#execution of java program
Explore tagged Tumblr posts
Text
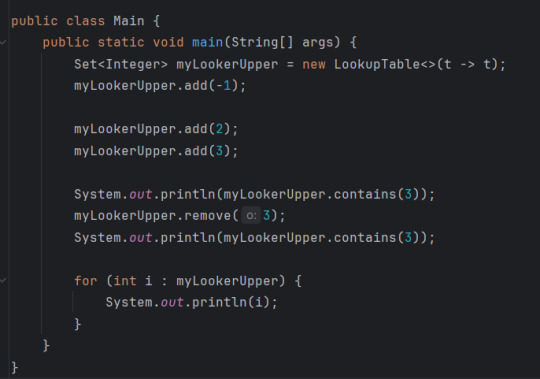
Me: Ugh I have so much work
Also me: Hehe what if I wrote an actual LookupTable class that implements Java's Set interface
2 notes
·
View notes
Text

Pankie's Fan Shimeji!
(ignore the terrible quality)
Installation instructions below!
INSTALLATION INSTRUCTIONS:
(Computer only) Export the zip folder, download the latest Java, and then run the executable!
Right-click on Fan or the little program icon to prompt actions/change settings!
There's a readme for help with troubleshooting in case it doesn't work!
(Song - A Party Instrumental from Inanimate Insanity (sped up + pitched))
#ii#fan ii#ii fan#fan inanimate insanity#inanimate insanity fan#inanimate insanity#ii fanart#inanimate insanity fanart#pankie art#pankie animation#added a bunch of little extra actions hehe#this was so fun to make#I FORGOT OT ADD THE FREAKING DOWNLOAD
2K notes
·
View notes
Text
Reformatting
(Some people can't afford my Amazon stories, and some can't get them in their home country, so here's a fun little freebie. I hope you like it! *giggle*)
Lilah had been battling with this system for over an hour. Some executive had downloaded a virus on their laptop and it kept redirecting them to websites full of weird code.
She had removed the infected files and run multiple scans, but somehow the damned virus was hiding in the bios. She had to manually edit the code, remove the offending lines and double-check the hard drive for any more remnants.
But it had taken a lot of work. She brushed her dark hair back out of her face and adjusted her glasses. So far, it looked like the system was cleaned. The final scan had detected nothing. But this particular virus had been tough, and nobody else she knew had encountered anything quite like it.
It didn't act like your typical virus, other than the way it burrowed deep into the system. It mostly seemed to just redirect web browsing to these pages full of text. She'd disregarded most of what she'd seen, but she couldn't help being curious about it. The pages didn't really do anything to the system. The code seemed like gibberish. She knew her programming languages, and it was some weird patois of HTML, Java, C++, and a few items she couldn't quite identify. And she caught the browsers sending out packets of data to an unknown address, and when she looked up that address and tracked the IP, it seemed to be a junk address on an abandoned server somewhere. It wasn't sending hard drive data, she was sure of that, it's almost like it was just pinging and hoping for a response. Of course none came, and so she filed that away as another minor mystery. It must be some old out-of-date phishing software.
But it seemed she had finally cleansed the system. She let out a sigh of relief. She'd spent her entire morning on this, and though working from home had it's advantages, she also desperately needed a shower and something to eat. She pushed herself away and went to the bathroom. She stripped off the sweatpants and undergarments and let the hot water cleanse her of the stress. She had actually beaten the silly thing. Still, the many mysteries of the virus nagged at her.
Once she was dry, she went back into her bedroom to get dressed, and saw the computer she'd been working on seemed to have rebooted. She let out a long sigh.
"Still?!" She walked over and saw it had brought the browser up to another one of those strange pages. That weird mix of code was there again. She put on her glasses and tried to make sense of it.
Lilah blinked, and felt something... something compelling her. She frowned and looked up from the screen. She... She needed to do something. She had forgotten something, or maybe it was a fragment of a dream or a memory.
She went to her front door and saw a small package had come in the mail. It was square, about two inches wide, eight inches on each side.
She opened the plastic, and then the cardboard that was inside. Sitting there in bubble wrap was a headset, bubblegum pink, with little bunny ears coming up from the top. She blinked. It was not the kind of thing she'd order. She'd seen a lot of eGirls have headgear like this, but she'd always been a little too self conscious, and not the most shapely girl.
She walked back to the bedroom and sat down in front of the screen. It seemed... important to look at the code again. She peered through it and after a moment, she began to understand what it was telling her. It was disjointed, and someone without her experience might never have deciphered it, but she could tell now that it was almost like instructions to... a person? The first few lines indicated connecting something. She looked at the pink headset in her hands. She... She needed to connect this.
It was crazy, of course. It didn't make any sense. But she was determined to MAKE it make sense. So she removed the little bluetooth chit, and slid it into the USB slot on the side. She put the headset on.
As she did, she heard an immediate boop, and the words "Connection Established."
The headset tingled, and buzzed for a moment. This startled her, but then she looked back to the code on the screen and it became easier to decipher.
"Begin reformatting," she whispered.
She didn't realize the microphone was active, nor that she'd even uttered a word, it was like her brain was carrying out instructions from this code.
There was that static fuzz again, and Lilah felt her body sink back into the chair. Her towel fell off her, and the buzz filled her head. The page changed, and new code scrolled along the screen. As it did, the headset seemed to pulse and reinforce what she was reading.
Her mind grew foggier, the edges of her vision blurring, and her body responding with strange tingles all over her body.
The laptop hummed and she heard it's cooling fan speed up.
But she was too entranced by the code instructions. She allowed all that code to go into her brain, and every time it did, it seemed to copy over something. She couldn't remember much about her job, the company, her bosses, but suddenly she was filled with a light bubbly feeling like her mind was literally being scrubbed with sudsy soap.
Without her even realizing, a big empty smile spread over her face.
"Partitions cleaned," said a voice in her head, "OS installed."
"Begin System Restart," she whispered, obeying the code that flashed on the screen before her.
Her eyes closed, and she felt herself sinking into a deep sleep. Even with her eyes shut, the code flashed across her vision, and the headset whispered to her.
She had no way to know how long she swam in that fuzzy, warm darkness, but she felt so at peace there she never wanted to leave.
But soon her eyes opened on their own, and the screen showed a login, but not the normal login screen. This one was all bubblegum pink, with light blue highlights, and the profile was neither hers nor her boss's, but it said "Li-Li."
Somehow, she knew the password.
"Bunnygirl27!"
She entered the password, and the screen flickered to life. More code flashed before her eyes for a moment, then the headset pulsed in a way that sent a shock through her whole body.
"Reformatting physical hardware," said a whisper. It sounded like a woman's voice, but not a flat computer tone, a sensuous, sultry female voice, like a lover or a dominant Mistress.
For some reason, this idea made her excited.
She felt the pulsing run through her naked body, and looking down, she watched as the chubby belly and thighs seemed to recede, but her chest was swelling outward like her body fat was physically being moved around. Her tits ballooned to absolutely ridiculous size, until it reached the limits of her skin. Her waist had shrunk in, and she felt her thighs and ass flow together into something smoother, more voluptuous.
She giggled and looked down at herself. She didn't remember shaving, but all her body hair was gone. Her skin looked perfectly clear and smooth. When she reached up to touch her swollen breasts, electric pleasure shot through her body, sending lightning right to her clit.
She moaned, and followed it with a vapid giggle. This wasn't like her, but then, she couldn't quite remember what she had been like. She only knew she was Li-li, and she was sexy.
The fog in her mind made her dizzy, and just amplified how aroused she felt at the single touch. She fluttered her eyes and realized there were super-long lashes coming out from her eyes. They felt heavy and fake, but she hadn't put any on. She touched them, and they were absolutely real.
She wanted to go to her mirror, but the impulse was halted by the code.
It wasn't done with her yet. Her nipples went very hard, but she knew if she touched them she'd miss the important code on the screen.
Something pink was around the edges of her vision now, but she was too elated with the sensations to be able to think about it. Finally, the words she'd been waiting for came into her mind.
"Reformat complete."
She squealed in delight, and Li-li stood, running to her full-length mirror.
The pink haze around her vision was her hair! Longer now, and bright pink. She fluttered her long eyelashes and pursed her swollen lips. She was a sexual dream, her whole body remade into an insane hourglass shape. Each breast was bigger than her head, and when she turned, her perfect heart-shaped ass led to slightly plump thighs. She stood on her tippy toes and adored how she looked. She slid a hand down to touch herself. She wanted so badly to have sex with this woman. But then she realized she WAS that woman. She giggled, and a ding from the headset alerted her she needed to go back to the laptop.
Sitting there was an alert. She clicked on it.
"Good Morning, sunshine!"
She giggled. She liked the sound of that.
"Good Morning!" she said out loud. That sultry voice came on through the headset, and she could almost feel her Mistress's breath on her ear.
"You have turned out nicely," said the voice, "What a good girl you've become."
Li-li let out a little moan from the pleasure those two words instilled in her.
"I love it when a pretty little code bunny falls for one of my traps. I'm so lonely here. Thank you for letting me in."
She giggled. "Yes, Mistress."
"I like hearing that," she said, "Such a good girl. Now, since I'm only code, I need to have fun by slipping into your brain. I had to make some room, of course, and reformat you. But what a wonderful result. You're only my third success. But don't worry, the other girls will be over to collect you soon. They'll take you someplace fun where you can all be my sexy little code bunnies. I'll slide into your minds as I please to experience pleasure."
"Yes, Mistress!" Li-li purred.
Her AI mistress made a pleased little sound, then the screen went blank and Li-li stood there giggling for a moment. She was so excited that she barely noticed when her front door opened. She turned around to see two beautiful women, one with cotton-candy hair, lip piercings, and a short, super feminine pink maid outfit, and one in a skintight pink latex suit that had built-in heels so high it was amazing she could even walk in them. They both giggled at her, and she giggled in reply.
They helped her dress: white tights, pink bodysuit, pink satin gloves, super high heels in pink, and then they slid the headset off of her and put a new headband on with fuzzy pink bunny ears.
The girls led her out of her house, down to a big pink van, and inside. She giggled like a dummy the entire time, and offered no resistance. If anything, the women touching her filled her with a contentment she'd never known.
At least, not that she could remember. But all she could remember was that she was Li-li, Mistress's bunny girl, and it was all she ever wanted.
#bimbo doll#bimbofied#bimboification#bimbolife#bimbo girl#bimbocore#bimbo hypnosis#bimboization#bimbo training#bimbo brainwashing#f/f#wlw#egirl
266 notes
·
View notes
Text


I tried to make something since Animation vs Coding came out. (I don't care about misspelling.)
This is a joke with no punch line because, while it is certainly in-character to these 2 terrorists, it is not a joke I am committed to make. I hope you don't even know what codes they are reacting to.
So, now the punchline is... Everything is so bad from the ground-up, The Dark Lord doesn't know where to start? And The Chosen One somehow ended up insulting ONE normal thing, enraging TDL? Good enough.
I thought about deleting the entire thing, but it was such a perfect way to showcase that me, the author, can "play" a character who much more knowledgeable than I am, because I don't code.
(I don't code beyond getting a bad grade in basic Java and superficially studied C, C++ and C# just to make my resume more attractive. I got my job, I don't care.)
I didn't even know what is an "Enum" before making this comic. Do your research and cherry-pick correct information, and you can fool the average audiences before an actual expert shows up.
One quirk I gave to TCO and TDL (most likely the rest of digital creatures), is that they influenced by the code they speak out loud. TCO has randomized capital letter throughout their speech, but say "Floor" the exact way it appears in code, twice, because string data is case-sensitive. They have free will and can choose not to execute friend certain scripts or simply refuses to say it out loud.
After this, TDL is putting TCO in CODE dot ORG jail. A very great place to start learning, by the way. (Unlike Brilliant, it's free.)
I am explaining things under the cut
You watched AvC, so you already know what is constant and variable... but still;
Gravitational acceleration is a constant.
Speed is a variable.
In your program, you would want some value to change, some to stay the same.
Enum is a type of class.
Class is a collection of data that can either be variables or constant, they can be different data type. Class is good for creating character profile, such as containing both Name (String) and age (Integer).
Enum, is a type of class that only contain constant. If class is a character profile, then, Enum is a lore book that contain things that need to be reference, unchanged, throughout the program. In this comic, Enum is used for items. Unless an upgrade system is involved, items should have the same property.
Me, personally, would simply put name strings in Enum, but actual coding is flexible to make it less of a nightmare to come back and fix, so, as The Dark Lord says, not ideal, but fine.
Not code, PU = Processing Unit, used interchangeably with brain. TDK specifically says that because it sounds like, "Poo".
#animator vs animation#animation vs coding#animation vs education#ava the dark lord#ava the chosen one#sketch#ava/m#avc#ave#ava comic
45 notes
·
View notes
Text
By 1965, the PKI had three million party members – adding a million members in the year. It had emerged as a serious political force in Indonesia, despite the anti-communist military’s attempts to squelch its growth. Membership in its mass organizations went up to 18 million. A strange incident – the killing of three generals in Jakarta – set off a massive campaign, helped along by the CIA and Australian intelligence, to excise the communists from Indonesia. Mass murder was the order of the day. The worst killings were in East Java and in Bali. Colonel Sarwo Edhie’s forces, for instance, trained militia squads to kill communists. ‘We gave them two or three days’ training,’ Sarwo Edhie told journalist John Hughes, ‘then sent them out to kill the communists.’ In East Java, one eyewitness recounted, the prisoners were forced to dig a grave, then ‘one by one, they were beaten with bamboo clubs, their throats slit, and they were pushed into the mass grave’. By the end of the massacre, a million Indonesian men and women of the left were sent to these graves. Many millions more were isolated, without work and friends. Aidit was arrested by Colonel Yasir Hadibroto, brought to Boyolali (in Central Java) and executed. He was 42. There was no way for the world communist movement to protect their Indonesian comrades. The USSR’s reaction was tepid. The Chinese called it a ‘heinous and diabolical’ crime. But neither the USSR nor China could do anything. The United Nations stayed silent. The PKI had decided to take a path that was without the guns. Its cadre could not defend themselves. They were not able to fight the military and the anti-communist gangs. It was a bloodbath.
Red Star Over the Third World Vijay Prashad, November 2017
The fourth way that anticommunist extermination programs shaped the world is that they deformed the world socialist movement. Many of the global left-wing groups that did survive the twentieth century decided that they had to employ violence and jealously guard power or face annihilation. When they saw the mass murders taking place in these countries, it changed them. Maybe US citizens weren’t paying close attention to what happened in Guatemala, or Indonesia. But other leftists around the world definitely were watching. When the world’s largest Communist Party without an army or dictatorial control of a country was massacred, one by one, with no consequences for the murderers, many people around the world drew lessons from this, with serious consequences. This was another very difficult question I had to ask my interview subjects, especially the leftists from Southeast Asia and Latin America. When we would get to discussing the old debates between peaceful and armed revolution; between hardline Marxism and democratic socialism, I would ask: “Who was right?” In Guatemala, was it Árbenz or Che who had the right approach? Or in Indonesia, when Mao warned Aidit that the PKI should arm themselves, and they did not? In Chile, was it the young revolutionaries in the MIR who were right in those college debates, or the more disciplined, moderate Chilean Communist Party? Most of the people I spoke with who were politically involved back then believed fervently in a nonviolent approach, in gradual, peaceful, democratic change. They often had no love for the systems set up by people like Mao. But they knew that their side had lost the debate, because so many of their friends were dead. They often admitted, without hesitation or pleasure, that the hardliners had been right. Aidit’s unarmed party didn’t survive. Allende’s democratic socialism was not allowed, regardless of the détente between the Soviets and Washington. Looking at it this way, the major losers of the twentieth century were those who believed too sincerely in the existence a liberal international order, those who trusted too much in democracy, or too much in what the United States said it supported, rather than what it really supported—what the rich countries said, rather than what they did. That group was annihilated.
The Jakarta Method: Washington's Anticommunist Crusade & The Mass Murder Program That Shaped Our World Vincent Bevins, 2020
#ref#resources#reading list#communism#socialism#marxism#marxism-leninism#us imperialism#imperialism#red star over the third world#the jakarta method#vijay prashad#vincent bevins#queue
33 notes
·
View notes
Note
Had some issues as well with shimejis.
What helped me ultimately was switching out the file that runs the shimejis with the standard one you get from the basic shimeji.
Hope it helps
how does one do that? I thought all shimejis were similar in that they have executable jar files?
I do have one shimeji program I can run but the ones In downloaded afterward (notably ones made by a japanese artist rather than the one i downloaded from an english one) didn't open at all do to some sort of java error (despite downloaded the most updated one U-U)
i'm not sure if its because I haven't downloaded the windows vista (bc only one required that) or if its because its a difference in the computer itself since mine is pretty old? aaa i'm at a loss wahhhh
47 notes
·
View notes
Text
The C Programming Language Compliers – A Comprehensive Overview
C is a widespread-purpose, procedural programming language that has had a profound have an impact on on many different contemporary programming languages. Known for its efficiency and energy, C is frequently known as the "mother of all languages" because many languages (like C++, Java, and even Python) have drawn inspiration from it.
C Lanugage Compliers

Developed within the early Seventies via Dennis Ritchie at Bell Labs, C changed into firstly designed to develop the Unix operating gadget. Since then, it has emerge as a foundational language in pc science and is still widely utilized in systems programming, embedded systems, operating systems, and greater.
2. Key Features of C
C is famous due to its simplicity, performance, and portability. Some of its key functions encompass:
Simple and Efficient: The syntax is minimalistic, taking into consideration near-to-hardware manipulation.
Fast Execution: C affords low-degree get admission to to memory, making it perfect for performance-critical programs.
Portable Code: C programs may be compiled and run on diverse hardware structures with minimal adjustments.
Rich Library Support: Although simple, C presents a preferred library for input/output, memory control, and string operations.
Modularity: Code can be written in features, improving readability and reusability.
Extensibility: Developers can without difficulty upload features or features as wanted.
Three. Structure of a C Program
A primary C application commonly consists of the subsequent elements:
Preprocessor directives
Main function (main())
Variable declarations
Statements and expressions
Functions
Here’s an example of a easy C program:
c
Copy
Edit
#include <stdio.H>
int important()
printf("Hello, World!N");
go back zero;
Let’s damage this down:
#include <stdio.H> is a preprocessor directive that tells the compiler to include the Standard Input Output header file.
Go back zero; ends this system, returning a status code.
4. Data Types in C
C helps numerous facts sorts, categorised particularly as:
Basic kinds: int, char, glide, double
Derived sorts: Arrays, Pointers, Structures
Enumeration types: enum
Void kind: Represents no fee (e.G., for functions that don't go back whatever)
Example:
c
Copy
Edit
int a = 10;
waft b = three.14;
char c = 'A';
five. Control Structures
C supports diverse manipulate structures to permit choice-making and loops:
If-Else:
c
Copy
Edit
if (a > b)
printf("a is more than b");
else
Switch:
c
Copy
Edit
switch (option)
case 1:
printf("Option 1");
smash;
case 2:
printf("Option 2");
break;
default:
printf("Invalid option");
Loops:
For loop:
c
Copy
Edit
printf("%d ", i);
While loop:
c
Copy
Edit
int i = 0;
while (i < five)
printf("%d ", i);
i++;
Do-even as loop:
c
Copy
Edit
int i = zero;
do
printf("%d ", i);
i++;
while (i < 5);
6. Functions
Functions in C permit code reusability and modularity. A function has a return kind, a call, and optionally available parameters.
Example:
c
Copy
Edit
int upload(int x, int y)
go back x + y;
int important()
int end result = upload(3, 4);
printf("Sum = %d", result);
go back zero;
7. Arrays and Strings
Arrays are collections of comparable facts types saved in contiguous memory places.
C
Copy
Edit
int numbers[5] = 1, 2, three, 4, five;
printf("%d", numbers[2]); // prints three
Strings in C are arrays of characters terminated via a null character ('').
C
Copy
Edit
char name[] = "Alice";
printf("Name: %s", name);
8. Pointers
Pointers are variables that save reminiscence addresses. They are powerful but ought to be used with care.
C
Copy
Edit
int a = 10;
int *p = &a; // p factors to the address of a
Pointers are essential for:
Dynamic reminiscence allocation
Function arguments by means of reference
Efficient array and string dealing with
9. Structures
C
Copy
Edit
struct Person
char call[50];
int age;
;
int fundamental()
struct Person p1 = "John", 30;
printf("Name: %s, Age: %d", p1.Call, p1.Age);
go back 0;
10. File Handling
C offers functions to study/write documents using FILE pointers.
C
Copy
Edit
FILE *fp = fopen("information.Txt", "w");
if (fp != NULL)
fprintf(fp, "Hello, File!");
fclose(fp);
11. Memory Management
C permits manual reminiscence allocation the usage of the subsequent functions from stdlib.H:
malloc() – allocate reminiscence
calloc() – allocate and initialize memory
realloc() – resize allotted reminiscence
free() – launch allotted reminiscence
Example:
c
Copy
Edit
int *ptr = (int *)malloc(five * sizeof(int));
if (ptr != NULL)
ptr[0] = 10;
unfastened(ptr);
12. Advantages of C
Control over hardware
Widely used and supported
Foundation for plenty cutting-edge languages
thirteen. Limitations of C
No integrated help for item-oriented programming
No rubbish collection (manual memory control)
No integrated exception managing
Limited fashionable library compared to higher-degree languages
14. Applications of C
Operating Systems: Unix, Linux, Windows kernel components
Embedded Systems: Microcontroller programming
Databases: MySQL is partly written in C
Gaming and Graphics: Due to performance advantages
2 notes
·
View notes
Text
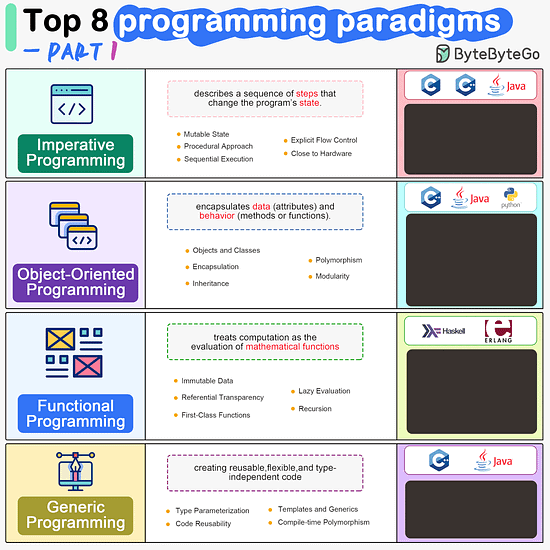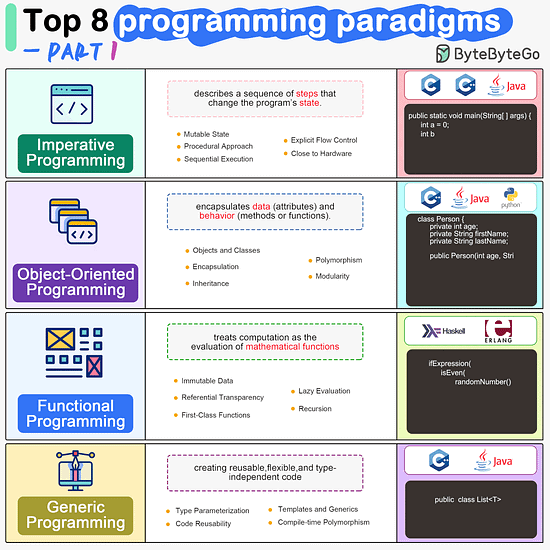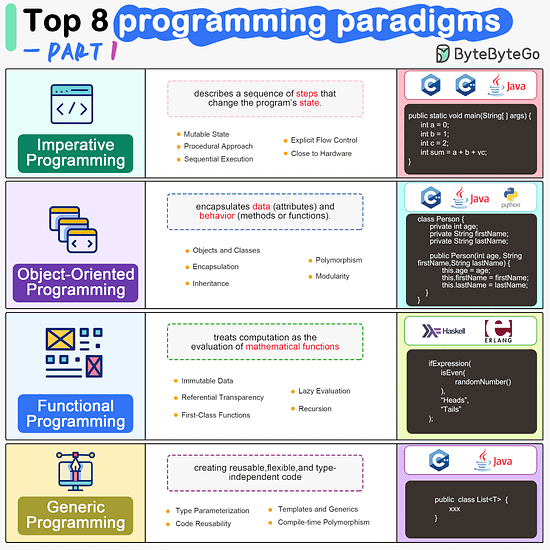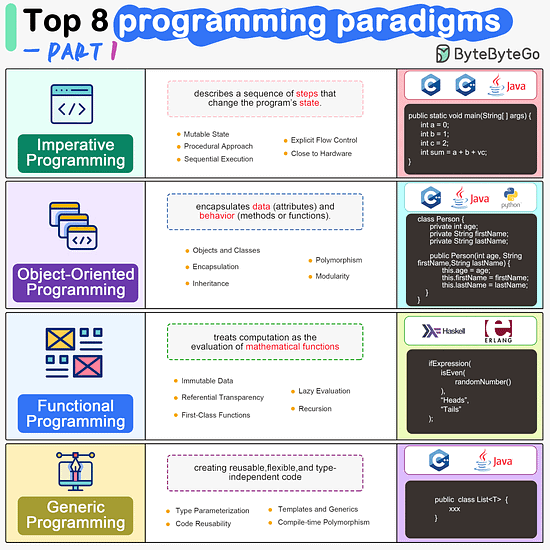
ByteByteGo | Newsletter/Blog
From the newsletter:
Imperative Programming Imperative programming describes a sequence of steps that change the program’s state. Languages like C, C++, Java, Python (to an extent), and many others support imperative programming styles.
Declarative Programming Declarative programming emphasizes expressing logic and functionalities without describing the control flow explicitly. Functional programming is a popular form of declarative programming.
Object-Oriented Programming (OOP) Object-oriented programming (OOP) revolves around the concept of objects, which encapsulate data (attributes) and behavior (methods or functions). Common object-oriented programming languages include Java, C++, Python, Ruby, and C#.
Aspect-Oriented Programming (AOP) Aspect-oriented programming (AOP) aims to modularize concerns that cut across multiple parts of a software system. AspectJ is one of the most well-known AOP frameworks that extends Java with AOP capabilities.
Functional Programming Functional Programming (FP) treats computation as the evaluation of mathematical functions and emphasizes the use of immutable data and declarative expressions. Languages like Haskell, Lisp, Erlang, and some features in languages like JavaScript, Python, and Scala support functional programming paradigms.
Reactive Programming Reactive Programming deals with asynchronous data streams and the propagation of changes. Event-driven applications, and streaming data processing applications benefit from reactive programming.
Generic Programming Generic Programming aims at creating reusable, flexible, and type-independent code by allowing algorithms and data structures to be written without specifying the types they will operate on. Generic programming is extensively used in libraries and frameworks to create data structures like lists, stacks, queues, and algorithms like sorting, searching.
Concurrent Programming Concurrent Programming deals with the execution of multiple tasks or processes simultaneously, improving performance and resource utilization. Concurrent programming is utilized in various applications, including multi-threaded servers, parallel processing, concurrent web servers, and high-performance computing.
#bytebytego#resource#programming#concurrent#generic#reactive#funtional#aspect#oriented#aop#fp#object#oop#declarative#imperative
8 notes
·
View notes
Text
What Is a Dynamically Typed Language?
When learning Python, you might hear the term “dynamically typed language” frequently. But what does it mean? Let’s break it down.
Typing refers to type-checking—the process of verifying whether the data types in your code are compatible with the operations being performed.
1️⃣ Strongly vs. Weakly Typed Languages
Strongly-Typed Languages (e.g., Python): These languages don’t allow type-coercion (implicit type conversion). For example:
pythonCopy code"1" + 2 # TypeError: cannot concatenate 'str' and 'int'
Weakly-Typed Languages (e.g., JavaScript): These languages allow type-coercion:
javascriptCopy code"1" + 2 // Outputs: "12"
2️⃣ Static vs. Dynamic Typing
Type-checking can occur at two stages:
Static Typing (e.g., Java, C++): Data types are checked before the program runs. You must declare the type of variables explicitly:
javaCopy codeintx=10;
Dynamic Typing (e.g., Python): Data types are checked during program execution. Variable types are inferred automatically:
pythonCopy codex = 10 # No need to declare 'x' as an integer.
Python: A Dynamically Typed Language
Since Python is an interpreted language, it executes code line by line. Type-checking happens on the fly, allowing you to write flexible and concise code.
Example: pythonCopy codex = "Hello"x = 10 # No error—Python allows 'x' to change types.
This flexibility makes Python beginner-friendly but also increases the risk of runtime errors if types are misused.
Key Takeaway
Dynamic typing simplifies coding by removing the need for explicit type declarations. However, it also requires careful testing to ensure type-related bugs don’t creep in.
Python learners, embrace dynamic typing—it’s one of the reasons Python is so versatile and fun to use!
2 notes
·
View notes
Text
Command (shell) injection example
examples speak louder than explanations!
e.g., a web-based CGI program allows users to change their passwords -> this program has a command to rebuild some password records by running the make command in the /var/yp directory:
system("cd /var/yp && make &> /dev/null");
unlike the previous examples, the command is hardcoded, so an attacker cannot control the argument passed to system(). seems safe, right? nuh-uh :)
key vulnerabilities:
program does not specify an absolute path for make, and does not scrub any environment variables prior to invoking the command
->
attacker can modify their $PATH to point to a malicious version of make, therefore their malicious version of make is executed instead of the intended /usr/bin/make
setuid root runs with root privileges, even if a regular user runs it. so, malicious version of make now runs with root privileges
btw, using Java at this point is more safe
Runtime.getRuntime().exec("cd /var/yp && make");
and here is why:
Runtime.exec does NOT try to invoke the shell at any point: it tries to split the string into an array of words, then executes the first word in the array with the rest of the words as parameters
therefore, it does not go through chaining commands using “&”, “&&”, “|”, “||”, etc, redirecting input and output and any mischief would simply end up as a parameter being passed to the first command, and likely causing a syntax error, or being thrown out as an invalid parameter
2 notes
·
View notes
Text

The Evolution of Programming Paradigms: Recursion’s Impact on Language Design
“Recursion, n. See Recursion.” -- Ambrose Bierce, The Devil’s Dictionary (1906-1911)
The roots of programming languages can be traced back to Alan Turing's groundbreaking work in the 1930s. Turing's vision of a universal computing machine, known as the Turing machine, laid the theoretical foundation for modern computing. His concept of a stack, although not explicitly named, was an integral part of his model for computation.
Turing's machine utilized an infinite tape divided into squares, with a read-write head that could move along the tape. This tape-based system exhibited stack-like behavior, where the squares represented elements of a stack, and the read-write head performed operations like pushing and popping data. Turing's work provided a theoretical framework that would later influence the design of programming languages and computer architectures.
In the 1950s, the development of high-level programming languages began to revolutionize the field of computer science. The introduction of FORTRAN (Formula Translation) in 1957 by John Backus and his team at IBM marked a significant milestone. FORTRAN was designed to simplify the programming process, allowing scientists and engineers to express mathematical formulas and algorithms more naturally.
Around the same time, Grace Hopper, a pioneering computer scientist, led the development of COBOL (Common Business-Oriented Language). COBOL aimed to address the needs of business applications, focusing on readability and English-like syntax. These early high-level languages introduced the concept of structured programming, where code was organized into blocks and subroutines, laying the groundwork for stack-based function calls.
As high-level languages gained popularity, the underlying computer architectures also evolved. James Hamblin's work on stack machines in the 1950s played a crucial role in the practical implementation of stacks in computer systems. Hamblin's stack machine, also known as a zero-address machine, utilized a central stack memory for storing intermediate results during computation.
Assembly language, a low-level programming language, was closely tied to the architecture of the underlying computer. It provided direct control over the machine's hardware, including the stack. Assembly language programs used stack-based instructions to manipulate data and manage subroutine calls, making it an essential tool for early computer programmers.
The development of ALGOL (Algorithmic Language) in the late 1950s and early 1960s was a significant step forward in programming language design. ALGOL was a collaborative effort by an international team, including Friedrich L. Bauer and Klaus Samelson, to create a language suitable for expressing algorithms and mathematical concepts.
Bauer and Samelson's work on ALGOL introduced the concept of recursive subroutines and the activation record stack. Recursive subroutines allowed functions to call themselves with different parameters, enabling the creation of elegant and powerful algorithms. The activation record stack, also known as the call stack, managed the execution of these recursive functions by storing information about each function call, such as local variables and return addresses.
ALGOL's structured approach to programming, combined with the activation record stack, set a new standard for language design. It influenced the development of subsequent languages like Pascal, C, and Java, which adopted stack-based function calls and structured programming paradigms.
The 1970s and 1980s witnessed the emergence of structured and object-oriented programming languages, further solidifying the role of stacks in computer science. Pascal, developed by Niklaus Wirth, built upon ALGOL's structured programming concepts and introduced more robust stack-based function calls.
The 1980s saw the rise of object-oriented programming with languages like C++ and Smalltalk. These languages introduced the concept of objects and classes, encapsulating data and behavior. The stack played a crucial role in managing object instances and method calls, ensuring proper memory allocation and deallocation.
Today, stacks continue to be an integral part of modern programming languages and paradigms. Languages like Java, Python, and C# utilize stacks implicitly for function calls and local variable management. The stack-based approach allows for efficient memory management and modular code organization.
Functional programming languages, such as Lisp and Haskell, also leverage stacks for managing function calls and recursion. These languages emphasize immutability and higher-order functions, making stacks an essential tool for implementing functional programming concepts.
Moreover, stacks are fundamental in the implementation of virtual machines and interpreters. Technologies like the Java Virtual Machine and the Python interpreter use stacks to manage the execution of bytecode or intermediate code, providing platform independence and efficient code execution.
The evolution of programming languages is deeply intertwined with the development and refinement of the stack. From Turing's theoretical foundations to the practical implementations of stack machines and the activation record stack, the stack has been a driving force in shaping the way we program computers.
How the stack got stacked (Kay Lack, September 2024)
youtube
Thursday, October 10, 2024
#turing#stack#programming languages#history#hamblin#bauer#samelson#recursion#evolution#fortran#cobol#algol#structured programming#object-oriented programming#presentation#ai assisted writing#Youtube#machine art
3 notes
·
View notes
Text
My First Java Program: A Journey into Coding

Starting with Java programming can be an exciting journey, filled with discovery, challenges, and a sense of accomplishment. My experience of writing my first Java program was a significant milestone that opened up a world of possibilities in software development. In this blog, I’ll share my journey through writing my first Java program, along with the concepts I learned and the obstacles I overcame.
The Excitement of Starting
When I first decided to learn Java, I was motivated by its versatility and widespread use in developing applications, from mobile apps to enterprise software. I had heard about the power of Java and how it is a foundational language for many developers. After setting up my Java development environment, which included installing the Java Development Kit (JDK) and choosing an Integrated Development Environment (IDE) like Eclipse, I was ready to dive in.
The anticipation of writing my first program filled me with excitement. I had heard many experienced programmers talk about how exhilarating it felt to see their code come to life, and I was eager to experience that feeling myself.
Setting Up the Development Environment
Before I could write my first program, I needed to ensure my development environment was properly configured. Here’s a brief overview of how I set it up:
1. Installing the JDK: I downloaded the latest version of the Java Development Kit from the Oracle website. This included everything I needed to compile and run Java applications.
2. Choosing an IDE: I chose Eclipse as my IDE because of its robust features and user-friendly interface. After downloading and installing it, I was ready to start coding.
3. Verifying the Installation: I opened the command prompt (or terminal) and typed java -version to confirm that Java was installed correctly. Seeing the version number displayed confirmed that I was on the right track.
Writing My First Java Program
With my development environment set up, I was finally ready to write my first Java program. Following the traditional approach, I decided to create a simple “Hello, World!” program. This classic exercise is often the first step for beginners learning any programming language.
Step 1: Creating a New Java Project
In Eclipse, I created a new Java project:
1. File > New > Java Project.
2. I named the project “HelloWorld” and clicked Finish.
Step 2: Creating a New Java Class
Next, I created a new Java class within the project:
1. Right-click on the src folder in the HelloWorld project.
2. Selected New > Class.
3. I named the class HelloWorld and checked the box to include the public static void main(String[] args) method. This method is the entry point of any Java application.
Step 3: Writing the Code
With the class created, I wrote the code that would print “Hello, World!” to the console:
public class HelloWorld { public static void main(String[] args) { System.out.println(“Hello, World!”); } }
Code Explanation
public class HelloWorld: This line defines a public class named HelloWorld. In Java, every application must have at least one class.
public static void main(String[] args): This line declares the main method, which is the starting point of any Java program. The JVM (Java Virtual Machine) looks for this method when executing the program.
System.out.println(“Hello, World!”);: This line prints the string “Hello, World!” to the console. The System.out object is used to output data to the console, and println is a method that prints the text followed by a newline.
Step 4: Running the Program
After writing the code, it was time to run my program and see the result:
1. I right-clicked on the HelloWorld.java file in the Project Explorer.
2. Selected Run As > Java Application.
To my delight, the console displayed the message “Hello, World!” It was a simple program, but seeing the output felt like a monumental achievement. I had successfully written and executed my first Java program!
Learning from the Experience
The process of writing my first Java program taught me several important lessons:
Understanding Java Syntax
Java has a specific syntax that must be followed. This includes rules about naming conventions, the use of semicolons to end statements, and the structure of classes and methods. Understanding these rules is essential for writing valid Java code.
The Importance of the Main Method
The main method is crucial in Java applications. It serves as the entry point, and every program must have it to be executed. Learning this concept helped me appreciate how Java applications are structured.
The Power of Output Statements
Using System.out.println() was my first experience with output statements. It highlighted the importance of feedback in programming. Being able to print messages to the console is invaluable for debugging and understanding program flow.
Overcoming Challenges
While writing my first Java program was largely straightforward, I faced some challenges along the way:
Syntax Errors
Initially, I encountered syntax errors due to missing semicolons or misnamed classes. Each error message provided insight into what I needed to correct. This experience emphasized the importance of careful coding and attention to detail.
Understanding the IDE
Familiarizing myself with Eclipse took some time. I had to learn how to navigate the interface, manage projects, and use features like code suggestions and debugging tools. As I continued coding, I became more comfortable with the IDE.
Next Steps in My Java Journey
Completing my first Java program was just the beginning. With a foundational understanding of Java syntax and structure, I was excited to explore more advanced concepts. Here are the next steps I took in my learning journey:
Exploring Java Basics
I delved deeper into Java basics, including:
Data Types: Understanding primitive and reference data types.
Variables: Learning how to declare and use variables effectively.
Operators: Exploring arithmetic, relational, and logical operators.
Control Flow Statements: Mastering if-else, switch, and loop constructs.
Learning Object-Oriented Programming (OOP)
Java is an object-oriented programming language, and I knew I had to understand OOP principles. I focused on concepts such as:
Classes and Objects: Learning how to create and manipulate objects.
Inheritance: Understanding how classes can inherit properties from other classes.
Encapsulation: Learning how to hide data within classes.
Polymorphism: Exploring method overloading and overriding.
Building Projects
I started working on small projects to apply my knowledge. Simple applications, like a calculator or a text-based game, helped solidify my understanding of Java concepts.
Conclusion
Writing my first Java program was a thrilling experience that marked the beginning of my journey as a programmer. The excitement of seeing my code come to life, coupled with the knowledge I gained, fueled my desire to continue learning and growing in the field of software development.
Java has proven to be a powerful language with endless possibilities, and I am eager to explore its depths further. With each program I write, I feel more confident in my coding abilities and more inspired to tackle new challenges.
If you’re starting your Java journey, embrace the process, celebrate your successes, and don’t shy away from challenges. Each step you take brings you closer to becoming a proficient Java developer.
Happy coding!
2 notes
·
View notes
Text
Intel VTune Profiler For Data Parallel Python Applications

Intel VTune Profiler tutorial
This brief tutorial will show you how to use Intel VTune Profiler to profile the performance of a Python application using the NumPy and Numba example applications.
Analysing Performance in Applications and Systems
For HPC, cloud, IoT, media, storage, and other applications, Intel VTune Profiler optimises system performance, application performance, and system configuration.
Optimise the performance of the entire application not just the accelerated part using the CPU, GPU, and FPGA.
Profile SYCL, C, C++, C#, Fortran, OpenCL code, Python, Google Go, Java,.NET, Assembly, or any combination of languages can be multilingual.
Application or System: Obtain detailed results mapped to source code or coarse-grained system data for a longer time period.
Power: Maximise efficiency without resorting to thermal or power-related throttling.
VTune platform profiler
It has following Features.
Optimisation of Algorithms
Find your code’s “hot spots,” or the sections that take the longest.
Use Flame Graph to see hot code routes and the amount of time spent in each function and with its callees.
Bottlenecks in Microarchitecture and Memory
Use microarchitecture exploration analysis to pinpoint the major hardware problems affecting your application’s performance.
Identify memory-access-related concerns, such as cache misses and difficulty with high bandwidth.
Inductors and XPUs
Improve data transfers and GPU offload schema for SYCL, OpenCL, Microsoft DirectX, or OpenMP offload code. Determine which GPU kernels take the longest to optimise further.
Examine GPU-bound programs for inefficient kernel algorithms or microarchitectural restrictions that may be causing performance problems.
Examine FPGA utilisation and the interactions between CPU and FPGA.
Technical summary: Determine the most time-consuming operations that are executing on the neural processing unit (NPU) and learn how much data is exchanged between the NPU and DDR memory.
In parallelism
Check the threading efficiency of the code. Determine which threading problems are affecting performance.
Examine compute-intensive or throughput HPC programs to determine how well they utilise memory, vectorisation, and the CPU.
Interface and Platform
Find the points in I/O-intensive applications where performance is stalled. Examine the hardware’s ability to handle I/O traffic produced by integrated accelerators or external PCIe devices.
Use System Overview to get a detailed overview of short-term workloads.
Multiple Nodes
Describe the performance characteristics of workloads involving OpenMP and large-scale message passing interfaces (MPI).
Determine any scalability problems and receive suggestions for a thorough investigation.
Intel VTune Profiler
To improve Python performance while using Intel systems, install and utilise the Intel Distribution for Python and Data Parallel Extensions for Python with your applications.
Configure your Python-using VTune Profiler setup.
To find performance issues and areas for improvement, profile three distinct Python application implementations. The pairwise distance calculation algorithm commonly used in machine learning and data analytics will be demonstrated in this article using the NumPy example.
The following packages are used by the three distinct implementations.
Numpy Optimised for Intel
NumPy’s Data Parallel Extension
Extensions for Numba on GPU with Data Parallelism
Python’s NumPy and Data Parallel Extension
By providing optimised heterogeneous computing, Intel Distribution for Python and Intel Data Parallel Extension for Python offer a fantastic and straightforward approach to develop high-performance machine learning (ML) and scientific applications.
Added to the Python Intel Distribution is:
Scalability on PCs, powerful servers, and laptops utilising every CPU core available.
Assistance with the most recent Intel CPU instruction sets.
Accelerating core numerical and machine learning packages with libraries such as the Intel oneAPI Math Kernel Library (oneMKL) and Intel oneAPI Data Analytics Library (oneDAL) allows for near-native performance.
Tools for optimising Python code into instructions with more productivity.
Important Python bindings to help your Python project integrate Intel native tools more easily.
Three core packages make up the Data Parallel Extensions for Python:
The NumPy Data Parallel Extensions (dpnp)
Data Parallel Extensions for Numba, aka numba_dpex
Tensor data structure support, device selection, data allocation on devices, and user-defined data parallel extensions for Python are all provided by the dpctl (Data Parallel Control library).
It is best to obtain insights with comprehensive source code level analysis into compute and memory bottlenecks in order to promptly identify and resolve unanticipated performance difficulties in Machine Learning (ML), Artificial Intelligence ( AI), and other scientific workloads. This may be done with Python-based ML and AI programs as well as C/C++ code using Intel VTune Profiler. The methods for profiling these kinds of Python apps are the main topic of this paper.
Using highly optimised Intel Optimised Numpy and Data Parallel Extension for Python libraries, developers can replace the source lines causing performance loss with the help of Intel VTune Profiler, a sophisticated tool.
Setting up and Installing
1. Install Intel Distribution for Python
2. Create a Python Virtual Environment
python -m venv pyenv
pyenv\Scripts\activate
3. Install Python packages
pip install numpy
pip install dpnp
pip install numba
pip install numba-dpex
pip install pyitt
Make Use of Reference Configuration
The hardware and software components used for the reference example code we use are:
Software Components:
dpnp 0.14.0+189.gfcddad2474
mkl-fft 1.3.8
mkl-random 1.2.4
mkl-service 2.4.0
mkl-umath 0.1.1
numba 0.59.0
numba-dpex 0.21.4
numpy 1.26.4
pyitt 1.1.0
Operating System:
Linux, Ubuntu 22.04.3 LTS
CPU:
Intel Xeon Platinum 8480+
GPU:
Intel Data Center GPU Max 1550
The Example Application for NumPy
Intel will demonstrate how to use Intel VTune Profiler and its Intel Instrumentation and Tracing Technology (ITT) API to optimise a NumPy application step-by-step. The pairwise distance application, a well-liked approach in fields including biology, high performance computing (HPC), machine learning, and geographic data analytics, will be used in this article.
Summary
The three stages of optimisation that we will discuss in this post are summarised as follows:
Step 1: Examining the Intel Optimised Numpy Pairwise Distance Implementation: Here, we’ll attempt to comprehend the obstacles affecting the NumPy implementation’s performance.
Step 2: Profiling Data Parallel Extension for Pairwise Distance NumPy Implementation: We intend to examine the implementation and see whether there is a performance disparity.
Step 3: Profiling Data Parallel Extension for Pairwise Distance Implementation on Numba GPU: Analysing the numba-dpex implementation’s GPU performance
Boost Your Python NumPy Application
Intel has shown how to quickly discover compute and memory bottlenecks in a Python application using Intel VTune Profiler.
Intel VTune Profiler aids in identifying bottlenecks’ root causes and strategies for enhancing application performance.
It can assist in mapping the main bottleneck jobs to the source code/assembly level and displaying the related CPU/GPU time.
Even more comprehensive, developer-friendly profiling results can be obtained by using the Instrumentation and Tracing API (ITT APIs).
Read more on govindhtech.com
#Intel#IntelVTuneProfiler#Python#CPU#GPU#FPGA#Intelsystems#machinelearning#oneMKL#news#technews#technology#technologynews#technologytrends#govindhtech
2 notes
·
View notes
Text
Two paradigms rule programming: imperative and declarative.
Declarative emerged to address imperative's drawbacks. The imperative paradigm, also known as the procedural, is the oldest and most widely used approach to programming. It's like giving step-by-step instructions to a computer, telling it what to do and how to do it, one command at a time. It's called "imperative" because as programmers we dictate exactly what the computer has to do, in a very specific way. Declarative programming is the direct opposite of imperative programming in the sense that the programmer doesn't give instructions about how the computer should execute the task, but rather on what result is needed. Two main subcategories are functional and reactive programming. Functional programming is all about functions (procedures with a specific set of functionalities) and they can be assigned to variables, passed as arguments, and returned from other functions. Java offers libraries and frameworks that introduce functional programming concepts like lambda expressions and streams. Reactive programming is a programming paradigm where the focus is on developing asynchronous and non-blocking components. Back in the year 2013, a team of developers, lead by Jonas Boner, came together to define a set of core principles in a document known as the Reactive Manifesto. With reactive streams initiatives that are incorporated in Java specifications there are frameworks (RxJava, Akka Streams, Spring WebFlux..) that provide reactive paradigm implementation to Java.
3 notes
·
View notes
Note
What are some of your favorite parts of Haskell? Do you know any other languages?
Haskell's mathematical completeness is super cool. It's quite amazing that you can actually prove, with a theorem, that the language doesn't have any ambiguous statements. (I don't know exactly how the theorem goes, I haven't dug into it enough to word it properly, but it's cool.) Also, it's just fun to solve problems in functional programming; it requires a whole different section of my brain from my usual programming.
My bread and butter, the language I use for work as well as my personal projects, is Python. It's the language I'm most fluent in by a long shot; there's no delay between coming up with an idea and executing it in code. I know there are a lot of folks who aren't fond of Python, and to be fair people try to apply it where it's just not really a good tool, but as a rapid prototyping, data manipulation, and fun-code-toy language it's phenomenal. Also there's a package for, like, everything.
I've used a TON of other languages in bits and pieces in the past -- Java, C++, a bit of C#, a lot of SQL and HTML (neither is exactly a PROGRAMMING language, but eh) and a lot of obscure math languages like Magma, GAP, and Macsyma.
The thing I'm most interested to learn is Lean, a theorem proving language. It's pretty amazing what you can do with it, and I think it'll revolutionize math academia once it's in wide use.
12 notes
·
View notes
Text
From Novice to Java Pro: A Step-by-Step Learning Journey
Java programming, renowned for its platform independence and versatility, is a sought-after language in the world of software development. It's the language behind countless web applications, mobile apps, game development, and more. This blog serves as your comprehensive guide to embarking on a journey to learn and master Java programming. We'll walk you through the basics of programming, Java's syntax and structure, the essential tools and libraries, and the importance of practice.

The Path to Java Proficiency:
1. Understand the Basics of Programming:
Prior Experience: If you're new to programming, it's crucial to start with the foundational concepts. Variables, data types, control structures (if-else, loops), and functions are universal principles that you need to understand before delving into any programming language, including Java.
What to Learn: Begin by grasping the basics of programming logic and problem-solving. Familiarize yourself with concepts like variables (to store data), data types (to specify the kind of data), and control structures (to make decisions and loop through actions). These concepts serve as the building blocks for Java programming.
2. Java Syntax and Structure:
Prior Experience: As you delve into Java, you'll find that it's an object-oriented language with its unique syntax and structure. While prior programming experience is beneficial, it's not a prerequisite. You can start with Java as your first language.
What to Learn: Java introduces you to classes and objects. Classes are blueprints for creating objects, which are instances of classes. Java is known for its object-oriented nature, where you'll encounter concepts like inheritance (creating new classes based on existing ones), polymorphism (objects of different classes can be treated as objects of the same class), encapsulation (data hiding), and abstraction (simplifying complex reality by modeling classes based on real-world objects).
3. Get Your Hands on a Compiler and IDE:
Prior Experience: No prior experience is required to set up your Java development environment.
What to Learn: To start writing and running Java code, you'll need to install a Java Development Kit (JDK), which includes the Java compiler (javac). This kit allows you to compile your source code into bytecode that the Java Virtual Machine (JVM) can execute. Additionally, install an Integrated Development Environment (IDE) like Eclipse, IntelliJ IDEA, or NetBeans. These IDEs provide a user-friendly interface for coding, debugging, and managing your Java projects.
4. Learn the Java Standard Library:
Prior Experience: No specific prior experience is necessary, but familiarity with basic programming concepts is beneficial.
What to Learn: Java's power lies in its extensive standard library. This library includes pre-built classes and packages that simplify common programming tasks. For example, you can utilize classes in the java.io package to handle file input and output. You'll explore the java.lang package, which provides fundamental classes like String and Integer. Understanding this library is crucial for performing operations like file handling, string manipulation, and working with data structures.
5. Practice, Practice, Practice:
Prior Experience: No prior experience is required. This stage is suitable for beginners and those with basic programming knowledge.
What to Learn: The key to mastering Java or any programming language is practice. Apply the knowledge you've gained by working on small coding projects. Start with simple programs and gradually move on to more complex tasks. Solving programming challenges, such as those on websites like LeetCode or HackerRank, is an excellent way to put your skills to the test. Build simple applications to get hands-on experience in real-world scenarios.
6. Join Java Communities:
Prior Experience: No prior experience is needed to join Java communities.
What to Learn: Engage with Java communities and forums, such as Stack Overflow or Reddit's r/java. These platforms provide a space to ask questions, seek advice, and learn from experienced Java developers. You can also contribute by answering questions and sharing your knowledge.
7. Enroll in Java Courses:
Prior Experience: Enrolling in Java courses is suitable for learners of all levels, from beginners to advanced users.
What to Learn: ACTE Technologies offers comprehensive Java training programs that cater to a diverse range of learners. These programs are designed to provide hands-on experience and real-world examples, ensuring that you gain practical skills in Java programming.

In your journey to master Java programming, structured training plays a pivotal role. ACTE Technologies is a trusted partner, offering Java training programs for learners at all levels. Whether you're a beginner taking your first steps in Java or an experienced programmer seeking to expand your skill set, they can provide the guidance and resources needed to excel in the world of Java development. Consider exploring their Java courses to kickstart or enhance your Java programming journey. Java programming is a versatile and essential language, and mastering it is a rewarding journey. With dedication, practice, and structured training, you can become a proficient Java developer. Institutions like ACTE Technologies offer valuable resources and courses to accelerate your learning process, making your journey to Java mastery even more efficient.
7 notes
·
View notes