#mobile hackers
Text

Hire a hacker in PrimaryHackers!
We are offering all of hacking services.
Phone hacking, Whatsapp hacking, Facebook hacking, Instagram hacking, websit hacking etc.
1 note
·
View note
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
75 notes
·
View notes
Text











The Leverage OT3 in Every Episode
Leverage: 01x07 The Two-Horse Job
#such a good episode#I say that every gifset but still#love the Eliot horse girl episode#also just generally a sweet episode#so hard to frame some of these scenes tho so many people moving#I just love the ot3 looks and communication in this episode#like even just in a team way (because Eliot goes off and does stuff ya know) but still#it’s just so fun I love the looks they’re so funny#like Parker and Hardison in the car#and Parker’s fear of the horses#like when Parker says they’re not as murderous Hardison and Eliot’s looks like it’s so funny#they’re like I can’t believe her but also we love her so#leverage#inde gifs#the two-horse job#inde gifs: the two-horse job#inde gifs: leverage ot3#inde gifs: the leverage ot3 in every episode#one day I will actually link that tag to the title of these posts#and add the alt text my goodness#my tumblr fails at alt text on mobile when I try to add it#I’m so sorry#leverage ot3#ot3: hitter hacker thief#eliot spencer#alec hardison#Parker#the leverage ot3 in every episode
53 notes
·
View notes
Text




wacker fursona [scalesona??] real [he's a velociraptor !]
furry merc doodles ft @sicc-nasti 's horse courier and @pinkpegacorn 's cat jack [:
#ignore that i forgot quinces stubble in the last one i added it later but im on mobile and only have this version#anyways i found out that furries are like. unreasonably fun and easier to draw#this is awesome#art tag#my ocs#people's ocs#hacker#furry
42 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project
For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
20 notes
·
View notes
Text
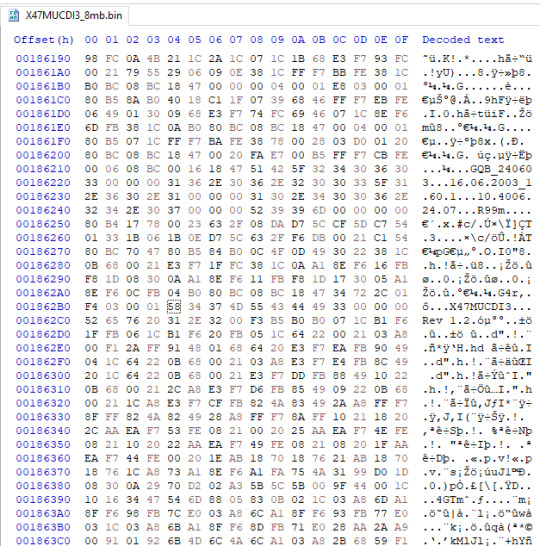
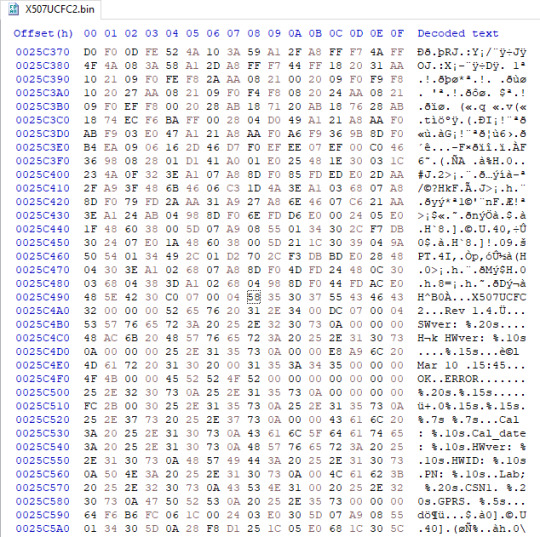


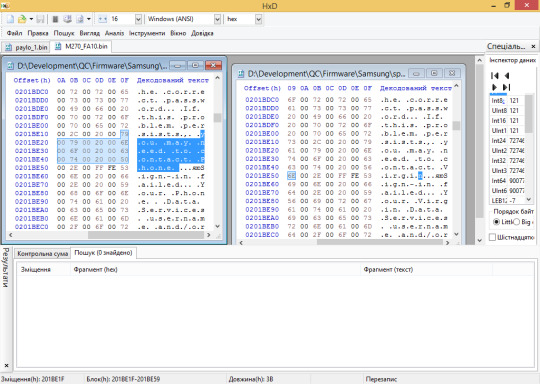
Samsung SGH-X427m and X507 dumped, plus a modified SPH-M270 firmware shipping on a prepaid carrier device..?
I know posting has been slow, but rest assured phone preservation has shown no signs of slowing down!
Some new firmware dumps as of late:
Samsung SGH-X427m, version X47MUCDI3 (incomplete; 8 of 16MB)
Samsung SGH-X507, version X507UCFC2. A previously undumped model!
Samsung SPH-M270, version FA10 on Virgin Mobile. Read on for the story of the previous FA10 dump…
The previous Samsung SPH-M270 dump was done on an unsuspecting device with a Q Link Wireless sticker on it, and appeared to be based on an existing Virgin Mobile firmware, itself still having some Sprint remains.
It wasn't put into question until the phone in question had much less restrictions compared to any Virgin Mobile feature phone, including a working Qualcomm Diagnostic port as well as working test dial codes (such as the ##2739# BREW code).
When known BREW contributor kraze1984 picked up his own M270, he noted that none of the dial codes which worked on the Q Link device worked on his, and that it only allowed for an MTP connection when plugged into a PC.
One JTAG dump later, and it was found that every single mention of Virgin Mobile was replaced with "Phone", resulting in the phrase "You may need to contact Phone" being found on the modified firmware.
It is yet to be known who made the modifications to the M270 firmware for Q Link Wireless, or why they even bothered to do such…
Last but certainly not least, thank you to MC4f for the recent donations and krzbrew for dumping the stock SPH-M270! I hope to be able to share info on a very interesting reference device soon…
#digital preservation#flip phone#samsung#mobile phone#sprint#virgin mobile#q link wireless#unknown hacker who modded a cheap flip phone's firmware where are you
10 notes
·
View notes
Text
Yooo i did it!! Had to write the text on mobile and then post from browser because my keyboard is broken and it would have been hard tagging the stuff without using S and A
#i ramble#hacker man#!!!!#i hate tunglr mobile all my homies hate tunglr mobile#i say as i never use the browser version#this just makes everything more complicated
17 notes
·
View notes
Text
Times leche has been locked out of his apartment: 4
Times leche has been locked out of his apartment and therefor his job cause the keys are on the same ring: 2
#ooc. » .001 ✦#mobile mode#hacker voice: I’m back in#you know I’m gonna just update this to laugh at myself
13 notes
·
View notes
Text

#hackerslist#hire a hacker#hacking#cybernetics#cybersecurity#cyberpunk 2077#cybercore#iphone#android#mobile hacker#social media
2 notes
·
View notes
Text
[every day the urge to give lonnie a leverage au grows...]
#[pspspsps leverage fans u know your muses wanna mentor an nb anti-establishment anarchist catgirl hacker....]#[they can fit so much child figure energy into them]#[like the opposite of someone who is a parent figure to young characters; theyre a child figure to adultier characters]#{ooc}#{mobile post}
2 notes
·
View notes
Text
How To Increase Your Photo Size In Mobile..! | @BigTvTechMan
youtube
#snapeditapp#snap#editing#bigtvtechman#photoediting#apps#whatsapp#newfeature#chandrayaan3#gaganyaan#operatingsystemmaya#indiaoperatingsystem#whatsappredtick#mobile#photosize#hackers#gmailnotrecovery#hacking#Youtube
2 notes
·
View notes
Text

1 note
·
View note
Text
Weekly output: applied AI, open innovation, Mastodon updates, AI equity, 1Password, Signal, Eve Air Mobility, travel tech, travel tips
After getting back from Brazil early Saturday morning, I’ve napped more than usual but have also spoken at an event in D.C., gotten in some gardening, and enjoyed a shorter-than-usual bike ride.
5/1/2023: Companies adopting AI need to move slowly and not break things, Fast Company
I wrote about how two companies I’ve covered elsewhere recently–the satellite-imagery firm Planet and the…

View On WordPress
#1Password#AI#air taxi#Bluesky#Brasil#Brazil#Eve Air Mobility#eVTOL#frequent flyer#FTU#FTU DC#Intercom#Mastodon#miles and points#Planet#Rio de Janeiro#Signal#travel hackers#Web Summit#Web Summit Rio
2 notes
·
View notes
Text
Hire a Mobile hacker to monitor your partner's chat activity

Related: Best Mobile Hack to Track Your Teenage Child #1
Mobile phones have become an essential part of our daily lives, acting as our communication hub, personal assistant, and entertainment source. But with this increased dependency comes the growing threat of mobile hacking. Understanding mobile security is crucial to protect your personal information from malicious attacks.
💢 What is Mobile Hacking?
Mobile hacking involves unauthorized access to a mobile phone's system, data, or communication. Hackers use various methods to exploit vulnerabilities in mobile devices, often without the owner's knowledge. Common misconceptions include the belief that only outdated or unprotected phones are at risk. In reality, even the latest models with advanced security features can be targeted.
💢 How Hackers Target Mobile Phones
Hackers use several techniques to gain access to mobile phones:
🔸 Phishing Attacks: Sending fake messages or emails to trick users into revealing personal information.
🔸 Malware: Installing malicious software that can steal data or monitor activities.
🔸 Network Spoofing: Creating fake Wi-Fi networks to intercept data transmitted over them.
🔸 Exploiting Vulnerabilities: Taking advantage of security flaws in the phone’s operating system or apps.
💢 Is My Phone Hacked?
Wondering if your phone might be hacked? Look out for these signs:
🔹 Unusual Battery Drain: Malicious software running in the background can cause your battery to deplete faster than usual.
🔹 Slow Performance: If your phone is suddenly slow or crashes often, it could be compromised.
🔹 Strange Messages: Receiving unusual texts or emails, especially from unknown sources, is a red flag.
🔹 Data Usage Spikes: Unexpected increases in data usage may indicate that malware is transmitting data from your phone.
💢 What to Do if My Phone is Hacked
If you suspect your phone is hacked, act quickly:
📕 Disconnect from the Internet: Turn off Wi-Fi and mobile data to prevent further data transmission.
📕 Scan for Malware: Use trusted security apps to scan and remove any malicious software.
📕 Change Passwords: Update all your passwords, especially for sensitive accounts.
📕 Factory Reset: As a last resort, perform a factory reset to remove all data and restore the phone to its original settings.
💢 Can My iPhone Be Hacked?
While iPhones are renowned for their security, they are not immune to hacking. iOS security features include:
📒 Sandboxing: Restricts apps from accessing data from other apps.
📒 App Store Vetting: Thorough review process for apps before they are available for download.
However, vulnerabilities can still be exploited through techniques like jailbreaking or by installing malicious apps from unofficial sources.
💢 How to Find Out Who Hacked Your Phone
Tracing the hacker is challenging but possible. Here are some steps:
📘 Check Activity Logs: Review your phone's activity logs for unusual behavior.
📘 Consult Professionals: Seek help from cybersecurity experts.
📘 Report to Authorities: File a report with local law enforcement or cybercrime units.
💢 Hackers can use your phone number to:
📗 SIM Swapping: Transfer your phone number to another SIM card, gaining access to your accounts.
📗 Phishing: Send malicious links via SMS.
Protect your phone number by avoiding sharing it publicly and using two-factor authentication for your accounts.
💢 Hacked Phone: What to Do?
If your phone is hacked, follow these steps:
📙 Identify the Source: Determine how your phone was hacked to prevent future attacks.
📙 Remove Malware: Use security software to clean your device.
📙 Update Software: Ensure your operating system and apps are up-to-date.
📙 Secure Accounts: Change passwords and enable two-factor authentication.
💢 Best Mobile Hacker
There should be some essential features to be considered the best mobile hacker.
🔎 First, a deep understanding of various programming languages like Python, Java, and Swift is crucial.
🔎 Second, strong cybersecurity awareness to protect against and exploit vulnerabilities is necessary.
🔎 Third, proficiency in using popular hacking tools like Metasploit, Wireshark, and Nmap is vital.
🔎 Fourth, ethical conduct to ensure responsible hacking practices is essential.
🔎 Fifth, practical experience through real-world applications and simulated environments is important.
🔎 Lastly, continuous learning to stay updated with the latest trends and techniques is indispensable.
💢 If My Phone is Hacked, What Should I Do?
Here’s a practical guide:
Stay Calm: Panicking won't help. Take methodical steps to secure your phone.
Backup Data: Before making any changes, backup your important data.
Use Security Software: Regularly scan your phone for threats.
Educate Yourself: Stay informed about the latest security threats and how to counter them.
💢 Why Hire a Mobile hacker
In the age of smartphones, mobile security is more important than ever. Have you ever wondered how secure your mobile app or device really is? That's where a mobile hacker comes in. But why should you consider hiring one? Let's dive into the world of mobile hacking and explore its benefits.
💢 Benefits of Hiring a Mobile Hacker
Enhancing Mobile Security
Mobile hackers can significantly enhance the security of your mobile applications and devices. They identify and address vulnerabilities that could be exploited by malicious actors.
Preventing Data Breaches
By identifying potential weaknesses, mobile hackers help prevent data breaches that could compromise sensitive information.
Identifying Vulnerabilities
Hackers can pinpoint specific vulnerabilities that might be overlooked during standard security checks.
Related: Hire Professional Social Media Hackers
💢 Best Hacking Apps
Some of the top hacking apps used by professionals (often for ethical hacking) include:
Metasploit: Used for penetration testing and finding vulnerabilities.
Nmap: Network scanning tool that identifies open ports and services.
Wireshark: Network protocol analyzer for troubleshooting and analysis.
While these apps have legitimate uses, they can be misused for illegal activities.
🔘 Finishing Touch
Mobile hacking is a serious threat that requires vigilance and proactive measures. By understanding how hackers operate, recognizing the signs of a compromised phone, and taking appropriate steps to secure your device, you can protect your personal information and privacy. Stay informed, stay secure, and don't hesitate to seek professional help if needed.
FAQs
Q-1: Can my phone be hacked if I only use official app stores?
A-01: While using official app stores reduces the risk, it does not eliminate it completely. Always read reviews and check permissions before downloading apps.
Q-2: How often should I change my passwords?
A-02: It’s recommended to change your passwords every three to six months and use unique passwords for different accounts.
Q-3: Is it safe to use public Wi-Fi?
A-03: Public Wi-Fi is generally not secure. Use a VPN to protect your data when connecting to public networks.
Q-4: Can resetting my phone remove all hacking threats?
A-04: A factory reset can remove most malware, but it's important to also change all passwords and update your security settings.
0 notes
Video
youtube
Shield Your Smartphone - Outsmart Hackers Now!
#youtube#Smartphone Security Hackers Protect Digital Safety Outsmart Cybersecurity Mobile Threats Tutorial
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#cell phone hack#cell phone hacker#cell phone hacking#cell phone hacked#mobile hacker#mobile hacking#hackerslist
0 notes