yourself whatever items/stats you want
Use gameshark codes in your 3DS games, cartridge or digital (one of the homebrew apps the tutorial has you install comes with a list of every Gameshark code ever made for the 3DS, and all you have to do is turn them on)
and, of course, piracy (I'll have a whole section on that down below)
Disadvantages of jailbreaking your 3DS include
Nothing
Literally nothing at all
Jailbreaking is free and 99% of the software you will install is open source
You can still play games online download updates from the eShop, and even install new firmware versions after jailbreaking
All of your games, home menu themes, and save data will be exactly where you left them
Every single thing you could do on your 3DS before jailbreaking works exactly the same after
The main home menu/interface of the 3DS does not change at all -- all of the added functionality comes from the new apps it has you install and the Rosalina hacks menu you can open by pressing a key combo.
Sold yet? Great! Head on over to https://3ds.hacks.guide, follow all the instructions they give you, then come back here. I mentioned piracy earlier, and there are a few more apps you'll need to install if you want... the full experience.
there's a homebrew app you can install called hShop, which contains all content ever released on the eShop in every country the 3DS released in, AND every cartridge exclusive game AND every demo cartridge (the versions of games you'd have played if you walked up to a 3DS in a store) plus a few fan translations for the foreign-language-only titles and a few homebrew apps, all available for free. The 3DS's wifi chip is a little slow for downloading games, though, and there's a desktop app you can use to download games from your PC and then copy them onto the SD card that runs *way* faster than FBI does. I'll make a tutorial on using that if anyone's interested.
You can also install TWiLightMenu++ to play .nds ROMs straight from your SD card, no need for a flashcart, along with a cutesy little file browser styled after the DSi Menu (theme customizable). You can download a ROM file of every DS game ever released from archive.org, here. there's currently no way to browse that library from the 3DS itself, unfortunately, so you'll have to download them from your PC. it doesn't really matter where you put the files since TWiLightMenu will be able to find them regardless, but the default location is SD root/roms/nds/)
you can also install openAGBfirm to play GBA ROMs off your SD card using the 3DS's little-known GBA compatibility mode. Since they run natively rather than using software emulation, they run in full speed with perfect compatibility (assuming your GBA ROM is 32MB or smaller to fit within the 3DS's RAM and doesn't have any extra hardware like WarioWare's tilt sensor/rumble pack or or Boktai's light sensor). The downside is that since this isn't an emulator, you can't create savestates, and closing the clamshell doesn't pause the game. (This one comes as a FIRM file rather than a homebrew app, so you'll need to extract the .firm file into SD root/luma/payloads/, and you access it by holding the start button while turning the handheld on
NOTE: if you want to really take advantage of this wealth of content, you'll need a larger SD card than the 4GB one the 3DS comes with. The 3DS doesn't have a maximum SD card size, but it requires them to be formatted FAT32, and the built in Windows format tool will refuse to format any disk larger than 32GB with FAT32 even though FAT32 supports up to 2TB. Why? Because Microsoft would rather you use their newer filesystem, exFAT, which has worse compatibility, but more features, and, more importantly, which Microsoft collects royalties on. if you want to use a larger SD card than that, you'll need a separate tool to format them, such as guiformat. I have a 128GB SD card in my 3DS and it works great!

I made this a couple of months ago but. hack your 3ds. do it right now.
31K notes
·
View notes
Text
Broken Segoe Fluent Icons in Windows 10 & 11
Back in June of 2019, my old computer's motherboard decided to stop working, and I found myself having to build a new computer. Originally I ran Windows 10 on this computer, since the license from the old computer could be moved over. And while this computer has been serving me well for the past few years, there's been a small graphical problem that I've not been able to resolve until now.
Occasionally, when installing a software update, I've noticed that certain icons would just turn into a blank box. And this was despite going back and clean installing Windows to try and correct the problem. And it was always something random, like the little lock icon to show an encrypted WiFi SSID, or something like that.
And it turns out, I wasn't alone with this particular issue. I've found a few articles on Microsoft's website. All of which suggested to re-install either the Segoe MDL2 Assets or Segoe Fluent Icons fonts to correct the problem. So I would take a copy of the font from my laptop and try to re-install it on my desktop. But that would never correct the problem. And a few of these articles also mentioned that this fix would not work for them as well. Yet none have offered a solution.
After years of scratching my head over this, I may have finally figured out the solution. I'm not sure what causes it in the first place. Possibly it's because I use a lot of custom installed fonts, which could be messing with these settings. But this solution seems to have fixed the issue.
So, in the past, I found that creating a new user profile would correct the problem. But at the same time, it would delete any fonts I installed. Originally I thought that the fonts were being stored in C:\Windows\Fonts. But it turns out that they're actually being stored in C:\Users\[username]\AppData\Local\Microsoft\Windows\Fonts\. At the same time, there is a registry key that points to all of the fonts a user has installed. HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Fonts. So when I looked in that key, there is a string that reads Segoe Fluent Icons (TrueType). And I found that instead the value being set to "SegoeIcons.ttf", it was set to "SegoeIcons_1.ttf". Somehow a copy of the font was created and this registry key was set to use the corrupted copy to draw icons on the taskbar, start menu, and task manager.
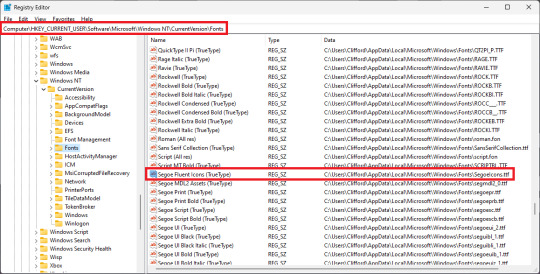
Changing this value back to "SegoeIcons.ttf" then rebooting the computer finally ended up resolving this problem.
I'm not sure if this will help anyone, but I figured I'd at least document this fix just in case.
1 note
·
View note
Text
DaVinci Resolveのアップデート 原文・Deeplによる一部翻訳
About DaVinci Resolve 18.6
The free version of DaVinci Resolve 18.6 includes all of the same high quality processing as DaVinci Resolve 18.6 Studio and can handle unlimited resolution media files. However it does limit project mastering and output to Ultra HD resolutions or lower. DaVinci Resolve 18.6 only supports a single processing GPU on Windows and Linux and 2 GPUs on the latest Mac Pro.
If you need features such as support for multiple GPUs, 4K output, motion blur effects, temporal and spatial noise reduction, multiple AI-based tools, HDR tools, camera tracker, voice isolation, multiple Resolve FX, 3D stereoscopic tools and remote rendering, please upgrade to DaVinci Resolve 18.6 Studio.
We hope you do decide to upgrade as your facility grows and you do more advanced work!
What's new in DaVinci Resolve 18.6.1
Systems now default to prefer proxy for single and multi user projects.
Addressed a cloud sync issue with projects updated from 18.5.
Addressed delays when performing ripple edits on long timelines.
Addressed issue where editing or moving clips would stop playback.
Addressed issue showing retimed clips with handles on the color page.
Addressed issue navigating clips with show handles enabled.
Addressed issue with grabbing stills after deleting a gallery album.
Addressed issue importing suffixed multi mono files from media storage.
Addressed waveform jump issue when performing multiframe nudges.
Addressed issue navigating powergrades album in certain sort modes.
Improved in or out point behavior in the transcription window.
Dolby Vision 300 nit target display is now available.
Addressed issue with multiple timelines showing as current timeline.
Addressed a crash when using certain fonts on Text3D.
Addressed issue with grid depth occlusion in the USD viewer.
Addressed issue with disappearing key markers in the splines view.
Addressed issue with moving locked point selections in the splines view.
Addressed issue with polyline point scale and twist in the Edit viewer.
General performance and stability improvements.
---------------------
単一ユーザーおよび複数ユーザーのプロジェクトで、システムがデフォルトでプロキシを優先するようになりました。 18.5 から更新されたプロジェクトでのクラウド同期の問題に対処しました。 長いタイムラインでリップル編集を行う際の遅延に対応しました。 クリップを編集または移動すると再生が停止する問題に対応しました。 リタイミングされたクリップがカラーページにハンドル付きで表示される問題に対応しました。 ハンドルの表示を有効にしてクリップをナビゲートする問題に対応しました。 ギャラリーアルバムを削除した後に静止画を取り込む際の問題に対応しました。 メディアストレージからサフィックス付きマルチモノラルファイルをインポートする際の問題に対応しました。 マルチフレームナッジ実行時の波形ジャンプの問題に対応しました。 特定のソートモードでパワーグレードアルバムをナビゲートする問題に対応しました。 トランスクリプションウィンドウのインまたはアウトポイントの動作を改善しました。 Dolby Vision 300 nit のターゲット表示が可能になりました。 複数のタイムラインが現在のタイムラインとして表示される問題に対応しました。 Text3D で特定のフォントを使用するとクラッシュする問題に対応しました。 USD ビューアでグリッドの深度オクルージョンが発生する問題に対応しました。 スプライン ビューでキーマーカーが消える問題に対応しました。 スプラインビューでロックされたポイント選択を移動する際の問題に対処しました。 編集ビューアでのポリラインポイントのスケールとツイストの問題に対処しました。 一般的なパフォーマンスと安定性の改善
---------------------
Minimum system requirements
Windows 10 Creators Update.
16 GB of system memory. 32 GB when using Fusion.
Blackmagic Design Desktop Video 10.4.1 or later.
Integrated GPU or discrete GPU with at least 2 GB of VRAM.
GPU which supports OpenCL 1.2 or CUDA 11.
NVIDIA/AMD/Intel GPU Driver version – as required by your GPU.
Installing DaVinci Resolve software
Double-click the DaVinci Resolve Installer icon and follow the onscreen instructions. To remove DaVinci Resolve from your system, go to the Programs and Features control panel, select DaVinci Resolve, click on Uninstall and follow the onscreen prompts.
Migrating legacy Fairlight projects to DaVinci Resolve
In order to import legacy Fairlight DR2 projects into DaVinci Resolve, download and install the following utility on your Windows system: https://downloads.blackmagicdesign.com/DaVinciResolve/Fairlight-Project-Importer.zip
After installing the utility, you should see an option to "Import Fairlight Project" in the Fairlight menu in DaVinci Resolve.
Additional information
Please refer to the latest DaVinci Resolve configuration guide for details on Windows support, including certified driver versions for third party hardware. It is available from www.blackmagicdesign.com/support/.
You will also need to download and install the latest Blackmagic Design Desktop Video software for monitoring with your Blackmagic Design video hardware. Desktop Video is available from www.blackmagicdesign.com/support/.
© 2001-2023 Blackmagic Design Pty. Ltd. All rights reserved. Blackmagic Design, Blackmagic, DeckLink, Multibridge, Intensity, H.264 Pro Recorder and "Leading the creative video revolution" are trademarks of Blackmagic Design Pty. Ltd., registered in the U.S.A and other countries. Adobe Premiere Pro, Adobe After Effects and Adobe Photoshop are registered trademarks of Adobe Systems. Avid Media Composer and Avid Pro Tools are registered trademarks of Avid. Apple Final Cut Pro, Apple Motion and Apple Soundtrack Pro are registered trademarks of Apple Computer.
Updated October 05, 2023.
0 notes
Text
Chapter 4
White-hot shower spray scalded the malaise of isolation off my skin. The needles on my legs and fur on my pits were 3 or 4 days long. I opened a fresh razor to erase them. After rinsing the errant hairs away, I remained under the showerhead for 4 more indulgent, liminal, lavender-scented minutes before shutting the water off.
After lotion and skincare, I left the clinging fog of the bathroom to let the dry air wash over my naked skin. A playlist of recent trial updates was still looping on my laptop. I half-listened while working out what to wear. The mess of short jackets and shorter dresses hanging in my small, single closet would compress into a diamond one day. I sifted through hangers like a file folder. Fitting, since every article of clothing looked like a manila envelope to me.
“The footage initially submitted to evidence by the federal attorney’s office shows Chambers drawing a gun before being shot down by U.S. Marshals in Athens, Georgia,” a CNN newscaster named Stephanie Gutiérrez said over footage of lawyers descending the court steps. “However, months later, a former Ek Inc. employee leaked evidence to the Miami Herald proving the video was altered using the company’s facial recognition and reconstruction software, deepfaEk.”
My phone said 1:24 PM. Deep breath in. Slow breath out. It was just a function. No need to read into Lear suddenly demanding to see me in person. He wasn’t mad at me. That’s a leap to make, even if he is so notoriously unhinged that it earned him a nickname in prison.
There, on the floor of the closet in a nest of designer shoes: the go-bag, a black duffle with shaggy holes and worn straps. Static crawled up my spine. I looked back to my laptop screen.
The camera cut from Stephanie Gutiérrez’s face to 2 videos side-by-side, both of Joseph Chambers getting ventilated by half a dozen Marshals, an almost-matching pair of shaky-cam snuff-films. On the left, an enraged face and an arm rising from his hip, the black smudge of a pistol in his hand. On the right, an open palm and wince of fear.
They loved that side-by-side. I’d seen it maybe a hundred times, in every newscast, every recap, every update. One article even had an embedded gif, Chambers’s final moments looping over and over and over and over and over and over and over.
My fingers found stiff stretch-fabric. It was my favorite dress, one of Angelo’s, black and white, tight and simple. I freed it from its hanger; held it in my arms.
Getting ready got easier after that. A smooth-cupped, copper-colored bra would be invisible under the bar of white jacquard down the front of the otherwise black bodycon dress. Through Angelo’s sartorial alchemy, I never needed shapewear with his garments. You could pull one of his dresses on and all you needed was to smooth it down. A bad bitch in ten seconds flat. I could breathe again.
Dolling myself up brought my pulse down. Rich foundation, smooth contouring, dark lipstick, stiletto eyeliner—multiple layers of security. It had the satisfaction of turning each lock on my door. In the mirror, I didn’t look like a mouse hiding in the dark hole of my apartment. I was a fugitive hacker; a cyber-revolutionary; a big, bad criminal. If Lear was going to off me, I’d damn well look like someone who deserved it.
I went to my desk. My 2 monitors made a sideways T shape: one a Kali Linux desktop in night mode, a few scant icons adrift a #00000 sea; the other turned vertically, Visual Studio with top-to-bottom code, an obsidian monolith carved with runes that acted as an invocation. My laptop nestled between, corners scuffed and keys greasy.
Stephanie Gutiérrez was back on camera. “With missing eyewitnesses, vanishing chat logs, and Ek’s legal team alleging 6th amendment violations,” she said, “sources say Julian Ek’s acquittal was no surprise.”
Vanishing chat logs. Missing eyewitnesses. 6th amendment violation. Stephanie Gutiérrez stared down the barrel of the camera, and I swear she was looking right at me. Stupid, she seemed to say to me. Sloppy. I slammed my laptop shut. After 3 3-second-long breaths, I unplugged the laptop to stuff it in my patch-covered shoulder-bag.
I checked the mirror on the back of my door. Something wasn’t right. Donning my leather jacket and swapping my heels for black, badass Tank Steiger boots was an improvement, but not the problem. I prodded, pinched, preened my reflection, searching for the bug in my code. Something stiff clicked in the front pocket of my jacket: my oversized, prescription sunglasses.
Aha. I swapped out my round spectacles, and there it was, the closed bracket of Anna-Wintour anonymity. Clean build, no errors found. Whatever bad code was running under the hood—my racing brain, my shaking hands, my unsteady breath—the front-end was functioning to perfection.

“I had a dream. I was in a strange land. A vast wilderness. I went on and on, but met no one. I called, I shouted... but no one answered. I was alone.”
-Akira Kurosawa, Ran
Chapter 1
Look, I get this question a lot for obvious reasons, so I know you won’t like the answer. It’s dissatisfying. But, because you asked, the best cybersecurity commercially available is something called an air-gapped computer.
An air-gapped computer has no network card. You won’t see a cerulean ethernet cord spouting from the stern of the case. There’s no hard, hollow plastic antenna to receive a wifi signal. It doesn’t have Bluetooth. My compsci professor at Tech explained it like this: there’s a literal wall of air—a gap—between the computer and anything that could inject it with compromising code. This abstinence-only approach makes air-gapped computers cheap, simple, and impenetrably secure.
But much like celibacy, not a lot of people opt for the air-gapped method. What’s the point of a computer, they ask, without e-mail and Twitter and porn? And I understand that. There were days I got so dog-tired of the manual data dumps, of examining each file down to the binary before connecting the USB, of hand-transcribing scraps of code onto sheets of paper, of the day-to-day ennui of existence inside those invisible walls. But when I broke into a system, all I saw back then was each and every way very, very bad things could get in.
The air wall was better. It let me breathe.
My laptop had to be online so I could access those vulnerable systems, but my desktop was air-gapped—a little black lockbox of my pdfs, jpgs, pngs, mp3s, mp4s, xls, txts, zips, bins, bats, dats, all my associate backgrounds and every line of my code. Knowing how safe they were in there calmed me at times like this, when I felt Julian Ek’s omniscient data network watching me like an enormous, electronic eye.
Notifications came like machine-gun fire into my phone. My apartment was dark, black under blackout curtains. I saw nothing, heard nothing, felt nothing but automated search alert after automated search alert filling my notifications: ek trial, julian ek trial, ek trial update, ek trial verdict, ek inc, joseph chambers, joseph chambers shooting, joseph chambers deepfaEk, deepfaEk, deepfaEk scandal, deepfaEk shooting edit, deepfaEk trial. More and more, on and on. I With dread, I went to Twitter, and there it was in blue and white. #EkAcquitted. It was the #2 trending topic, below #NationalVideoGamesDay. My hands began to shake. It had to be misreported—a mistake. I searched “Ek trial” and clicked the first link, scrolling past Ashlan’s disbarment and the Marshals’ conspiracy convictions to read the 6 words I’d dreaded for 4 years.
Julian Ek acquitted on all charges.
Ek walked. I went to the Herald for nothing; became a fugitive for nothing. I gave up my parents, my friends, my condo—my dream job obviously. I blew my whole life up, and now I’m stuck here, all alone on the other side of the world. Jeopardy attached, meaning I was officially of no use to anyone; meaning I could never, ever go back home. This dusty, pitch-black 300-square foot apartment really was my life.
I was hyperventilating. Breath after keening breath, air refused to reach my lungs, only rattle in the back of my throat. My head and stomach and knees went fuzzy. My phone screen smeared as it slipped from my hands. I reached for it and missed. The clatter of it hitting the floor—the dull pain of my thigh hitting the floor too—degraded into garbling static as I sank into gasping, grasping unconsciousness.
#sry this was late i have no excuses#lesfic#lesbian fiction#ff romance#lgbt reads#sapphic#sapphic romance#wlw#wlw romance#contemporary romance#crime#sapphfic#lesbian romance#queer fiction#queer books#serial fiction#substack#authors#excerpt#write#prose#lesbian author
26 notes
·
View notes
Text
⌖ Think I’m GOOD ENOUGH with a COMPUTER to get into SOMEONE ELSE’S? FIND OUT ON MY ALT STATION!
#⌖ online#// it doesn't involve a ton of technical knowledge!#tl;dr she's in her scambaiting arc and what happens is scammers pretend to be a reputable company and use remote access software to get into#a victim's computer. but it requires the victim to believe the scammer and download the software and accept connection. what baiters do is#simultaneously request access to the scammer's computer and social-engineer their way into getting the scammer to accept it.#newer scammers (who are usually the 'front line' ppl who pick up the calls) don't know better and accept the baiter's request.#and thus the scambaiter gets into the scammer's computer and wreaks havoc. (sometimes this means stealing their files. this hinders their#operation and takes away their list of victims and also have evidence to give to authorities. sometimes it means destroying their computer#by unleashing viruses/ransomware or locking them out of their computer by changing the password or syskeying.)#Al just wants to see if she can get access. She's watched her friend wreak havoc but she's not experienced with the remote softwares enough#to pull off a syskey. Not yet. She'll probably change their desktop to a picture of her though. Something silly like that.#Screenshot their desktop and then delete their icons and replace their desktop with a pic of the bg + icons so they can go insane clicking#on the 'icons' and wondering why the icons won't open. Set the text on their computer backwards. Basically... be a nuisance.#Her friend subscribed a scammer to Al's channel (as well as his own) so she'll probably subscribe the scammer to her and her friend.#(yes she considers her scambaiter v*xtuber friend to be her friend! they are friends now. superficial friends.)
1 note
·
View note
Text
Three resources that are absolutely game changing for image descriptors (or at least they were for me):
1- Image to text converters
I realized recently that a lot of people don't know this: you don't actually have to manually transcribe the written contents of an image! There are softwares that do it for you and all you have to do is copy and paste. And most of them are very good!
If you have an Android phone, you even have a built-in app that does it for you. It's called Google Lens. Anytime you open a picture in Google Photos, there will be a Google Lens icon in the bottom (it's the third icon). Just click there and then select the text you want to copy and done!
Note: I wouldn't normally recommend Google services due to privacy reasons, but in Google Lens' case, you literally can't uninstall it from your Android phone. So since it's already there, might as well use the commodity
Apple has recently launched a similar feature for their phones, but it's only available on the latest models and I believe it's in beta. However, even for Apple users or desktop users, there are online options! I've not used them extensively but I have tested ImageToText dot info and it works well, including on mobile. If anyone has a suggestion for other sites that do that service, feel free to add them
2- Case converters
The bane of my existence was having to do plain text of long caps lock sequences (or worse, alternated cases sequences) since even copying and pasting doesn't work, so you do have to transcribe everything it says manually. Except wait, no you don't! There are online resources that do that for you. Just copy the text, paste there, select "Regular formatting" and done!
I have always used ConvertCase dot net. Mobile friendly, has a "copy to clipboard" button, and never gave me a single problem
If you don't understand why that's useful, you can check out my plain text masterpost in the link below:
Link
3- The accessibility server
I am once again recommending the accessibility server. I was not involved with its creation and am not a mod there, just a regular, and I still promote it almost daily, so you know it's good
The accessibility server is a server where you can ask volunteers to do an ID for you! Yes, that's right, no more waiting for the time and energy and ending up with 300 undescribed posts in your drafts, laughing at your misery. If you're a newbie or want to start your hand at image describing but don't feel like you're good enough, it's also a great resource!
You can also use it to ask questions, ask someone to check over your ID, ask someone to look through the notes to find an ID for you if you're using the app and the notes aren't working, ask for audio transcriptions and video descriptions, find help for accessibility-related projects, ask for resources on how to do IDs, meet other descriptors, and much more! It has made my life so much easier and it really is a great space. Link to join below:
Link
TLDR
Three great resources for doing IDs are: image to text converters (Google Lens, ImageToText dot info), case converters (ConvertCase dot net) and the accessibility server on Discord, where you can ask people to do IDs for you
215 notes
·
View notes
Note
Hello, can I request headcanon from Germany and Prussia with an S/O that, being higher, always charges them when they are distracted? (I believe in the supremacy of tall couples)
Gilbert Beilschmidt, Ludwig Beilschmidt, Antonio Fernandez Carriedo and Lovino Vargas with Tall S/O who Always Charges Them When They Are Distracted.
➽───────────────❥➽───────────────❥
A/N: Hello there Anon! I'm not sure if you want this headcanon as fluff or as a comedy because I can see that these characters would have a funny reaction when they are surprised with the S/O Antics. Anyway, I hope you like the final result.
Gender: Neutral
Warning: None
➽───────────────❥➽───────────────❥
Gilbert Beilschmidt - Prussia

It is canon that Gilbert Beilschmidt height is 177 centimetres, which is around 5'9 in feet which is kind of tall but not as tall as Netherland, which is 185 in height. Because of that, I can see he would have S/O who's higher than him.
With Gilbert's Personality, he would also nonstop make puns about how much tall you are. He would also give ridiculous nicknames, calling you beanpole, tower, or skyscraper.
However, if you are tall but still a little bit shorter than him below 177 centimetres. Gilbert still gonna tease you about your height as he would call you Shortie, Chibi (Shrimp), or Pipsqueak.
Because of his non-stop teasing and his height jokes towards you. You decide to do an act of revenge on your boyfriend to make him stop teasing you.
You have a genius idea of how to repay Gilbert's pranks as you realize that you can take an advantage of your height to prank him as the devil on your shoulder snickers.
You can imagine his expression when you are running up to him like a bull as he was distracted. It was one hundred percent worth it, seeing him shriek like a little girl.
Correct, you were charging up to him by running with a maximum speed as he was feeding his Gilbird. He didn't realize you were watching him from far as you sprint like there was no tomorrow.
"GILBERRRRRTTTT!" You scream, earning a loud German crurse from Gilbert who immediately drops the seeds on his hands and putting his hands on his chest to calm his racing heart. It was worth it.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
A pair of (S/C) hands holding out a shiny metallic object on their/her/his hands before putting it on top of the table carefully, knowing the object that they/she/he held in their hands is cost an arm and a leg. (Y/N) nails slid into a thin lines between of the stuff before pulling it upwards, showing a computer screen.
A bright light shines throughout your whole bedroom, showing many icons on it along with desktop and other software. (Y/N) (L/N) glances at the clock before starting to type down the given assignment from their/her/his boss and there were many of them. Not wanting those papers to pile up, you began writing them to lessen the loads from your boss.
But all of those peaceful moments with a cup of coffee on your table are ruined in an instant. From far away, a pair of red eyes with platinum blonde locks standing behind the door of your bedroom with evil written all over his lips and his smile. It is a perfect chance for the Prussian male to distract you from your job and cause trouble for you.
Prussia slowly came up to you after pushing the door open without causing any kind of sound since he did not want to alarm you. It was silent for a few seconds until you look up to see some of the papers that were on the table are gone as if it just disappears into a thin air. Panicking, your eyes glancing around to see where you could have put it.
'KESESESESE' You hear your boyfriend laughter.
"Gilbert! I know you are teasing me! Where did you put it!" You turn around and giving him a menacing glare.
"Vhat are you talking about? I don't know chat do you mean by it," he's playing an 'I'm innocent' card at you.
Pushing up both of your knees, you began walking around to search for the missing paper until you saw it was on top of your wardrobe. Because of your height, you were able to take it away without any struggles but once you turn around to scold your boyfriend, he already disappear somewhere else, causing you to be even more peeved than before.
Timeskip
It was lunchtime and everything was peaceful, as well as your boyfriend Gilbert who is feeding his birds with seeds in his hands as he was humming out a song. (Y/N) almost feel bad doing this but he did pull a prank on you when you were working so he needs to get a little bot of repayment after the stunt that he just pulled.
By all of your might, both of your feet clicked against the floor as your arms swung side by side with full power. 'GILLLBERRRRTTTTT!" You shouted, charging up at him like a raging bull to scare the living shit out of your boyfriend. Hearing your scream, Gilbert immediately shrieked 'SHIT!' before spilling the seeds from his hands.
Seeing his reaction, you couldn't help but laugh at his reaction. You did not expect he would scream in surprise like that. Gilbert turn around with confusion and surprise still written all over his face "V-vhat just happened? Did jou just scream like a banshee?" he asks. With a cheeky yet sheepish smile, (Y/N) nods, pulling out their/her/his innocent smile.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
❀
❀
Ludwig Beilschmidt - Germany
Unlike Gilbert, he isn't as prankster as his brother and he never makes fun of your height as Gilbert did. Even if he is teasing your height, it's not as annoying as what Gilbert did.
In this case, it is you that often pranking your boyfriend Germany since he has a funny and cute reaction sometimes after teasing your tall boyfriend.
Anyway, it is canon that Ludwig Beilschmidt's height is 180 centimetres which is 5'11 in feet, a little bit taller and bigger than his older brother who is 177 centimetres.
Because of his height, it would be kind of hard to see s/o who is taller than him in case you are female but I can see someone taller than him in case you are male.
Many people would be intimidated by the two of you since you two are tall and your best friends would tease the two of you that you two have the power of tall couples.
As I was saying, you often annoy him either in purpose or not on purpose but today it seems that your tickle bones are tickling after a long time of boredom.
As he was smearing the chocolate on the cake after baking, you decide it was a good idea to scare the living shit out of your boyfriend, Ludwig Beilschmidt.
Because you made him drop the chocolate icing and made a mess on the cake. Ludwig made you icing the cake as he watch your every movement with an intimidating glare.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
It was a beautiful day with the light of the sun shining throughout the window, flowers blooming and birds twitting their morning songs to wake the civilians. A giant ambled around the kitchen, preparing some of the ingredients that he needs to make a chocolate cake for a snack as he grabs all-purpose flour, eggs, sugar, cocoa powder and other important stuffs.
His eyes focused on the view of the outside where he can see people passing by and enjoying the spring where flowers are blooming and decorating the town. Ludwig takes a deep breath before he starts to heated up the oven before starting to make the dough for the cake along with the icing.
On the other side of the bedroom, a person with (H/C) and (E/C) snores throughout the morning until their/her/his alarm starts to ring out loud. The deafening ring made (Y/N) jump in fright before they/her/his eyes opened to look around the bedroom to see Ludwig already gone from the bed.
'Huh? Where is he?' (Y/N) asks themselves/herself/himself.
Feeling still a little bit drowsy from the slumber, (Y/N) rubs their/her/his eyes and stretches the arms out along with the legs to feel the satisfying pop. (Y/N) carefully steps out from the bed before walking to the bathroom to see the reflection which was really messy because of the birds nest hair, wrinkled shirt, and dried drools underneath the mouth.
Embarrassed with the current state where you look hazardous, your hands cupping the water that were running after you twist the knob and splash your face with the running water before turning it off and dried your face with a napkin.
After cleaning, you slowly leaving out of the bedroom and go to the kitchen where you can see your husband Ludwig Beilschmidt baking with the 'kiss the chef' apron. which looks ridiculous on him but cute nonetheless since the apron was the gift from you in April fool.
A bulb appears on top of your head and a smirk adorns your face. Getting ready, you prepare yourself by walking backwards without causing any noises before starting to run from far away "LUUUUDWIGGG!!!!" You shouted.
The bowl that was in his hands immediately dropped with a loud crashing sound and chocolate was spilt everywhere "Scheiße!!!" he curses before dropping the icing on the ground. everything suddenly turns silent and you realize the stunt you just pulled are going to bite you back "Oh...no..."you whisper, backing away and getting ready to escape Germany's wrath.
"(Y/N).......Come here,"Ludwig commanded
"Hey Schätzchen (Sweetheart), l-let's talk about this," you began to sweatdrop.
"Eins.....Zwei... " Ludwig began counting down.
"UUUHHHH GOTTA GO!!" You ran away from mad Ludwig.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
❀
❀
Antonio Fernandez Carriedo - Spain

It is canon that Antonio is quite tall but not as tall as Ludwig. He is just one centimetre shorter than Prussia which means he is 176 centimetres.
I can see he has a S/O who is taller than him or just a few centimetres than him which means you're also tall for your peers. You two literally look like a walking model since you two are gorgeous.
People are jealous of you and your boyfriend's height. They would ask you two how you two can get so tall and what kind of exercises you two did.
Antonio can be quite a prankster but not as annoying as Gilbert because of this. You did a prank on him when he was distracted by charging at him like a bull.
The pranks that he would pull aren't as hardcore as Prussia. It would most likely just be a silly nickname such as calling you Torre de Cristal (The highest building in Spain)
However, he used to be a matador of a bull so he can sense that you are coming up at him to scare him so he just smirks or smile innocently and stepped away.
Instead of you who win the prank, it was him who were laughing his ass off when you look at him with a priceless face when he dodges you charging up at him.
Don't worry, he did apologize to you for the prank that he pulled twice by making delicious churros for you if you like sweets or his special spanish dish as a way for him to say sorry.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
It was really hot on the outside, especially around 12 in the afternoon when the light of the sun feels like a stabbing needle pricking your skin with heat. It was very tiring to work in tomato field when outside was really hot, especially when digging to plant the tomatoes seeds and picking the ripe tomatoes.
Wiping the streaming sweats on the forehead, (Y/N) (L/N) decides to stop for a moment before standing up after putting the tomatoes inside of a basket "el cariño (Sweetheart), I need to go to the kitchen and take a drink. Is it okay for me to rest?" You ask your husband.
The young Spanish man with curly brown hair, green eyes, lightly tanned skin and a khaki suit glances up at you with a smile on his face, "Sure, Mi ángel (My angel). You can rest, I will continue picking the ripe tomatoes," Antonio chrips happily as he's continuing his activities whereas you're going to the kitchen.
Inside the kitchen, your hands pulled the door of the fridge as you look up for any kind of cold drinks but there were none until you open the freezer which was higher. You're tall but you're not as tall as your boyfriend and because of this, it annoys you because you had to be on your tip toes before taking one of them and drinking the cold beverage. This makes you plan to revenge on your boyfriend.
Timeskip
After leaving the room, (Y/N) sees Spain is digging a new holes for the tomato seeds and it is a perfect chance for you to prank him since he is focused on his job. From far away, you began running up to Spain at maximum speed "ANTONIOOO!!!" You shouted as you got really close to him.
However, his reaction makes you surprised because he did not jump in surprise or scream like you hope. He was just standing there and before you crash, he immediately stepped away before turning around to look at you with a cheeky yet innocent smile "Aww, did mi ángel try to scare me? You forgot I used to be a matador so I already know when to dodge~" he teases you.
His mockery causes you to get more peeved with his action as you start to gritting your own teeth "YOU!!" You shouted. After those words escape, everyone in the neighbourhood could see you chasing your laughing husband around as they were amused with the comedic sight in front of them.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
❀
❀
#hetalia#aph hetalia#hetalia headcanons#hetalia imagines#hetalia scenarios#hetalia fluff#hws hetalia#1p hetalia#hetalia axis powers#hetalia allies#hetalia x reader#hetalia x gender neutral reader#hws prussia#aph prussia#hetalia prussia#hws germany#aph germany#hetalia germany#hws spain#aph spain#hetalia spain#prussia x reader#germany x reader#spain x reader#hetalia x you#hetalia world stars#hetalia world twinkle
43 notes
·
View notes
Text
General Device Maintenance for Windows
It is common for people to think they need a new laptop or desktop after a few years of use, and it is running slow. However, I’m going to show you a few tricks that I have perfected over the years to help a machine run in tip top shape. These are especially great to do after you have been uninstalling and reinstalling video games on them or just general use from office activity. These are, in my professional experience, the General Maintenance your company should be running on their Windows machines once a year, but probably is not…
-Work Machine-
Please note that for any commands I’m referencing to with quotes, you will not enter the quotes, it’s just the industry standard when specifying a string of data. We’ve all been there, on a work machine and it’s locked down on the permissions. Great news, you can run “gpupdate /force” (Group Policy Update) from Command Prompt. It’s pretty fast and either works or gives you an error that you can screenshot and send to your Service Desk, saving a ton of time. Fundamentally what it does is checks with your company’s server to make sure your computer follows the parameters of the domain. It’s typically the first thing your IT person will run and can be done with any account.
-Personal Machine-
If you haven’t already done it, you should uninstall any Bloatware. This is software that came on your computer when you got it, you don’t necessarily need or use it and it doesn’t seem to contribute to how your computer runs the way you are going to use it. Navigate to the “uninstall a program” area of your Control Panel and you will see the list, then just right click > uninstall (sometimes with stuff like Office there is a “Repair” option). If you see “Wave Browser” while in the control panel you will want to get rid of that at once and run a malware scan; actually, if you see any program you don’t recognize, Google it and/or the publisher to check that it’s legitimate or see what it does. (Note: modern browsers have Java built in, you no longer need it installed on your machine.) You may also have to do it from what we used to call the “Start” area and have no idea why they changed it, er the windows icon and “All Apps”.
-Light Clean-
Clearing your temp folders might seem like it’s not that important, but the closer your SSD drive gets to 50% the slower it performs. This is the random cache your computer stores during regular use of moving files, installing programs, error logs…etc. You’d be surprised at just how junked up they can get, I’ve seen them take up to 8GB worth of data.
From any account: Go to start > Run and type in “%temp%”. (The actual path is “C:\Users\\AppData\Local\Temp”)
With administrative rights, follow the same steps but instead type “temp”.(“C:\Windows\Temp”)
-Update Drivers-
If it’s not one thing, it’s the drivers. Easiest way you can check is to look for a caution mark on one of the listed items in the Device Manger; you might have to drop down the tree. These are the kernel code that binds your operating system and programs with the motherboard. You can set them to auto update, but sometimes the list doesn’t synchronize. Some laptops such as Lenovo have a program that you can download from their website or find in the Microsoft Store like “Lenovo Vantage” and it can be ran from a user account. If you want to look for them yourself the command is: “wmic bios get serialnumber”. The top two to look for and download if they have a newer version are the BIOS and Firmware/Chipset Management Engine.
-More in Depth Commands-
(You will need administrative rights)
Similar to Linux there are terminal commands that are native to the Windows environment that you can run to improve your system. To run these, go to start > Command Prompt > right click > run as administrator:
#1 System File Checker = "sfc /scannow"
This one will take roughly 10 minutes but it’s safe to use the machine while it runs; however, I wouldn’t install anything while it goes. It basically goes through your filesystem and makes sure everything lines up the way it should be, the right system files point to the correct location and there’s no junk files that shouldn’t be there linking to something else. This is just layman’s term, and feel free to look into it more but I assure you it’s perfectly fine to run even if you don’t know what you’re doing.
#2 DISM = "dism /online /cleanup-image /restorehealth"
It can take 15 to 45 minutes, depending on how bad your machine is, but again it’s safe to use while it runs. This connects with the Microsoft servers responsible for updates and ensures that your operating systems image matches the lines of code it should have. You can actually do a lot with dism commands.
#3 Check Disk = "chkdsk /f /r /x" (stands for: find, repair, dismount)
Please note that you will not be able to use the machine until it’s finished running and it can take up to an hour. It should automatically restart your machine after entering it so make sure to save and close everything beforehand. It sometimes gets stuck at “100%, please do not turn off or restart your machine”, but it’s safe to hard reset (press the power button or pull cord). This checks your hard drive for any irregularities and makes sure nothing is corrupt or damaged. There are several ways to run this, however this is the one I find most useful as it runs it at a very low level right after bios when it is loading the kernel (code that makes hardware talk to software).
#4 Cipher = "cipher /w:c:\"
This one will take a while, like up to 2 hours, and I wouldn’t plan on using it, so it goes faster. For when you drastically want to really clean your hard drive to sell or donate This command wipes the dark void of the strange quarks files turn into after the recycling bin. Basically, preventing anyone from restoring anything you deleted and maximizing the free space available in some parts per million way. — And that’s pretty much it! There are a few snazzy programs that I will leave below to help keep your computer stay in shape and safe. Other than that, Congratulations!!! You could be an entry level IT person now.
Noteworthy programs: ATF Cleaner, JRT Remover, Glary Utilities, CCleaner and Malwarebytes
#it support#computer repair#windows administrator#service desk#help desk#toolkit#information technology
3 notes
·
View notes
Text
Notes on a cybersecurity talk
A master social engineer did a talk on the current trends in how hackers target people. I took some notes. This is corporate-oriented, but also applies to individuals. Useful to be aware of!
TL;DR - Hackers are very good at emotional manipulation. Be paranoid of all unexpected phone calls, don't click links in legit-seeming emails unless you're very sure, and don't use the same password in more than one place!
Phishing attacks are more than 80% of incidents now.
An attacker will start by figuring out who and how to target. The goal is to trick the target to:
hand over a password or access (for example asking for remote desktop in a new way)
click on a link
download a file
directly send money or data
Hackers do research using OSINT for precise targeting. Typically using Google and social media. They try to find out who your coworkers are, what software you use, what icon/avatar you have. Any personal likes/dislikes so it sounds like they're someone who knows you already. Anything that they can use to tailor their attack, to seem like it comes from a familiar, trusted source.
Any kind of selfies reveal personal information, but most especially if you foolishly have any sensitive sticky notes or computer screens visible in the background. If they see your screen, they see the icons on your desktop and/or task bar, and so they find out what software you use, and can modify their attack accordingly.
Safest not to reveal anything work-related on social media - projects, coworkers, clients, successes or failures. The more opaque and vague you are, the safer you are from social engineering attacks. LinkedIn is a particular vector for personal information leakage for any corporate employees.
Why would anyone fall for a scam, you may ask. Unfortunately, an attack with the right timing and backstory can trick most people.
Some psychological factors that will be used in an attack:
Reciprocity; if the attacker tells you something, you feel socially compelled to reciprocate and tell something as well. The attacker will use things they know about you and your work to volunteer bits of information, hoping you mention something off-handedly in response.
Commitment and consistency; we are socially conditioned to move from easy questions to hard questions, for example starting with friendly smalltalk and harmless questions, establishing a psychological acceptance of their questions, then follow up with more dangerous questions. But at that point you're already socially committed into answering them, since starting to question the friendly person suddenly would feel awkward and humans are terrified of awkwardness.
Social proof; name dropping of someone you know. Perhaps saying the other person already did this thing they're asking you to do, maybe getting you to feel you've been left out of the loop and should follow suit.
Liking; if you like someone, you want to help them out. Social engineers deliberately try to mirror your behavior, mannerisms, and communication style, to appear similar and likable to you.
Authority; people tend to obey authority. They may pretend to be a boss to get you to follow an order easily. Or they may pretend to be completely without authority, like a confused newbie who needs help and advice and information.
Scarcity; people are more likely to act when there's a sense of urgency. An attacker may use a timeboxed request, which invokes fear. For example, your account will be locked if you don't do this within one hour etc.
Sympathy; trying to evoke empathy by sounding stressed and miserable to get you to do something you wouldn't normally do.
These are combined to form effective attacks. (A lot of these can be avoided by just never taking phone calls, if that's an option. Assume every unexpected phone call is trying to manipulate you.)
The attacker may target someone other than you and trick them to relay a dangerous request to you. The attacker may target someone else through you by getting you to relay a dangerous request.
To hack accounts, all an attacker needs: full name, current or recent address, birthday, email addresses, phone numbers. They can use these to progressively take over your social media and email accounts, sending password reset and change requests.
Google yourself: search for your real name and address. Is it found that easily? Your real name plus phone number? Family member names? That stuff should not be public. It will be used against you. Delist yourself from everywhere.
Google has a delisting tool, free for everyone, might help to deter casual hackers. But delisting from Google isn't enough by itself.
Your social media info can be used to gain access to any company that has your info on file. When you buy something from a company, they will typically record your name and address and other information, and a hacker can easily trick them to hand out all that recorded information, if they already know parts of it. Therefore never reveal which companies actually have your information on record. Don't post on social media about companies you've bought products from.
Hackers can fake a person's voice too, so just because someone sounds like the real person over a phone, doesn't prove anything. Realtime voice modification technology is easily and cheaply available on any app store. Hackers can also easily fake caller id on phones, so when you get a call, you don't know if it's really from the number or person your phone shows it coming from.
Multifactor authentication does help. Also, if an unusual request comes from a normally-trusted source over just one line of communication, use a second channel (sms, whatsapp, teams, slack, email) to double-check the suspicious request is genuine.
Don't click on links in e-mails. Double-check if the URL is the known official legit one. Go directly to the relevant site in your browser instead of via the mailed link. Seeing a green HTTPS lock in the browser URL field does not mean a website is the real one; that's old advice, no longer relevant.
Most common attacks happening now:
Tech support scam; remember, when you need help, you contact them, they shouldn't contact you!
Exec impersonation gift card scams; hi, I need you to send some gift cards to this "client"!
Bank impersonation
Coworker impersonation
IT support impersonation; they may have learned about an IT-related problem you have and say they now have a fix, just log in normally at this friendly URL…
If anyone contacts you and tells you to log in somewhere, it's probably a scam, so don't do it without double-checking the source.
Don't reuse the same password in multiple places. The most important way to protect your accounts. If they gain access to your email, maybe using your password from some other breached service, they can change all your service passwords. Most password dumps from security breaches are openly and easily for sale on the internet, so any reused password is probably available somewhere in there.
52% of people reuse passwords on multiple accounts…
You may think yourself unimportant and unlikely to be targeted. But minimally-personalised scams are mass-sent to hundreds or thousands of targets. You'll get some too.
If you work with sensitive information, you are more likely to be targeted.
If you are customer-facing, you have more attack surface and thus more likely to be targeted.
If you have a lot of access, you are a juicy target; if little access, you can be used to target someone else.
For personal use, some recommended password manager software includes 1password, lastpass, keypass, bitwarden.
The number one thing to do right now - make sure every password you use is different and complex, and use multi-factor authentication everywhere.
2 notes
·
View notes
Text
how to make this style of ‘security footage’ gif for your sims gifs:

things you’ll need
a screen recording software (i personally use OBS, free and literally the best)
photoshop version with a timeline (i use photoshop 2020)
know how to make a basic gif. lots of tutorials online!! and on tumblr.
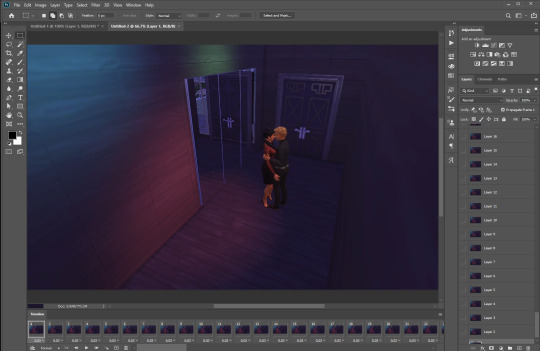
okay, first off all, you’ll need your video! there are many OBS tutorials online so im skipping explaining how to record your screen (it can either be your full desktop window or just the sims 4 window). with OBS since its outside the sims, you can use reshade to record your videos with no problem.
after your video is recorded, we have to import our video frames to layers. to do this you go file > import > video frames to layers. look for your video in the folder you saved!

you now get this pop-up window:
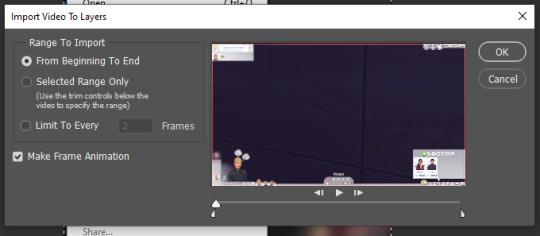
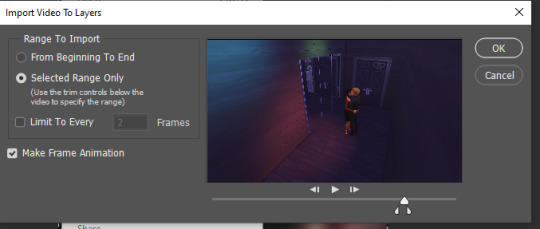
i recommend: NOT limit to 2 frames or more. it looks wonky, it skips, and it uhm... NOT AESTHETICALLY NICE !!!!!!! for a smooth animation, you want every layer! so you’ll now select ‘Selected Range Only’ and with the lil white markers below the video, look for the exact part you want to make a gif:
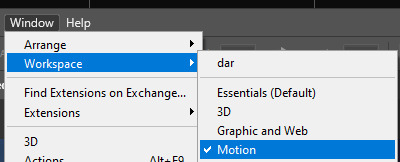
click okay!!! now your photoshop will load all the layers. as a reminder, remember you are on the ‘motion’ workspace.
so overall it should be lookin kinda like this :
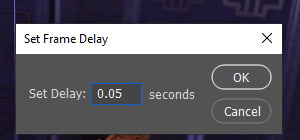
again, not a gif tutorial! if you have a preferred gif speed, go ahead and change it! i like to do 0.05. if you’re like what the hell is she saying?, you do this by going on the lil three bars on the timeline bar on the right, clicking select all frames,
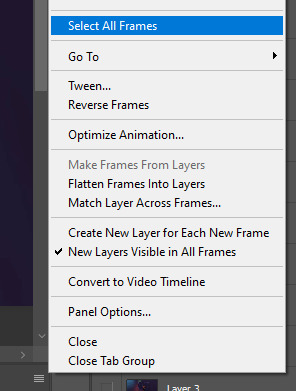
then clicking on whatever frame arrow, clicking ‘other...’ and on the pop up menu changing it to 0.05 and clicking ‘ok’

now you have to convert to timeline. you do this by clicking on well, the convert to timeline icon next to ‘Forever’

now your timeline should be lookin like this!!

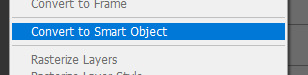
to put the ‘security camera’ footage effect, we have to convert it to a smart object. to do this you select ALL layers in your Layers panel:
MAKE YOU YOU HAVE ALL LAYERS!!!!!!!!!!!!!!!!!! right click on whichever and select ’convert to smart object’.
now your file should be lookin like this in the layer panel and on the timeline:


if you click the playbutton (or the space bar) and the gif moves, then WOOO!! we made it!!! you have a gif!! but we arent done yet! im skipping showing you this, but crop it to your preferred dimensions, add your psd if you have one, etc. the next step after you do all this is adding a black and white filter.
you go layer > adjustment layer > black and white. i prefer black and white to just adding a simple gradient because you can make certain colors brighter or darker.


if you have NO idea what any of those numbers mean, you can play around or leave them like it is! for a thing in my gif, i know theres reds and blues, so if i change the values, this being if i decrease the reds, they’re gonna get darker. if i increase them, the reds are gonna get brighter. so it all depends on your video/gif!
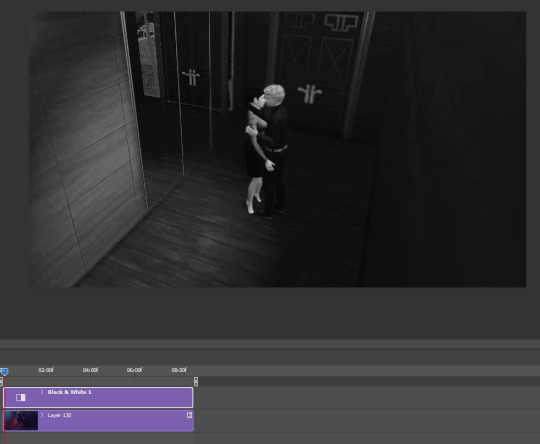
what we’re gonna do next is add the ‘camera footage’ effect, which is really JUST adding noise to the gif. we do, while making sure we are on your smart object layer, for me this is Layer 130, filter > noise > add noise
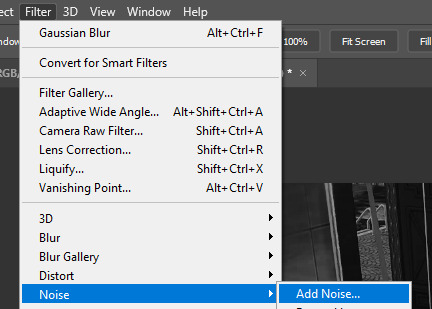
the amount of noise is really up to you! when you have your desired value, click ok!

so now your gif should move and have a noise effect! so we are HALFWAY there

now, we need a camera footage overlay! you can literally google ‘security footage overlay‘ and use whichever you want and see fit! im using this one for this tutorial and its literally the first result ehkjdfjksdf

copy paste into your gif, remember it has to be on top in the layers panel! and adjust so its around the same size as your gif:


next, we change the layer mode to SCREEN so you can see through it!


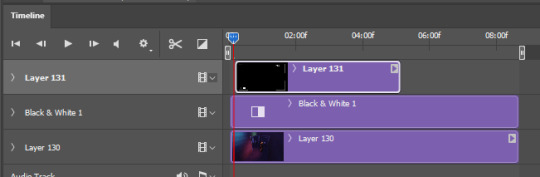
in the timeline, you’re gonna have to increase the overlays length to match your gif’s. when you go near its corner a lil icon will appear and you just have to drag it.

now, our gif is DONE!!!!!! A WIN !!!! we made it. now to save it, its file > export > save for web.

remember to select gif on this drop down menu:
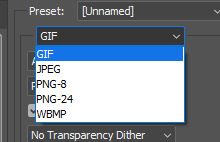
AND for saving gifs i use these settings:

now its the time of TRUTH!!!! tumblr has a size limit of 8mb for gifs. depending on the size of the video (mine is 1920x1280), you’ll either have to: trim the gif OR decrease the size. sometimes decreasing the size works, but sometimes its not enough and YOU’LL HAVE TO trim the gif.
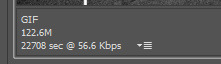
[everyone laughed] BUT if your gif is under 8mb ... CONGRATS!!! you can save the gif and it’ll work on tumblr if not..............we have 2 make some sacrifices. click ‘cancel’ and lets go back to the file. we’ll resize it first.
go to image > image size

make sure the lil lock is clicked and resize to a smaller size. if your gif was like, 9mb, then you dont have to decrease the size SO much. maybe 100px less, but since mine is HUGE im resizing it to tumblr’s size of 540px
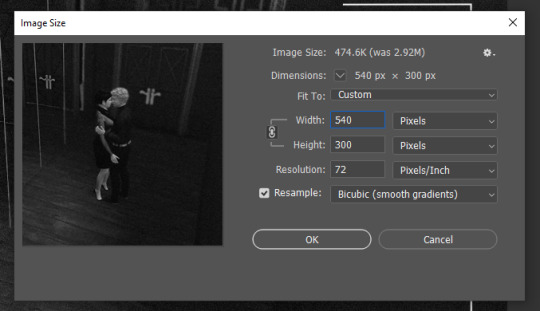
now that we resized, lets go trim out clip! to do that just move the lil marker at the edge of your timeline closer to the other one
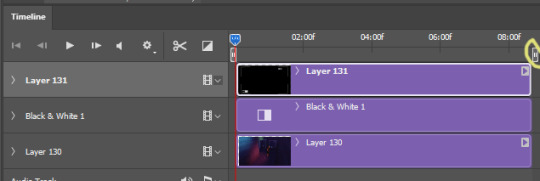
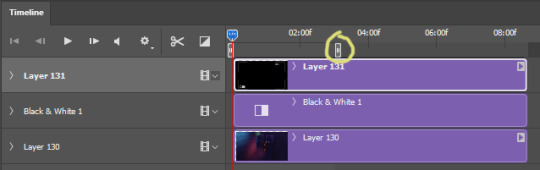
now lets go check our gif size! remember, under 8mbs is the goal. again file > export > save for web

under 8mbs! a win. now click ‘Save...’ and save on your desired folder/destination!! we are NOT done yet. theres still one more step to go!! you’ll have to open your recently saved gif. just go on file > open and look for it!
after your open your recently saved gif, you should be looking at something like this :
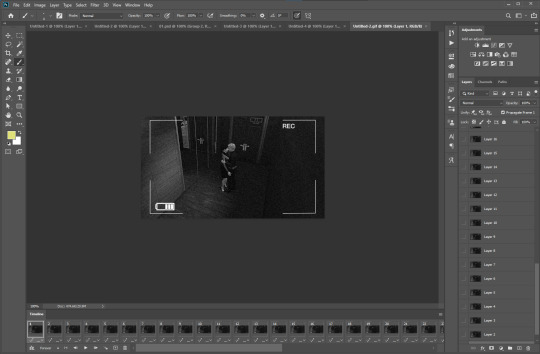
the reason why you have to reopen its because smart objects by default increase the speed. so remember how we saved the gif with 0.05? by saving it as a smart object, it got increased to 0.07. so it’ll be SKIPPY n slow. to fix that we do the same steps of selecting all layers as above.

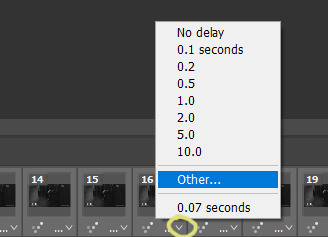

now all you need to do is ONCE AGAIN, save it like before. im skippin showing u this bc i explained it before!! file > export > save for web etc. AND WE ARE DONE !!!!!!!!!!!! AAAAAAAAAAAAAAAAAAAAAAAA

#howto#THIS POST is long. and for some reason i had to rewrite these tags like 5 times#thanks tumblr FOR NOTHING!!!#but if anyone is wondering how i made other gifs just lmk!! i dont do many just bc u know...if u do them too often its borin#gifs are special treats mhm !!!#idk what to tag this again#ts4 tutorial#ts4#ts4 simblr#simblr#ts4 resources
78 notes
·
View notes
Text
I finally got my computer to working again! Had a peculiar crash.
Was using my word processor the other night when, for reasons totally unknown, the whole desktop went away! The word processor appeared to be working normally, so I finished up what I was doing and shut down. Figured that a new start would be like a restart, right? WRONG!!
Tried a new start after powering down, Got the usual start up right up to the lock screen. Put in my pin, Got a gray screen. Took a few moments and got my cursor. NOTHING ELSE! Shut off power and restart. SAME STORY, second verse!
This persisted through the day, except for a water haul. FINALLY, I tried a bunch of things that I thought might help. ESC. Nope. Page Up and Page down, Nope. Several other things, all NOPE!
Remembered Ctrl, Alt, Delete. That got me a blue screen and a short menu. Tried Task Manager: NO APPS RUNNING. Duh, Gee, REALLY?
There was one that was enigmatic. Just LOCK. Figured that it could hardly make things worse, so I tried it. There was my familiar Lock Screen. Put in pin and got ~ ~ the grey screen again!
Tried Ctrl, Alt, Delete again and went to Lock. There down in the corner were icons for web connected and a software power off. Tried the software power off and got a menu with RESTART!
Got it to Restart and finally, here I am!
3 notes
·
View notes
Text
Avast Antivirus Free Download For Mac Os X

The best free antivirus platforms for Mac in 2021 By Jon Martindale May 1, 2021 If you’re a Mac user, you probably love the sleek desktop experience and how easy it is to use and understand.
Free Mac Antivirus Protection. There's another angle to the variation in Mac antivirus pricing. How about paying nothing at all? Avast Security for Mac, AVG AntiVirus for Mac, Avira Free Antivirus.
Avast Antivirus Free Download For Mac Os X 10 10 Yosemite Download
Avast Antivirus Free Download For Mac Os X El Capitan
Avast Antivirus Free Download For Mac Os X Catalina
Avast Free Antivirus is an antivirus developed for Windows and Mac OS X platforms that not only detects and destroys a wide variety of known viruses, but can also detect traces of the modifications produced by unknown viruses. It integrates fully into your operating system environment, and boasts two types of user interfaces: a simple one for casual users, and an advanced option for expert users. It includes a resident scanner that, once activated, will remain minimized as an icon on your system tray. Each time you run a file or access an application, avast! checks it for possible threats. The program will also keep track of and verify your backed-up data, to make sure that it won't suffer any damage in case your computer is seriously infected. The application is constantly updated to keep it current with the latest threats. And did we mention it's totally free? So what are you waiting for?
Avast Cleanup Premium 2020 (Crack and Key) has an ability to download and install the application of category Antivirus. Avast Cleanup Premium 2020 has latest updated and virus definitions that will protect us from the different attacks like Virus, Trojans, spywares etc. Avast cleanup crack can be downloaded from the link given below i.e. The Avast cleanup Premium 2019 download free. Avast Security for Mac is a free download. Avast Premium Security is licensed for 1, 2, or 3 years for with single or multi-device options (up to 10). The premium version offers a 60-day free trial and a 30-day money-back guarantee. Download Avast for Mac and get: Real-time protection: Blocks malware, spyware, Trojans, and viruses in real-time.


Avira Free Antivirus For Pc
Avast antivirus 2018 free download - Avast Free Antivirus, Avast Mobile Security 2018 - Antivirus & App Lock, Avast Pro Antivirus, and many more programs. Avast swgrootcert for mac.
We design Mac hardware and software with advanced technologies that work together to run apps more securely, protect your data, and help keep you safe on the web. And with macOS Catalina available as a free upgrade, it’s easy to get the most secure version of macOS for your Mac.*
Apple T2 chip. The next generation of security.
USB Drive AntiVirus for Mac OS X: Best alternatives You can use one of these USB Drive AntiVirus for Mac alternatives which were thoughtfully chosen by our editors and user community. Free Mac Security is a program developed for people who wish to prevent unauthorized users from accessing private data, and protect their computers.
The Apple T2 Security Chip — included with many newer Mac models — keeps your Mac safer than ever. The Secure Enclave coprocessor in the Apple T2 chip provides the foundation for Touch ID, secure boot, and encrypted storage capabilities. Touch ID gives you a seamless way to use your fingerprint to unlock your Mac, fill passwords in Safari, and make purchases with Apple Pay. Secure boot helps ensure that you are running trusted operating system software from Apple, while the Apple T2 chip automatically encrypts the data on your Mac. So you can be confident knowing that security has been designed right into the architecture of your Mac, from the ground up.
Avast Antivirus For Mac Os
Even Macs Need Antivirus Protection. The myth that Macs don’t suffer malware attacks has been.
Antivirus for mac 10.7 free download - AVG AntiVirus for Mac, Course For Mac OS X 10.7 101 - Core Lion, Trend Micro Antivirus for Mac, and many more programs.
Just like AVG AntiVirus for Mac, Avast Free Mac Security uses traditional signature-based detection and heuristic monitoring. The software identifies and quarantines not only malware targeting Macs but also Windows malware. According to AV-TEST, Avast Free Mac Security stopped 99.17% of Mac OS X.
Apple helps you keep your Mac secure with software updates.
The best way to keep your Mac secure is to run the latest software. When new updates are available, macOS sends you a notification — or you can opt in to have updates installed automatically when your Mac is not in use. macOS checks for new updates every day, so it’s easy to always have the latest and safest version.
Protection starts at the core.
The technically sophisticated runtime protections in macOS work at the very core of your Mac to keep your system safe from malware. Download ntfs for mac paragon. This starts with state-of-the-art antivirus software built in to block and remove malware. Technologies like XD (execute disable), ASLR (address space layout randomization), and SIP (system integrity protection) make it difficult for malware to do harm, and they ensure that processes with root permission cannot change critical system files.
Download apps safely from the Mac App Store. And the internet.
Avast Antivirus Mac Os X Free Download
Now apps from both the App Store and the internet can be installed worry-free. App Review makes sure each app in the App Store is reviewed before it’s accepted. Gatekeeper on your Mac ensures that all apps from the internet have already been checked by Apple for known malicious code — before you run them the first time. If there’s ever a problem with an app, Apple can quickly stop new installations and even block the app from launching again.
Stay in control of what data apps can access.
Apps need your permission to access files in your Documents, Downloads, and Desktop folders as well as in iCloud Drive and external volumes. And you’ll be prompted before any app can access the camera or mic, capture keyboard activity, or take a photo or video of your screen.
FileVault 2 encrypts your data.

With FileVault 2, your data is safe and secure — even if your Mac falls into the wrong hands. FileVault 2 encrypts the entire drive on your Mac, protecting your data with XTS-AES 128 encryption. And on Mac systems with an Apple T2 Security Chip, FileVault 2 keys are created and protected by the Secure Enclave for even more security.
Avast Free Antivirus For Mac Os X 10.5.8
Designed to protect your privacy.
Avast Antivirus Free Download For Mac Os X 10 10 Yosemite Download
The most secure browser for your Mac is the one that comes with your Mac. Built-in privacy features in Safari, like Intelligent Tracking Prevention, help keep your browsing your business. Automatic strong passwords make it easy to create and use unique passwords for all the sites you visit. And iCloud Keychain syncs those passwords securely across all your devices, so you don’t have to remember them. You can also easily find and upgrade any weak passwords you’ve previously used (and reused and reused and reused).
Automatic protections from harmful sites.

Safari also helps safeguard you against fraudulent websites and those that harbor malware — before you visit them. If a website seems suspicious, Safari prevents it from loading and notifies you. And when connecting to unencrypted sites, Safari will warn you. So everything you need to browse without worry is right at your fingertips.
Find your missing Mac with Find My.
Avast Antivirus Free Download For Mac Os X El Capitan
The Find My app combines Find My iPhone and Find My Friends into a single, easy-to-use app on Mac, iPad, and iPhone. Find My can help you locate a missing Mac — even if it’s offline or sleeping — by sending out Bluetooth signals that can be detected by nearby Apple devices. These devices then relay the detected location of your Mac to iCloud so you can locate it in the Find My app. It’s all anonymous and encrypted end-to-end so no one — including Apple — knows the identity of any reporting device or the location of your Mac. And it all happens silently using tiny bits of data that piggyback on existing network traffic. So there’s no need to worry about your battery life, your data usage, or your privacy being compromised.
Keep your Mac safe. Even if it’s in the wrong hands.
Avast Antivirus Free Download For Mac Os X Catalina
All Mac models with the Apple T2 Security Chip support Activation Lock — just like your iPhone or iPad. So if your Mac is ever misplaced or lost, the only person who can erase and reactivate it is you.

1 note
·
View note