#Cloud Data Governance
Explore tagged Tumblr posts
Text
Unity Catalog: Unlocking Powerful Advanced Data Control in Databricks
Harness the power of Unity Catalog within Databricks and elevate your data governance to new heights. Our latest blog post, "Unity Catalog: Unlocking Advanced Data Control in Databricks," delves into the cutting-edge features
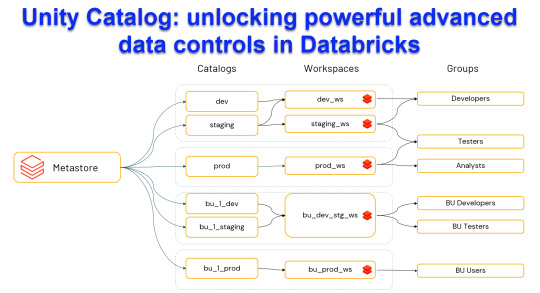
View On WordPress
#Advanced Data Security#Automated Data Lineage#Cloud Data Governance#Column Level Masking#Data Discovery and Cataloging#Data Ecosystem Security#Data Governance Solutions#Data Management Best Practices#Data Privacy Compliance#Databricks Data Control#Databricks Delta Sharing#Databricks Lakehouse Platform#Delta Lake Governance#External Data Locations#Managed Data Sources#Row Level Security#Schema Management Tools#Secure Data Sharing#Unity Catalog Databricks#Unity Catalog Features
0 notes
Text
#governanceoncloud #lean data governance
0 notes
Text
Eric Schmidt: AI misuse poses an ‘extreme risk’
New Post has been published on https://thedigitalinsider.com/eric-schmidt-ai-misuse-poses-an-extreme-risk/
Eric Schmidt: AI misuse poses an ‘extreme risk’
Eric Schmidt, former CEO of Google, has warned that AI misuse poses an “extreme risk” and could do catastrophic harm.
Speaking to BBC Radio 4’s Today programme, Schmidt cautioned that AI could be weaponised by extremists and “rogue states” such as North Korea, Iran, and Russia to “harm innocent people.”
Schmidt expressed concern that rapid AI advancements could be exploited to create weapons, including biological attacks. Highlighting the dangers, he said: “The real fears that I have are not the ones that most people talk about AI, I talk about extreme risk.”
Using a chilling analogy, Schmidt referenced the al-Qaeda leader responsible for the 9/11 attacks: “I’m always worried about the Osama bin Laden scenario, where you have some truly evil person who takes over some aspect of our modern life and uses it to harm innocent people.”
He emphasised the pace of AI development and its potential to be co-opted by nations or groups with malevolent intent.
“Think about North Korea, or Iran, or even Russia, who have some evil goal … they could misuse it and do real harm,” Schmidt warns.
Oversight without stifling innovation
Schmidt urged governments to closely monitor private tech companies pioneering AI research. While noting that tech leaders are generally aware of AI’s societal implications, they may make decisions based on different values from those of public officials.
“My experience with the tech leaders is that they do have an understanding of the impact they’re having, but they might make a different values judgement than the government would make.”
Schmidt also endorsed the export controls introduced under former US President Joe Biden last year to restrict the sale of advanced microchips. The measure is aimed at slowing the progress of geopolitical adversaries in AI research.
Global divisions around preventing AI misuse
The tech veteran was in Paris when he made his remarks, attending the AI Action Summit, a two-day event that wrapped up on Tuesday.
The summit, attended by 57 countries, saw the announcement of an agreement on “inclusive” AI development. Signatories included major players like China, India, the EU, and the African Union.
However, the UK and the US declined to sign the communique. The UK government said the agreement lacked “practical clarity” and failed to address critical “harder questions” surrounding national security.
Schmidt cautioned against excessive regulation that might hinder progress in this transformative field. This was echoed by US Vice-President JD Vance who warned that heavy-handed regulation “would kill a transformative industry just as it’s taking off”.
This reluctance to endorse sweeping international accords reflects diverging approaches to AI governance. The EU has championed a more restrictive framework for AI, prioritising consumer protections, while countries like the US and UK are opting for more agile and innovation-driven strategies.
Schmidt pointed to the consequences of Europe’s tight regulatory stance, predicting that the region would miss out on pioneering roles in AI.
“The AI revolution, which is the most important revolution in my opinion since electricity, is not going to be invented in Europe,” he remarked.
Prioritising national and global safety
Schmidt’s comments come against a backdrop of increasing scrutiny over AI’s dual-use potential—its ability to be used for both beneficial and harmful purposes.
From deepfakes to autonomous weapons, AI poses a bevy of risks if left without measures to guard against misuse. Leaders and experts, including Schmidt, are advocating for a balanced approach that fosters innovation while addressing these dangers head-on.
While international cooperation remains a complex and contentious issue, the overarching consensus is clear: without safeguards, AI’s evolution could have unintended – and potentially catastrophic – consequences.
(Photo by Guillaume Paumier under CC BY 3.0 license. Cropped to landscape from original version.)
See also: NEPC: AI sprint risks environmental catastrophe
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
#adversaries#agile#agreement#ai#ai & big data expo#ai action summit#AI development#ai governance#AI research#amp#approach#Artificial Intelligence#automation#autonomous#BBC#biden#Big Data#california#CEO#China#Cloud#Companies#comprehensive#conference#cyber#cyber security#data#deepfakes#development#Digital Transformation
6 notes
·
View notes
Text
trying to focus on my(online, untimed) final exam but my head is full of hiveswap. what the hell do jadebloods do after exile.
#ooc#what structure does the alternian government have? do they have physical records stored on some kind of bookhiveship? bookhivestation?#planet?#where do trials take place?#where does his honourable tyrrany come in#are alternian doccuments (off planet i mean) all based in the cloud?#and by the cloud i mean kept in physical servers that are accessed via colony/warships remotely#in my head im imagining a station where helmsmen are maintained and exchanged or stored. stored helms powering the empire's data servers#uuuuu#helmspa. not that i think it would be very spalike#but i do like to imagine helmsmen getting unplugged and bathed and rested every once in a while#washed up by their helmsmechanics#i imagine the mechanics socialize between ships but i also imagine most helmsmen are too drained to do much socialization#ANYWAY none of this is necessarily canon to foly's timeline im just brainstorming#i think a massive data storage space station would be cool#weapons development also. scienterrorists developing new helming technology
3 notes
·
View notes
Text
I think every computer user needs to read this because holy fucking shit this is fucking horrible.
So Windows has a new feature incoming called Recall where your computer will first, monitor everything you do with screenshots every couple of seconds and "process that" with an AI.
Hey, errrr, fuck no? This isn't merely because AI is really energy intensive to the point that it causes environmental damage. This is because it's basically surveilling what you are doing on your fucking desktop.
This AI is not going to be on your desktop, like all AI, it's going to be done on another server, "in the cloud" to be precise, so all those data and screenshot? They're going to go off to Microsoft. Microsoft are going to be monitoring what you do on your own computer.
Now of course Microsoft are going to be all "oooh, it's okay, we'll keep your data safe". They won't. Let me just remind you that evidence given over from Facebook has been used to prosecute a mother and daughter for an "illegal abortion", Microsoft will likely do the same.
And before someone goes "durrr, nuthin' to fear, nuthin to hide", let me remind you that you can be doing completely legal and righteous acts and still have the police on your arse. Are you an activist? Don't even need to be a hackivist, you can just be very vocal about something concerning and have the fucking police on your arse. They did this with environmental protesters in the UK. The culture war against transgender people looks likely to be heading in a direction wherein people looking for information on transgender people or help transitioning will be tracked down too. You have plenty to hide from the government, including your opinions and ideas.
Again, look into backing up your shit and switching to Linux Mint or Ubuntu to get away from Microsoft doing this shit.
42K notes
·
View notes
Text
Master Data Governance (MDG) on Cloud
PiLog Lean Data Governance is a subscription-based digital platform designed to manage various essential data sets, including materials, vendors, services, customers, and assets. This powerful platform offers a suite of tools and resources to help businesses establish effective governance practices, streamline Master data governance on cloud, and gain greater visibility and control over their critical business information.
1 note
·
View note
Text
Future-Proofing IT: Building a Technology Roadmap for 2030 and Beyond.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in A forward-thinking guide for senior IT leaders on building a technology roadmap for 2030 and beyond. Discover expert insights, real-world lessons, and actionable strategies to shape your future with confidence and clarity. In today’s fast-changing tech world, planning is not a luxury. It is a necessity for IT leaders. I have…
#AI In IT#business-IT alignment#CIO priorities 2030#cloud optimization#Cybersecurity Strategy#data-driven decision making#digital transformation leadership#emerging technology strategy#enterprise IT planning#FinOps#Future-proof IT#innovation management#IT budgeting#IT Governance#IT operating model#IT Strategy#News#Sanjay Kumar Mohindroo#Tech Leadership#technology roadmap
0 notes
Text

Master Data Governance - Effective Procedures for Enhanced Outcomes
Optimize data governance to drive business success. Learn essential steps and industry best practices to enhance your data management strategy
0 notes
Text
Best Strategies to Protect Your Data Privacy and Security in the Cloud?
In today’s digital world, businesses are rapidly migrating to the cloud to streamline operations, reduce costs, and enhance scalability. However, with the increasing adoption of cloud computing comes a crucial challenge — ensuring data privacy and security in the cloud.
youtube
Cyber threats, data breaches, and compliance failures can cost businesses millions, tarnishing reputations and leading to severe legal repercussions. So, how can organizations safeguard their cloud-stored data effectively? Let’s explore the best cloud security practices and actionable strategies you can implement to secure sensitive information.
1. Implement Strong Data Encryption
Encryption is a fundamental pillar of cloud security. By encrypting data at rest, in transit, and during processing, businesses can prevent unauthorized access. Using Advanced Encryption Standards (AES-256) and robust key management practices ensures that even if cybercriminals intercept data, they won’t be able to decipher it.
2. Multi-Factor Authentication (MFA) for Enhanced Access Control
Many data breaches occur due to weak or compromised passwords. Implementing multi-factor authentication (MFA) ensures that only authorized personnel can access sensitive data. Biometric authentication, OTP-based logins, and smart token verification add extra layers of security to cloud platforms.
3. Regular Security Audits & Compliance Adherence
Following ISO 27001, GDPR, HIPAA, and SOC 2 standards ensures cloud security compliance. Conducting regular penetration testing and vulnerability assessments helps identify and fix security loopholes before hackers exploit them.
4. Implement Zero Trust Security Model
Adopting a Zero Trust Architecture (ZTA) ensures that every access request is verified, regardless of its origin. This model enforces strict access policies, continuously authenticating users and devices before granting permissions.
5. Secure API Endpoints & Cloud Applications
Cloud services heavily rely on APIs, making them a prime target for cyber threats. Securing APIs with OAuth, OpenID Connect, and API gateways helps prevent unauthorized data exposure and API abuse.
6. Data Backup & Disaster Recovery Plans
Data loss due to cyberattacks or cloud failures can cripple businesses. Implementing automated cloud backups, disaster recovery solutions, and redundancy strategies ensures seamless data restoration during emergencies.
7. Train Employees on Cloud Security Awareness
Human error remains one of the biggest cybersecurity risks. Conducting regular security awareness training helps employees recognize phishing attacks, suspicious activities, and best practices for maintaining cloud data privacy.
Watch the Full Expert Guide on Cloud Security
For a comprehensive breakdown of cloud data security strategies, watch this insightful video: How Can You Ensure Data Privacy and Security in the Cloud?
This video dives deeper into the latest security trends, risk mitigation techniques, and best practices to keep your cloud data safe. Don’t miss out — stay ahead in cyber security!
Final Thoughts

If you found this article valuable, share it with your network and let’s make cloud security a top priority! For more expert insights, be sure to subscribe to PiLog Group’s YouTube channel and stay updated with the latest in cloud security and data governance.
1 note
·
View note
Text
Is Your Data Storage Strategy AI-Ready?
New Post has been published on https://thedigitalinsider.com/is-your-data-storage-strategy-ai-ready/
Is Your Data Storage Strategy AI-Ready?


The adoption of AI has caused an increased need for proper data governance, and companies are now under pressure to ensure data maturity. Globally, many companies are either using or exploring AI, with over 82% actively leveraging or considering AI for business operations. Yet, according to Gartner only 14% of cyber leaders can balance maximizing the efficient use of their data and securing their data to hit business objectives.
As more businesses rush to utilize AI, they need to ensure they are operating at peak data maturity with a proper framework to handle the increasing amount of critical data they are managing. By leveraging a data maturity model framework, organizations can identify the most effective ways to optimize data usage, helping pinpoint gaps in security and foster greater data efficiency. As part of this framework, organizations also need a mature data management strategy.
One of the most overlooked parts of a mature data management strategy is having the proper storage requirements to backup and store critical data. Businesses face many threats when it comes to their data security, and proper storage to handle AI workloads may be the only way to prevent AI-generated data from being lost or tampered with due to ransomware or another disaster. Your business may be AI-capable, but is your storage infrastructure AI-ready?
Why Storage Has to Be Involved in the AI Conversation
There are several reasons why proper storage is essential for data created and consumed by AI— businesses need to ensure data remains easily accessible, is secure against evolving threats, can be recovered in the case of a disaster, and must be optimized for AI workloads.
Accessibility is important because developers must be able to quickly and efficiently find and leverage data to train other AI algorithms. Most of the time this type of data is considered “mission critical” and can be the most valuable to business operations. Having this type of data readily available is key to ensuring streamlined processes when it matters most.
This data also needs to have the highest level of security while it is being stored. Given that 96% of ransomware attacks now target backup data, storage needs to be ransomware-proof and able to withstand any downtime or outage an organization may face. Backups are primary targets for attackers because they render companies unable to restore their data, making it more likely that they will pay the ransom to retrieve critical data. In the meantime, businesses could be left defenseless and face extended periods of IT outages if their “mission-critical” data is not accessible. This could cause both reputational and monetary loss that would be devastating for shareholders, customers, and employees alike.
Cybersecurity attacks are not the only reason storage may be lost or manipulated. Production data, or the data used in a business’s daily operations, should always be treated as though it was destroyed or corrupted. Therefore, a golden recovery copy, or a clean, reliable, and isolated copy of critical data is mandatory. Accidental deletion, overwriting data, or any other kind of mistake caused by human error can compromise your data. Software and hardware failures such as corruption or viruses can also put your data at risk, especially if your software and hardware do not have the most recent updates. Lastly, environmental factors such as power outages, floods, and extreme weather are all good reasons to ensure your backup data can be recovered.
What’s more, AI tools can produce an excessive amount of data at an exponential rate, and traditional storage architectures may not be able to keep up with the amount of data needed to be stored. Therefore, storage for AI must be equipped to handle massive workloads efficiently. Using scalable and secure data storage, such as tiered storage solutions, will present optimal capabilities so data is being monitored and saved.
The Best Storage of AI Data (Without Breaking the Bank)
Tiered backup storage ensures that vital data is quickly accessible and is one of the most cost-effective solutions. It allows for data retention, permitting data to be accessed and reused at any time. Tiered storage and backups organize data based on its importance and frequency of access. High-priority data goes on fast, expensive storage like SSDs, while less critical data is stored on cheaper, slower media like HDDs or cloud storage. Specifically, AI data should be stored on tier 0 or tier 1 given the above requirements. Tier 0 is high-speed storage for mission-critical data with NVMe media types and all-flash storage arrays. Tier 1 is high-performance storage for frequently accessed data with SSDs and hybrid Flash storage media types.
Taking it a step further, backing up the data housed in tiered storage as often as possible will allow for quick access in the face of a disaster, such as human error or malicious alteration. Ensuring copies of backup data stored in multiple locations, with several types of encryptions, and on various media types is the only way to be sure backups are secure.
When choosing a ransomware-proof backup and storage vendor, it is important to ensure you are selecting immutable storage that can withstand any kind of disaster that could put your data at risk. It’s important to note that not all immutable storage delivers on this agreement. If ‘immutable’ data can be overwritten by a backup or storage admin, a vendor, or an attacker, then it is NOT a truly immutable storage solution. Understanding the core concept of true immutability will help separate secure backup systems from empty vendor claims.
These five requirements help define a backup storage environment that delivers immutability:
S3 Object Storage: A fully documented, open standard with native immutability that enables independent penetration testing
Zero Time to Immutability: Backup data must be immutable the moment it is written
Zero Access to Destructive Actions: No administrator—internal or external—should be able to modify, delete, or reset immutable data.
Segmentation of Backup Software and Storage: Backup software and backup storage must be physically isolated to prevent compromised credentials from being used to alter or destroy data, and to provide resilience against other disasters.
Hardware Form Factor: A dedicated appliance isolates immutable storage from virtualized attack surfaces and should remove all risks during setup, updates, and maintenance.
By meeting these requirements, organizations can assure immutability and thereby ensure that whatever happens—ransomware, insider threats, or credential breaches—backup data remains protected and recoverable.
As AI becomes a consistent tool for businesses, they need to adopt and identify better data management and infrastructure to ensure data maturity. The answer to this may lie in tiered storage and backups as the best way to secure the excessive amounts of data created and trained by AI and allow for the ability to quickly access and secure this critical and expansive data.
#Accessibility#admin#adoption#agreement#ai#AI data governance#ai tools#Algorithms#Arrays#attackers#backup#backups#bank#Business#Cloud#cloud storage#Companies#compromise#credential#credentials#cyber#cybersecurity#data#Data Governance#Data Management#data security#data storage#data usage#delete#developers
0 notes
Text
Data Management Trends for 2025
The data landscape is constantly evolving, driven by technological advancements and changing business needs. As we move into 2025, several key trends are shaping the future of data management. 1. AI-Powered Data Management Automated Data Processes: AI-driven automation will streamline tasks like data cleaning, classification, and governance. Enhanced Data Insights: AI-powered analytics will…
0 notes
Text
Unlock the Power of Azure AI: Dive into Our Latest Blog on Essential Computing Power!

Curious about what drives today’s AI breakthroughs? From autonomous vehicles to smart assistants, it's all about robust computing power. ECF Data’s latest blog, "IT Insights: Essential Computing Power for Azure AI," reveals how Azure AI and Azure Compute Services are at the forefront of these advancements.
Discover how Microsoft’s cutting-edge tools empower researchers and businesses to push the boundaries of AI. Whether you're a tech enthusiast or a business leader, this is your guide to understanding the backbone of modern AI technology.
Ready to explore? Click here to read the full blog and see how Azure is shaping the future of AI!
LET'S CONNECT
#Azure AI#Azure compute Services#Generative AI#Hybrid Cloud#AI Infrastructure#Data Governance#Cloud Migration#azure services#cyber security#azure ai services#it services in las vegas#usa#ai productivity tools#las vegas nevada#nevada#it services new york#managed service provider
1 note
·
View note
Text
Master Data Management Solution | MDM Tools | Master Data Record Manager
PiLog Master Data Record Manager (MDRM) is a powerful MDM solution, which makes it easy to create and manage multi-site, multi-language Master Data Records.
#Master Data Management Solutions#Cloud Master Data Management Solutions#Master Data Record Management Solutions#Master Data Solutions#Master Data Governance
0 notes
Text

Ensuring data quality and completeness is fundamental to effective data governance, which helps maintain accurate, reliable, and up-to-date information across the organization. By implementing clear data standards, policies, and procedures, organizations can systematically manage data to minimize errors and inconsistencies.
As data scales rapidly in cloud environments, strong governance is crucial for maintaining accuracy and ensuring proper integration from diverse sources, thereby enhancing analytics and decision-making. Adhering to governance policies also safeguards data security and privacy, ensuring compliance with regulatory requirements and protecting sensitive information in the cloud.
Explore our blog to dive deeper into Data Governance practices tailored for cloud-native environments.
0 notes
Text
How to Use Telemetry Pipelines to Maintain Application Performance.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Optimize application performance with telemetry pipelines—enhance observability, reduce costs, and ensure security with efficient data processing. 🚀 Discover how telemetry pipelines optimize application performance by streamlining observability, enhancing security, and reducing costs. Learn key strategies and best…
#AI-powered Observability#Anonymization#Application Performance#Cloud Computing#Cost Optimization#Cybersecurity#Data Aggregation#Data Filtering#Data Normalization#Data Processing#Data Retention Policies#Debugging Techniques#DevOps#digital transformation#Edge Telemetry Processing#Encryption#GDPR#HIPAA#Incident Management#IT Governance#Latency Optimization#Logging#Machine Learning in Observability#Metrics#Monitoring#News#Observability#Real-Time Alerts#Regulatory Compliance#Sanjay Kumar Mohindroo
0 notes
Text
How Do Lean Data Governance and ISO Standards improve Cloud Data Management ?
In today’s fast-evolving digital landscape, organizations are increasingly relying on cloud data management to store, process, and analyze massive volumes of information. However, without a structured data governance framework, companies risk poor data quality, security breaches, and non-compliance with industry regulations. This is where Lean Data Governance and ISO Standards come into play, offering a strategic approach to optimizing data management while ensuring compliance and efficiency.
youtube
The Importance of Lean Data Governance in Cloud Management
Lean Data Governance focuses on minimizing redundancies, improving data accuracy, and fostering a culture of accountability. Unlike traditional data governance models that can be rigid and cumbersome, Lean Data Governance aligns with agile methodologies, making it adaptable to cloud environments.
Some key benefits of Lean Data Governance include:
Enhanced Data Quality: Ensuring accurate, complete, and consistent data across cloud platforms.
Improved Compliance: Adhering to ISO standards, GDPR, and other regulatory frameworks.
Optimized Cost Efficiency: Reducing storage waste and improving cloud resource utilization.
Faster Decision-Making: Providing high-quality data for AI, analytics, and business intelligence.
Role of ISO Standards in Cloud Data Management
ISO standards provide globally recognized guidelines to enhance data security, privacy, and governance in the cloud. Some essential ISO standards for cloud data management include:
ISO/IEC 27001: Information security management system (ISMS) for safeguarding cloud data.
ISO/IEC 38505–1: Governance of data for cloud-based applications.
ISO/IEC 8000: Ensuring high-quality, accurate, and reliable data.
By implementing these standards, organizations can establish trust, mitigate risks, and align their data management strategies with industry best practices.
How Lean Data Governance & ISO Standards Work Together
Combining Lean Data Governance with ISO standards creates a powerful synergy that optimizes cloud data management. Lean principles streamline data operations, while ISO compliance ensures security, consistency, and regulatory adherence. This integrated approach empowers businesses to:
Eliminate data silos and inconsistencies.
Strengthen cybersecurity measures against potential threats.
Improve operational efficiency and scalability in cloud environments.
Learn More: Watch the Full Video
This video breaks down the core principles of Lean Data Governance and ISO Standards, offering real-world use cases and actionable insights to help organizations refine their cloud data management strategies.

Final Thoughts
As cloud adoption continues to grow, organizations must prioritize Lean Data Governance and ISO Standards to ensure seamless data management. By implementing these best practices, businesses can achieve greater data quality, security, and compliance, paving the way for long-term success in the digital era.
Stay ahead of the curve by adopting Lean Data Governance & ISO Standards today!
For more expert insights, don’t forget to watch the full video: Click Here and subscribe to our PiLog Group YouTube Channel for more valuable content!
#Lean Data Governance#Data Cloud#Cloud Data Management#iso standard#youtube#piloggroup#data management solutions#big data#iso certification#data governance#data analytics#data scientist#Youtube
0 notes