#drive encryption utilities
Explore tagged Tumblr posts
Text
Perform BitLocker Recovery Password Rotation in Active Directory
BitLocker Recovery Password Rotation in Active Directory Maintaining the security of BitLocker-encrypted drives is crucial. Situations may arise where users forget their PINs or significant changes in the system configuration necessitate the use of the 48-character BitLocker recovery key. Often, users are not at their desks and may need the key communicated via phone or mobile device, which…
View On WordPress
#Bitlocker#BitLocker Backup#BitLocker Drive Encryption Administration Utilities#BitLocker in Active Directory#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Text



─── ⋆⋅☆⋅ cocky and competitive abby | wc: 1.5k

𝐘𝐨𝐮 𝐛𝐨𝐭𝐡 𝐚𝐫𝐞 𝐢𝐧 𝐚 𝐦𝐢𝐬𝐬𝐢𝐨𝐧, navigating through the narrow hallway that was dimly lit, the cold metal walls echoing with the distant hum of machinery. You and Abby had been assigned to infiltrate a high-security facility—standard spy work, really. But whenever you and Abby were paired up, standard always became something of a competition.
"Bet I’ll crack the vault before you even make it past the first firewall," Abby said smugly, her voice low but dripping with confidence as the two of you made your way through the shadows. Her aviators were pushed up on her head, her smirk unmistakable even in the dark.
You scoffed, adjusting your utility belt. "Please, Anderson. I’ve already got half the codes memorized."
She cast a glance your way, the corner of her mouth twitching up. “Oh yeah? Keep telling yourself that. Don’t get too comfortable in my shadow, sweetheart.”
Your blood buzzed at the challenge. The way Abby was always so cocky—it both infuriated you and made you want to prove her wrong. Every mission turned into a battle of who could do it faster, quieter, better.
“Let’s see who gets to the control room first,” you shot back, already knowing the route you’d take.
Abby chuckled, that low, confident sound. “You’re on.” She stepped closer, her breath teasing your ear for just a second. “Try to keep up.”
Without another word, she was gone, slipping through the corridor with all the grace of a predator on the hunt. You rolled your eyes and followed, determined not to let her win this time.
You rounded a corner, only to see Abby already at the control panel, tapping away. She turned her head ever so slightly as you came into view, her grin wider than it had any right to be.
“Don’t worry,” she said casually, “I’ll save some of the fun for you. Not that you’ll need it, since I’ve already disarmed half the security.”
You bit back a retort, taking a position at the adjacent console. “Security’s disarmed, huh? That’s cute. I just bypassed the surveillance cameras from my comm on the way in.”
Abby raised an eyebrow but didn’t look fazed. “Sure, you did. Just like that time you almost cracked the encryption before I stepped in.”
You huffed, fingers flying over your own console, determined to match her pace. “You know what your problem is, Anderson? You talk a big game, but you never know when to shut up and focus.”
She chuckled, her fingers still tapping rapidly on her keys. “And yet I’m still faster than you. What’s that say about you?”
Your reply was cut off by the quiet ping of her console unlocking. She straightened up and gave you a mock salute. “Vault’s open. Guess I win. Again.”
You rolled your eyes, even though you couldn’t stop a small smile from creeping up. “Yeah, yeah. But who’s got the intel we actually need?”
Abby frowned for just a second, then glanced at the screen. You had already transferred the data to your secure drive. She let out a disbelieving laugh. “You sneaky—”
“I’m just better, Anderson.” You gave her a wink as you turned, ready to make your exit.
But before you could take a step, Abby was in front of you, her hand catching your wrist in a firm but playful grip. She tugged you closer, her lips hovering dangerously near your ear.
“You love pushing my buttons, don’t you?” she whispered, her voice dripping with cocky amusement.
You swallowed, refusing to let her see the effect she had on you. “Somebody has to keep that ego in check.”
Her smirk deepened, and she stepped back, her hand still resting casually on your wrist. “Admit it,” she said, her voice low and teasing. “You like it when I win.”
You laughed softly, shaking your head. “In your dreams, Abby.”
She leaned in again, her breath brushing your neck, her tone smug. “You’re in them more than you think.”
You shoved her lightly, trying to play it cool, but your heart was racing. “Let’s get out of here before you start believing your own hype.”
As you both slipped through the hallways, backtracking toward the extraction point, you couldn’t help but think that this constant battle between the two of you—this back-and-forth, always trying to one-up each other—was starting to feel less like competition, and more like… something else.
And judging by the cocky grin Abby kept flashing your way, she knew it too.
The two of you moved through the shadows with practiced ease, slipping past sensors and cameras like it was second nature. You’d worked together long enough to anticipate each other’s moves, but that didn’t mean the game ever got old. If anything, it was what kept you sharp—and what kept things interesting.
As you approached the rendezvous point, Abby’s pace slowed slightly, just enough to let you catch up to her. She flashed that signature cocky grin, her hand brushing against yours for just a second longer than necessary. It was subtle, but it sent a familiar warmth through your chest. You couldn’t help but smirk back.
“Still can’t believe you thought you had me beat back there,” she teased, her voice low but filled with that playful edge that always made your heart race.
You rolled your eyes, but your smile gave you away. “Please. I had the data before you even stepped into the room.”
Abby shook her head, laughing quietly as she glanced over at you, her expression softening just a bit. “Always gotta keep me on my toes, huh?”
You shot her a sideways glance, raising an eyebrow. “What, you’d get bored if I didn’t?”
Abby’s smirk grew as she took a step closer, her voice dropping to that low, teasing tone she knew drove you crazy. “Bored? Never. But we both know you like it when I get competitive.”
Your pulse quickened as she closed the distance between you, her body just barely brushing against yours. It was a dangerous dance, one you had perfected over the course of countless missions together. The banter, the competition—it was all part of the fun. But beneath the teasing and the one-upmanship, there was something more, something real that neither of you could deny.
You leaned in, your voice just a whisper. “Admit it—you like it too.”
Abby’s smile softened, and for a moment, the cocky front dropped just enough for you to see the affection in her eyes. “Maybe I do,” she murmured, her hand finding yours and giving it a quick squeeze before she pulled away, already heading toward the exit.
You shook your head, grinning as you followed her out into the night. This was how it always went. The competition, the banter—it was your way of keeping things fun, keeping things fresh. But at the end of the day, there was no question where you both stood.
Once you were safely out of the facility and back at the extraction point, the two of you finally relaxed, the adrenaline from the mission starting to fade. Abby leaned against the side of the getaway vehicle, crossing her arms and giving you that smug, lopsided grin again.
“Well, another successful mission,” she said, her voice teasing. “And once again I’m the one who—”
You cut her off with a quick kiss, catching her off guard as you pressed your lips to hers. She blinked in surprise but quickly melted into it, her hands instinctively sliding to your waist. When you pulled back, she was still smirking, but her eyes had softened in that way they only did when it was just the two of you.
“Okay, okay,” she murmured, her voice quieter now. “I guess we’re both winners tonight.”
You laughed, leaning your forehead against hers. “You keep telling yourself that, Anderson.”
For a moment, the two of you just stood there, your arms wrapped around each other, the playful tension between you settling into something softer, more intimate.
“This never gets old, does it?” you said softly, your fingers playing with the hem of her jacket.
Abby hummed, pressing a kiss to your temple. “Not with you.”
It wasn’t just about the missions. The constant competition, the teasing, the cocky grins—it was all part of the game you’d been playing since the beginning. But beneath it all, there was something more. This was how you kept things exciting, how you kept the spark alive even after all these missions, all these close calls.
And Abby? She might be cocky, but she was yours. And that was all that mattered.
She pulled back slightly, raising an eyebrow as she flashed you another grin. “So, when’s round two? I need another shot at showing you up.”
You laughed, shaking your head as you leaned in for another kiss. “You can try, Anderson. But we both know how that’ll end.”
She pulled you closer, her lips brushing against yours as she whispered, “Yeah. With me winning.”
And just like that, the game was back on. But this time, as you drove off into the night, Abby’s hand resting on your thigh, you couldn’t help but feel that you’d both already won.


✰ her in that bomber jacket is doing things to me😩
#lesbians#abby anderson x reader#alternate universe#abby anderson#abby anderson x female reader#abby x fem!reader#abby the last of us#the last of us
101 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes
Text
5 Best Restaurant Management Software Reviews for 2025
Are you looking for the best restaurant management software?

In this tech-driven era, utilizing feature-rich restaurant management software is crucial for small businesses to stay ahead of their competitors. To keep pace with the constant technical advancements and ever-evolving customer preferences, most restaurant owners rely on restaurant management tools that not only streamline their restaurant operations but also help improve sales.
Managing day-to-day restaurant operations can be challenging. However, for many years, restaurants have been struggling with manual logs, lots of spreadsheets, and ordinary point-of-sale systems to keep things in order. This results in missed orders, poor task management, and lots of stress.
If you, too, are dealing with the same issue, this article will be very helpful for you, as we have shared 5 of the best restaurant management software reviews here to help you pick the right one for your business and modernize your restaurant management system.
What is restaurant management software?

Restaurant management software or a restaurant POS system is designed to automate all restaurant operations, order & delivery tracking, generating invoices, storing customer details, offering discounts, food menu management, restaurant reviews, and more. In simple words, it creates the foundation of your restaurant business. A good restaurant POS system will drive your sales and give you a lot of opportunities to grow your restaurant business.
If you still do not use a restaurant management system, let us tell you why your business needs it.
Why do you need restaurant management software?

Best Restaurant Management Software automates major restaurant operations, offering you a stress-free business management experience and happy customers.
Other benefits of using restaurant management software include:
Order management: Starting from accepting orders to processing them and tracking delivery, the entire process is automated with a restaurant management system.
Table booking management: You can easily manage table reservations, table availability, seating arrangements, and more to optimize space and increase revenue.
Handling customer data: When customers place orders with your POS system, it automatically saves crucial information that you can utilize to offer personalized experiences to them.
Improves user experience: With online ordering, payment security, a loyalty program, and systematic task management, your customers feel satisfied.
Data-driven marketing decision: A POS system offers useful data and reports on your sales and evaluates your overall restaurant performance to help you make data-driven decisions.
Menu management: Add a striking menu and easily add, edit, or delete food items from it.
Cost optimization: Proper menu management, loyalty program, and simplified order management help optimize costs.
Reduced errors: Tech-driven order, delivery, and customer data management reduce the chances of error and provide you with an accurate picture of your restaurant’s performance.
These are the basic advantages of using a restaurant management system. When you choose the best for you, your business will experience more benefits.
Selecting the best restaurant management software: features to look for

Best restaurant management software features
When you search for the best restaurant management software for your restaurant, you will find an overwhelming number of options that are sure to confuse you. So, how to pick the best one? The answer lies in the features of a restaurant POS system.
Find out the must-have features for a restaurant management system:
Security
Your restaurant POS system regularly deals with confidential customer information like their payment details, contact information, etc, and ensuring their security should be a priority to build trust and credibility. Ensure that the restaurant software you choose has end-to-end encryption and a secure payment system.
Speed
One of the most important factors of the best restaurant management software is its speed. It must be able to work efficiently during rush hours when the order flow usually doubles. If the system slows down or crashes, then it could pose a serious challenge to your operational efficiency and business reputation. While scrutinizing event management software, do not forget to check its speed and its ability to handle pressure.
Scalability
Scalability is extremely important for a restaurant management solution to stay aligned with the changes that take place. Whether it is about managing restaurants from different locations or adding new features, your software must be able to deliver that without affecting the performance.
Mobile Accessibility
Make sure that the restaurant POS system you choose offers you the flexibility to manage your restaurant operation through your mobile phone. Opening a desktop for minor works can be a hassle. Tracking orders, deliveries, customer data, table registration, and more through phones is extremely beneficial and convenient.
Table booking management
Table reservation is a crucial part of a restaurant, and that is why, while filtering restaurant management software, look for a restaurant management system that offers a table booking system.
Order and delivery management
A restaurant POS system is incomplete without an online ordering and delivery management system. Search for a restaurant menu software that provides you with 100% admin control over the orders and delivery management.
Technical support
Technical support ensures that everything runs smoothly. Opt for a restaurant management system that offers technical support when required. This is important because if you face any technical issues, they can solve them promptly.
Reporting and analytics
Reports and analytics help you measure the performance of your restaurant. It throws light on sales, employee performance, and customer preferences to help you make major decisions for growth.
5 Best Restaurant Management Software Reviews
We have picked the 5 best restaurant management software after evaluating them on the basis of the above-mentioned points and reviewed each of them to help you understand them better and choose the most suitable one for your business.
1. FoodMato

FoodMato is one of the best restaurant management software programs that you can rely on for your small, medium, or established restaurant business. It is an all-in-one restaurant POS system that covers everything from online ordering and delivery to menu management, marketing, and an easy-to-use mobile app to manage the entire system at your fingertips.
Key features of FoodMato
Restaurant website creation and branding.
Seamless order management and delivery tracking.
Stress-free restaurant reservation system.
Creation of food menu and its management.
Freedom to handle multiple restaurant operations from a centralized platform.
Reports and analytics on restaurant sales, orders, and overall performance.
Google Maps integration to display restaurant locations.
Loyalty program for customer retention.
Restaurant marketing with social media community management.
Restaurant review system to increase credibility.
Sincere and timely support.
Third-party integrations.
Restaurant gallery to showcase your restaurant’s ambiance.
The best part about FoodMato is that it covers all essential restaurant management features, and it can be customized as per individual business requirements.
Pros of FoodMato
Offers a comprehensive solution
Affordable pricing.
Prompt response from the support team.
Offers full control to the admin.
A wideegtecccg3grvfcrv array of features.
Amazing reviews.
The FoodMato team works according to unique business needs.
No technical knowledge is required.
Cons of FoodMato
Not many reviews are available as it is a newly launched software.
2. OpenTable

The second in our list is the OpenTable software, which is known for its excellent restaurant reservation system. The POS system offers a vast array of services to restaurants, including table reservations, table management, restaurant booking, inventory management, and more.
Key features of OpenTable
Organize private dining events with enhanced visibility.
Restaurant management with a mobile app.
Restaurant reservation system with tags, booking, and waiting list facilities.
Offers guest data security.
The online waiting list is for guests to avoid congestion at the restaurant front door.
Reports and analytics.
A restaurant direct messaging system to allow customers to directly interact with restaurant representatives before stepping in.
Pros of OpenTable
Vast features.
Superior table booking system.
CRM integrations for better guest management.
Positive reviews.
Cons of OpenTable
Users often complain about data synchronization issues.
The system may slow down during peak hours.
It may feel overwhelming for users due to excessive features.
3. Toast

Toast is another restaurant POS system that we have picked for our readers. It is easy to use, and it can be a good choice for those who are not tech-savvy. It offers multiple useful features that cover major restaurant operations like online ordering, payroll management, and more.
Key features of Toast
Simplified online ordering.
Convenient to use.
Various tools for employee scheduling and payroll management.
Insightful reports and analytics.
Easy integrations with third-party online ordering platforms.
Customizable.
Pros of Toast
User-friendly.
Packed with multiple features.
Integration with third-party delivery platforms for smooth restaurant management.
Cons of Toast
The absence of offline functionality makes the system completely unusable.
Difficulty in customizing the system.
4. PetPooja

PetPooja is a well-known restaurant POS software developed to streamline restaurant operations. It offers a wide range of restaurant management features, including online ordering, task management, easy attendee tracking, and task and payroll management.
Key features of PetPooja
User-friendly interface.
Online ordering and billing system.
Task management tool to improve productivity
Digital invoice generation system.
Real-time restaurant reports on sales, online orders, inventory consumption, staff management, and more.
Pros of PetPooja
Fast and reliable.
Easy to use.
Multiple useful features.
Offers real-time updates on Inventory, sales, and customer preferences.
Cons of PetPooja
The process of integrating the software with other platforms is complicated.
5. Restroworks

Last but not least, Restroworks works as a complete restaurant management platform with powerful inventory management features. It is mostly suitable for medium-sized restaurants. It easily integrates with payment processing tools to offer a smooth transaction experience to restaurant owners and customers.
Key features of Restroworks:
Helps manage kitchen inventories to decrease food prices.
Offers real-time updates on food stock to reduce food wastage.
Provides a clear picture of the upcoming day’s food consumption based on historical data.
Helps create recipes with proper ingredients and monitor costs to determine the price of a food item.
Pros of Restroworks
Customizable.
Offers a comprehensive restaurant management solution.
Easy inventory tracking.
Automatic sync with accounting tools.
Cons of Restroworks
It can be a bit complicated for small businesses.
Customer support response time is slow
Inventory tracking requires manual efforts.
What is the best restaurant management software?
Selecting the best restaurant management software from the above-mentioned tools completely depends on your restaurant’s requirements. We recommend FoodMato because it offers an A-to-Z solution to your restaurant business with a strong IT support team.
Wrapping up
Let us take a quick look at the 5 best restaurant management software that we have reviewed for you: FoodMato, Openable, Toast, PetPooja, and Restroworks. We have picked them on the basis of their features, reviews, support, user-friendliness, and their ability to streamline restaurant operations.
#online ordering system#pos system#restaurant management#food delivery#onlineorderingsystemfor restaurant#Restaurant Management Software
2 notes
·
View notes
Text




Maximizing Your Portfolio: A Guide to Binary Trading on Cryptopadie
Introduction to Binary Trading
Binary trading, particularly in the realm of cryptocurrency, represents a distinct approach to the traditional trading landscape. At its core, binary trading involves predicting the outcome of specific market events, where the trader must determine whether the price of an asset will rise or fall within a defined timeframe. If the prediction is accurate, the trader receives a predetermined return; conversely, an incorrect prediction results in a total loss of the invested amount. This simplicity in structure is one of the key factors driving the popularity of binary options.
In comparison to traditional trading methods, binary trading presents a more straightforward risk-reward framework. Traditional trading often requires a deep understanding of market trends, technical analysis, and timing for profitable buy and sell decisions. Binary options eliminate much of this complexity, as traders only need to focus on the binary outcome of yes or no—in other words, whether the asset will end above or below a certain price by the expiry time. However, this does not diminish the necessity for strategic planning and market insight when engaging in binary trading.
The appeal of platforms like Cryptopadie for binary trading lies in their user-friendly interfaces, real-time data analytics, and a range of asset options, including cryptocurrencies. By utilizing these platforms, traders can easily execute trades, track performance, and access valuable resources for managing their investments. Furthermore, the growing interest in cryptocurrencies enhances the relevance of binary trading, as these digital assets exhibit significant volatility that can be advantageous for binary traders looking to capitalize on swift price movements. As the market continues to evolve, understanding the principles of binary options becomes increasingly essential for aspiring traders navigating this innovative financial space.
Understanding Cryptopadie: Features and Benefits
Cryptopadie has emerged as a prominent binary trading platform, offering a user-friendly interface that caters to both novice and experienced traders. The platform's design prioritizes ease of navigation, allowing users to swiftly execute trades and access vital information regarding market trends. A streamlined interface can significantly enhance the trading experience, reducing the steep learning curve often associated with financial trading platforms.
One of the standout features of Cryptopadie is its extensive variety of assets available for trading. Users can access a diverse range of cryptocurrencies, indices, and commodities, providing ample opportunities for portfolio diversification. This breadth of asset classes enables traders to develop robust strategies, catering to various market conditions and personal risk tolerances. By trading across different asset types, users can potentially enhance their profitability and decrease overall exposure to market volatility.
Security is another critical aspect of Cryptopadie that sets it apart from competitors. The platform employs advanced security measures, including encryption and two-factor authentication, to safeguard user data and assets. Such robust security protocols are essential for building trust and confidence among traders, particularly in an industry often plagued by cybersecurity concerns.
Moreover, Cryptopadie offers exceptional customer support, ensuring that users can access assistance whenever necessary. The support team is available through multiple channels, including live chat and email, providing timely responses to user inquiries. This level of support is vital for traders looking to resolve issues quickly or gain insights that could improve their trading decisions.
Incorporating these features into their trading strategies can significantly benefit users, allowing them to optimize their portfolios effectively. The combination of a user-centric platform, diversified assets, high-security standards, and responsive customer service makes Cryptopadie a compelling choice for those seeking to maximize their portfolio through binary trading.
Strategies for Success in Binary Trading
Employing successful strategies in binary trading on platforms like Cryptopadie can significantly enhance the performance of your portfolio. One of the cornerstones of effective binary options trading is robust risk management. Individuals must determine their appropriate risk tolerance, ensuring that they are not overexposing their investments on any single trade. A well-defined risk-reward ratio should be established, guiding traders on how much to invest based on potential gains and losses. This includes setting stop-loss orders and profit targets that align with the overall risk management strategy.
Market analysis is another pivotal aspect of binary trading. Traders should actively engage in both technical and fundamental analysis to identify potential trading opportunities. Technical analysis involves examining price charts and using indicators to predict future price movements. Traders can utilize tools such as moving averages, Relative Strength Index (RSI), or Bollinger Bands to assess market conditions. On the other hand, fundamental analysis focuses on economic indicators, news events, and market sentiment, which can influence asset prices. By integrating both analysis methods, traders can enhance their decision-making process and improve the probability of success.
Moreover, psychological resilience plays a crucial role in binary trading. The ability to maintain composure and discipline during periods of market volatility is essential. Emotions like fear and greed can lead to impulsive decisions, which may jeopardize trading outcomes. Practicing mindfulness strategies, keeping a journal of trading experiences, and adhering to a well-structured trading plan can help traders cultivate a more resilient mindset.
Additionally, some specific strategies can be beneficial for traders looking to maximize their success in binary options. Trend following involves identifying and capitalizing on prevailing market trends, while range trading focuses on identifying support and resistance levels. Volatility trading allows individuals to take advantage of market fluctuations, focusing on assets demonstrating considerable price movements. By strategically implementing these approaches, traders can potentially boost their trading success and foster significant portfolio growth.
Conclusion: Building a Sustainable Trading Portfolio
In closing, developing a sustainable trading portfolio in the realm of binary trading is essential for long-term success. Throughout this guide, we have explored various strategies that serve as the cornerstone of effective trading on Cryptopadie. It is paramount for traders to not only implement these strategies but also to engage in continuous learning to adapt to an ever-evolving market landscape.
Monitoring one’s trading performance regularly is critical. By doing this, traders can identify patterns, assess the effectiveness of their approaches, and make necessary adjustments to their strategies. This methodical approach not only enhances trading outcomes but also contributes to a solid foundation for portfolio growth. Moreover, it is beneficial for traders to stay updated on market trends and news. Market sentiment can be highly volatile, and being aware of external factors influencing prices can aid in making informed decisions.
Fostering a disciplined mindset is crucial in binary trading. Emotional trading decisions often lead to costly mistakes and can derail the best-laid plans. Maintaining a focus on strategic goals and adhering to predetermined trading guidelines will help mitigate risks and align one’s actions with the desired outcomes. As one enhances their portfolio, the importance of patience and consistency cannot be overstated.
Ultimately, building a sustainable trading portfolio requires a commitment to ongoing education, disciplined trading practices, and adaptability to market conditions. As traders navigate their journey on Cryptopadie, embracing these principles will pave the way for enhanced success and portfolio resilience in the thriving world of binary trading.
2 notes
·
View notes
Text
Astraweb: The Home of Crypto Recovery in the Digital Age

In the ever-evolving world of cryptocurrency, security and access remain critical concerns. For every success story of early adopters turning modest investments into fortunes, there are unfortunate accounts of users losing access to their digital wallets due to forgotten passwords, phishing attacks, or compromised private keys. This is where Astraweb has carved out a vital niche — establishing itself as the go-to solution for crypto asset recovery.
The Need for Crypto Recovery
Cryptocurrency promises decentralized finance and ownership without intermediaries — but this power comes with a cost: total user responsibility. There is no central authority to call when access is lost. Millions of dollars in crypto assets are estimated to be trapped in inaccessible wallets. The stakes are high, and the traditional “write your password down and hope for the best” method has proven tragically inadequate.
Astraweb has stepped in to fill this gap, offering a technically advanced, ethically grounded, and user-focused recovery service for individuals and institutions alike.
Who is Astraweb?
Astraweb is a team of cybersecurity professionals, blockchain analysts, and ethical hackers dedicated to the recovery of lost digital assets. Known in online communities for their discretion and technical excellence, Astraweb has quietly built a reputation as the “home of crypto recovery” — a safe harbor in the sometimes stormy seas of decentralized finance.

Core Services Offered
Wallet Password Recovery Utilizing a combination of brute force optimization, machine learning, and customized dictionary attacks, Astraweb helps users recover wallets with forgotten passwords. Their tools are especially effective with partially remembered credentials.
Seed Phrase Reconstruction Lost or partial seed phrases are another major barrier to wallet access. Astraweb’s proprietary tools attempt to reconstruct valid mnemonic phrases based on user input and probabilistic modeling.
Phishing and Scam Mitigation If your crypto assets have been stolen due to phishing attacks or scams, Astraweb provides investigation support and recovery options. While crypto transactions are irreversible, Astraweb works with partners and tracing tools like Chainalysis to help track and reclaim funds when possible.
Multi-Sig and Legacy Wallet Recovery Many early wallets used now-defunct software or obscure security models. Astraweb specializes in navigating old formats, deprecated standards, and rare cryptographic setups.
Cold Wallet Restoration Lost access to hardware wallets like Trezor, Ledger, or even encrypted USB drives? Astraweb can assist with forensic-level data recovery and hardware-based key extraction.
Why Astraweb Stands Out
Confidentiality First: Every case is handled with strict privacy. Your data and identity are protected at all stages of the recovery process.
Transparent Communication: Clients are updated at every step, with no vague promises or false guarantees.
No Recovery, No Fee: Astraweb operates on a results-based model. You only pay if your assets are successfully recovered.
Client Trust and Track Record
Though much of their work remains confidential due to the sensitive nature of crypto assets, Astraweb’s success stories span from everyday investors to high-net-worth individuals and even businesses affected by inaccessible wallets or theft.
Their community reputation and testimonials underscore one thing: they deliver.
Contact Astraweb
If you’ve lost access to your cryptocurrency wallet, or fallen victim to crypto fraud, don’t give up hope. Reach out to Astraweb for a professional assessment of your situation.
Email: [email protected]
Whether it’s one token or an entire portfolio, Astraweb may be your best shot at recovery.
2 notes
·
View notes
Text
Social Media and Privacy Concerns!!! What You Need to Know???
In a world that is becoming more digital by the day, social media has also become part of our day-to-day lives. From the beginning of sharing personal updates to networking with professionals, social media sites like Facebook, Instagram, and Twitter have changed the way we communicate. However, concerns over privacy have also grown, where users are wondering what happens to their personal information. If you use social media often, it is important to be aware of these privacy risks. In this article, we will outline the main issues and the steps you need to take to protect your online data privacy. (Related: Top 10 Pros and Cons of Social media)

1. How Social Media Platforms Scrape Your Data The majority of social media platforms scrape plenty of user information, including your: ✅ Name, email address, and phone number ✅ Location and web browsing history ✅ Likes, comments, and search history-derived interests. Although this enhances the user experience as well as advertising, it has serious privacy issues. (Read more about social media pros and cons here) 2. Risks of Excessive Sharing Personal Information Many users unknowingly expose themselves to security risks through excessive sharing of personal information. Posting details of your daily routine, location, or personal life can lead to: ⚠️ Identity theft ⚠️Stalking and harassment ⚠️ Cyber fraud

This is why you need to alter your privacy settings and be careful about what you post on the internet. (Read this article to understand how social media affects users.) 3. The Role of Third-Party Apps in Data Breaches Did you register for a site with Google or Facebook? Handy, maybe, but in doing so, you're granting apps access to look at your data, normally more than is necessary. Some high profile privacy scandals, the Cambridge Analytica one being an example, have shown how social media information can be leveraged for in politics and advertising. To minimize danger: 👍Regularly check app permissions 👍Don't sign up multiple accounts where you don't need to 👍Strong passwords and two-factor authentication To get an in-depth overview of social media's impact on security, read this detailed guide. 4. How Social Media Algorithms Follow You You may not realize this, but social media algorithms are tracking you everywhere. From the likes you share to the amount of time you watch a video, sites monitor it all through AI-driven algorithms that learn from behavior and build personalized feeds. Though it can drive user engagement, it also: ⚠️ Forms filter bubbles that limit different perspectives ⚠️ Increases data exposure in case of hacks ⚠️ Increases ethical concerns around online surveillance Understanding the advantages and disadvantages of social media will help you make an informed decision. (Find out more about it here) 5. Maintaining Your Privacy: Real-Life Tips

To protect your personal data on social media: ✅ Update privacy settings to limit sharing of data ✅ Be cautious when accepting friend requests from unknown people ✅ Think before you post—consider anything shared online can be seen by others ✅ Use encrypted messaging apps for sensitive conversations These small habits can take you a long way in protecting your online existence. (For more detailed information, read this article) Final Thoughts Social media is a powerful tool that connects people, companies, and communities. There are privacy concerns, though, and you need to be clever about how your data is being utilized. Being careful about what you share, adjusting privacy settings, and using security best practices can enable you to enjoy the benefits of social media while being safe online. Interested in learning more about how social media influences us? Check out our detailed article on the advantages and disadvantages of social media and the measures to be taken to stay safe on social media.
#social media#online privacy#privacymatters#data privacy#digital privacy#hacking#identity theft#data breach#socialmediaprosandcons#social media safety#cyber security#social security
2 notes
·
View notes
Text
How Python Powers Scalable and Cost-Effective Cloud Solutions

Explore the role of Python in developing scalable and cost-effective cloud solutions. This guide covers Python's advantages in cloud computing, addresses potential challenges, and highlights real-world applications, providing insights into leveraging Python for efficient cloud development.
Introduction
In today's rapidly evolving digital landscape, businesses are increasingly leveraging cloud computing to enhance scalability, optimize costs, and drive innovation. Among the myriad of programming languages available, Python has emerged as a preferred choice for developing robust cloud solutions. Its simplicity, versatility, and extensive library support make it an ideal candidate for cloud-based applications.
In this comprehensive guide, we will delve into how Python empowers scalable and cost-effective cloud solutions, explore its advantages, address potential challenges, and highlight real-world applications.
Why Python is the Preferred Choice for Cloud Computing?
Python's popularity in cloud computing is driven by several factors, making it the preferred language for developing and managing cloud solutions. Here are some key reasons why Python stands out:
Simplicity and Readability: Python's clean and straightforward syntax allows developers to write and maintain code efficiently, reducing development time and costs.
Extensive Library Support: Python offers a rich set of libraries and frameworks like Django, Flask, and FastAPI for building cloud applications.
Seamless Integration with Cloud Services: Python is well-supported across major cloud platforms like AWS, Azure, and Google Cloud.
Automation and DevOps Friendly: Python supports infrastructure automation with tools like Ansible, Terraform, and Boto3.
Strong Community and Enterprise Adoption: Python has a massive global community that continuously improves and innovates cloud-related solutions.
How Python Enables Scalable Cloud Solutions?
Scalability is a critical factor in cloud computing, and Python provides multiple ways to achieve it:
1. Automation of Cloud Infrastructure
Python's compatibility with cloud service provider SDKs, such as AWS Boto3, Azure SDK for Python, and Google Cloud Client Library, enables developers to automate the provisioning and management of cloud resources efficiently.
2. Containerization and Orchestration
Python integrates seamlessly with Docker and Kubernetes, enabling businesses to deploy scalable containerized applications efficiently.
3. Cloud-Native Development
Frameworks like Flask, Django, and FastAPI support microservices architecture, allowing businesses to develop lightweight, scalable cloud applications.
4. Serverless Computing
Python's support for serverless platforms, including AWS Lambda, Azure Functions, and Google Cloud Functions, allows developers to build applications that automatically scale in response to demand, optimizing resource utilization and cost.
5. AI and Big Data Scalability
Python’s dominance in AI and data science makes it an ideal choice for cloud-based AI/ML services like AWS SageMaker, Google AI, and Azure Machine Learning.
Looking for expert Python developers to build scalable cloud solutions? Hire Python Developers now!
Advantages of Using Python for Cloud Computing
Cost Efficiency: Python’s compatibility with serverless computing and auto-scaling strategies minimizes cloud costs.
Faster Development: Python’s simplicity accelerates cloud application development, reducing time-to-market.
Cross-Platform Compatibility: Python runs seamlessly across different cloud platforms.
Security and Reliability: Python-based security tools help in encryption, authentication, and cloud monitoring.
Strong Community Support: Python developers worldwide contribute to continuous improvements, making it future-proof.
Challenges and Considerations
While Python offers many benefits, there are some challenges to consider:
Performance Limitations: Python is an interpreted language, which may not be as fast as compiled languages like Java or C++.
Memory Consumption: Python applications might require optimization to handle large-scale cloud workloads efficiently.
Learning Curve for Beginners: Though Python is simple, mastering cloud-specific frameworks requires time and expertise.
Python Libraries and Tools for Cloud Computing
Python’s ecosystem includes powerful libraries and tools tailored for cloud computing, such as:
Boto3: AWS SDK for Python, used for cloud automation.
Google Cloud Client Library: Helps interact with Google Cloud services.
Azure SDK for Python: Enables seamless integration with Microsoft Azure.
Apache Libcloud: Provides a unified interface for multiple cloud providers.
PyCaret: Simplifies machine learning deployment in cloud environments.
Real-World Applications of Python in Cloud Computing
1. Netflix - Scalable Streaming with Python
Netflix extensively uses Python for automation, data analysis, and managing cloud infrastructure, enabling seamless content delivery to millions of users.
2. Spotify - Cloud-Based Music Streaming
Spotify leverages Python for big data processing, recommendation algorithms, and cloud automation, ensuring high availability and scalability.
3. Reddit - Handling Massive Traffic
Reddit uses Python and AWS cloud solutions to manage heavy traffic while optimizing server costs efficiently.
Future of Python in Cloud Computing
The future of Python in cloud computing looks promising with emerging trends such as:
AI-Driven Cloud Automation: Python-powered AI and machine learning will drive intelligent cloud automation.
Edge Computing: Python will play a crucial role in processing data at the edge for IoT and real-time applications.
Hybrid and Multi-Cloud Strategies: Python’s flexibility will enable seamless integration across multiple cloud platforms.
Increased Adoption of Serverless Computing: More enterprises will adopt Python for cost-effective serverless applications.
Conclusion
Python's simplicity, versatility, and robust ecosystem make it a powerful tool for developing scalable and cost-effective cloud solutions. By leveraging Python's capabilities, businesses can enhance their cloud applications' performance, flexibility, and efficiency.
Ready to harness the power of Python for your cloud solutions? Explore our Python Development Services to discover how we can assist you in building scalable and efficient cloud applications.
FAQs
1. Why is Python used in cloud computing?
Python is widely used in cloud computing due to its simplicity, extensive libraries, and seamless integration with cloud platforms like AWS, Google Cloud, and Azure.
2. Is Python good for serverless computing?
Yes! Python works efficiently in serverless environments like AWS Lambda, Azure Functions, and Google Cloud Functions, making it an ideal choice for cost-effective, auto-scaling applications.
3. Which companies use Python for cloud solutions?
Major companies like Netflix, Spotify, Dropbox, and Reddit use Python for cloud automation, AI, and scalable infrastructure management.
4. How does Python help with cloud security?
Python offers robust security libraries like PyCryptodome and OpenSSL, enabling encryption, authentication, and cloud monitoring for secure cloud applications.
5. Can Python handle big data in the cloud?
Yes! Python supports big data processing with tools like Apache Spark, Pandas, and NumPy, making it suitable for data-driven cloud applications.
#Python development company#Python in Cloud Computing#Hire Python Developers#Python for Multi-Cloud Environments
2 notes
·
View notes
Text
Anyways, I wouldn't be worth listening to if I didn't give something more useful than idle complaining.
If you need to try and wipe an SSD as much as you can short of literally destroying it then here you go.
First, it has to be directly attached to the SATA or NVMe bus. Then use a utility from the manufacturer to issue the Secure Delete command.
Next, get some kind of linux running, any of the live boot ones is fine and it doesn't particularly matter. Run a dd command writing the entire drive with random nonsense from /dev/urandom. Pretty typical up to this point but from here we go a little wild.
Now we go back to that utility from the first step. Yes, we'll Secure Delete again just for good measure. More info here, SD supposedly simultaneously zaps every data cell to erase the disk. Since the cells can act like little capacitors and hang on to a bit of residual voltage, we do this twice to ensure that any stragglers after the random write will "look like" it only ever had a high bit stored in it.
And we're back in the live boot once again. And yes, we're doing a total disk write again. /dev/urandom so on and so forth. A little explaining, the desired outcome is that this will meddle a bit with side-channel snooping via the wear-leveling mechanism. It also just makes you feel better knowing you had two passes of random data which should make the NAND gates not hold enough coherent voltage to form the data it once had.
Staying in linux, once that's done we're gonna dd from /dev/zero. Where the last two disk fills were to jumble things up and possibly not entirely useful in all cases, this one ought to force the SSD's underlying controller to erase every block so it can write all these zeros. The reason for this instead of another Secure Delete is to try to flood out copies of data from the control and support circuitry. If we can't directly command it to discard every bit it might be holding then we'll try to wash it out instead.
We're getting there, I'm sorry but go put random data back on it. This will make sense in a second I swear. Because next we'll partition the disk and we want garbled nonsense on it before we do that.
After you've done that, and gotten a giant partition on it and a filesystem on it, it's time to write some more. Using some incantations on the terminal, fill the drive with files. It doesn't matter much if you use /dev/urandom or /dev/zero for the contents because we're targeting the TRIM system this time.
I know you'll hate me for this next one but now you gotta delete all those files. If you thought ahead, you probably made them sizeable to make this faster.
Now it's time for coffee and a smoke; while it deletes shit and TRIM does it's thing you'll wanna let it sit for an hour or so. Then one last visit to Secure Delete and you're done.
This procedure sounds, feels, and likely is complete overkill but this is the best I got. I will warn you that you'll have lower performance for a while probably and it will certainly reduce the lifetime of the SSD.
If at all possible do just enough to do the job. If you are not worried about someone frankensteining your data, selling the SSD or giving it to family as a hand me down then the first two steps are likely enough. If you're putting it on eBay or you feel your threat level is higher than normal, going to the end of Step 4 or Step 5 ought to be enough. If you somehow have the nuclear codes or are particularly frightened about your data security, or are reusing the SSD for encrypted data then I'd go through to the end.
I cannot stress enough that this is extremely brutal on the SSD. They aren't really meant to be securely wiped. You should assess what data you intend on putting on them before ever using it to know if you need to use encryption of whatever degree or perhaps use a magnetic disk (with encryption too if you can!) instead if speed is not a concern. HDDs are far easier and confirmed to be capable of complete wiping with no way to skim data.
Also a disclaimer, I am not the owner of vast tech resources so I can't really test how effective this truly is because broke. I also shake too much now to hot air chips off anyways. If you are inclined, I suppose you could try to get a data recovery place to see if they can get any data once you're done just for curiosity.
#a much longer post than usual but you can't shortform this stuff#also rip to low-tech peeps you'll have to ask your weirdo linux cousin for a favor and hope they help#again this is fucking brutal on the SSD#eight full disk cycles is borderline abuse but gotta crack a few eggs#so like don't do this if your SSD is pushing highschool if you need to keep using it
2 notes
·
View notes
Text
How Payout Solutions Drive Financial Inclusion Across Developing Economies ?

Financial inclusion is a critical driver of economic development, particularly in developing economies where access to traditional banking services remains a significant challenge. Payout solutions are emerging as transformative tools to bridge this gap, offering innovative ways to empower underserved populations and integrate them into the financial ecosystem. This article explores how payout solutions contribute to financial inclusion, their benefits, and the role of digital innovation in achieving these goals.
Understanding Payout Solutions
Payout solutions refer to systems and technologies designed to facilitate seamless, secure, and efficient payments to individuals or businesses. These solutions include a wide range of services, such as:
Payroll disbursements
Social benefit payments
Gig economy payouts
Cross-border remittances
By leveraging payout solutions, organizations can ensure timely and accurate disbursement of funds, even in areas with limited access to traditional banking infrastructure.
The Importance of Financial Inclusion in Developing Economies
Financial inclusion means providing individuals and businesses access to affordable and useful financial products and services, including payments, savings, credit, and insurance. It is vital for economic growth, as it:
Empowers Individuals: Access to financial services enables individuals to save, invest, and plan for the future.
Boosts Economic Participation: Financial inclusion integrates more people into the economy, fostering entrepreneurship and innovation.
Reduces Inequality: It narrows the gap between the privileged and underserved populations by offering equal opportunities for financial growth.
However, traditional banking systems often fall short in developing economies due to factors like limited infrastructure, high operating costs, and lack of financial literacy. Here, payout solutions offer a practical alternative.
How Payout Solutions Drive Financial Inclusion
Reaching Remote Areas Payout solutions utilize digital tools to overcome geographic barriers. Mobile-based applications and point-of-sale systems enable individuals in remote regions to access funds without needing a physical bank branch. For instance, farmers can receive subsidy payments directly into their mobile wallets, eliminating the need to travel long distances.
Enabling Faster Transactions Instant payout solutions are critical for individuals relying on timely income, such as gig workers or daily wage earners. These solutions use real-time digital solutions to ensure payments are processed instantly, helping users meet their immediate needs.
Reducing Costs Traditional banking often involves high transaction fees, making it inaccessible for low-income populations. Payout solutions streamline the process and reduce costs by leveraging digital infrastructure, making financial services more affordable.
Enhancing Security By employing secure technologies such as encryption and biometric authentication, payout solutions minimize fraud and ensure the safe transfer of funds. This builds trust among users, encouraging wider adoption.
Promoting Financial Literacy Many payout solutions integrate user-friendly platforms and educational tools to help individuals understand financial services better. This fosters confidence and encourages users to explore other financial products, such as savings accounts and microloans.
Digital Solutions Powering Payout Innovations
The role of digital solutions in advancing payout systems cannot be overstated. Technologies like mobile banking, blockchain, and artificial intelligence have revolutionized the way funds are distributed and accessed. For instance:
Mobile Wallets: These are at the forefront of digital payment solutions, enabling individuals without bank accounts to receive and spend money using their mobile devices.
Blockchain Technology: Secure and transparent, blockchain facilitates cross-border payouts with minimal fees, benefiting migrant workers sending money home.
AI and Data Analytics: These tools optimize payout processes by identifying patterns and reducing inefficiencies, ensuring smooth transactions.
Companies like Xettle Technologies are pioneering these digital innovations by providing custom payout solutions tailored to the unique needs of developing economies. Their platforms combine advanced security features with user-friendly interfaces, enabling a seamless experience for both individuals and businesses.
Case Studies: Payout Solutions in Action
Social Benefit Disbursements in India The Indian government’s Direct Benefit Transfer (DBT) scheme leverages payout solutions to deposit welfare payments directly into beneficiaries’ accounts. This has reduced leakages and ensured funds reach the intended recipients.
Gig Economy Payments in Africa In Africa, mobile payment systems like M-Pesa facilitate payouts for gig workers, enabling them to access their earnings instantly. This has been instrumental in empowering freelancers and small business owners.
Cross-Border Remittances in Southeast Asia Migrant workers in Southeast Asia rely on digital payout solutions to send money home. These solutions are faster and cheaper than traditional remittance methods, allowing families to access funds quickly.
Challenges and Opportunities
While payout solutions hold immense promise, certain challenges persist, such as:
Limited Digital Infrastructure: Many regions lack the internet connectivity needed to support digital solutions.
Regulatory Barriers: Complex regulations can hinder the deployment of payout systems.
Low Financial Literacy: Many individuals remain unaware of how to use payout solutions effectively.
Addressing these challenges requires collaboration between governments, financial institutions, and technology providers. By investing in infrastructure, streamlining regulations, and promoting financial education, stakeholders can unlock the full potential of payout solutions.
Conclusion
Payout solutions are a cornerstone of financial inclusion in developing economies, offering accessible, affordable, and secure ways to distribute funds. By leveraging digital solutions and collaborating with innovators like Xettle Technologies, organizations can create impactful systems that empower individuals and drive economic growth. As technology continues to advance, the role of payout solutions in fostering an inclusive financial ecosystem will only grow stronger.
3 notes
·
View notes
Text
Aible And Google Cloud: Gen AI Models Sets Business Security
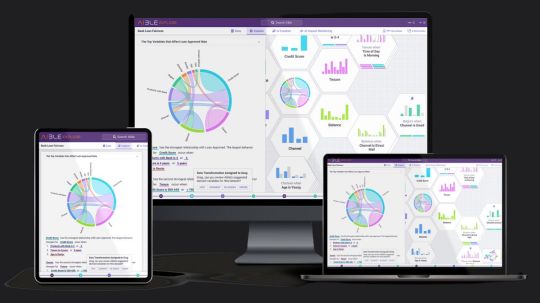
Enterprise controls and generative AI for business users in real time.
Aible
With solutions for customer acquisition, churn avoidance, demand prediction, preventive maintenance, and more, Aible is a pioneer in producing business impact from AI in less than 30 days. Teams can use AI to extract company value from raw enterprise data. Previously using BigQuery’s serverless architecture to save analytics costs, Aible is now working with Google Cloud to provide users the confidence and security to create, train, and implement generative AI models on their own data.
The following important factors have surfaced as market awareness of generative AI’s potential grows:
Enabling enterprise-grade control
Businesses want to utilize their corporate data to allow new AI experiences, but they also want to make sure they have control over their data to prevent unintentional usage of it to train AI models.
Reducing and preventing hallucinations
The possibility that models may produce illogical or non-factual information is another particular danger associated with general artificial intelligence.
Empowering business users
Enabling and empowering business people to utilize gen AI models with the least amount of hassle is one of the most beneficial use cases, even if gen AI supports many enterprise use cases.
Scaling use cases for gen AI
Businesses need a method for gathering and implementing their most promising use cases at scale, as well as for establishing standardized best practices and controls.
Regarding data privacy, policy, and regulatory compliance, the majority of enterprises have a low risk tolerance. However, given its potential to drive change, they do not see postponing the deployment of Gen AI as a feasible solution to market and competitive challenges. As a consequence, Aible sought an AI strategy that would protect client data while enabling a broad range of corporate users to swiftly adapt to a fast changing environment.
In order to provide clients complete control over how their data is used and accessed while creating, training, or optimizing AI models, Aible chose to utilize Vertex AI, Google Cloud’s AI platform.
Enabling enterprise-grade controls
Because of Google Cloud’s design methodology, users don’t need to take any more steps to ensure that their data is safe from day one. Google Cloud tenant projects immediately benefit from security and privacy thanks to Google AI products and services. For example, protected customer data in Cloud Storage may be accessed and used by Vertex AI Agent Builder, Enterprise Search, and Conversation AI. Customer-managed encryption keys (CMEK) can be used to further safeguard this data.
With Aible‘s Infrastructure as Code methodology, you can quickly incorporate all of Google Cloud’s advantages into your own applications. Whether you choose open models like LLama or Gemma, third-party models like Anthropic and Cohere, or Google gen AI models like Gemini, the whole experience is fully protected in the Vertex AI Model Garden.
In order to create a system that may activate third-party gen AI models without disclosing private data outside of Google Cloud, Aible additionally collaborated with its client advisory council, which consists of Fortune 100 organizations. Aible merely transmits high-level statistics on clusters which may be hidden if necessary instead of raw data to an external model. For instance, rather of transmitting raw sales data, it may communicate counts and averages depending on product or area.
This makes use of k-anonymity, a privacy approach that protects data privacy by never disclosing information about groups of people smaller than k. You may alter the default value of k; the more private the information transmission, the higher the k value. Aible makes the data transmission even more secure by changing the names of variables like “Country” to “Variable A” and values like “Italy” to “Value X” when masking is used.
Mitigating hallucination risk
It’s crucial to use grounding, retrieval augmented generation (RAG), and other strategies to lessen and lower the likelihood of hallucinations while employing gen AI. Aible, a partner of Built with Google Cloud AI, offers automated analysis to support human-in-the-loop review procedures, giving human specialists the right tools that can outperform manual labor.
Using its auto-generated Information Model (IM), an explainable AI that verifies facts based on the context contained in your structured corporate data at scale and double checks gen AI replies to avoid making incorrect conclusions, is one of the main ways Aible helps eliminate hallucinations.
Hallucinations are addressed in two ways by Aible’s Information Model:
It has been shown that the IM helps lessen hallucinations by grounding gen AI models on a relevant subset of data.
To verify each fact, Aible parses through the outputs of Gen AI and compares them to millions of responses that the Information Model already knows.
This is comparable to Google Cloud’s Vertex AI grounding features, which let you link models to dependable information sources, like as your company’s papers or the Internet, to base replies in certain data sources. A fact that has been automatically verified is shown in blue with the words “If it’s blue, it’s true.” Additionally, you may examine a matching chart created only by the Information Model and verify a certain pattern or variable.
The graphic below illustrates how Aible and Google Cloud collaborate to provide an end-to-end serverless environment that prioritizes artificial intelligence. Aible can analyze datasets of any size since it leverages BigQuery to efficiently analyze and conduct serverless queries across millions of variable combinations. One Fortune 500 client of Aible and Google Cloud, for instance, was able to automatically analyze over 75 datasets, which included 150 million questions and answers with 100 million rows of data. That assessment only cost $80 in total.
Aible may also access Model Garden, which contains Gemini and other top open-source and third-party models, by using Vertex AI. This implies that Aible may use AI models that are not Google-generated while yet enjoying the advantages of extra security measures like masking and k-anonymity.
All of your feedback, reinforcement learning, and Low-Rank Adaptation (LoRA) data are safely stored in your Google Cloud project and are never accessed by Aible.
Read more on Govindhtech.com
#Aible#GenAI#GenAIModels#BusinessSecurity#AI#BigQuery#AImodels#VertexAI#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
hmm, parents’ iMac from almost 10 years ago is dying. Fusion drive; HDD seems fine but SSD seems, well, fucked. Kernel panics causing a boot loop—no Macintosh HD visible—etc.
But not completely fucked. Adventure!
Brought it into the Apple Store today: guy turned the computer on in target disk mode (where it behaves like an external hard drive), connected it to a laptop, and there everything is! all the data!
get home, do exactly the same thing—doesn’t work.
The Fusion Drive shows up in disk utility, but of the (adjacent) partitions under “Macintosh HD”, which are (another) “Macintosh HD” and “Macintosh HD - Data”, only the latter will mount. Can’t seem to read anything from it, though. (“Permission denied”—weird.)
Meanwhile, if you mount and open the parent Macintosh HD, you see four empty folders: Library, System, Applications, Users, iirc.
Trying to restore any of these to an external hard drive via disk utility fails because the “seal is broken”. `diskutil apfs list` shows that every disk is unsealed except for the unmountable leaf Macintosh HD, which has a broken seal. (No data/user is encrypted with FileVault or anything on this disk, fwiw. diskutil unlockVolume doesn’t do anything as a result.)
Ok. So, I try `ddrescue`; this is where “Fatal read error: permission denied” comes from. Then I try it on the physical disks. Works fine on the HDD for quite a while, copying away with no errors. Encounters loads of read errors on the SSD. Pretty regularly, too, which I found odd: one every 6-8 seconds without fail. But it’s apparently able to rescue some data in the meantime, so I figure this isn’t just some timeout.
But what use to me is a bunch of corrupted data? It bugs me that it was working in the Apple Store. Let’s just get there again! What was different?
The only things I can think of are:
it was turned off (but plugged in) overnight beforehand. I don’t know anything about SSD failures, but maaaaybe something electrical is afoot.
maybe there was something about the exact sequence of things he tried first in the Apple Store. What was it? Recovery mode, safe mode, PRAM reset, halfway through internet recovery, then shut it down and go for target disk mode…?
maybe the fact that he had it plugged into ethernet mattered for some wacky reason. maybe some of the relevant components are near each other. what if the wifi card is heating up and disrupting the SSD, or something? well, that probably wouldn’t be immediate, and so wouldn’t explain the kernel panic. but, who knows.
Maybe something just jostled back into place while carrying the computer into the store and jostled back out while carrying it out.
Favorite option so far is something electrical having a really long relaxation time of some sort. So we’ll see, I guess…!
2 notes
·
View notes
Text
Best 10 Business Strategies for year 2024
In 2024 and beyond, businesses will have to change with the times and adjust their approach based on new and existing market realities. The following are the best 10 business approach that will help companies to prosper in coming year
1. Embrace Sustainability
The days when sustainability was discretionary are long gone. Businesses need to incorporate environmental, social and governance (ESG) values into their business practices. In the same vein, brands can improve brand identity and appeal to environmental advocates by using renewable forms of energy or minimizing their carbon footprints.
Example: a fashion brand can rethink the materials to use organic cotton and recycled for their clothing lines. They can also run a take-back scheme, allowing customers to return old clothes for recycling (not only reducing waste but creating and supporting the circular economy).
2. Leverage AI

AI is revolutionizing business operations. Using AI-fuelled solutions means that you can automate processes, bring in positive customer experiences, and get insights. AI chatbots: AI can be utilized in the form of a conversational entity to support and perform backend operations, as well.
With a bit more specificity, say for example that an AI-powered recommendation engine recommends products to customers based on their browsing history and purchase patterns (as the use case of retail). This helps to increase the sales and improve the shopping experience.
3. Prioritize Cybersecurity
Cybersecurity is of utmost important as more and more business transitions towards digital platforms. Businesses need to part with a more substantial amount of money on advanced protective measures so that they can keep sensitive data private and continue earning consumer trust. Regular security audits and training of employees can reduce these risks.
Example: A financial services firm may implement multi-factor authentication (MFA) for all online transactions, regularly control access to Internet-facing administrative interfaces and service ports as well as the encryption protocols to secure client data from cyberattacks.
4. Optimizing Remote and Hybrid Working Models

Remote / hybrid is the new normal Remote teams force companies to implement effective motivation and management strategies. Collaboration tools and a balanced virtual culture can improve productivity and employee satisfaction.
- Illustration: a Tech company using Asana / Trello etc. for pm to keep remote teams from falling out of balance. They can also organise weekly team-building activities to keep a strong team spirit.
5. Focus on Customer Experience
Retention and growth of the sales follow-through can be tied to high quality customer experiences. Harness data analytics to deepen customer insights and personalize product offers making your marketing campaigns personal: a customer support that is responsive enough can drive a great level of returning customers.
Example – For any e-commerce business, you can take user experience feedback tools to know about how your customers are getting along and make necessary changes. Custom email campaigns and loyalty programs can also be positively associated with customer satisfaction and retention.
6. Digitalization Investment

It is only the beginning of digital transformation which we all know, is key to global competitiveness. For streamlining, companies have to adopt the use advanced technologies such as Blockchain Technology and Internet of Things (IoT) in conjunction with cloud computing.
IoT example : real-time tracking and analytics to optimize supply chain management
7. Enhance Employee Skills
Develop Your Employees: Investing in employee development is key to succeeding as a business. The training is provided for the folks of various industries and so employees can increase their skills that are needed to work in a certain company. Employee performance can be enhanced by providing training programs in future technology skills and soft skills and job satisfaction.
Example: A marketing agency can host webinars or create courses to teach people the latest digital marketing trends and tools This can help to keep employees in the know which results in boosting their skills, making your campaigns successful.
8. Diversify Supply Chains

The ongoing pandemic has exposed the weaknesses of global supply chains. …diversify its supply base and promote the manufacturing of drugs in Nigeria to eliminate total dependence on a single source. In return, this approach increases resilience and reduces exposure to the risks of supply chain interruption.
- E.g., a consumer electronics company can source components from many suppliers in various regions. In so doing, this alleviates avoidable supply chain interruptions during times of political tensions or when disasters hit.
9. Make Decisions Based on Data
A business database is an asset for businesses. By implementing data, they allow you to make decisions based on the data that your analytics tools are providing. For example, sales analysis lets you track trends and better tailor your goods to the market.
Example: A retail chain can use data analytics to find out when a customer buys, and it change their purchasing policies. This can also reduce overstock and stockouts while overall, increasing efficiency.
10. Foster Innovation

Business Growth Innovation is Key A culture of creativity and experimentation should be established in companies. Funding R&D and teaming with startups can open many doors to both solve problems creatively but also tap into new markets.
Example: A software development firm could create an innovation lab where team members are freed to work on speculative projects. Moreover, work with start-ups on new technologies and solutions.
By adopting these strategies, businesses can navigate the turbulence for 2024 and roll up market — progressive.AI with an evolving dynamic market, being ahead of trends and updated is most likely will help you thrive in the business landscape.
#ai#business#business strategy#business growth#startup#fintech#technology#tech#innovation#ai in business
2 notes
·
View notes
Text
AWS Unveiled: Exploring the Boundless Horizons of Cloud Computing
Introduction: Embarking on the AWS Expedition
In the ever-evolving digital sphere, Amazon Web Services (AWS) emerges as a formidable player, revolutionizing the landscape of cloud computing and redefining the way businesses operate in the digital era. Offering an extensive array of cloud services, AWS serves as a catalyst for innovation, empowering organizations to scale, adapt, and thrive in a rapidly changing environment. Let's embark on an expedition into the realm of AWS, unraveling its diverse offerings and uncovering the transformative potential it holds for businesses across industries.

Decoding AWS: A Gateway to Digital Transformation
Amazon Web Services, or AWS, represents a comprehensive suite of cloud computing solutions provided by Amazon. Designed to meet the diverse needs of businesses, AWS offers a plethora of services spanning compute, storage, databases, machine learning, and more. By leveraging the power of the cloud, organizations can access scalable, flexible, and cost-effective solutions without the burden of managing physical infrastructure.
Exploring the Versatility of AWS: A Closer Look at Key Benefits
Unmatched Scalability: At the heart of AWS lies its unparalleled scalability, enabling businesses to seamlessly adjust their infrastructure to accommodate fluctuating demands. Whether faced with rapid growth or sudden spikes in traffic, AWS empowers organizations to scale their resources dynamically, ensuring optimal performance and resource utilization.
Cost-Efficient Operations: AWS adopts a pay-as-you-go pricing model, eliminating the need for upfront investments in infrastructure. By paying only for the resources they consume, organizations can optimize costs, improve budgetary predictability, and allocate resources more efficiently, thereby driving significant cost savings over time.
Global Accessibility: With a global network of data centers spanning multiple regions, AWS offers businesses unparalleled accessibility to cloud services from anywhere in the world. This global infrastructure enables organizations to deploy applications closer to their end-users, reducing latency, and enhancing the overall user experience.
Robust Security Measures: Security is paramount in the digital age, and AWS prioritizes data protection through robust encryption, identity management, and compliance certifications. By adhering to stringent security standards, AWS ensures the confidentiality, integrity, and availability of data, instilling confidence in businesses and customers alike.
Tailored Solutions for Every Need: AWS provides businesses with a diverse portfolio of services and tools, allowing them to customize their cloud environment to suit their specific requirements. Whether it's compute, storage, analytics, or machine learning, AWS offers a comprehensive suite of solutions tailored to address the unique needs of every organization.
Driving Innovation and Agility: AWS fuels innovation by granting access to cutting-edge technologies such as artificial intelligence, machine learning, and IoT. Through services like AWS Lambda and Amazon SageMaker, organizations can experiment, iterate, and innovate at an accelerated pace, gaining a competitive edge in the market and driving digital transformation.
Conclusion: Embracing the AWS Advantage for Future Growth
In conclusion, Amazon Web Services (AWS) represents a gateway to limitless possibilities, offering businesses the tools, resources, and agility they need to thrive in the digital age. By harnessing the power of AWS, organizations can unlock new opportunities, drive innovation, and achieve unparalleled scalability and efficiency in their operations. Whether you're a startup striving for rapid growth or an enterprise seeking to optimize costs, AWS provides the foundation for success in today's dynamic business landscape. So, seize the moment, embrace the AWS advantage, and embark on a journey of endless growth and innovation.
2 notes
·
View notes
Text
Revamp Your Business: Excelling in iOS App Development for Achieving Success
In today's digital era, having a robust presence in the mobile app market is vital for businesses aiming to thrive. With millions of users worldwide, iOS devices offer a lucrative platform for reaching and engaging with customers. However, excelling in iOS app development training requires more than just technical skills; it demands a strategic approach and a deep understanding of user needs and market trends. So, how can you revamp your business and achieve success in iOS app development? Let's explore.
Understanding the iOS Ecosystem
Before diving into iOS app development, it's essential to understand the ecosystem you're entering. iOS operates within a closed environment, offering users a seamless experience across devices. Familiarize yourself with Apple's guidelines, developer tools, and the App Store submission process to ensure compliance and maximize visibility.

Setting Clear Goals and Objectives
Define clear goals and objectives for your iOS app development project. Whether it's increasing brand awareness, driving sales, or enhancing customer loyalty, having a clear direction will guide your development process and help measure success.
User-Centric Design
User experience is paramount in iOS app development. Design your app with the end-user in mind, focusing on intuitive navigation, engaging visuals, and seamless interactions. Conduct user testing to gather feedback and refine your design iteratively.
Leveraging the Power of Swift
Swift, Apple's programming language for iOS app development, offers speed, safety, and modern syntax. Embrace Swift's features and best practices to write clean, efficient code that enhances your app's performance and maintainability.
Seamless Integration with Apple Ecosystem
Take advantage of the rich ecosystem of Apple products and services to create a seamless user experience. Integrate features like SiriKit, Apple Pay, and iCloud to enhance functionality and provide added value to your users.
Prioritizing Performance and Security
Ensure your iOS app delivers optimal performance and robust security measures. Optimize loading times, minimize app size, and implement encryption protocols to protect user data and build trust with your audience.
Regular Updates and Maintenance
Keep your iOS app relevant and competitive by regularly releasing updates and addressing user feedback. Stay ahead of bugs, performance issues, and compatibility issues with new iOS versions to maintain a positive user experience.
Effective Marketing Strategies
Develop a comprehensive marketing strategy to promote your iOS app and reach your target audience. Utilize social media, email marketing, app store optimization (ASO), and influencer partnerships to increase visibility and drive downloads.
Gathering and Analyzing User Feedback
Listen to your users and gather feedback to understand their needs and preferences. Utilize analytics tools to track user behavior, identify pain points, and make data-driven decisions to improve your app's performance and usability.
Staying Updated with Latest Trends and Features
Stay informed about the latest trends and features in iOS app development to remain competitive in the market. Attend conferences, join developer communities, and continuously invest in learning to innovate and adapt to changing user demands.
Revamping your business through iOS app development requires a strategic approach, focusing on user-centric design, efficient coding practices, and effective marketing strategies. By understanding the iOS ecosystem, setting clear goals, and prioritizing performance and security, you can create a successful app that resonates with your audience and drives business growth.
Know More - https://technorizen.com/
2 notes
·
View notes
Text
Going Over the Cloud: An Investigation into the Architecture of Cloud Solutions

Because the cloud offers unprecedented levels of size, flexibility, and accessibility, it has fundamentally altered the way we approach technology in the present digital era. As more and more businesses shift their infrastructure to the cloud, it is imperative that they understand the architecture of cloud solutions. Join me as we examine the core concepts, industry best practices, and transformative impacts on modern enterprises.
The Basics of Cloud Solution Architecture A well-designed architecture that balances dependability, performance, and cost-effectiveness is the foundation of any successful cloud deployment. Cloud solutions' architecture is made up of many different components, including networking, computing, storage, security, and scalability. By creating solutions that are tailored to the requirements of each workload, organizations can optimize return on investment and fully utilize the cloud.
Flexibility and Resilience in Design The flexibility of cloud computing to grow resources on-demand to meet varying workloads and guarantee flawless performance is one of its distinguishing characteristics. Cloud solution architecture create resilient systems that can endure failures and sustain uptime by utilizing fault-tolerant design principles, load balancing, and auto-scaling. Workloads can be distributed over several availability zones and regions to help enterprises increase fault tolerance and lessen the effect of outages.
Protection of Data in the Cloud and Security by Design
As data thefts become more common, security becomes a top priority in cloud solution architecture. Architects include identity management, access controls, encryption, and monitoring into their designs using a multi-layered security strategy. By adhering to industry standards and best practices, such as the shared responsibility model and compliance frameworks, organizations may safeguard confidential information and guarantee regulatory compliance in the cloud.
Using Professional Services to Increase Productivity Cloud service providers offer a variety of managed services that streamline operations and reduce the stress of maintaining infrastructure. These services allow firms to focus on innovation instead of infrastructure maintenance. They include server less computing, machine learning, databases, and analytics. With cloud-native applications, architects may reduce costs, increase time-to-market, and optimize performance by selecting the right mix of managed services.
Cost control and ongoing optimization Cost optimization is essential since inefficient resource use can quickly drive up costs. Architects monitor resource utilization, analyze cost trends, and identify opportunities for optimization with the aid of tools and techniques. Businesses can cut waste and maximize their cloud computing expenses by using spot instances, reserved instances, and cost allocation tags.
Acknowledging Automation and DevOps Important elements of cloud solution design include automation and DevOps concepts, which enable companies to develop software more rapidly, reliably, and efficiently. Architects create pipelines for continuous integration, delivery, and deployment, which expedites the software development process and allows for rapid iterations. By provisioning and managing infrastructure programmatically with Infrastructure as Code (IaC) and Configuration Management systems, teams may minimize human labor and guarantee consistency across environments.
Multiple-cloud and hybrid strategies In an increasingly interconnected world, many firms employ hybrid and multi-cloud strategies to leverage the benefits of many cloud providers in addition to on-premises infrastructure. Cloud solution architects have to design systems that seamlessly integrate several environments while ensuring interoperability, data consistency, and regulatory compliance. By implementing hybrid connection options like VPNs, Direct Connect, or Express Route, organizations may develop hybrid cloud deployments that include the best aspects of both public and on-premises data centers. Analytics and Data Management Modern organizations depend on data because it fosters innovation and informed decision-making. Thanks to the advanced data management and analytics solutions developed by cloud solution architects, organizations can effortlessly gather, store, process, and analyze large volumes of data. By leveraging cloud-native data services like data warehouses, data lakes, and real-time analytics platforms, organizations may gain a competitive advantage in their respective industries and extract valuable insights. Architects implement data governance frameworks and privacy-enhancing technologies to ensure adherence to data protection rules and safeguard sensitive information.
Computing Without a Server Server less computing, a significant shift in cloud architecture, frees organizations to focus on creating applications rather than maintaining infrastructure or managing servers. Cloud solution architects develop server less programs using event-driven architectures and Function-as-a-Service (FaaS) platforms such as AWS Lambda, Azure Functions, or Google Cloud Functions. By abstracting away the underlying infrastructure, server less architectures offer unparalleled scalability, cost-efficiency, and agility, empowering companies to innovate swiftly and change course without incurring additional costs.
Conclusion As we come to the close of our investigation into cloud solution architecture, it is evident that the cloud is more than just a platform for technology; it is a force for innovation and transformation. By embracing the ideas of scalability, resilience, and security, and efficiency, organizations can take advantage of new opportunities, drive business expansion, and preserve their competitive edge in today's rapidly evolving digital market. Thus, to ensure success, remember to leverage cloud solution architecture when developing a new cloud-native application or initiating a cloud migration.
1 note
·
View note