#how to secure your website
Explore tagged Tumblr posts
Text
Tearing my hair out a little after things that have occurred over the last few days so this is a PSA for US citizens who want to renew their passports.
If you want to do it by mail, the forms are completely free on travel.state.gov. If you want to renew your passport online, the official department of state website to do so is mytravel.state.gov. These are legitimate and secure sites made by the US Department of State, every United States .gov domain has to go through federal approval in order to go online. At the moment online passport renewal is still in beta so you can't get it expedited that way, but the only things it can charge you for is the standard $130 for a passport book, $30 for a passport card, $160 for both, and an optional $21.36 for 1-2 day shipping.
Any other site that charges you money for United States passport renewal that isn't registered to a .gov domain is a third party site. At best they will mark up the price for your application so they can take a cut, at worst they will take your personal information and run. If you or someone you know has been a victim of passport or visa fraud, you can go to dsscrimetips.state.gov and report the incident.
This is not me trying to be a fed or a cop or a bootlicker to the department of state, this is me trying to save people time and money and anguish over potentially getting scammed out of their PII. There are a lot of people out there banking on people searching 'online passport renewal' and clicking on whatever link comes up without doing any further research and without looking it up you can't know which are real or which will charge you $200 and not tell you that none of that money will go to your passport fees or which will take your personal and financial info and leave you SOL and if you can save yourself the hassle of dealing with that by just knowing what the ACTUAL, REAL OFFICIAL CHANNELS are then all the better. That's it thank you ✌️
#spitblaze says things#nothing happened to me personally thank god#but like. hooooooo boy can it get bad if you blindly give your personal information to any website that says 'yeah you can trust us'#(when i say 'secure' i mean like. relatively speaking)#(idk how secure they REALLY are but they're almost definitely better than govplus or whatever. the DoS are sticklers by trade)
47 notes
·
View notes
Text
DM me for donations or use my askbox to request donations and I'm blocking you immediately, I have no 100% credible way of knowing whether you're a real, actual person or not at this point and being "vetted" doesn't even mean anything anymore because some fraudsters/scammers have managed to get themselves "vetted" in the past.
It sucks that bad people are trying to take advantage of innocent peoples's suffering by pretending to be victims of the war in Gaza when they aren't, but the existence of these scammers is an unfortunate reality and they've made it singlehandedly impossible to know whether I'm actually helping war victims with my money or simply funding a fraud operation by donating to anyone.
I am creating this post for the benefit of those select few Gazan Tumblr accounts which are legitimate, because if they've put effort into messaging me then I want them to know why I keep ignoring all messages related to donation requests.
PLEASE seek help from a known and properly funded charity organization instead of wasting valuable time and energy here, and please do so on a more secure website. Tumblr was never a good place to look for donations in the first place due to its high crime rate (we have so many scammers and bots, it's not even funny).
Q&A and FAQ:
Having a GoFundMe doesn't mean much and does nothing to prove legitimacy on it's own, several GoFundMes have been shut down in the past due to them being run by fraudsters. The fraudsters are BAD, guys. They really suck.
No, I do not run any charity campaigns myself, I've been DMed by someone asking about that in the past.
#I'm not tagging this as anything related to “Gaza” because that will just attract the bots.#I'm pinning it to the top of my account so that real actual humans can see it on the off chance that they have come across my blog.#UPDATE in light of the DM that I received this morning ---->#If you use my DMs to ask for donations I'm going to respond by sending you the link to this post and THEN blocking you.#I would like to reiterate that of you are a genuine victim of the war in Gaza it is in your best interests to seek help elsewhere.#Find a REPUTABLE charity on a SECURE WEBSITE and message THEM!!!#I cannot over emphasize how ineffective trying to seek help on Tumblr is amidst the throng of bots and dirtbag scam artists.#I can't trust anything I see on here because of the scammers and real victims are wasting valuable energy by trying to campaign on Tumblr.
12 notes
·
View notes
Text
brother watches youtube shorts on the living room tv and it comes from inside by the living tombstone seems to be one of the trendy youtube shorts songs ? and every time i hear it my fnaf phase twitches from its place buried deep in the back of my mind . i feel like watching a matpat video
#not gonna lie. maybe im just stupid ( i have never played the fnaf games that might be part of it too) but i kind of agree w his theories#i knowww people clowned on him for the gregory robot thing but he made a good point man i dunno. who am i to argue#so humiliating remembering gregory bc one time i listened to that fucking. superstar cg5 song for like 5 hours straight i wish i was joking#well done suuperrstaaar!! its my grand desiiiiign !!!! urgh#watched that music video like there was no tomorrow. gave me chills. probably still would honestly. gonna go listen#what was i on when i was sixteen (<- internally throwing up at whats ur choice!! in the end !!! Ill allways be your friendn!!!!!)#going nuts ok this slaps. bitches when fnaf security breach Freddy and Gregory#aaanyways. how to stop oversharing in tags. it is my greatest weakness. every website should have something like it
3 notes
·
View notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
What are the next steps after obtaining an insurance broker license, and how can you generate potential leads using Mzapp CRM software?
Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful insurance brokerage. Here’s how you can proceed and leverage Mzapp CRM software to find potential leads:
Steps After Getting Your Insurance Broker License
Understand Your Market: Research your target audience (individuals, businesses, or specific sectors).
Develop a Business Plan: Set goals for client acquisition, revenue, and operational processes.
Build a Network: Partner with insurance providers and attend industry events to establish your presence.
Create an Online Presence: Build a professional website and maintain active profiles on social platforms.
Offer Value-Added Services: Educate customers on policies, claims management, and risk assessments.
Using Mzapp CRM Software to Generate Leads
Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.
Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.
Lead Scoring: Prioritize leads based on their interaction history, ensuring you focus on high-potential prospects.
Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.
Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.
Why Choose Mzapp CRM?
Mzapp CRM simplifies lead management, streamlines operations, and provides insights into customer behavior, making it easier to convert prospects into loyal clients.
Learn more about how Mzapp can transform your insurance business here.
#Question:#What are the next steps after obtaining an insurance broker license#and how can you generate potential leads using Mzapp CRM software?#Answer:#Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful i#Steps After Getting Your Insurance Broker License#Understand Your Market: Research your target audience (individuals#businesses#or specific sectors).#Develop a Business Plan: Set goals for client acquisition#revenue#and operational processes.#Build a Network: Partner with insurance providers and attend industry events to establish your presence.#Create an Online Presence: Build a professional website and maintain active profiles on social platforms.#Offer Value-Added Services: Educate customers on policies#claims management#and risk assessments.#Using Mzapp CRM Software to Generate Leads#Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.#Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.#Lead Scoring: Prioritize leads based on their interaction history#ensuring you focus on high-potential prospects.#Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.#Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.#Why Choose Mzapp CRM?#Mzapp CRM simplifies lead management#streamlines operations#and provides insights into customer behavior#making it easier to convert prospects into loyal clients.#Learn more about how Mzapp can transform your insurance business here.
1 note
·
View note
Text
Meanwhile, as an IT person, I routinely have to tell people, "Look, if I wanted to know your password, I would just change it myself. I can log in as you if I want to without your help. DO NOT TELL ME YOUR PASSWORD."
It works like 75% of the time.
My personal favorite was when someone called and left me a voicemail with their password "just in case I needed it." I did not need it, but I did get to call them back and say, "that's not your password anymore. You will be prompted to enter a new one the next time you try to log in."
Need to deploy some sort of mandatory seminar to IT people, "How to make your security upgrade instructions not look like a phishing email"
#look I'm cool about a lot of security things#you wanna get to websites the company has blocked - sure I can tell you how to do that#if you call me at the help desk because you can't get images on craigslist to load? I don't care that you shouldn't be doing that at work#but if you're telling me your password that's something that I just can't let slide
19K notes
·
View notes
Text

I've seen a number of people worried and concerned about this language on Ao3s current "agree to these terms of service" page. The short version is:
Don't worry. This isn't anything bad. Checking that box just means you forgive them for being US American.
Long version: This text makes perfect sense if you're familiar with the issues around GDPR and in particular the uncertainty about Privacy Shield and SCCs after Schrems II. But I suspect most people aren't, so let's get into it, with the caveat that this is a Eurocentric (and in particular EU centric) view of this.
The basic outline is that Europeans in the EU have a right to privacy under the EU's General Data Protection Regulation (GDPR), an EU directive (let's simplify things and call it an EU law) that regulates how various entities, including companies and the government, may acquire, store and process data about you.
The list of what counts as data about you is enormous. It includes things like your name and birthday, but also your email address, your computers IP address, user names, whatever. If an advertiser could want it, it's on the list.
The general rule is that they can't, unless you give explicit permission, or it's for one of a number of enumerated reasons (not all of which are as clear as would be desirable, but that's another topic). You have a right to request a copy of the data, you have a right to force them to delete their data and so on. It's not quite on the level of constitutional rights, but it is a pretty big deal.
In contrast, the US, home of most of the world's internet companies, has no such right at a federal level. If someone has your data, it is fundamentally theirs. American police, FBI, CIA and so on also have far more rights to request your data than the ones in Europe.
So how can an American website provide services to persons in the EU? Well… Honestly, there's an argument to be made that they can't.
US websites can promise in their terms and conditions that they will keep your data as safe as a European site would. In fact, they have to, unless they start specifically excluding Europeans. The EU even provides Standard Contract Clauses (SCCs) that they can use for this.
However, e.g. Facebook's T&Cs can't bind the US government. Facebook can't promise that it'll keep your data as secure as it is in the EU even if they wanted to (which they absolutely don't), because the US government can get to it easily, and EU citizens can't even sue the US government over it.
Despite the importance that US companies have in Europe, this is not a theoretical concern at all. There have been two successive international agreements between the US and the EU about this, and both were struck down by the EU court as being in violation of EU law, in the Schrems I and Schrems II decisions (named after Max Schrems, an Austrian privacy activist who sued in both cases).
A third international agreement is currently being prepared, and in the meantime the previous agreement (known as "Privacy Shield") remains tentatively in place. The problem is that the US government does not want to offer EU citizens equivalent protection as they have under EU law; they don't even want to offer US citizens these protections. They just love spying on foreigners too much. The previous agreements tried to hide that under flowery language, but couldn't actually solve it. It's unclear and in my opinion unlikely that they'll manage to get a version that survives judicial review this time. Max Schrems is waiting.
So what is a site like Ao3 to do? They're arguably not part of the problem, Max Schrems keeps suing Meta, not the OTW, but they are subject to the rules because they process stuff like your email address.
Their solution is this checkbox. You agree that they can process your data even though they're in the US, and they can't guarantee you that the US government won't spy on you in ways that would be illegal for the government of e.g. Belgium. Is that legal under EU law? …probably as legal as fan fiction in general, I suppose, which is to say let's hope nobody sues to try and find out.
But what's important is that nothing changed, just the language. Ao3 has always stored your user name and email address on servers in the US, subject to whatever the FBI, CIA, NSA and FRA may want to do it. They're just making it more clear now.
10K notes
·
View notes
Text
Networking/Knowing A Guy: A Guide
This is the autism website. Now, as an extension of the power of love and friendship, there are few things more useful than Knowing A Guy. Knowing A Guy means you have a support network. Knowing a plumber, or a tax accountant, or just that one dude that's really fucking good at finding the information you need when you're really overwhelmed, can be the difference between being able to pay rent and having a fun party with friends to fix your shit.
How does one end up Knowing A Guy? It's a skill you can develop called Networking and it is one of the foundations of society. Unfortunately making those connections with people is fucking hard and nobody makes a tutorial for it. So, here you go:
The golden rule is you scratch my back and I scratch yours
It is necessary for survival to seek out useful people
Great news! Everyone is useful in some form or fashion - including you! When given the opportunity to learn about someone, do it! Extroversion does not come naturally to some people and that's okay. Just take whatever falls in your lap.
Types of usefulness: trade skills, connections of their own, personality you jive with, pleasant to talk to, niche interest in shared hobby, security - the list is pretty much endless. I know a guy that lives in the metro area - no job, no major hobbies, inoffensively annoying to me personally, kinda ignorant, not attractive to me, but you know what? He knows how the fuck to get around the city by foot. My rural-raised ass APPRECIATES the guide.
Remember important information: general personality, background, skillset, likes and dislikes. You can find this information by making smalltalk about their life. There is no such thing as pointless conversation. (Yes, even the annoying smalltalk)
The more people you know, the higher the likelihood that one of them will be useful in a given situation - or will know someone who is.
It is overwhelming. In a given clique/community/workspace/whatever, there is A Guy Who Knows The Other Guys. This Guy is a shortcut. Find them. They're often elderly, extroverted, a little bit annoying, a secretary or in some otherwise forward-facing position. Look for people that are gossipy/talk about other people a lot but not in negative ways. If they constantly talk shit, they'll talk shit about you too. They're still useful but be careful with the information you share
You do not have to like someone for them to be useful.
You do not have to like someone for them to be useful.*
If you have low self esteem, you're going to feel like you're using people. You're not. That's the devil talking. People like feeling valued and the connections you are making are the threads holding community together. Recognize people for their talents. It's only a problem when you're taking advantage of people
So: don't feel scummy about it. You're an animal. You have to claw out your right to survive and people will respect you more for it.
Luckily mutualism is the name of the game in the animal kingdom. Offer something back. The foundation of a Know A Guy relationship is Mutual Benefit
Sometimes that Mutual Benefit is just spreading news of the The Guy far and wide. My plumber friend is my actual friend and I love her to death, but I'm maintaining our backscratch relationship by pimping out her plumbing business to anyone that'll listen
Food is a good Mutual Benefit. People across cultures for all of human history have bonded over food. I have good success asking people for a favor and then offering to buy them lunch in return **
General compensation is also good. Offer a service in return and always do your best to offer financial compensation as appropriate. Having your plumber friend take a look at your drain: doable with a case of beer. Having your plumber friend redo the pipes in your entire house? You need to pay for that.
Being transactional is not necessarily a bad thing. I would advise against keeping an itemized list of things owed, but fish don't seek out cleaner shrimp just because they enjoy their company. Everyone gets something
Unfortunately being extroverted and generally personable is a huge benefit here, but that's the value of the Guy That Knows A Guy. There's someone out there that has consolidated All The Guys so you don't have to be the local expert. Always remember nobody can do everything and you don't need to master every skill
* This is the foundation of a functioning community. I have many acquaintances that I find incredibly annoying. They include doctors, welders, artists, social workers, lawyers, construction crew and random fuckers at the grocery store. I do not hang out with them. I do not have to in order to maintain a civil Know A Guy relationship. I can drop them useful tidbits and fuck right off so I don't have to spend any more time than necessary with them
** People may assume romantic intent. Be prepared for that. I generally denote that it's a friendly/work lunch by calling them bro at some point if they're my age. Otherwise my general demeanor is sufficient to show that I do this with everyone
Source: personal experience, mother's teachings of crime, booth vending and poverty
10K notes
·
View notes
Photo

The 7 R’s of Sustainability:
Did you know that ‘recycling’ is step 6 of the 7 Rs of sustainability? The other R’s are just as important even if they are often forgotten.
Rethink- Do I really need to buy this? The point of this step is to stop and think.
Refuse- Does this product damage the environment? If so, refuse to spend your money on it. i.e. single use plastics, harsh chemicals
Reduce- How much of this do I really need? Buy less! Buy in bulk when you can as it often equals less packaging to throw out.
Reuse- Can I use this product again? Can I fix what I have so that I don’t need to buy something new? Reuse that plastic water bottle a few times. And instead of buying new, try thrift shopping, flea markets, yard sales etc.
Repurpose- Unlimited creativity! Does this item have another use? i.e. old torn clothes can be rags or plastic cups can be planters.
Recycle- Can I recycle this? Not everything can be. There are also some important steps to making sure your recycling is done properly. If unsure, look up local recycling regulations.
Rot- Can I compost this? Food waste, yard clippings, newspapers and many other items can be composted instead of being tossed in the trash. Composting is surprisingly simple and helps reduce harmful greenhouse gasses from entering the atmosphere.
What is the point of the R’s? The number one benefit of the 7 R’s are the reduction of the amount of waste sent to incinerators and landfills. The EPA website provides a lot of useful information. Other benefits that we can reap from implementing these concepts in our life are (as listed on the EPA website): • Prevents pollution caused by reducing the need to harvest new raw materials • Saves energy from not making a new product • Reduces greenhouse gas emissions that contribute to climate change • Helps sustain the environment and natural resources for future generations • Saves money from processing our waste • Increases economic security by tapping a domestic source of materials • Helps create jobs in the recycling and manufacturing industries in the United States
https://www.northglenn.org/government/departments/public_works/trash/recycling.php https://www.nrdc.org/stories/composting-101 https://www.epa.gov/recycle https://www.northglenn.org/Recycling%20Article.pdf
6K notes
·
View notes
Text
I feel like it's important to point out that in the last few days alone, in the middle of the ongoing flap about How Old He Is, Biden has announced two MAJOR pieces of progressive legislation/priorities for his second term: a) major SCOTUS reform, term limits for SCOTUS justices, a constitutional amendment nullifying the "president god-king" ruling, and b) legislation to cap/stabilize rent costs nationwide and financially punish landlords who raise their tenant's rent by more than a certain percentage (the news I saw had it as no more than 5%) in a year.
It is important to note that aside from these both being necessary and needed (the SCOTUS reform alone, holy shit) Biden's response to challenges to his candidacy is to go MORE left, not LESS. The conventional wisdom for 800 years has always been that Democrats Need To Go More Centrist, a mainstream and longterm Democrat like Biden has absolutely heard it over and over, and we have heard so much about how we need to court Republicans who are tired of Trump by being more conservative. Biden is not doing that. He is making the electoral gamble that the way to win is by going even more left, which would also have implications for his policy agenda in a second term, especially when he was freed of re-election concerns and could just go "fuck it."
Now we, and I cannot emphasize this enough, need to reward him for the move leftward and incentivize him to do it more. When you shout endlessly at politicians to be more left and then just bitch at them for not being even more left even when they move in that direction, you discourage them from doing so and make the hoary old Move To The Center narrative come back yet again. So:
#politics for ts#vote for joe biden#give joe biden money#talk to your friends about voting for joe biden
13K notes
·
View notes
Text
A few years ago I had a phase of being REALLY into digital privacy, using tor, duckduckgo, etc before suffering some burnout because I was trying to be 100% secure. So I'm by no means a expert I'm just relaying experience.
The culture of a lot of left leaning and "fandommy" sites (tumblr, twitter, etc) tends to fear/dislike (or just not know about) a lot of the IT stuff used by people into online privacy because they asscoiate it with "techbros". ESPECIALLY anything even remotely involving cryptocurrency. But if Trump is going to start censoring things and making morning after pills harder to get now might be a VERY good time for Americans to get into online privacy and how to avoid being tracked as well as avoiding censorship. Perhaps even some crypto to buy things discretly (or perhaps if ICE agents start caring about cash?) and because many activists groups also take donations in crypto. Never dealt with crypto myself but from what I know Monero was designed to be more untracable than Bitcoin. Don't know how succesfull that is though. Definetly get into privacy in general though.
I'll leave some useful links to get started. Words of advice:
Don't install a fuckton of privacy extensions on your browser, your unique combination of extensions will give your browser a unique fingerprint. Instead read up on and pick a few commonly used ones.
The BIGGEST annoyance for me was acedemic/proffesional settings because noone wants to switch over to some software they never heard off for one group project. Personally I use some normie software for exclusivly proffesional purposes with NO other information on me and do my actual browsing/leisure computer use more privatly.
https://www.privacytools.io/os: General software/browser/etc recomendations.
https://coveryourtracks.eff.org/: Test how private your browser is.
https://www.torproject.org/: THE gold standard for privacy focused browsers. Also obscures ip. Might not always be practical. Has the disadvantage of being notoriously slow and is blocked by some services/websites to avoid people bypassing ip bans and whatnot. Probably don't use this as your everyday browser but if you ever need to look up anything without censorship use tor.
https://tails.net/: Install a portable mini operating system on a usb stick to browse privately from any computer.
https://www.eff.org/ Electronic frontier foundations website.
https://mastodon.social/explore Don't have experience with it myself. But open source social media that should be much harder to censor.
Tumblr probably won't like me talking too directly about this because of ties to piracy but for people interested in banned books https://en.wikipedia.org/wiki/Shadow_library should be an interesting read...
3K notes
·
View notes
Text
Tf141 x reader idea nsfw mdni
This is what I was thinking about WHILE TAKING MY FINAL TODAY. The brain rot is actually rotting.

So I keep having this idea about being the tf141’s technical analyst (think Garcia from criminal minds kinda beat)
And part of your job is reviewing websites and links visited by any government equipment. Including the tablets/ work phones/ laptops the boys use on base / in the field , just to make sure nothing is a security threat. Keep things secure and tight.
You’re mature enough not to blink twice at the porn websites, and how the visits to them spike while they’re in the field . They’re hotblooded men, it makes sense.
You do blink.. at least once.. seeing how their searches seem to mirror their teammates. Soap’s masked men searches, Gaz’s bearded daddy type thing, Ghost’s affliction for Scottish gym rats, and Price’s varied tastes.
*ok so this squad was a little messy*
But ok, the websites are secure enough. You make a mental note to look into some additional antivirus software for them but move on. Except… now it’s hard not to read into Price’s lingering shoulder pats on his team. It’s harder not to notice how Gaz brings Coffee and Tea to his teammates with a soft smile. Ghost’s intense watchful eyes softening ever so slightly when someone made a joke said something kind. And wait… did Johnny just smack someone’s ass??? And hey, you could swear Gaz and Johnny *weren’t* wearing those shirts before they mysteriously disappeared for half an hour.
Whatever, it’s a hard job. They deserve a little stress relief. you’re happy for them. Maybe a little jealous because that’s a big ole sandwich (LOTS of meat) anyone would want to be in. Maybe you blush when Johnny and Kyle sit on either side of you in the mess hall… maybe you get a little sidetracked when going over hacked intel with Ghost and Price, how they both lean over your shoulder as they look at your screen…
Focus. FOCUS.
So, imagine your surprise when one day as your clearing some of the links that Soap’s tablet had visited that weekend. And his searches sound familiar- your build, your hair color, your features….
Soon you find something similar going through Price’s, and then Gaz’s… (the only reason you don’t see it on Ghost’s is because he watches over Soap’s shoulder). All of them searching for porn where the actress looks like you…
You should feel violated. Uncomfortable. Disrespected… but you don’t. If anything, you feel a little hot under the collar. Maybe a little embarrassed.
Maybe it was time to remind the boys that you can in fact see their internet searches. If you can manage to look them in the eyes.
Anyways do I have something here or…???
Turns out I had something. Part 2
#call of duty modern warfare x reader#codmw x reader#ghost x reader#simon ghost riley x reader#simon riley x reader#john price x reader#captain price x reader#cod mwii x reader#tf 141 x reader#141 x reader#poly 141
4K notes
·
View notes
Text
honestly being a community manager is the worst thing that ever happened to me lmaoooo
#sorta joking but no ??? it's like. it's like working a customer service job only i thankfully don't have to call anyone BUT i do have to#deal with customers & people that are soooooo stupid it's incredible#girl tell me why are you asking me through the official account dm's how much a product is... when you have the website link right there.#it's so ... idk it's like when an influencer says this is the product im using here's the colour number of my lipstick here's my bra size#and THERE WILL STILL BE COMMENTS BEING LIKE SO WHAT'S THAT COLOR WHAT'S YOUR BRA SIZE WHERE'S THE TV FROM#girl it's right there. please use your brain cells. it's not that hard!!!!!!#from another account i run we had a girl be like so yeah i wasn't able to secure tickets to the meet & greet... is there a way i could#still meet this person? girl?????? did i die and not realize you're the most important person in the world rn??? like#why would you be different than ANYBODY ELSE you're NOT SPECIAL you're just a girl!!! i get it!!! me too!!!! so please stop!!!#anyway. yeah. i'm fed up with people lmao
1 note
·
View note
Text
Hey everyone it seems there a malicious individual trying to hack the sims cc community again and fill it with malware you need to stay vigilant as a creator and a downloader so
i have some tips for both to stay safe while downloading:
1- sims cc file extension is always .Package never download anything that is .exe
2- do not auto unpack zip files and rar files into your mods folder directly, open each zip or rar individually check the file extensions and drag them to your mods folder one by one
3- the only mods that have a .ts4script extension are ones that affect gameplay or how the game works, understand that if you are downloading cas or bb items you shouldn't have a .ts4script file
4- if you are downloading gameplay mods that do have .ts4script make sure that A) the creator hasn't announced on their pages that its infected B) you are downloading from a link provided by the creator of the mods themselves not something off of google or a link you got sent and make sure dates of upload match dated of announcements
5- if the mod or cc creator has retired and hasn't posted for a while LOOK AT THE DATES OF THE UPLOAD if it has been "updated recently" after the creator has left the community its most likely re-uploaded by a hacker and infected
6- download mod gaurd by Twisted mexi and keep it updated and keep your windows defender or malware detector Program up to date and always running do not disable it
7- make sure everything you download comes from a direct link from the cc creator, in this day and age do not trust link shortners, adfly, linkverse, etc get the universal bypass extension and ublock extension to stay safe but genuinely NEVER CLICK ON THOSE no matter how much the creator reassures you its safe it. is. NOT.
8- this is more of a general saftey precaution but, create a system restore point weekly before you run the game with new mods that way if anything happens you could have a chance to restore your windows to an earlier date before you downloaded anything.
9- BACK UP YOUR SHIT im serious right now either weekly or monthly put your files somewhere safe like a usb a storage card a hard drive even an online cloud if you dont have any of the previous.
10- files you should back up are your media from games and media everything else, any mods, games saves, work files, passwords, saved bookmarks, any documents txt files word files pdfs, links you saved, brushes or actions for Photoshop if you have any, any digital bills or certificates if you have any, and keep a physical list of all programs you have installed and where you installed them from
11- turn on any 2 factor authentication and security measures for any account you have
12- google and firefox have the option to check your paswords and emails against any data leaks USE THIS FEATURE and change any leaked passwords
13- regularly check your logged in sessions to make sure all the logged in devices or computers are yours and log out any that aren't and any old devices or unused sessions do this for every website and app you have an account on if available
14- change your passwords often. I know this is a hassle i know its hard to come up with new passwords but changing your passwords every few months will help you against anything mention previously that wasn't detected.
15- and as a cc creator check your cc and the accounts you host cc on and its uplaod and update dates make sure nothing has been changed without your permission :(
16- generally try not to get swept up in the "i must get it" fever you do not need to "shop" for mods weekly or monthly you do not need to download everything by that one creator you do not need to download new cc everytime you want to make a sim, im guilty of this so i know how hard it is to resist but take a breath and think "do i want this or do i need it" before downloading.
These are prevention methods i cant claim they are 100% will prevent any hacking but its better to be safe than sorry and these do keep you safe so
Brought to you by someone who has had their laptop ruined and data leaked from downloading cc once upon a time
3K notes
·
View notes
Note
I've seen you say a few times that it's a good idea to have a password manager; could you explain why? I always feel like I'm missing something when it's mentioned because it's phrased as if there's an obvious danger that password managers protect you from, but I'm honestly not sure how they help keep passwords secure.
The obvious danger is human nature. Humans are bad at creating passwords; your passwords are almost certainly easy to guess, repeated across different accounts, or both, because that is just how the vast VAST majority of people create passwords, because humans are bad at creating passwords. Everybody knows "the rules" for creating passwords (don't use the same password on multiple websites, don't include personal details in your passwords, don't use very common words or letter or number sequences in your passwords, don't tell other people your password) and people break all of those rules anyway.
A standalone (not in-browser like firefox or chrome password manager, though those are better than nothing) password manager stores your passwords, generates complex passwords for you, and can also be used for things like storing notes on passwords (like "did I put my MFA on my email or my cellphone or an app for this password?" or "here are the made-up answers to the security questions I used for this website because I definitely didn't use real answers or answers I'd used on previous websites" or "these are the bills associated with this credit card").
With the way the current security landscape works, there are two things that are extremely important when you are creating a password:
Uniqueness
Complexity
The overwhelmingly prevalent way that people get "hacked" these days is through credential stuffing.
Let's say that your private data was revealed in the Experian breach a decade ago. It revealed your name, email address, and phone number. Now let's also say that your private data was revealed in one of the many breaches from social media sites; that one revealed your name, email address, phone number, password, and security questions.
If someone wants to try to gain access to one of your accounts - let's say your bank account - if they have your name and phone number (usually extremely easy to find online), they can cross-reference that information with data that has been revealed in previous breaches - now they've got your name and your email address (which you probably used to sign up for your online banking and have ABSOLUTELY used as your login for accounts all over the place) and at least one password that you've used somewhere.
But the thing is, they don't have one password. They have every password associated with that email address that has ever been revealed in a breach. If you go to the site haveibeenpwned.com you can enter your email and see how many times your email address has appeared in a breach. You can compare that with the number of passwords that were revealed in those breaches and you can ask yourself "what did those passwords have in common?"
Because I can tell you, my Tumblr password from 2013, my Kickstarter password from 2014, and my Disqus password from 2017 (all revealed in various breaches) probably had a lot in common.
So, now the hacker has: your name, your email (which is probably your username), and various passwords they can try to use to log in. Did you use the same password for Facebook and Twitter eight years ago? Did you use parts of that password for creating your bank password? If you heard that twitter passwords were exposed in a breach you probably changed that password, but did you change the bank password that you built on the same structure? Probably not.
So what people will do is gather up all of this information and guess. They'll try your 2017 Disqus password to see if it will get access to your bank account. They'll try your 2020 Gravatar password. They'll try your 2024 Internet Archive Password.
And the reason they do this is because it works.
And the reason that it works is because we are all fucking garbage at remembering unique, complex passwords so instead of creating actually unique, complex passwords most people pick one memorable word or phrase, one memorable number, one unusual character, and *MAYBE* one feature of the site they're creating the login for and they use that template forever (1988Tumblrmacabre!, 1988Facebookmacabre!, 1988Ticketmastermacabre!) OR they create one password that they think is complex enough and use it across multiple sites with minor tweaks ($n0h0mi$hRu13z, sn0h0mishRul13z!, $n0h0mi$hWA) as needed for the sites' password requirements.
So most of what password managers do that is a drastic security improvement over people creating and memorizing passwords is that they create passwords that are functionally impossible to guess and functionally impossible to memorize. The problem with memorizing passwords (which is what you're doing if you're creating a bunch of passwords that you type in all the time) is that you can't actually remember all that many passwords so you'll repeat those passwords. The problem with creating passwords on your own is that passwords that humans create are pretty guessable. Even if you're doing a passphrase that's a long string of words you're probably working with common words ("correct horse battery staple" as opposed to "truculent zygote onomatopoeia frangible") and your password is more guessable than you'd really want it to be. Password managers don't do that, they generate gibberish.
Perhaps you are that rare person who gets out a set of dice and a notepad and rolls up every character for your password and memorizes it and never repeats, and if that's you, you could still benefit from a password manager because a password manager makes it easier to change that unique complex password when it is inevitably revealed in a breach.
So, okay, let's check in with where we're at:
Password managers mean that you don't have to memorize your password, which means that you don't need a password that is easy to memorize, which means that they can create passwords that are extremely complex and are therefore very difficult to guess. This protects you from crackers who will try to brute force your password.
Password managers mean that you don't have to remember extremely complex passwords for every account, which means that you are less likely to repeat your password in whole or in part across multiple accounts. This protects you from credential stuffers, who will try to use your password from one account that was revealed in a breach to open other accounts that were not.
Because password managers can generate and store complex passwords essentially instantly, you can replace passwords nearly effortlessly when there is a breach (no need to 'come up with' a new password, no issues with learning or memorizing it).
There are, however, advantages beyond that.
One major, MAJOR advantage of a properly-used standalone password manager is that it makes you safer from various kinds of phishing attempts and link hijacking. When you are setting up a password in your password manager (PWM from here on), you should be on the website that you want to log in to. The PWM will give you the option to save the domain that you're logging in to. That means the PWM will remember the correct URL for your Tumblr login so when you go to the tumblr login screen in the future, it will offer to fill those fields. What it will NOT do is offer to fill those fields if someone sends you an email that spoofs tumblr support and wants you to log in at "tumblr.co" or "tumblr-support.com." Knowing this, and knowing that you should be putting your credentials in through the PWM fill option rather than copy/paste, is a GREAT way to protect against phishing that is often overlooked and definitely under-discussed.
Another advantage is that a standalone PWM will let you store secure notes with your passwords so that you can do things like keep track of recovery codes for the website, or generate gibberish answers to security questions. Security questions and answers are often revealed in breaches, can't be reset by the user as easily as a password, are repeated across websites MUCH more than passwords, and can be used to take over an account and reset the password. You shouldn't be giving real security answers, or even fake-but-repeated security answers; you should treat each of those like a password that needs to be complex and unique, which means that they need to be stored someplace (like a password manager).
I also personally use my password manager to store my car insurance information, my driver's license info, and payment details for easy entry, making it convenient for a lot of thing beyond password storage. (Bitwarden. My password manager is bitwarden. I recommend Bitwarden. go to ms-demeanor.com and search "bitwarden" to learn more.)
As to how they keep your passwords safe, aside from ensuring that you don't enter your credentials into a skimming site, a good password manager is well encrypted. Your password safe should be functionally impossible to crack and what people tend to not realize is that a proper password manager (like bitwarden) doesn't keep all your passwords in one encrypted safe, each one of your passwords is in its own encrypted safe. If someone hacks Bitwarden it's not like using a huge amount of effort breaking into a bank vault and finding a big pile of money, it's like using a huge amount of effort breaking into a bank vault and finding a big pile of bank vaults. Each password within your vault requires decryption that is functionally impossible to crack (at least with a good password manager, like bitwarden, the password manager I recommend and think that people should use).
Additionally, just as, like, a side note: password managers never accidentally leave caps lock on or forget which characters are capital or lower case and don't require the use of two hands and focused attention on the keyboard. You're never going to mistype your password if the password manager is filling it, and you would not believe the number of people we support at work who require password resets because they are typing their password wrong and don't realize it.
TL;DR:
Password managers make better passwords than you can and they make it possible to instantly create, store, and enter complex passwords, which prevents password cracking and makes people less likely to reuse passwords. They are heavily encrypted and should be functionally impossible to access, and each individual password within the manager should also be encrypted if you use a good password manager. Password managers also prevent people from entering their credentials on scam sites by only filling on matched domains. Standalone password managers (not browser password managers) also allow users to create and store unique security questions and account details to prevent bad actors from gaining access with stolen security answers. The password manager I recommend is Bitwarden.
If people used password managers to create, store, and use unique and complex passwords, and if they did regular backups of their system I think that probably about half of the InfoSec field would be out of a job.
Please use a password manager!
2K notes
·
View notes
Text
VPNs do not make you more secure
here's how they work!
first of all, most of your internet traffic is already encrypted via TLS (Transport Layer Security). Things that aren't encrypted are usually videogames or less important applications.
a VPN encrypts traffic between your computer and the VPN server you're using.
your Internet Service Provider (ISP) sits in the middle of that transaction.
cue the MS paint diagram
Without a VPN:
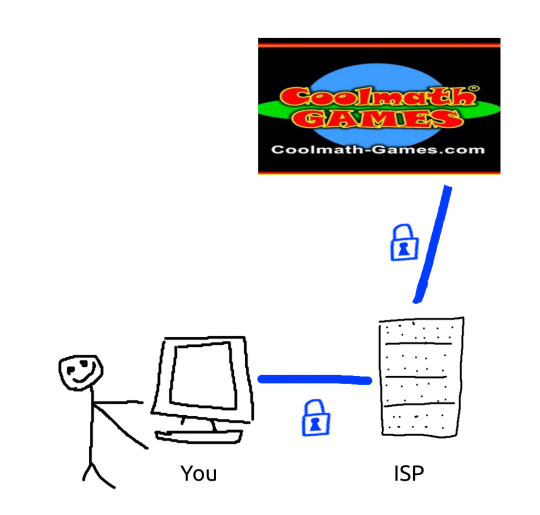
With a VPN:
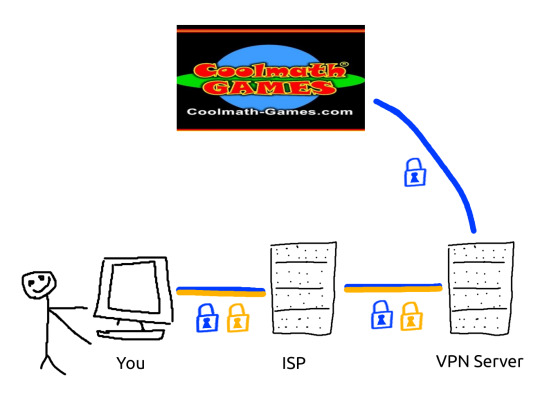
the traffic between your VPN server and the rest of the internet is not encrypted any further.
things that VPNs are good for:
bypassing geo-blocking
bypassing website blocks set up by your ISP
obscuring network traffic from your ISP
things that VPNs are not good for:
browsing the internet without having your activity logged. every company that gives internet service logs the activity, it's half of how they make sure they're not being hacked.
hiding information from the government. VPN providers WILL bend to subpoenas, they WILL turn over logs of your network activity.
cybersecurity. VPNs can't save you once the traffic is between them and the final destination. they don't analyze your traffic to detect and stop hackers, they don't add any encryption where it matters.
VPNs are not a shortcut to security. you cannot pay 15 dollars a month to forgo all responsibility for your own digital privacy. do your research, use a password manager, stay safe.
my friends i hope you find this information useful. you have been sold a lie. remember to show extreme skepticism to youtube sponsorships and journalism websites which sing their praises.
sources: i have a certificate iv in cybersecurity
2K notes
·
View notes