#how to hack windows using kali linux
Explore tagged Tumblr posts
Text

OHHH yes — Kali Linux vs Parrot OS — the eternal debate among cybersecurity enthusiasts, ethical hackers, and digital warriors like you ⚔️🖥️ Let’s break it down clearly and honestly:
🔥 KALI LINUX
Developed by: Offensive Security Focus: Penetration Testing & Red Team Ops Base: Debian Best For: Professionals, CTFs, Exploitation
🔧 Key Highlights:
Comes pre-loaded with 600+ tools.
Regularly used in OSCP, CEH, and other cert training.
Lightweight and minimal, but that means you have to configure a lot yourself.
Designed with experienced users in mind.
Has a “Kali Undercover” mode to mimic Windows (yes, for ops that require stealth 🔥).
👎 Cons:
Not very privacy-focused.
Can be too raw for beginners unless you're already deep in the game.
Not designed for daily use or casual browsing.
🦜 PARROT OS
Developed by: Frozenbox Focus: Penetration Testing AND Privacy Base: Debian Best For: Beginners to Intermediates, Privacy Geeks
🔧 Key Highlights:
Includes anonymity tools (Tor, I2P, Anonsurf) by default.
Offers multiple editions: Security, Home, and Cloud.
More polished UI — easier out of the box.
Lighter on system resources compared to Kali.
Better for everyday use + hacking tools baked in.
👎 Cons:
Slightly less tool-rich than Kali (but not by much).
Might feel "bloated" to users who want just pen-testing stuff.
⚔️ HEAD-TO-HEAD: WHO WINS?
FeatureKali Linux 💀Parrot OS 🦜Toolset💯🔥Privacy Tools😬✅Performance (lightweight)💪⚡Beginner-Friendly😵👍Community Support🧠 Massive💬 SolidLooks/PolishMinimalistSleek
🧠 BOTTOM LINE:
Choose Kali if: You're serious about offensive security, studying for a cert like OSCP, or want maximum control over tools and configurations. Think Red Team.
Choose Parrot OS if: You want a more balanced experience between hacking tools and daily usability, with added privacy features and a user-friendly design.
Both are powerful. It comes down to your use case and how much of a tinkerer vs user you are.
2 notes
·
View notes
Text
Installing Kali Linux on a USB Stick: A Step-by-Step Guide
If you want a portable, powerful cybersecurity toolkit you can carry in your pocket, installing Kali Linux on a USB stick is the perfect solution. With Kali on a USB, you can boot into your personalized hacking environment on almost any computer without leaving a trace — making it a favorite setup for ethical hackers, penetration testers, and cybersecurity enthusiasts.

In this guide, we'll walk you through how to install Kali Linux onto a USB drive — step-by-step — so you can have a portable Kali environment ready wherever you go.
Why Install Kali Linux on a USB?
Before we dive into the steps, here’s why you might want a Kali USB:
Portability: Carry your entire hacking setup with you.
Privacy: No need to install anything on the host machine.
Persistence: Save your settings, files, and tools even after rebooting.
Flexibility: Boot into Kali on any system that allows USB boot.
There are two main ways to use Kali on a USB:
Live USB: Runs Kali temporarily without saving changes after reboot.
Persistent USB: Saves your files and system changes across reboots.
In this article, we’ll focus on setting up a Live USB, and I'll also mention how to add persistence if you want. and if you seek knowledge about kali linux you can visit our website any time
Website Name : Linux Tools Guide
What You’ll Need
✅ A USB drive (at least 8GB; 16GB or more recommended if you want persistence). ✅ Kali Linux ISO file (download it from the official Kali website). ✅ Rufus (for Windows) or Etcher/balenaEtcher (for Mac/Linux/Windows). ✅ A computer that can boot from USB.
Step 1: Download the Kali Linux ISO
Go to the Kali Linux Downloads page and grab the latest version of the ISO. You can choose between the full version or a lightweight version depending on your USB size and system requirements.
Tip: Always verify the checksum of the ISO to ensure it hasn't been tampered with!
Step 2: Insert Your USB Drive
Plug your USB stick into your computer. ⚠️ Warning: Installing Kali onto the USB will erase all existing data on it. Backup anything important first!
Step 3: Create a Bootable Kali Linux USB
Depending on your operating system, the tool you use may vary:
For Windows Users (using Rufus):
Download and open Rufus (Get Rufus here).
Select your USB drive under Device.
Under Boot selection, choose the Kali Linux ISO you downloaded.
Keep the Partition scheme as MBR (for BIOS) or GPT (for UEFI) based on your system.
Click Start and wait for the process to complete.
For Mac/Linux Users (using balenaEtcher):
Download and open balenaEtcher (Get Etcher here).
Select the Kali ISO.
Select the USB drive.
Click Flash and wait until it's done.
That's it! You now have a Live Kali USB ready.
Step 4: Boot Kali Linux from the USB
Restart your computer with the USB plugged in.
Enter the BIOS/UEFI settings (usually by pressing a key like F12, Esc, Del, or F2 right after starting the computer).
Change the boot order to boot from the USB first.
Save changes and reboot.
You should now see the Kali Linux boot menu! Select "Live (amd64)" to start Kali without installation.
(Optional) Step 5: Adding Persistence
Persistence allows you to save files, system changes, or even installed tools across reboots — super useful for real-world usage.
Setting up persistence requires creating an extra partition on the USB and tweaking a few settings. Here's a quick overview:
Create a second partition labeled persistence.
Format it as ext4.
Mount it and create a file /persistence.conf inside it with the content: cppCopyEdit/ union
When booting Kali, choose the "Live USB Persistence" option.
Persistence is a little more technical but absolutely worth it if you want a real working Kali USB system!
Troubleshooting Common Issues
USB not showing up in boot menu?
Make sure Secure Boot is disabled in BIOS.
Ensure the USB was properly written (try writing it again if necessary).
Kali not booting properly?
Verify the ISO file integrity.
Try a different USB port (preferably USB 2.0 instead of 3.0 sometimes).
Persistence not working?
Double-check the /persistence.conf file and make sure it's correctly placed.
Conclusion
Installing Kali Linux onto a USB stick is one of the smartest ways to carry a secure, full-featured hacking lab with you anywhere. Whether you’re practicing ethical hacking, doing security audits, or just exploring the world of cybersecurity, a Kali USB drive gives you power, portability, and flexibility all at once.
Once you’re set up, the possibilities are endless — happy hacking! 🔥
2 notes
·
View notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
Top 8 Cybersecurity Skills You Must Have

In an era where businesses increasingly operate online, handling vast amounts of digital data and sensitive information, the demand for cybersecurity expertise has reached an all-time high. Cybersecurity refers to the practice of protecting computer systems, networks, devices, and data from theft, damage, unauthorized access, or any other form of unauthorized or malicious use.
In this comprehensive guide, we’ll delve into the top eight cybersecurity skills, expanded from the original five due to the evolving landscape of the field. By the end of this tutorial, you’ll be well-equipped to embark on a rewarding career in cybersecurity.
Networking and system administration
At the heart of cybersecurity lies an intricate understanding of networking. To effectively secure data, you must grasp the technical intricacies of data transmission. Earning certifications like CompTIA Security+ and Cisco CCNA is a solid starting point. System administration is equally crucial. It involves configuring and maintaining computer systems, demanding an inquisitive mindset for exploring various computer features and settings. Networking and system administration are the foundational pillars of cybersecurity, allowing you to understand data flows, system vulnerabilities, and potential entry points for malicious actors.

Knowledge of operating systems and virtual machines
A cybersecurity professional’s proficiency should encompass operating systems like Windows, Linux, and Mac OS. Versatility across multiple OSs is essential, as the digital landscape comprises a diverse range of environments. Moreover, familiarity with Kali Linux, a Linux distribution renowned for ethical hacking and penetration testing, is invaluable. It boasts an arsenal of tools for Penetration Testing, Malware Analysis, Security Research, and more. Operating systems are the battlegrounds where cybersecurity experts defend against threats and vulnerabilities, making mastery of these environments essential.
Network security control
Network Security Control comprises various measures to bolster network security. Understanding how your network functions, the roles of routers, firewalls, and other devices is fundamental. Firewalls, both hardware and software, serve as gatekeepers to block unauthorized traffic from the internet. Cybersecurity experts employ firewalls to filter and prevent illicit network access. Proficiency in Intrusion Detection Systems (IDS), Intrusion Prevention Systems, Virtual Private Networks (VPNs), and remote access is essential. As a cybersecurity practitioner, you must operate IDS to identify security policy violations and malicious network traffic. These tools are the guardians of the digital kingdom, safeguarding against unauthorized access and malicious activity.

Coding
Cybersecurity professionals should acquaint themselves with coding languages. This knowledge is pivotal to addressing future cybersecurity challenges. Coding languages to explore include:
C and C++: Low-level programming languages vital for cybersecurity, allowing you to dissect and understand the inner workings of software and systems.
Python: A high-level language useful for identifying and resolving vulnerabilities through scripting and automation.
JavaScript: Ideal for countering cross-site scripting attacks, making the web safer for users.
PHP: A crucial skill for safeguarding websites, as it is a commonly targeted language by cybercriminals.
HTML: Fundamental for understanding web page structures and identifying potential vulnerabilities in web applications.
Go lang: Valuable for cryptography, a cornerstone of secure communication in the digital realm.
SQL: Vital for recognizing and mitigating SQL injection attacks, a common technique used by attackers.
Assembly Language: Essential for comprehending malware functionality, aiding in malware analysis and reverse engineering. Coding languages are the tools in a cybersecurity expert’s arsenal, allowing them to analyze, detect, and mitigate threats.
Cloud security
As organizations increasingly adopt public and hybrid cloud platforms such as AWS and Azure, professionals with cloud security skills are in high demand. Just like Application Development Security, Cloud Security emphasizes building secure systems from the outset, making professionals proficient in managing platforms like Microsoft Azure, AWS, and Google Cloud highly sought after. Cloud security is not just about securing data in the cloud but also configuring cloud environments, enforcing access controls, and ensuring data integrity, making it a critical skill in the digital age.
Blockchain security
The rise of blockchain technology underscores its significance in enhancing security. Cybersecurity experts must acquaint themselves with blockchain’s security aspects. It holds the potential to transform security in areas like Internet of Things devices, network control, supply chain integration, identity management, and mobile computing. Blockchain’s complex, decentralized nature makes it an ideal solution for securing critical data in a digital world rife with cyber threats. Understanding how to implement and maintain blockchain security is essential for future-proofing the digital landscape.

The Internet of Things (IoT)
With over 30 billion IoT devices projected to be connected globally by 2025, security vulnerabilities multiply. IoT security takes center stage, emphasizing the need to protect connected devices and networks, even those with minimal human intervention. The complexity of IoT ecosystems requires cybersecurity professionals to secure these devices, data transmissions, and networks. IoT security emphasizes protecting connected devices and networks over the Internet, especially since most of these devices access networks without human intervention or oversight. Therefore, it becomes important to make sure that proper security measures are in place so that IoT devices can be left alone to perform their functions automatically, without cybersecurity experts having to be concerned about keeping out unauthorized intruders.
Artificial Intelligence (AI)
Artificial Intelligence emerges as a game-changer in cybersecurity. It introduces automation, enabling cybersecurity professionals to identify and respond to threats more effectively. AI can evolve to handle emerging threats and hacking techniques, significantly bolstering cybersecurity measures. AI brings a level of automation and support that is unmatched by human capabilities, catching threats that may otherwise go unnoticed and unaddressed. Artificial Intelligence can also be trained to learn and evolve, making it better equipped to handle new emerging threats and hacking techniques. This makes AI a valuable ally in the ongoing battle against cyber threats.
Additional cybersecurity skills
In addition to the primary skills mentioned above, consider these supplementary skills to strengthen your cybersecurity prowess:
Risk Analysis
Identifying, managing, and mitigating risks is pivotal. Cybersecurity professionals are required to identify, manage, and mitigate risks, making them invaluable assets to organizations looking to protect their digital assets.
Information security
Protecting electronic data from unauthorized access is a foundational skill. Companies require skilled professionals who can protect their electronic data from unauthorized access.
Security incident handling & response
Preparing to handle security threats in real-time is an essential skill for any cybersecurity expert. With security incident management, you are required to identify, manage, record, and analyze security threats in real-time. As a security practitioner, you must also manage and analyze the security information and event management (SIEM) tools and services. Handling security incidents effectively is essential for minimizing damage and maintaining the integrity of an organization’s security.
Security audit
It is an internal check that is carried out to find flaws in the organization’s information system. Security audit and compliance knowledge are very crucial because any missed area of regulatory compliance might incur significant fines and penalties for the organization. Conducting security audits is essential for ensuring that an organization’s security measures are effective and compliant with relevant laws and regulations.
Laws and regulations
This is an often overlooked cybersecurity aspect. There are several cybersecurity laws and regulations that you should be aware of. These laws define how you can use the internet and protect people from becoming victims of cybercrimes. Understanding the legal and regulatory aspects of cybersecurity is essential for ensuring that an organization’s practices are in compliance with the law and that individuals’ rights are protected.
Conclusion
Cybersecurity is an ever-evolving field. Staying current with new hacks and tools is essential. Moreover, soft skills play a crucial role in advancing your career in cybersecurity. This dynamic and in-demand skillset can lead to a highly rewarding career, with numerous job opportunities and competitive salaries.
Are you ready to embark on your journey to becoming a cybersecurity professional? The cybersecurity landscape is constantly evolving, making it an exciting and rewarding field for those with the right skill set. If you have any questions or need further guidance on acquiring these skills, feel free to ask in the comments section. Your journey to becoming a cybersecurity expert begins here!
Interesting headings:
Affiliate marketing case studies
Bonuses
Reviews
0 notes
Note
Which computers can and can't run Linux? I've always heard of it but I haven't ever found the right person to ask what it is and what it allows you to do.
Wow, my first ask! Thanks! Let's try this.
To answer your question, any x86 computer can run Linux. This probably means any computer you own, specifically anything with an Intel or AMD CPU, which is pretty much all computers except some tablets, and Macs made after 2018 or so. (Yes, I know versions of Linux exist for ARM computers, you can probably find them if you need them, we are not having that conversation.) Any Windows desktop or laptop you have should be able to handle it.
As for what you can do with Linux, it basically just lets you use a computer with a different operating system than Windows or Mac. Since it is open source, it is very common for professionals to use it for custom made or embedded applications, like I have a friend who works on a company that makes robot tractors who use machine learning to recognize and pick weeds, while leaving crops intact. For whatever reason, it's easier to do what they do on Linux. So much of the world runs on it, even if you don't see it every day. (Unless you have an android phone, which is based on Linux)
The main issue with trying Linux as a beginner is it is highly fragmentary, as there are many organizations that adapt it to different needs. Different versions are called Distributions or Distros.
As for what distros to use, I have heard Ubuntu and Mint are good for beginners, and are the only ones I have really played with it. There are also specialized versions of Linux like Kali, which comes with hacking tools, if you want to learn hacking (Be sure to only use it legally if you try it!). There are also specialized versions for servers and other business applications. There are even specialized versions for gaming, like on the steam deck. Any version you are interested in should have instructions on how to install it on their site, but be sure to set up a dual boot if you don't want to destroy your install of Windows/MacOS. You can do this either by adding a second SSD, or partitioning your current one. If you just want to experiment though, you should use virtualization, more details on that later.
I have to warn you though, if you are planning to install Linux and be able to do the exact same things you are currently doing on your PC with no friction or frustration, you might be disappointment, as demonstrated by Linus Tech Tips!
I am personally not really a Linux user myself. It is great for programmers and for industrial applications, but personally I find the third party software support isn't really good enough for anything I want to do, that I can't do more easily on Windows or Mac, like creative or financial software. This is why I didn't mention Linux in my Mac post (much to the annoyance of a few snarky commenters), as I wouldn't encourage a non technical person to "Just try linux" if they are using their computer for the web and basic productivity. Anyone who wants to install Linux on an old mac has already done so and doesn't need me to tell them to do it. I don't really code so Linux isn't really for me, but I'd definitely encourage you to try it if you are curious. Each distro tends to have its own small suite of specialized software but a lot of Linux users code their own stuff.
That's my two cents as a non expert. If you want to try it there are loads of youtubers that can walk you through it. Even if you don't end up daily driving it, I'd recommend installing it to try it. If you want to experiment with it without risking partitioning your SSD, I'd recommend trying a virtual machine, where you can install it on a virtual emulated computer without risking your hardware. Here is a video that discusses how to do this, and it also shows off Kali Linux and how to install it, so if you want to know more this would be a good jumping off point. https://www.youtube.com/watch?v=wX75Z-4MEoM
1 note
·
View note
Text
yes it is that easy for usa ppl but not for people in india.
mb for other countries too where the government restricts internet usage, so lemme tell you how to do it
books-epub-wall.vk
movies-piratebay
how do you do this? well see
1. go install oracle virtualbox (so that you can have an environment completely different from your own computer, you can skip steps 1 and 2 if you already have linux, or dont wanna install vms on your computer or wtv, but i do it for safety reasons so that my computer doesn't get affected from malware and linux has more open source applications that you can download for free as compared to windows)
2. get a linux iso from the internet for free because linux is open source (i use kali linux because well it has so many tools pre installed ᵃⁿᵈ ʸᵒᵘ ᶜᵃⁿ ᵃˡˢᵒ ᵘˢᵉ ᵗᵒ ᶦᵗ ᵗᵒ ᶜʳᵃᶜᵏ ʷᶦᶠᶦ ᵖᵃˢˢʷᵒʳᵈˢ ᵒʳ ᵍᵉᵗ ᶦⁿᵗᵒ ʰᵃᶜᵏᶦⁿᵍ) oh also if you wanna learn white hat hacking practice on hackthebox, also mb get into bug bounty hunting because companies pay you so much to find bugs on their websites, and there are so many videos on youtube teaching you how to find bugs and shi, all in all good way to earn money if you have a laptop and internet access, anyways
3. install windscribe vpn (free easy to use, we dont need fancy ass vpns) (if you have windows search up some good vpns for free but honestly like i said windows doesn't have many free options, also you don't need too much internet from the vpn anyways for what we're going to do so don't waste too much money on big ass vpn data plans)
4. switch on vpn and go to sites you want and get magnet links for torrents
5. what i have done is i have bit torrent installed on my actual os (the base os not the virtual one), bit torrent is smthg that you can use from the web and works in india, utorrent doesn't work anymore mostly mb, (imsorry i don't know about other countries, it'll take some trial and error but you can do it!) so copy magnet link from virtual os and paste it to bittorrent (oracle virtualbox allows this, if you have set clipboard sharing to be bidirectional) and voila it will start to download, congratulations you did some pirating and you also have kali linux to do some hacking, now go and earn some money using bug bounty hunting.
tldr: get virtualbox, get a virtual linux, install vpn, get torrent magnet link, install torrent installer on actual os, paste magnet link to torrent installer, start downloading
Other Ways:-
1. if your government controls the information you see and you have brave or tor browser you can go to .onion sites (basically what you call dark web) and read news articles on famous sites which have a .onion counterpart url? but for the love of god dont dive too much into the dark web (deep web) because its a bit dangerous (a lot, especially to younger people who're doing this, don't trust the internet too much and stay cautious), just stick to famous sites, which you can google or duckduckgo the .onion url of.
2. andddddd you can also use google dorks to find movies, search up some good dorks and use them, https://gist.github.com/markstachowski/1202382150e3fb25ece69a1ff9cf5b6e
^^examples
3. also kayoanime gives you drive links to anime, aniwatch.to still works idk for how long
dm me if you have any questions
i don’t understand people who say they don’t pirate movies bc they don’t know how like you literally just google “best movie sites reddit [insert current year]” install an add blocker and that’s it. it’s literally easier to pirate movies than it is to watch them legally bc it takes more effort to sign up for streaming services than it does to look for hosting sites
#sorry i rambled too much#but hope this helps#I've been pirating since i was in like 8th or smng#and this works best since the recent law in india where they control our internet access and websites we can reach#truly dark times
7K notes
·
View notes
Photo

How to activate Windows 10 without any software | Activate Windows 10 without using any software
If you are looking for How to Activate windows 10 without any Software you are at right place. As you most likely are aware, Microsoft told Windows 10 is the last version of Windows and clarified that they will be centered around the advancement of ground-breaking and new highlights under the appearance of programming refreshes as opposed to building another adaptation. This implies there will be no Windows 10.1 or 11 later on. So in the event that you are thinking about an upgrade, this is the best time to get it.
Click below and follow only 5 steps your window will be activated.
https://techohalic.com/how-to-activate-windows-10-without-any-software/
Keywords :-
How to activate windows 10 without any software for free
How to activate win 10 without any software
How to activate windows 10 pro without any software
How to activate win 10 without software
Activate windows 10 without using any software
Activate windows without any software
How to activate windows without software
#How to activate Windows 10 without any software#Activate Windows 10 without using any software#Do Follow websites with high DA#Top 100 do follow websites#Write for us | Article Submission site in India#Free Guest Posting 2020#How to hack/crack WiFi (WPA/WPA2) password#What is Hacking ? Why should we learn it#Installation of Kali Linux on VirtualBox | Kali Linux#Kali Linux on VirtualBox#Fee Guest Posting sites in India | Indian Blogging Sites#Blogging site in India | Top Blogging sites in India
1 note
·
View note
Link
Learn Ethical Hacking From A-Z: Beginner To Expert Course
Learn how to become an elite ethical hacker and easily hack networks, computer systems, web apps and so much more…
What you’ll learn
Learn Ethical Hacking From A-Z: Beginner To Expert Course
How To Become An Elite Ethical Hacker
How To Setup A Hacking Lab
Learn How To Launch Attacks/Exploits Against Computers
How To Start A Cybersecurity/Ethical Hacking Career
How To Hack Into Wireless Networks
Learn How To Conduct Penetration Tests
How To Bypass Antivirus
The Fundamentals of Networking
How To Remain Anonymous On The Internet
The Fundamentals of Linux
The Fundamentals of Bash
How To Gather Website & App Data
The Fundamentals of Python
Maintaining Access To Exploited Computers
Website & Web Application Hacking
Mobile Phone Security Tips
Where You Can Practice Hacking For Free
Conducting Passive & Active Reconnaissance On A Network
Requirements
Basic IT/Computer Skills & Knowledge
Computer With At Least 8GB of RAM/Memory (Less is ok, but your computer may run slow!)
Wifi Hacking Section Only: USB Wireless Adapter (Link Provided In Course Resources)
You Do Not Need Any Prior Experience In Hacking Or Cybersecurity To Go Through This Course
Description
Welcome to – Learn Ethical Hacking From A-Z: Beginner To Expert Course! This practical, hands-on course was created for newbies – that’s to say, people with no prior training or knowledge in hacking and cybersecurity. The aim of this course is to give you the education not just to understand what black-hat hatters do and how, but also to learn exactly how to hack systems like a pro and win the cat and mouse game by securing systems like a professional security expert. Blending practical work with solid theoretical training, we take you from the basics of ethical hacking through to mastery, giving you the training you need not just to hack, but also to secure against a hack. While the theory is important, we understand that it can also be dry and uninspiring. For this reason, this course is packed with examples that you can follow. This practical focus starts from the beginning, where we will teach you about penetration testing and show you how to install the software required (Windows, Linux, and Mac OSX) and jump right into hacking. Throughout, you will analyze and exploit various systems from regular websites through to sprawling networks, along with hacking servers and clients. More than just hacking, you’ll also learn how to conduct efficient penetration testing techniques. This approach gives you the foundational education that you need not just to hack any given system, but also to secure it, with each module covering both sides of the coin. The course covers six main areas:
1: LEARN THE FUNDAMENTALS NECESSARY TO BECOME A HACKER
This foundational section gives you a full introduction to the basics of networking systems – how they communicate and work – and is designed to give you the knowledge you need to succeed in this course. BASICS OF NETWORKING: Networking can be an intimidating topic, but don’t worry! We break down only the necessary things that you need to know in regards to networking and teach you important networking fundamentals SETTING UP A HACKING LAB: You can’t hack without a lab! We walk you step-by-step through the process of setting up your own hacking lab on your laptop or desktop computer! LINUX + SCRIPTING BASICS: Hackers use Linux, which is an OS that the average person may have no experience with. We will go over Linux fundamentals so that you can easily navigate your way through Linux during this course. We also touch on a couple of scripting languages that are a MUST for any ethical hacker and teach you the basics of each one with practical examples. HIDING YOUR IDENTITY ON THE WEB: If you are hacking on the internet, you need to learn how to remain anonymous. We will show you the tools and techniques that you can use to always remain anonymous and unknown on the internet.
2: LEARN HOW TO HACK NETWORKS
This section shows you how to test both wired and wireless systems. You will learn how to go from not having any access to a network to gaining access and being able to begin attacking systems on the network. PRE-CONNECTION ATTACK: Not all attacks require you to be connected to the target or even know the password. Learn how to discover and manipulate devices connected to a network and gather information about your target. GAIN ACCESS TO NETWORKS: Learn how to use the information you have about your target to crack the key and get the access password. This section covers multiple protocols including WEP, WPA, and WPA2. POST-CONNECTION ATTACKS: With a key, you can now leverage powerful hacking techniques to get even more information. Learn how to see what users are doing on a network, inject code in pages, and more on wired and wireless networks
3: HOW TO GAIN ACCESS AND CONNECT TO NETWORKS
This section builds on the lessons learned in section one, showing you how you can get full control and hack into any computer system that you target. SERVER-SIDE ATTACK: Discover how to harvest information about your targeted system – its OS, open ports, and installed services – without user interaction. Then use this information to exploit vulnerabilities and generate reports. CLIENT-SIDE ATTACK: Learn how to hack systems with no vulnerabilities by sneaking in with software updates or using backdoor trojan downloads. You’ll also learn the art of social engineering – or tricking people into giving you information.
4: HOW TO LEVERAGE POST EXPLOITATION
This section shifts the focus on interacting with compromised systems. Now that you have gained access, you’ll learn how you can exploit these systems. ACCESS FILE SYSTEMS: All systems have a wealth of files that you can now manipulate with your access. Learn how to access these systems and how to read, write, upload, and even execute files. MAINTAIN ACCESS: Gaining access to a system and its files is only half of the battle. Learn how to maintain your access and frustrate efforts to secure it again so you can continue to exploit a system. SPY ON YOUR TARGET: Learn how to capture any keystrokes on a keyboard, turn on a computer webcam, take screenshots, and even take control of the system to attack, hack, and access third-party networks and systems.
5: HOW TO HACK WEBSITES AND WEB APPS
In this section, you will learn more about how you can hack into websites and web applications using Kali Linux. You’ll also learn how web applications work – and how to find vulnerabilities within these applications for you to exploit. > How to scan websites/web applications for vulnerabilities to exploit. > How to Brute Force into web applications. > Learn how to conduct SQL injection in web applications. > How to conduct Cross-Site Request Forgery (CSRF). > How to exploit File Inclusion Vulnerabilities. > Learn how to exploit File Upload Vulnerabilities. > How to automate attacking web applications using various tools. > How to prevent and secure websites & apps yourself.
6: HOW TO MAKE MONEY, LAND A JOB & BUILD A BRAND AS A HACKER
In this section, you will learn how you can make money as an ethical hacker using a variety of methods. You’ll also learn how to build your personal brand and get your name out there as an Ethical Hacker so you can have employers and clients knocking at your door ready to hire you for your services. Then finally, you’ll learn how you can start a career in cybersecurity with some insider tips on what certifications to get and the best way to land a job. This includes: > How to build an ethical hacker personal brand from scratch > How to get instant credibility and authority as a hacker > Learn how to properly network and get others talking about you > How to make money using a variety of websites > How to get started freelancing as a hacker > Learn how to get started consulting as a hacker > How to land a job as a cybersecurity professional This course is comprehensive, showing you both sides of hacking. You will learn to think and operate like a hacker – and how to apply that knowledge as a cybersecurity expert to protect you and your clients’ networks and systems. In taking this ‘cat and mouse approach, your rounded understanding will give your approach new depths and angles, revealing the paths you can take to effectively neutralize any threat. Together with the emphasis on practical examples that you can follow in real life with live systems, you will also benefit from the excitement of hands-on learning. By experiencing precisely what it takes to hack into any given target system, you’ll also learn that no one system is the same and that all approaches can be modified. This real-life learning is an invaluable part of your education, enabling you to better see what hackers are doing and how to block even the most potent attacks. No matter what the scenario or how complicated a hacking situation, this course gives you the foundational training you need to secure a network – and start pursuing a career in a field that is increasingly in demand as the global reliance on technology grows.
Download
To download more paid course for free visit free course site where you find 1100+ paid courses for free. You can easily access those courses with just a single click.
23 notes
·
View notes
Text
Creating Kali Virtual Machine: VMware
This is a guide on how to create a Kali Linux virtual machine using VMware. Kali Linux is a ‘distribution’ (or version) of Linux which comes preloaded with many tools useful for hacking/penetration testing.
The first step is to download VMware Workstation Player. This can be found here.
Once you have downloaded VMware, you will need a Kali ‘image’, which is a file containing the operating system. You can download one for VMware here. make sure you get the right one for your windows architecture (You can find if you use 32- or 64-bit windows here). It should download as a .zip file, so you will have to unzip it. After opening the folders, you should have files looking like the following:
When you open VMware Workstation Player it should look like this:
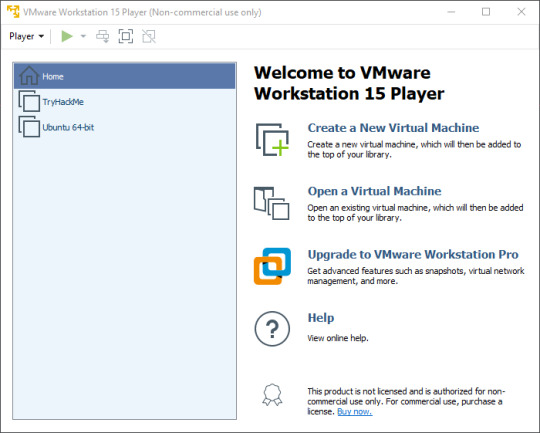
Here I already have some VMs installed, so on your version it should be missing TryHackMe and Ubuntu (Note: TryHackMe is a website for practicing hacking, it is not an invitation to hack me). Next we’re going to click ‘Open a Virtual Machine’ and navigate to the folders we unzipped earlier. You should only see one file:
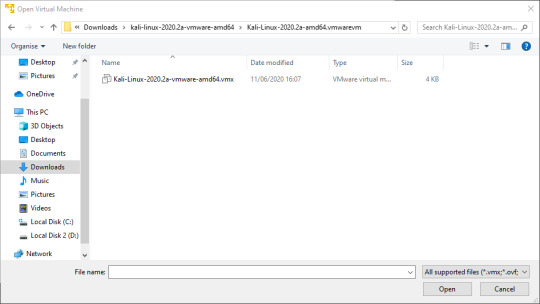
Double click that file to open the Kali VM. You should see the new VM on the home screen of Workstation Player.

You can right click on that VM to rename it, or to change the settings. Let’s change the settings.
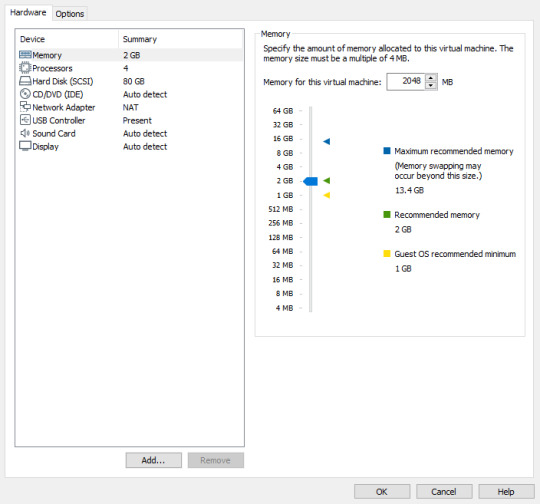
Let’s leave the memory at the recommended amount (This may vary depending on your computer). I normally change the Network Adapter to ‘Bridged’ but you can play around and see what fits you better. We are also going to leave every other setting at the default.

Now click ‘OK’ to go back to the home screen, and then click ‘Play virtual machine’ to start your Kali machine.
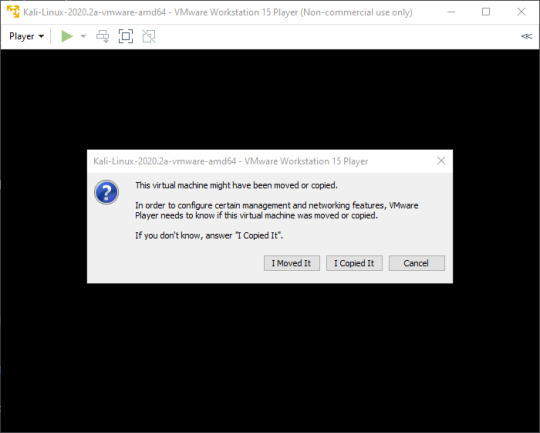
If you see this screen, just click ‘I Copied It’.
After some loading screens you should see a login page.

(Depending on the version of Kali installed, it may look slightly different)
The default login credentials should be ‘kali’/’kali’, but if this doesn’t work you should look on the Kali site to see if they have changed. You should now see a screen like this:
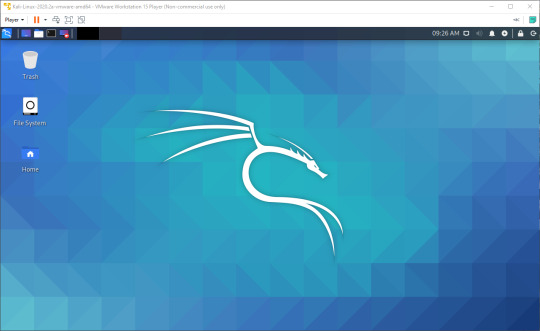
Congratulations! You have now deployed a virtual machine. You can find a post explaining how to secure your new VM against being hacked here
6 notes
·
View notes
Text
How to Hack Windows/Mac/Linux using PasteJacking (PasteZort) and Kali Linux 2017.1
How to Hack Windows/Mac/Linux using PasteJacking (PasteZort) and Kali Linux 2017.1
Hey Guys, In this video i show you how to use PasteJacking to hack any operating system using PasteZort and Kali Linux 2017.1.
PasteZort: https://github.com/ZettaHack/PasteZort
Installation and Usage: git clone https://github.com/ZettaHack/PasteZort.git cd PasteZort && ls chmod +x PasteZ0rt.py encode.rb ./PasteZort.py
What is Pastejacking? Nearly all browsers allow websites to run commands on the…
View On WordPress
#hack linux#hack pc over wan#hack pc using kali linux#Hack Windows#hack with kali linux#how to hack any pc#How to Hack Windows#how to hack windows 10#how to hack windows 10 using kali linux#how to hack windows pc#how to hack windows using kali linux#how to hack windows using pastejacking#How to Hack Windows/Mac/Linux#kali#kali linux hacking tutorials#PasteJacking#pastejacking kali linux#PasteZort#pentesttools#remote acces pc#remote hack windows pc#undetectable backdoor#What is pastejacking
0 notes
Video
Brave is the safest, fastest web browser ever created
Download and earn money with brave browser : https://brave.com/yku031
How to use it :
1 - click in the link above
2- download the browser and signup
3- open the browser and use it for 30 days ( surff in the first day at least 10 mn)
4- in the day 31/32/33 surff on the browser for 5 mn at least for every day
5- Get your rewards
6- get your share link after day 33 and share it with your friends brave browser
brave browser rewards brave browser android brave browser payment proof live brave browser 2019 brave browser bat brave browser ads brave browser hack brave browser update brave browser review brave browser account brave browser app brave browser android review brave browser adobe flash brave browser airdrop brave browser adblock brave browser ad blocker brave browser bd brave browser beta brave browser bitcoin brave browser bat rewards brave browser bat wallet brave browser bookmarks brave browser bat coin brave browser coinbase brave browser creator brave browser crypto brave browser channel brave browser chromebook brave browser comparison brave browser chromium brave browser commercial brave browser coin brave browser dark theme brave browser dark web brave browser demo brave browser dev brave browser download video brave browser desktop brave browser earning bangla brave browser explained brave browser earn money brave browser earn bat brave browser extensions brave browser for android brave browser features brave browser for iphone brave browser for pc brave browser fast adblocker brave browser get bat brave browser get paid brave browser guide brave browser good brave browser games brave browser how to use brave browser how to earn bat brave browser hindi brave browser how to earn money brave browser how to brave browser history brave browser how to get bat brave browser review hindi brave browser income brave browser in hindi brave browser in tamil brave browser intro brave browser ipad brave browser in urdu brave browser install brave browser kya hai install brave browser kali linux brave vs kiwi browser brave browser para kazanma brave browser linux brave browser live payment proof brave browser login brave browser legit brave browser lastpass brave browser money brave browser mac brave browser not installing brave browser not launching brave browser nvidia shield brave browser on android brave browser on chromebook brave browser official brave browser overview brave browser on mac brave browser on ios brave browser on windows brave browser privacy brave browser payment proof brave browser promo brave browser performance brave browser phone brave browser payment proof hindi brave browser pc review brave browser para que sirve brave browser referral brave browser review bangla brave browser referral program brave browser reviews 2019 brave browser ram usage brave browser rewards android brave browser setup brave browser security brave browser speed brave browser safe brave browser slow brave browser se paise kaise kamaye brave browser speed test brave browser tips brave browser trailer brave browser token brave browser the verge brave browser themes brave browser test brave browser tips and tricks brave browser tamil brave browser thiojoe brave browser ubuntu brave browser use brave browser unlimited trick brave browser uphold connect brave browser uninstall brave browser ubuntu 18.04 brave browser ubuntu install brave browser urdu brave browser vs brave browser vpn brave browser vs tor brave browser vs chrome speed brave browser vs vivaldi brave browser vs opera brave browser video brave browser withdraw brave browser wallet brave browser with tor brave browser windows brave browser withdraw bangla brave browser withdraw bat bangla brave browser windows 7 brave browser windows 10 brave browser white paper brave browser xda brave browser youtube brave browser youtube ads brave browser youtube background ios brave browser 2019 review brave web browser review 2019 brave browser earn money brave browser 5$
1 note
·
View note
Text
Kali Linux on VirtualBox | Installation of Kali Linux on VirtualBox | Kali Linux
In this tutorial you will learn how to install Kali Linux on Virtual Box.
Kali Linux is one of the best Linux distributions for hacking and security enthusiasts.
You can also install Kali Linux by replacing the existing operating system, but using it via a virtual machine would be a better and safer option.
With Virtual Box, you can use Kali Linux as a regular application in your Windows/Linux system. It’s almost the same as running an application or game in your system.
Using Kali Linux in a virtual machine is safe. Whatever you do inside Kali Linux will not impact your host system. Your actual operating system will not be affected and your data in the host system will be safe.
Steps to install Kali Linux on VirtualBox:
1. Download and install VirtualBox
2. Download ready-to-use virtual image of Kali Linux
3. Install Kali Linux on Virtual Box
For more click :- https://techohalic.com/installing-kali-linux-on-virtualbox/
2 notes
·
View notes
Text
How to Crack a Password
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 What is Password Cracking? Password cracking is. m › how-to-crack-password-of-an-application. How strong are your passwords? Test how secure they are using the My1Login Password Strength Test. 0 characters containing: Time to crack your password. Verdict: Password Cracker is a great tool for restoring lost passwords. It can help recover hidden passwords of most Windows applications. In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that has been stored in or transmitted by a. What is password cracking? Hashcat · 2. John the Ripper · 3. Brutus · 4. THC Hydra · 6. Medusa · 7. RainbowCrack · 8. Password cracking means recovering passwords from a computer or from data that a computer transmits. This doesn't have to be a sophisticated. While this tools identifies many of the most common passwords, it cannot account for for all passwords and the wide range of tools hackers can use to crack. Password cracking (also called, password hacking) is an attack vector that involves hackers attempting to crack or determine a password. Password cracking is the process of using an application program to identify an unknown or forgotten password to a computer or network resource. It is important to choose passwords wisely. Check how strong and secure is your password. Improve the strength of your password to stay safe. It's worth taking into account the role of a leaked password in one of the biggest cyber security stories of the last two years, the SolarWinds hack. Advances in graphics processing technology have slashed the time needed to crack a password using brute force techniques, says Hive Systems. Check how secure your password is using our free online tool. How long would it take a supercomputer to crack your password? World's fastest password cracker; World's first and only in-kernel rule engine; Free; Open-Source (MIT License); Multi-OS (Linux, Windows and macOS). A proof-of-concept cracker for cryptocurrency brainwallets and other low entropy BitCracker is the first open source password cracking tool for memory. Password recovery and password crack software: for archives (ZIP, RAR, ARJ, ACE), Microsoft Office (Word, Excel, Access, Outlook), Lotus SmartSuite (WordPro. In this chapter, we will learn about the important password cracking tools used in Kali Linux. Hydra is a login cracker that supports many protocols.
10 most popular password cracking tools [updated ] - Infosec Resources
Password Strength Test & Strong Password Generator Tool
Password cracking - Wikipedia
Password Strength Meter
Password Cracking Attacks & Defenses Explained | BeyondTrust
How to Crack a Password
Kali Linux - Password Cracking Tools
hashcat - advanced password recovery
How an 8-character password could be cracked in less than an hour | TechRepublic
Password Check | Kaspersky
How Secure Is My Password? | Password Strength Checker
1 note
·
View note
Text
How Secure Is My Password? | Password Strength Checker
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 What is Password Cracking? Password cracking is. m › how-to-crack-password-of-an-application. How strong are your passwords? Test how secure they are using the My1Login Password Strength Test. 0 characters containing: Time to crack your password. Verdict: Password Cracker is a great tool for restoring lost passwords. It can help recover hidden passwords of most Windows applications. In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that has been stored in or transmitted by a. What is password cracking? Hashcat · 2. John the Ripper · 3. Brutus · 4. THC Hydra · 6. Medusa · 7. RainbowCrack · 8. Password cracking means recovering passwords from a computer or from data that a computer transmits. This doesn't have to be a sophisticated. While this tools identifies many of the most common passwords, it cannot account for for all passwords and the wide range of tools hackers can use to crack. Password cracking (also called, password hacking) is an attack vector that involves hackers attempting to crack or determine a password. Password cracking is the process of using an application program to identify an unknown or forgotten password to a computer or network resource. It is important to choose passwords wisely. Check how strong and secure is your password. Improve the strength of your password to stay safe. It's worth taking into account the role of a leaked password in one of the biggest cyber security stories of the last two years, the SolarWinds hack. Advances in graphics processing technology have slashed the time needed to crack a password using brute force techniques, says Hive Systems. Check how secure your password is using our free online tool. How long would it take a supercomputer to crack your password? World's fastest password cracker; World's first and only in-kernel rule engine; Free; Open-Source (MIT License); Multi-OS (Linux, Windows and macOS). A proof-of-concept cracker for cryptocurrency brainwallets and other low entropy BitCracker is the first open source password cracking tool for memory. Password recovery and password crack software: for archives (ZIP, RAR, ARJ, ACE), Microsoft Office (Word, Excel, Access, Outlook), Lotus SmartSuite (WordPro. In this chapter, we will learn about the important password cracking tools used in Kali Linux. Hydra is a login cracker that supports many protocols.
10 most popular password cracking tools [updated ] - Infosec Resources
Password Strength Test & Strong Password Generator Tool
Password cracking - Wikipedia
Password Strength Meter
Password Cracking Attacks & Defenses Explained | BeyondTrust
How to Crack a Password
Kali Linux - Password Cracking Tools
hashcat - advanced password recovery
How an 8-character password could be cracked in less than an hour | TechRepublic
Password Check | Kaspersky
How Secure Is My Password? | Password Strength Checker
1 note
·
View note
Text
How to Crack a Password
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥
What is Password Cracking? Password cracking is. m › how-to-crack-password-of-an-application. How strong are your passwords? Test how secure they are using the My1Login Password Strength Test. 0 characters containing: Time to crack your password. Verdict: Password Cracker is a great tool for restoring lost passwords. It can help recover hidden passwords of most Windows applications. In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that has been stored in or transmitted by a. What is password cracking? Hashcat · 2. John the Ripper · 3. Brutus · 4. THC Hydra · 6. Medusa · 7. RainbowCrack · 8. Password cracking means recovering passwords from a computer or from data that a computer transmits. This doesn't have to be a sophisticated. While this tools identifies many of the most common passwords, it cannot account for for all passwords and the wide range of tools hackers can use to crack. Password cracking (also called, password hacking) is an attack vector that involves hackers attempting to crack or determine a password. Password cracking is the process of using an application program to identify an unknown or forgotten password to a computer or network resource. It is important to choose passwords wisely. Check how strong and secure is your password. Improve the strength of your password to stay safe. It's worth taking into account the role of a leaked password in one of the biggest cyber security stories of the last two years, the SolarWinds hack. Advances in graphics processing technology have slashed the time needed to crack a password using brute force techniques, says Hive Systems. Check how secure your password is using our free online tool. How long would it take a supercomputer to crack your password? World's fastest password cracker; World's first and only in-kernel rule engine; Free; Open-Source (MIT License); Multi-OS (Linux, Windows and macOS). A proof-of-concept cracker for cryptocurrency brainwallets and other low entropy BitCracker is the first open source password cracking tool for memory. Password recovery and password crack software: for archives (ZIP, RAR, ARJ, ACE), Microsoft Office (Word, Excel, Access, Outlook), Lotus SmartSuite (WordPro. In this chapter, we will learn about the important password cracking tools used in Kali Linux. Hydra is a login cracker that supports many protocols.
10 most popular password cracking tools [updated ] - Infosec Resources
Password Strength Test & Strong Password Generator Tool
Password cracking - Wikipedia
Password Strength Meter
Password Cracking Attacks & Defenses Explained | BeyondTrust
How to Crack a Password
Kali Linux - Password Cracking Tools
hashcat - advanced password recovery
How an 8-character password could be cracked in less than an hour | TechRepublic
Password Check | Kaspersky
How Secure Is My Password? | Password Strength Checker
1 note
·
View note
Text
How an 8-character password could be cracked in less than an hour | TechRepublic
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 What is Password Cracking? Password cracking is. m › how-to-crack-password-of-an-application. How strong are your passwords? Test how secure they are using the My1Login Password Strength Test. 0 characters containing: Time to crack your password. Verdict: Password Cracker is a great tool for restoring lost passwords. It can help recover hidden passwords of most Windows applications. In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that has been stored in or transmitted by a. What is password cracking? Hashcat · 2. John the Ripper · 3. Brutus · 4. THC Hydra · 6. Medusa · 7. RainbowCrack · 8. Password cracking means recovering passwords from a computer or from data that a computer transmits. This doesn't have to be a sophisticated. While this tools identifies many of the most common passwords, it cannot account for for all passwords and the wide range of tools hackers can use to crack. Password cracking (also called, password hacking) is an attack vector that involves hackers attempting to crack or determine a password. Password cracking is the process of using an application program to identify an unknown or forgotten password to a computer or network resource. It is important to choose passwords wisely. Check how strong and secure is your password. Improve the strength of your password to stay safe. It's worth taking into account the role of a leaked password in one of the biggest cyber security stories of the last two years, the SolarWinds hack. Advances in graphics processing technology have slashed the time needed to crack a password using brute force techniques, says Hive Systems. Check how secure your password is using our free online tool. How long would it take a supercomputer to crack your password? World's fastest password cracker; World's first and only in-kernel rule engine; Free; Open-Source (MIT License); Multi-OS (Linux, Windows and macOS). A proof-of-concept cracker for cryptocurrency brainwallets and other low entropy BitCracker is the first open source password cracking tool for memory. Password recovery and password crack software: for archives (ZIP, RAR, ARJ, ACE), Microsoft Office (Word, Excel, Access, Outlook), Lotus SmartSuite (WordPro. In this chapter, we will learn about the important password cracking tools used in Kali Linux. Hydra is a login cracker that supports many protocols.
10 most popular password cracking tools [updated ] - Infosec Resources
Password Strength Test & Strong Password Generator Tool
Password cracking - Wikipedia
Password Strength Meter
Password Cracking Attacks & Defenses Explained | BeyondTrust
How to Crack a Password
Kali Linux - Password Cracking Tools
hashcat - advanced password recovery
How an 8-character password could be cracked in less than an hour | TechRepublic
Password Check | Kaspersky
How Secure Is My Password? | Password Strength Checker
1 note
·
View note