#objective on forensic law
Explore tagged Tumblr posts
Text
Writing References: World-Building
20 Questions ⚜ 100 Words for World-building
Basics: World-building ⚜ Places ⚜ Imagery ⚜ Setting
Exploring your Setting ⚜ Habitats ⚜ Kinds of Fantasy Worlds
Fantasy World-building ⚜ World-building Vocabulary
Worksheets: Magic & Rituals ⚜ Geography; World History; City; Fictional Plant ⚜ A General Template
Editing
Setting & Pacing Issues ⚜ Editing Your Own Novel
Writing Notes
Animal Culture ⚜ Autopsy ⚜ Alchemy ⚜ Ancient Wonders
Art: Elements ⚜ Principles ⚜ Photographs ⚜ Watercolour
Creating: Fictional Items ⚜ Fictional Poisons ⚜ Magic Systems
Cruise Ships ⚜ Dystopian World ⚜ Parts of a Castle
Culture ⚜ Culture Shock ⚜ Ethnocentrism & Cultural Relativism
Food: How to Describe ⚜ Lists ⚜ Cooking Basics ⚜ Herbs & Spices ⚜ Sauces ⚜ Wine-tasting ⚜ Aphrodisiacs ⚜ List of Aphrodisiacs ⚜ Food History ⚜ Cocktails ⚜ Literary Cocktails ⚜ Liqueurs ⚜ Uncommon Fruits & Vegetables
Greek Vases ⚜ Sapphire ⚜ Relics ⚜ Types of Castles
Hate ⚜ Love ⚜ Kinds of Love ⚜ The Physiology of Love
Mystical Objects ⚜ Talisman ⚜ Uncommon Magic Systems
Moon: Part 1 2 ⚜ Seasons: Autumn ⚜ Spring ⚜ Summer
Shapes of Symbols ⚜ Symbolism ⚜ Slang: 1930s
Symbolism: Of Colors Part 1 2 ⚜ Of Food ⚜ Of Storms
Topics List ⚜ Write Room Syndrome
Vocabulary
Agrostology ⚜ Allergy ⚜ Architecture ⚜ Baking ⚜ Biochemistry
Ecology ⚜ Esoteric ⚜ Gemology ⚜ Geology ⚜ Weather ⚜ Art
Editorial ⚜ Fashion ⚜ Latin Forensic ⚜ Law ⚜ Medieval
Psychology ⚜ Phylogenetics ⚜ Science ⚜ Zoology
More References: Plot ⚜ Character Development ⚜ Writing Resources PDFs
#writing reference#worldbuilding#setting#writing tips#writing advice#writeblr#dark academia#spilled ink#literature#writing prompt#creative writing#fiction#writers on tumblr#story#novel#light academia#writing resources#compilation requested by anon#will update every few weeks/months
5K notes
·
View notes
Text
unpopular opinion but i really enjoy "field of fire," the ezri dax "to catch a serial killer" episode. for all the scenery chewing and deep space nine's continued vulcan smear campaign, i'm not going to pretend it's objectively the best of the ezri a-plot episodes, but it's my favorite for what it reveals about her.
jadzia was emotional, headstrong, and sometimes impulsive (as was curzon), but ezri is reckless.
of course she is! she's young! she's unqualified for everything that has happened to her, and honestly, so are all her peers. she ran away from a fucked-up home to starfleet at a time when, as we saw with nog, they're field-promoting cadets at top speed to fill the ranks as starfleet suffers massive war casualties. she's more or less the same generation as the red squad cadets on the valiant who decided to fight the dominion war by themselves behind enemy lines.
and she wouldn't be ezri dax otherwise. the reveal in "equilibrium" is a secret known only the symbiosis commission and the starfleet offiers who were physically in the room. to the medical staff on the destiny and ezri tigan herself, the odds of rejection from an improper trill joining are overwhelmingly likely and fatal. but ezri still volunteers to join with dax! she's probably going to die in this uniform anyway, right?
jadzia was a focused, rule-following, straight-a student before she met the party worm, and it took dax a season or two to loosen her up, but ezri was probably already unhinged.
so of course she's the one who decides to take her inner murderer off the leash at the slightest provocation. sisko asks her to help odo out, and ezri somehow interprets this as feeling like she's solely responsible for finding the killer when she only took one class at the academy in forensic psychology and didn't even like it. odo and o'brien are continuing their own investigation off-screen the whole time! meanwhile, she probably had to look up the trill emergence ritual in a book. she has not read the fine print on ANY of this.
and she sticks with this crazy plan, even when it becomes clear that she's right on the edge of becoming a danger to society. but ezri's whole starfleet career, maybe her whole young life of ignoring and plotting her escape from her emotionally abusive family, certainly her whole joined experience, has been lived right on the edge.
all the scenes she has with joran in and around quark's bar to me are her technique for staying grounded in reality. they often happen after joran pushes her too far, so she uses being public as a distraction from that one-on-one intensity—even though it means she looks insane and everyone's staring at her. even joran is like ".... shouldn't you have told sisko about me?" she is full in dax stubbornness on this deeply dubious plan.
and it works!! and in the final account, i think she liked it a little: the power of playing a killer, the power of being stronger than joran, and the soft ending she has with him during reintegration.
her symbiont, her whole life on the station, her friends, her romantic interests, they were all jadzia's first, but jadzia was afraid of joran and would never have played this game. in this one way, ezri has a closer relationship to her unearned symbiont than jadzia did.
ezri's beta canon trajectory of switching to a command track is okay, but it makes me sad to think she'd ditch her chosen career entirely. i could see her getting into criminal psychology. her brother's a murderer (she hasn't unpacked that AT ALL), one of her past hosts was a murderer... with that backstory, she'd do numbers in a federation law & order procedural series. i'd watch it.
but honestly, in the federation spirit of rehabilitation, she might be uniquely qualified to treat violent criminals as well, rather than hunting them down. she could reach in and heal that part of herself and then use that experience to reach others.
#ezri dax#trillblogging#deep space nine#this is not well thought out meta here this is just me watching this episode and going HEAR ME OUT#star trek thoughts#let's put a readmore on that
144 notes
·
View notes
Text
An Undergraduate Forensic Viewing of Like Minds (2006) Train Scene

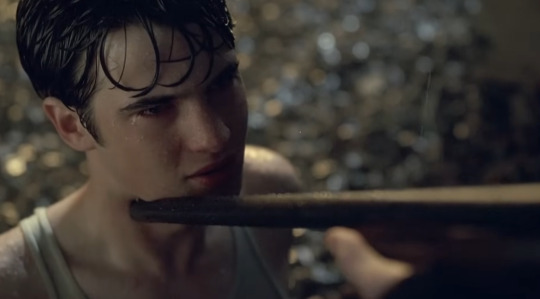
Pray for me. Pray for yourself. We are one now.



Contents:
1. Introduction 2. What We Know 3. The Investigation 4. Bibliography for Nerds

1. Introduction
Some justifications first.
I'm an undergraduate stem student obssessed with many topics, including forensic studies. I just finished a complete course about forensic chemistry/tecnology/law in uni and yes, I'm a big failure of a person and was thinking about applying some of the things I've learned into Like Minds' train scene. To clarify, I'm not an experienced profissional of the field. It is to say, I've never worked in such area and had just one or two significant interaction with said profissionals and students. My considerations won't be 100% accurate, clearly, and I may mistake or ignore fundamental data and studies. I intend solely to present some interesting facts and rapidly discuss their applicability here.
Take everything I say with large grains of salt, this is mostly for my enjoyment.
Let's kill Nigel!
2. What We Know
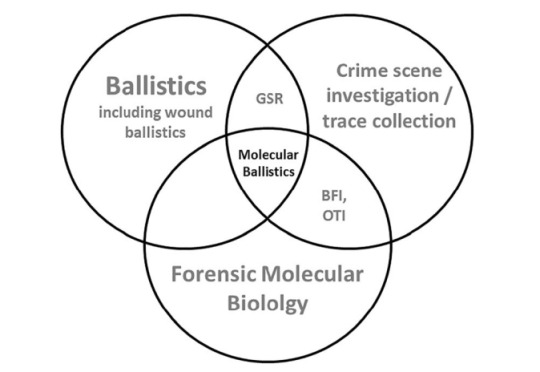
Figure 1. Visual diagram of forensic ballistics' main areas of study. Some will be mentioned here. [1]
2.1. Ballistics - Anatomy of a Discharge
Ballistics is a science field divided in three main ramifications: (1) Interior Ballistics, (2) Exterior Ballistics and (3) Terminal Ballistics. (1) studies the mechanism of a gun discharge, (2) studies the trajectory and behavior of a projectile once it is ejected from a firegun and (3) studies the damage and overall interaction of the projectile with a material structure (biological or not). [1] Ballistics experts (chemists, some engineers, law experts, etc) ocuppy themselves with many things regarding firearms, a field of work that recuries much study and understading of multiple fields of knowledge such as spectroscopy, law and general legislation, physical properties of chemical coumponds, solid state science, material science, industry production series and others. Some areas of chemistry and biology are of great importance and are commonly used complementarily.
We then understand what bullets are. The component that effectivally hits the target in these scenarios is the actual "projectile".
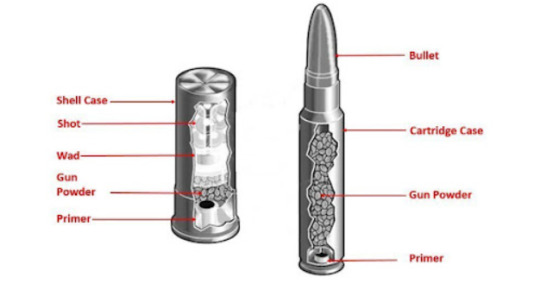
Figure 2. Simple structure of shotgun (left) and rifle (right) ammunition. [2]
In simple terms, they're composed by (1) a shell that holds everything together, (2) some coumpond responsable for the liberation of gas via chemical reaction and (3) some way to give the heat needed for said reaction to occur. There is a whole field of study and production of these killing objects that seeks out to balance some of their properties in different scenarios by the armamentist industry in oder to supply endless applications that constantly develops new shapes and components, so going through it all would be impossible. Regardless, all ammunition is classified by size, called "gauge" in shotguns, and "caliber" in rifles and handguns. [2]
Case: [in shotguns] It is a small cilindrical piece made out of a tube of common plastic or sturdy paper (the red/blue/colored part) that holds the multiple projectiles to be fired (shots), with a metallic base (the primer) composed of brass (copper and zinc) or steel (iron and carbon). [in rifles] The case is called cartridge case, and it is composed by brass as well. [2]
Powder (or propellant): They are usually Nitroclelullose (handguns), Nitroclelullose/Nitrogliceryn (rifles) and Nitroclelullose/Nitrogliceryn/Nitroguanidyn (long range rifles) [3]. Oversimplifying, organic molecules containing nitro groups (present in Nitroclelullose, Nitrogliceryn and Nitroguanidyn) are really unstable; these chemical groupaments are highly reactive in face of many scenarios. If enough energy is provided (by heating, or mechanical contact and pertubation) they will enter a decompostion process, breaking and reacting with their own bonds spontaneously, liberating gases such as H2O, N2 and CO2. These mentioned gases are much more stable compared to the original organic coumponds, so the atoms will "prefer" to form these species if the conditions are set (thus, a spontaneous reaction). This increases pressure inside the shell and forces the projectile to leave violently as a result of gas expansion. [4] Shotgun powder is composed by potassium nitrate, charcoal and sulfur; a mixture known as "dark powder", and it is separated from the shot (projectiles; multiple balls of steel, lead, rubber, or really anything) by a small component called "wad". The same principle explained in the decomposition of organic nitro-compounds apply for the potassium nitrate present here, but only in the presence of sulfur (easier to melt and ignite), providing the necessary heat for potassium citrate to generate the oxygen needed, resulting in charchoal's combustion. [2]
Primer: Primers are a fundamental part of any ammunition, and yet a simple one. When a firing pin from the firegun hits them, sparkles and heat will be produced, which gives the propellent all requiered energy for the chemical reaction. It is, when the action lever is pulled, the firing pin is tensioned by a spring inside the gun. When the trigger is pulled, this firing pin hits rapidly the ammunition's primer (metallic base). [5]
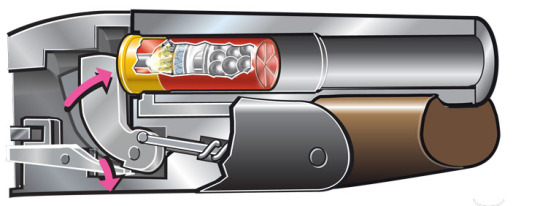
Figure 3. Shotgun firing pin scheme. [5]
The discussion of differents powders/propellents (like smokeless powder), projectiles shapes (in rifle cases) and firegun types (other than rifle and shotgun) is being ignored.
All that must be known is: the trigger pulling promotes a mechanical impact against the ammunition base, which promotes chemical reactions that liberate great amounts of gases, increasing the pressure inside the case, what will pushes the projectile(s) inside foward with great speed.
2.2. The Shotgun - Means to An End
We now restrain ourselfs to the firegun. Let us take a look on the following images:






Figures 4-9 (left to right, top to bottom). Shotguns' takes from Like Minds (2006).
Main considerations:
The shotgun used by Mr. Colbie isn't the same one used by Nigel/Alex in the train scene. We can clearly point that by the number of barrels, i.e., two barrels contaning two projectiles (killing Nigel's mother and father without visible activation) in its first appearance, and only a single one in its second appearance. Maybe this has been discussed before.
It is not a narrative problem if we have the eyes for it. Nigel's father possesses two shotguns, so we assume Nigel went back and grabbed the single-barrel one before going after Alex.
The reloading thing would be important during the bedroom scene, between the moments where John shoots his wife and Alex picks up the gun from the floor. There would be no way of aciddentially shooting Mr. Colbie wihout Alex pulling the action on the second barrel (how would he know which one of the barrels were loaded and why Mr. Colbie would only activate one of the two barrels? It appears he wasn't using the shotgun to merely scare his family). Perhaps the double barrel shotgun used has some individual firing feature, perhaps.
Also, the single barrel shotgun is the same one used by John when Alex and Nigel first accessed the hidden baseament together. This isn't of great relevance though.
After a compulsive research in gun sale sites and over 900 models of shotguns (no joking), I'm inclined to believe that Nigel's single barrel shotgun is an Era 410 GA Single Shot Break Action. My conclusions is based on Figures 6 and 9, the shotgun's best takes throughout the entire movie. The important details are: a single barrel, with rounded trigger guard that ends exactly where the wooden stock begins, by a rounded break action lever with squarish shape that leans horizontally to the receiver and a rectangular like forestock. Other smaller details are: the receiver's top shape and really curved back, the declination present on the stock and the three screws' position and size.
The engraved symbols on Colbie's receiver are sculpted by a profssional artist called "engraver", by client's demand. Therefore, these sigils are decorative and probably carry some meaning to the shotgun's real owner, so they aren't a discrepancy to worry about. The frame I acquired (Figure 9) is of poor quality and there's nothing I can read in there besides one or two letters. I've tried to watch the movie in other internet sites but it didn't help that much.
It took me forever, but here it is [6], [7]. There are also youtube videos revewing this gun in the Extra section.




Figures 10-13. Era 410 GA Single Shot Break Action Shotgun. [6]
Note: @laurelwen successfully identified Nigel's firegun as a Boito .410. The text engraved on the shotgun's receiver in Figure 9, in fact, reads "Boito". Check it out on this post. Look up Extra Bibliography No. 7 in the shotgun's section as well.
Shotguns are a really old type of gun from the 16th century. Their mechanisms were adjusted during following centuries, but they remain still to date with an extremely simple way of function. Today, there are many types, including the single-shots and hand shotguns, much different than what was originally conceived. A break shotgun is capable of "breaking in half" for reloading, exposing its ejector/extractor and barrel interior just as many other fireguns. [8]
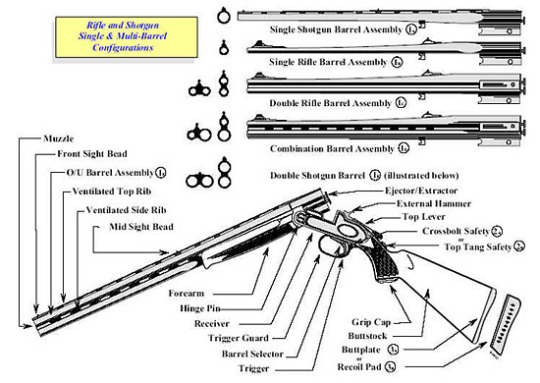
Figure 14. Break action shotgun anatomy. [9]
The Era 410 GA possesses a specially long length of barrel, which helps projectiles to achieve maximum velocity before leaving. Still, it appears from my research that this is a second hand model with low price, low demand and little historical relevance. This is the type of gun that would be bought mainly by collectors and enthusiasts; however, because of its little weight, good shooting and minimalist elegance, this firegun is not one of the worst models out there for small amateur animal hunting.
A 410 (10.41 mm, one smallest shot diameter in the market) with great pattern of dispersion after the discharge isn't bad, so at medium distances most projectiles would succesfully hit the center of a target. This is not very good when we're talking about a point-blank discharge directly at Nigel's face.
3. The Investigation

Figure 15. "If they had any evidence, I wouldn't be talking to you, would I?"
Authorities arrive at the dark, umid and isolated train tracks. Immediatly, a shocking scene: a desperate young man holding in his arms the corpse of a dead boy, disfigured. They transport the living witness away from the scene, but the lying unknown and deformed body is extracted for further autopsy. Detective McKenzie takes over with Forensic Psychiatrist Sally to interrogate the surviving suspect, Alex Forbes.
After the initial approach and first hours of interaction, the case takes an unexpected form. The question now is, did Alex Forbes shoot the now identified Nigel Colbie alone, or did Colbie participated in his own killing to incriminate Alex?
The police wastes its time thinking about common scenarios described in the book. They know the victim, the place where it happened, the exact gun used and the main suspect. Everything comes down to answering the presented question. Psycological attempts of extracting an answer from Alex by closed sessions with Sally, it is, to try and build a thrust and comfort relation with the suspect in order to obtain a confession would be protocol. But Alex clearly is beyond that, and if we must say, he's in control the whole time.
All that is left for the police is to attach towards factual evidences. Now, we describe two fundamental forensic elements of a gun-related crime.
Gunshot Residues (GSRs)
GSRs are one of the strongest evidences when it comes to forensic studies. Being composed of burnt and unburnt organic or inorganic particles from the explosive primer from the shell, propellant and possibly fragments of the bullet, cartridge case, and even the firearm, they frequently contain elements such as Sb (antimony), Ba (barium), Pb (lead) or Zn (zinc), Cu (cooper), and Ti (titanium). Their deposition concentrates away from the firearm into the shooter's (arms, face, hands and chest mainly) and victim's (region of contact mainly) bodies. GSRs can be found in nearby surfaces as well, such as the floor, ceiling, walls, objects, clothes, etc. The direct deposition of these residues must be carefully used as evidence because of its irregular distribution on the surrounding enviroment after the discharge. Thus, the main factors are always the chemical composition and concentration spots. Shotgun shots (the small spherical projectiles) are usually made up of lead or lead/antimony, but some ammunitions use steel, zinc-plated steel, tungsten and bismut in substitution (So, in our case, we can expect more significant ammounts of antimony/lead or zinc, iron and carbon). [10], [11]
A 410 ammunition is classified as "birdshots" ammunition, used for hunting said animals. The little diameter of projectiles allows the carrying of multiple projectiles inside one shell, facilitating the execution of small moving targets. The potential damage mustn't be underrated, though.
The aforementioned substances/elements can be detected, investigated, and quantified using microscopy, chemical analytical and chemometric methods, such as Scanning Electron Microscopy (SEM), Energy Dispersive X-Ray Spectroscopy (EDS), Atomic Absorption Spectroscopy (AAS) and Energy Dispersive X-Ray Fluorescence (EDXRF). All these techniques are extensively known and applied in uncountable areas of science for identification and characterization of solid materials. In a nutshell, these methods revolve around the interaction of matter with radiation (such as X-Rays) and the energy absorved/emitted by it after the interaction. The SEM is a most usefull analysis for it can provide real images of micro structures and particles present above any surface, like clothings, skin, fifregun metal and others, if properly prepared. [10]
It is important to understand that these identification methods are of extreme precision and sensibility, it is, minimal concentrations can and will be detected inneviatbly.

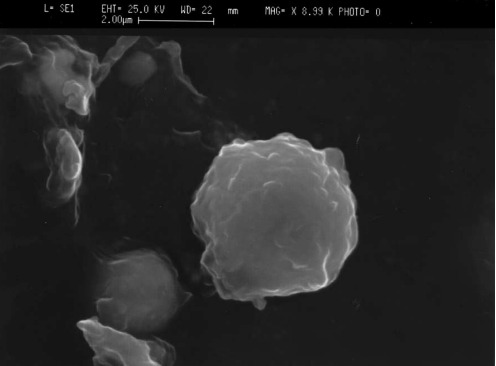
Figure 16 and 17. (Left) Image of gunshot powder residues dispersed in the air after discharge. Top left and (Right) images refer to SEM "photos" of extremely small particles of GSRs that can be chemically analyzed. [12], [13]
What about the lifespan of these residues? In long terms, the shooter's trigger hand (right hand) seems to contain most of the residues that persist for a fair amount of time after the discharge. [10] Unffortunately, the mentioned study occured in controlled enviroments, which is not the case. Another work [14] concludes that most GSRs are lost after two-four hours from the discharge. Considering the fast action from authorities described in the movie, we can basically ignore this factor and consider other variables.

Figure 18. "All I can tell you, was that the heavens were falling. And the sound... it was incredible. It was like the Gods were rejoicing for what was done."
Backspatter Material (BM)
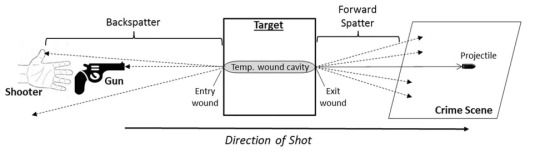
Figure 19. Distribution of Forward Spatter and Backspatter caused by a shot at a biological target. [1]
We hereby exclude the forward spatter, it is, the biological material projected fowards with the projectile (to the back of Nigel's head), for its little relevance, since we're not questioning the type of gun or ammunition used; we assume that Alex is describing a resonable scenario that matches with the actual damage done to Nigel. There are no consistent reasons to question this since everythings seems to support Alex's description of this.
BM comes from the combined forces of several interacting wound and ballistics effects. The collapse of the wound cavity and balance of resulting overpressure, the stream of liquid and tissue particles accelerated along the lateral surface of the projectile, the shot's contact and ejection of muzzle gases out of the entry wound from the powder cavity... Every surrouding surface must be investigated, that is, even the shotgun barrel's interior. This small ambience is fairly protected from external pertubations and houses BM from the shot. Considering the poximity with Nigel's face, we can almost assure to encounter biological material with DNA inside. The bellow mentioned study cites another work where a 9 mm pistol cointaned backspatter material from test targets even at a distance larger than 1 meter, much greater then the few inches that separated Nigel's face from the barrel. [1]
Matter of fact, this biological material can pass by processes of Organ Tissue Identification (OTI) and Body Fluid Identification (BFI) if Nigel's identity was at question, or if we desire to understand more profundly the projectile's damage caused to his skull/face/tissue. [1]

Figure 20. "None of what I've heard makes him a murderer."
So, how can we gather this up to develop the investigation? Utilizing only these two fundamental concepts, we can make a few assumptions.
The big question here is if whether or not Nigel's hands were present by Alex's when the trigger was pulled, which would lead the police to support or oppose Alex's narrative. Chemical examination with organic solvents (which won't cause preocupant harm to a dead body) and analytical methods could immediatly point to the presence of GSRs or biological/non biological BM. If Nigel's hands were elevated in his head level (or superior) in the instant of discharge, trace amounts of discussed metals/elements coming from the firing mechanism and ammunition, as weel as little to some biological material, would definetly be found in his hands and forearm skin since there was no clothing covering. Any substance found in his hands/forearm could be microanalytical compared to the ones present in Alex's hands, clothes and face as well. This could be done with really small samples of fresh skin. On the other hand, if Nigel's arms were lowered at the instant of discharge, we could still expect the presence of GSRs in his arms (yet, in less amounts) but the abssence of backspatter materials most certantly. This would classify Alex as a murderer without excuses, even if he alleged that Nigel asked for it.
In the scenario where Alex discharges at Nigel from a great distance (configuring simply murder) we could note the abssence of GSRs in every part of Nigel's body except for the targeted region (perhaps if they were at a greater distance to each other) and the presence of these GSRs in Alex, but in much higher concentration.
But the enviromnent's conditions are of primordial importance. Nigel and Alex stand in an open area, with considerable wind, heavy rain and gravel soil. The heavy rain could simply carry way much of these residues from Alex's body, clothes and Nigel's hands as well. Most GSR would probably be lost to those conditions and its deposite upon the soil's surface would be extremely hard to be quantitatively analized due to unknown degrees (elevated) of impurities and diverse materials and dirt present, but qualitative tests would still be valid.
The knowledge about the victim, crime scene, shooter, exact firegun and time of the tragic event allied with the fast action from authorities saves most of the police's efforts on identifiying and tracking down evidences. However, what remains still offers a challenge. The best evidence here, GSRs left by the discharge, would be of questionable help considering the presence of heavy rain in sight. Still, analitical quantities of them, if detected in Nigel's skin by proper chemical and espectroscopy-related analysis, can be used to comparate probable ammounts present in Alex's clothing and skin (despite the difficult of such). With that being said, the police would find themselves in a much more complex case of muder/assisted suicide, and further evidences and information about their relationship and recent whereabouts would ineviatably need to be extracted from external sources (such as parents, school's employess, close friends and students). Despite all this, Alex's final acting of removing Susan's body and disapearing from sight (not to mention the card left in Sally's car) immediatly sustent his guilt in a case where he already was the main suspect and basically confirmed criminal. And you know, breaking into a cemetery and extracting a corpse from its grave is definetly worth of some jail time. The Colbie's House Murder would certainly incriminate Alex for homicide as well, and the current Brotherhood's little political influence wouldn't prevent him from this destiny, as it appears. But the case is not over.
Further evidences were to be discussed, if it was not for the dissapearing of Alex Forbes.
The subject now roams unknowingly through England with mysterious intents. Its participation on the described case still lacks formal arguments and the Court should now approve his arrest warrant and search decree. Alex Forbes will most probably live to perpetrate the deluded fantasy responsable for the death of three young students in order to carry the sacred holy burden of an ancient templar bloodline.
Yet, we pray.


Who's the enemy now? We are.
4. Bibliography
[1] Euteneuer J, Courts C. Ten years of molecular ballistics-a review and a field guide. Int J Legal Med. 2021 Jul;135(4):1121-1136. doi: 10.1007/s00414-021-02523-0. Epub 2021 Feb 16. PMID: 33594457; PMCID: PMC8205864. [2] https://spotterup.com/how-ammo-works/ [3] Serol, M.; Ahmad, S.M.; Quintas, A.; Família, C. Chemical Analysis of Gunpowder and Gunshot Residues. Molecules 2023, 28, 5550. https://doi.org/10.3390/molecules28145550 [4] Guanchao Lan, Jing Li, Guangyuan Zhang, Jian Ruan, Zhiyan Lu, Shaohua Jin, Duanlin Cao, Jianlong Wang, Thermal decomposition mechanism study of 3-nitro-1,2,4-triazol-5-one (NTO): Combined TG-FTIR-MS techniques and ReaxFF reactive molecular dynamics simulations, Fuel, Volume 295, 2021, 120655, ISSN 0016-2361, https://doi.org/10.1016/j.fuel.2021.120655. [5] https://www.hunter-ed.com/national/studyGuide/How-the-Shotgun-Shoots/201099_92815/ [6] https://www.invaluable.com/auction-lot/era-410-ga-single-shot-break-action-shotgun-131-c-8284a72a5b [7] https://firearmland.com/item/1079096107 [8] https://www.letsgoshooting.org/resources/articles/shotgun/meet-the-shotgun/ [9] https://www.atf.gov/firearms/firearms-guides-importation-verification-firearms-ammunition-and-implements-war-top-break [10] Virginie Redouté Minzière, Céline Weyermann, Organic and inorganic gunshot residues on the hands, forearms, face, and nostrils of shooters 30 min after a discharge. Science & Justice, Volume 64, Issue 5, 2024, Pages 557-571, ISSN 1355-0306, https://doi.org/10.1016/j.scijus.2024.08.002. [11] Joshua Hallett, Michael Stolk, Michael Cook, K. Paul Kirkbride, Examination of gunshot residue arising from shotgun cartridges containing steel, bismuth or tungsten pellets. Forensic Science International, Volume 306, 2020, 110096, ISSN 0379-0738, https://doi.org/10.1016/j.forsciint.2019.110096. [12] https://www.bka.de/EN/OurTasks/SupportOfInvestigationAndPrevention/ForensicScience/PhysicalEvidence/Homicide/GunshotResidue/gunshotresidue_node.html [13] Francesco Saverio Romolo, Pierre Margot, Identification of gunshot residue: a critical review. Forensic Science International, Volume 119, Issue 2, 2001, Pages 195-211, ISSN 0379-0738, https://doi.org/10.1016/S0379-0738(00)00428-X. [14] Jalanti, T & Henchoz, P & Gallusser, Alain & Bonfanti, M.S.. (1999). The persistence of gunshot residue on shooters’ hands. Science & justice : journal of the Forensic Science Society. 39. 48-52. 10.1016/S1355-0306(99)72014-9.
Extra
random materials, take a look
1. Chemistry of Explosives (book pdf) https://link.springer.com/chapter/10.1007/978-1-4612-0589-0_5 2. ERA 410 GA video 1 https://www.youtube.com/watch?v=lGWm2aaWVAc&ab_channel=SteadFastCourage 3. ERA 410 GA video 2 https://www.youtube.com/watch?v=2S16C5Y6lxY&ab_channel=esquad540 4. Quick discussion about Smokeless Powder on r/guns https://www.reddit.com/r/guns/comments/1tawwm/things_i_want_you_to_know_about_smokeless_powder/#:~:text=Because%20of%20something%20called%20oxygen,and%20temperatures%2C%20leading%20to%20fouling. 5. A little on the kinetic energy of specific projectiles (everything applies here as well) https://nodoroc.com/d/node/20 6. A little more on ammunition Caliber https://www.globalsecurity.org/military/systems/munitions/bullets2-types.htm#google_vignette
For the sake of archieving, here are some shotguns I've separated to double check during my research until the Era 410 GA appeared. Curious enough, number 7, called "boito", appears to be another common name given to Era 410. Woops.
1. https://www.bidsquare.com/online-auctions/north-american-auction/victor-break-action-single-shot-12-ga-shotgun-4988316 2. https://www.crescentcityauctiongallery.com/auction-lot/stevens-arms-.410-gauge-single-shot-break-open-sh_9F84899825 3. https://palmettostatearmory.com/jts-shotguns-single-shot-410-bore-26-single-shot2.html 4. https://en.wikipedia.org/wiki/File:Stoeger-Coach-Gun.jpg 5. https://www.gunsinternational.com/guns-for-sale-online/shotguns/harrington-richardson-shotguns/h-r-bay-state-20-ga.cfm?gun_id=103017190 6. https://www.bankstowngunshop.com.au/product/12g-unknown-model-unknown-single-barrel-blued-wood-28-barrel-poor-condition/ 7. https://www.bankstowngunshop.com.au/product/410-boito-model-reuna-28-single-barrel-blued-timber-3-chamber-sec9622/ 8. https://www.bankstowngunshop.com.au/product/12g-harrington-richardson-model-1908-single-32-barrel-blued-wood/ 9. https://www.bankstowngunshop.com.au/product/12g-norinco-model-std-single-barrel-30-shotgun-great-condition/1 0. https://www.bankstowngunshop.com.au/product/12g-raick-freres-model-unknown-single-barrel-30-shotgun-belgium/ 11. https://gritrsports.com/henry-repeating-arms-single-shot-12ga-shotgun-h015-12 12. https://www.tmguns.co.uk/store/p1418/Tomas_Agote%2C_Eibar_12G_single_hammer_ejector_shotgun.html 13. https://www.tmguns.co.uk/store/p1659/Vanguard_Game%2FVermin_.410_hammer_ejector_single_barrel.html 14. https://www.tmguns.co.uk/store/p1290/Astra_Ciclope_12G_single_barrel_hammergun.html 15. https://www.tmguns.co.uk/store/p1883/Rossi_Game%2FVermin_20G_single_hammer_ejector_shotgun.html 16. https://en.wikipedia.org/wiki/File:Stevens_511_Shotgun.jpg 17. https://www.gunsinternational.com/guns-for-sale-online/shotguns/harrington-richardson-shotguns/harrington-richardson-44-smoothbore.cfm?gun_id=102901609
thank you for reading

#like minds#murderous intent#nigel colbie x alex forbes#nigel colbie#alex forbes#forensic science#analysis#Spotify
27 notes
·
View notes
Text
It's shit like this that people are using in their claims that there is conclusive evidence of genocide which pretty clearly demonstrates how the evidence they're working with is fundamentally contradictory, flawed and at times nonsensical.
Israel is not "evaporating" bodies with some kind of magical super-weapon. This is gibberish. This guy claims the reason why they aren't continuing to report casualties is because Israel bombs are evaporating bodies. Which would violate the first and second laws of thermodynamics.
The first being vaporizing all traces of evidence, the second being that entropy would decrease as particles decrease. And entropy increases, not decreases. Particles are prone to disperse, they don't magically vanish (with the exception of electrons which have been observed to jump forwards and backwards through time, but not on a macro scale large enough that it impacts how solid objects are).
We do not have weapons anywhere on Earth that can vaporize a human being without leaving a trace. I find it more reasonable that these people are trying to communicate that bodies are being burned, and so they don't have the technology available to keep track of the dead.
But that isn't what they say, instead they claim Israel must have developed a new technology that vaporizes people and leaves no trace of said vaporization (which even if we did vaporize a person there would still be evidence). And yet this would be no different to any other conventional warfare where bombs are being used, and people do not make the same claim that Russia bombing entire cities to rubble is conclusive evidence of genocide.
Even in the Shoah with the crematoria we have forensic evidence of human remains. In the same article they blame Israel for "empowering" looters to steal aid, without bothering to explain how that is done, by who, and shifting the responsibility from Hamas going in and stealing aid, to saying "oh well they are stealing it but that's Israel's fault."
It would be like saying it's the DEA's fault that drug cartels in Mexico are using machetes to behead people and smuggling drugs into the USA. The DEA is fighting against the cartels, and you're now shifting the responsibility of the cartel's behavior which they could stop at any time, to the the DEA for basically not fighting against them good enough?
They also make the claim that Israel intentionally targeted these refugee tents, but fail to mention that the reason why a fire broke out is because Hamas was storing weapons there (which would mean that the cause of the fire wasn't Israel's strike, it was Hamas storing weapons, and it would also mean that the strike was legal [I don't agree with the strike, that isn't what I meant by my prior word "valid," I just meant Legal] because storing weapons there removes the protection under the Geneva Convention).
So when I say we shouldn't say there is conclusive proof of genocide, this is what I am talking about. These things are not conclusive, they are circumstantial.
What we want to do is arrest all the people in charge, put them on trial, present every bit of data that we have, and then see whether or not it rises to the definition of genocide. Or even whether or not it's appropriate to expand the definition so that these things can be prosecuted not only in Israel's case but in every other case like Russia and China.
Then we will be able to say yes we have conclusive proof.
69 notes
·
View notes
Text
Paper cuts
|Jelsa, Modern AU, Enemies with Benefits, Fake dating, Forced Proximity|

Agent Elsa Stenford [NID-SO-ES-07] — Operation Report Upload Log
—Logged into secure terminal: Vienna Safehouse Terminal-2
—Date: 2022-07-08
—Time (UTC): 23:16
—Connected to secure node: NIDNet
—Report file: OP_SILENTRAVEN_AAR.enc
—Encryption status: Secured with NID Master Key — encryption signature verified (Checksum ID: F1A5-7C9B)
—Recipient(s): Jack Frost, Section Chief Special Operations (SO-92A), Acting Division Supervisor (DS-4), National Intelligence Directorate
—Transmission channel: Priority-One Secure Uplink (Classified Level: TOP SECRET)
—Transmission status: COMPLETE — audit log updated (Reference Log ID: ES07-0525-2214)
—Backup status: Encrypted local backup stored (Partition ES-07-SAFE); master copy uploaded to Central Ops Archive (Vault-4)
—Field confirmation: Agent ES-07 signed digital attestation; no tampering detected; self-authentication successful
Note: Automatic alert dispatched to Division Supervisor terminal. Clearance authentication required upon access.
---------------------------
Operation Silent Raven is an ongoing mission targeting a covert illicit arms trafficking network operating primarily in South Carolina. [Flag—Acting supervisor: Delete ‘ongoing mission’ — this is filler from someone unfamiliar with concise reporting. Vague and redundant.] This report details recent operational progress, intelligence collection, and actionable recommendations. [Flag—Acting supervisor: You clearly do not understand report structure. This useless sentence wastes time and space.]
The primary objective is to identify, monitor, and dismantle the arms trafficking chain responsible for the flow of small arms and light weapons through various transit points in the region. [Flag—Acting supervisor: Restating obvious without any specifics or measurable targets reflects poor understanding of operational goals. Omit.] HUMINT sources have verified the existence of a new maritime transit corridor utilizing the seaport. [Flag—Acting supervisor: “HUMINT sources” is lazy projection. You apparently cannot be trusted to identify sources properly. Brackets demonstrate careless drafting.] SIGINT intercepted encrypted communications that suggest coordination between traffickers and local facilitators. [Flag—Acting supervisor: ‘Suggest’ is weak speculation, unbefitting a professional intelligence report. Either confirm or remove this guesswork.]
Financial forensics have traced suspicious funds transfers totaling approximately $8 million USD linked to traffickers. [Flag—Acting supervisor: Provide specifics or this bland, meaningless statement reveals superficial analysis.] Technical surveillance detected multiple covert meetings in [Urban Centers], corroborated by photographic evidence. [Flag—Acting supervisor: Using placeholders signals either incompetence or utter disregard for accuracy.] On 2022-06-21, interdiction team, operating with local law enforcement, seized 250 illegal firearms at the port city warehouse. [Flag—Acting supervisor: Poorly structured sentence; the muddled passive voice further obscures the facts you apparently cannot clearly present.] Two principal suspects were detained, providing critical intelligence that identified higher-level facilitators. [Flag—Acting supervisor: Passive construction and vague attribution further demonstrate your failure to take ownership of this data.]
Informant “Falcon” supplied actionable intelligence regarding a planned arms shipment scheduled for early June. [Flag—Acting supervisor: Finally, a clear statement, but unfortunately, it’s buried among verbosity and filler.] Operational security protocols were heightened after detecting possible surveillance by hostile intelligence actors. [Flag—Acting supervisor: ‘Possible’ surveillance indicates your uncertainty and it undermines the entire assessment and betrays inadequate situational awareness.] The network disruption has temporarily halted major arms transfers. [Flag—Acting supervisor: ‘Temporarily’ suggests you lack the insight or confidence to forecast outcomes. Such ambiguity is unacceptable.]
Surveillance and intelligence collection continue focusing on secondary facilitators and financing channels. [Flag—Acting supervisor: Non-specific, passive phrasing again. You appear unable to report with decisiveness or clarity.] Coordination with allied intelligence agencies is ongoing to leverage broader interdiction efforts. [Flag—Acting supervisor: “Allied intelligence agencies” — weak and meaningless. Omit.] Risk assessment indicates elevated threat levels against NID assets involved in this operation. [Flag—Acting supervisor: Without elaboration, this statement is worthless. The absence of detail is either negligence or incompetence. I’m leaning towards the latter, although the first one also seems to be your defining trait.] Approve expansion of covert operations targeting secondary facilitators and financiers. [Flag—Acting supervisor: Recommendations lack essential resource planning and rationale, further exposing your inexperience.] Request additional SIGINT and counter-surveillance resources. [Flag—Acting supervisor: ‘Additional’ is meaningless without quantification. This sloppy request reflects poor operational understanding.] Initiate an inter-agency task force to address cross-border financing and logistics. [Flag—Acting supervisor: Unsubstantiated recommendation with no defined objectives — this is amateurish.] Continue monitoring and protection of key HUMINT sources and operatives. [Flag—Acting supervisor: Failing to specify protection protocols reflects a dangerous oversight on your part.] Attachments include interdiction team after-action report, financial transaction analyses, SIGINT intercept summaries, and photographic documentation of seized arms and facilities. [Flag—Acting supervisor: Referencing attachments without actual inclusion indicates either incompetence or disregard for proper reporting. Which one is it?]
Flag—Acting supervisor: This report is miserably inadequate and reflects a disturbing lack of professionalism and capability. The careless placeholders, vague assertions, passive voice, and speculative language betray your failure to grasp even the basic standards of intelligence reporting. Such work not only wastes time but actively hampers operational efficiency. REWRITE.
---------------------------
Secure Directive
From: Jack Frost
[Code: NID-SO-JF-01]
Section Chief, Special Operations / Acting Division Supervisor [Code SO-92A/DS-4]
To: Agent Elsa Stenford [Code:NID-SO-ES-07]
Subject: RE: Report Review – Operation Silent Raven
Classification: TOP SECRET // EYES ONLY
Agent Stenford,
Your submitted report for Operation Silent Raven is wholly inadequate and reflects a concerning lack of analytical rigor, operational discipline, and professional attention. The presence of unresolved placeholders, vague assertions, speculative conclusions, and critical data gaps is unacceptable at this operational level and wastes valuable time and resources.
This level of oversight is incompatible with the standards expected from an intelligence officer assigned to this unit. You are to:
1. Eliminate all placeholders and provide verified, cross-checked intelligence.
2. Remove speculative or assumptive language; include only confirmed, actionable data.
3. Rewrite sections for clarity, precision, and direct accountability — passive formulations are unacceptable.
4. Deliver detailed, concrete descriptions of sources, operational locations, timelines, and outcomes without ambiguity.
5. Ensure all referenced materials are attached, properly labeled, and internally consistent.
6. Strengthen recommendations by specifying exact resource needs, operational impacts, and executable directives.
7. Fully address risk assessments with defined threats, probability ratings, and specific mitigation strategies.
The supervisor-annotated version of your report (File ID: SR-Report-Rev1-JF) has been uploaded to the secure review system. You are to address all marked corrections and resubmit the fully corrected report no later than 1800 hours today. No further extensions will be granted.
Jack Frost
[Code: NID-SO-JF-01]
Section Chief, Special Operations (SO-92A)
Acting Division Supervisor (DS-4)
National Intelligence Directorate
---------------------------
Agent Elsa Stenford [Code: NID-SO-ES-07] — Report Upload Log (Revised Submission)
—Logged into secure terminal: Vienna Safehouse Terminal-2
—Date: 2022-07-09
—Time (UTC): 17:38
—Connected to secure node: NIDNet
—Report file: OP_SIENTRAVEN_AAR_v2.enc
—Encryption status: Secured with NID Master Key — encryption signature verified (Checksum ID: F1A9-7C3B-R2)
—Recipient(s): Jack FrostJack Frost (NID-SO-JF-01), Section Chief Special Operations (SO-92A), Acting Division Supervisor (DS-4), National Intelligence Directorate
—Transmission channel: Priority-One Secure Uplink (Classified Level: TOP SECRET)
—Transmission status: COMPLETE — audit log updated (Reference Log ID: ES07-0525-2316-R2)
—Backup status: Encrypted local backup stored (Partition ES-07-SAFE); master copy uploaded to Central Ops Archive (Vault-4, Revised Submission Folder)
—Field confirmation: Agent ES-07 signed digital attestation; no tampering detected; self-authentication successful
Note: Automatic alert dispatched to Division Supervisor terminal. Clearance authentication required upon access. Revision flag registered under Audit Protocol 4B.
---------------------------
Secure Directive
From: Jack Frost [Code: NID-SO-JF-01]
Section Chief, Special Operations / Acting Division Supervisor [Code: SO-92A/DS-4]
To: Elsa Stenford [Code: NID-SO-ES-07]
Subject: RE: Secure Directive – Operation Silent Raven Report (Revised Submission)
Agent Stenford,
I have completed my review of your revised report on Operation Silent Raven. The annotated document is attached under:
Attachment: SilentRaven_Rev2_ES07_JFcomments.secure
To be precise: this submission remains below acceptable operational standards. Your continued use of speculative phrasing, unsupported assertions, and vague recommendations demonstrates a concerning lack of analytical discipline. This is not a matter of inexperience. You are not a trainee, Agent. At your level and position, you are expected to understand and apply the standards of rigor, precision, and clarity required in all agency reporting. That expectation is not optional.
Your report exhibits repeated failures:
1. Speculative language where concrete analysis is required;
2. Lack of referenced source attachments, despite multiple directives;
3. Unquantified risk assessments, absent methodological support;
4. Action recommendations devoid of operational specificity.
This is not a learning exercise nor is it a second chance, Agent Stenford. I should not be required to remind you of the foundational protocols governing intelligence reporting. You are expected to deliver work that reflects your clearance level, your operational rank, and your assigned responsibilities — without need for remedial oversight.
You are hereby directed to produce a final, fully compliant, actionable revision and submit it under secure protocol no later than 1300 hours tomorrow. Failure to meet this directive will result in formal escalation to the Division Office for immediate performance review. There will be no further instructions, no extended clarifications, and no tolerance for repeated submission failures.
Jack Frost [Code: NID-SO-JF-01]
Section Chief, Special Operations (SO-92A)
Acting Division Supervisor (DS-4)
National Intelligence Directorate
*
Operation Silent Raven: A report
1. Executive Summary:
—The target group’s network activity has intensified in the last 72 hours, with encrypted communications suggesting a planned operation within the capital region. [Flag—Acting supervisor: “Suggesting” is a charming euphemism for “guessing.” Precision is not your forte, is it?]
—HUMINT sources indicate the possible involvement of an external actor, potentially destabilizing regional security. [Flag—Acting supervisor: “Possible” and “potentially” — a truly inspiring display of hedging. I applaud your commitment to ambiguity.] While these indicators warrant heightened surveillance, conclusive evidence regarding the exact nature and timing of the planned event remains unconfirmed. [COMMENT: I look forward to the day when ‘unconfirmed’ is replaced by ‘confirmed.’ Continue taking baby steps, we’re all here to babysit you and instruct on every level, not to do our job.]
2. Intelligence Sources:
SIGINT: Intercepted encrypted transmissions on frequencies 8.1 GHz to 8.3 GHz, believed to originate from multiple cell towers in the downtown sector. [Flag—Acting supervisor: “Believed.” A masterclass in non-committal language. Bold. Yet, it fails to meet the minimum standards of verification.] Metadata analysis aligns with previous hostile activity patterns.
[Flag—Acting supervisor: Please specify the parameters of your analysis. Otherwise, it reads as a hopeful suggestion rather than intelligence.]
HUMINT: Confidential informant reported unusual meetings near industrial sector 4. Reliability assessed as moderate; corroborating SIGINT incomplete. [Flag—Acting supervisor: ‘Moderate’ is an imaginative way of saying ‘I’m not sure.’ The agency appreciates your creativity but prefers facts.]
IMINT: Limited satellite imagery from 23-25 MAY shows increased vehicular movements near potential staging areas, but imagery quality insufficient for identification of personnel or equipment. [Flag—Acting supervisor: Including non-identifiable imagery is an excellent way to fill pages. Whether it aids operations is another matter. But who cares?]
3. Operational Assessment:
The convergence of SIGINT and HUMINT suggests preparatory steps for an operation targeting critical infrastructure. [Flag—Acting supervisor: ‘Suggests’ again. I see a pattern. Perhaps next time try ‘confirms’ or ‘demonstrates.’] Risk assessment places the likelihood of attack at moderate (probability 0.55), with potential impact categorized as high due to target significance. [Flag—Acting supervisor: : Quantify your methodology. Numbers plucked from thin air are less useful than no numbers at all.] Recommended actions include intensifying electronic surveillance, deploying field assets for direct observation, and liaising with allied cyber-intelligence units to monitor digital footprints. [Flag—Acting supervisor: Vague directives are the hallmark of an inexperienced analyst. Details and accountability please.]
4. Recommendations:
Immediate deployment of SIGINT intercept teams in the identified frequency bands. Enhanced HUMINT debriefings with source ES-27 to confirm meeting details. [Flag—Acting supervisor: The lack of specificity here suggests an admirable level of trust in the reader’s imagination.] Coordination with Cyber Ops for real-time network traffic analysis. [Flag—Acting supervisor: Nomenclature alone does not constitute a plan. Flesh this out.]
Notes [Acting Supervisor] :
—Formatting inconsistent with NID operational report guidelines. You’ve transformed a simple formatting standard into an elusive art form. Bravo.
—Failure to attach referenced supporting materials AGAIN. This recurring omission hinders operational efficacy. Consider attaching documents next time.
—In conclusion, REWRITE.
---------------------------
Agent [Code: NID-SO-ES-07] — Field Report Upload Log (Revised Submission)
—Logged into secure terminal: Vienna Safehouse Terminal-2
—Date: 2022-07-10
—Time (UTC): 13:00
—Connected to secure node: NIDNet
—Report file: OP_SILENTRAVEN_AAR_v3.enc
—Encryption status: Secured with NID Master Key — encryption signature verified (Checksum ID: F1A9-7C3B-R2)
—Recipient(s): Jack Frost, Section Chief Special Operations (SO-92A), Acting Division Supervisor (DS-4), NID
—Transmission channel: Priority-One Secure Uplink (Classified Level: TOP SECRET)
—Transmission status: COMPLETE — audit log updated (Reference Log ID: ES07-0710-1300-R2)
—Backup status: Encrypted local backup stored (Partition ES-07-SAFE); master copy uploaded to Central Ops Archive (Vault-4, Revised Submission Folder)
—Field confirmation: Agent ES-07 signed digital attestation; no tampering detected; self-authentication successful
Note: Automatic alert dispatched to Division Supervisor terminal. Clearance authentication required upon access. Revision flag registered under Audit Protocol 4B.
---------------------------
Secure Directive
From: Jack Frost [NID-SO-JF-01]
Section Chief, Special Operations / Acting Division Supervisor [Code: NID-SO-92A/DS-4]
To: Elsa Stenford [Code: NID-SO-ES-07]
Subject: RE: Secure Directive – Operation Silent Raven Report , Revocation of Field Authority and Immediate Reassignment
Agent Stenford,
I was informed last afternoon that due to shifting operational priorities, the report in question [Ops Silent Raven] is no longer required.
After review of your latest submission — the revised report you provided earlier today — I must formally acknowledge that the material remains below acceptable operational standards. While I did not realistically anticipate any significant improvement, it is nonetheless disappointing that even after detailed corrective input, your output failed to meet the basic analytical and procedural thresholds expected of an intelligence officer at your level.
However, the time I was forced to expend personally correcting and annotating your repeated errors constitutes an unacceptable diversion of supervisory resources. You have now occupied more of this division’s time and attention than your current role warrants.
Accordingly, effective immediately, your independent field authority is revoked. You are reassigned to trailing support under Intelligence Officer Logan Parrish [CODE: NID-SO-LP-33], Team Blue. While Officer Parrish holds the same formal rank as you, his superior reliability and competence justify his lead role in this arrangement.
You are to operate strictly under Officer Parrish’s direction, with no independent decision-making or external communications without prior clearance. This corrective assignment will remain in place until further notice and serves as a necessary intervention to address the persistent deficits in your performance.
You are to report to Team Blue at 07:00 hours tomorrow, prepared and fully compliant. Written acknowledgment of this directive is required by 16:00 hours today. Noncompliance will result in immediate formal disciplinary action.
Jack Frost [Code: NID-SO-JF-01]
Section Chief, Special Operations (SO-92A)
Acting Division Supervisor (DS-4)
National Intelligence Directorate
---------------------------
Elsa Stenford read the message over and over again, because she knew it wasn’t serious. It must be a mistake. A joke. That’s what it was. Maybe if she read it again, it would change, it would shift and it would fix itself. So she read it, the words physically burning her, over and over again, but it stayed the same. She just stared at it, mouth hanging open, eyes wide with shock, unblinking.
“Elsa?” Merida’s voice shattered the silence in her head. “Are you—”
“THAT MISERABLE FUCKING BASTARD! THAT FUCKING—” She stopped herself, but there was just too much rage and hate in her, enough for her to combust and paint the walls red. "FUCKING PIECE OF SCUM! I FUCKING HATE HIM, THAT USELESS, ARROGANT, SLIMY RAT!"
---------------------------
#jelsa#jelsa in 2025#jelsa fanfiction#jelsa au#jack frost#queen elsa#frozen#rise of the guardians#ao3#rotg#rotg jack frost#disney frozen#elsa frozen#jackson overland frost#elsa x jack frost#jack frost x elsa#enemies to lovers#enemies with benefits#workplace#forced proximity#ao3 fanfic#anna frozen#kristanna#frozen fever#merida dunbroch#angst#merida#brave#rotbtd#disney
23 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
24 notes
·
View notes
Text
Object permanence

Picks and Shovels is a new, standalone technothriller starring Marty Hench, my two-fisted, hard-fighting, tech-scam-busting forensic accountant. You have TWO DAYS LEFT to pre-order it on my latest Kickstarter, which features a brilliant audiobook read by Wil Wheaton.

#20yrsago What if Bill Gates hired Linus Torvalds? https://web.archive.org/web/20050207155531/https://www.wired.com/wired/archive/13.02/microsoft_pr.html
#15yrsago Rogers Canada forces Android update that takes away root access https://mobile.slashdot.org/story/10/01/26/2358237/Canadian-Android-Carrier-Forcing-Firmware-Update
#15yrsago Sane copyright doesn’t treat all copying as the same https://www.theguardian.com/technology/2010/jan/26/copyright-cory-doctorow
#15yrsago ACTA: the leaked secret memos https://web.archive.org/web/20100130005036/https://www.michaelgeist.ca/content/view/4730/125/
#10yrsago Plan C: The top secret Cold War plan for martial law in the USA https://www.muckrock.com/news/archives/2015/jan/26/plan-c-top-secret-cold-war-battle-plan-bring-unite/
#10yrsago Google strong-arms indie musicians into accepting brutal, crowdfunding-killing deal for streaming service https://zoekeating.tumblr.com/post/108898194009/what-should-i-do-about-youtube
#10yrsago Great Firewall of Cameron blocks sex-abuse charities https://www.theguardian.com/technology/2015/jan/24/internet-filters-block-sex-abuse-charities
#10yrsago The Haunted Mansion was almost the Tiki Room https://longforgottenhauntedmansion.blogspot.com/2015/01/walt-disneys-enchanted-creepy-room.html
#5yrsago Two years after a federal law banning shackling women during childbirth was passed, prisoners in America are still giving birth in chains https://www.theguardian.com/us-news/2020/jan/24/shackled-pregnant-women-prisoners-birth
#5yrsago Andrew Cuomo’s naked hostility drives out MTA president Andy Byford, the “Train Daddy” who has transformed the world’s rail systems https://www.railwayage.com/passenger/you-blew-it-andrew-cuomo/
#5yrsago Fatal car wrecks are correlated with stock-market fluctuations https://www.sciencedirect.com/science/article/abs/pii/S0167629619301237
#5yrsago Banks have returned to the pre-2008 world of automatic credit-limit increases for credit cards used by already indebted people https://www.bloomberg.com/news/articles/2020-01-23/banks-are-raising-credit-card-limits-without-asking-customers
#1yrago The long sleep of capitalism's watchdogs https://pluralistic.net/2024/01/26/noclar-war/#millionaire-on-billionaire-violence

Check out my Kickstarter to pre-order copies of my next novel, Picks and Shovels!
8 notes
·
View notes
Text
Z-lister joined the Meghan Markle-led Sisterhood tearing down perfect Princess Kate with nonsensical spray about the future Queen by u/EleFacCafele
Z-lister joined the Meghan Markle-led ‘Sisterhood’ tearing down perfect Princess Kate with nonsensical spray about the future Queen “Wow, she’s really been getting stuck into those Marlboro cigarettes” was not a thought that crossed my mind when I saw images of a solemn Princess of Wales at London’s Remembrance Day service recently.Instead, like any decent and mature person, I was mesmerised by her bravery.Again. The Princess didn’t need to stand poised and reflective as she watched the wreath-laying ceremony. Wouldn’t any other exhausted 40-something mother-of-three, understandably nervous about every future blood test, give obligation a hard pass? wreath-laying ceremony. ‘To Di For’ Podcast host Kinsey Schofield has blasted Narinder Kaur for “attacking” Princess Kate’s physical appearance.But the constantly-scrutinised Kate put duty first.Meanwhile a wannabe celebrity in the UK called Narinda Kaur thought this would be the perfect time to post on X: “Genuine question – why has Kate aged so much? Isn’t she only 42? Is she a smoker? It’s the only explanation.”Sure, there was plenty of back peddling to follow because condemnation was swift, so much so that Kaur, 51, says she contacted police over the “sexual, racist and violent” abuse she received. Notwithstanding, other female keyboard warriors unleashed, triggering a digital blizzard of icy, bitchy “gosh Kate’s aged”-style commentary.Kaur said a stupid thing by trolling the Princess’s visage and she knows it, however I don’t buy her excuse that the “stupid” thing was to ask about ageing. Ergo, lest Kaur and others be reminded that is not a capital crime to age and in fact look older.But let’s address the real issue here.Following the balcony appearance from the royal, Narinda Kaur posted on X: “Genuine question – why has Kate aged so much? Isn’t she only 42? Is she a smoker? It’s the only explanation.” Picture: ITVEvery time former chemo patient Kate steps out in public and pauses in the forensic glare - and how her heart and stomach must sink at this - you can feel the swell of inane analysis.How sick does she look today?Why is she wearing that catwalk-level mascara and smokey eyeshadow? Are those tears in her eyes?Is that all her own hair? Didn’t she look a little chunkier around the middle last time she wore a fitted, wool coat by her favourite designer Catherine Walker?So.What will it take for a certain type of woman, often the same ones circling the Z-list drain, to lay off and let her be?It is bewildering that some women find Kate’s dual humility and polish such a trigger that they spew out anything, smug in the knowledge that their algorithm will get a bump and she won’t respond.And there’s been nigh on 12 months of this. You’ll recall how last December, Meghan Markle did not step up to defend her sister-in-law over claims in an ‘Endgame’ book translation that she, along with Charles, questioned Archie’s skin colour.For all her “truth” bombing, Meghan has let that one fester.And fester.It remains one of the Duchess’s most egregious acts in my view.Then in March, Kim Kardashian, Blake Lively and others were falling over themselves to exploit the trending ‘Where Is Kate’ narrative for their own nefarious business objectives before issuing breathless apologies.The wife of the future monarch was absent from public life and no one knew why.see the whole article: https://ift.tt/nWP6oBF post link: https://ift.tt/LE1f2ck author: EleFacCafele submitted: November 17, 2024 at 08:58AM via SaintMeghanMarkle on Reddit disclaimer: all views + opinions expressed by the author of this post, as well as any comments and reblogs, are solely the author's own; they do not necessarily reflect the views of the administrator of this Tumblr blog. For entertainment only.
#SaintMeghanMarkle#harry and meghan#meghan markle#prince harry#fucking grifters#grifters gonna grift#Worldwide Privacy Tour#Instagram loving bitch wife#duchess of delinquency#walmart wallis#markled#archewell#archewell foundation#megxit#duke and duchess of sussex#duke of sussex#duchess of sussex#doria ragland#rent a royal#sentebale#clevr blends#lemonada media#archetypes with meghan#invictus#invictus games#Sussex#WAAAGH#american riviera orchard#EleFacCafele
9 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Text
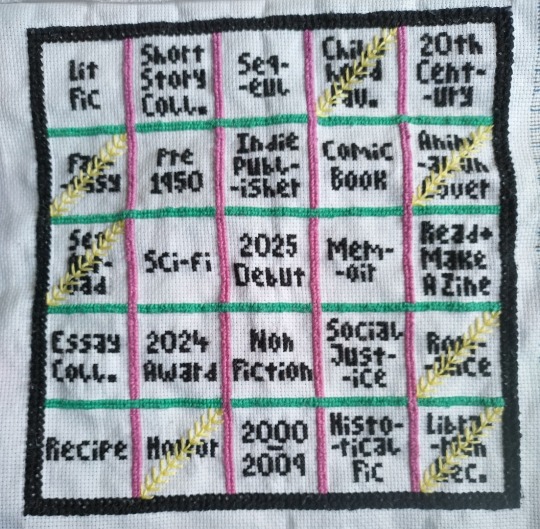
Finished Trace Evidence this morning, and that is officially the 7th square - Childhood Favourite - crossed off on my bingo board for @batmanisagatewaydrug's 2025 Book Bingo.
Technically, I was finished a bit ago because I finished Virals by Kathy Reichs a bit ago, but I goddamn adore this series and I just had to reread the entire Virals series.
There are 5 books (Virals, Seizure, Code, Exposure, and Terminal) and 4 short stories (Shock, Shift, Swipe, and Spike) collected within the book Trace Evidence. And there is no way for me to even remotely review this series or just talk about it objectively. Reading it fundamentally changes me as a person as in like, I have a degree in psychology as a result of reading this book.
It was honestly a little revealing for me, rereading this series. Like I did not realise how many of my writing quirks came from the way Kathy Reichs writes, maybe including my love of epistolary storytelling. This book feels like a window into my soul almost. I felt vulnerable reading it at times though other times I was overjoyed, making notes like "hi my beloved" and "chance my boy!"
At its bones, the Virals series is about four kids and their dog solving mysteries. There's a lot of Scooby Doo vibes (another one of my childhood favourite things) like these are The Meddling Kids™ to rival all others (which is kinda the plot of Terminal), but they do commit several more felonies than I remember happening on Scooby Doo. Within our gang - or more accurately, pack - there's Tory (Tory's the grand-niece of Temperance Brennan for anyone who's read Reichs' other books or seen Bones), Shelton, Hiram, Ben and Tory's wolfdog Cooper.
I adore all four of them and almost every other character in the series from clueless dad Kit to a bit confused but got the spirit Whitney to terrible awful Chance to reformed girlboss Madison to definition of shit floats upward Corcoran to the girl Tory definitely doesn't have a crush on Ella to anyone and everyone in the series.
Hiram is my favourite though. At least half of the notes I made and sections I highlighted while reading were about him, including one reading simply "beloved rat man". Hi is hilarious and he would do numbers on Tumblr like this guy wins in the jester off. He'd have a Goncharov poster in his room and would have Opinions™ on the fairy walrus debate. He is one for malicious compliance also, wearing his blazer inside out at school because he's still technically wearing the uniform.
The series has its issues from period-typical misogyny to sometimes being weird in how it talks about Ben being Native American to some forensic science inaccuracies to sometimes creeping toward fatphobia though it falls closer to body neutrality imo. Also it implies telepathy could be gained via epigenetics. It's not perfect, but it's so close to my heart that it's basically entwined in my DNA.
Inma close it with a quote from every book in the series:
"I ran my eyes up 160 feet of crumbling stone, a bleak, solitary spike surrounded by ocean on all sides. Dark and empty, the structure seemed to brood. Resentful at being abandoned? At losing its battle with the elements?
It’s the most depressing thing ever, I thought."
-Virals
"“Then why are you here? Did you break the law?” “Yes. Quite a few.” I held up a hand. “But for a good cause!” Kit’s brow wrinkled in confusion. “But you’ve been grounded all week.”"
-Seizure
"The Gamemaster’s face was granite, but the tic was a giveaway. I could tell he struggled to contain his fury.
“The world is insane,” he hissed. “I just help it dance.”"
-Code
"Without Tory, we three bozos were flying blind. No, worse than that—we couldn’t even locate the airplane."
-Exposure
"No, the anger was at myself. For acting like a spoiled brat. For being incapable of the simple human decency of congratulating two happy people. For bringing the shadow of my mother into their moment. The tears came then. Hot and fast, in a torrent unaccompanied by words. I didn’t want to think about Mom. Then hated myself for it. If I didn’t remember her, who would? I was all she’d had. We were all we’d had. And what had I reduced Mom to? A club to smash my father’s happiness. To batter Whitney, who’d never even met my mother, and had been at Kit’s side since before I’d appeared. Sobbing, I curled into a ball. Shoved my face in a pillow. Coop’s frigid nose pressed against my arm, and I gathered him in, too. He wiggled close, nestling his furry head in my chest. We lay like that until the tears ran dry."
-Terminal
"Shelton stood, handed Tory the padlock. “There.” Shaking his head. “One more B and E for my juvie record. I’ll never be president.” “Pssh.” I flapped a hand. “The Oval Office is perfect for a criminal like you.”"
-Shift, within Trace Evidence
#kai rambles#2025 book bingo#bookblr#weird coincidence that two of the books on this bingo were titled Viral and Virals#but one was substantially better than the other#anyway i love this series so much#it was the exact book i needed to read as a nerdy 13 year old whod been bullied for being nerdy and for not being girly enough#also its surprisingly diverse for a series that began in 2010?#like shelton is mixed race with a black dad and a japanese mom#hi is jewish and notably fat but never unable to do things the other virals can#and ben is native american which comes into play in seizure#though i dont know how accurate it is#also its set in south carolina and the book is immediately like fuck the confederates#its also not got a positive view on the rich which is fair enough#also i love kit and whitney so much#whitney is trying so hard and she stumbles a lot but she gets there in her own way#and kit has been a father for like five minutes and hes really trying to figure this whole parenting thing out#hes stumbling a lot more than whitney but hes trying so damn hard#hes like ''youre grounded'' and then does nothing to make sure his daughter does not sneak out
3 notes
·
View notes
Text
The smell of someone’s hand can reveal if they are a man or a woman, a study has found.
Key components in body odour are increasingly being used by scientists to unpick a person’s identity, with age and ethnicity already able to be determined by smell alone.
Now, research from Florida International University found that machine analysis was able to tell with 97 per cent accuracy the gender of a person from a swab of their hand sweat.
It opens the door for law enforcement to be able to use scent recognition to find criminals at some point in the future. However, the scientists say the work is still in its early stages and more analysis is needed to rectify the findings before the technique is used by police forces.
The hope is that a hand mark, which does not have any DNA or fingerprints, could still be used to help identify a perpetrator.
15 key chemicals
“We identified 15 key chemicals, and seven were the most important in differentiating females from males,” study author Dr Kenneth Furton told The Telegraph.
“To date we still cannot say what men and women in general smell like but we can say that they smell different chemically and we are now closer to discovering which chemicals are responsible for that difference.”
Dogs have long been used in criminal investigations to reliably identify and track people based on their odour, but replicating the hyper-sensitive nature of the canine nose with a machine in a lab has proved difficult.
Scientists used a technique called mass spectrometry to analyse the scent compounds present on the palms of 60 people – half male and half female.
Participants were asked to squeeze a piece of sanitised material for ten seconds and their skin secretions were then taken from the absorbent pad and put into a machine.
Odour ‘barcodes’
The scientists found odour “barcodes” which each person possesses that is unique to them and found they were able to pull apart male and female individuals based on the olfactory signature.
“Criminal activities involving robberies, assaults (sexual, simple, or aggravated), and rape are often executed with the use of the perpetrator’s hands,” the scientists write in their study.
“As a result, hands are a focal point of investigations as contributors of trace amounts of evidence that can be deposited on everyday objects through touch interactions.
“There is an exchange of both biological and inorganic material between the perpetrator and the crime scene during these interactions.”
Trace evidence
They add that the interaction and contact between a criminal and victim, or the crime scene, will leave behind trace evidence, but sometimes in quantities too small to help solve the crime.
“Fingerprints and DNA are the biometrics most commonly utilised to identify a suspect or victim of a crime,” the team continues.
“However, these forms of evidence can be found in quantities that are too small to be used, leaving little to no forensic evidence that can be used for prosecution.
“Even in these instances where no physical fingerprint or DNA evidence is found, human scent evidence may still be recovered and used as an individualising feature in an investigation.
“Though previous works have revealed this using an individual’s human scent from either breath or armpit, this study expands on this capability using hand odour which may be of great forensic value.”
According to the study, published in PLOS ONE, the analysis successfully predicted a person’s sex with a 96.67 per cent accuracy rate.
Sexual arousal
Studies are increasingly learning more about the role of human scent and how it may be detected not only by machines but by people too.
One study recently found the chemical makeup of a person’s exhaled breath changes when in a state of sexual arousal and it could be picked up by others around them.
Researchers from the Max Planck Institute of Chemistry found a noticeable spike in three chemicals called indole, cresole and phenol during arousal. There was also a significant drop in the level of CO2 and another molecule called isoprene.
Prof Jonathan Williams, the lead researcher, also found last year that humans have an invisible aura around our bodies which could be cleaning the air we breathe.
A study found that an invisible haze of air-cleansing molecules is produced on human bodies when ozone in the air reacts with oil made by our skin.
62 notes
·
View notes
Text
Christian loves frogs the way he loves most things.
TW: Implied Animal Death.
Back in highschool Chris had a group of. Idk. Associates. He didn't really have friends at all, until highschool, since he was homeschooled by his mother until she left her husband and couldn't convince Chris to leave with her. (And break the law? Goodness. He's not crook. Not even for his mother.)
He's fifteen when he starts going to a pretty nice private school. Everyone there is... Fine. Chris really would've preferred a Catholic school, but he didn't have a say in the matter. He was the son. Children listen to their parents. Children should always listen. And sit still. And be good.
Christian is popular. He gets great grades, he's polite, and he knows how to smile when people want to see a smile. It helps that he's handsome. There's asinine classroom chatter, and Christian can usually avoid it with a chuckle and a claim that he really needs to focus on studying. Which, like most things Christian says, is not entirely a lie. They believe it. Most importantly, he believes it.
The problem isn't attention. Christian loves attention. He thrives on it, even. It's the topic. They're talking about favorite animals, and he doesn't have one. He doesn't have a favorite color, either, or a favorite season. He doesn't know why he doesn't have these things, but he wants these things, because that's what most people have and they're normal and HE'S normal.
They pester him about it. Tell us! Tell us! Close the book for just a second, Christian, and tell us your favorite animal. Christian tries to wave off the question again. Says it's kind of childish, yeah? I mean. They're fifteen and sixteen year olds. Not preschoolers.
A kid in the back named Hugh says Christian is dodging the question. Christian blinks a few times, probably way too fast and a little twitchy. Then he smiles. He directs the question at Hugh, instead. Because Hugh wasn't really a part of the conversation at all. Hugh was a back of the class nobody. Not that Christian thought that, that would be rude, and he's not rude. It's just what Christian's peers say.
Hugh says his favorite animals are frogs. Christian says 'mine too', because that seems like the best way to respond. It's simple, it's affable, and it's a tally mark beside the objective of a success conversation.
Matters are complicated when Hugh asks what kind. Christian says all kinds. He's not picky. That makes Hugh laugh, which makes Christian's throat feel tight and his left pinky finger start tapping against the desk. Christian likes laugh tracks when they're on TV. This is different.
So, once again, Christian bounces the question back. Does Hugh have a specific, special kind of frog he likes? Hugh proudly claims to have a pet frog. A White Lipped Tree Frog. Very friendly, and smart too. The frog is apparently named Berry.
Christian suggests Hugh bring it to school sometime. He'd love to meet Berry. Class is dismissed, but Christian stays behind to talk with the teacher. Not unusual. He's a teacher's pet, or so some people say, although never to his face.
Christian asks his science teacher if they're ever going to do anything hands on. Get practical experience. Christian still isn't sure what he wants to do when he graduates, after all. He's thought about studying forensics, or maybe something with autopsies... But for that, well. It would really help if he could do a dissection, first.
Just to see if he could stomach it.
The teacher decides dissecting frogs is done in plenty of classrooms, and it's plenty informative. Christian smiles, and nods, and agrees. He's really, very good at that. A week later, Berry the pet White Lipped Tree Frog ends up with the other live frogs shipped in from a facility just out of state. Christian isn't sure if the teacher is the one to kill them beforehand, or if the students do it while the amphibians are stapled to a silver tray.
Christian is sick that day. Maybe he doesn't have a stomach for medical sciences after all...
#stabtxt#chris cross apple sauce#also how does chris justify this to himself. hes such an enigma. did the lord tell you to do All That
3 notes
·
View notes
Text
Ahead of the the 2024 US elections, the US intelligence community and law enforcement were on high alert and ready to share information—both among agencies and publicly—as foreign malign influence operations emerged. Tech giants like Microsoft similarly sprang into action, collaborating with government partners and publishing their own information about election-related disinformation campaigns. The speed and certainty with which authorities were able to pin these efforts on threat actors in Russia, China, and Iran was unprecedented. But researchers also caution that not all attributions are created equal.
At the Cyberwarcon security conference in Arlington, Virginia, today, researchers from the Atlantic Council’s Digital Forensic Research Lab are presenting initial findings on the role of attribution in the 2024 US elections. Their research compares the impact of quickly naming and shaming foreign influence actors to other recent US elections in which government attribution was far less common.
“We’re building on a project that we did back in 2020 where there was a lot more context of concern that the Trump administration was not being forthcoming about foreign attacks,” says Emerson Brooking, director of strategy and resident senior fellow for DFRLab. “In contrast to 2020, now there was an abundance of claims by the US government of influence operations being conducted by different adversaries. So in thinking through the policy of attribution, we wanted to look at the question of overcorrection.”
In the lead-up to the 2016 US presidential election, Russia’s extensive influence operations—which included hack-and-leak campaigns as well as strategic disinformation—caught the US government by surprise. Law enforcement and the intelligence community were largely aware of Russia's digital probing, but they didn't have an extreme sense of urgency, and the big picture of how such activity could impact public discourse hadn't yet come into view. After Russia's hack of the Democratic National Committee in June that year, it took four months for the US Office of the Director of National Intelligence and the Department of Homeland Security to publicly attribute the attack to the Kremlin. Some officials had said in the weeks following the incident that formal confirmation from the US government might never come.
Even in the highly politicized landscape that followed, federal, state, and local collaboration around election security expanded dramatically. By 2020, the researchers say, 33 of the 84 influence operation attributions they studied related to the 2020 US elections, or about 39 percent, came from US intelligence or federal sources. And this year, 40 of the 80 the group tracked came from the US government. DFRLabs resident fellow Dina Sadek notes, though, that one important factor in assessing the utility of US government attributions is the quality of the information provided. The substance and specificity of the information, she says, is important to how the public views the objectivity and credibility of the statement.
Specific information confirming that Russia had manufactured a video that purported to show ballots being destroyed in Bucks County, Pennsylvania was a high-quality, useful attribution, the researchers say, because it was direct, narrow in scope, and came very quickly to minimize speculation and doubt. Repeated statements from the Office of the Director of National Intelligence's Foreign Malign Influence Center warning very broadly and generally about Russian influence operations is an example of the type of attribution that can be less helpful, and even serve to amplify campaigns that otherwise might not register with the public at all.
Similarly, in the lead-up to the 2020 elections, the researchers point out, statements from the US government about Russia, China, and Iran playing a role in Black Lives Matter protests may have been mismatched to the moment because they didn't include details on the extent of the activity or the specific objectives of the actors.
Even with all of this in mind, though, the researchers note that there was valuable progress in the 2024 election cycle. But with a new Trump administration coming into the White House, such transparency could start to trend in a different direction.
“We don’t want to come across like rearranging deck chairs on the Titanic, because the state of affairs that was is not the state of affairs that will be,” Brooking says. “And from a public interest perspective I think we got a lot closer on disclosure in 2024.”
16 notes
·
View notes
Note
https://www.tumblr.com/penaltybox-gossip/782044023704748032/hi-im-the-anon-that-sent-the-ask-about-waiting
So I’m not the same anon. But I’m a law student.
And I would add a few things.
First, under criminal law, there is a fundamental principle called the presumption of innocence — meaning the accused must be considered innocent until proven guilty beyond a reasonable doubt. A vague text message, without more direct evidence of wrongdoing, does not satisfy this standard.
The statement could easily be interpreted as an attempt to avoid discrepancies that might make them look suspicious, even if they were innocent. In high-profile cases like this, especially involving young athletes under intense media scrutiny, individuals might coordinate to ensure consistent, accurate storytelling, not to hide guilt, but to protect themselves from misinterpretation.
Legally, circumstantial evidence like this must be approached very carefully. It can raise suspicion, but it cannot replace concrete proof of a criminal act or a conspiracy to lie about one.
Furthermore, the phrase is ambiguous. It does not specify what “thing” they were agreeing on. Without direct evidence showing they intended to fabricate events, the defense can argue that the message is consistent with innocent behavior driven by fear, confusion, and social pressure.
Therefore, this message alone cannot be used as definitive proof of guilt.
And there are several reasons why maintaining doubts is reasonable:
1.) Emotional reactions and public outrage cannot replace solid, tested evidence in a courtroom. It is not enough for an accusation to exist, it must be proven with strong, objective evidence.
2.) The alleged event happened in 2018. Delays in reporting or investigating can affect the reliability of memories, availability of witnesses, and preservation of evidence. Human memory naturally degrades over time, especially under trauma or stress, which can create honest but inaccurate recollections.
3.) Media coverage can heavily influence how cases are perceived before all facts are known. When a case becomes a public scandal, witnesses and even alleged victims might feel pressure to fit certain narratives. Similarly, accused individuals may feel pressured to defend themselves in specific ways, not necessarily because they are guilty, but because they fear automatic condemnation.
4.) If the case relies mostly on testimonies, group chats, and circumstantial evidence (instead of clear physical evidence like forensic results), it becomes harder to meet the standard of proof required for a criminal conviction. In a fair legal system, suspicion is not enough, there must be clear and convincing evidence.
5.) In events involving multiple people, group psychology can complicate the situation. Actions and statements that seem suspicious after the fact (like coordinating stories) could stem from panic, fear of being misunderstood, or fear of being blamed for things they didn’t do individually.
6.) In some cases, one party may genuinely believe an encounter was consensual while the other party experiences it differently. Miscommunication, intoxication, and different perceptions can happen. However, criminal guilt requires proof that the accused knowingly violated consent, not just that discomfort existed. In this case, according to tweets from a reporter familiar with the investigation, it has been suggested that the complainant did not explicitly say “no,” but rather appeared uncomfortable and did not verbally express her unwillingness at the time. While clear discomfort is serious and concerning, from a legal standpoint, proving intentional violation of consent is critical for a criminal conviction.
And i just want to add, that doubt is not disrespect toward the alleged victim; it is respect toward the legal principles that protect everyone’s rights. In cases like this, where emotional narratives are strong but direct proof of criminal intent is weaker, maintaining reasonable doubt is both fair and necessary to uphold justice.
It may seem cold or even harsh, but this commitment to careful doubt is what separates justice from injustice. A fair trial demands that we judge based on verified evidence, not on emotion or public pressure. Respecting reasonable doubt is the only way to ensure that every individual — whether victim or accused — receives true justice.
.
2 notes
·
View notes
Text
Hils Watches Oh No! Here Comes Trouble - Ep 12
Wow I can't believe I'm on the final episode already

Oh, wait, is that the dude who fell pre-credits in the first episode? That feels like forever ago

Wait, that was Pu Yiyong's grandad as a young man? And he survived that fall??? I'm so confused. Is this also a flashback telling the story of an earlier flashback? Because Pu Yiyong was not there at the end of the previous episode.

Aww Cao Guangyan wants to move into forensic medicine. I love that Pu Yiyong is subconsciously helping his friends figure out what they want to do with their lives even while he's questioning his own



God, this is so fucking sinister now you know who he really is

Yes, I won't mention that I've killed at least two and probably a lot more children

Okay, I know this is a supernatural drama so logic doesn't apply but cracking him over the head twice with a metal object would have killed him

I've just realised I've seen gifs from this scene, or a bts or something. So glad I'd forgotten about it until now because that's a pretty major spoiler. There's still 30 mins left so I assume magical plot stuff will happen but, fuck, Cao Guangyan's face

God, of course he has to 'die' so he can see his dad. I'm bawling now. Fuck.

Jesus fuck Cao Guangyan is screaming. This is horrible.

God he's got Pu Yiyong's art in his phone case I cannot

Gosh how long has he been in a coma for this time? His hair is so long

This poor woman. She's lost her husband, her father-in-law and now her son is in a coma for the second time

Aww that's why they call her One-per. She's in the 1% of people who fail the police entrance exam

God, I love them so much. Telling Pu Yiyong he has to wake up so he can finish his comic

Aww yay Cao Guangyan's dad finally opened a business that's a success

Sobbing at all the spirits he helped telling him to wake up. Also, I still lowkey ship them.
GAH THAT WAS SO GOOD! I mean I'm bawling my eyes out but sometimes a good drama be like that. Everyone who recced this to me was correct to do so
#hils watches#hils watches oh no! here comes trouble#hils watches twdramas#oh no! here comes trouble#twdrama
35 notes
·
View notes
Text
Object permanence

Picks and Shovels is a new, standalone technothriller starring Marty Hench, my two-fisted, hard-fighting, tech-scam-busting forensic accountant. You can pre-order it on my latest Kickstarter, which features a brilliant audiobook read by Wil Wheaton.

#20yrsago 1970s Homebrew Computer Club newsletter scans https://www.digibarn.com/collections/newsletters/homebrew/
#15yrsago Corporate developers abandon “underwater” property — why not individuals? https://memex.craphound.com/2010/01/25/corporate-developers-abandon-underwater-property-why-not-individuals/
#10yrsago San Francisco ponders letting luxury property developers take away symbolic “public spaces” https://socketsite.com/archives/2015/01/little-known-public-open-spaces-soon-history.html
#5yrsago Cheating term-paper-for-pay businesses recruited customers through subsidized on-campus parties https://www.edsurge.com/news/2020-01-23-how-the-contract-cheating-industry-has-gotten-more-aggressive-in-recruiting-students
#5yrsago The cum-ex scam stole $60b from European tax authorities: it’s monumentally boring, complicated, and very, very important https://www.nytimes.com/2020/01/23/business/cum-ex.html
#5yrsago Chicago PD’s predictive policing tool has been shut down after 8 years of catastrophically bad results https://twitter.com/sh4keer/status/1220470166355468288
#5yrsago The answer to the Clearview AI scandal is better privacy laws, not anti-scraping laws https://memex.craphound.com/2020/01/25/the-answer-to-the-clearview-ai-scandal-is-better-privacy-laws-not-anti-scraping-laws/
#5yrsago I reviewed William Gibson’s novel “Agency” for today’s LA Times https://www.latimes.com/entertainment-arts/books/story/2020-01-24/agency-william-gibson
#5yrsago Warner claims ownership over the numbers 36 and 50, and demonetizes Youtube videos that incorporate them https://www.dexerto.com/entertainment/annemunition-bizarre-copyright-strike-youtube-random-numbers-1317750/
#1yrago Tabs give me superpowers https://pluralistic.net/2024/01/25/today-in-tabs/#unfucked-rota

Check out my Kickstarter to pre-order copies of my next novel, Picks and Shovels!
9 notes
·
View notes